SQL (structured query language) injection attack defensive system and defensive method based on grammar transformation
A technology of injection attack and defense system, applied in the field of network security, it can solve the problems of difficulty in establishing normal SQL statements and SQL injection attacks, large and diverse data volume, high false positive rate and false negative rate, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
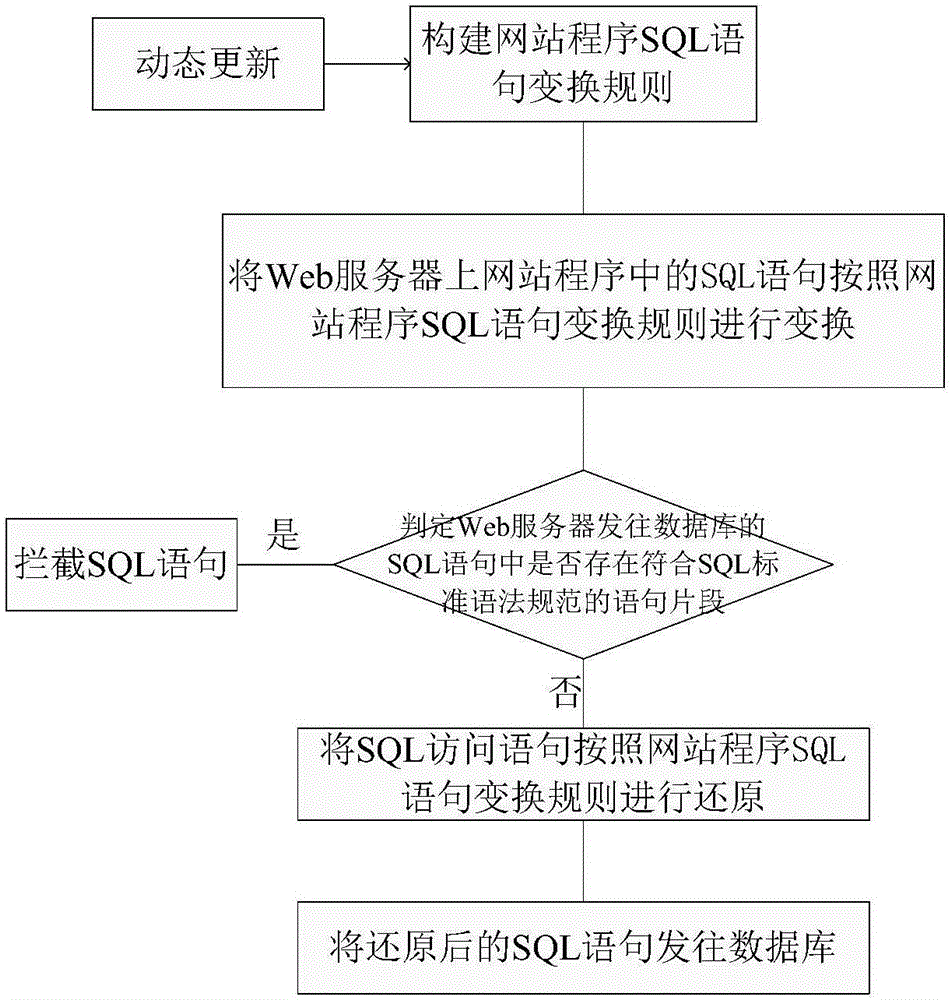
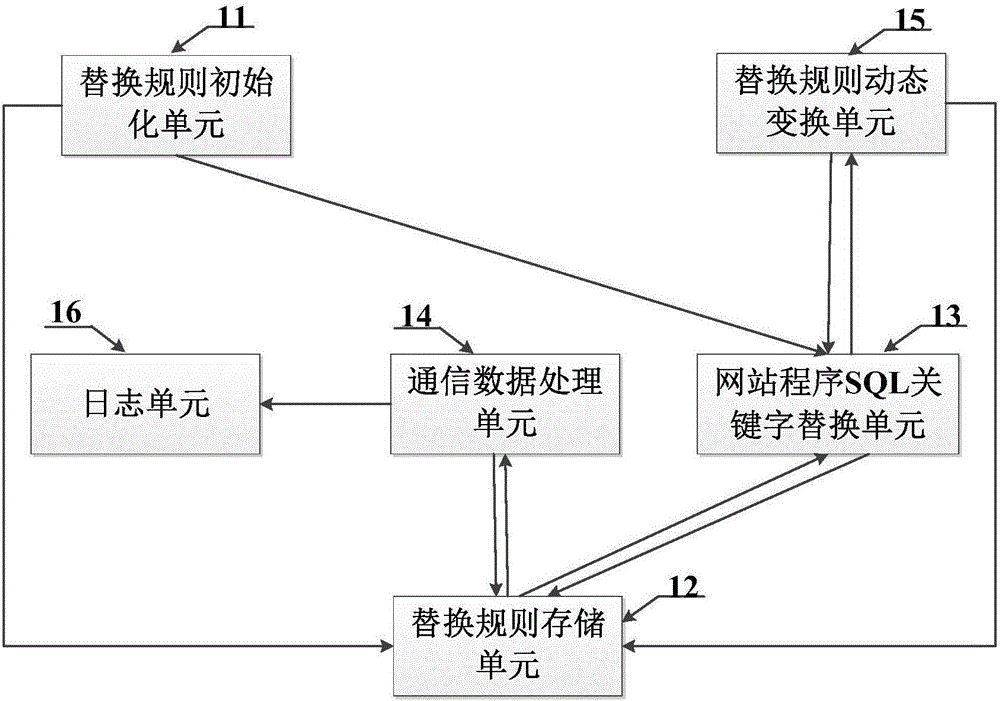
[0079] Preferred implementation scheme: SQL injection attack defense scheme based on SQL keyword replacement and grammatical analysis.
[0080] Firstly, on the basis of the aforementioned SQL injection attack defense concept based on syntax transformation, the basic principle of this SQL injection attack defense scheme based on SQL keyword replacement and syntax analysis is described in detail.
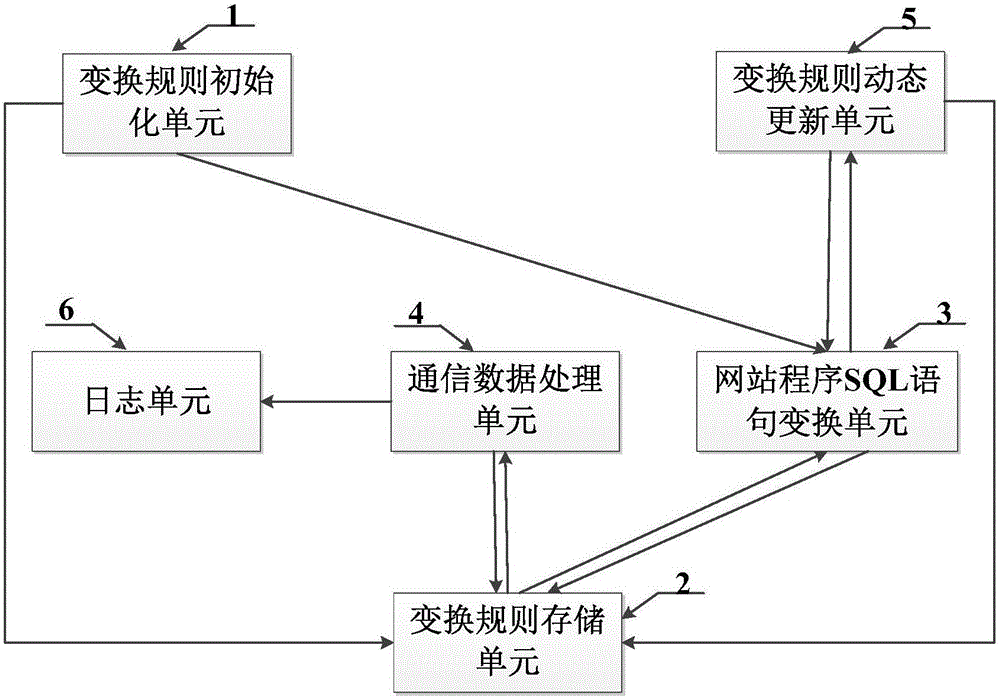
[0081] First, technicians determine all or common SQL keywords (including select, where, union, and, or, etc.) used to operate the database, and input them through the user configuration module to form a SQL keyword set, which is recorded as set A, set A Each element in corresponds to an SQL keyword. Then construct a set B corresponding to one of them according to the set A, and correspond to each element in the set A with a character string that has no specific meaning and is not common (the string is randomly generated, guaranteed not to be repeated, and does not include keys relate...
Embodiment 1
[0104]Embodiment 1 is an example of a normal user operating the database. Assume that the SQL query statement for login verification in a website program is select*from users where name='username entered by the user' and pw='password entered by the user'; the correct user name is admin, and the correct password is password, Username admin and password password are stored in the database. According to the user-configured SQL keyword set A {..., select, where, and, ...}, the constructed website program SQL keyword replacement rule set C is {..., select→string h, where→string i , and→string j, ...} (here, for the convenience of description, the replacement string is also briefly described). First, replace the content of the website program, and replace the SQL keywords written in the website program for operating the database according to the corresponding rules of set B, that is, replace select with the string h, where with the string i, and with into a string j. Assuming tha...
Embodiment 2
[0106] Embodiment 2 gives an example in which the user inputs the same character string as the SQL keyword, but it is only used as access data and belongs to a normal user operation database example. Assume that the SQL query statement for login verification in a website program is select*from users where name='user name entered by the user' and pw='password entered by the user'; the correct user name is select, and the correct password is password, The user name select and password password are stored in the database; according to the user-configured SQL keyword set A {..., select, where, and, ...}, the constructed website program SQL keyword replacement rule set B is {..., select→string h, where→string i, and→string j, ...} (here is a brief description of the replaced irregular string for the convenience of description); first, replace the content of the website program, Replace the SQL keywords used to operate the database in the website program according to the correspondi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com