WebShell detection method and system
A detection method and remote detection technology, applied in the field of Internet security, can solve the problems such as the inability to detect the WebShell, and achieve the effects of improving the detection rate and detection efficiency, improving the accuracy rate, and reducing the false negative rate and false positive rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
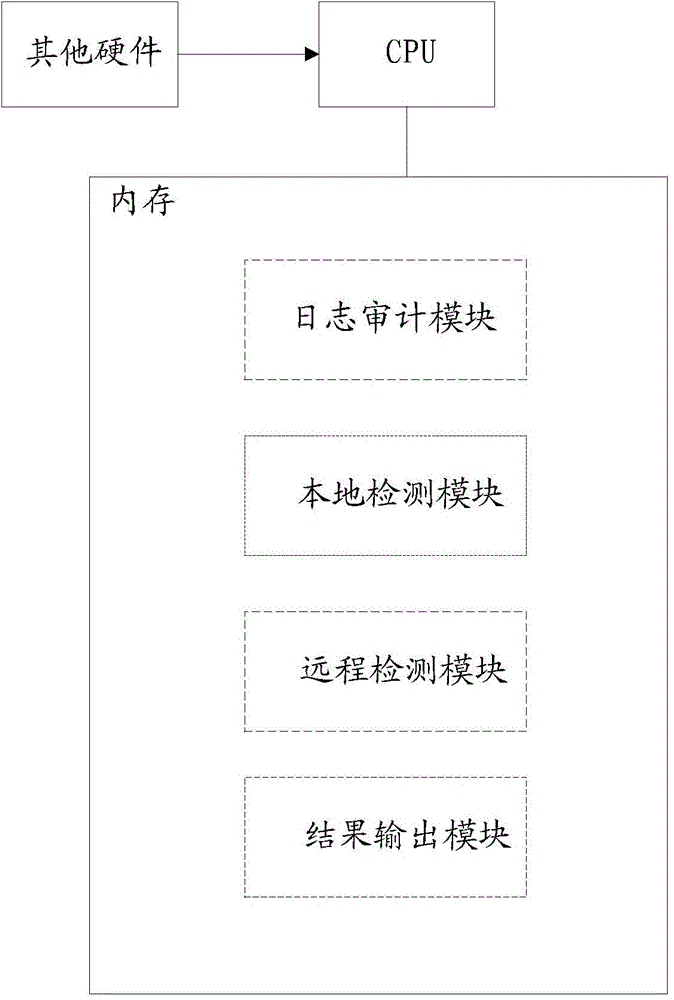
[0034] Combine below figure 1 and figure 2 The technical scheme of the present invention is further described in detail.
[0035] The present invention pre-sets suspicious WebShell path library, local detection fingerprint library and remote detection fingerprint library as basic basis for detection. The following describes how the present invention implements a comprehensive WebShell detection process in combination with network security detection technology.
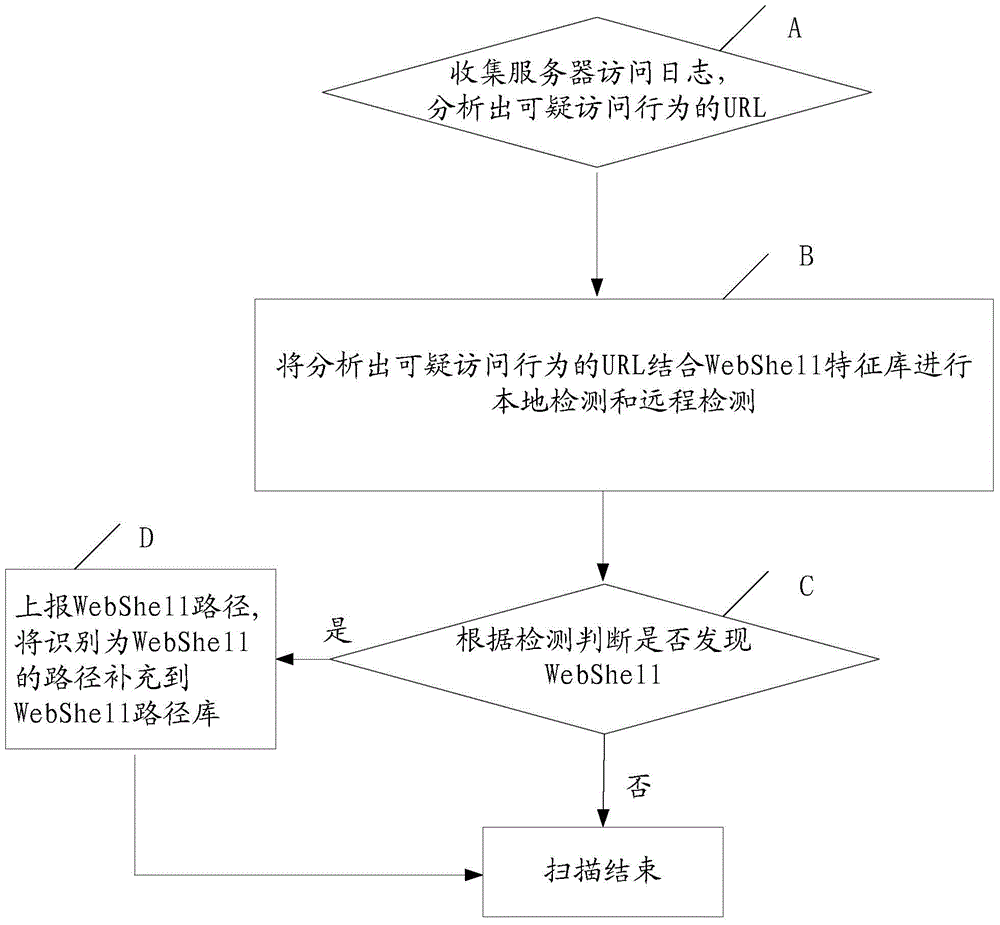
[0036] figure 1 It is a flow chart of a WebShell detection method in the present invention. In a preferred embodiment, the method of the present invention is specifically as follows:
[0037] A. Collect server access logs and analyze URLs with suspicious access behaviors.
[0038] Specifically, log in to the server through SSH to obtain access logs generated by web middleware (apache, tomcat, iis, etc. software). The access logs record URLs and parameters for each user visit. Check and find out the pages most su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com