Intelligent Trojan horse detecting device based on behavior features in network flows and method thereof
A network traffic and detection method technology, applied in the direction of electrical components, transmission systems, etc., to achieve the effects of low false negative rate and false negative rate, high detection accuracy and high detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
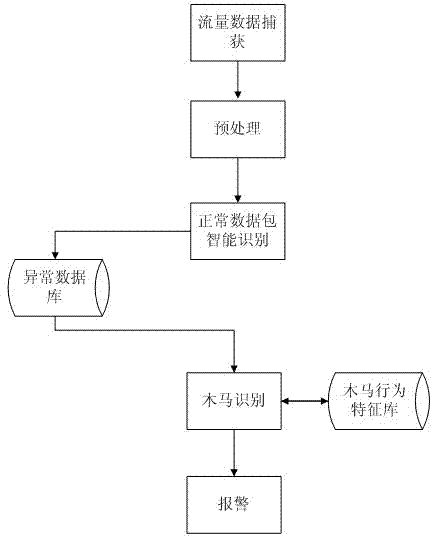
[0054] Embodiments of Flow Data Capture Devices
[0055] At present, the mainstream data packet capture tools include Libpcap, Winpcap, etc. Different platforms can choose different capture tools, for example, Winpcap can be selected under the Windows platform, and Libpcap can be selected under the Unix platform. This example uses Winpcap, a packet capture tool. Winpcap is composed of three modules: NPF, packet.dll and wpcap.dll. NPF is the packet capture driver, packet.dll is the underlying dynamic link library and wpcap.dll is the High-level dynamic link library. Because the Trojans are basically transmitted based on the TCP protocol and the UDP protocol, protocol-based filtering is required here, and only TCP and UDP packets are captured. No matter which capture tool is selected, it is within the protection scope of this patent.
[0056] Embodiment of the pretreatment device
[0057] This embodiment is used to convert the TCP / UDP data packets obtained by the flow data ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com