Attack defense method, device, Internet of Things device, and computer-readable storage medium
A technology of Internet of Things equipment and computers, applied in the field of Internet of Things, can solve problems such as poor defense capabilities, and achieve the effect of improving the ability to deal with attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
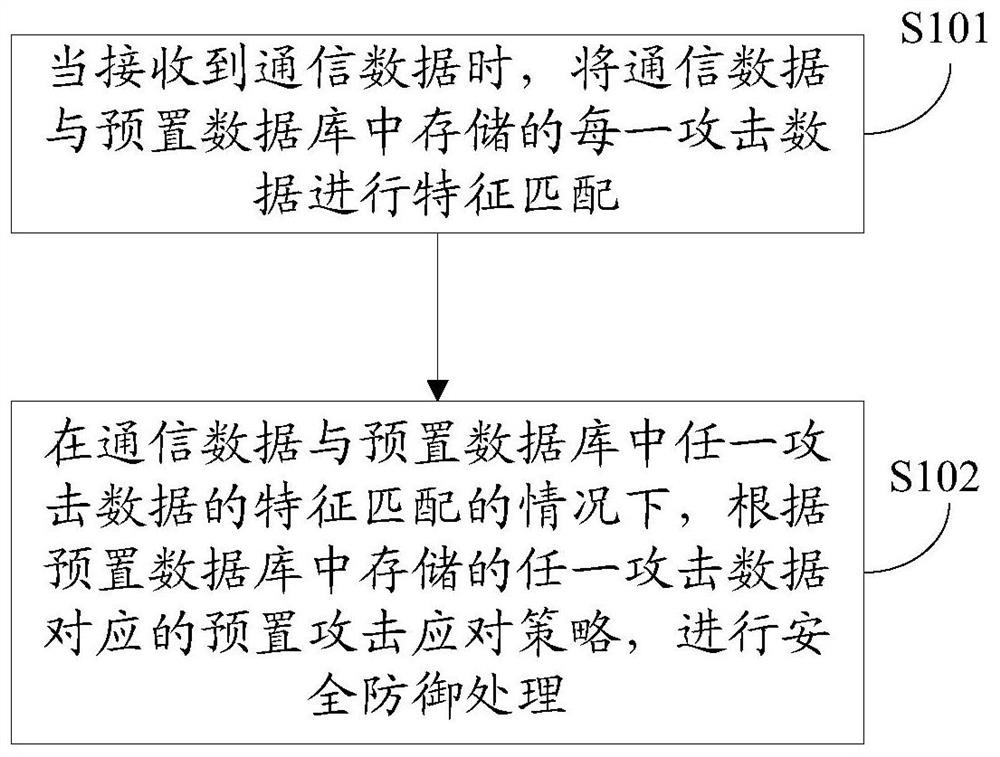
[0050] In the first embodiment of the present invention, an attack defense method is applied to Internet of Things devices, such as figure 1 As shown, the method includes the following specific steps:
[0051] Step S101, when the communication data is received, perform feature matching on the communication data and each attack data stored in the preset database.
[0052] In this embodiment, the number of preset databases is not specifically limited, and the number of preset databases is one or more.
[0053] In this embodiment, the way of matching the communication data with each attack data stored in the preset database includes but not limited to: according to the LDA (Linear Discriminant Analysis, linear discriminant analysis) algorithm, the communication data and the preset Each attack data stored in the configuration database is used for feature matching.
[0054]By performing feature matching on the communication data and each attack data stored in the preset database,...
no. 2 example
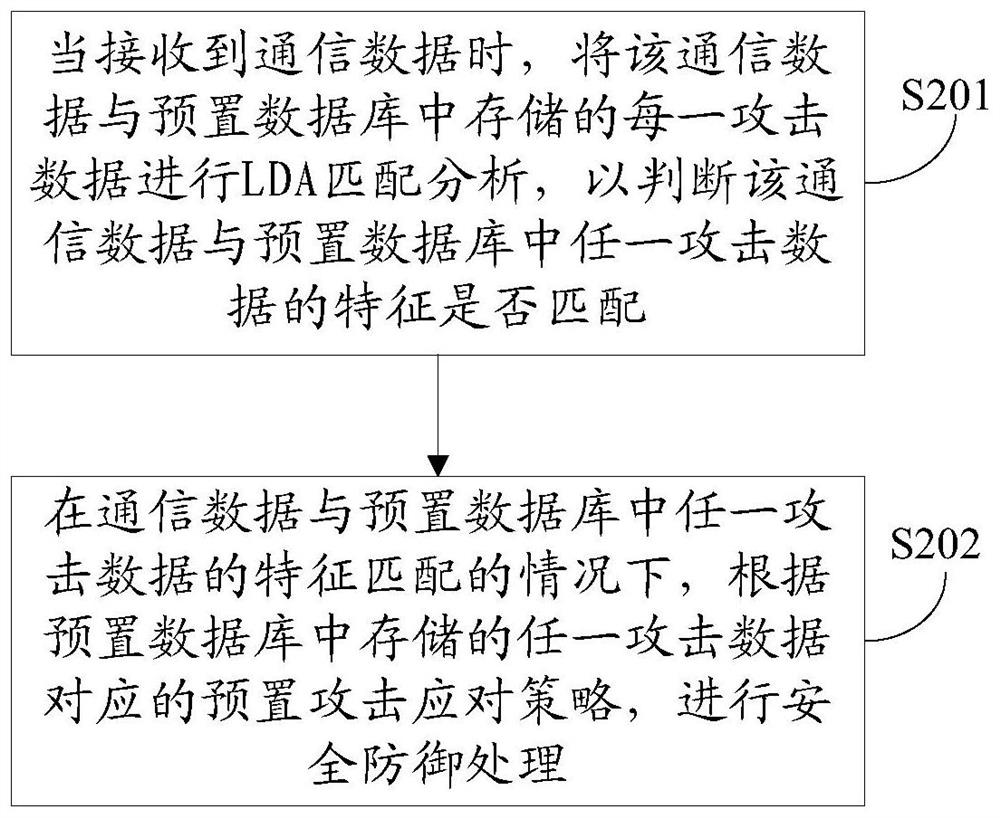
[0062] In the second embodiment of the present invention, an attack defense method is applied to IoT devices, such as figure 2 As shown, the method includes the following specific steps:
[0063] Step S201, when the communication data is received, LDA matching analysis is performed on the communication data and each attack data stored in the preset database, so as to determine whether the characteristics of the communication data match any attack data in the preset database.
[0064] LDA is used to classify and match the communication data with each attack data stored in the preset database. The degree of coupling between classifications is low, and the degree of aggregation within the classification is high. It can effectively and quickly identify whether the communication data is attack data, and improve the accuracy of attack data. Recognition efficiency and recognition speed.
[0065] Step S202, when the communication data matches the characteristics of any attack data i...
no. 3 example
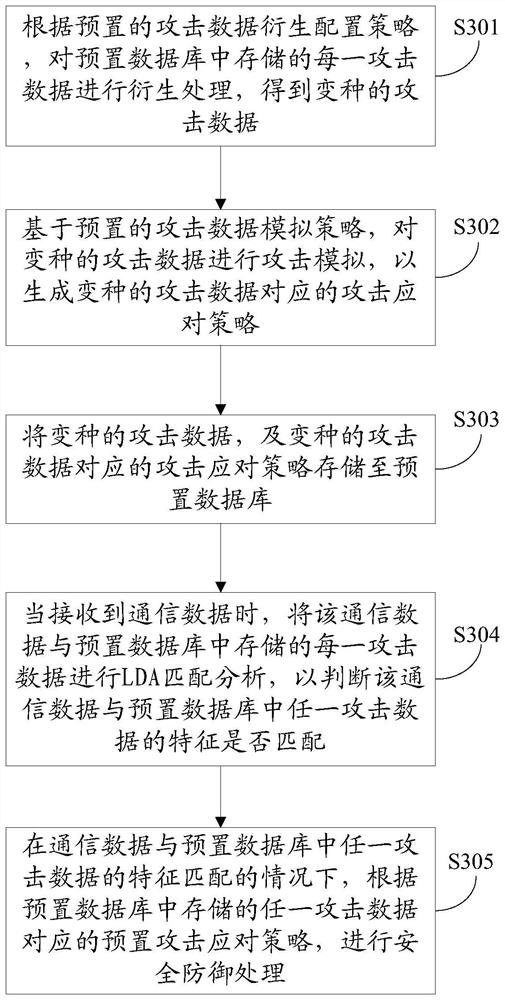
[0067] In the third embodiment of the present invention, an attack defense method is applied to IoT devices, such as image 3 As shown, the method includes the following specific steps:
[0068] Step S304, when the communication data is received, perform LDA matching analysis on the communication data and each attack data stored in the preset database, so as to judge whether the communication data matches the characteristics of any attack data in the preset database.
[0069] Step S305, when the communication data matches the characteristics of any attack data in the preset database, perform security defense processing according to the preset attack response strategy corresponding to any attack data stored in the preset database.
[0070] In this embodiment, the attack defense method further includes:
[0071] Step S301, according to the preset attack data derivation configuration strategy, derivation processing is performed on each attack data stored in the preset database t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com