Indirect distributed denial of service attack defense method and system based on Web agency
A distributed denial and indirect technology, applied in the field of network communication, can solve the problem that the victim server cannot establish a cooperative relationship with the server, the attack behavior is difficult to be discovered and filtered by the DDoS defense system, and the server is difficult to rely on the intermediate Web proxy security settings to be attacked, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The present invention will be described in detail below with reference to the accompanying drawings.
[0061] The present invention adopts following several technologies:
[0062] 1. Extract the spatio-temporal locality of the network flow
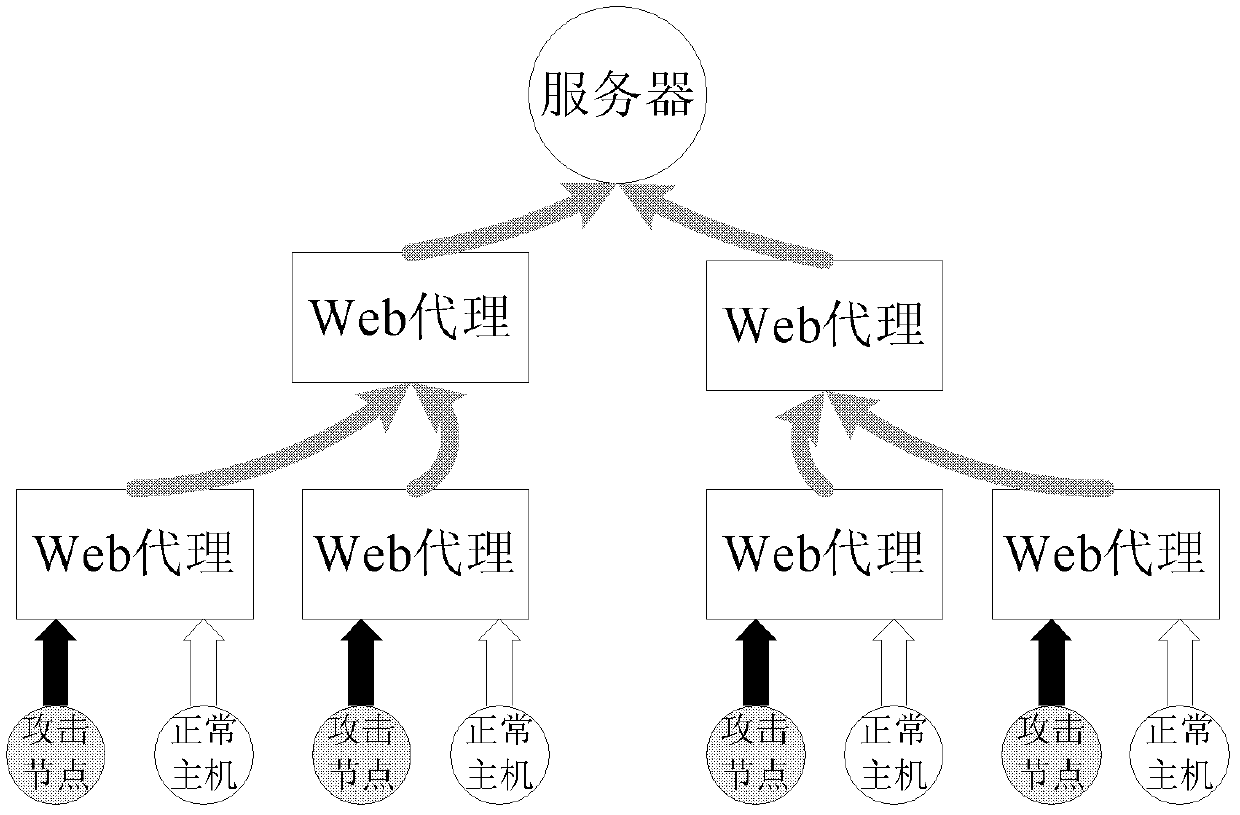
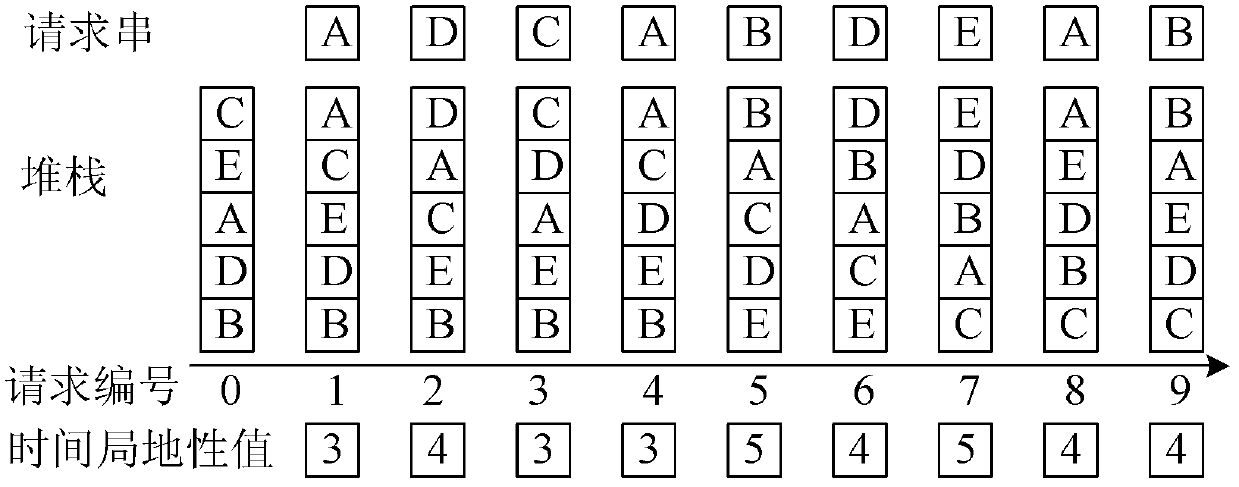
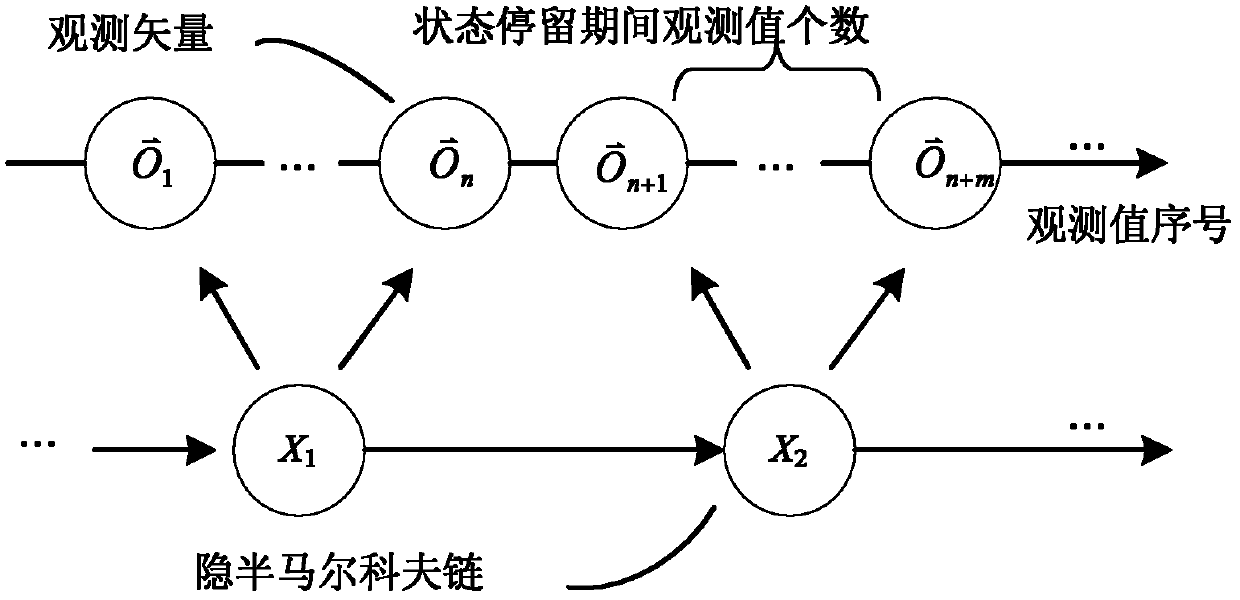
[0063]The network flow sent by a given Web proxy to the server is called proxy-to-server (P2S), and P2S is the external manifestation of the interaction between a Web proxy and the server. Through the mining and analysis of P2S, the potential behavior characteristics of Web proxy can be found, which can provide reference for attack defense.
[0064] In the present invention, the observable structural properties of P2S need to meet two requirements: (1) it can characterize the essential properties of P2S, and has nothing to do with the Web content / URL on the server; (2) it can consume the target in the attack flow The server has previously extracted this attribute, enabling early detection. For this reason, the present invention u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com