Attack response method and system
A technology of coping methods and objects, applied in the field of coping, can solve the problem that there is no way to ensure the smooth application of products, and achieve the effect of preventing attacks and receiving
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
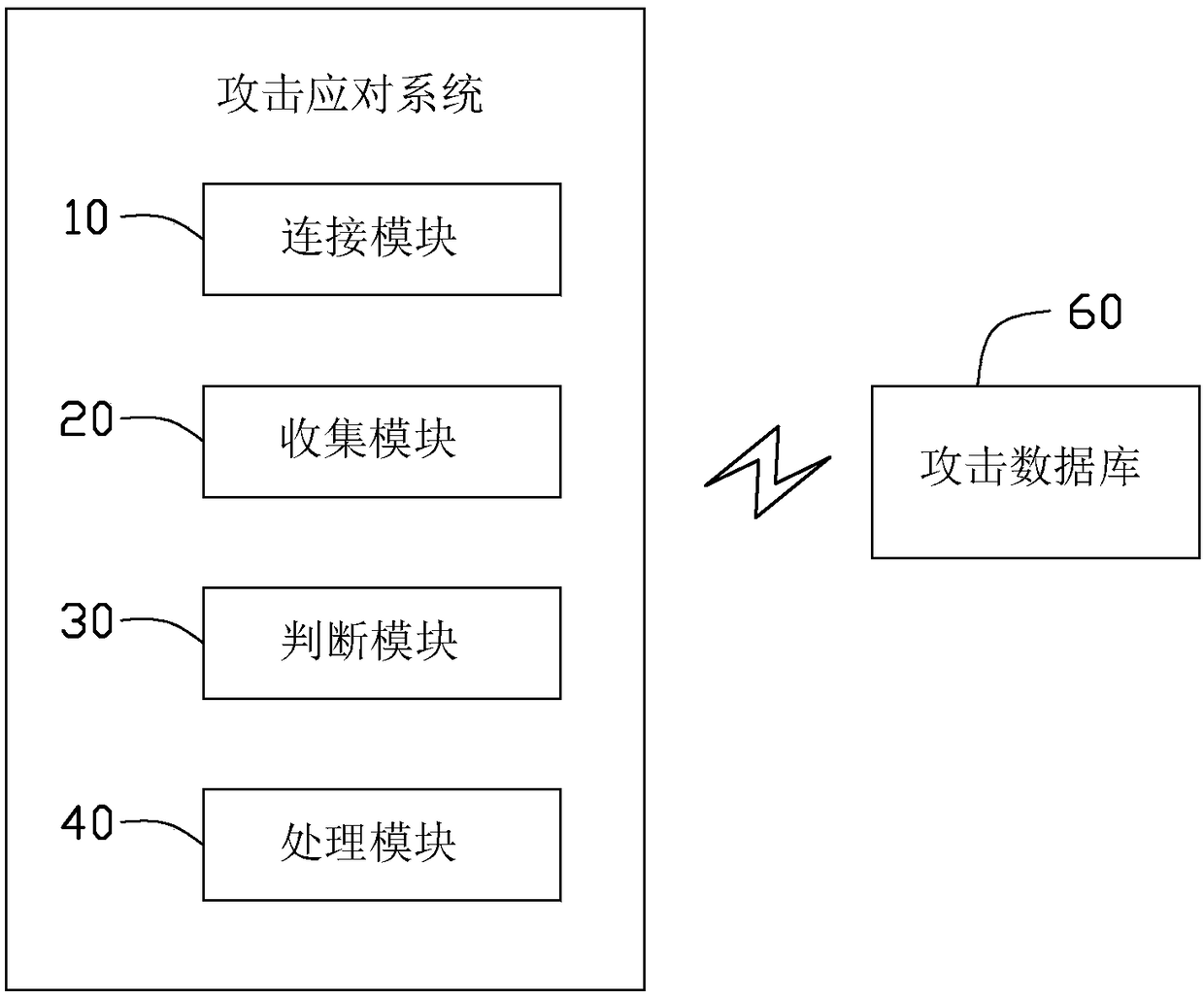
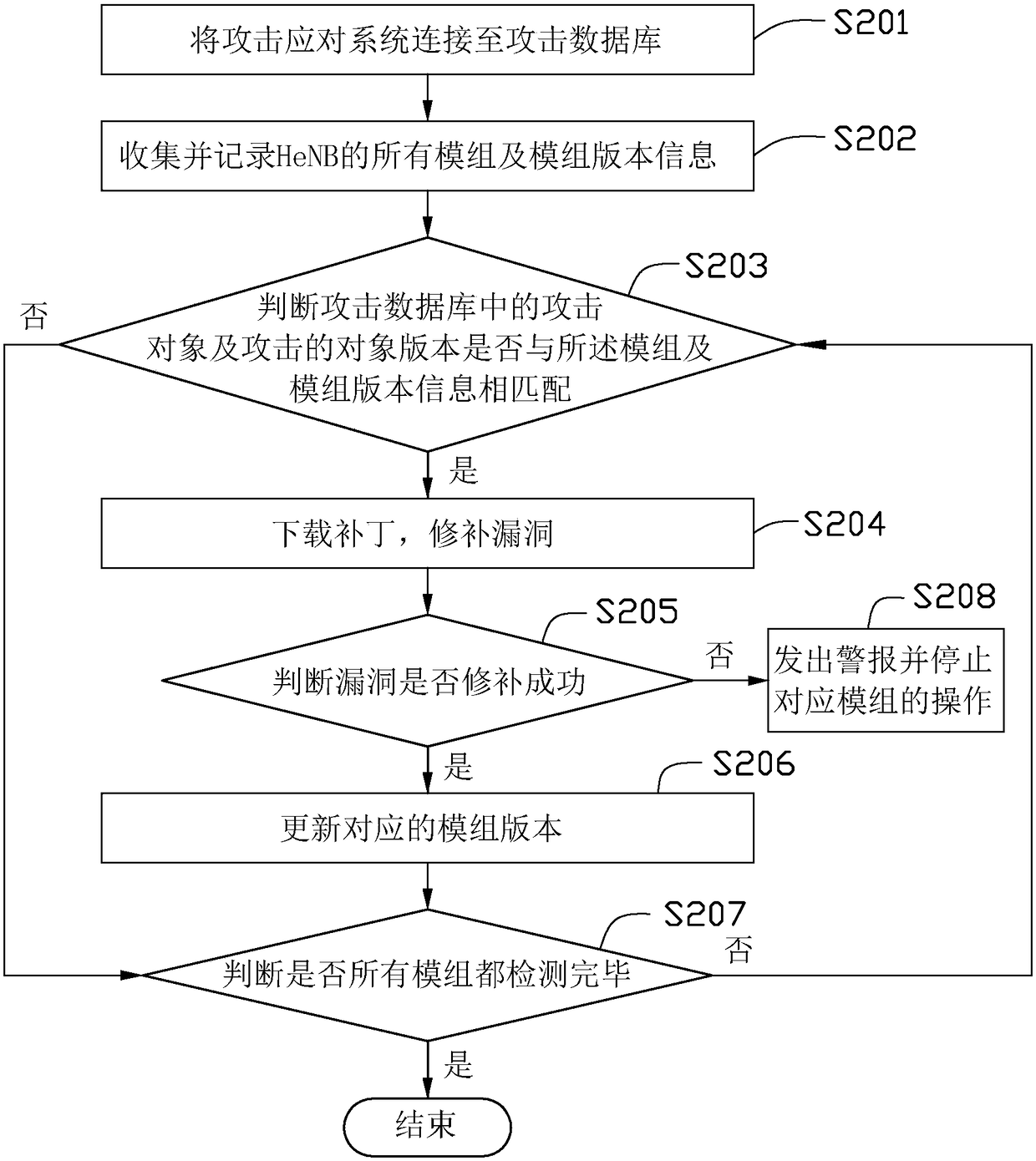
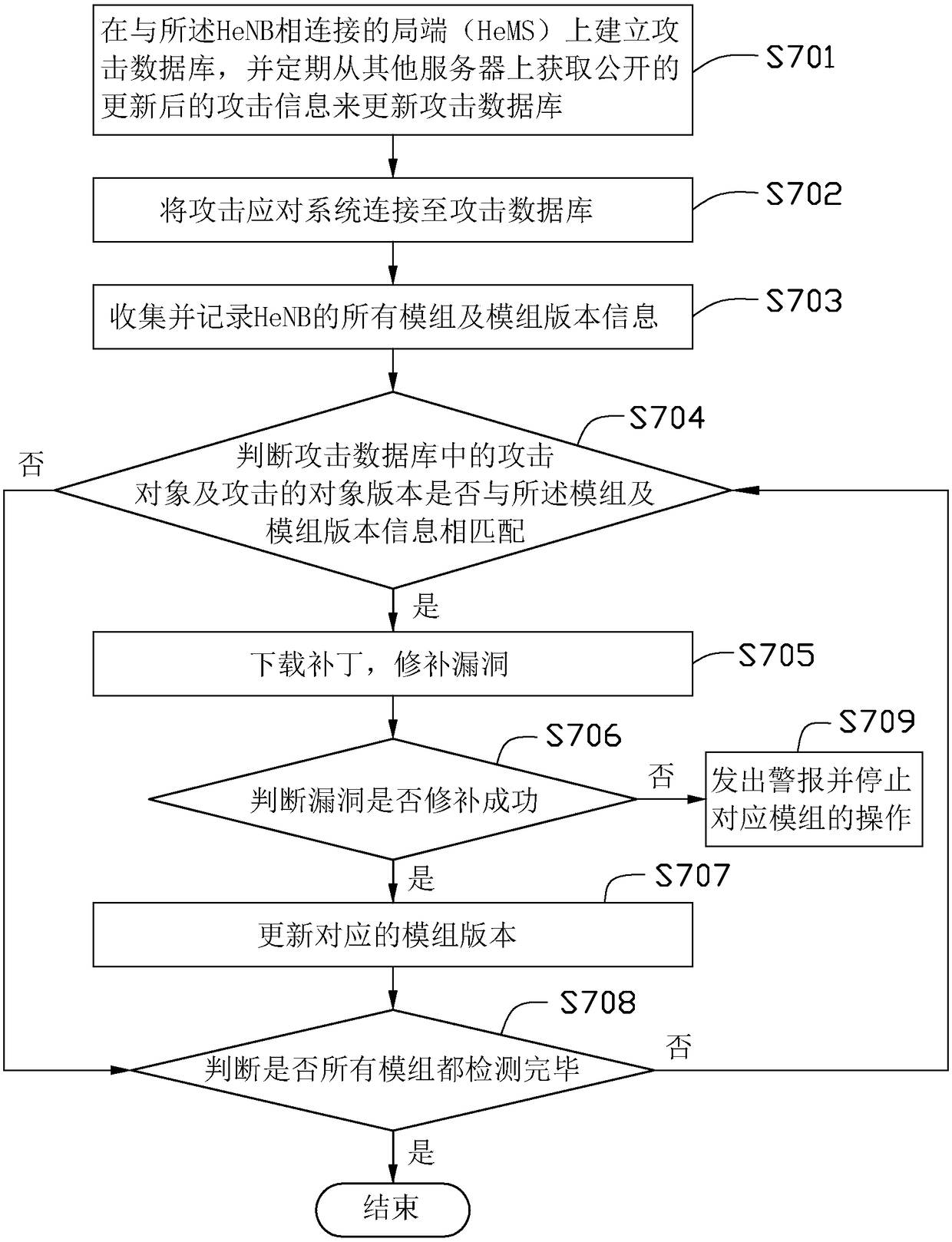
[0021] see figure 1 , in a preferred embodiment, an attack response system includes a connection module 10 , a collection module 20 , a judging module 30 and a processing module 50 . The attack response system may be set on a HeNB (Home evolved Node B, home evolved base station), or on a central office (HeMS) connected to the HeNB.
[0022] The connection module 10 is used for connecting the HeNB to an attack database 60 . Attack information is stored in the attack database 60 . The attack information includes an attack name, an attack object, an attack object version, an attack severity, a corresponding solution, and the like.
[0023] The name of the attack is a file or program with attack power. The attack object is the module or file attacked by the attack name. Said solutions include patching, raising an alert, stopping the use of the attack object, etc.
[0024] The attack database 60 can be directly stored on a cloud server or other servers, and the attack informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com