Ddos attack distributed detection and response method based on information entropy
An information entropy and distributed technology, applied in transmission systems, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
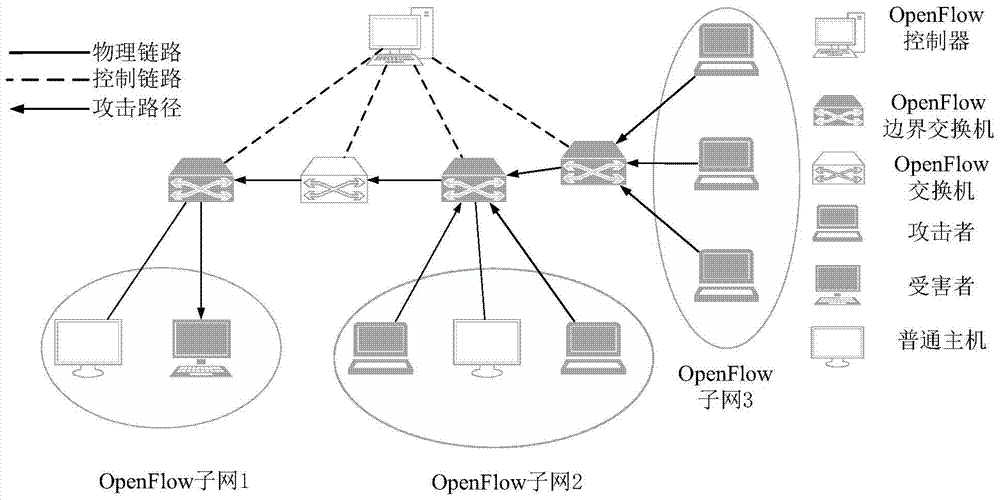
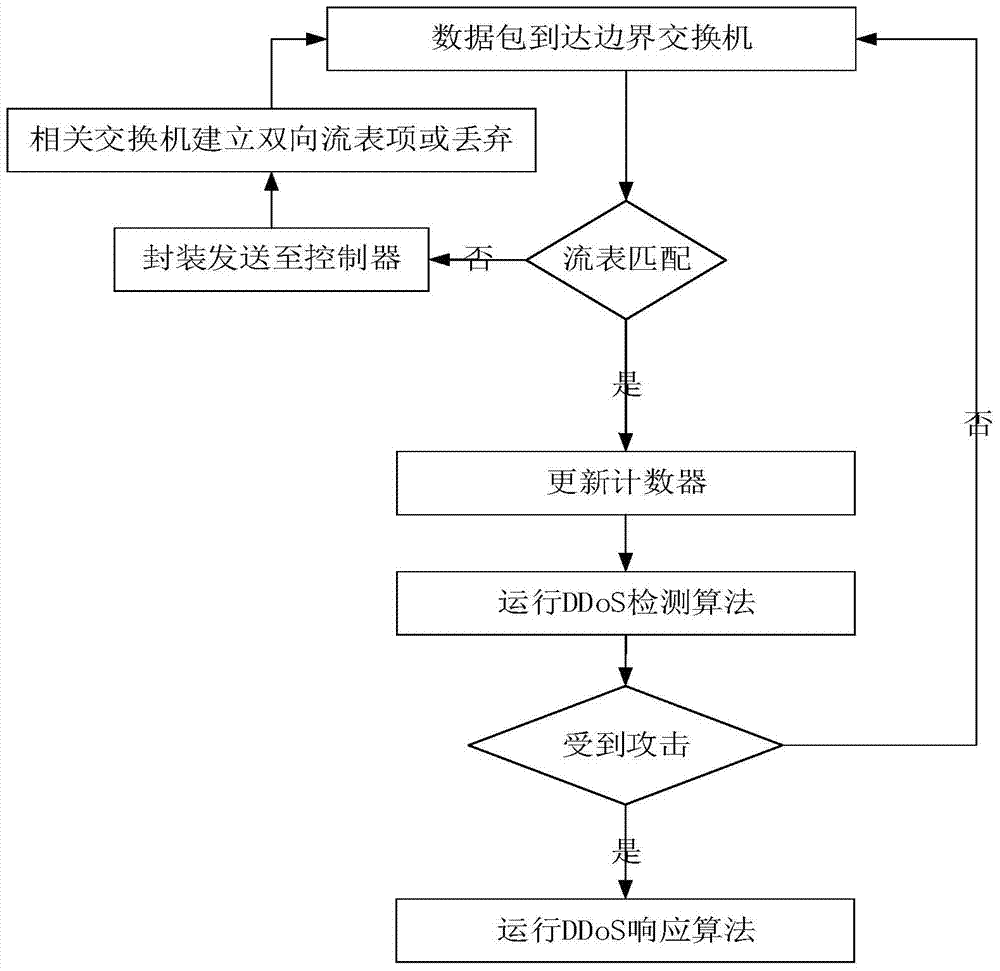
[0071] For the SDN / OpenFlow network architecture, the SDN / OpenFlow architecture used in the present invention is as attached figure 1 As shown, the attacker and the attack route in the figure are examples of DDoS attacks dealt with by the present invention. The present invention proposes two algorithms, a DDoS attack detection algorithm and an attack response algorithm.
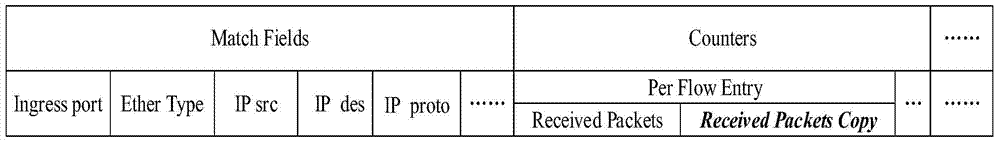
[0072] At present, to detect DDoS attacks in SDN networks, most of them need the controller to continuously poll the current flow table information in the switch, and then analyze the flow table information to detect whether there is a DDoS attack. This method has advantages in small-scale SDN networks. However, when the number of switches increases, the scale of flow tables obtained and analyzed by the controller increases geometrically, and obtaining too many flow tables affects its...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com