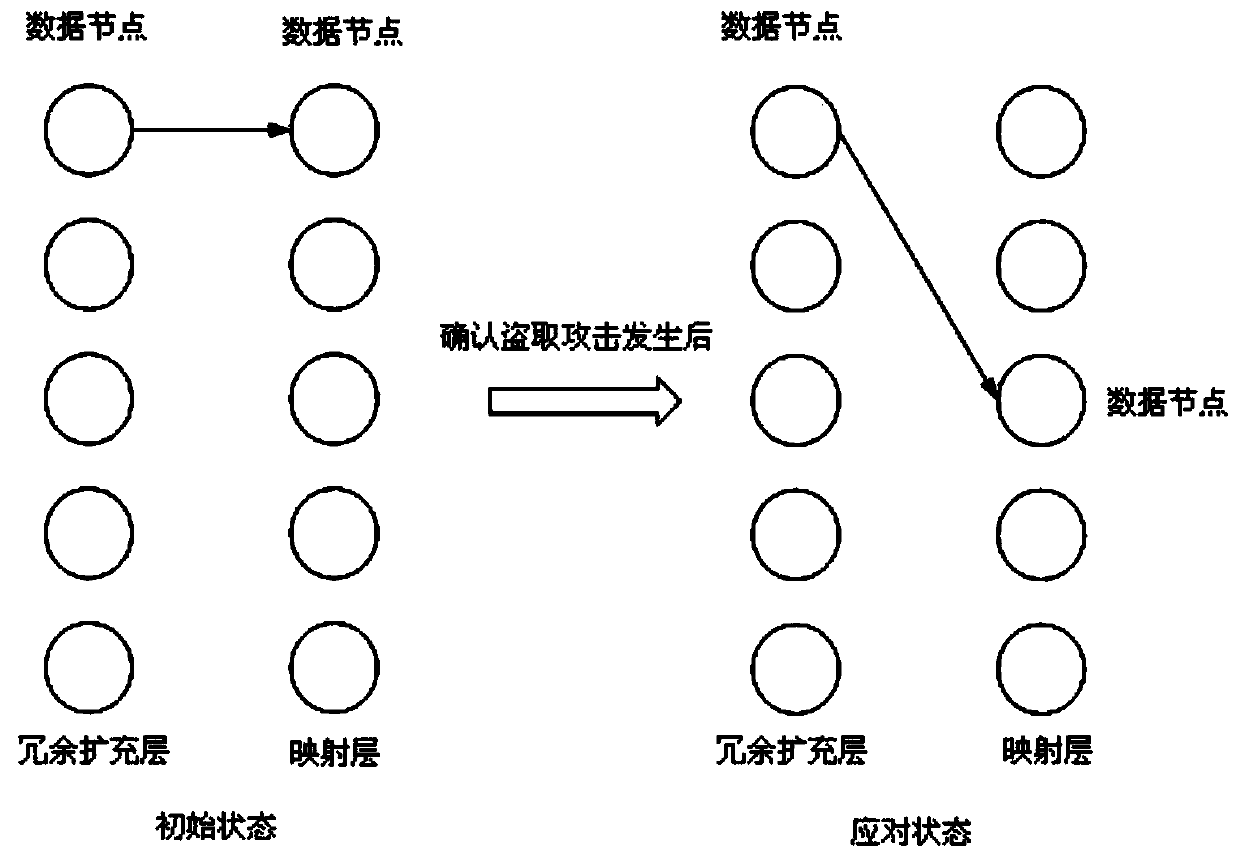
Heterogeneous iris authentication method with theft attack response mechanism
An authentication method, iris technology, applied in digital data authentication, computer parts, instruments, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0067] Under the framework of claim 1, the operation of a certain person (named A, A’s information is stored in the authentication system, and the test iris and the template iris are the same equipment, the same collection environment is used for collection, and no theft attack occurs) The whole process:
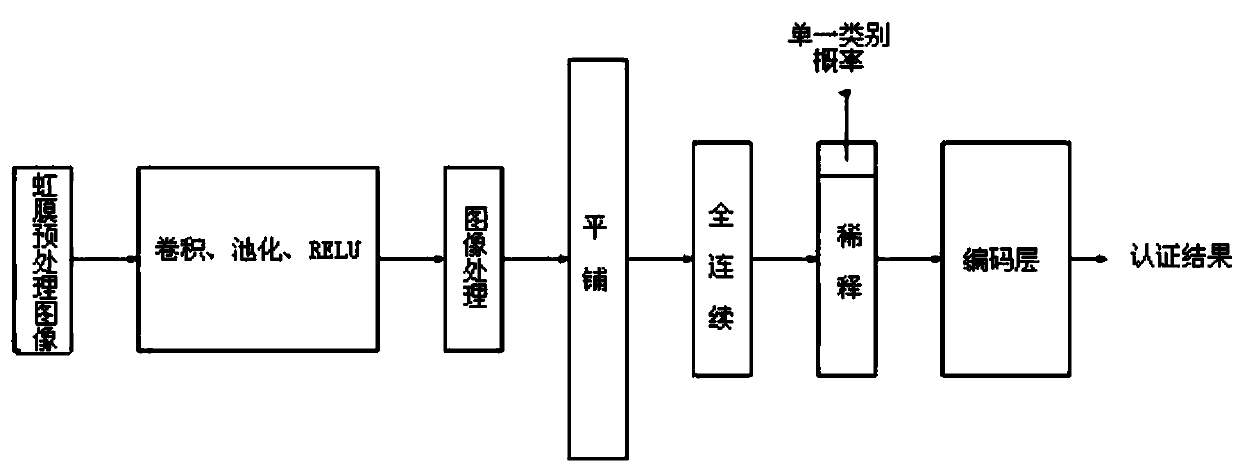
[0068] 1) The computer first collects the iris image of A through the iris collector, and then converts the eye image of A into a 256×32-dimensional iris normalized and enhanced image through the Daugman rubber band method and equalized histogram, and normalizes the iris of A to An augmented image is input into a convolutional layer.
[0069] 2) The iris normalized enhanced image of A goes through the first convolutional layer, the first pooling layer, the first ReLU layer, the second convolutional layer, the second pooling layer, the second ReLU layer, and the third convolutional layer , the third pooling layer, the image processing layer, and the tiling layer, enter the f...
Embodiment 2
[0074] Under the framework of claim 1, for a certain person (named B, the information of B is not saved in the authentication system, it belongs to a new category, and the test iris and the template iris will be collected through different equipment and different collection environments, and there is no theft attack behavior Occurrence) The whole process of operation:
[0075] 1) The computer first collects H iris images of B through the iris collector p, and then converts the H images of B's eyes into 256×32-dimensional iris normalized enhanced images through the Daugman rubber band method and equalized histogram. The iris normalized and enhanced images of H sheets of B are sequentially input into the convolutional layer.
[0076] 2) The iris normalized enhanced images of H pieces of B go through the first convolutional layer, the first pooling layer, the first ReLU layer, the second convolutional layer, the second pooling layer, the second ReLU layer, and the third volume ...
Embodiment 3
[0085] Under the framework of claim 1, the whole operation process of a certain person (named C, C’s information is not saved in the authentication system, and no theft attack occurs):
[0086] 1) The computer first collects the iris image of C through the iris collector, and then converts the eye image of C into a 256×32-dimensional iris normalized and enhanced image through the Daugman rubber band method and equalized histogram, and normalizes the iris of A to An augmented image is input into a convolutional layer.
[0087] 2) The iris normalized enhanced image of C goes through the first convolutional layer, the first pooling layer, the first ReLU layer, the second convolutional layer, the second pooling layer, the second ReLU layer, and the third convolutional layer , the third pooling layer, the image processing layer, and the tiling layer, enter the fully connected layer.
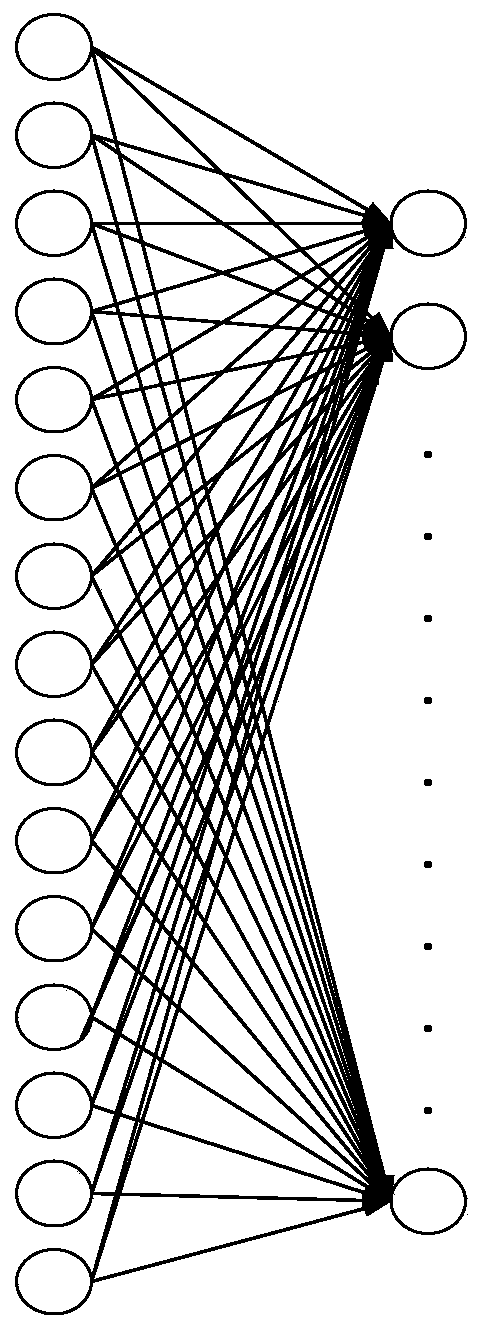
[0088] 3) From the tiling layer to the fully connected layer, the 15 data of the tiling layer are...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com