Network attack result detection method and system
A network attack and detection method technology, applied in the field of network security, can solve the problem of high operation and maintenance processing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
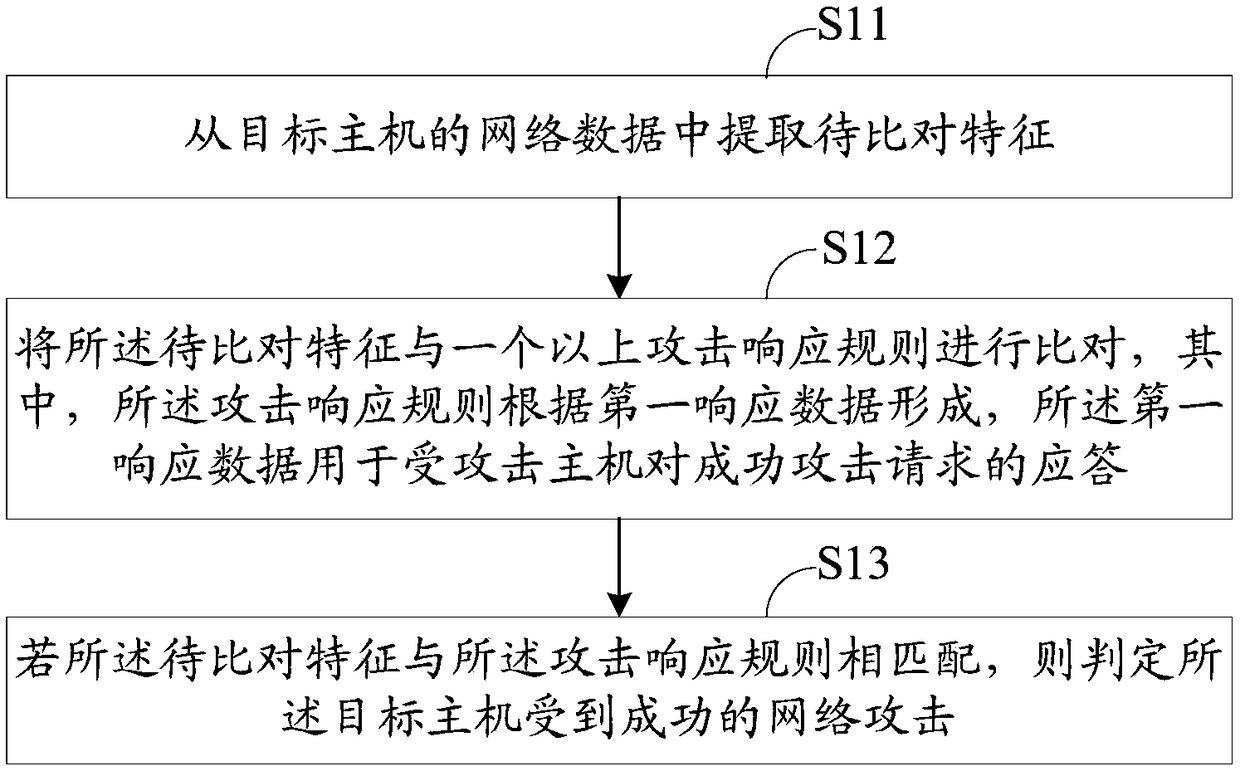
[0139] This embodiment provides a network attack result detection method, figure 1 is a schematic flow chart of the network attack result detection method, and the network attack result detection method includes:
[0140] Step S11, extracting features to be compared from the network data of the target host;
[0141] Step S12, comparing the feature to be compared with more than one attack response rule, wherein the attack response rule is formed according to the first response data, and the first response data is used for the attacked host to successfully attack the request answer;
[0142] Step S13, if the feature to be compared matches the attack response rule, it is determined that the target host is successfully attacked by the network.
[0143] Specifically, the target host may be a server providing various services, a personal computer capable of realizing specific functions, or other network devices capable of providing network services. The target host may receive re...
Embodiment 2
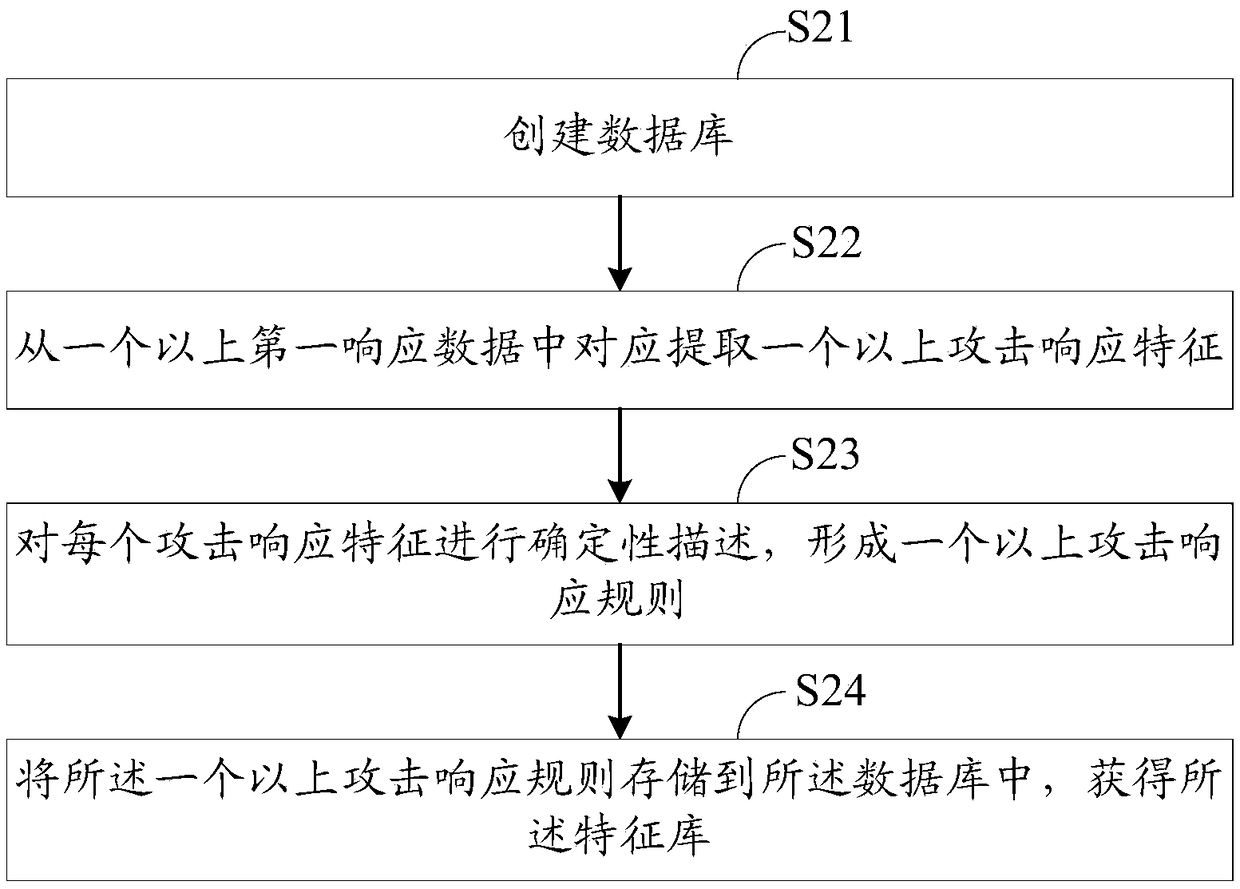
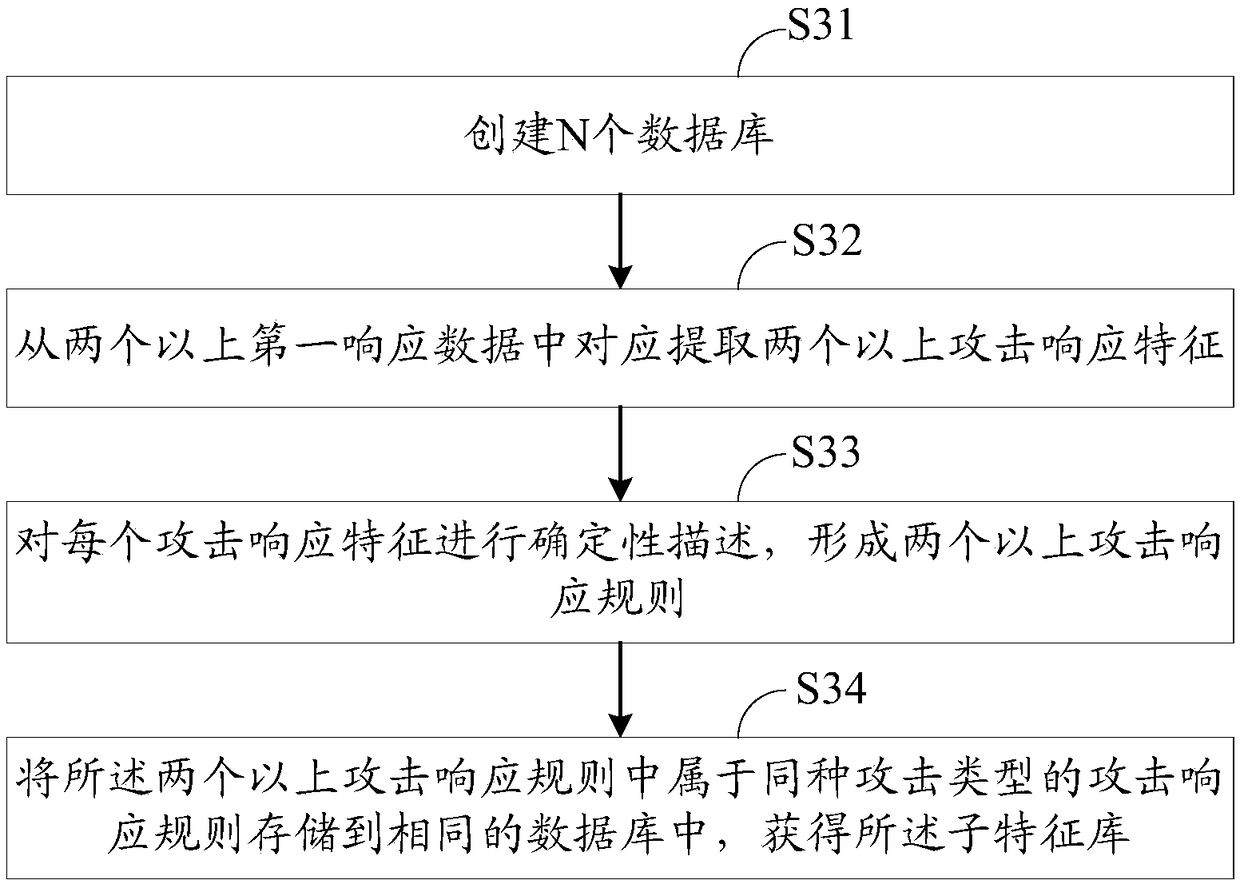
[0166] This embodiment provides another network attack result detection method. Compared with the network attack result detection method provided in Embodiment 1, before extracting the features to be compared from the network data, it also includes: according to the network The data detects whether the target host is attacked by the network; if the target host is attacked by the network, the step of extracting the features to be compared from the network data is performed.
[0167] To detect whether the target host is under network attack, a traditional network attack detection method may be used. Considering that the traditional network attack detection method has the defects of high false negative rate and poor flexibility, this embodiment provides a specific method for detecting whether the target host is under network attack. Figure 4 It is a schematic flow diagram of detecting whether the target host is under network attack, and the detecting whether the target host is u...
Embodiment 3
[0184] This embodiment provides another network attack result detection method. Compared with the network attack result detection method provided in Embodiment 2, after comparing the features to be compared with more than one attack response rule, an alarm can also be generated. Information, wherein the alarm information includes the attack type of the network attack, whether the network attack is successful, and the attack action of the successful network attack. For example, when the target host is attacked by SQL injection but the attack is unsuccessful, the alarm information can be "under SQL injection attack, the attack is invalid"; when the target host is attacked by SQL injection and the attack is successful, the specific attack action It uses the floor() function to report an error injection, and the alarm information can be "under SQL injection attack, the attack is successful, and the floor() function reports an error injection".
[0185] Further, after the alarm inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com