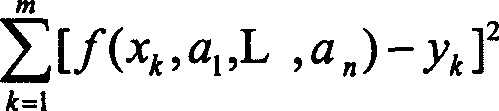Patents
Literature
103 results about "Attack time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In telecommunication, attack time is the time between the instant that a signal at the input of a device or circuit exceeds the activation threshold of the device or circuit and the instant that the device or circuit reacts in a specified manner, or to a specified degree, to the input. Attack time occurs in devices such as clippers, peak limiters, compressors, and voxes.
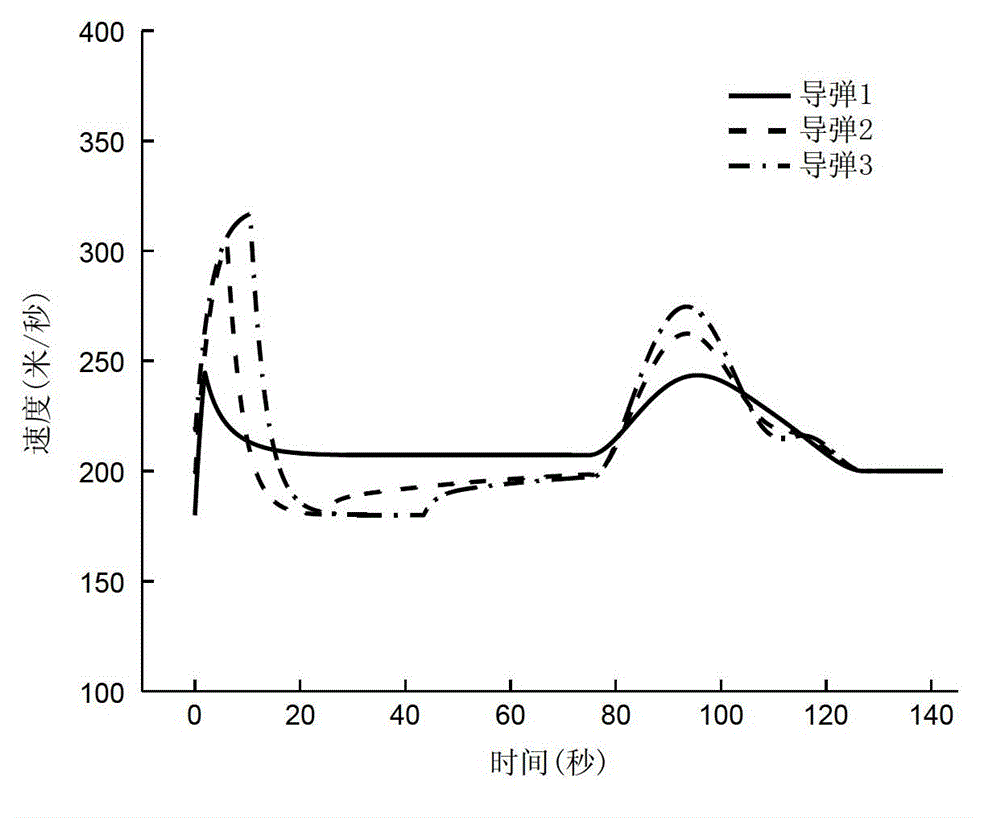
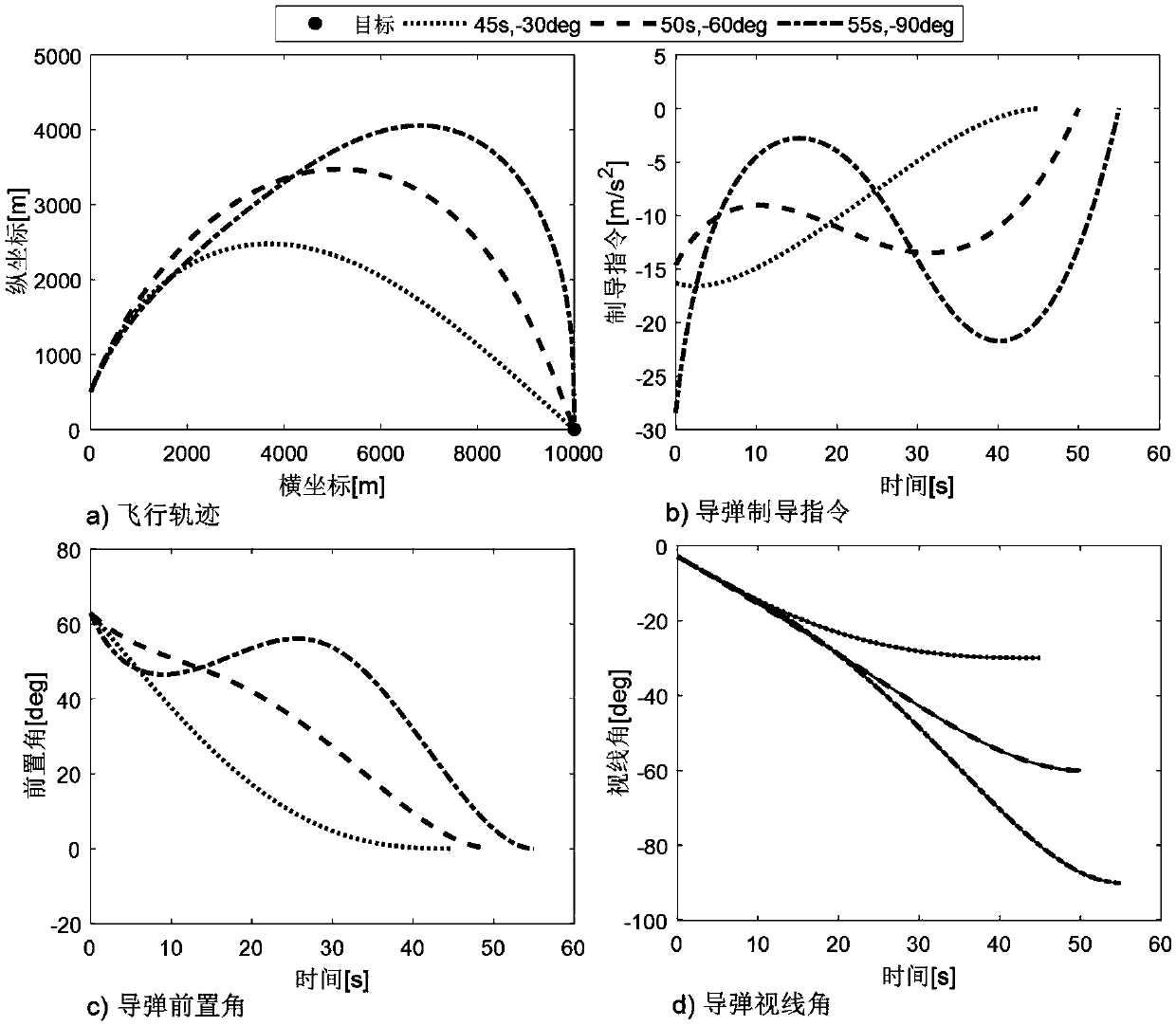
Method for controlling attack angle and attack time of multiple missiles
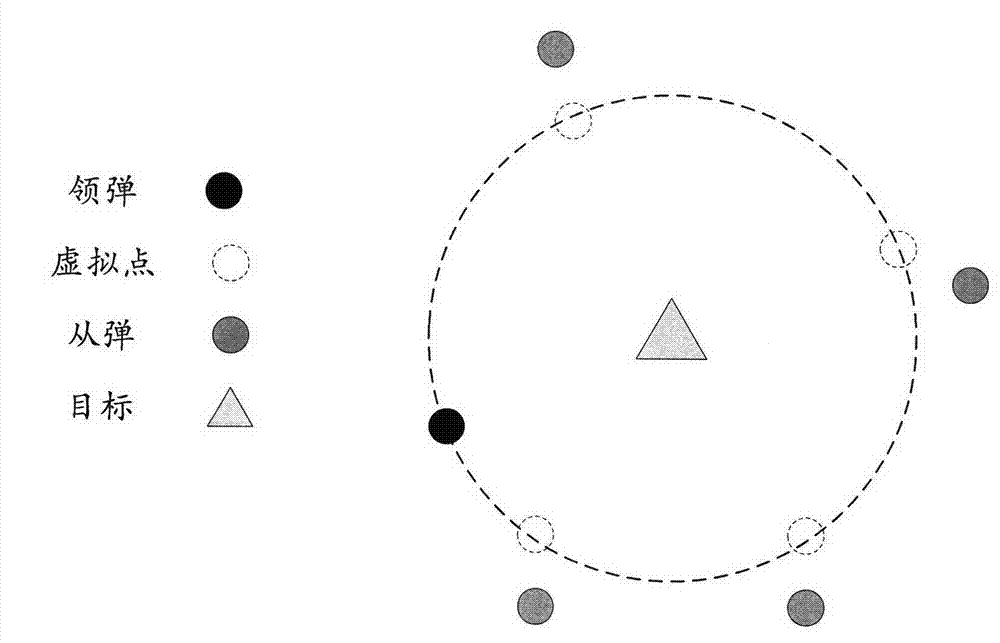
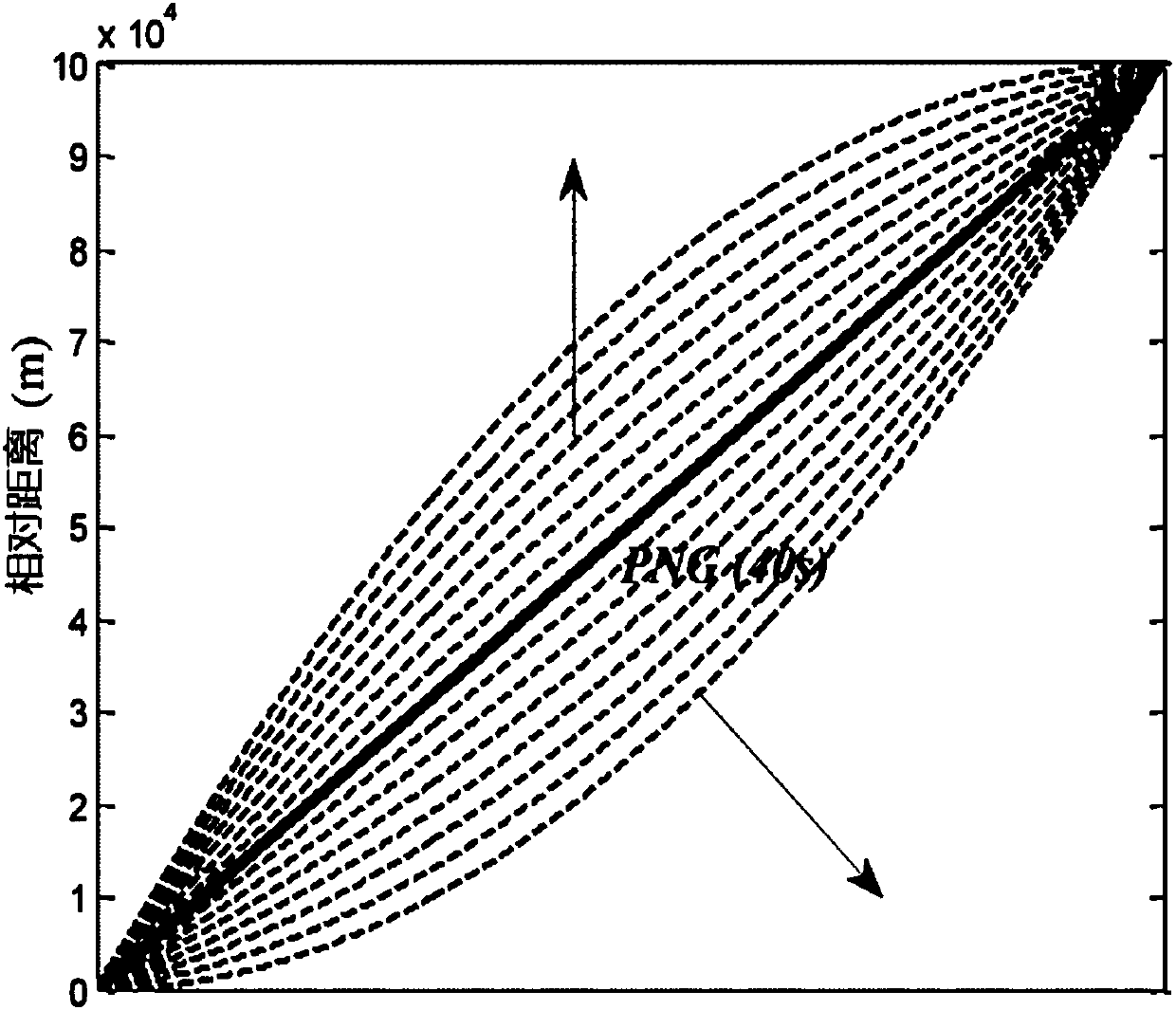
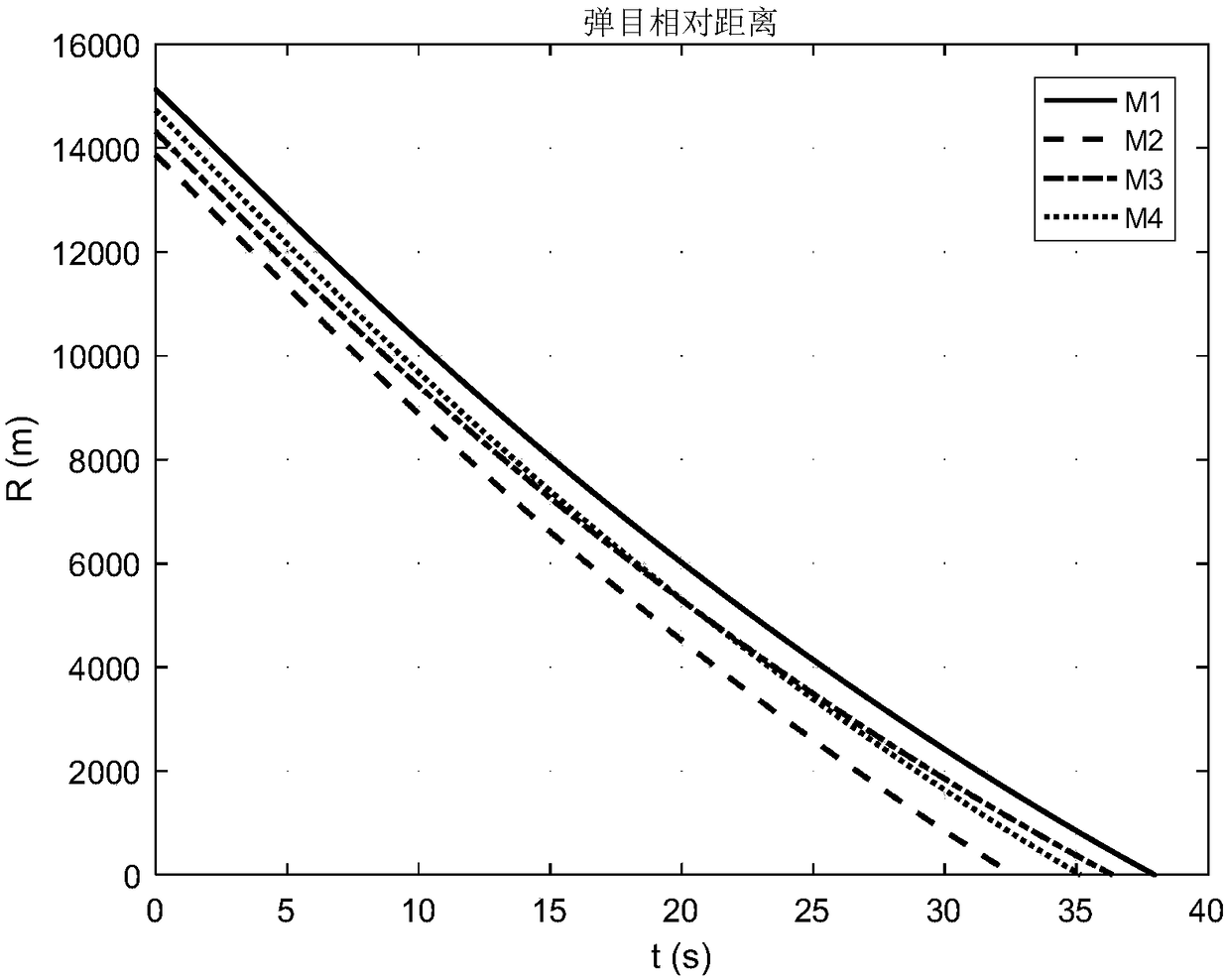
The invention provides a method for controlling the attack angle and the attack time of multiple missiles. With the adoption of the method, the attack angle and the attack time of the multiple missiles can be accurately controlled. The method comprises the following steps: arbitrarily selecting one missile from multiple missiles to serve as a master missile; constructing a virtual sphere by taking a target as a sphere center and taking distance between the master missile and the target as a radius; defining the residual missiles as slave missiles; selecting virtual points for each slave missile on the surface of the virtual sphere, wherein direction of a connection line of each virtual point and the target is a preset ideal attack angle corresponding to the slave missile; and by controlling a slave missile movement locus, approaching and tracking a virtual point locus, so that control of the attack angle and the attack time of multiple missiles is realized. The method for controlling the attack angle and the attack time of the multiple missiles is realized by approaching and tracking the virtual point corresponding to the slave missile by the slave missile, so that the attack angle and the attack time of the slave missiles can be controlled without appointing ideal attack time for each slave missile in advance.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
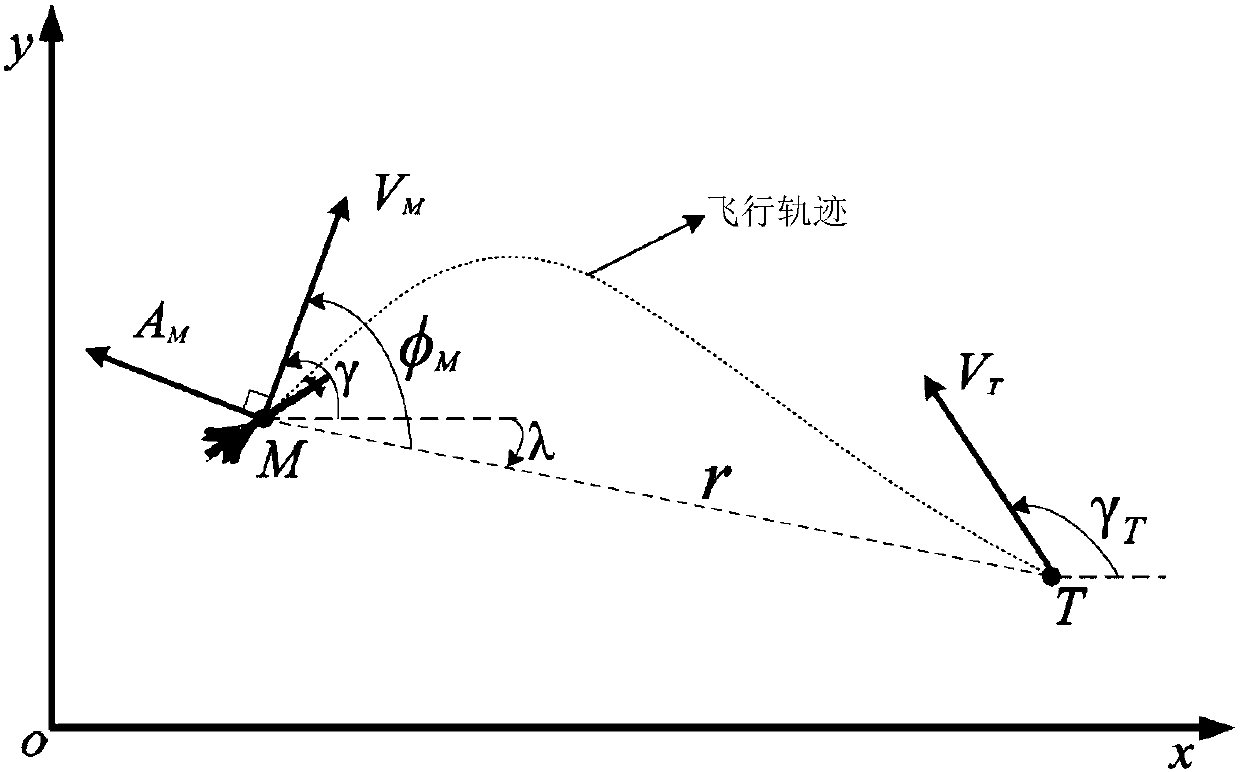
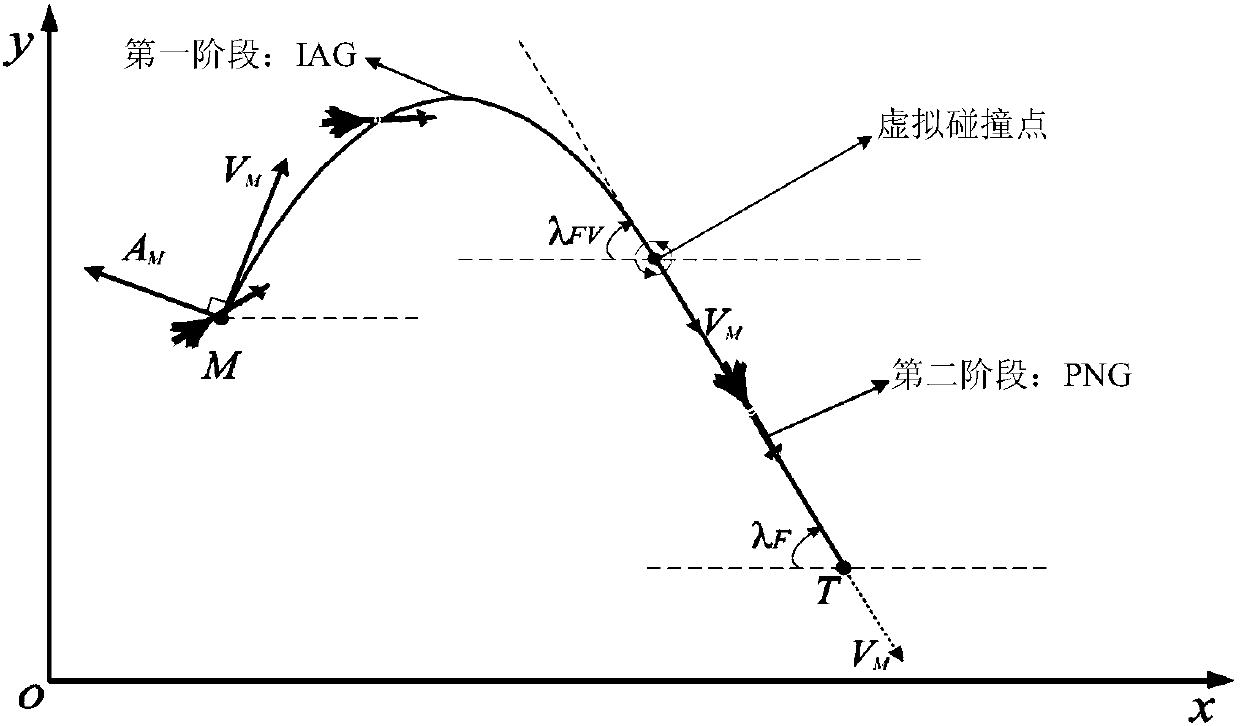
Attack time and attach angle constrained guidance strategy
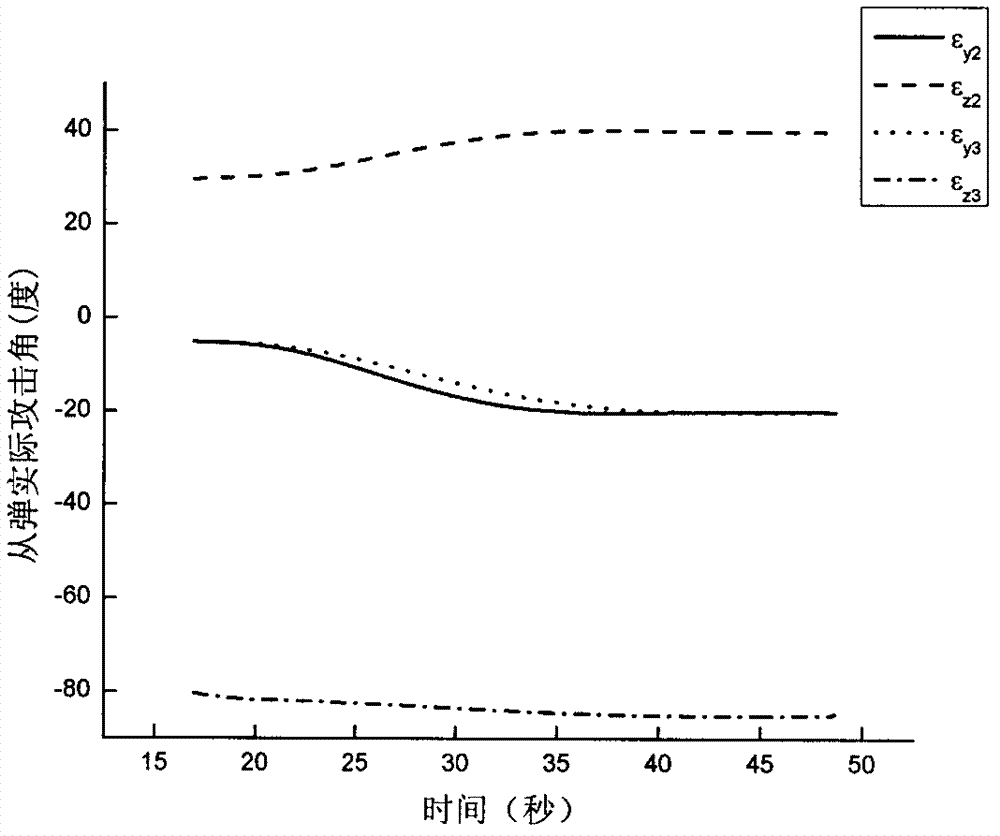
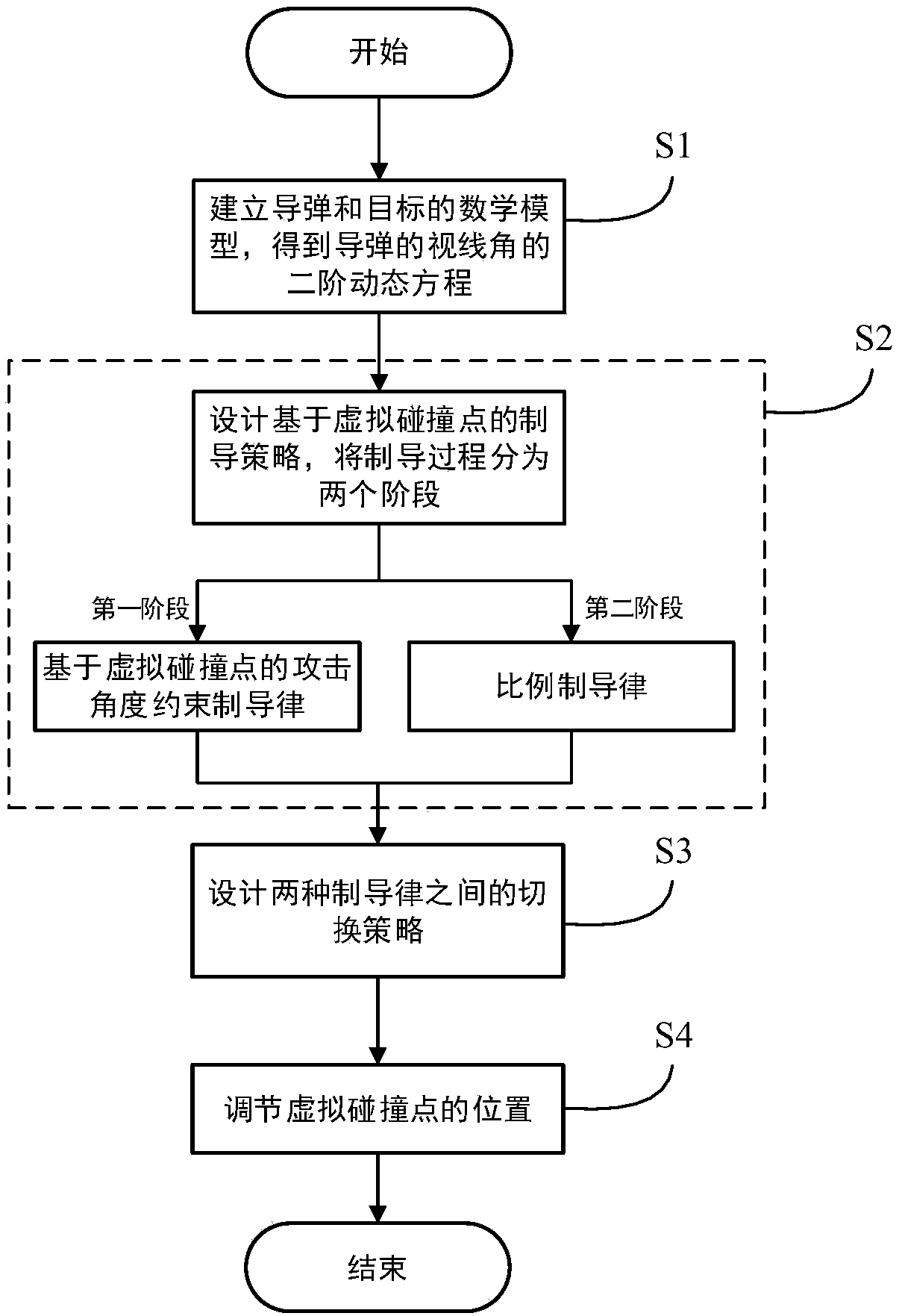
The invention discloses an attack time and attach angle constrained guidance strategy. The attack time and attach angle constrained guidance strategy comprises the following steps of using a two-dimensional horizontal plane where a missile and a target are located as an attack plane, establishing a missile and target mathematical model and acquiring a missile sight angle second-order dynamic equation; designing the guidance strategy based on a virtual collision point, dividing the guidance process into two stages, designing an attack angle constrained guidance law based on the virtual collision point for the first stage and designing a proportional guidance law for the second stage; designing a switching strategy of the attack angle constrained guidance law and the proportional guidance law based on the virtual collision point; and adjusting the location of the virtual collision point. By means of the guidance strategy based on the virtual collision point, there is no need to conduct linearization and differential equation conversion based on the cross-range on the model and depend on estimation on remaining time information; the attack time and attach angle constrained guidance strategy is applicable to target moving tasks under multiple constraint conditions and has the characteristics that the design method is simple, and the applicability is high.
Owner:BEIHANG UNIV
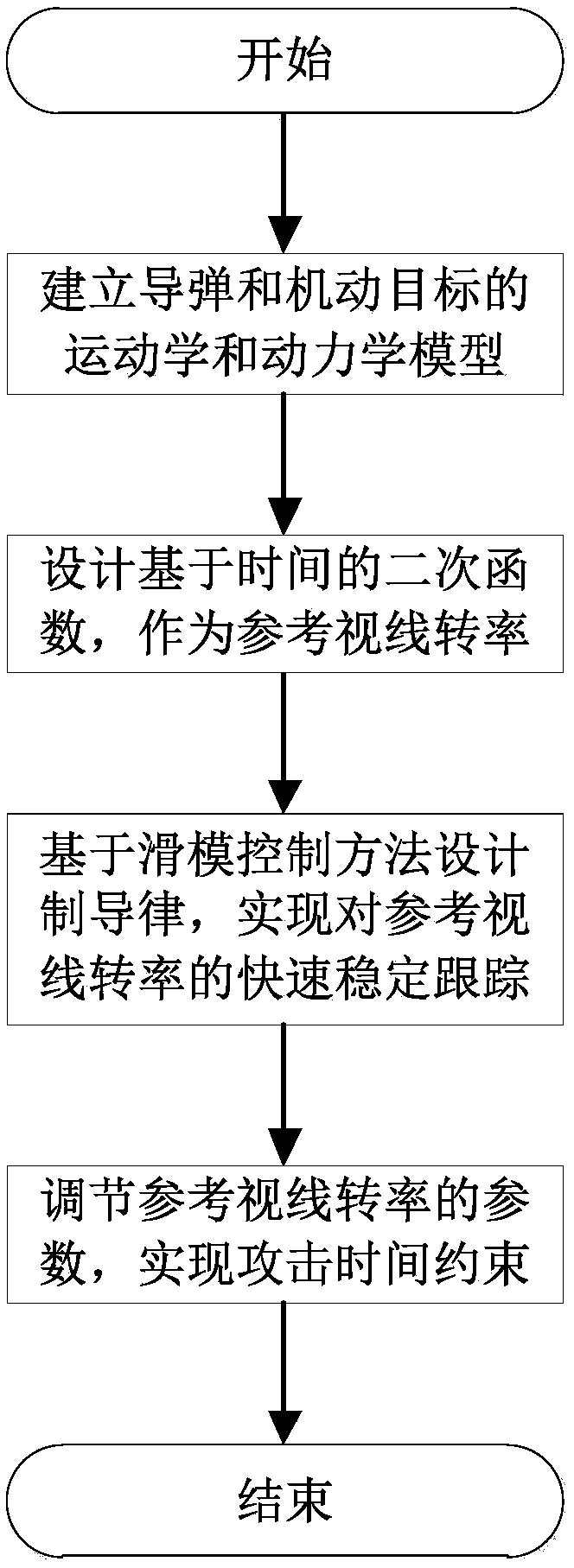
Attack-time-constraint guidance-law design method of intercepting maneuvering target
ActiveCN108416098AAttack Time GuaranteeImprove robustnessDesign optimisation/simulationSpecial data processing applicationsDynamic equationEngineering
The invention provides an attack-time-constraint guidance-law design method of intercepting a maneuvering target. The method comprises the steps of: obtaining a second-order dynamic equation of a line-of-sight angle of a missile; designing a time-based quadratic function to use the same as a reference line-of-sight rate which the missile needs to track; and adopting a sliding-mode control method to design a guidance law with an attack time constraint on the basis of the second-order dynamic equation of the line-of-sight angle. The design method of the invention is a reference line-of-sight rate-based sliding-mode guidance-law design method, designs the guidance law which has anti-interference performance, and is capable of quickly tracking the expected line-of-sight rate and precisely hitting the target, and realizes the constraint on attack time through adjusting parameters of the reference line-of-sight rate.
Owner:BEIHANG UNIV
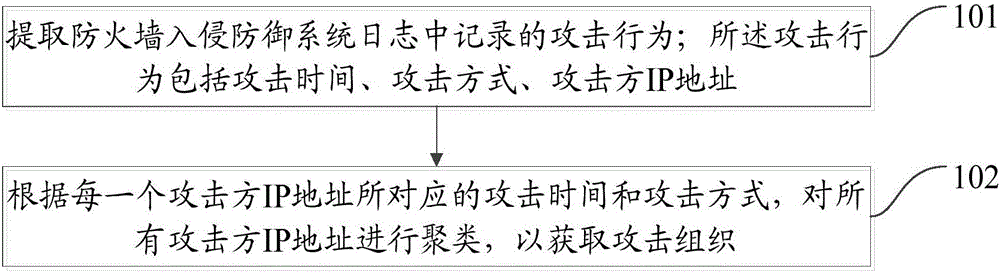
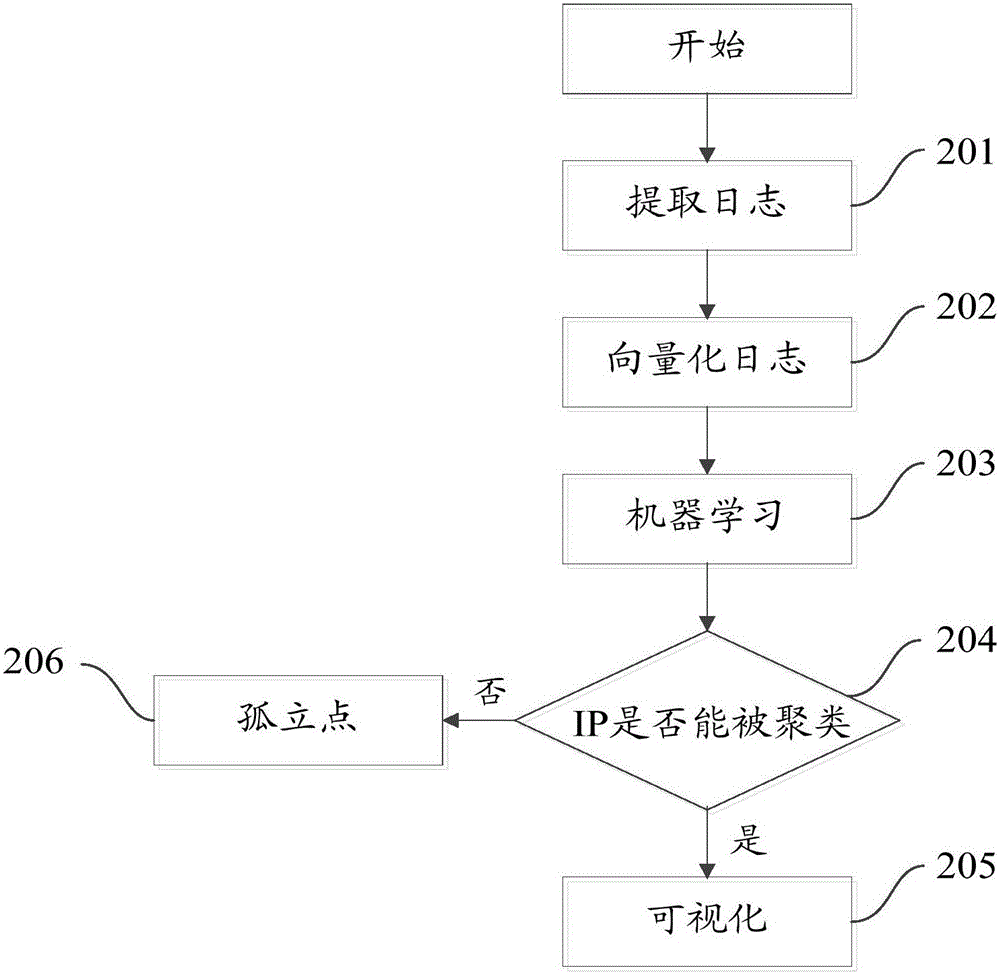
Mining method and device of attacking organization
ActiveCN106375331ARapid positioningUnderstand intuitiveTransmissionIp addressIntrusion prevention system
The invention discloses a mining method of an attacking organization. The mining method of the attacking organization comprises the steps of extracting attacking behaviors recorded in a firewall intrusion prevention system log, wherein each attacking behavior comprises attacking time, an attacking mode and an IP address of an attacker; and clustering the IP addresses of all the attackers based on the attacking time and the attacking mode corresponding to the IP address of each attacker to obtain the attacking organization. The invention also discloses a mining device of the attacking organization.
Owner:BEIJINGNETENTSEC
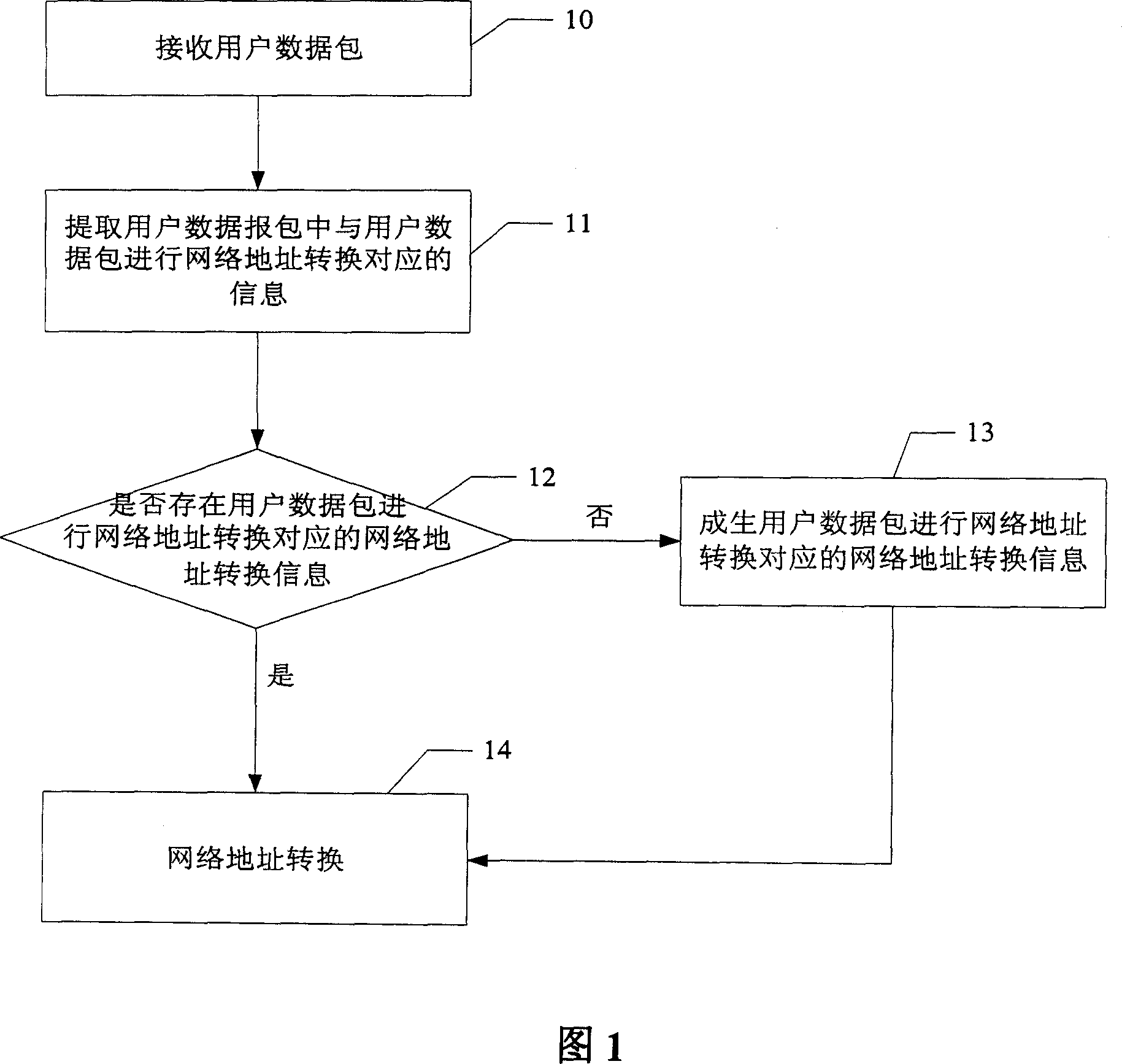
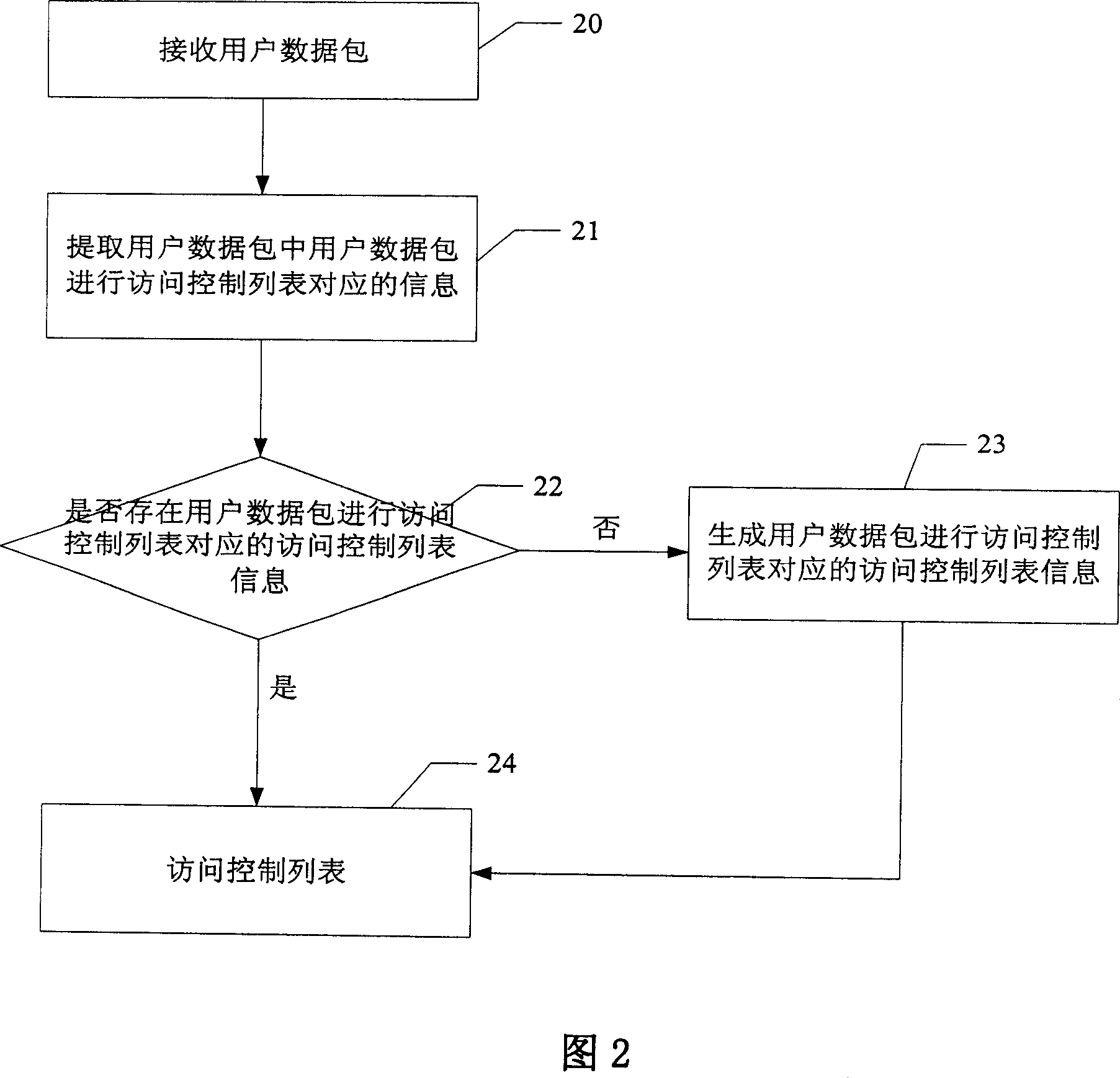
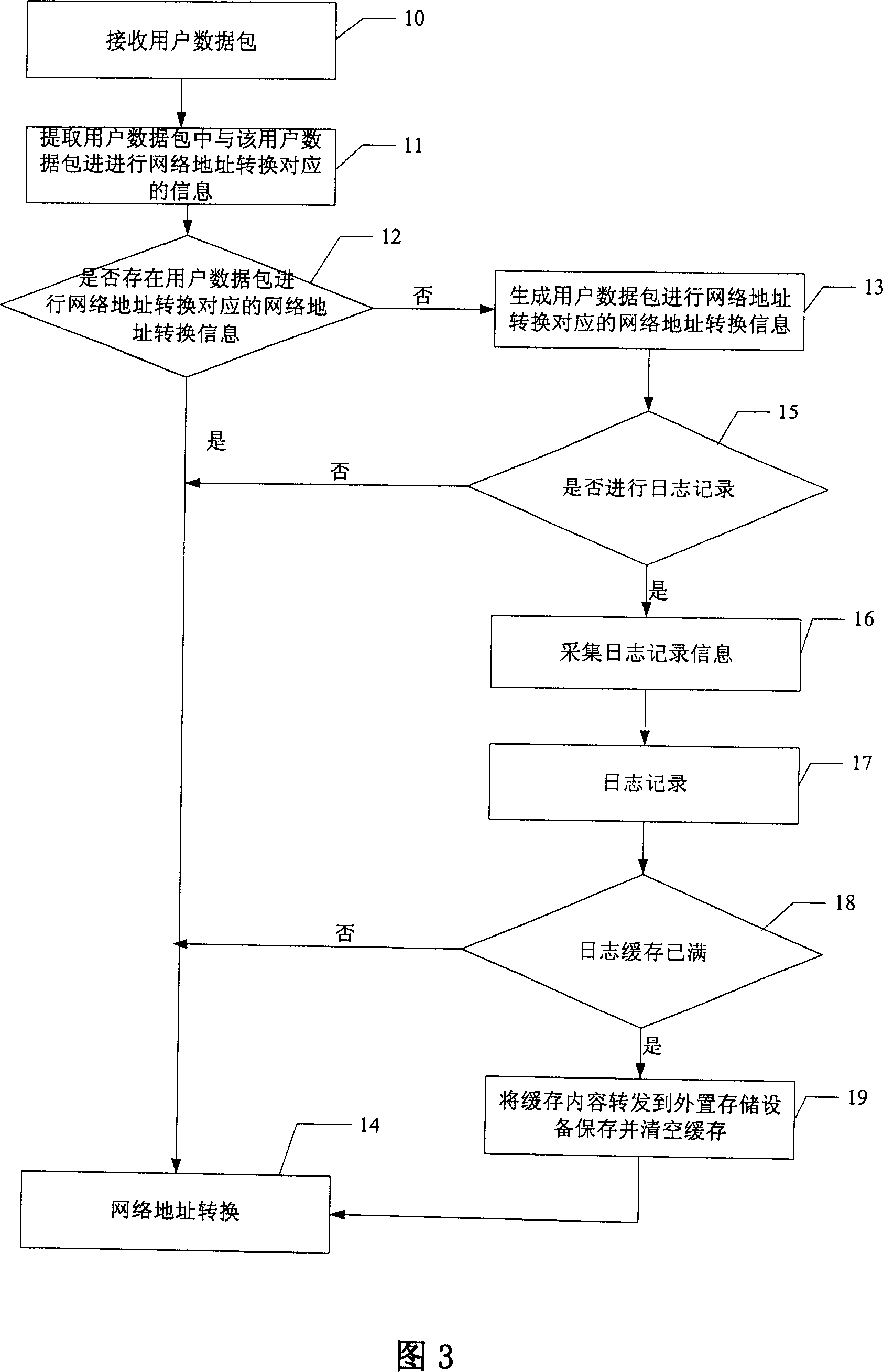
NAT method and method for realizing access control list
InactiveCN101079798ALow costReduce workloadMultiplex system selection arrangementsData switching networksAccess methodNetwork addressing
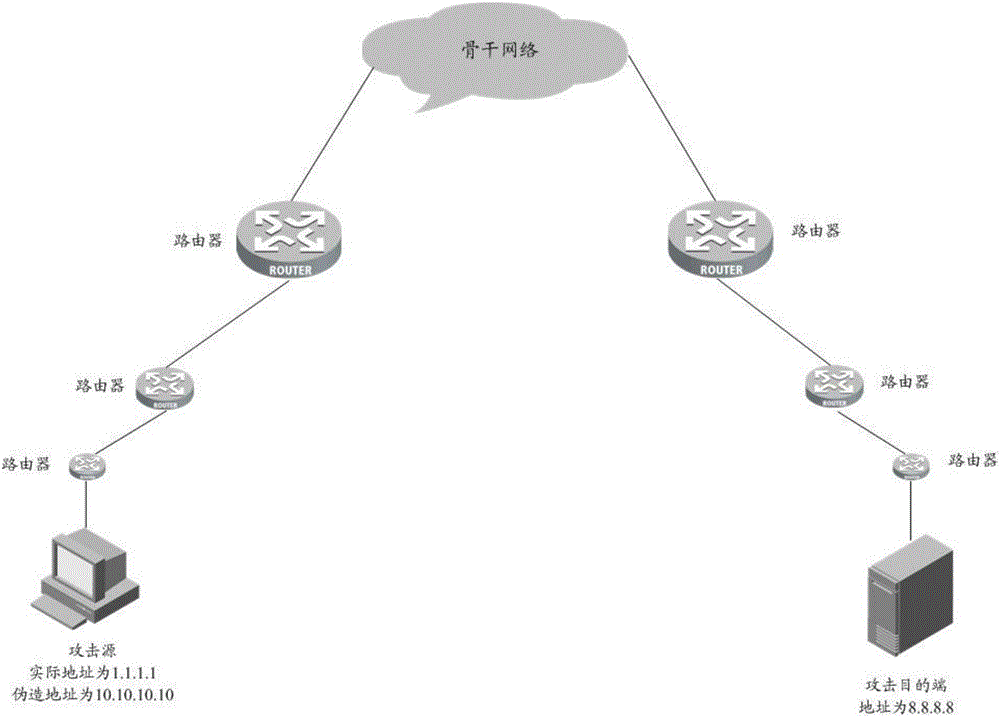
The invention discloses a control list conversing and accessing method of network address, which comprises the following steps: A. judging whether network address is conversed into network address conversion information through the user data pack; executing the step C if the judging result is to converse; executing the step B if the result is not to converse; B. generating the user data pack to converse the network address into the network address conversion information; recording the journal; C. conversing the network address of the user data pack according to the network address conversion information corresponding to the user data pack. The invention is convenient for user to access the historical information, on-line and off-line time, which is accurate to judge the attack source and attack time when the network is attached and off-line.
Owner:HUAWEI TECH CO LTD
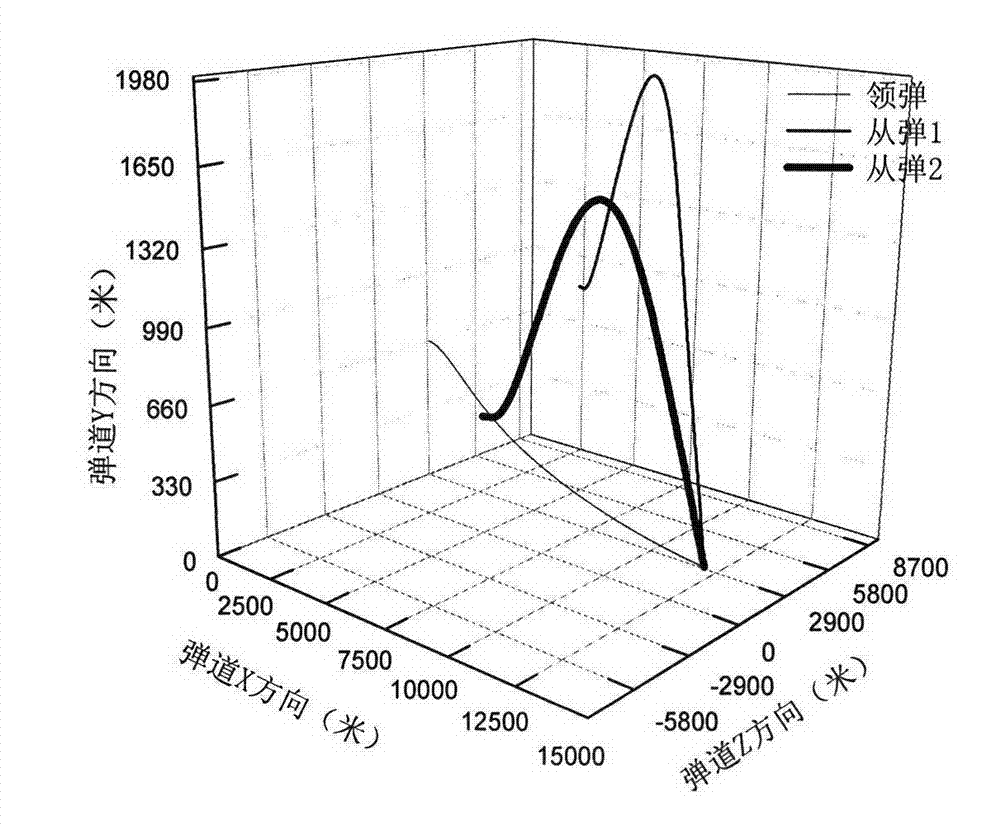
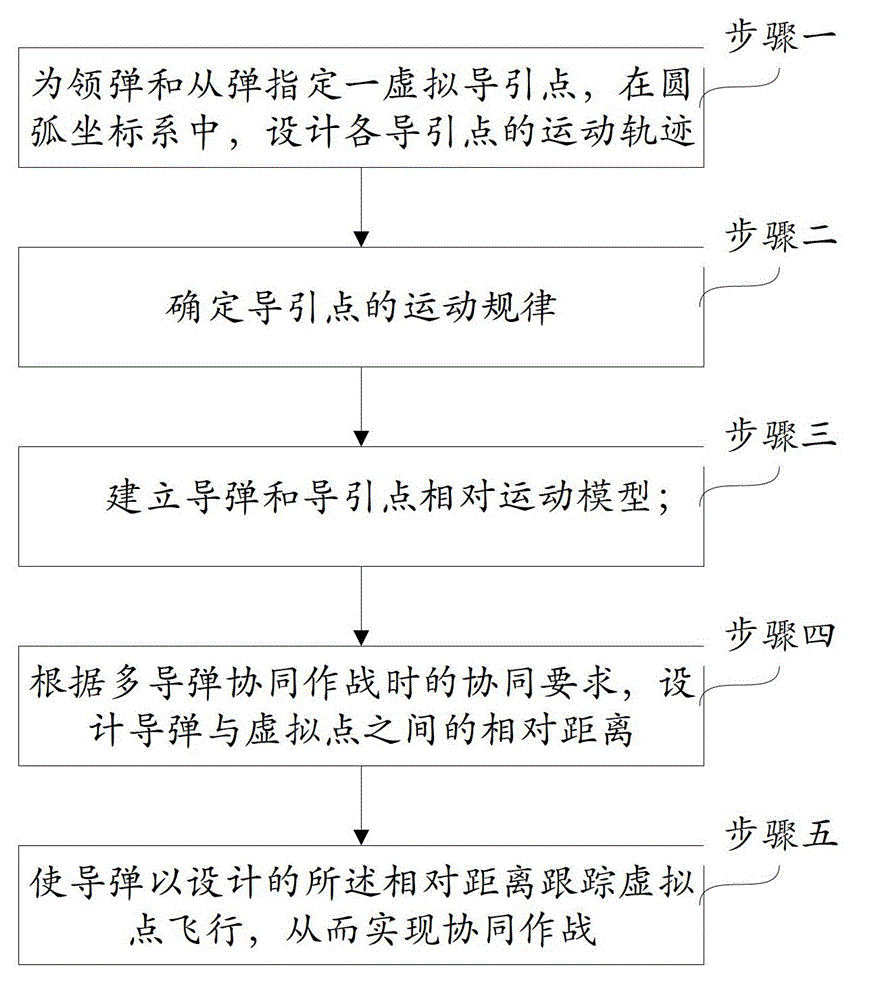
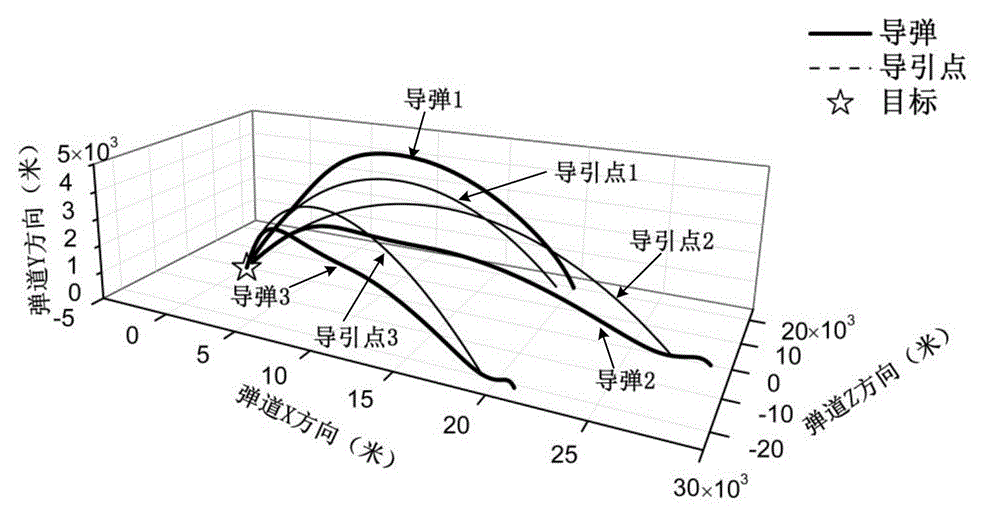
Method for controlling coordinated operation of multiple missiles
ActiveCN102980449AIdeal attack speedIdeal hitSelf-propelled projectilesAngular degreesKinetic theory
The invention provides a method for controlling coordinated operation of multiple missiles, which can accurately control the position, attack time, attack angle and attack velocity of each of the multiple missiles. The method comprises the following steps: selecting one missile from the multiple missiles to serve as a driving missile, and defining the rest missiles as driven missiles; assigning a virtual lead point to the driving missile as well as each of the driven missiles, and designing the path of motion of each lead point; determining the law of motion of the lead points in an arc coordinate system; establishing a model of relative motion of missiles and the lead points; designing the relative distances xr, yr and zr between the missles and the virtual lead points according to the needs of the missiles for cooperation in terms of position, attack angle and attack velocity; and designing a tracking controller based on the relative kinetics theory and allowing the missiles to fly in a way of tracking the virtual lead points with the designed relative distances, so as to perform coordinated operation. The method has the advantages of convenience in application and flexibility in use and has broad application prospects in the military field.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method for preventing MAC address cheat
InactiveCN101043355APrevent cheatingSolve the problem of not notifying the CPU for processingData switching networksSecuring communicationHuman–machine interfaceMan machine
The disclosed method for preventing the cheat of MAC address comprises: CPU system sets the dynamic MAC address transmission list item on up port as static state, and simulates the aging mechanism of chip MAC address for former up port list item to prevent cheating MAC address. This invention can record user port suffered malevolent attack and the attack time to notify user through CPU system man-machine interface and network management system in time.
Owner:HUAWEI TECH CO LTD
Attack angle and attack time control method based on trajectory planning
ActiveCN107132765AEstimate calculation is simpleImprove efficiencyTarget-seeking controlAttitude controlVirtual targetTrajectory planning
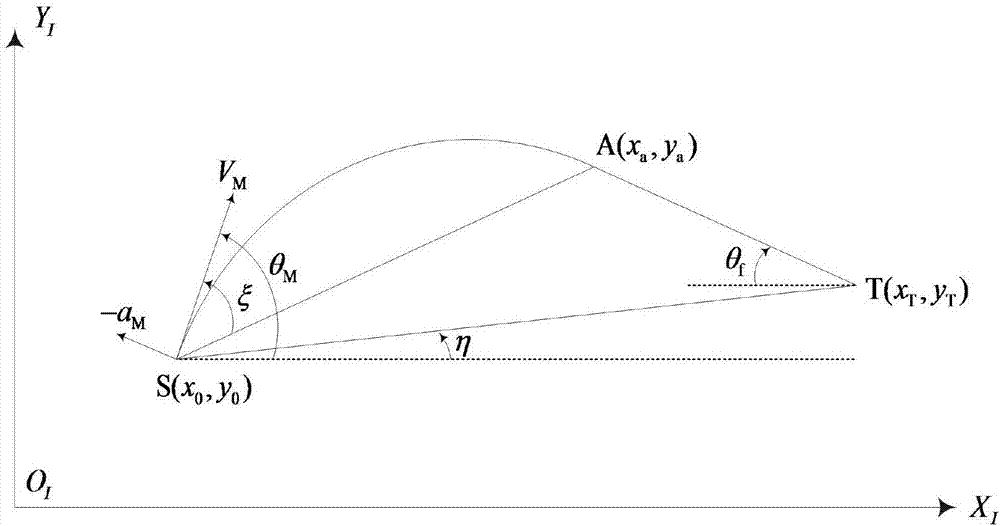
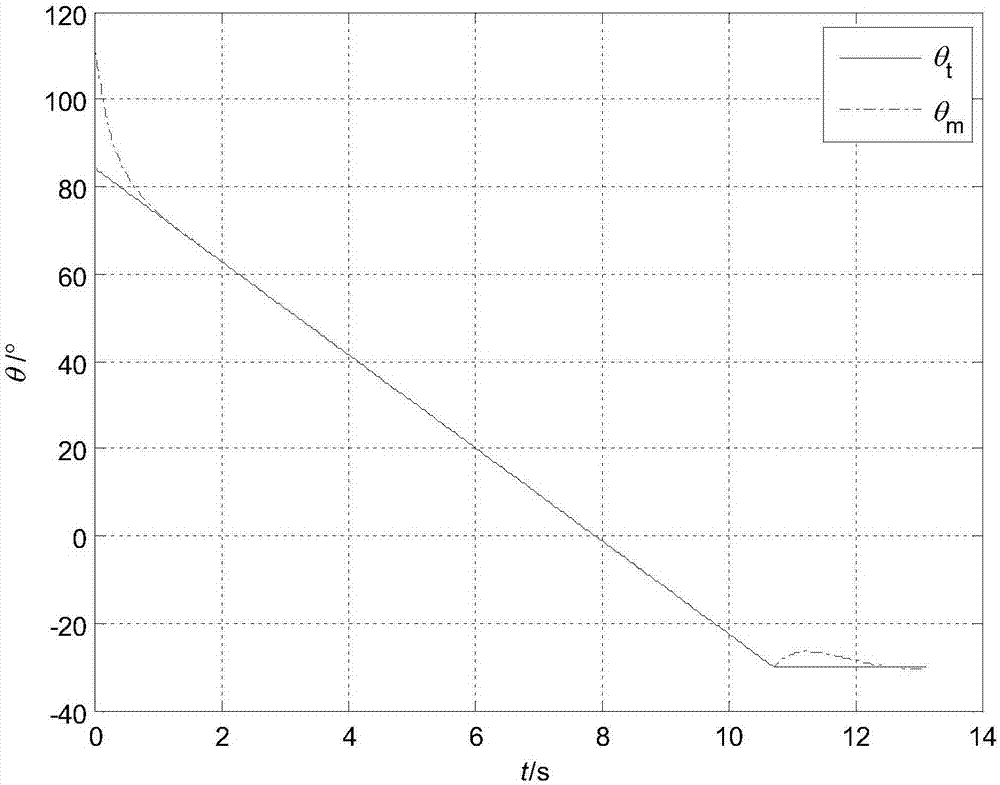
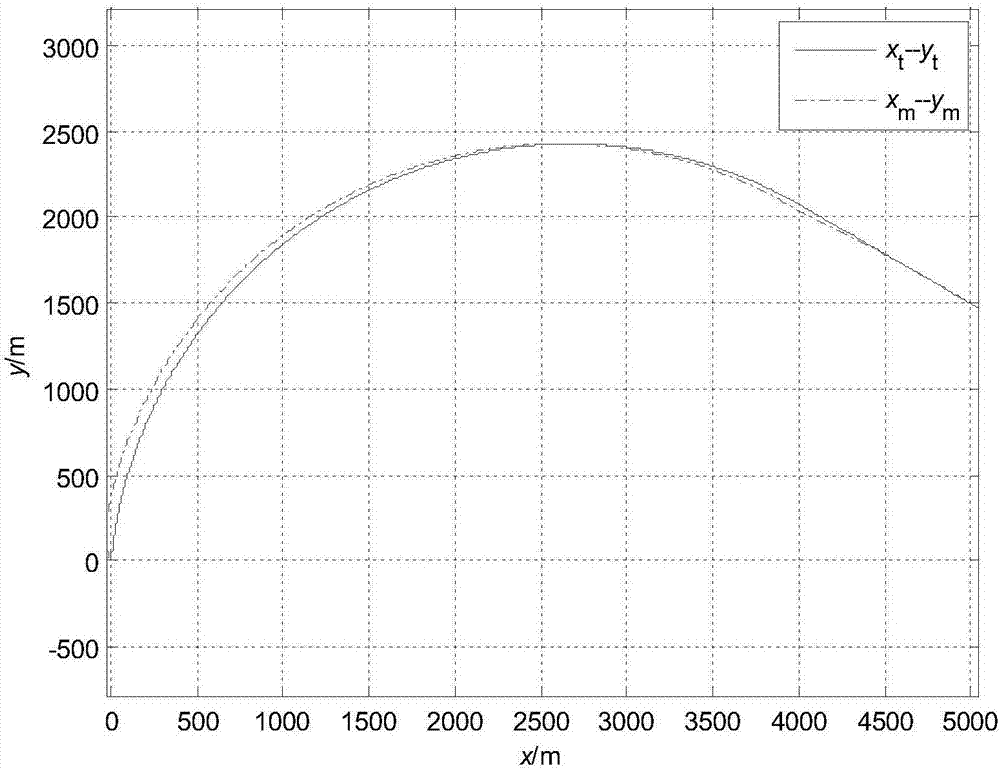
The invention discloses an attack angle and attack time control method based on trajectory planning. Firstly, a planned missile flying trajectory is assumed to be composed of an arc section SA and a line section AT, the arc section SA has a radius of R, and the line section AT passes across a target point T(xT, yT) and the requirement that the tail attack angle of the missile is thetaf is met; the arc section SA starts at the initial position S (x0, y0) of the missile and is tangent to the line section AT at a to-be-determined point A(xa, ya), and the point A(xa, ya) is obtained by specified missile attack time tf through an iterative algorithm. On the basis of trajectory planning, the invention provides a trajectory tracking control algorithm based on a virtual target; a feedforward and feedback composite control scheme is put forward in the arc section, and a sight line angle PD control scheme is put forward in the line section; and the method has a small calculation amount, and engineering implementation is facilitated.
Owner:YANTAI NANSHAN UNIV +1
Multiple missile collaborative ballistic planning method to deal with penetration
ActiveCN107818219ARadar threat is smallLow detection threatDirection controllersDesign optimisation/simulationNonlinear optimal controlRadar equation
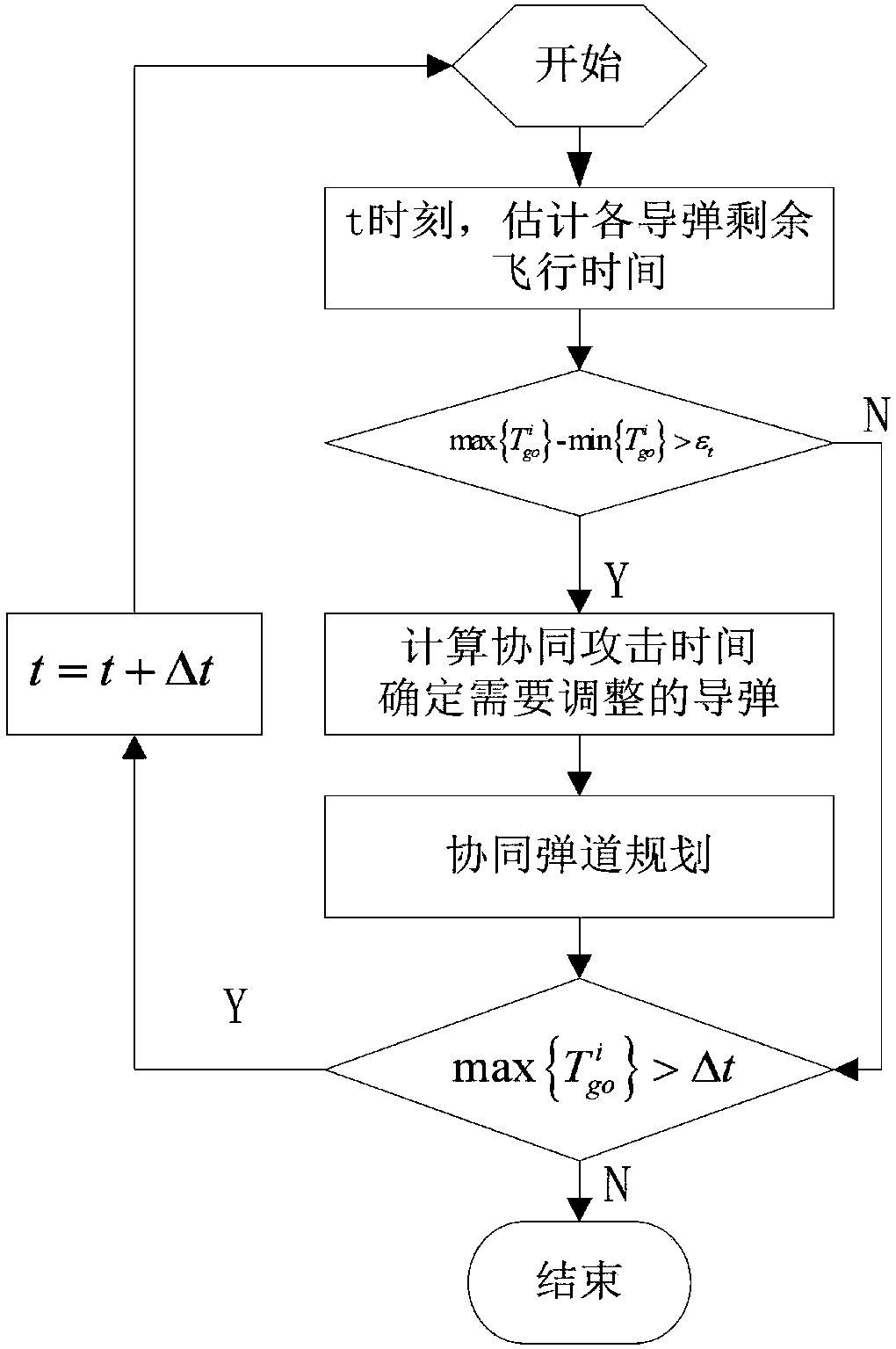
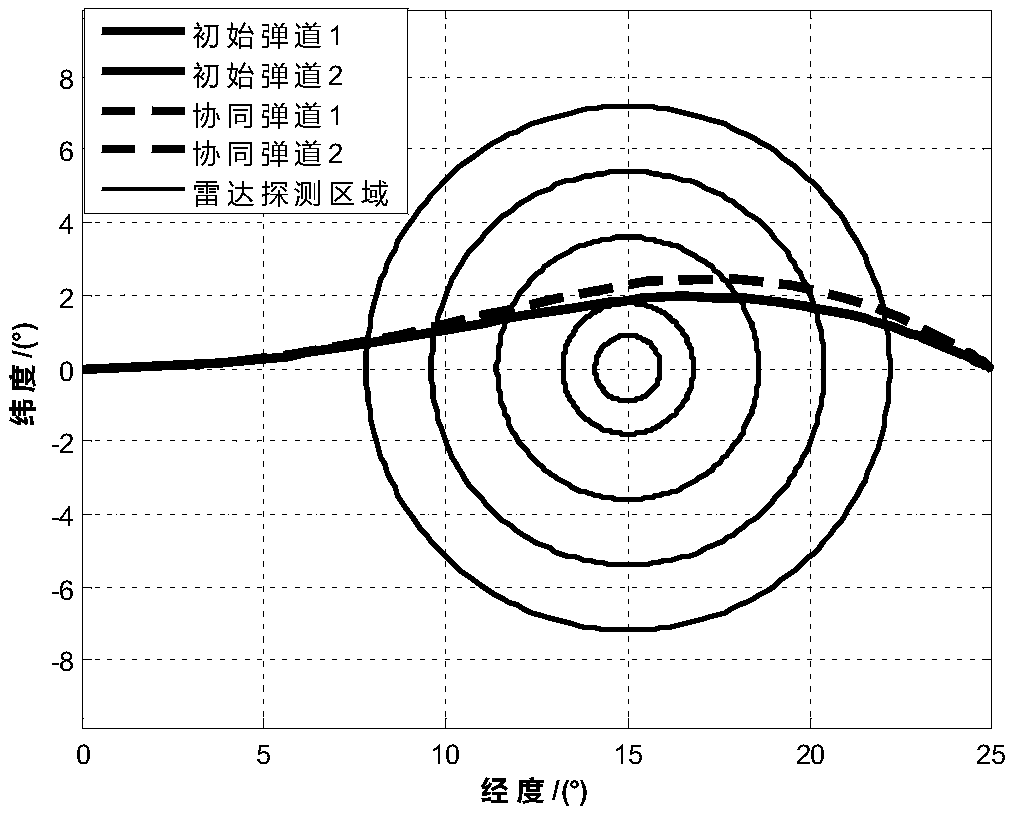
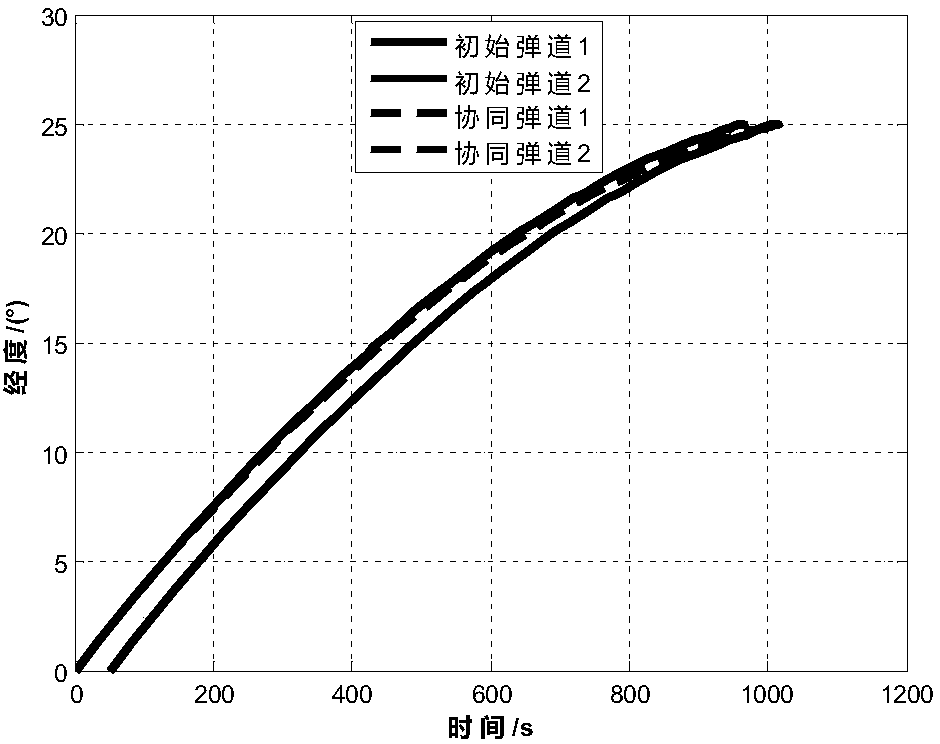
The invention provides a multiple missile collaborative ballistic planning method to deal with penetration. The method comprises the specific steps that step 1, based on the radar equation, a radar threat quantification model is established to describe the threat of a radar detection area to a missile; step 2, a collaborative control model is established, the collaborative control model comprisesa collaborative time control model and a collaborative angle control model; step 3, a collaborative attack problem is converted into a nonlinear optimal control problem which is solved based on a hp-self adaptive Radau pseudospectral method, which means at one moment of the flight, the remaining flight time of each missile is determined, whether or not a collaboration is necessary, if necessary, the time for the collaborative attack is calculated and the missile to be adjusted is determined, and the collaborative ballistic planning is conducted on the missile needs to be adjusted. According tothe multiple missile collaborative ballistic planning method, multiple missiles attacking a target on the same attacking time and with the same attacking angle is ensured; meanwhile, the radar detection threat is smallest during the flight, and the comprehensive combat effectiveness is effectively improved.
Owner:NAT UNIV OF DEFENSE TECH
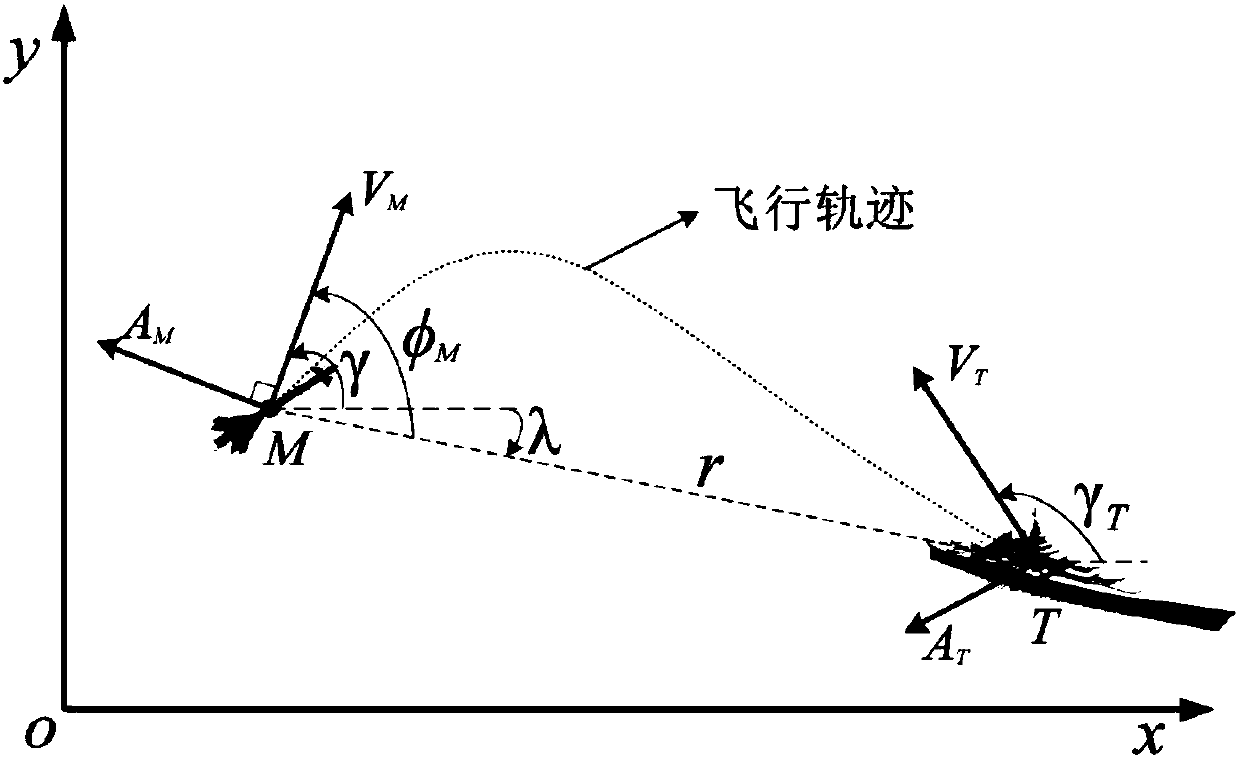
Reference sight angle signal-based design method of multi-constraint terminal guidance law
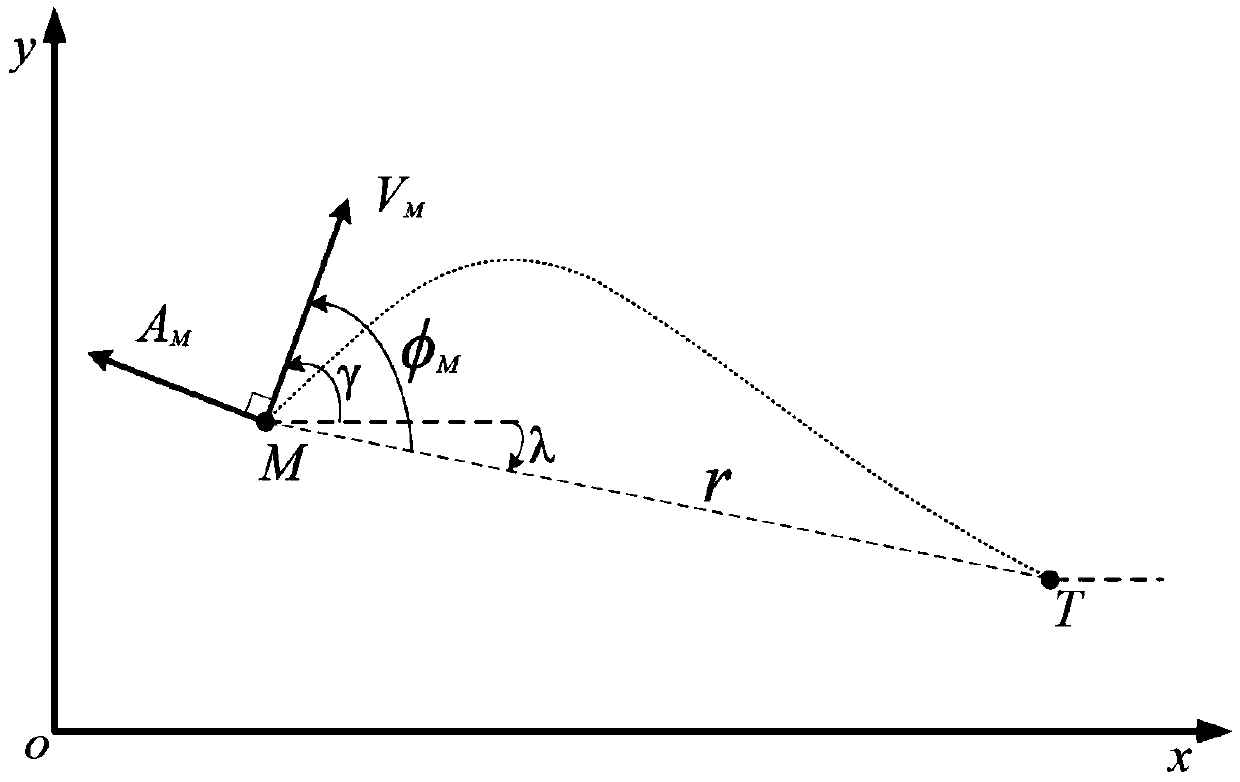
ActiveCN109597423AImprove applicabilityImprove reliabilityAttitude controlPosition/course control in three dimensionsDynamic equationClassical mechanics
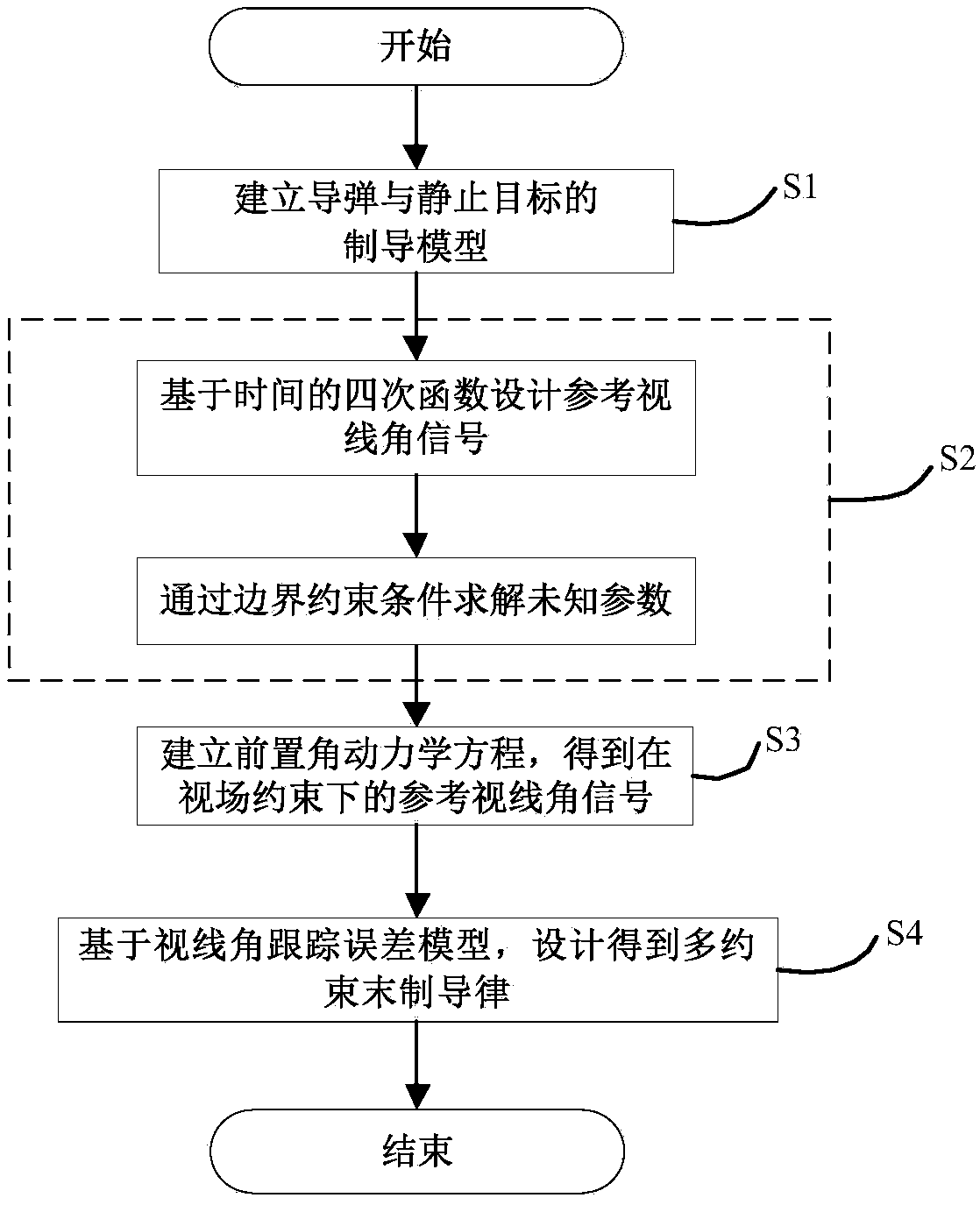
The invention discloses a reference sight angle signal-based design method of a multi-constraint terminal guidance law. The design method comprises the following steps: a guidance model of a guided missile and a static target in a horizontal plane is built, and a sight angle second-order dynamic equation is obtained; a reference sight angle signal is designed based on a quartic function of time, and unknown parameters in the reference sight angle signal are solved through boundary conditions, attack time and angle constraints; a guided missile advance angle kinetic equation is built to obtainthe reference sight angle signal expected to be tracked under a view field constraint of a guidance head; and the multi-constraint terminal guidance law is obtained based on an error model. The tracking reference sight angle signal-based method is adopted; no model linearization hypothesis exists; the residual flight time does not need to be estimated; and the method is suitable for a terminal guidance task with attack time, attack angle and guidance head view field constraints, and has relatively high applicability and relatively high reliability.
Owner:BEIHANG UNIV
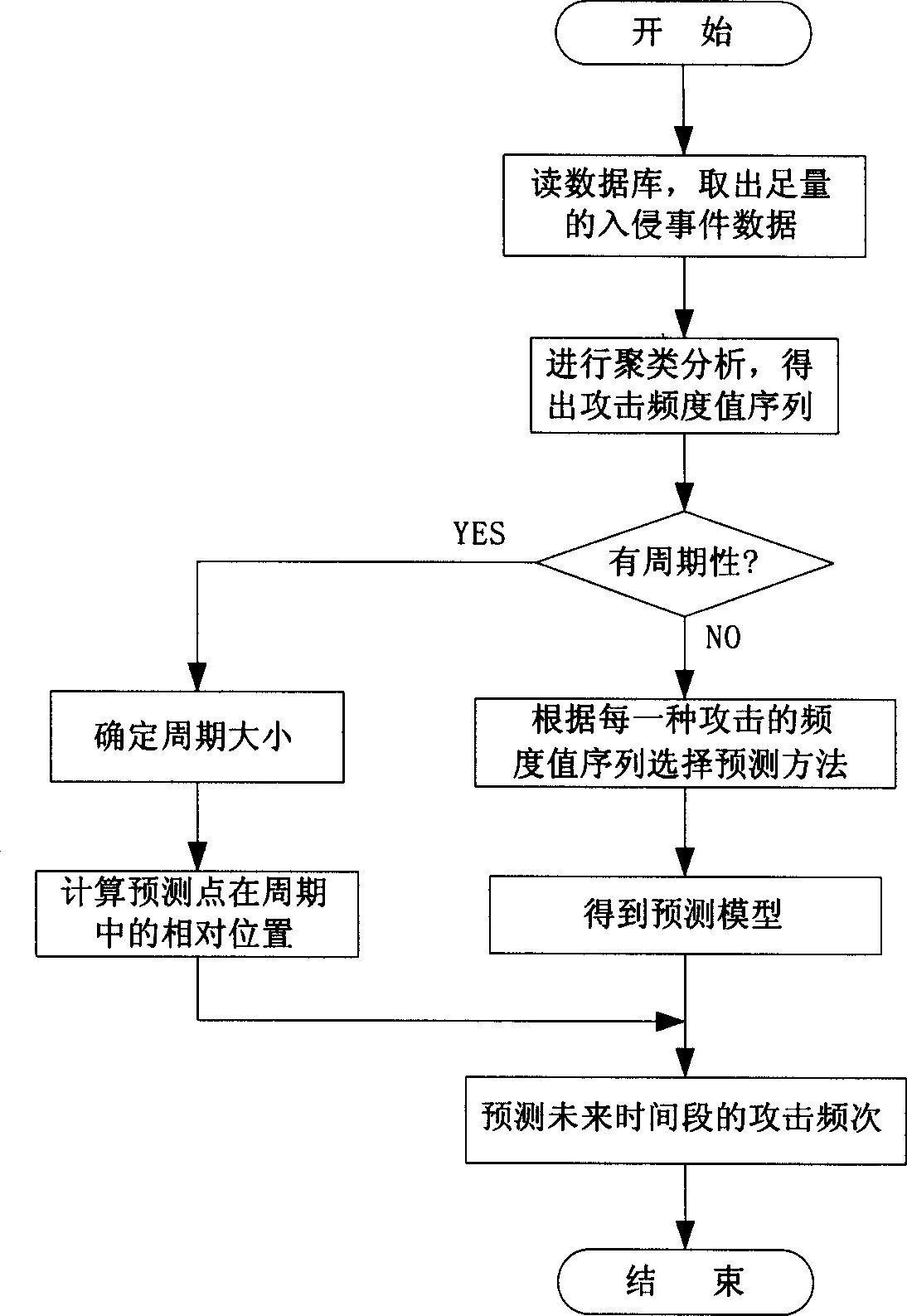
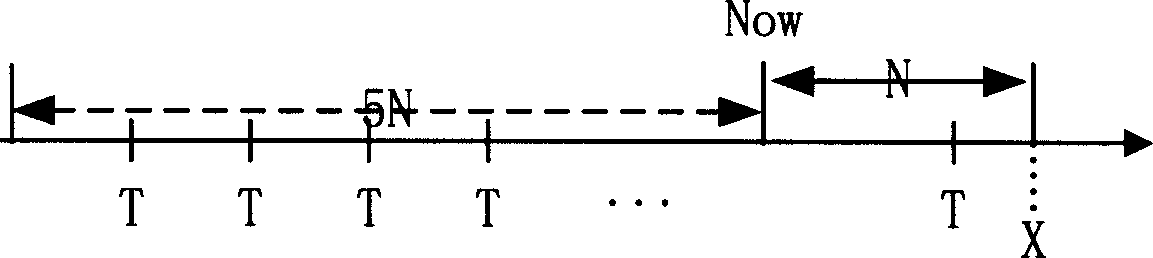
Network safety pre-warning method
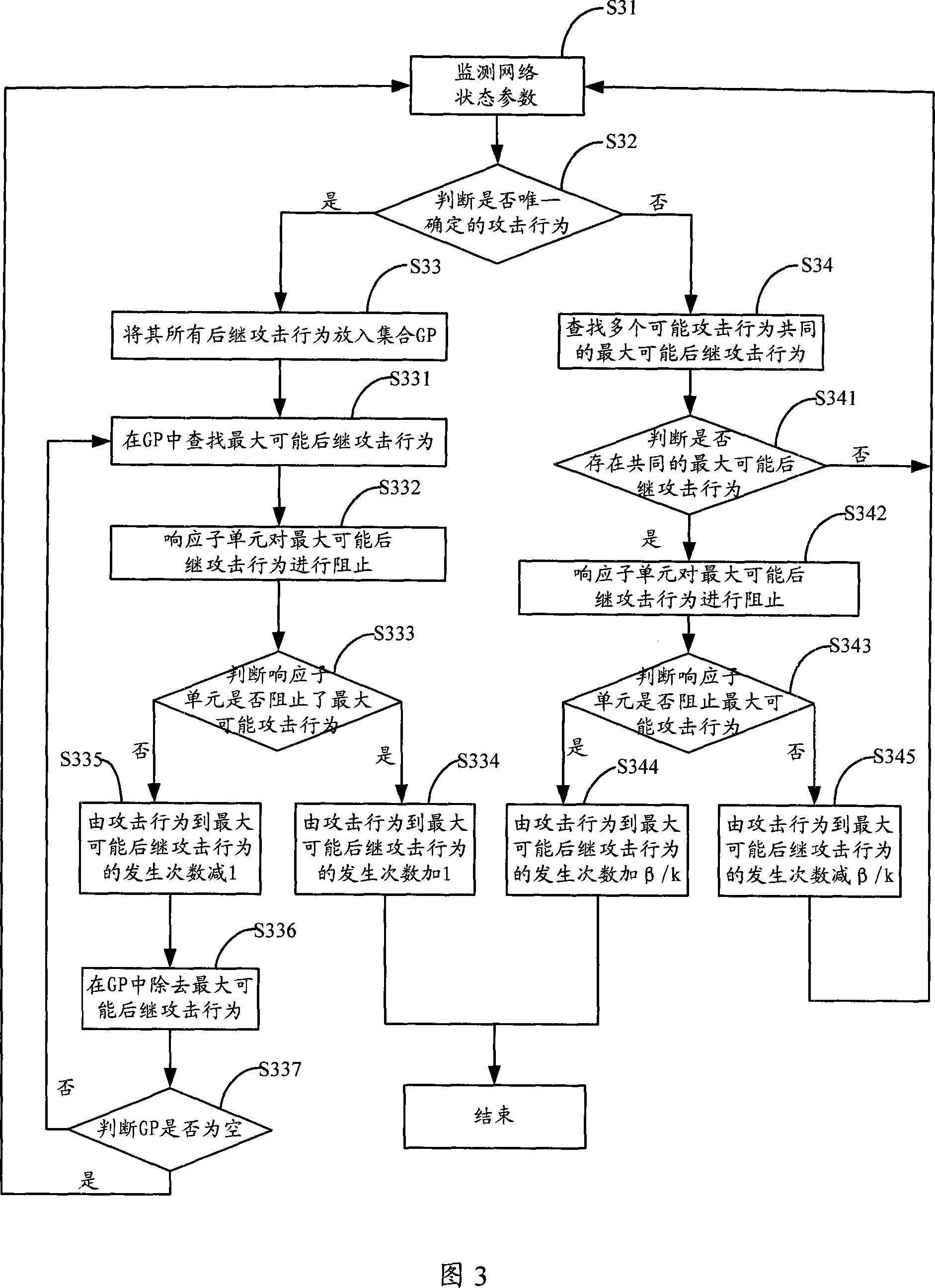
This invention discloses one network safety pre-alarming method, which comprises the following steps: a, reading database and taking enough attack affair data; b, processing the polymer analysis on the attack time to get the attack frequency values sequence; c, judging the frequency value sequence circle, if yes, then continuing; if not then executing the sixth step; d, determining circle length; e, computing predict data relative position in the circle and executing eighth step; f, selecting prediction method according to attack frequency value sequence; g, determining prediction type according to the prediction method; h, predicting future time section attack times. The method in this invention can predict future attack situations for both short and long safety trend prediction.
Owner:ZTE CORP
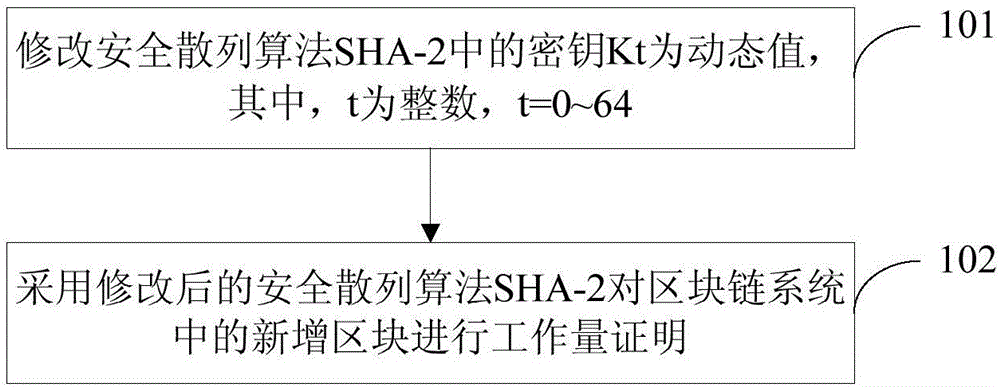
Method of carrying out proof of work on block in block chain system and device thereof
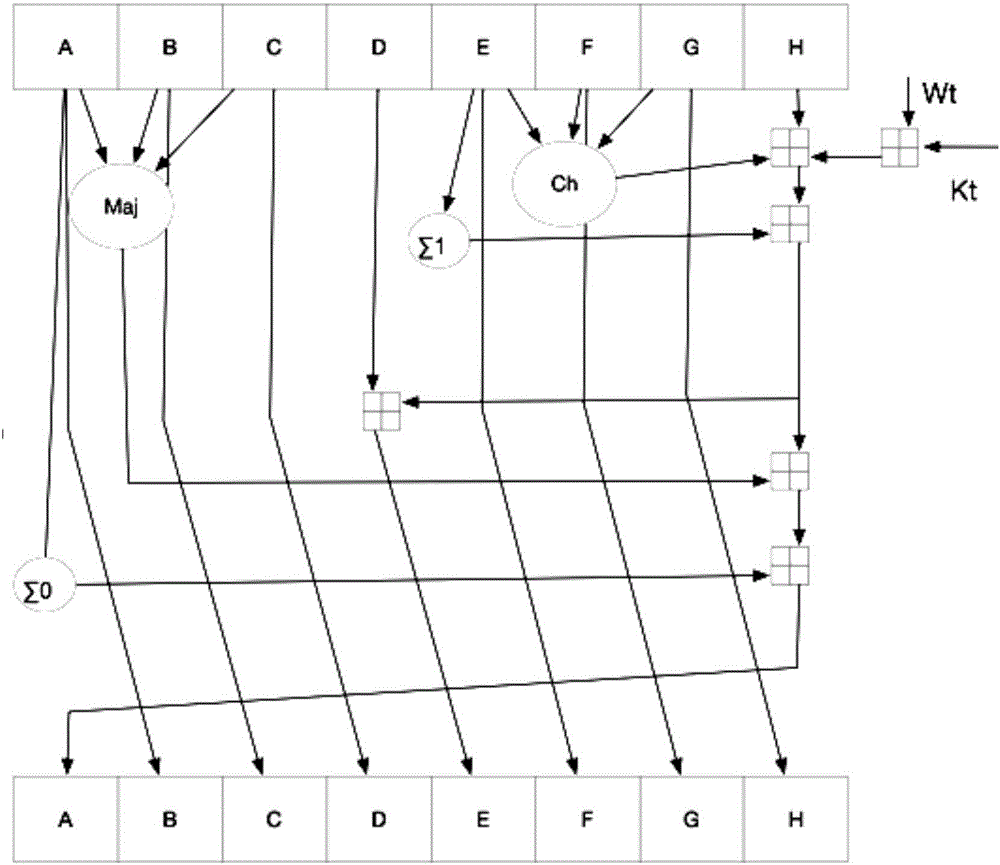
ActiveCN106571925AImprove securityImprove stabilityMultiple keys/algorithms usageUser identity/authority verificationComputer hardwareChain system
The invention provides a method of carrying out proof of work on a block in a block chain system and device thereof. The method comprises the following steps of modifying a secret key Kt in a security hash algorithm SHA-2 to be a dynamic value, wherein the t is an integer and the t equals to 1-64; and using the corrected security hash algorithm SHA-2 to carry out proof of work on a newly-increased block in the block chain system. In the prior art, a value of the secret key Kt is a fixed value. Compared to the prior art, in the invention, the value of the secret key Kt is modified to be a dynamic value and an attacker uses long time to construct a proper hash conflict so that an attack time requirement is increased, and safety and stability of the block chain system are improved.
Owner:北京云图科瑞科技有限公司
Method and apparatus for predicting network attack behaviour
InactiveCN101075917AImprove securityTo achieve the purpose of early warningPlatform integrity maintainanceData switching networksCommunications securityManagement unit
Owner:HUAWEI TECH CO LTD +1
Hearing aid
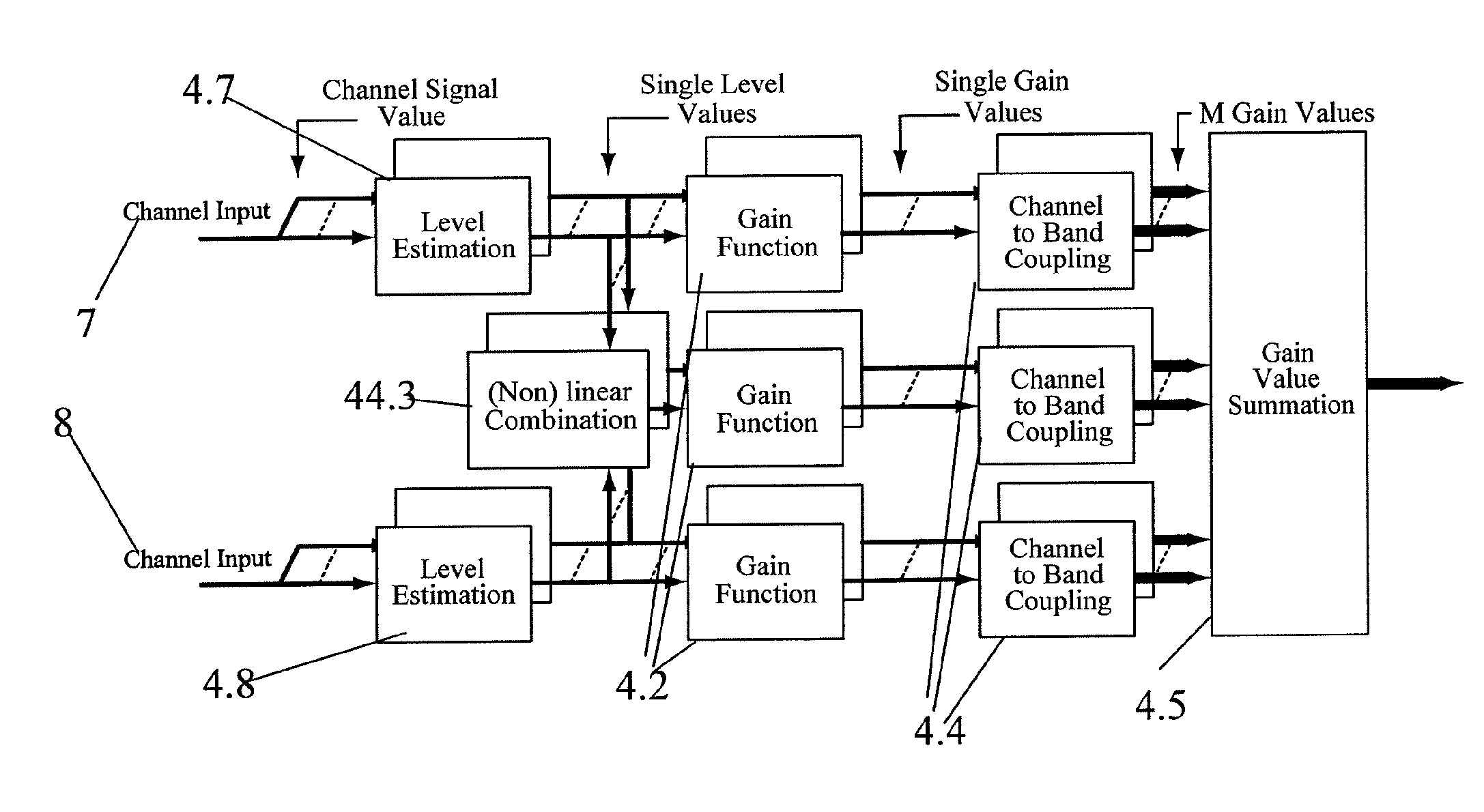
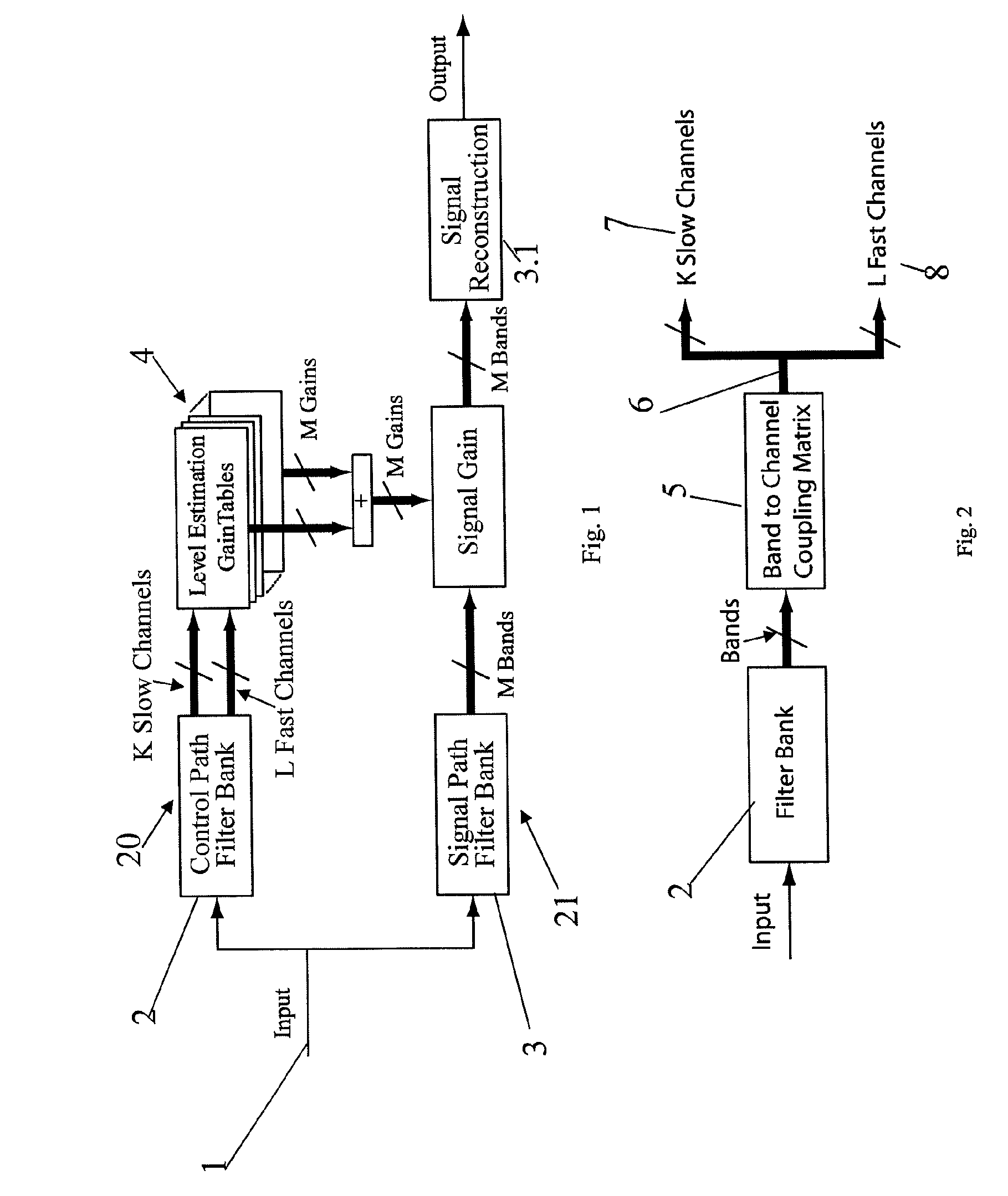
InactiveUS8165328B2Improve intelligibilityQuality improvementDeaf-aid setsCombination controlsRC time constantTelecommunications link
Owner:OTICON
Hearing aid
InactiveUS20070058828A1Avoid changeAttack time time be shortenedSignal processingGain controlAudio power amplifierRelease time
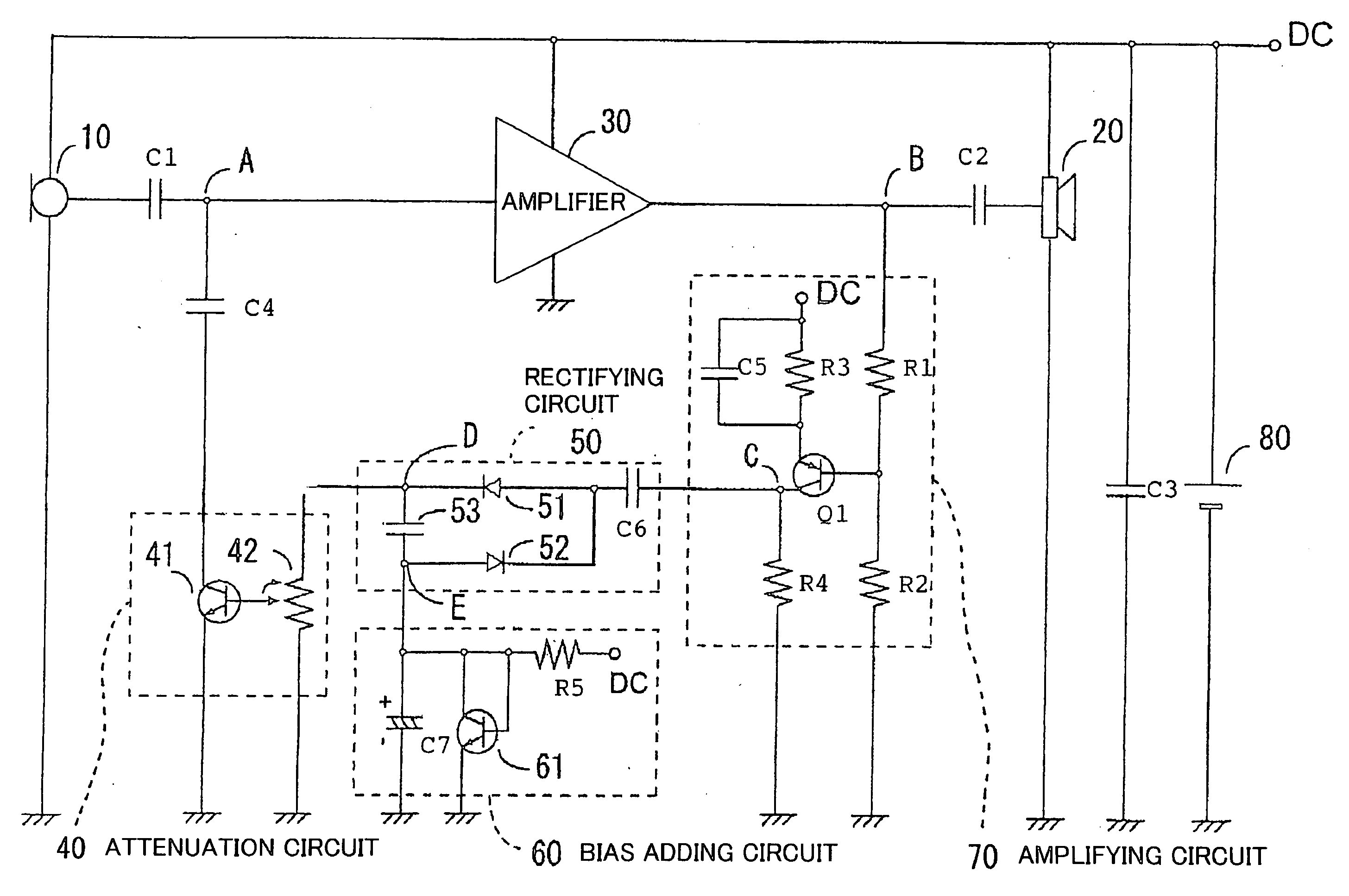
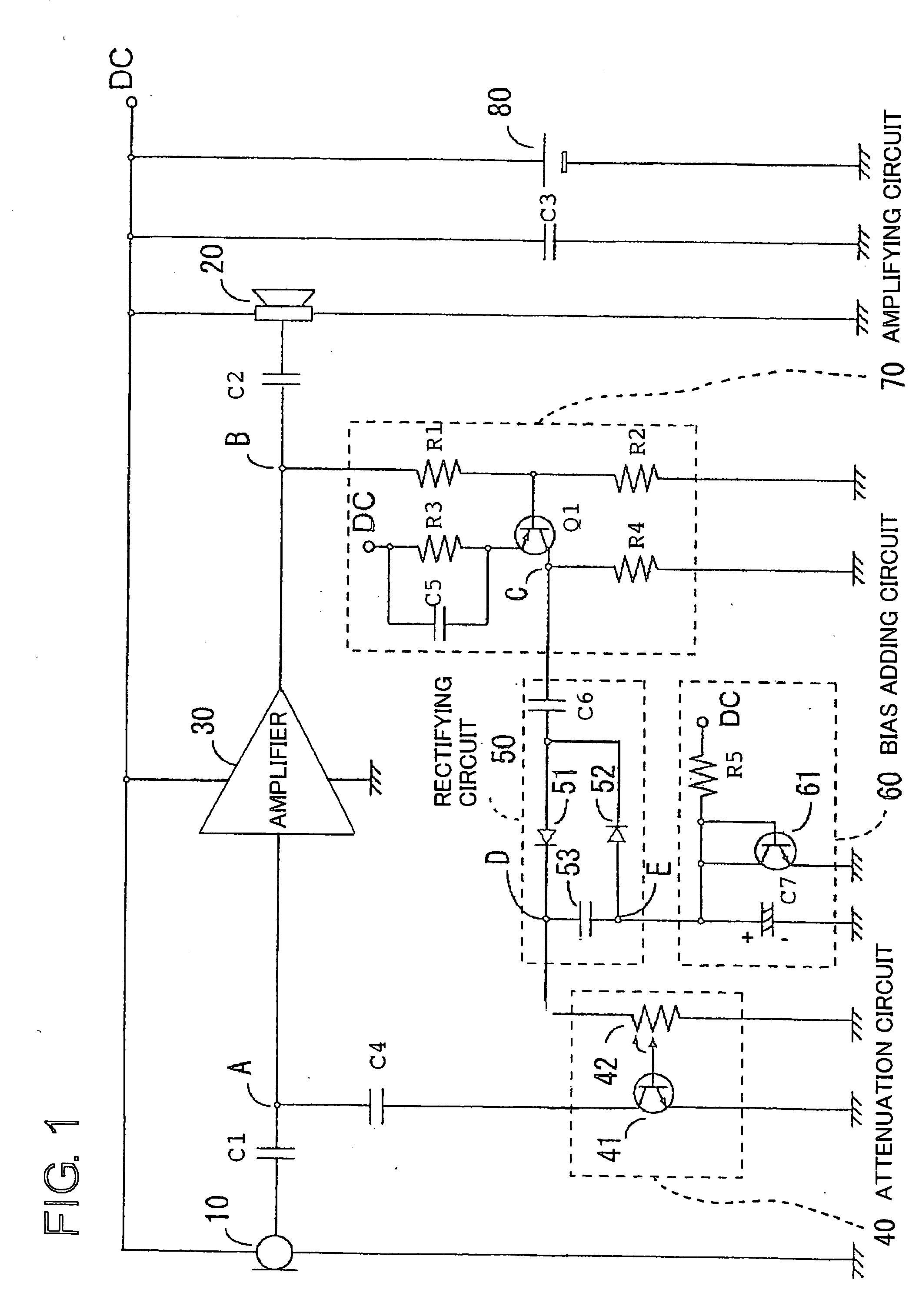
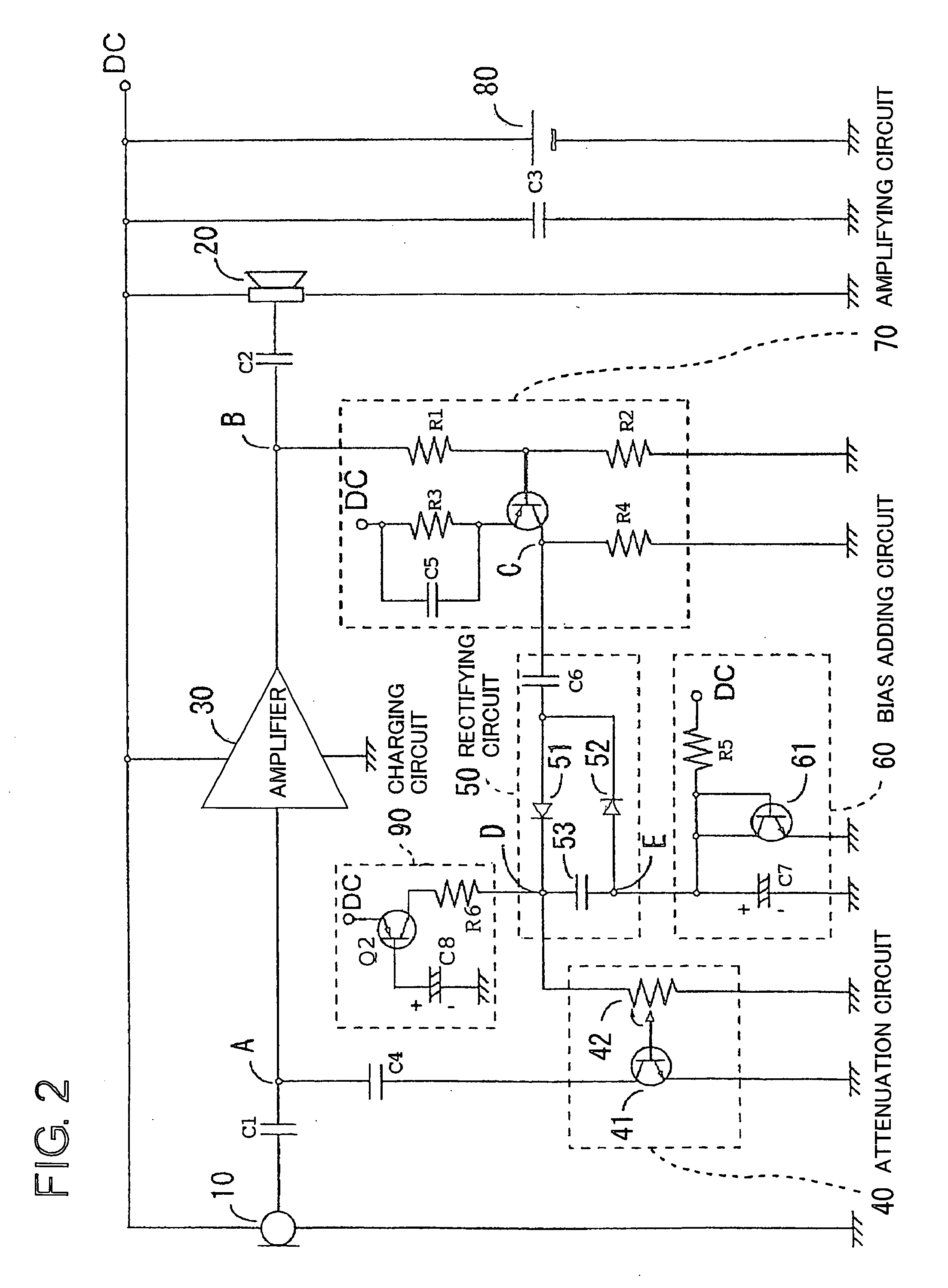
A technique is disclosed, which can shorten attack time and release time without using RC filter with time constant. According to this technique, diodes 51 and 52 rectify AC signal at output stage of an amplifier 30 by voltage doubler rectification, and a smoothing capacitor 53 smoothens the signals rectified by the diodes 51 and 52. A transistor 41 of an attenuation circuit 40 turns on when DC voltage smoothened by the smoothing capacitor exceeds a predetermined level, and level of the output signal of the amplifier is attenuated by drawing the input signal of the amplifier.
Owner:PANASONIC CORP
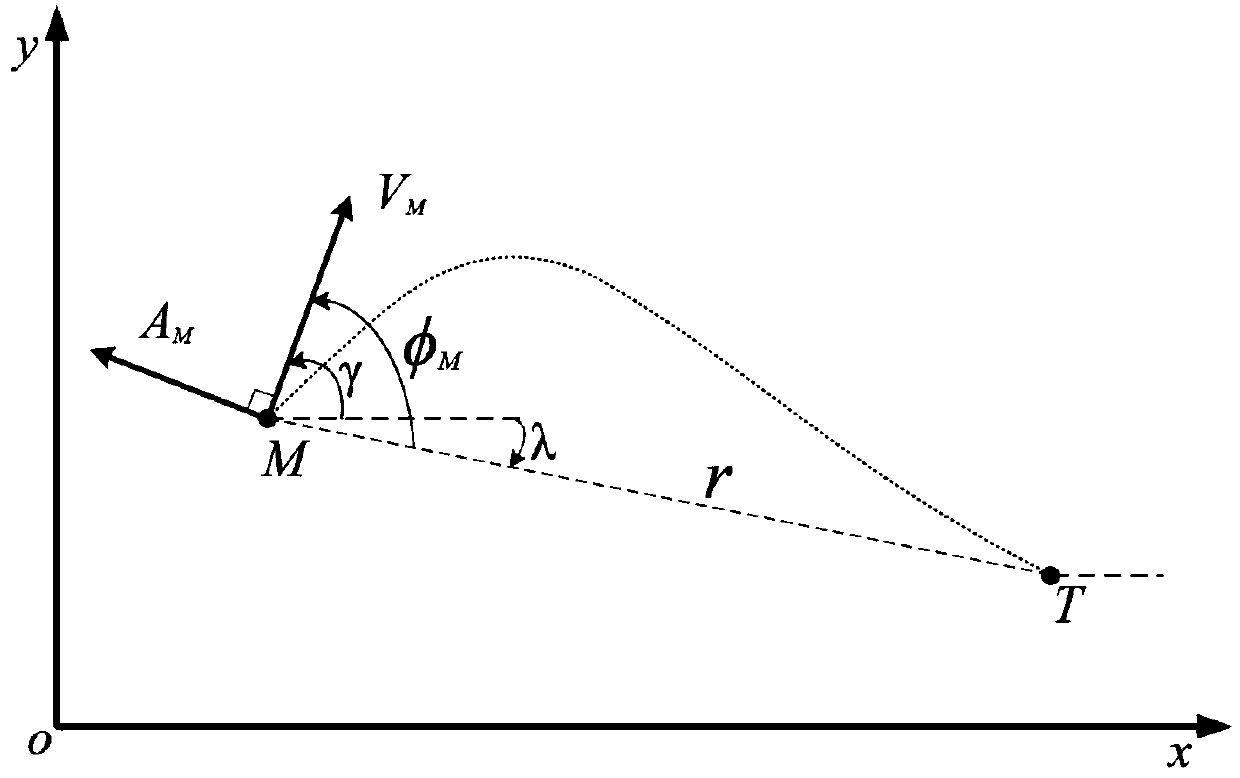
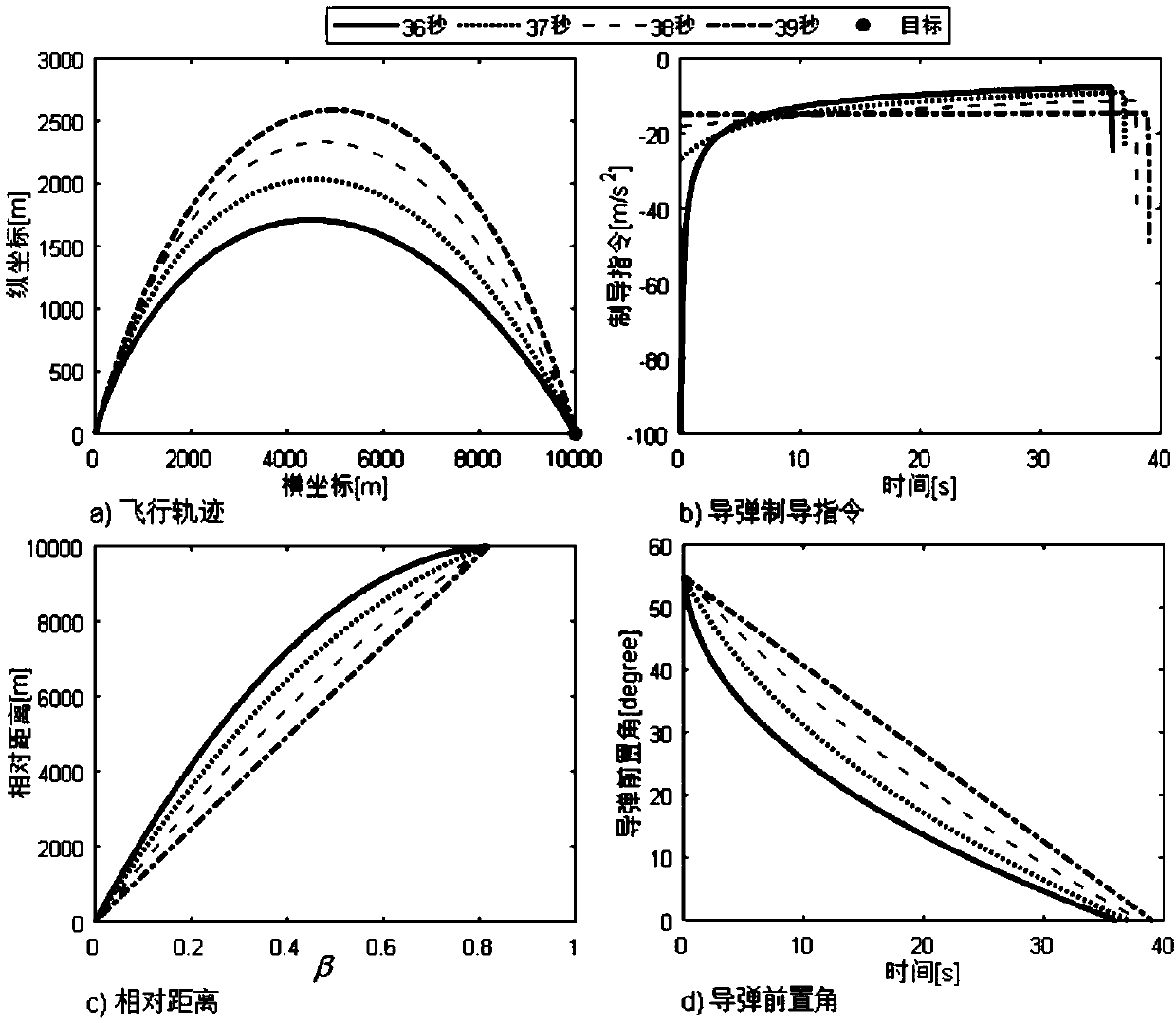
Guidance law analysis method with attack time and seeker view field constraint
ActiveCN109614756AGuaranteed Field of View ConstraintsAttack time constraintsDesign optimisation/simulationSelf-propelled projectilesDependabilityAnalysis method
The invention discloses a guidance law analysis method with attack time and seeker view field constraint. The method comprises the following steps: establishing a guidance equation of intercepting a static target in a two-dimensional horizontal plane by a missile; designing an intermediate variable related to the missile preposition angle, and converting the guidance equation into a differential equation based on the intermediate variable to obtain a guidance law expression; designing a quadratic function based on the intermediate variable as an expected relative distance curve; realizing theview field angle constraint of the seeker through the condition that the first derivative of the expected curve is greater than zero; and based on boundary conditions and attack time constraints, unknown parameters of the expected curve are solved, and a guidance law and an attack time reachable domain in an analysis form are obtained. The method adopts an analysis method based on relative distance remodeling, does not need to linearize the model, does not depend on estimation of remaining time, is suitable for guidance tasks with attack time constraint and limited strapdown seeker field of view, and has the characteristics of simple design, high reliability, strong applicability and the like.
Owner:BEIHANG UNIV
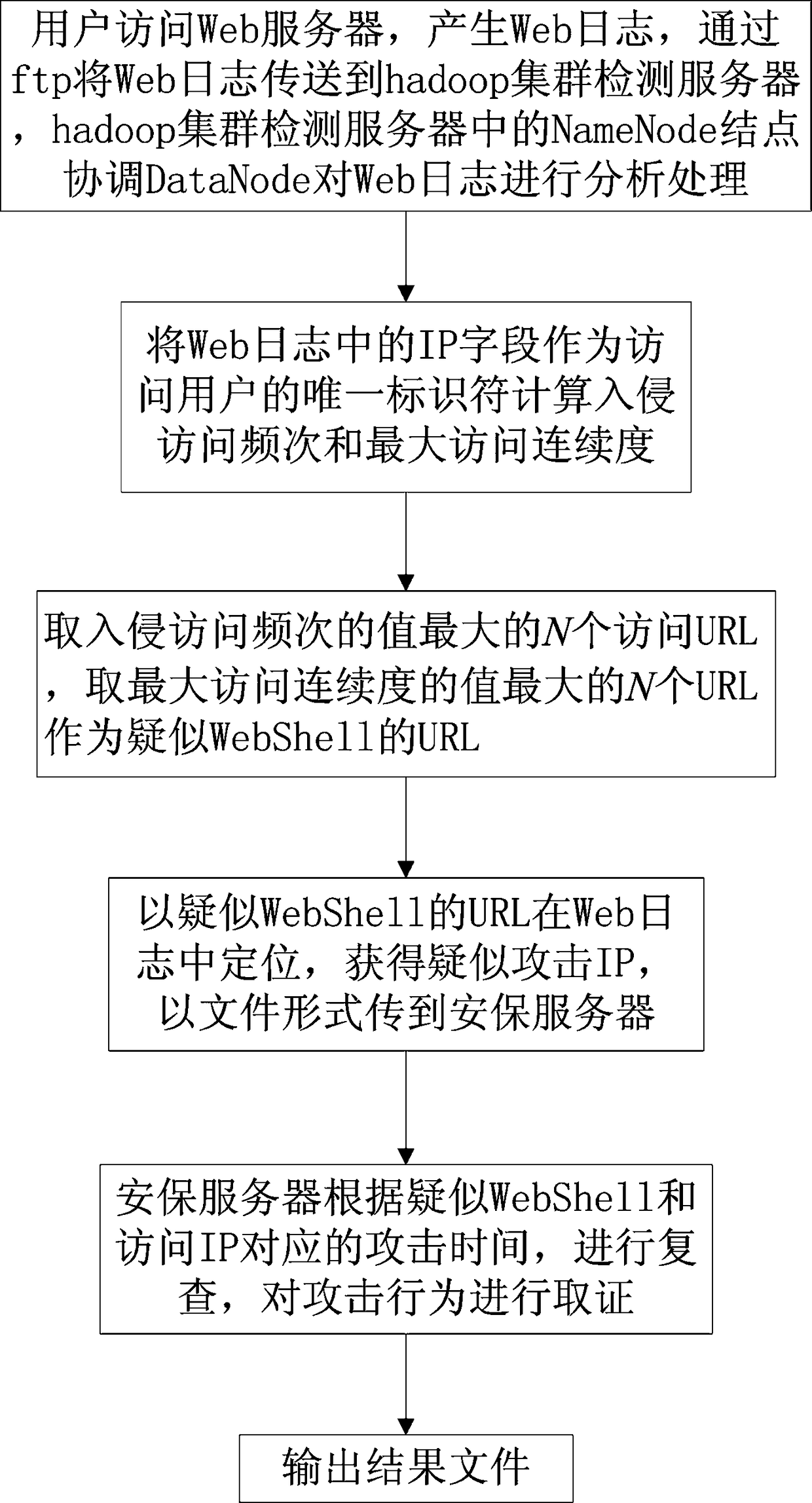
WebShell detection method
The invention relates to a WebShell detection method. A web log generated by a web server accessed by a user is preprocessed, an IP field in the web log is used as the unique identifier of the accessuser to calculate the intrusion access frequency and the maximum access continuity, and adopt the N URLs having the maximum value as the URL of the suspected WebShell, and then a suspected attack IP is acquired by carrying out the location in the Web log, and the suspected attack IP is transmitted to the security server in a form of a file, and the security server is used to review the corresponding attack time according to the suspected WebShell and the access IP, and at last, an attack behavior can be collected and output. According to the invention, attacks and even non-dynamic webpage attacks can be effectively detected, and a problem of a parsing result difference is prevented, and therefore detection of various browser attacks can be realized, a problem of a high false alarm rate caused by detection of a single index is prevented, and effective detection of unknown WebShell also can be realized.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD +1
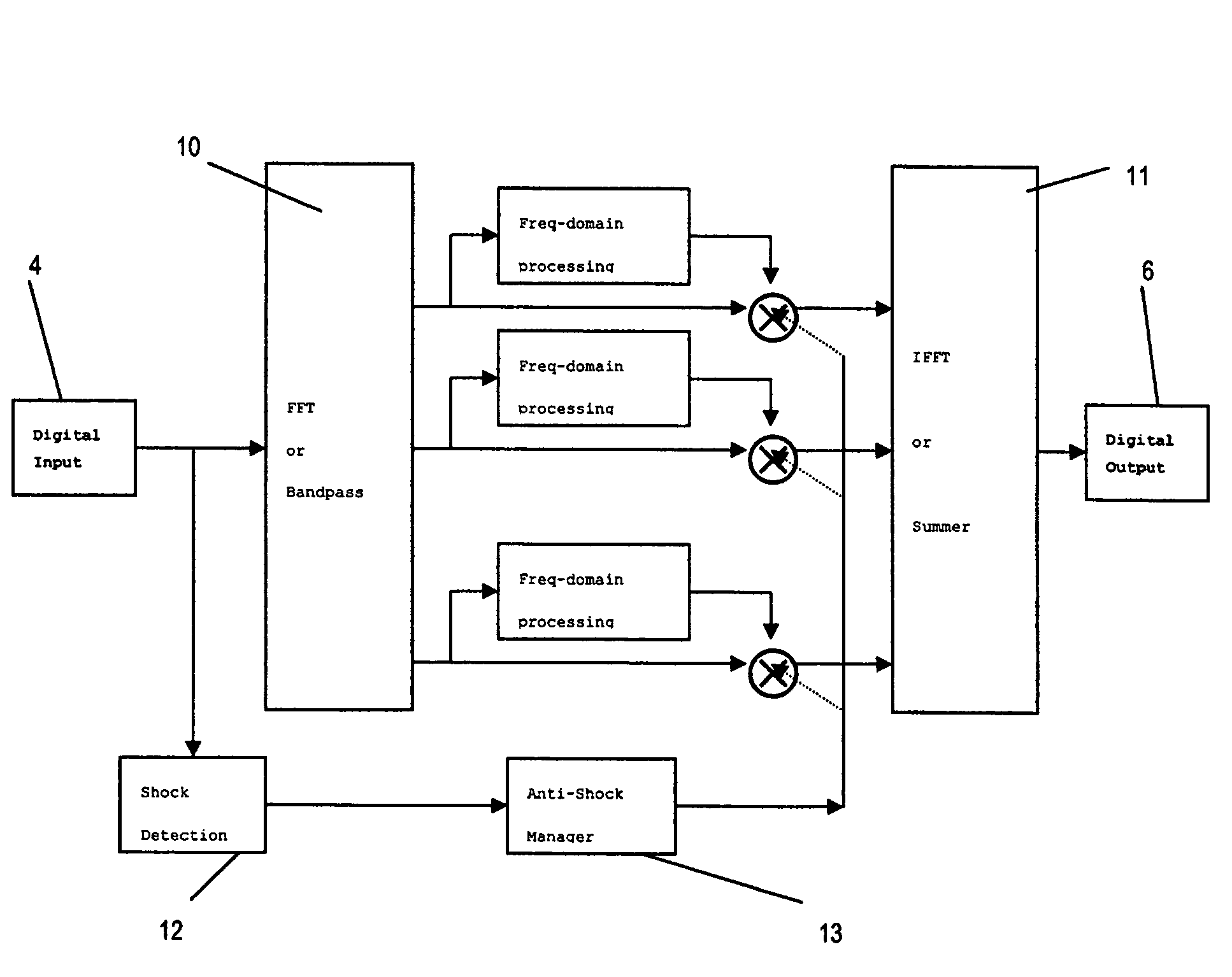
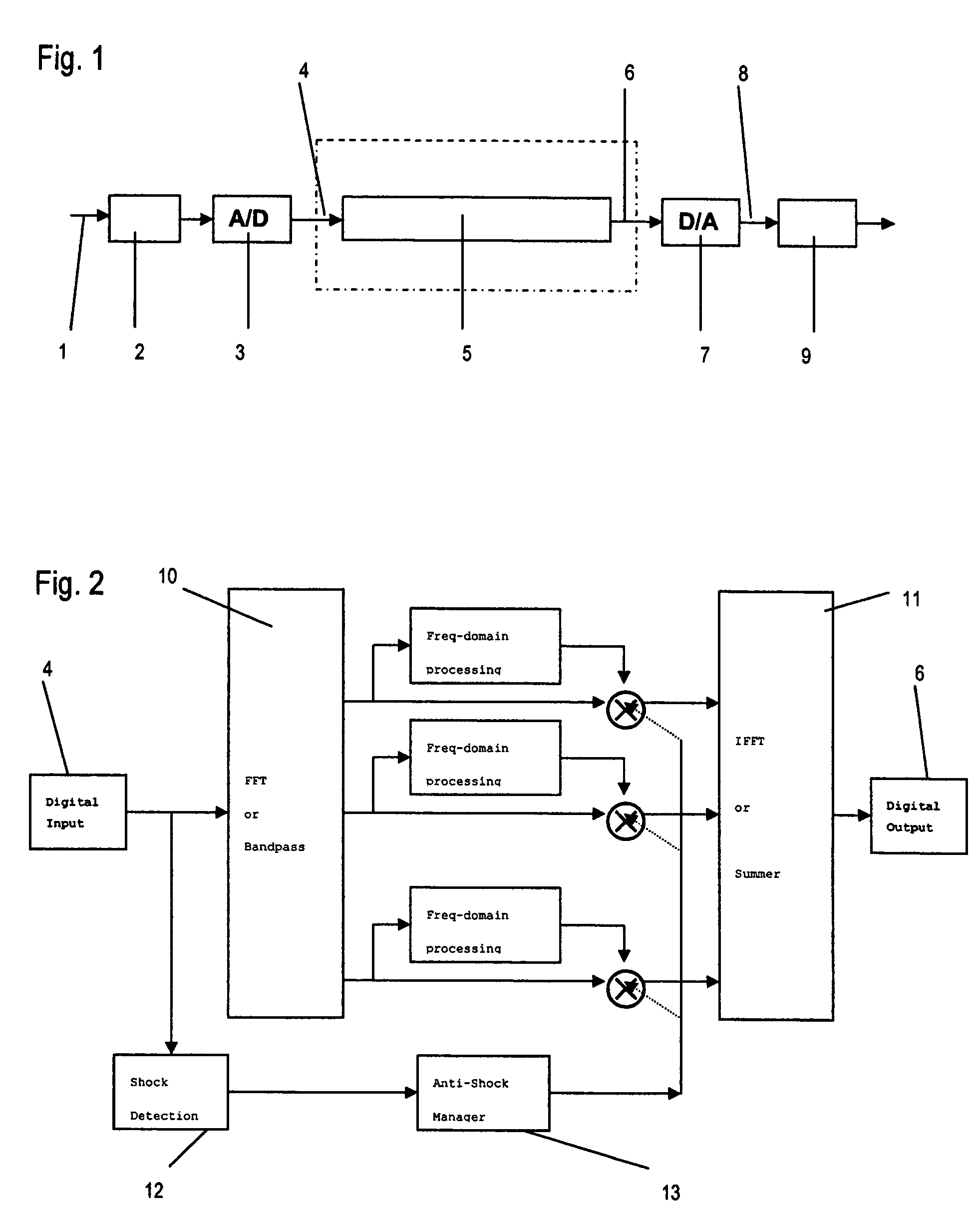
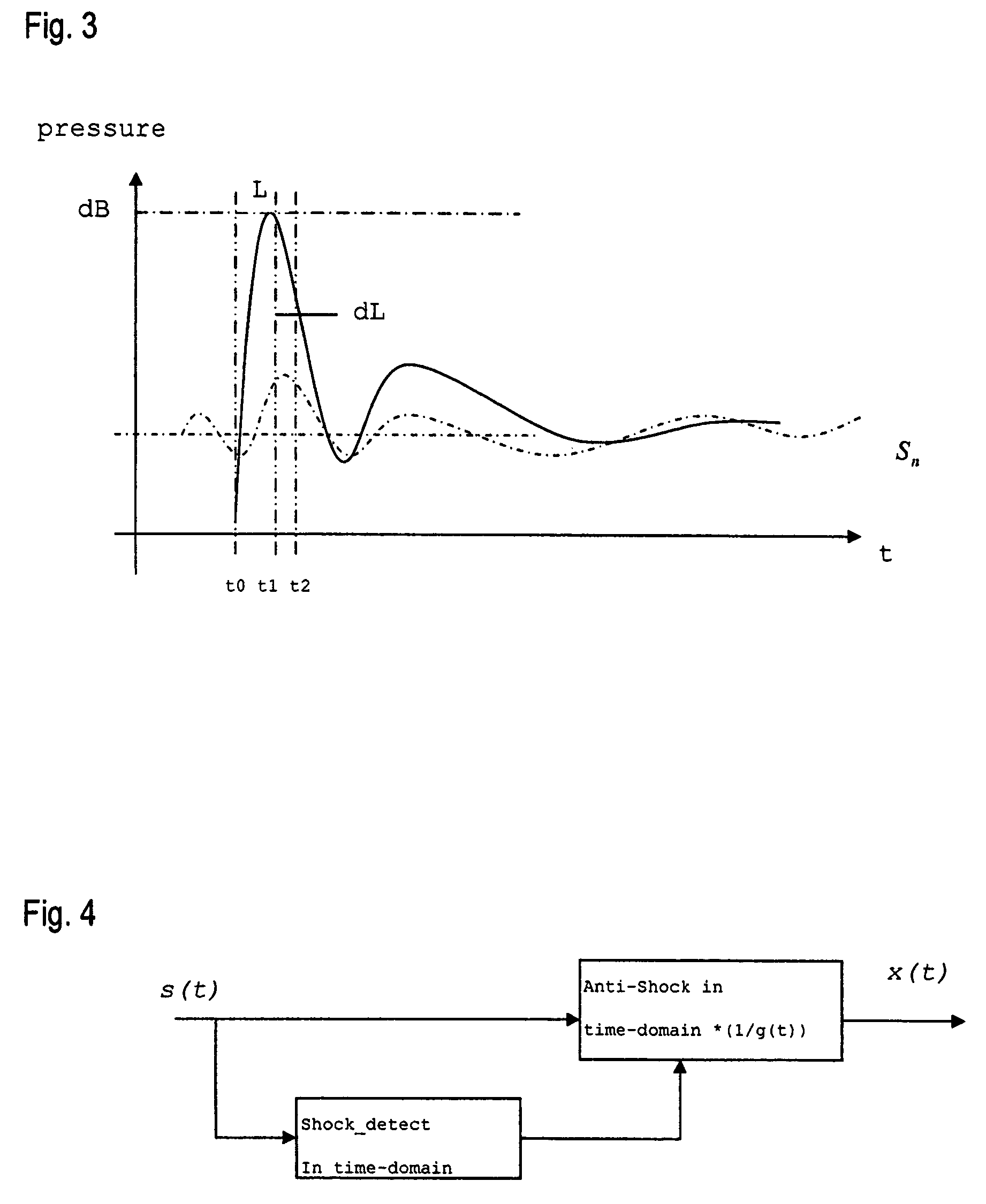
Method and system for acoustic shock detection and application of said method in hearing devices
ActiveUS7983425B2Reliably and fast detectingRapid and reliableHearing aids testing/monitoringContrast levelPresent method
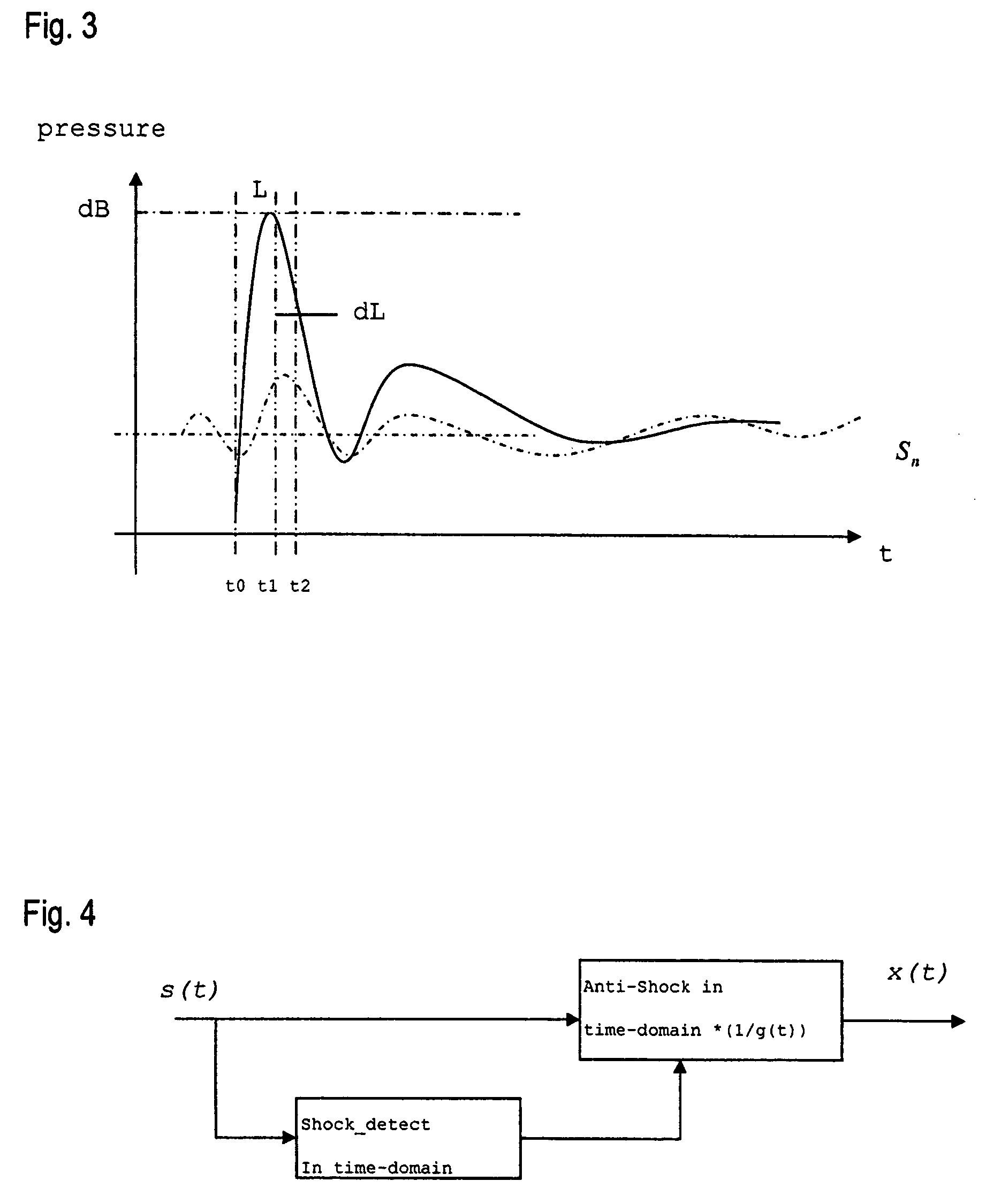
The present invention provides a method for detecting acoustic shock in an audio input signal (s(t)), comprising the steps of monitoring the input signal (s(t)) in the time-domain. Thereby detecting the signal floor (Sn), detecting the peak level of the input signal (L), detecting the attack time of the input signal (t1-t0), detecting the duration of the input signal (T). Based on those detections, determining a shock contrast level (SCL) as difference between the peak level (L) and the signal floor (Sn), determining a shock index (SI) by use of a shock index normalization constant (σ) and comparing the shock contrast level (SCL) and the shock index (SI) with respective thresholds and indicating an acoustic shock if one or both thresholds are exceeded. Thus, the present method provides a quick and reliable shock detector that operates in the time-domain. The shock detection takes place with zero time delay, or even predicts the shock before it fully goes through the signal processing.
Owner:SONOVA AG
Method for detecting persistent attack of cloud storage system
ActiveCN106612287ASuppress aggressive behaviorImprove data privacy performanceTransmissionAttack modelCloud storage system
The invention discloses a method for detecting a persistent attack of a cloud storage system, and relates to computer storage and information security. The provided method for detecting the persistent attack of the cloud storage system can realize an optimal equipment scanning time interval by adopting an intensive learning method without foreseeing a specific advanced persistent attack model, and can suppress the attack motive of an attacker, reduce the attack frequency and improve the data privacy of cloud storage. The provided method for detecting the persistent attack of the cloud storage system has the advantages that a defense system can design a detection scheme adaptive to a dynamic network and an attack mode according to the attack time interval and duration of an advanced persistent attack in cloud storage equipment and other similar information by intensive learning without knowing the specific advanced persistent attack model. The attack motive of an attacker can be suppressed, the attack frequency can be reduced, and the data privacy of cloud storage can be improved.
Owner:XIAMEN UNIV +1
Method and system for acoustic shock detection and application of said method in hearing devices
ActiveUS20070286428A1Reliably and fast detectingRapid and reliableHearing aids testing/monitoringTime domainContrast level
The present invention provides a method for detecting acoustic shock in an audio input signal (s(t)), comprising the steps of monitoring the input signal (s(t)) in the time-domain. Thereby detecting the signal floor (Sn), detecting the peak level of the input signal (L), detecting the attack time of the input signal (t1-t0), detecting the duration of the input signal (T). Based on those detections, determining a shock contrast level (SCL) as difference between the peak level (L) and the signal floor (Sn), determining a shock index (SI) by use of a shock index normalization constant (σ) and comparing the shock contrast level (SCL) and the shock index (SI) with respective thresholds and indicating an acoustic shock if one or both thresholds are exceeded. Thus, the present method provides a quick and reliable shock detector that operates in the time-domain. The shock detection takes place with zero time delay, or even predicts the shock before it fully goes through the signal processing.
Owner:SONOVA AG
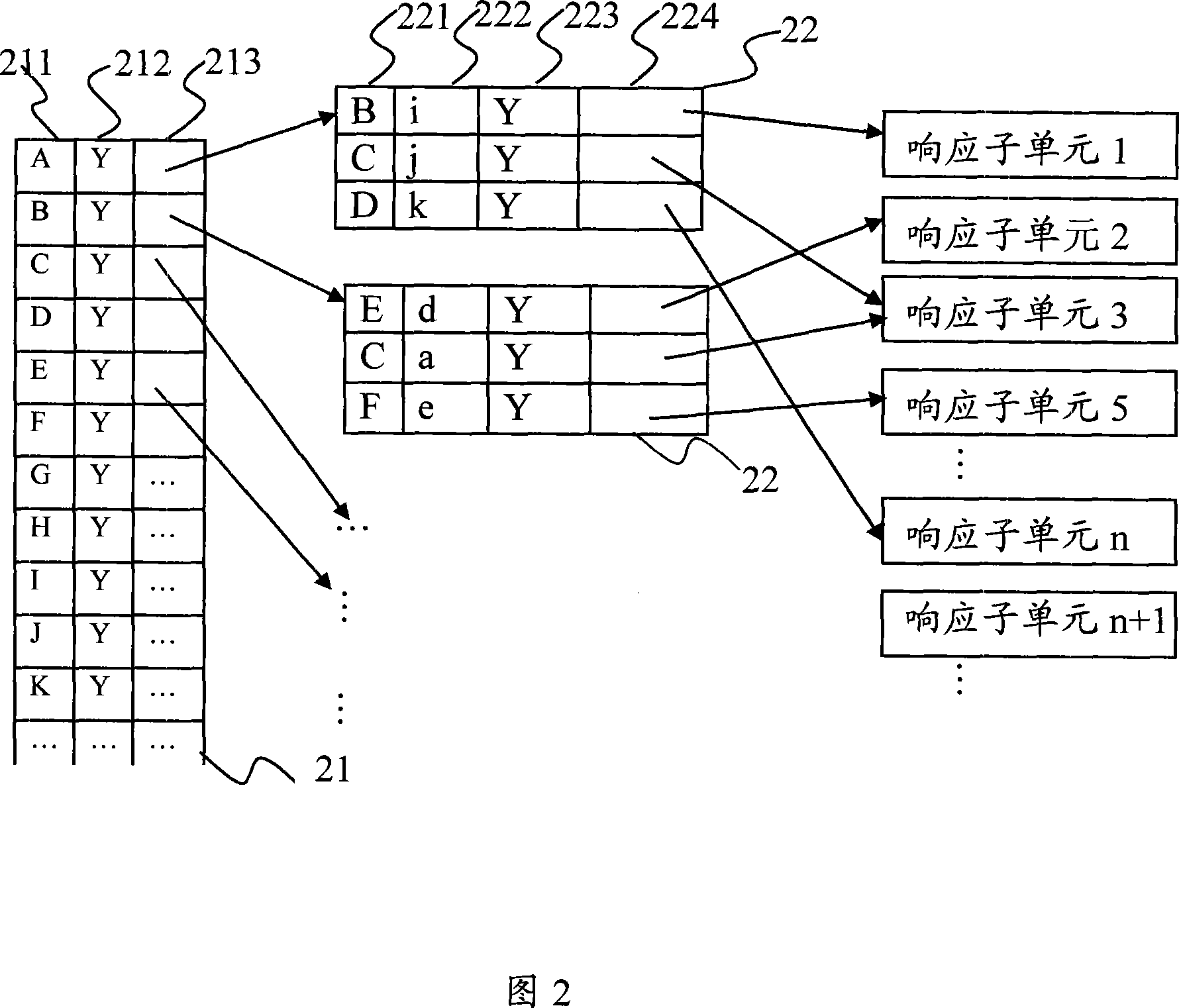
Method, device and system for detecting multiple attack behaviors
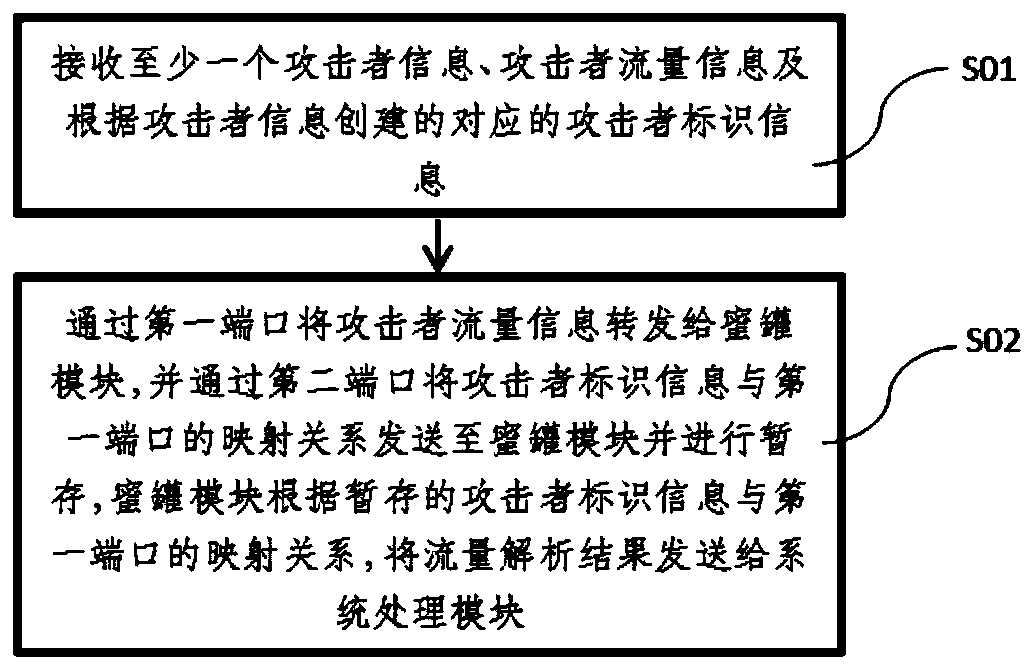
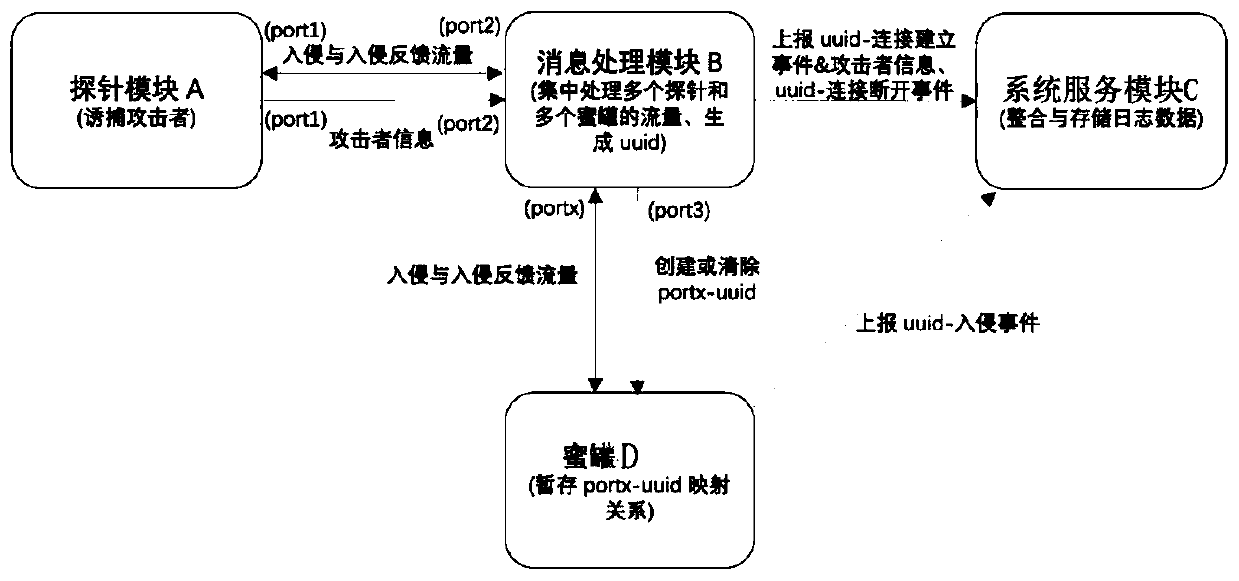
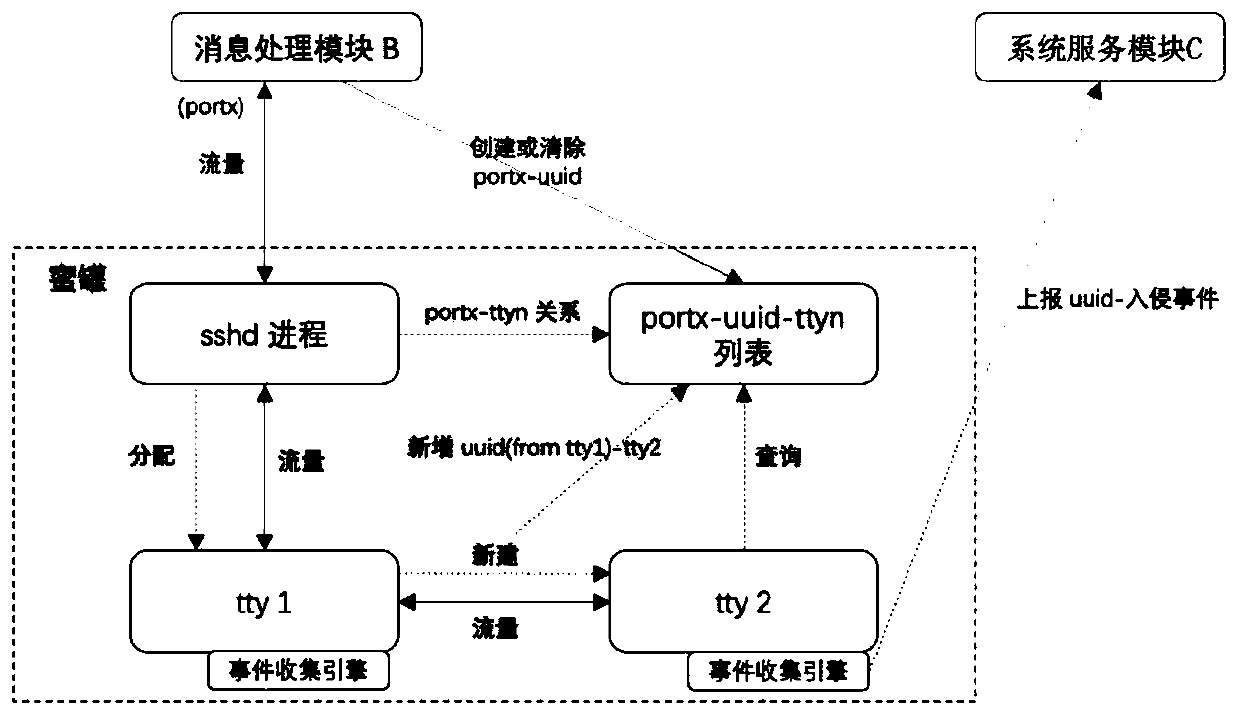
The embodiment of the invention discloses a method for acquiring multiple pieces of attack behavior information. The method comprises the following steps: receiving at least one piece of attacker information, attacker flow information and corresponding attacker identification information created according to the attacker information; forwarding the attacker flow information to the honeypot throughthe first port; sending the mapping relationship between the attacker identification information and the first port to the honeypot through the second port and temporarily storing the relationship; and enabling a honeypot to send the flow analysis result to the system service module according to the temporarily stored mapping relationship between the attacker identification information and the first port. According to the technical scheme disclosed by the invention, the effect of completely recording and restoring the attack timeline under the condition of multi-node management can be achieved.
Owner:北京长亭未来科技有限公司
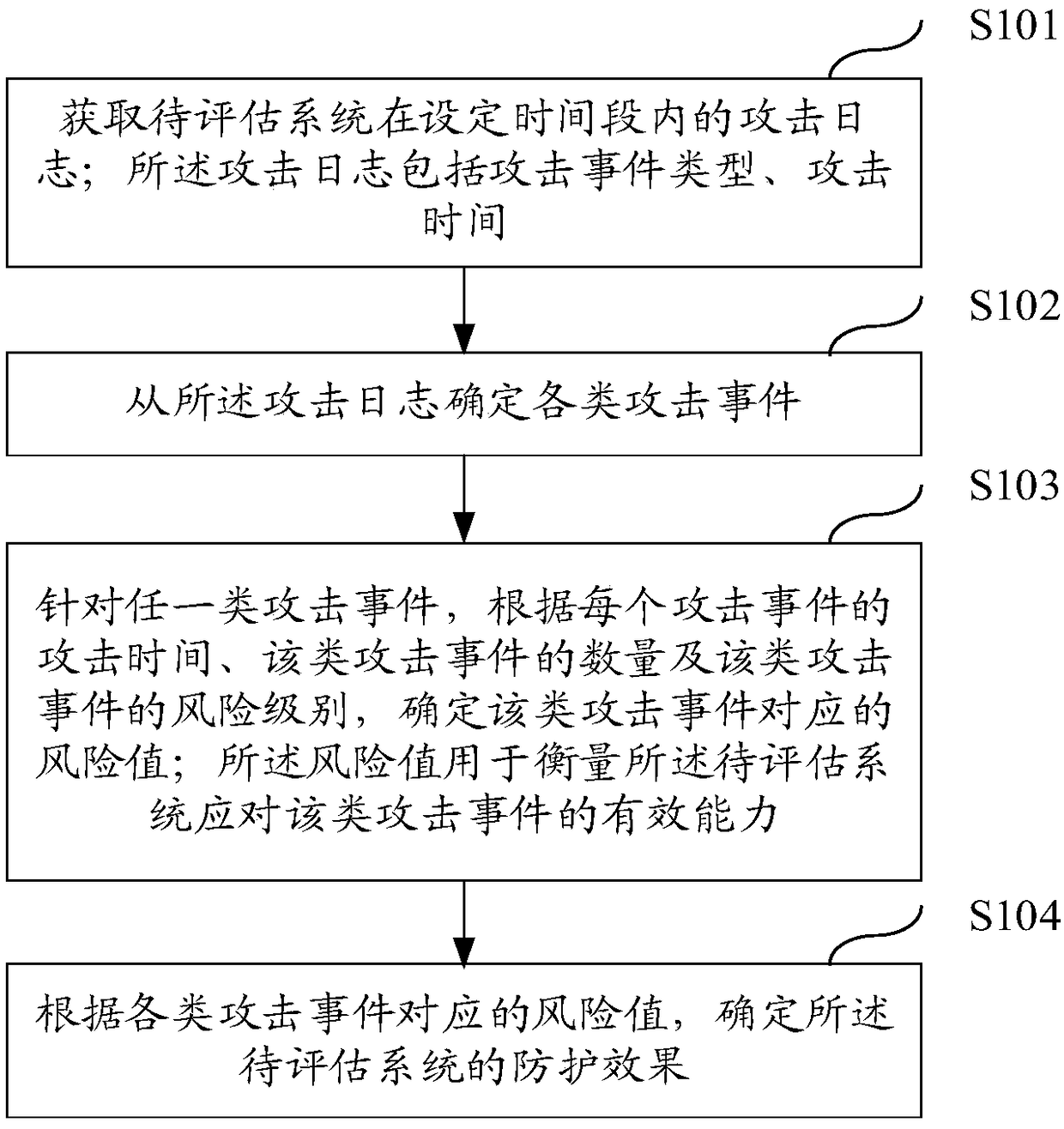
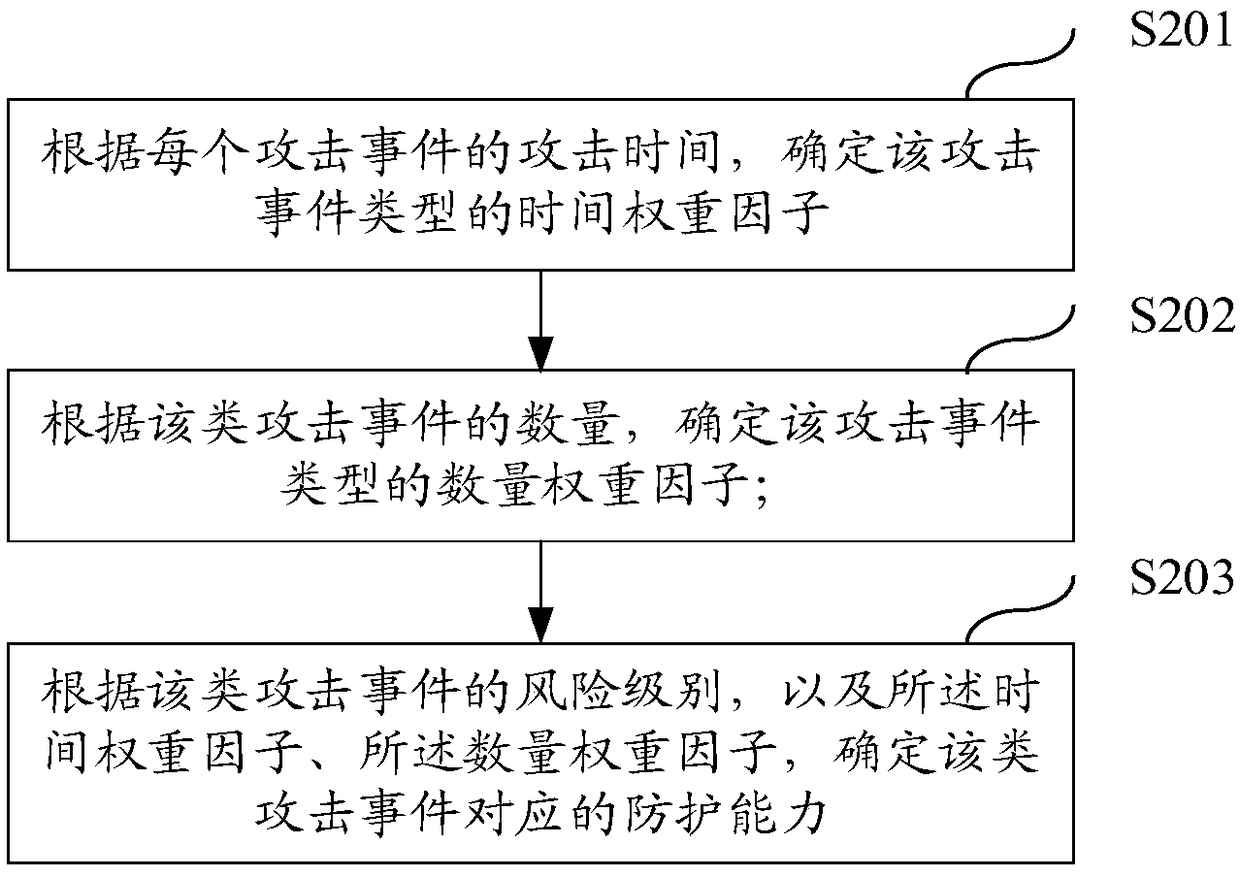
Method and device for determining Web application protecting effect
ActiveCN108229176ADetermining the effectiveness of protectionPlatform integrity maintainanceRisk levelEvent type
The embodiment of the invention discloses a method and device for determining the Web application protecting effect. The method comprises the steps of obtaining an attacking log within a set durationof a to-be-evaluated system, and determining all kinds of attacking accidents according to the types and attacking times of the attacking accidents; determining the risk value of each type of attacking accident according to the attacking time, the number of the attacking accidents and the risk level of the attacking accident; then determining the protecting effect value of the to-be-evaluated system according to the risk values of all kinds of attacking accidents. As can be seen, since the risk values of all kinds of attacking accidents can be independently measured according to two factors ofthe attacking times and the number of the attacking accidents, and the risk value of each kind of attacking accident can show the attacked severity degree of the to-be-evaluated system when the accident takes place and show the protecting effect of sites under the to-be-evaluated system, and therefore, the overall protecting effect and the attacked severity degree of the to-be-evaluated system can be accurately and visually determined according to all the risk values.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
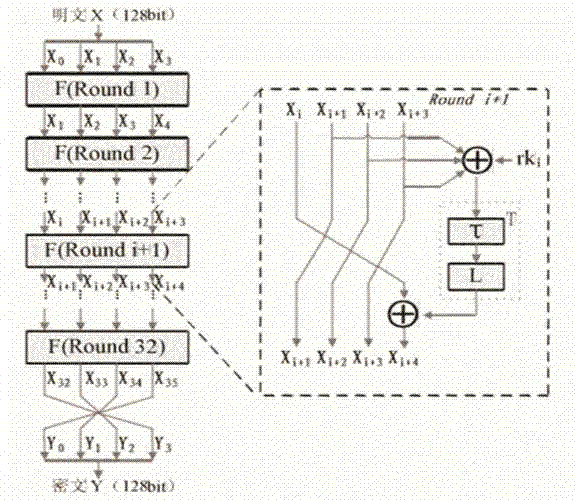
Side channel energy attack method aiming at SM4 password round function output
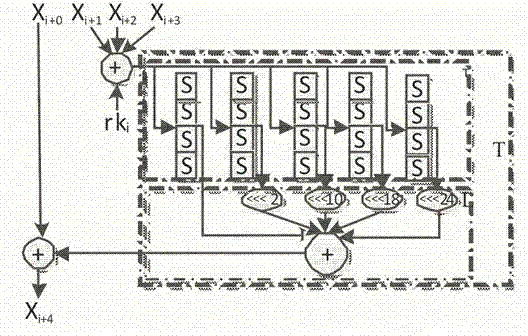
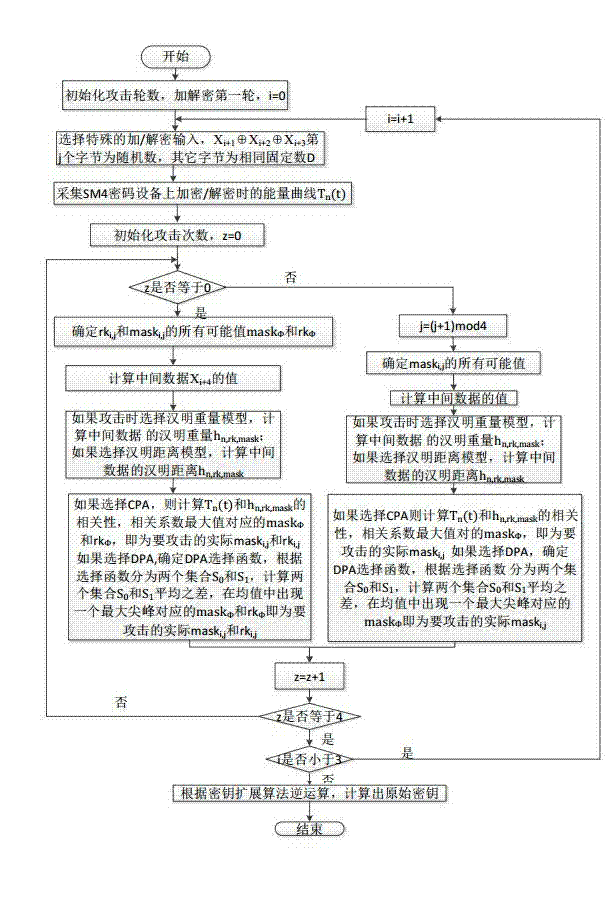
ActiveCN104753665AImprove attack efficiencyIncrease flexibilityEncryption apparatus with shift registers/memoriesPlaintextPassword
The invention discloses a side channel energy attack method selecting a clear text or a cipher text aiming at SM4 password round function output. The method includes the following steps: S1 selecting clear text input or cipher text input to enable one byte of (Xi+1 Xi+2 Xi+3) to be a random digit and other bytes to be identical fixed digits, adopting the side channel energy attack method to first attack bytes of a round key and the fixed digits in linear transformation and then attack other fixed digits in linear transformation, conducting corresponding computing on attacked data to obtain the complete round key rki, wherein i= 0, 1, 2, 3; S2 conducting reversible calculation to obtain an initial key through a password expansion algorithm according to rk0, rk1, rk2 and rk3 of first four rounds of the round keys. By means of the analysis method, the collection curve attack times and the clear text selection times can be reduced, and analysis flexibility, attack efficiency and successfully rate are improved.
Owner:CHENGDU UNIV OF INFORMATION TECH +2
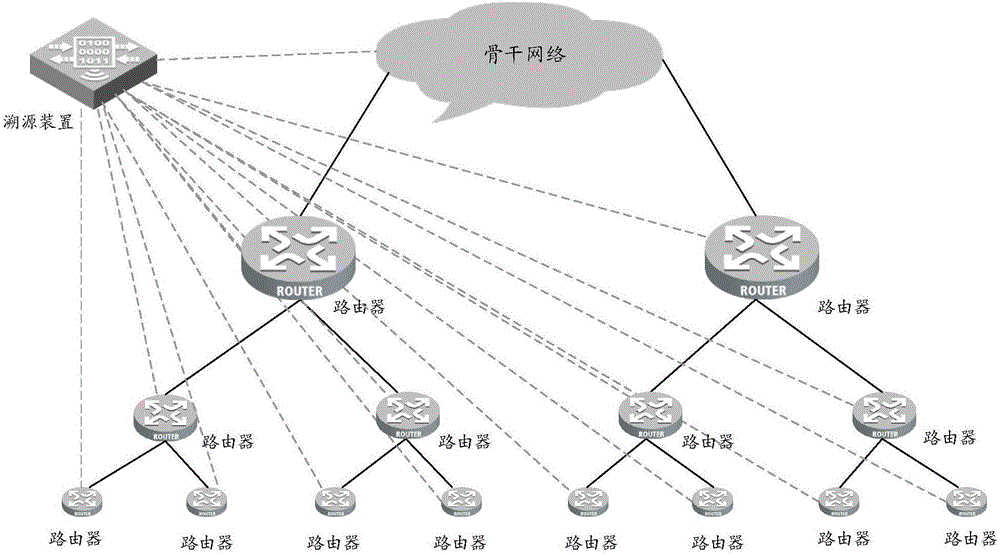
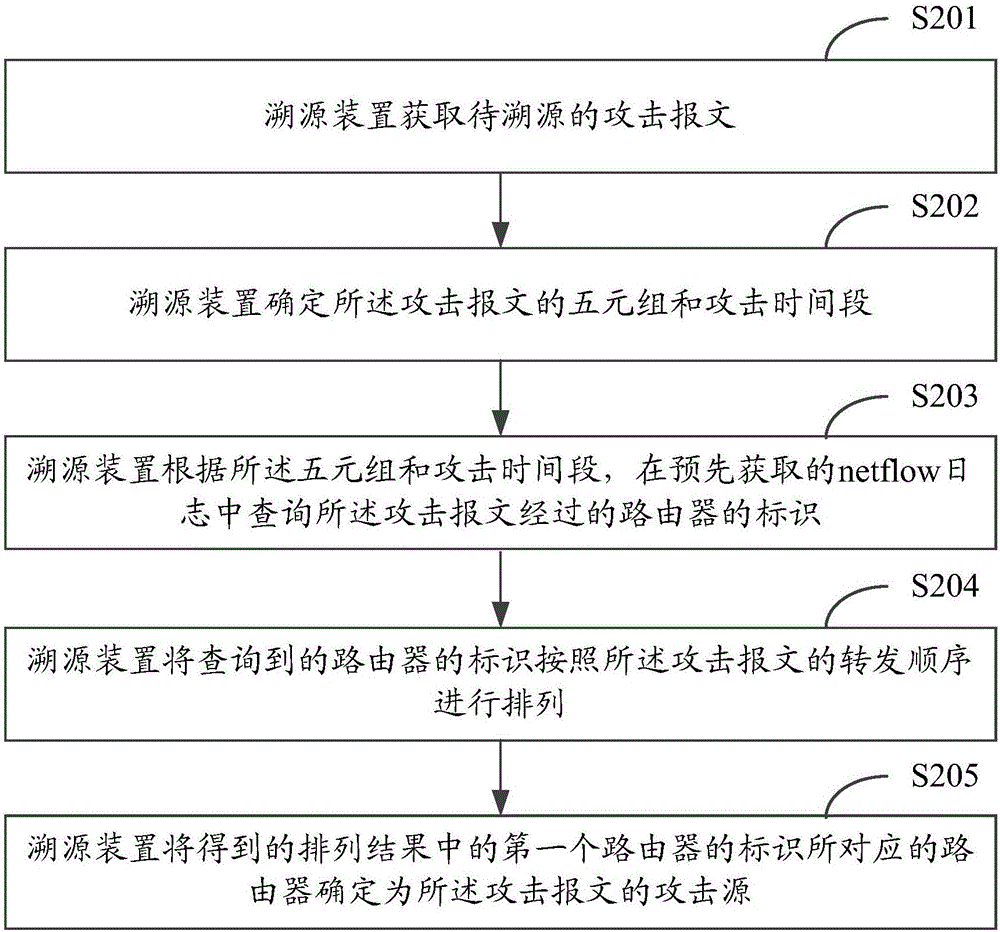
Method and device for tracing attack message
The invention provides a method and a device for tracing an attack message. The method comprises the steps of acquiring an attack message to be traced; determining a quintuple and an attack time period of the attack message; querying identifiers of routers by which the attack message passes in a netflow log acquired in advance according to the quintuple and the attack time period; arranging the queried identifiers of the routers according to a forwarding sequence of the attack message; determining a router corresponding a first router identifier in an acquired arrangement result to be an attack source of the attack message. According to the method provided by the invention, the netflow log is utilized, no matter whether a source IP address carried by the captured attack message is true or not, a forwarding path of the known attack message can be analyzed through the netflow log, and thus the true source of the attack message is determined.
Owner:HANGZHOU DPTECH TECH
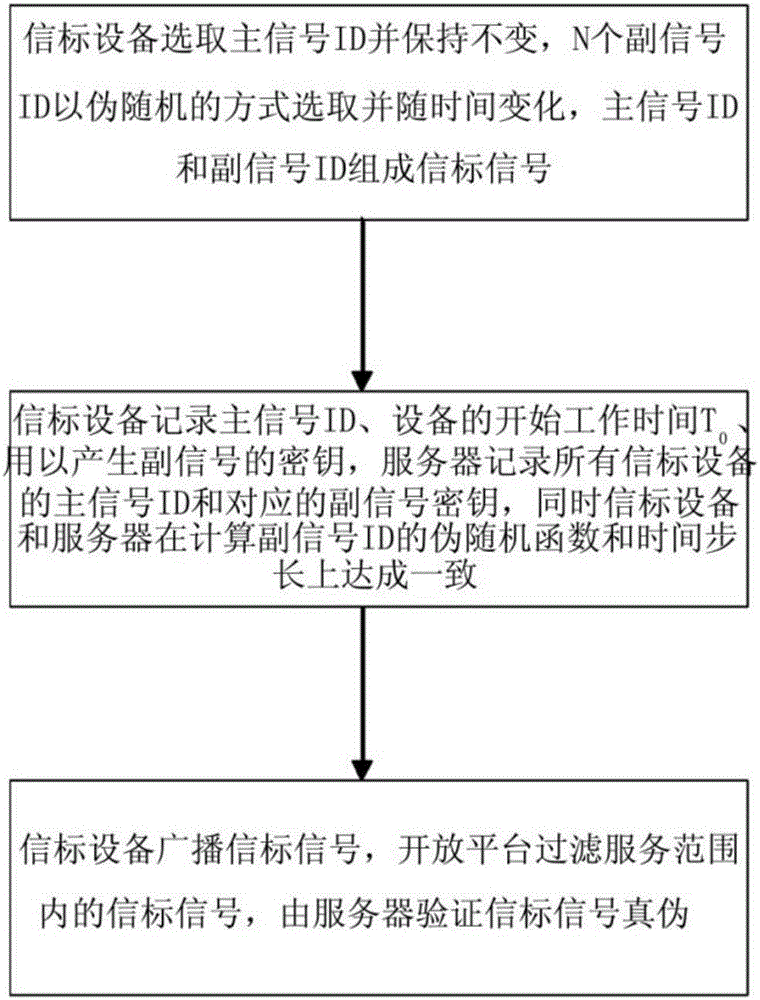
Method for preventing beaconing devices from being forged or copied
The invention relates to the technical field of wireless Internet, in particular to a method for preventing beaconing devices from being forged or copied. The method comprises the following steps: selecting main signal IDs to be unchanged by the beaconing devices, and selecting N secondary signal IDs in a pseudorandom manner and changing along with time, wherein the main signal IDs and the secondary signal IDs form beaconing signals; recording the main signal IDs, the attack time T0 of the devices and a group of secret keys K1,..., KN for generating secondary signals by the beaconing devices, recording the main signal IDs of all the beaconing devices and the corresponding secondary signal secret keys by a server, and simultaneously the beaconing devices and the server reaching an agreement on the pseudorandom function SLAVE_ID for calculating the secondary signal IDs and time step delta T; broadcasting the beaconing signals by the beaconing devices, filtering the beaconing signals in a service range by an open platform, and verifying true and false of the beaconing signals by the server. The method has the beneficial effects that forged and copied third-party devices still can be identified under the condition that the open platform is free of a forging and copying preventing mechanism, so that the security of the third-party devices under the open platform is guaranteed.
Owner:杭州微飞胜科技有限公司
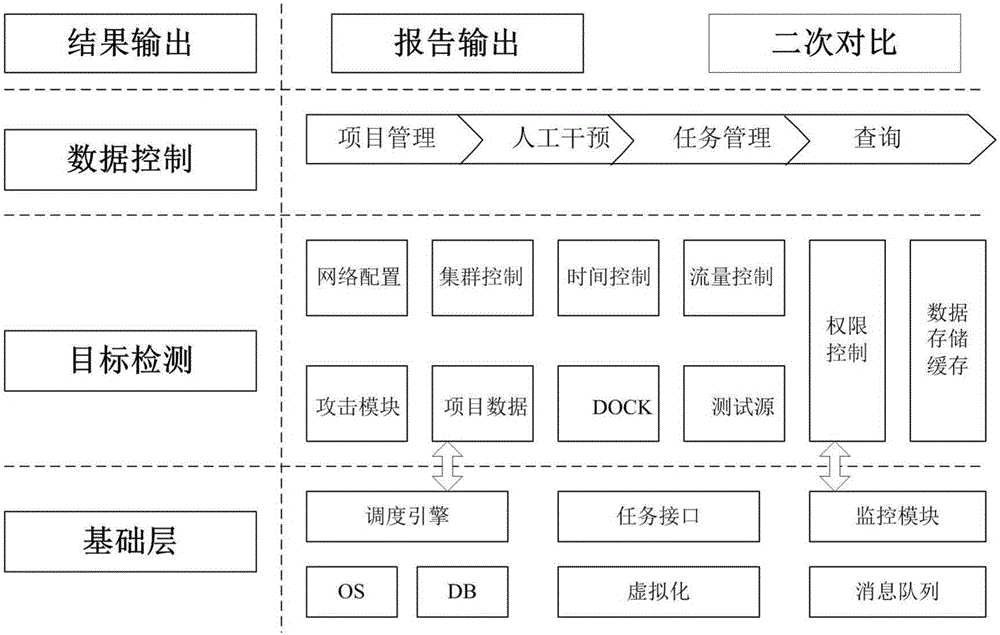
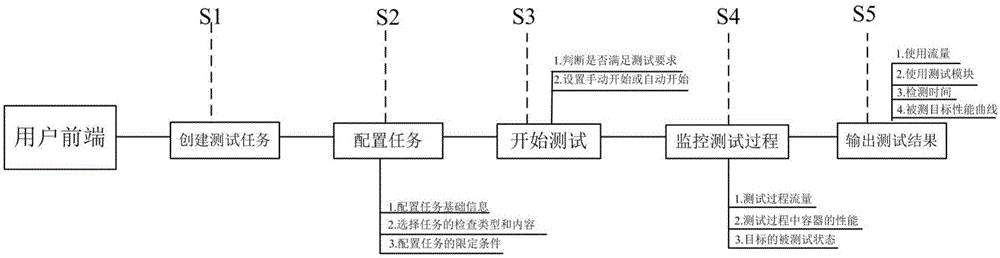
Intelligent detection system for anti-compression test on information system, and detection method
The invention discloses an intelligent detection system for an anti-compression test on an information system. According to the detection system, a base module is arranged at and applied to a main server, and the base module employs modularization design and a distributed disposition mode and is used for realizing data layer acquisition and interaction; information acquisition and interaction of the base information comprises task interfaces, the virtual technology, a monitoring module and a task management message queue, the main server greatly utilizes distributed technologies to arrange attack nodes, real-time flow detection is carried out, the attack time is controlled, and an attack node attack source contains attack source frequency statistics, attack source flow statistics, system performance monitoring, attack flow K-line indexes and test node detailed data statistics. The system is advantaged in that intelligent detection on a target is realized through simulating thinking and methods of an invalid attacker, so accuracy, high efficiency, low cost, safety and controllability are realized, and the system is easy for popularization and application.
Owner:JIANGSU CIMER INFORMATION SECURITY TECH
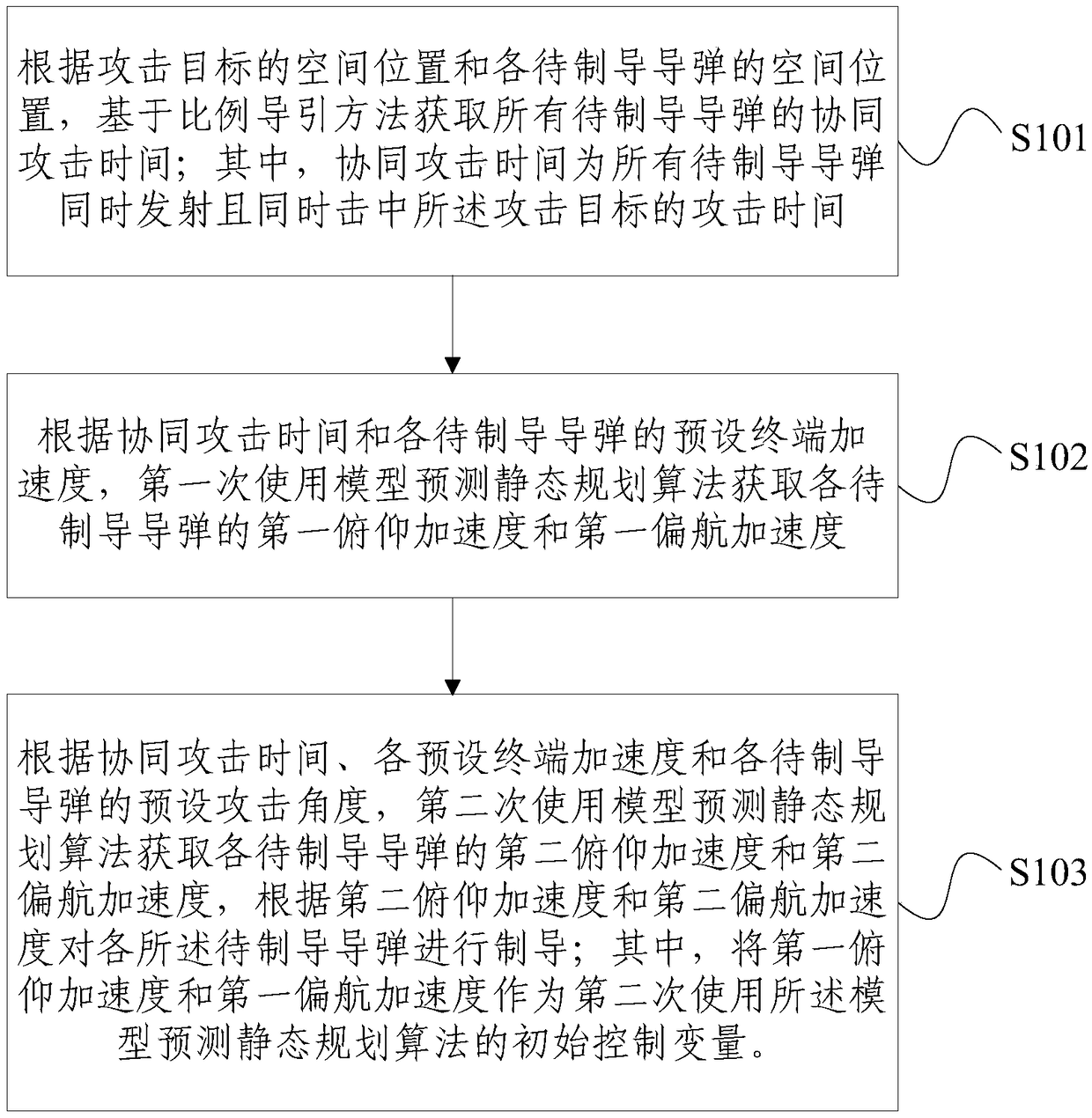
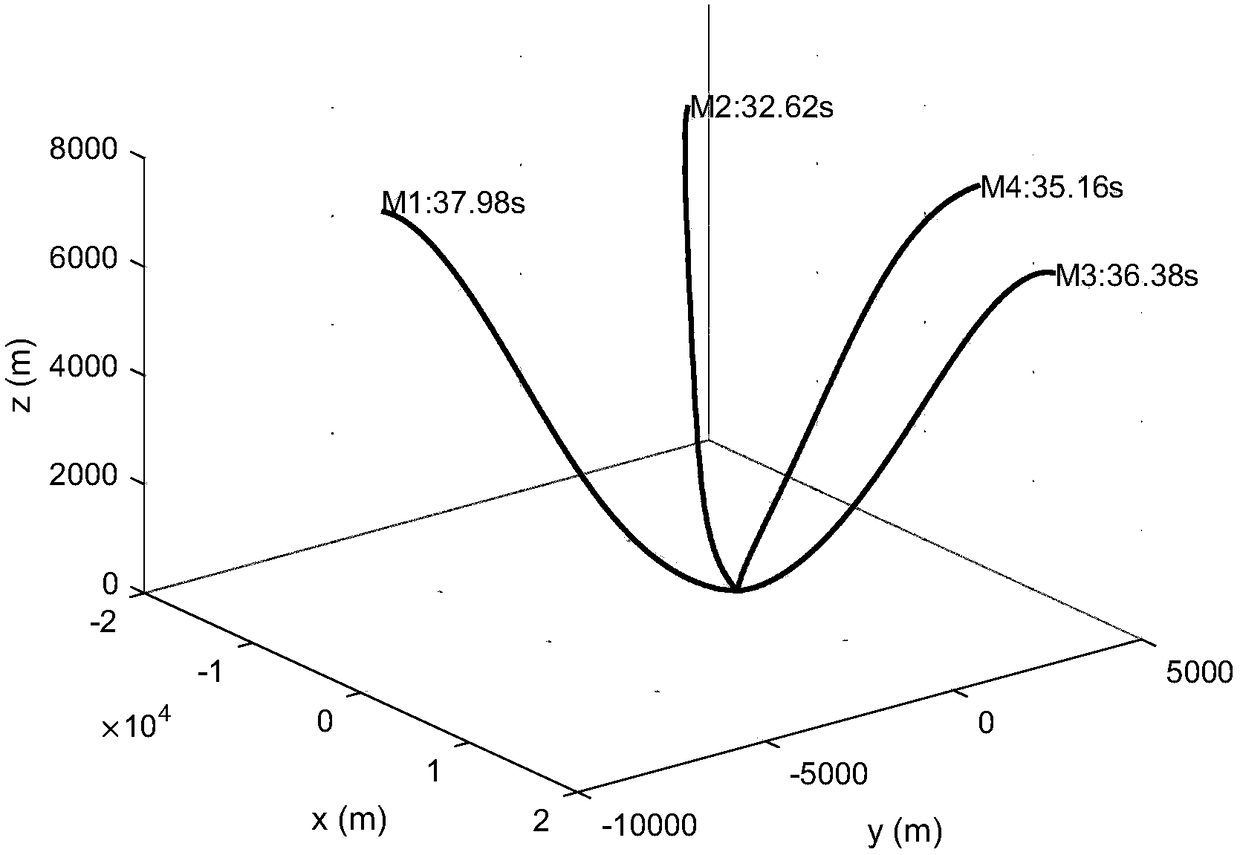
Missile guidance method and device
ActiveCN109084641AFast convergenceImprove efficiencyAiming meansSelf-propelled projectilesComputer scienceAttack time
The embodiment of the invention provides a missile guidance method and device. The missile guidance method comprises the steps that according to the spatial position of an attack target and the spatial positions of all to-be-guided missiles, the coordinated attack time of all the to-be-guided missiles is obtained based on a proportional guidance method; according to the coordinated attack time andpreset terminal acceleration of all the to-be-guided missiles, a model prediction and static planning algorithm is used for the first time to obtain a set of control variables; according to the coordinated attack time, all the preset terminal acceleration and preset attack angles of all the to-be-guided missiles, the model prediction and static planning algorithm is used for the second time to guide all the to-be-guided missiles; and the control variables serve as initial control variables for using the model prediction and static planning algorithm for the second time. According to the missile guidance method and device, attack time and attack angle coordinated guidance of the multiple missiles is achieved, meanwhile, the model prediction and static planning algorithm can be rapidly converged, and the guidance efficiency and precision are improved.
Owner:BEIHANG UNIV
Electronic musical instrument
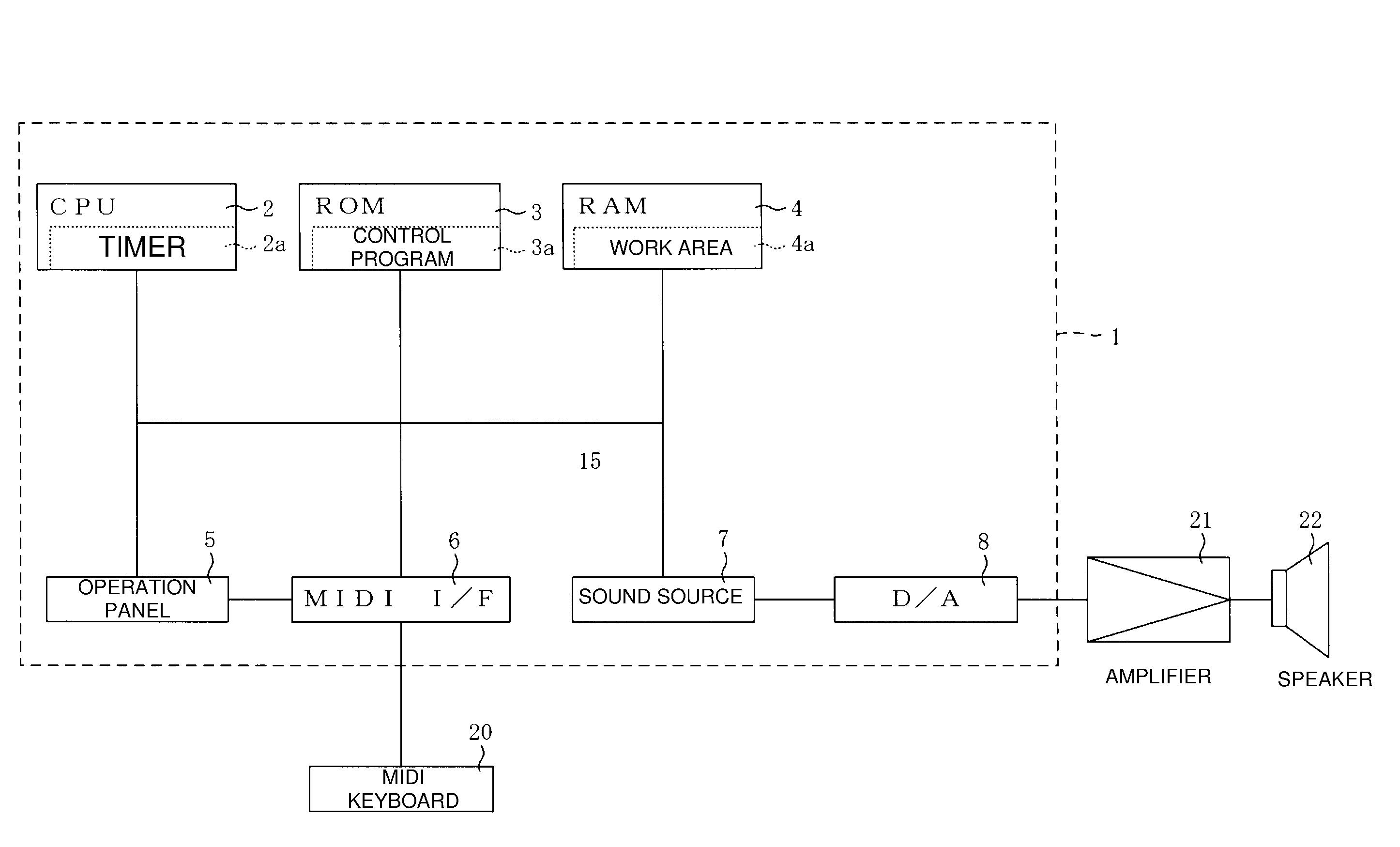
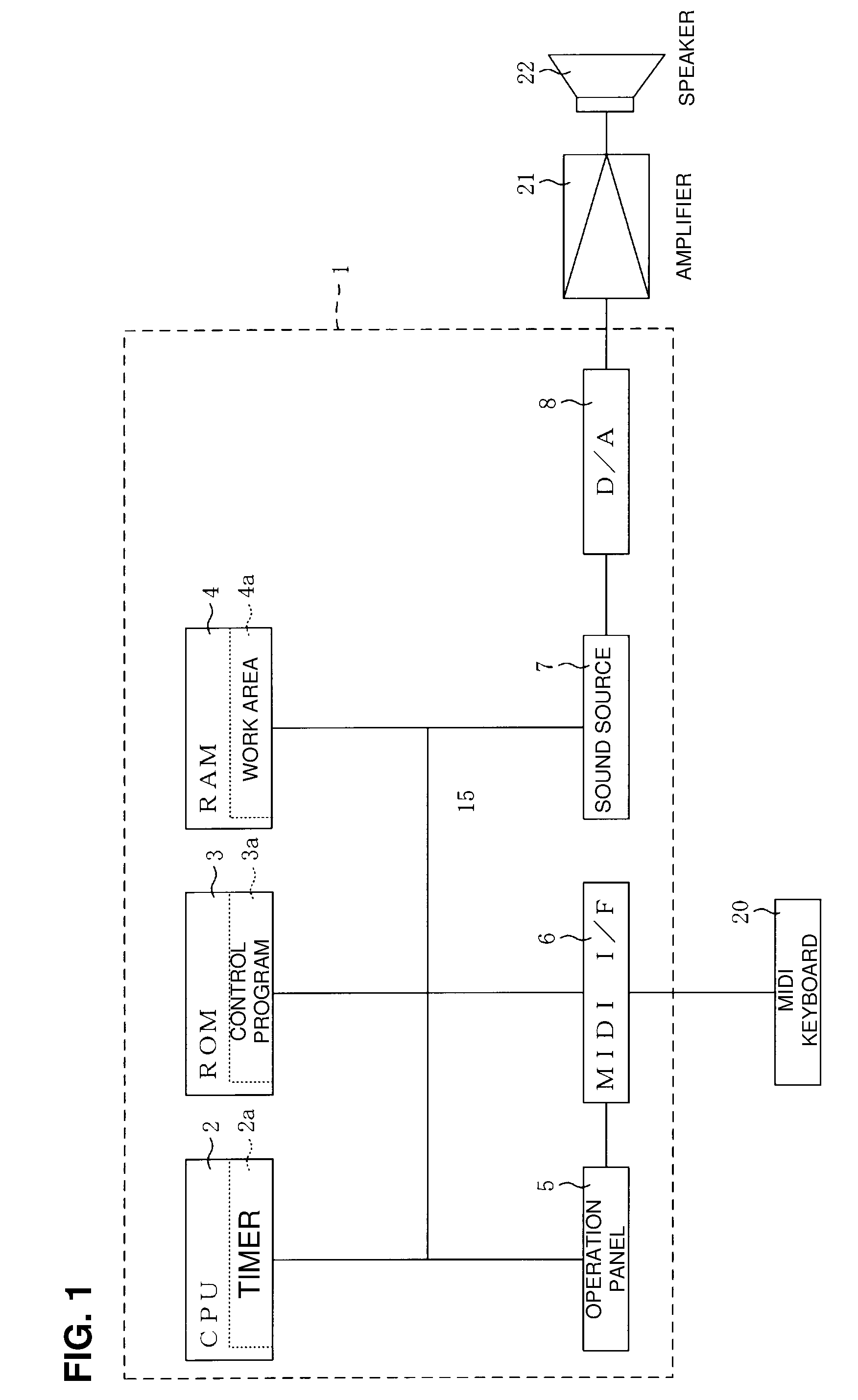
ActiveUS20090249943A1Short startup timeClear processGearworksMusical toysSound generationSound sources
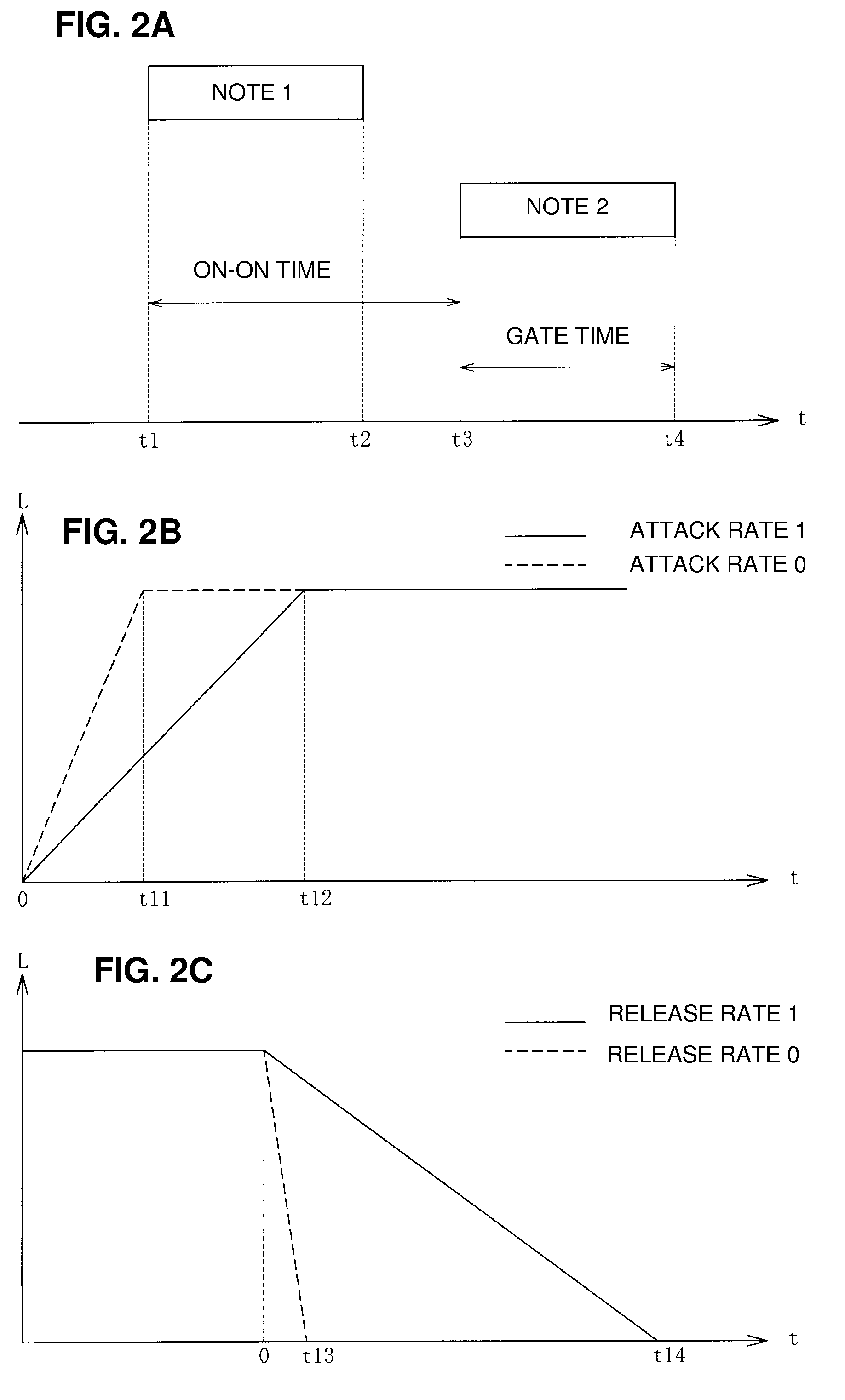
An electronic musical instrument includes: an input device that inputs a sound generation instruction that instructs to start generating a musical sound and a stop instruction that instructs to stop the musical sound being generated by the sound generation instruction; a sound source that starts generation of a musical sound in response to the sound generation instruction, and stops generation of the musical sound in response to the stop instruction; an on-on time timer device that measures a time difference between a first sound generation instruction inputted by the input device and a second sound generation instruction inputted next to the first sound generation instruction; a gate time timer device that measures a time difference between the second sound generation instruction and a stop instruction that instructs to stop a musical sound generated in response to the second sound generation instruction; an attack characteristic setting device that sets an attack characteristic of the musical sound generated in response to the second sound generation instruction to have a shorter attack time as the time difference measured by the on-on time timer device becomes shorter; a release characteristic setting device that sets a release characteristic of the musical sound generated in response to the second sound generation instruction to have a shorter release time as the time difference measured by the gate time timer device becomes shorter; and an instruction device that instructs the sound source to start generation of a musical sound with an attack characteristic set by the attack characteristic setting device in response to an input of the second sound generation instruction by the input device, and instructs the sound source to stop generation of a musical sound with a release characteristic set by the release characteristic setting device in response to an input of the stop instruction by the input device.
Owner:ROLAND CORP
High-speed analysis and recovering method for VPN encrypted channel
InactiveCN106789524AAuthentication aggressivenessVerify validityNetworks interconnectionDecoding methodsData link layer
The invention discloses a high-speed analysis and recovering method for a VPN encrypted channel. The method comprises the steps of high-speed analysis and recovering of a PPTP encrypted channel; high-speed analysis and recovering of an L2TP encrypted channel; and high-speed analysis and recovering of an IPSec active mode channel.The method starts from the bottom-layer protocol of the VPN channel, data link layer and network layer protocols of the VPN are emphatically studied, the security mechanism of the protocol is analyzed, unsafe points during an authentication interaction process and an encrypted transmission process are found, then an analysis and decoding method for the VPN encrypted channel is provided, and sensitive information on the VPN encrypted channel is further recovered in real time. The high performance computation technology in the method can effectively improve the decoding speed, reduces attack time and spatial complexity of encryption algorithms such as RC4 and DES in the VON, and enlarges categories of cracking algorithms by integrating Hashcat source codes.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
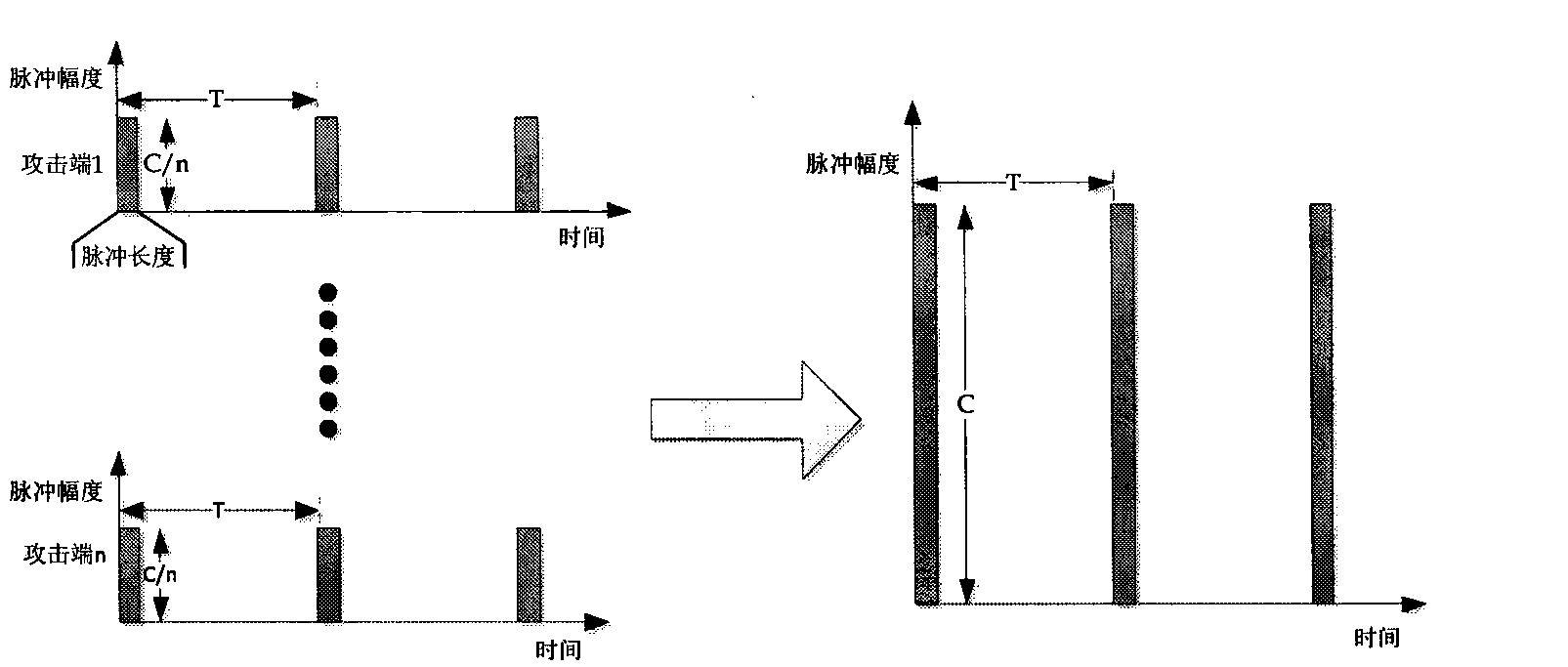
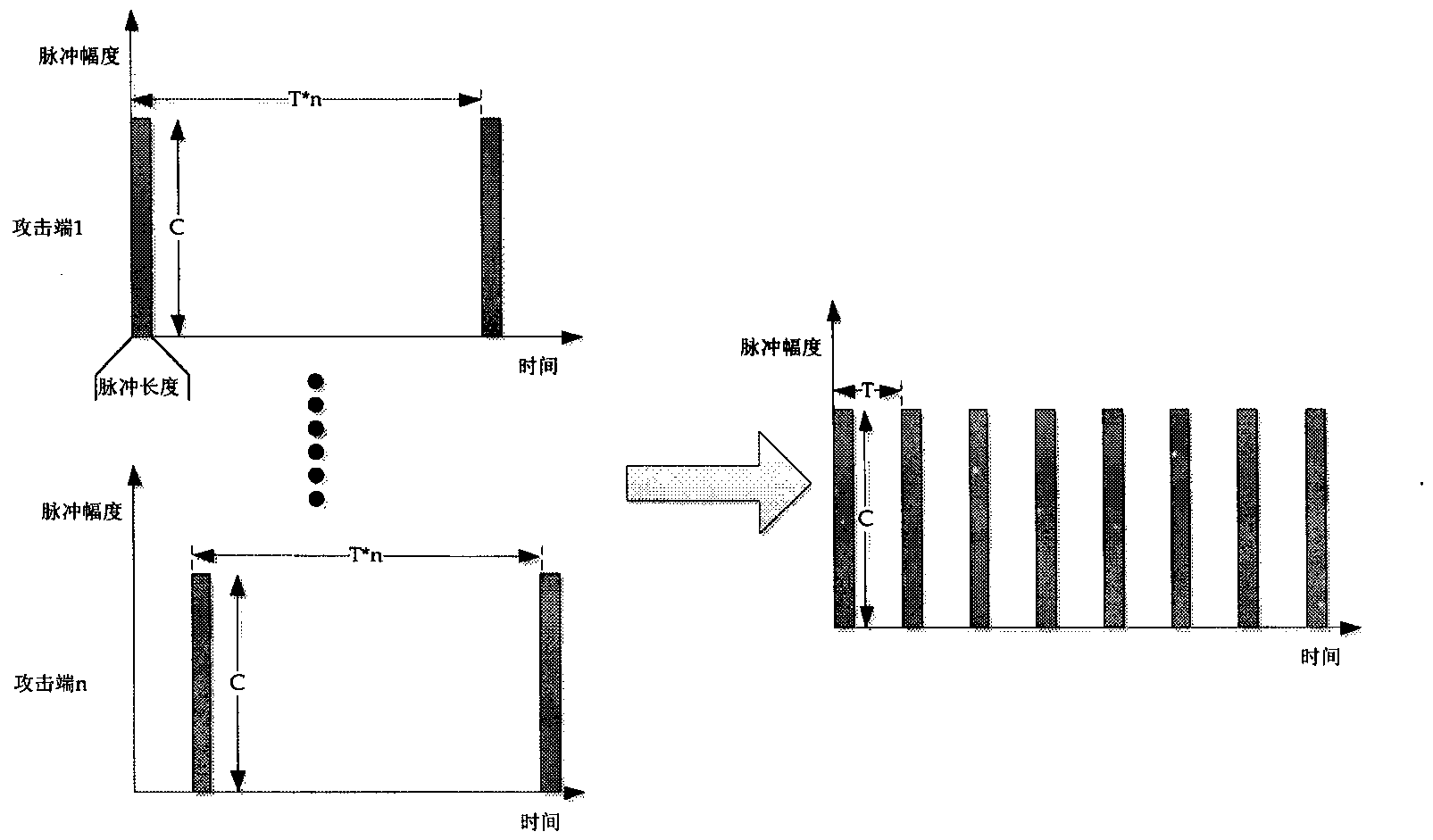
LDDoS attack time synchronization and flow convergence method based on cross correlation
The invention relates to an LDDoS attack time synchronization and flow convergence method based on cross correlation. The invention relates to flow convergence and time synchronization of LDDoS (Low-rate Distributed Denial of Service) attacks. The LDDoS attacks are formed through gathering of a large quantity of organized LDDoS attacks. A signal cross correlation algorithm aims at ensuring that each distributed attack pulse is gathered and accurately synchronized at a sufferer end so as to form a powerful pulse. A simulation result shows that an LDDoS attack effect of attack pulses adjusted through a signal cross correlation algorithm is significantly reinforced.
Owner:CIVIL AVIATION UNIV OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com