WebShell detection method
A detection method and technology of hadoop cluster, applied in electrical components, transmission systems, etc., can solve the problems of high false alarm rate and false alarm rate, high false alarm rate, influence of detection results, etc., to achieve effective detection and avoid false alarm rate higher effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
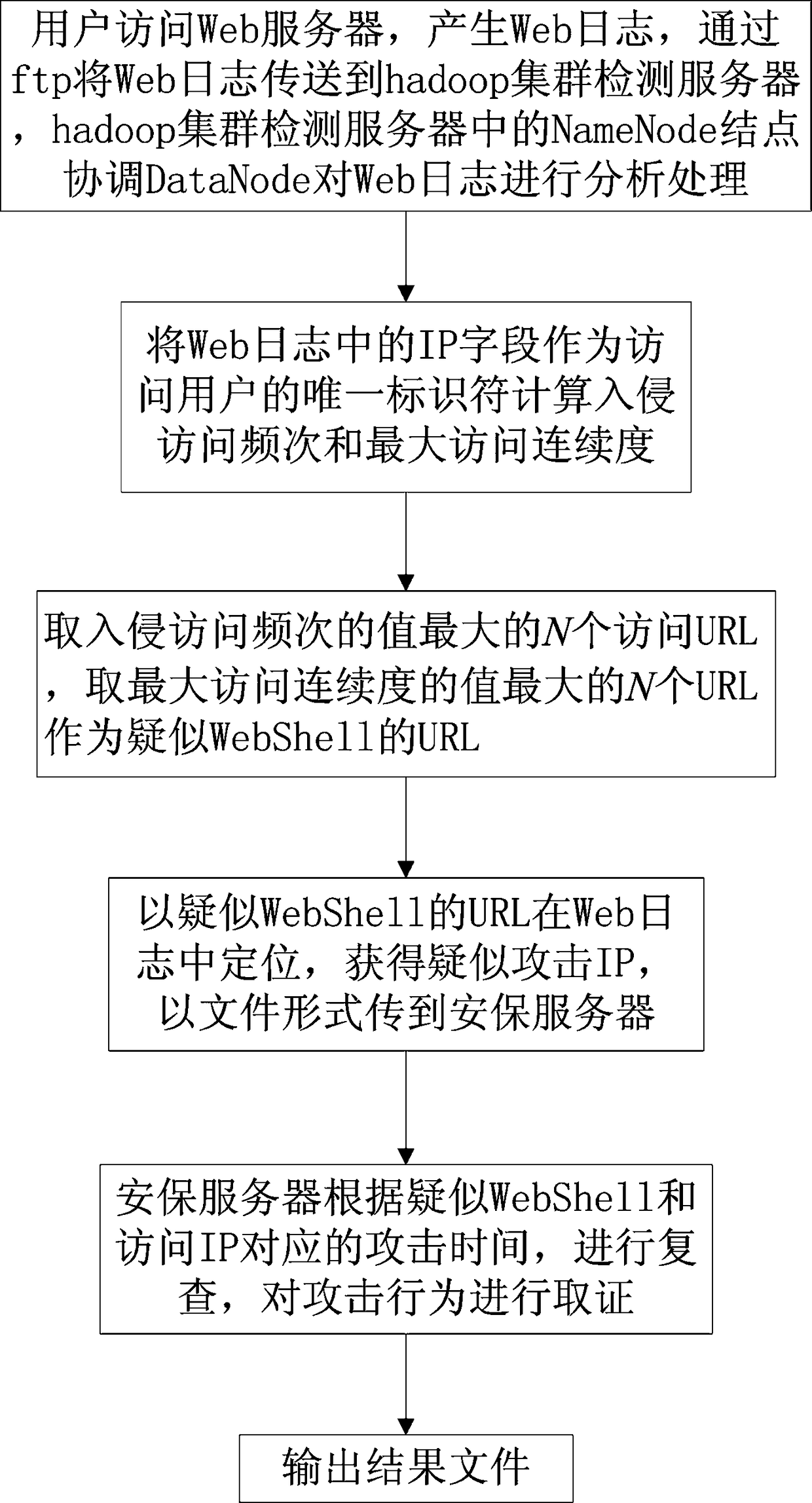
[0038]The present invention relates to a WebShell detection method. In the embodiment, the operating system adopted is centos7_x64, and the operating system has been installed and configured with auditd. The Web server software adopted in this embodiment is ApacheTomcat, and the Web log used comes from a real website. In order to facilitate evidence collection, auditd is configured with rules so that auditd can monitor key system file directories. In the evidence collection stage, this embodiment also uses Other files include auditd log files.
[0039] In the present invention, auditd is an audit tool on the Linux system, and its basic function is to monitor the operation of files and directories through configuration rules.
[0040] The method includes the following steps.
[0041] Step 1: The us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com