Method and apparatus for predicting network attack behaviour
A technology for predicting network and network attacks, applied in the direction of data exchange network, special data processing applications, instruments, etc. safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
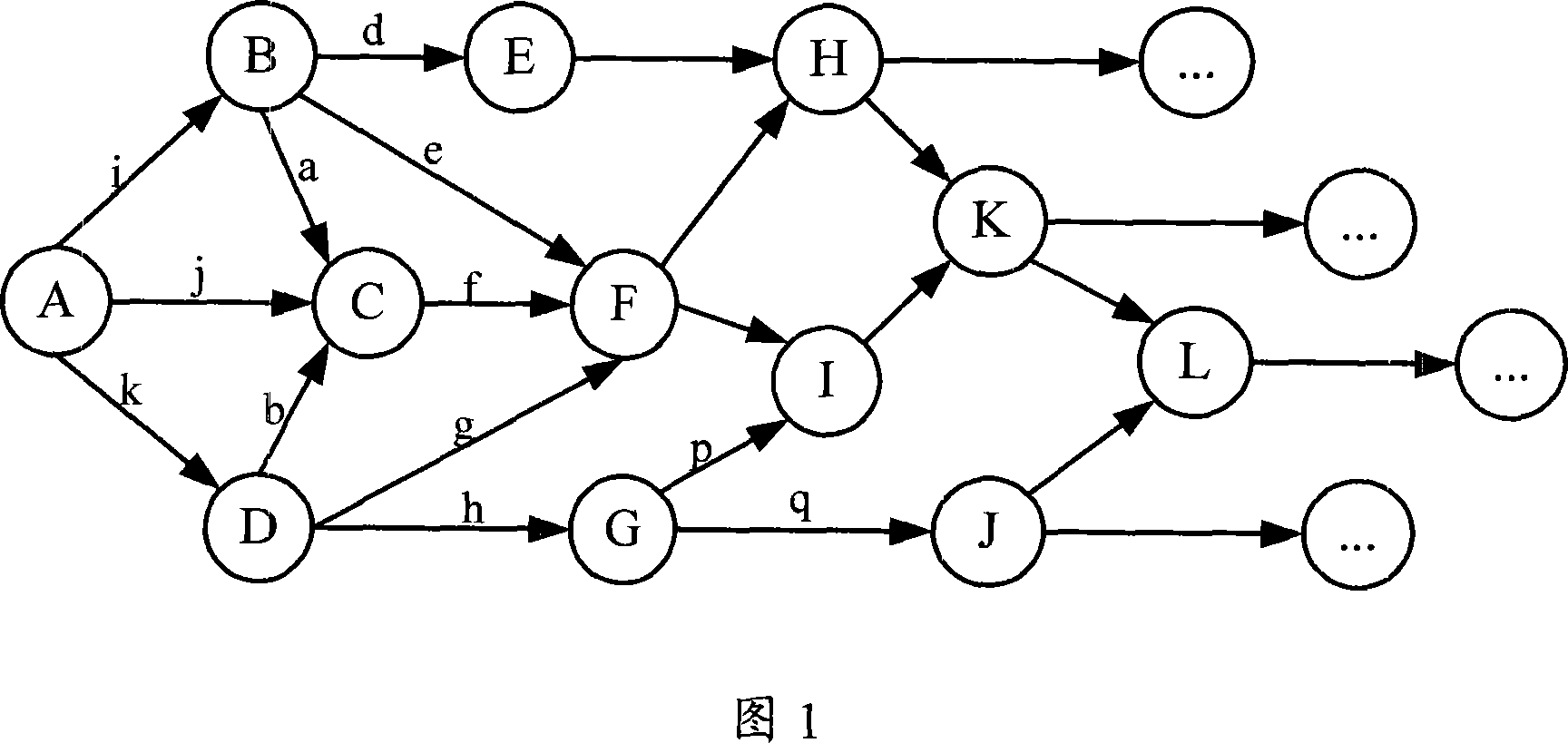
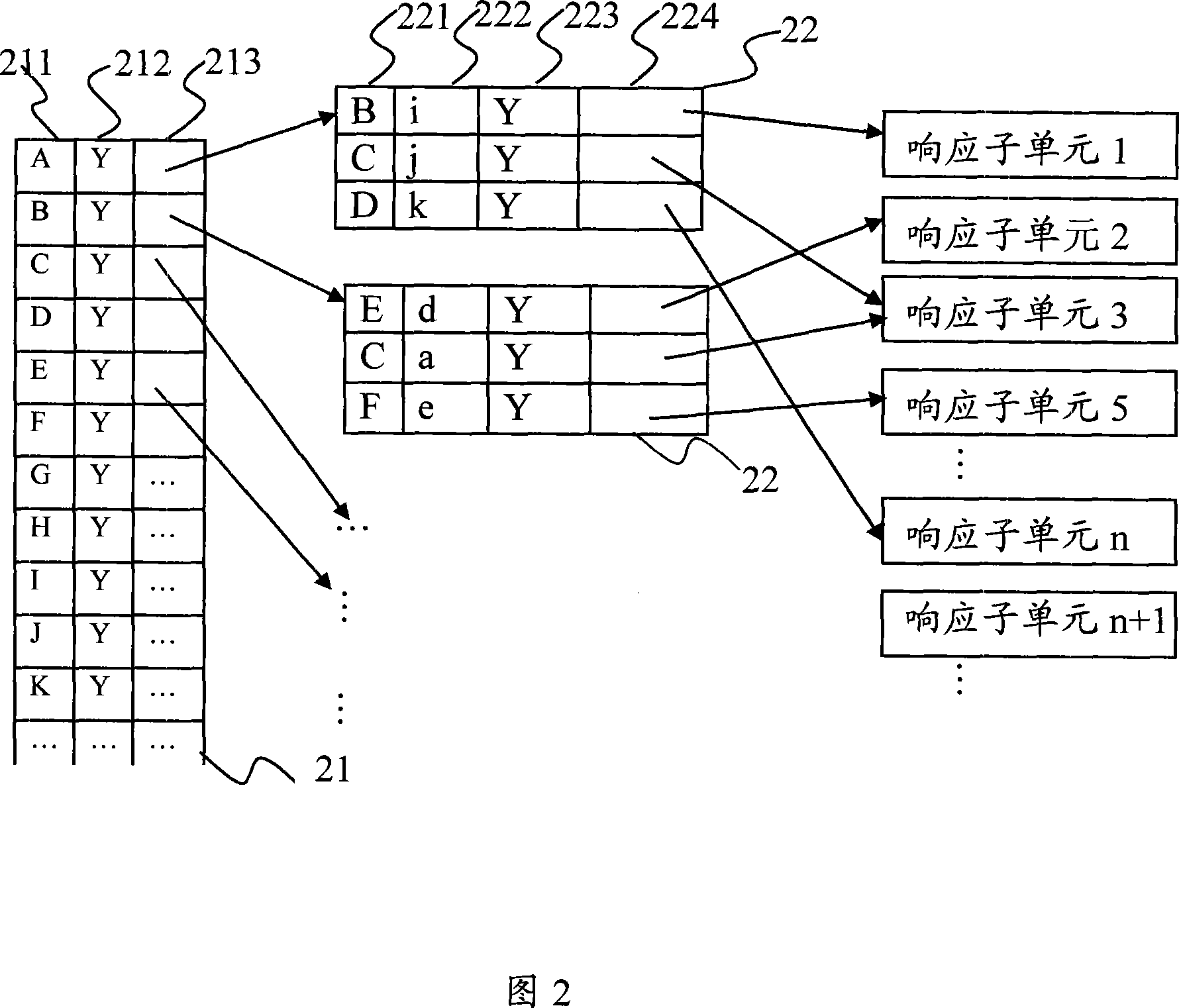
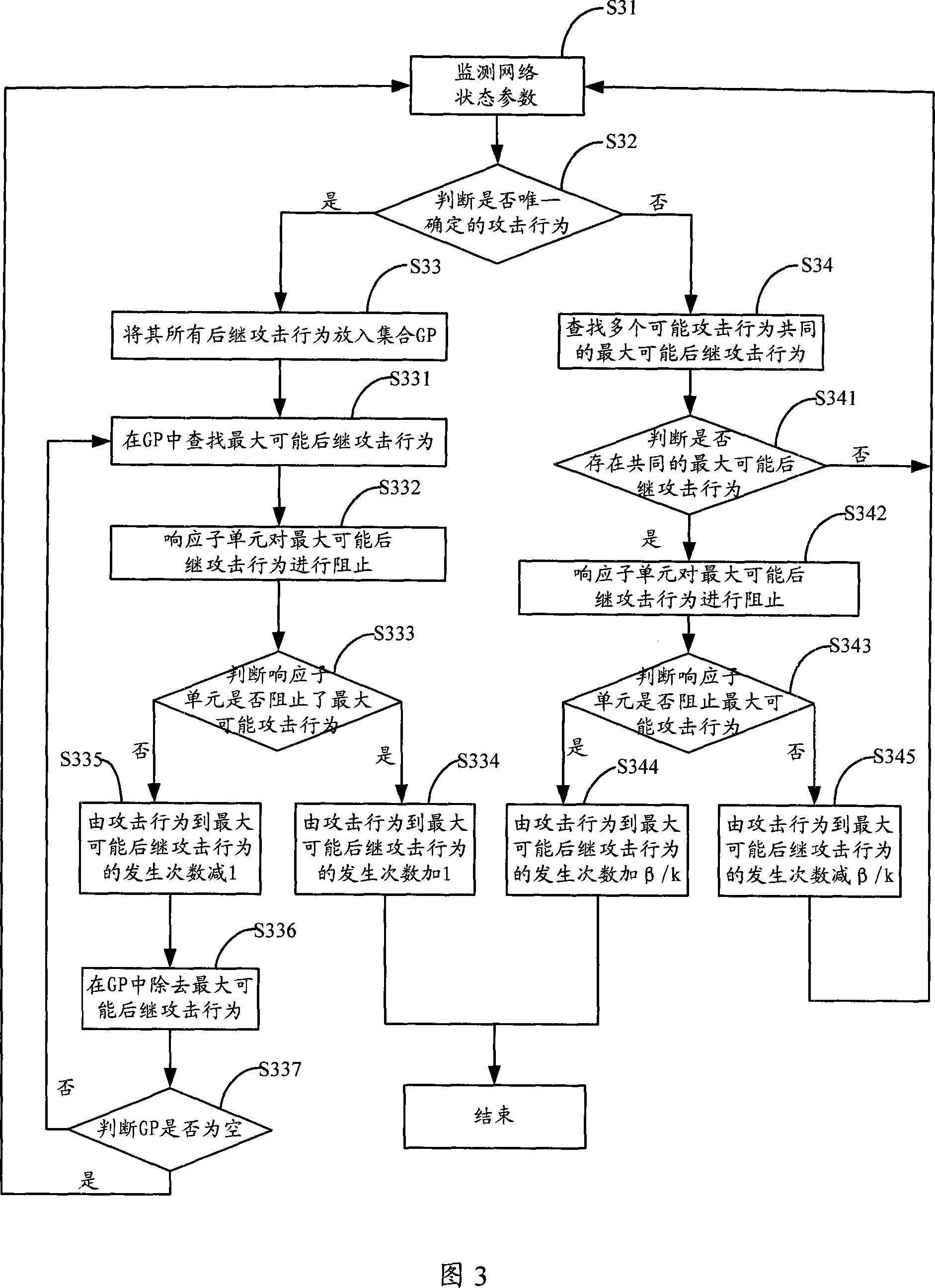
[0020] Combining with Figure 1 and Figure 2, we will introduce the method of describing network attack behavior in detail. The correspondence between the attack behavior and its subsequent attack behavior is represented by a weighted directed graph of the attack behavior. Fig. 1 is a structural diagram of an attack behavior weighted directed graph describing a network attack behavior in an embodiment of the present invention. Circles are vertices in the attack behavior weighted directed graph, and each vertex represents an attack behavior. The letter in represents the name of the specific attack behavior; the arrow line is the arc in the weighted directed graph of the attack behavior, the arc represents the pointing relationship from the attack behavior to the subsequent attack behavior, the arc tail conn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com