High-coverage intranet honeypot system
A high-coverage, honeypot technology, applied in the field of network security, can solve problems affecting the allocation of business system IP addresses and occupying IP addresses, so as to increase the probability of being attacked, reduce system costs, and avoid allocation and change.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0022] The following combination figure 1 and figure 2 Embodiment 1 of the present application will be described.
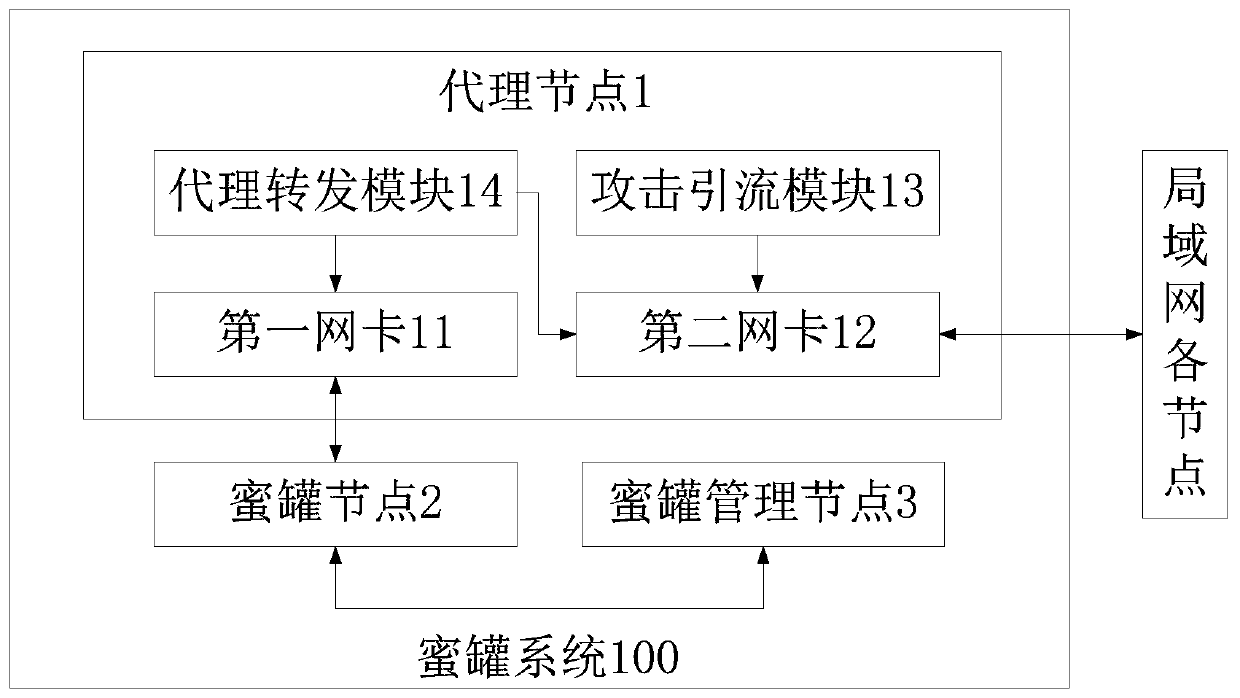
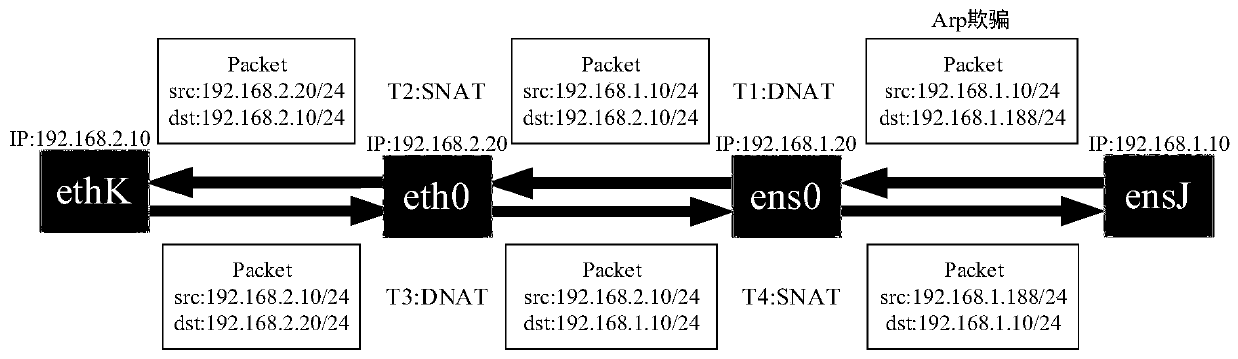
[0023] Such as figure 1 As shown, the present embodiment provides a high-coverage intranet honeypot system. The honeypot system is suitable for local area networks. The honeypot system includes: an agent node 1 and at least one honeypot node 2; the agent node 1 includes an attack drainage module 13, The first network card 11, the second network card 12 and the agent forwarding module 14, the attack diversion module 13 is used to cheat by ARP, and guide the LAN access request whose destination address is an idle IP address in the network segment where the LAN is located to the agent node 1, the first network card The IP address of 11 is in the same network segment as the honeypot IP address, the first network card 11 is used to communicate with the honeypot node 2, the IP address of the second network card 12 is in the same network segment as the IP address of ...
Embodiment 2
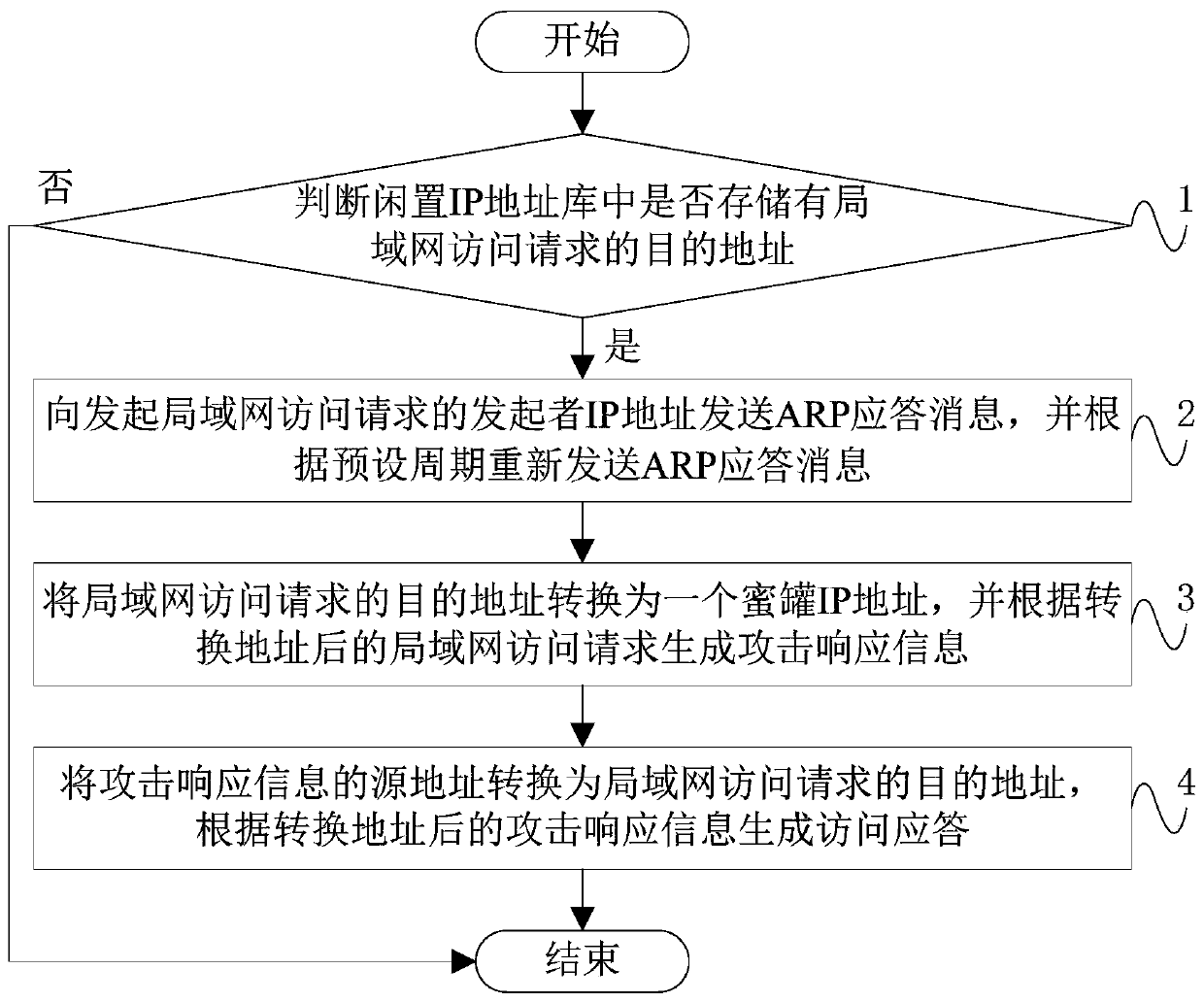
[0042] Such as image 3 As shown, the present embodiment provides a control method of a high-coverage intranet honeypot system, the control method comprising: Step 1, judging whether the destination address of the LAN access request is stored in the idle IP address library, and if so, performing the steps 2;
[0043] Step 2, sending an ARP response message to the initiator IP address of the LAN access request, and resending the ARP response message according to a preset period;
[0044] Specifically, by means of Scapy, an ARP response message is sent to the LAN IP address that initiates the access request through the second network card, and the source IP of the response message is set to the idle IP address of the ARP request, and the source mac address is set to the proxy node second network card 12 mac address to direct the connection to the proxy node. To prevent the ARP cache update from interrupting the connection, the ARP reply message is resent at a certain interval,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com