Sample security test method and device and equipment
A technology for security testing and samples, applied in the direction of platform integrity maintenance, etc., can solve the problem that the virus cannot be detected in time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
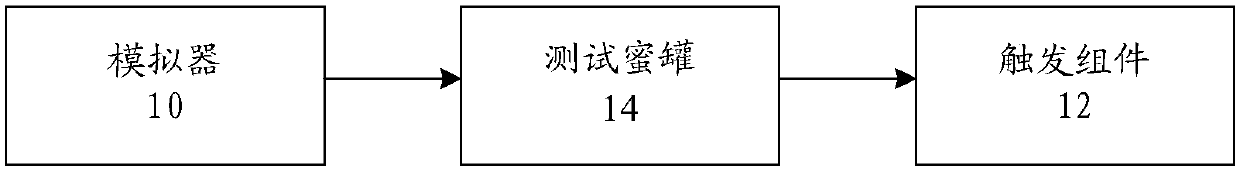
[0051] According to an embodiment of the present application, a sample safety testing device is also provided, figure 1 It is a schematic structural diagram of the safety testing equipment of the sample according to Implementation 1 of the present application, and the safety testing equipment of the sample includes:
[0052] The simulator 10 is used to simulate the operating environment in which the honeypot system operates.
[0053] In the above-mentioned devices in this application, the simulator can simulate from user-level behavior data and simulator architecture features, which can include forged user SMS records, contacts, browsers, device numbers, installed application packages, and filtered simulator-specific files And set the real machine properties, etc.
[0054] In an optional embodiment, the emulator can use the qemu emulator provided by Google to emulate the operating environment of the honeypot system.
[0055] What needs to be explained here is that using a si...
Embodiment 2
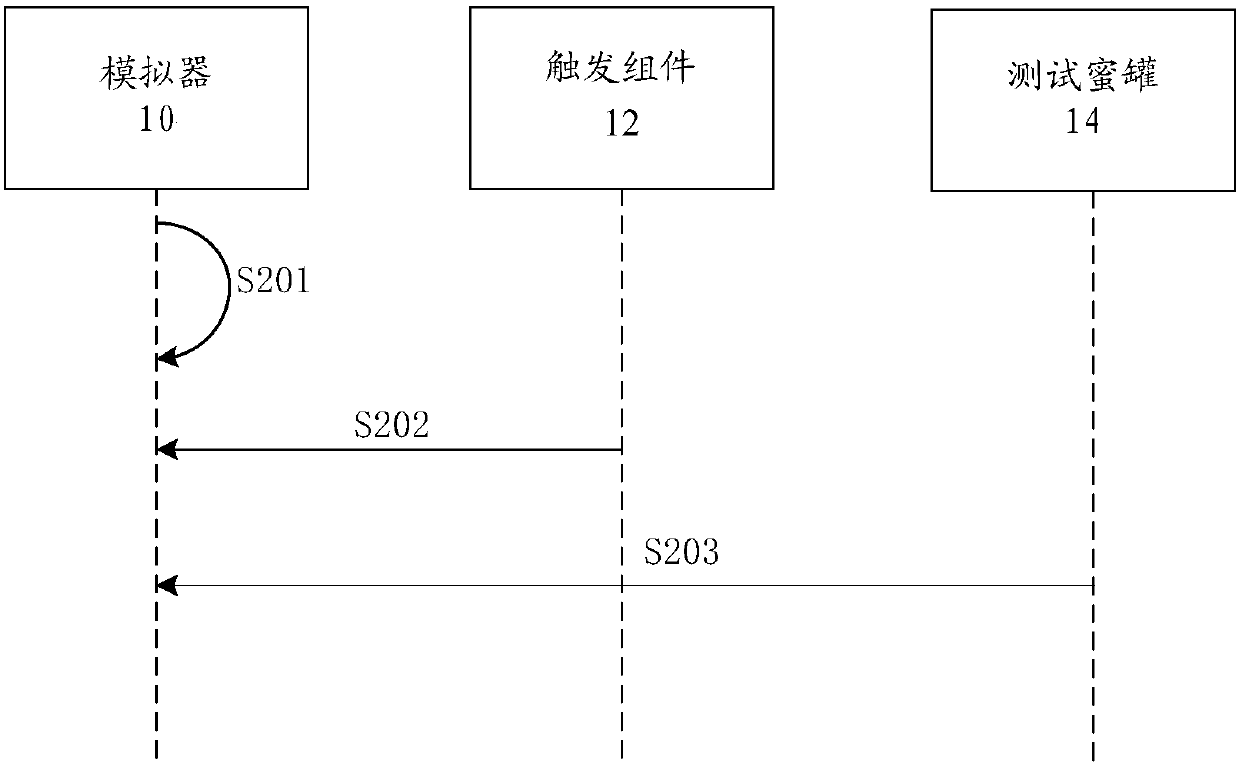
[0101] According to an embodiment of the present invention, a method embodiment of a sample testing method is also provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and , although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
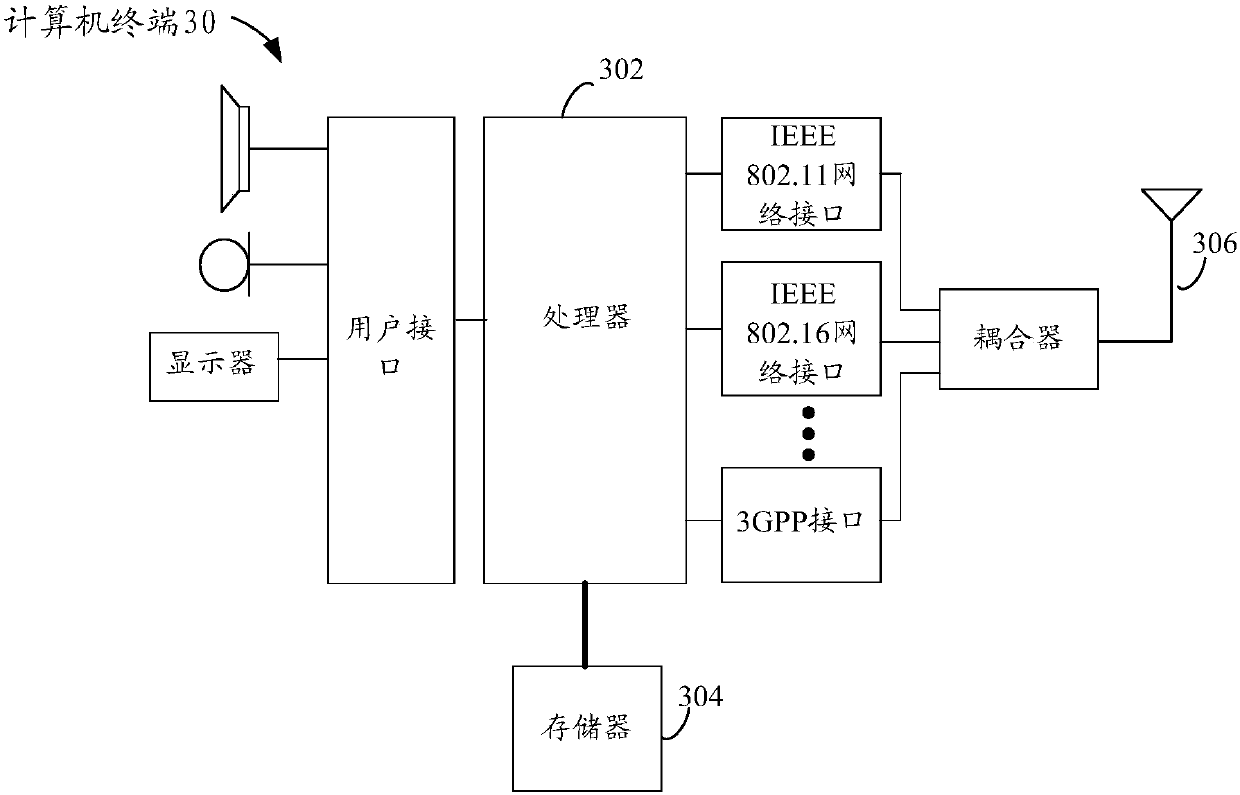
[0102] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, image 3 It is a hardware structure block diagram of a computer terminal of a sample testing method in the embodiment of the present invention. Such as image 3 As shown, the computer terminal 30 may include one or more (only one is shown in the figure) processor 302 (the processor 302 ...
Embodiment 3
[0126] Under the above operating environment, this application also provides Figure 5 Safety test method for the samples shown. Figure 5 It is a flow chart of a sample safety testing method according to Embodiment 3 of the present invention.
[0127] Step S501, obtaining a pre-configured honeypot system, and the sample to be tested runs in the operating environment determined by the honeypot system.
[0128] In the above steps of the present application, the sample may be any one or more application programs or software in the preset sample library, and the sample library may be a database containing multiple application programs or software. For example, the sample database can be stored in the network storage area of the network platform, and the sample to be tested can be extracted from the network storage area when performing sample testing.
[0129] There are many ways to acquire the sample database, and this application does not specifically limit it, but only prov...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com