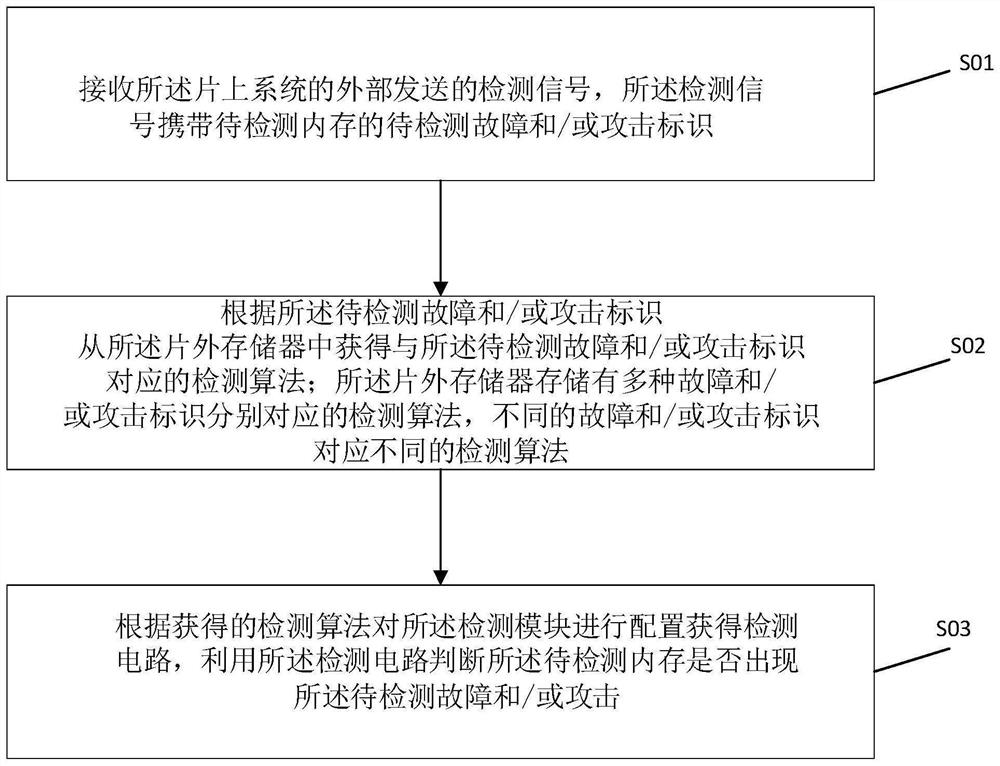
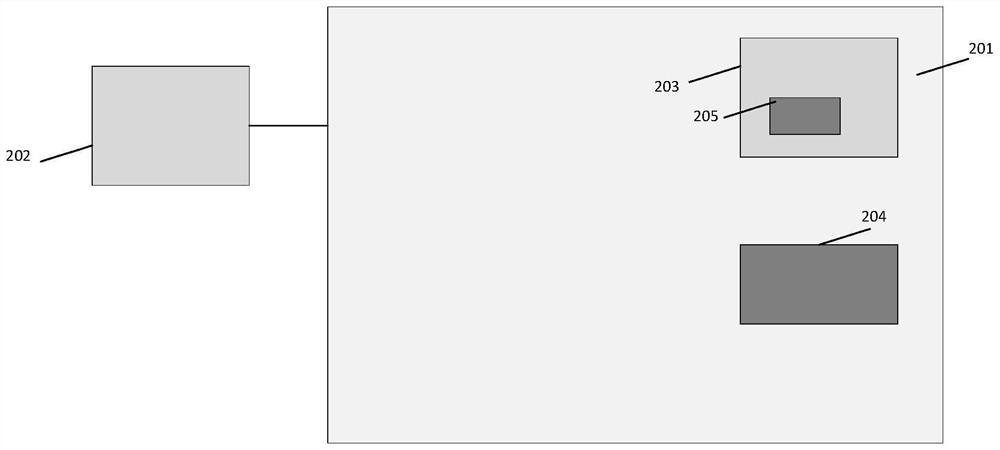
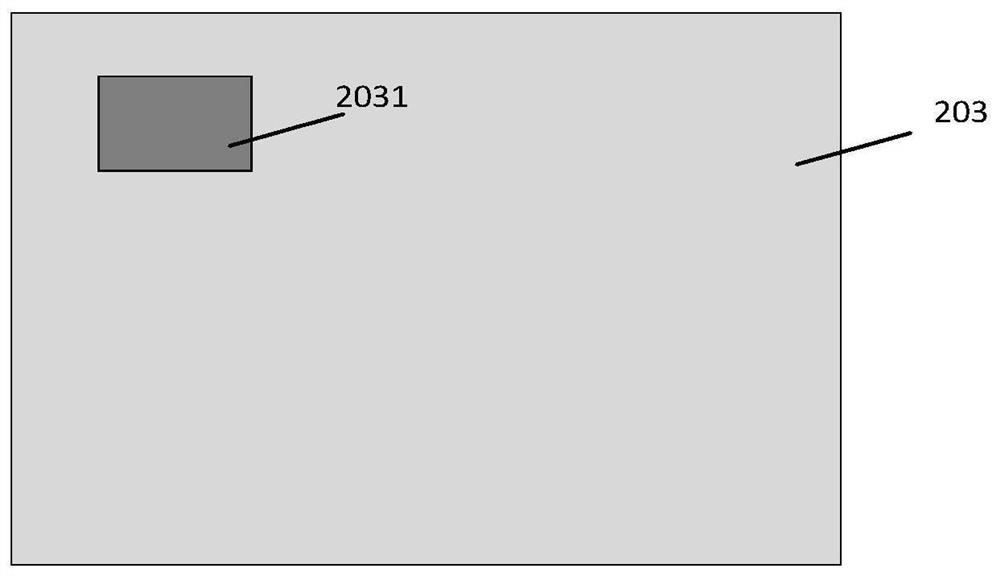
Memory security detection method and system on chip
A system-on-chip and detection method technology, applied in faulty hardware testing methods, error detection/correction, faulty computer hardware detection, etc., can solve problems such as increased system overhead, difficult management, high power consumption, etc., to improve detection coverage efficiency, reduce power consumption, and improve detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] In order to make the above-mentioned purpose, features and advantages of the present application more obvious and understandable, the specific implementation manners of the present application will be described in detail below in conjunction with the accompanying drawings.
[0055] In the following description, a lot of specific details are set forth in order to fully understand the application, but the application can also be implemented in other ways different from those described here, and those skilled in the art can do it without violating the content of the application. By analogy, the present application is therefore not limited by the specific embodiments disclosed below.
[0056] As described in the background art, with the rapid development of IoT technology, IoT devices are widely used. Users use IoT devices to make life convenient and fast. IoT devices rely on users to provide users with various services while collecting their personal information.
[0057]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com