Patents
Literature
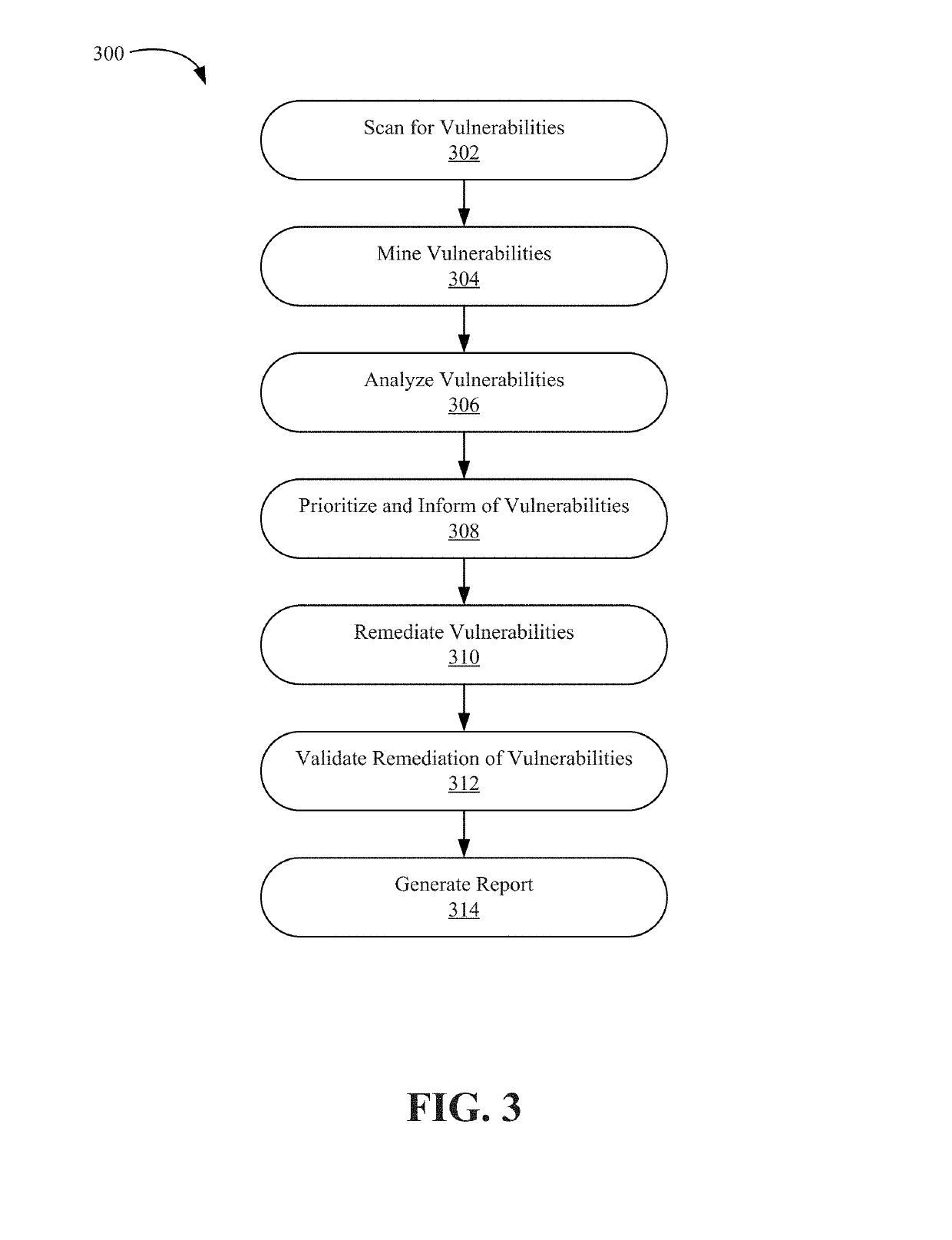
80 results about "Vulnerability scanner" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A vulnerability scanner is a computer program designed to assess computers, networks or applications for known weaknesses. In plain words, these scanners are used to discover the weaknesses of a given system.
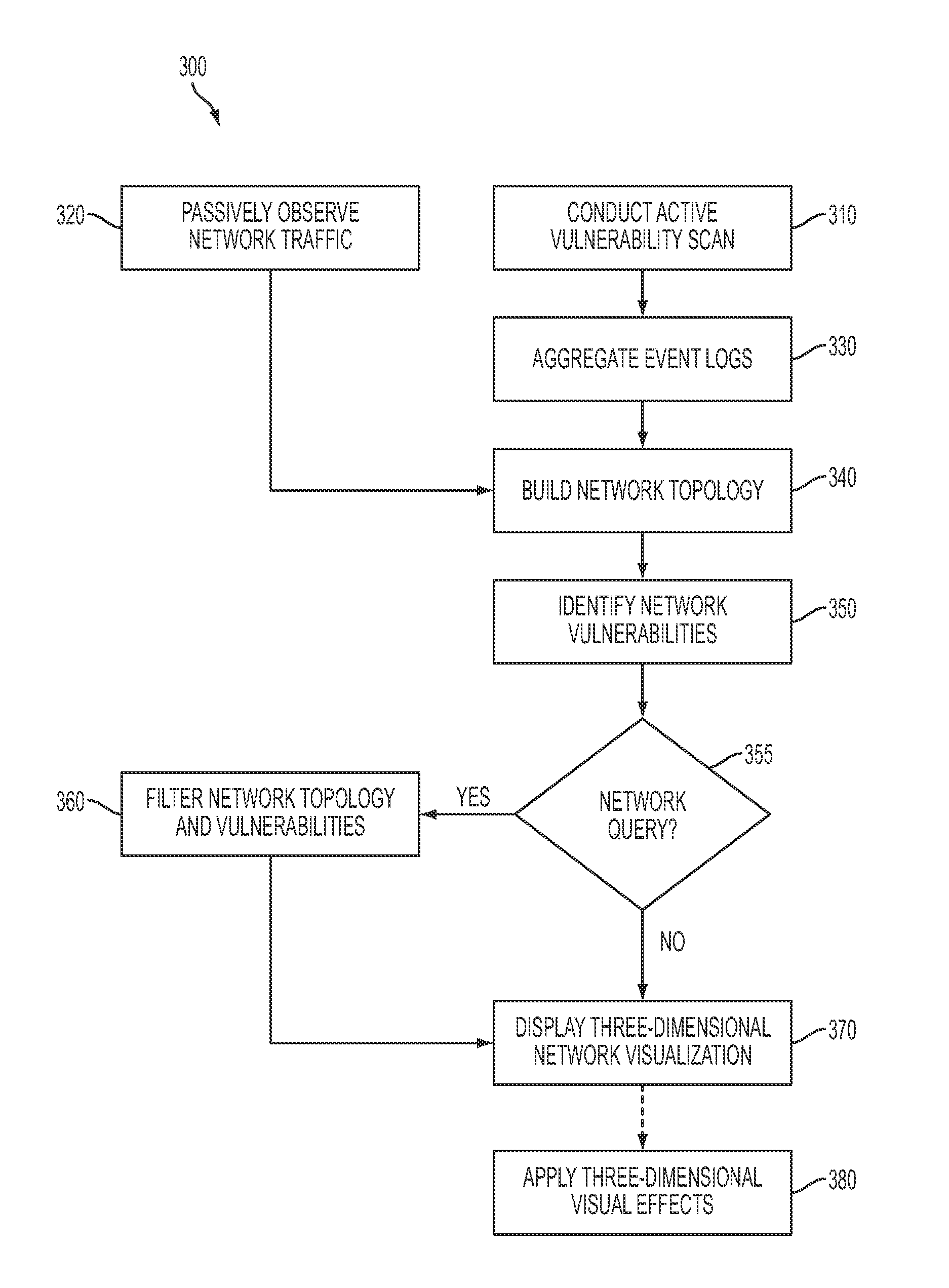
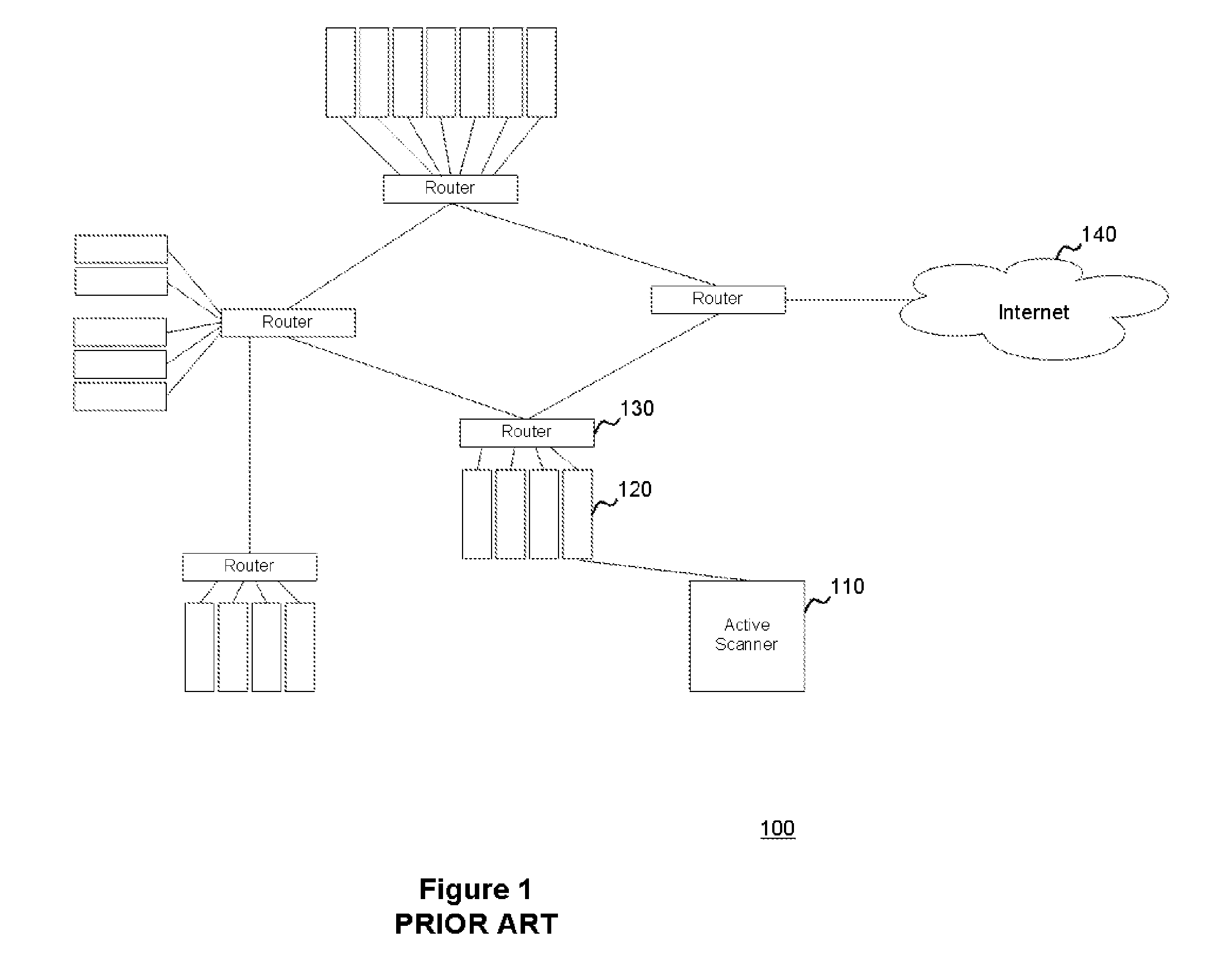
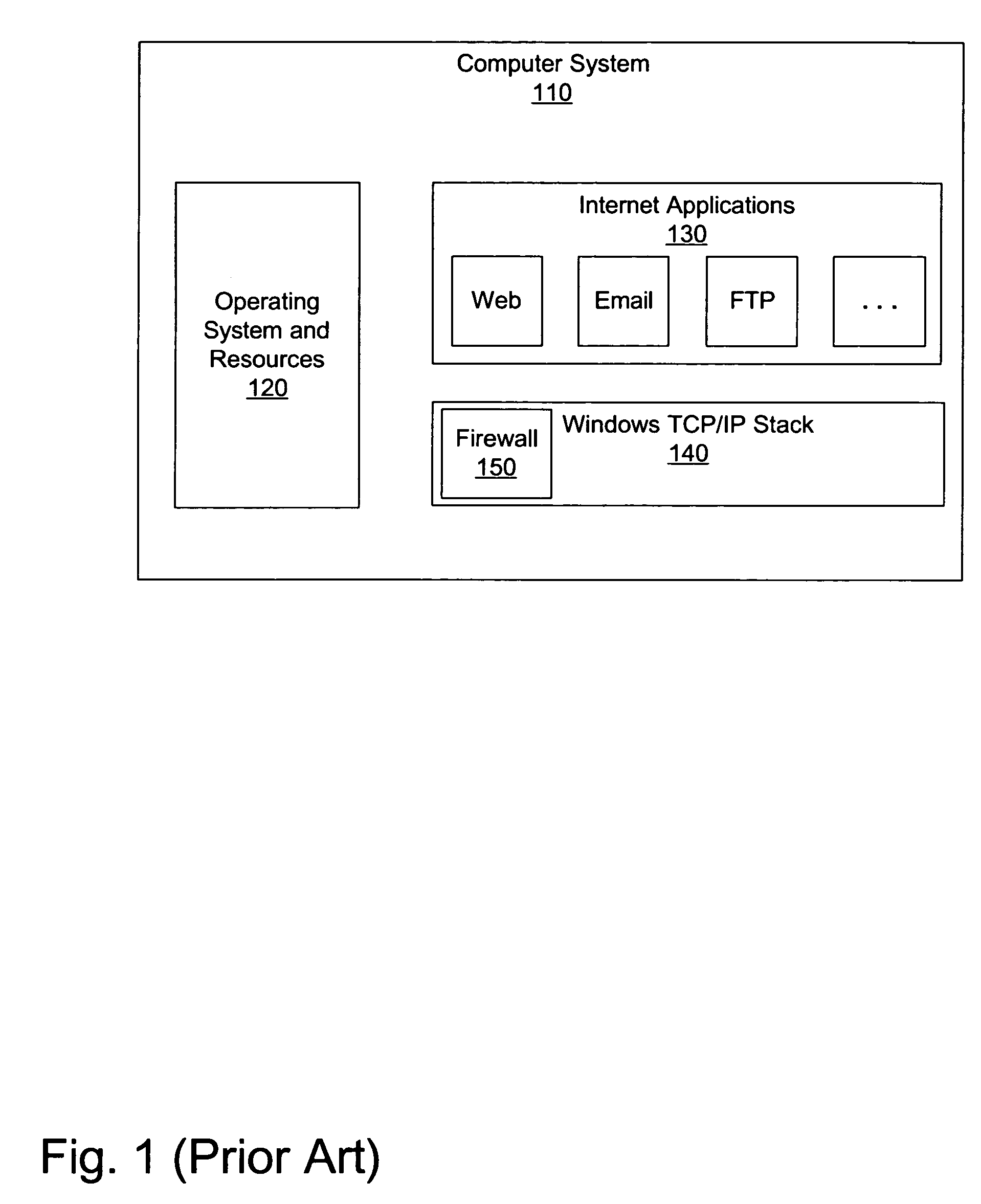
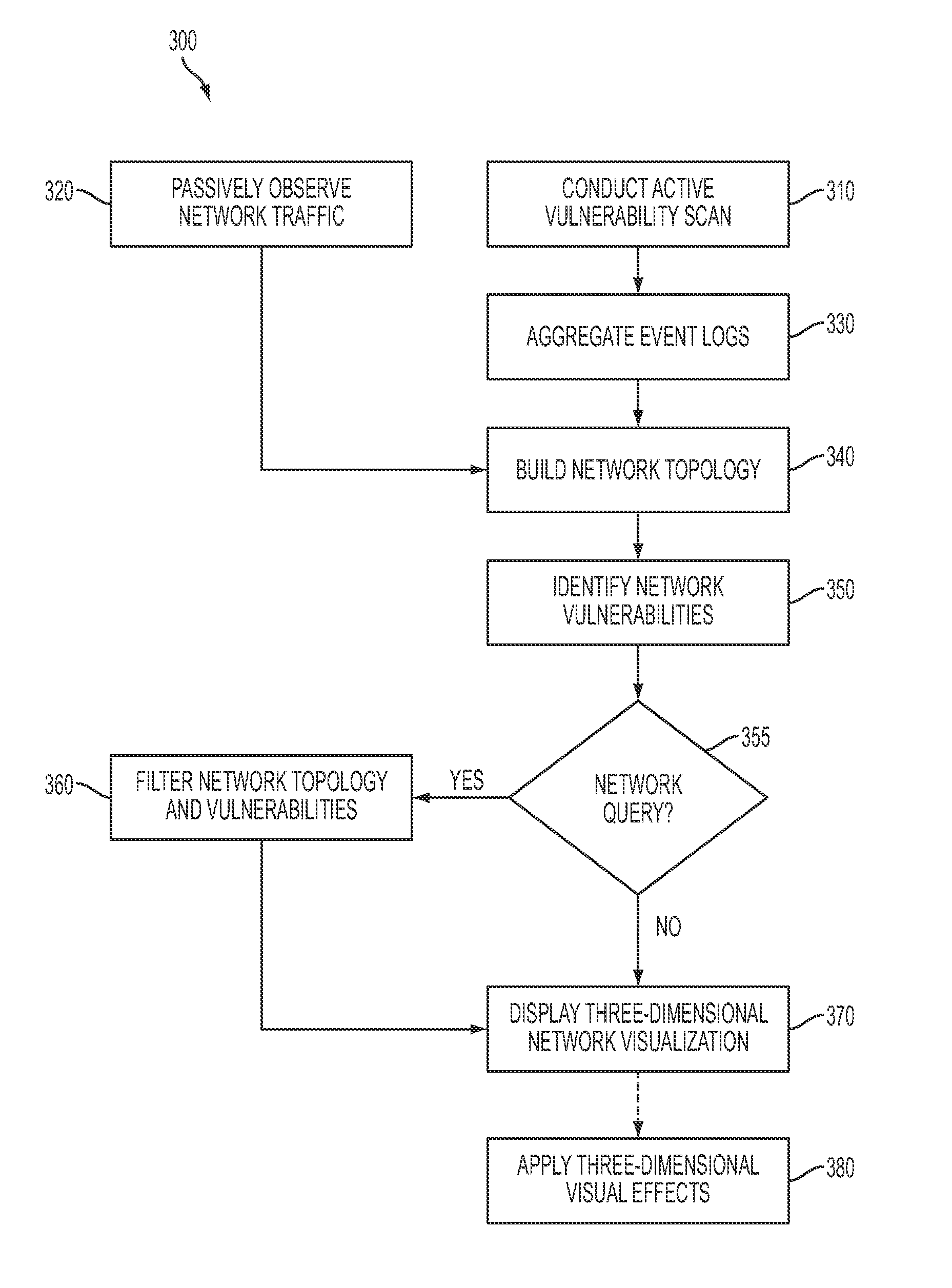
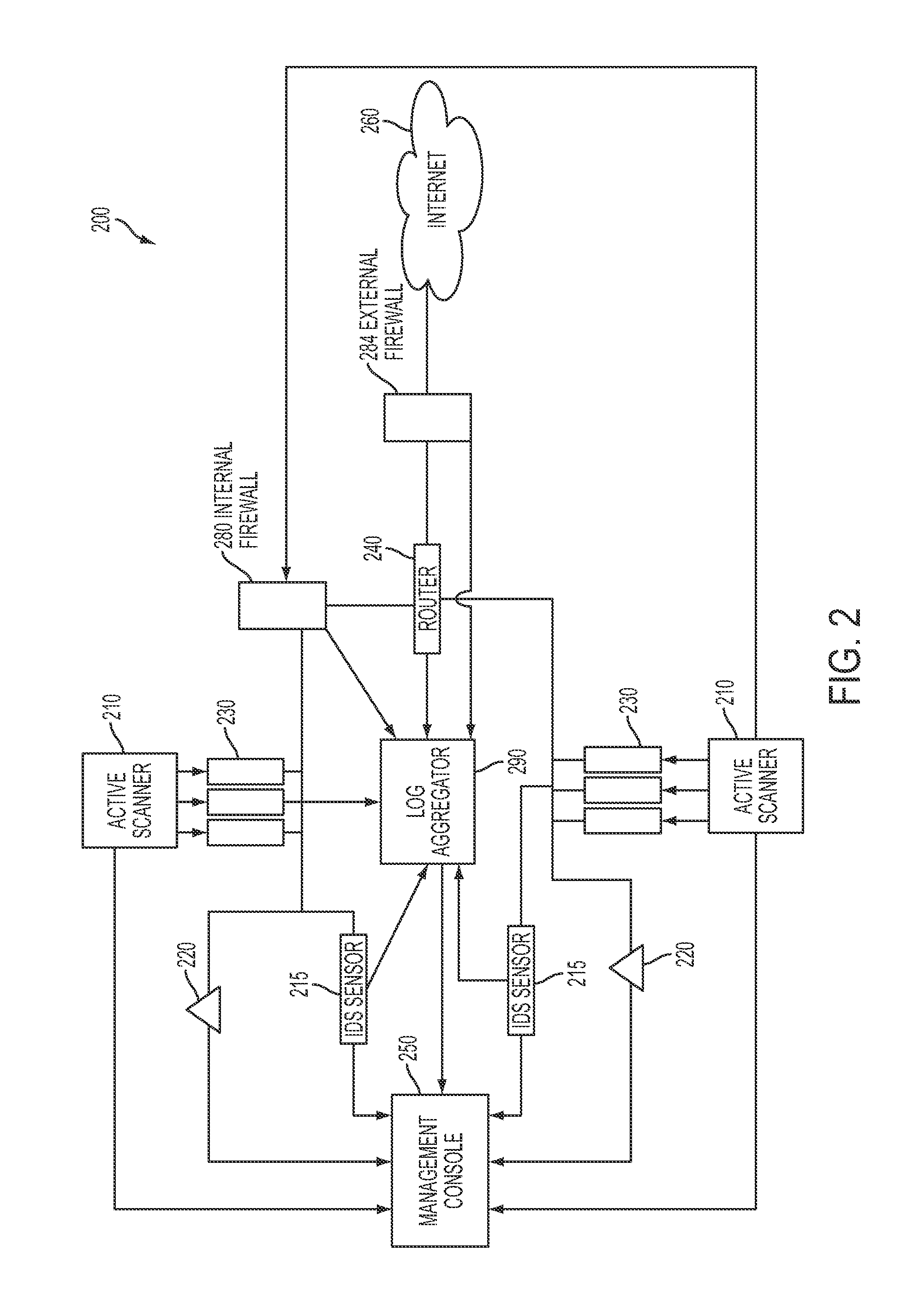
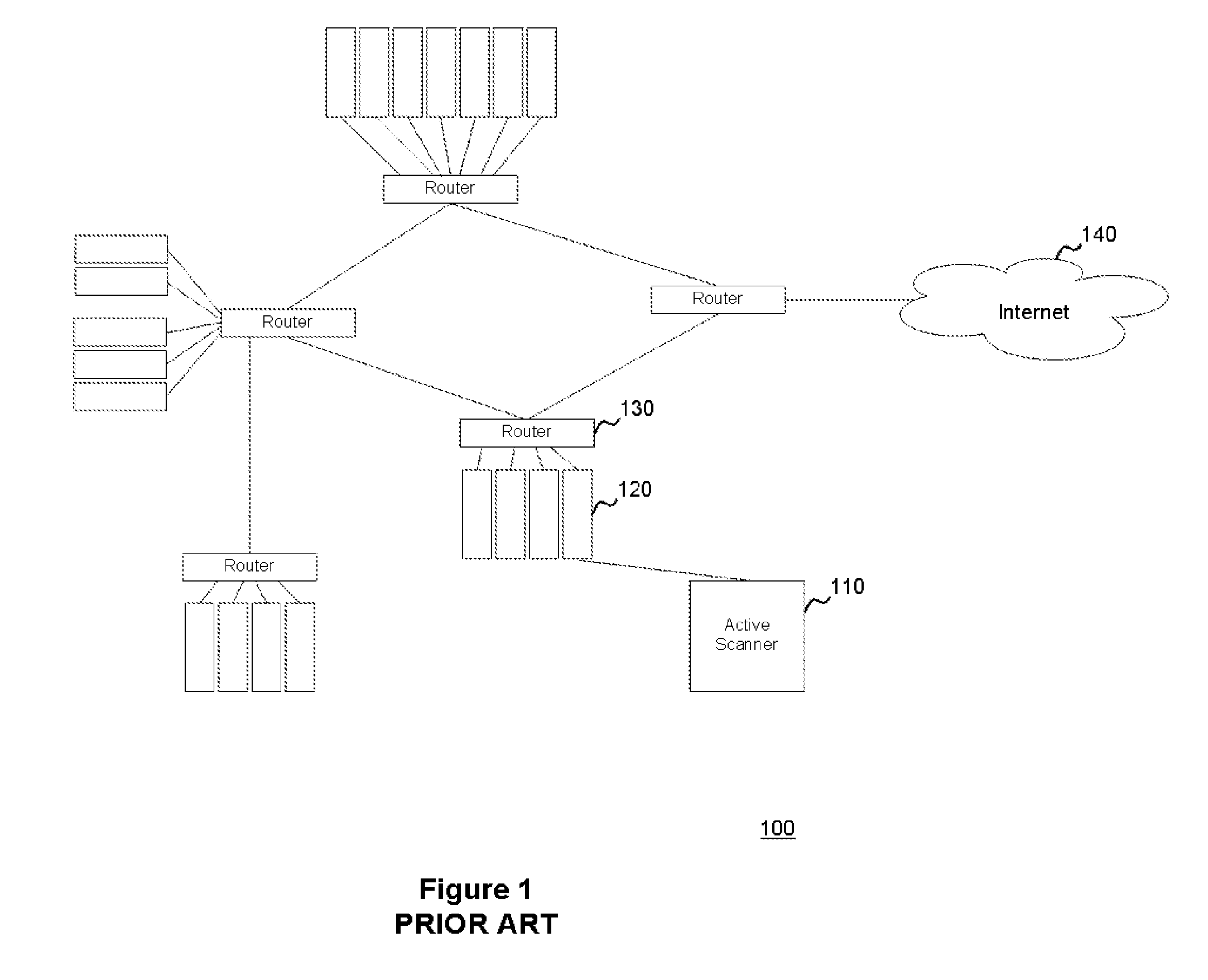
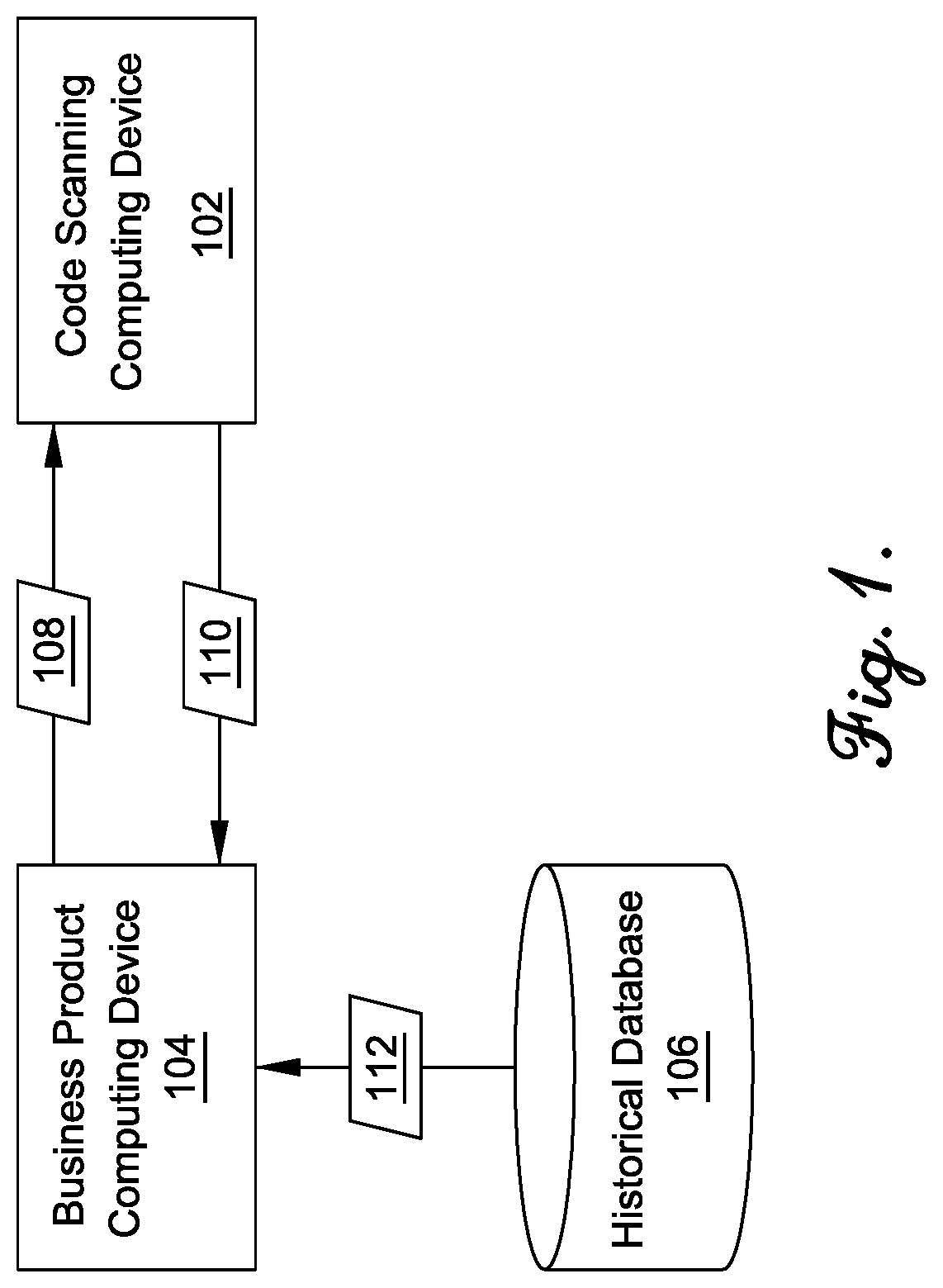
System and method for three-dimensional visualization of vulnerability and asset data
ActiveUS20110277034A1Simplify the management processMemory loss protectionError detection/correctionGraphicsVulnerability scanning
The system and method for three-dimensional visualization of vulnerability and asset data described herein may provide a management console that integrates various active vulnerability scanners, various passive vulnerability scanners, and a log correlation engine distributed in a network. In particular, the management console may include a three-dimensional visualization tool that can be used to generate three-dimensional visualizations that graphically represent vulnerabilities and assets in the network from the integrated information that management console collects the active vulnerability scanners, the passive vulnerability scanners, and the log correlation engine distributed in the network. As such, the three-dimensional visualization tool may generate three-dimensional representations of the vulnerabilities and assets in the network that can be used to substantially simplify management of the network.
Owner:TENABLE INC
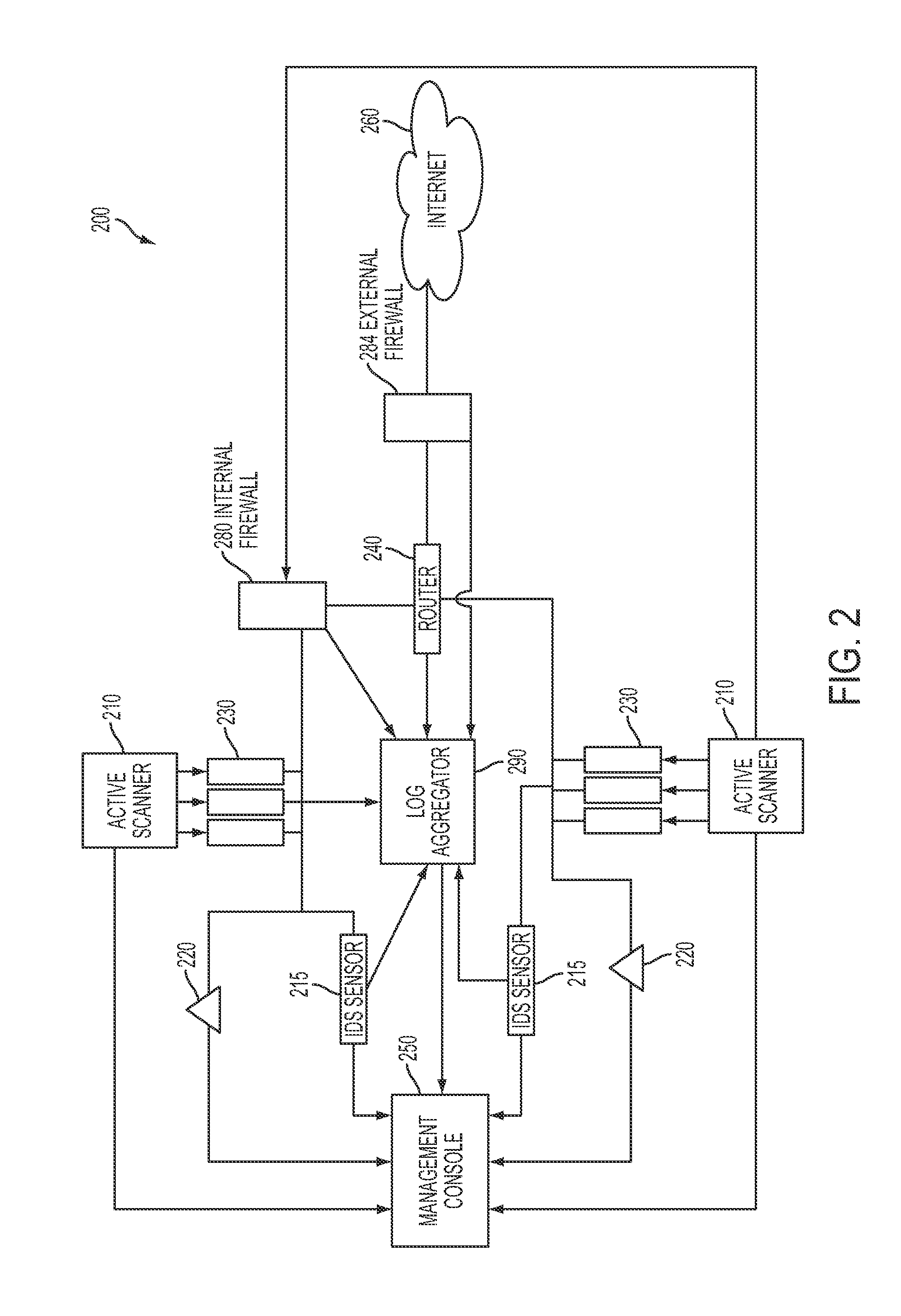
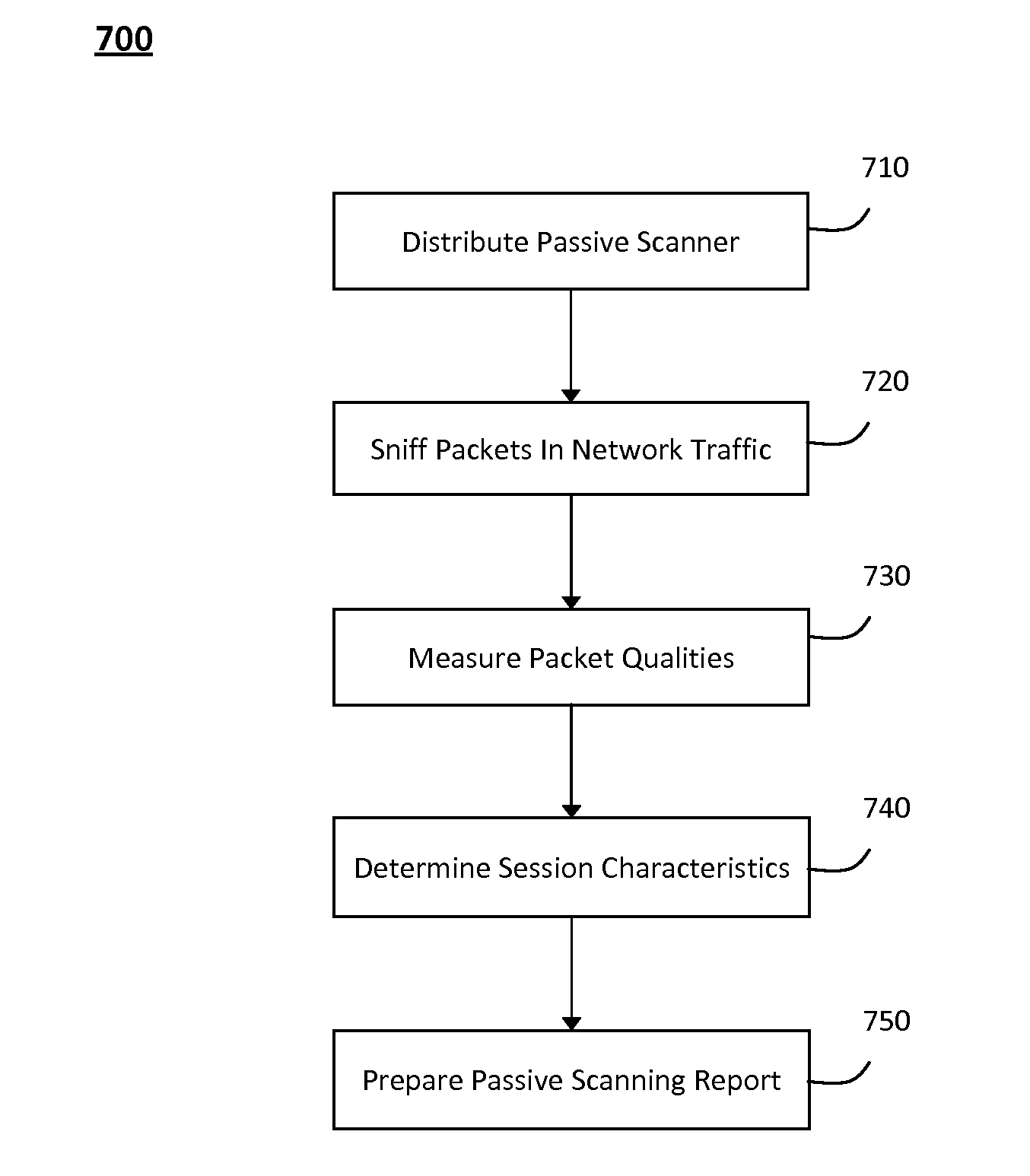
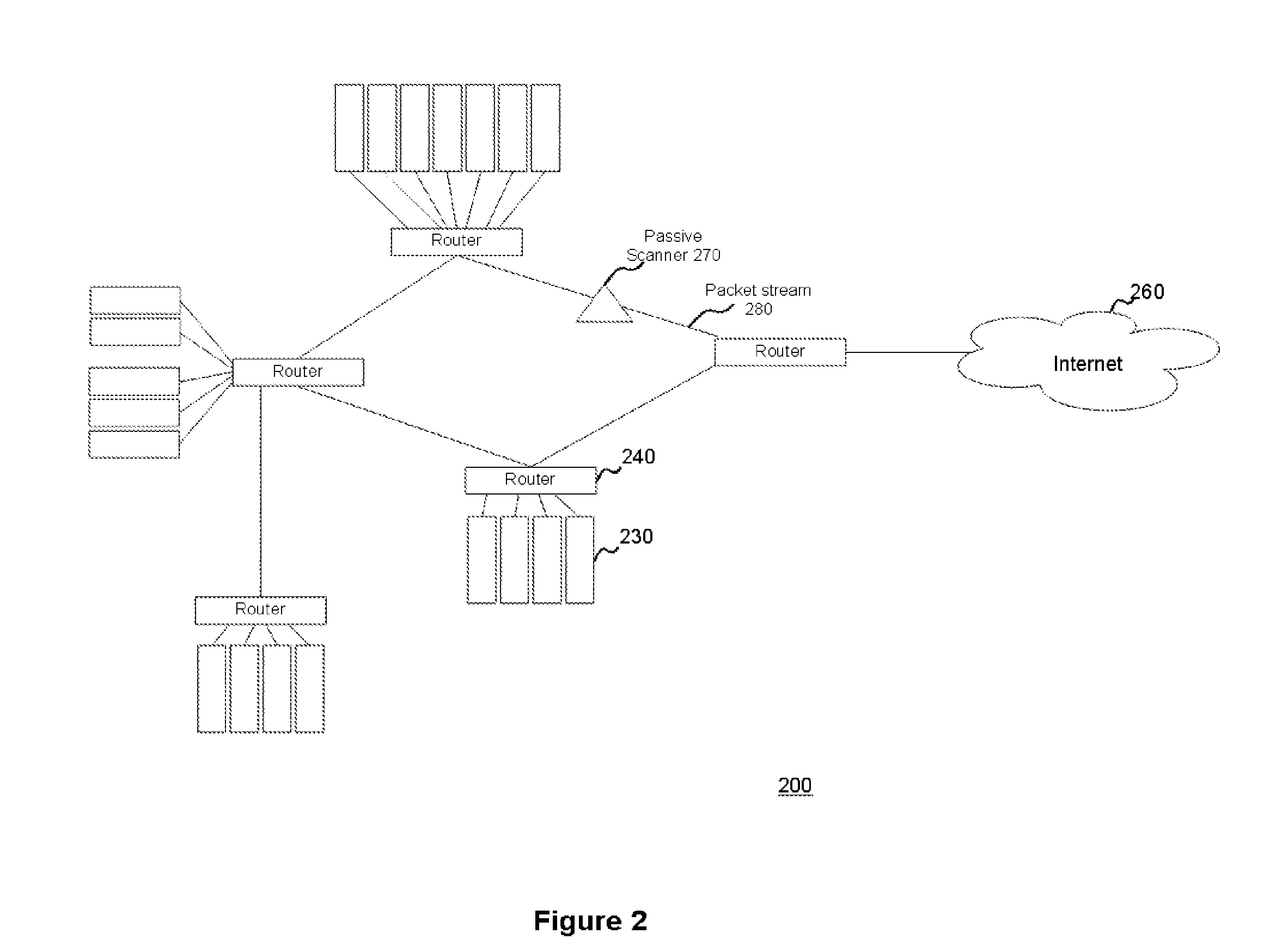
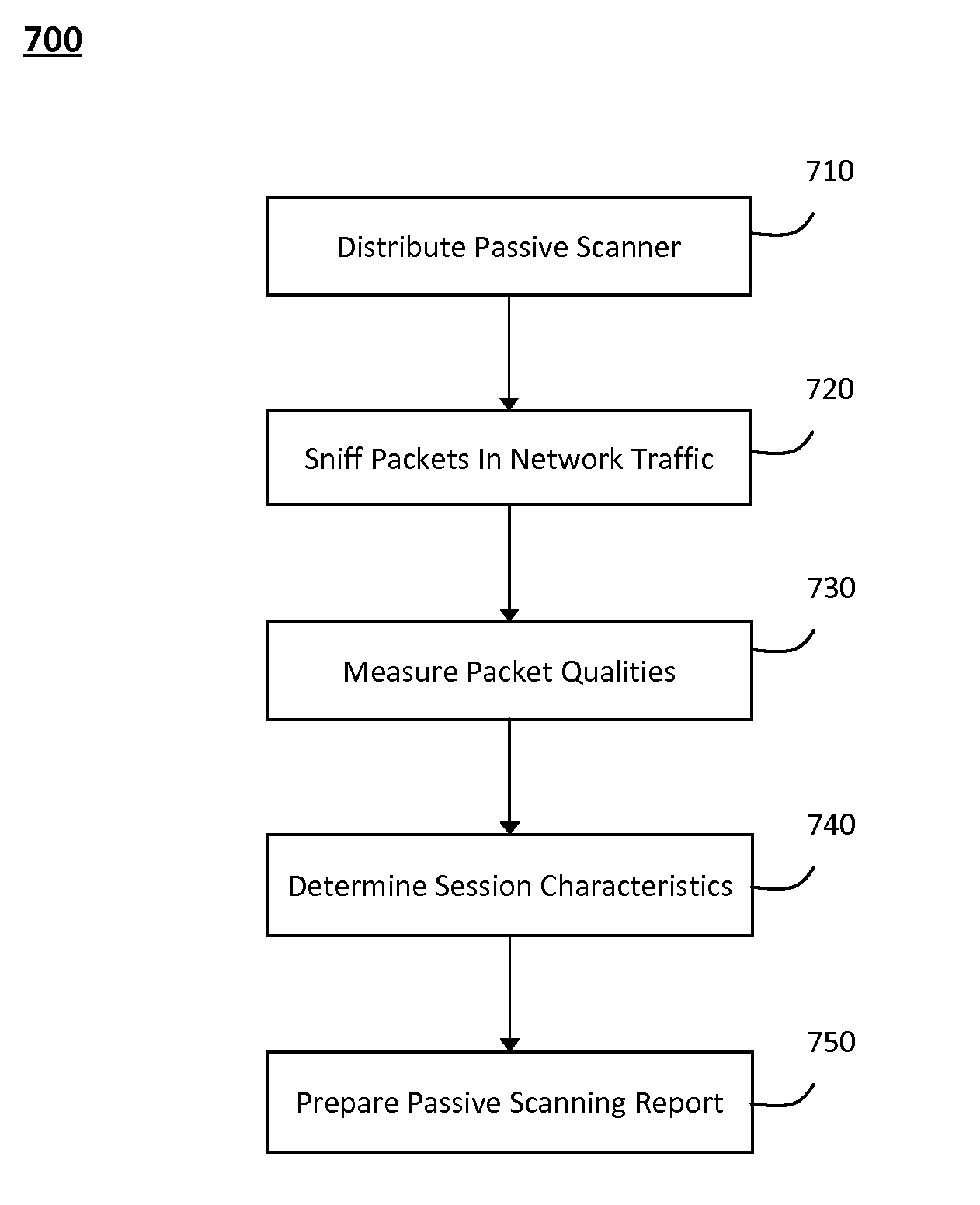
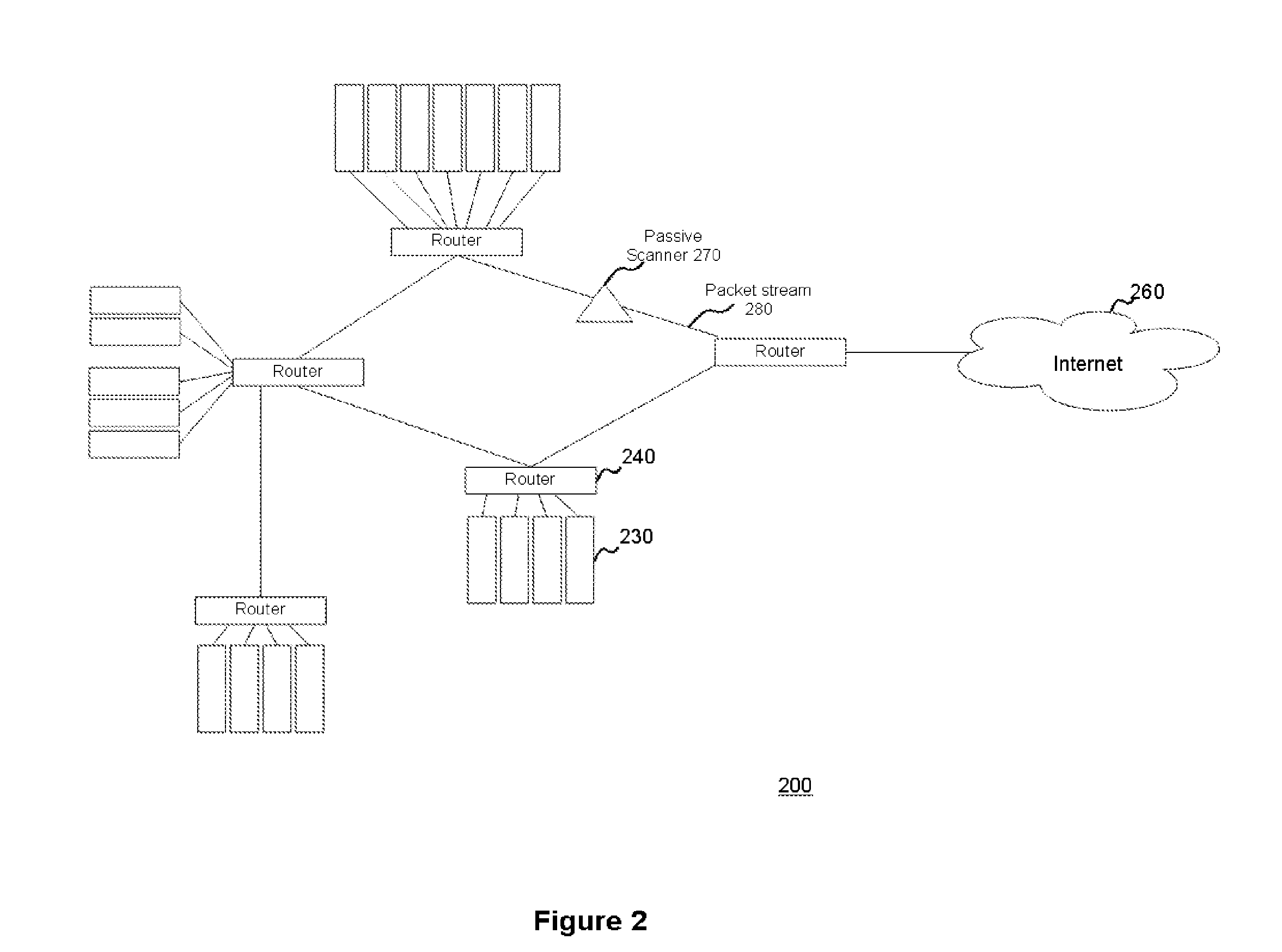
System and method for passively identifying encrypted and interactive network sessions
The system and method for passively identifying encrypted and interactive network sessions described herein may distribute a passive vulnerability scanner in a network, wherein the passive vulnerability scanner may observe traffic travelling across the network and reconstruct a network session from the observed traffic. The passive vulnerability scanner may then analyze the reconstructed network session to determine whether the session was encrypted or interactive (e.g., based on randomization, packet timing characteristics, or other qualities measured for the session). Thus, the passive vulnerability scanner may monitor the network in real-time to detect any devices in the network that run encrypted or interactive services or otherwise participate in encrypted or interactive sessions, wherein detecting encrypted and interactive sessions in the network may be used to manage changes and potential vulnerabilities in the network.
Owner:TENABLE INC
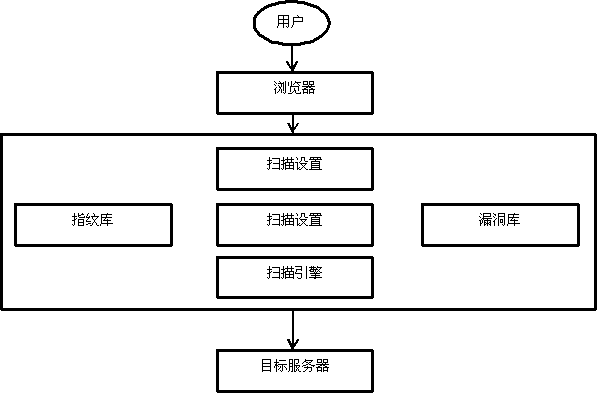
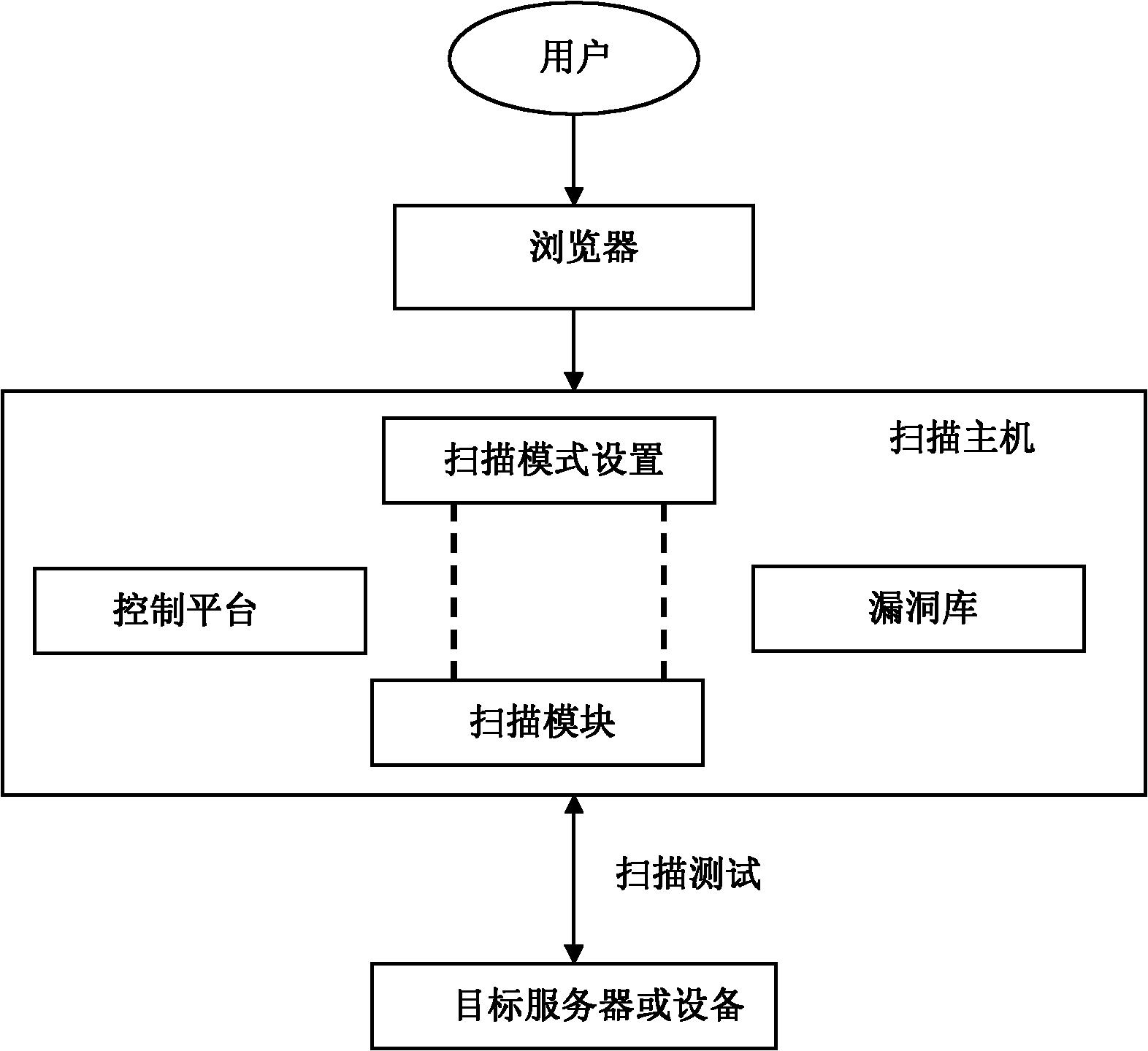
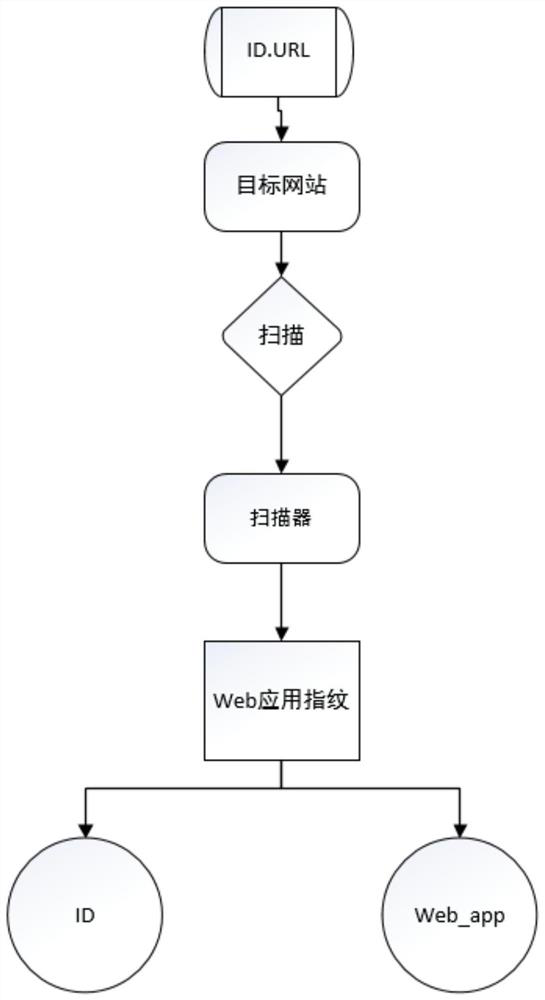
WEB vulnerability scanning method and vulnerability scanner based on fingerprint recognition technology
InactiveCN103065095AImprove accuracyEasy to addPlatform integrity maintainanceTransmissionWeb siteWeb service
The invention provides a WEB vulnerability scanning method and a vulnerability scanner based on fingerprint recognition technology. Since a feature library based security scanning scheme is used to replace a common site security vulnerability scanning scheme based on fully crawling, the scanner is improved in terms of accuracy of vulnerability scanning, flexibility of further processing after detecting vulnerabilities, efficiency of discovering vulnerabilities, and the like, and accordingly a new scheme is provided for the system security scanning and the network vulnerability scanning. The scanner comprises a user side, a browser, a scanning host and a WEB server. According to the abstract appended drawing, the scanning host comprises a control module, a scan parameter setting module, a scan engine module, a WEB fingerprint library module and a WEB vulnerability library module. The user sets scanning parameters in the scan parameter setting module through the control module, the scanning engine is firstly used for fingerprint recognition on the basis of sent parameters, and finally, the vulnerability library is used for testing site vulnerabilities and sending a test report. The scanner is capable of accurately and rapidly helping users to test and analyze vulnerability of the target website, and directly perform corresponding operations on the browser with no need of installation of client side software.
Owner:SICHUAN UNIV
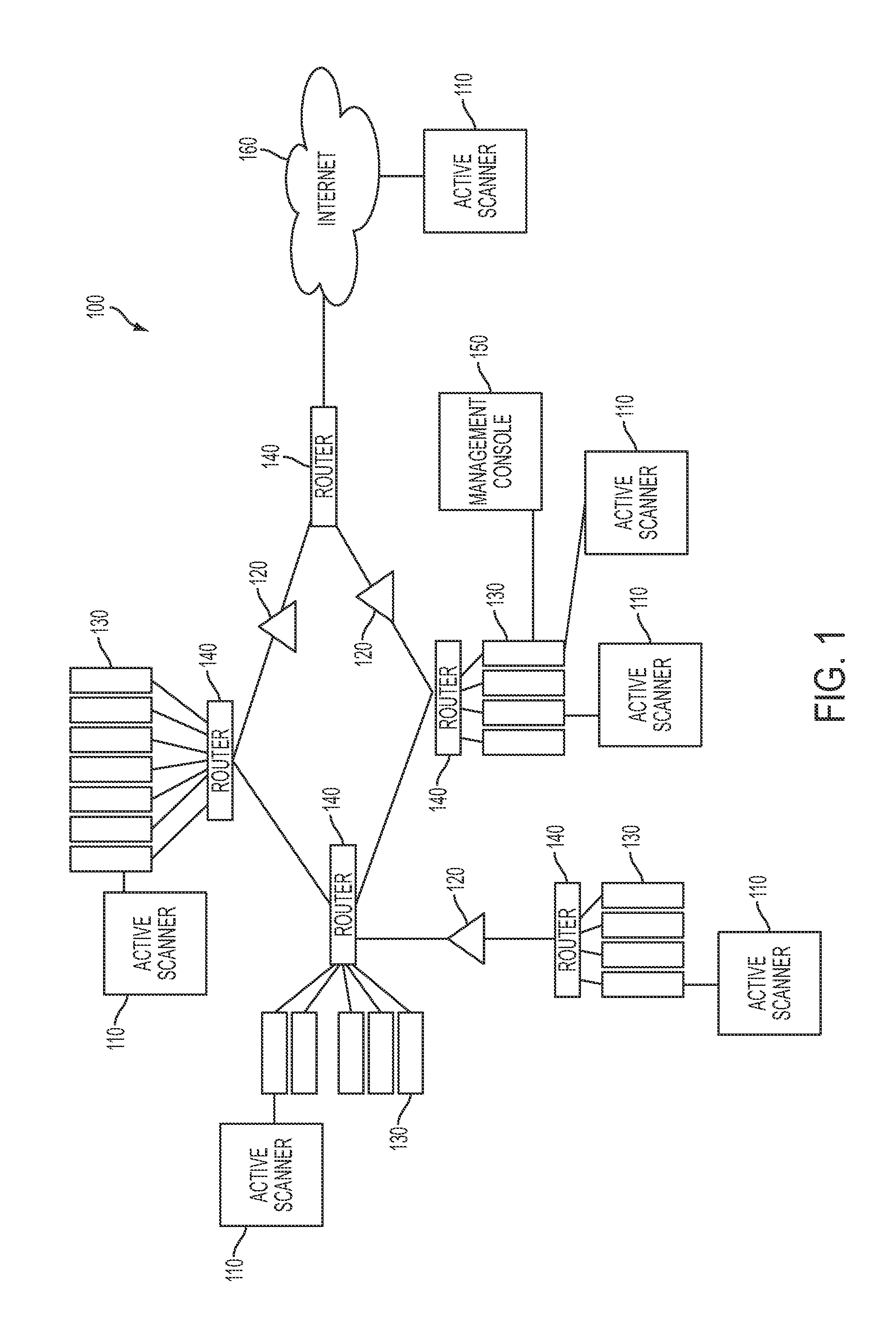
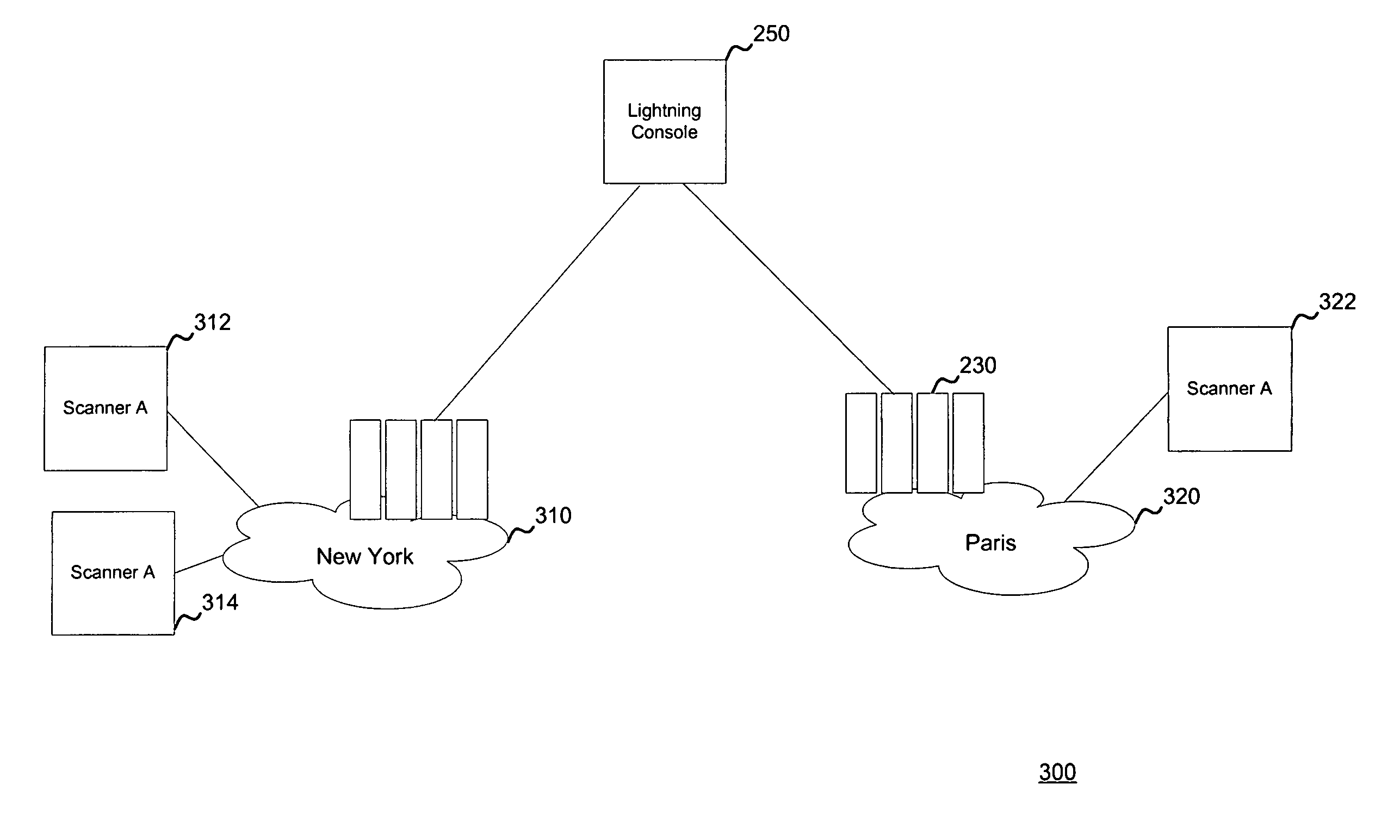
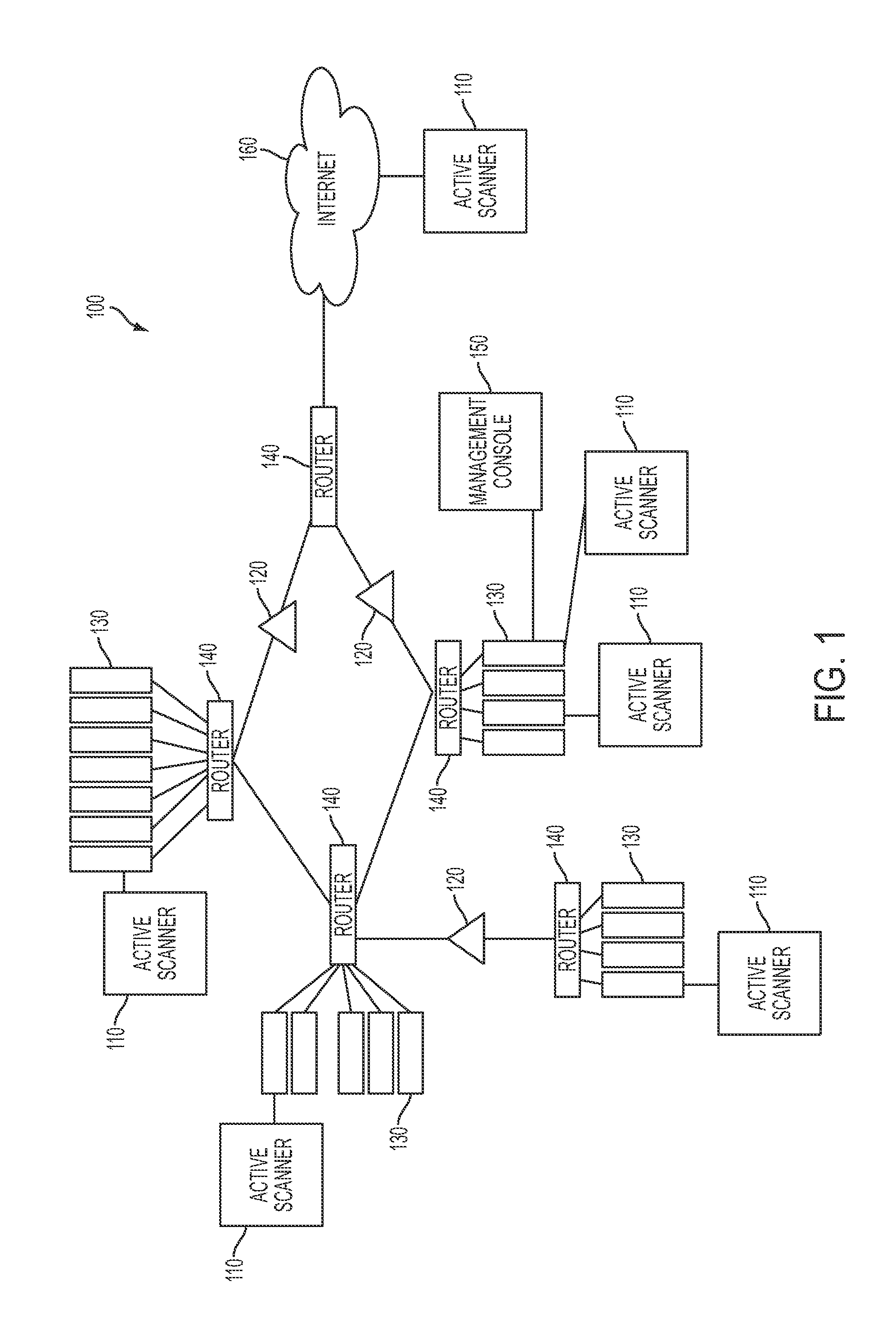
System and method for managing network vulnerability analysis systems
ActiveUS7926113B1Memory loss protectionError detection/correctionSystems managementDistributed security
Systems and methods to manage multiple vulnerability scanners distributed across one or more networks using a distributed security management system, herein called a Lightning Console. By distributing multiple scanners across a network, the work load of each scanner may be reduced to significantly reduce the impact on the network routing and switching infrastructure. In addition, scanners may be placed directly behind firewalls for more thorough scanning. Further, scanners may be placed closer to their scanned networks. By placing vulnerability scanners closer, the actual scanning traffic does not cross the core network switch and routing fabric, thereby avoiding potential network outages due to scanning activity. In addition, the closer distance of the scanners to the scanned targets speeds scan times by reducing the distance that the packets must traverse.
Owner:TENABLE INC
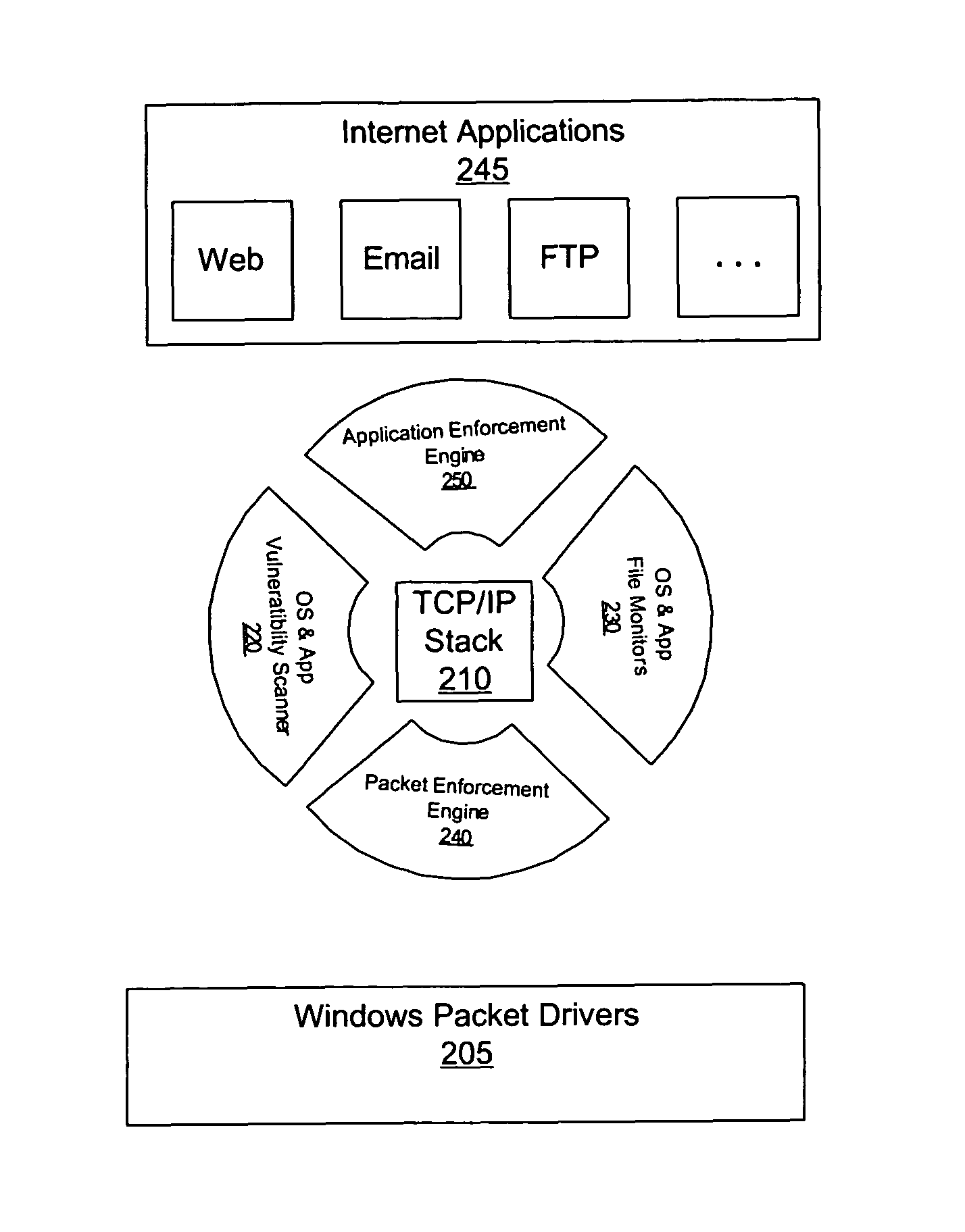
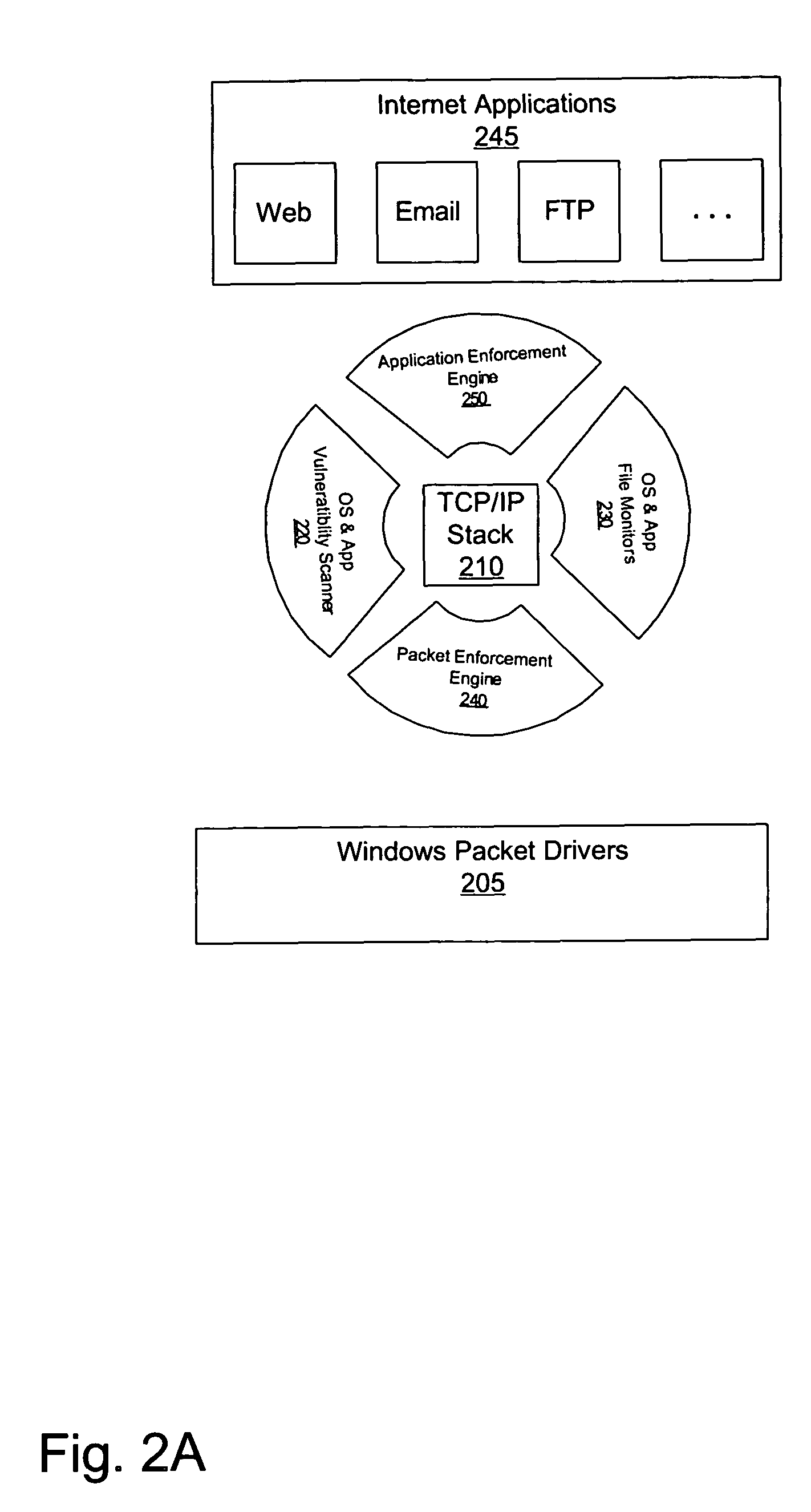
Method and apparatus to secure a computing environment
InactiveUS7797752B1Ensure integrityMemory loss protectionError detection/correctionOperational systemComputerized system
A method and apparatus for a surround security system is provided. The surround security system is embodied on a computer readable medium and includes a packet enforcement engine to screen packets to and from the network and a TCP / IP stack, an application enforcement engine to screen packets to and from the TCP / IP stack and applications on the computer system, a file monitor to verify integrity of files on the computer system and a vulnerability scanner to ensure that the computer system complies with a set level of security. The surround security system provides security which protects accesses through the TCP / IP stack for applications, and an operating system of the computer system.
Owner:RPX CORP
System and method for three-dimensional visualization of vulnerability and asset data
ActiveUS8549650B2Simplify the management processMemory loss protectionError detection/correctionGraphicsVulnerability scanning
The system and method for three-dimensional visualization of vulnerability and asset data described herein may provide a management console that integrates various active vulnerability scanners, various passive vulnerability scanners, and a log correlation engine distributed in a network. In particular, the management console may include a three-dimensional visualization tool that can be used to generate three-dimensional visualizations that graphically represent vulnerabilities and assets in the network from the integrated information that management console collects the active vulnerability scanners, the passive vulnerability scanners, and the log correlation engine distributed in the network. As such, the three-dimensional visualization tool may generate three-dimensional representations of the vulnerabilities and assets in the network that can be used to substantially simplify management of the network.
Owner:TENABLE INC
Web vulnerability scanning method and device based on infiltration technology
The invention provides a web vulnerability scanning method and device based on an infiltration technology. The scanning device comprises a client, a Web browser, a scanning host and a Web server which are sequentially connected and is characterized in that the scanning host comprises a control platform, a scanning mode setting module, a scanning module and a vulnerability library, a scanning modeis set in the scanning mode setting module by a user through the control platform, a scanning depth is extended from a first-class scanning to a second-class scanning or even a deeper scanning in thescanning module, and finally, a target website is scanned by using the vulnerability library and a test report is given. By virtue of the complete crawling-based website security vulnerability scanning method, improvements on a further treatment (strengthening the depth of detection) after vulnerabilities are detected and the flexibility of a detection mode are realized, and a comprehensive and effective solution is provided for system / network vulnerability scanning and processing.
Owner:WUXI TONGWEI TECH
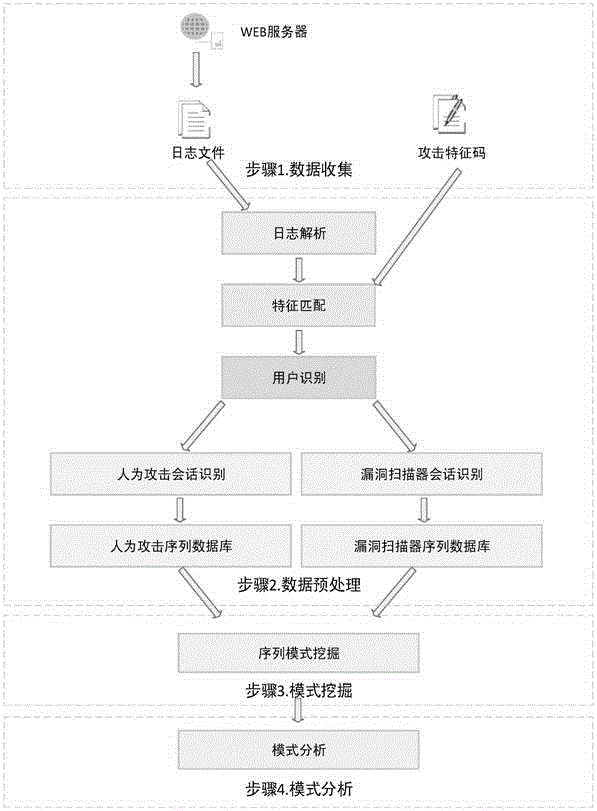
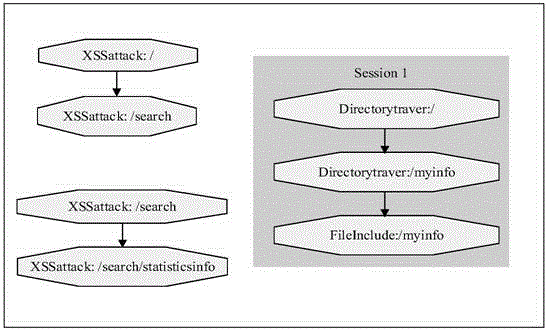
Method for mining attack frequent sequence mode from Web log
ActiveCN105721427ATransmissionSpecial data processing applicationsSequence databaseUniform resource locator
The invention relates to data mining in the field of network security and especially relates to a method for mining an attack frequent sequence mode from a Web log. The method comprises the following steps: collecting website access log files, website information and attack feature codes; analyzing a website log structure, matching analyzed URLs with the collected attack feature codes, obtaining attack records, and clearing up the URLs; performing user identification on attack log data and distinguishing manual attacks and attacks of a loophole scanner; respectively performing session identification to obtain a sequence database of the manual attacks and a sequence database of the loophole scanner; converting a character string database into a digital database, and respectively mining a frequent sequence of the sequence database by use of a sequence mode mining method; and maximizing the frequent sequence obtained through mining and converting a sequence mode into visual figure language. The process is indicated in the first graph. The method provided by the invention can realize visualization of an attack mode and explores a scanning sequence in the loophole scanner.
Owner:HUNAN UNIV
System and method for passively identifying encrypted and interactive network sessions
The system and method for passively identifying encrypted and interactive network sessions described herein may distribute a passive vulnerability scanner in a network, wherein the passive vulnerability scanner may observe traffic travelling across the network and reconstruct a network session from the observed traffic. The passive vulnerability scanner may then analyze the reconstructed network session to determine whether the session was encrypted or interactive (e.g., based on randomization, packet timing characteristics, or other qualities measured for the session). Thus, the passive vulnerability scanner may monitor the network in real-time to detect any devices in the network that run encrypted or interactive services or otherwise participate in encrypted or interactive sessions, wherein detecting encrypted and interactive sessions in the network may be used to manage changes and potential vulnerabilities in the network.
Owner:TENABLE INC
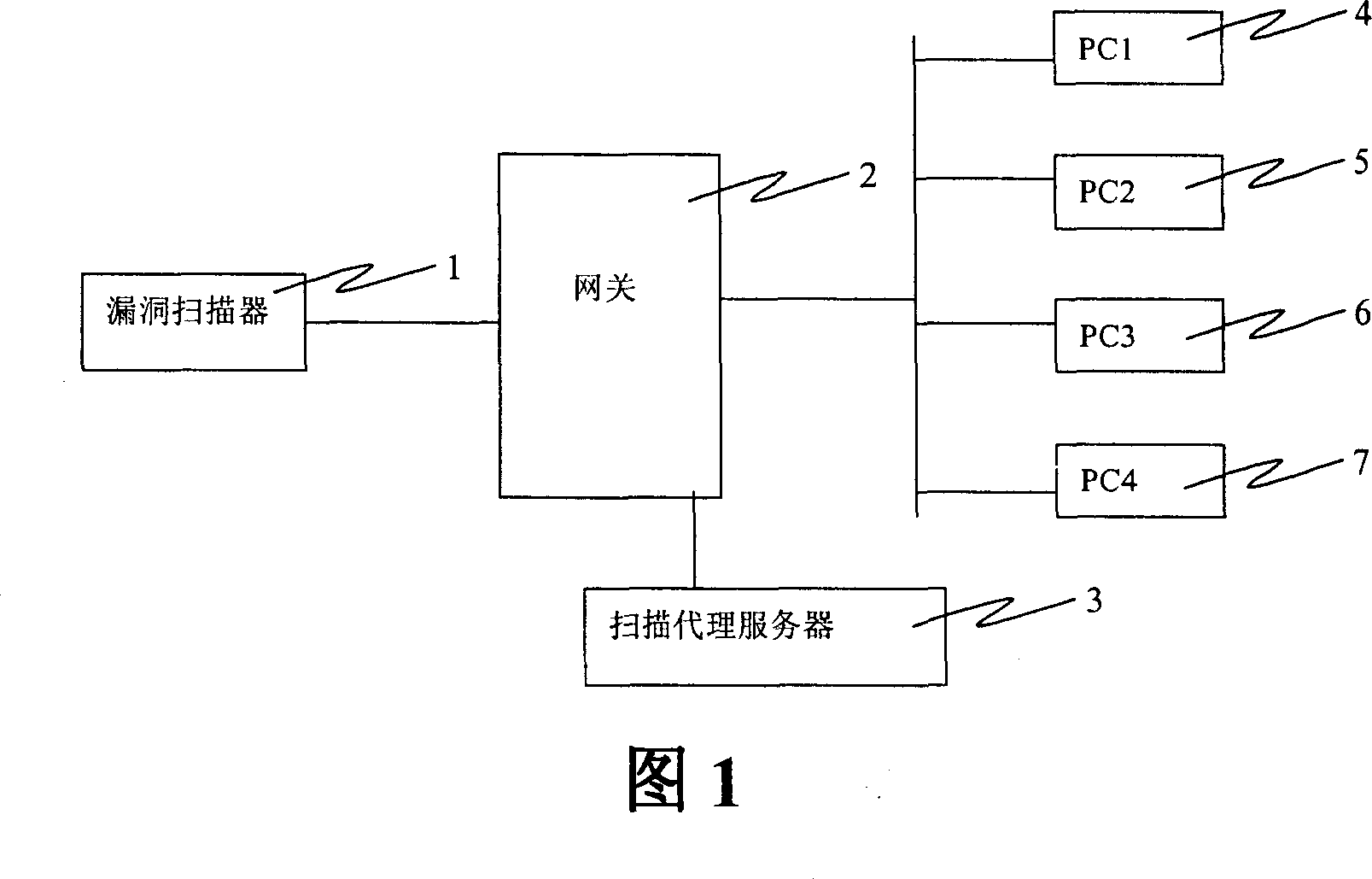
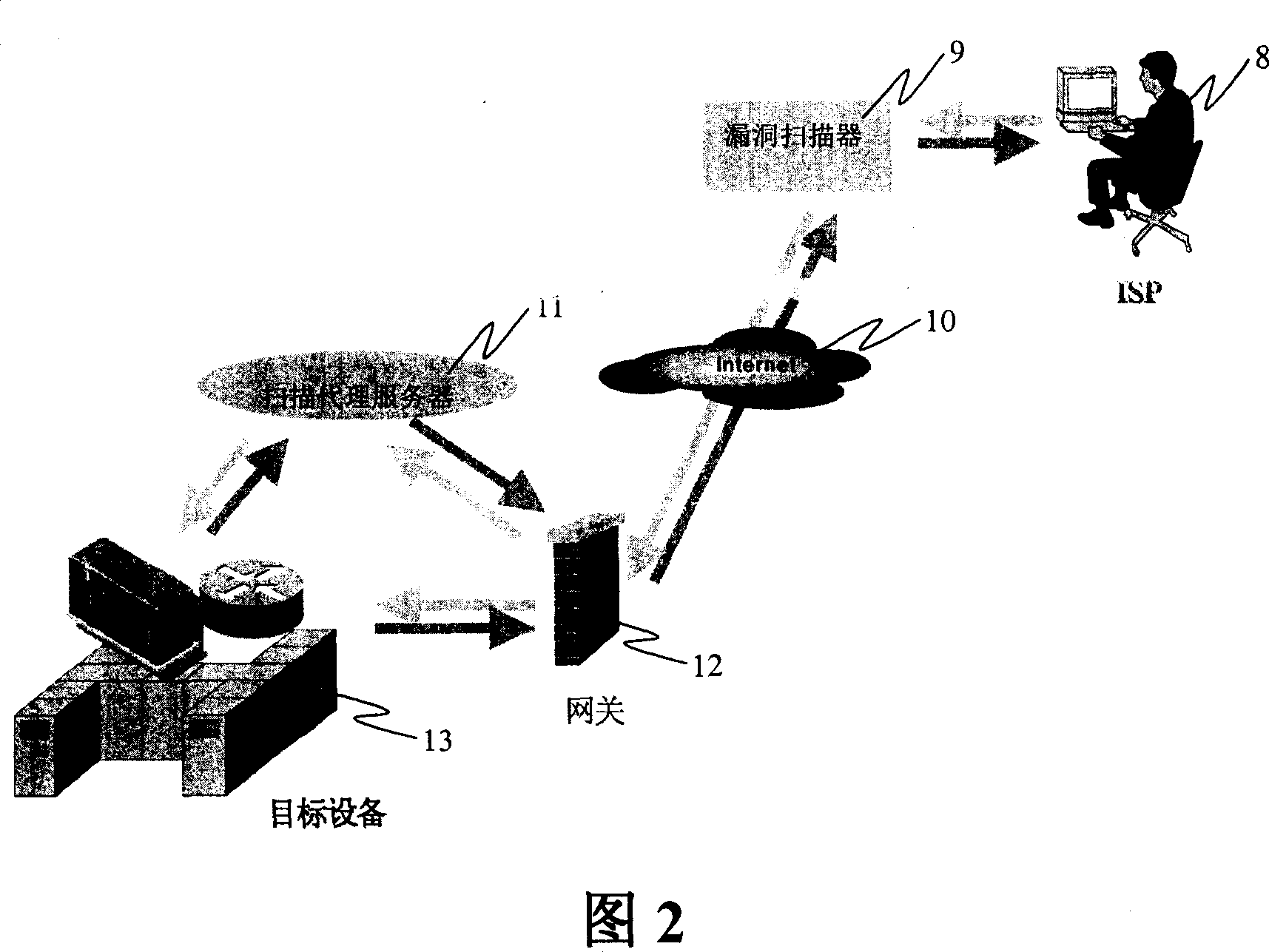
Computer network risk evaluation device and method therefor
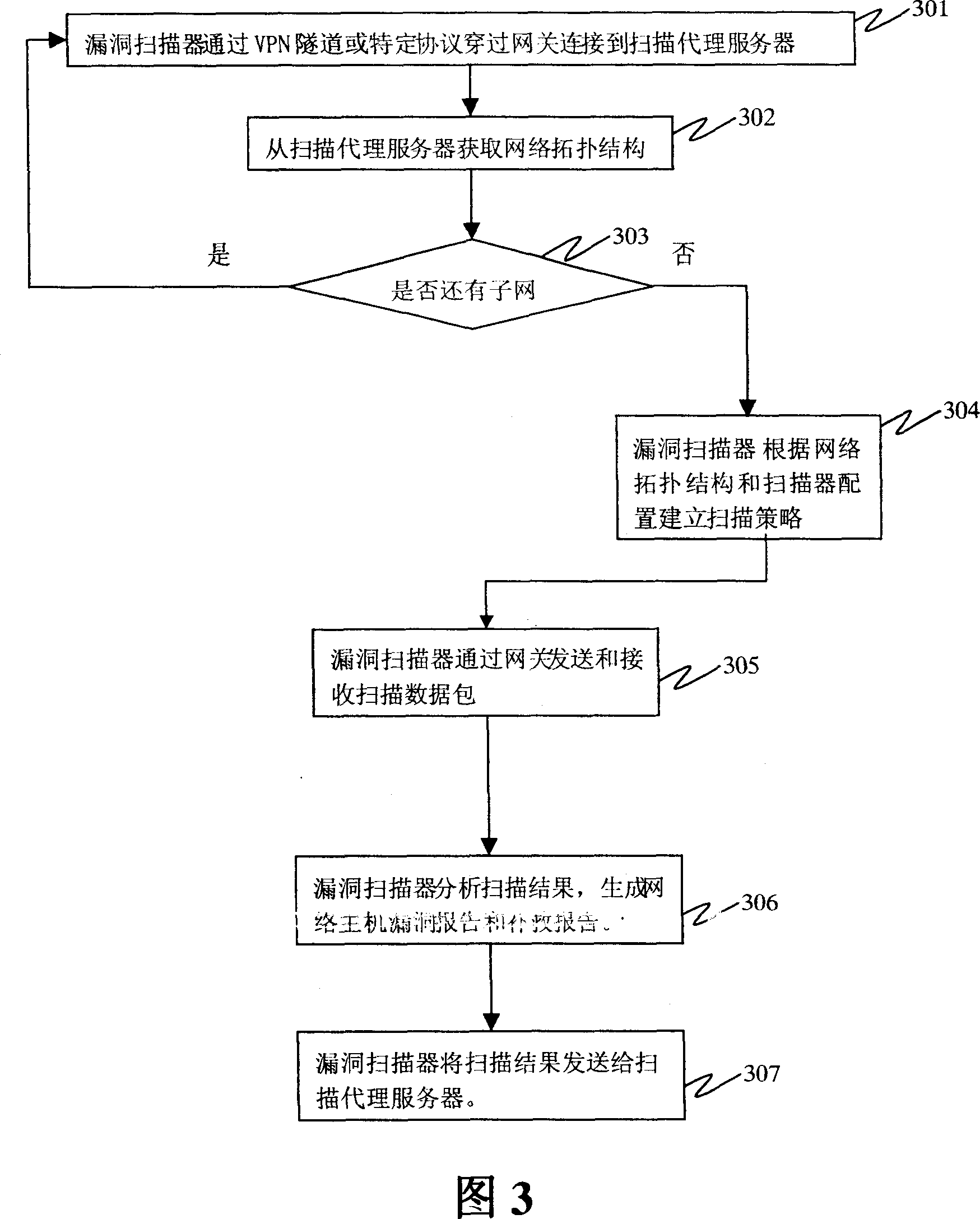
ActiveCN101064736AImprove the protective effectLow costData switching by path configurationProxy serverRisk evaluation
The invention discloses a device and method for assessing the risk of computer network, the device in invention includes: gateway, which can obtain the network topology structure information; loophole scanner, which can obtain the network topology structure information from the scanning agent sever, and builds the scanning strategy according to the network topology structure information and the allocation. The method in the invention includes following steps: step1. The scanning agent sever obtains the network topology structure information from the gateway; step 2, loophole scanner obtains the network topology structure information from the scanning agent sever; step 3, the loophole scanner builds the scanning strategy according to the network topology structure information, and scans according to the scanning strategy; step 4, the loophole scanner analyzes the scanning result, and generates the loophole report and / or remedy report. Using the invention it can protect the risk in the internal web effectively.
Owner:FORTINET
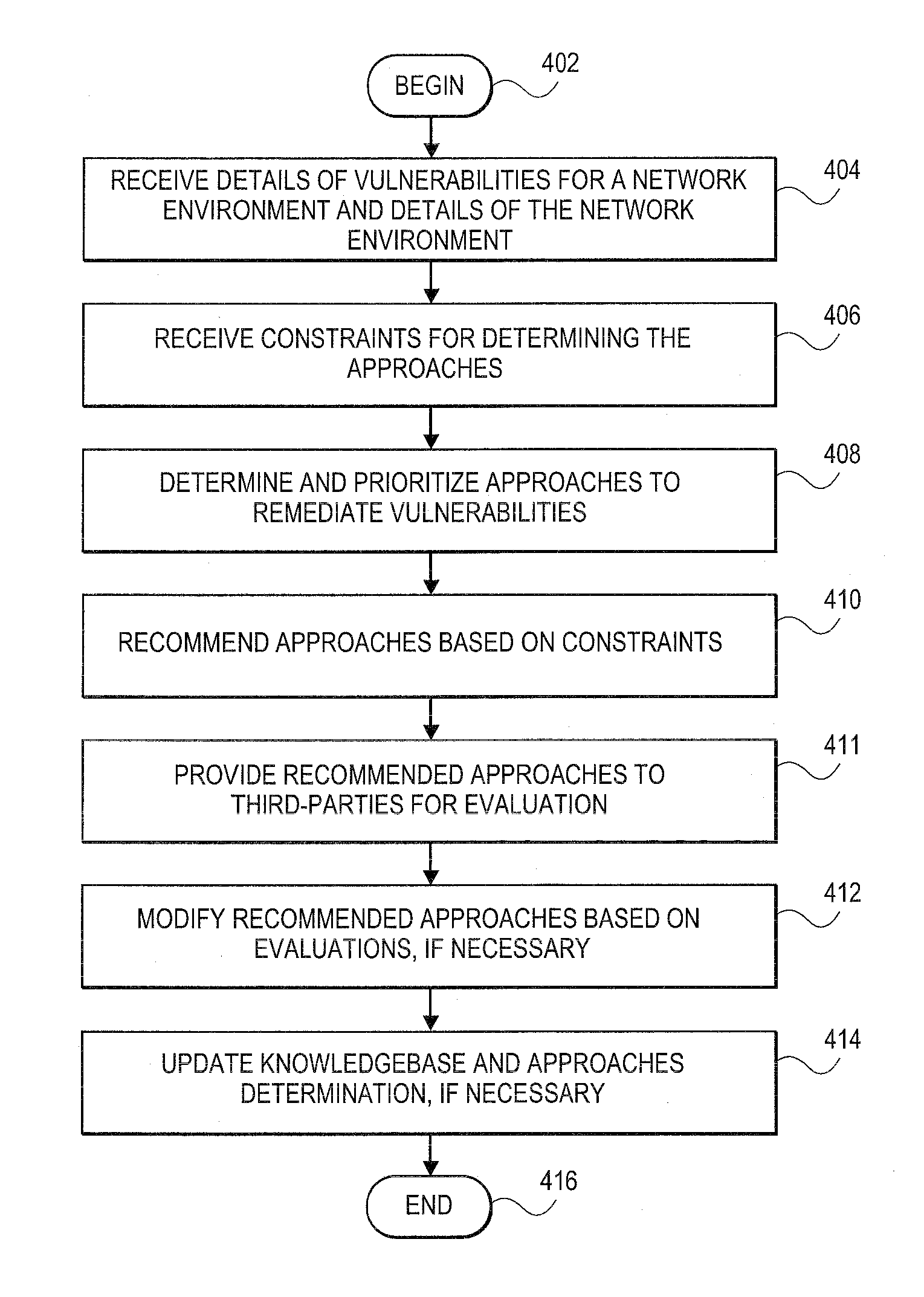
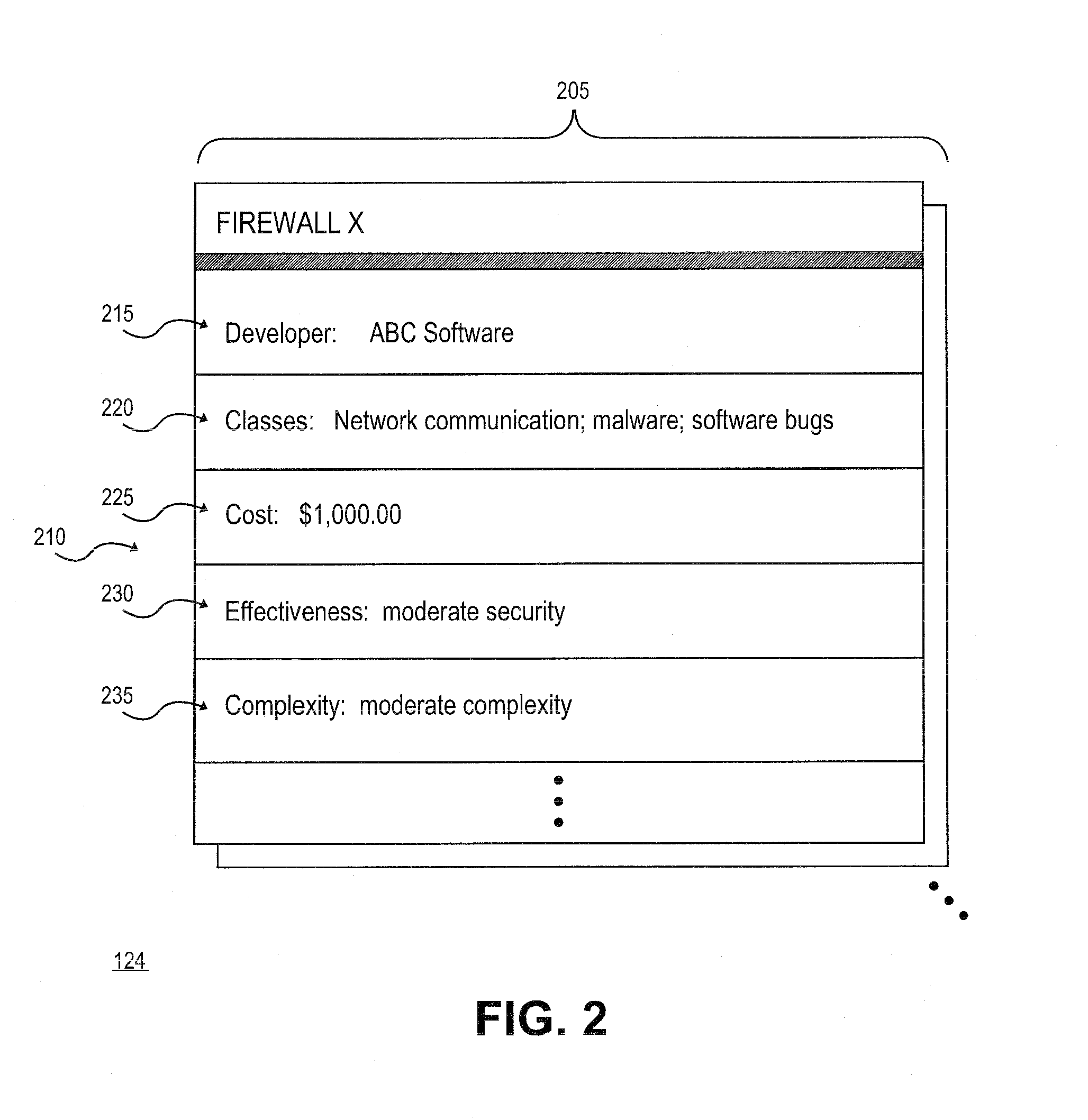
Methods and systems for providing recommendations to address security vulnerabilities in a network of computing systems
A solution recommendation (SR) tool can receive vulnerabilities identified by a vulnerability scanner and / or penetration testing tool. The SR tool can determine various approaches for remediating or mitigating the identified vulnerabilities, and can prioritize the various approaches based on the efficiency of the various approaches in remediating or mitigating the identified vulnerabilities. The SR tool can recommend one or more of the prioritized approaches based on constraints such as cost, effectiveness, complexity, and the like. Once the one or more of the prioritized approaches are selected, the SR tool can recommend the one or more prioritized approaches to third-party experts for evaluation.
Owner:RAPID7
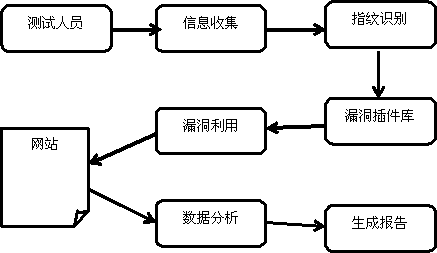
Method for realizing loophole scanning
InactiveCN1558605AAvoid one-sidednessOverall security situationData switching networksWeb browserRemote control
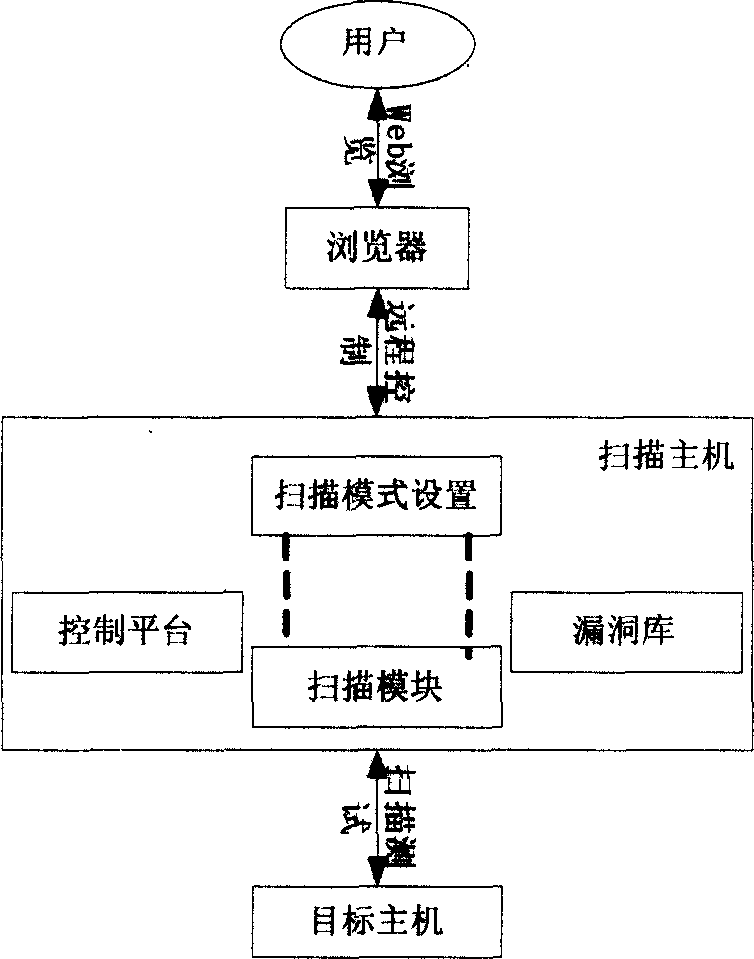
The present invention discloses a method for scanning loophole which is realized by a loophole scanner comprising a user end, a browser, a scanning host machine and a destination host, wherein the scanning host machine portion comprises a control platform, a scanning mode configuration module, a scanning module and a loophole library, the scanning mode configuration module is embedded in the control platform, the user end performs remote control to the remote scanning host machine through Web browsers.
Owner:SHANGHAI JIAO TONG UNIV
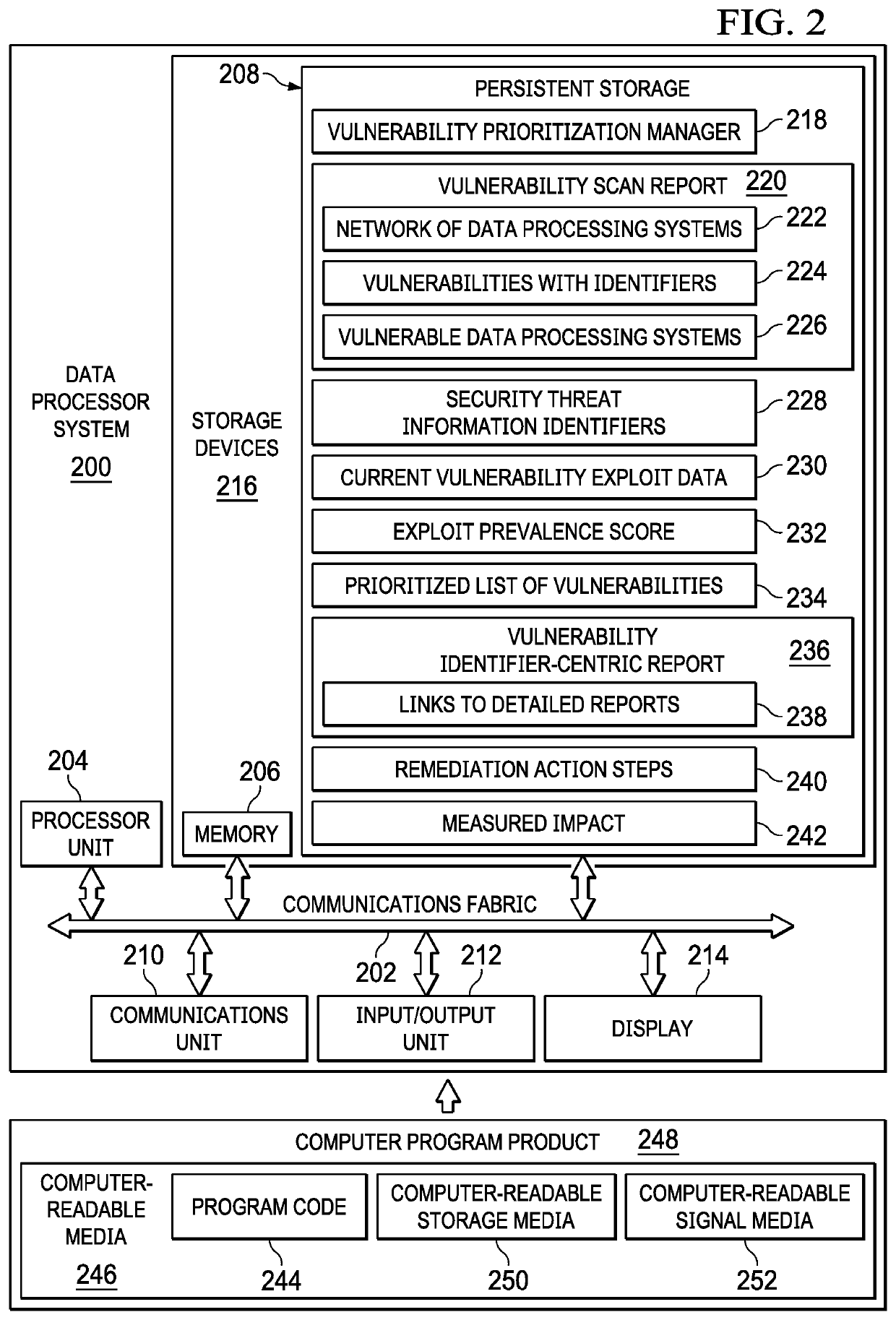
Prioritizing vulnerability scan results
Prioritizing vulnerability scan results is provided. Vulnerability scan results data corresponding to a network of data processing systems are received from a vulnerability scanner. The vulnerability scan results data are parsed to group the vulnerability scan results data by vulnerability identifiers. A corresponding security threat information identifier is associated with each vulnerability identifier. A correlation of each associated security threat information identifier is performed with a set of current vulnerability exploit data that corresponds to that particular security threat information identifier. Current security threat information that affects host data processing systems in the network is determined based on the correlation between each associated security threat information identifier and its corresponding set of current vulnerability exploit data. The current security threat information is prioritized based on a number of corresponding current vulnerability exploit attacks.
Owner:IBM CORP
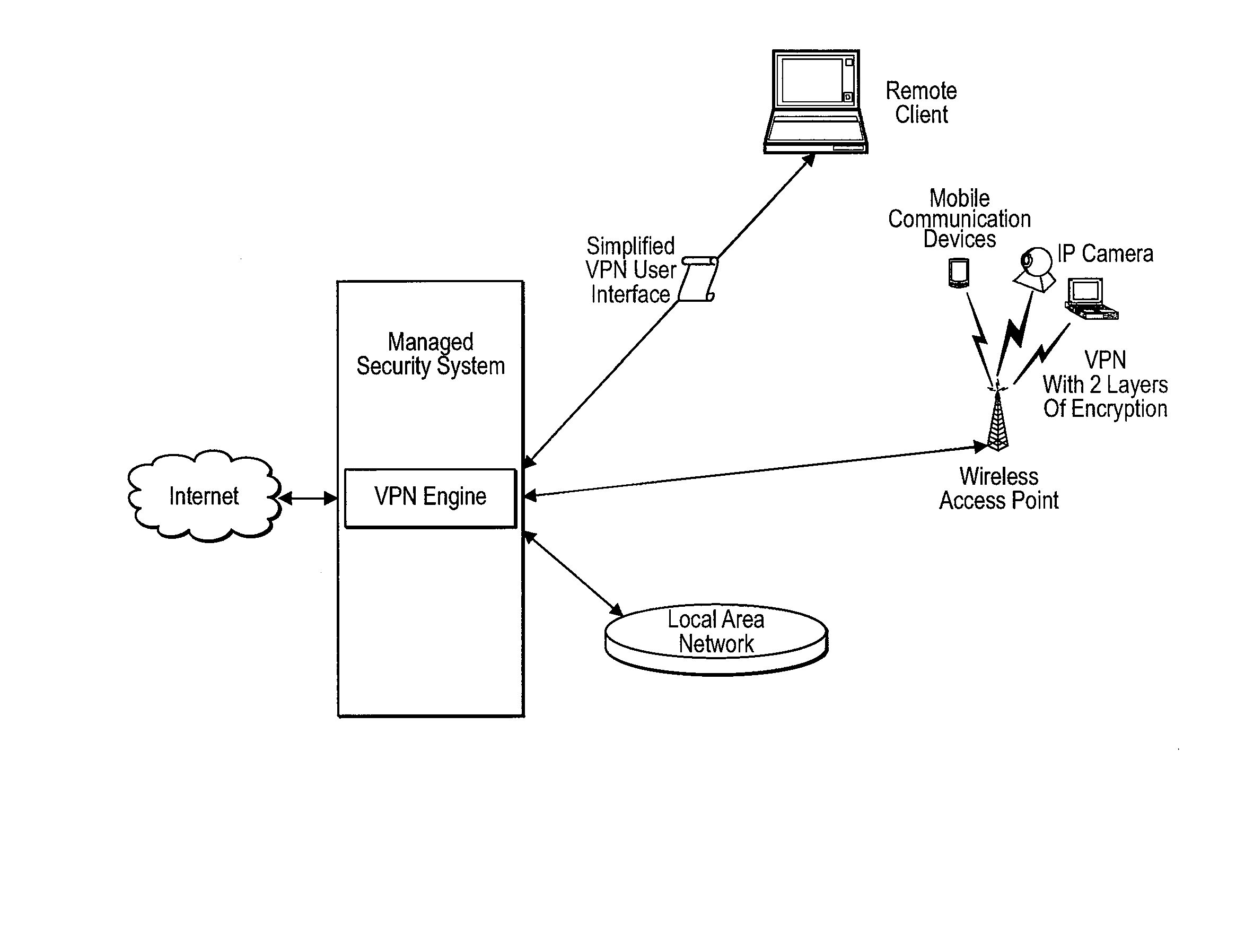
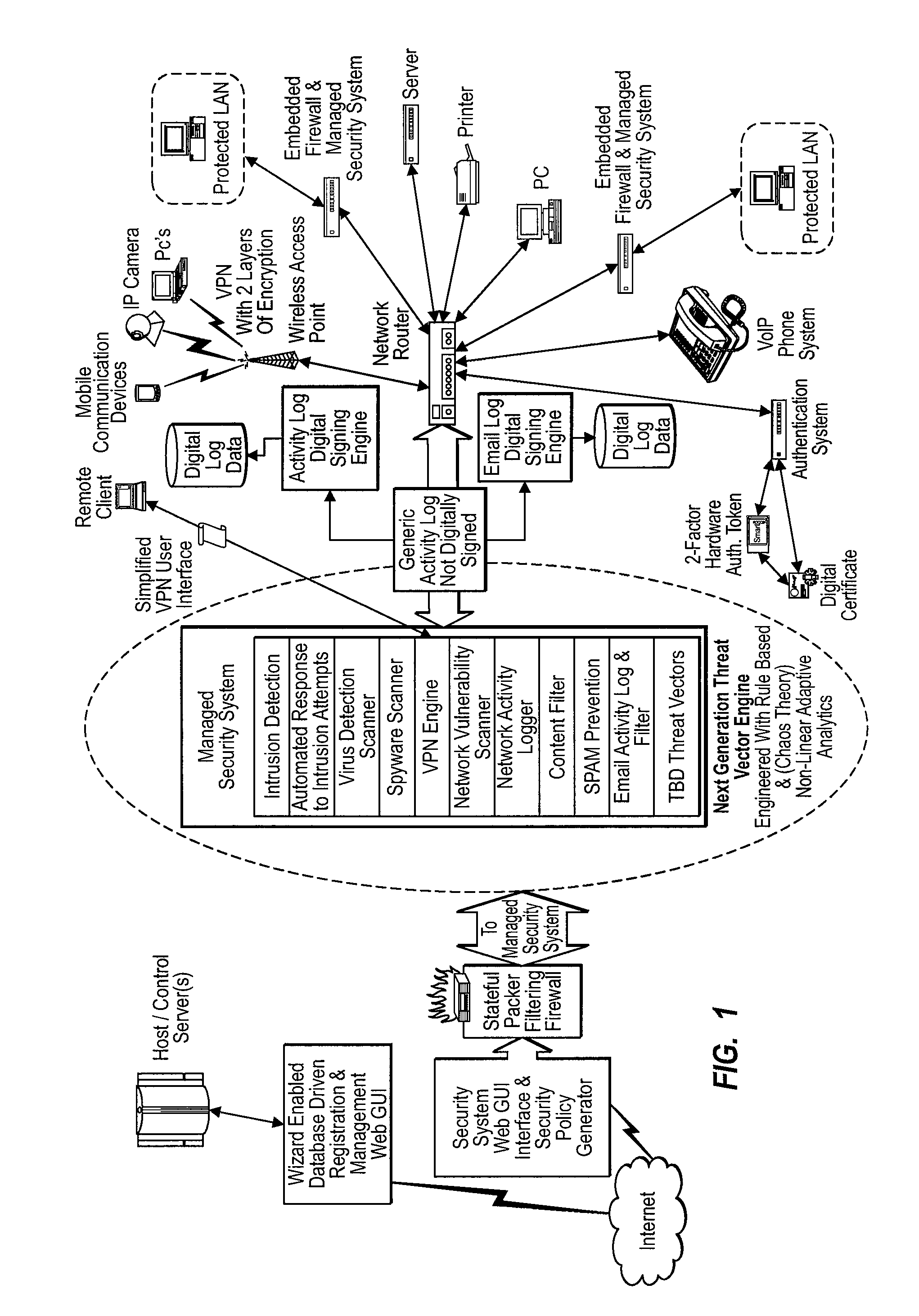
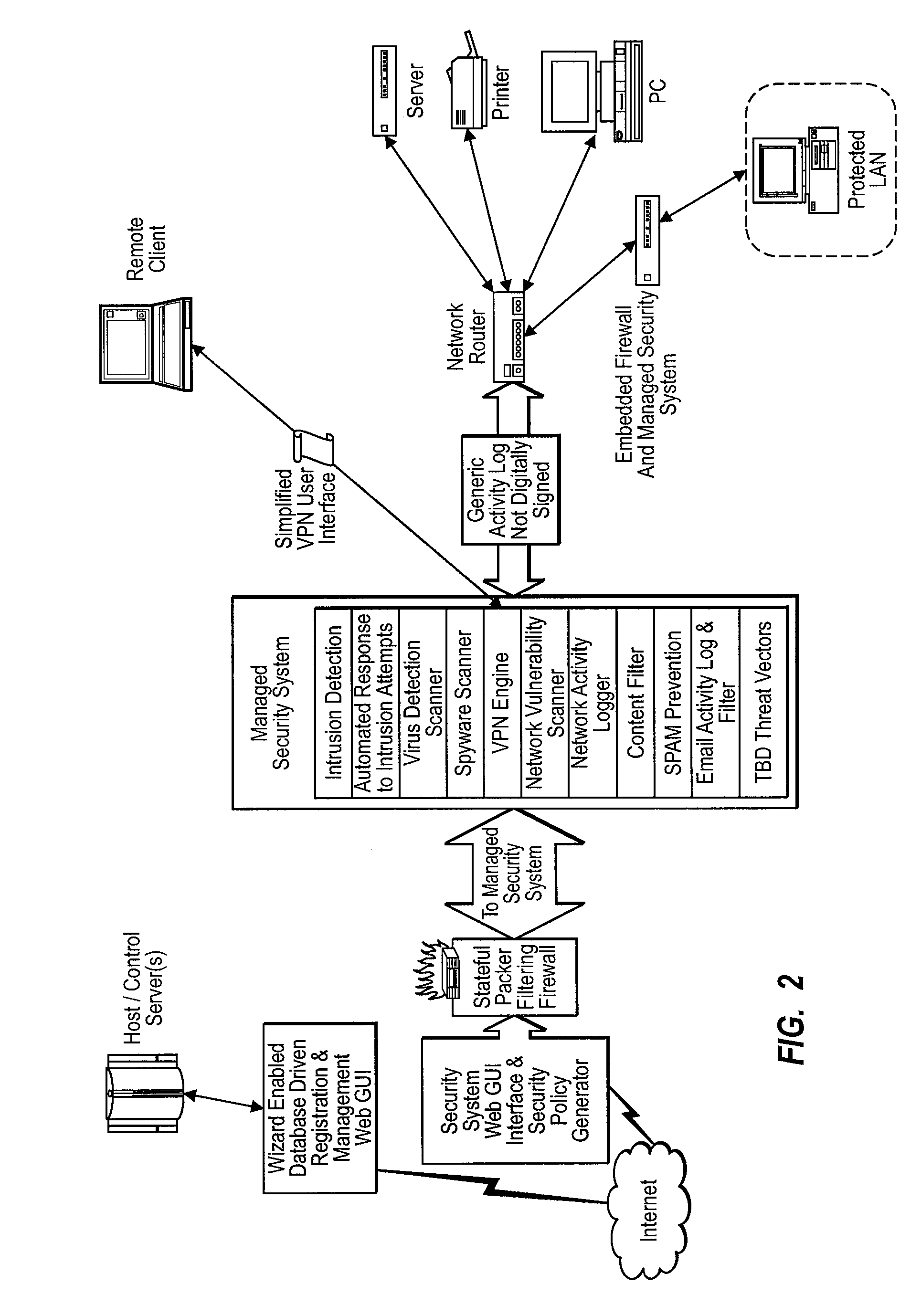
Methods and Systems for Comprehensive Management of Internet and Computer Network Security Threats
InactiveUS20070220602A1Reduce complexityAvoid lostMemory loss protectionError detection/correctionPrivate networkSpamming
The invention relates to systems and methods for management of internet and computer network security threats comprising: a centralized monitoring service; a security management center, wherein the security management center is engineered with rule based and non-linear adaptive analytics to provide intrusion detection, automated response to intrusion attempts, virus detection scanner, spyware scanner, a virtual private network engine, network vulnerability scanner, network activity logger, content filter, SPAM prevention, email activity log and filter, and TBD threat vectors; a remote client; and a hardware device located at the client, wherein the hardware self boots and automatically initiates a virtual private network session with the hosted monitoring and management center after connection to the internet and electrical power.
Owner:SENTRY TECH GROUP
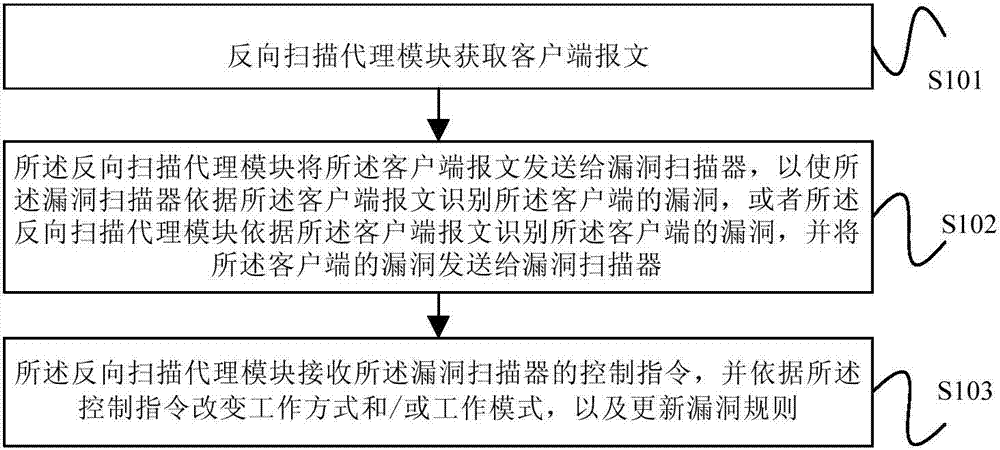
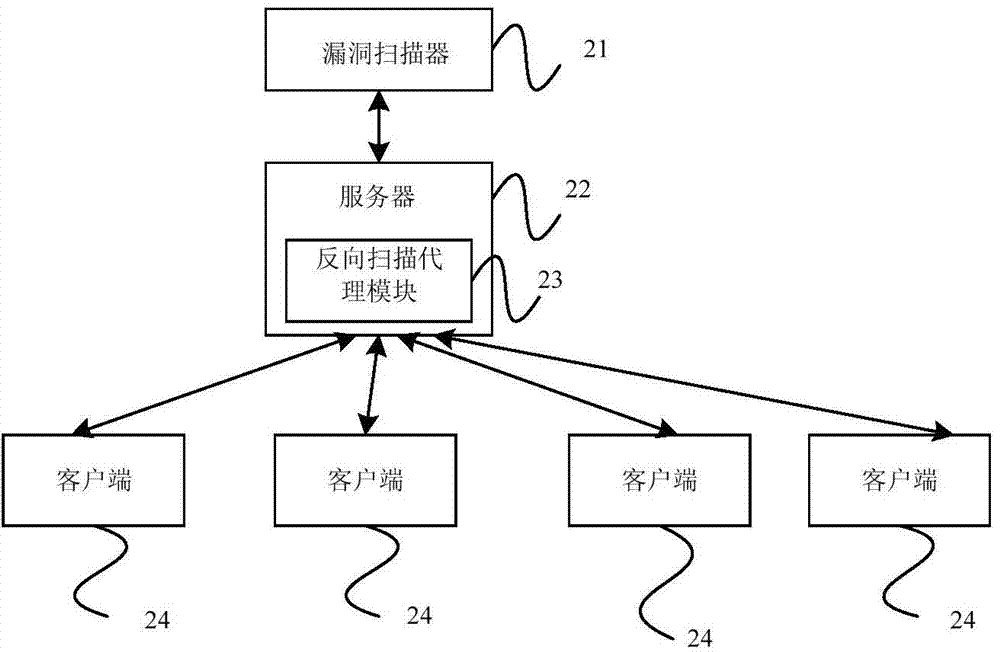
Method and device for scanning vulnerability
ActiveCN104506522AImprove analysisRaise security concernsComputer security arrangementsTransmissionComputer moduleClient-side
The embodiment of the invention provides a method and a device for scanning vulnerability. The method comprises the steps of obtaining a client side message by a reverse scanning agent module; sending the client side message to a vulnerability scanner by the reverse scanning agent module, and enabling the vulnerability scanner to identify vulnerabilities of a client side according to the client side message; or identifying the vulnerabilities of the client side by the reverse scanning agent module according to the client side message, and sending the vulnerabilities of the client side to the vulnerability scanner; receiving a control command of the vulnerability scanner by the reverse scanning agent module, changing a working way and / or a working mode according to the control command, and updating a vulnerability rule. According to the method and the device provided by the embodiment of the invention, the client side message is obtained through the reverse scanning agent module, the client side message is analyzed so as to identify the vulnerabilities existing in the client side, and analysis on a safety problem of the client side is added on the basis of the safety problem of a remote detection server, so the safety detection on the whole network environment is realized.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Vulnerability scanner and plug-in scheduling method thereof
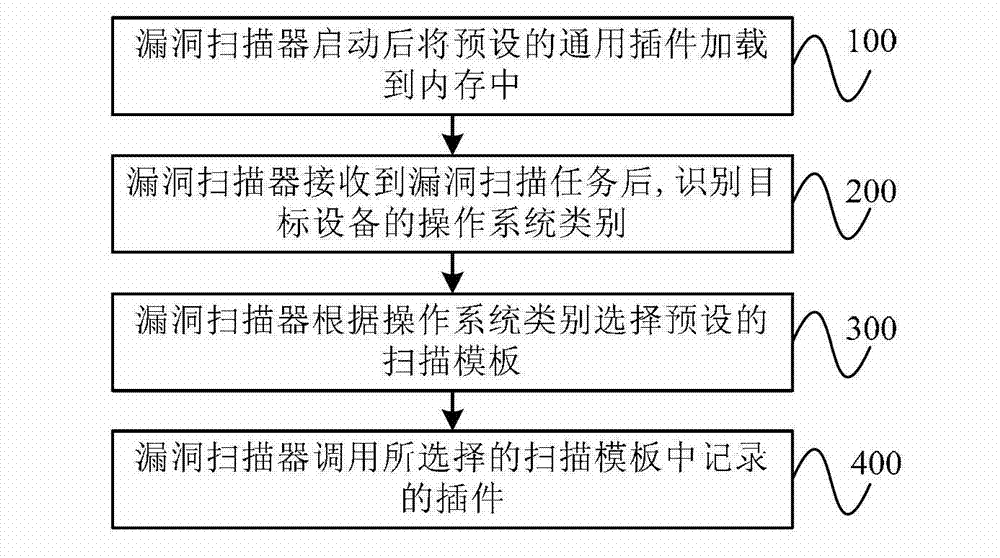
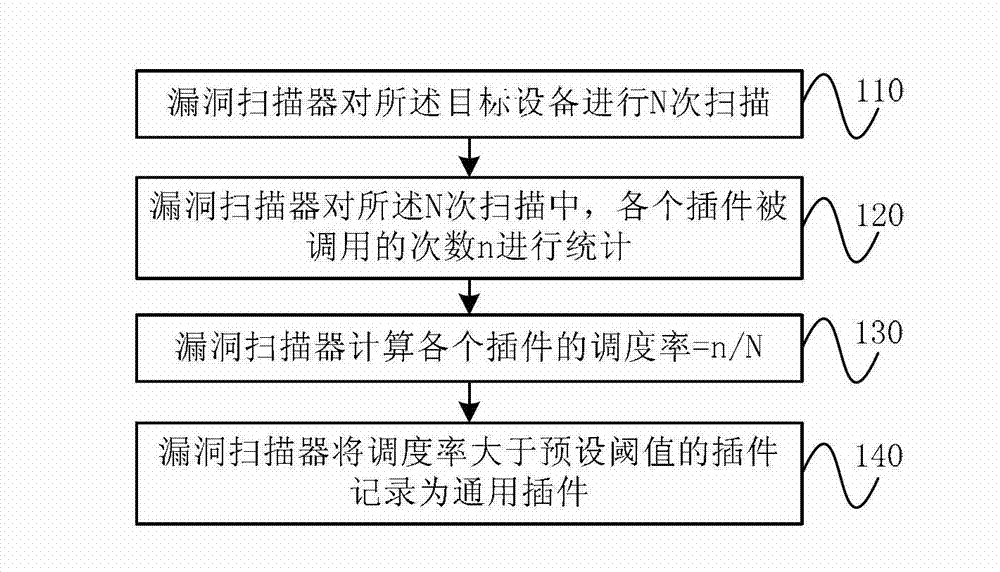
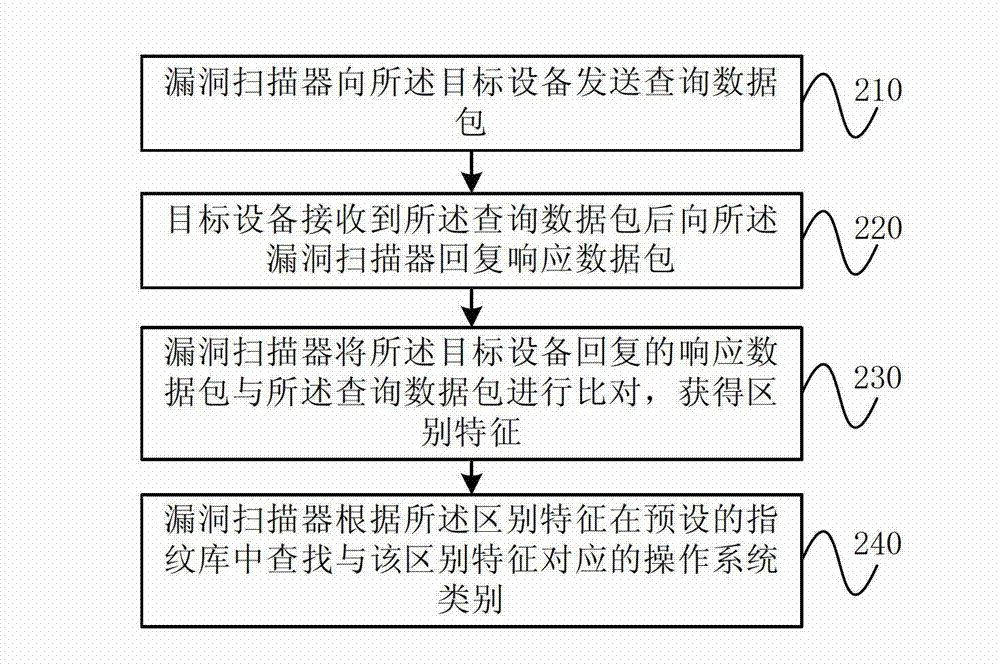
ActiveCN102779252ALow costImprove loading timeComputer security arrangementsInternal memoryOperating system
The invention provides a vulnerability scanner and a plug-in scheduling method thereof. The plug-in scheduling method includes: loading a preset general plug-in into an internal memory after the vulnerability scanner is started up; recognizing the category of an operation system of a target device after receiving the vulnerability scanning task; selecting a preset scanning template according to the category of the operation system; and invoking plugs-in recorded in the selected scanning template. According to the plug-in scheduling method, the general plug-in is invoked first, the category of the operation system of the target device is then recognized, and the corresponding plugs-in are loaded into the internal memory for invoking. Compared with the mode of loading all plugs-in into the internal memory in one time in the prior art, the plug-in scheduling method shortens loading time, accordingly improves scanning speed, reduces requirements for capacity of the internal memory, and accordingly is favorable for reducing hardware cost.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD
Method and device for recognizing malicious system vulnerability scanner
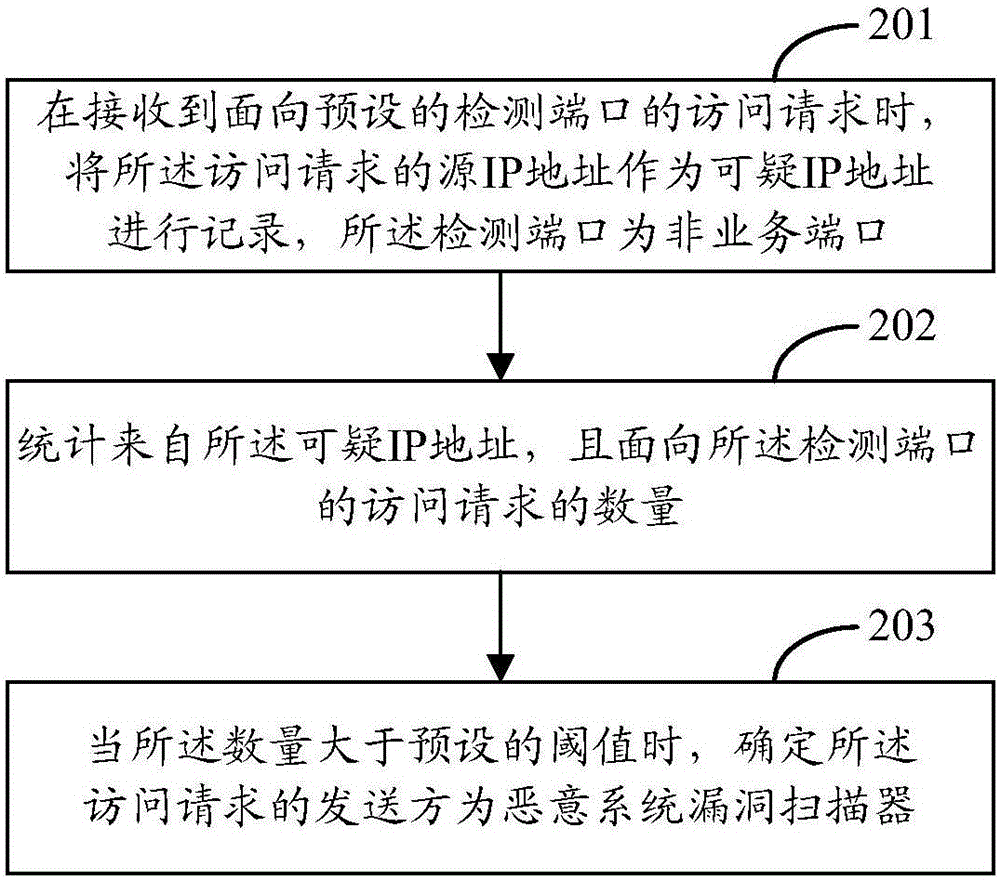
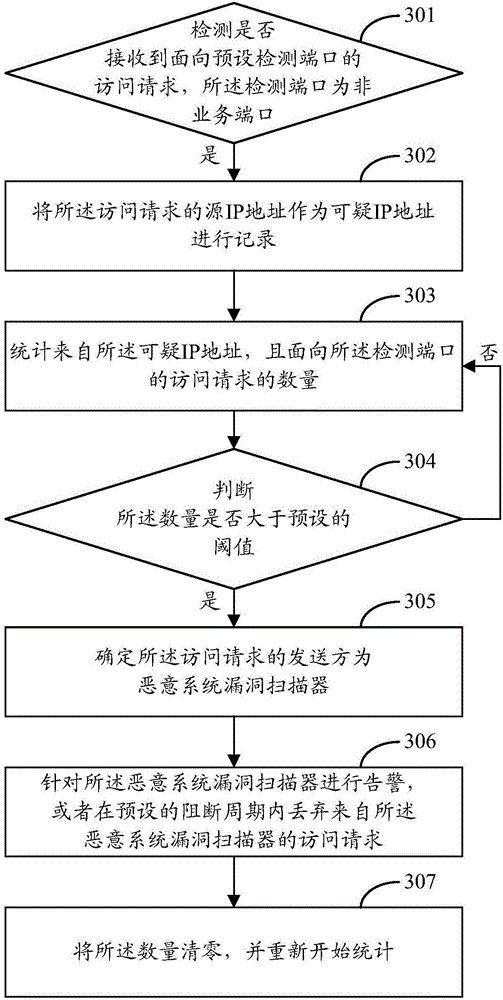
ActiveCN106330944AAccurate identificationImprove accuracyTransmissionIp addressVulnerability scanner
The invention provides a method and device for recognizing a malicious system vulnerability scanner. The method comprises the steps of receiving an access request which is oriented towards a preset detection port, recording a source IP address of the access request as a suspicious IP address, wherein the detection port is a non-service port; counting the number of access requests which are from the suspicious IP address and oriented towards the detection port; and determining a sending party of the access request is a malicious system vulnerability scanner when the number is greater than a preset threshold. The technical scheme provided by the invention can recognize a malicious system vulnerability scanner quickly and accurately.
Owner:杭州迪普信息技术有限公司
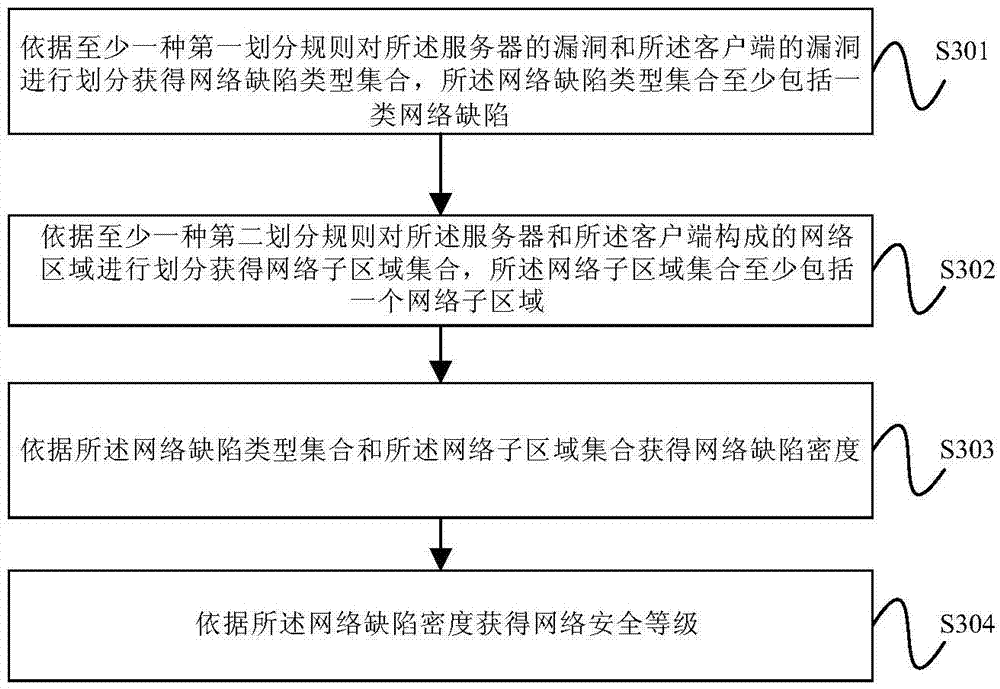
Vulnerability contextualization
An embodiment of the disclosure provides a method for contextualizing vulnerabilities. The method is performed by a server including a processor and a non-transitory computer-readable medium with computer-executable instructions stored thereon, such that when the instructions are executed by the processor, the server performs the method including: (a) importing raw vulnerability data from a vulnerability scanner, the raw vulnerability data including one or more vulnerability data wherein each vulnerability data includes a vulnerability identification (ID) and an asset value; (b) importing an asset inventory from an asset database; (c) merging the asset inventory and the raw vulnerability data to obtain contextual vulnerability data, the contextual vulnerability data including one or more vulnerability data linked to a vulnerability ID, an asset value, and an asset owner; (d) categorizing the contextual vulnerability data; and (e) generating a report of the categorized contextual vulnerability data.
Owner:AETNA
Vulnerability detection method and device
ActiveCN107948120AReduce development costsImprove vulnerability detection efficiencyTransmissionUniform resource locatorComputer science
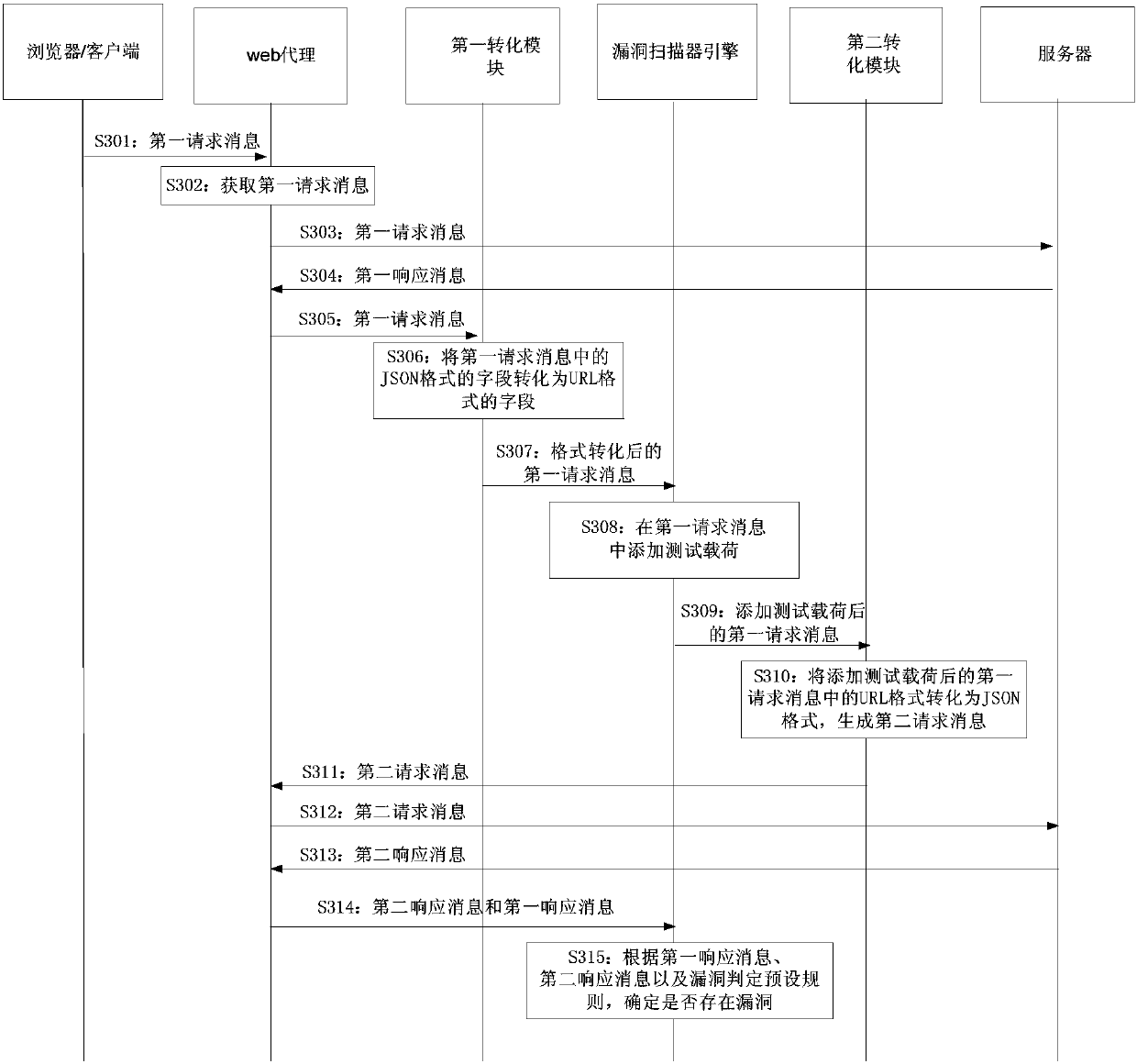
The present application provides a vulnerability detection method and device. According to the vulnerability detection method and device of the invention, a step for converting a field of the JSON format in a first request message to a field of the URL format is added in a vulnerability detection process, and therefore, with an existing URL format-based vulnerability scanner engine unmodified, a test load is added to the field of the URL format, and the test load-added field in the URL format is converted into a field of the JSON format; a second request message is generated and is sent to a server, so that the server can identify the second request message; a second response message which is corresponding to the second request message and returned by the server is directly compared with afirst response message which is returned by the server after a first request message is sent to the server; and a vulnerability detection result is obtained on the basis of vulnerability judgment reset rules in a vulnerability knowledge base; and thus, JSON format-based automatic vulnerability detection is realized, development costs are saved, and vulnerability detection efficiency can be improved.
Owner:ALIBABA GRP HLDG LTD
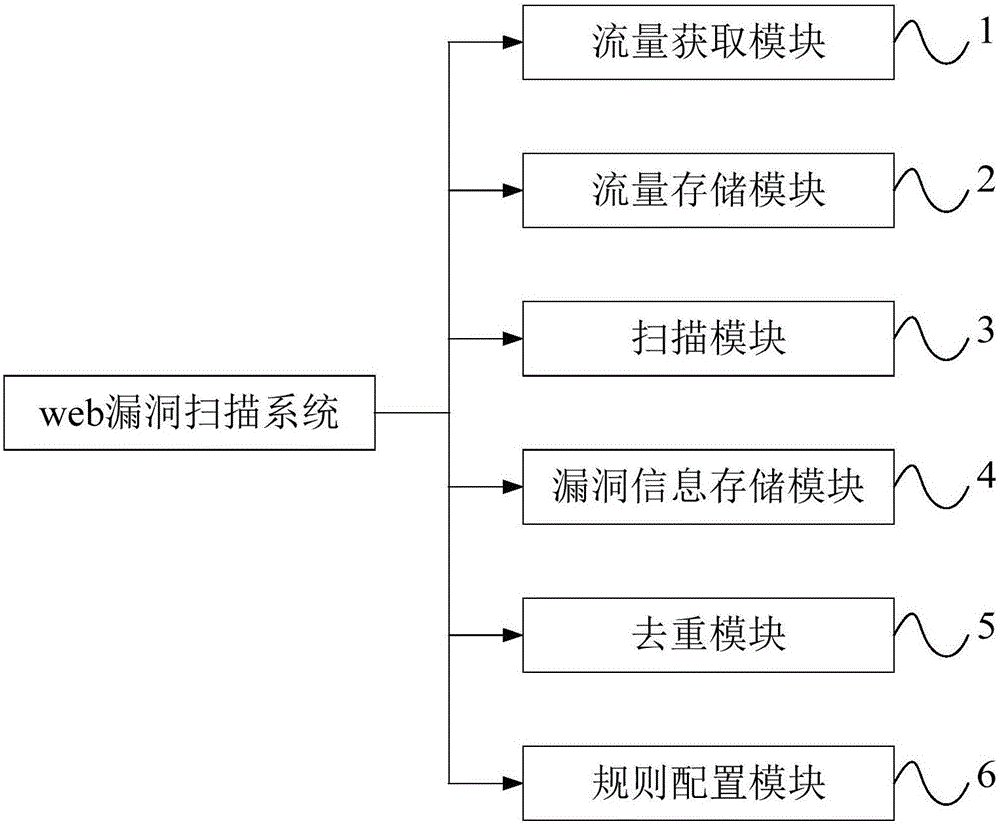
Web vulnerability scanning system
InactiveCN105791273ASolve the problem of low efficiency of crawlersIncrease elasticityData switching networksMessage queueMirror image
The invention discloses a web vulnerability scanning system, comprising a flow acquisition module, used for acquiring web system access flow of a user by a flow mirror image port of a switch; a flow storage module, used for storing the flow in a first message queue; a scanning module, used for scanning the flow according to a scanning rule; and a vulnerability information storage module, used for storing vulnerability information scanned by the scanning module. According to the web vulnerability scanning system disclosed by the invention, the flow is acquired by the switch in a bypass mode, the problem of low crawler efficiency of a traditional web vulnerability scanner is solved, an effective user cookie can be loaded to simulate a real request of a user, meanwhile, the distributed scanning mechanism of the web vulnerability scanning system disclosed by the invention improves the elasticity of the scanning system, and moreover, the web vulnerability scanning system improves the scanning logic to a rule level, so the flexibility of the scanning system is improved.
Owner:SHANGHAI CTRIP COMMERCE CO LTD
Vulnerability scanning method and vulnerability scanning device
InactiveCN107392031AAlleviate technical problems with high labor costsPlatform integrity maintainanceTransmissionTerminal equipmentOperating system
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Vulnerability scanner and plug-in scheduling method thereof
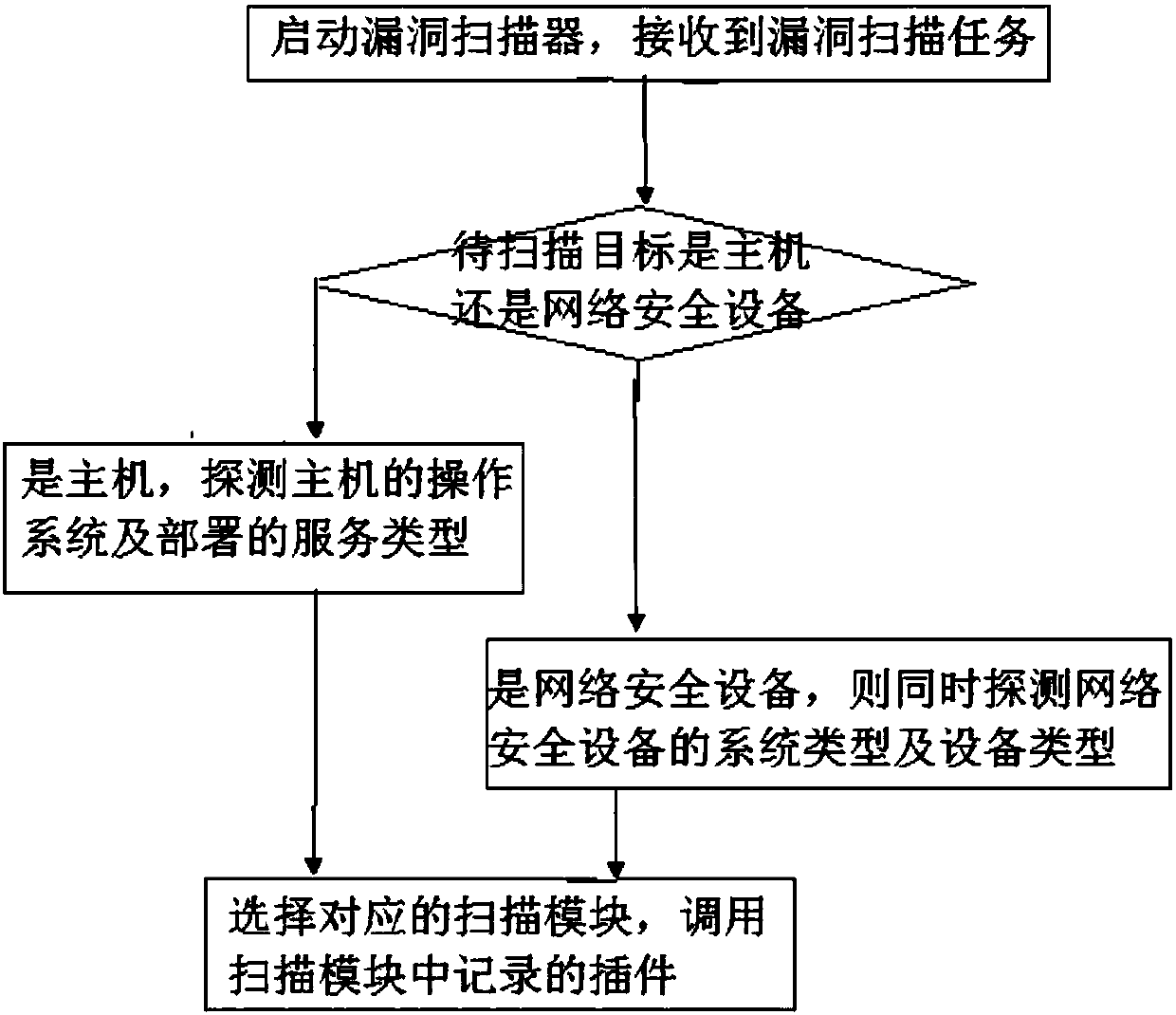
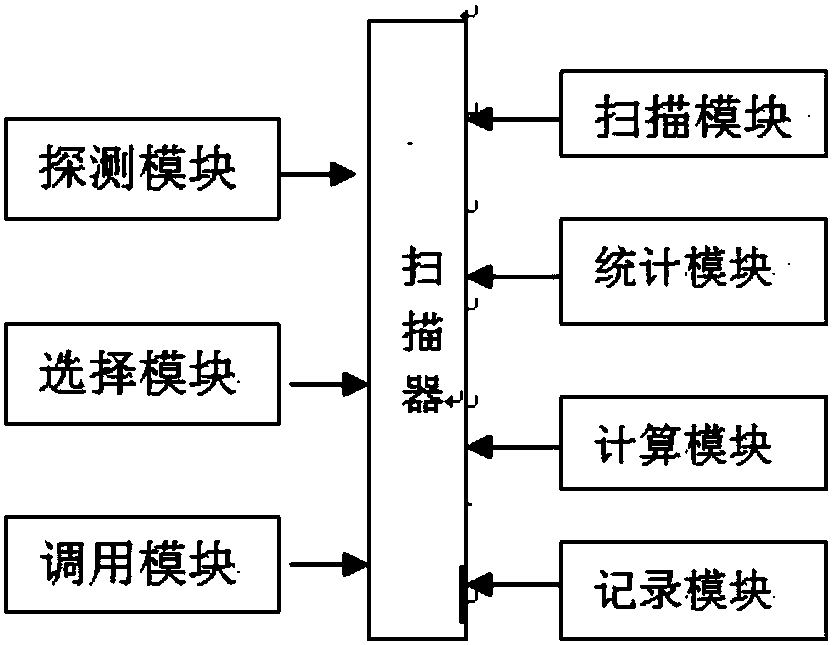
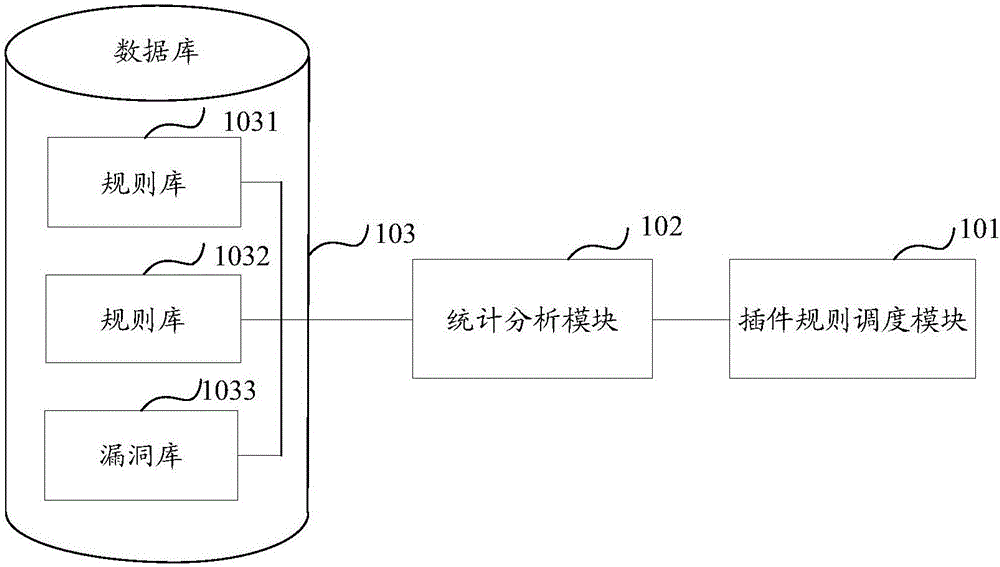
InactiveCN107944276ASave memory spaceFast scanningResource allocationPlatform integrity maintainanceOperational systemTerm memory
The invention belongs to the field of network security, in particular to a vulnerability scanner and a plug-in scheduling method thereof. The method comprises the following steps that: starting the vulnerability scanner, and identifying whether a target to be scanned is a host or network security equipment after a vulnerability scanning task is received; if the target to be scanned is the host, detecting the operating system of the host and a deployed service type, and selecting a preset scanning module according to the operating system and the service type; and if the target to be scanned isthe network security equipment, detecting the system type and the equipment type of the network security equipment, selecting a preset scanning module, and calling a plug-in recorded in the selected scanning module. The invention also discloses a scanner. On the basis of the above operating system type of the host, the service type or the operating system type and the equipment type of the networkequipment, the corresponding plug-in module can be selected and called, then, the corresponding plug-in is loaded into memory, and finally, the plug-in in the memory is read to be executed. Therefore, memory space is saved, and scanning speed is quickened.
Owner:西安交大捷普网络科技有限公司
Method and device for scanning plug-in and determining rule scheduling sequence in plug-in
ActiveCN106685954ASolve the slow scanning speedImprove scanning efficiencyPlatform integrity maintainanceTransmissionComputer resourcesResource consumption
The invention discloses a method and device for scanning a plug-in and determining the rule scheduling sequence in the plug-in. The method includes: during the determining stage of the rule scheduling sequence in the plug-in, determining the resource consumption of each independent rule in rule channels and the hit rate of loophole scanning of the rule channels; determining the scheduling sequence of each rule channel according to the resource consumption and the hit rate; during a scanning stage, sequentially performing loophole scanning according to the scheduling sequence of each rule channel. The method has the advantages that the plug-in is granulated according to the independent rules, the minimum unit of scanning scheduling is granulated into the rule channels, the reasonable rule channel scheduling sequence is determined automatically, plug-in scanning speed and efficiency are increased, computer resources are saved at the same time, and the overall scanning performance of a loophole scanner is increased.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
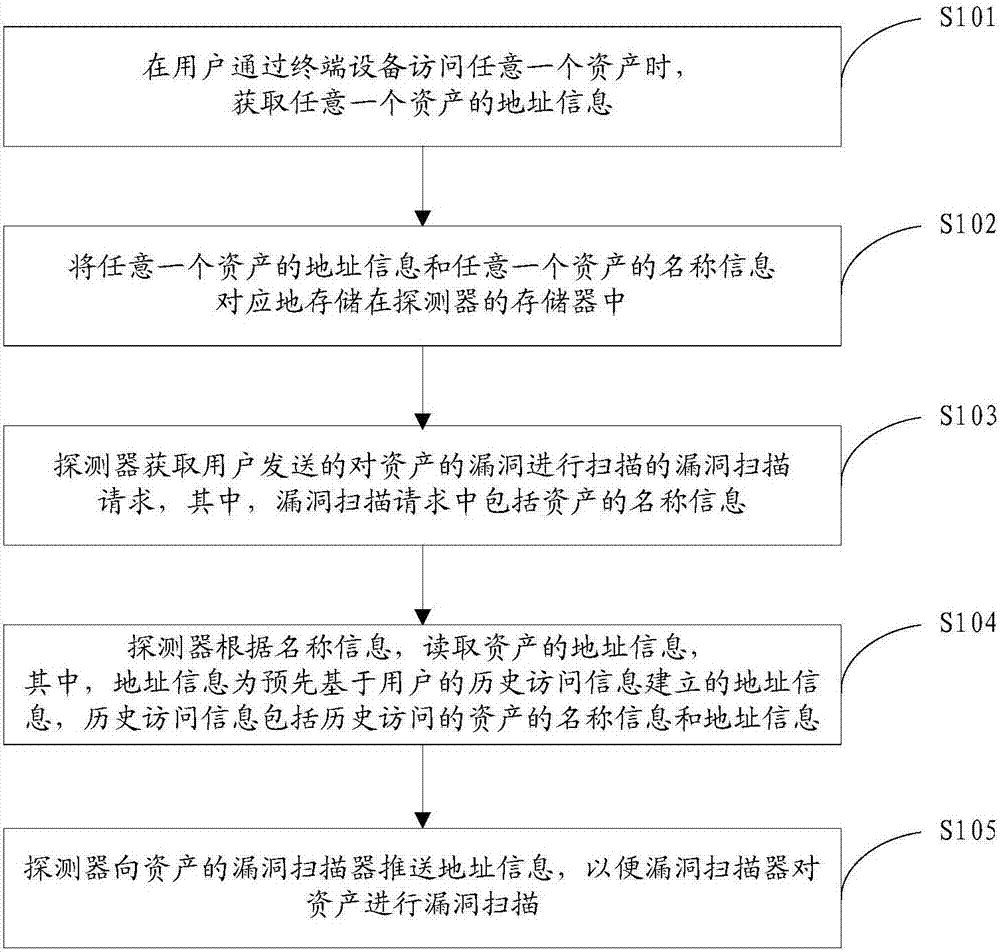
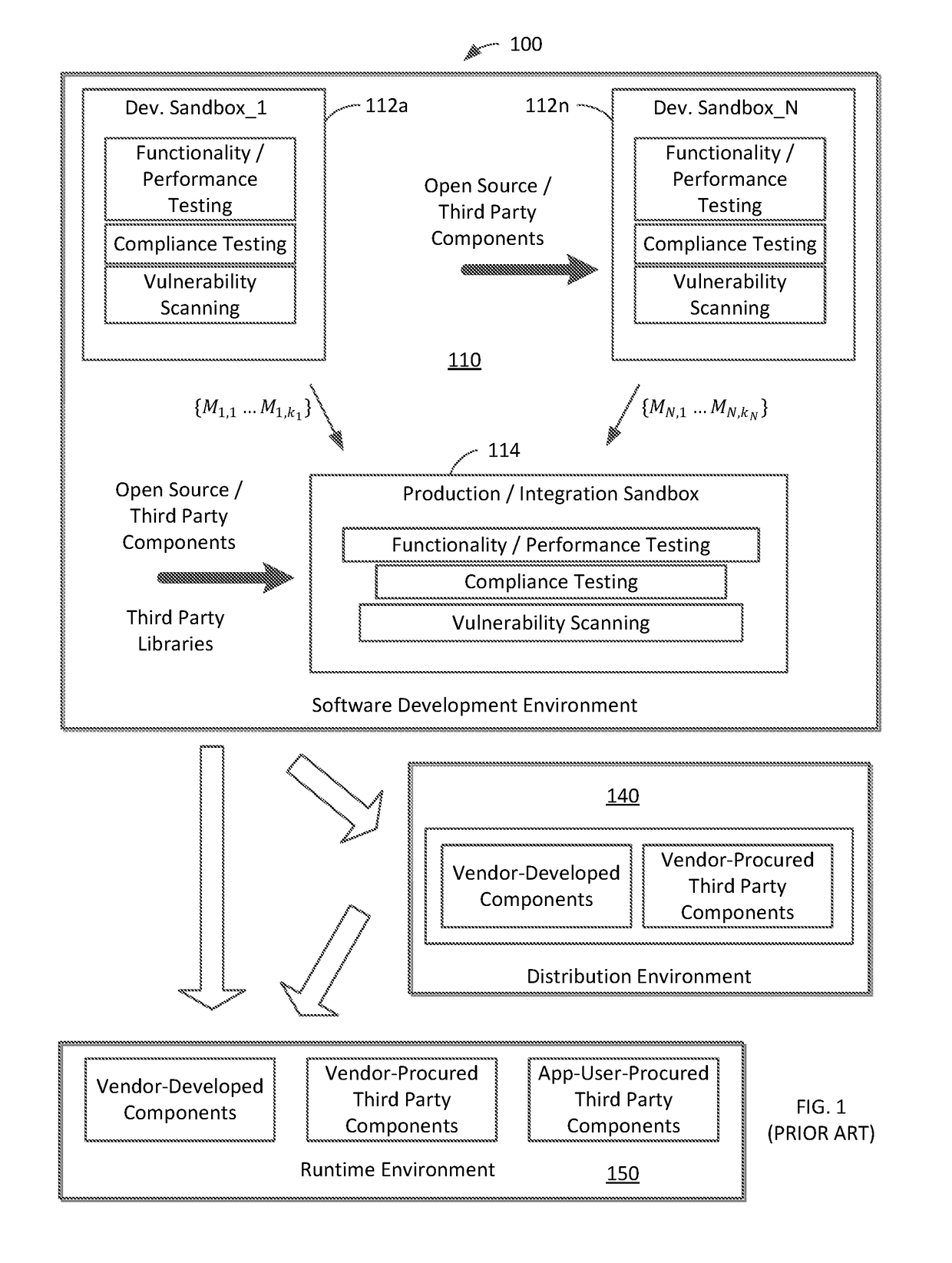
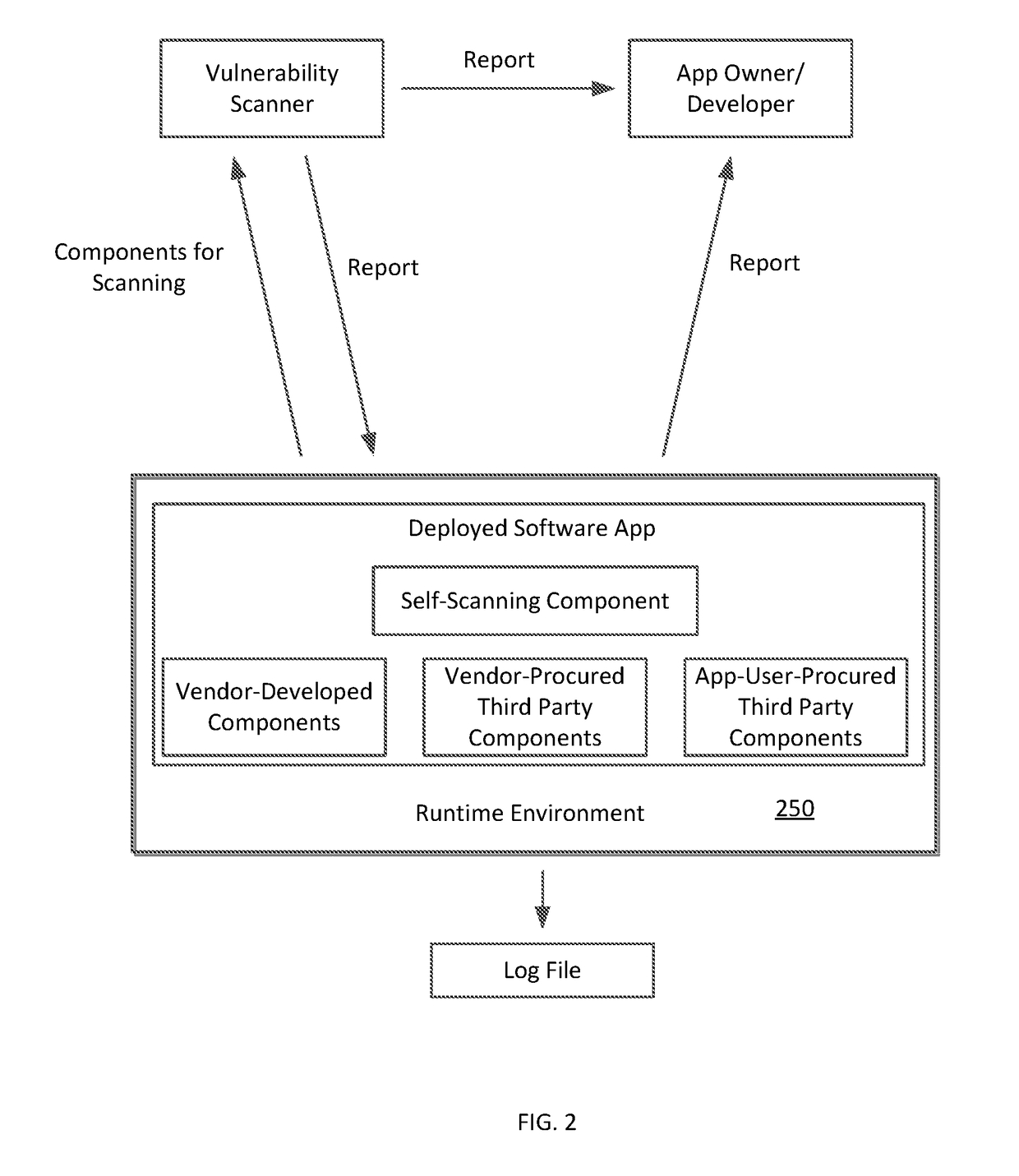
Systems and methods facilitating self-scanning of deployed software applications
ActiveUS20180349611A1Easy to analyzePlatform integrity maintainanceTransmissionPartial applicationMultiple criteria
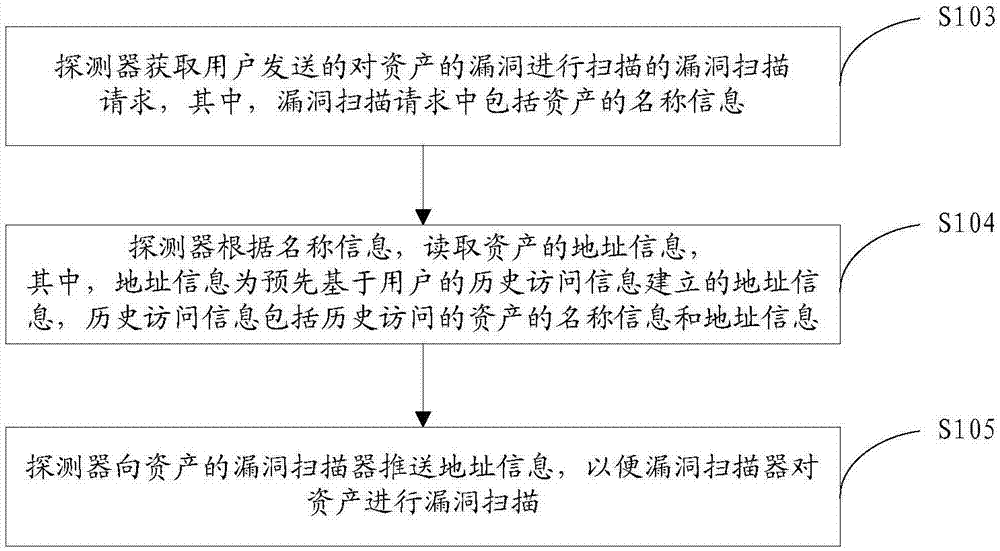
In a system for facilitating detection of vulnerabilities in a deployed software application, a software component (also called a self-scanning component) is provided for integration with the software application. The self-scanning component is configured to detect one or more conditions associated with the deployment of the software application and, upon the detection of such condition(s), to collect and / or transmit at least a portion of the application code to a vulnerability scanner. The self-scanning component can receive a vulnerability report from the scanner and can present the report as received or an analysis of the report. The presentation can be a display or inclusion of the report or analysis thereof in a log generated by the software application.
Owner:VERACODE
Web vulnerability scanning method, system and device, storage medium and computer equipment
PendingCN112182587AGood effectWeb data indexingPlatform integrity maintainanceData packWeb application
The invention provides a Web vulnerability scanning method which comprises the following steps: constructing a data packet through a URL crawled by a web crawler, sending the data packet to a plug-in,and performing vulnerability scanning based on the plug-in; sending a request to a Web application server, and obtaining response information to the server; analyzing the response information, and judging whether the vulnerability exists in the server or not to obtain potential safety hazard information; and generating a report file according to the potential safety hazard information; the overall architecture of the Web vulnerability scanner is divided into a main body module and a scanning plug-in module; wherein the main body module is used for information collection work in a penetrationtechnology, and the scanning plug-in module is used for detecting different Web vulnerabilities, so that a Web application vulnerability scanner can detect common Web vulnerabilities, and certain helpcan be brought to testers in penetration work.
Owner:CENT SOUTH UNIV
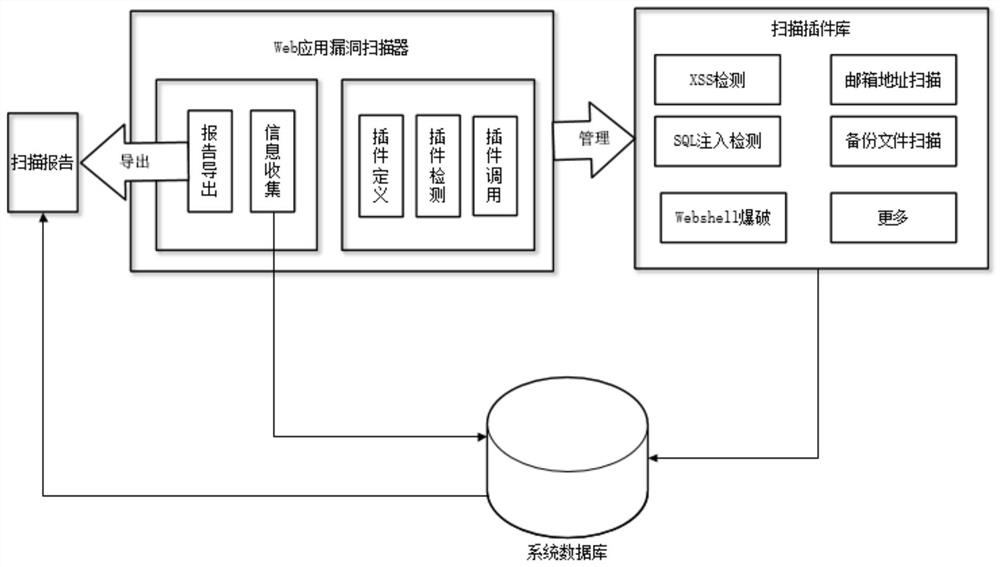
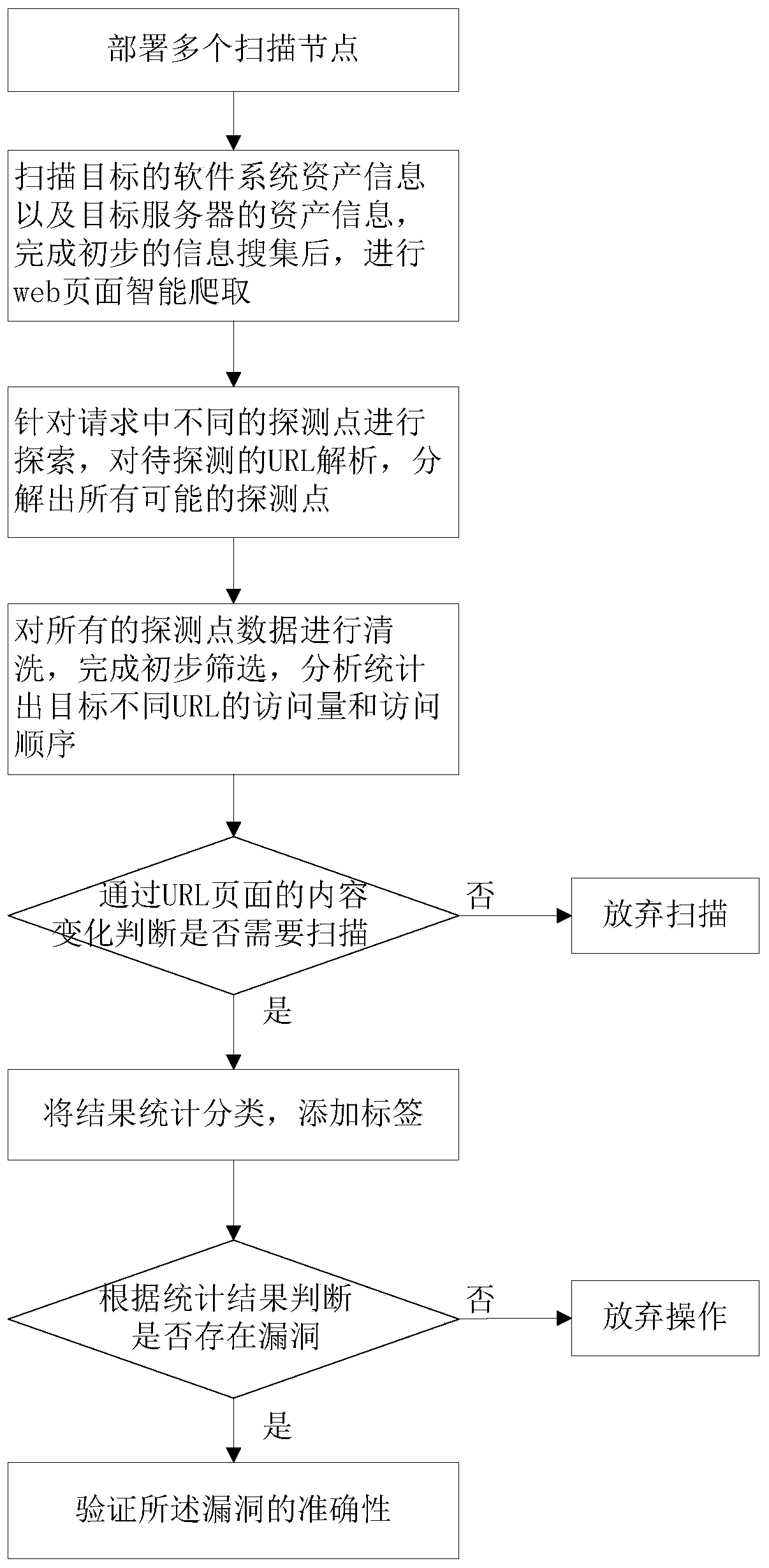
Web vulnerability scanning method and vulnerability scanner
The invention relates to a web vulnerability scanning method and a vulnerability scanner. The web vulnerability scanning method comprises the following steps: deploying a plurality of scanning nodes;scanning the asset information of the target software system and the asset information of the target server, and carrying out web page intelligent crawling after completing preliminary information collection; after crawling is completed, exploring different detection points in the request, analyzing the URL to be detected, and decomposing to obtain all possible detection points; cleaning all the detection point data, completing preliminary screening, analyzing and counting to obtain the page view and the access sequence of different URLs of the target, judging whether scanning is needed or notaccording to the content change of URL pages, if scanning is needed, performing statistical classification on results, adding labels, and otherwise, giving up scanning; and judging whether a vulnerability exists or not according to a statistical result, verifying the accuracy of the vulnerability if the vulnerability exists, and otherwise, giving up the operation. The method is beneficial to improving the efficiency and verifying the accuracy of the vulnerability.
Owner:江苏亨通工控安全研究院有限公司
Anti-scan detection method and system based on various URL changes
InactiveCN106485143AImprove reliabilityPlatform integrity maintainanceTransmissionObfuscationWeb application
The present invention proposes an anti-scan detection method and system based on various URL changes. The method comprises: acquiring an original code accessed by a user through a Web application request; when it is detected that the user accesses the original code for the first time, modifying a real URL address and an access topic in the original code according to a fault URL obfuscation algorithm; and when it is detected that the user accesses the original code for the second time or for many times, continuing to modify the real URL address and the access topic in the original code according to the fault URL obfuscation algorithm, so that a vulnerability scanner cannot obtain the real URL address, and then cannot obtain the web page, wherein results of modifying the real URL address and the access topic for each time are different. According to the method and system proposed by the present invention, a crawler module, the core module of the scanner is disturbed, the detection mechanism of the vulnerability scanning is avoided, and the scanning problem is completely eliminated, so that the current scanner is invalid, and the security of the target system is ensured as much as possible.
Owner:WEBRAY TECH BEIJING CO LTD
Physical and network security system and methods
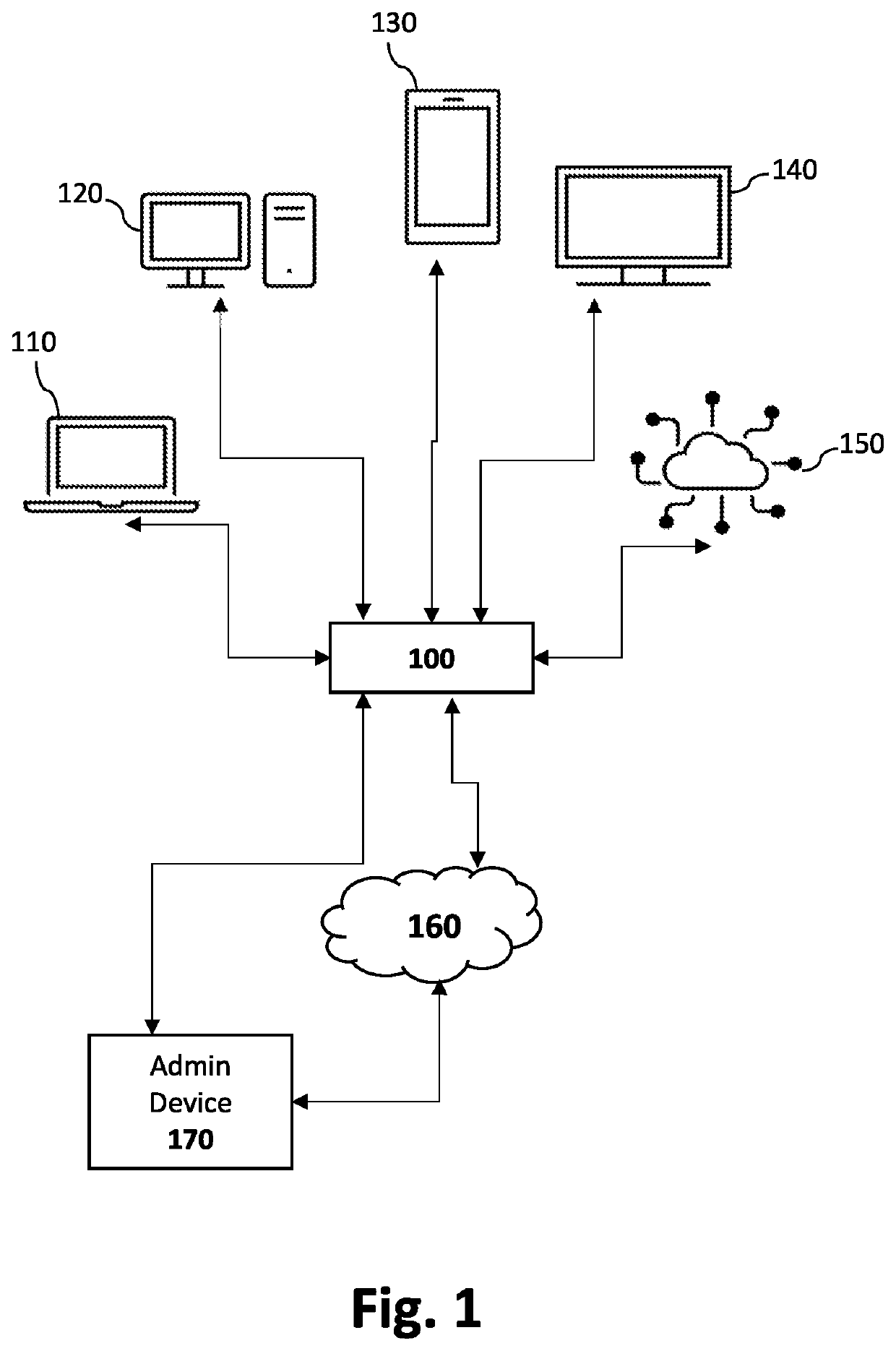
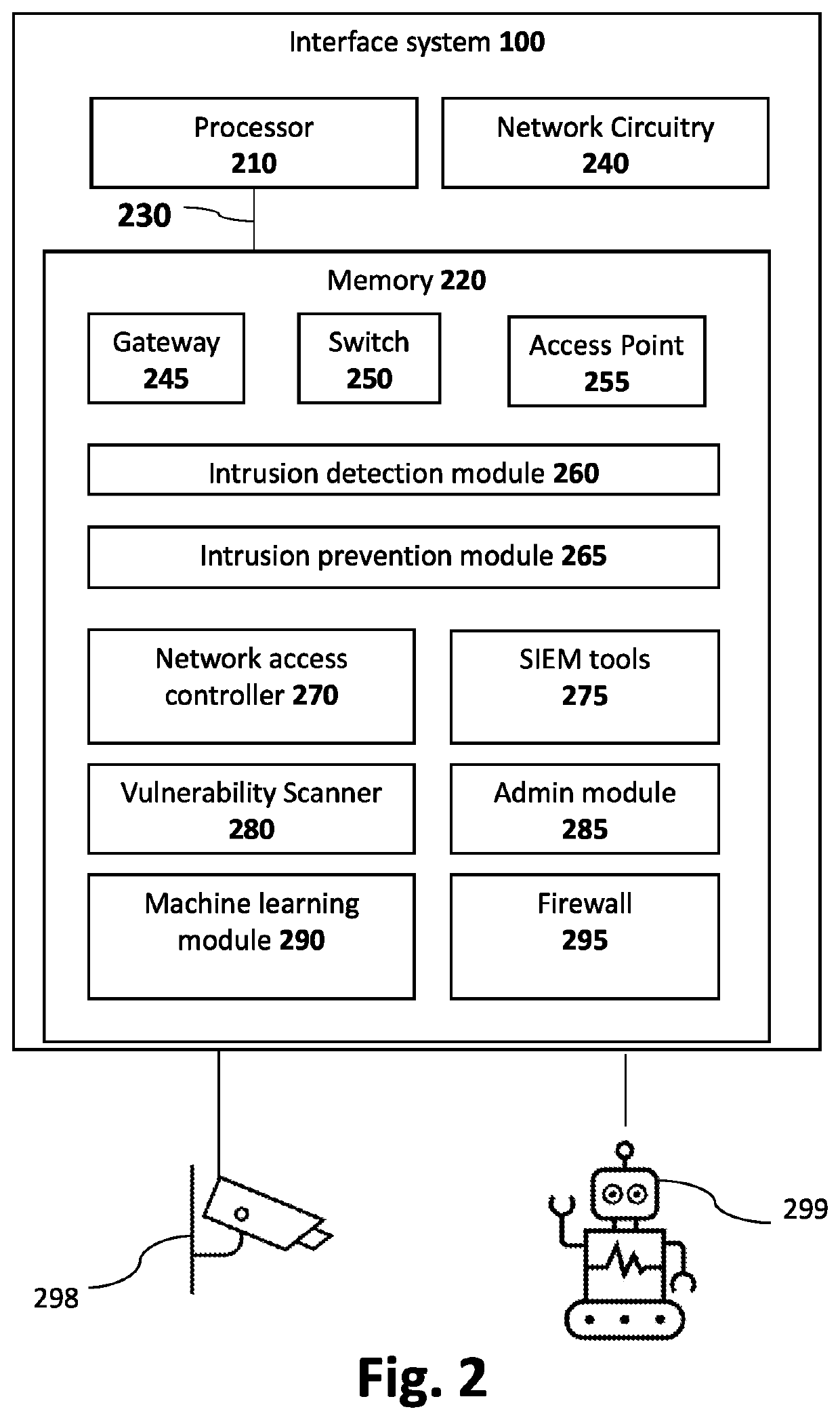
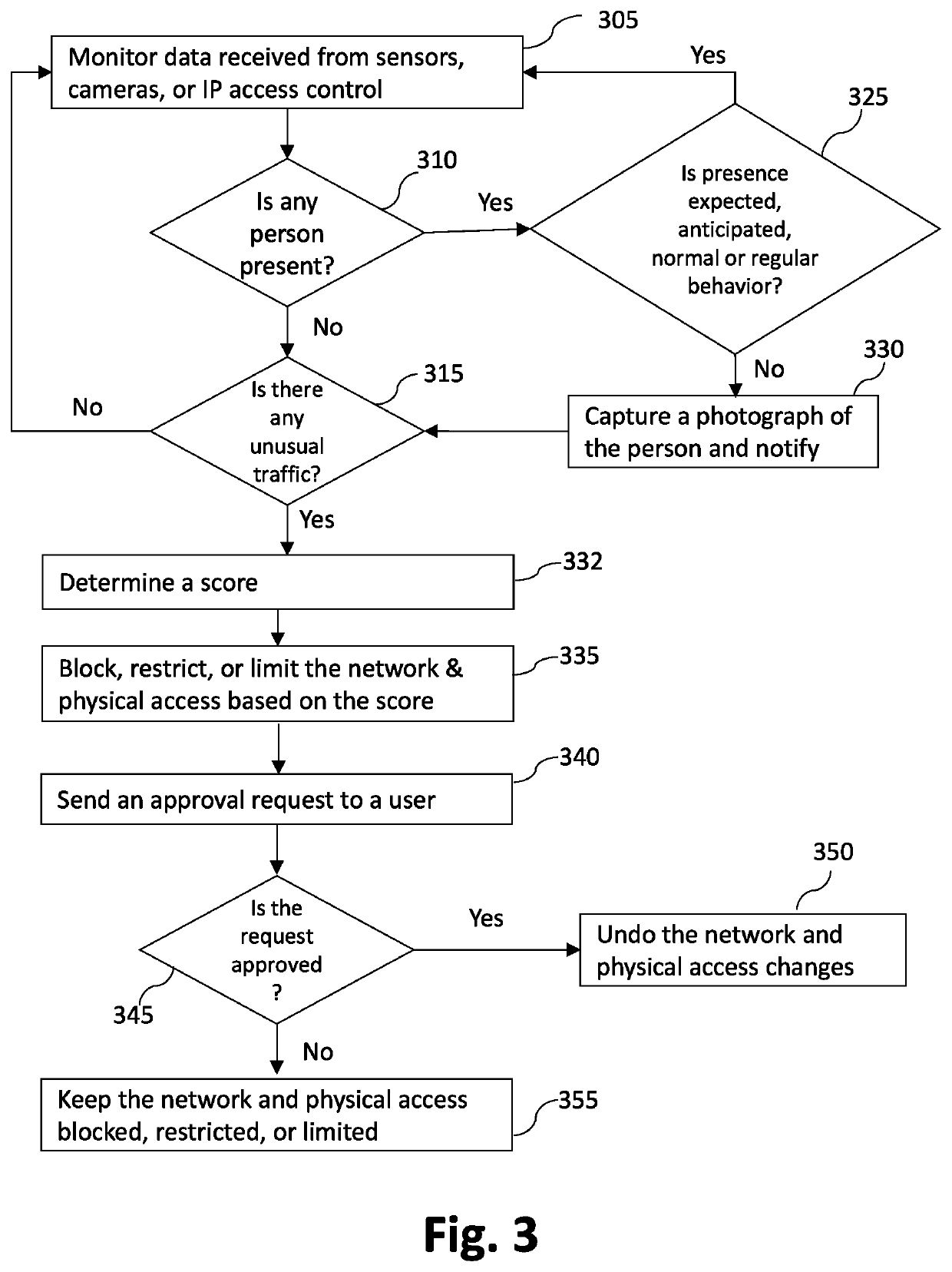
ActiveUS20220141239A1Internal/peripheral component protectionSecuring communicationNetwork onEngineering
An interface system for securing devices on a network gaining access to an external wide area network, such as Internet. The interface system includes a gateway, a vulnerability scanner, switch, cameras, network access controller, and machine learning module. The interface system detects any unusual activity from a device on the network and can take autonomous decisions based on calculated scores to allow or block the unusual activity.
Owner:ZAMAN ASNA SUHAIL +1
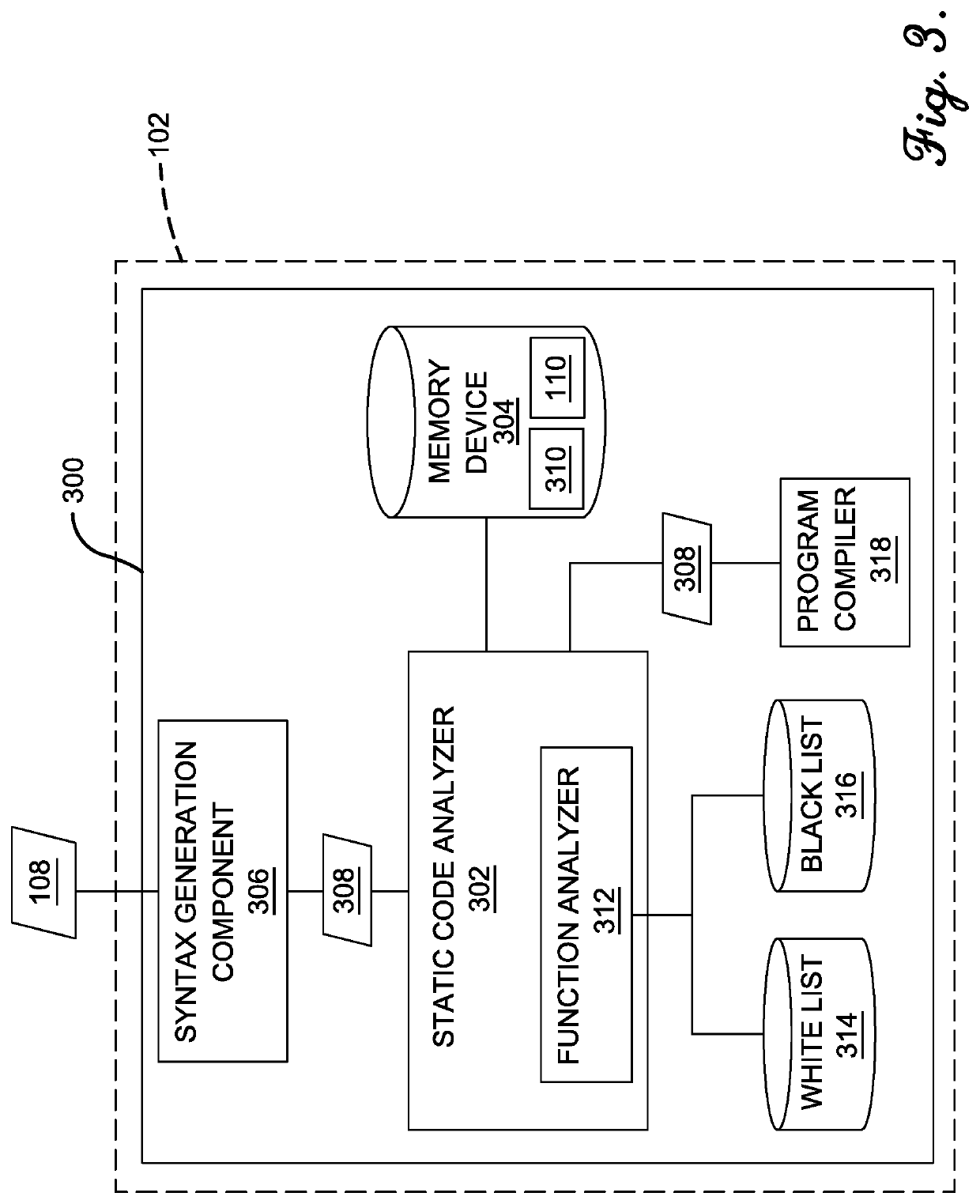
Functional language source code vulnerability scanner
A code scanning system has a syntax generation component that receives source code and generates an abstract syntax tree file. The system includes a white list of permitted pure functions, and a black list of prohibited impure functions. In addition, the system includes a static code analyzer for performing static analysis of the source code. The static code analyzer includes a function analyzer that receives the AST file and identifies the functions. Each function is compared to the white list, and if it is present, marked as permitted in a static analysis file. If the function is not on the white list, it is compared to the black list. If it is present on the black list, it is marked as prohibited in the static analysis file. If the function is not on the white or black list, it is marked as “unknown” and subjected to manual analysis.
Owner:STATE FARM MUTUAL AUTOMOBILE INSURANCE
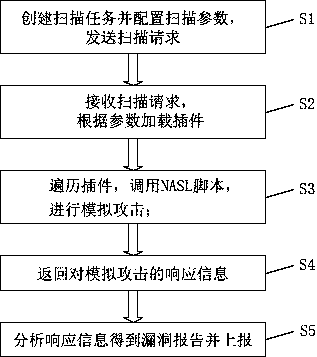
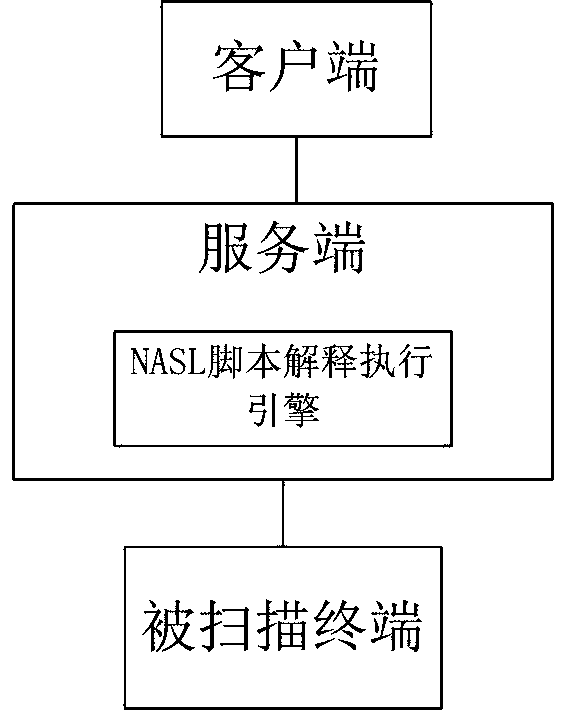
Vulnerability scanning method and system based on plug-in technology
InactiveCN110263542ADiscovered in timeEasy to callPlatform integrity maintainanceProgram loading/initiatingComputerized systemTest object
The invention aims to provide a vulnerability scanning method and system based on a plug-in technology. When the vulnerability scanner starts to work; reading plug-in numbers, calling an NASL script engine and transmitting corresponding data parameters; and then loading, explaining and executing scripts to test and check an actual computer system or network, analyzing a return result of the tested object to detect whether a vulnerability which can be used by attacks exists in the system or network, and outputting or storing the detected vulnerability information of the object. On the basis of the plug-in technology and the NASL script engine, the NASL script can be called better and faster, then the target host is subjected to simulated attack, and then vulnerabilities are found in time.
Owner:西安交大捷普网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com