Web vulnerability scanning system
A vulnerability scanning and vulnerability technology, applied in the field of web vulnerability scanning systems, can solve problems such as difficulty in meeting the vulnerability scanning requirements of large-scale web systems, and achieve the effects of solving the inefficiency of crawlers, improving elasticity, and improving flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention is further illustrated below by means of examples, but the present invention is not limited to the scope of the examples.
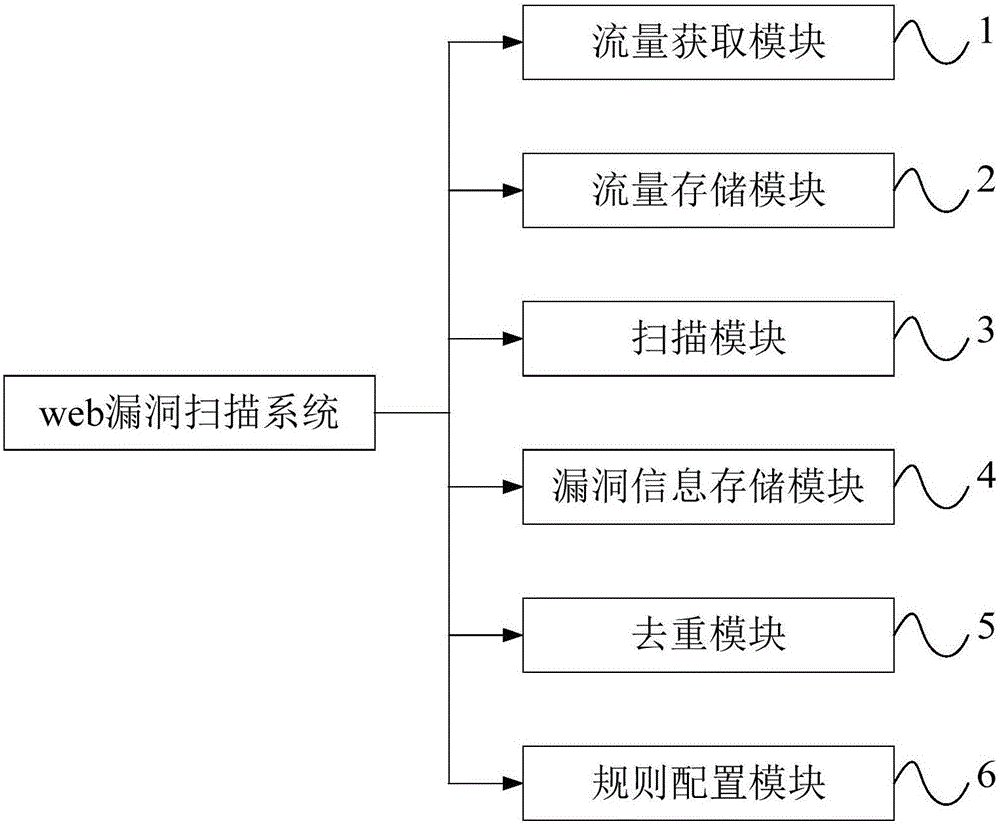
[0024] Such as figure 1 As shown, the web vulnerability scanning system of the present invention includes a traffic acquisition module 1 , a traffic storage module 2 , a scanning module 3 , a vulnerability information storage module 4 , a deduplication module 5 and a rule configuration module 6 .
[0025] Wherein, the traffic acquisition module 1 is used to acquire the traffic of the user accessing the web system through the traffic mirroring port of the switch, so as to obtain the url list of the web system through the bypass mode of the switch, and solve the problem that the scanner in the prior art obtains the web system through a crawler. The problem of low efficiency of the url list of the web system; specifically, in the present invention, the traffic acquisition module 1 can acquire the traffic based on the preset black...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com