Method for realizing loophole scanning
A vulnerability scanning and implementation method technology, applied in the network field, can solve the problems of fixed scanning method, inflexibility, and single vulnerability scanning method, and achieve the effect of convenient operation and accurate testing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] This vulnerability scanning implementation method is applied to the S219 Dongfang.com server security enhancement platform, mainly for simulated attack tests such as vulnerability scanning.
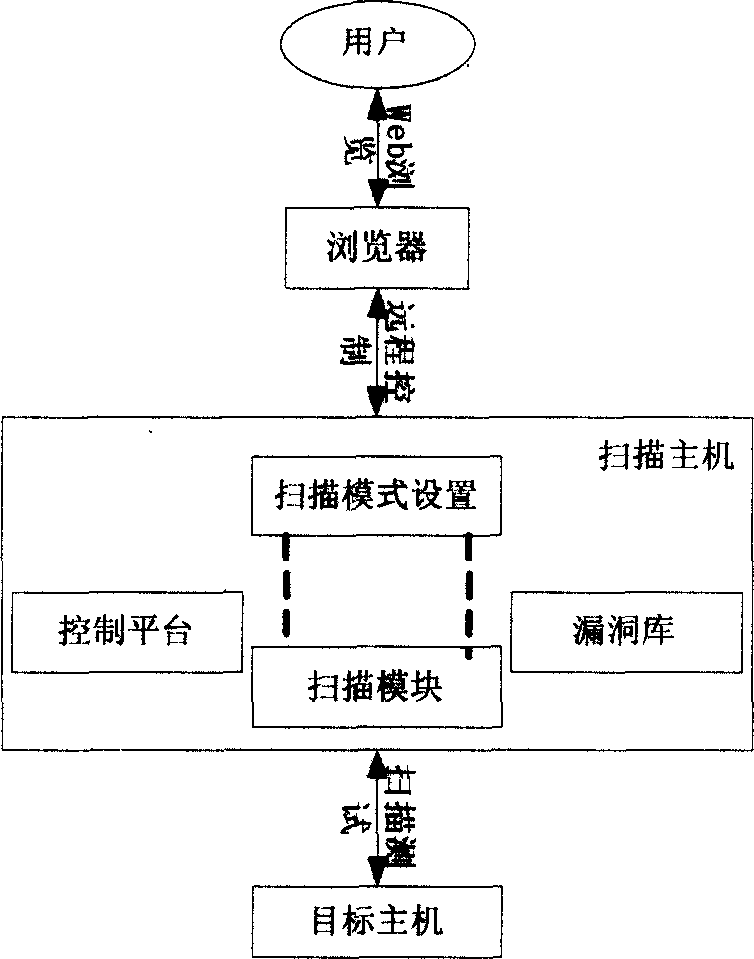
[0032] Vulnerability scanning tests mainly include common Web service vulnerabilities such as HTTP and CGI (Common Gateway Interface) and mail service vulnerabilities such as POP (receiving email) and SMTP. The schematic diagram of the scanning method of the present invention is shown in figure 1 .
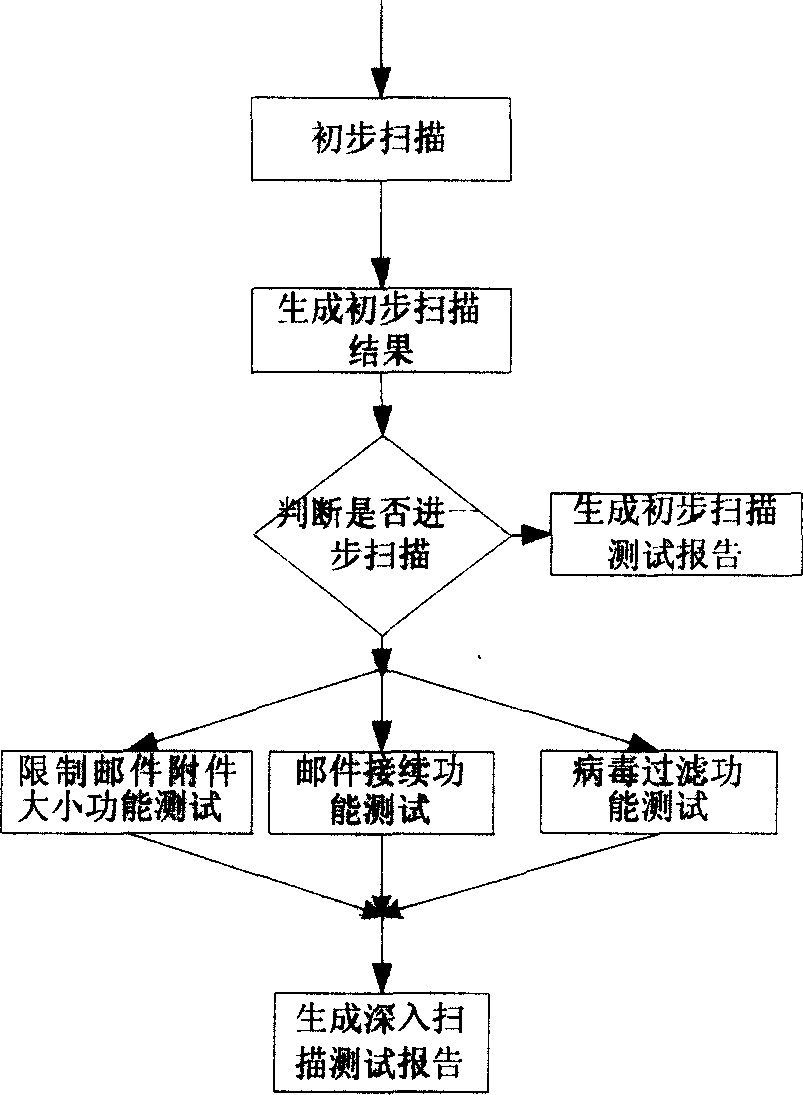
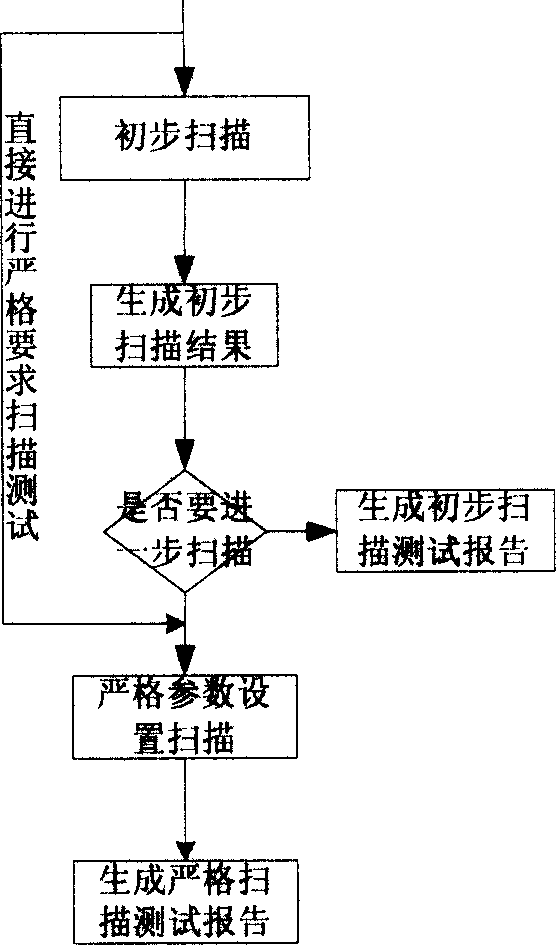
[0033] Such as figure 1 As shown: the user uses a web browser to remotely control the remote scanning host, and through the control platform on the scanning host, the user sets the scanning depth and scanning method (that is, chooses to perform SMTP scanning or HTTP vulnerability scanning of the Web server), and uses The function of the scanning module expands the scanning depth from single scanning to secondary scanning or even deeper scanning; after setting, you can use the vulnera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com