Computer network risk evaluation device and method therefor
A computer network and risk assessment technology, which is applied in the field of computer network risk assessment, can solve problems such as high cost and complicated operation, and achieve the effects of reducing cost, improving protection ability, and simplifying complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
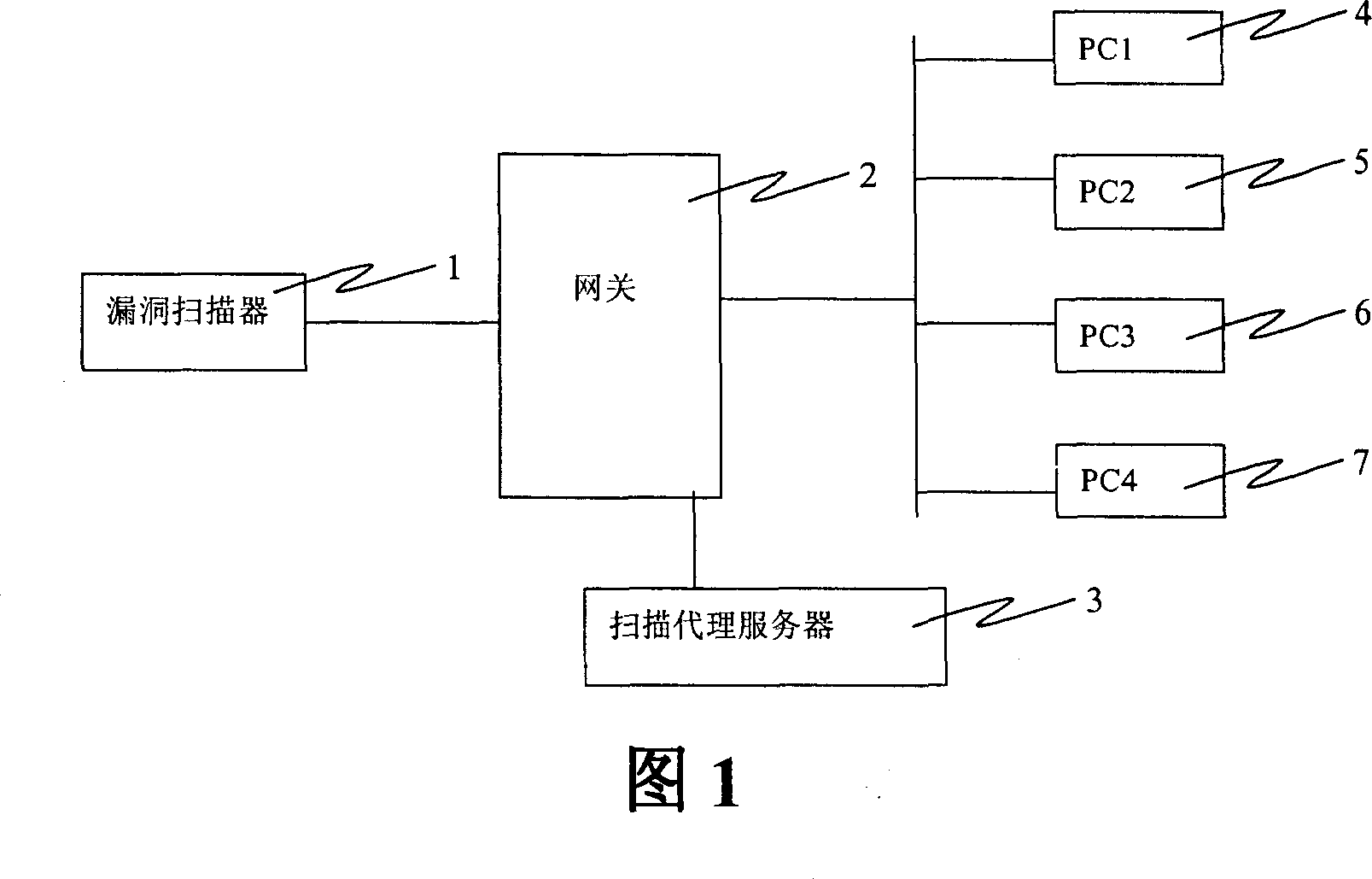
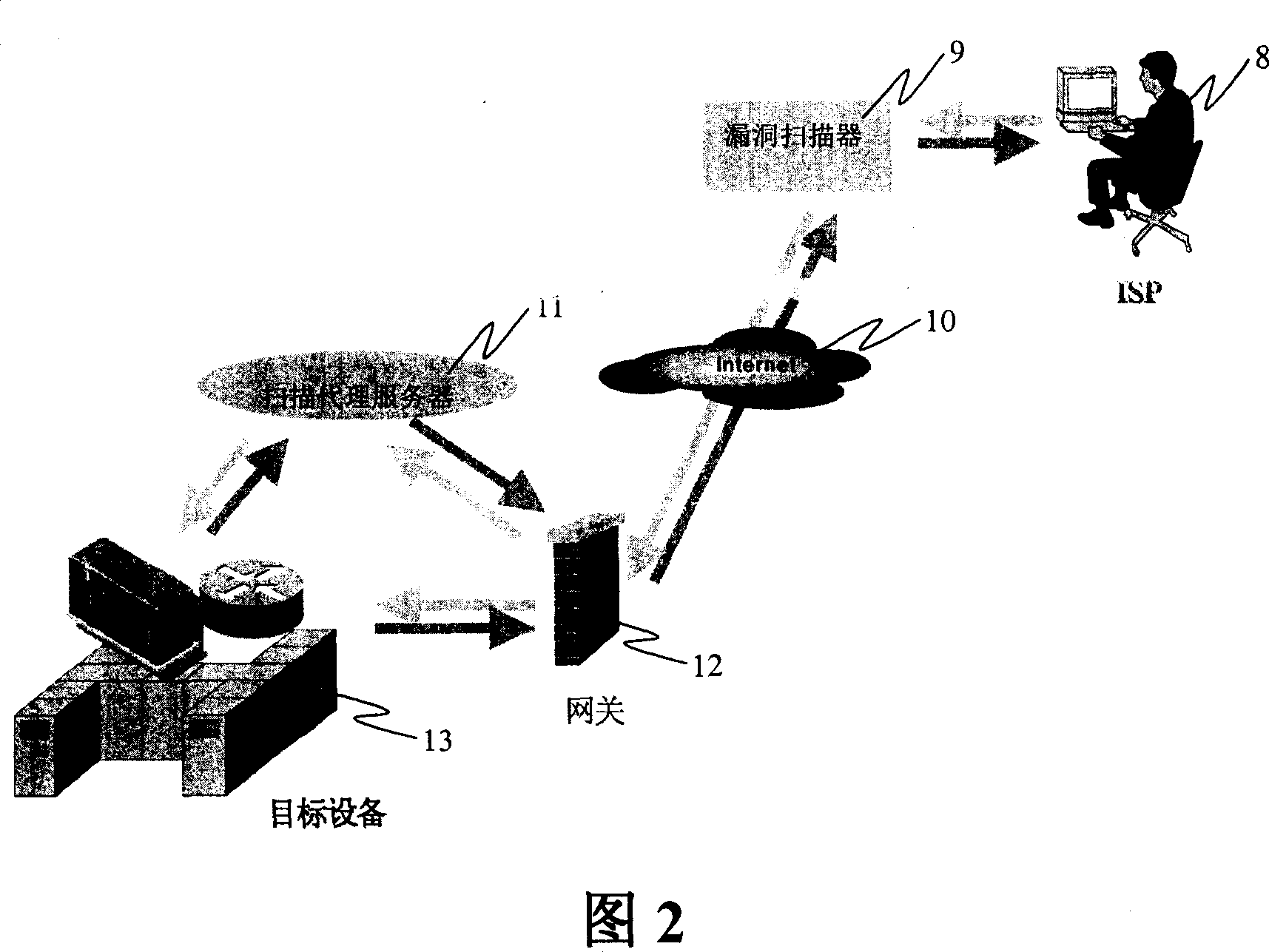
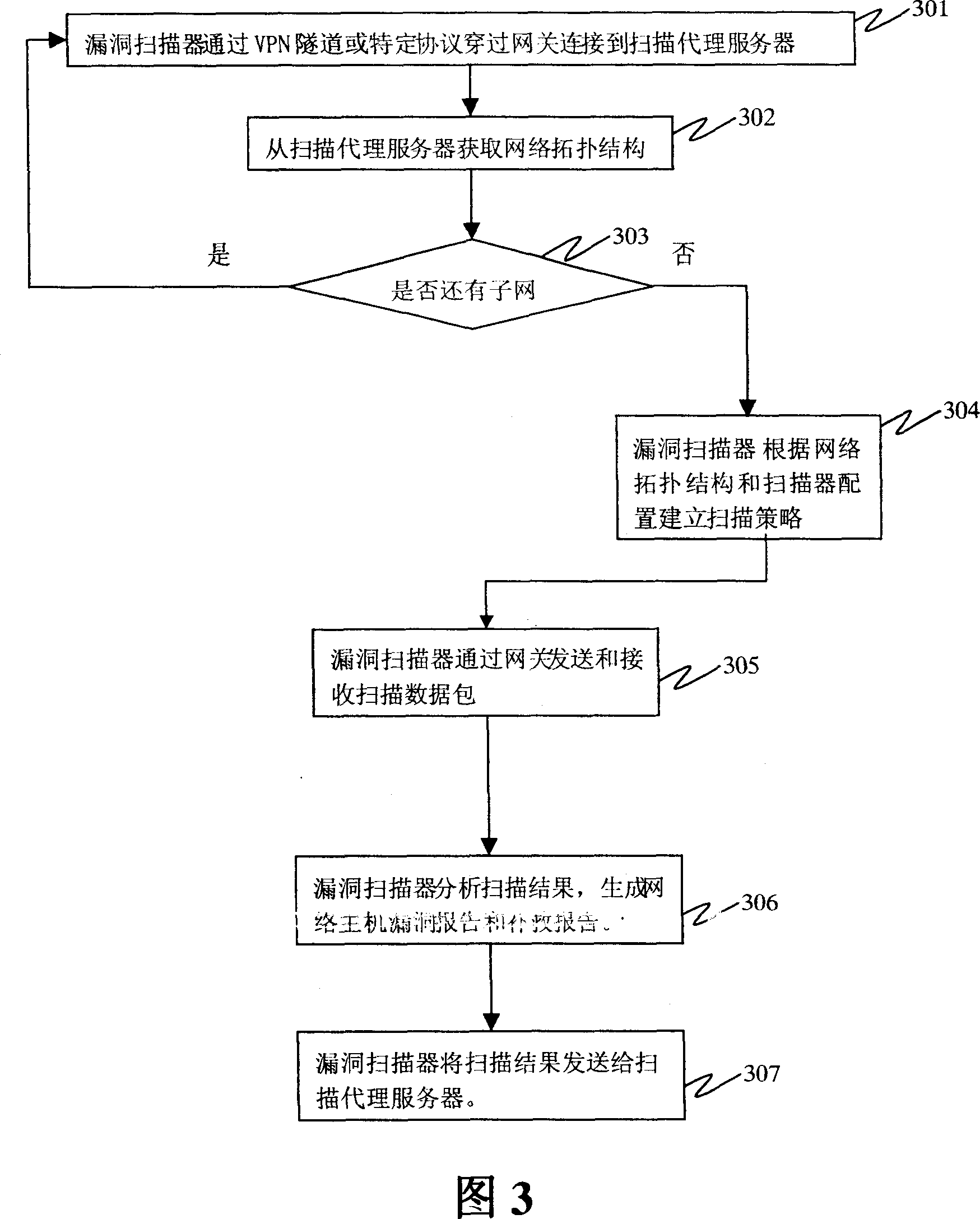
[0027] FIG. 1 is a block diagram of a network risk assessment device of the present invention. As shown in FIG. 1 , the network risk assessment device of the present invention includes a vulnerability scanner 1, a gateway device 2 (such as a firewall or a router), and a scanning proxy server 3 behind the gateway for generating a network topology and processing scanning data packets. Use the risk assessment device of the present invention to perform risk assessment on multiple hosts 4-7 in the network as shown in FIG. 1 as PC1-PC4. Among them, a gateway is a packet filtering device similar to a firewall and a router. It contains information about the topology of the network. The scanning proxy server 3 located behind the gateway can generate a network topology diagram by automatically obtaining information from the gateway device 2 or by manually configuring it. The vulnerability scanner 1 can obtain the network topology from the scanning proxy server through a VPN tunnel or ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com