Patents
Literature
49results about How to "Improve vulnerability detection efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
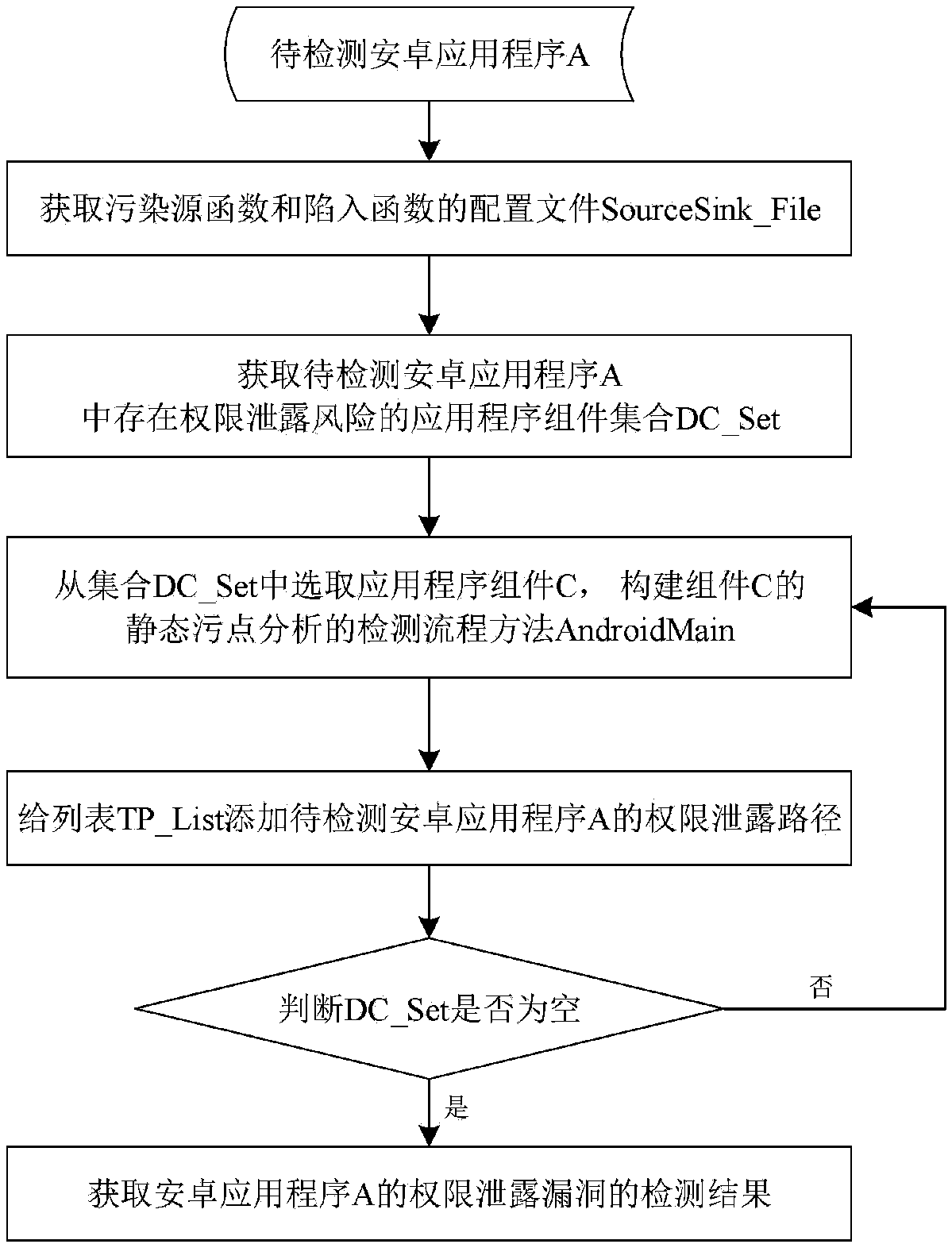
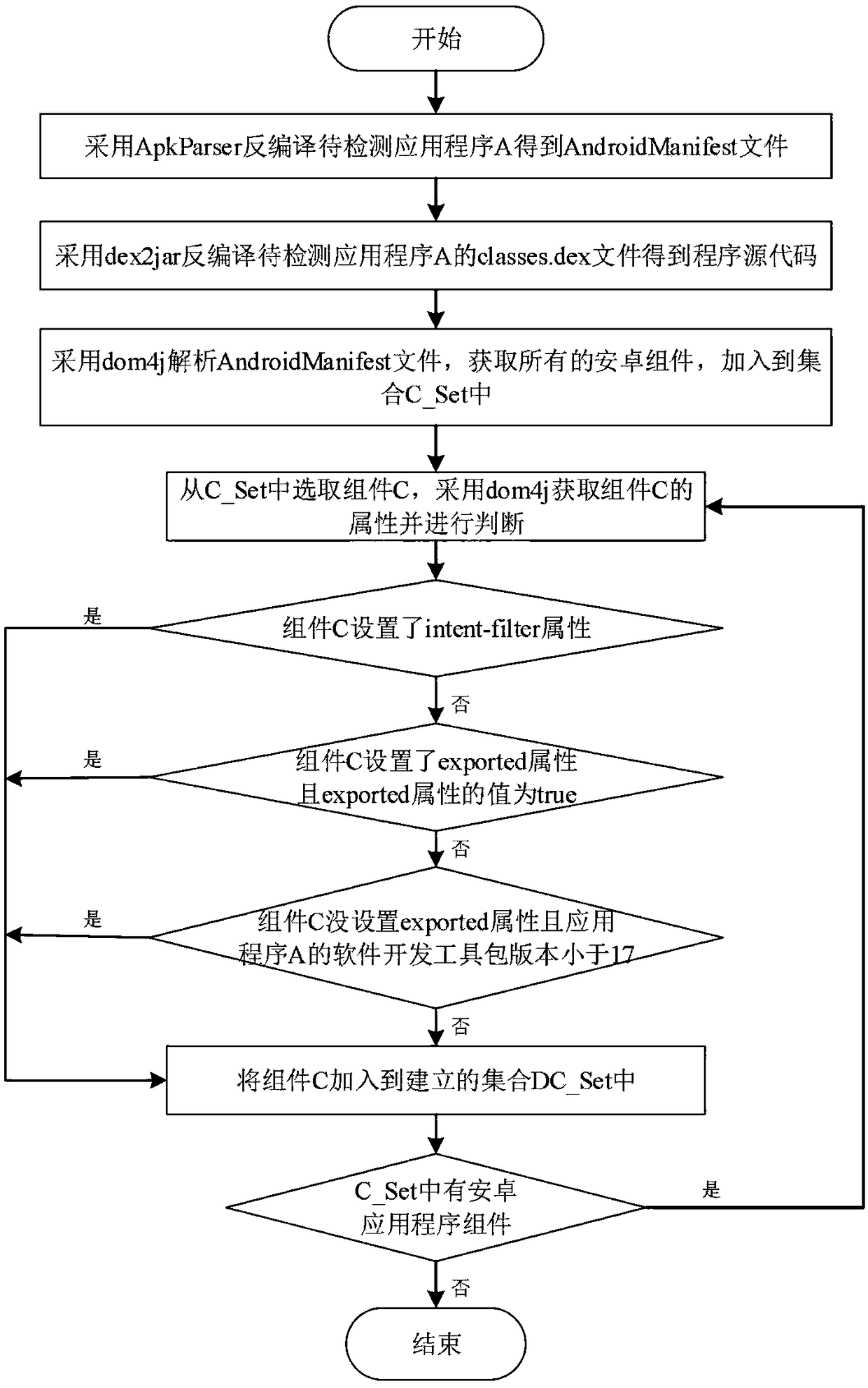
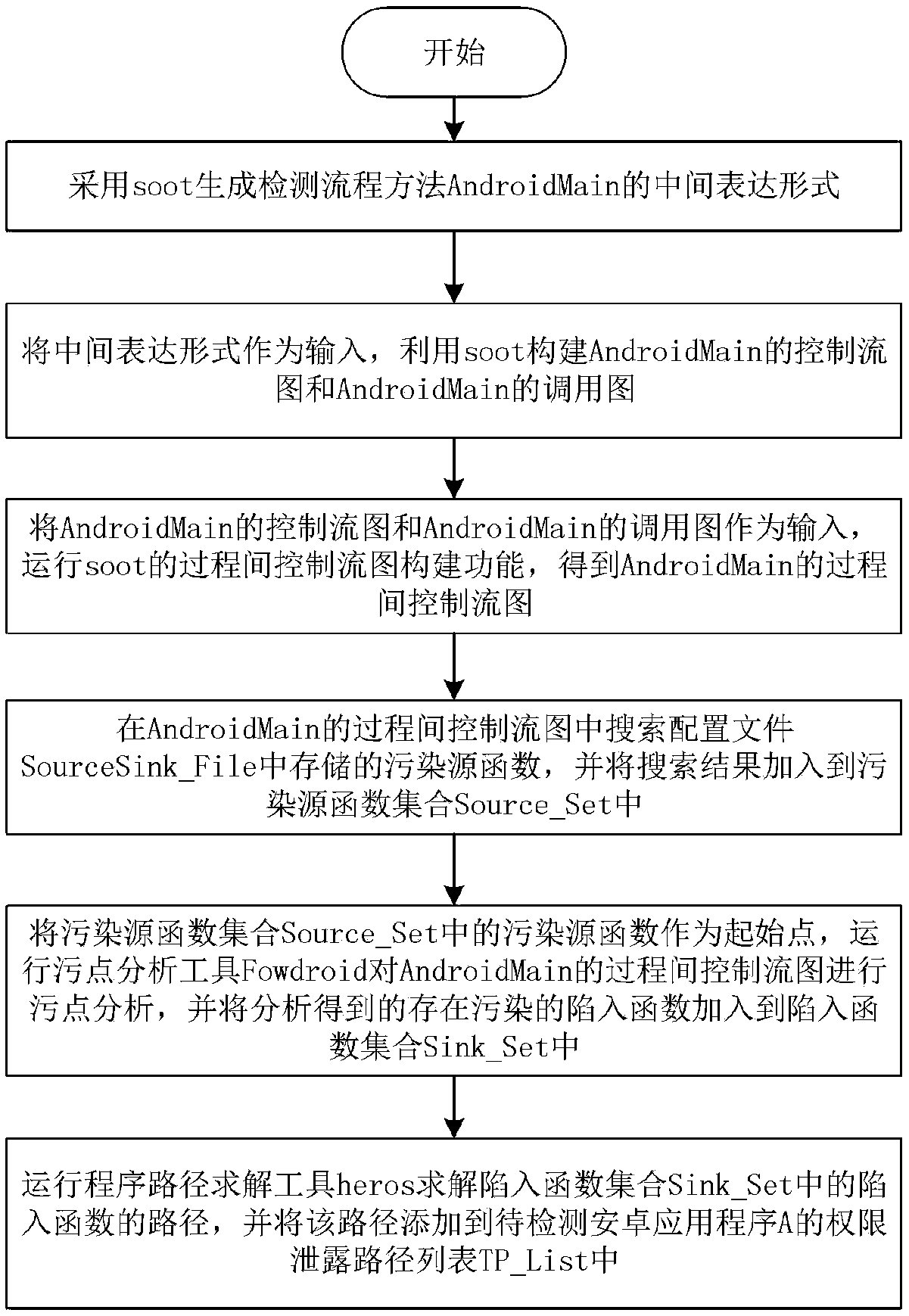
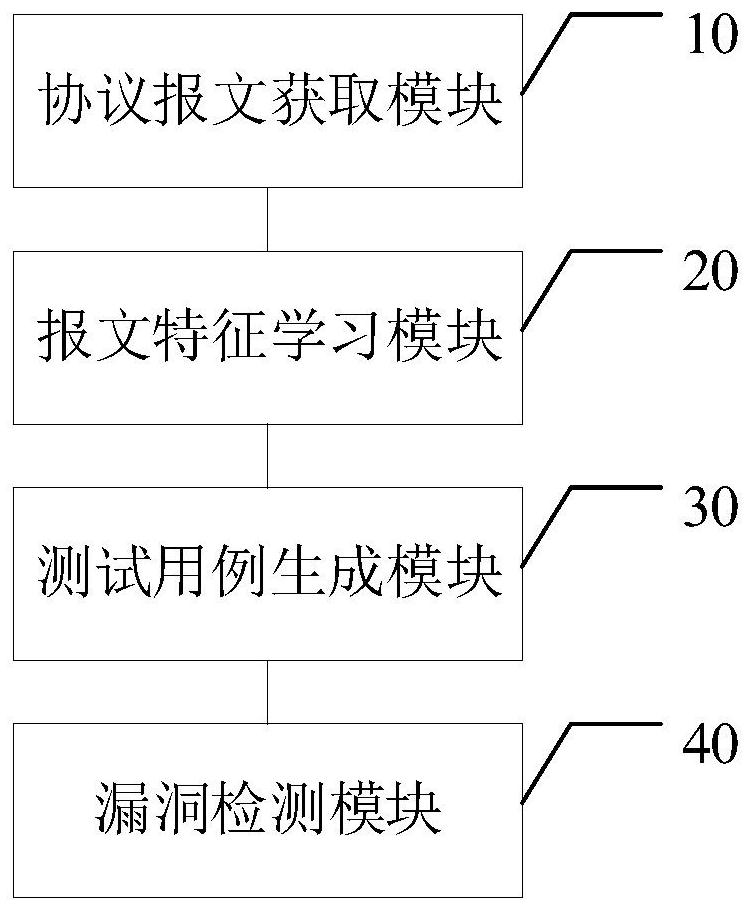
Android application privilege disclosure vulnerability detection method based on static stain analysis
InactiveCN108846282ASmall scaleImprove vulnerability detection efficiencyPlatform integrity maintainanceStatic timing analysisApplication programming interface
The invention provides an Android application privilege disclosure vulnerability detection method, which is used for solving the technical problems of low efficiency of application privilege disclosure vulnerability detection and incomplete detection result in the prior art. The method includes: extracting each application programming interface corresponding to an Android sensitive privilege froman Android system source code, and configuring pollution source functions and trap functions; performing reverse engineering on an application to be detected, analyzing the obtained resource file, andobtaining an application component with the risk of privilege disclosure; then, constructing a detection flow method of static stain analysis of the application component with the risk of privilege disclosure; performing the static stain analysis on the basis of the method, and obtaining a privilege disclosure path list of the application to be detected; finally, outputting the detection result of privilege disclosure vulnerability of the application to be detected. The invention can comprehensively and efficiently detect the Android application privilege disclosure vulnerability, and can beused for the analysis and research of the Android application privilege disclosure vulnerability.
Owner:XIDIAN UNIV
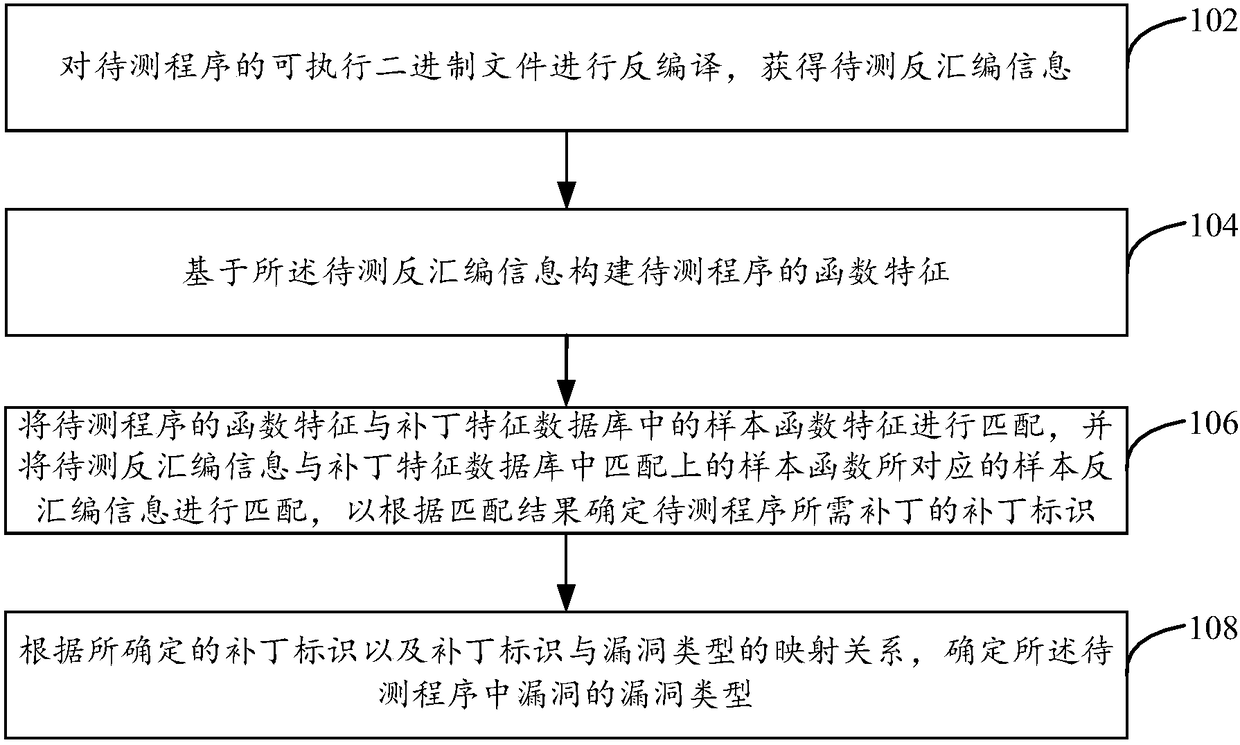
Vulnerability detection method, device and device
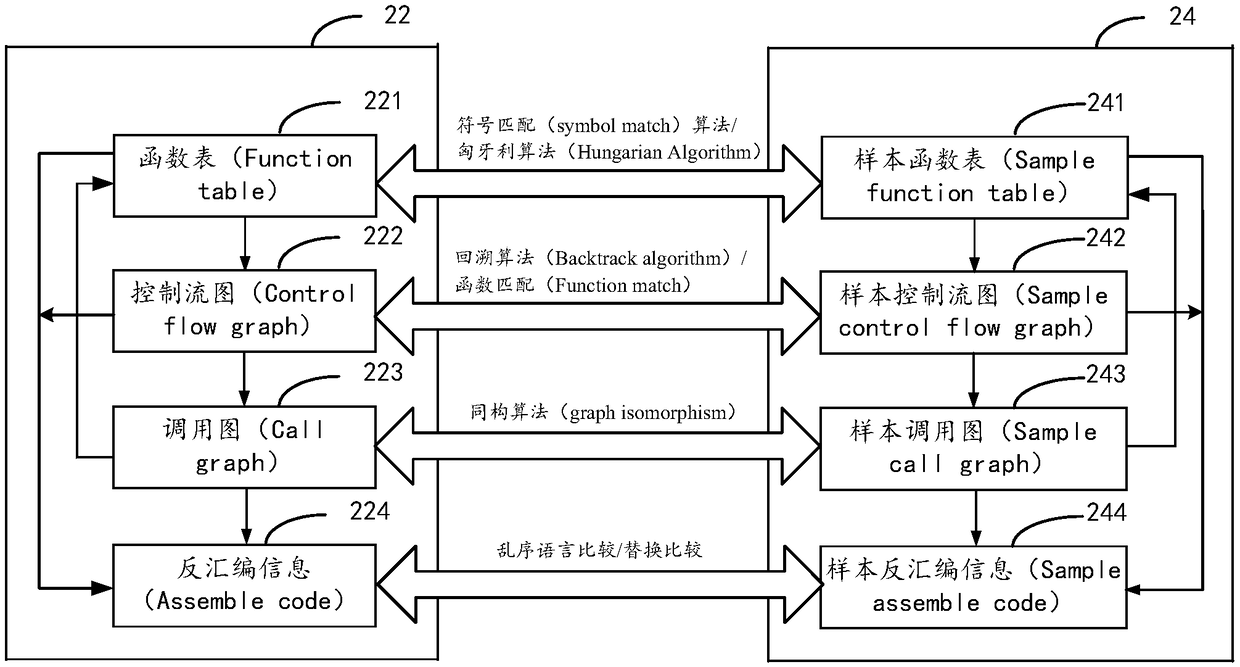
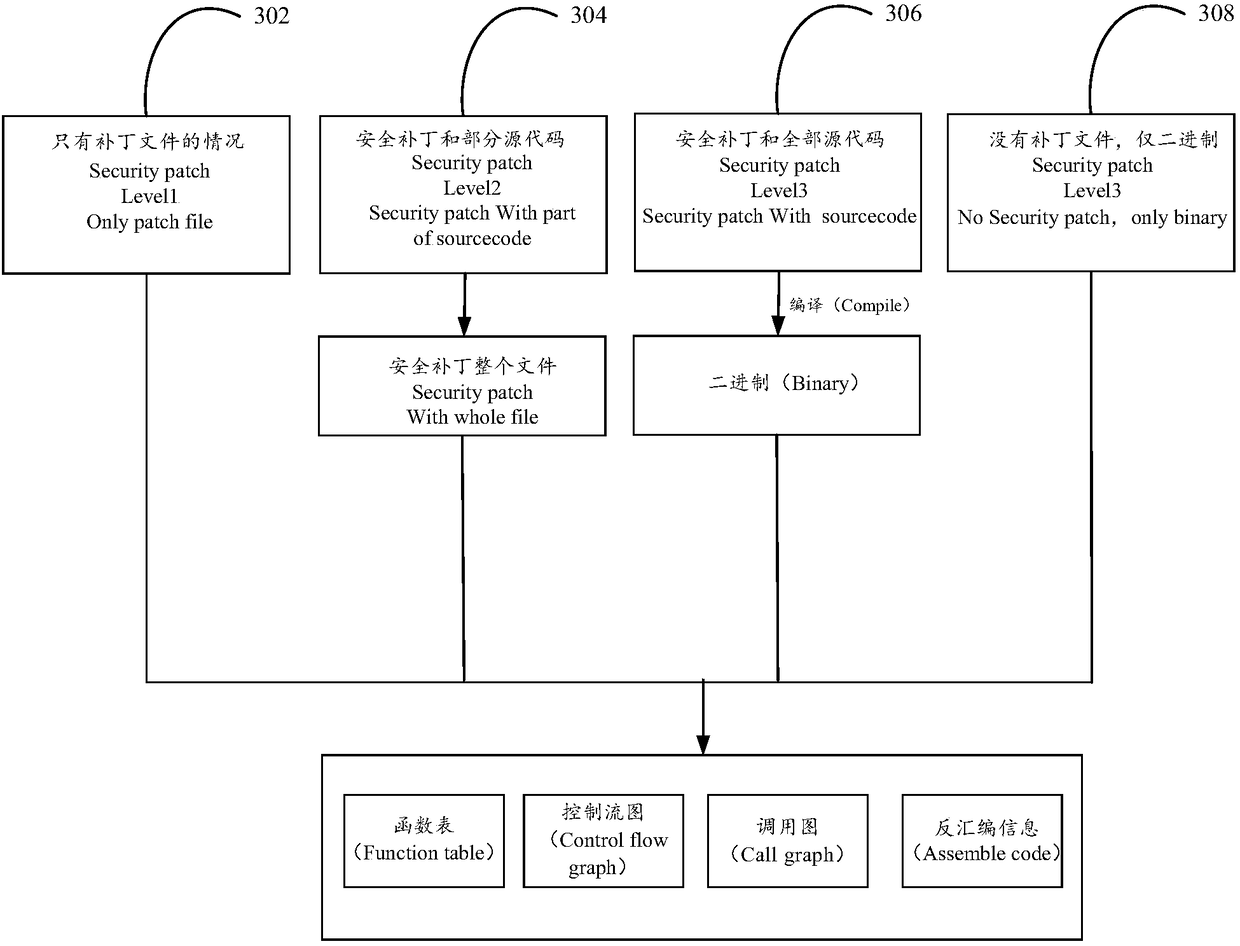
ActiveCN109359468AImprove vulnerability detection efficiencyImprove the accuracy of vulnerability detectionDecompilation/disassemblyPlatform integrity maintainanceMatched sampleFunctional features
the embodiment of that present specification provide a vulnerability detection method, Installations and equipment, the of that present specification exploit file related to historical vulnerabilities, especially patch files, generating a patch feature database including functional features and disassembly information, and utilizing executable binary file of the program to be tested to construct characteristic database of the program to be tested, Firstly, the function features of the program to be tested are matched with the sample function features in the patch feature database, The invention identifies as many functions as possible, and then matches the disassembly information to be tested with the sample disassembly information corresponding to the matched sample function in the patchfeature database, so as to determine whether the program to be tested exists corresponding patch according to the matching result, and when the corresponding patch exists, determines the vulnerabilitytype of the program to be tested according to the patch.
Owner:ADVANCED NEW TECH CO LTD
Method, device and system for optimizing test samples in fuzzy test
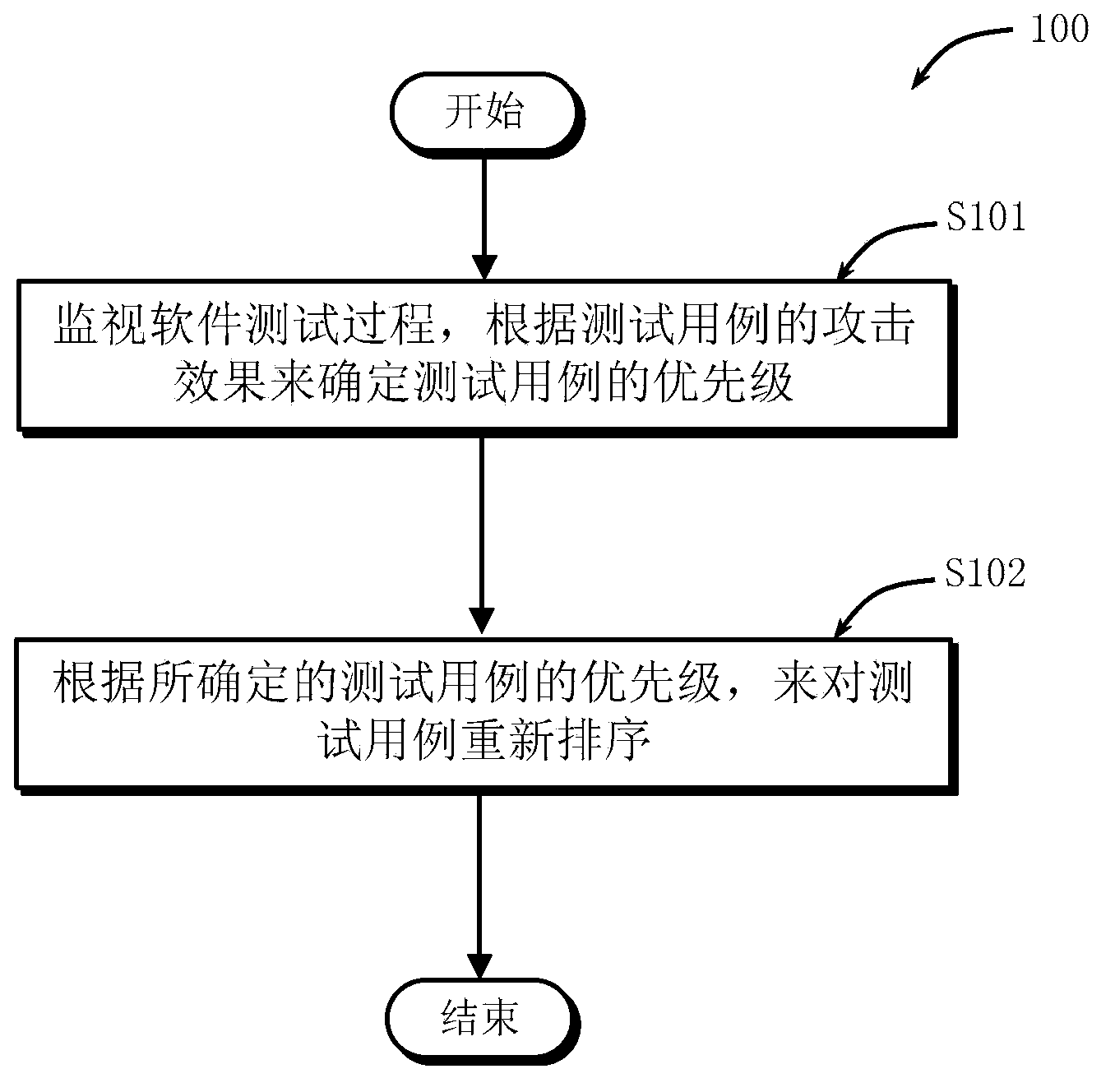
ActiveCN103699475AImprove vulnerability detection efficiencyOptimize test casesComputer security arrangementsSoftware testing/debuggingTest objectTest sample
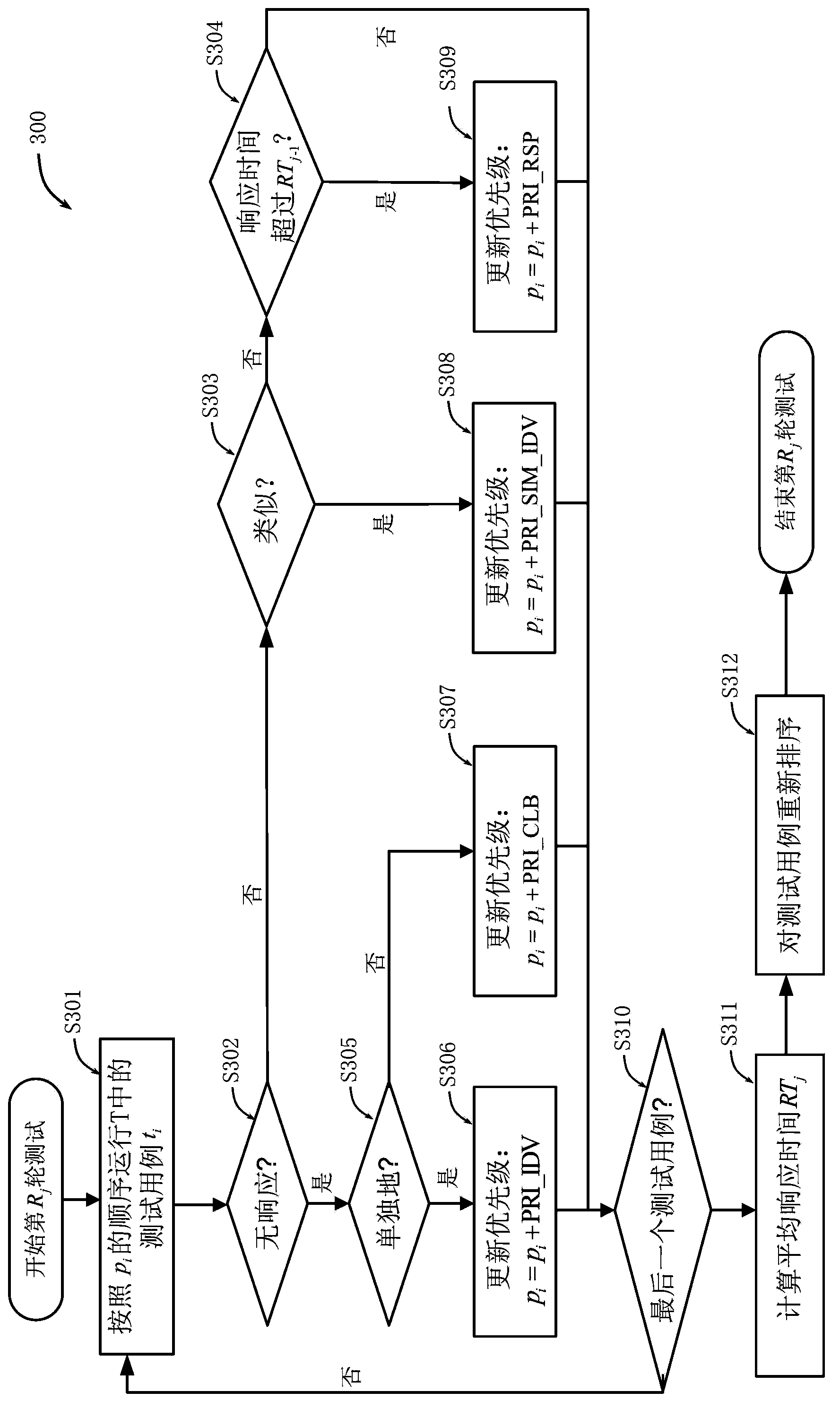
The invention provides a method, a device and a system for ranking test samples. The method comprises the following steps that the following steps are executed for one turn or several turns; each test samples in a plurality of test samples is used for testing a test object according to the ranging sequence of the test samples in an initial test sample set, the attacking effect of each test sample is monitored, and in addition, the priority of each test sample is determined according to the attacking effect corresponding to each test sample; the test samples in the initial test sample set are re-ordered again according to the determined priority of each test sample; the re-ordered test sample set obtained in the current turn can be used as the initial test sample set used in the execution process in the next turn.
Owner:SIEMENS AG
Bug detection method, device and equipment and computer storage medium
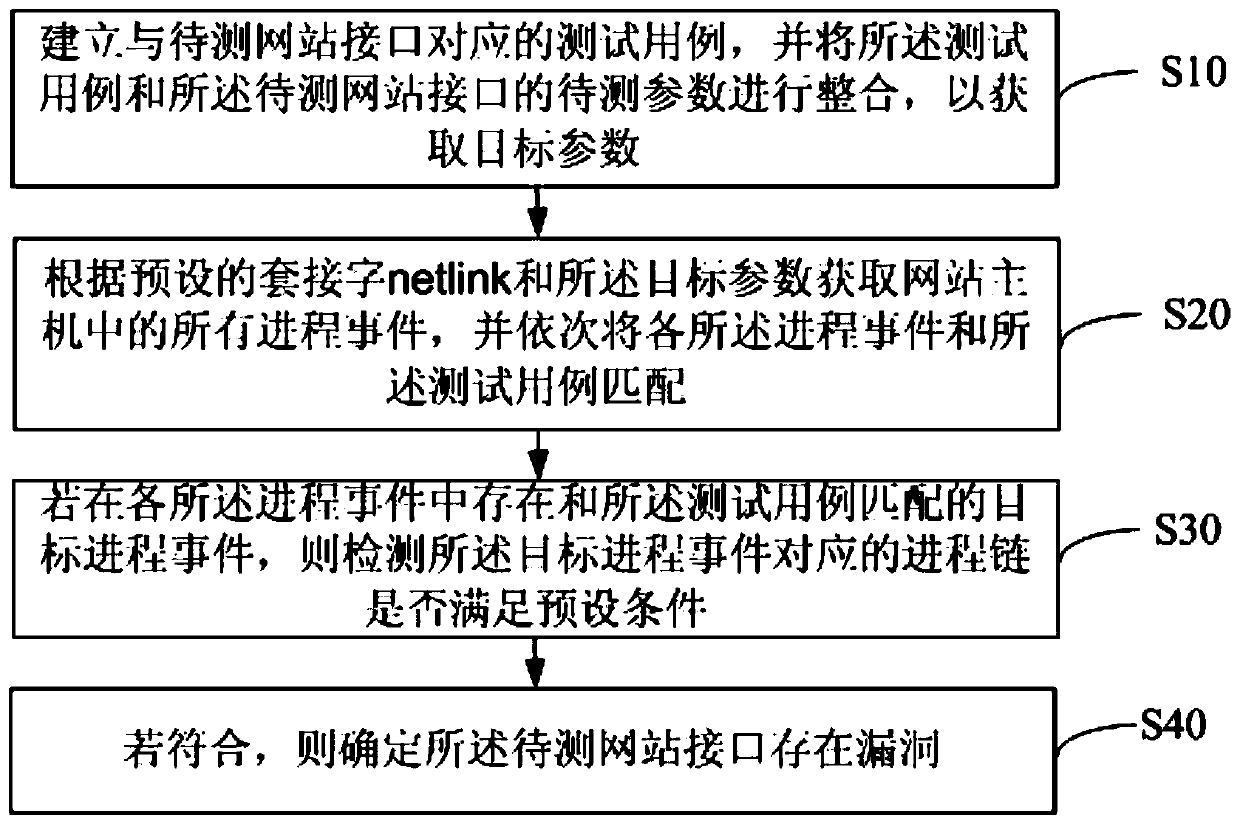
PendingCN110765464AImprove vulnerability detection efficiencyImprove accuracyPlatform integrity maintainanceWeb siteDatabase
The invention relates to the technical field of Fintech, and discloses a vulnerability detection method, which comprises the following steps of: establishing a test case corresponding to a website interface to be detected, and integrating the test case and a parameter to be detected of the website interface to be detected to obtain a target parameter; obtaining all process events in a website hostaccording to a preset socket netlink and the target parameter, and matching each process event with the test case in sequence; if a target process event matched with the test case exists in the process events, detecting whether a process chain corresponding to the target process event meets a preset condition or not; and if so, determining that the to-be-tested website interface has a vulnerability. The invention further discloses a vulnerability detection device and equipment and a computer storage medium. According to the invention, the vulnerability detection efficiency is improved.
Owner:WEBANK (CHINA)
Vulnerability detection method and device
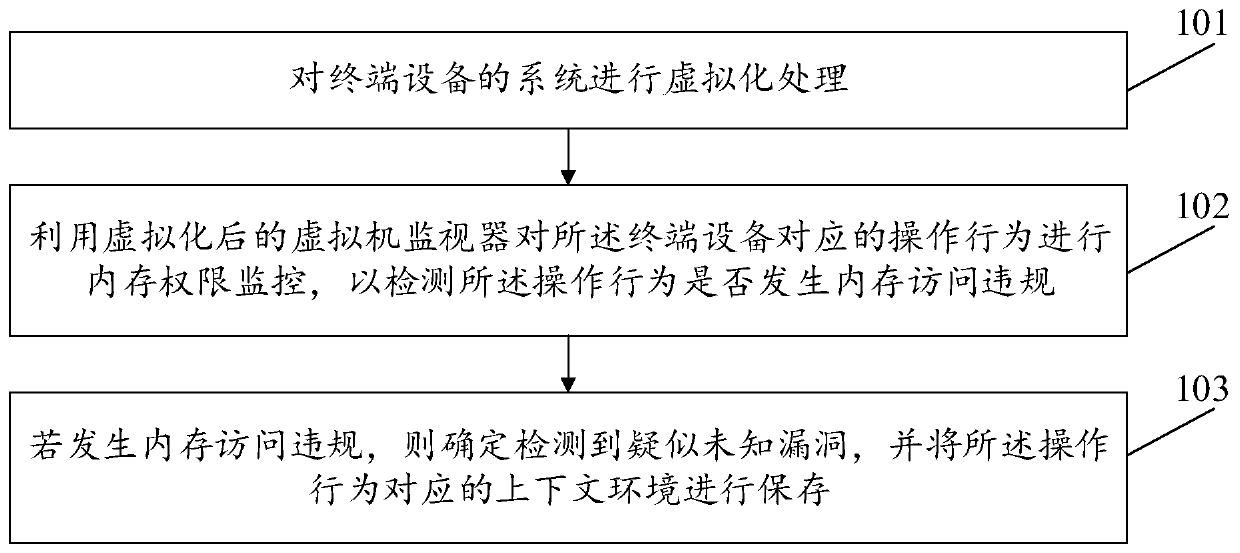
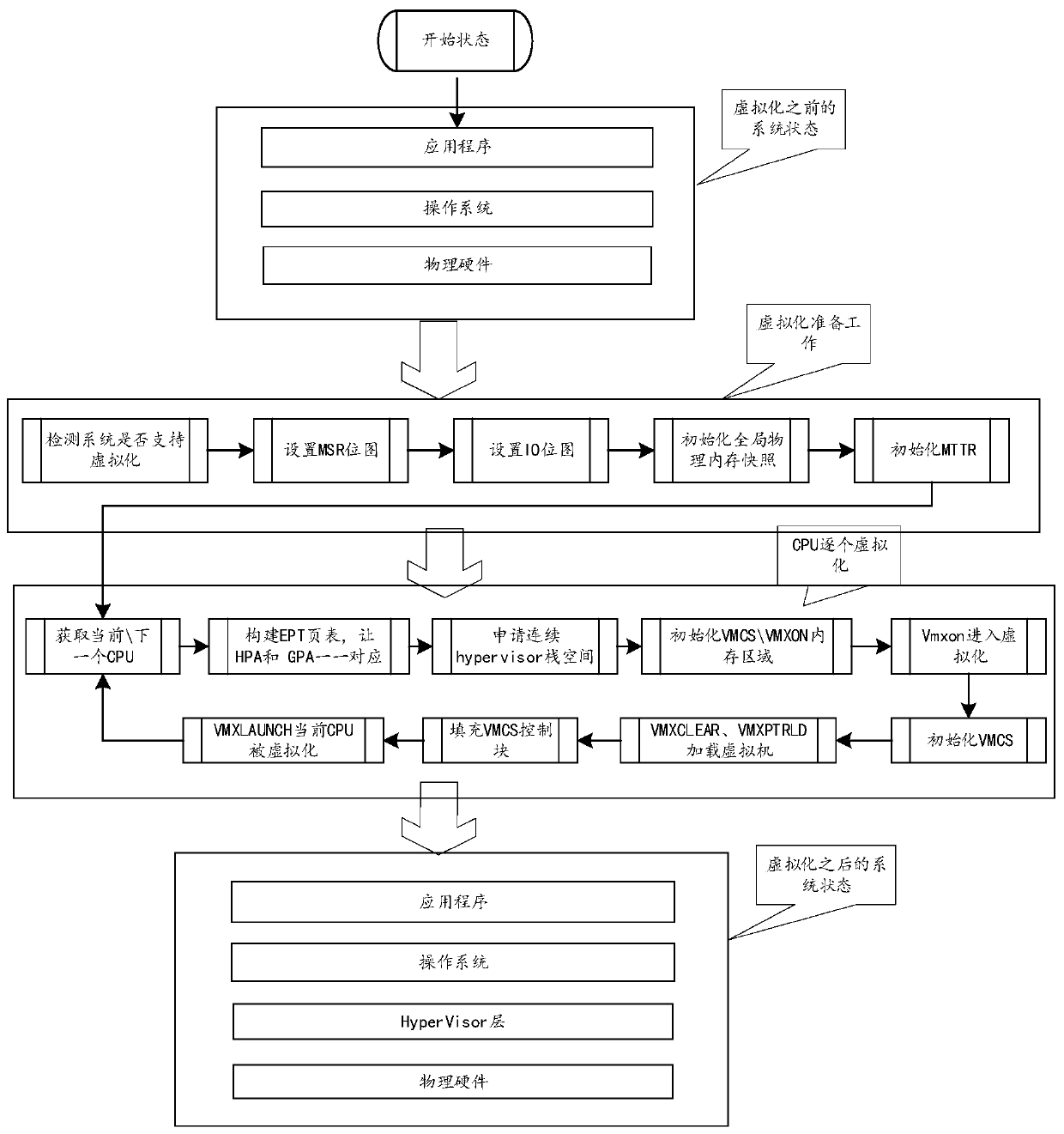
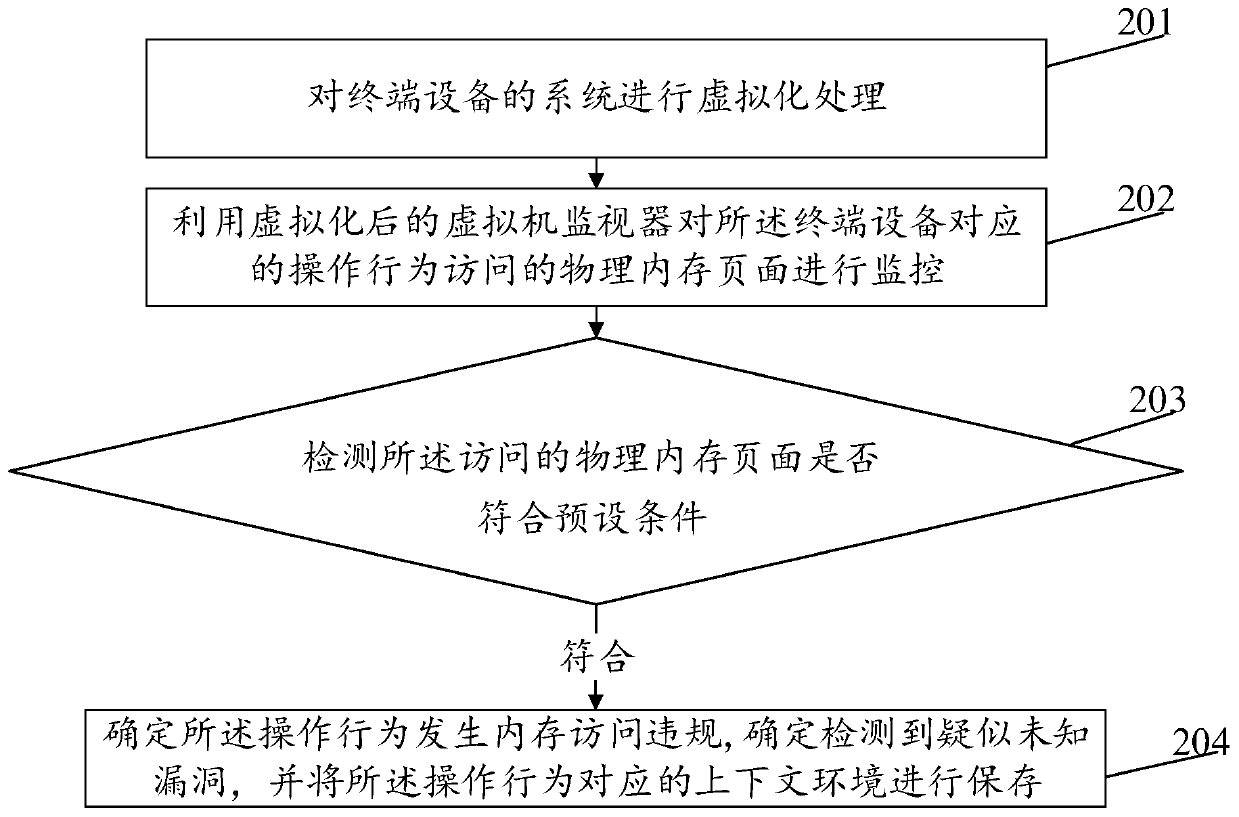
ActiveCN109784062ANarrow searchSimple processPlatform integrity maintainanceVirtualizationTerminal equipment
The invention discloses a vulnerability detection method and device, relates to the technical field of security, and mainly aims to reduce the search range of an unknown vulnerability detection hole,simplify the vulnerability detection process and save the time consumed by detection, thereby improving the vulnerability detection efficiency. The method comprises the following steps: carrying out virtualization processing on a system of terminal device; Using a virtualized virtual machine monitor to perform memory permission monitoring on an operation behavior corresponding to the terminal device so as to detect whether the operation behavior has a memory access violation or not; And if the memory access violation occurs, determining that a suspected unknown vulnerability is detected, and storing a context environment corresponding to the operation behavior, the context environment being used for further detecting the suspected unknown vulnerability. The method is suitable for vulnerability detection.
Owner:QI AN XIN SECURITY TECH ZHUHAI CO LTD +1
Intelligent fuzzy test method, device and system
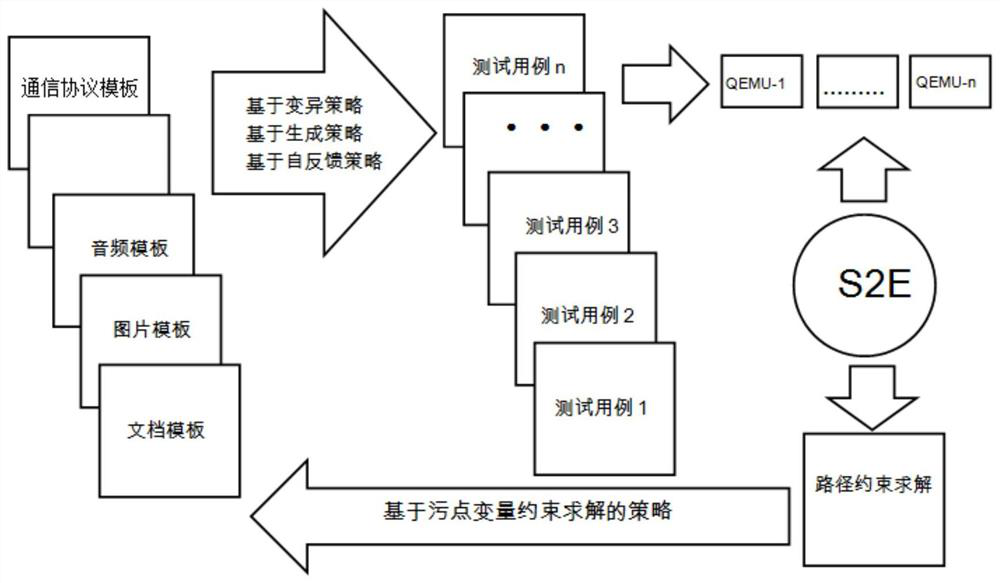
PendingCN112181833AIncrease coverageAvoid path explosionSoftware testing/debuggingPlatform integrity maintainanceComputer engineeringReal-time computing
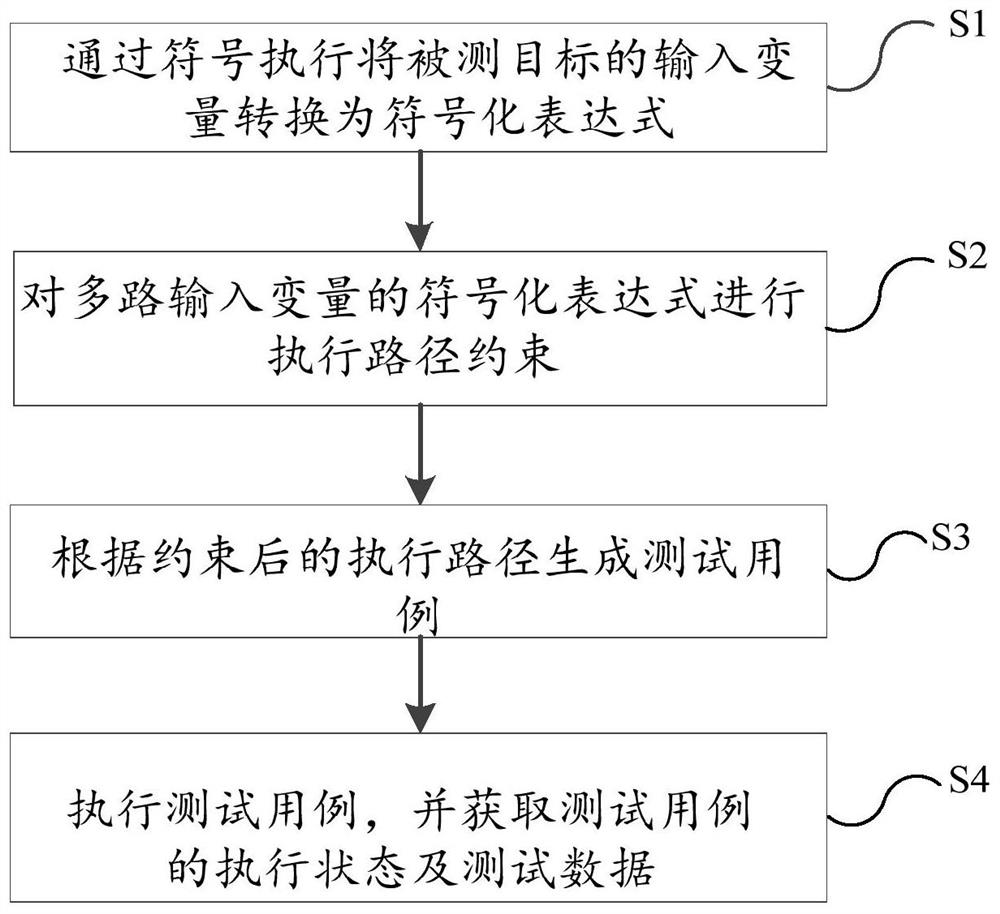
The invention discloses an intelligent fuzzy test method, device and system, and relates to the technical field of computers, and the method comprises the steps: converting an input variable of a tested target into a symbolic expression through symbolic execution; performing execution path constraint on the symbolic expression of the multiple paths of input variables; generating a test case according to the constrained execution path; and executing the test case, and obtaining an execution state and test data of the test case. The embodiment of the invention can solve the problem of low detection efficiency of the existing fuzzy test.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
Software source code vulnerability detection method based on artificial neural network
PendingCN111177731AReduce complexityReduce time investmentCharacter and pattern recognitionPlatform integrity maintainanceLinguistic modelFeature extraction
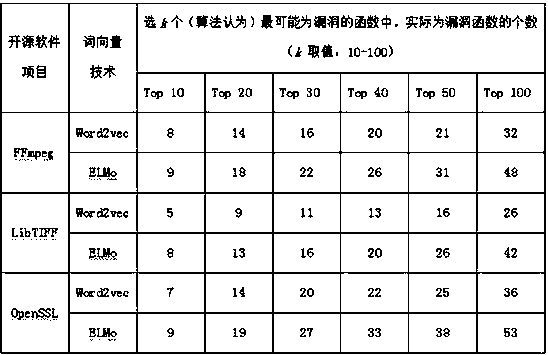
The invention discloses a software source code vulnerability detection method based on an artificial neural network, and the method is based on deep learning and a word vector technology derived froma language model, so that a hidden mode of a code can be automatically learned by a deep learning algorithm, thereby saving the time consumption and tedious process of manual feature extraction. And the complexity of code processing and analysis is further weakened, so that the time investment of code processing and analysis is saved. The ELMo-based deep learning framework can directly accept a source code sequence as input and output a prediction result, so that end-to-end detection on a source code level is realized in a real sense.
Owner:江苏深度空间信息科技有限公司
Vulnerability detection system and method of Android hybrid-application code injection
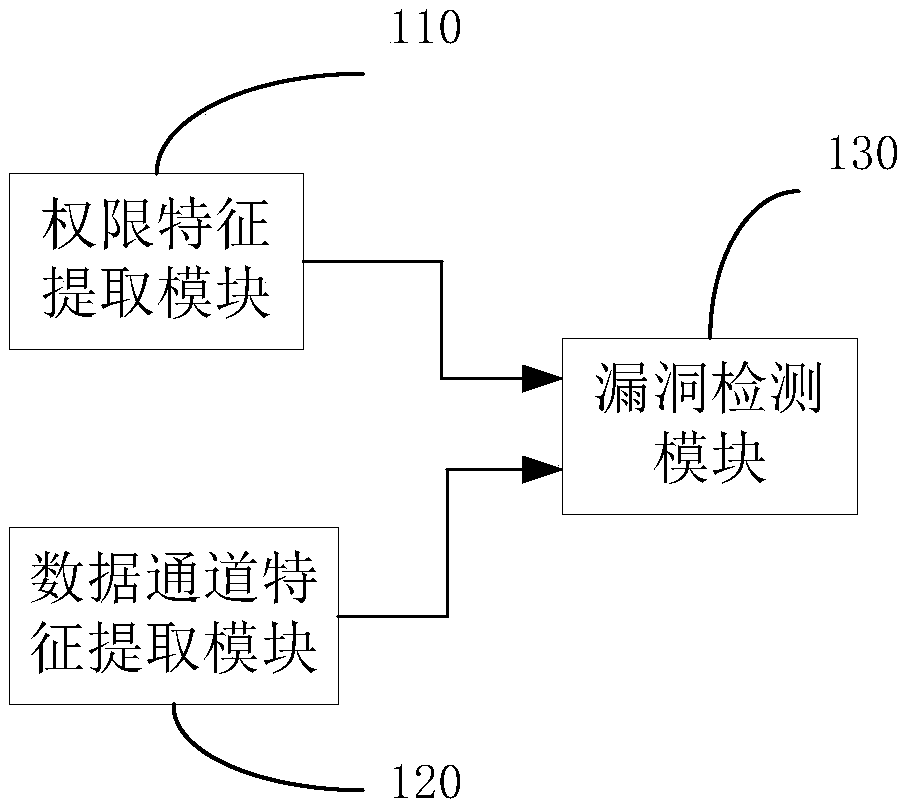
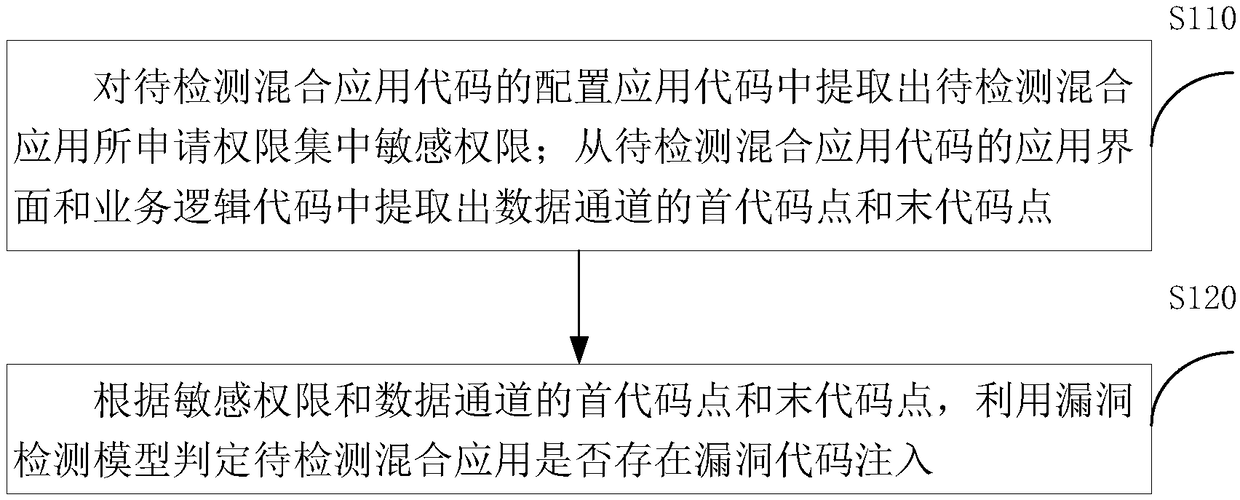
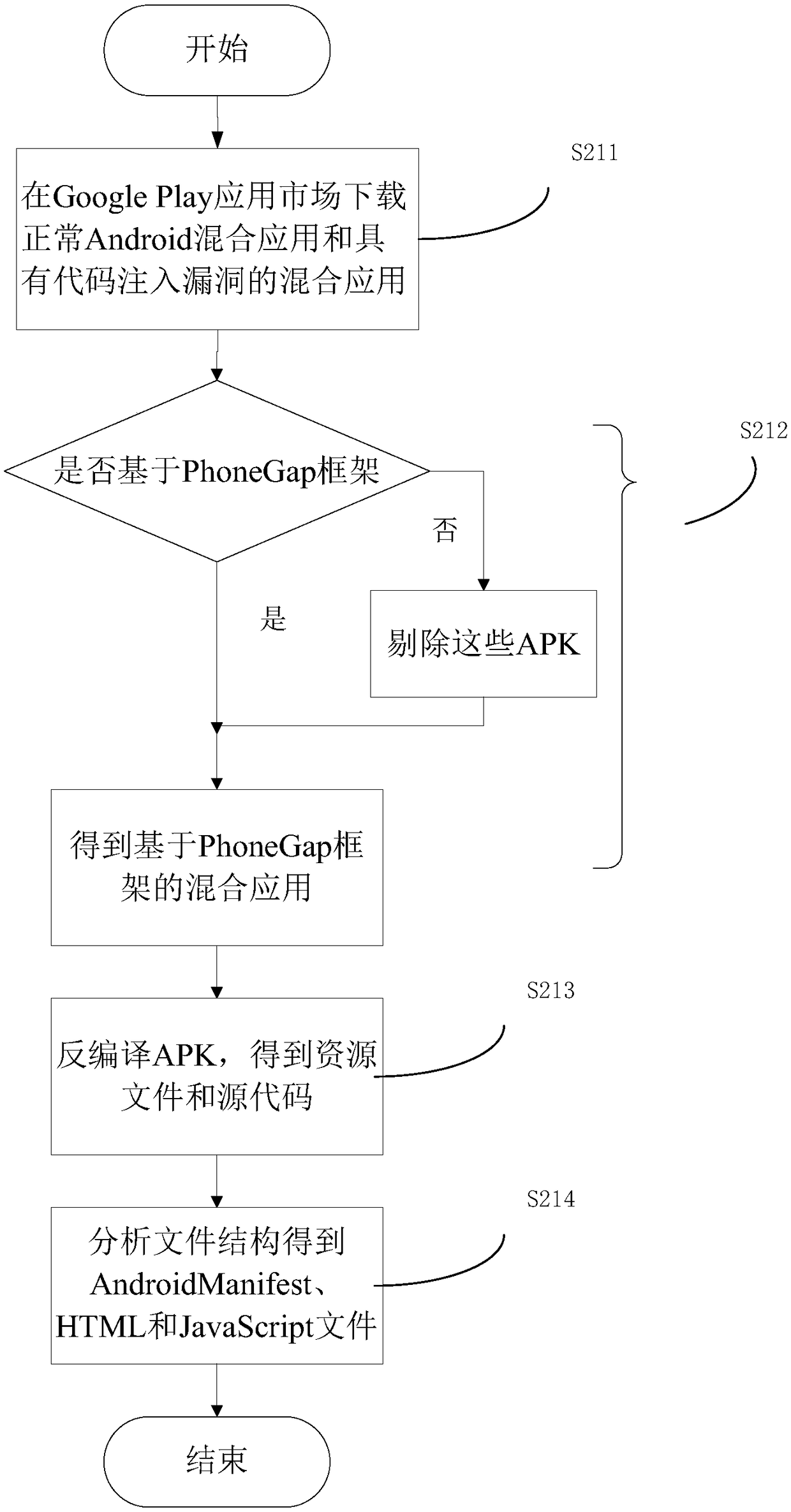
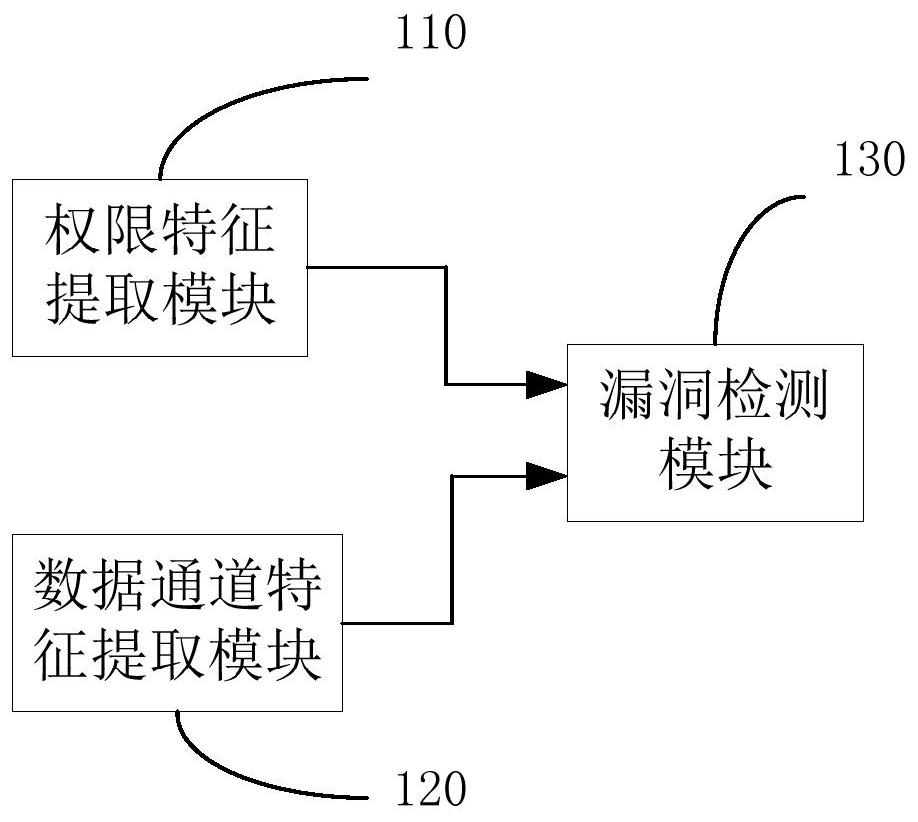
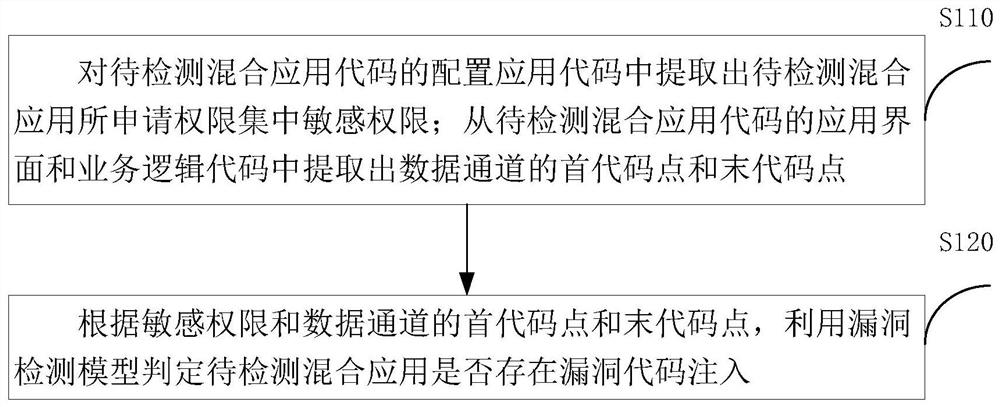
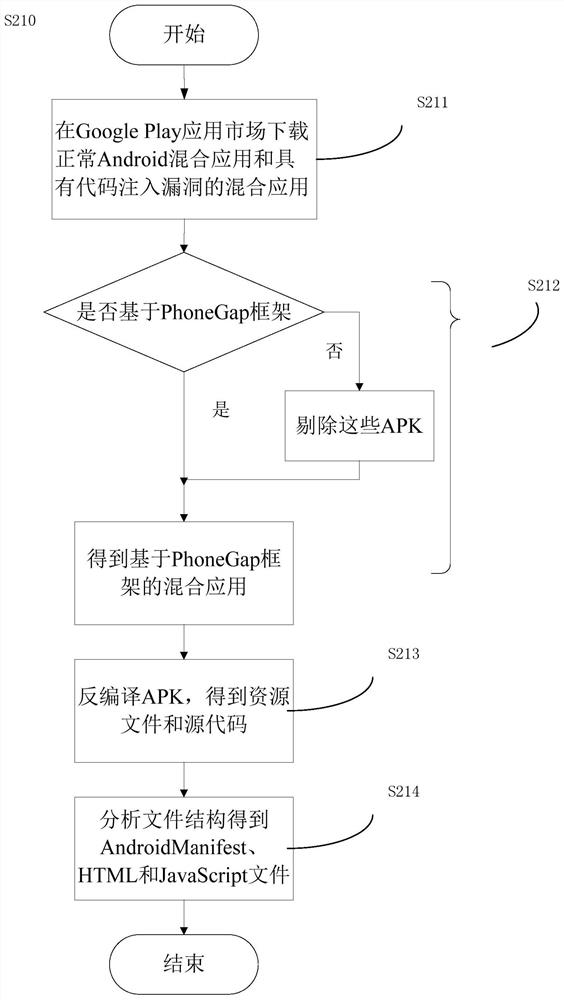
ActiveCN108647517AImprove vulnerability detection efficiencyImprove effectivenessPlatform integrity maintainanceVulnerability detectionPoint set
The invention discloses a vulnerability detection system and method of Android hybrid-application code injection. The system includes a permission feature extraction module, a data channel feature extraction module and a vulnerability detection module. The permission feature extraction module is used for extracting a sensitive permission application set of a to-be-detected hybrid application fromto-be-detected hybrid-application code. The data channel feature extraction module is used for extracting a source point set and a receiving point set of data channels from the to-be-detected hybrid-application code. A first input end of the vulnerability detection module is connected to the output end of the permission feature extraction module, and the second input end thereof is connected to the output end of the data channel feature extraction module. The vulnerability detection module is used for according to sensitive permissions and the source point set and the receiving point set of the data channels, using a vulnerability detection model to determine whether vulnerability code injection of the to-be-detected hybrid application exists. Compared with traditional detection methods based on control flow and program call graphs, the method of the invention has higher efficiency, is very high in classification accuracy, and has very good usability.
Owner:HUAZHONG UNIV OF SCI & TECH
Vulnerability detection method and system
ActiveCN111935149AEnsure success rateEnsure efficiencyPlatform integrity maintainanceTransmissionData miningData science
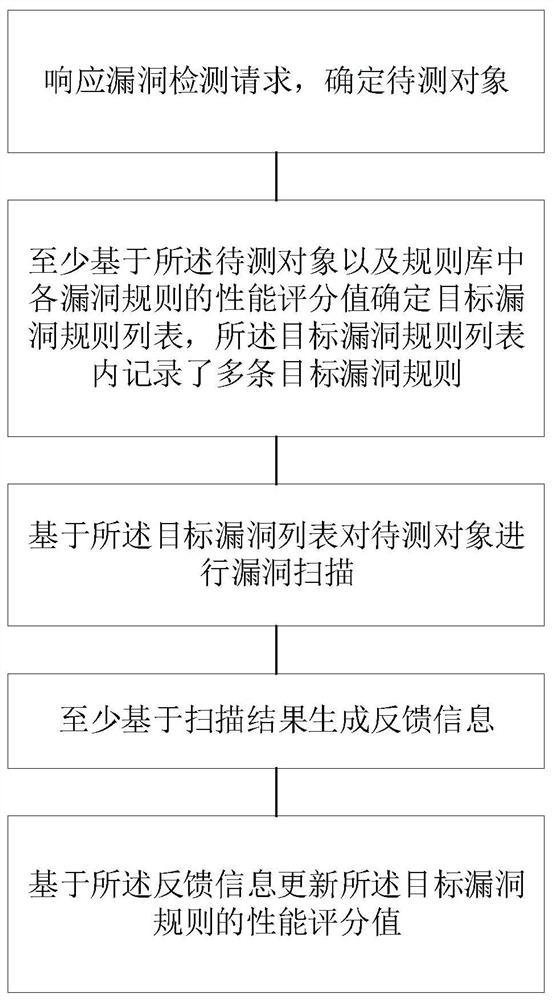
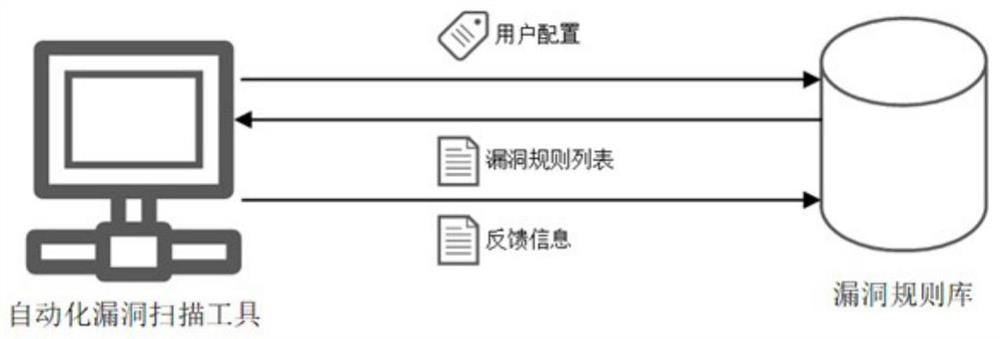
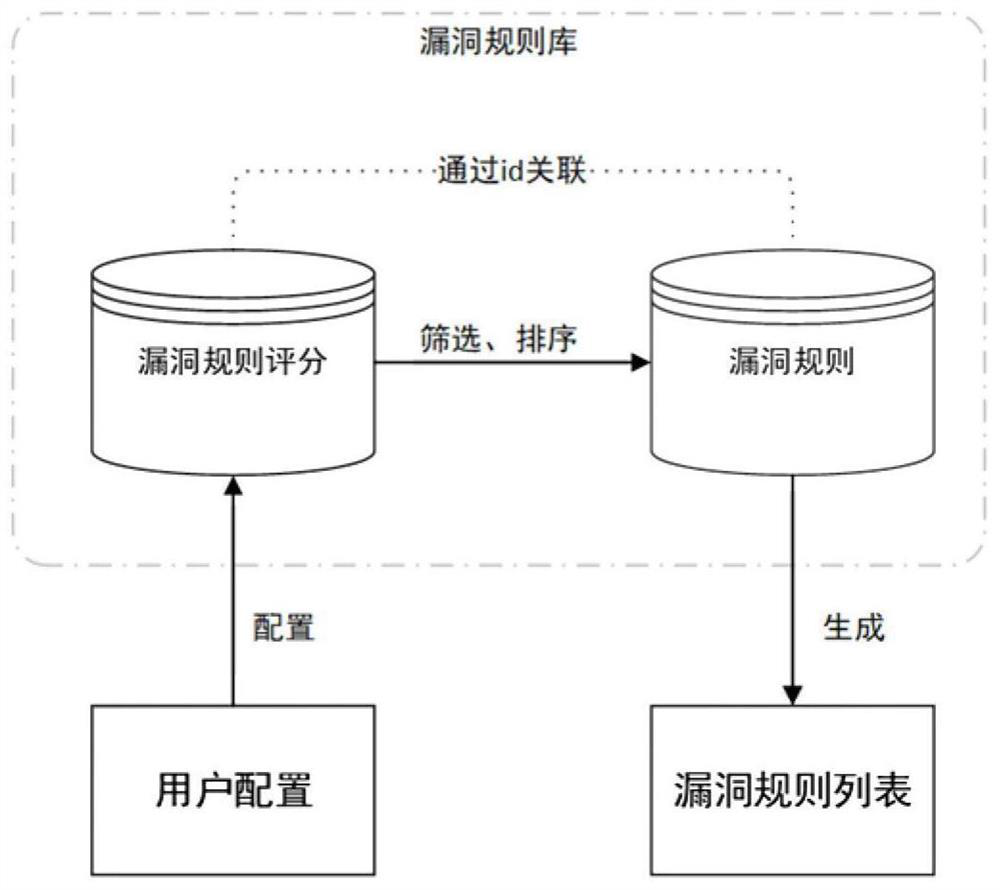
The invention provides a vulnerability detection method and system, and the method comprises the steps: responding to a vulnerability detection request, and determining a to-be-detected object; determining a target vulnerability rule list at least based on the to-be-detected object and the performance score value of each vulnerability rule in a rule base, wherein a plurality of target vulnerability rules are recorded in the target vulnerability rule list; performing vulnerability scanning on the to-be-detected object based on the target vulnerability list; generating feedback information at least based on the scanning result; and updating a performance score value of the target vulnerability rule based on the feedback information. According to the vulnerability detection method, the optimal vulnerability rule can be automatically determined and updated, so that the success rate and speed of each vulnerability detection are ensured.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Bug detection method and device, storage medium and electronic equipment
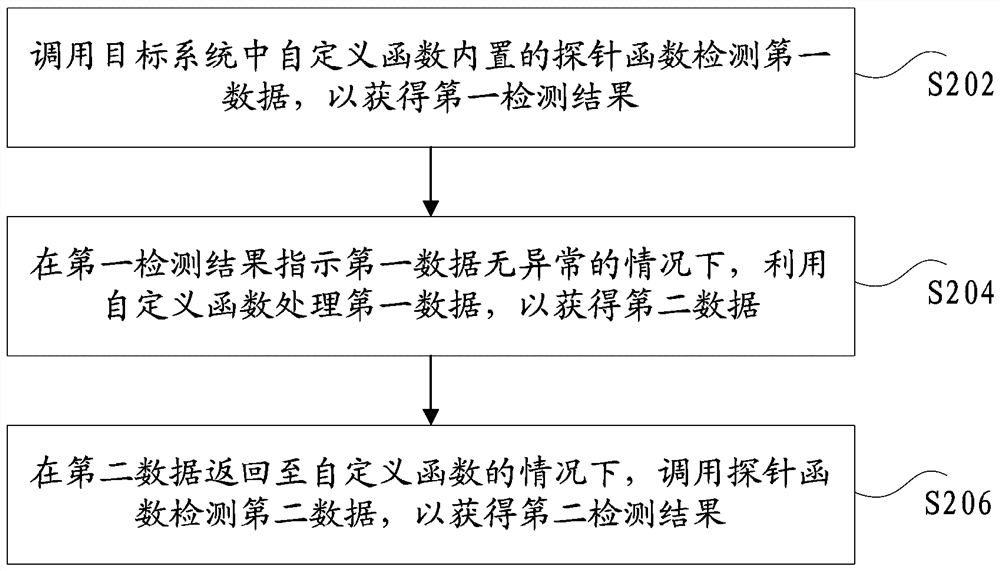
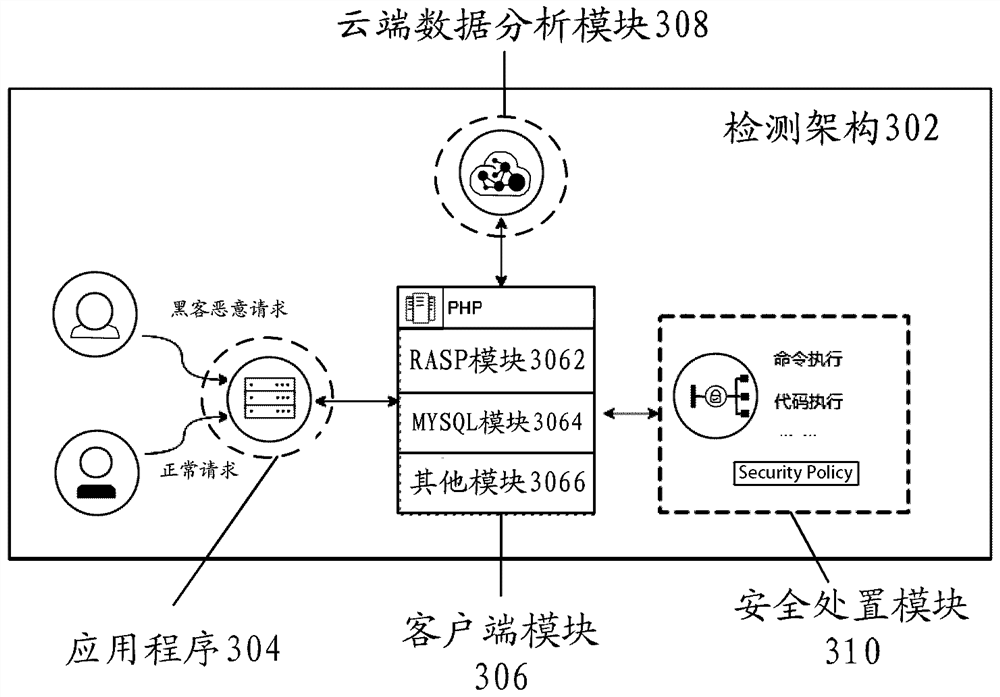
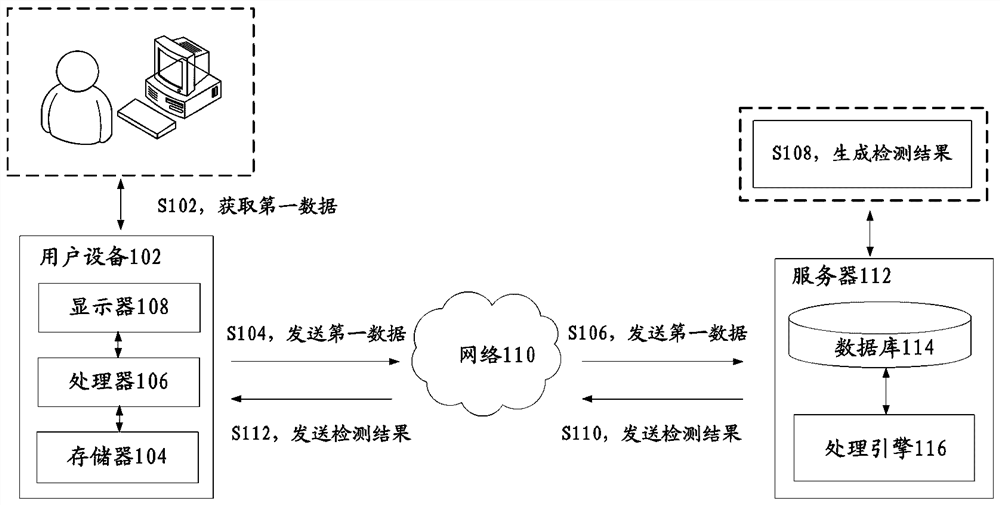
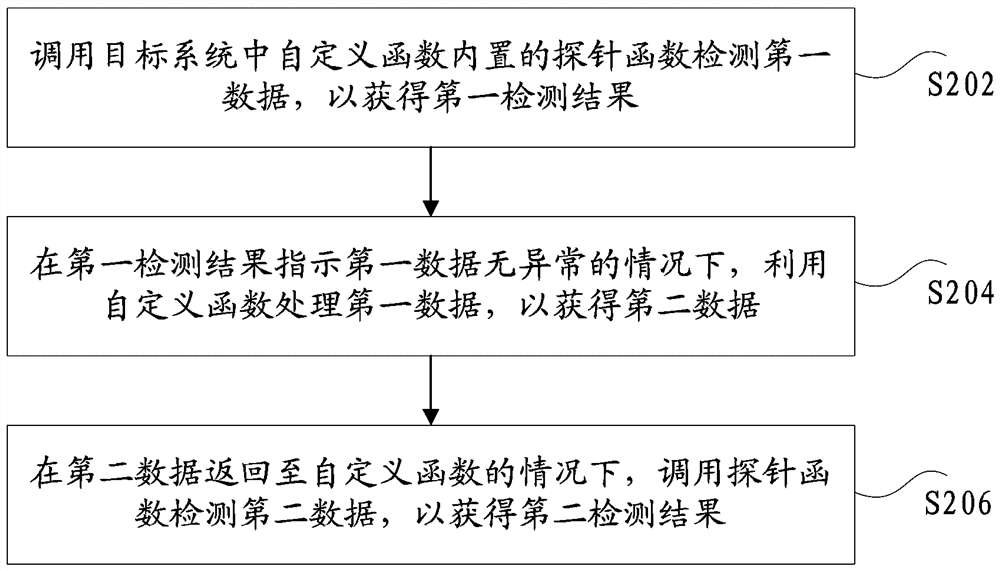
ActiveCN112528296AGuaranteed accuracyImprove vulnerability detection efficiencyPlatform integrity maintainanceTransmissionDatabaseComputer engineering
The invention discloses a vulnerability detection method and device in a cloud technology scene, a storage medium and electronic equipment, and particularly relates to technologies such as protectionin the field of cloud security. The method comprises the following steps: calling a probe function built in a custom function in a target system to detect first data so as to obtain a first detectionresult; under the condition that the first detection result indicates that the first data is not abnormal, processing the first data by utilizing a custom function to obtain second data; under the condition that the second data is returned to the custom function, calling the probe function to detect the second data to obtain a second detection result, wherein the second detection result is used for indicating whether the target system has vulnerabilities or not. The technical problem of low vulnerability detection efficiency is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Vulnerability detection method and device, server and storage medium
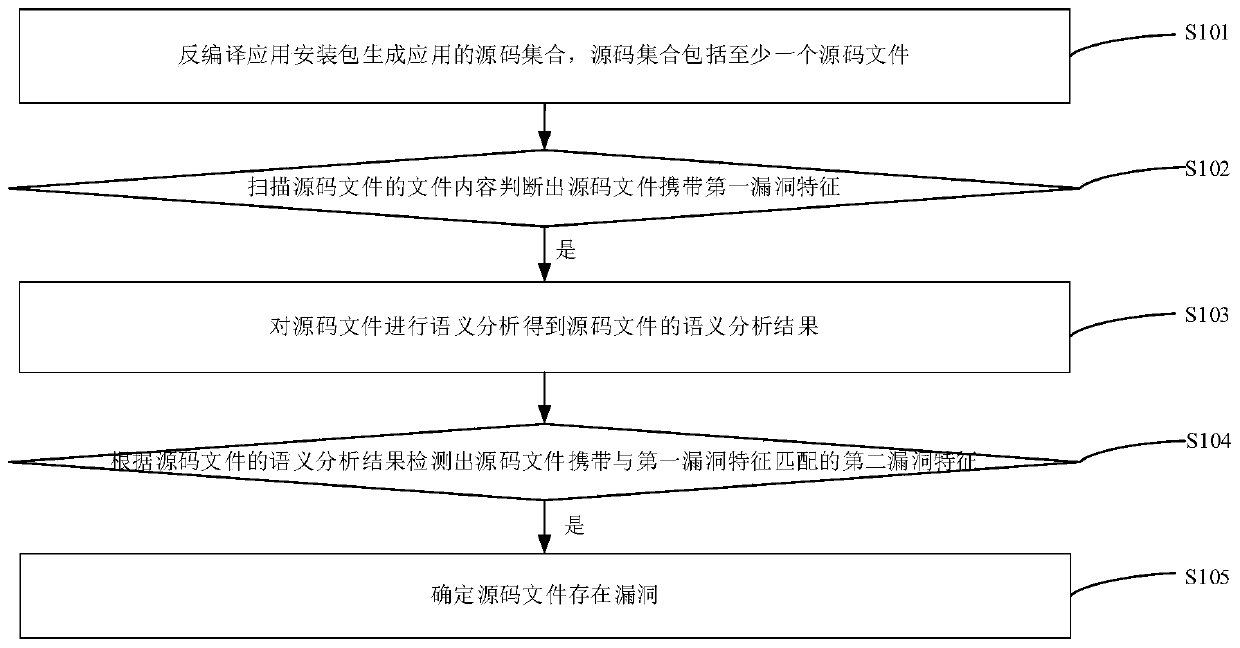
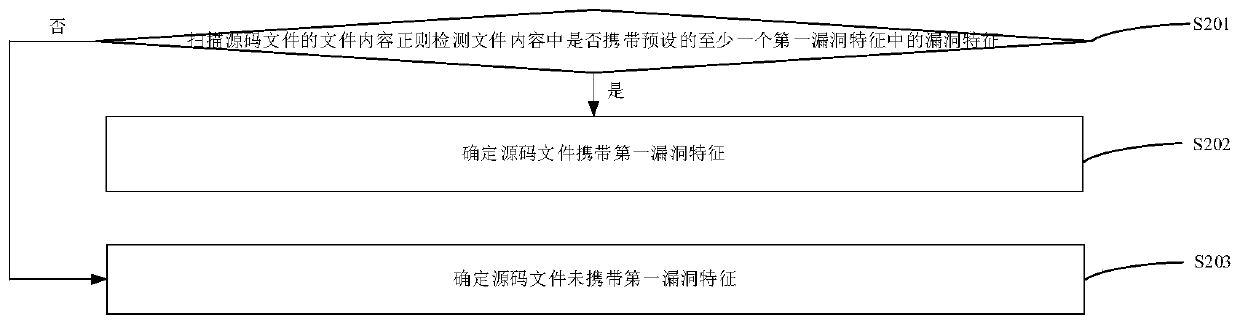
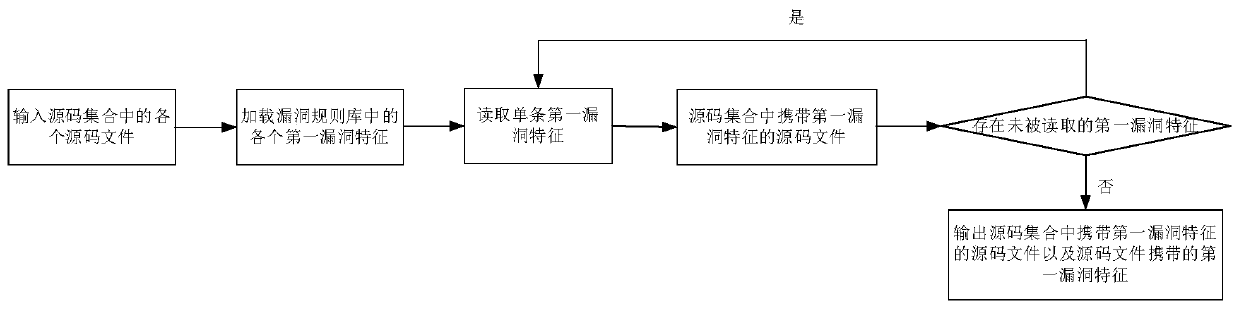
ActiveCN110968874AImplementation of Vulnerability DetectionImprove vulnerability detection efficiencyPlatform integrity maintainanceCode compilationSource code fileDatabase
The invention provides a vulnerability detection method and device, a server and a storage medium. The method includes: generating a source code set of an application by decompiling an application installation package; scanning file content of a source code file in the source code set to judge whether the source code file carries a first vulnerability feature or not; under the condition that the source code file carries the first vulnerability feature, performing semantic analysis on the source code file, detecting whether the source code file carries a second vulnerability feature matched with the first vulnerability feature based on a semantic analysis result of the source code file, and if the source code file carries the second vulnerability feature matched with the first vulnerabilityfeature, determining that the source code file has a vulnerability. According to the invention, whether the source code file possibly has the vulnerability or not is determined through the first vulnerability feature irrelevant to semantics; semantic analysis is performed on the source code file to determine whether the source code file really has the vulnerability on the basis that the source code file possibly has the vulnerability, so that the vulnerability detection of the source code file can be realized, and the vulnerability detection efficiency can be effectively improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Vulnerability management system based on network assets
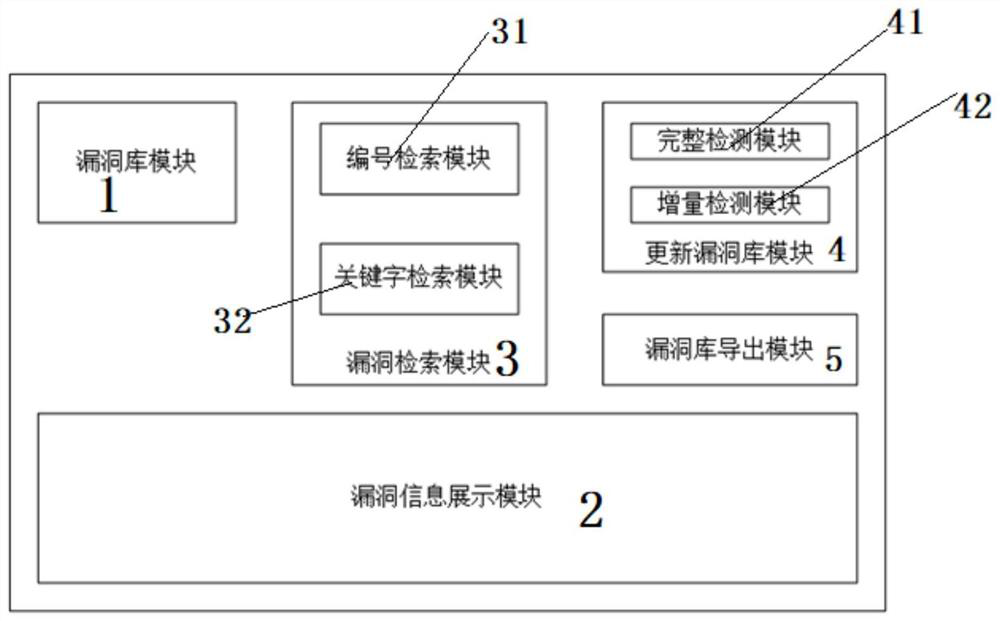
ActiveCN112822210AImprove vulnerability detection efficiencyAvoid hysteresisPlatform integrity maintainanceTransmissionVulnerability managementInformation presentation
The invention discloses a vulnerability management system based on network assets. The system comprises a vulnerability library module, a vulnerability information display module, a vulnerability retrieval module, a vulnerability library updating module and a vulnerability library exporting module; wherein the vulnerability library module classifies the detected vulnerability information; the vulnerability information display module displays specific vulnerability information under three different classifications of CNNVD, CNVD and CVE; the vulnerability retrieval module performs HTML (Hypertext Markup Language) analysis and arrangement on the screened information; the vulnerability library updating module stores the obtained useful information in a MongoDB database; the increment detection module completes increment update detection; the vulnerability library export module exports vulnerabilities. According to the method, automatic detection is performed on the network assets through the Scrapy framework, so that excessive dependence on manual detection is avoided; and then the network assets are continuously detected, and the vulnerability library is updated in time, so that the hysteresis of the database is effectively avoided, and meanwhile, the vulnerability information is favorably exported from the MongoDB database and is analyzed, and the security threat is solved.
Owner:HUANENG POWER INTERNATIONAL +1
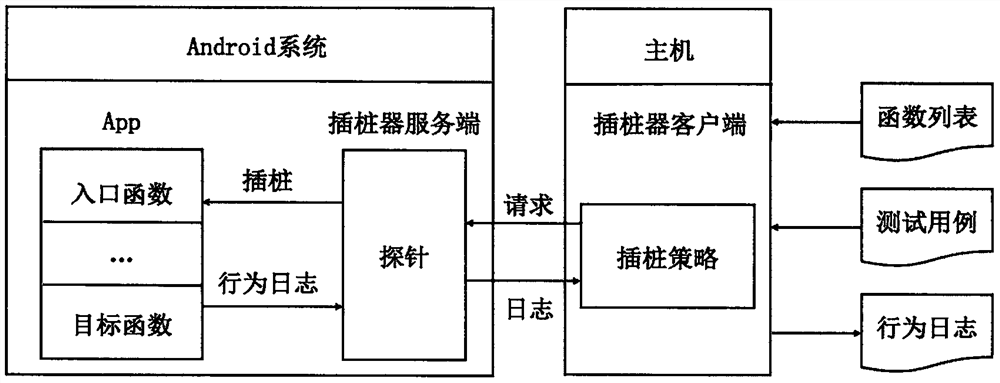
Zero false alarm detection method for Android App vulnerabilities
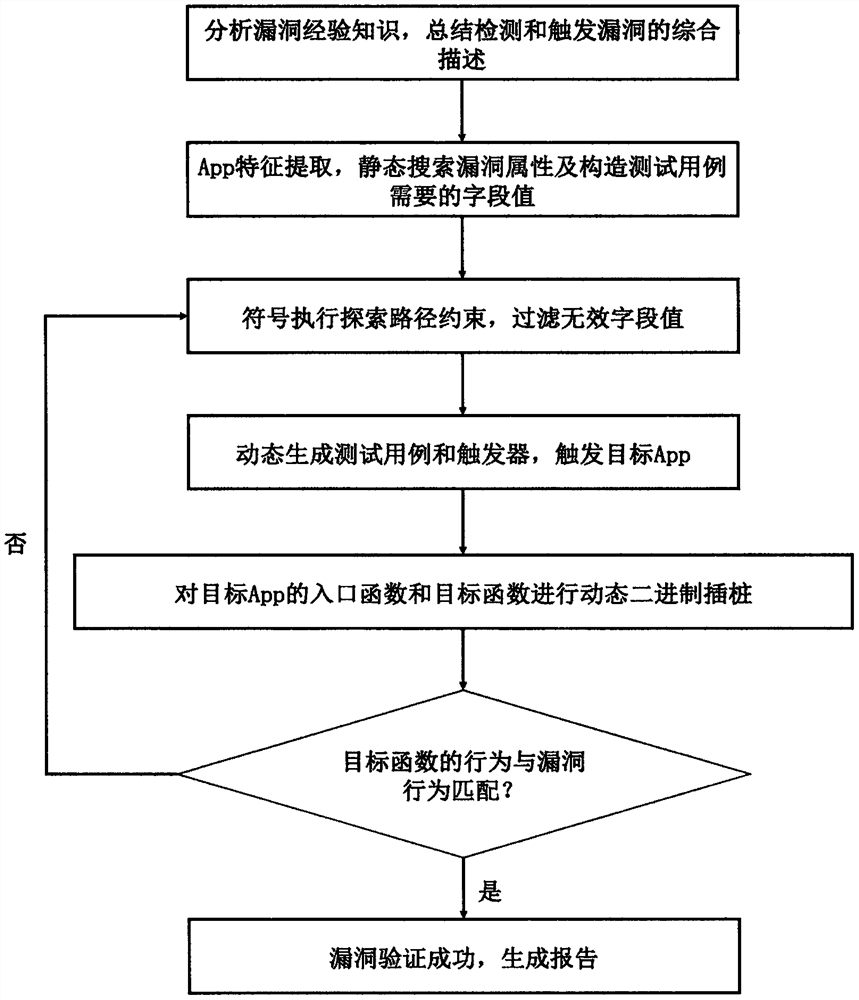
PendingCN111859380AImprove accuracySolve the high false positive ratePlatform integrity maintainanceFeature extractionAlgorithm
The invention discloses a zero false alarm detection method for Android App vulnerabilities, which comprises the following steps of: 1) analyzing experience knowledge (such as vulnerability attack paths, CVE reports and the like) of the Android App vulnerabilities, and summarizing, detecting and triggering comprehensive description of the vulnerabilities; 2) App feature extraction: statically searching vulnerability attributes and constructing field values required by a test case and a trigger; 3) performing exploration path constraints by using symbols, and filtering invalid field values in the step 2); 4) dynamically generating a test case and a trigger, and triggering the target App; 5) performing dynamic binary instrumentation on the entry function and the target function of the targetApp; 6), if the behavior of the target function is matched with the vulnerability behavior, judging that the vulnerability exists. According to the zero false alarm detection method, the informationfor detecting and triggering the vulnerability is summarized by analyzing the experience knowledge of the vulnerability; meanwhile, static analysis, symbolic execution and the dynamic binary instrumentation technology are combined for detecting and verifying the vulnerability, and the zero-false-alarm detection effect is achieved.
Owner:北京九州正安科技有限公司
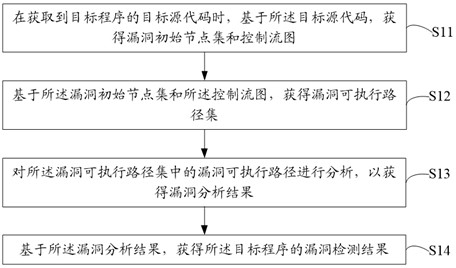
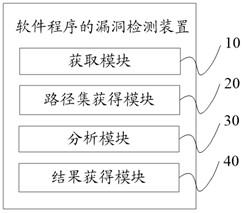
Program vulnerability detection method and device, terminal equipment and storage medium
ActiveCN113221127AImprove vulnerability detection efficiencyAnalysis data is smallPlatform integrity maintainanceCompiler constructionPathPingAlgorithm
The invention discloses a program vulnerability detection method. The method comprises the following steps: when a target source code of a target program is obtained, obtaining a vulnerability initial node set and a control flow diagram based on the target source code; obtaining a vulnerability executable path set based on the vulnerability initial node set and the control flow diagram; analyzing vulnerability executable paths in the vulnerability executable path set to obtain a vulnerability analysis result; based on the vulnerability analysis result, obtaining a vulnerability detection result of the target program. The invention further discloses a program vulnerability detection device, terminal equipment and a computer readable storage medium. By utilizing the vulnerability detection method of the program, the technical effect of improving the vulnerability detection efficiency of the program is achieved.
Owner:PENG CHENG LAB
Vulnerability detection method and device, equipment and storage medium
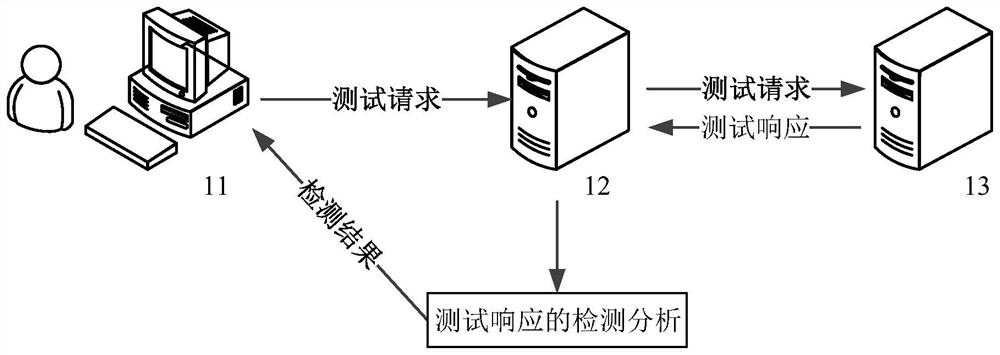
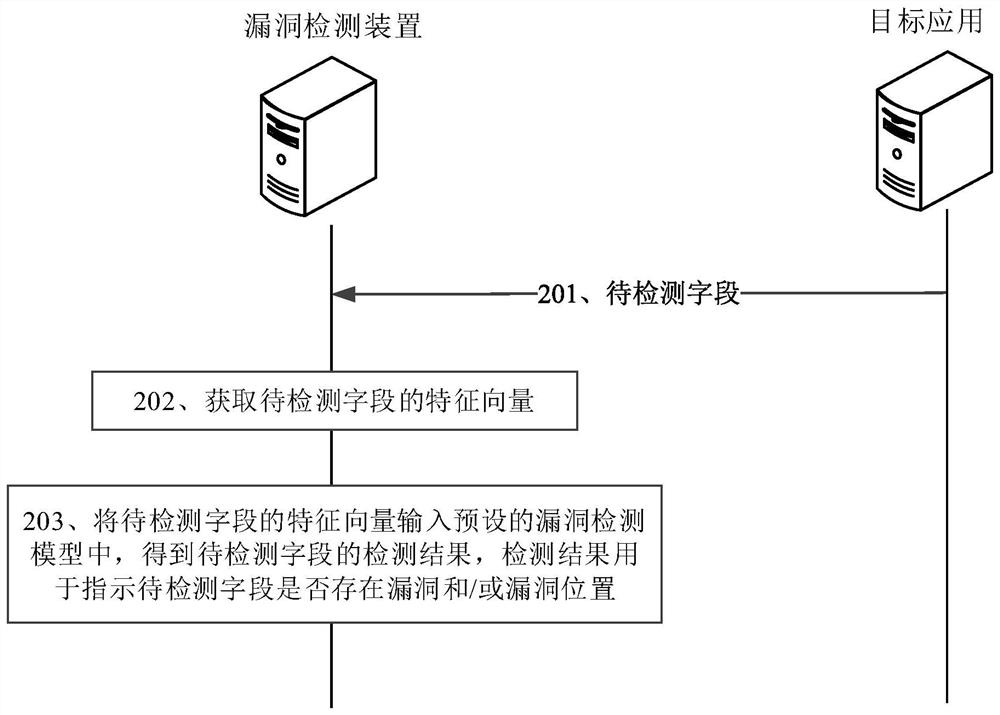
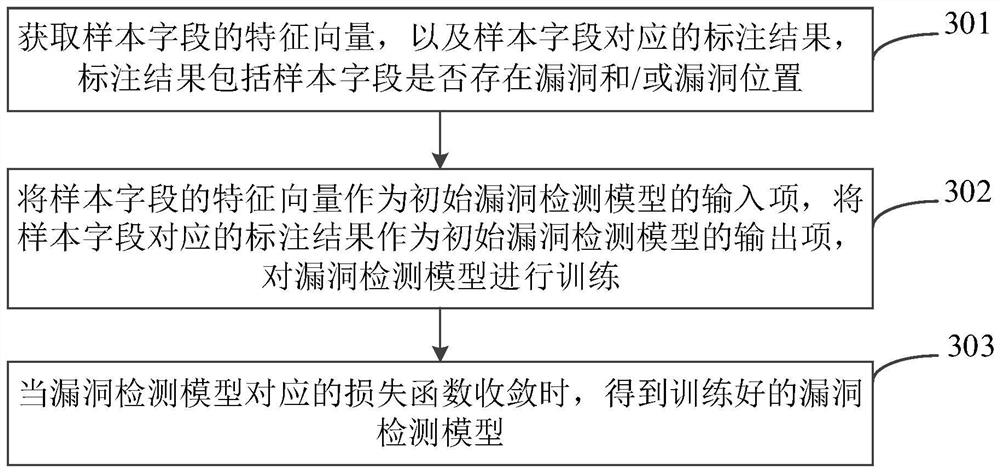
PendingCN114048480AImprove detection accuracyImprove vulnerability detection efficiencyPlatform integrity maintainanceMachine learningFeature vectorFeature extraction
The invention provides a vulnerability detection method and device, equipment and a storage medium. The method comprises the steps that after a to-be-detected field returned by a target application is received, feature extraction is conducted on the to-be-detected field, a feature vector of the to-be-detected field is obtained, the feature vector is input into a pre-trained vulnerability detection model, and a detection result of the to-be-detected field is obtained, the detection result is used for indicating whether a vulnerability and / or a vulnerability position exists in the to-be-detected field. By adopting the supervised machine learning model to perform vulnerability detection on the to-be-detected field, the detection accuracy is high. In addition, the detection process can assist testers in performing field preliminary screening, and the vulnerability detection efficiency is improved.
Owner:CHINA CONSTRUCTION BANK
Router automation vulnerability utilization method and system, and electronic device
ActiveCN109409094AImprove vulnerability detection efficiencyImprove securityPlatform integrity maintainanceThe InternetElectric equipment
The invention provides a router automation vulnerability utilization method and system and electronic equipment, and the method comprises the steps: obtaining a to-be-detected router, and determiningthe target version information of the to-be-detected router; determining a target vulnerability detection and identification method corresponding to the target version information in a router vulnerability utilization library according to the target version information; carrying out vulnerability detection on the to-be-detected router through a target vulnerability detection and identification method; and under the condition that the to-be-detected router has the vulnerability through detection, performing vulnerability utilization attack on the to-be-detected router through the target vulnerability utilization code corresponding to the target vulnerability detection and identification method. According to the invention, the vulnerability of the to-be-detected router can be automatically identified and utilized based on the router vulnerability utilization library, so that the router vulnerability detection efficiency is improved, the security of the Internet of Things equipment is improved, and the technical problem of low efficiency of an existing manual router vulnerability detection mode is relieved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
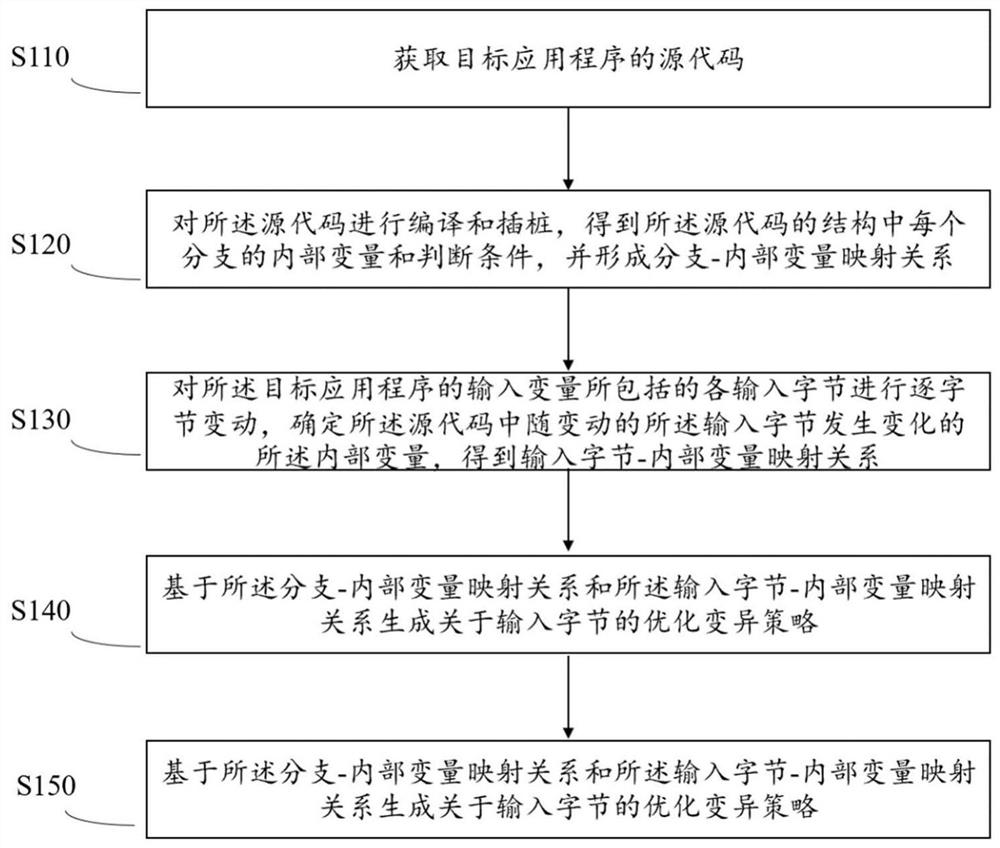
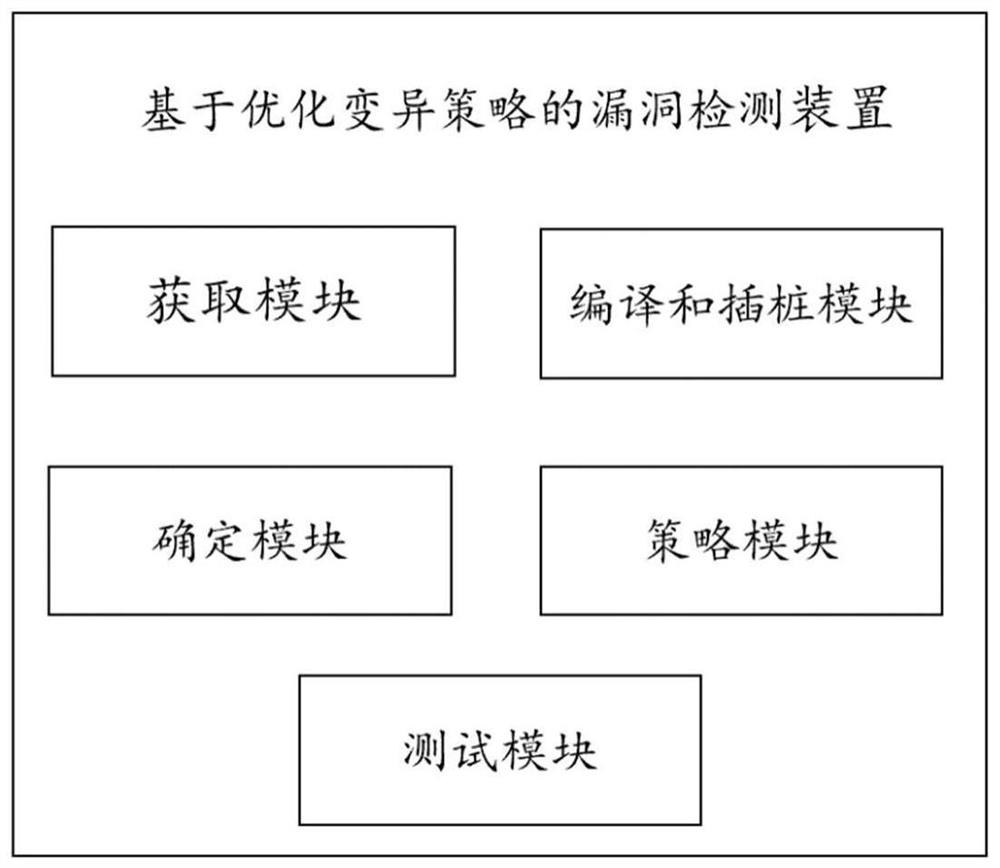
Vulnerability detection method and device based on optimization variation strategy, equipment and medium
ActiveCN112861134AEnsure safetyVulnerability detection is fastPlatform integrity maintainanceAlgorithmApplication procedure
The invention provides a vulnerability detection method and device based on an optimization variation strategy, equipment and a medium. The method comprises the following steps: acquiring a source code of a target application program; compiling and instrumenting the source code to obtain an internal variable and a judgment condition of each branch in the structure of the source code, and forming a branch-internal variable mapping relationship; performing byte-by-byte change on each input byte included in an input variable of the target application program, determining an internal variable which changes along with the changed input byte in the source code, and obtaining an input byte-internal variable mapping relationship; based on the branch-internal variable mapping relationship and the input byte-internal variable mapping relationship, generating the optimization variation strategy about the input bytes; and performing fuzzy testing on the source code based on the optimization variation strategy to obtain a vulnerability detection result. According to the method and the device, rapid vulnerability detection of the source code of the application program is realized, the security of the application program is ensured from the source, and the vulnerability detection efficiency is improved.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
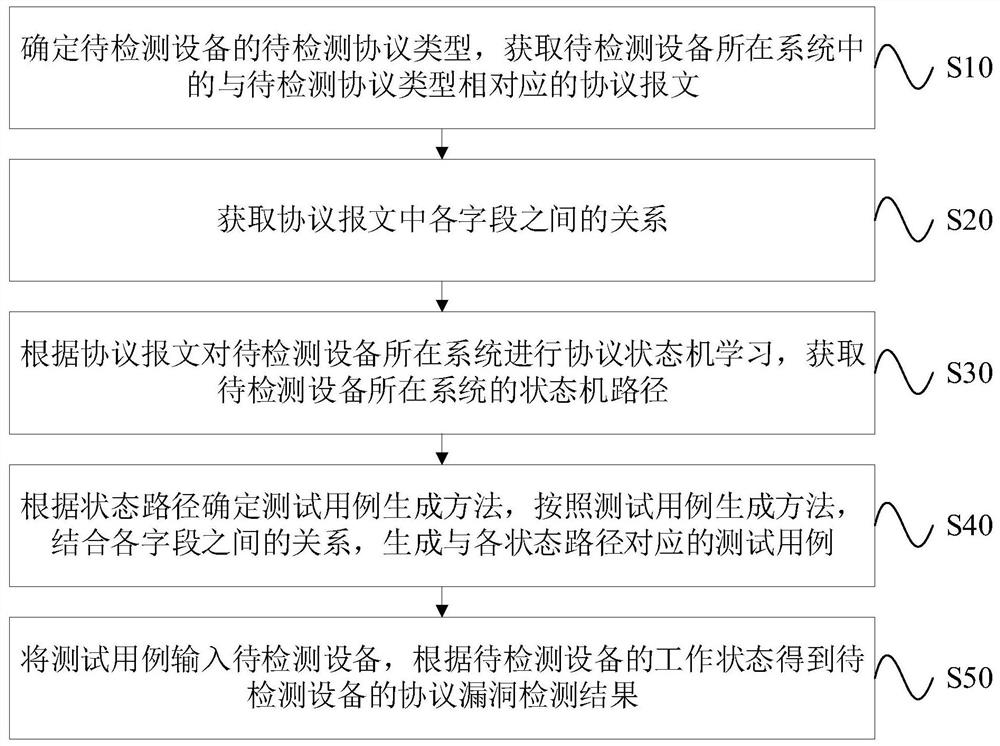
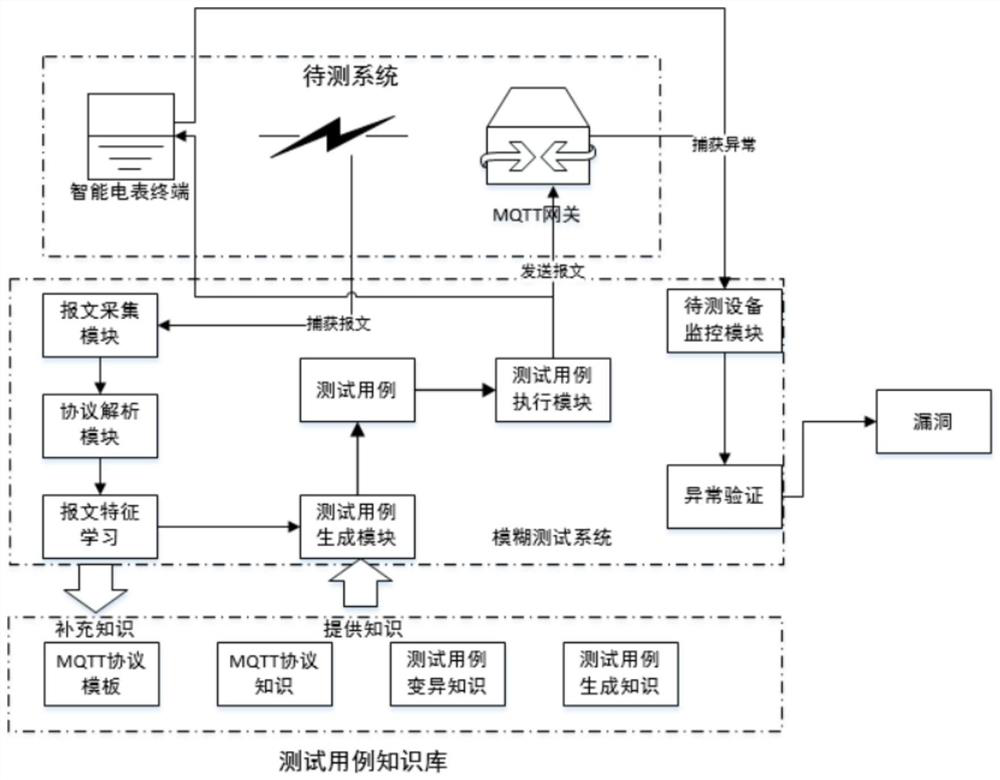
Equipment protocol vulnerability detection method and device
ActiveCN113572760AIncrease coverageImprove detection efficiencySoftware testing/debuggingPlatform integrity maintainancePathPingProtocol for Carrying Authentication for Network Access
The invention provides an equipment protocol vulnerability detection method and device, and the method comprises the steps: determining a to-be-detected protocol type of to-be-detected equipment, and obtaining a protocol message corresponding to the to-be-detected protocol type in a system where the to-be-detected equipment is located; obtaining a relationship between fields in the protocol message; performing protocol state machine learning on a system where the to-be-detected equipment is located according to the protocol message, and obtaining a state machine path of the system where the to-be-detected equipment is located; determining a test case generation method according to the state paths, and generating test cases corresponding to the state paths according to the test case generation method in combination with the relationship between the fields; and inputting the test case into the to-be-detected equipment, and obtaining a protocol vulnerability detection result of the to-be-detected equipment according to the working state of the to-be-detected equipment. According to the method and the device, the test cases are generated in combination with the relationship among the fields in the protocol message and the state path, so that a large number of redundant test cases are prevented from being generated, the code coverage rate is improved, and the vulnerability detection efficiency is improved.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
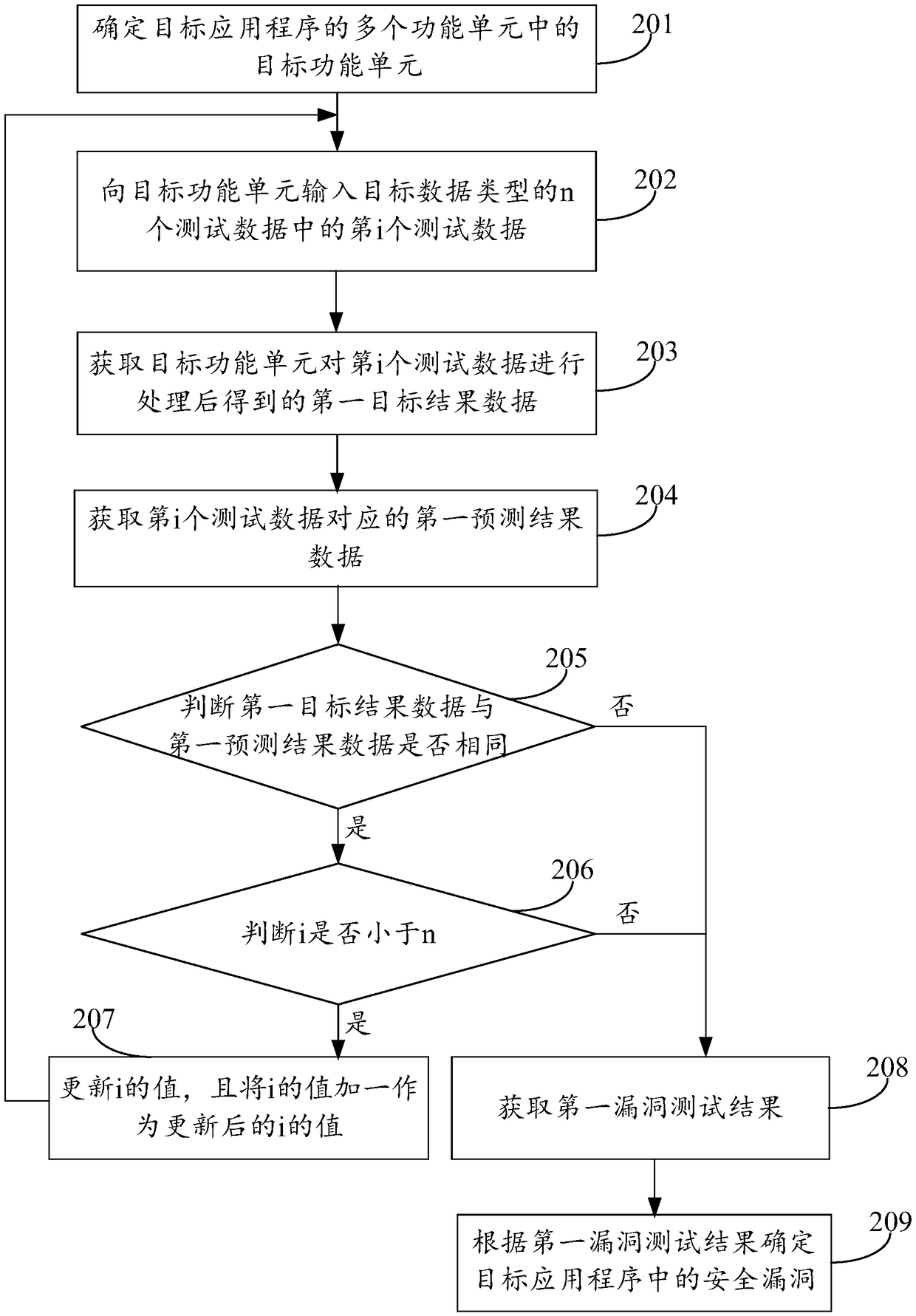
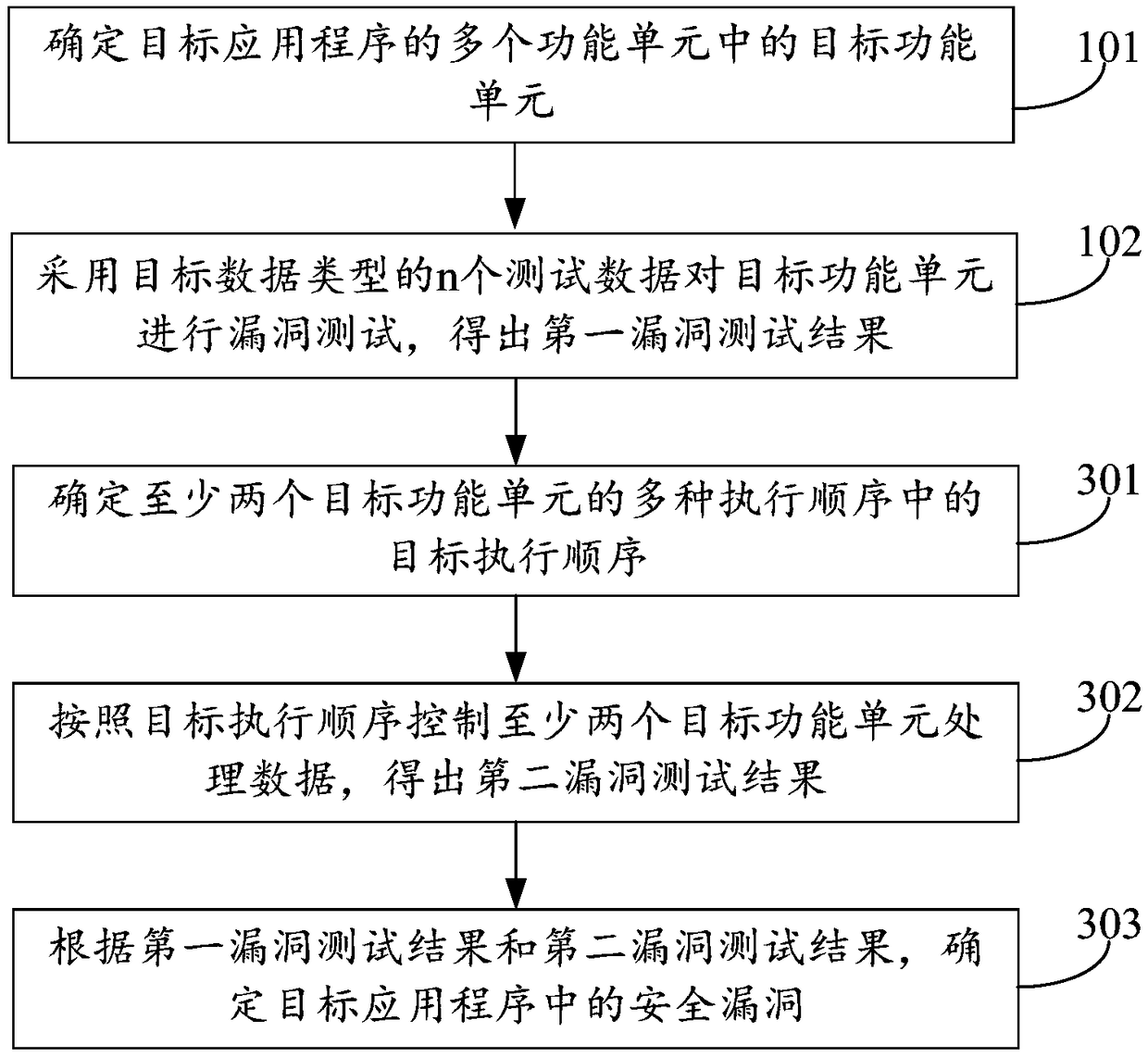
Vulnerability mining method and device, and readable storage medium
InactiveCN109376082AImprove securityImprove vulnerability detection efficiencySoftware testing/debuggingPlatform integrity maintainanceApplication securityData type
The invention discloses a vulnerability mining method and device and a readable storage medium, belonging to the field of software security. The method includes: determining a target functional unit among a plurality of functional units of a target application; using n test data of target data type to test the vulnerability of target functional unit to obtain a first vulnerability test result, wherein, the target functional unit is used for processing the data of the target data type, and the value of n is within the range of the experience value, and the experience value range is obtained according to the numb of times the data of the same data type is processed before the security vulnerability of the functional unit occurs; and based on the results of the first vulnerability test, a security vulnerability in the target application is identified. The present disclosure solves the problem of lower application security due to fewer security vulnerabilities of the excavated application.The present disclosure is used for security vulnerability mining.
Owner:BEIJING XIAOMI INTELLIGENT TECH CO LTD
Bug checking method and device and continuously integrated code bug checking method and device
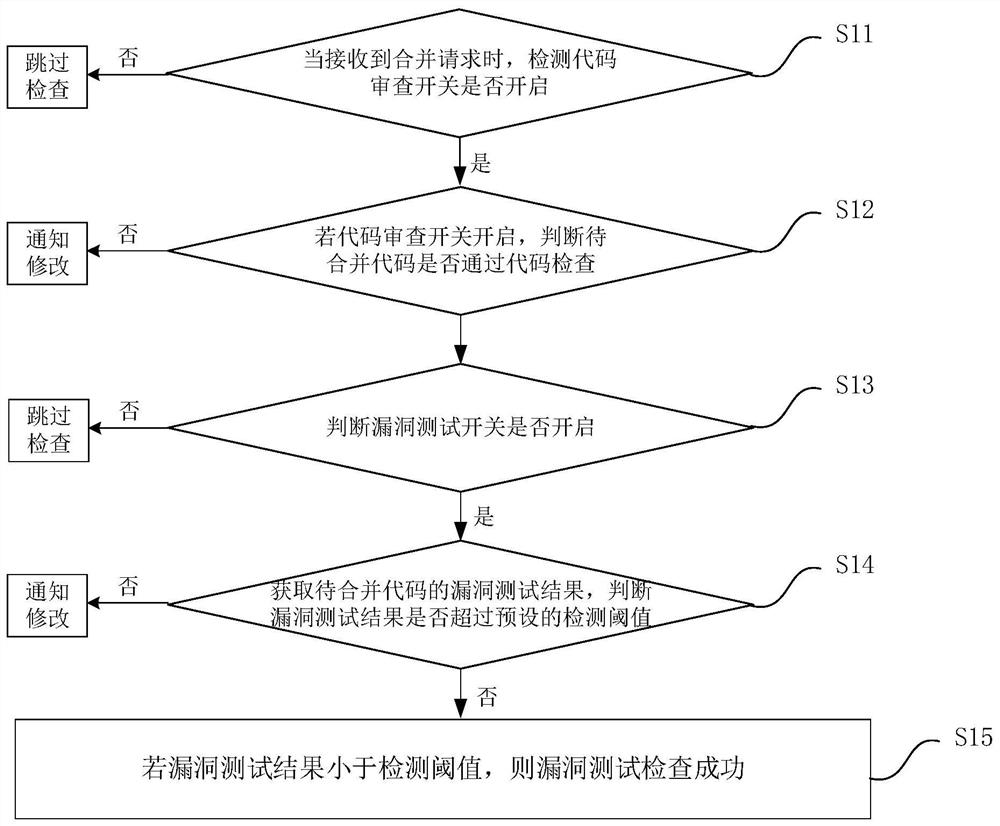
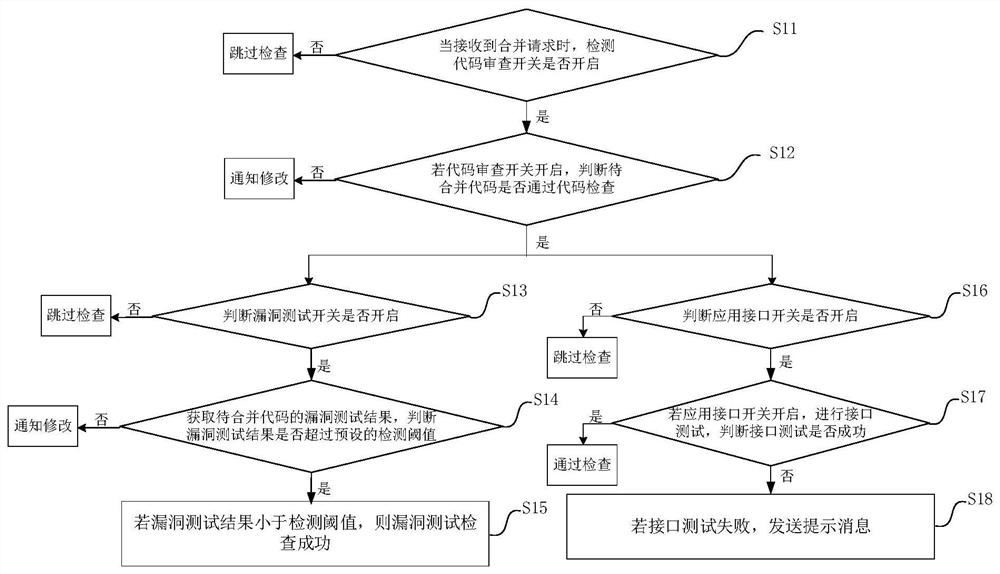
ActiveCN111783104AImprove vulnerability detection efficiencyAvoid Vulnerability Scanning ChecksPlatform integrity maintainanceDetection thresholdCode review
The invention discloses a vulnerability checking method and device and a vulnerability checking method and device for continuously integrating codes, and the method comprises the steps: detecting whether a code checking switch is turned on or not when a merging request is monitored; if the code review switch is turned on, judging whether the to-be-merged code passes code review or not; if the codecheck is passed, judging whether a vulnerability test switch is turned on; if the vulnerability test switch is turned on, obtaining a vulnerability test result of the to-be-merged code, and judging whether the vulnerability test result exceeds a preset detection threshold value or not; and if the vulnerability test result is smaller than the detection threshold, determining that vulnerability test check succeeds. By implementing the method and the device, the problems of high hardware resource consumption and server jamming caused by centralized triggering of vulnerability scanning due to large task concurrency at the same time are avoided, the situation that hardware and software resources are wasted when a project without code change is executed is avoided, the vulnerability detection efficiency is improved, the code integration efficiency is improved, and the labor cost is reduced.
Owner:北京自如信息科技有限公司
Out-of-authority vulnerability automatic detection method, equipment and medium
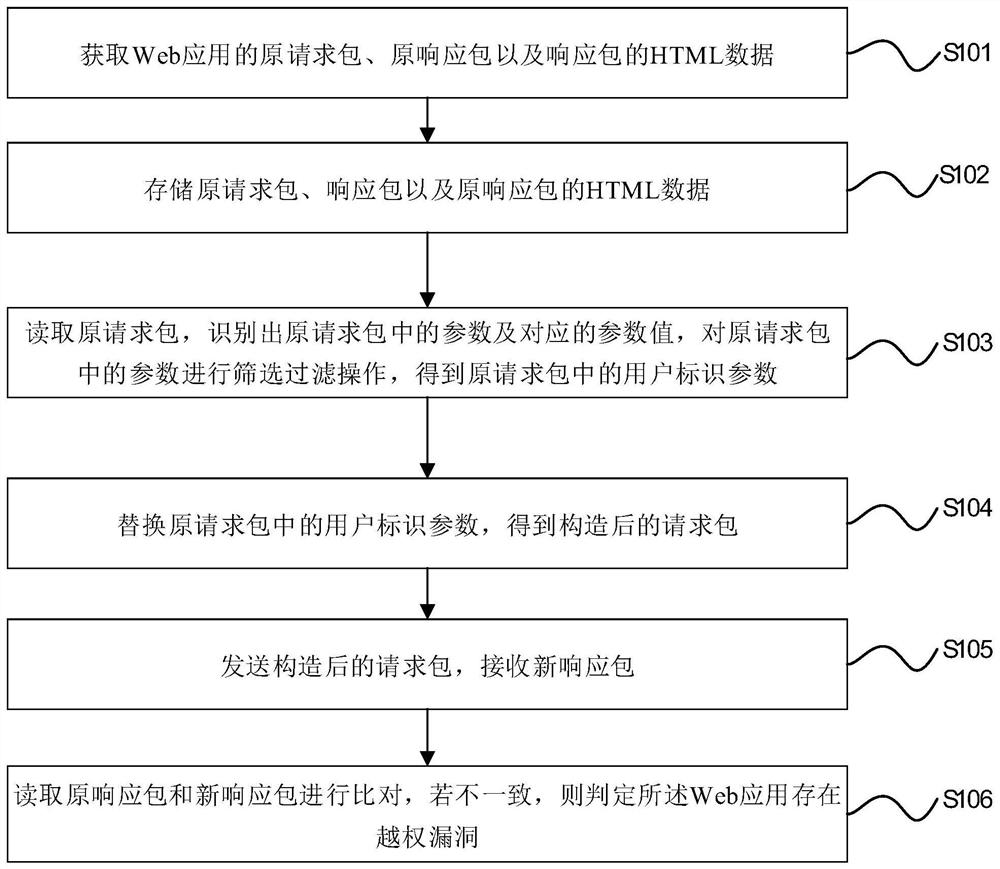
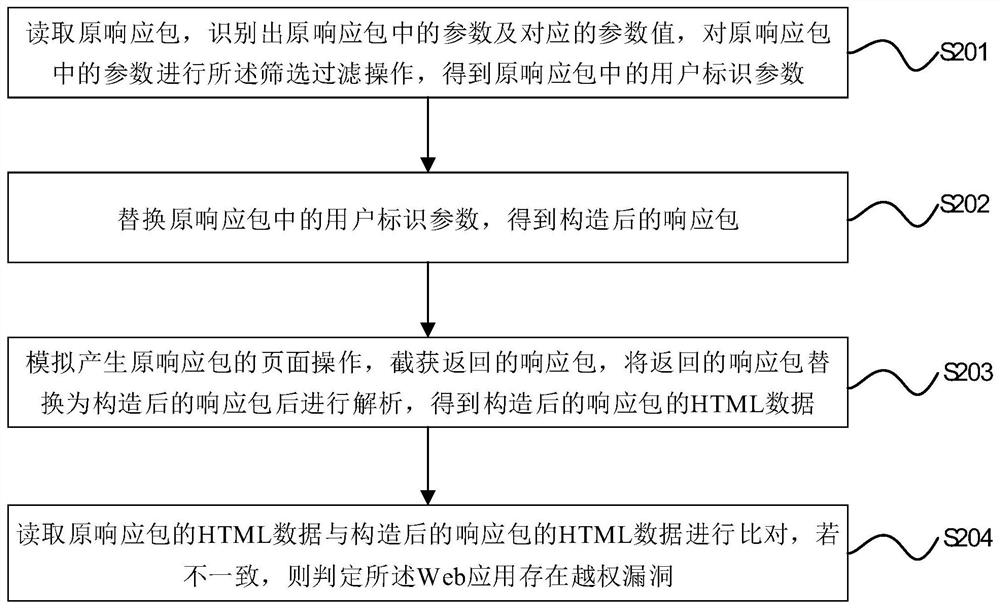
PendingCN112464250AIncrease success rateImprove vulnerability detection efficiencyPlatform integrity maintainanceTransmissionWeb applicationData mining
The invention discloses an unauthorized vulnerability automatic detection method, electronic equipment and a computer storage medium, relates to the technical field of network security, and aims to solve the problem of low unauthorized vulnerability detection efficiency. The method comprises the following steps: acquiring an original request packet and an original response packet of a Web application and HTML data of the original response packet; storing the HTML data of the original request packet, the original response packet and the original response packet; reading the original request packet, identifying parameters in the original request packet and corresponding parameter values, and performing screening and filtering operation on the parameters in the original request packet to obtain user identification parameters in the original request packet; replacing the user identification parameters in the original request packet to obtain a constructed request packet; sending the constructed request packet, and receiving a new response packet; and reading the original response packet and the new response packet for comparison, and if the original response packet and the new responsepacket are inconsistent, judging that the Web application has an unauthorized vulnerability.
Owner:GUANGTONGTIANXIA NETWORK TECH CO LTD
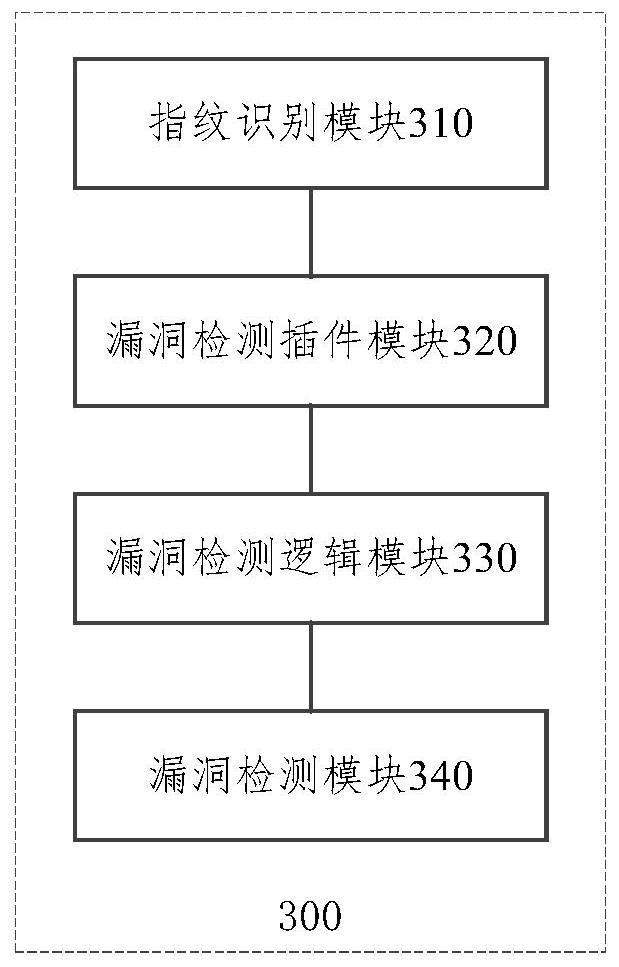
Vulnerability detection method, vulnerability detection model and vulnerability detection device
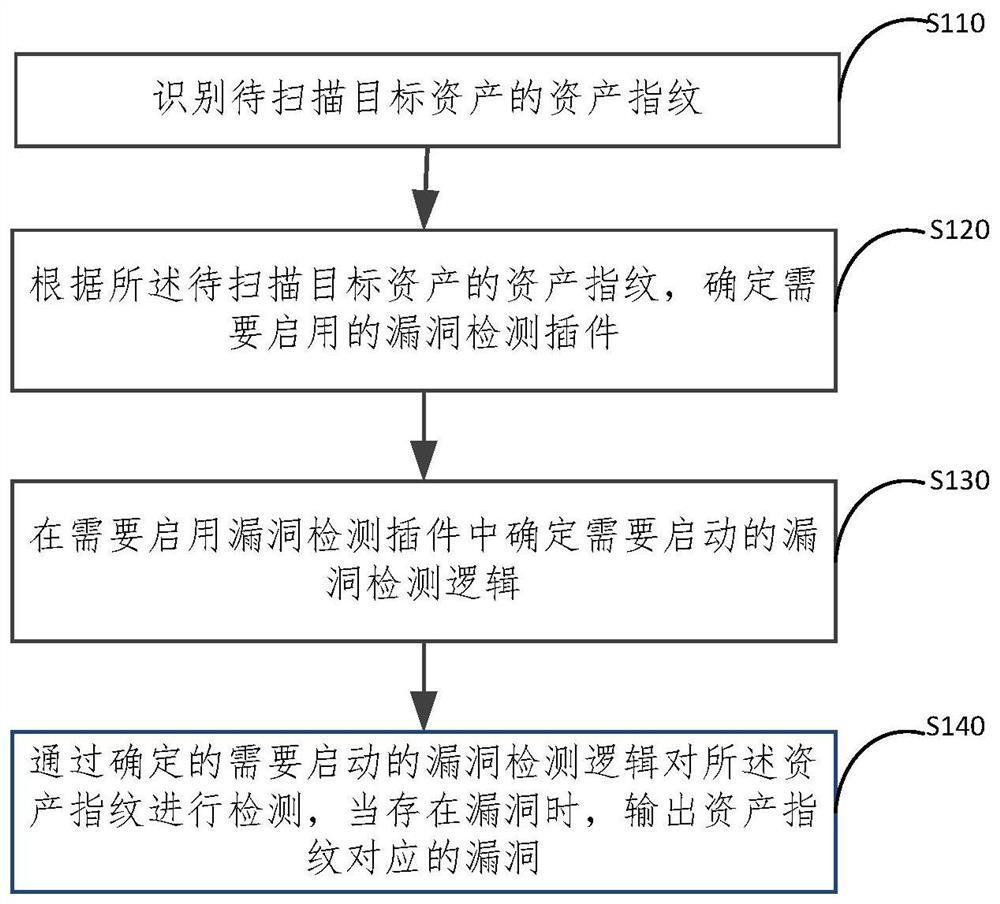
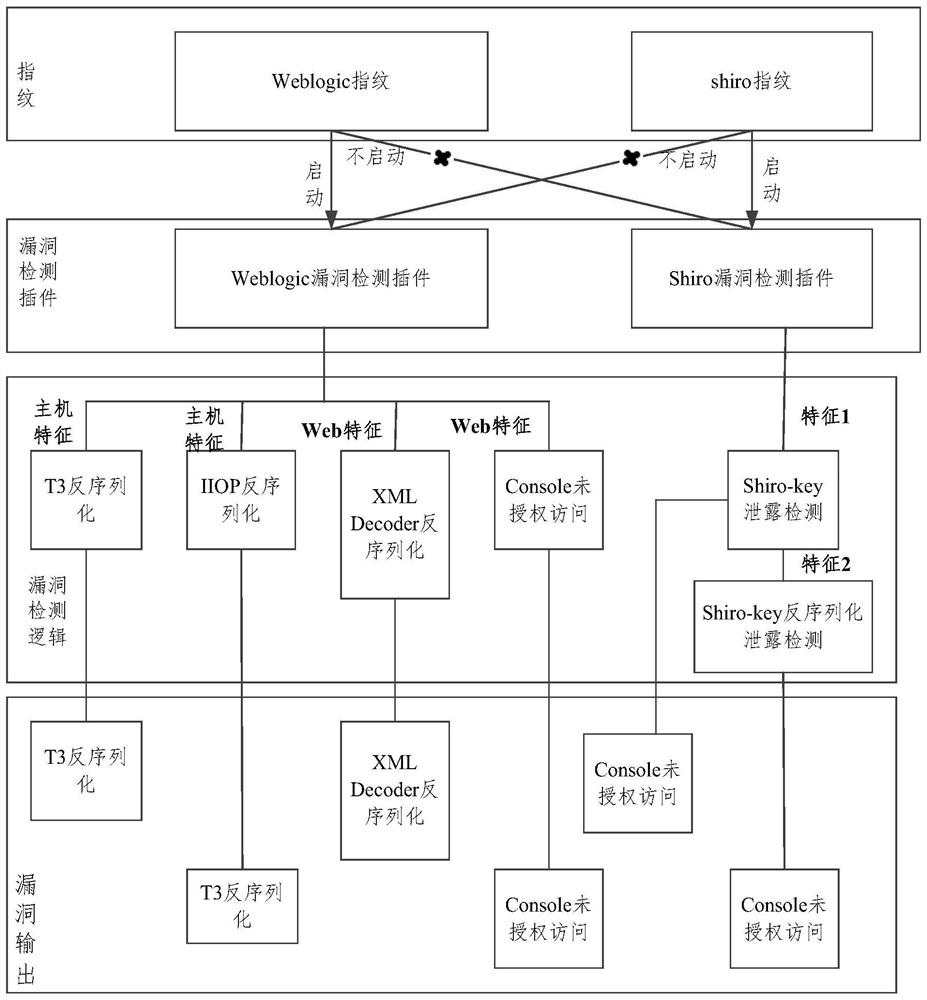
PendingCN113392406AAvoid joiningImprove vulnerability detection efficiencyCharacter and pattern recognitionPlatform integrity maintainanceReliability engineeringVulnerability detection
The embodiment of the invention provides a vulnerability detection method, a vulnerability detection model and a vulnerability detection device. The vulnerability detection method comprises the following steps: identifying an asset fingerprint of a to-be-scanned target asset; according to the asset fingerprint of the to-be-scanned target asset, determining a vulnerability detection plug-in needing to be started; determining vulnerability detection logic needing to be started in the vulnerability detection plug-in needing to be started; and detecting the asset fingerprint through the determined vulnerability detection logic needing to be started, and outputting the vulnerability corresponding to the asset fingerprint when the vulnerability exists. According to the method and the device, the vulnerability detection plug-ins are intelligently distributed and the corresponding vulnerability detection logic is dynamically scheduled in the vulnerability detection process, only effective vulnerability detection is performed, the addition of invalid vulnerability detection is avoided, and the vulnerability detection efficiency is improved.
Owner:BEIJING CHAITIN TECH CO LTD
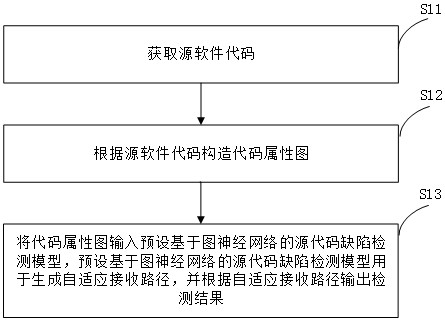
Software source code defect detection method and device
ActiveCN114385512AImprove vulnerability detection efficiencySoftware testing/debuggingAlgorithmTheoretical computer science
The invention relates to a software source code defect detection method and device, and the method comprises the steps: obtaining a source software code, constructing a code attribute graph according to the source software code, inputting the code attribute graph into a preset source code defect detection model based on a graph neural network, the source code defect detection model based on the graph neural network is preset to be used for generating the self-adaptive receiving path, and the detection result is output according to the self-adaptive receiving path, so that the influence of irrelevant code information can be reduced, and the code vulnerability detection efficiency can be improved.
Owner:北京北大软件工程股份有限公司
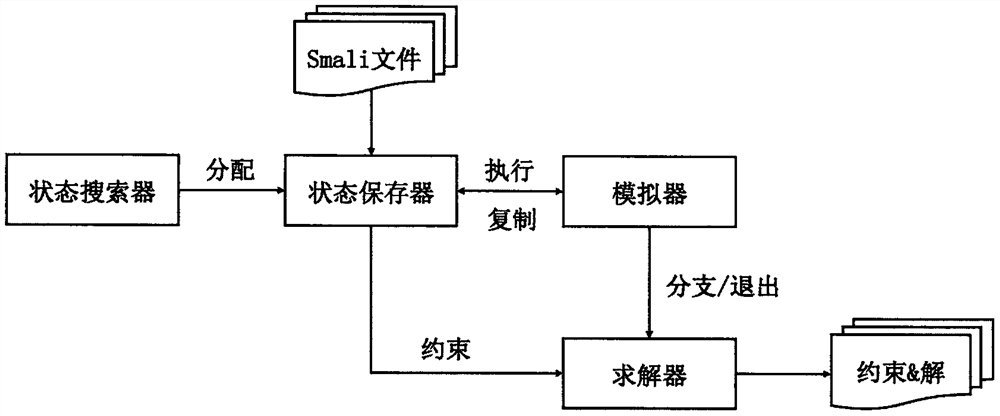
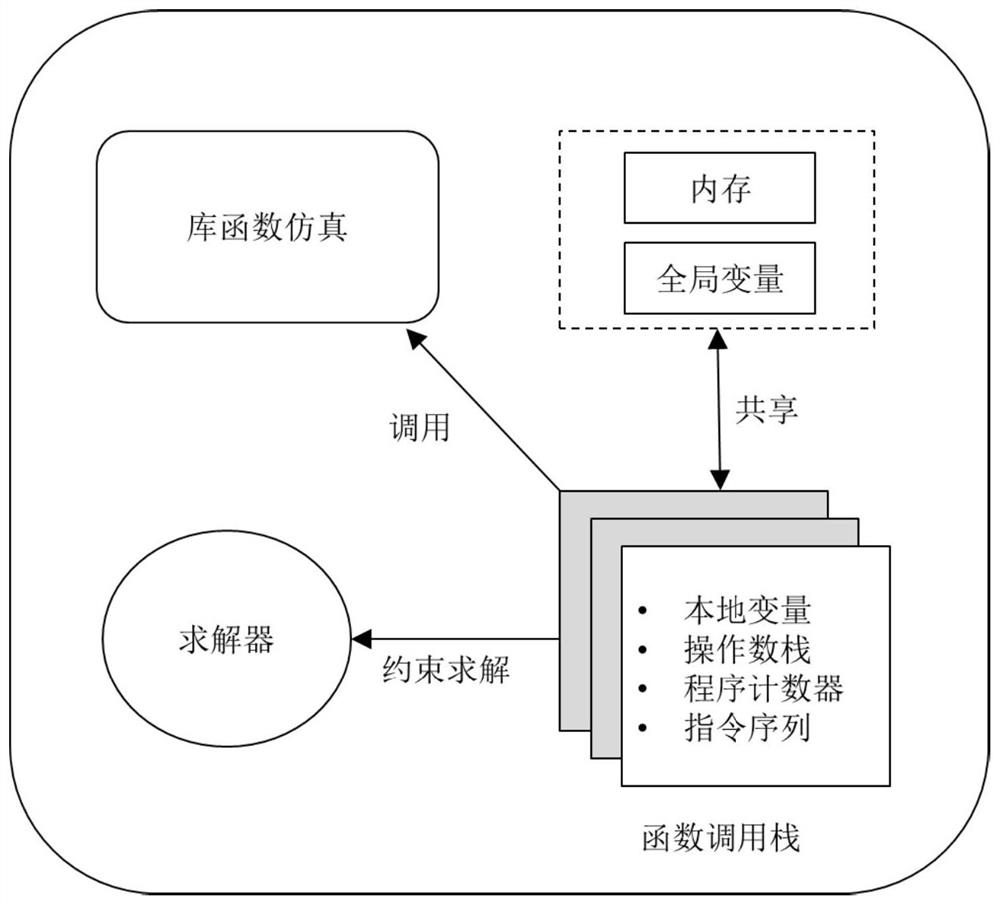
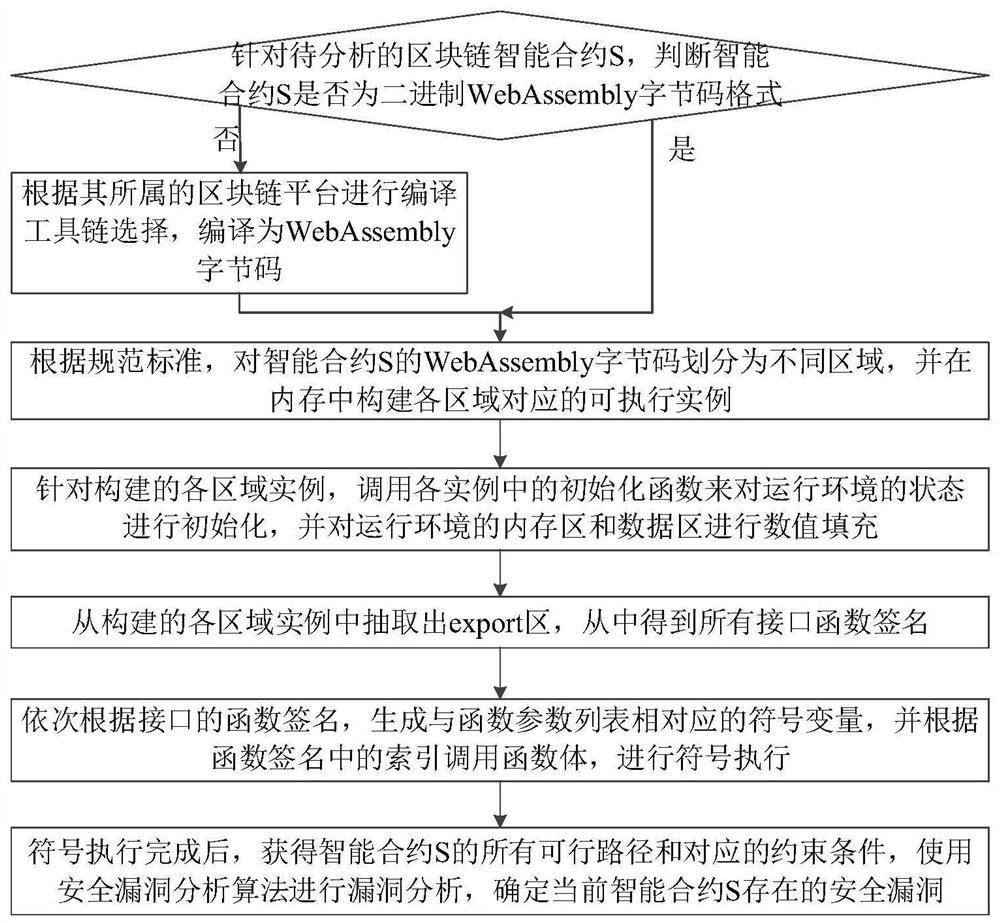
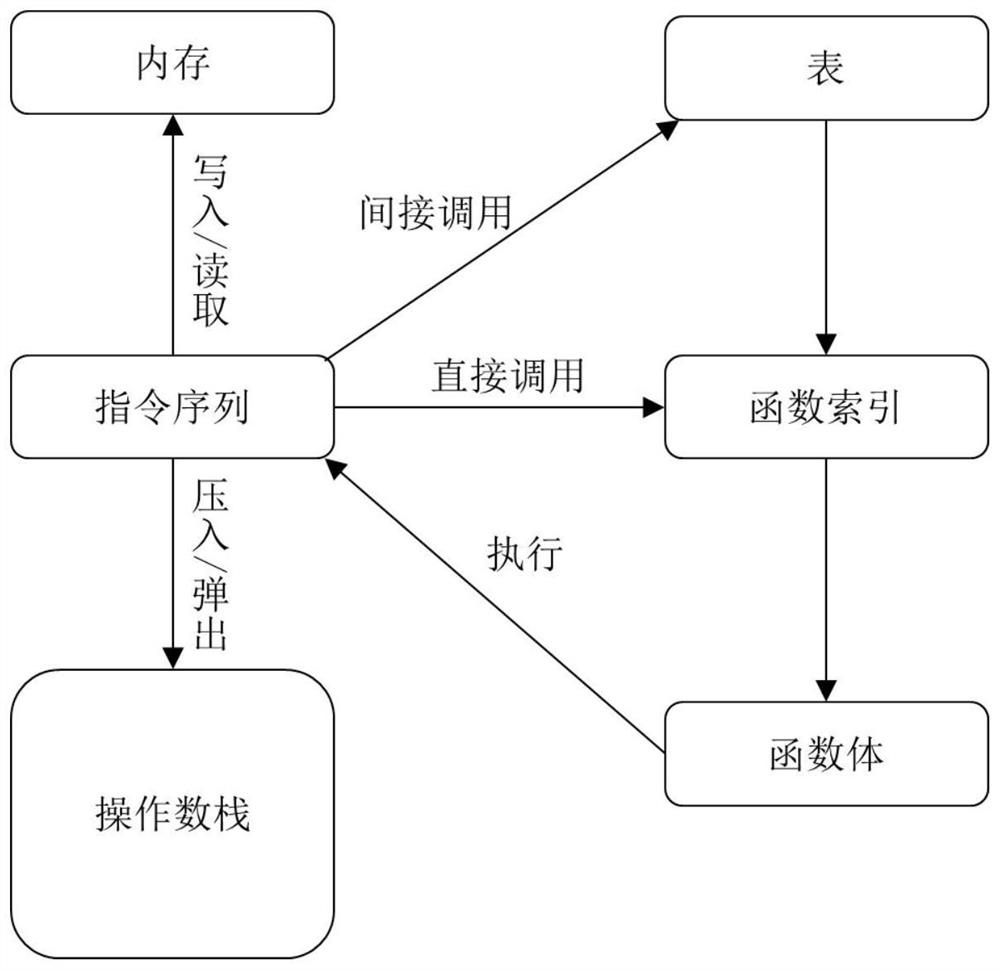
WASM smart contract vulnerability detection method based on symbolic execution
ActiveCN113672515AImprove vulnerability detection efficiencyRealize smart contract security vulnerability detection and analysisSoftware testing/debuggingEnergy efficient computingPathPingTerm memory
The invention provides a WASM smart contract vulnerability detection method based on symbolic execution, and belongs to the technical field of software testing. The method comprises the steps: constructing executable examples through WebAssembly byte codes of a to-be-analyzed smart contract, calling an initialization function in each example to initialize the state of a running environment, and filling numerical values of a memory area and a data area of the running environment; and further calling a function body to perform symbolic execution according to an index in a function signature, traversing an execution path of the byte code level smart contract to explore a possible state of the smart contract during actual operation, and analyzing potential security vulnerabilities of the smart contract according to the state. In addition, a general function interface and a special function are used for realizing simulation support for library functions of different block chain platforms, so that the integrity of a symbolic execution process is ensured. By setting a circulation upper limit and a branch access upper limit, the path explosion problem and the coverage rate problem in symbolic execution are solved.
Owner:BEIHANG UNIV
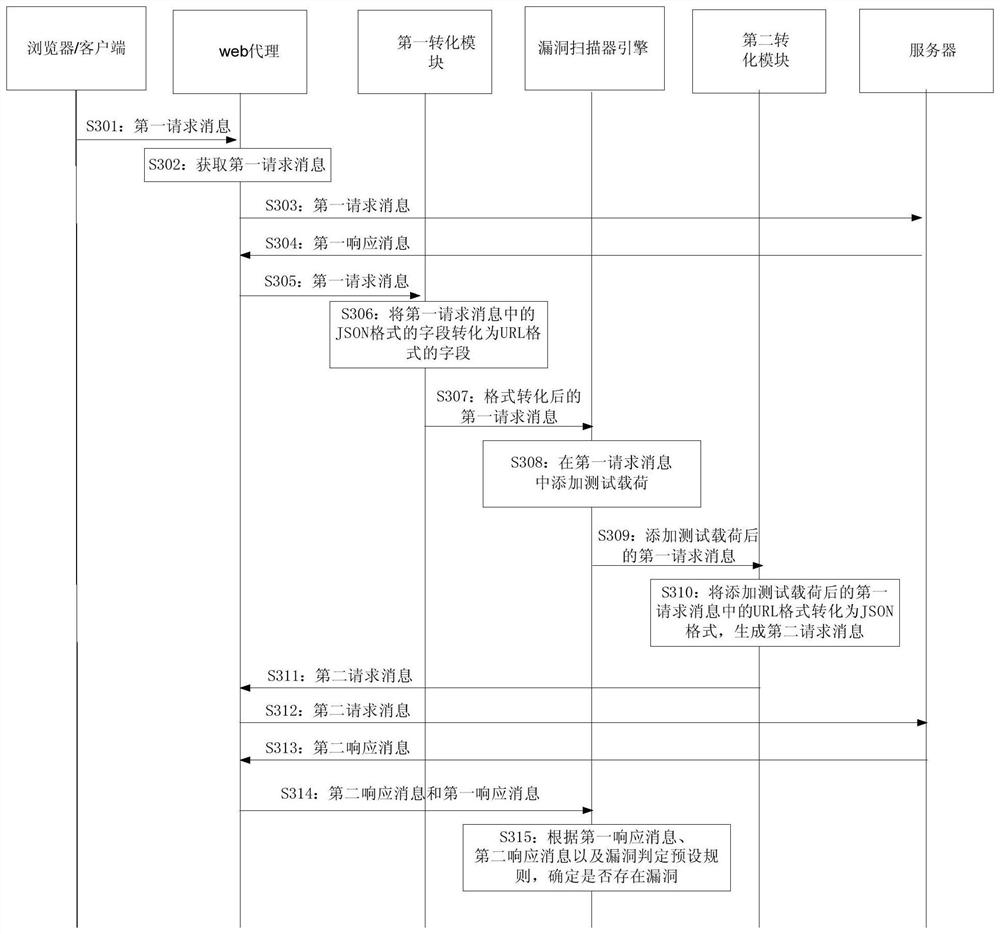
Vulnerability detection method and device
ActiveCN107948120BReduce development costsImprove vulnerability detection efficiencyTransmissionJSONServer
The present application provides a vulnerability detection method and device. According to the vulnerability detection method and device of the invention, a step for converting a field of the JSON format in a first request message to a field of the URL format is added in a vulnerability detection process, and therefore, with an existing URL format-based vulnerability scanner engine unmodified, a test load is added to the field of the URL format, and the test load-added field in the URL format is converted into a field of the JSON format; a second request message is generated and is sent to a server, so that the server can identify the second request message; a second response message which is corresponding to the second request message and returned by the server is directly compared with afirst response message which is returned by the server after a first request message is sent to the server; and a vulnerability detection result is obtained on the basis of vulnerability judgment reset rules in a vulnerability knowledge base; and thus, JSON format-based automatic vulnerability detection is realized, development costs are saved, and vulnerability detection efficiency can be improved.
Owner:ALIBABA GRP HLDG LTD
Weblogic deserialization vulnerability scanning detection method and tool
InactiveCN114826723AImprove vulnerability detection efficiencyImprove detection efficiencySecuring communicationEmbedded systemVulnerability scanning
The invention discloses a Weblogic deserialization vulnerability scanning detection method and tool, the tool comprises a vulnerability detection tool body, a vulnerability scanning host, a vulnerability detection module and a deserialization processing module, the vulnerability detection tool body is internally provided with the vulnerability scanning host, the vulnerability scanning host is connected with the deserialization processing module, and the deserialization processing module is connected with the vulnerability detection module. The input end of the vulnerability scanning host is connected with the input end of the vulnerability detection server, and the deserialization processing module is adopted to initialize the vulnerability scanning interface, so that the detection interface, the domain name address, the detection result and the user instruction are recovered to the initial running state at the same time; by adopting the mode, the detection interface, the domain name address, the detection result and the user instruction can be in the initial state before each vulnerability scanning, so that the vulnerability scanning detection tool does not need to be initialized by manually inputting the instruction, and the subsequent vulnerability detection efficiency of other Weblogic servers is effectively improved.
Owner:厦门农芯数字科技有限公司
Vulnerability detection method, device, storage medium and electronic equipment
ActiveCN112528296BGuaranteed accuracyImprove vulnerability detection efficiencyPlatform integrity maintainanceTransmissionDatabaseUser-defined function
The invention discloses a vulnerability detection method, device, storage medium and electronic equipment in a cloud technology scene, and specifically, it also relates to technologies such as protection in the field of cloud security. Wherein, the method includes: calling the built-in probe function of the self-defined function in the target system to detect the first data, so as to obtain the first detection result; when the first detection result indicates that the first data is normal, use the self-defined function to process The first data to obtain the second data; when the second data is returned to the custom function, call the probe function to detect the second data to obtain the second detection result, wherein the second detection result is used to indicate the target system Whether there is a vulnerability. The invention solves the technical problem of low loophole detection efficiency.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A port vulnerability detection method, terminal and computer readable medium
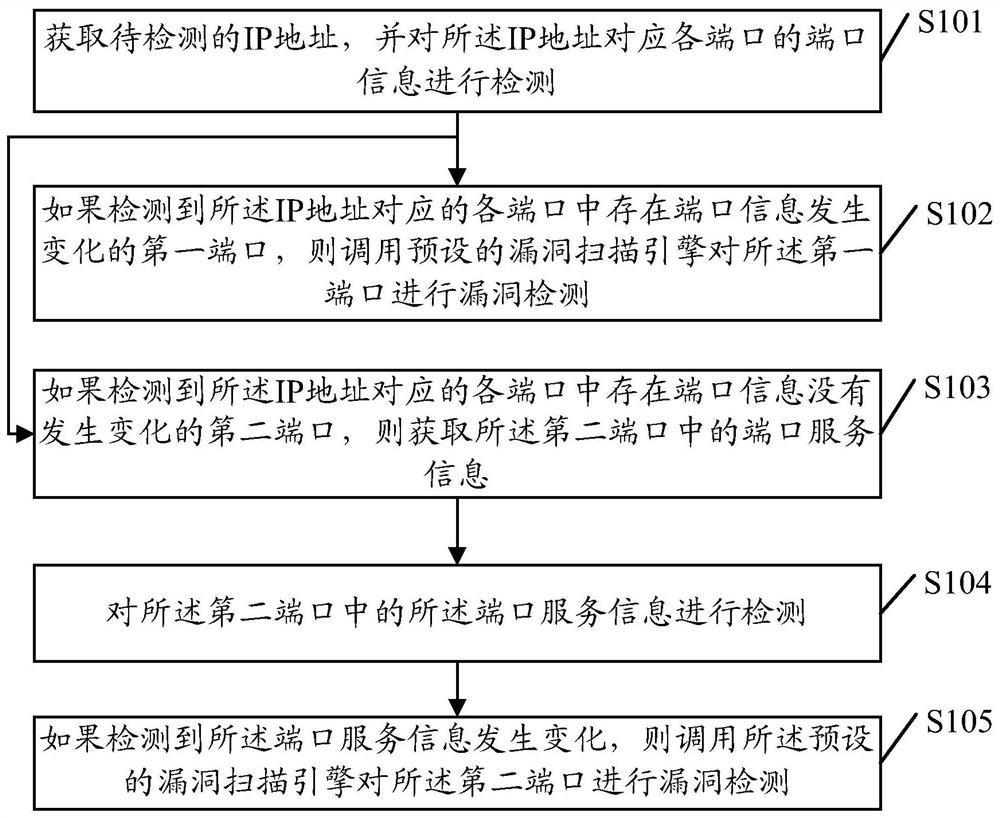
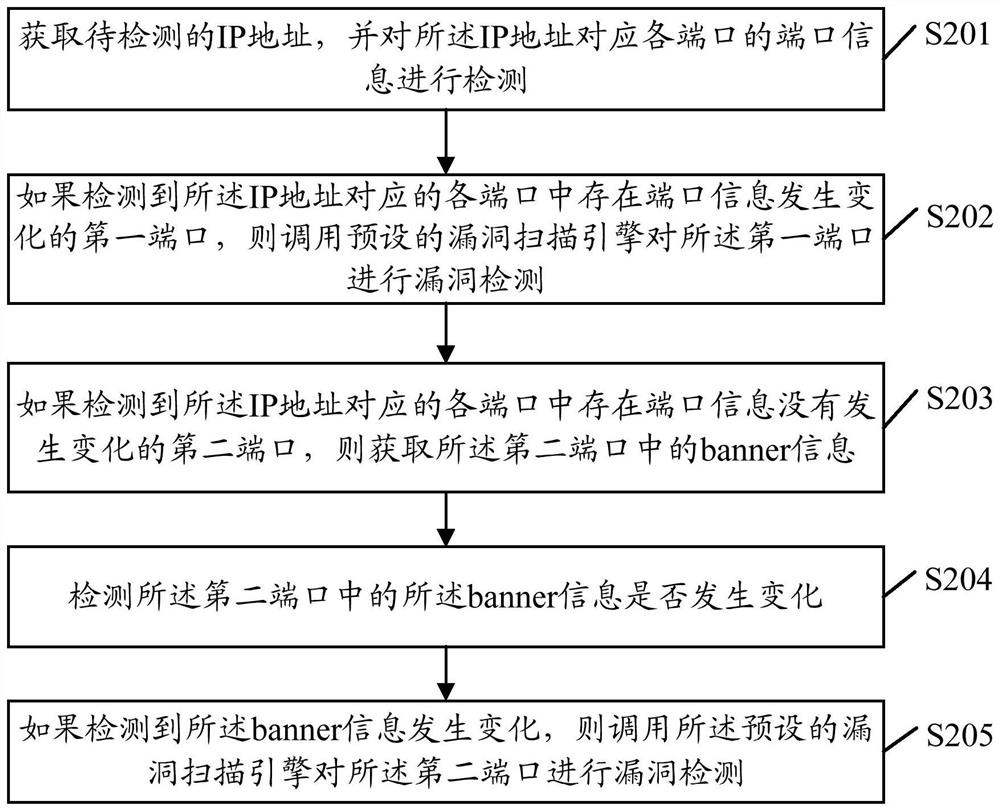
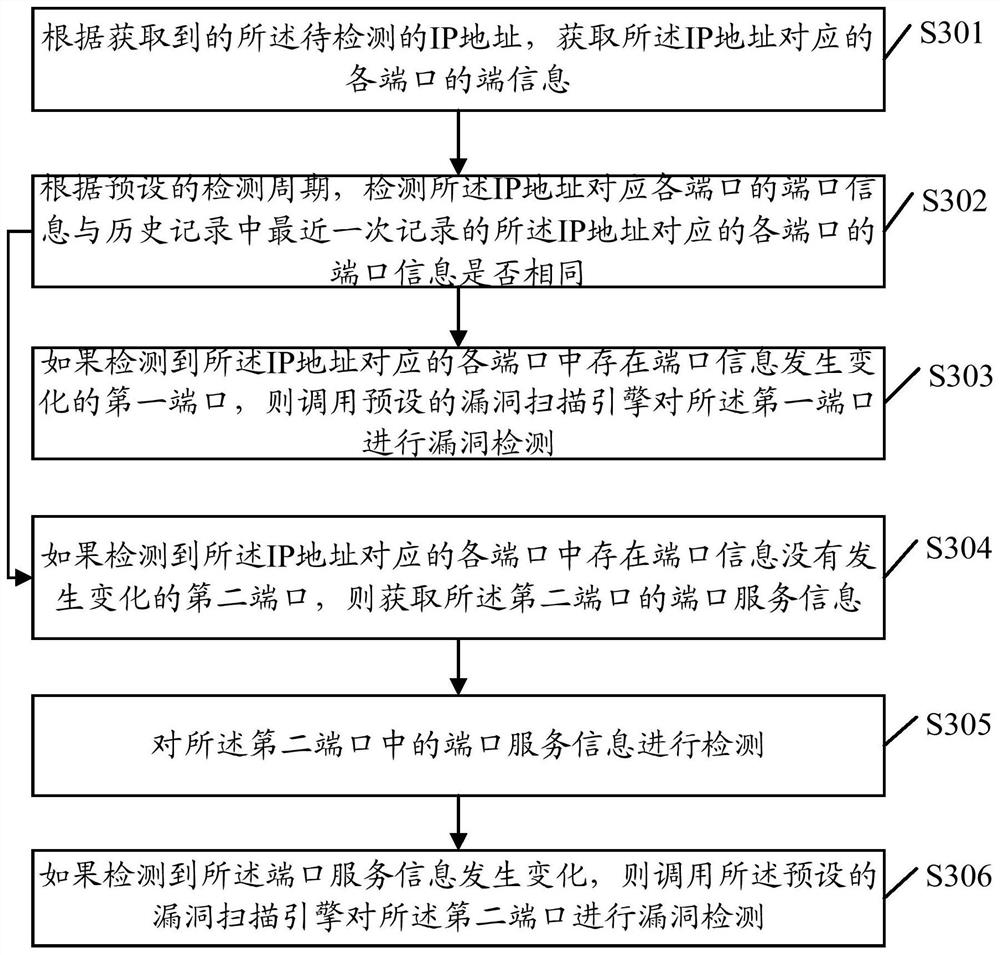
ActiveCN109067738BImprove vulnerability detection efficiencyEncryption apparatus with shift registers/memoriesIp addressService information
Embodiments of the present invention provide a port vulnerability detection method, a terminal, and a computer-readable medium. The method includes: obtaining an IP address to be detected, and detecting the port information of each port corresponding to the IP address; If there is a first port whose port information changes in each port corresponding to the IP address, then call the preset vulnerability scanning engine to detect the vulnerability of the first port; if it is detected that in each port corresponding to the IP address There is a second port whose port information has not changed, then obtain port service information in the second port; detect the port service information in the second port; if it is detected that the port service information has changed , the preset vulnerability scanning engine is invoked to detect the vulnerability of the second port, which realizes the vulnerability detection of the port whose port information changes, and improves the efficiency of vulnerability detection.
Owner:PING AN TECH (SHENZHEN) CO LTD
Vulnerability detection system and method for android hybrid application code injection
ActiveCN108647517BVulnerability detection worksConfusion resistancePlatform integrity maintainanceFeature extractionCall graph
The invention discloses a loophole detection system and method for Android mixed application code injection. The system includes an authority feature extraction module, a data channel feature extraction module and a vulnerability detection module. The authority feature extraction module is used to extract the mixed application code to be detected The sensitive permission application set of the hybrid application; the data channel feature extraction module is used to extract the source point set and the receiving point set of the data channel from the mixed application code to be detected; the first input terminal of the vulnerability detection module is the same as the output of the permission feature extraction module The second input terminal is connected to the output terminal of the data channel feature extraction module, which is used to determine whether there is vulnerability code injection in the mixed application to be detected by using the vulnerability detection model according to the sensitive authority and the source point set and the receiving point set of the data channel . Compared with the traditional detection method based on control flow and program call graph, it has higher efficiency, high classification accuracy and good usability.
Owner:HUAZHONG UNIV OF SCI & TECH
Cross-site script vulnerability detection method and system
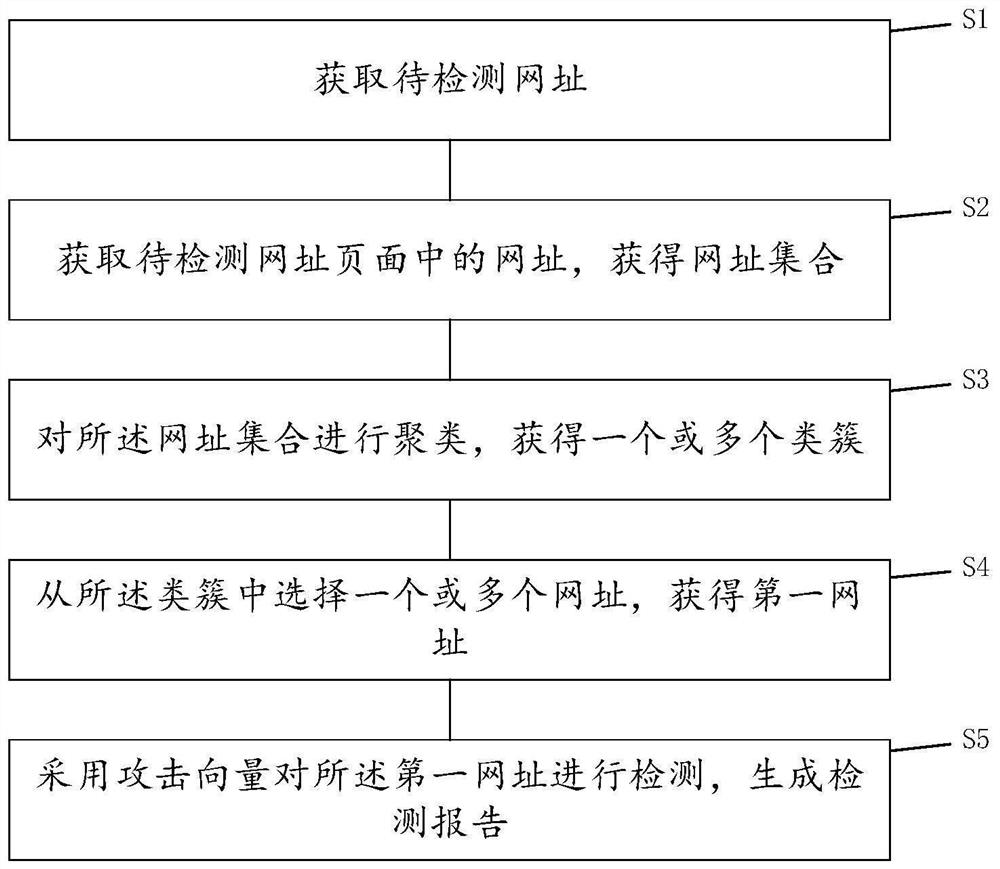
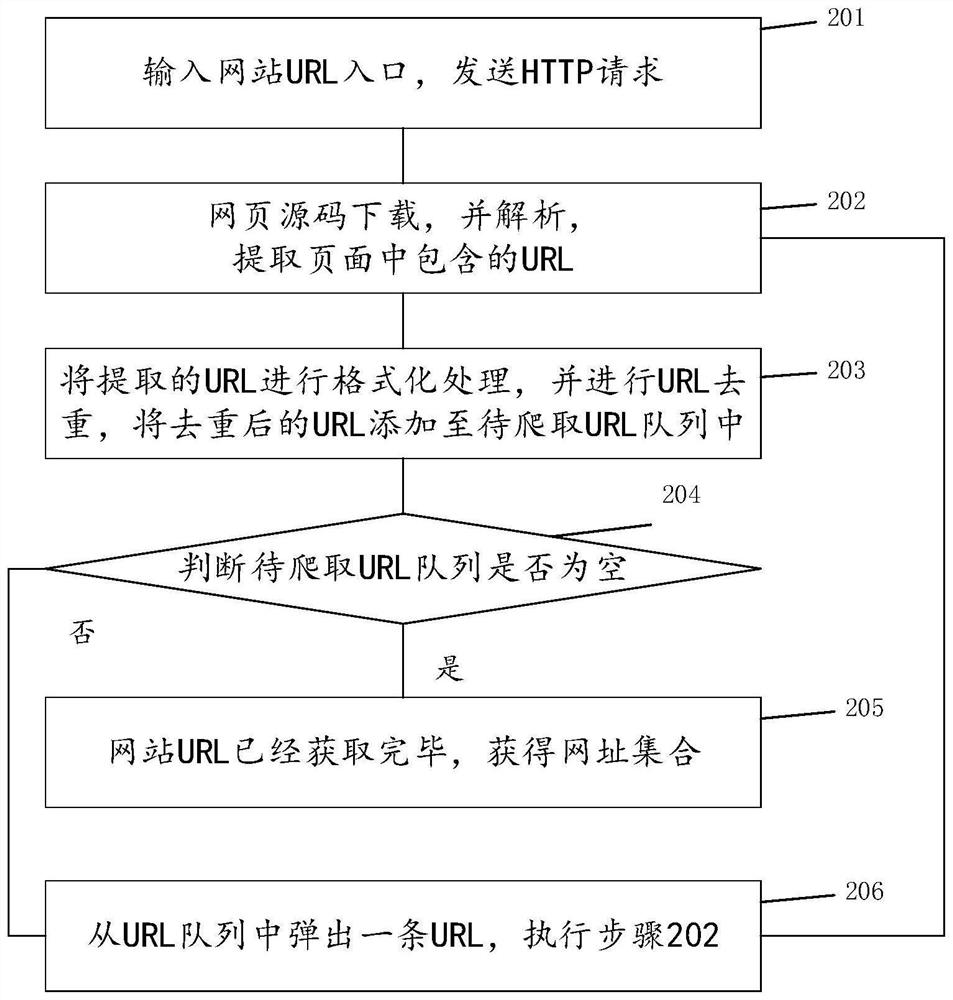
PendingCN114579979ANarrowing down the scope of vulnerability detectionAvoid duplicate detectionPlatform integrity maintainanceWebsite content managementAttackDuplicate detection
The invention discloses a cross-site script vulnerability detection method and system, and belongs to the technical field of vulnerability detection.The detection method comprises the steps that a website to be detected is obtained; obtaining websites in the website page to be detected, and obtaining a website set; clustering the website set to obtain one or more class clusters; selecting one or more websites from the class cluster to obtain a first website; and detecting the first website by adopting an attack vector. Clustering the website sets, and taking the websites with relatively high similarity as the same class of clusters; the structures of the same class of clusters are similar, the attribute similarity is high, one or more websites are adopted for vulnerability detection, the range of XSS vulnerability detection is narrowed, repeated detection of the same class of websites or pages is avoided, and therefore the vulnerability detection efficiency is improved.
Owner:BEIJING UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com