Bug checking method and device and continuously integrated code bug checking method and device
A detection method and vulnerability technology, applied in the field of information security, can solve the problems of low test efficiency, consumption of software and hardware resources, and high labor costs, and achieve the effect of improving vulnerability detection efficiency, avoiding wasting hardware and software resources, and avoiding large concurrency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
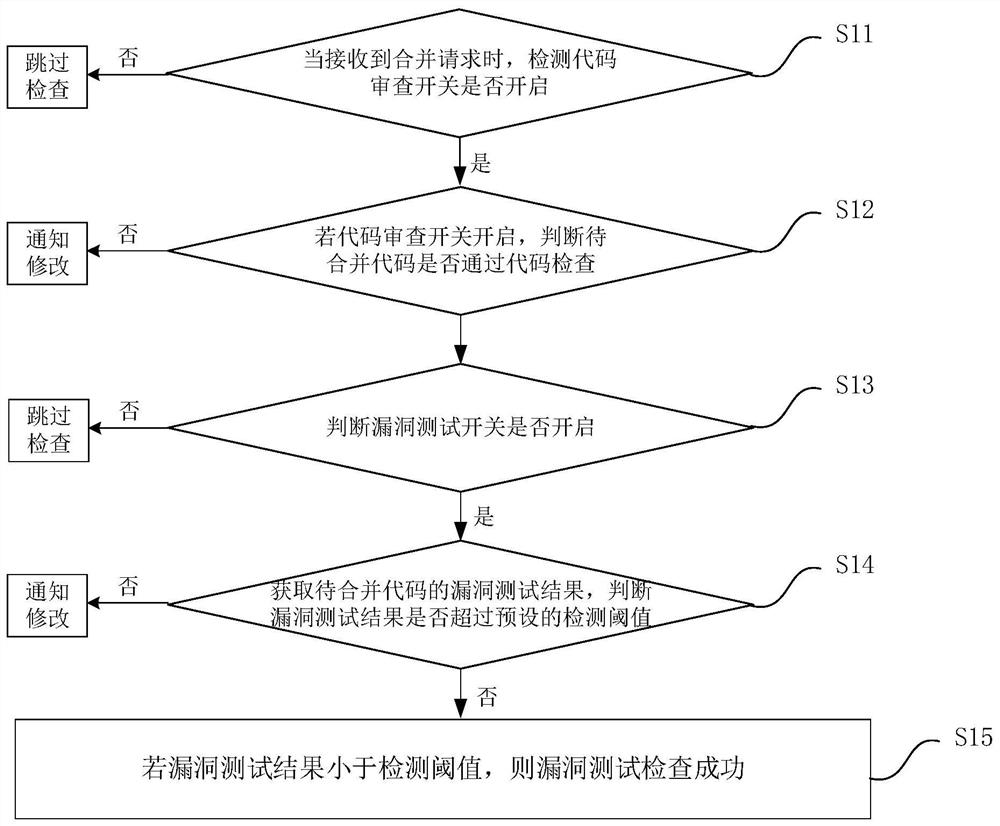
[0035] This embodiment provides a vulnerability checking method, which is applied to the vulnerability checking of integrated codes to improve development efficiency, such as figure 1 As shown, the vulnerability checking method includes the following steps:
[0036] S11, when a merge request is received, detect whether the code review switch is turned on.
[0037] Exemplarily, the merge request is a request initiated by the developer to the online master branch code after the developer completes the new function code. When a merge request is received, the code review switch is first detected to determine whether the code review switch has been turned on.
[0038] S12. If the code review switch is turned on, it is judged whether the code to be merged passes the code check.
[0039] Exemplarily, if it is detected that the code review switch is turned on, a code review is performed on the code to be merged. Code review mainly refers to the systematic review of the source code ...
Embodiment 2
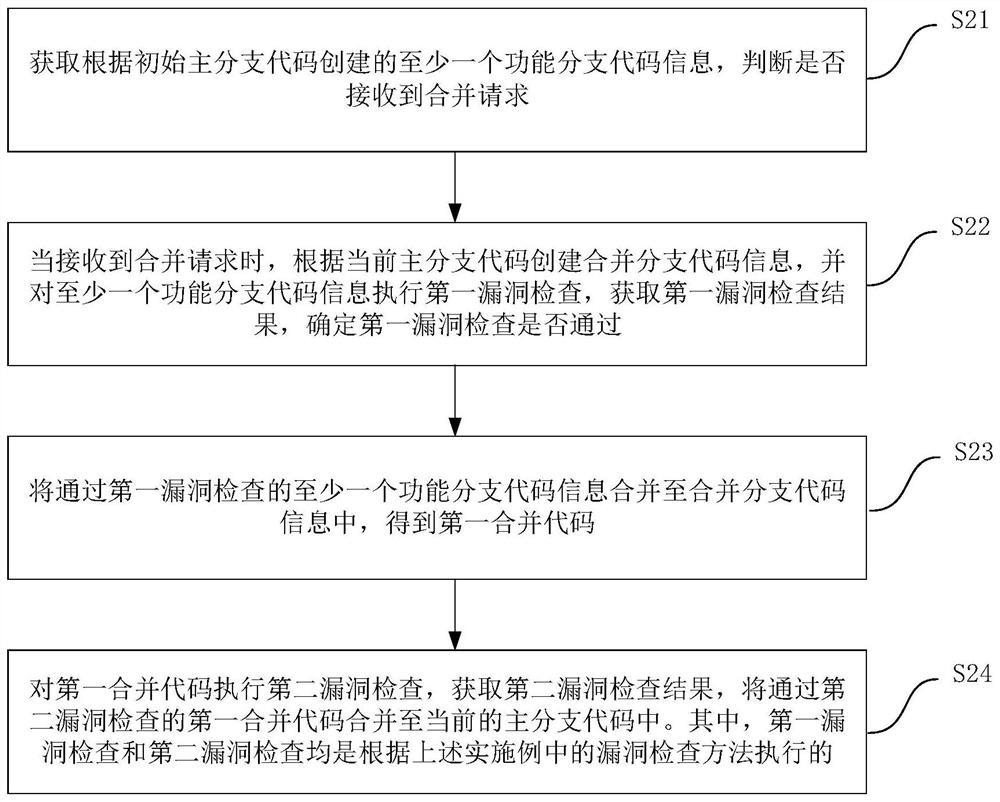
[0059] This embodiment provides a vulnerability inspection method for continuous integration code, which is applied to the vulnerability inspection of integrated code to improve development efficiency, such as image 3 As shown, the vulnerability checking method of the continuous integration code includes the following steps:
[0060] S21. Obtain at least one functional branch code information created according to the initial main branch code, and determine whether a merge request is received.
[0061] Exemplarily, the function branch code information is based on the initial main branch code, and the developer creates and develops the function code according to the initial main branch code. After the development of the function branch code is completed, a merge request can be initiated to the current main branch code, and the server can monitor in real time whether the merge request is received.
[0062] S22. When a merge request is received, create merged branch code informa...
Embodiment 3
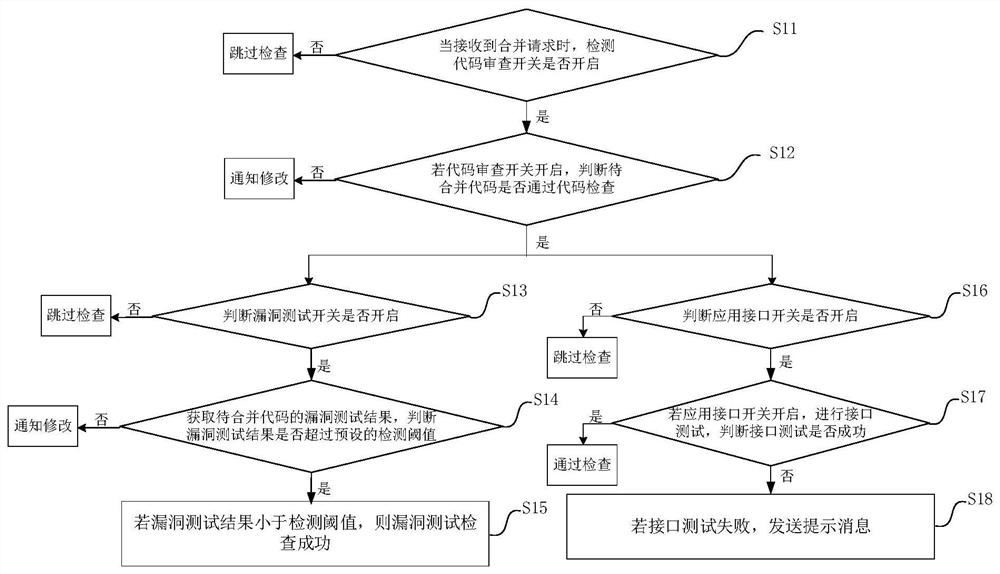
[0084] This embodiment provides a vulnerability checking device, which is applied to the vulnerability checking of integrated codes to improve development efficiency, such as Figure 10 As shown, the vulnerability checking device includes:
[0085] The detection module 31 is configured to detect whether the code review switch is turned on when a merge request is detected. For details, refer to the relevant description of step S11 in the foregoing embodiment, and details are not repeated here.
[0086] The first judging module 32 is configured to judge whether the code to be merged passes the code inspection if the code inspection switch is turned on. For details, refer to the relevant description of the corresponding step S12 in the foregoing embodiment, and details are not repeated here.
[0087] The second judging module 33 is used for judging whether the vulnerability testing switch is turned on if the code inspection is passed. For details, refer to the relevant descrip...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com