Patents
Literature
240 results about "User-defined function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A user-defined function (UDF) is a function provided by the user of a program or environment, in a context where the usual assumption is that functions are built into the program or environment.
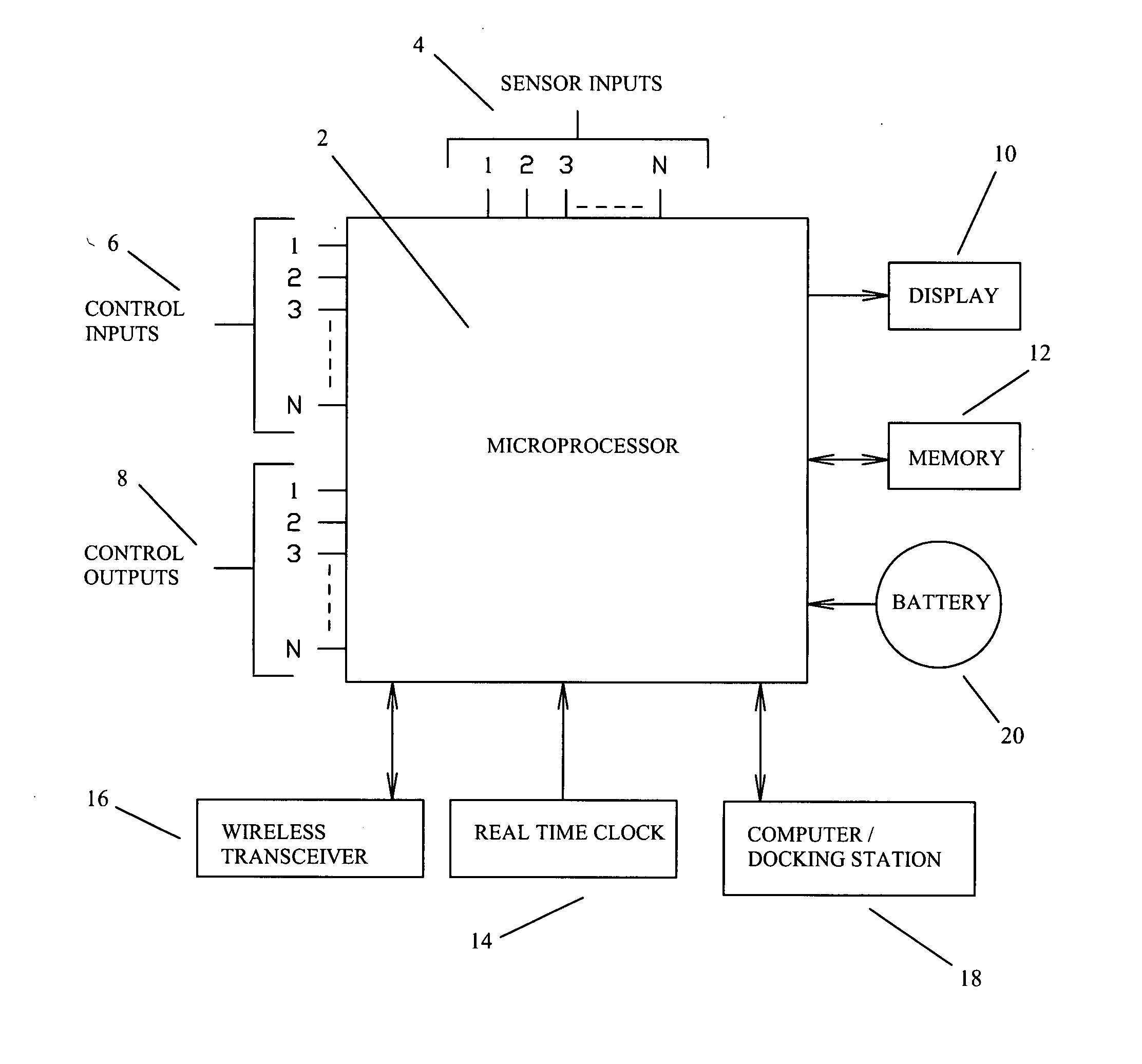
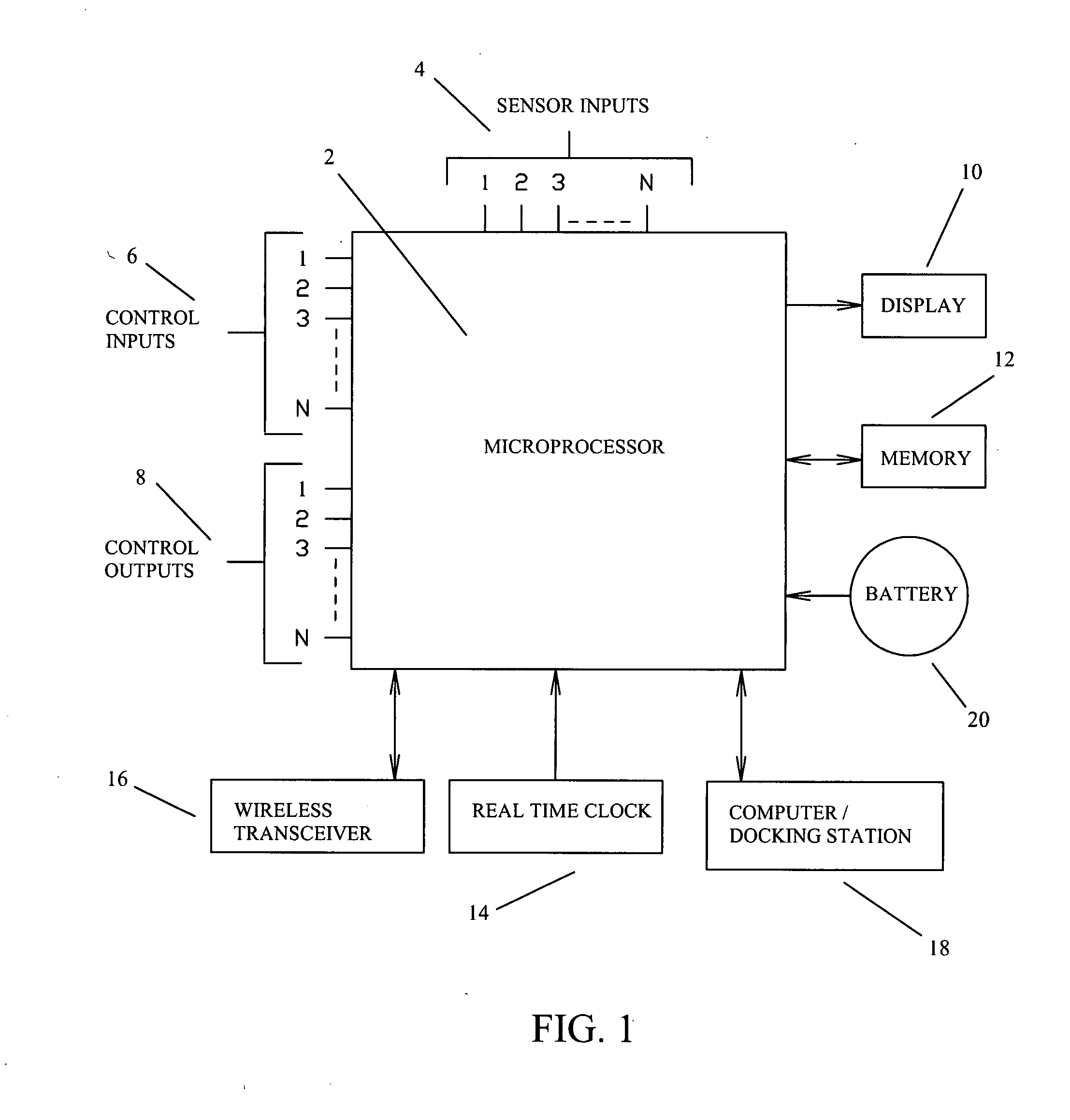
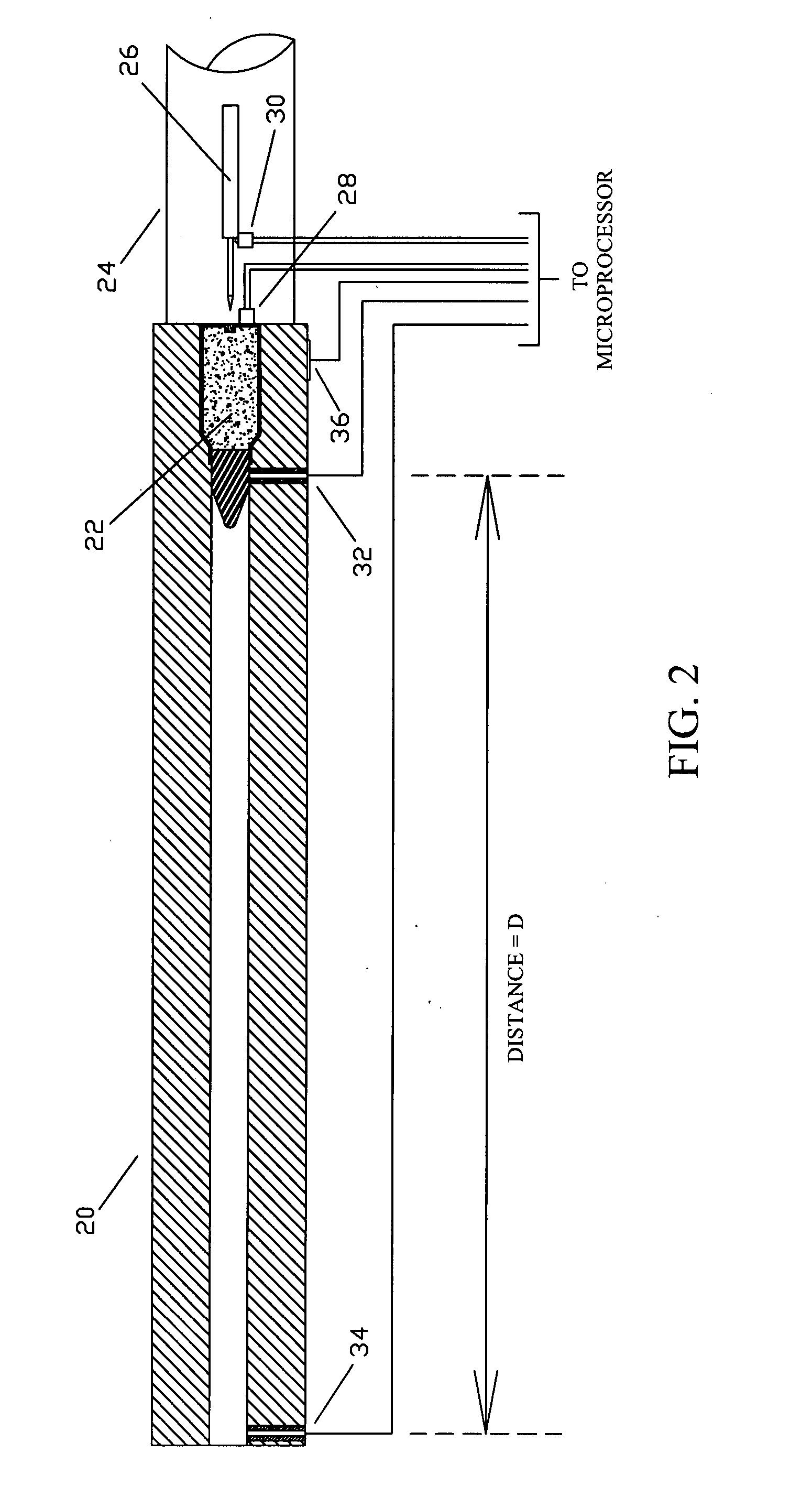
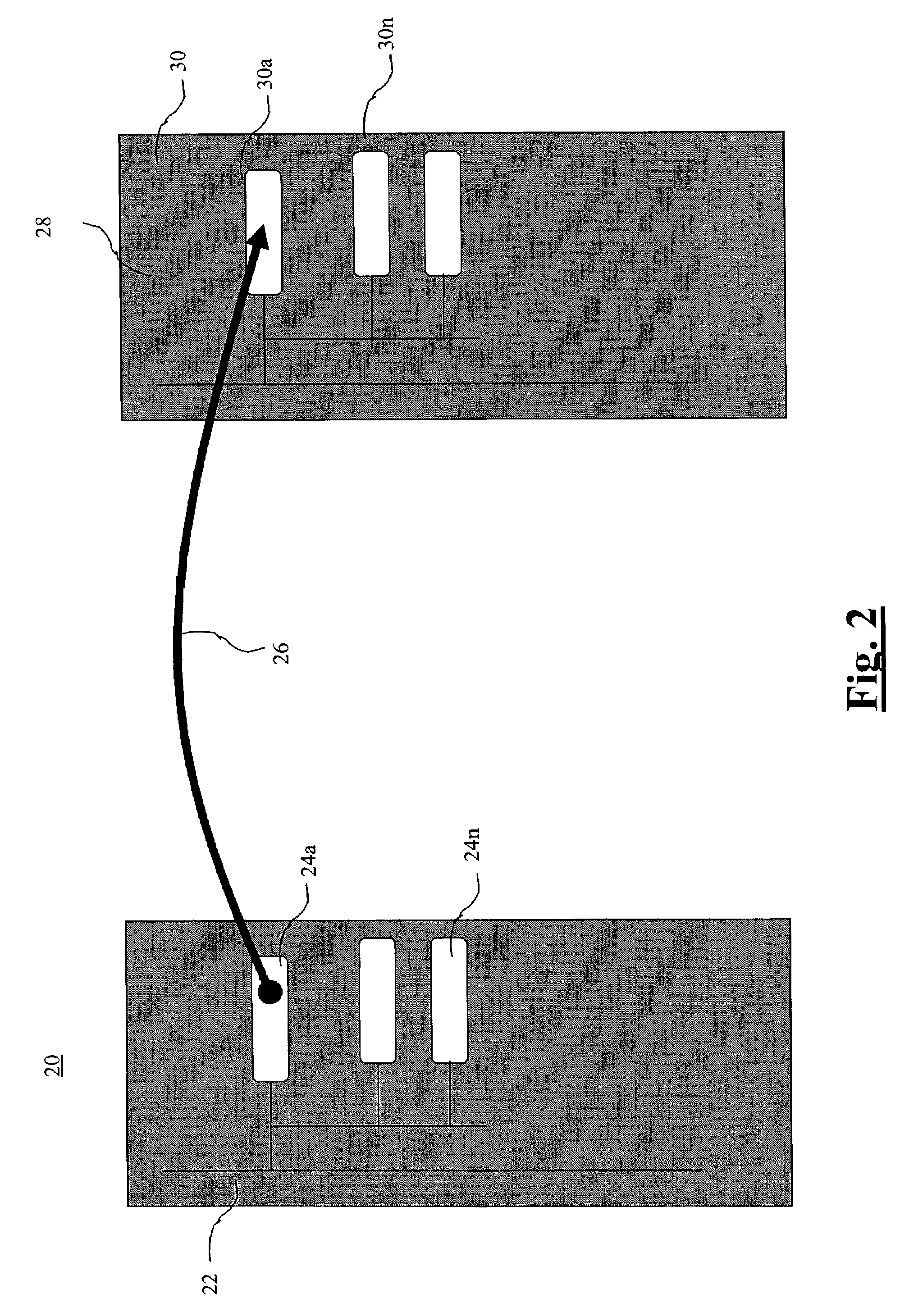
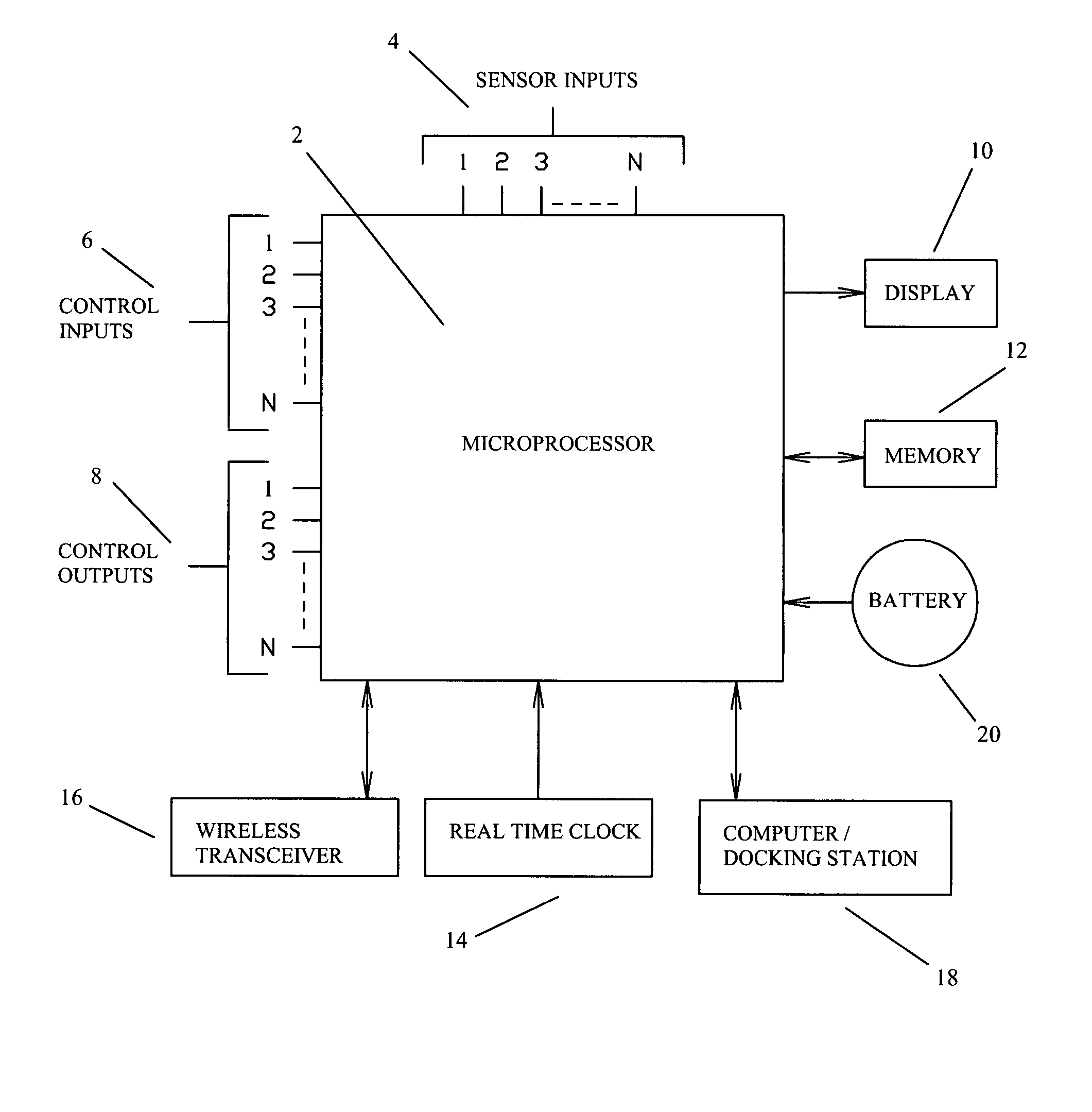
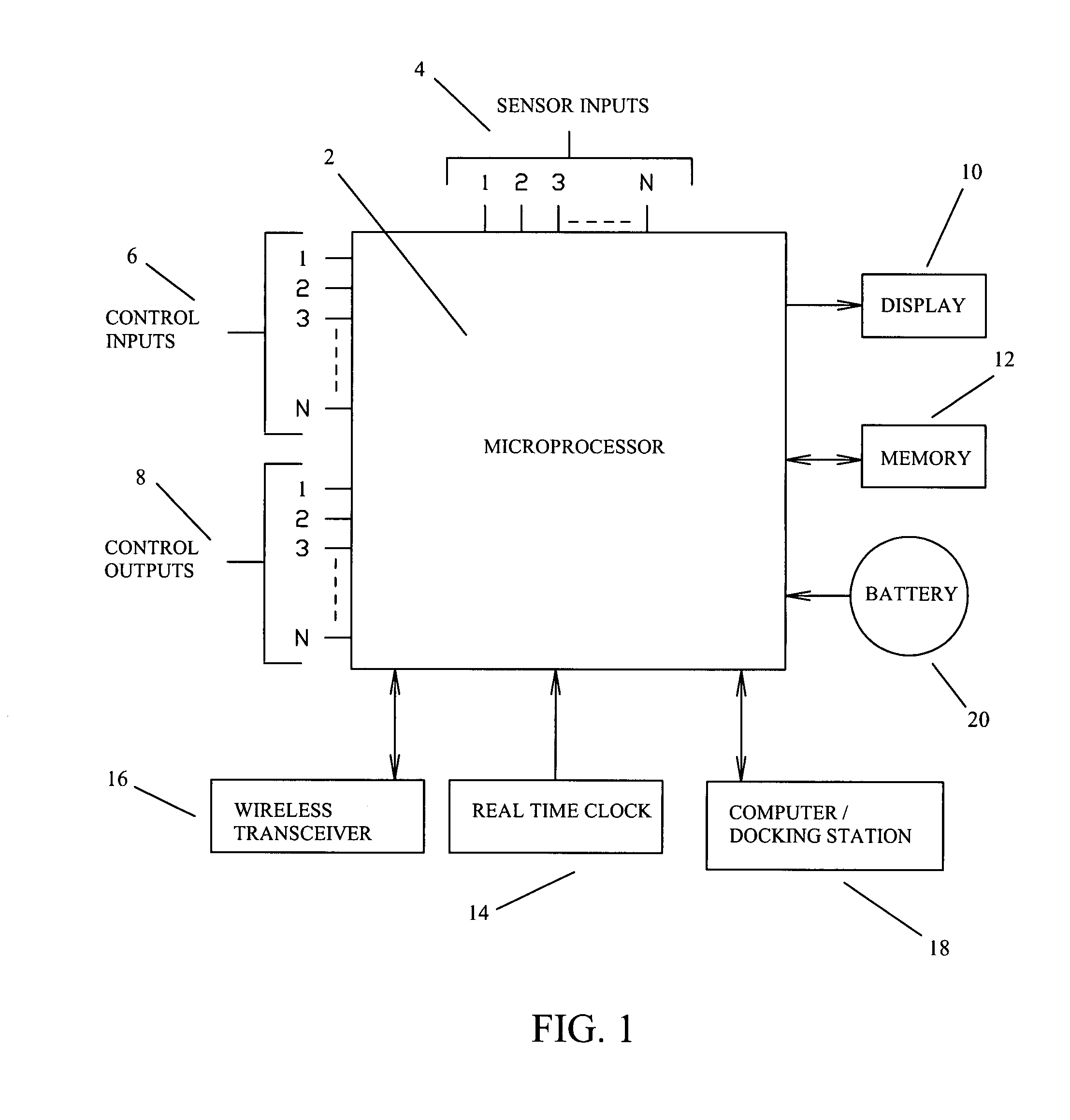
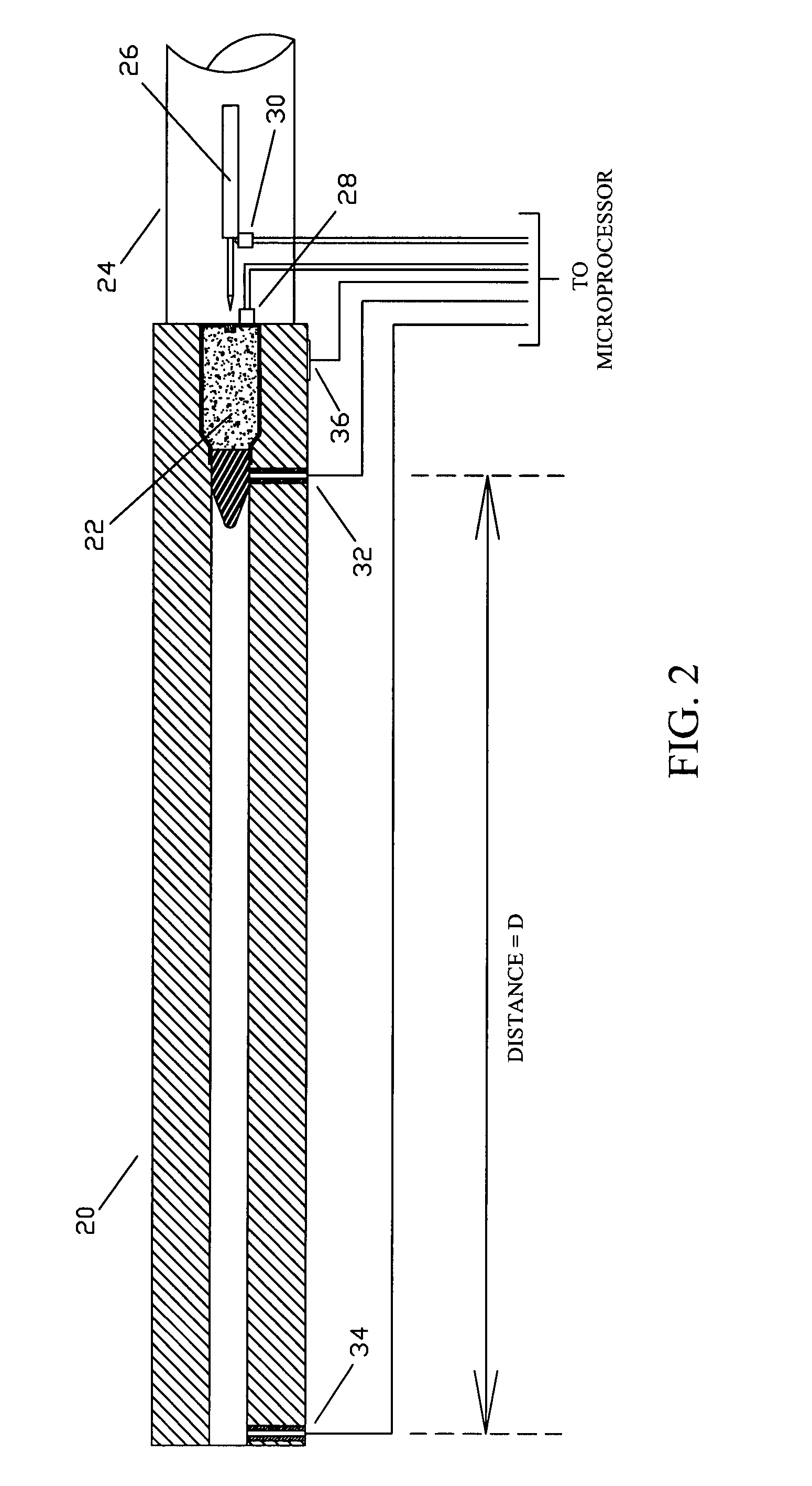
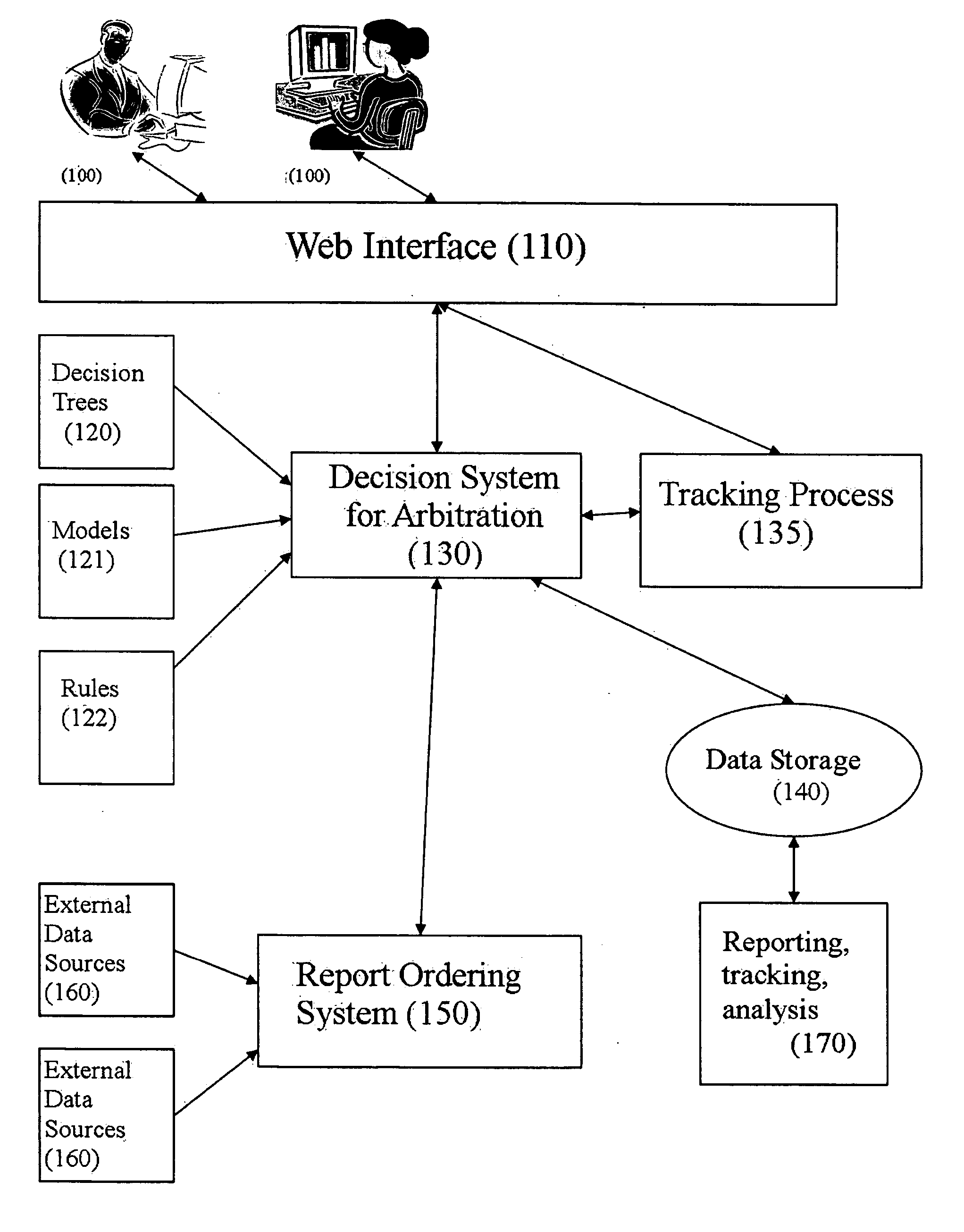
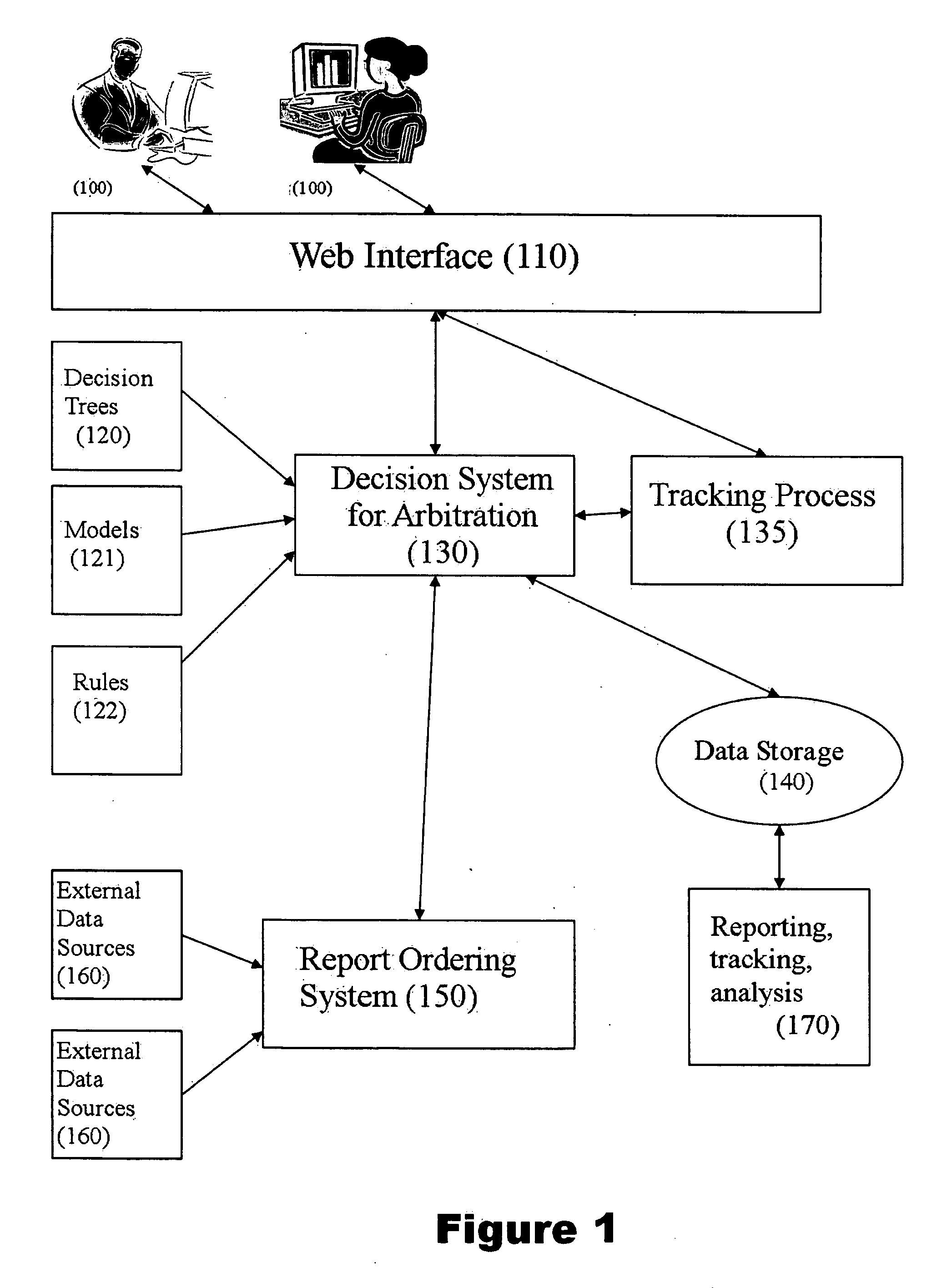
Firearm system for data acquisition and control
InactiveUS20080039962A1Input/output for user-computer interactionSafety arrangementDocking stationData acquisition
A microprocessor circuit that is used to monitor and control a firearm. The microprocessor circuit accomplishes this by monitoring various sensor & control inputs, and acting on these inputs to execute user defined functions. The microprocessor circuit can use the sensory input to determine firearm statistics. These statistics can include the number of times the firearm has been shot, the efficiency of the firearm automatic action, range-to-target, and et cetera. The firearm system can also use a combination of sensors to fabricate a bullet chronograph whereby the muzzle velocity of a cartridge can be determined. These statistics can be date-stamped and recorded into memory. Statistics from Law Enforcement firearms can be used for courtroom evidence and police reporting. These statistics can also be used for firearm maintenance and warranty repair. The microprocessor circuit can display the statistical data to the user via simple light emitting diodes, or sophisticated liquid crystal displays. Data can also be downloaded to a computer docking station as well. The microprocessor circuit can also display the information within the optics of a riflescope. When used in conjunction with a laser range finder sensor, the microprocessor circuit can adjust the electronic cross-hairs (reticle) to compensate for the bullet trajectory.
Owner:MCRAE MICHAEL WILLIAM
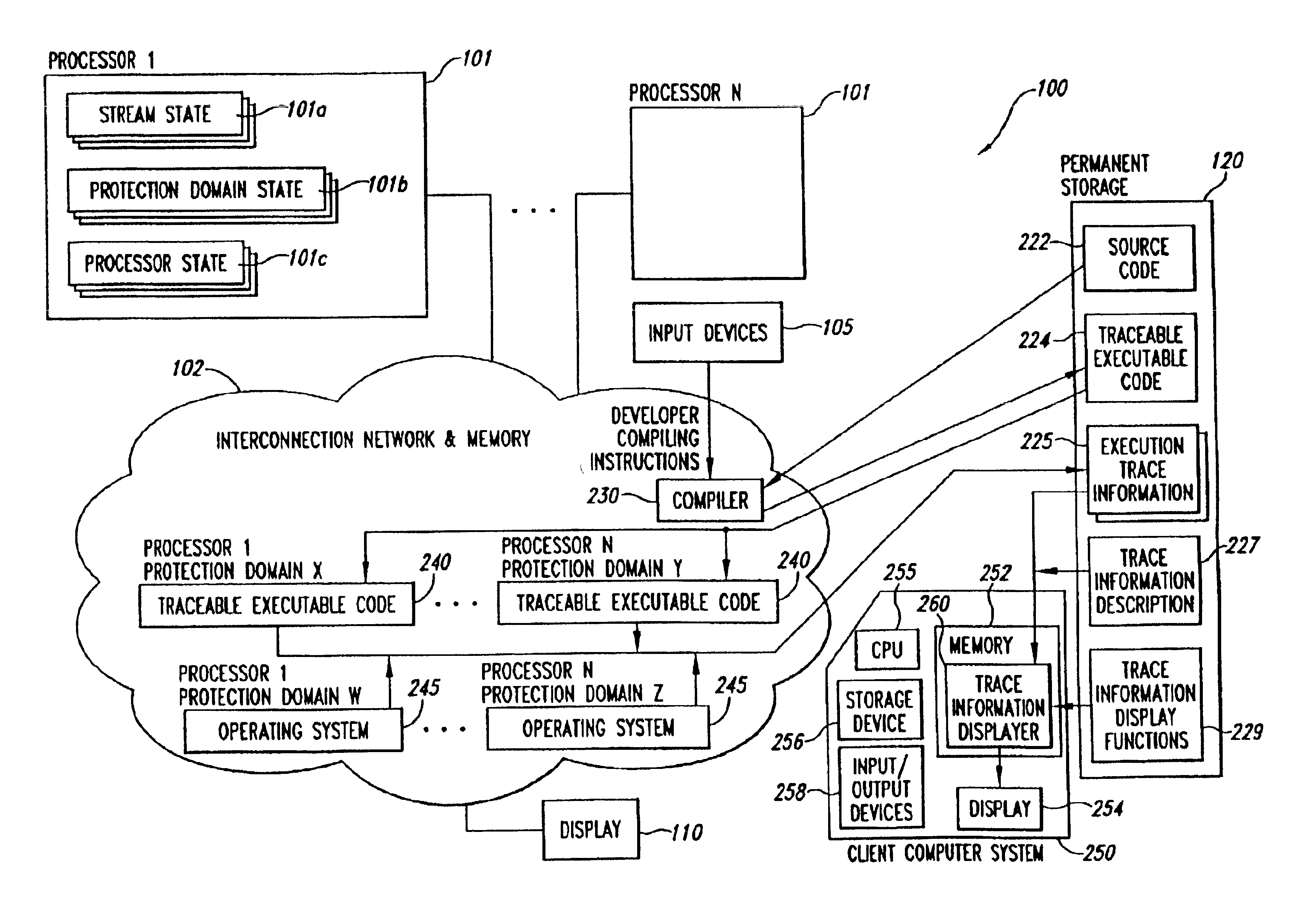
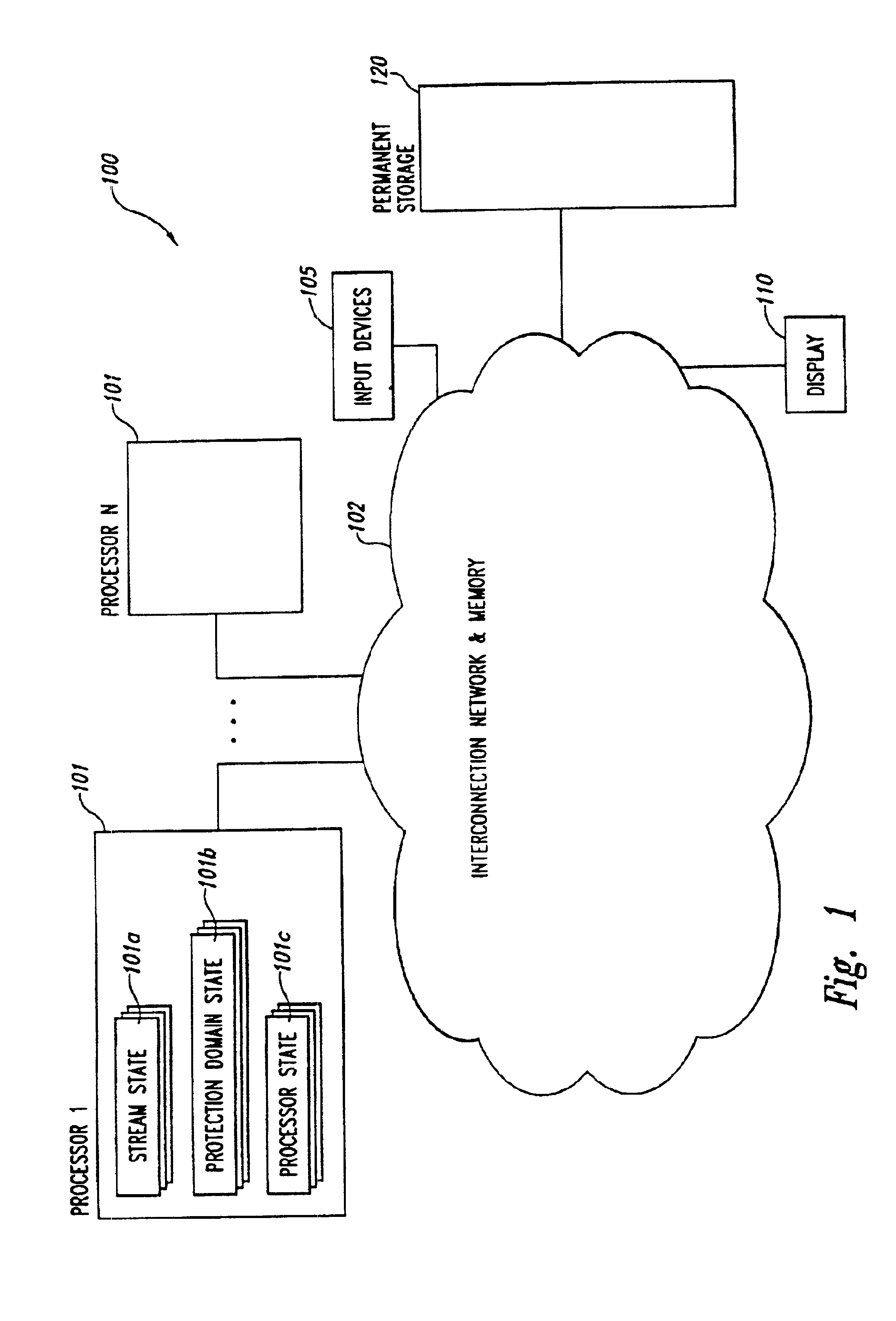
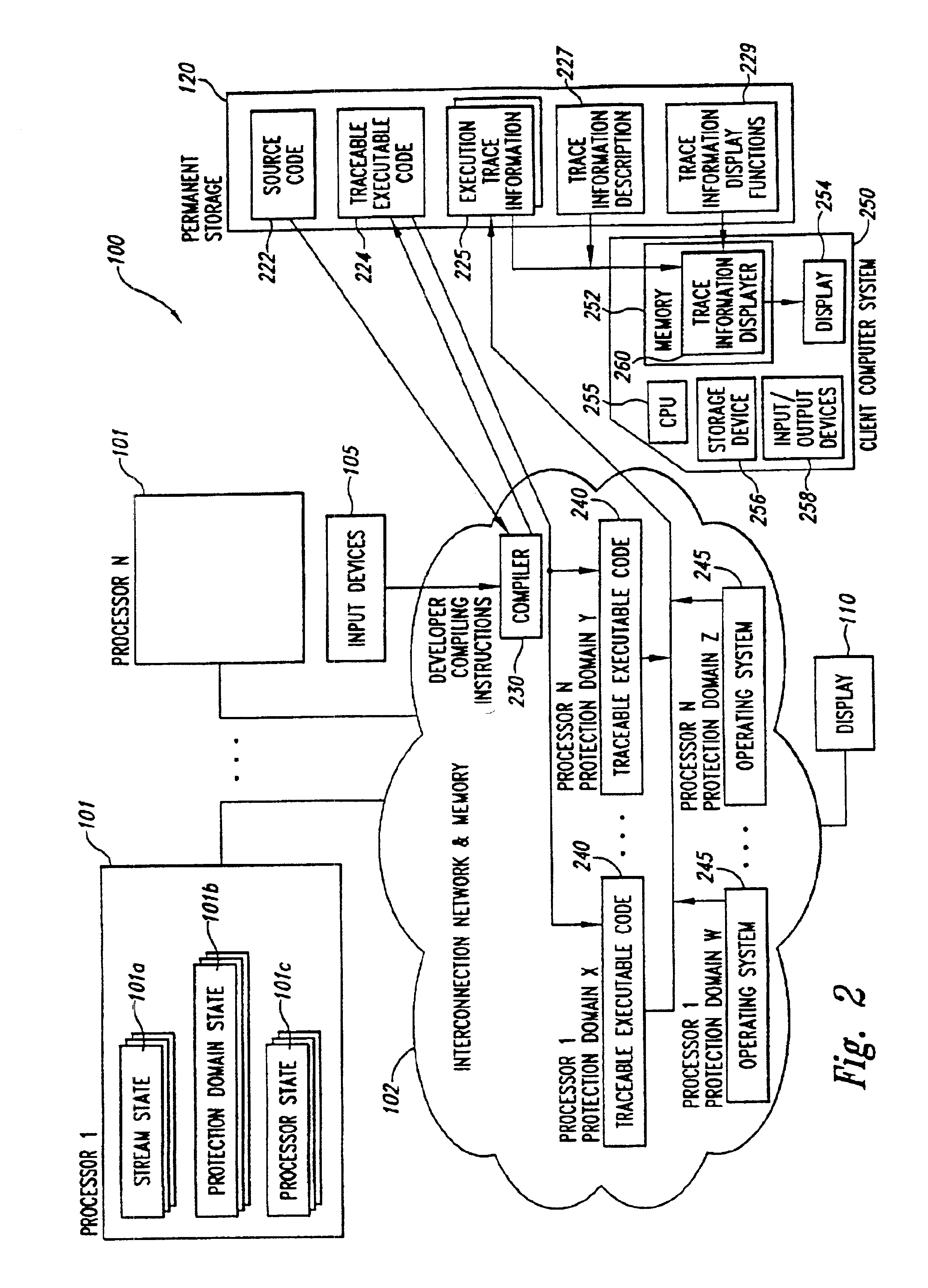
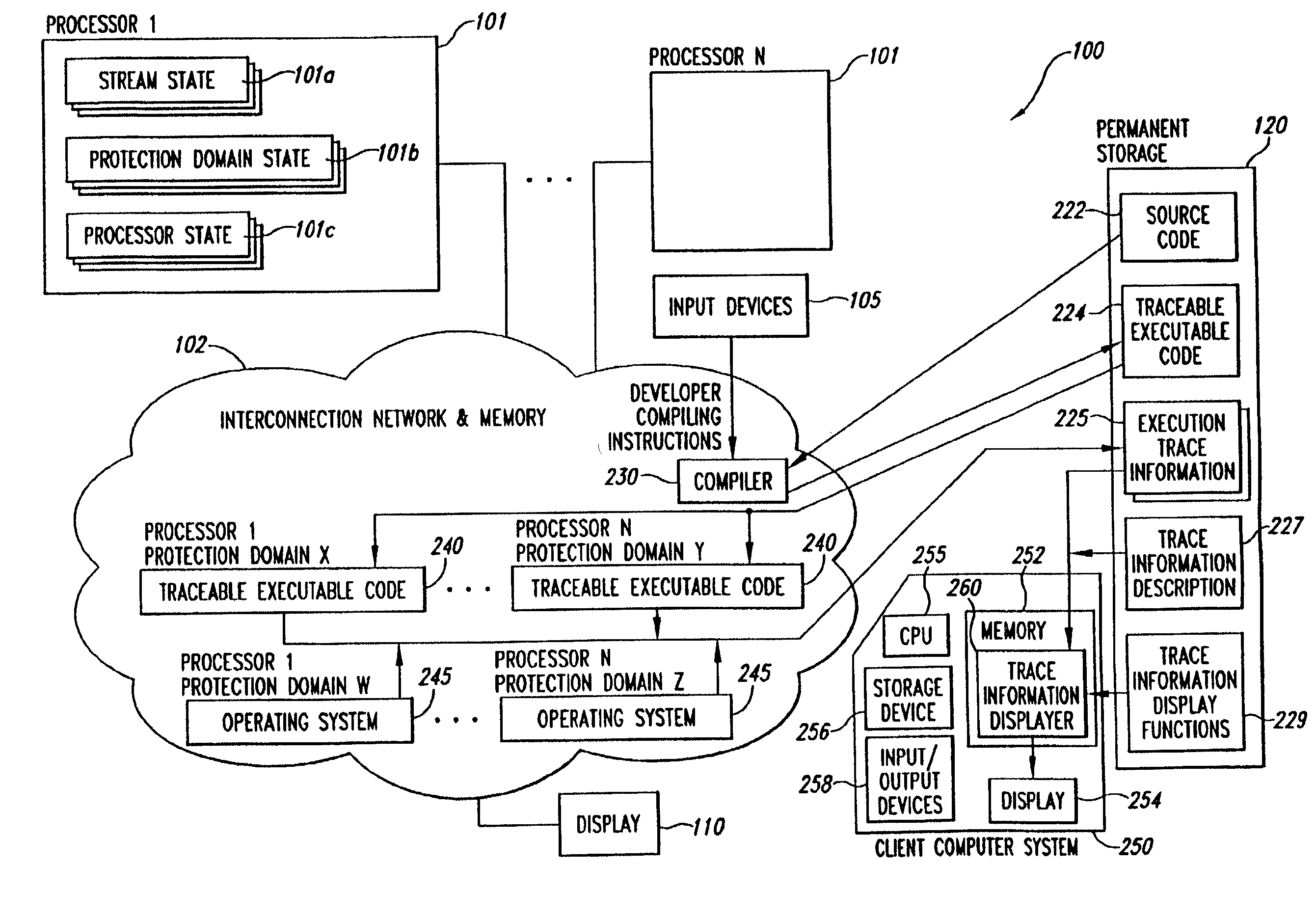
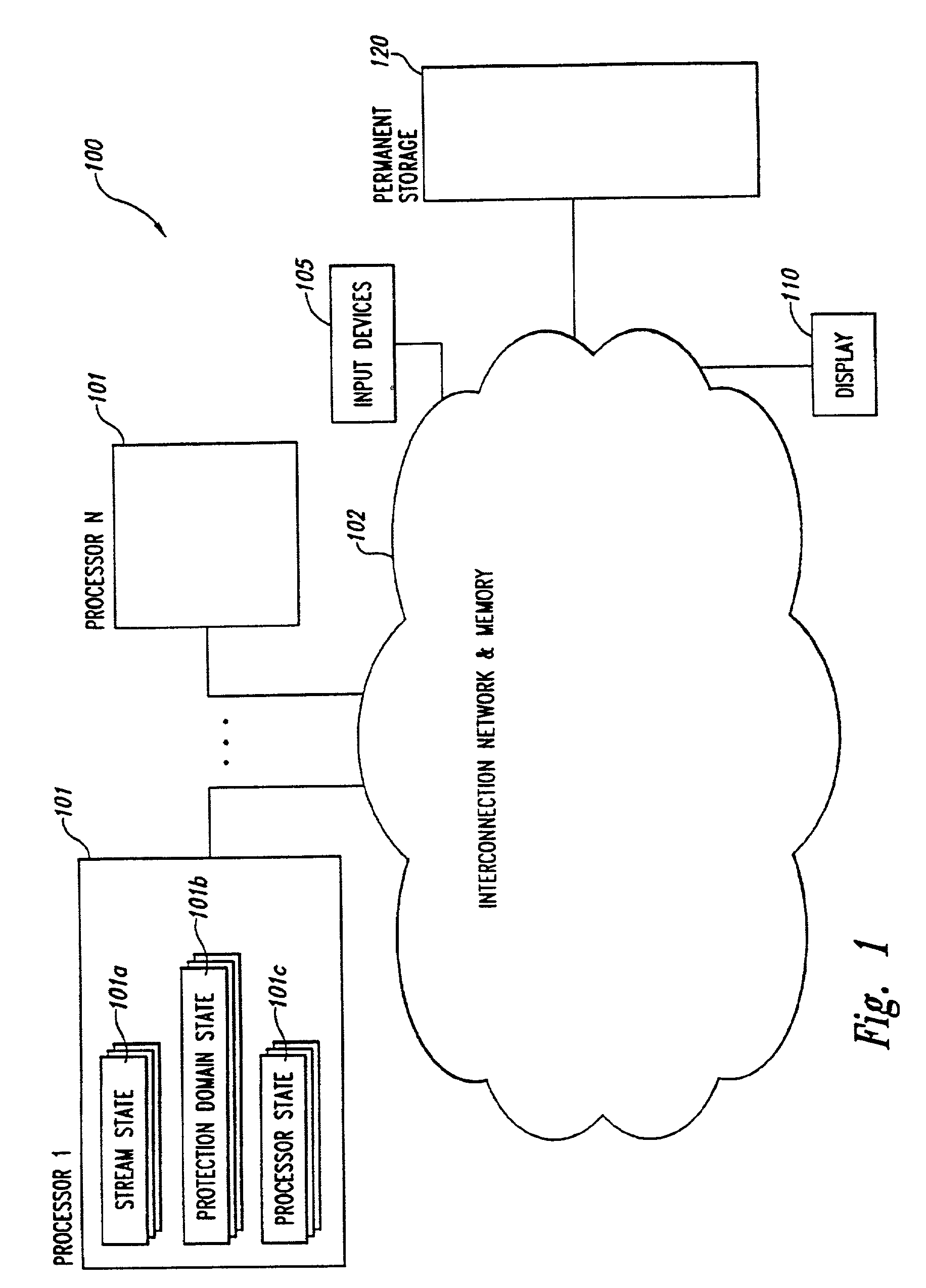
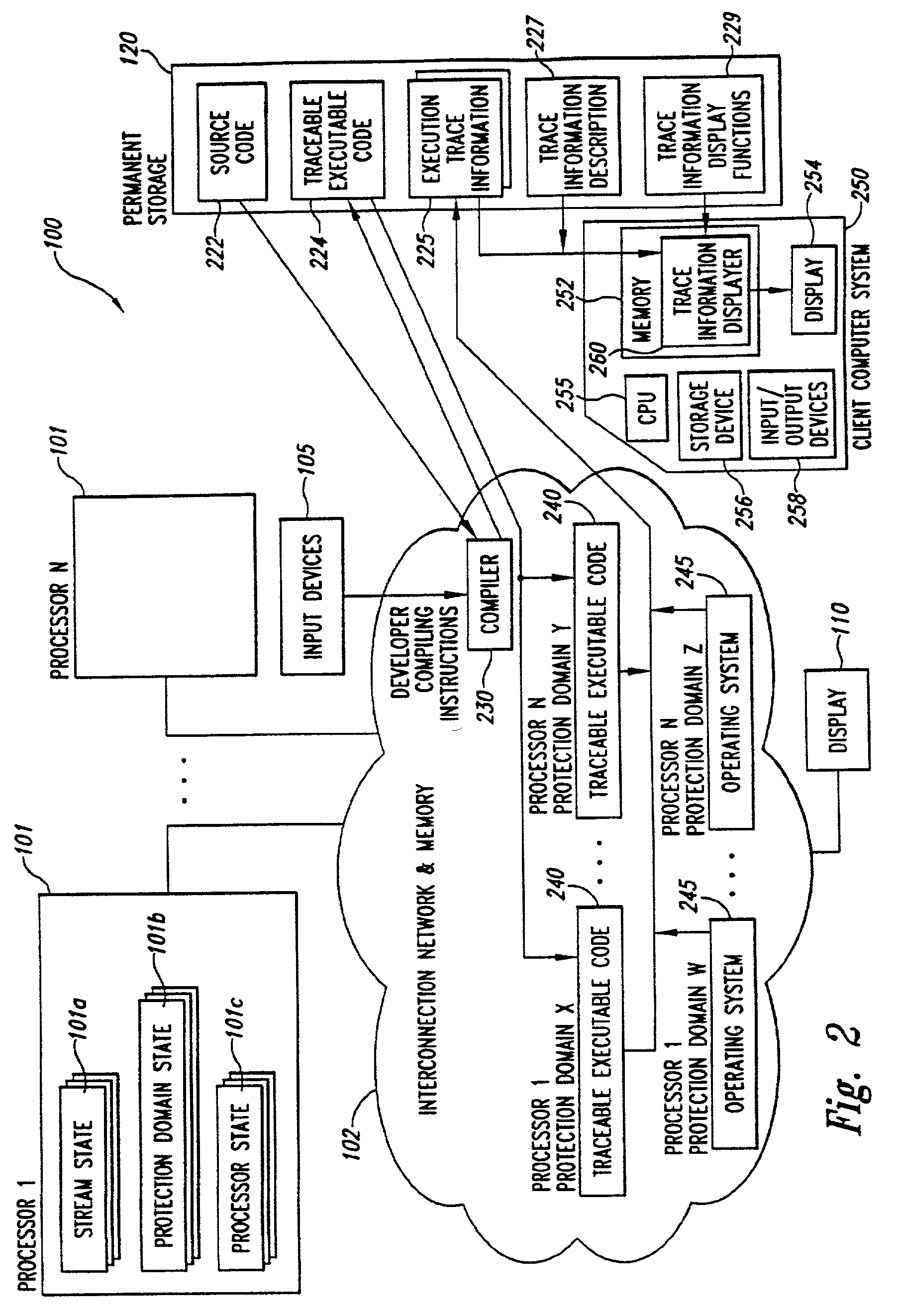
Parallelism performance analysis based on execution trace information
A system for conducting performance analysis for executing tasks. The analysis involves generating a variety of trace information related to performance measures, including parallelism-related information, during execution of the task. In order to generate the trace information, target source code of interest is compiled in such a manner that executing the resulting executable code will generate execution trace information composed of a series of events. Each event stores trace information related to a variety of performance measures for the one or more processors and protection domains used. After the execution trace information has been generated, the system can use that trace information and a trace information description file to produce useful performance measure information. The trace information description file contains information that describes the types of execution events as well as the structure of the stored information. The system uses the trace information description file to organize the information in the trace information file, extracts a variety of types of performance measure information from the organized trace information, and formats the extracted information for display. The system can use default or user-defined functions to extract and format trace information for display. After the system displays one or more types of performance measure information, a user of the system can then interact with the system in a variety of ways to obtain other useful performance analysis information.
Owner:CRAY
Subscription within workflow management systems
InactiveUS6122633AMinimizes implementation effortImprove performanceFinanceOffice automationWorkflow management systemActuator
The present invention relates to the area of workflow management systems (WFMS). More particularly the inventions extends WFMS by subscription means. The subscription means operate on an audit trail stored within a database. The subscription means may encompass a multitude of subscription monitors. Subscription monitors allow to subscribe to the audit trail, i.e. to formulate certain interests as subscription selectors on information entered into the audit trail. A subscription monitor autonomously checks the audit trail for subscribed audit records. If such audit records have been determined the subscription monitor executes a subscription actuator, i.e. a pre-defined program. The subscription actuator may inform the subscriber on the subscribed audit record or may start any type of program. The current invention teaches to implement the subscription monitors as database triggers of the database storing the audit trail. The subscription selectors are realized as search conditions of the database trigger. Finally the subscription actuator can be implemented according the current teaching as user-defined functions of the database.
Owner:IBM CORP
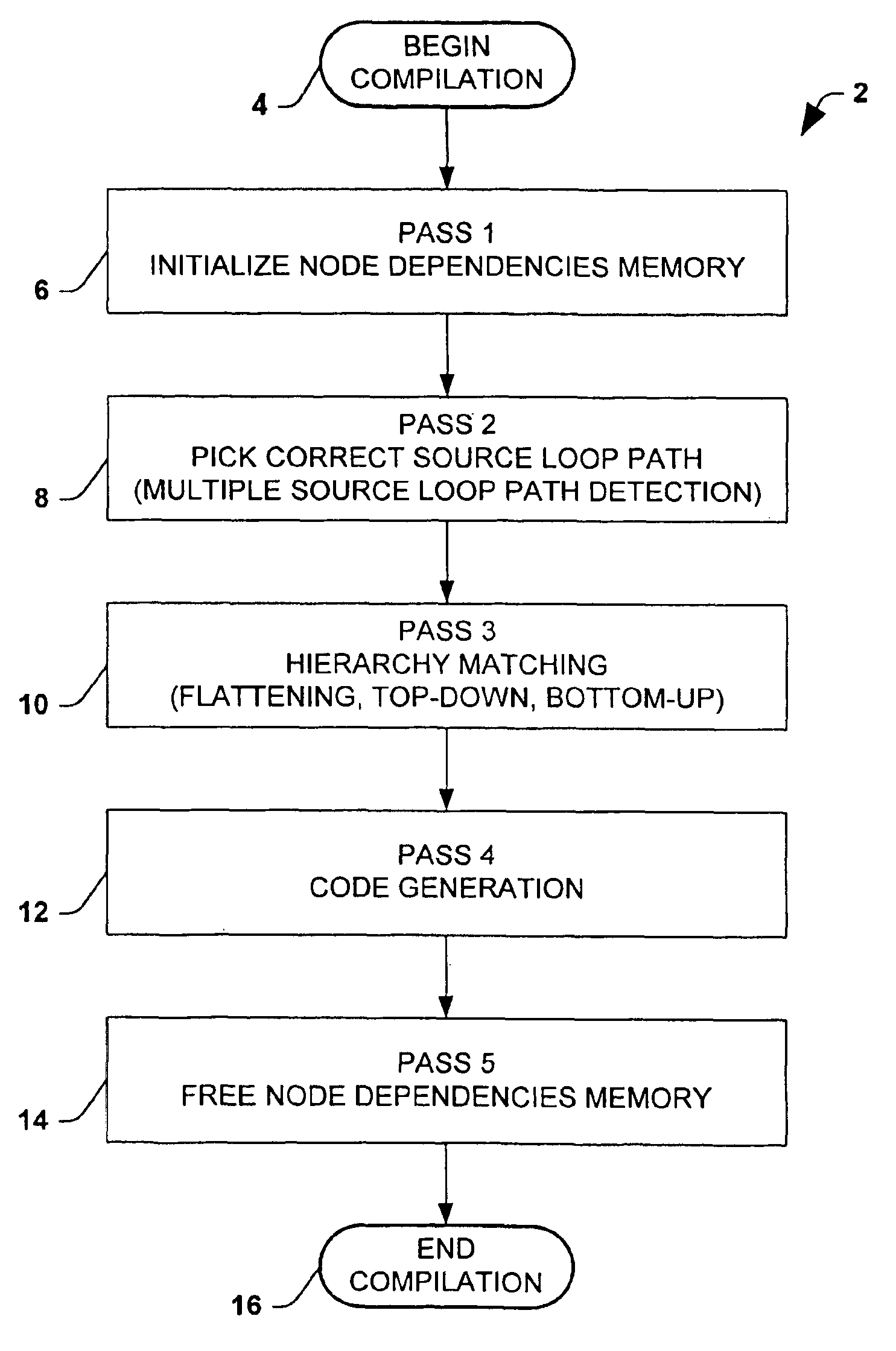
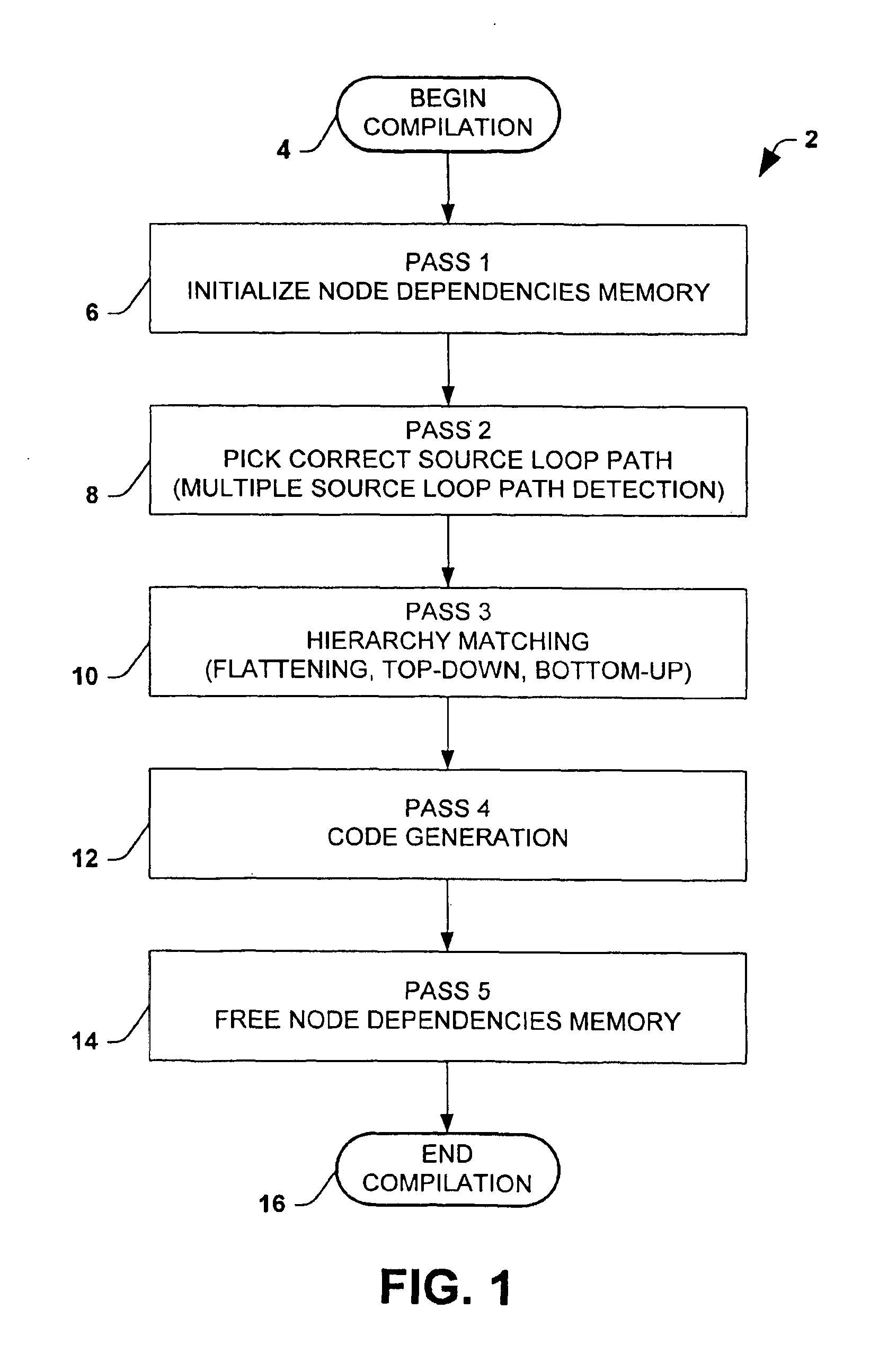
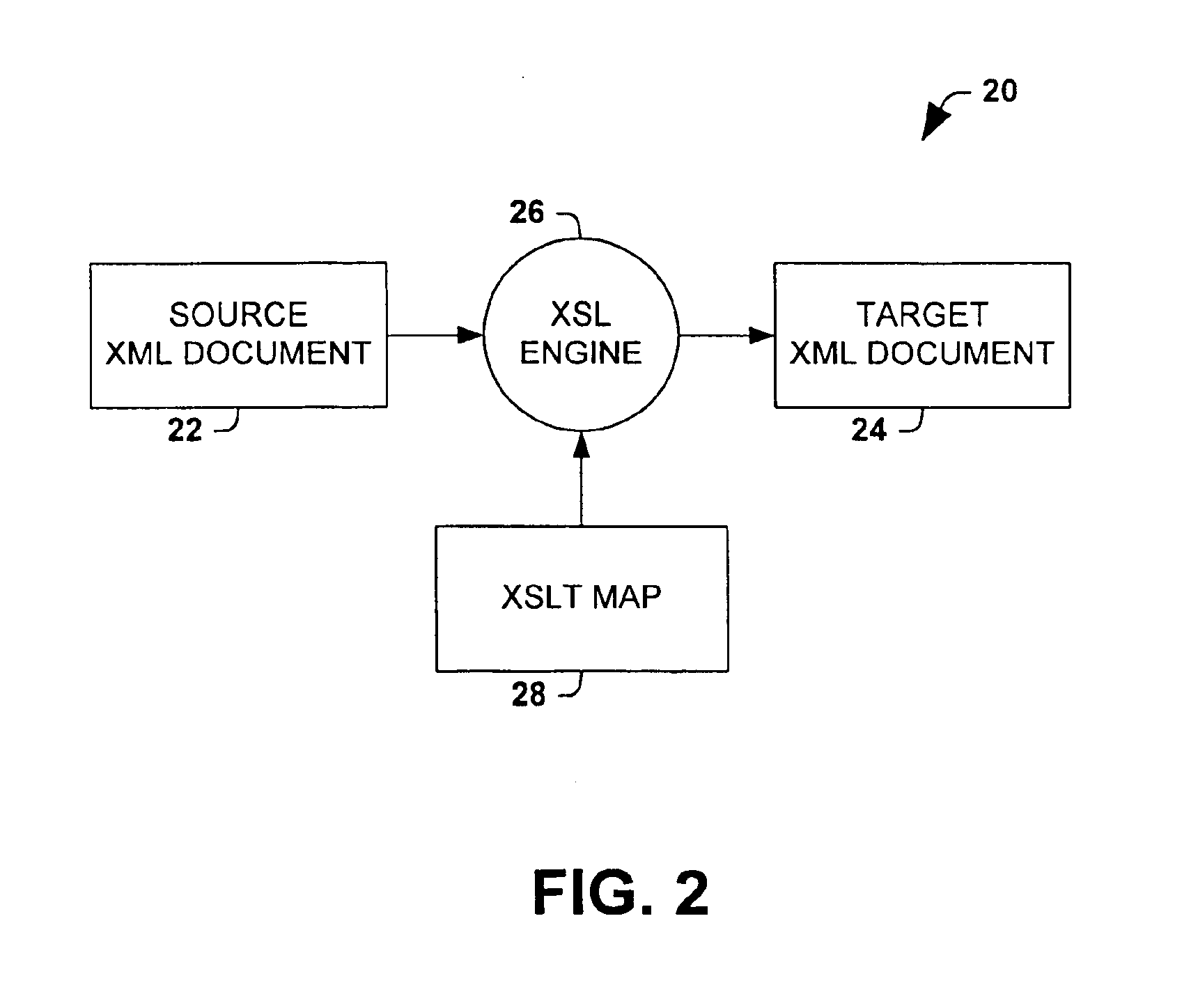
Method of compiling schema mapping
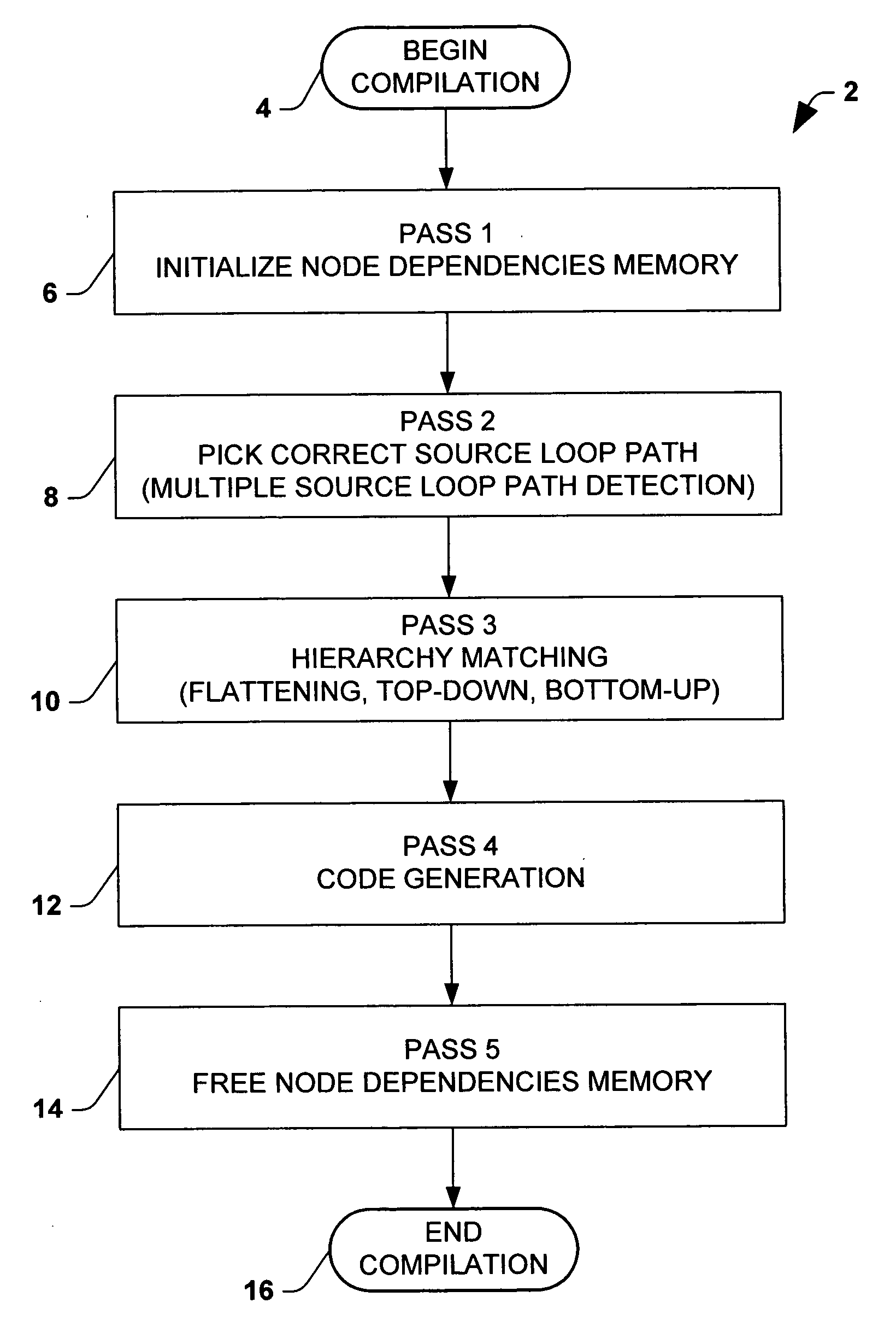
A method for compiling a mapping between a source schema and a target schema is provided. The method comprises multiple passes, including determining source node dependencies, matching hierarchy, and generating code. The method may further comprise initializing node dependency memory prior to determining source node dependencies, and freeing node dependency memory after code generation. The compiler algorithm provides for compiling user-defined functions in the mapping into the compiled representation. Another aspect of the invention provides for generating an XSL code representation of the mapping. An XSL style sheet representation may thus be generated from a visual mapping in accordance with the invention.
Owner:MICROSOFT TECH LICENSING LLC
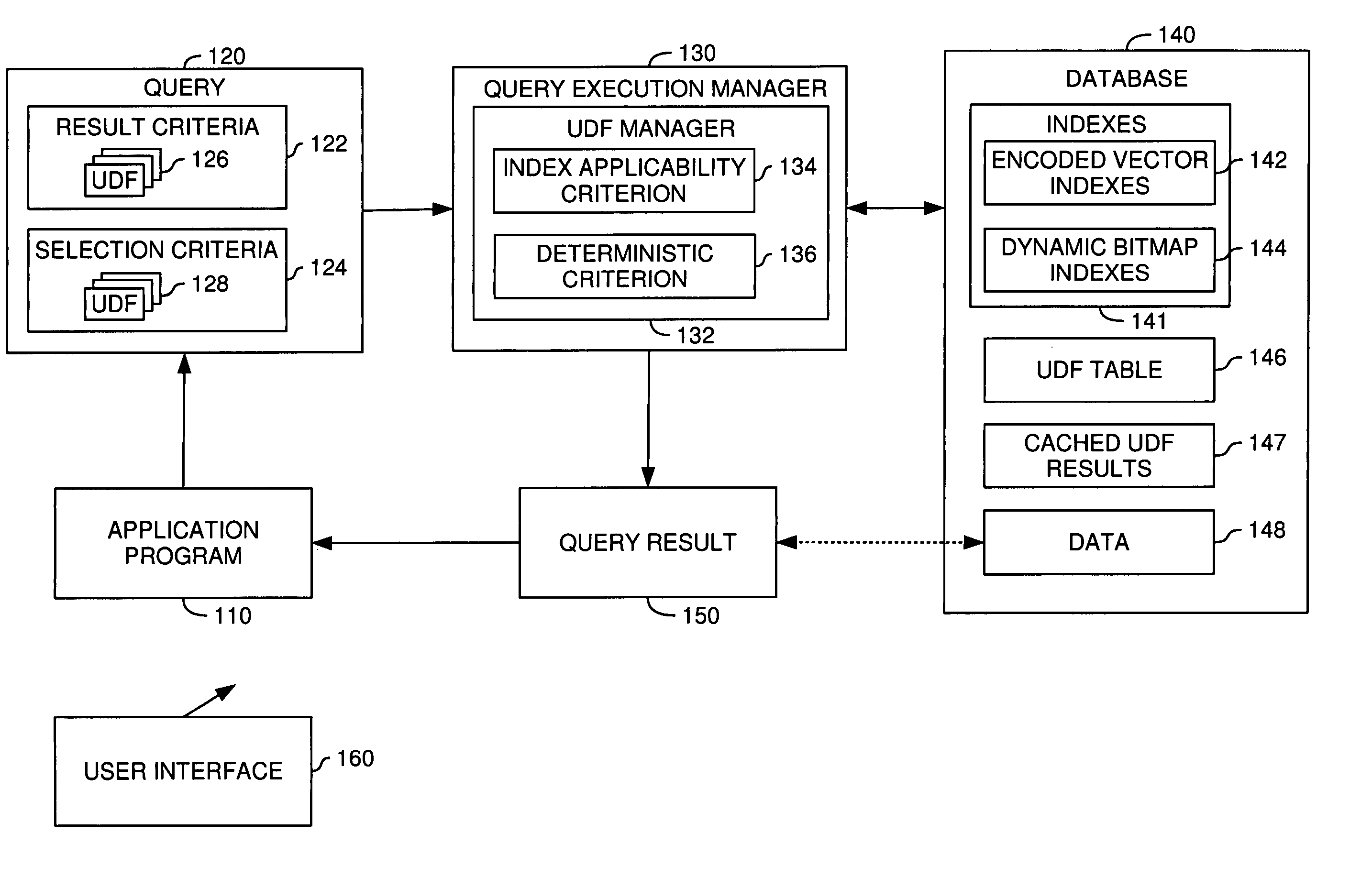
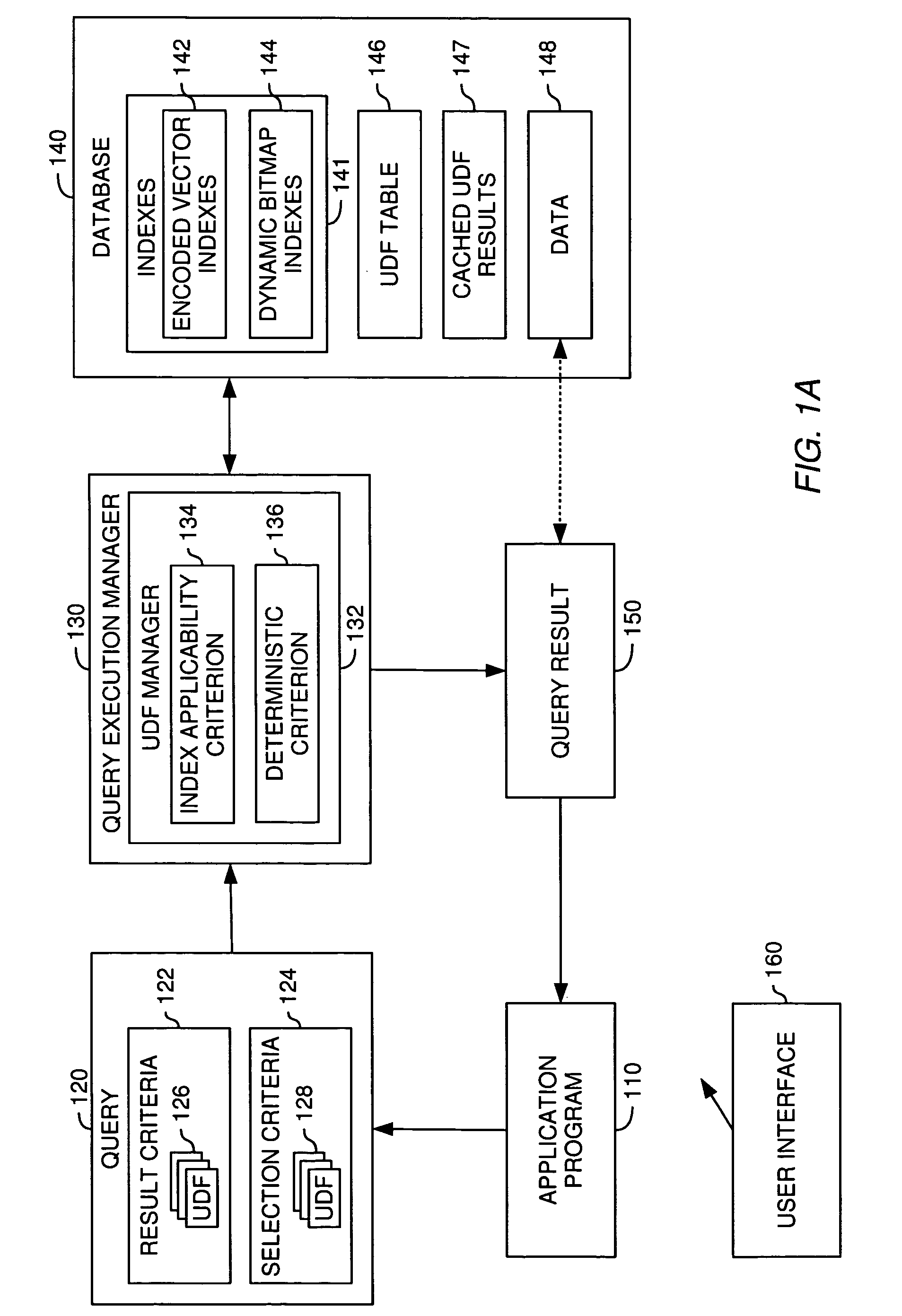
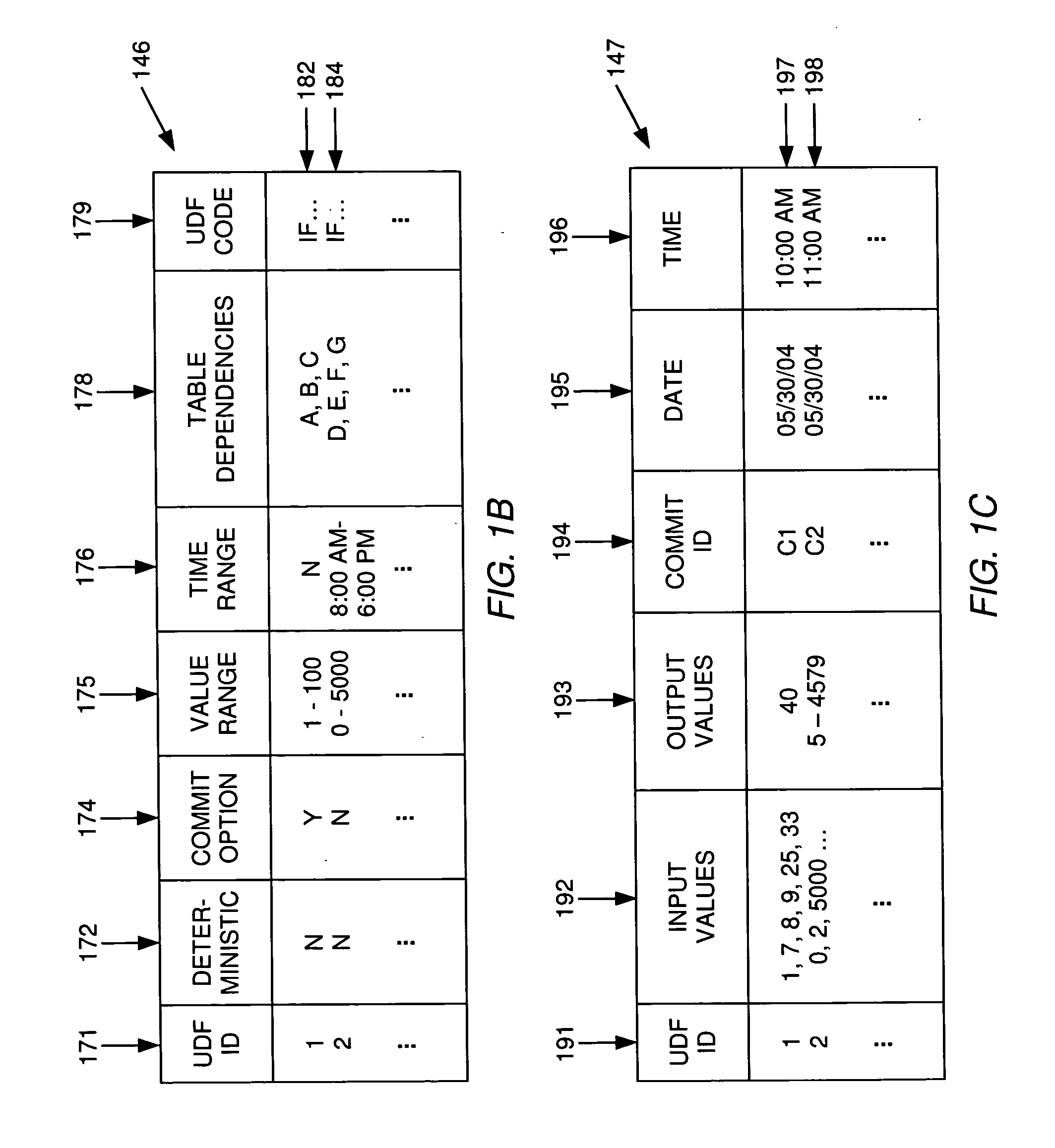
Techniques for processing database queries including user-defined functions
InactiveUS20060041544A1Digital data information retrievalDigital data processing detailsDatabase queryData processing system
A method, system and article of manufacture for query execution management in a data processing system and, more particularly, for managing execution of queries including user-defined functions. One embodiment provides a method for managing execution of a query against data of a database. The method includes receiving a query against the data of the database, the query having at least one query condition including a user-defined function. It is determined whether the user-defined function satisfies a predefined index applicability criterion. If the user-defined function satisfies the predefined index applicability criterion, an index over relevant data of the database is created for the user-defined function. The index is suitable for use in execution of the query against the data of the database to determine a corresponding query result.
Owner:IBM CORP
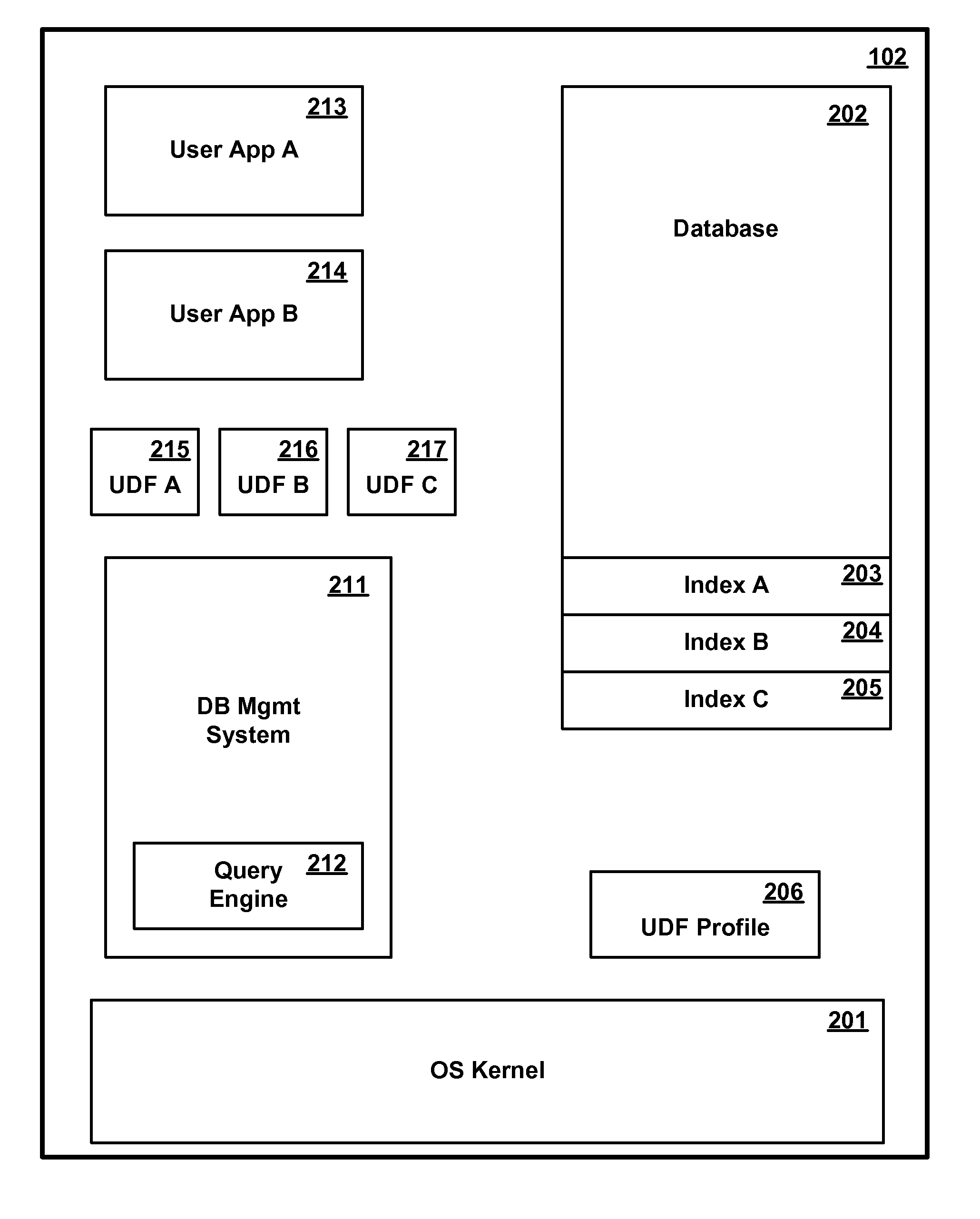
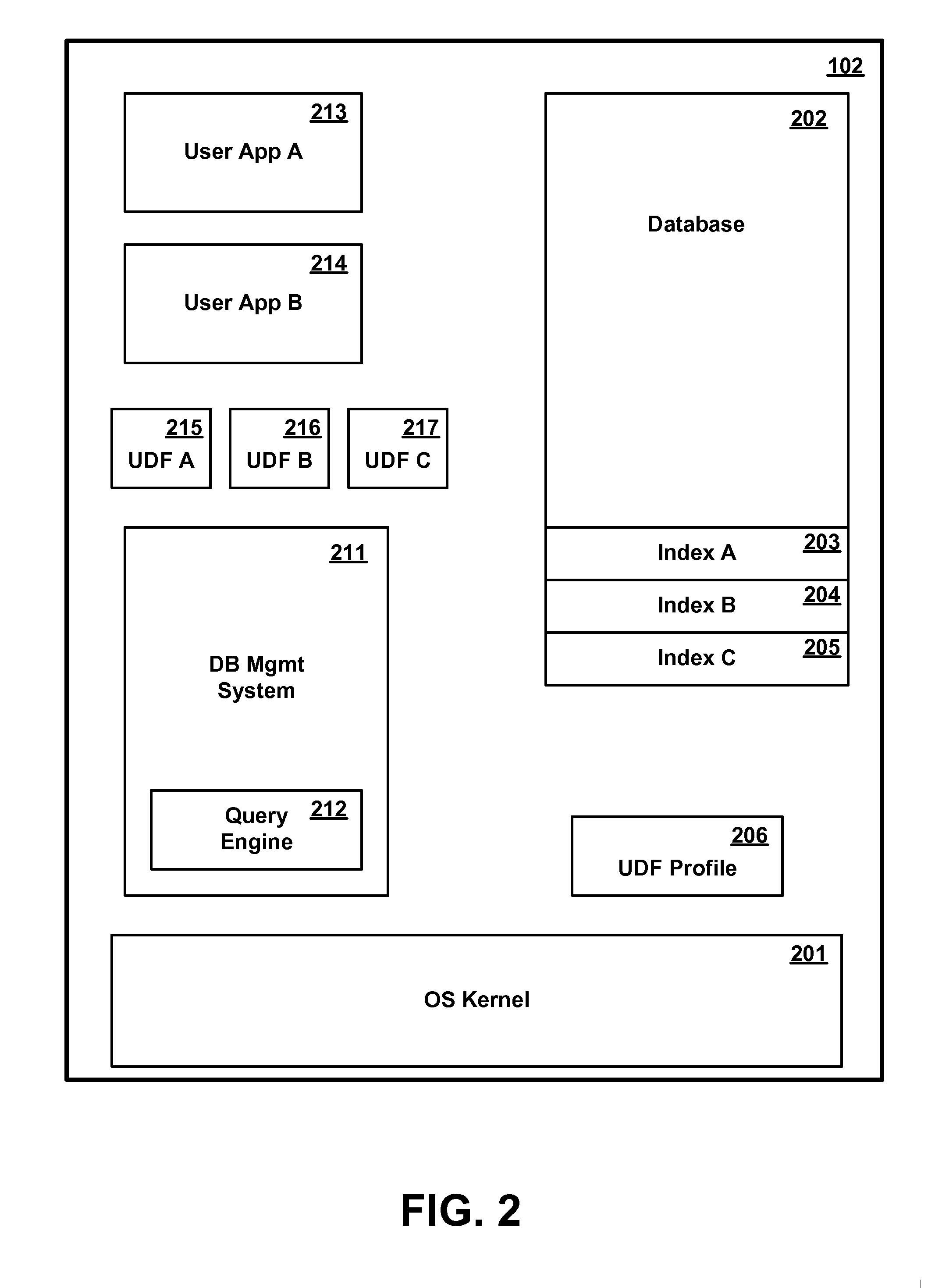
User defined function database processing
InactiveUS20120130963A1Digital data information retrievalDigital data processing detailsUser-defined functionDatabase
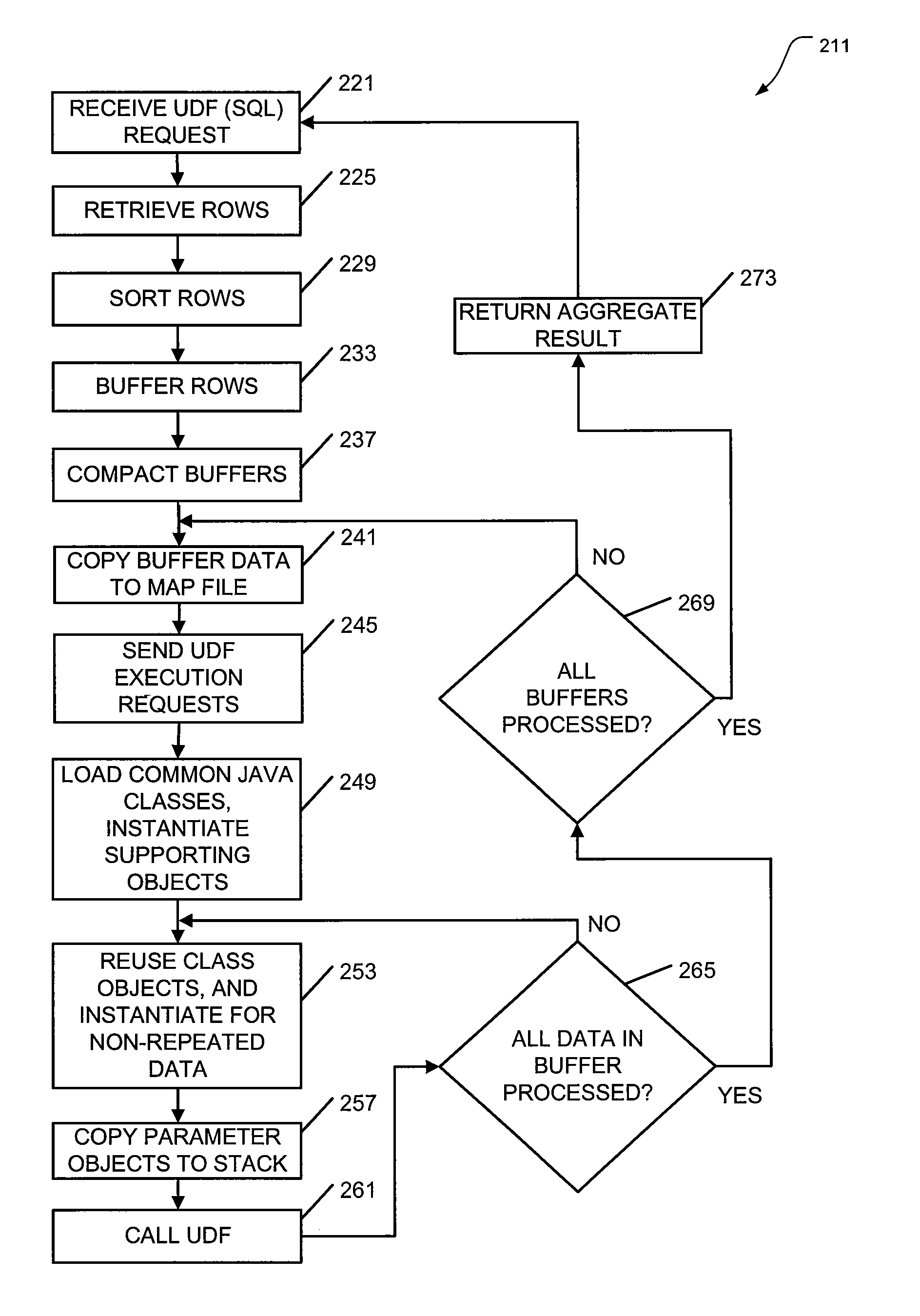
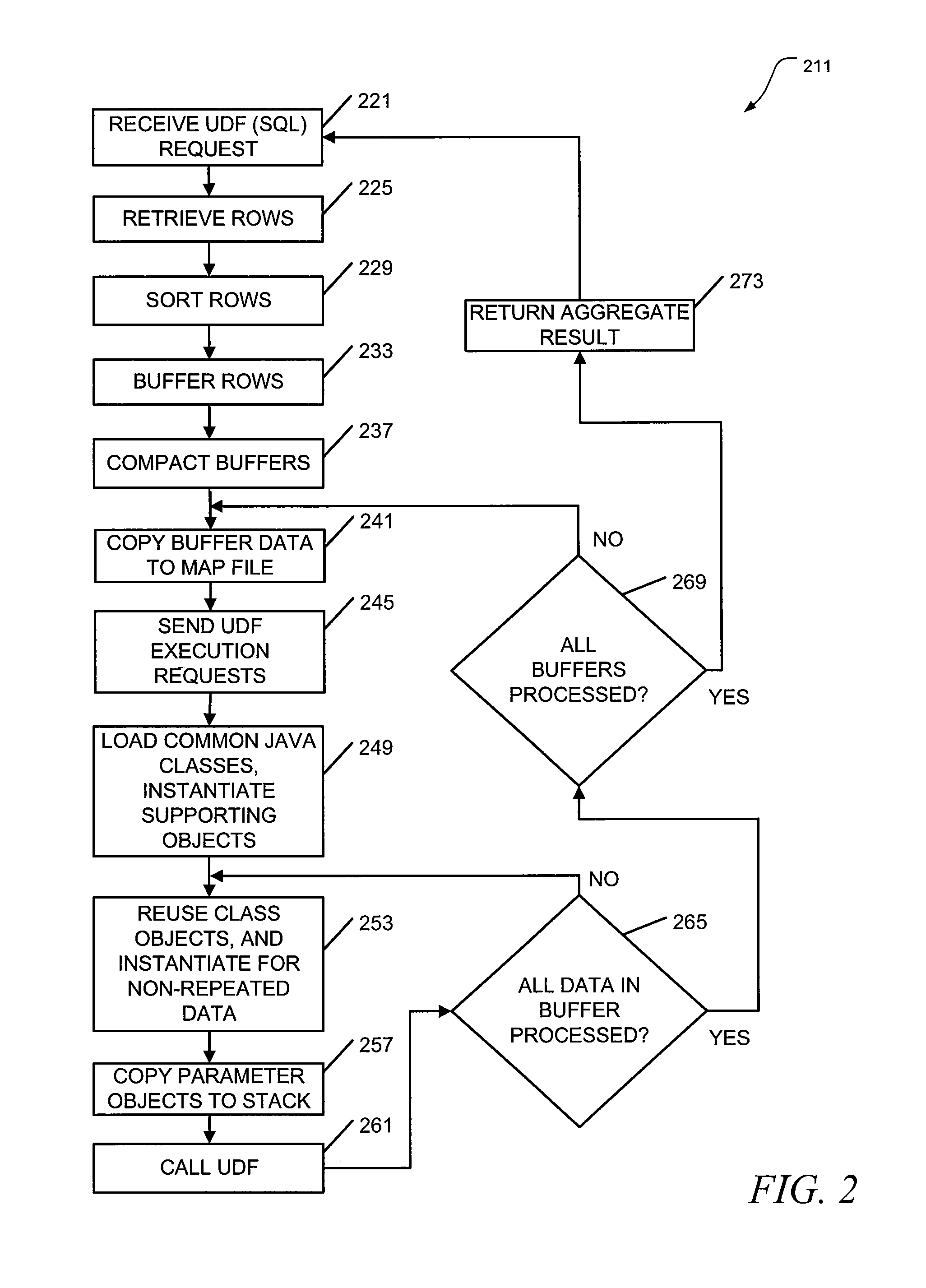
Apparatus, systems, and methods may operate to retrieve multiple rows of a database in response to receiving a request to execute an aggregate user defined function (UDF) over the multiple rows, to sort each of the multiple rows into common groups, grouping together individual ones of the multiple rows that share one of the common groups, and to send UDF execution requests to apply the aggregate UDF to aggregate buffers of the common groups to produce an aggregate result, so that one of the UDF execution requests and one context switch are used to process each of the aggregate buffers used within one of the groups to provide at least one intermediate result that can be processed to form the aggregate result. Other apparatus, systems, and methods are disclosed.
Owner:TERADATA US
Mapping binary objects in extended relational database management systems with relational registry
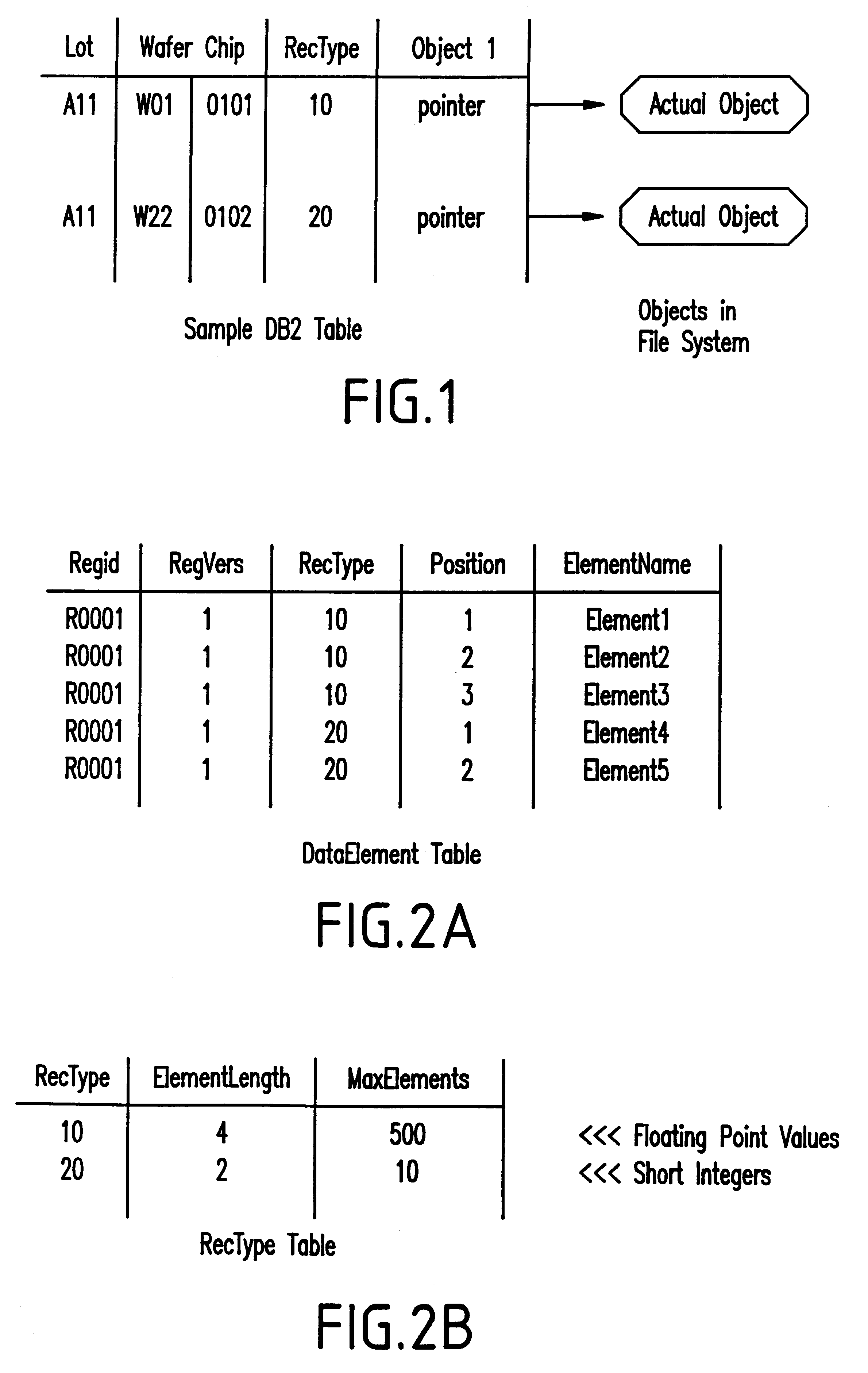
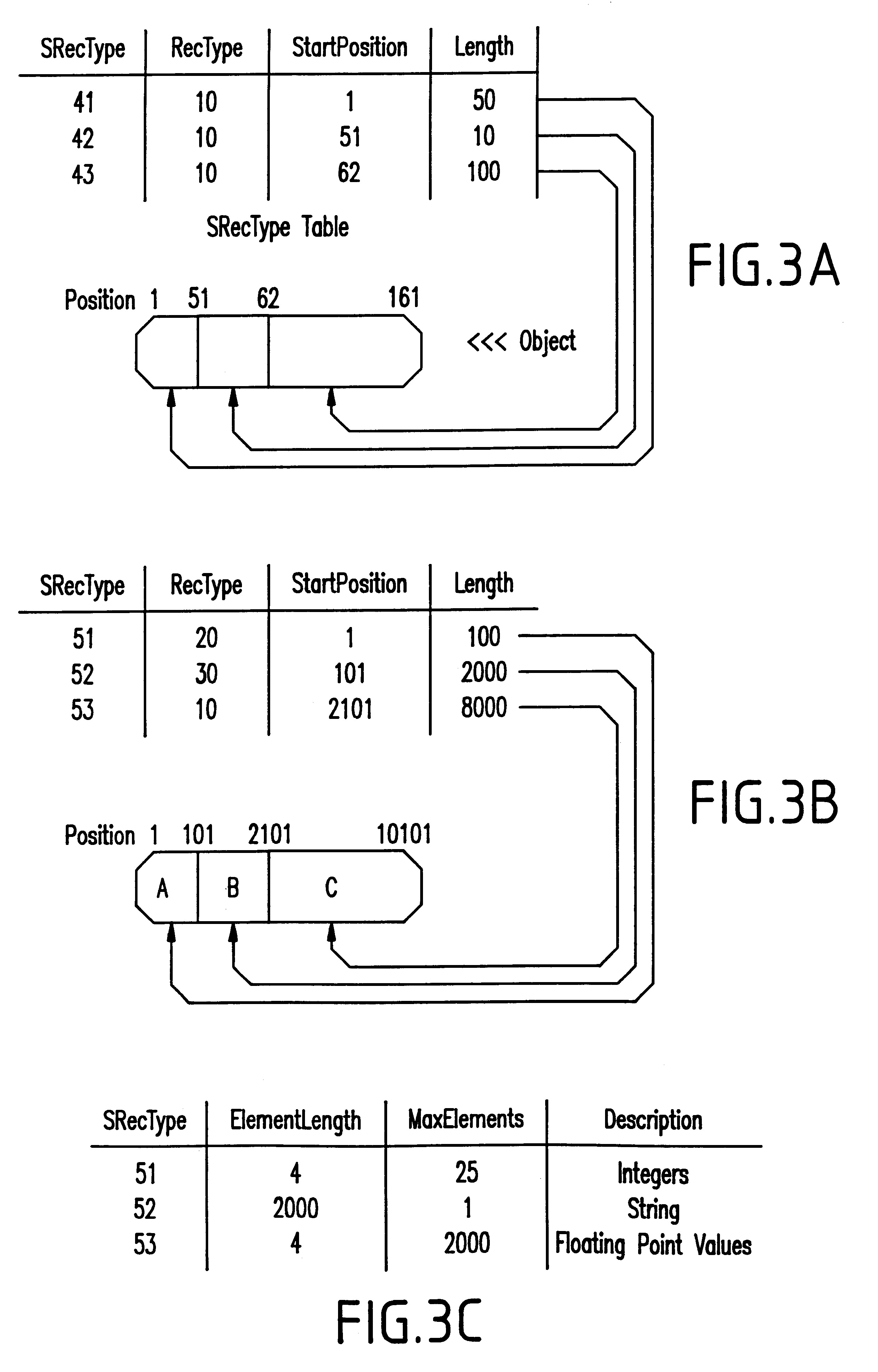
InactiveUS6502086B2Small footprintReduce maintenanceData processing applicationsDigital data information retrievalData processing systemAutomated data processing
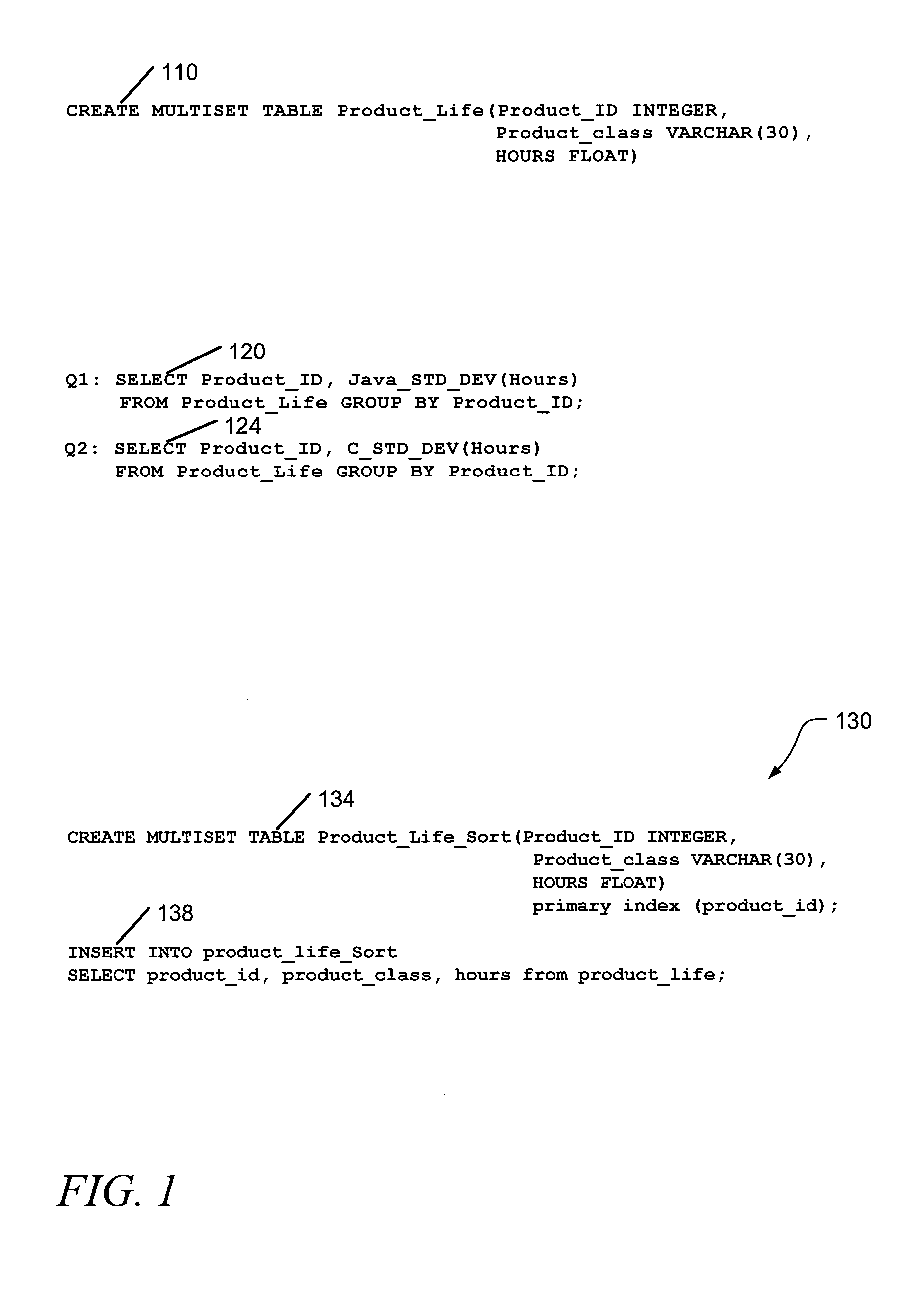
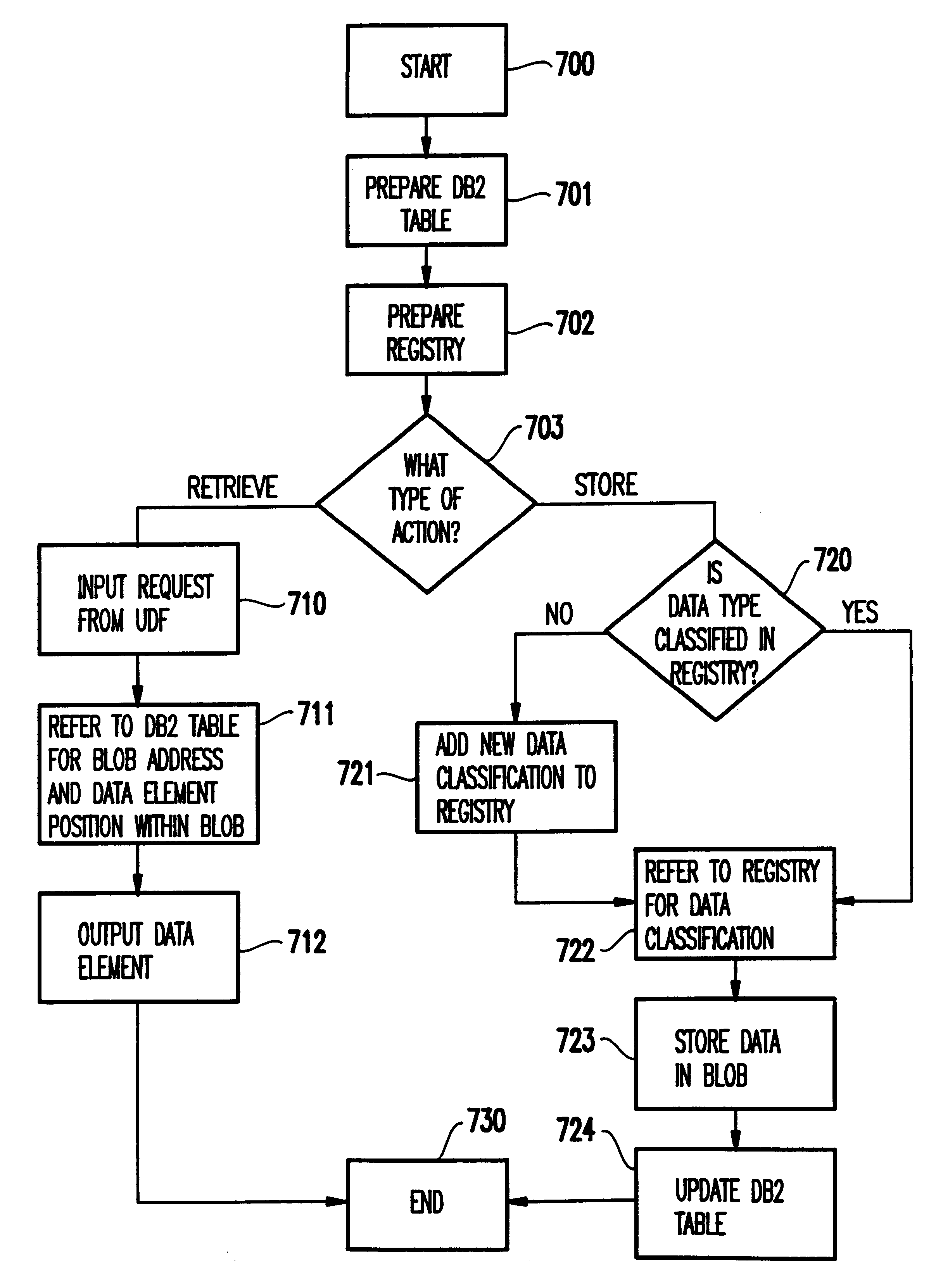
An automated data processing system includes a relational database engine, storage devices having a database table, registry and binary large objects created and updated by the relational database engine and a user defined function engine retrieving data elements stored in the binary large objects. The registry includes data element classifications. The database table includes relational information of the data elements, the data element classifications and pointers to the binary large objects, and the relational database engine creates and updates the binary large objects based on the database table and the registry.
Owner:IBM CORP
Customizable drag and drop for industrial software applications
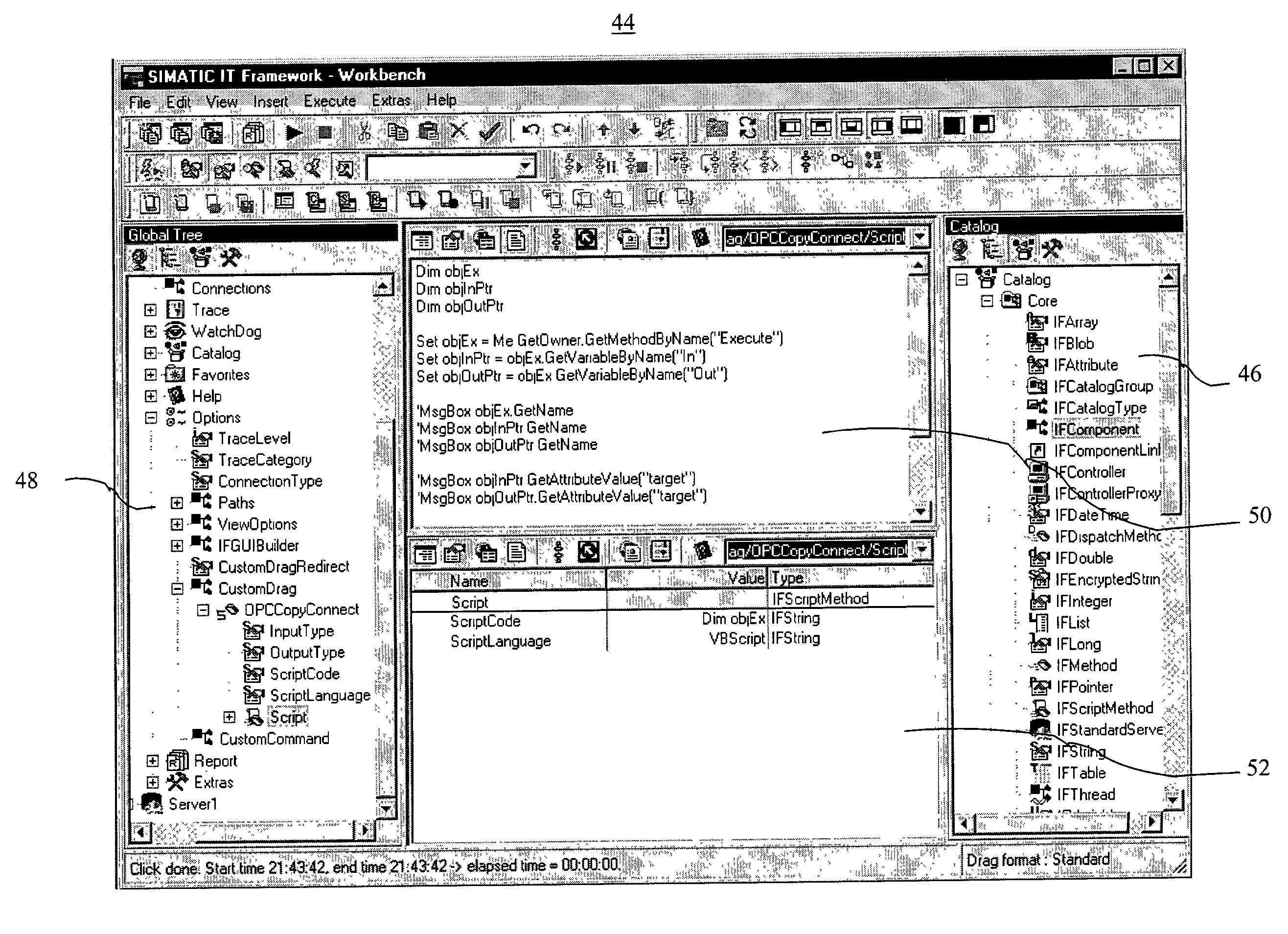
ActiveUS7337409B2Extend semanticsCathode-ray tube indicatorsSpecial data processing applicationsDrag and dropSpecific function
Customizable Drag & Drop enables easy activation of user defined or project specific functions concerning two related objects: A user interface graphically displays objects of a particular module. An extending function extends the drag and drop operation to allow the user to define a new set of semantics that is applied when a drag and drop operation is executed. In this way communication can be established using Customizable Drag & Drop extended by a user defined function. Also definition and modification of the deployment of an industrial automation system and hyperlinking of objects in manufacturing execution systems is achieved by Customizable Drag & Drop.
Owner:SIEMENS AG
Firearm system for data acquisition and control
Owner:MCRAE MICHAEL WILLIAM
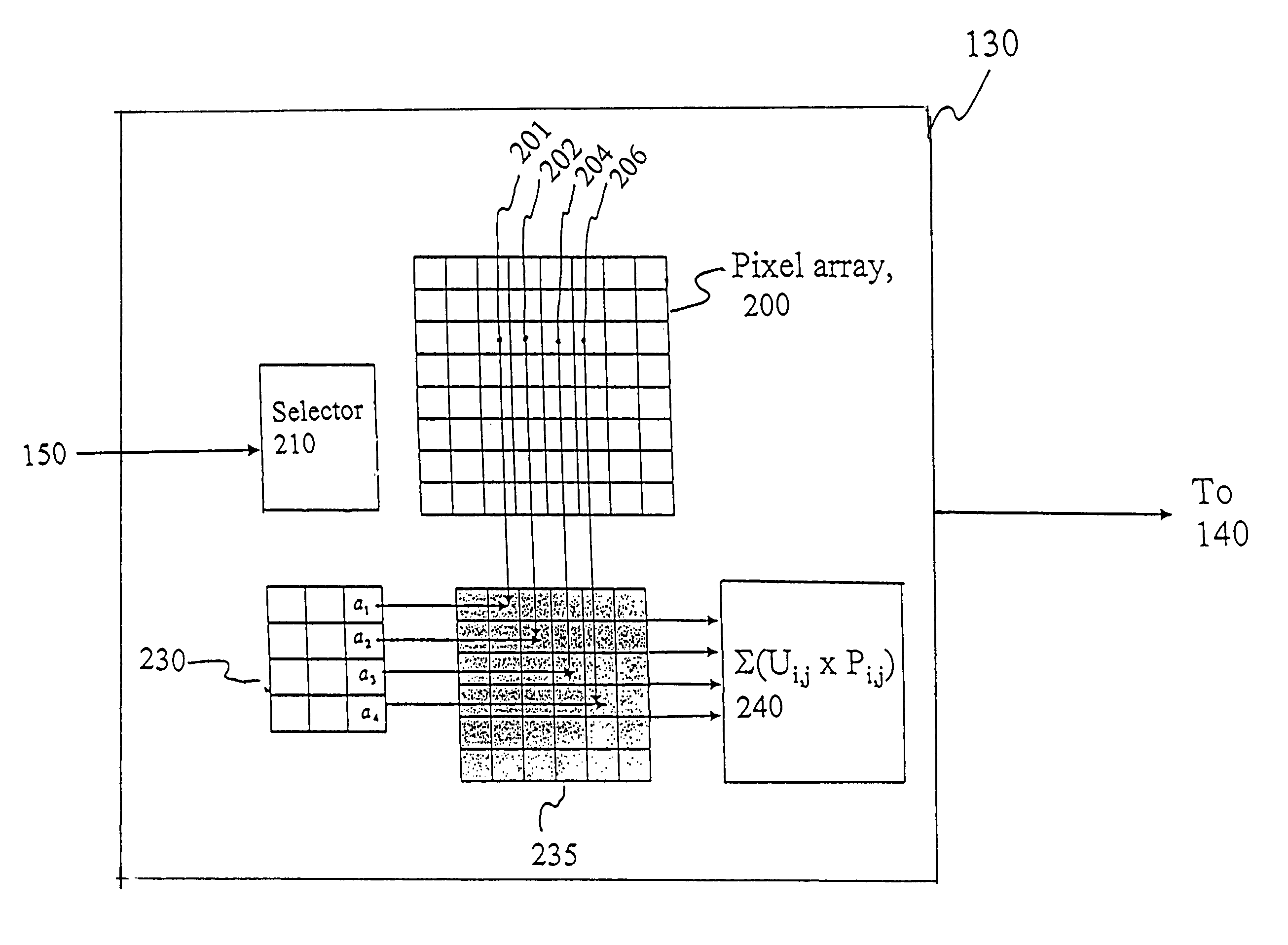
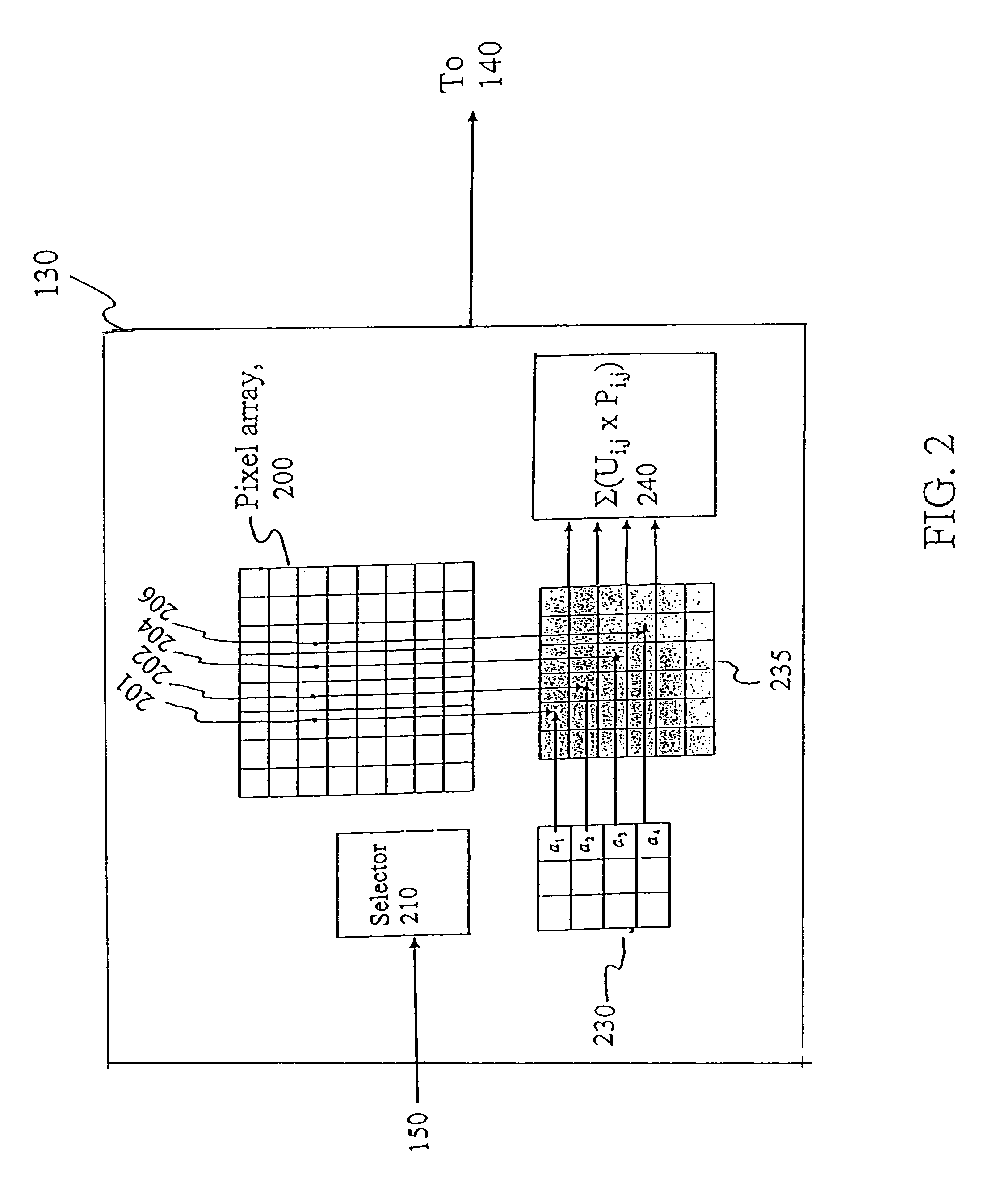
High throughput reconfigurable data analysis system
InactiveUS7471831B2Rapid and programmable analysisTelevision system detailsElectric signal transmission systemsProgrammable circuitsData analysis system
The present invention relates to a system and method for performing rapid and programmable analysis of data. The present invention relates to a reconfigurable detector comprising at least one array of a plurality of pixels, where each of the plurality of pixels can be selected to receive and read-out an input. The pixel array is divided into at least one pixel group for conducting a common predefined analysis. Each of the pixels has a programmable circuitry programmed with a dynamically configurable user-defined function to modify the input. The present detector also comprises a summing circuit designed to sum the modified input.
Owner:CALIFORNIA INST OF TECH
Parallelism performance analysis based on execution trace information
A system for conducting performance analysis for executing tasks. The analysis involves generating a variety of trace information related to performance measures, including parallelism-related information, during execution of the task. In order to generate the trace information, target source code of interest is compiled in such a manner that executing the resulting executable code will generate execution trace information composed of a series of events. Each event stores trace information related to a variety of performance measures for the one or more processors and protection domains used. After the execution trace information has been generated, the system can use that trace information and a trace information description file to produce useful performance measure information. The trace information description file contains information that describes the types of execution events as well as the structure of the stored information. The system uses the trace information description file to organize the information in the trace information file, extracts a variety of types of performance measure information from the organized trace information, and formats the extracted information for display. The system can use default or user-defined functions to extract and format trace information for display. After the system displays one or more types of performance measure information, a user of the system can then interact with the system in a variety of ways to obtain other useful performance analysis information.
Owner:CRAY
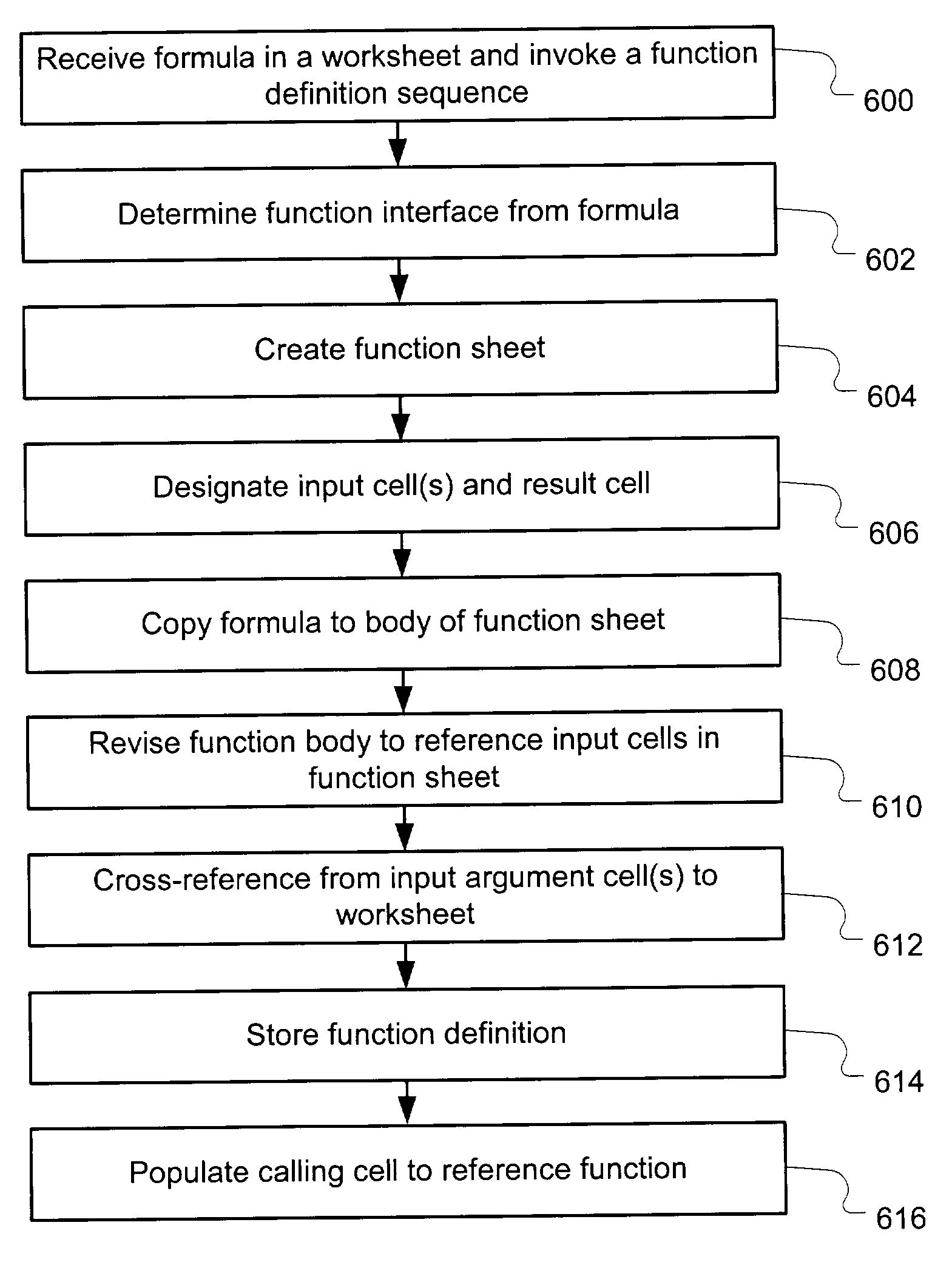
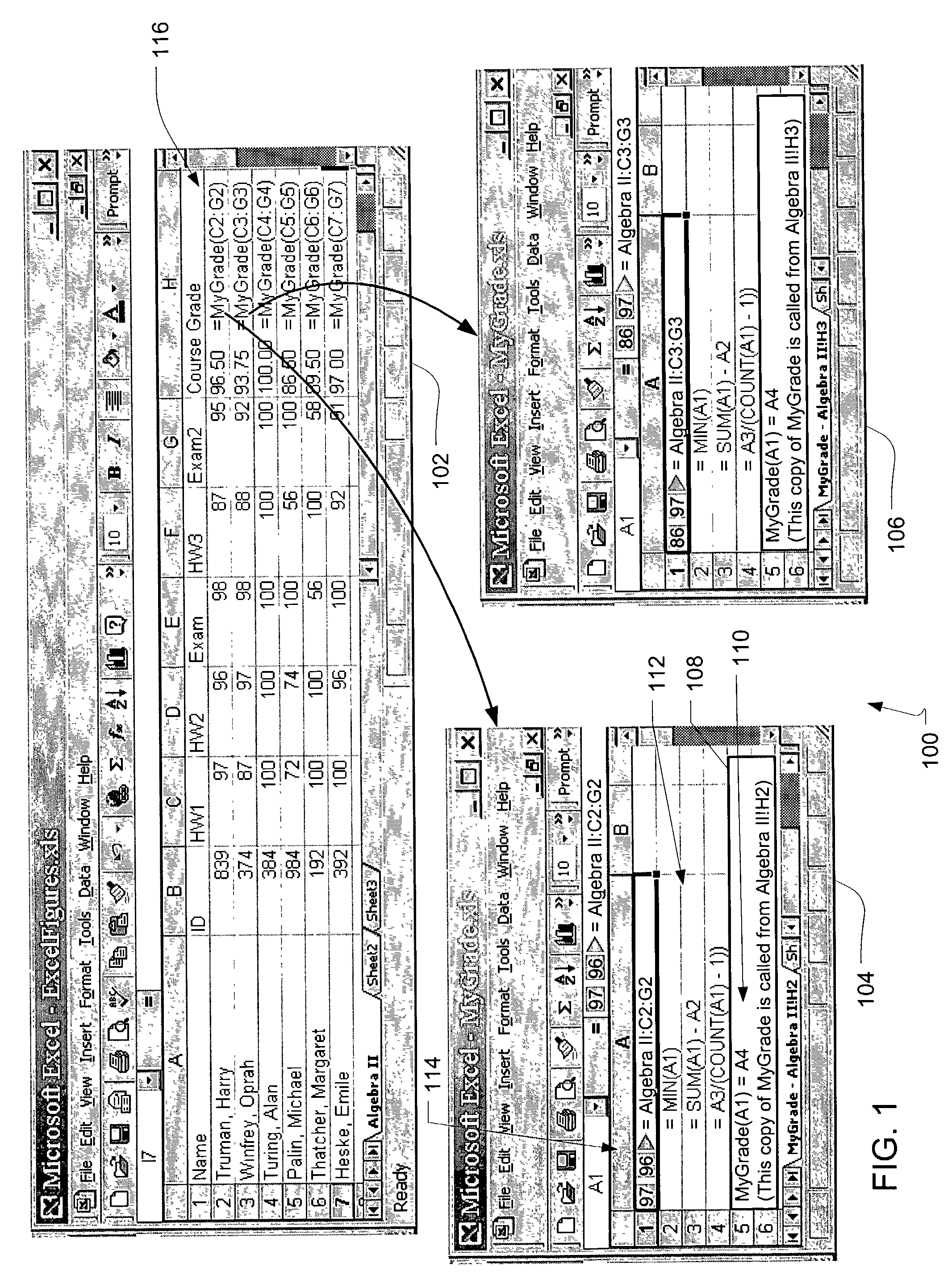
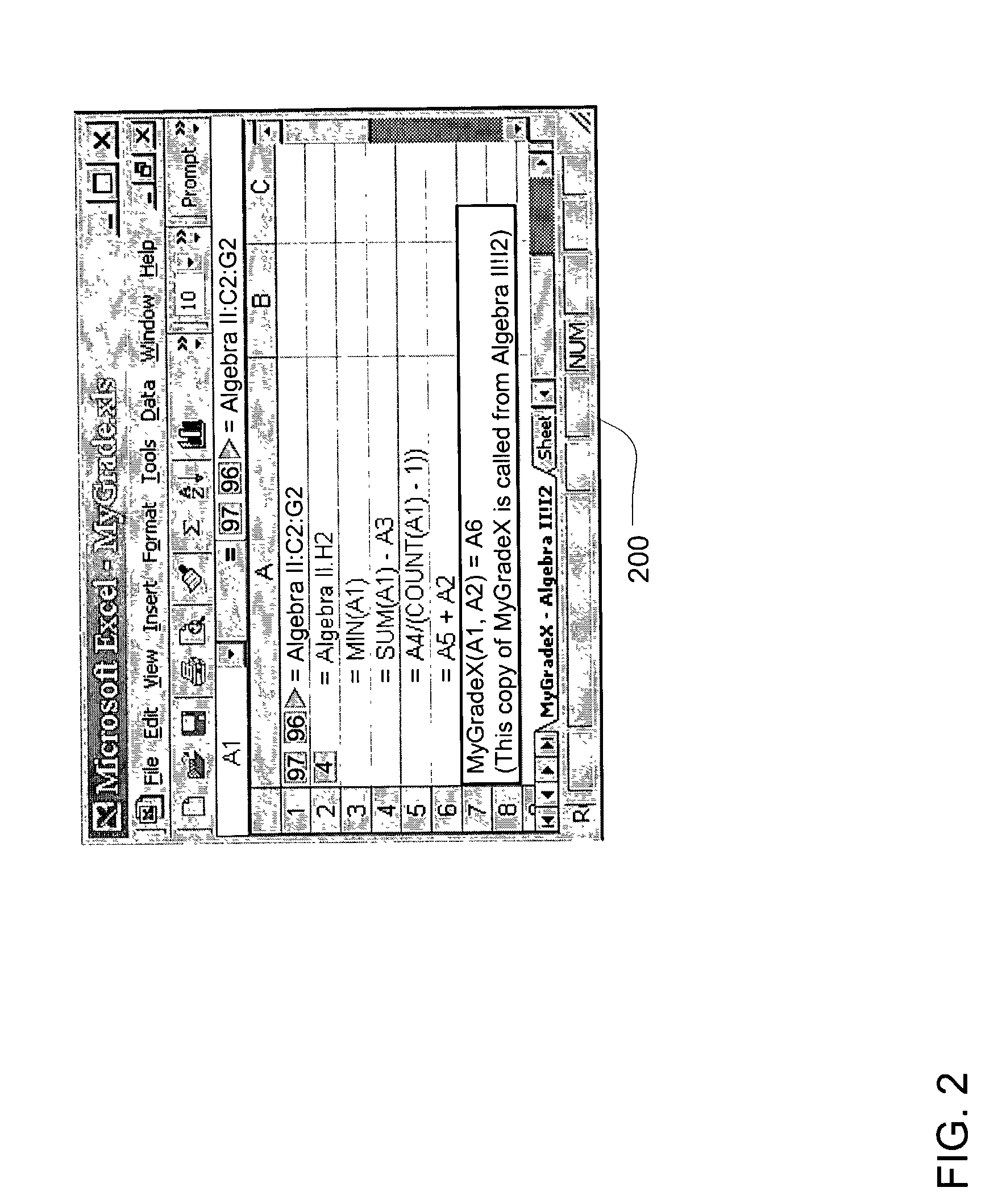
User defined spreadsheet functions
InactiveUS7266763B2Add featureData processing applicationsDigital data processing detailsProgramming languageElectronic form
A method of creating a user-defined function in a spreadsheet application is provided. The user-defined function is callable by a calling label in the spreadsheet application. A formula is received in the spreadsheet application. The formula is transferred to a function sheet of the spreadsheet application to define at least a portion of a function body. An interface is defined by identifying the calling label, an input parameter and a result parameter of the user-defined function. The function body operates on an argument corresponding to the input parameter and generates a result corresponding to the result parameter. The interface is stored in association with the function body to create the user-defined function.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for optimizing execution of database queries containing user-defined functions
ActiveUS20060026116A1Search strategyReduced execution timeData processing applicationsDigital data information retrievalDatabase queryUser-defined function
A query engine (or optimizer) which supports database queries having user-defined functions maintains historical execution data with respect to each of multiple user-defined functions. The historical execution data is dynamically updated based on query execution performance. When executing a query having user-defined functions, the query engine uses the historical execution data to predict an optimal evaluation ordering for the query conditions and, preferably, to dynamically adjust the evaluation order when appropriate. Preferably, the historical execution data includes historical execution time of the user-defined function and proportion of evaluated records which satisfied the query parameters.
Owner:IBM CORP
Method of compiling schema mapping
A method for compiling a mapping between a source schema and a target schema is provided. The method comprises multiple passes, including determining source node dependencies, matching hierarchy, and generating code. The method may further comprise initializing node dependency memory prior to determining source node dependencies, and freeing node dependency memory after code generation. The compiler algorithm provides for compiling user-defined functions in the mapping into the compiled representation. Another aspect of the invention provides for generating an XSL code representation of the mapping. An XSL style sheet representation may thus be generated from a visual mapping in accordance with the invention.
Owner:MICROSOFT TECH LICENSING LLC
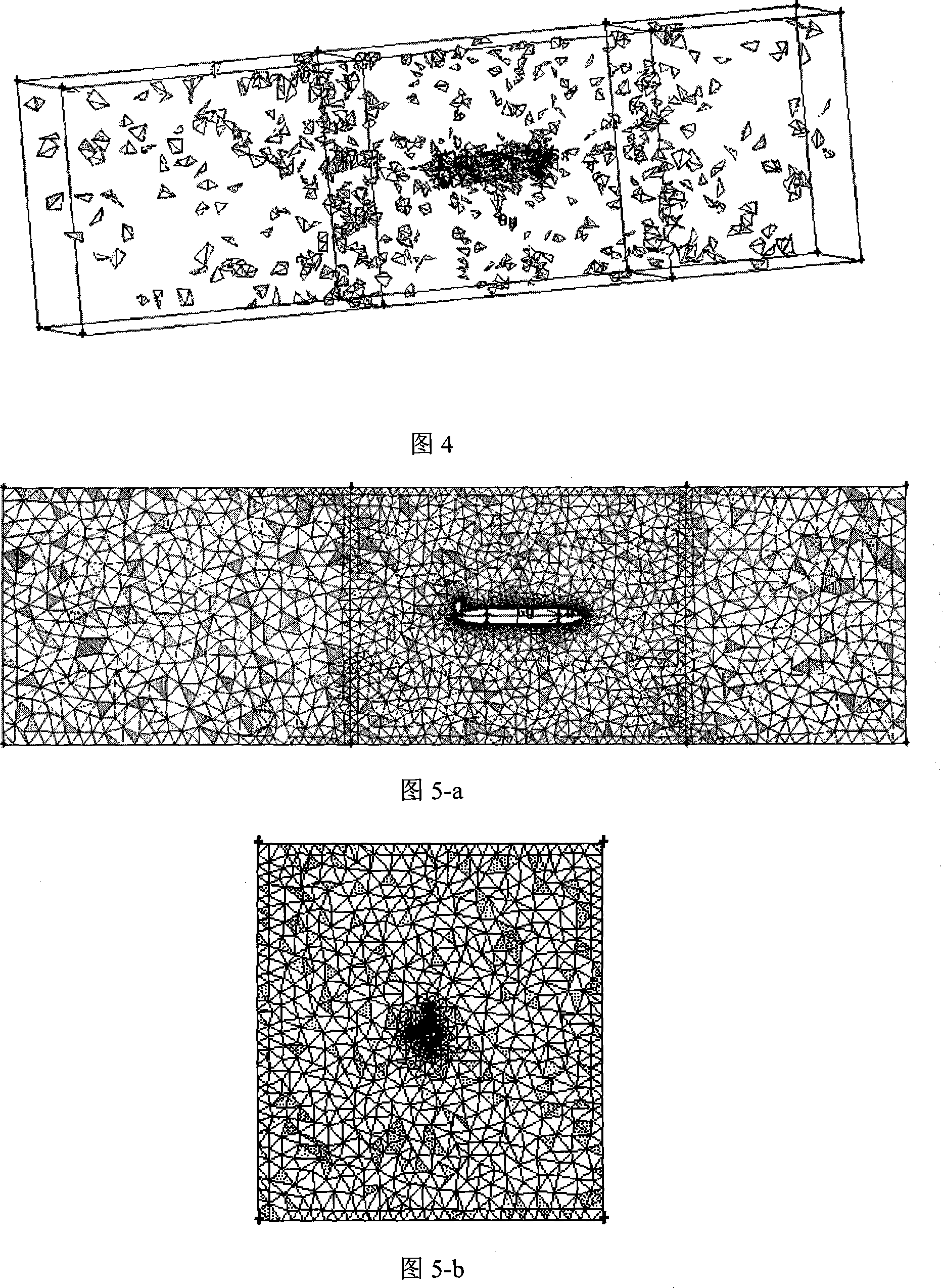
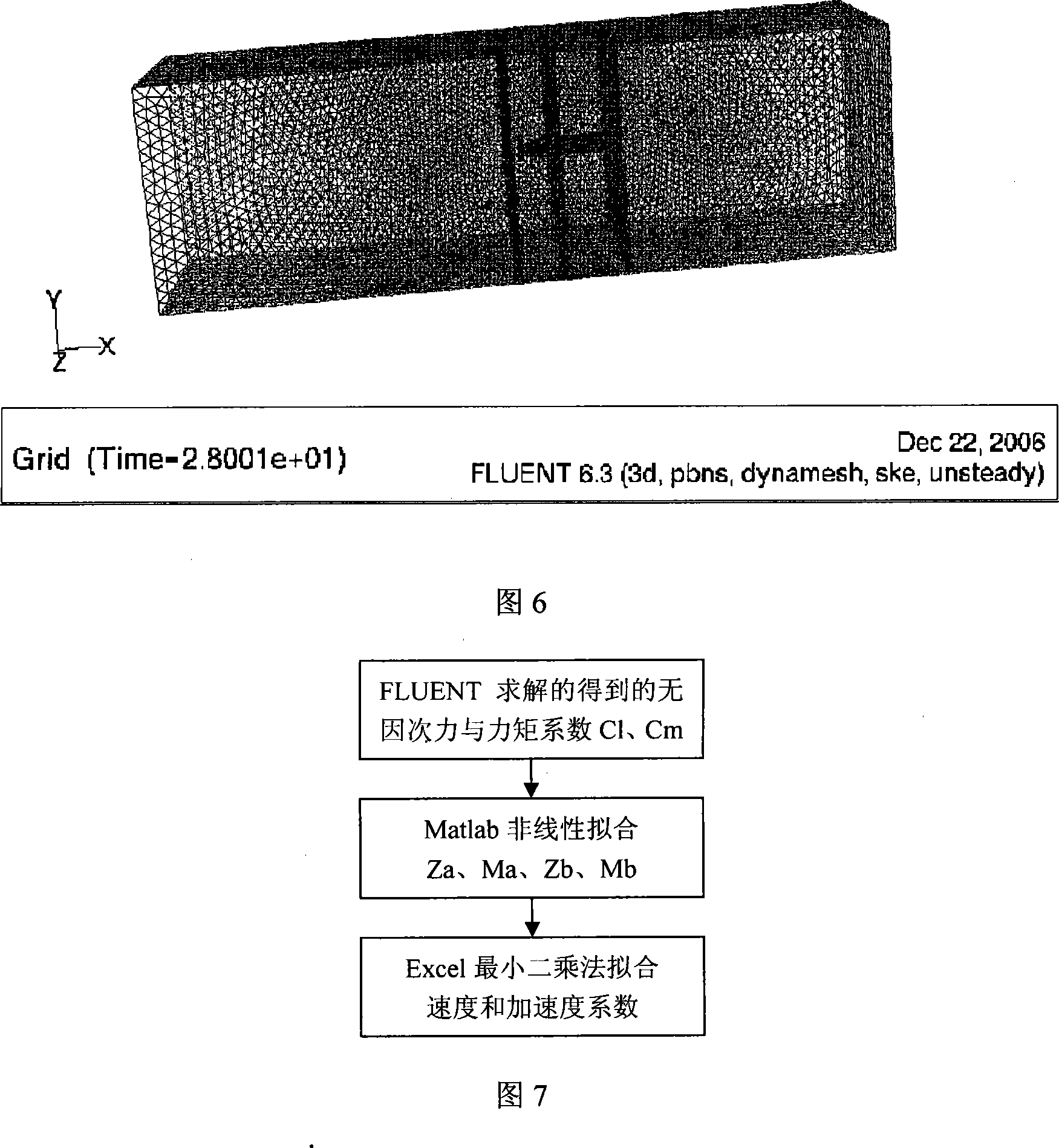
Digital ship model planar motion mechanism experimental method based on CFD software
InactiveCN101246515AAchieve pure swaying motionAccurate settingSustainable transportationSpecial data processing applicationsVertical planeResearch Object
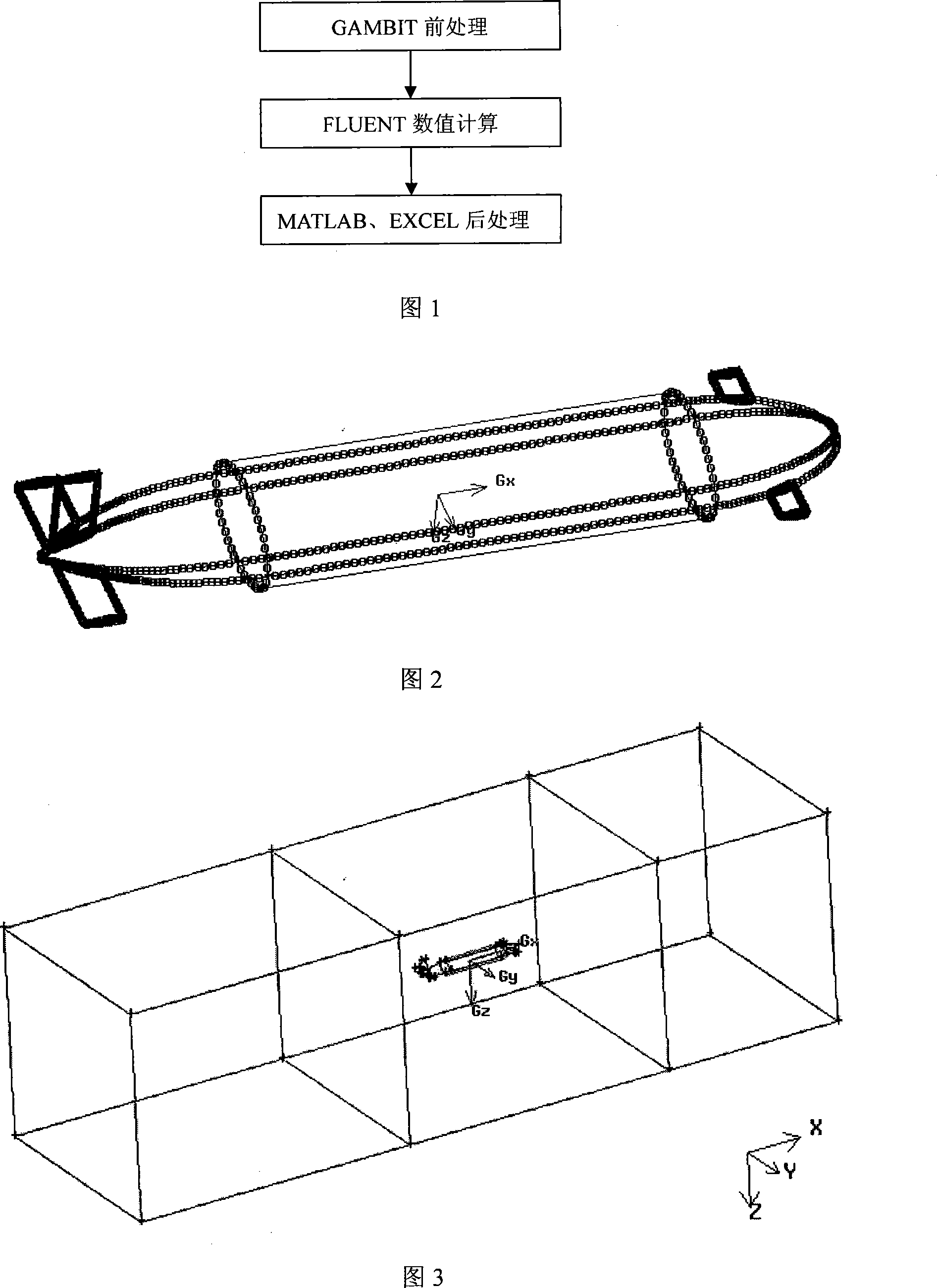
The invention provides a digital ship model plane motion organization experimental method based on computation fluid dynamics CFD software FLUENT. The method includes applying a FLUENT pre-process software GAMBIT to establish a research object model and a control domain; arranging a triangle grid on the model surface, then arranging a unstructured grid in the control domain; setting the boundary condition, joining an user-defined function UDF document, introducing dynamic grid technology, using a finite volume method based on the complete unstructured grid, realizing a pure swaying movement, a pure rising and falling movement, a pure oscillatory movement, a pure pitching movement and a pure rolling movement carried on by a plane motion organization experiment; applying a science computation software MATLAB to do Fourier expansion of a force and a moment coefficient obtained by the FLUENT, being fitted by EXCEL least squares method, obtaining a hydrodynamic force coefficient of a vertical plane and a horizontal plane as well as the related hydrodynamics analysis by dimensionless. The invention carries on the digit plane motion organization experiment using the CFD software, can satisfy the request of hydrodynamic force data in the design initial period of a submersible.
Owner:HARBIN ENG UNIV
Mapping binary objects in extended relational database management systems with relational registry
InactiveUS20010049693A1Small footprintReduce maintenanceDigital data information retrievalData processing applicationsData processing systemAutomated data processing
An automated data processing system includes a relational database engine, storage devices having a database table, registry and binary large objects created and updated by the relational database engine and a user defined function engine retrieving data elements stored in the binary large objects. The registry includes data element classifications. The database table includes relational information of the data elements, the data element classifications and pointers to the binary large objects, and the relational database engine creates and updates the binary large objects based on the database table and the registry.
Owner:IBM CORP
Security code activated access control system
InactiveUS6950944B2Easy to controlImprove securityDigital data processing detailsUser identity/authority verificationControl systemCard security code
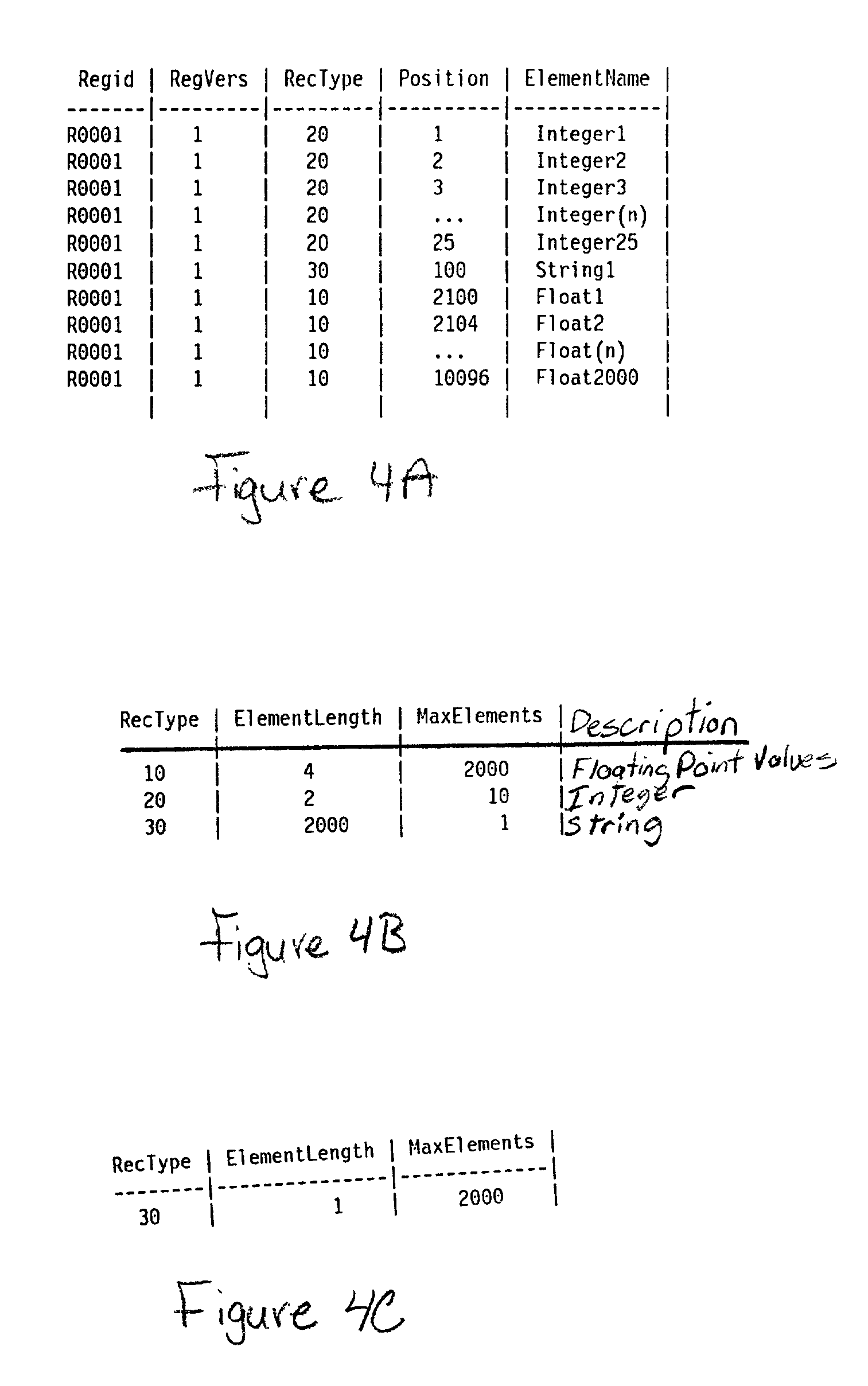
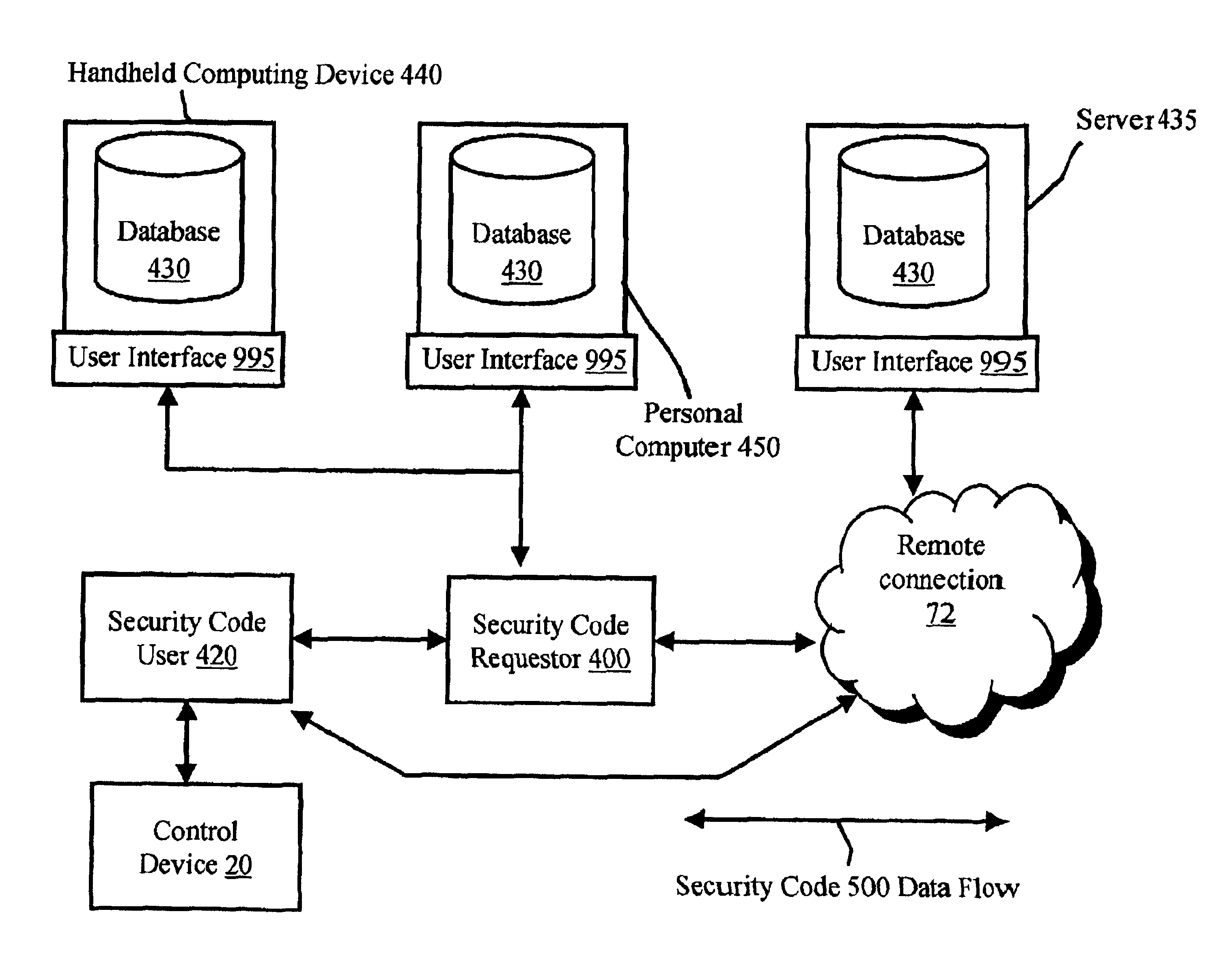
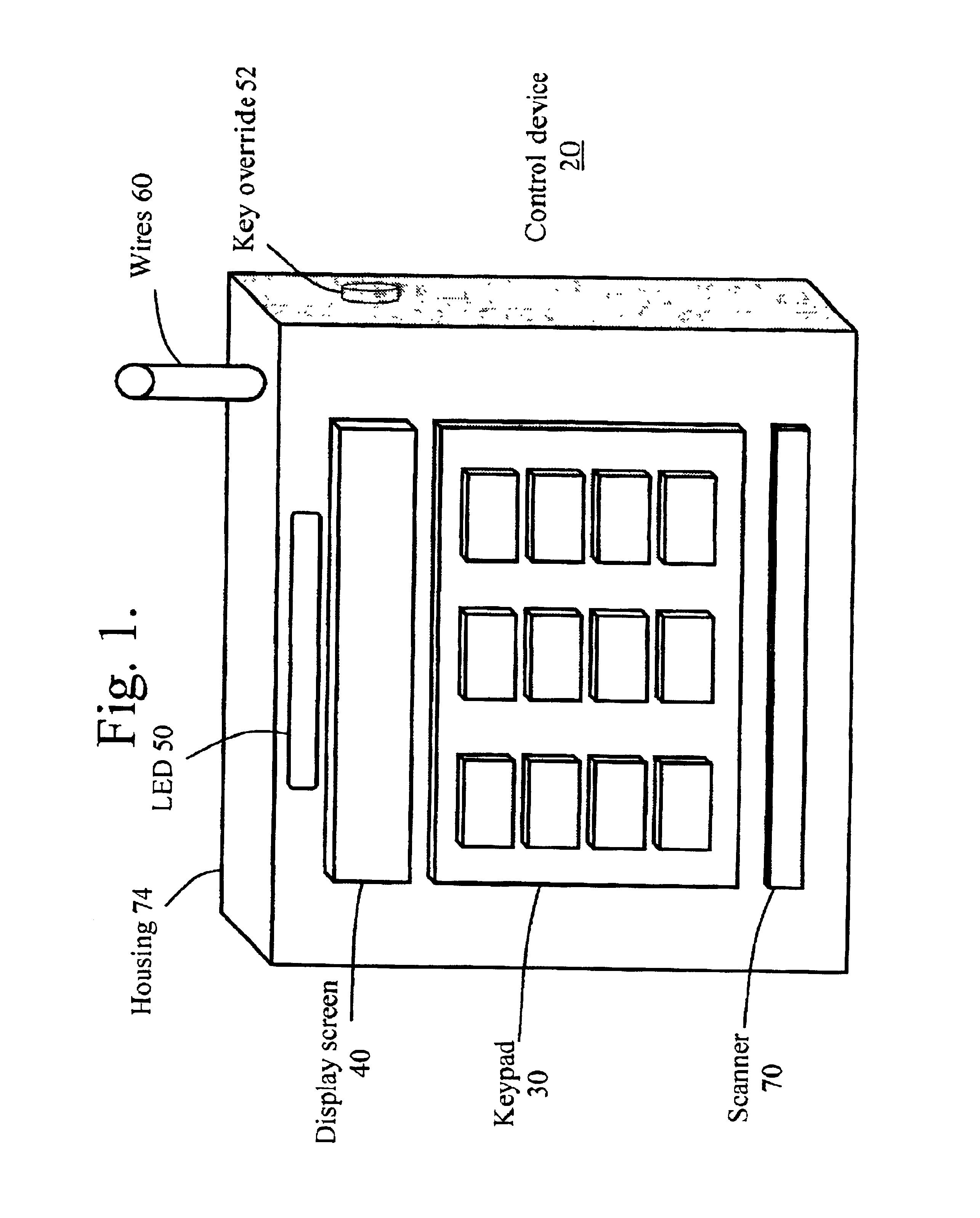
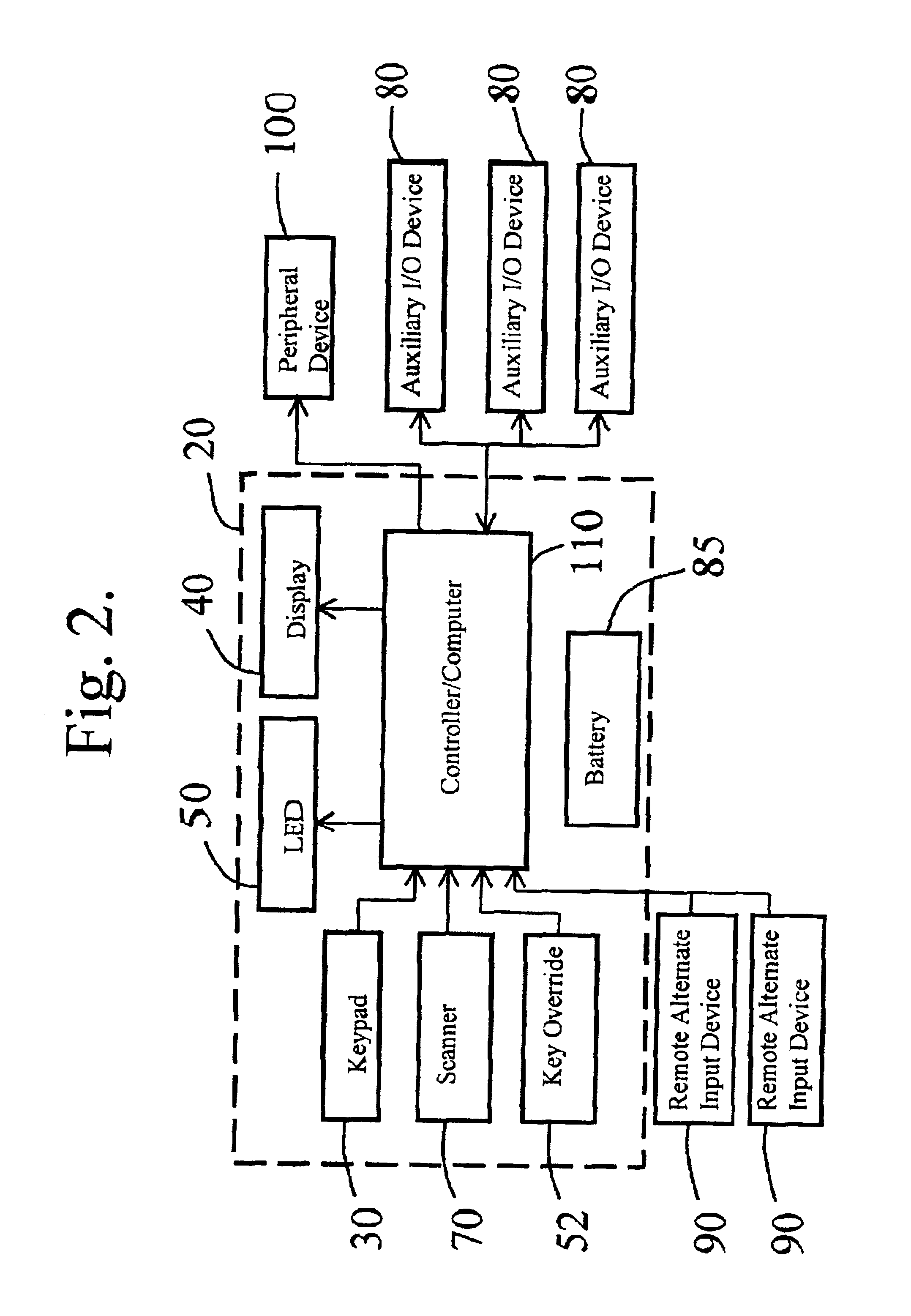
An access control system that utilizes security codes (500), a database (430), and a control device (20) is disclosed. Each security codes (500) is comprised of a unique key code (502) that provides security in addition to a use code (503) that is used to convey specific user defined functions. The use code (503) may be determined by the security code requester (400) at the time of security code (500) charge out from the database (430). The database (430) controls the issuance of security codes (500) and the control device (20) validates the key code (502) within the security code (500) against key codes (502) within control device (20) memory and if valid, performs an action based on the validation of the use code (503) parameters. As the key codes (502) that are within the control device (20) memory are used, the control device (20) then self-regenerates the key codes (502) in order to extend the control device (20) service life indefinitely. The database (430) and the control device (20) have security code (500) activities that are synchronized, though the two operate independently and are not electronically connected. The system provides a secure interface for obtaining access authority from the database (430). Security code requesters (400) contact the database (430) and request security codes (500) in order to activate a specific control device (20). After database (430) issuance, the security codes (500) are then input by the security code user (420) at the control device (20) location and activates the control device (20) if the key code (502) matches the key code (502) within the control device (20) and the use code (503) parameters are validated by the control device (20). The control device (20) and the database (430) key codes (502) are synchronized. This allows an unlimited supply of security codes (500) to be issued by the database (430) and used by the control device (20).
Owner:YAGER DAVID FR +1
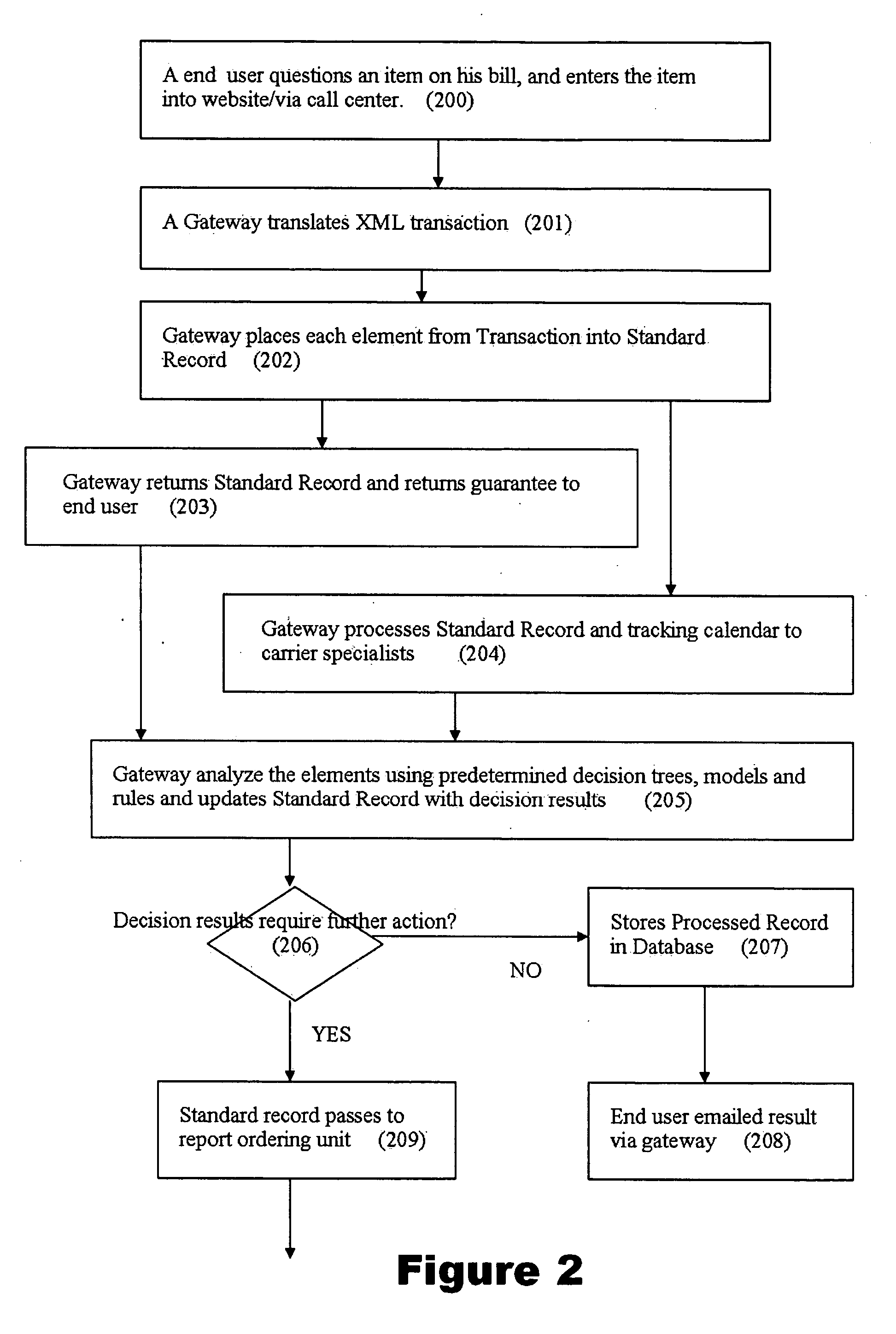
Dispute resolution processing method and system
InactiveUS20070027919A1Buying/selling/leasing transactionsSpecial data processing applicationsDecision modelDecision taking
A computer-implemented dispute resolution method includes receiving a dispute query from a user and generating a record based on the dispute query. A decision is electronically generated, including applying the record to a workflow algorithm including representations of one or more business rules, one or more segmentation or decision trees or both, one or more expression sequences, one or more data structures, one or more user-defined functions, and / or one or more decision models. It is determined whether to gather further information or take other further action based on said decision. The record is updated according to the decision, and stored. A result of the dispute query is communicated to the user based on the record.
Owner:MASTEL MISSY SUE
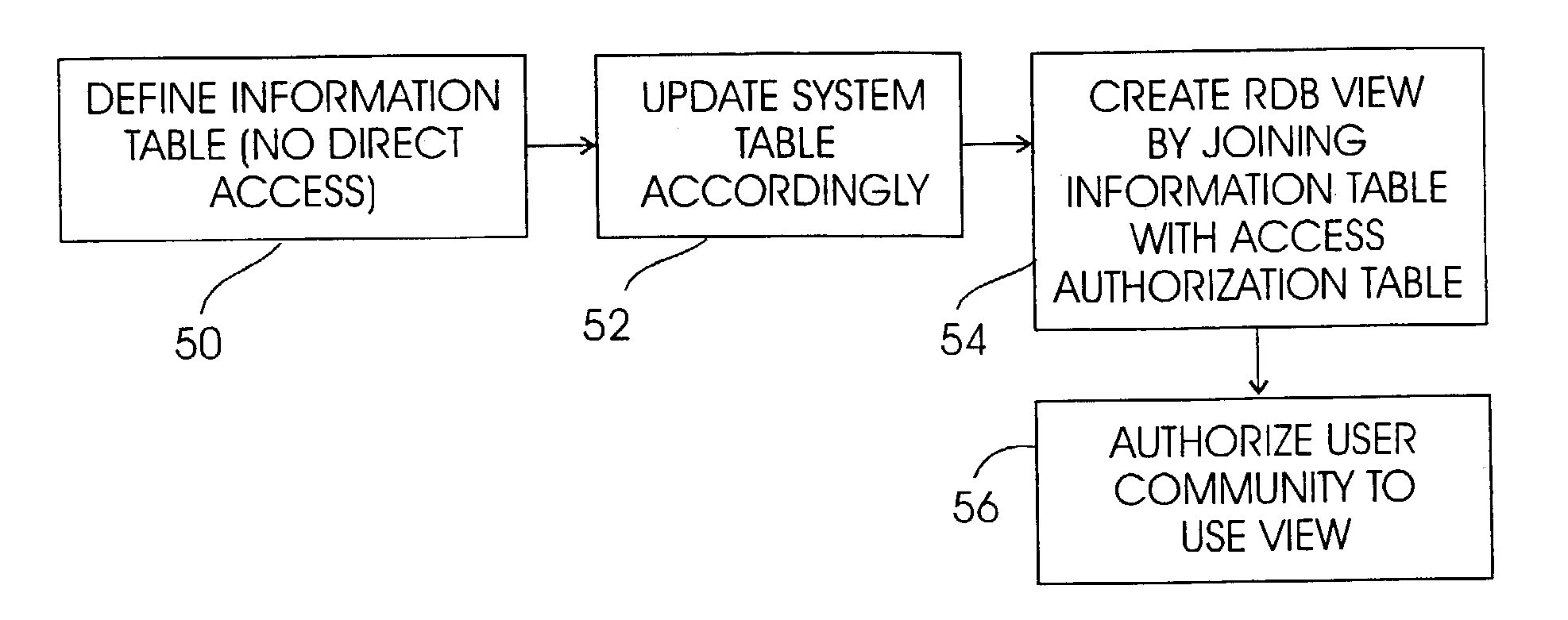
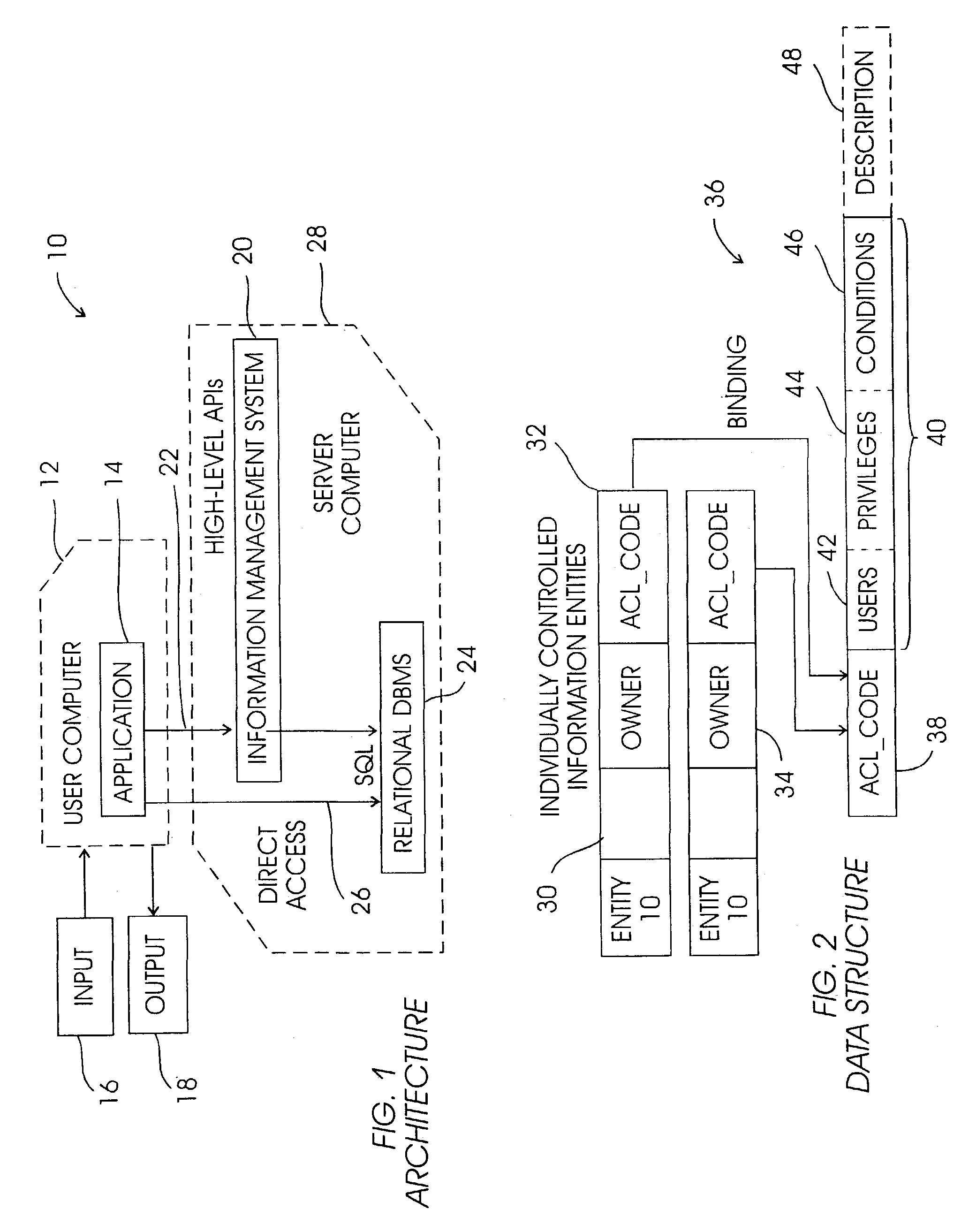
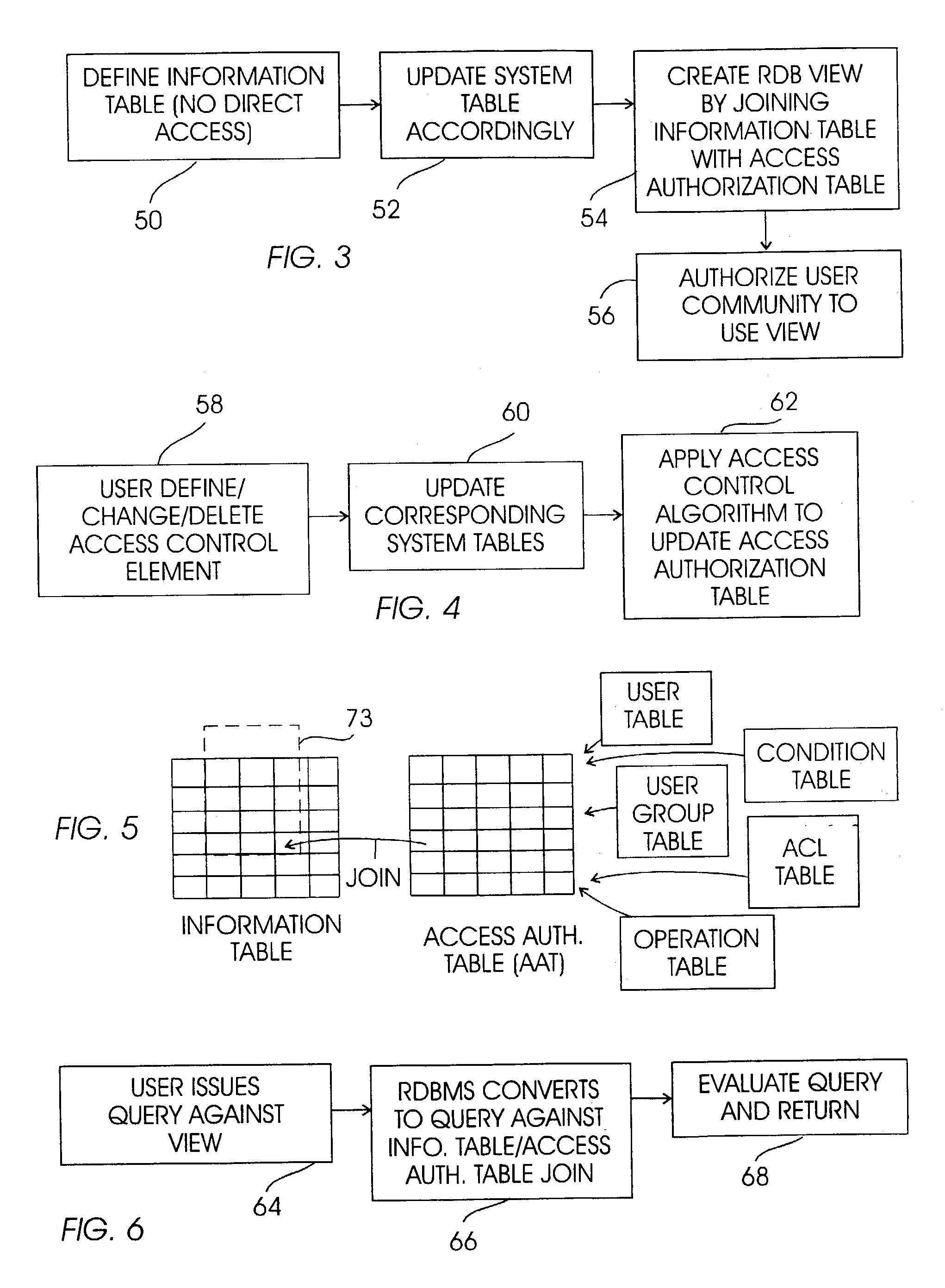
System and method for RDBMS to protect records in accordance with non-RDBMS access control rules
InactiveUS7216126B2Data processing applicationsDigital data processing detailsRelational database management systemApplication software
A system and method are provided for an information management system (IMS) having an underlying relational database management system (RDBMS) that allows applications to access the RDBMS directly for improved performance without going through the IMS, while maintaining access control. An access control list (ACL) is generated, with tables in the RDBMS being bound using codes in the ACL. At run time or, more preferably, pre-run time, user-defined functions (UDF) evaluate access control attributes and generate an access authorization table, which is joined with the appropriate information table(s) in response to a query against a view on the table. The view is presented to the querying user. Thus, access control rules are encapsulated in the view that is presented to the user.
Owner:IBM CORP
Flexible macrocell interconnect
InactiveUS6927601B1Improve fitGood flexibilitySolid-state devicesLogic circuits using elementary logic circuit componentsProgrammable logic deviceEngineering
Methods and apparatus for novel routing structures and methods that improve fitting of user-defined functions onto programmable logic devices. In particular, second time fitting is improved. Exemplary structures and methods include allowing product terms to be expanded using inputs from more than one neighboring macrocell by providing multiple expansion and bypassing paths. Also, product term OR shifting prevents macrocell output stages from being buried and made inaccessible, and macrocell outputs are provided on expander word lines, increasing efficiency of those lines, as well as conserving routing resources. Expansion, bypassing, OR shifting, and expander word lines may terminate at logic array block boundaries or may continue beyond these boundaries to other logic array blocks.
Owner:ALTERA CORP
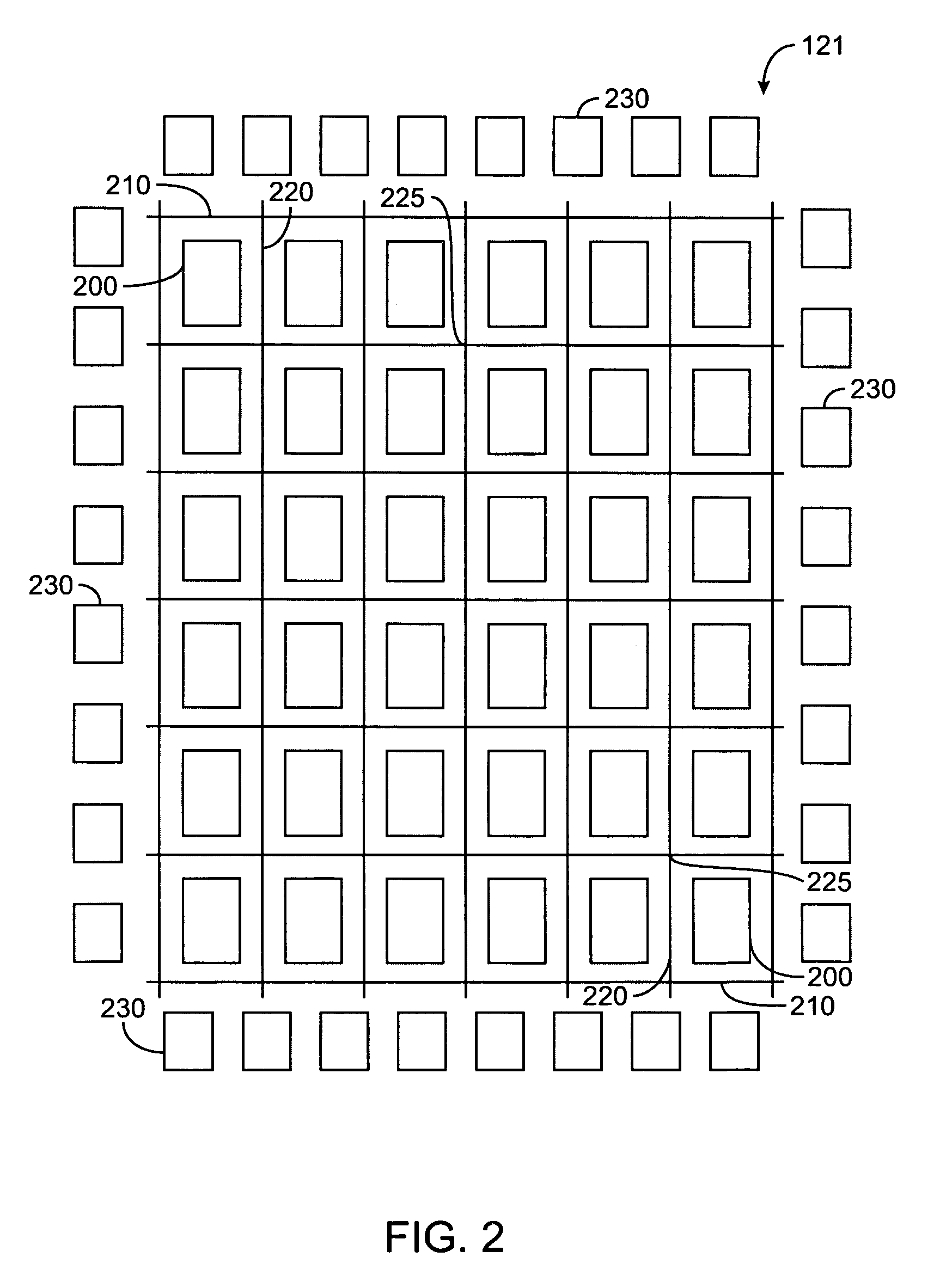
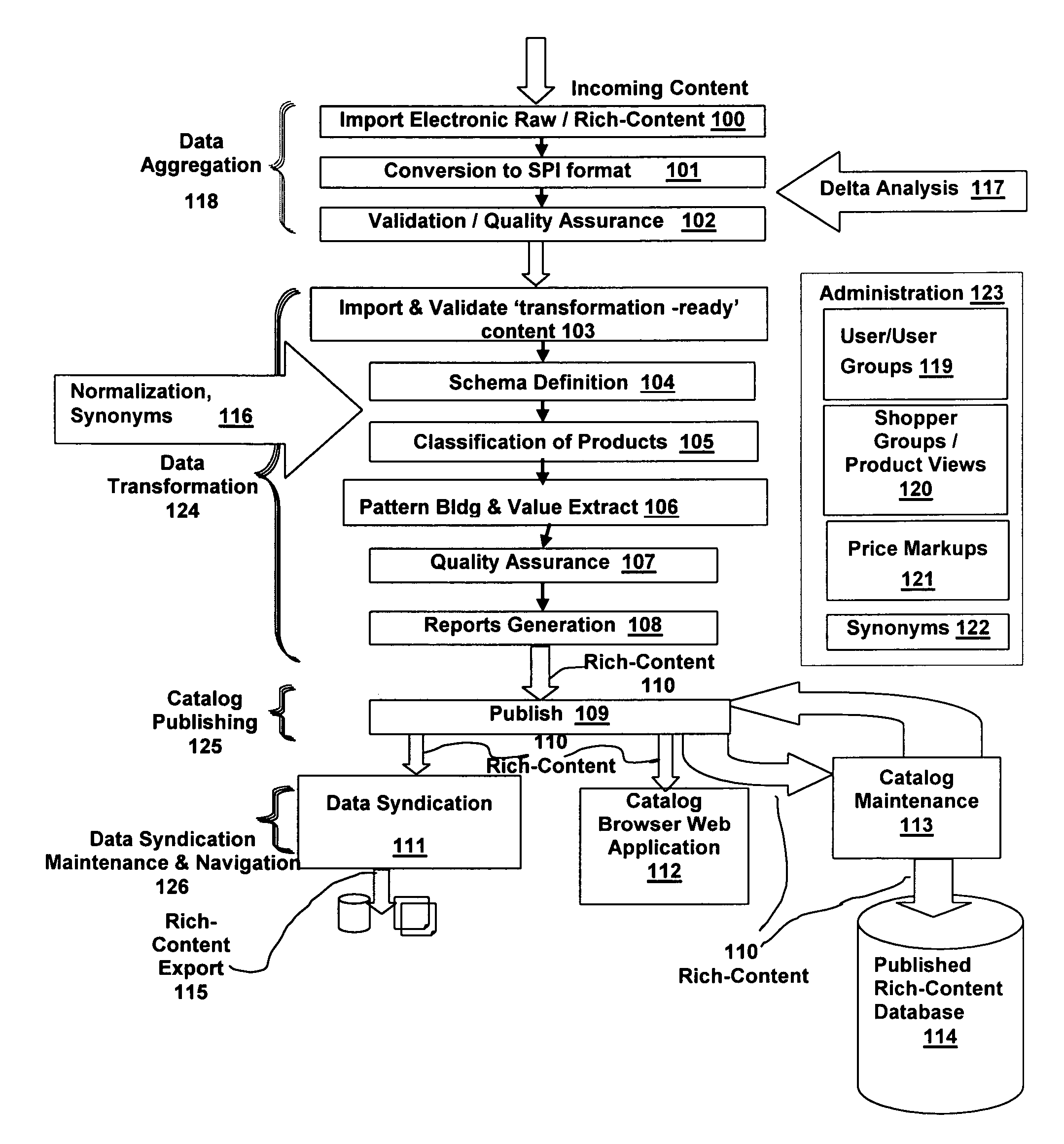
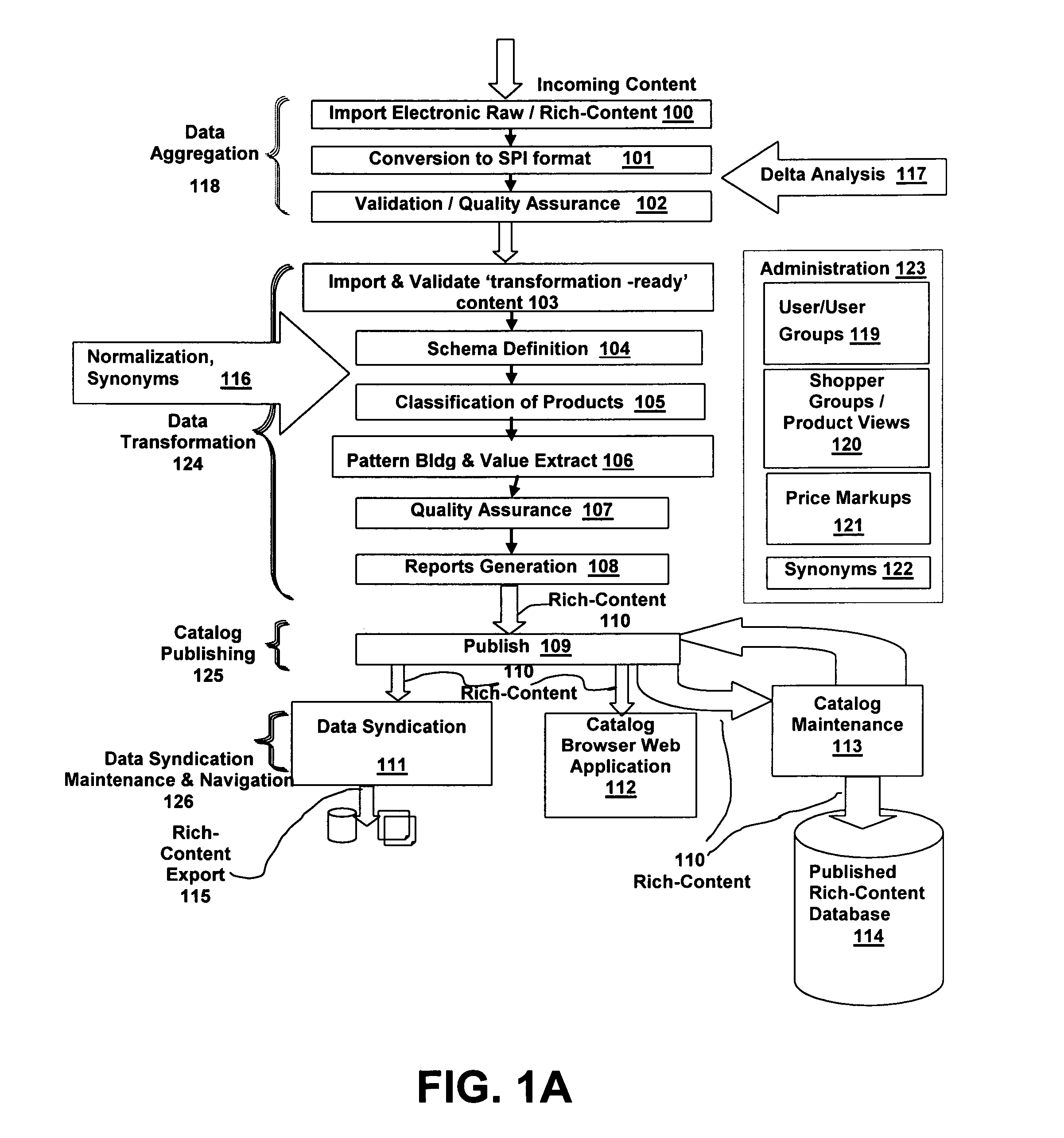
System and method for user creation and direction of a rich-content life-cycle
InactiveUS7526494B2Improve qualityGoals of a procuring organization are not compromisedMultiple digital computer combinationsApparatus for meter-controlled dispensingValue creationUser-defined function
A system and method are disclosed for creating, controlling and enhancing a life-cycle of at least one stage for a rich-content repository, such as a catalog of products and services. The item data is received from a source and is processed in accordance with a User-defined life-cycle, finally being published / syndicated as rich-content. At User direction, the rich-content life-cycle can include one or more stages such as item data receipt from a supplier, transformation under control of User-defined functions, and publication / syndication of the transformed, i.e., rich-content data. Maintenance of rich-content repositories is likewise provided using a User-defined life-cycle having User-defined functions.
Owner:EPLUS +1
Data item calibration method based on JSP page
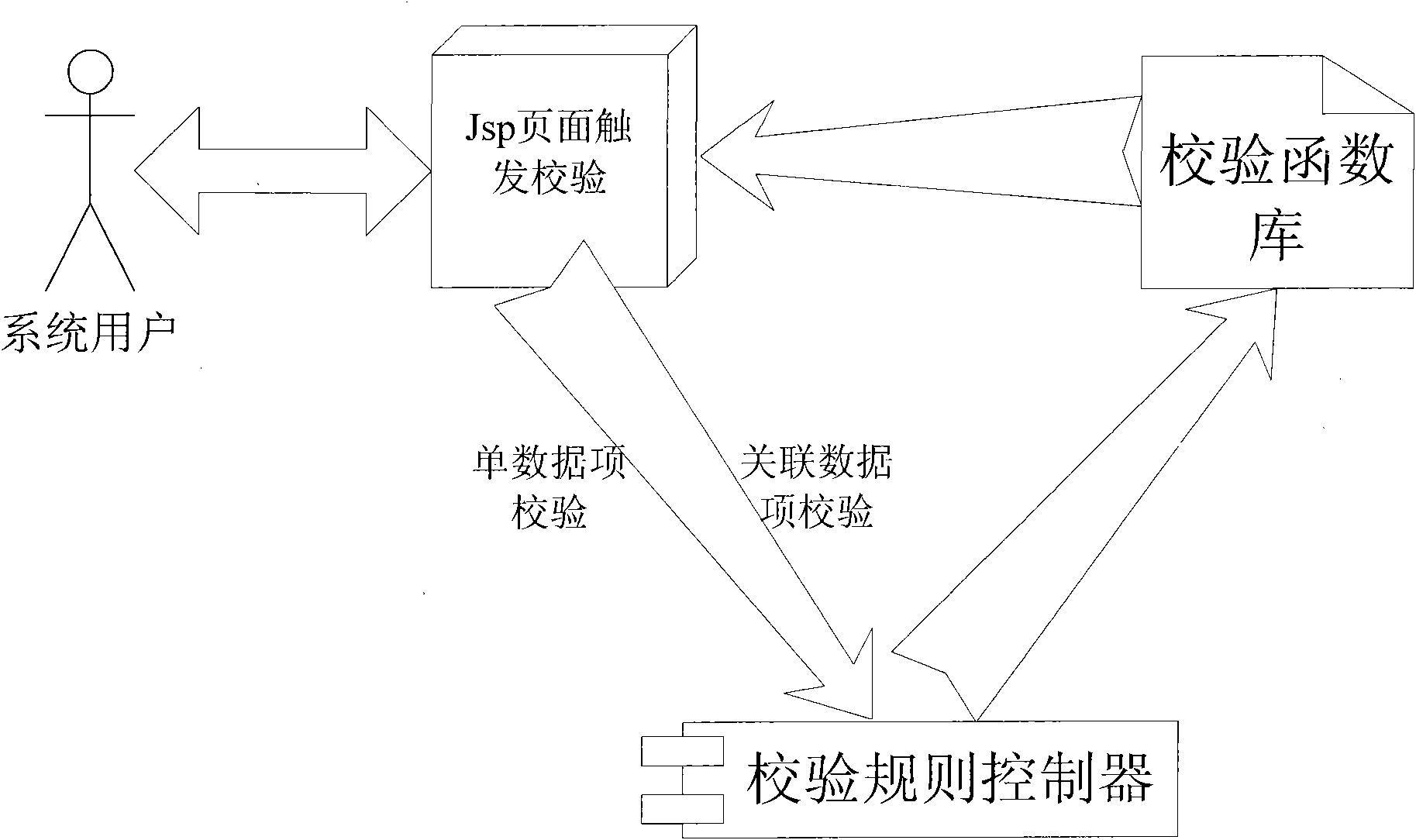
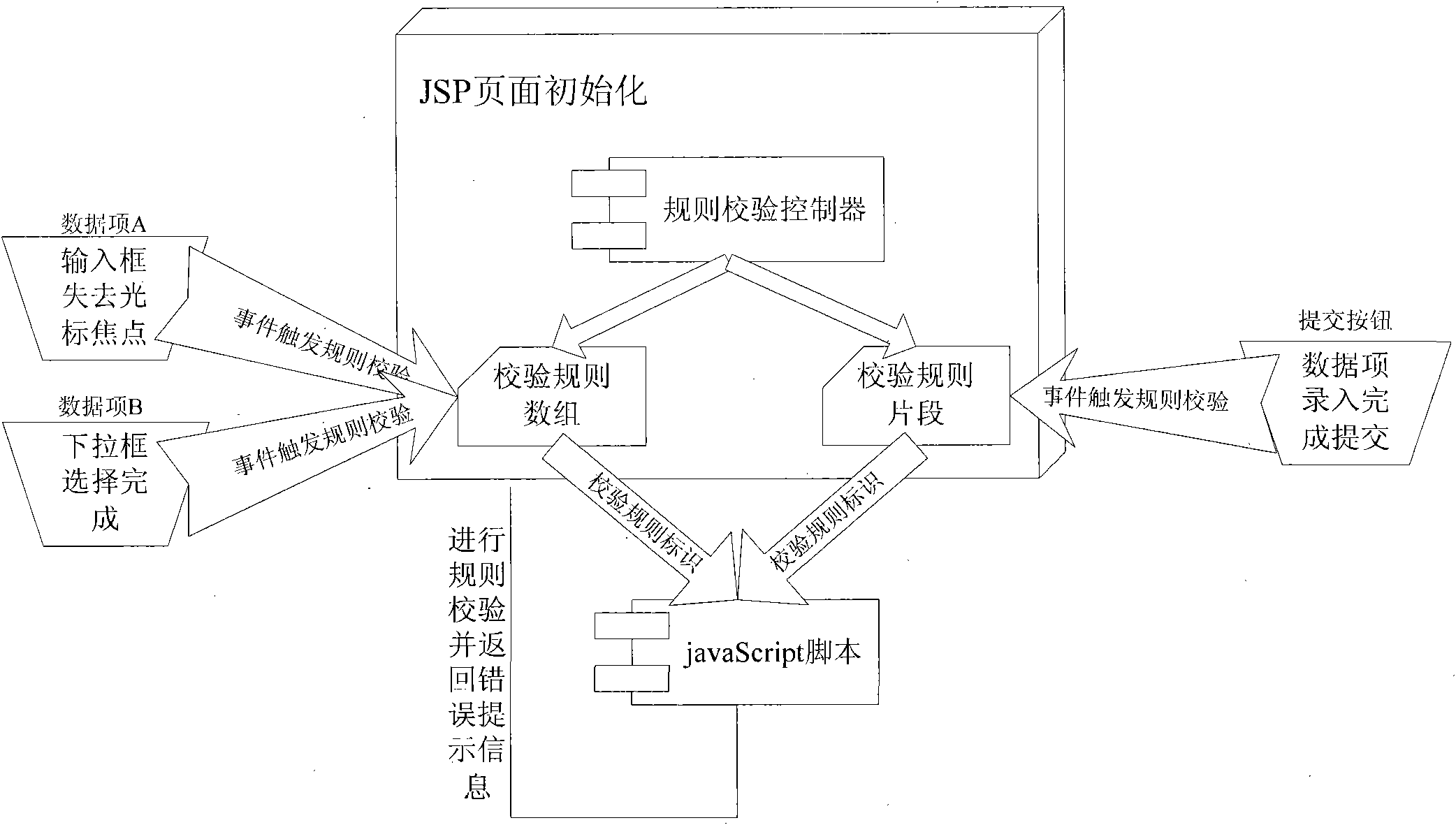
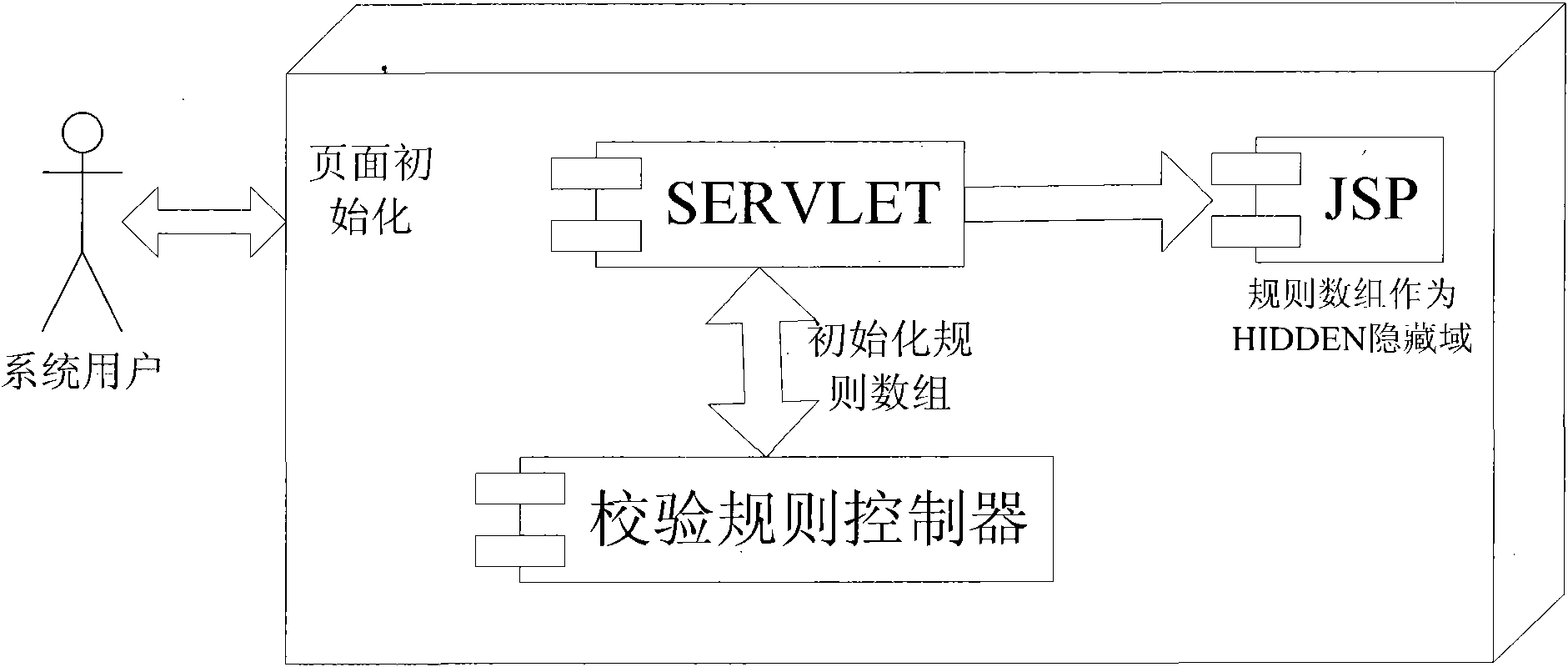
InactiveCN101788950AReduce development difficultyReduce development riskSoftware testing/debuggingSystem developmentComputer science
The invention discloses a data item calibration method based on a JSP page, belonging to a data item calibration method. A javaScript script file is written in JSP and is calibrated. The invention comprises (1) JSP, data item description, other page display contents, write-in data item and page submitting triggering; (2) a calibrating rule controller, an data item and route configuration of the calibrating rule, wherein the calibrating rule controller serves as a configuration file to store the corresponding relation of the data item and calibrating rule identification, is in an XML form and can realize rule route by simple configuration; and (3) a calibration database, comprising a public function, an arithmometer and a user-defined function library. Compared with the prior art, the data item calibration method based on a JSP page of the invention is simple and flexible, has low cost, can improve system development efficiency and can lower the technical requirements of on-site implementing maintenance personnel.
Owner:浪潮(山东)电子信息有限公司
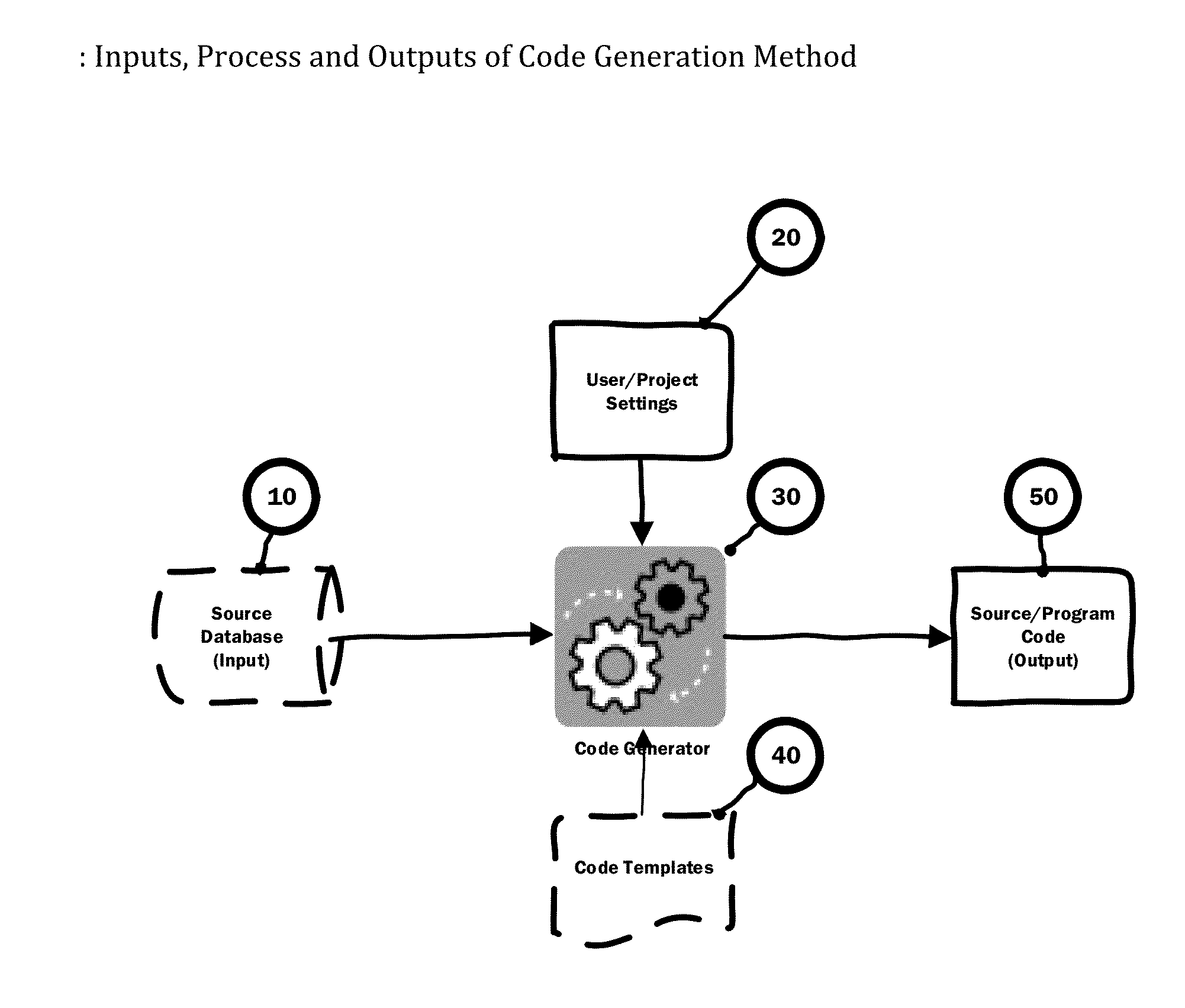
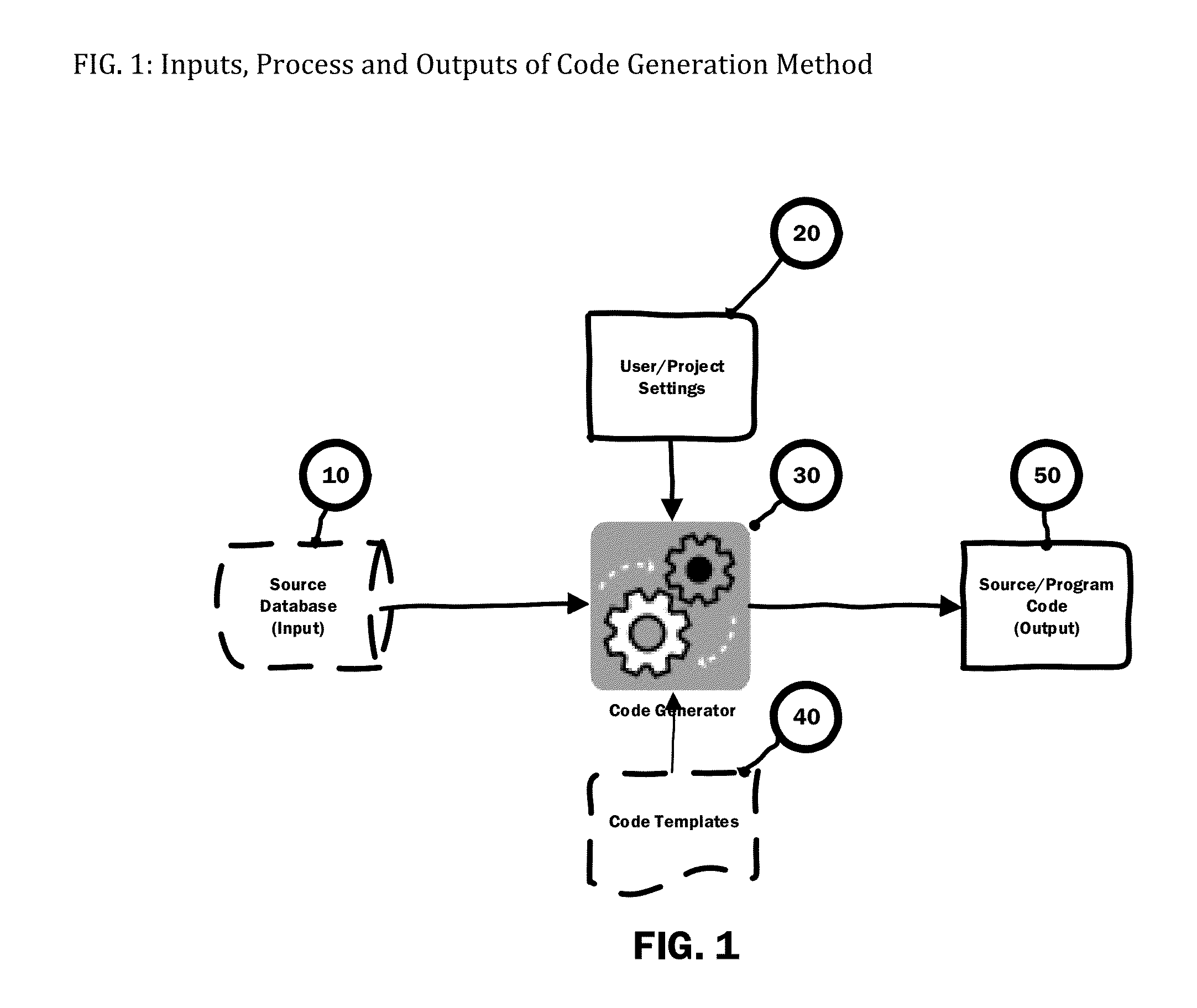
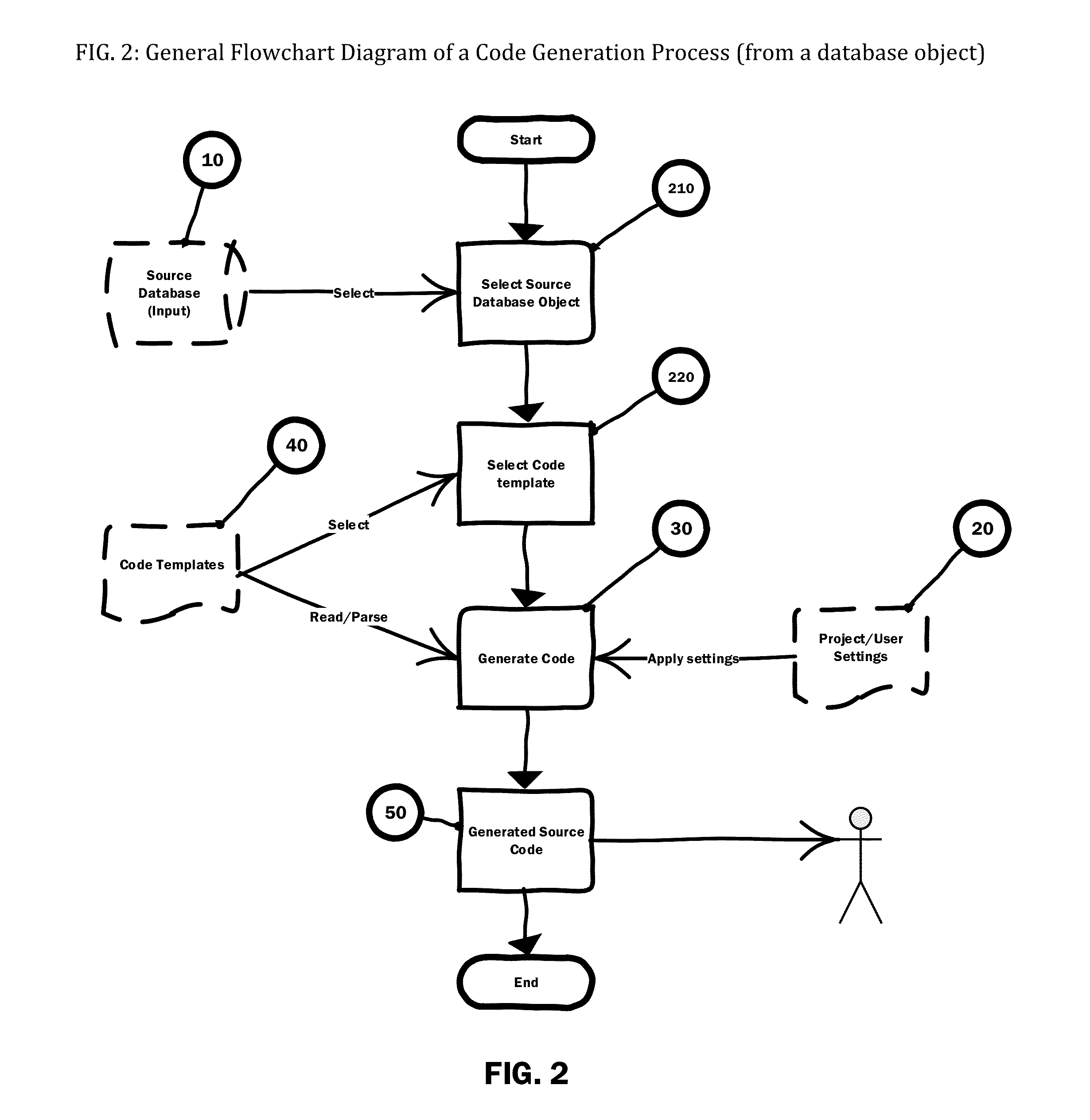
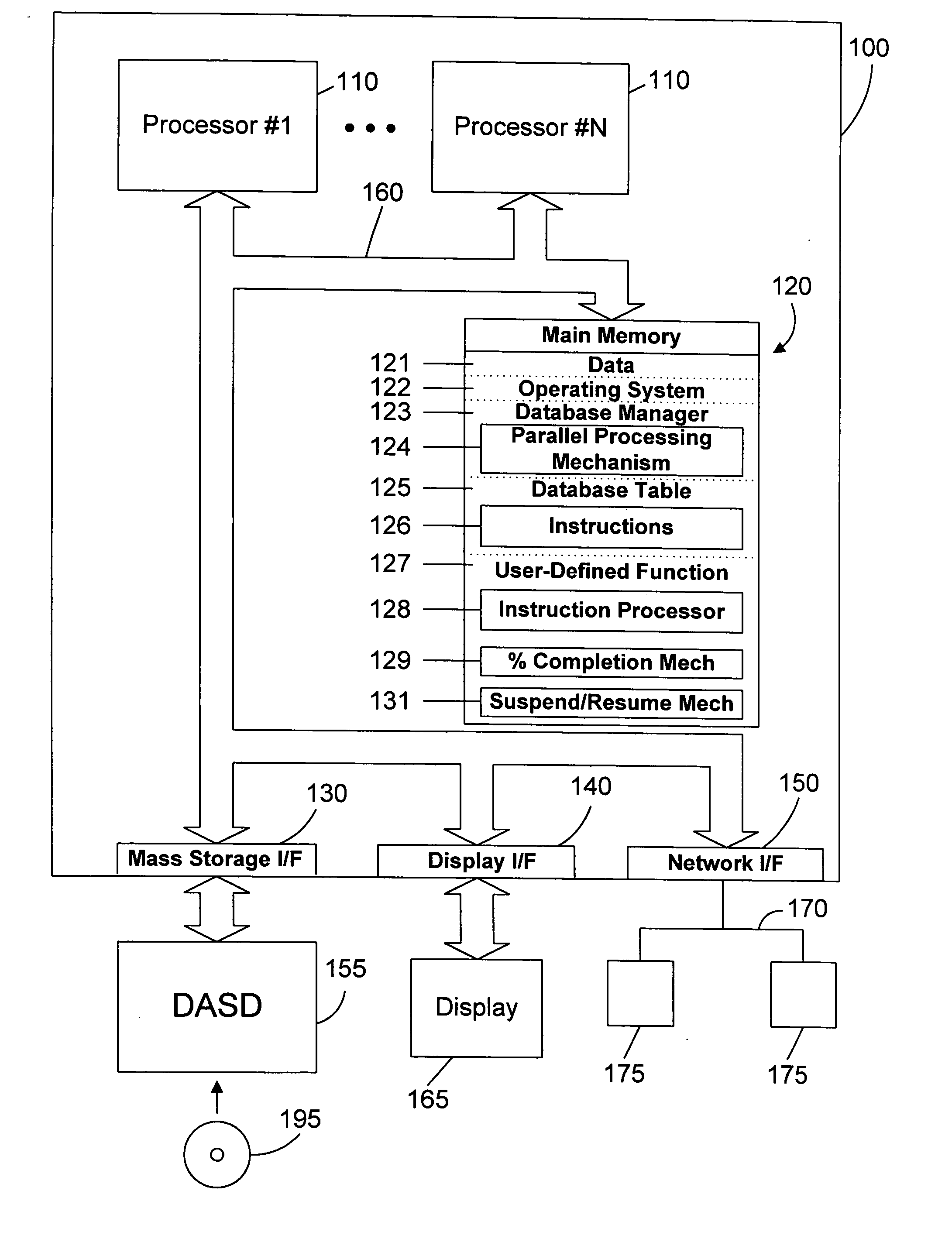
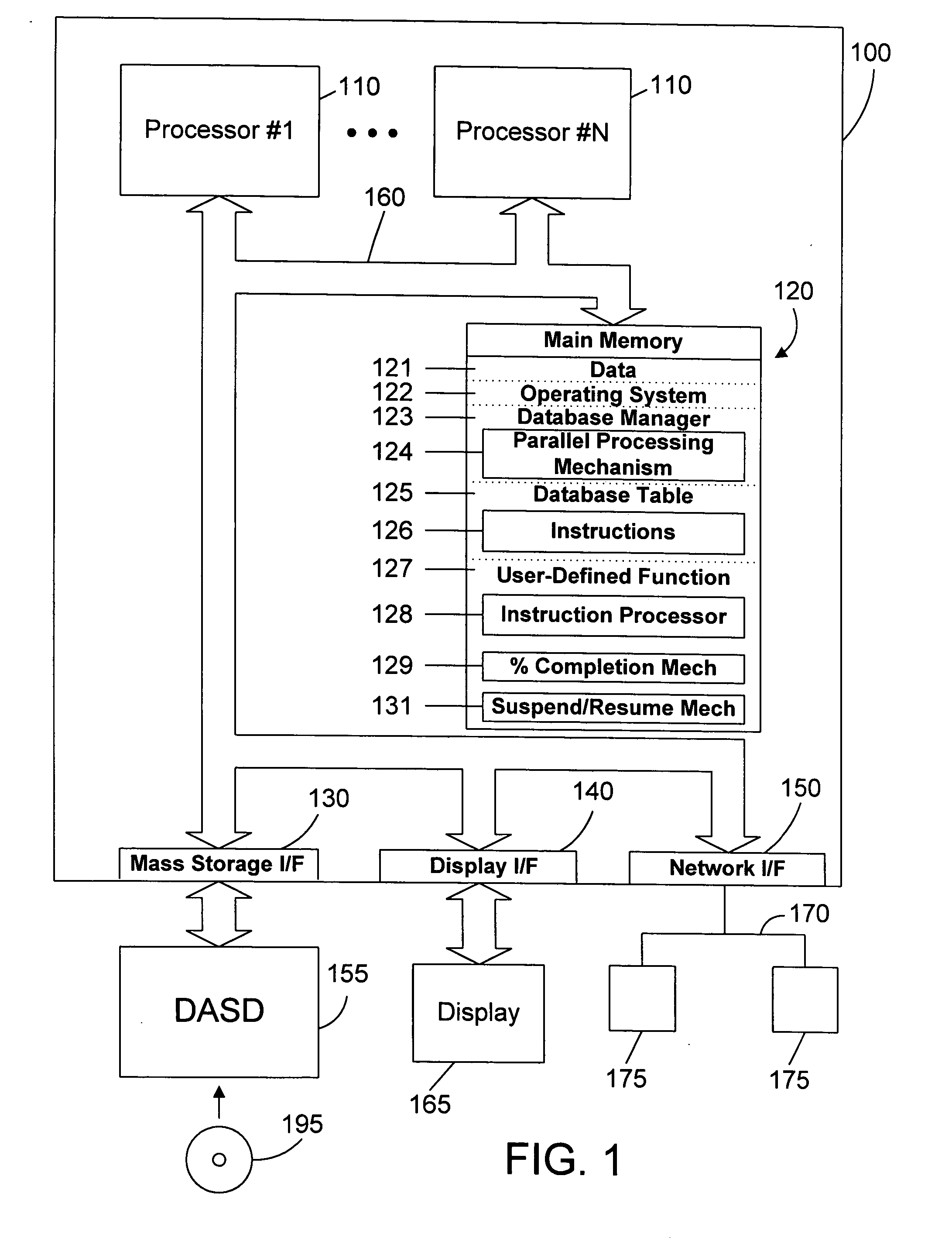
Computer Source Code Generator for Building Software Applications
InactiveUS20160041815A1Well formedEasy to integrateDigital data information retrievalSoftware reuseScripting languageTwo step
A computer program / software / tool that uses a method / technique / process and set of parameters for generating source code for a programming / database / scripting languages straight from a database model or database objects such as Tables, Views, Stored Procedures, User Defined Functions, Types, Sequences, Packages, Indexes and Constraints etc. The method includes steps of creating / generating re-usable program / components / source code for an application, where the developer selects the database object and the type of code they want to generate as an input to the code generator. The code generation method / technique / process utilizes information contained in the database system for the selected database object; uses specific code template; and uses set of parameters provided by the developer and generates source code as an output. A simple two-step process greatly reduces developer effort in going through many code generation options every time they want to generate the code either for an application or an individual component / program.
Owner:BHAGAT CHIRAG P
Apparatus and method for enabling parallel processing of a computer program using existing database parallelism
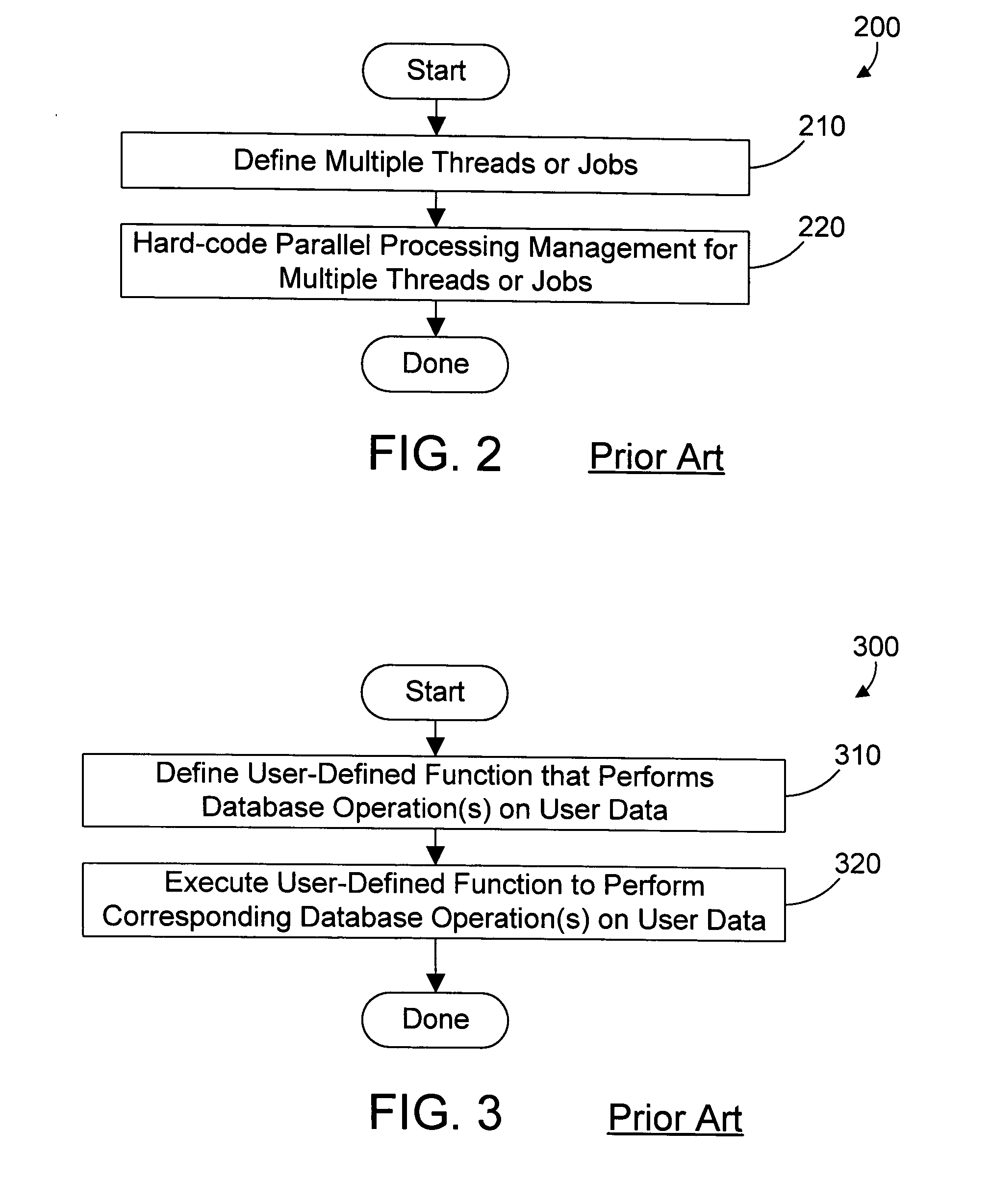
InactiveUS20050182782A1Easy to implementDigital data information retrievalDigital data processing detailsHard codingModem device
An apparatus and method enable parallelism in a computer program using parallelism that is built-in to many modem database managers. The parallelism provided by a database manager in executing user-defined functions provides an easy way to implement parallelism for database and non-database functions in a computer program without the need of hard-coding all the parallelism support in the computer program itself. A database table is defined with instructions the user wants to execute in parallel. A user-defined function is then defined that executes the instructions in the table. A database operation is then defined for the table that invokes the user-defined function. When the database operation is executed, the database manager provides parallelism by executing multiple tasks in parallel in the user-defined function. The built-in parallelism in many modem database managers thus may be used to enable parallelism in a computer program by using user-defined functions in a manner not previously thought of before.
Owner:LINKEDIN
Natural language support for query results
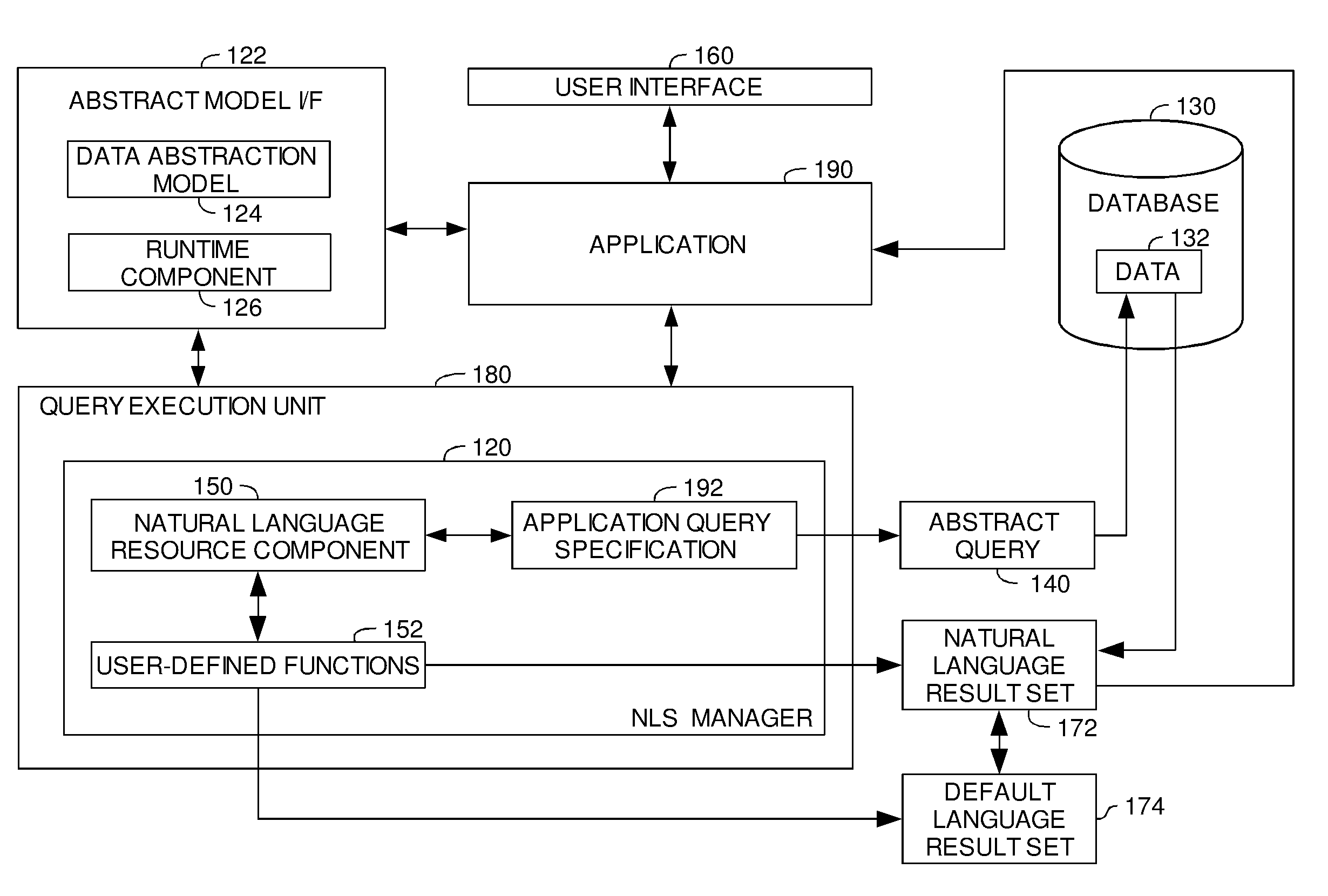
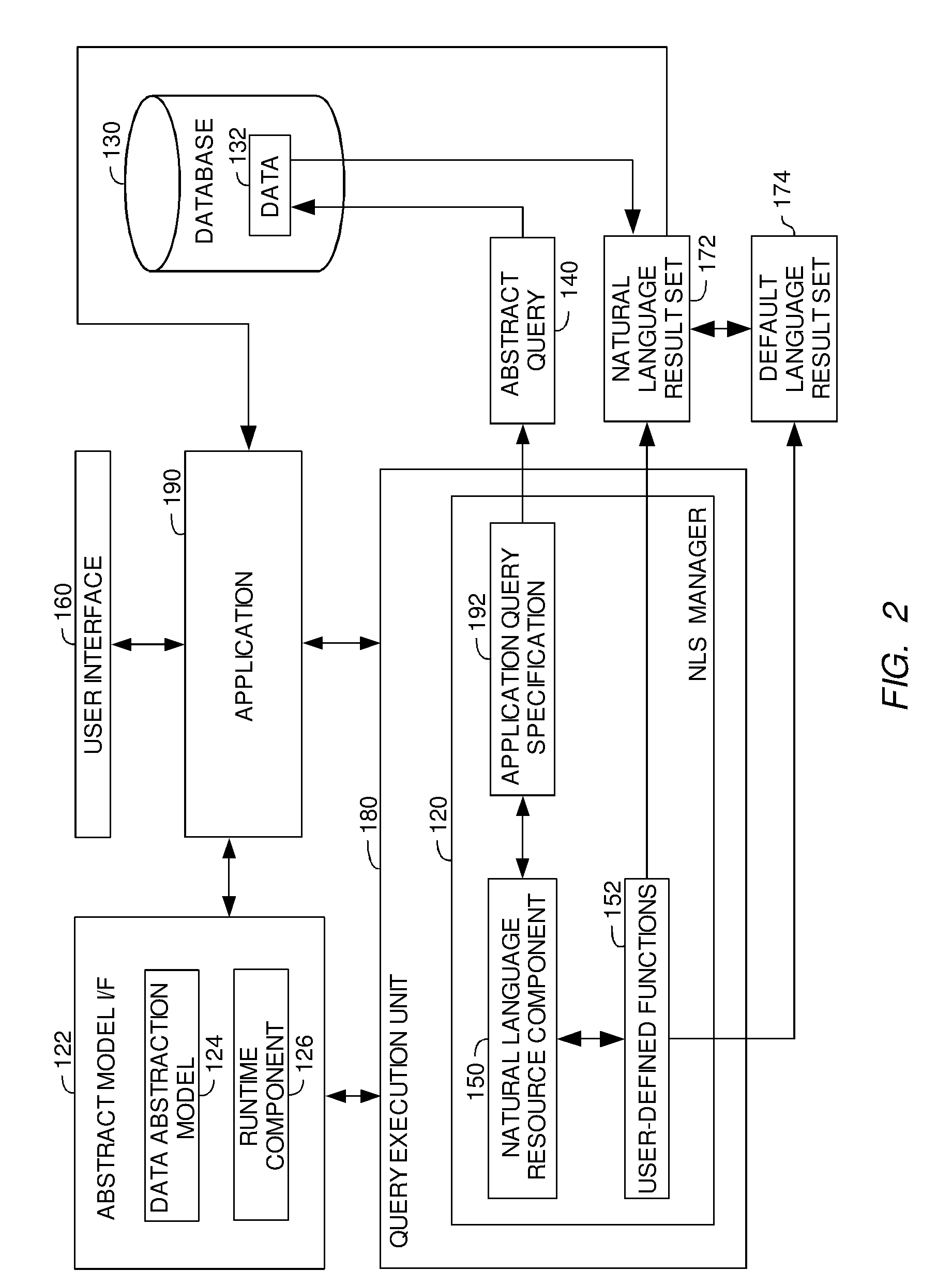
InactiveUS20080016049A1Provide supportDigital data information retrievalSpecial data processing applicationsUser-defined functionDatabase
A method, system and article of manufacture for providing language transformation support for a query result obtained in response to execution of a query against an underlying database containing physical data. The method comprises identifying one or more physical values defined by the physical data for the query result for the executed query. The method further comprises retrieving a user-defined function configured to transform the one or more identified physical values from a first language defined by the physical data in the underlying database into alternative values defined in a second language. The query result is outputted in the second language on the basis of the user-defined function.
Owner:IBM CORP
Optimizing Execution of Database Queries Containing User-Defined Functions
InactiveUS20080270392A1Reduced execution timeBetter strategyData processing applicationsDigital data information retrievalTheoretical computer scienceUser-defined function
A query engine (or optimizer) which supports database queries having user-defined functions maintains historical execution data with respect to each of multiple user-defined functions. The historical execution data is dynamically updated based on query execution performance. When executing a query having user-defined functions, the query engine uses the historical execution data to predict an optimal evaluation ordering for the query conditions and, preferably, to dynamically adjust the evaluation order when appropriate. Preferably, the historical execution data includes historical execution time of the user-defined function and proportion of evaluated records which satisfied the query parameters.
Owner:INT BUSINESS MASCH CORP
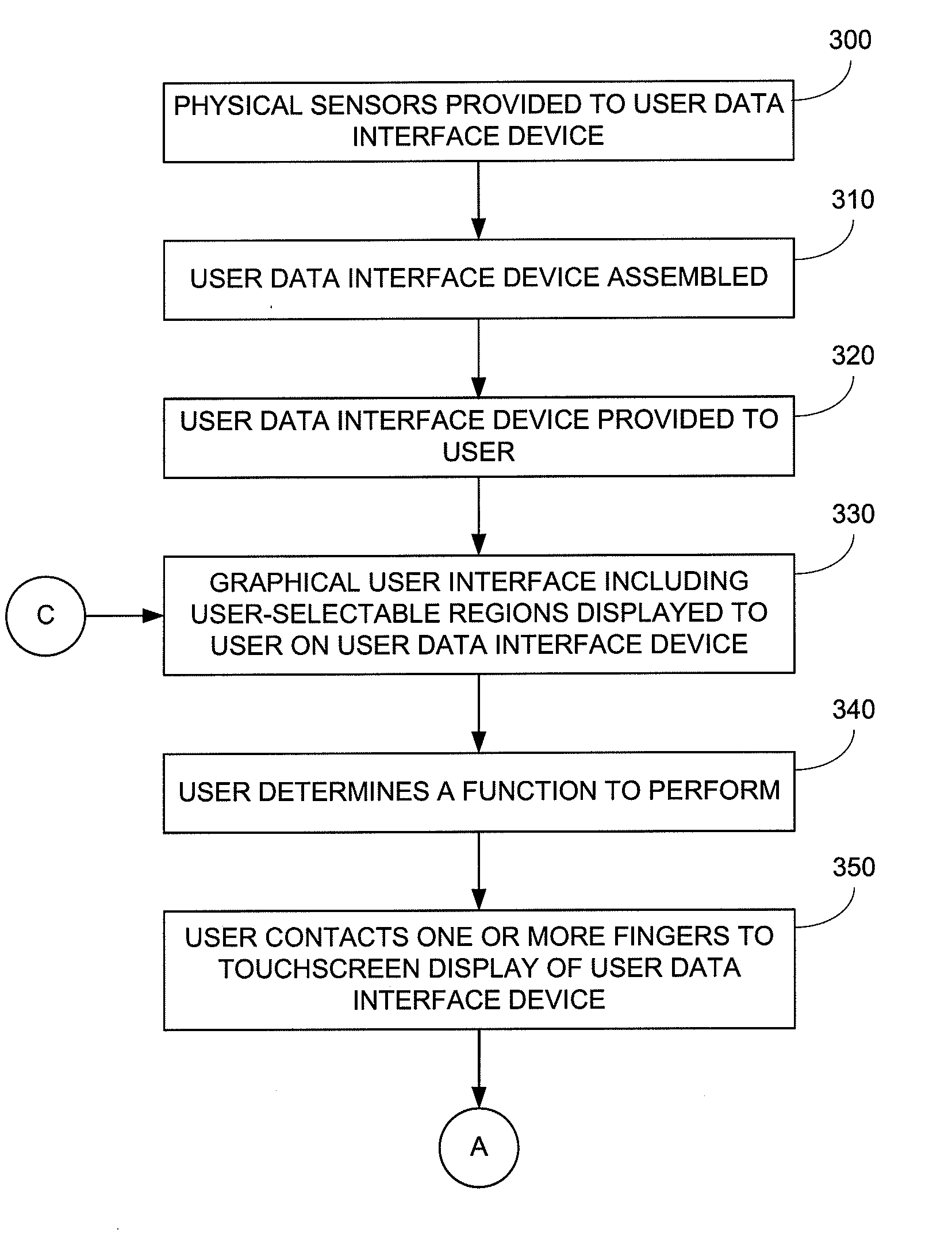
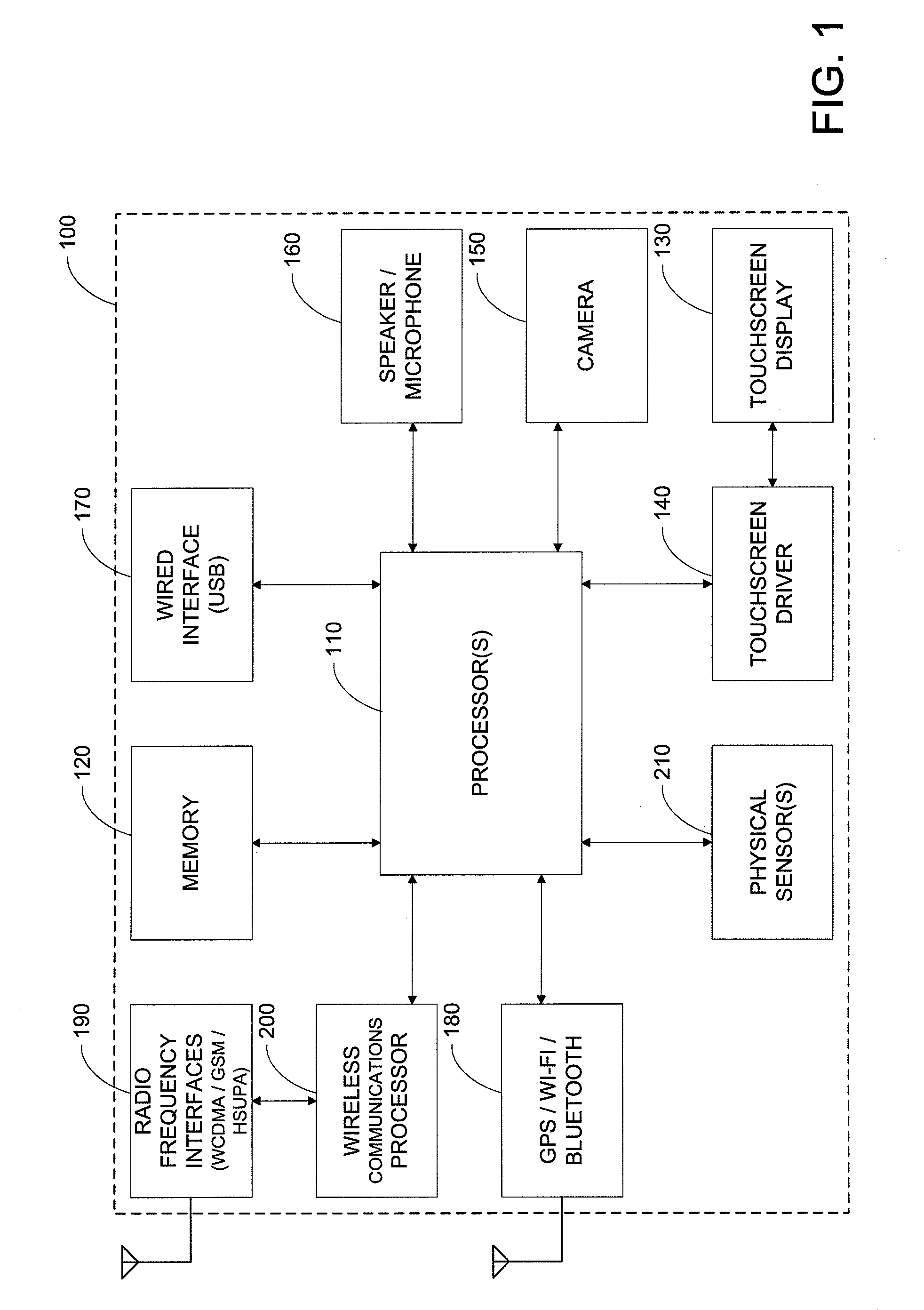
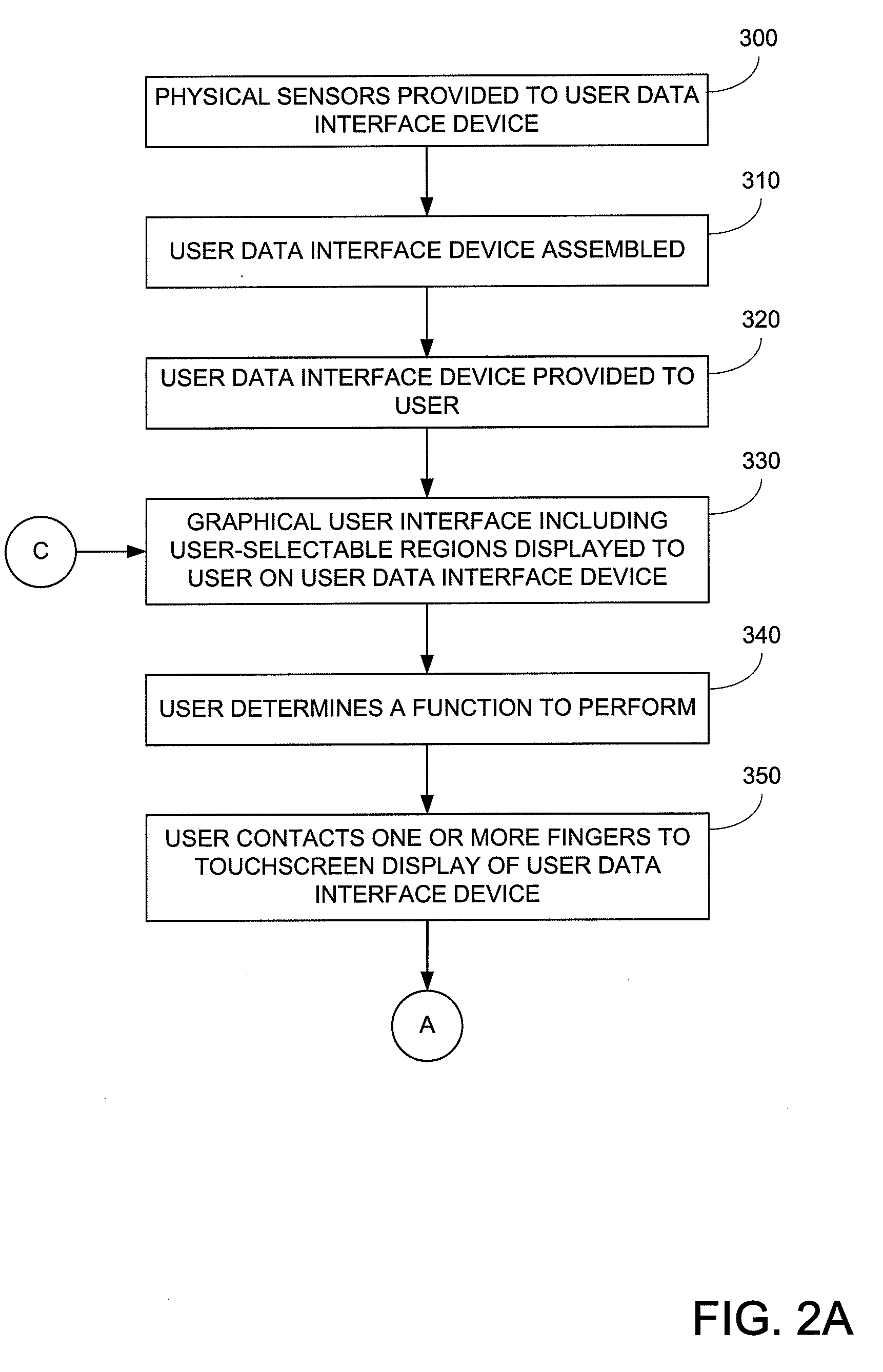
Touchscreen Operation Threshold Methods and Apparatus
ActiveUS20110291934A1Input/output for user-computer interactionCathode-ray tube indicatorsUser inputComputerized system
A computer implemented method for performing a user-defined function in a computer system, performed by the computer system that is programmed to perform the method includes determining by a display a display position in response to a change and a rate change in state of a user-controlled user input device, determining by a physical sensor a magnitude of change in sensed physical in response to the rate of change in the state, determining whether the magnitude of change exceeds a threshold level, determining a function to perform in response to display position when magnitude of change in sensed physical properties exceeds the threshold level, initiating performance of the function in response to the function, and inhibiting performance of the function when the magnitude of change in sensed physical properties does not exceed the threshold level.
Owner:MOVELLA INC
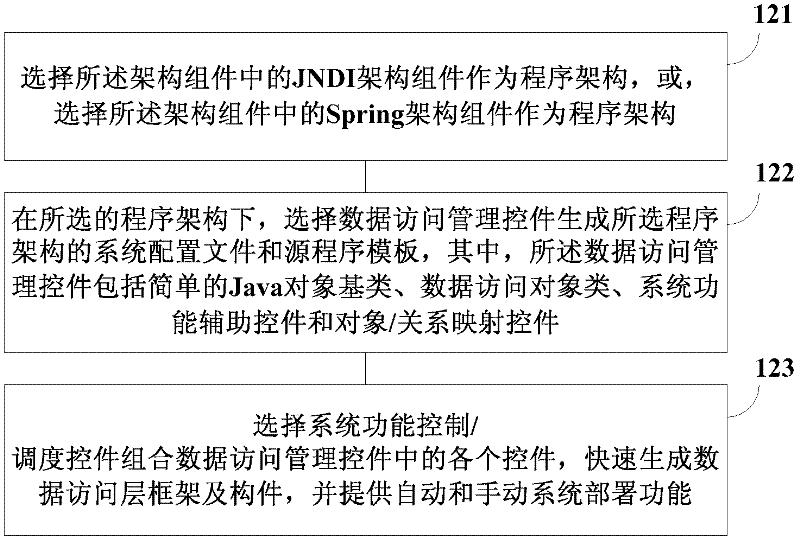
JDBC (java database connectivity) based data access layer building method and device utilizing same
ActiveCN102541996AImprove unityAchieve standardSpecial data processing applicationsSystem configurationSystem development
The invention provides a JDBC (java database connectivity) based data access layer building method and a device utilizing the same, which solve the problem that the system is complicated in configuration due to difference between the architecture of programs and the programming mode during development of the data access layer. The JDBC based data access layer building method includes: generating a JDBC based data access layer frame generating component which comprises an architecture component and function controls by integrating with a source opening component and packaging user-defined function members; selecting a program architecture according to the architecture component, selecting the corresponding function control according to the selected program architecture to generate system configuration files and source program templates applicable to the program architecture, and building a data access layer through relevant program configurations by the selected program architecture and the system configuration files and the source program templates thereof. By the generating component capable of generating the framework and members of the data access layer, complexity of system development is reduced and time thereof is shortened, and uniformity and standardization of development of the data access layer are realized.
Owner:DATANG SOFTWARE TECH
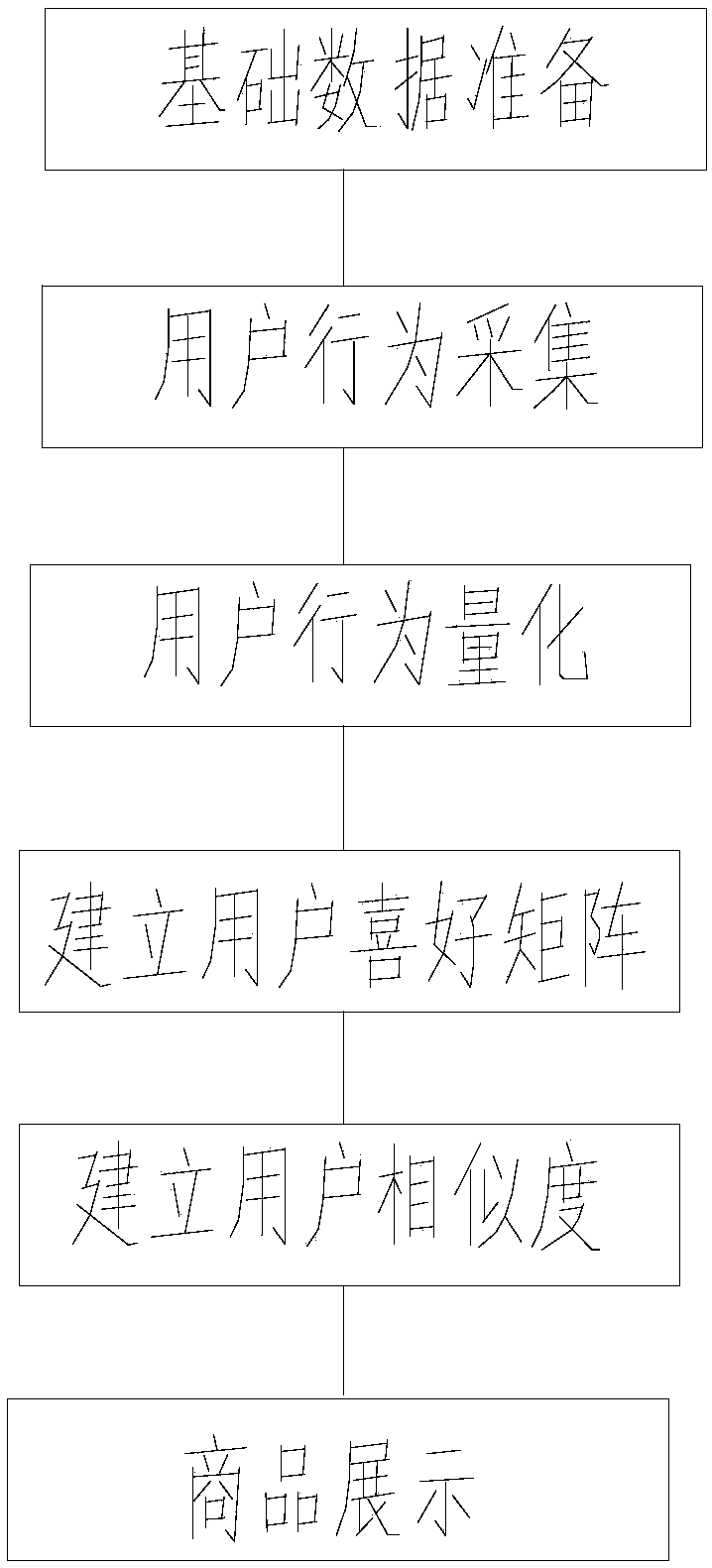
User shopping behavior identification method based on big data, storage equipment, and mobile terminal
ActiveCN107590675AImprove real-time performanceSimple logic theoryBuying/selling/leasing transactionsSpecial data processing applicationsOperabilityData preparation
The invention discloses a user shopping behavior identification method based on big data, which is applicable to computer equipment. The method includes the following steps: basic data preparation; user behavior acquisition: acquiring browse, click, collection, forwarding and purchase behavior data of users when users open web pages through an acquisition module; user behavior quantification: classifying and summarizing the acquired behavior data, and establishing the functional relationship of users, commodity labels and the behavioral attention of a user on a certain commodity label; establishing a user preference matrix: establishing a user preference function according to the functional relationship of users, commodity labels and the behavioral attention of a user on a certain commodity label; establishing user similarity; and displaying commodities. In the invention, user behaviors are quantified, and user preference and similarity functions are established. The logic theory is simple and highly operable. The purchase scenario and user participation are considered, and the analysis result is more accurate.
Owner:智选数字技术(广州)股份有限公司
System and method of analyzing data using bitmap techniques
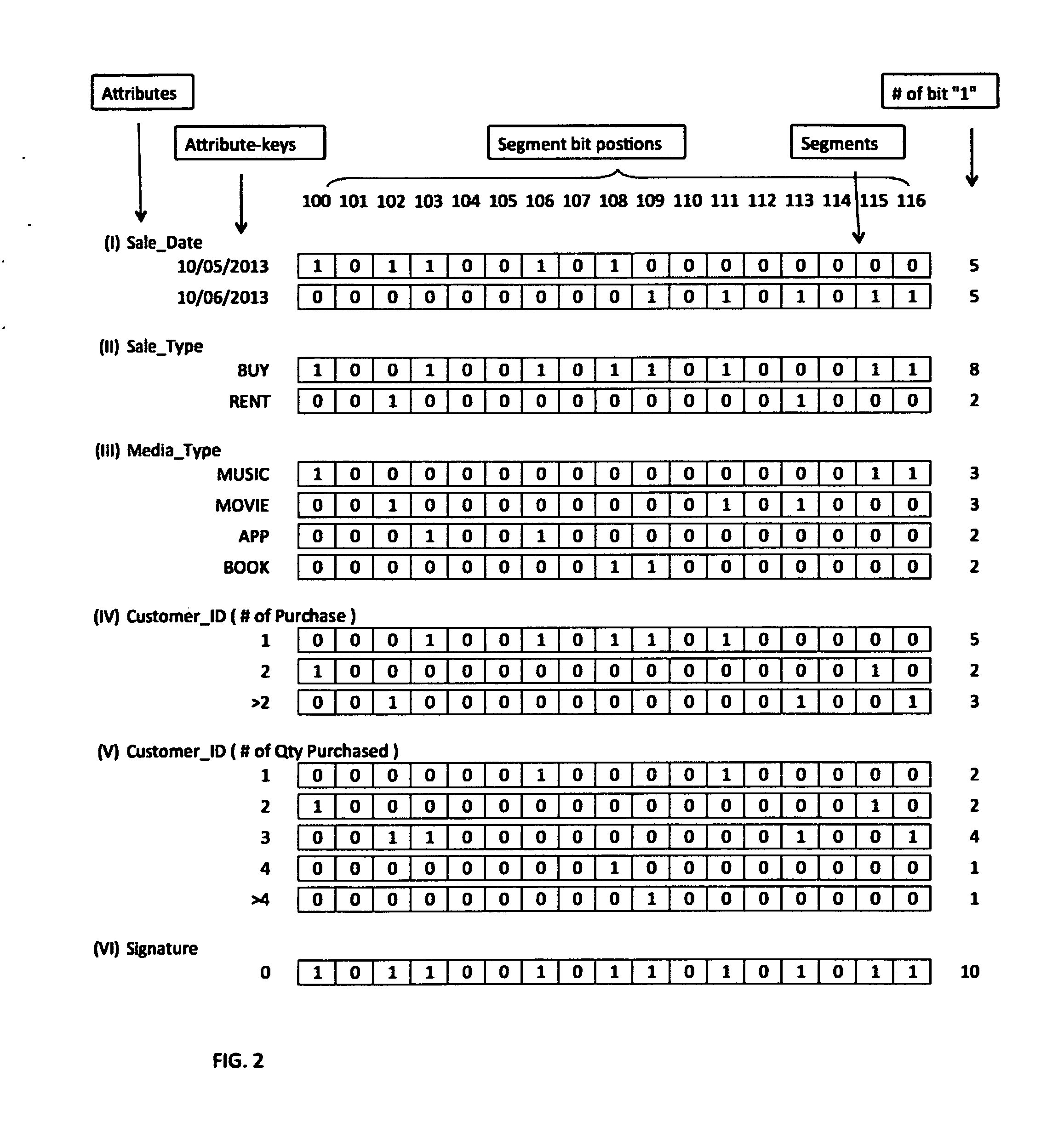
InactiveUS20160085832A1Digital data information retrievalDigital data processing detailsAnalysis dataData source
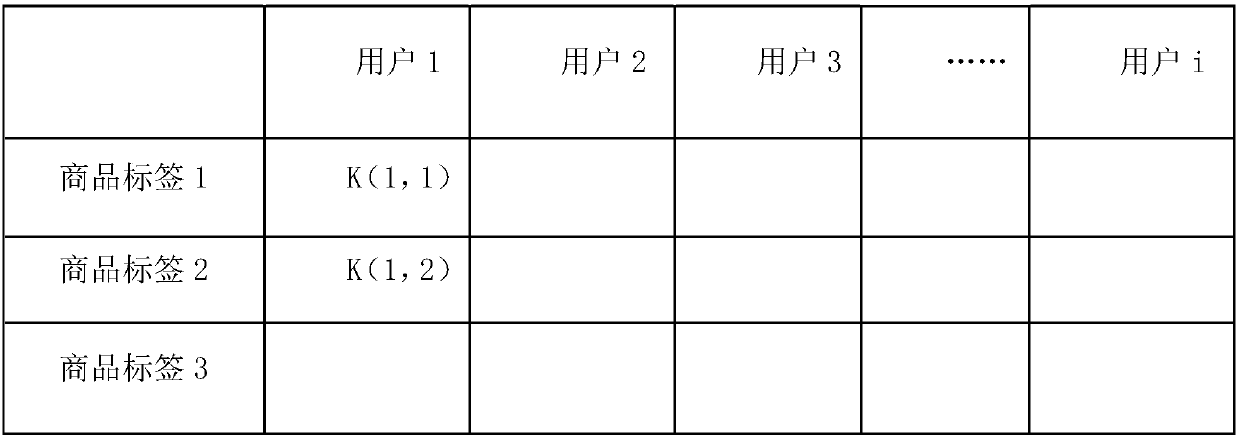
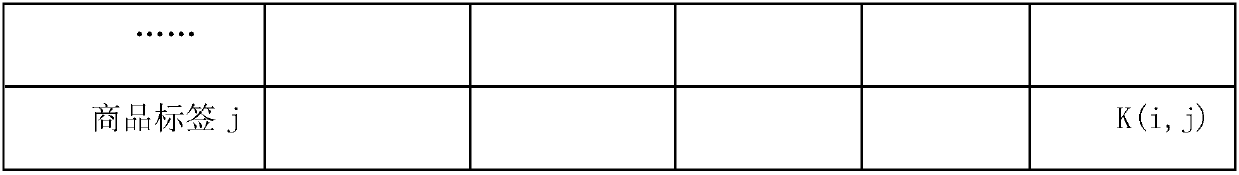
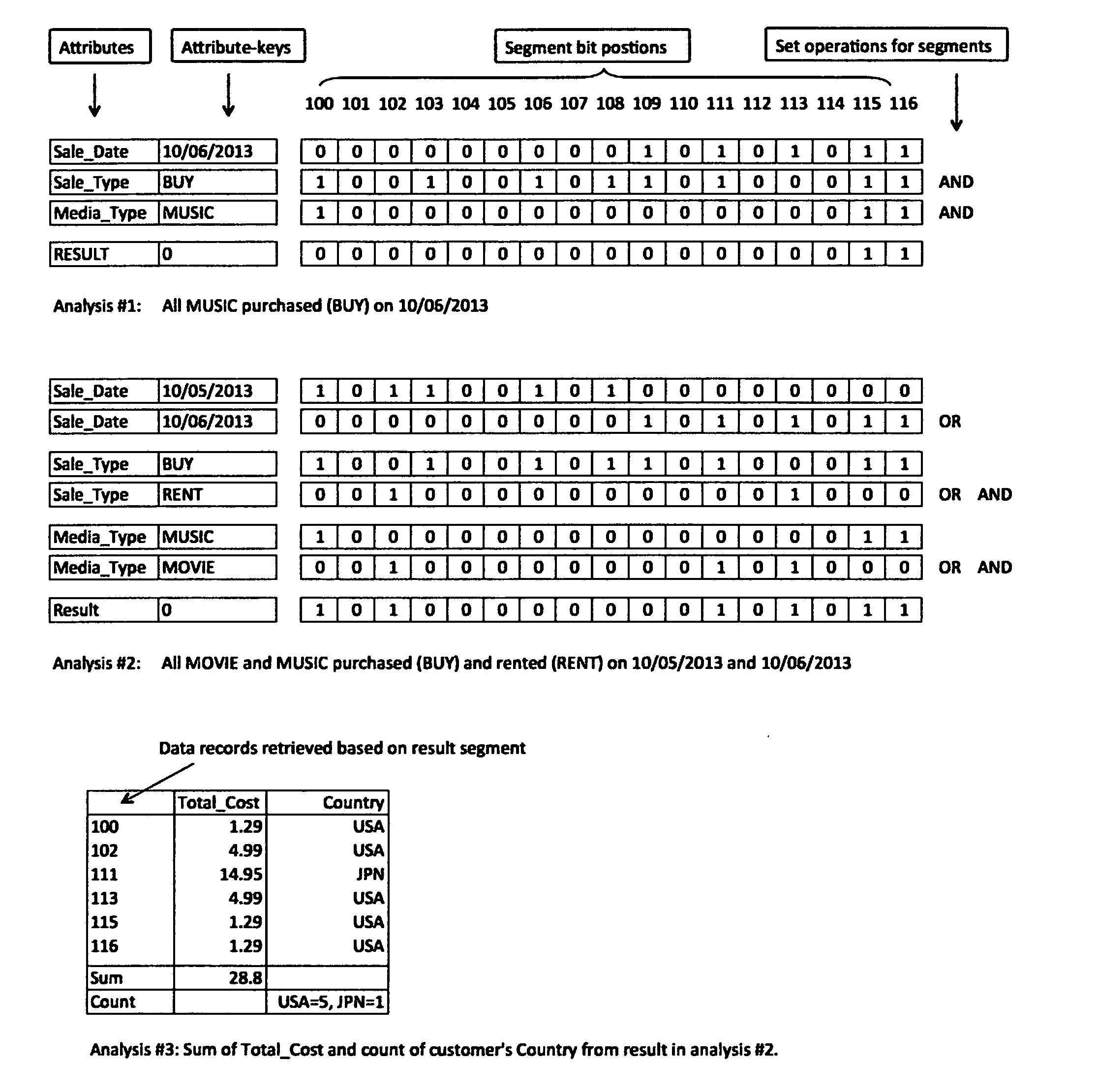
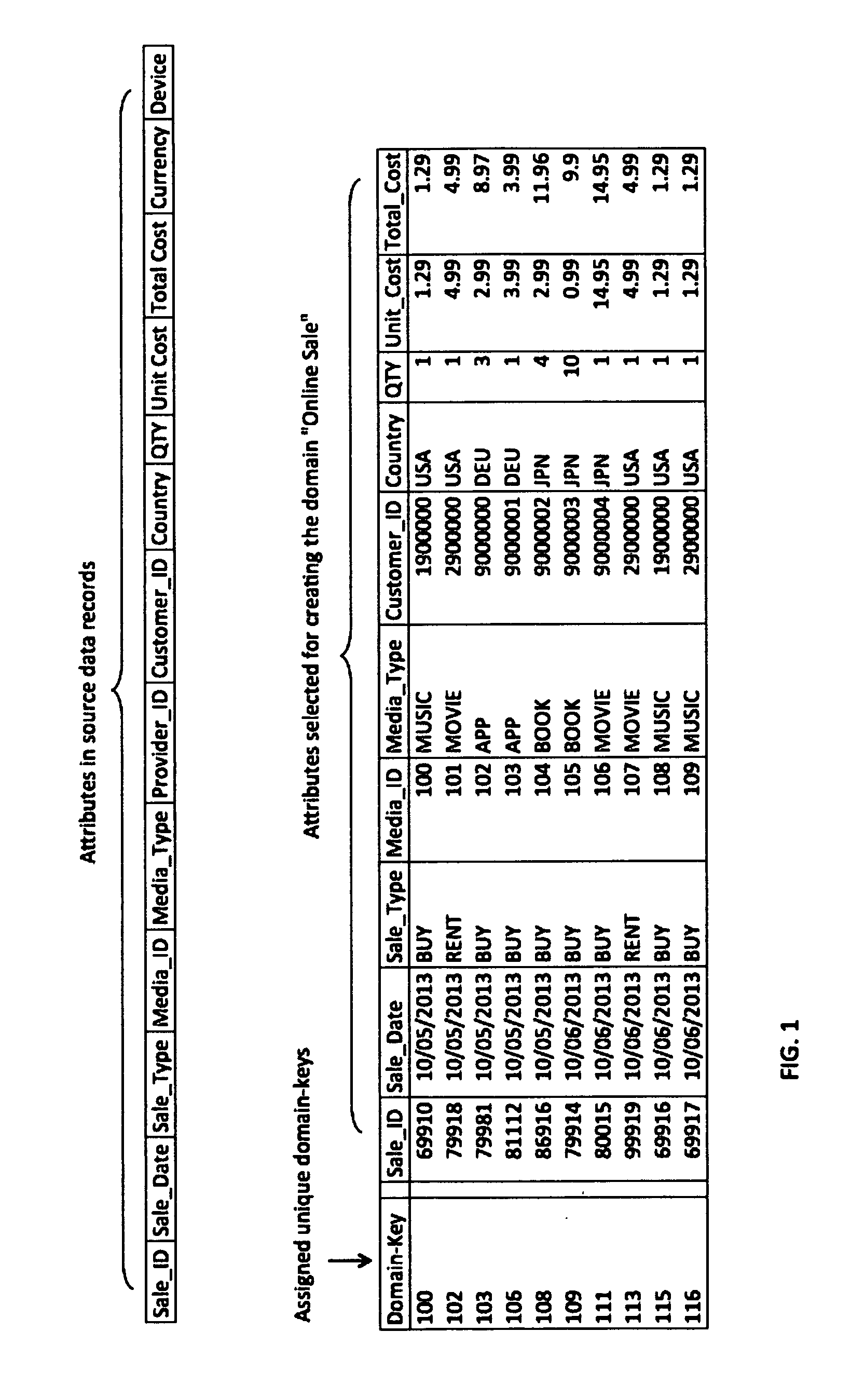
A method and system of analyzing data using bitmap techniques by first transforming source data records to key-value pairs, then selecting required attributes within said data source to create bitmap segments that are associated to the attribute's corresponding data records, where data analyses are performed by mean of formulating and executing required Set (or bit-wise) operations among the required bitmap segments to generate a final result bitmap segment, and based on which retrieving the corresponding result set of data records and perform further analyses by applying statistical and / or user-defined functions on the result set to generate the required result.
Owner:LAM RICHARD L
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com