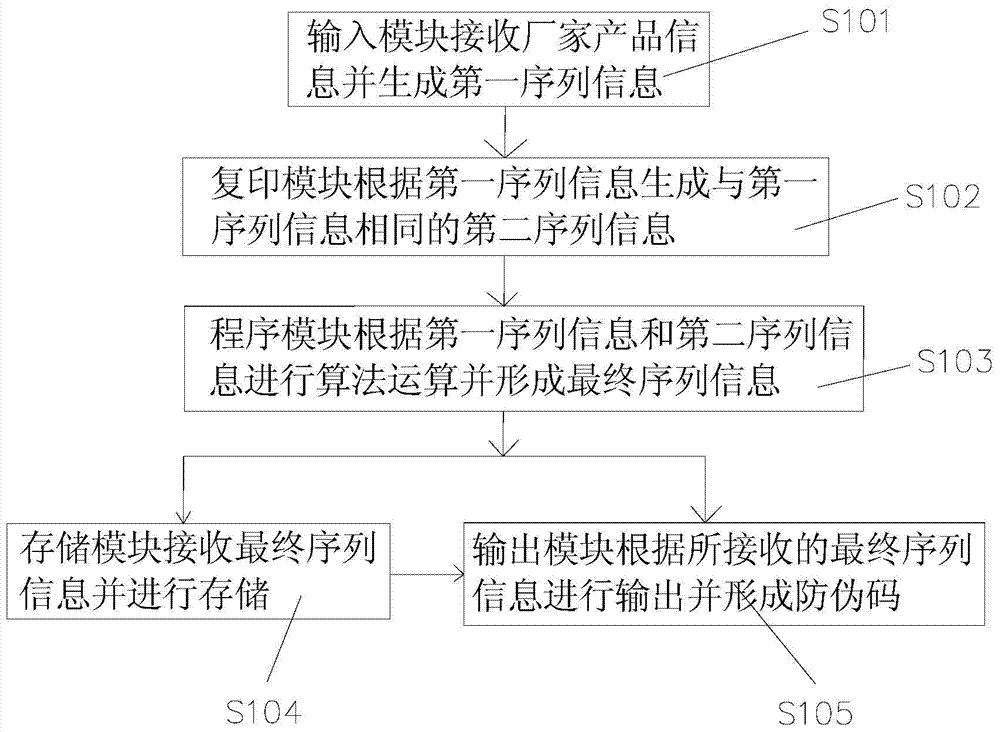
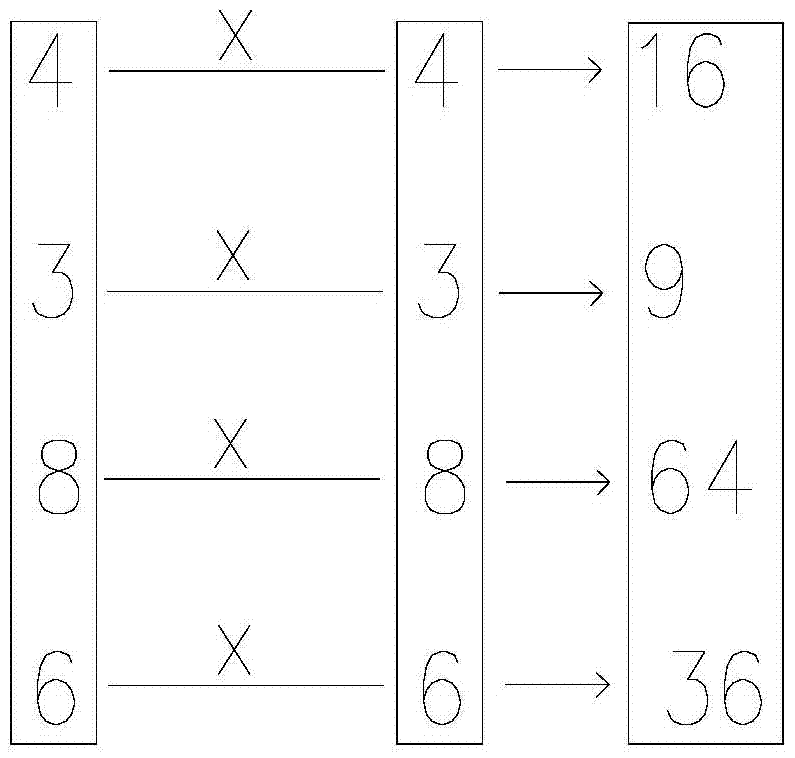
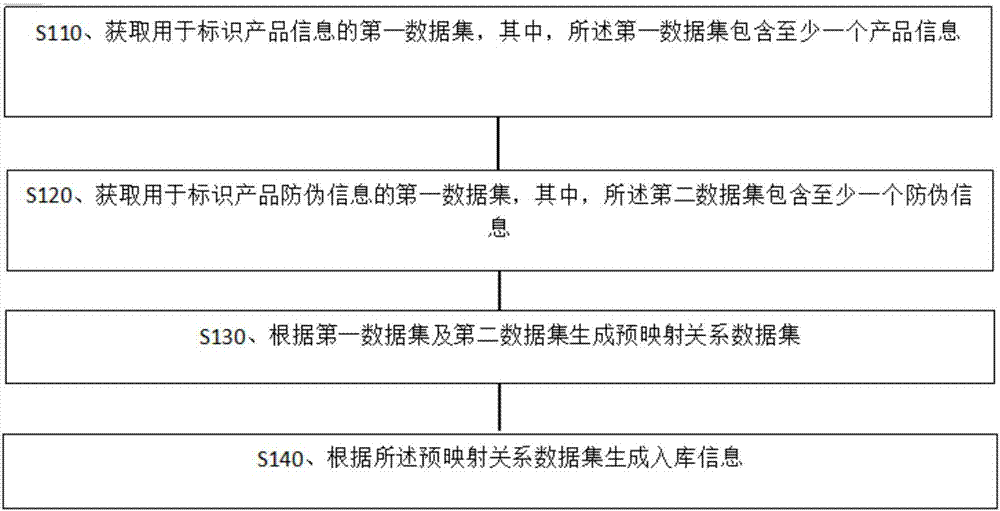
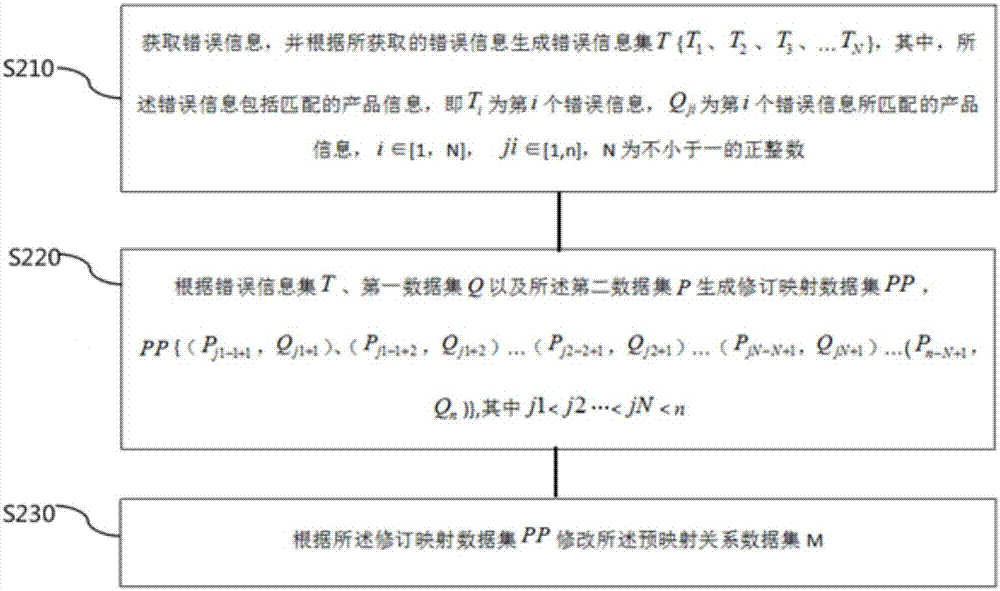
Patents
Literature
41 results about "Card security code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A card security code (CSC), card verification data (CVD), card verification number, card verification value (CVV), card verification value code, card verification code (CVC), verification code (V-code or V code), or signature panel code (SPC) is a security feature for "card not present" payment card transactions instituted to reduce the incidence of credit card fraud.
Electronic purse card value system card security method
InactiveUS6330978B1Payment architectureRecord carriers used with machinesCommunications systemModem device
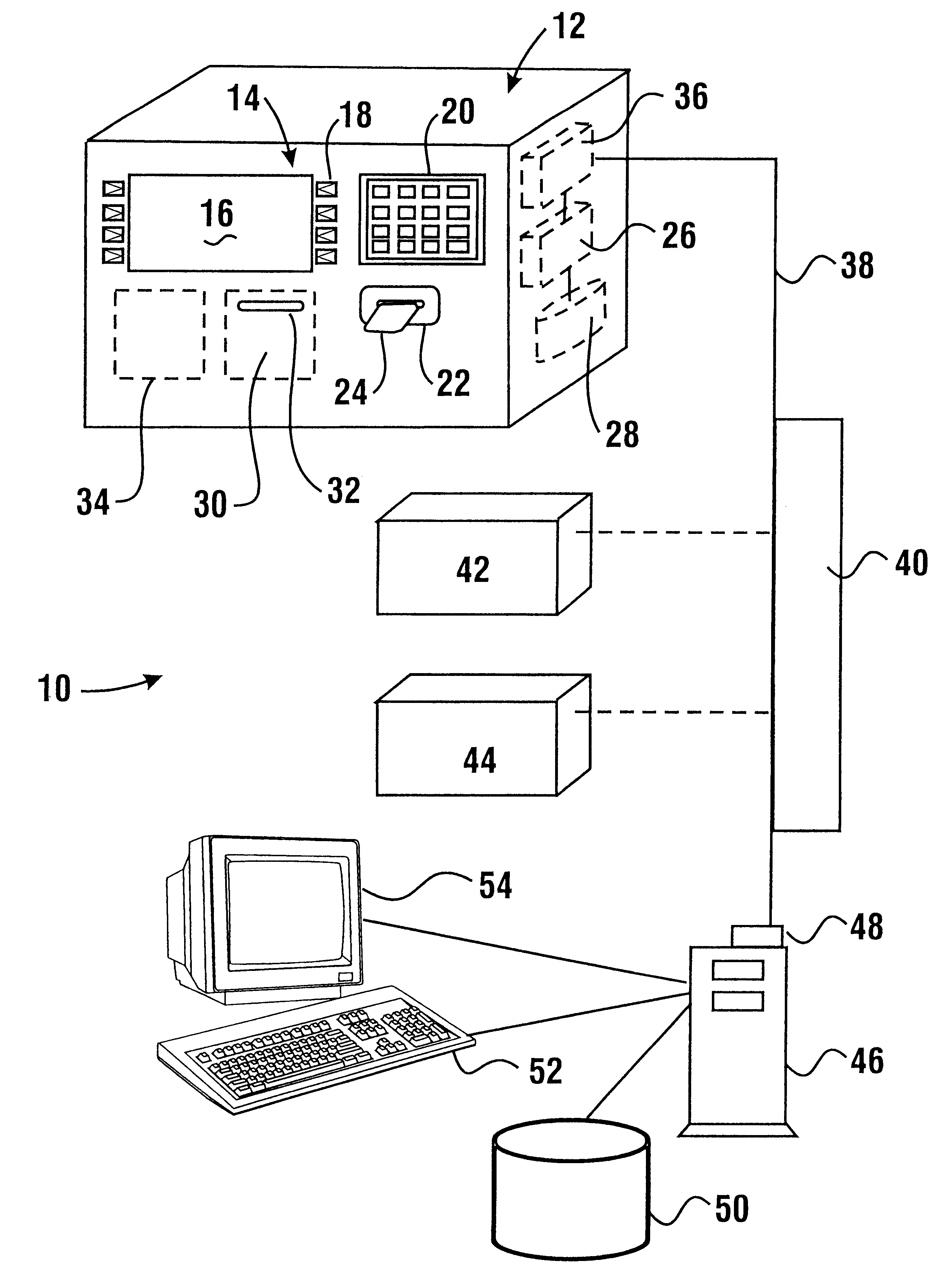
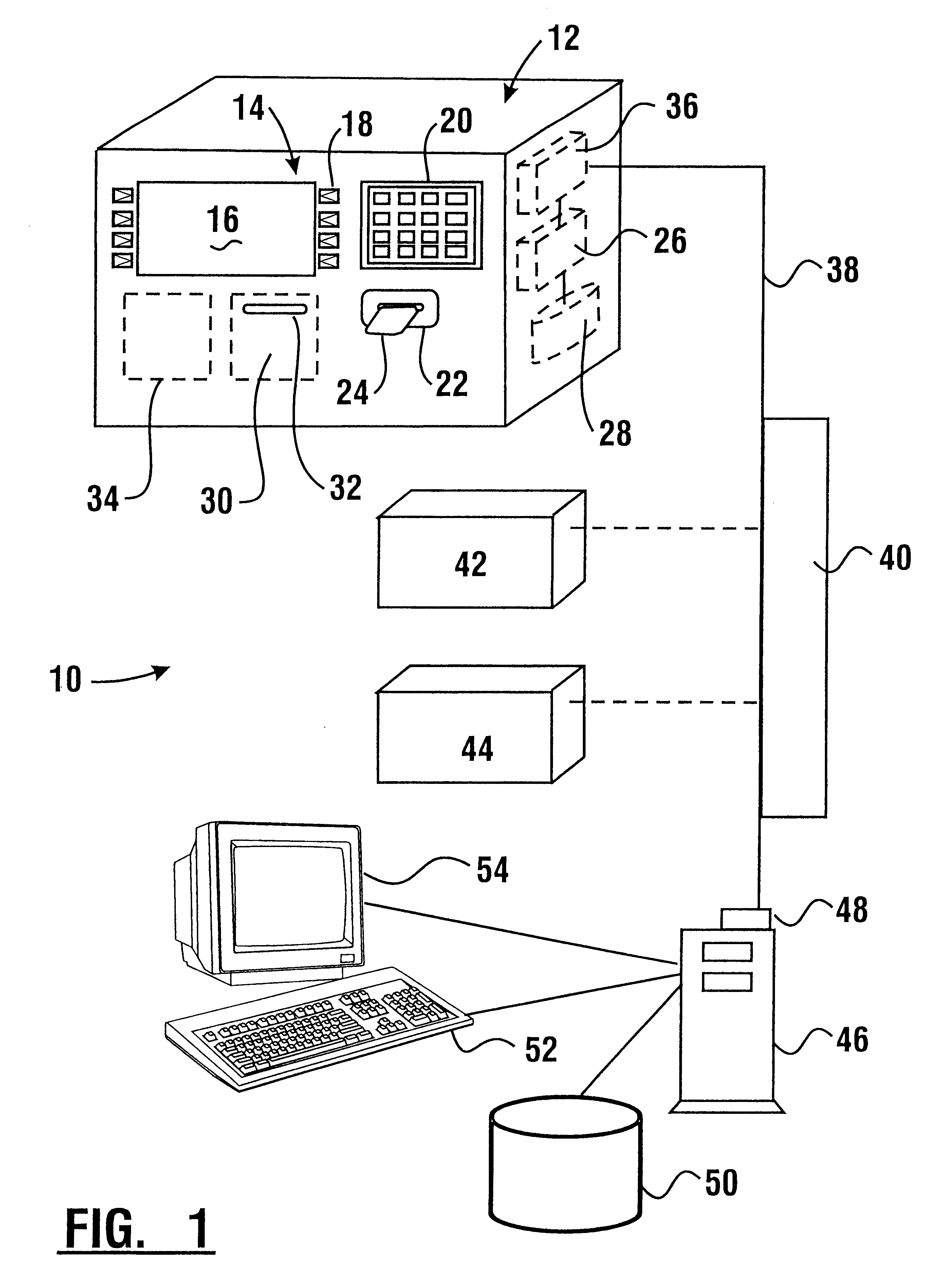
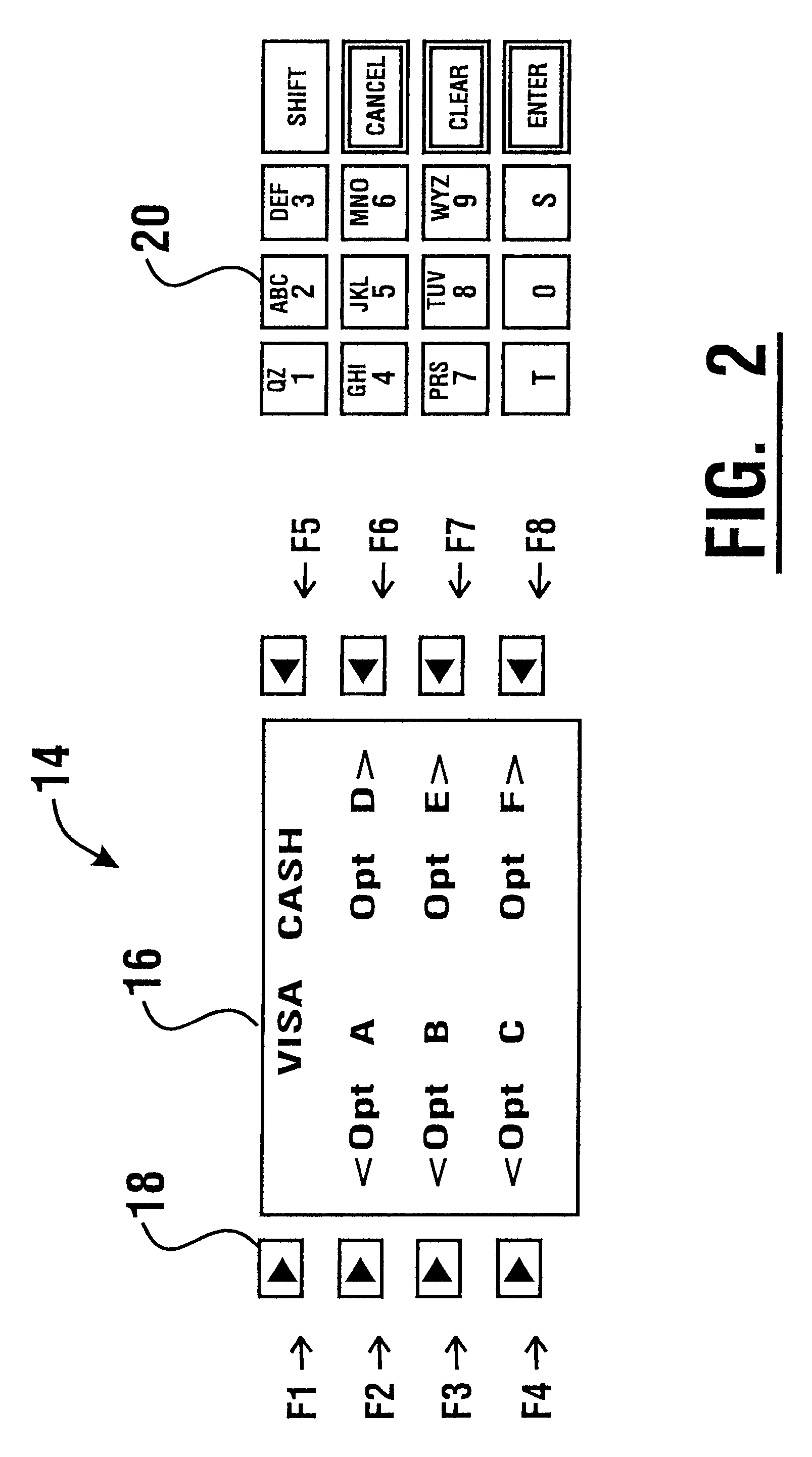
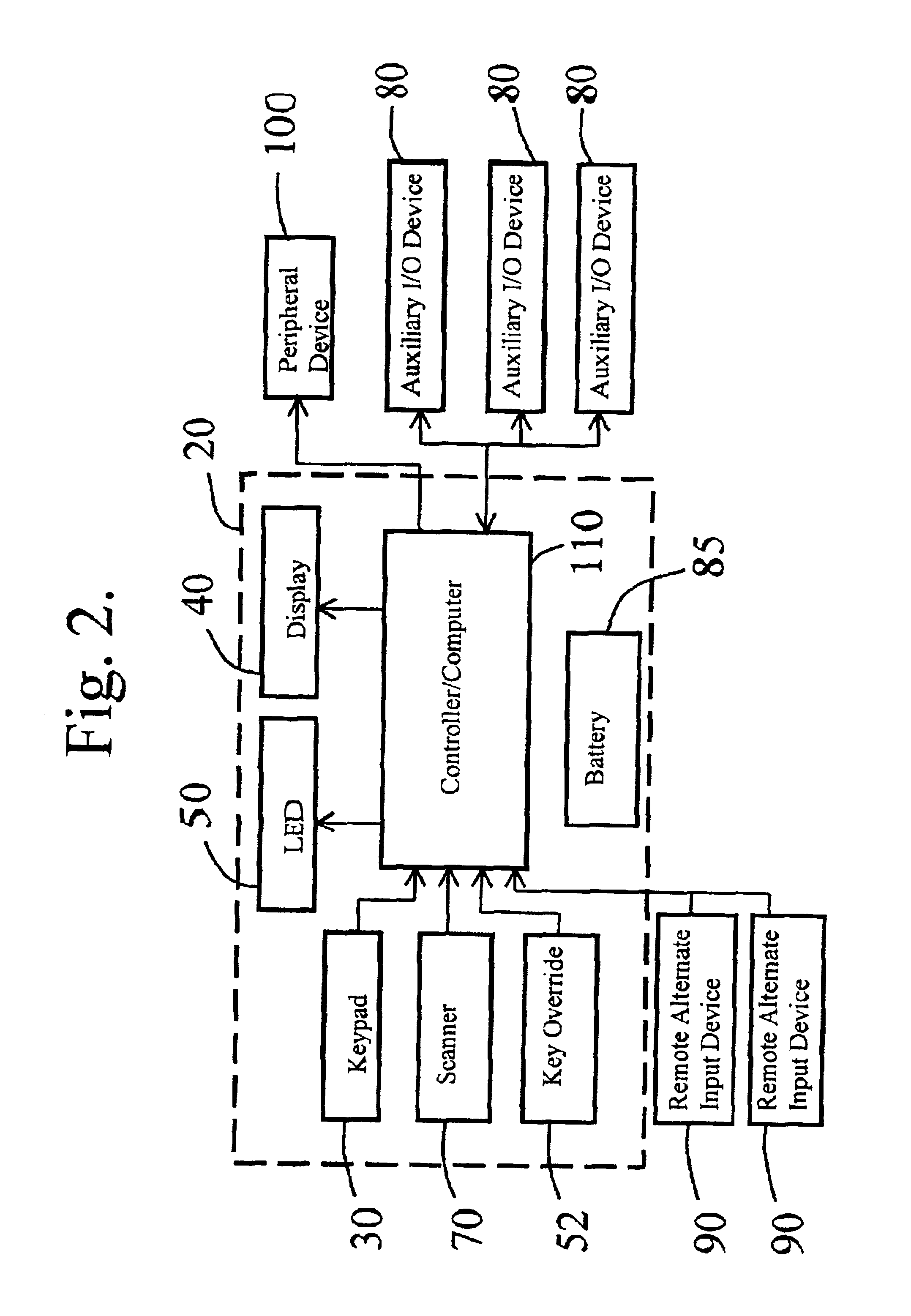
An electronic purse card value system (10) includes terminal devices (12). Each terminal device includes a processor (26) which is in operative connection with a memory (28) and a modem (36). The processor is further in operative connection with components of the terminal device including a customer interface (14) through which inputs are accepted and outputs are delivered, a card reader (22) and a printing device (30,34). The terminal devices are operative to communicate with host computers (42,44,46) through a communication system (38). The system is operative to carry out transactions in which data representative of value is loaded and unloaded from integrated circuit chips on customer cards (24). Data representative of value is stored in the memories of the cards such that certain value amounts are stored in one memory area while other value amounts are stored in a second memory area. A third amount is calculated which is a function of both the value amounts in the first and second memory areas and the third value is stored in memory on the card.
Owner:DIEBOLD NIXDORF
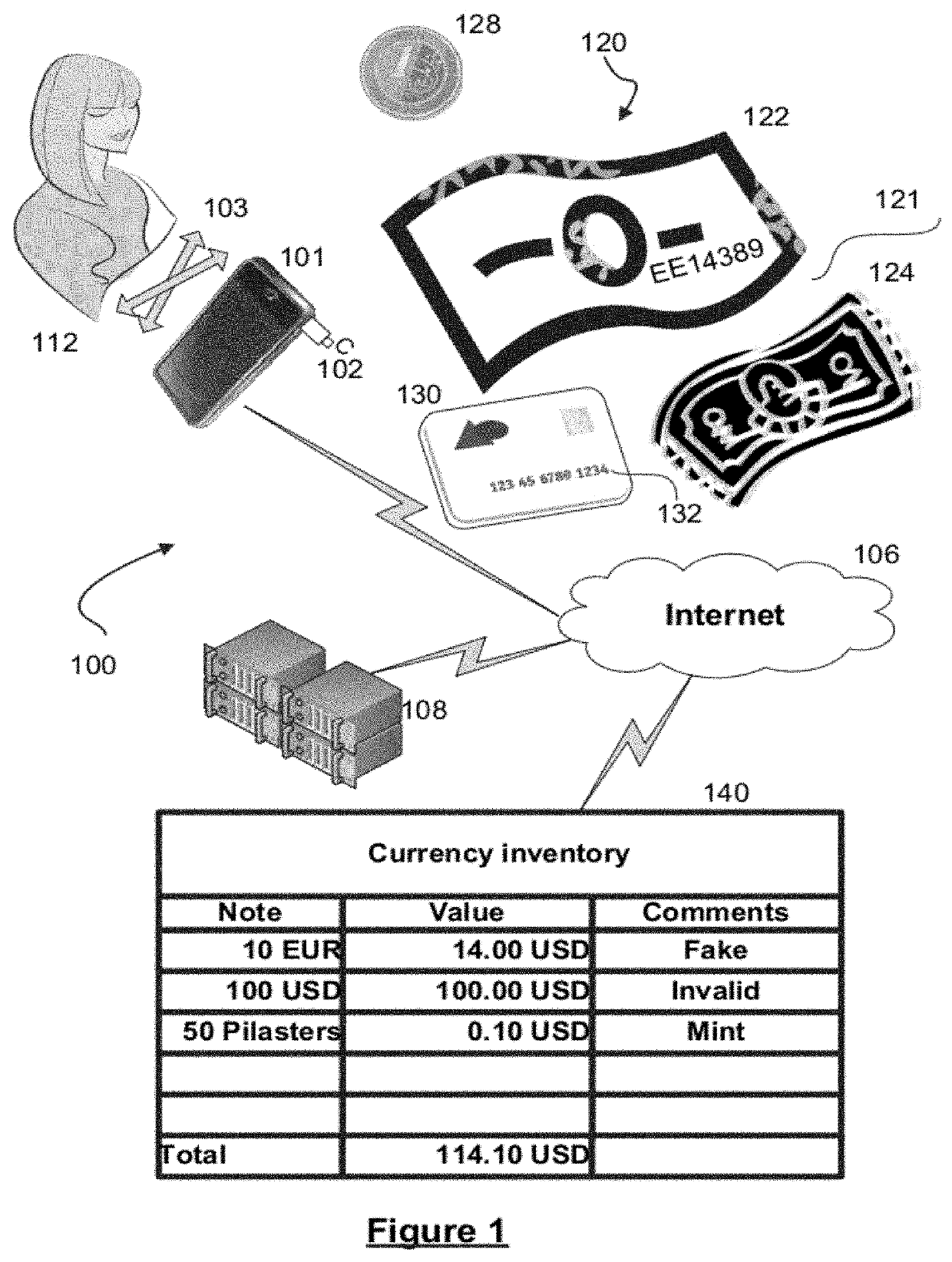
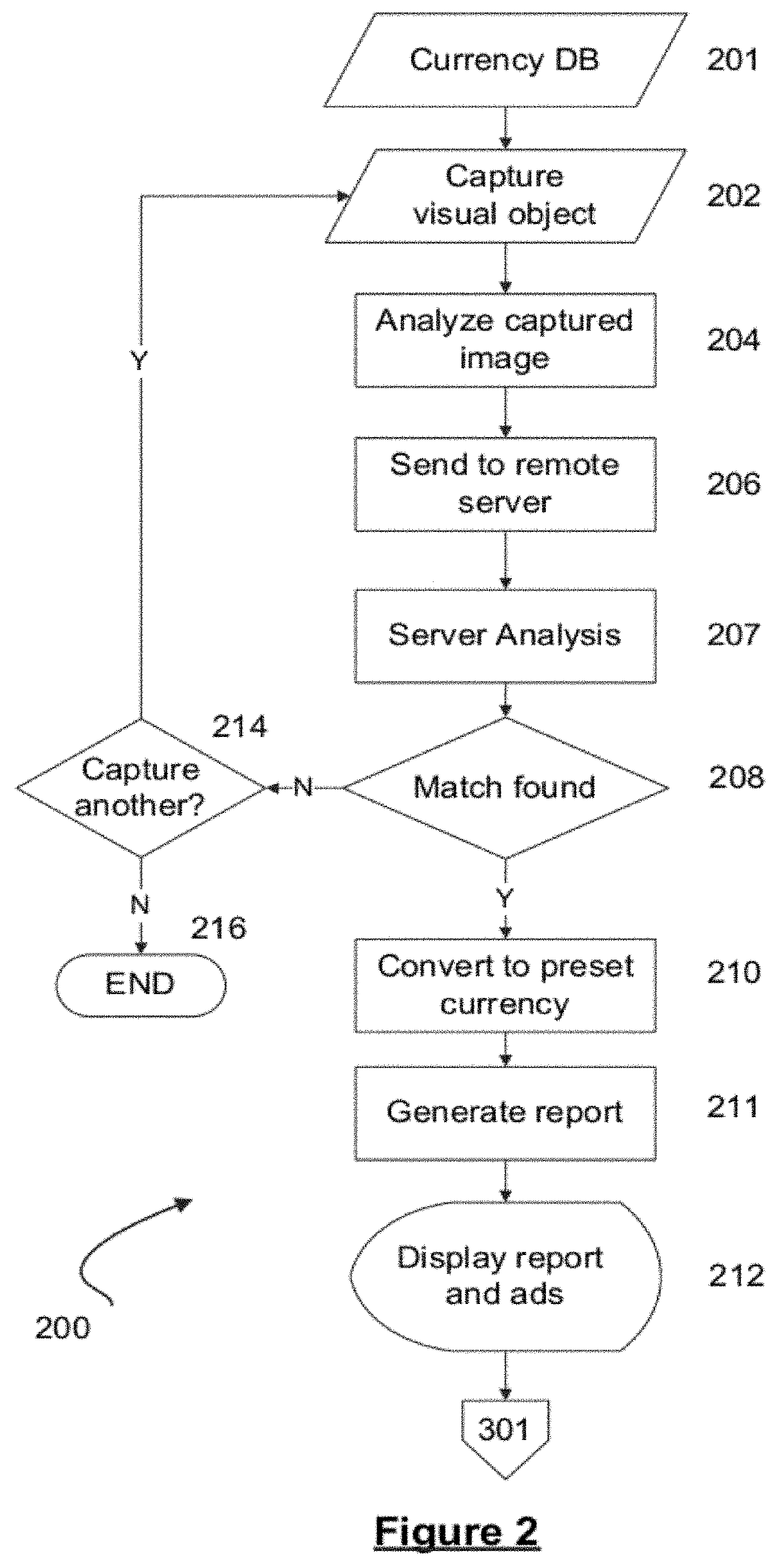
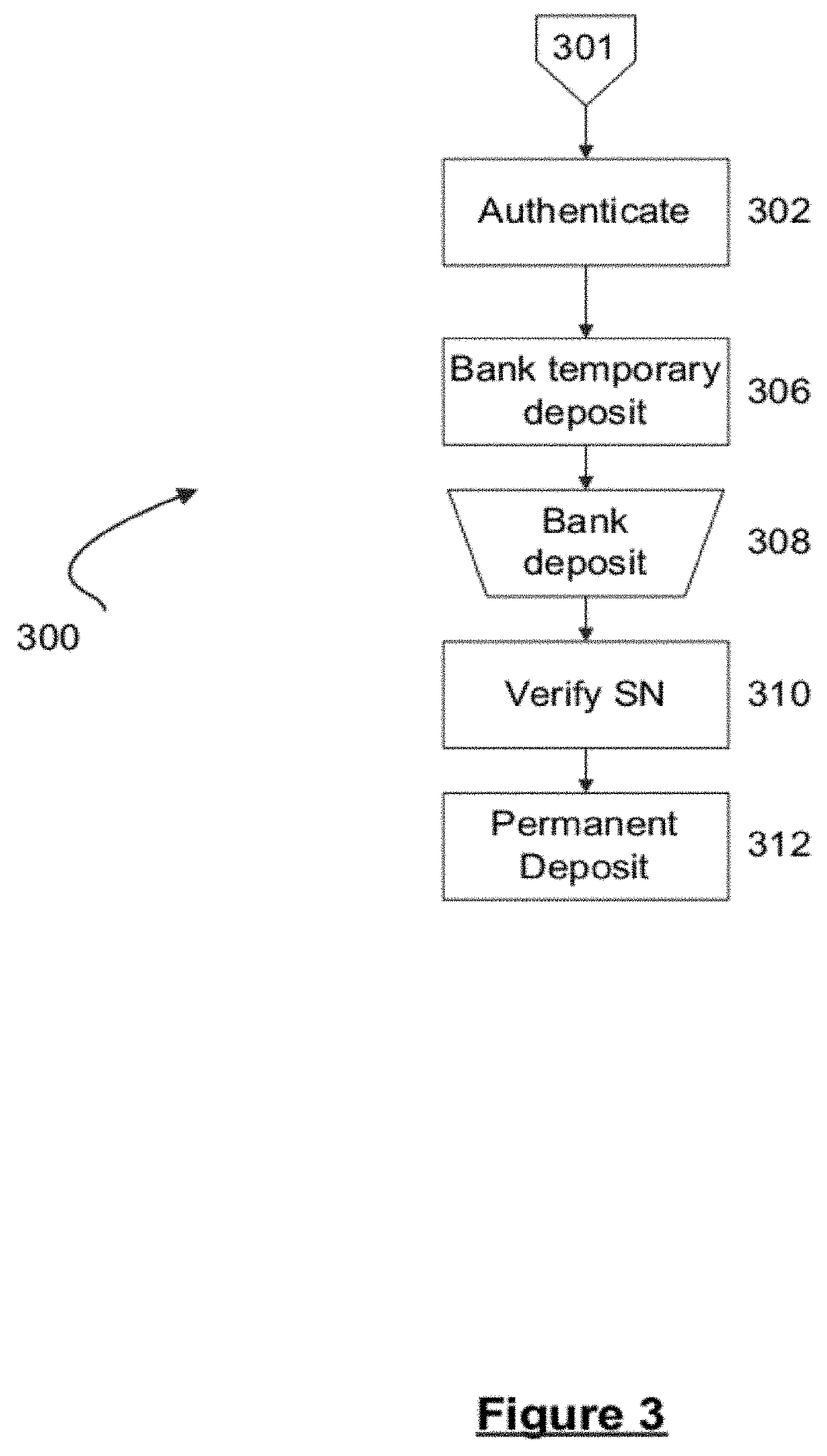
System and process for automatically analyzing currency objects
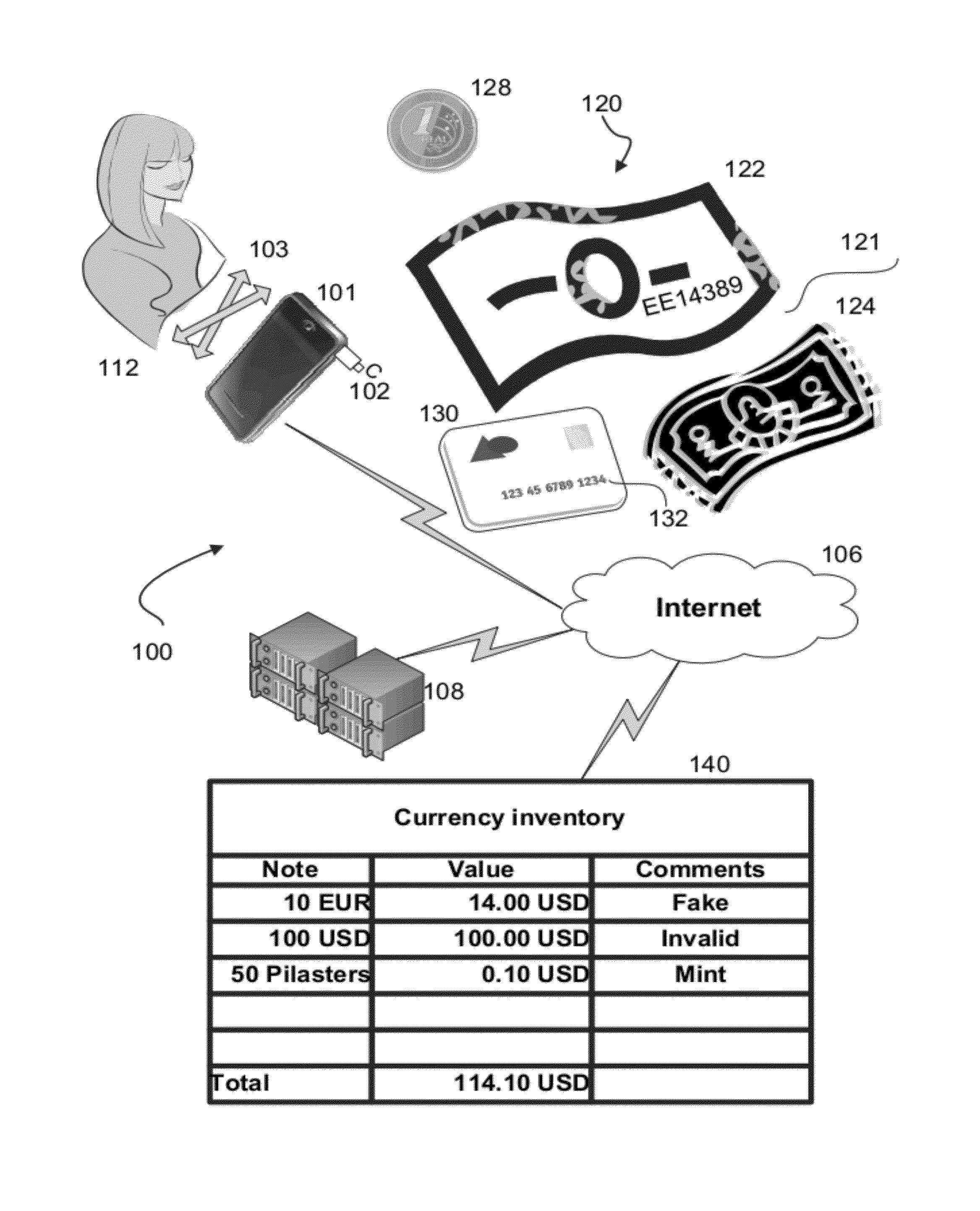
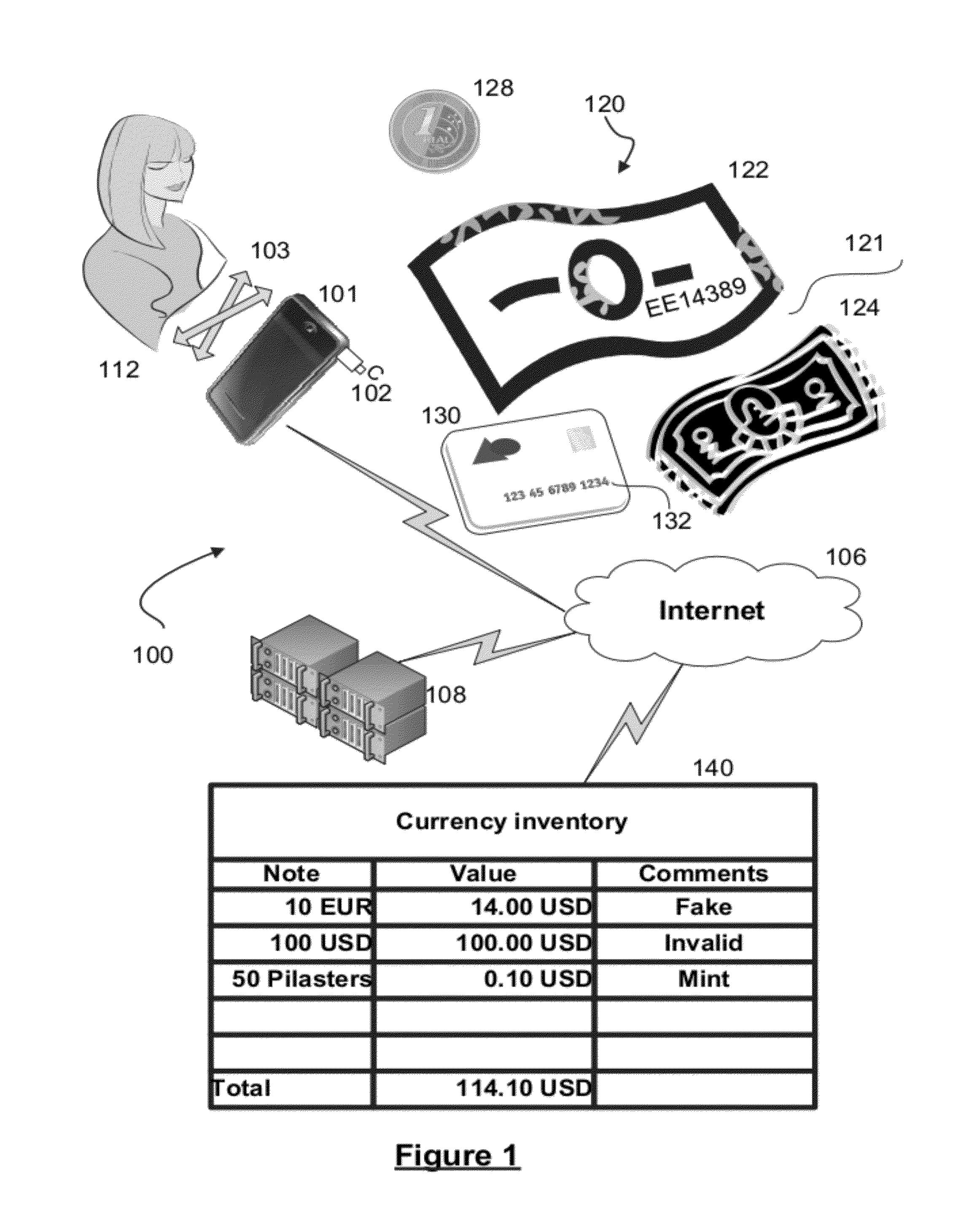
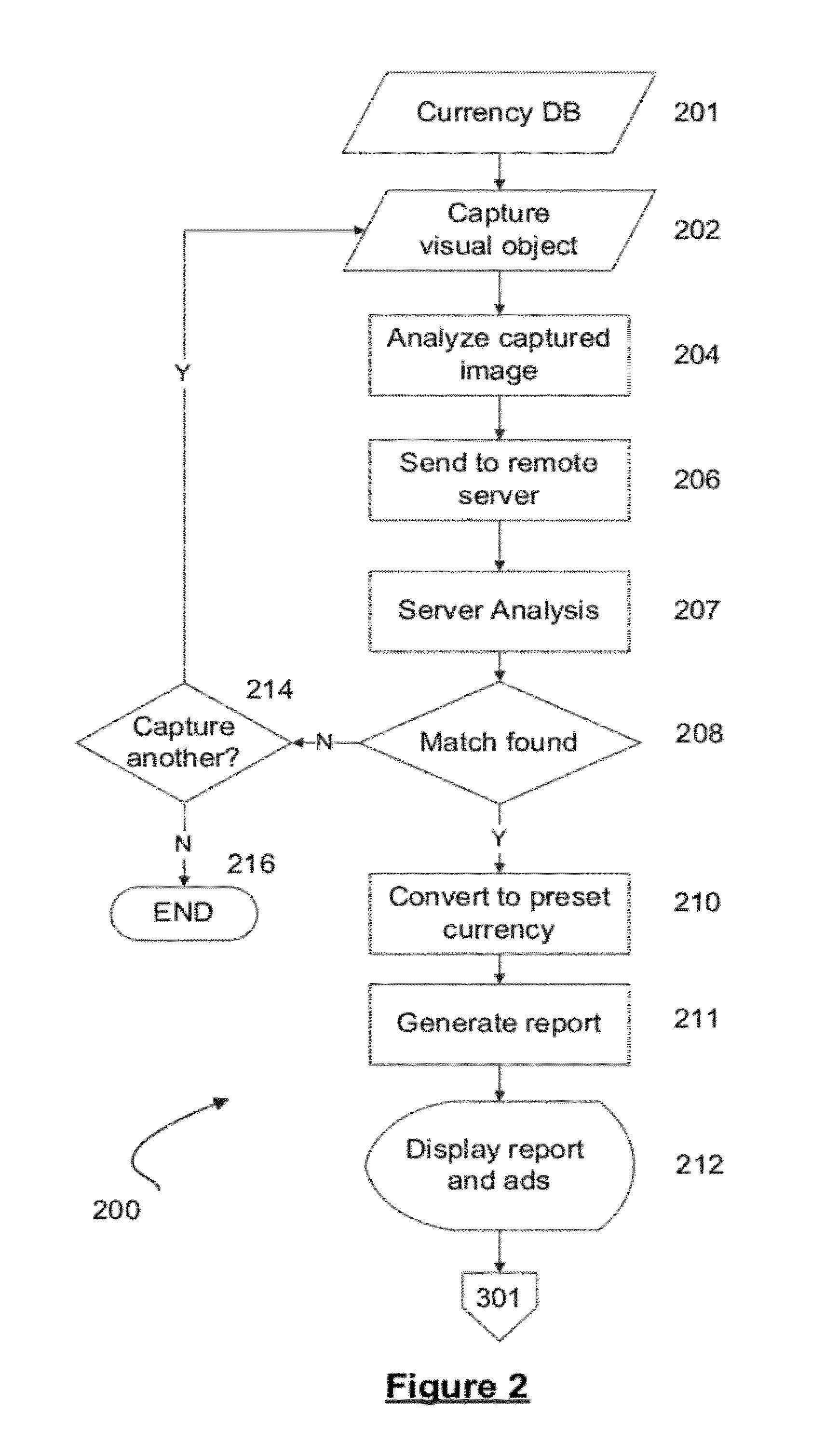
A method, system, and computer program product for analyzing images of visual objects, such as currency and payment cards, captured on a mobile device in determining their authenticity, and total amount of value. The system may be used in verifying the authenticity of hard currency, to count the total amount of the currency captured in one or more images, and to convert the currency using real time monetary exchange rates. The mobile device may also be used to verify the identity of a credit card user utilizing images of the card holder's face and signature, name on the card, card number, card signature, and card security code. Computerized content analysis of the captured images on the mobile devices as compared to images stored on a database facilitates a merchant processing a customer's payment and a financial institute accepting a cash deposit.
Owner:ATSMON ALON +1
Security code activated access control system
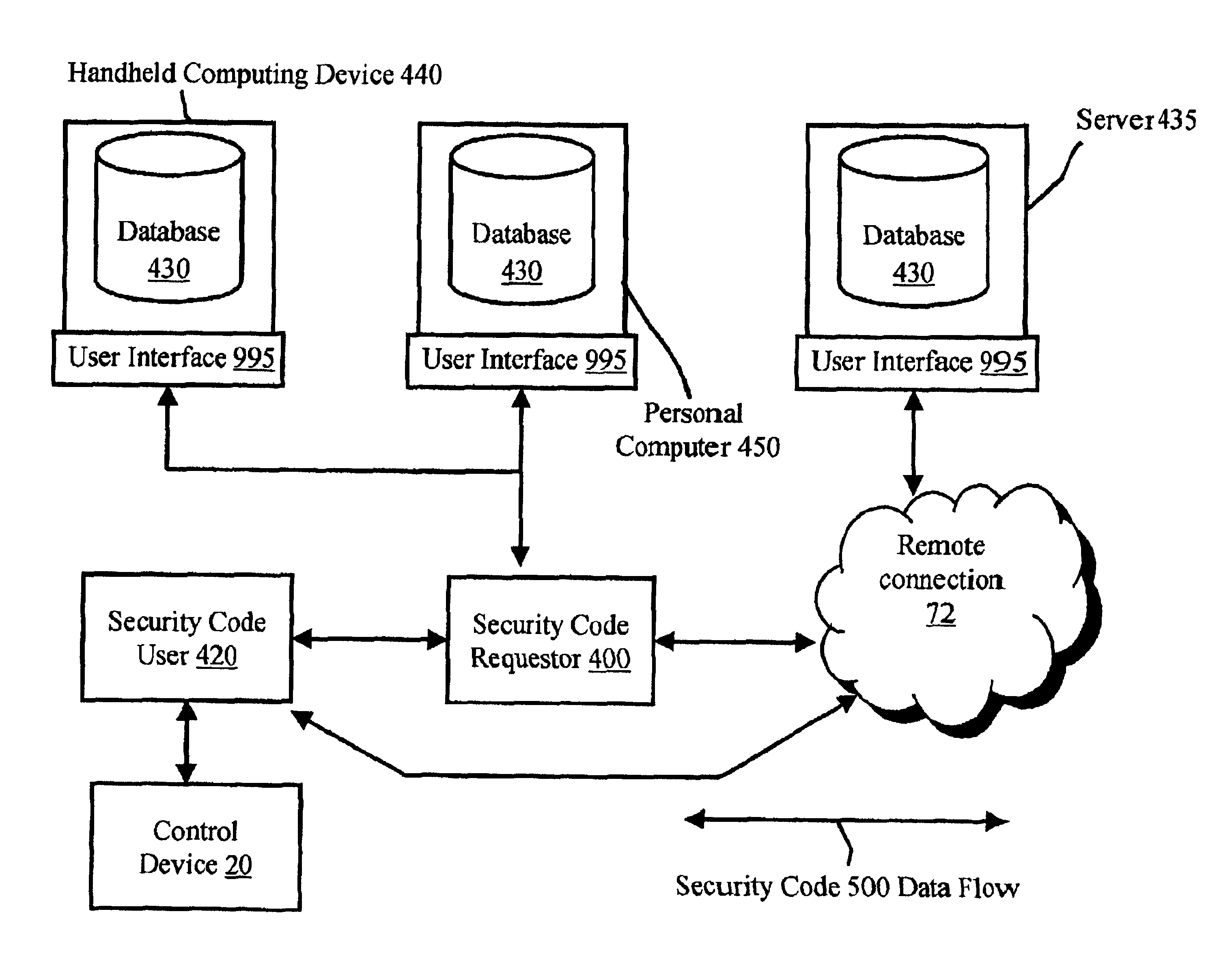
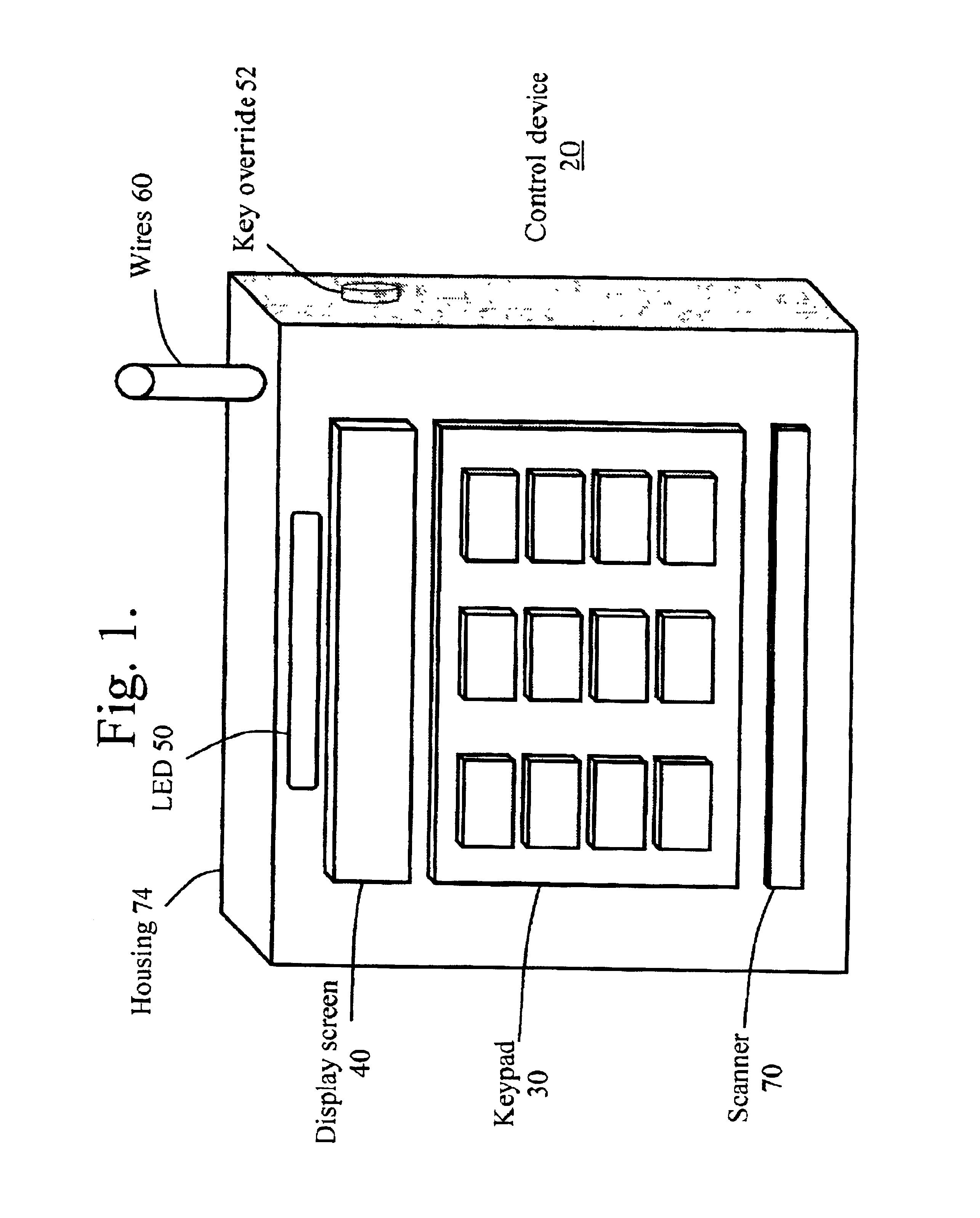
InactiveUS6950944B2Easy to controlImprove securityDigital data processing detailsUser identity/authority verificationControl systemCard security code
An access control system that utilizes security codes (500), a database (430), and a control device (20) is disclosed. Each security codes (500) is comprised of a unique key code (502) that provides security in addition to a use code (503) that is used to convey specific user defined functions. The use code (503) may be determined by the security code requester (400) at the time of security code (500) charge out from the database (430). The database (430) controls the issuance of security codes (500) and the control device (20) validates the key code (502) within the security code (500) against key codes (502) within control device (20) memory and if valid, performs an action based on the validation of the use code (503) parameters. As the key codes (502) that are within the control device (20) memory are used, the control device (20) then self-regenerates the key codes (502) in order to extend the control device (20) service life indefinitely. The database (430) and the control device (20) have security code (500) activities that are synchronized, though the two operate independently and are not electronically connected. The system provides a secure interface for obtaining access authority from the database (430). Security code requesters (400) contact the database (430) and request security codes (500) in order to activate a specific control device (20). After database (430) issuance, the security codes (500) are then input by the security code user (420) at the control device (20) location and activates the control device (20) if the key code (502) matches the key code (502) within the control device (20) and the use code (503) parameters are validated by the control device (20). The control device (20) and the database (430) key codes (502) are synchronized. This allows an unlimited supply of security codes (500) to be issued by the database (430) and used by the control device (20).
Owner:YAGER DAVID FR +1
Digital anti-counterfeiting method based on chaos password encryption
InactiveCN102184506AHas a cyclePseudo-randomUser identity/authority verificationCommercePasswordSecret code
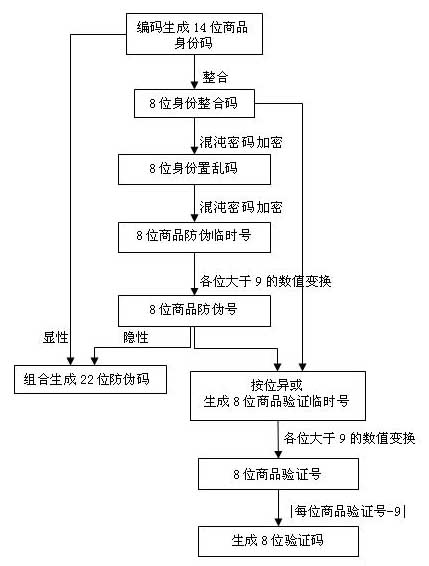
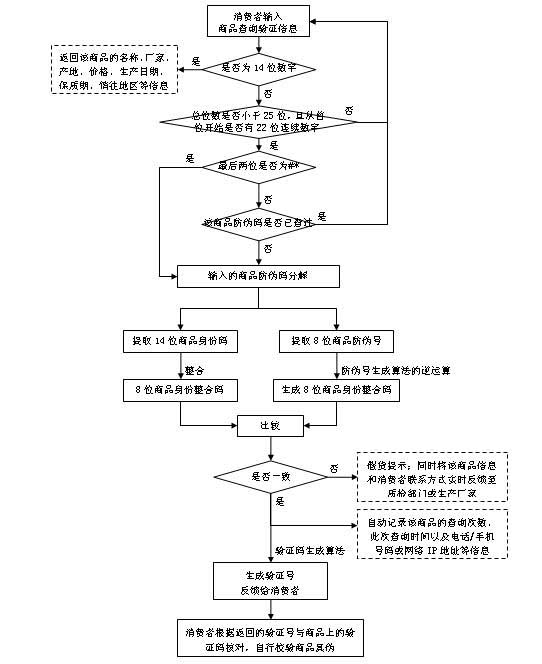
The invention discloses a digital anti-counterfeiting method based on chaos password encryption, which comprises a code making step and an inquiring and verifying step. Double-labeled double codes, namely a security code and a verification code, which can be automatically separated after the consumption are generated by using a chaos password encryption algorithm; a user can inquire many times in different inquiry ways; bidirectional verification is adopted for checking the authenticity of goods, that is to say, a digital anti-counterfeiting center verifies the authenticity of the goods according to the security code sent by a consumer, and the consumer can simultaneously identify the authenticity of the goods and the anti-counterfeiting center according to the verification code returned by the anti-counterfeiting center. The digital anti-counterfeiting method disclosed by the invention has the characteristics of high anti-counterfeiting security, wide application range, resource saving and the like; the method is convenient for carrying out large-scale anti-falsifying census, and can block loopholes on fakes made by means of recycled packing materials or by enterprise internal staff and dealers who take advantages of the positions.
Owner:NANTONG UNIVERSITY
Security for electronic transactions and user authentication
InactiveUS20180197171A1Improve user securityMinimizing adoption burdenCredit schemesDebit schemesPayment transactionFinancial transaction
System and method for generating, disseminating, controlling, and processing limited-life security codes used to authenticate users, particularly for electronic financial transactions, such as payment transactions. Providing a user with a single security code usable across multiple accounts or other secured systems is contemplated, each security code having a limited lifetime. Each security code is a random number from a random number generator. The respective security codes for each user correspond to a respective security code validity period of limited duration. Thus, a table or matrix that associates the plurality of users with the respective sets of randomly selected security codes (each having their respective validity periods) is generated, and that matrix is provided to the respective entities to which each user requires secured access. In parallel, at least a current security code is provided to each user, and this is how the respective entities being accessed can track which code from which user is currently valid.
Owner:TENDER ARMOR LLC
Commodity digital anti-counterfeit method
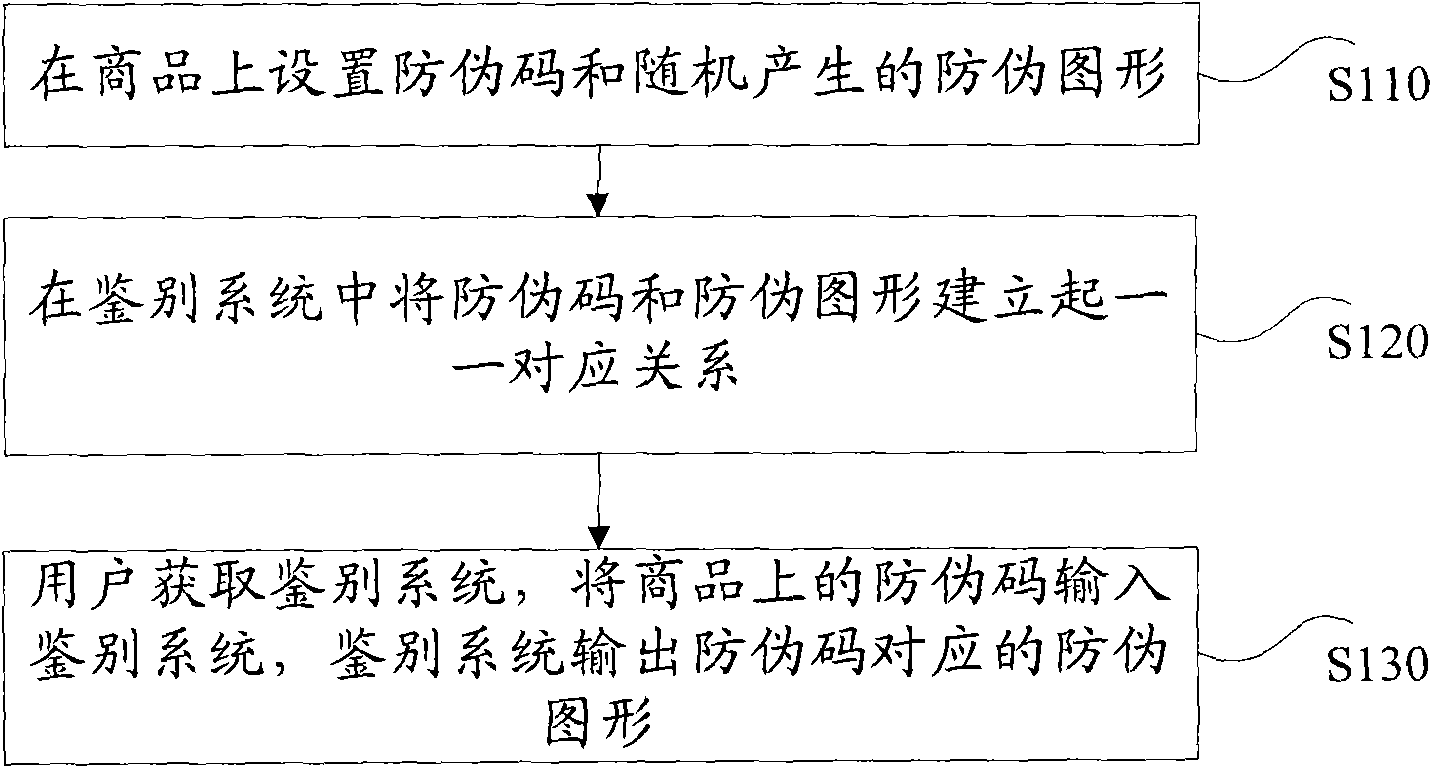
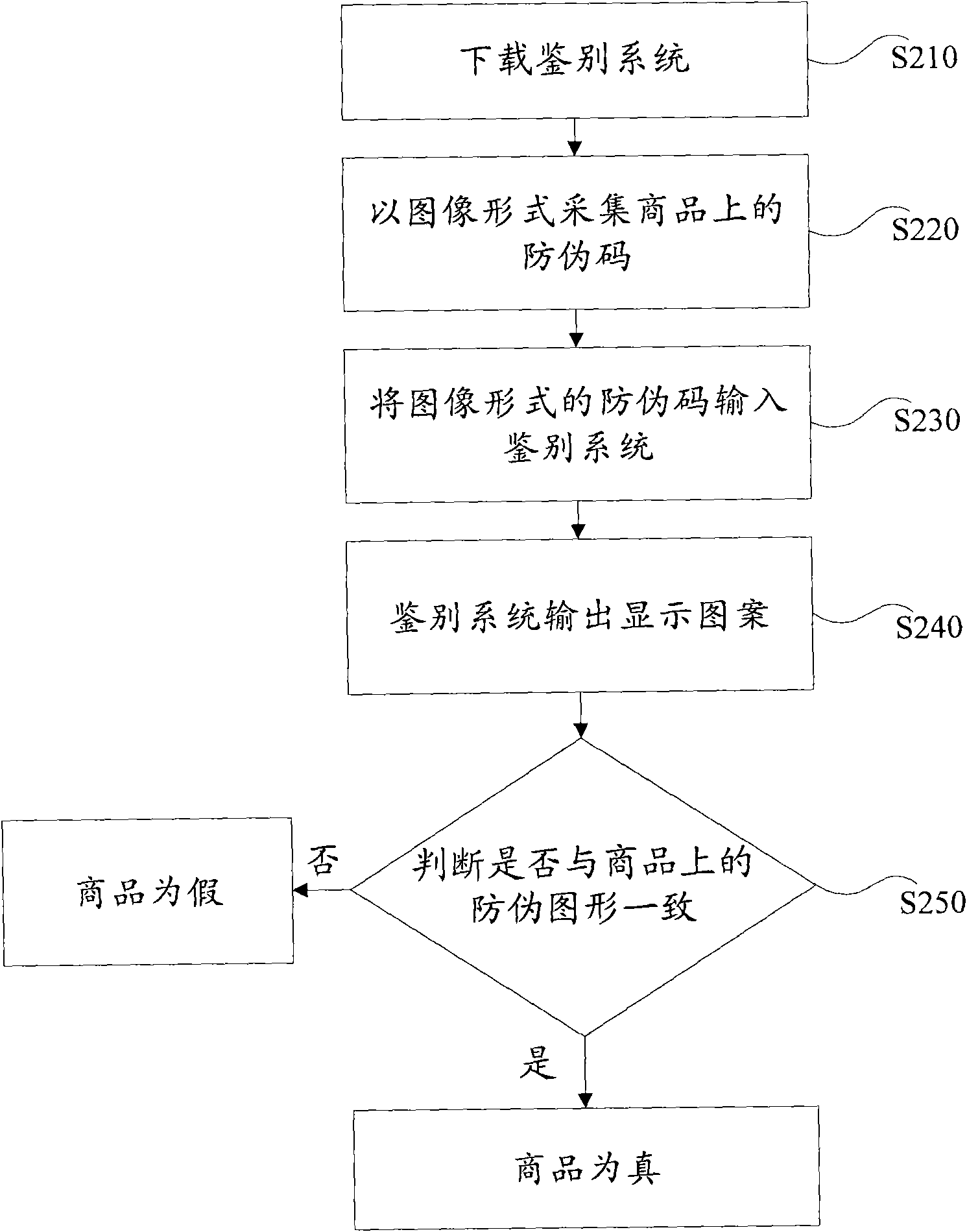
InactiveCN101673387ANot easy to imitateImprove query efficiencyCommerceSpecial data processing applicationsComputer hardwareGraphics
The invention provides a commodity digital anti-counterfeit method. The method comprises the following steps: setting security codes and randomly generated anti-forgery patterns on commodities; building one-one correspondence between the security codes and the anti-forgery patterns in an identification system; obtaining the identification system for users, inputting the security codes on commodities to the identification system, and outputting the anti-forgery patterns corresponding the security codes by the identification system. The method of the invention does not need real-time networkingsupport, the query efficiency is high and the query cost is low.
Owner:SHENZHEN JINJIA GRP
Policy abstraction mechanism
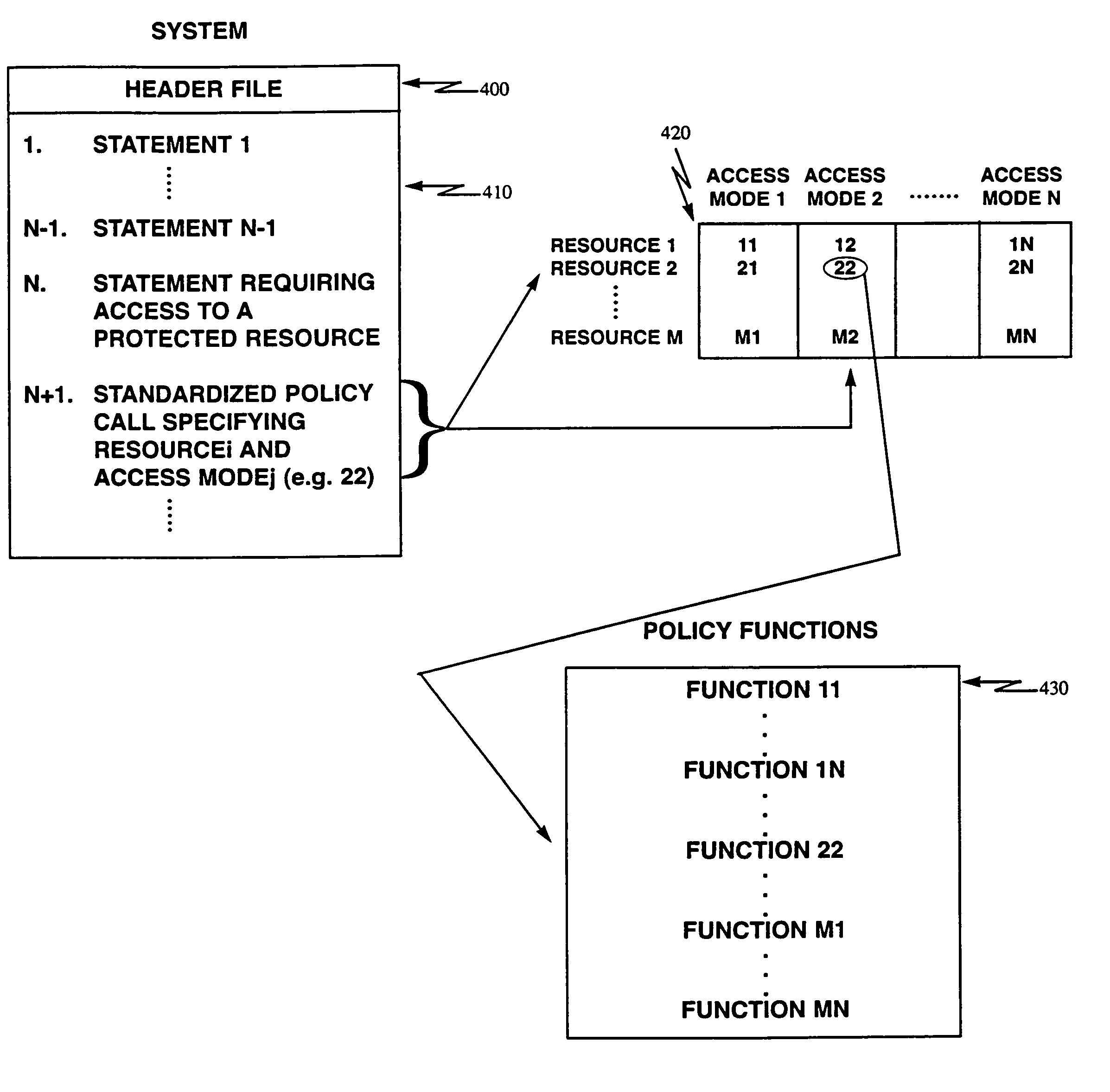
InactiveUS7185210B1Digital data processing detailsMultiprogramming arrangementsOperational systemCard security code
A secure operating system is disclosed in which all code implementing security functionality resides in a security module separate from the operating system code. Calls involving security functions are made using a format or interface which is standardized for all systems. Such a call identifies, inter alia the response and the access mode which are used to identify a call in a two dimensional table which contains a pointer to the needed security functions. In the way security functions are separately compilable and security solving changes can be made by linking in a new security module. Maintenance of security code is separated from maintenance of the underlying operating system.
Owner:ORACLE INT CORP
System and method for utilizing a mobile device to obtain a balance on a financial transaction instrument
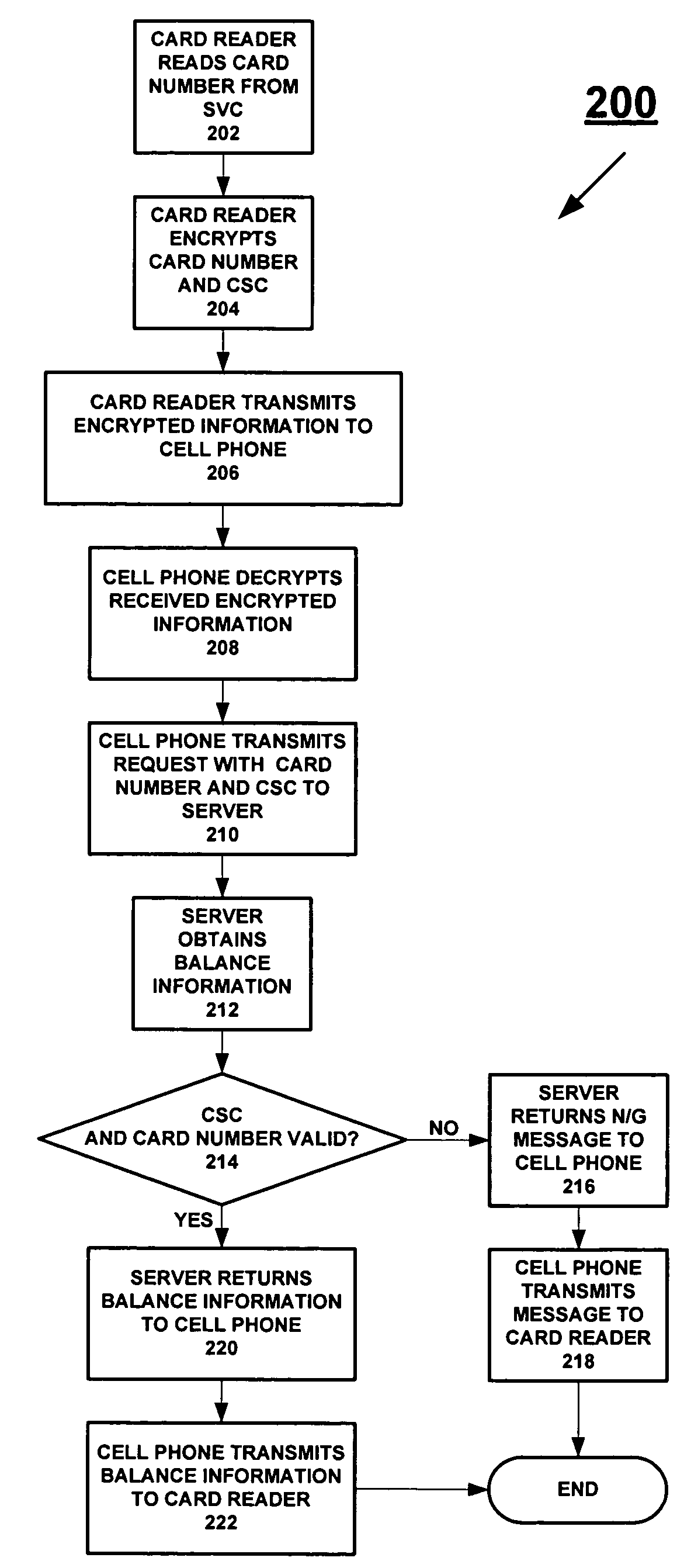
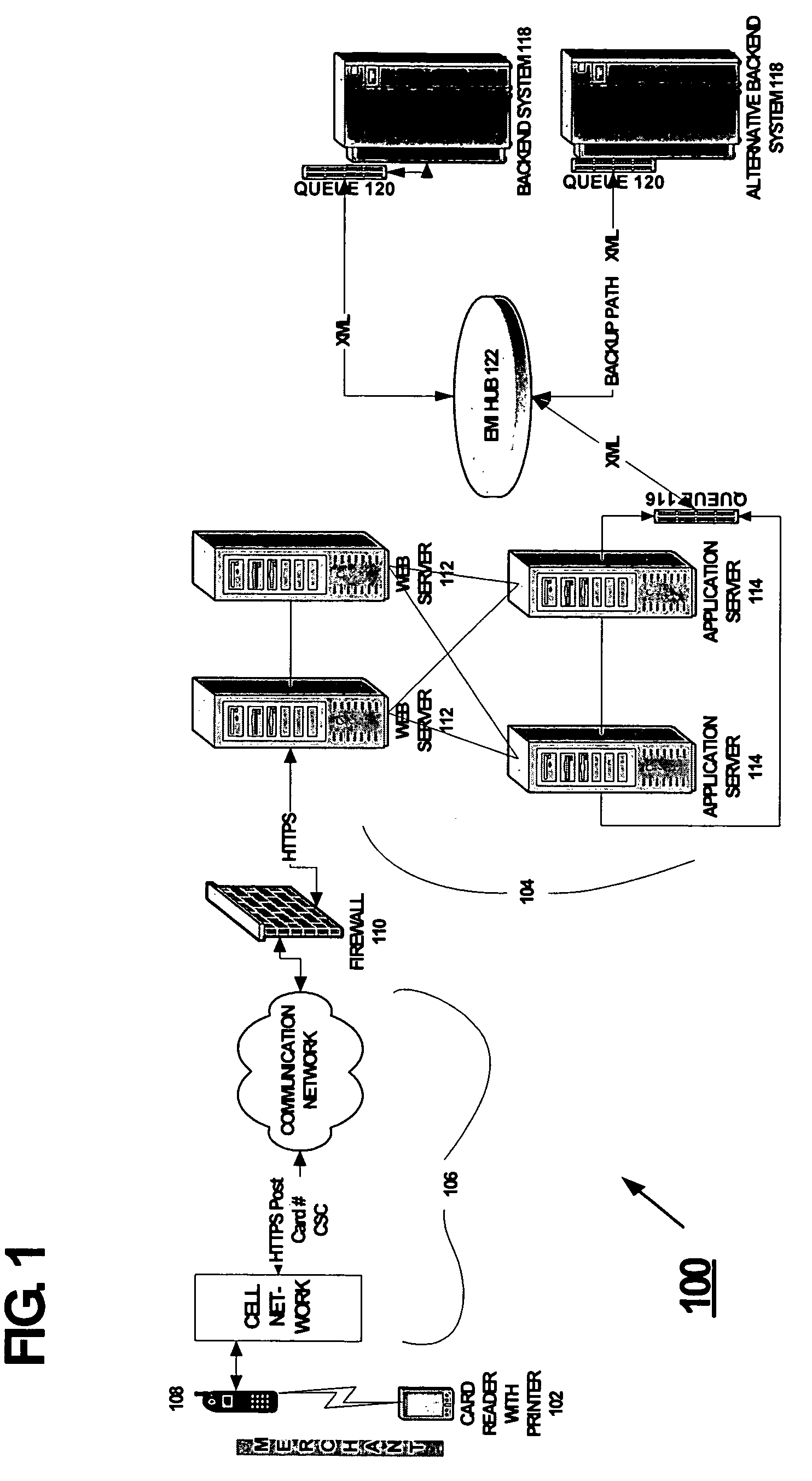
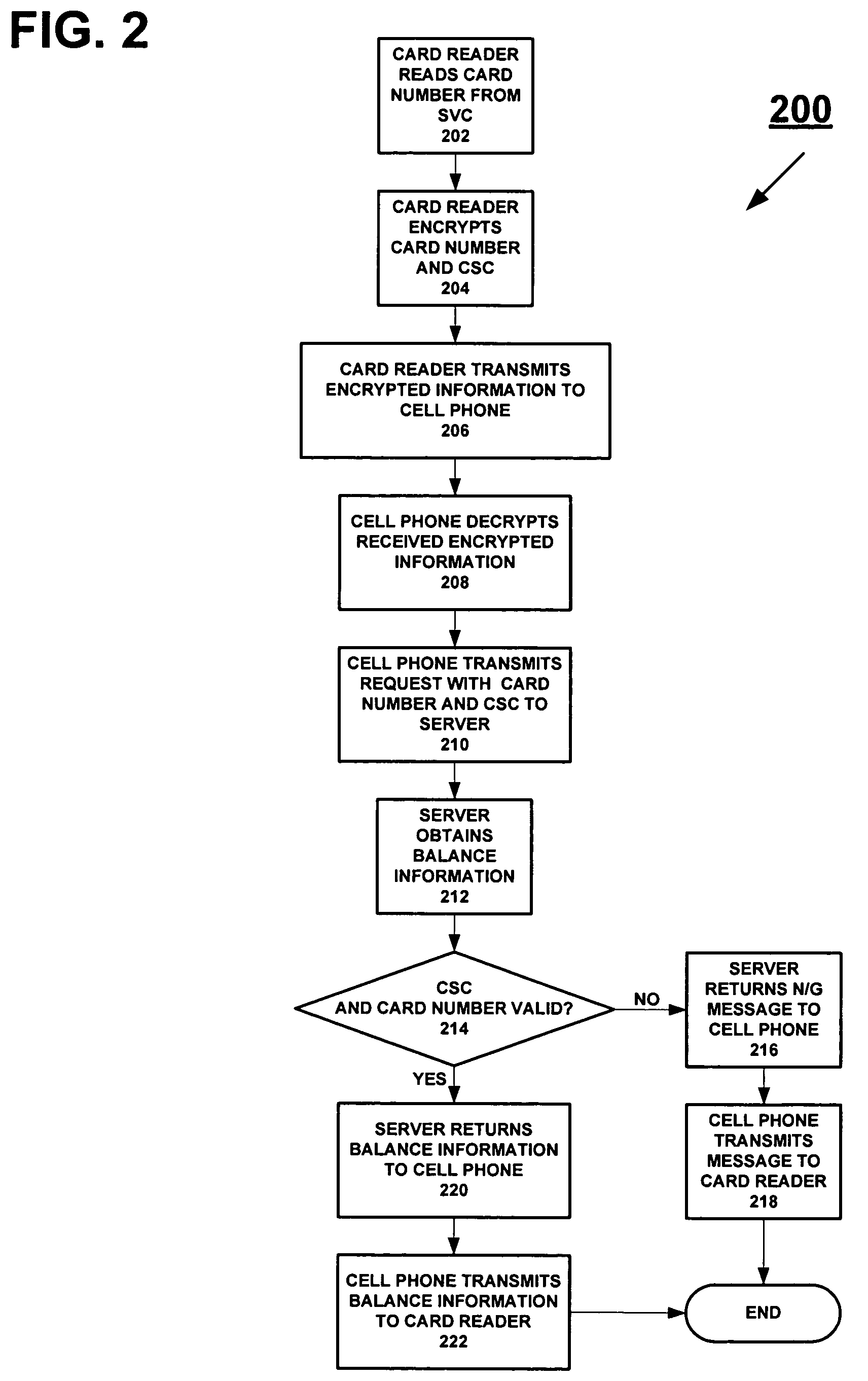
InactiveUS7635083B2Fast readBalance can be obtainedComplete banking machinesCredit registering devices actuationFinancial transactionCard reader
The balance of funds remaining for a stored-value card (“SVC”) may easily be determined without going through an actual purchase transaction with the SVC. The balance is obtained wirelessly from a server storing information pertaining to SVCs, and may be provided in a discreet manner. A card reader adds a card security code to a card number read from the SVC, and encrypts the card number and the CSC. The encrypted information is wirelessly sent to a cellular telephone. The cellular telephone decrypts the encrypted information and wirelessly transmits a balance-information request, which includes the card number and the CSC, to the server. The server receives the request and wirelessly sends the requested balance information to the cellular telephone and, in turn, the cellular telephone wirelessly sends the requested balance information to the card reader, which provides the information to the requester.
Owner:LIBERTY PEAK VENTURES LLC
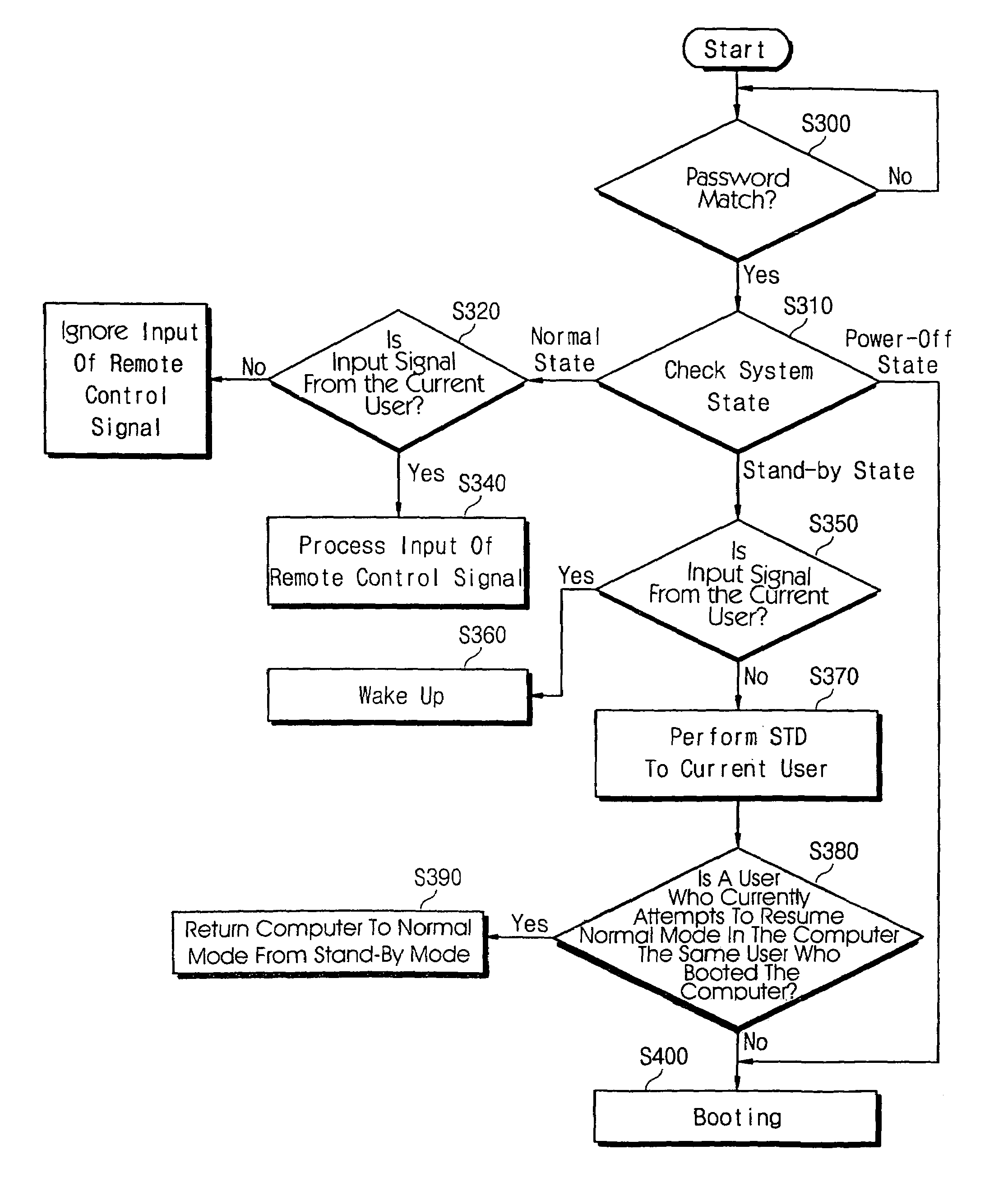
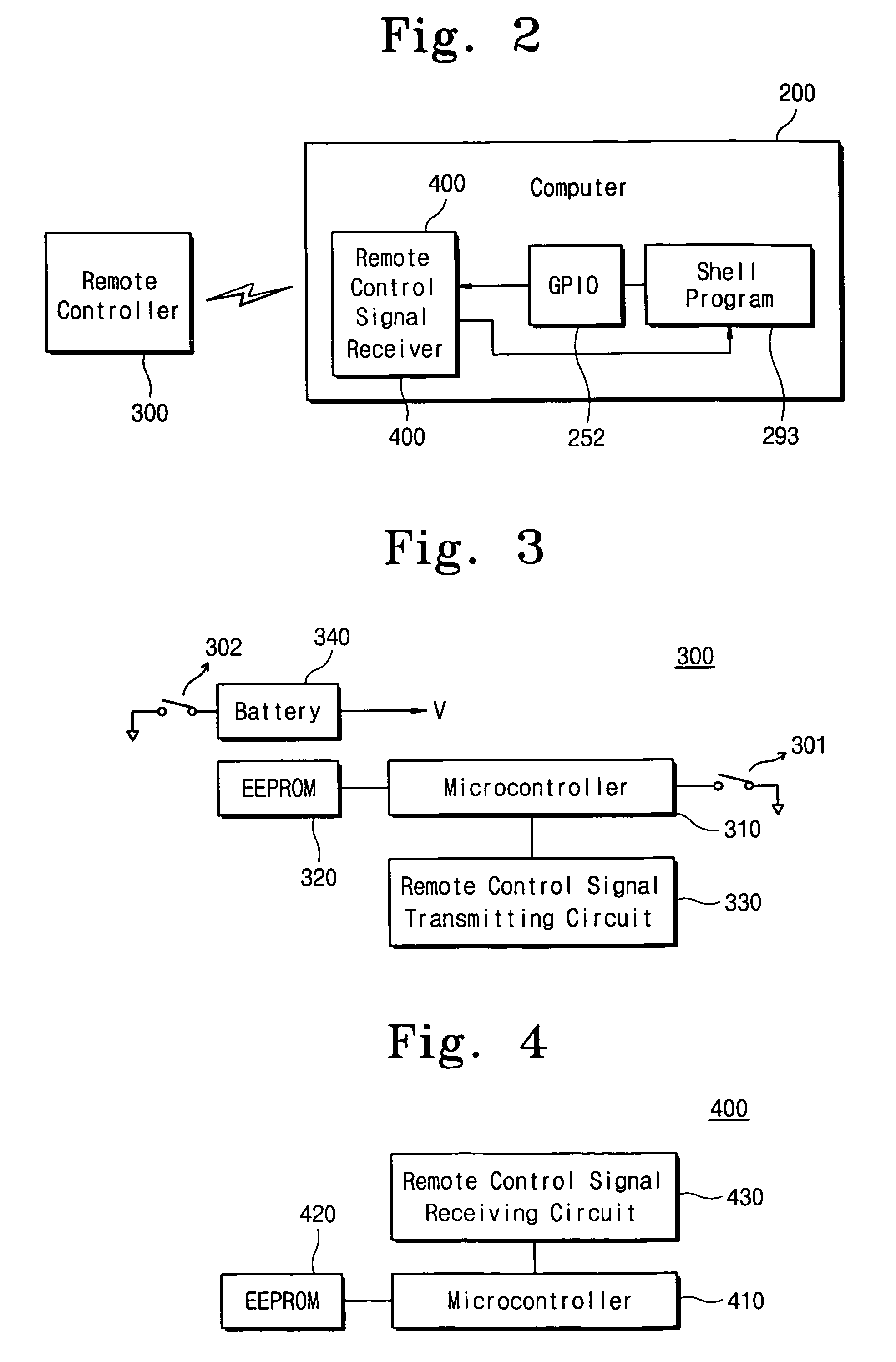
Method for automatically verifying security code of computer system operated by remote controller
InactiveUS7020785B2Convenient verificationMemory loss protectionError detection/correctionRemote controlControl system
A computer system includes a remote controller for generating a remote control signal to remotely control operations of the system, a remote control signal receiver for receiving the remote control signal generated from the remote controller, and a shell program for executing various remote control operations by the remote controller. If a security code verification operation is performed when the computer system returns from a stand-by state to a normal state by the remote controller, the shell program serves to automatically input a security code transmitted from the remote controller. This makes it possible to automatically input a security code that a user must directly input using an input device such as a keyboard, when the computer system returns to the normal state. Therefore, user convenience can be enhanced.
Owner:SAMSUNG ELECTRONICS CO LTD
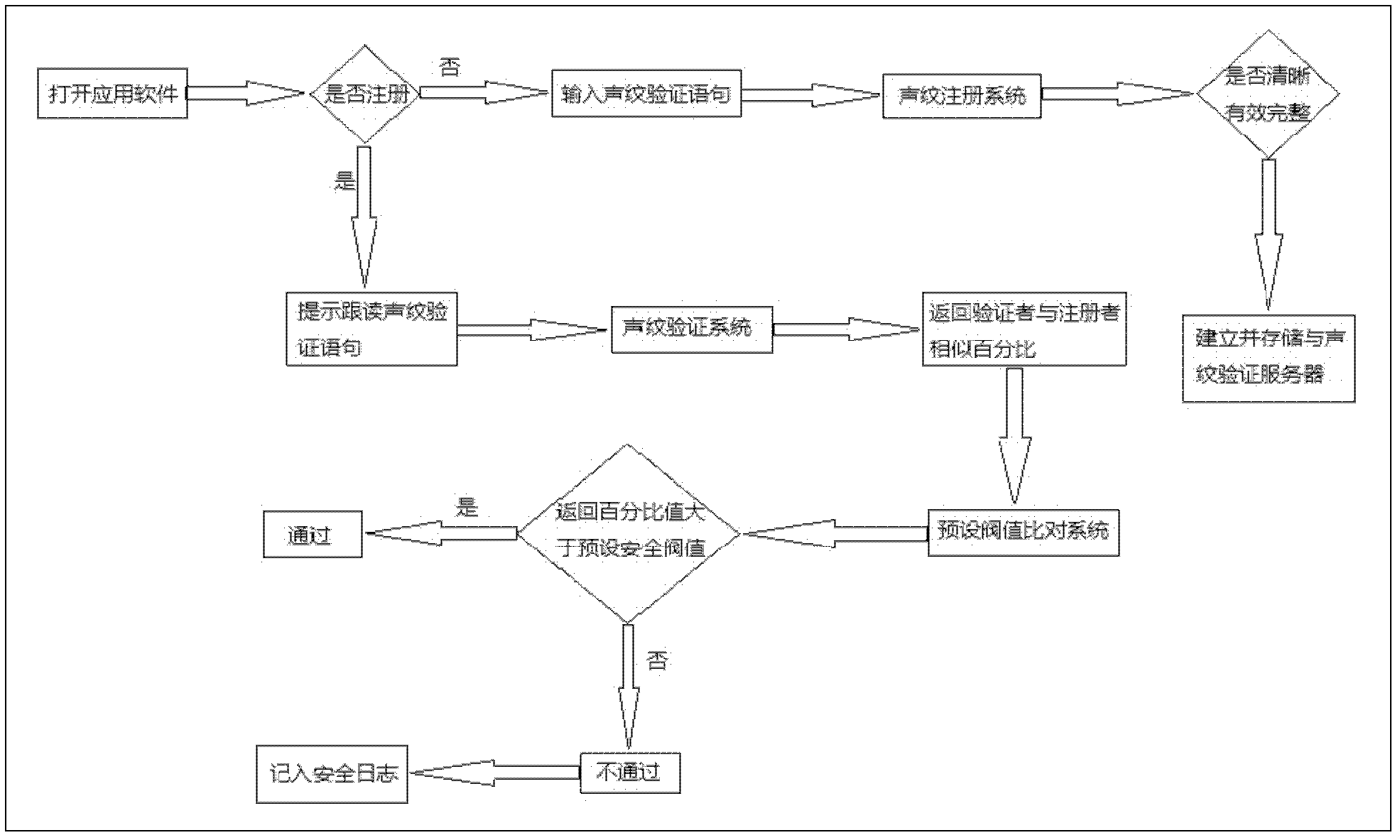
Technology for applying vocal print verification as security codes of mobile applications
InactiveCN102869008ASimplify the entry processThe effect is positive and obviousSecurity arrangementMobile Telephone NumberNetwork connection
The invention discloses a technology for applying vocal print verification as security codes of mobile applications. The technology comprises the steps as follows: using a mobile phone which comprises a vocal print sampling module; conducting vocal print registration for the first time, uploading a registration number and vocal print characters to a vocal print verification server through the mobile phone, and establishing a vocal print file of a register on the server; according to differences of the vocal print verification modes, enabling a user to follow to speak a verification sentence; sending a mobile phone number and verification voice stream to the vocal print verification server by application software through safe network connection; comparing vocal print characters of the voice stream and the vocal print of the mobile phone number in registration by the vocal print verification server, and returning the similar percentage; and according to self security requirement, allowing the user to use the software if the probability exceeds a set threshold value, otherwise, refusing using the software and making records into a security log. According to the scheme, the security is guaranteed by utilizing the uniqueness of personal voice and through verification by the vocal print verification server, meanwhile, the cracking possibility is reduced at the same time, and the use convenience effect can be achieved.
Owner:上海先先信息科技有限公司
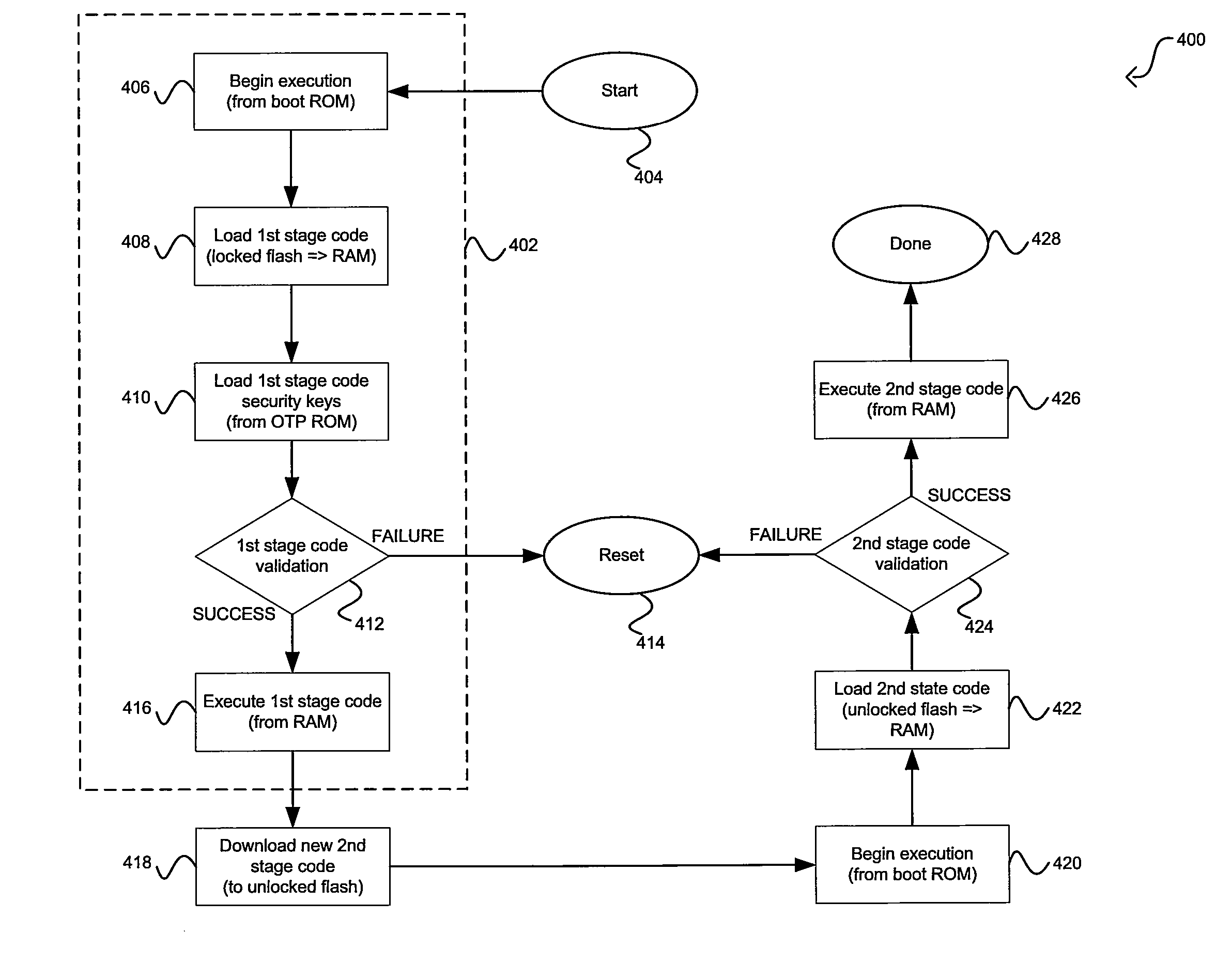
Method and system for two-stage security code reprogramming
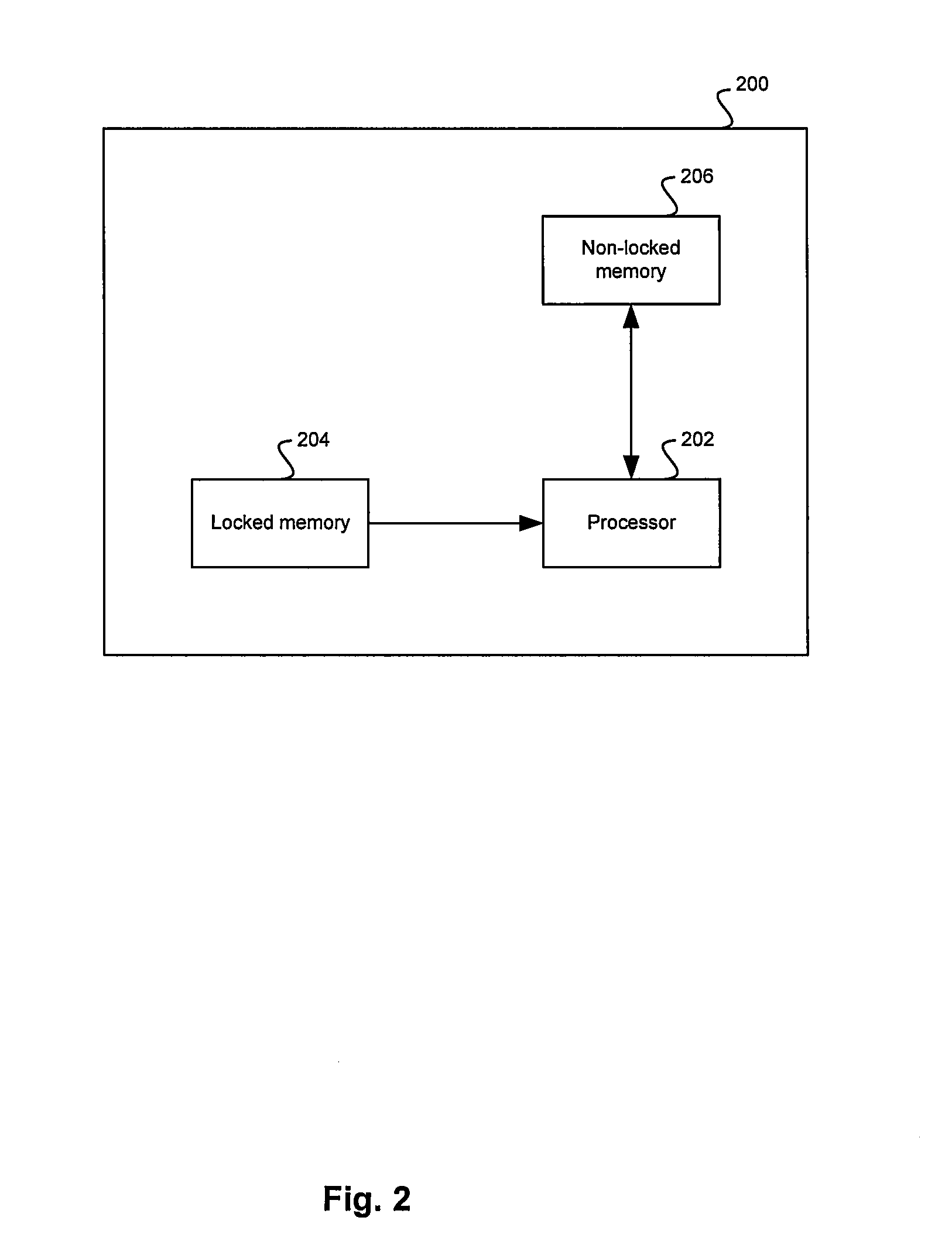
ActiveUS20080086628A1Digital computer detailsUnauthorized memory use protectionProgrammable read-only memoryReprogramming
A stored predefined unmodifiable bootable code set may be verified during code reprogramming of a device, and executed as a first stage of code reprogramming of the device. The predefined unmodifiable bootable code set may be stored in a locked memory such as a locked flash memory and may comprise code that enables minimal communication functionality of the device. The predefined unmodifiable bootable code set may be verified using a security algorithm, for example, a SHA-based algorithm. Information necessary for the security algorithm may be stored in a memory, for example, a one-time programmable read-only memory (OTP ROM). The stored information necessary for the security algorithm may comprise a SHA digest, a signature, and / or a key. A second stage code set may be verified and executed during the code reprogramming of the device subsequent to the verification of the stored predefined unmodifiable bootable code set.
Owner:AVAGO TECH INT SALES PTE LTD
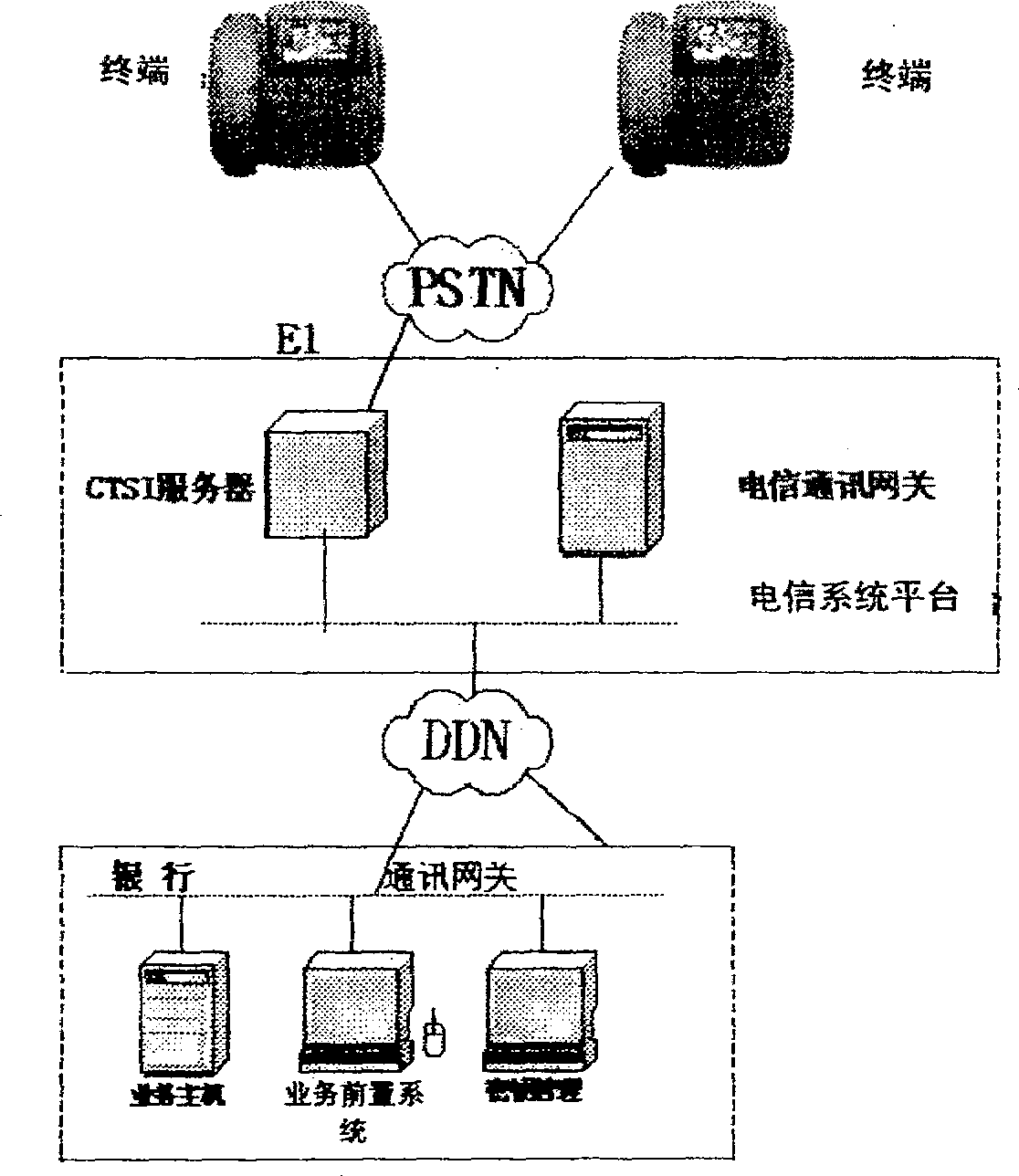
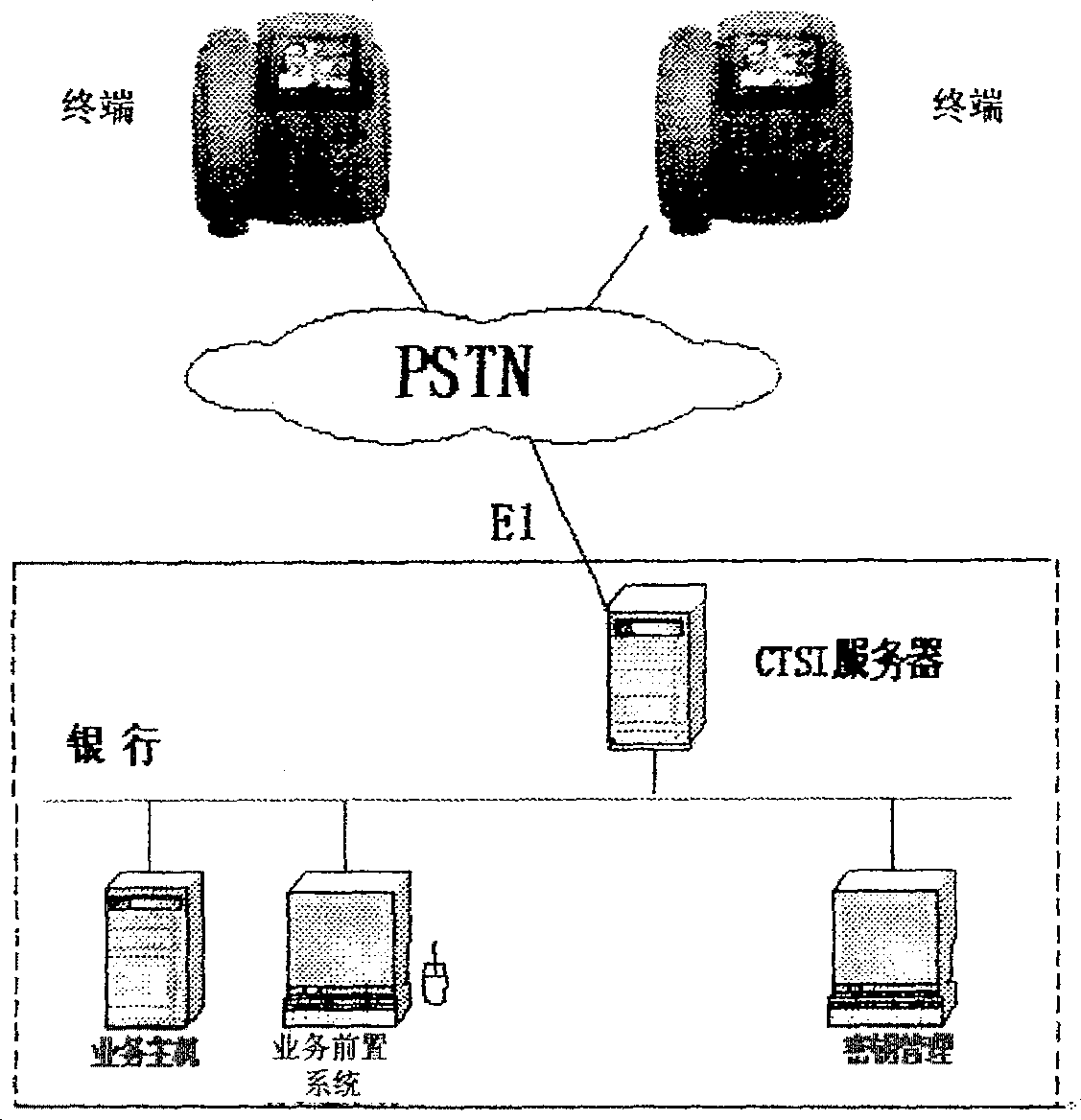
Bank terminal using fixed telephone network communication and its construction method
InactiveCN1858813APrevent theftReduce the possibility of being stolenComplete banking machinesTelephonic communicationEngineeringData memory
This invention relates to a bank terminal using fixed telephone network communication including a phone shell, an exterior line jack on the shell, a display screen, a swiping cards groove for keyboard and magcard / magstrip, a headphone connected with the shell, a CB in the shell with a microprocessor, a keyboard process circuit, a magcard / magstrip process circuit and a data storage on it, an IC card-plug slot on the shell and an IC card process circuit in the circuit on the CB, a keyboard inputting cipher information on the headphone, a SAM card base in the shell plugged with a SAM card security module for ciphering the account information input by swiping the card and cipher information input from keyboard to realize bank affairs including the payment function.
Owner:深圳市证通金信科技有限公司
System and method for generating a dynamic card value
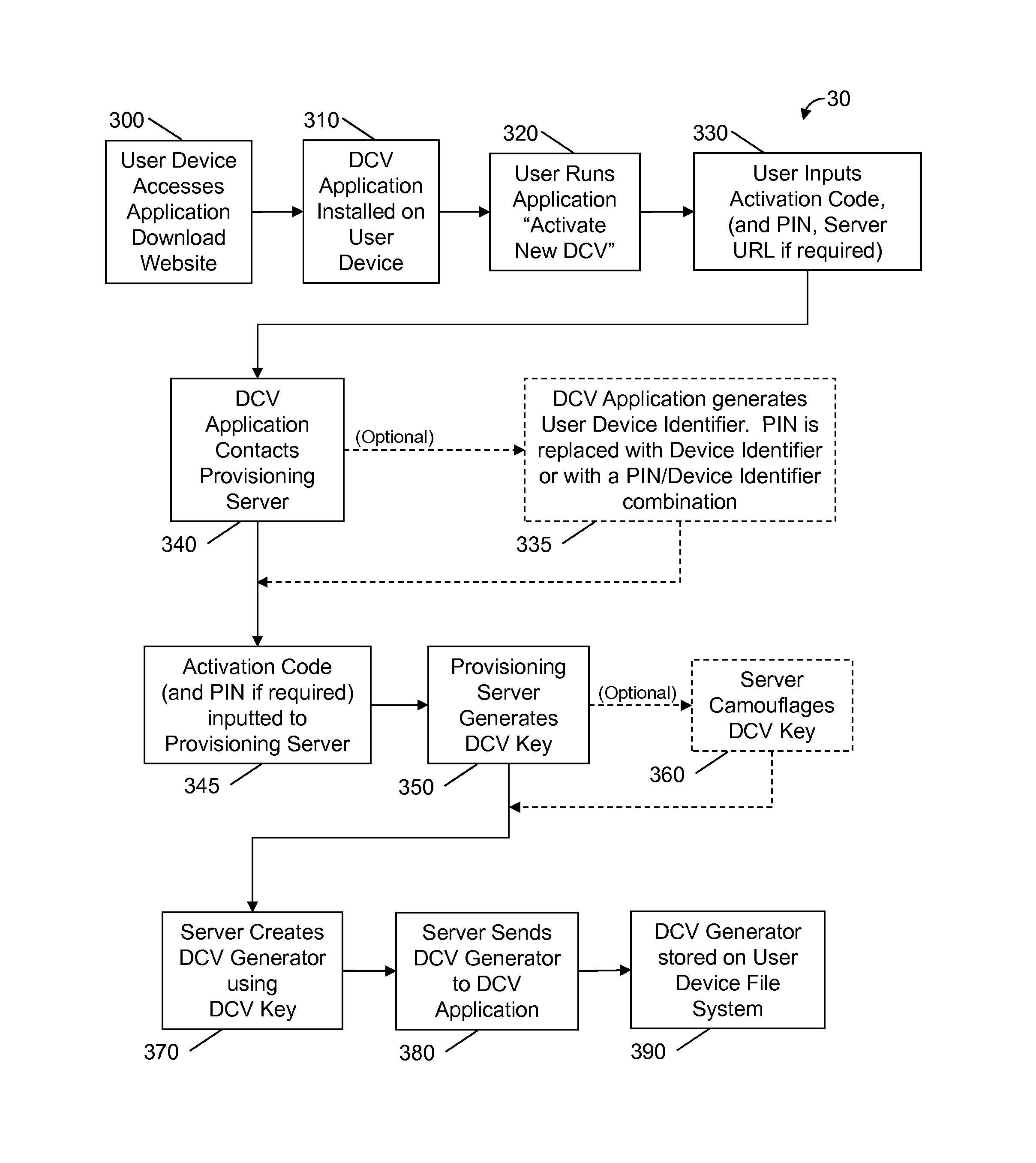
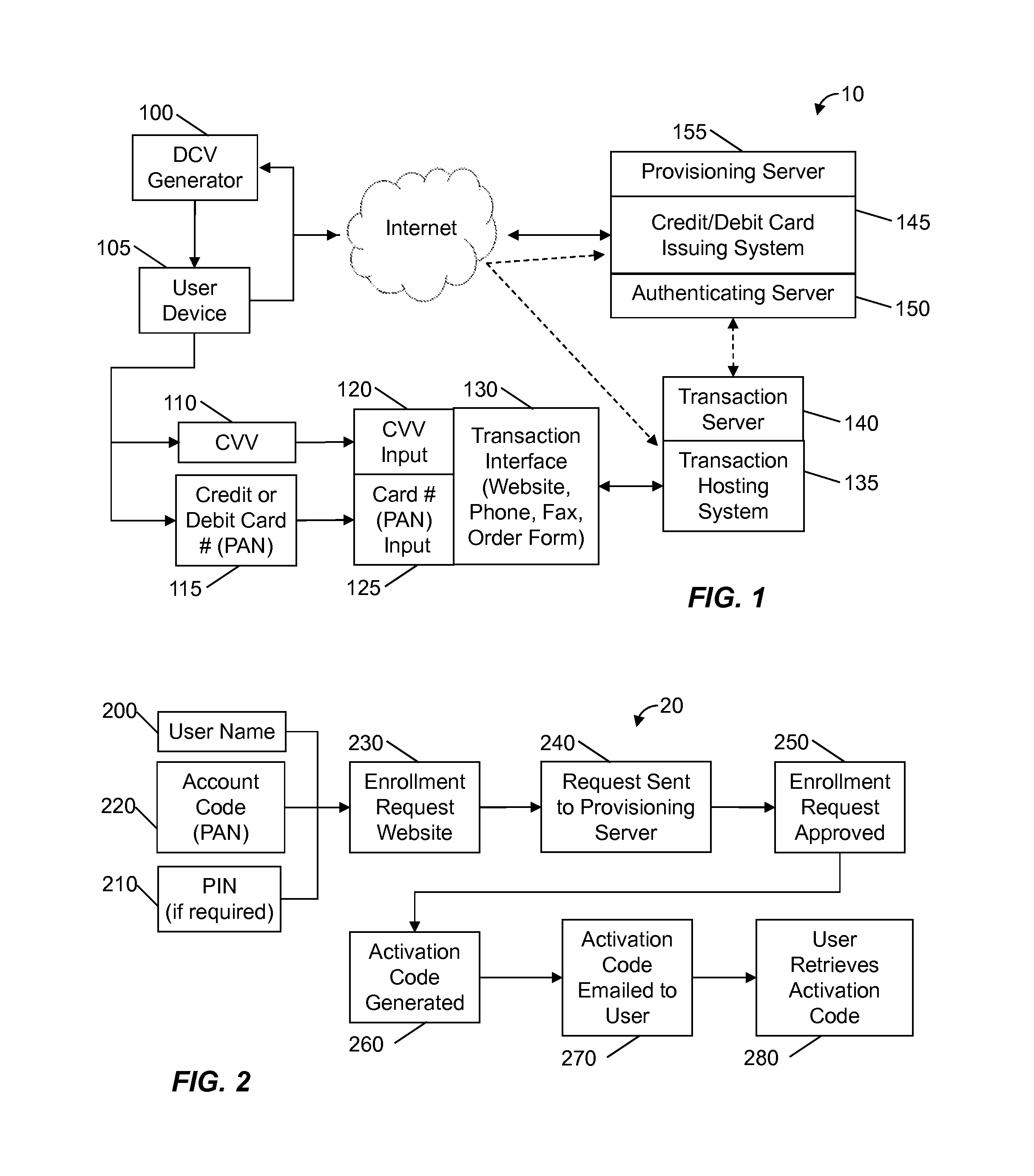
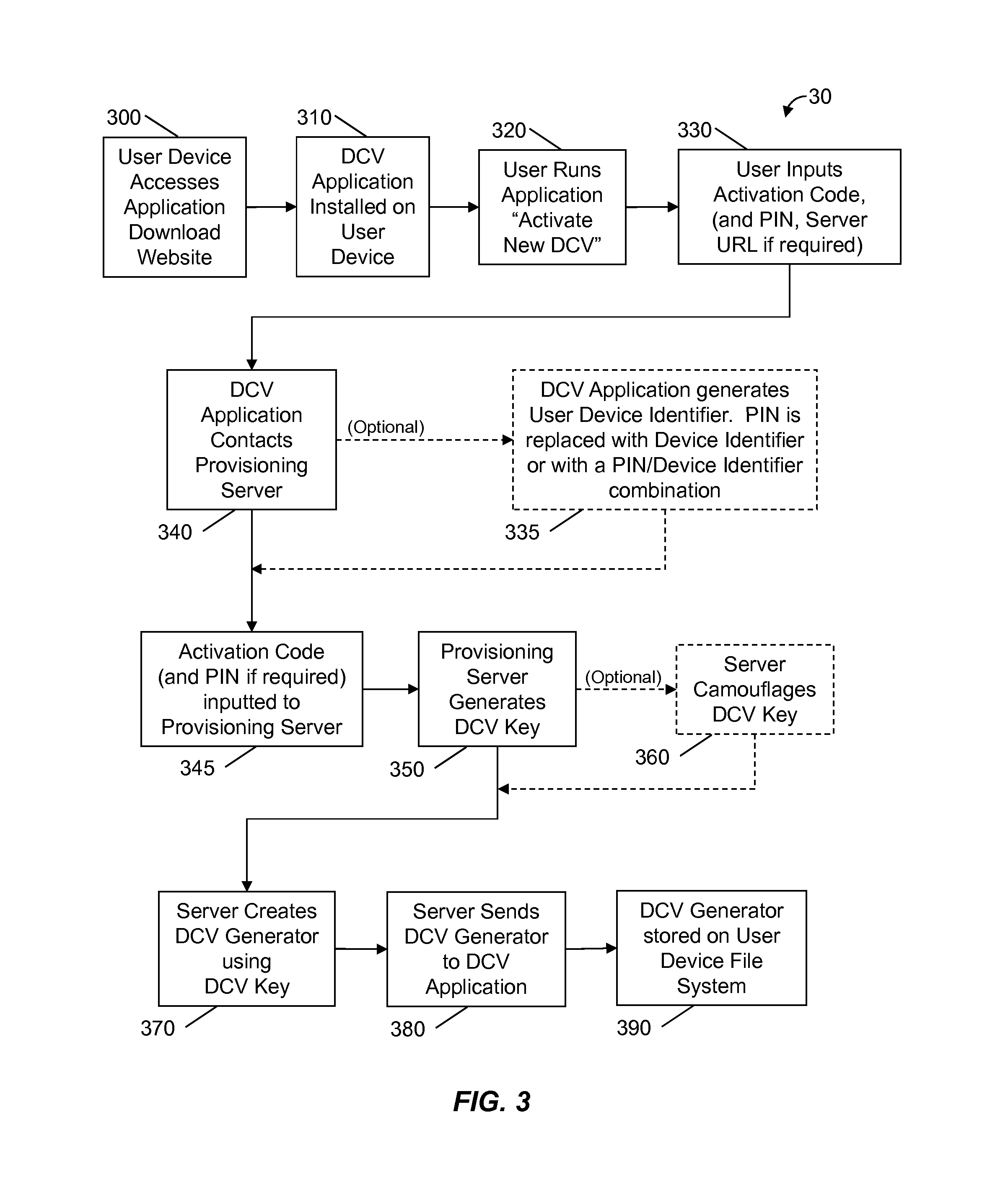
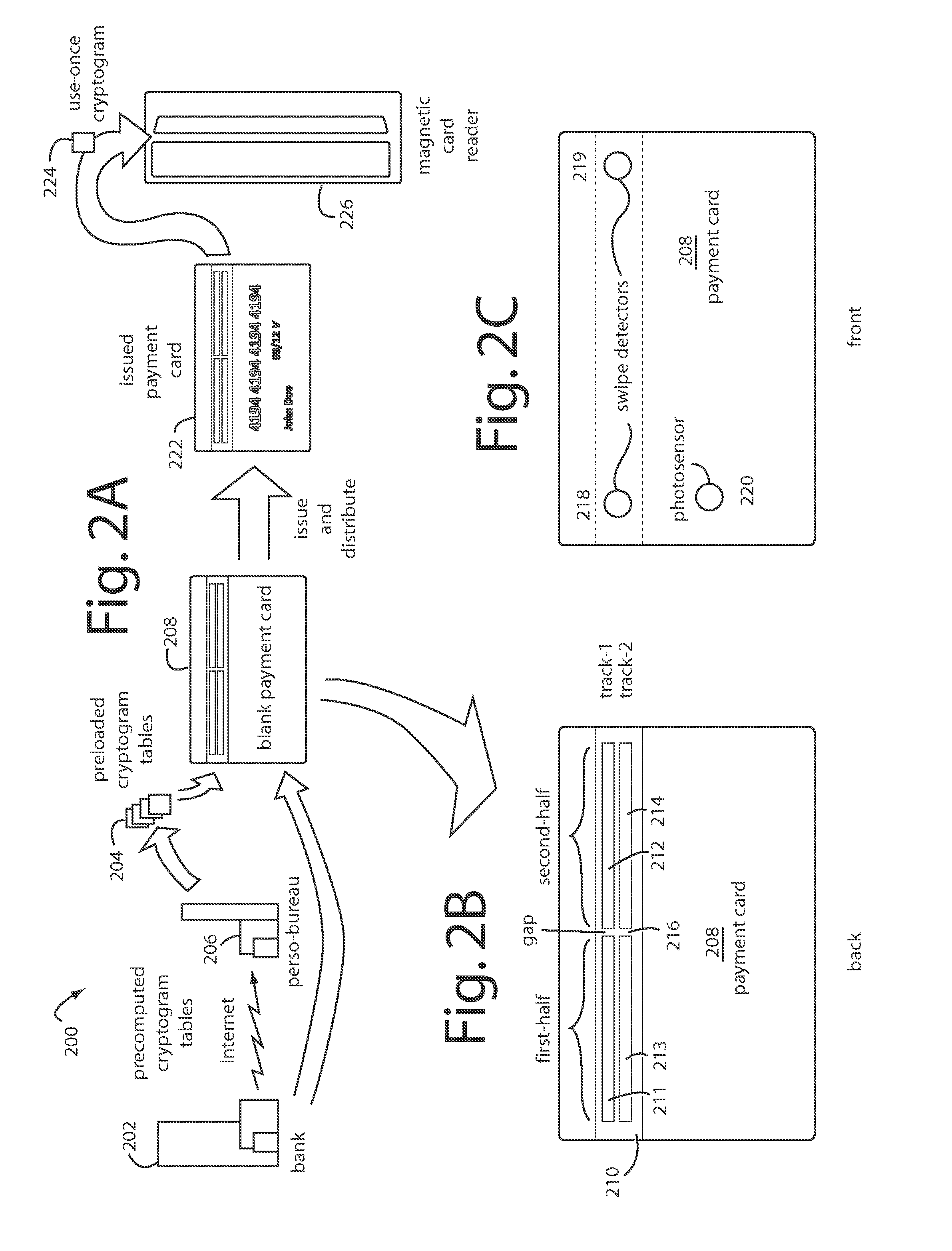
A method and system is provided for generating a dynamic card value (DCV) from a mobile user device for use in a transaction between a user cardholder and a transaction provider. The DCV may be configured for use as a card verification value (CVV), also known as a card security code (CSC), a primary account number (PAN), or a portion of a PAN. The DCV may be generated using a DCV generator which may include an algorithm and a DCV generation key. The DCV generation key may be camouflaged. Obtaining a DCV from the user device may require inputting a PIN, a device identifier, a challenge or transaction information. The DCV may be used for any transaction requiring the input of a user identification number and a verification value, including, credit card transactions, debit card transactions, online or telephonic transactions.
Owner:CA TECH INC
Goods false proof method and system based on Internet safety lock
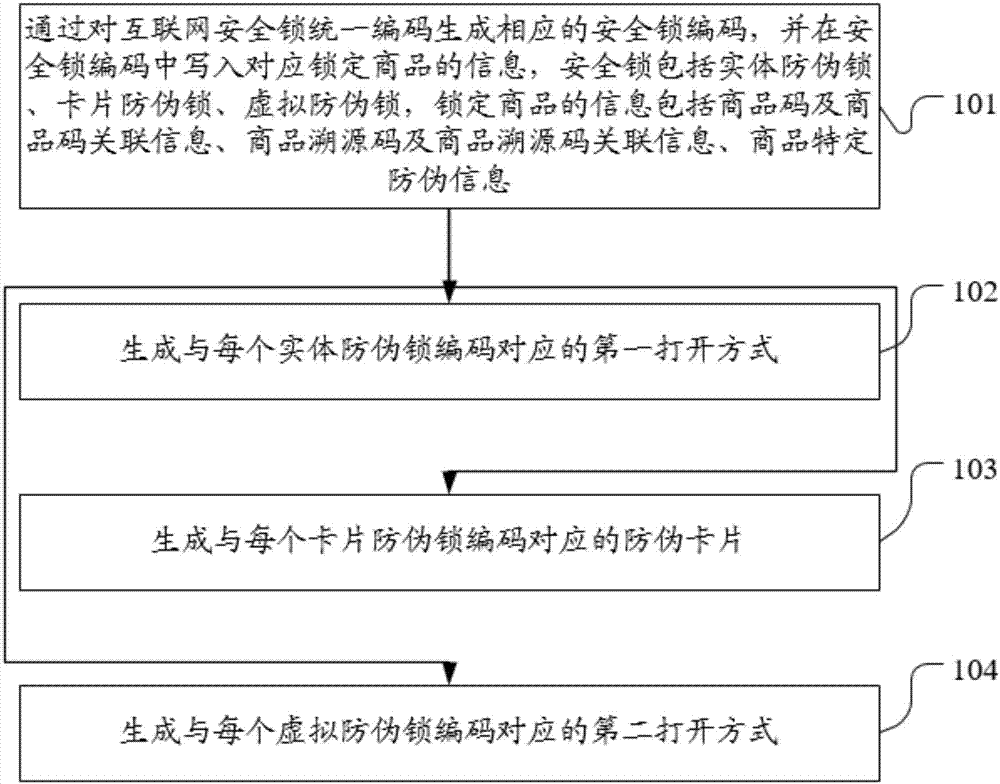
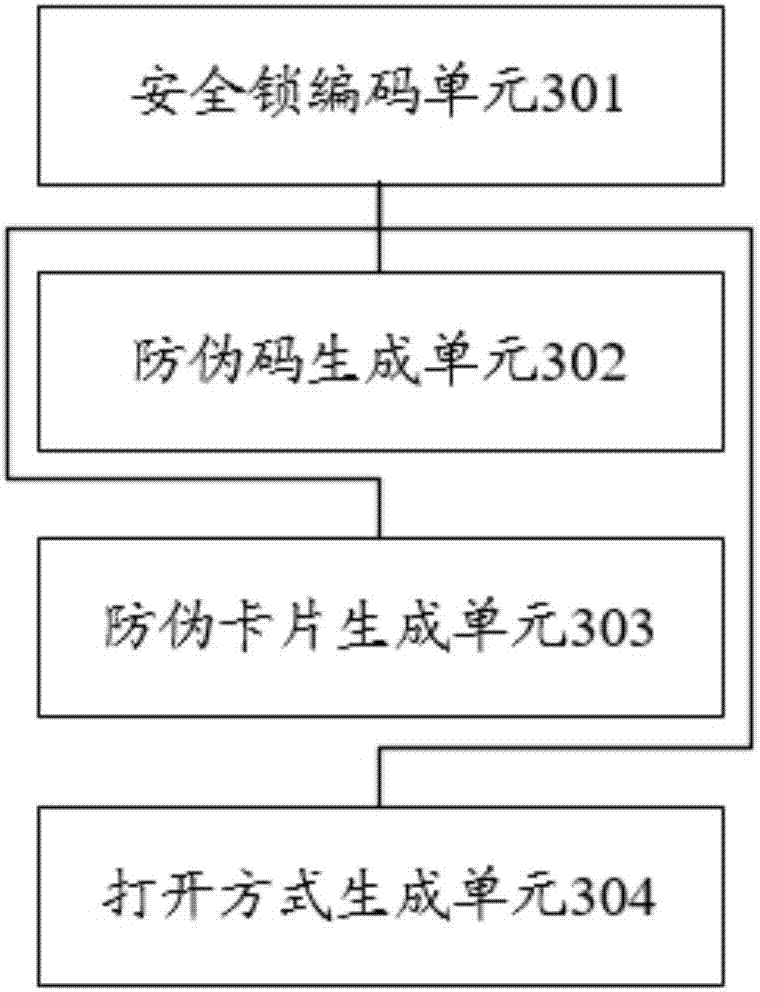
InactiveCN106940859AAchieve anti-counterfeiting goalsAnti-lostDigital data protectionCommerceProduct traceabilityCard security code
The embodiment of the present invention discloses a commodity anti-counterfeiting method and system based on an Internet security lock. By uniformly encoding the Internet security lock and writing the locked commodity information into the security lock code, the user can verify the identity of the commodity through the security lock. Information to identify the authenticity of the goods, so as to achieve anti-counterfeiting. The method in the embodiment of the present invention includes: generating a corresponding security lock code by uniformly encoding the Internet security lock, and writing information corresponding to locked commodities in the security lock code, the security lock includes a physical anti-counterfeiting lock, a card anti-counterfeiting lock, Virtual anti-counterfeiting lock, the information of the locked commodity includes commodity code and commodity code associated information, commodity traceability code and commodity traceable code associated information, commodity specific anti-counterfeiting information; generating the first opening method corresponding to each entity anti-counterfeiting lock code ; Generate an anti-counterfeit card corresponding to each of the card anti-counterfeit lock codes; generate a second opening method corresponding to each of the virtual anti-counterfeit lock codes.
Owner:李建魁
Credit card payment request processing method and device
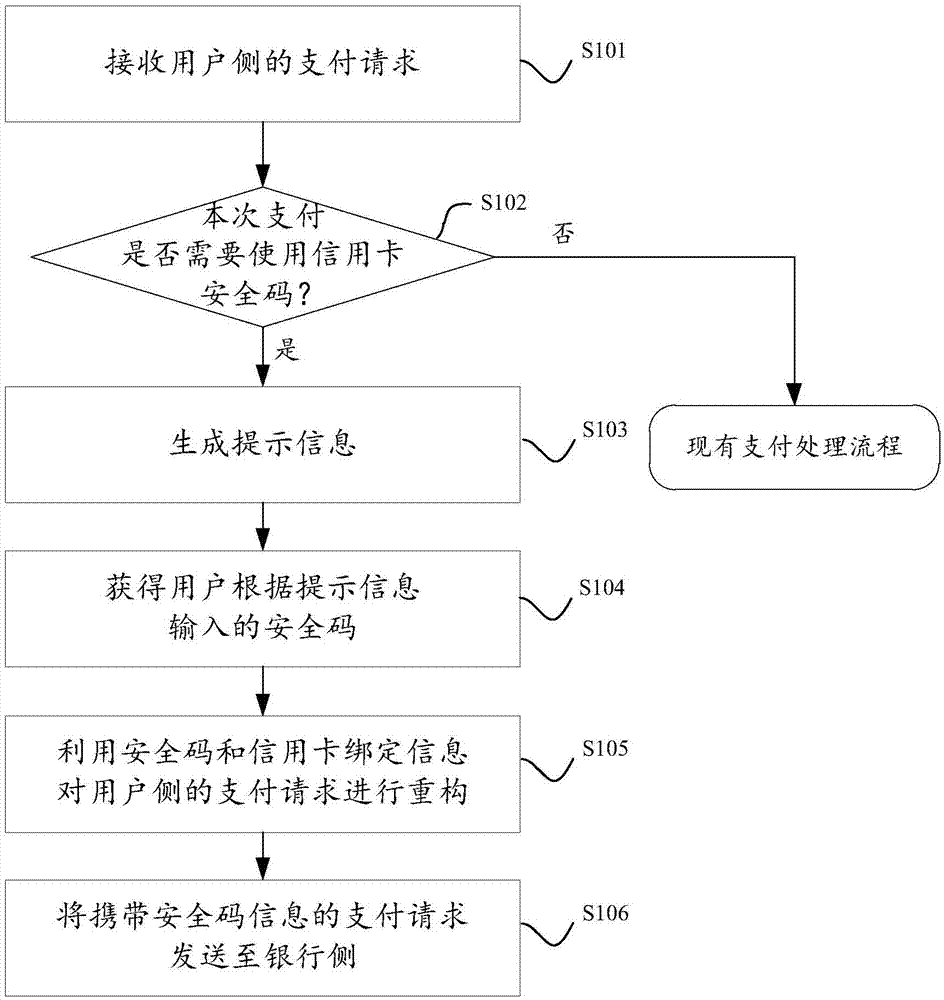
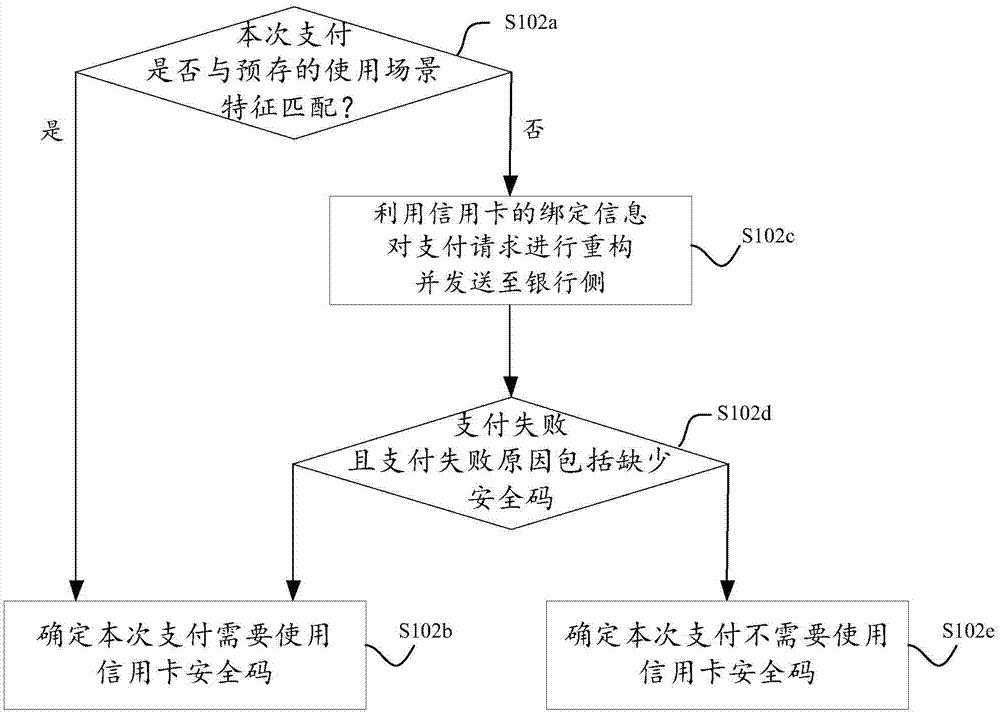
ActiveCN106934606AAvoid manual entryImprove operational convenienceProtocol authorisationThird partyFailure rate
The invention discloses a credit card payment request processing method and device. The credit card payment request processing method comprises the steps of receiving a payment request of a user side; judging whether a credit card security code is required to be used or not in the current time of payment under the condition that the payment request is a payment request based on a bound credit card; if so, generating a prompt message so as to prompt a user to input the security code of the credit card; acquiring the security code inputted by the user according to the prompt message; reconstructing the payment request of the user side by using the acquired security code and binding information of the credit card so as to acquire a payment request carrying security code information; and sending the payment request carrying the security code information to a bank side. According to the scheme, the user operation convenience and the input success rate can be improved, the payment failure rate of a third-party payment platform is reduced, and unnecessary consumption of system resources is reduced.
Owner:ADVANCED NEW TECH CO LTD
Method for encrypting real-time data into product security codes
InactiveCN102332080ARealize dynamic encryptionLow costUser identity/authority verificationVerifying markings correctnessComputer hardwareReal-time data
The invention discloses a method for encrypting real-time data into product security codes, which comprises the following steps that: firstly, product basic codes A are set according to product information, then, the product basic codes A are encrypted through an encryption formula key1, and basic security codes B are generated; and then, the real-time data D is encrypted through a randomly selected encryption algorithm key2, encryption data minD is generated, feature codes E are generated through the randomly selected encryption algorithm key2, finally, the basic security codes B, the feature codes E and the midD are ranged again according to the desequencing rule F corresponding to the feature codes E, and final codes C are obtained. The encryption and decryption processes of the method completely get out from the management of a database, the database support is not needed, the management of data with unlimited number is supported, the cost is reduced, the inquire speed optimization is realized, and the functions of anti-counterfeiting, reviewing, management and the like of products are realized.
Owner:贵州卓霖科技有限公司
Automatic forming method for goods code
InactiveCN1945620ARealize managementRealize the transactionCommerceSpecial data processing applicationsArabic numeralsE-commerce
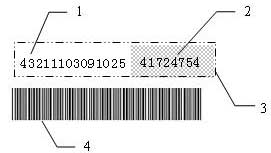
This invention discloses an automatic generation method of commodity code. The commodity code contains external code which is composed of prefix and suffix. The prefix is automatically generated after inputting the basic commodities information into computers, and the suffix is the serial number. The commodity code also includes the inner code ISN, commercial code and security code. The ISN is also formed by prefix and suffix. The prefix is the computer time when the commodity code is generated, and the suffix is the serial number. The commercial code is automatically generated by the user's code name and the foreign code. The security code is a number of automatic allocation Arabic numerals while the computer produces the ISN. The use of this invention to carry on the code for commodity, is standard, universal, practical, and can achieve the region commodity information management and transaction, independently carry on the different region maintenance of the commodity code, independently carry on the commodity security, and interpret the commodity information. It is applicable to the commodity information management system, the e-commerce system, the commodity information retrieval system, and also can be used in protecting the security.
Owner:庄晓锋
Portable security printed matter authentication device
InactiveUS8038063B2Easy to useAccurate authenticationPaper-money testing devicesCharacter and pattern recognitionMagnifying glassUltraviolet
Provided is a portable security printed matter authentication device for authenticating security codes printed on security printed matter such as currency, vouchers, passports, and identification cards. The portable security printed matter authentication device includes: a housing including an observation hole at a top portion of the housing; a magnifying lens disposed to be close to the observation hole inside the housing; an optical filter disposed below the magnifying lens; and a plurality of LED (light-emitting diode) lamps which are disposed below the optical filter and illuminate light toward the security printed matter, wherein the LED lamps are a combination of two or more types of ultraviolet (UV) LED lamps, color LED lamps, and infrared (IR) lamps.
Owner:M VISION
Electronic instrument having resettable security code and method for resetting security code
InactiveUS6323752B1Electric signal transmission systemsMultiple keys/algorithms usageComputer hardwareUser input
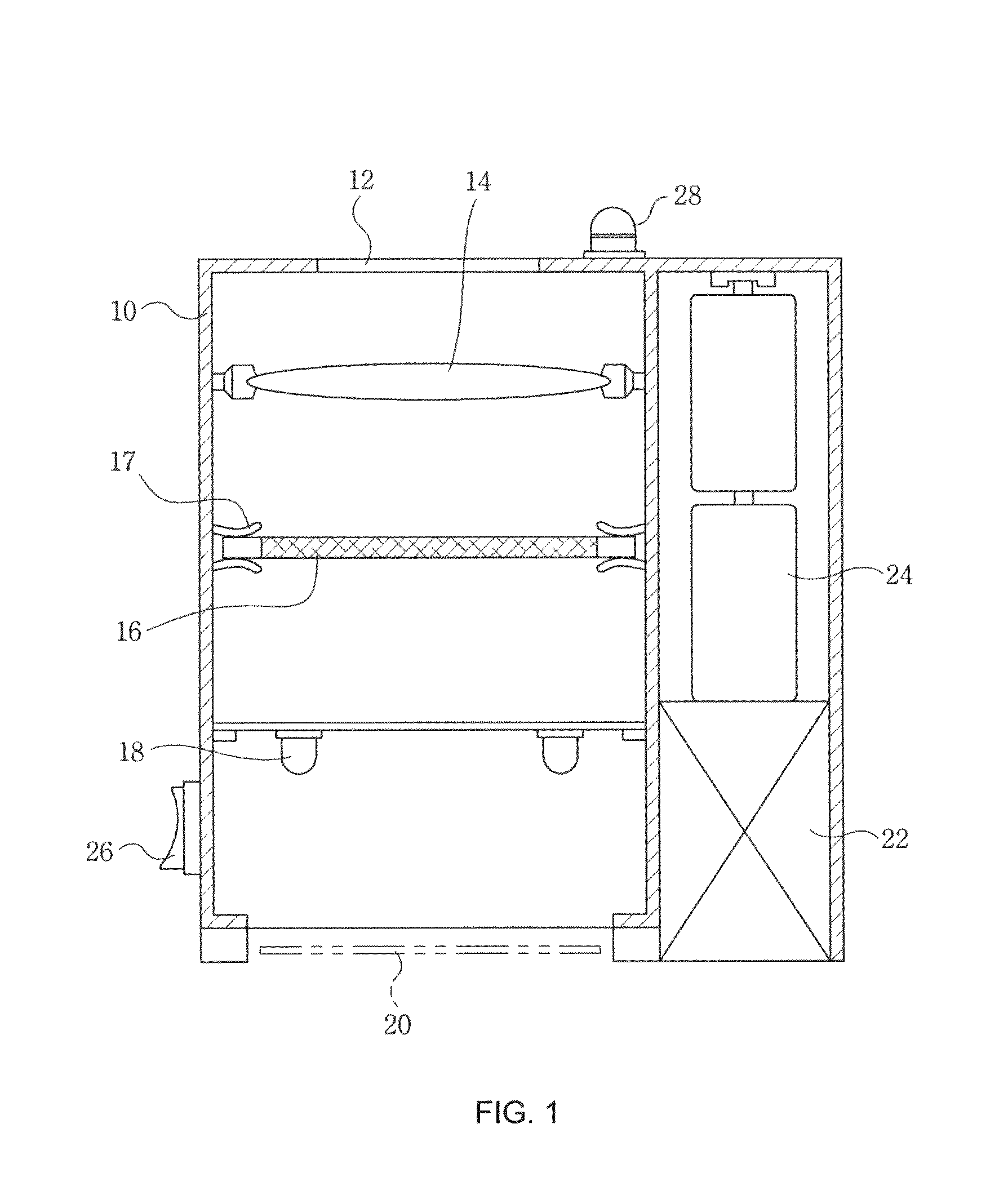
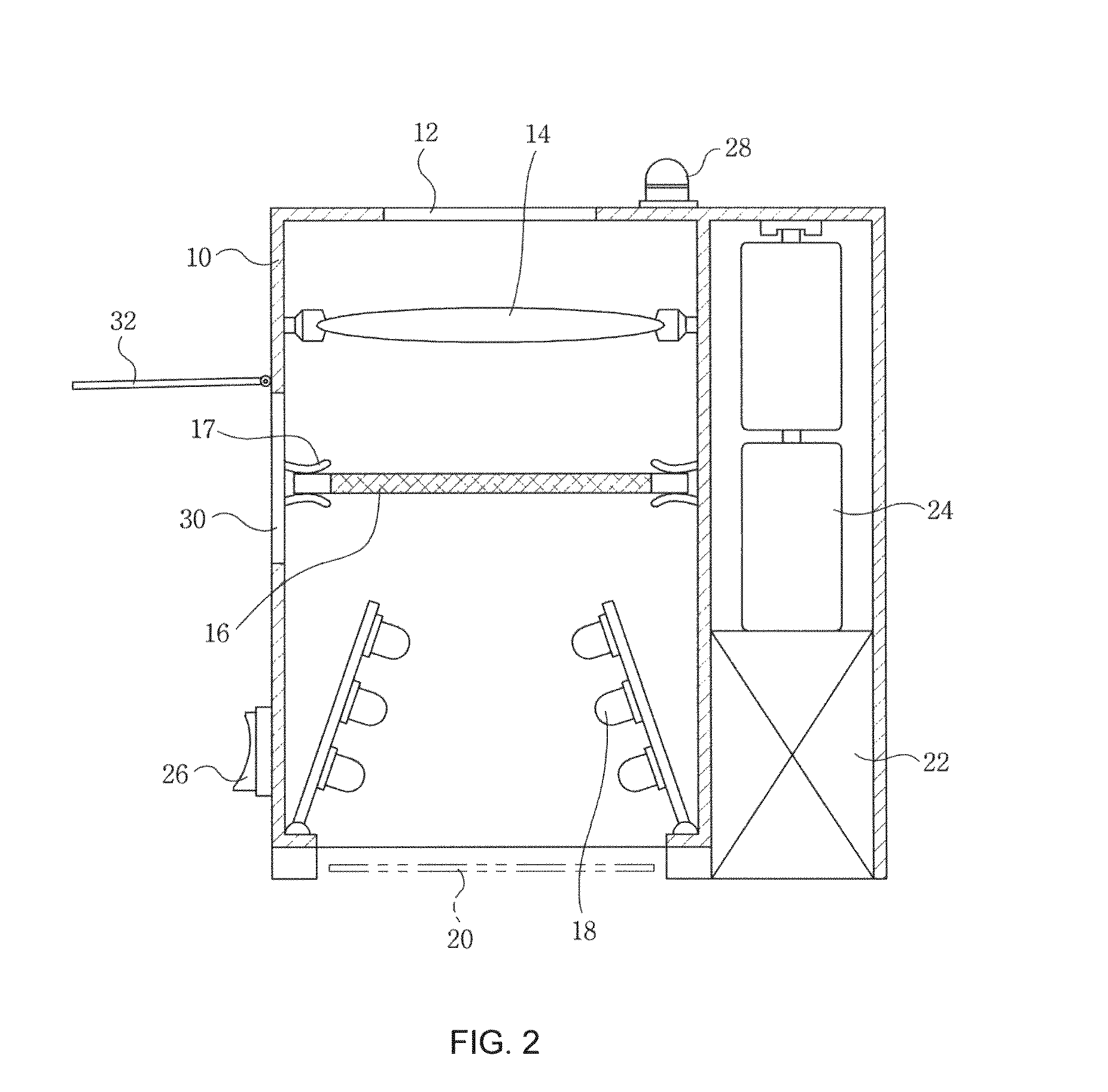
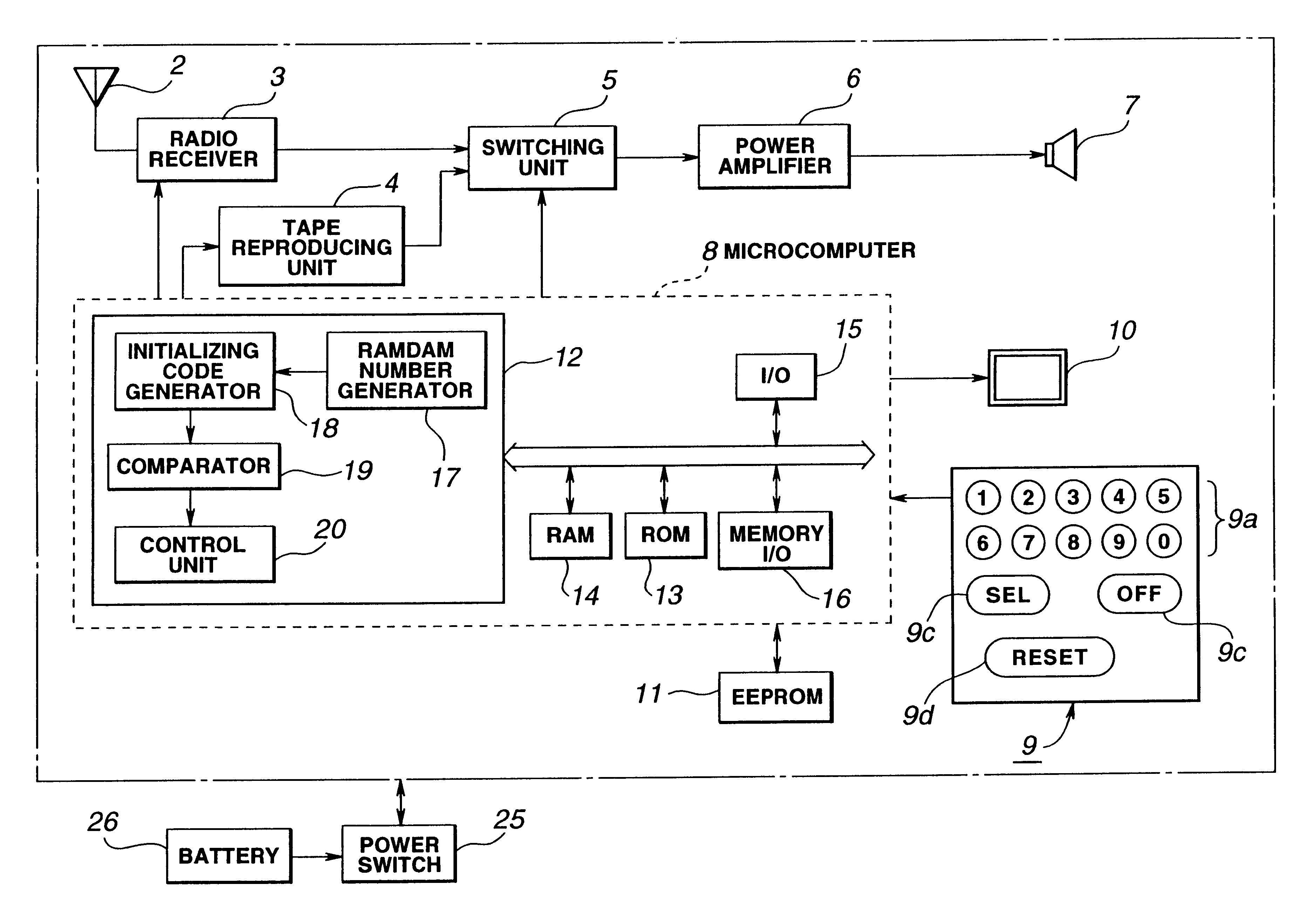
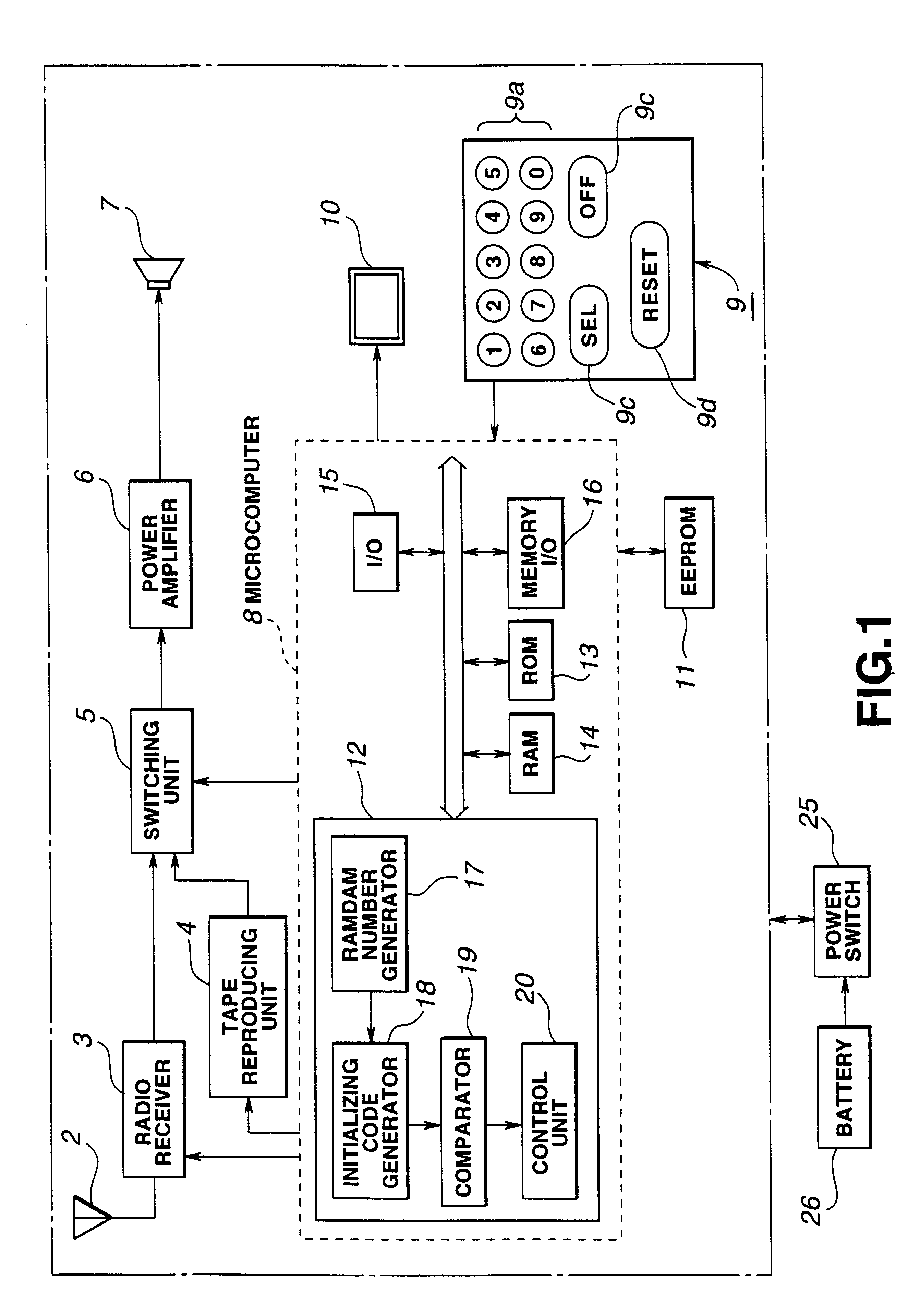
An electronic instrument having a resettable security code as a way of preventing the burglary of the electronic instrument mounted to a movable device such as a car. When the electronic instrument is mounted to the movable device or a battery is exchanged, the entry of the security code is required by the user. If the user does not know or remember the security code, a random number is automatically generated inside of the electronic instrument and converted into an initializing code according to the predetermined rules. The user reports the generated random number to a service company or the manufacturer. The service company or the manufacturer checks if the user is registered. When the user is certified, the service company or the manufacturer gives the initializing code corresponding to the random number to the user. Then, the user enters the given initializing code for resetting the security code.
Owner:SONY CORP
Method for generating and displaying a security code for a payment card, payment card
ActiveUS20160148085A1Improve securitySimple securityAcutation objectsCredit schemesComputer hardwareDisplay device
A payment card comprises a display device arranged on a face of the payment card, the display device comprising a field for displaying a security code for card verification operations carried out by a card verification server. The method comprises the operations of:displaying, in the field of the display device, a first value of the security code during a first time period,displaying, in the field of the display device, a second value of the security code during a second time period that follows the first time period, the first and second time periods being of different durations.
Owner:CB INVESTISSEMENTS
ATM replacement using two mobile devices
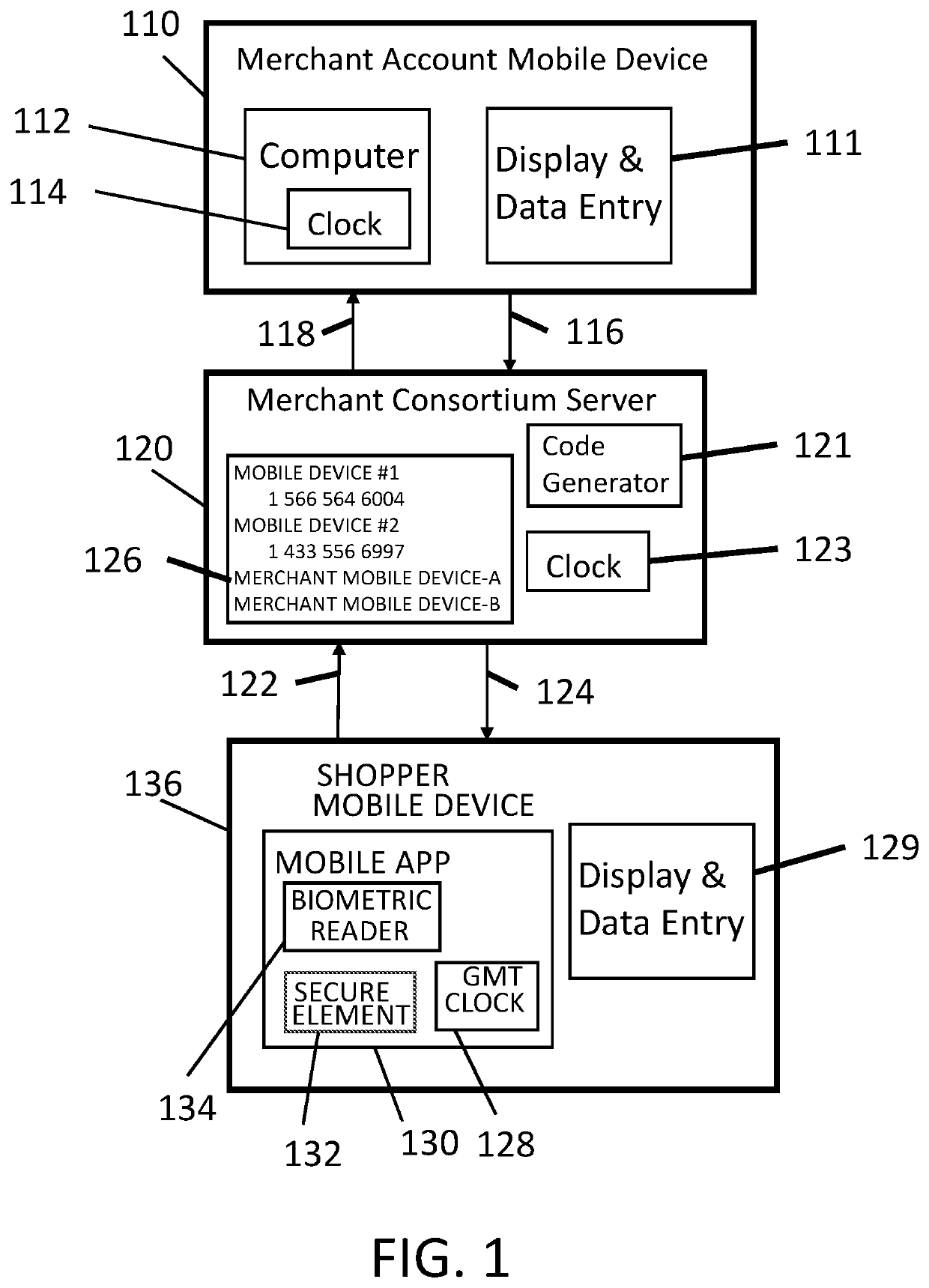
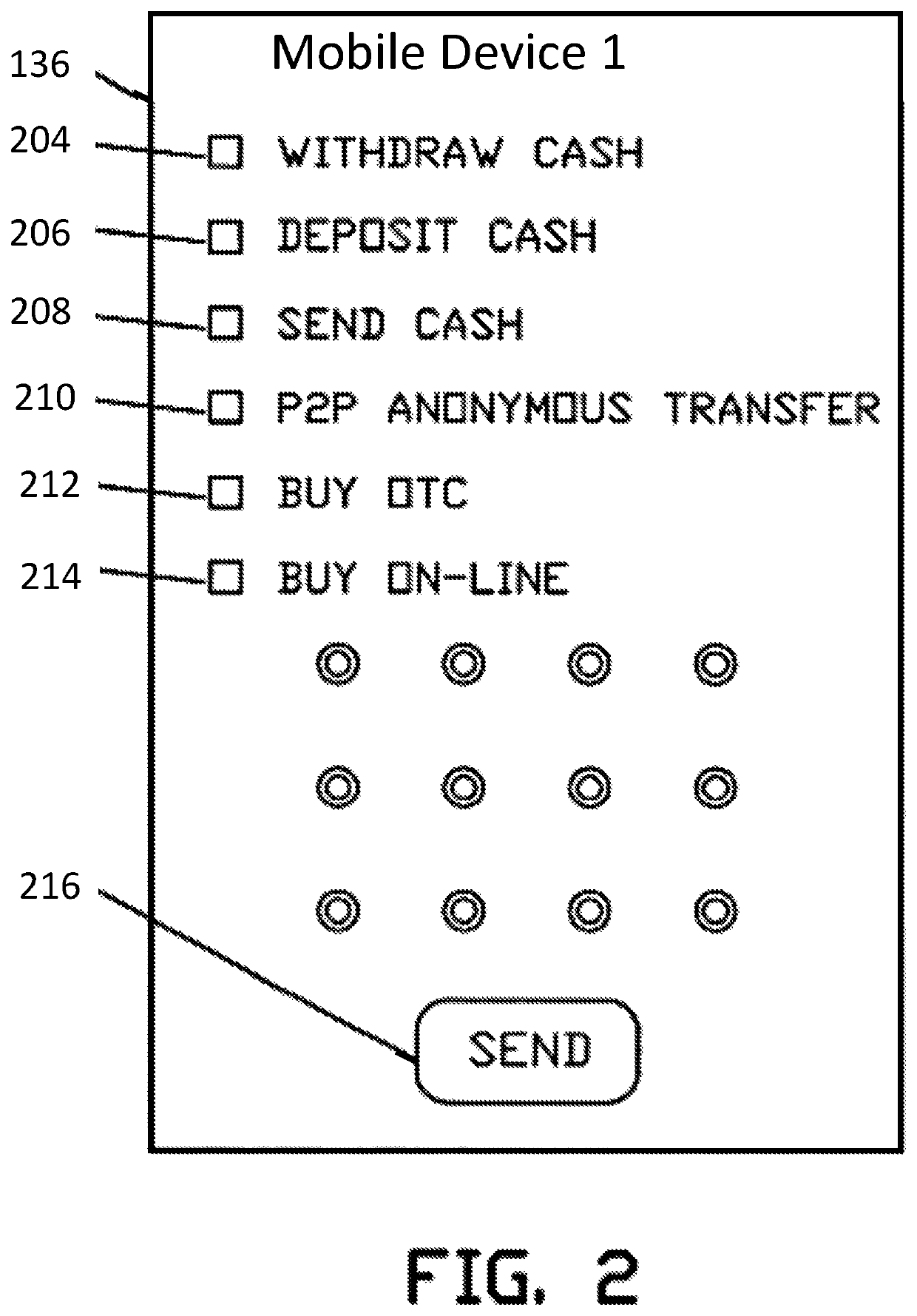
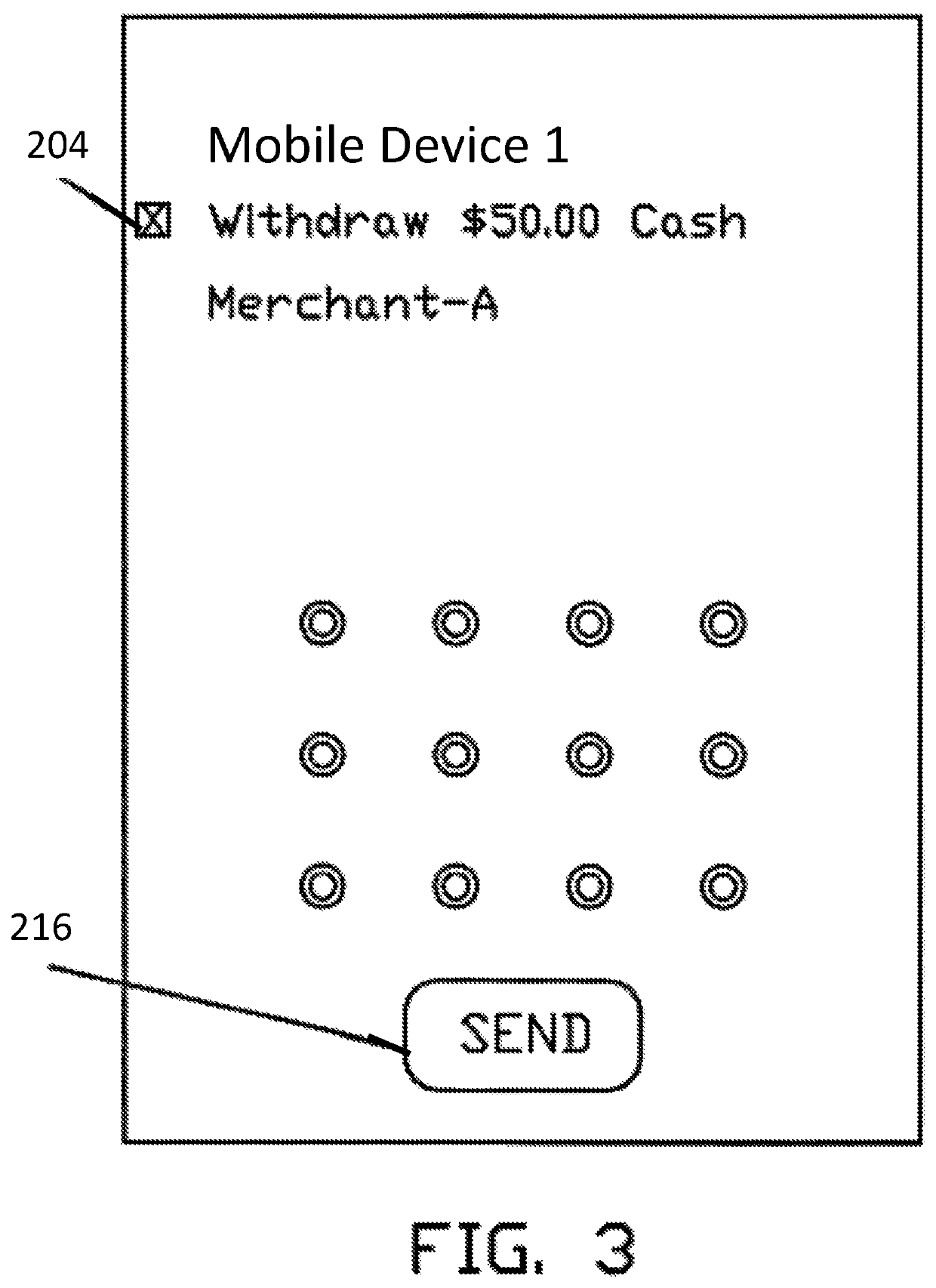
ActiveUS10510066B2Big advantageComplete banking machinesPayment protocolsGeolocationCard security code
A system, method, and program product for exchanging physical, virtual or fiat currency between two individuals at the same geographic location using account information stored on a server database. The payer activates payer mobile device using biometric identification, then inputs the amount to transfer along with a payee security code, then payer presses “send.” The payee activates payee mobile device using a biometric identification, then payee inputs the amount to receive along with a payer security code then payee presses “send”. Both the payer and the payee mobile devices simultaneously receive from the server an alphanumeric transaction code along with the amount. Transaction code and amount are displayed on the respective mobile screens. When payee verifies that both mobile devices display the same transaction code and dollar amount, then the payee presses “I Agree” key on payee mobile device. Then the funds are exchanged at the server database. Payer and payee may also exchange corresponding cash.
Owner:LOVETT ROBERT R
Optical contact loaded magnetic card
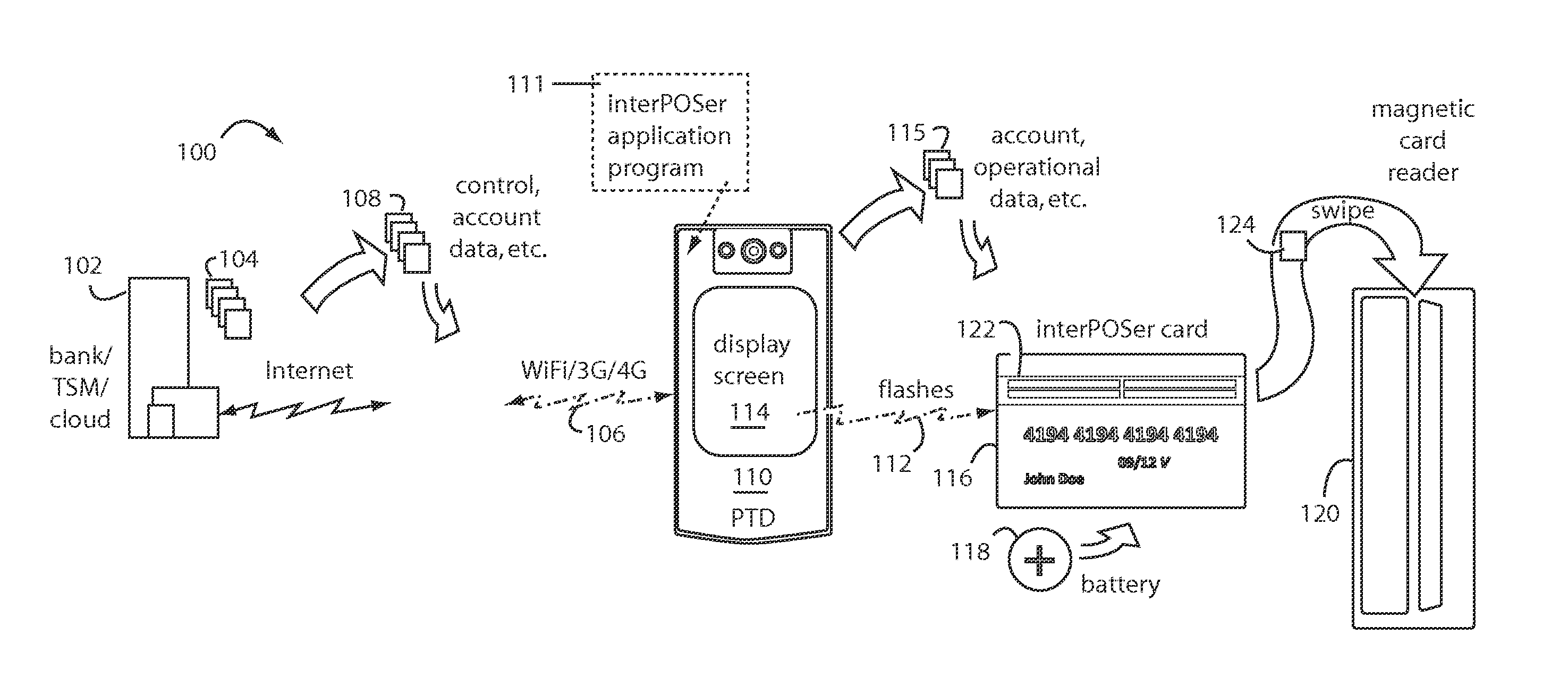
ActiveUS9010646B2Improve securityCommunication securityBuying/selling/leasing transactionsRecord carriers used with machinesPayment orderFinancial transaction
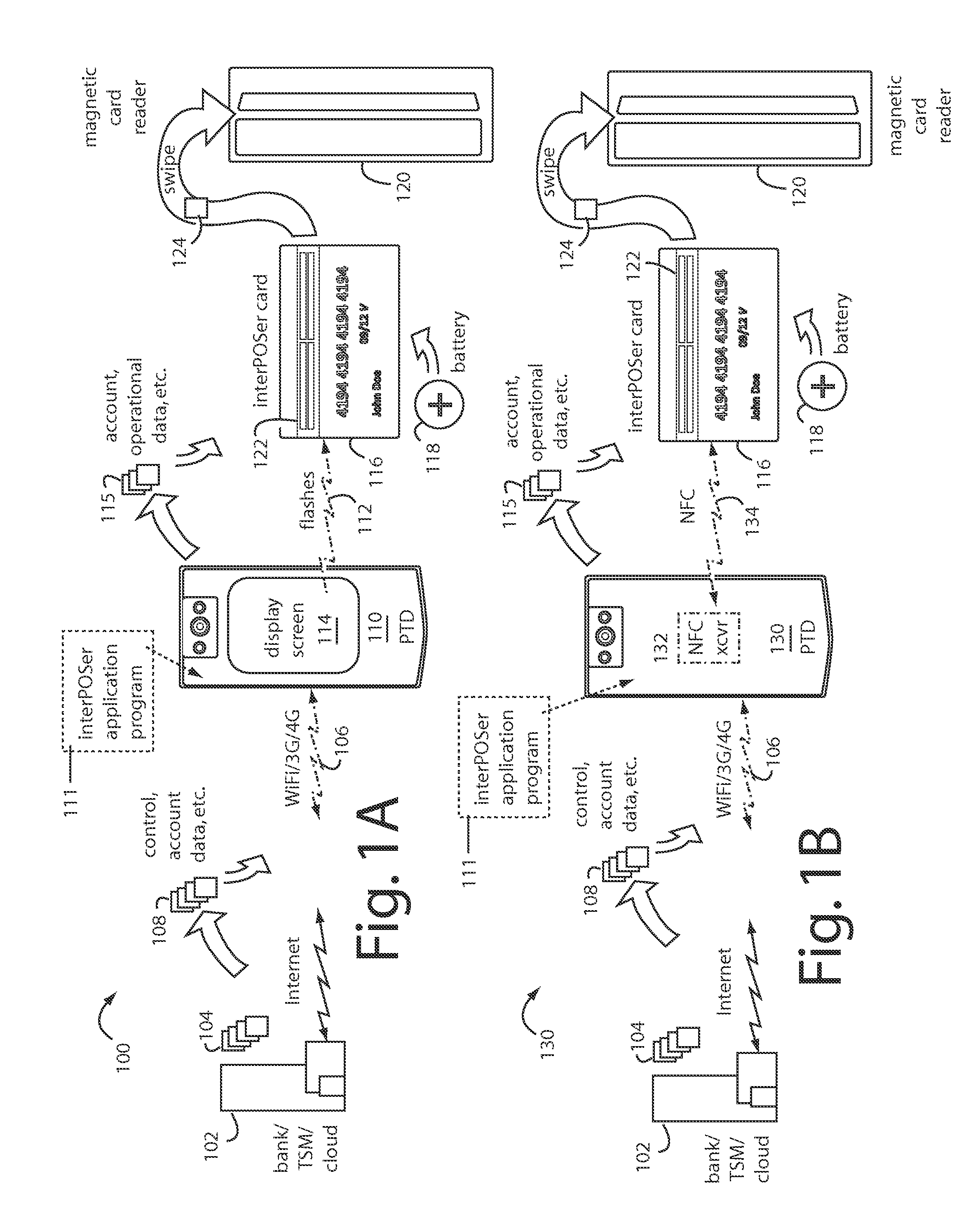
A magnetic interface card appears to be a payment card conventionally provided with an electromagnetic stripe and magnetic data tracks. A magnetic emissive element is disposed in the magnetic interface card body under the magnetic data tracks that can emit a variety of ISO-7813 track-2 data strings. A photo-sensor is included to receive a series of optically encoded flashes from a personal trusted device (PTD) smartphone screen that securely communicate one-time-use account information and operational parameters from a financial transaction server. The large installed base of legacy point-of-sale magnetic card readers can continue to be used without any hardware or software modifications, and card security is improved by the change to one-time-use access numbers.
Owner:FITBIT INC
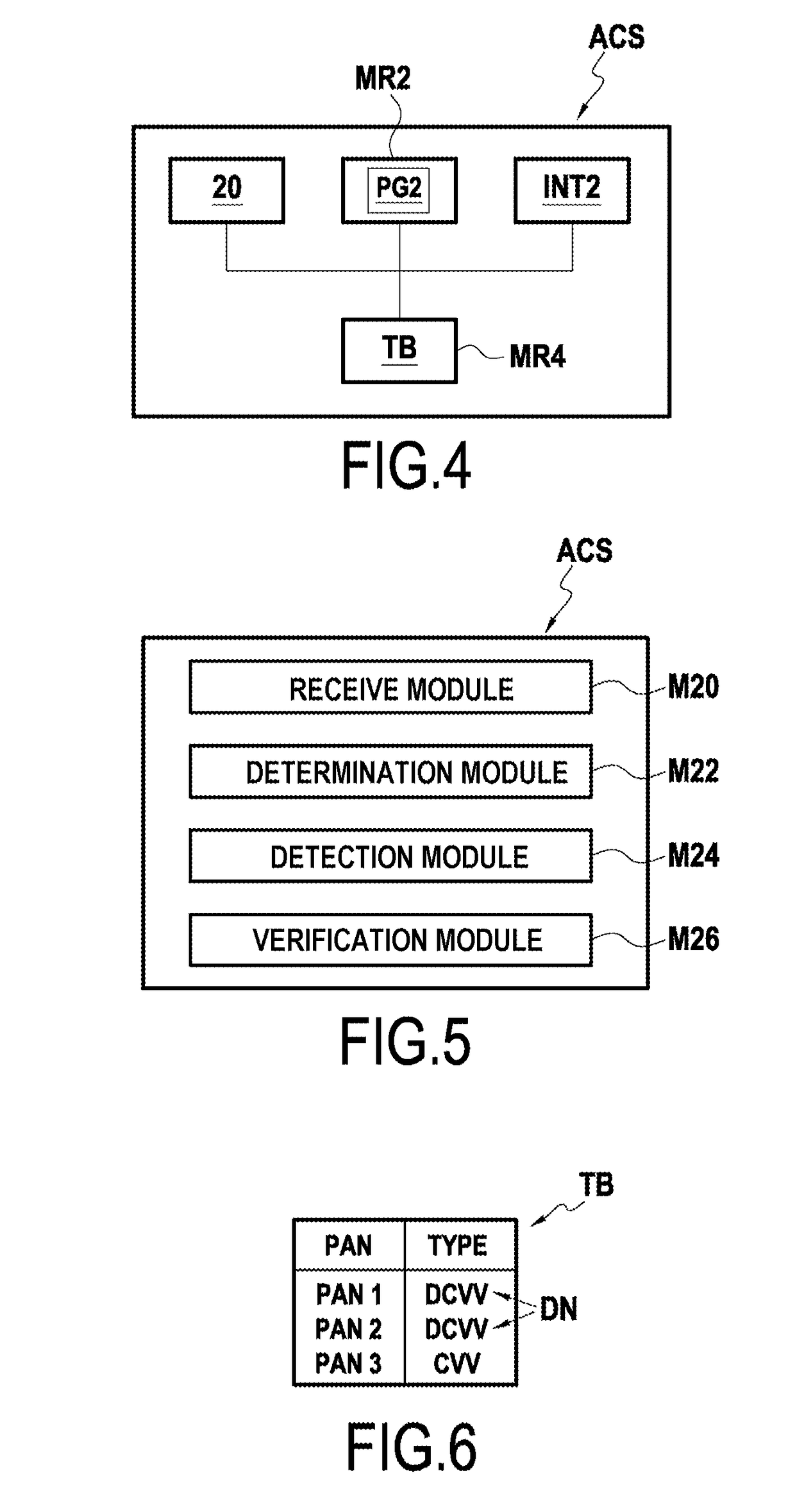
Authentication method
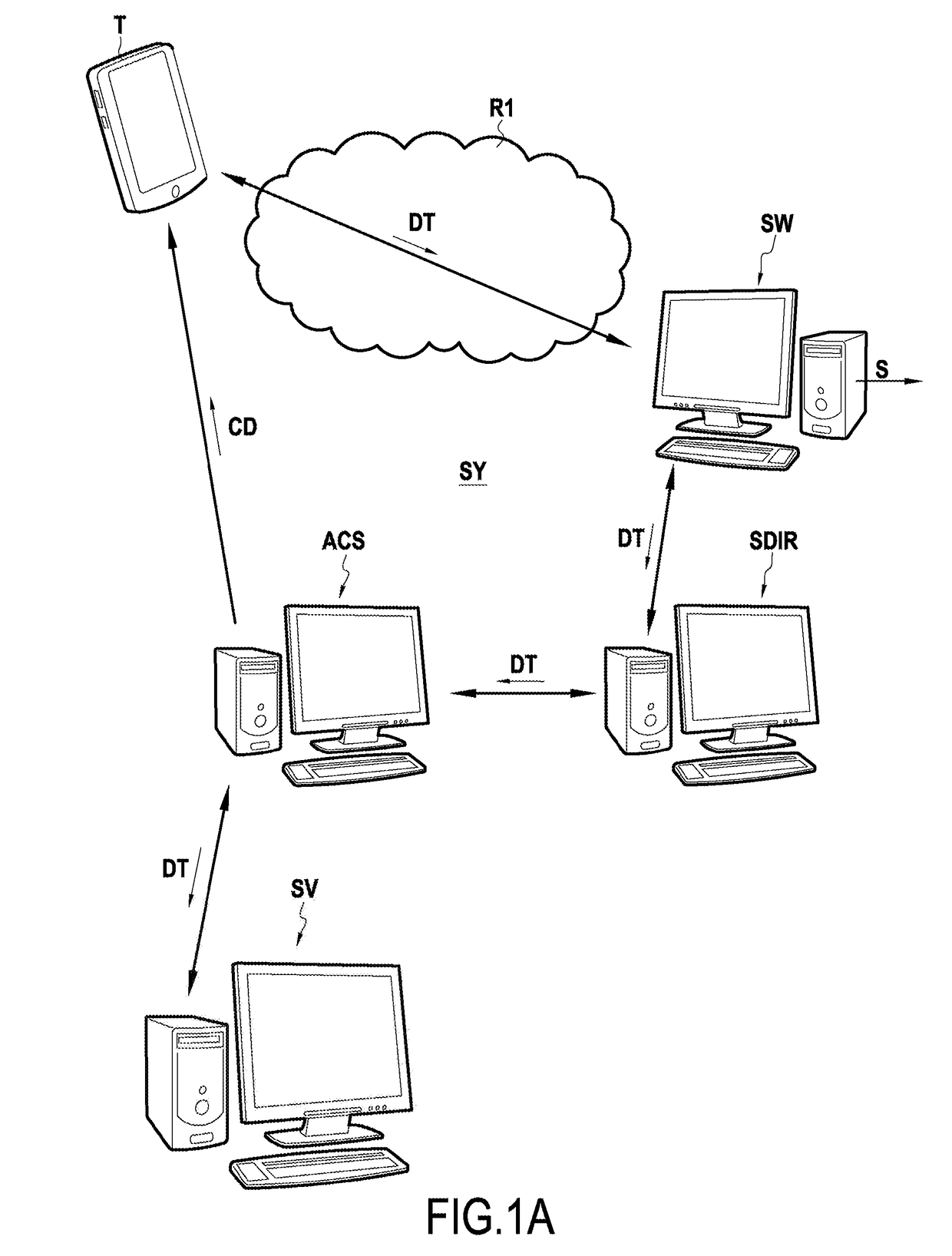
ActiveUS20190005490A1Mechanism is preventedFacilitate authenticating a userTransmissionProtocol authorisationTransaction dataAuthentication server
An authentication method performed by an authentication server (ACS). The method includes receiving from an access server (SW) giving access to a service (S), an authentication request including transaction data (DT) associated with an IC card; determining whether a security code included in the transaction data is of the DCVV type; and if so, detecting that no 3D secure (3DS) authentication is to be performed and co-operating with a verification server (SV) in order to verify the validity of the DCVV security code.
Owner:IDEMIA FRANCE
System and process for automatically analyzing currency objects
ActiveUS10504073B2Paper-money testing devicesCoin/currency accepting devicesVisual ObjectsCard holder
A method, system, and computer program product for analyzing images of visual objects, such as currency and / or payment cards, captured on a mobile device. The analysis allows determining the authenticity and / or total amount of value of the currency and / or payment cards. The system may be used to verify the authenticity of hard currency, to count the total amount of the currency captured in one or more images, and to convert the currency using real time monetary exchange rates. The mobile device may be used to verify the identity of a credit card user by analyzing one or more images of the card holder's face and / or card holder's signature, card holder's name on the card, card number, and / or card security code.
Owner:ATSMON ALON +1
Method for enhancing security of no-card payment transaction and credit card
ActiveCN108053213AReduce the likelihood of fraudProtocol authorisationComputer hardwarePayment transaction
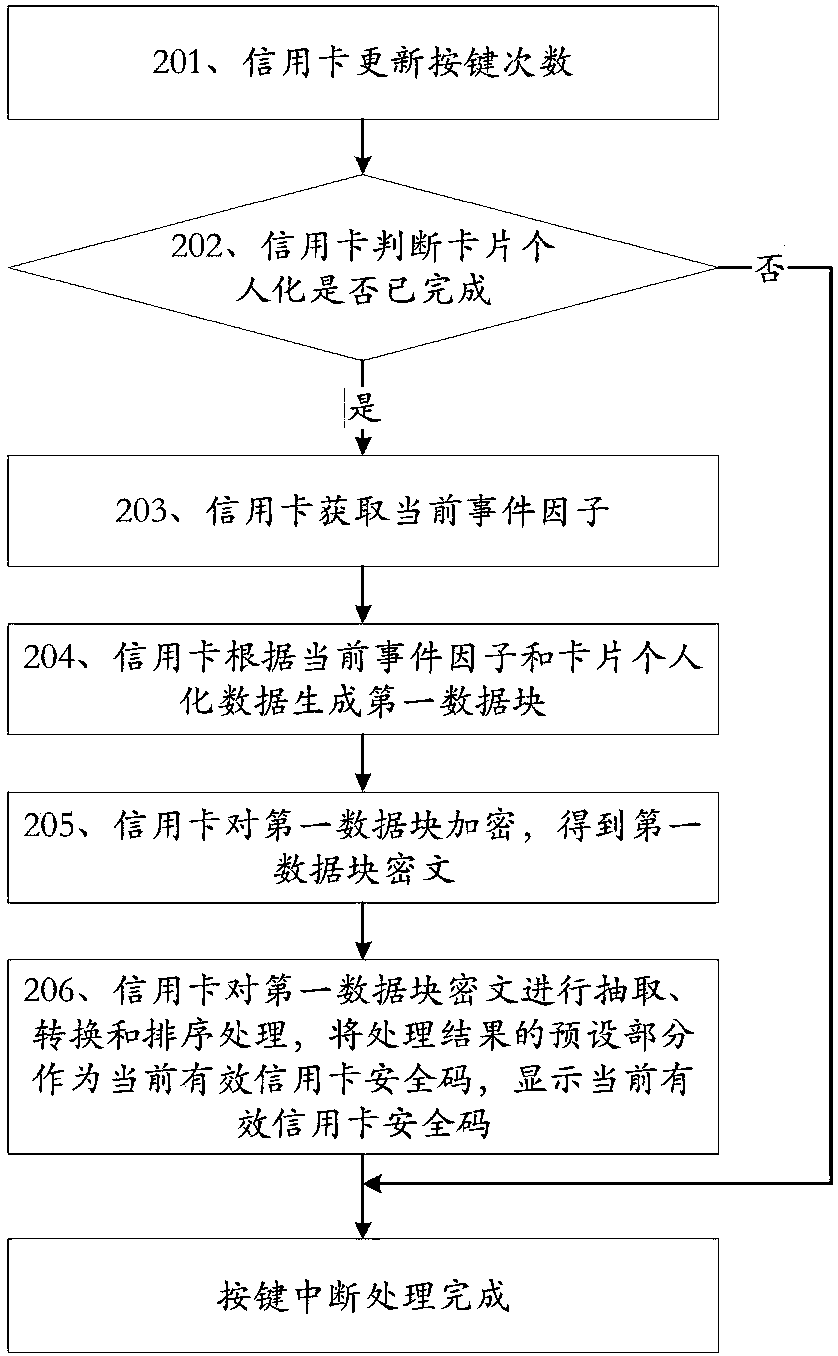
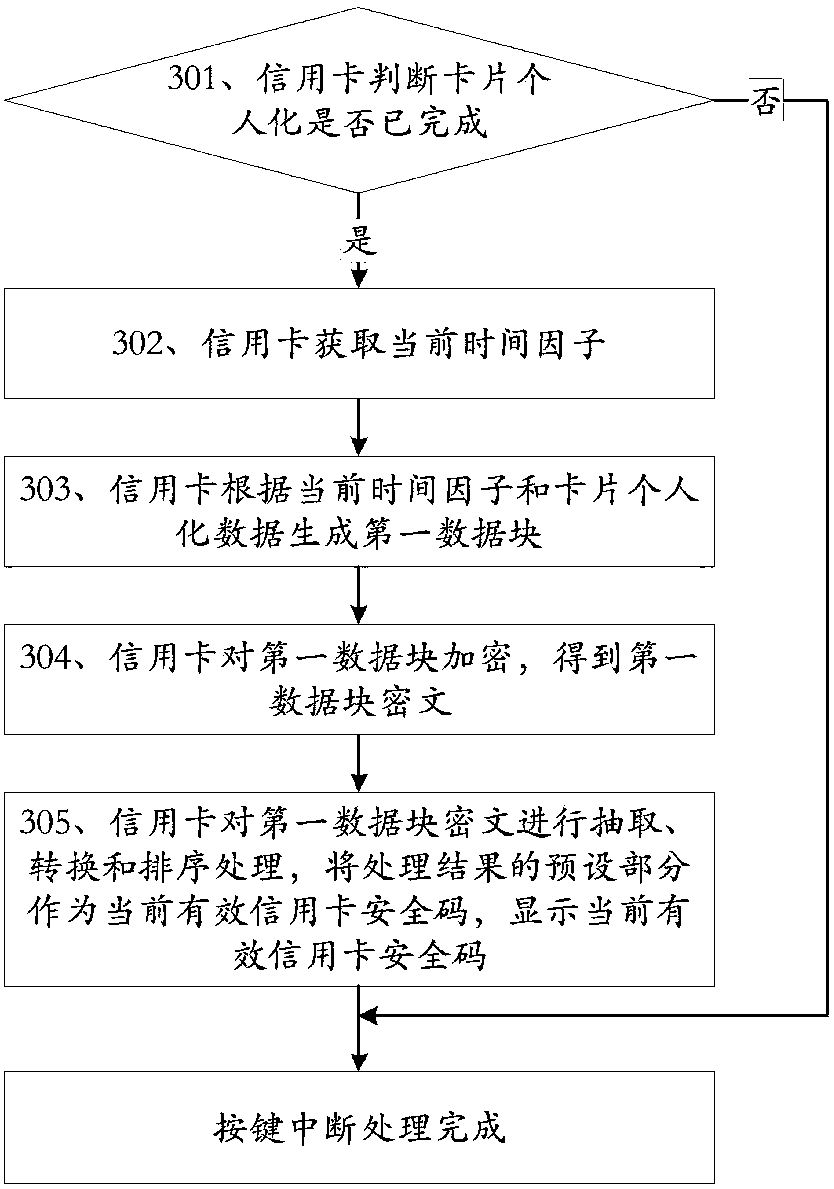
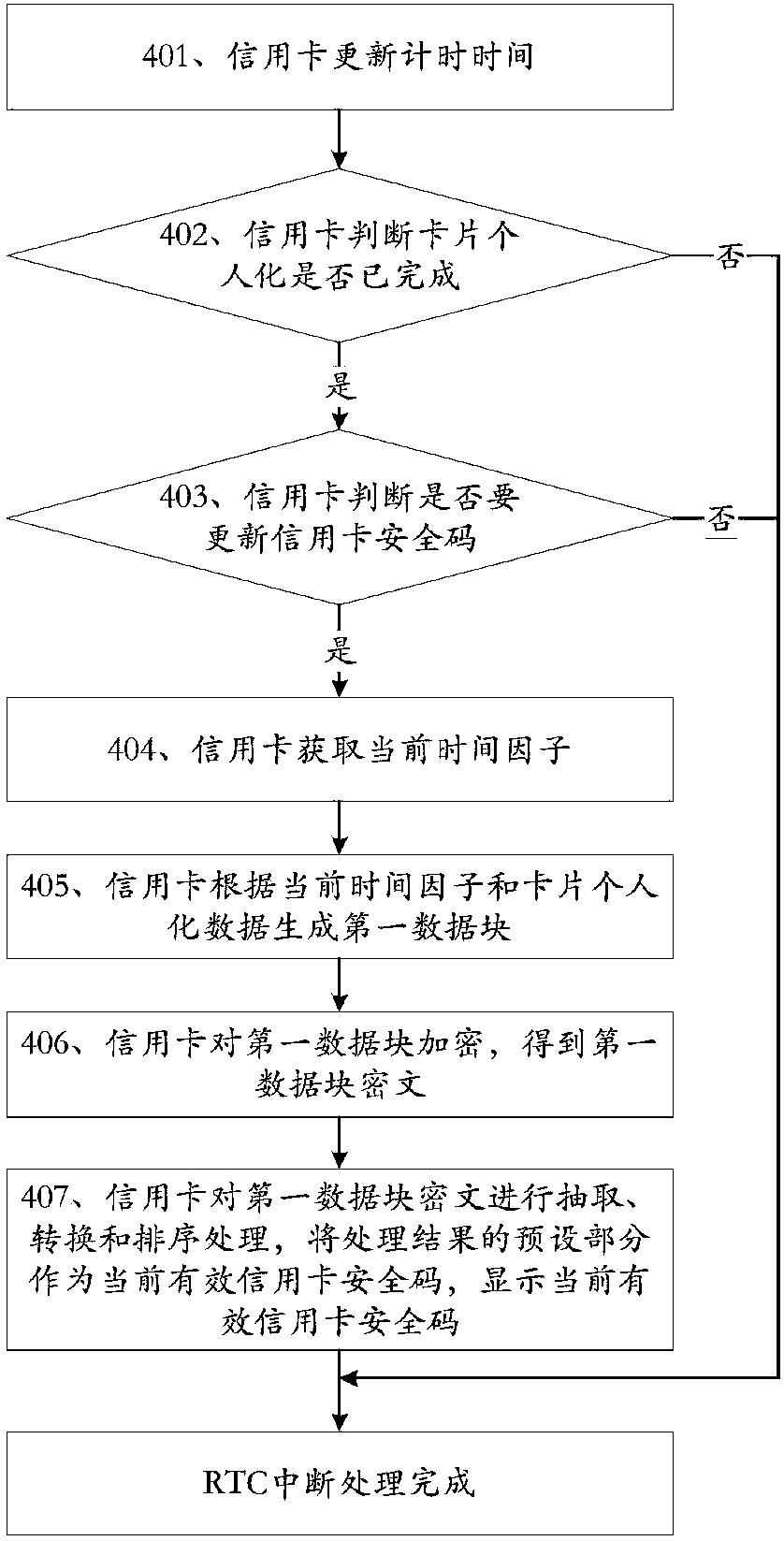
The invention discloses a method for enhancing security of no-card payment transaction and a credit card. The method includes the steps that 1, the credit card is powered on, and system initializationis conducted; 2, the credit card is dormant, the credit card is awakened when a preset interrupt is detected, and step 3 is conducted; 3, the credit card enters the preset interrupt treatment processto conduct the preset interrupt processing; when the preset interrupt treatment is completed, the credit card exits from the preset interrupt processing process and returns to the step 2. The creditcard comprises an electrifying module, an initialization module, a first dormancy module, a first detection module, a first awakening module and a first interrupt processing module. The method and thecredit card have the advantages of reducing the possibility of fraud by interception and storage of credit card security codes and enhancing the security of no-card payment transaction.
Owner:FEITIAN TECHNOLOGIES
Anti-counterfeiting code, generation system and application system of anti-counterfeiting code
ActiveCN104751217BEasy to forgeCommerceRecord carriers used with machinesProgramming languageCard security code
The invention discloses an anti-counterfeiting code comprising two sets of final sequence information generated by subjecting identical sequence information to algorithm computing. The invention further discloses an anti-counterfeiting code generating system and an anti-counterfeiting code application system. Elements in the two sets of identical sequence information (similar to the dual-helix structure of DNA (deoxyribonucleic acid) are subjected to algorithm computing according to a set program, the final sequence information of uniqueness is generated, and the anti-counterfeiting code is generated according to the final sequence information; thus, the problem that anti-counterfeiting labels on products of manufacturers are easily faked is solved.
Owner:BOA SHEN PAPER & PLASTIC PROD
Storage management method and system based on security information codes
ActiveCN107545443AAvoid confusionCommerceSpecial data processing applicationsLogistics managementConfusion
The invention provides a storage management method and system based on security information codes. According to the storage management method, the storage information of enterprise products can be automatically managed, before commodity warehouse entry, the identity information of the products can be set in an activation state through scanning the corresponding matched identity information including unique identification codes of the products, logistics identification codes of the products and security codes of the products. The storage management method is advantaged in that when the unique identification codes of the products, the logistics identification codes of the products or the security codes of the products have errors, automatic correction can be carried out through a preset formula, and commodity access flow confusion caused by the identity information corresponding errors can be avoided.
Owner:广州矽云信息科技有限公司
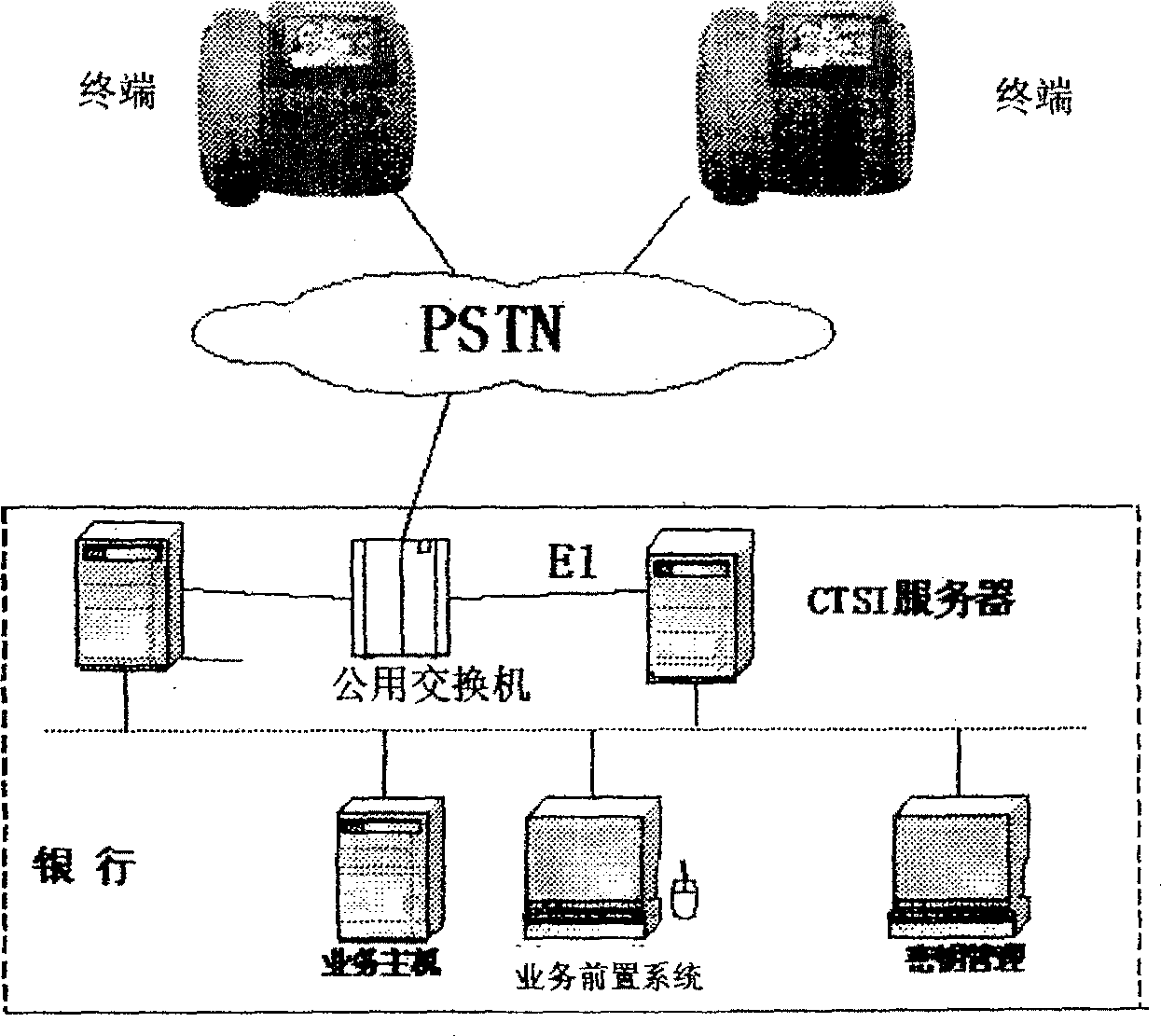
Bank terminal using fixed telephone network communication and its construction method
InactiveCN100498853CPrevent theftPrevent peepingComplete banking machinesTelephonic communicationEngineeringData memory
This invention relates to a bank terminal using fixed telephone network communication including a phone shell, an exterior line jack on the shell, a display screen, a swiping cards groove for keyboard and magcard / magstrip, a headphone connected with the shell, a CB in the shell with a microprocessor, a keyboard process circuit, a magcard / magstrip process circuit and a data storage on it, an IC card-plug slot on the shell and an IC card process circuit in the circuit on the CB, a keyboard inputting cipher information on the headphone, a SAM card base in the shell plugged with a SAM card security module for ciphering the account information input by swiping the card and cipher information input from keyboard to realize bank affairs including the payment function.
Owner:深圳市证通金信科技有限公司
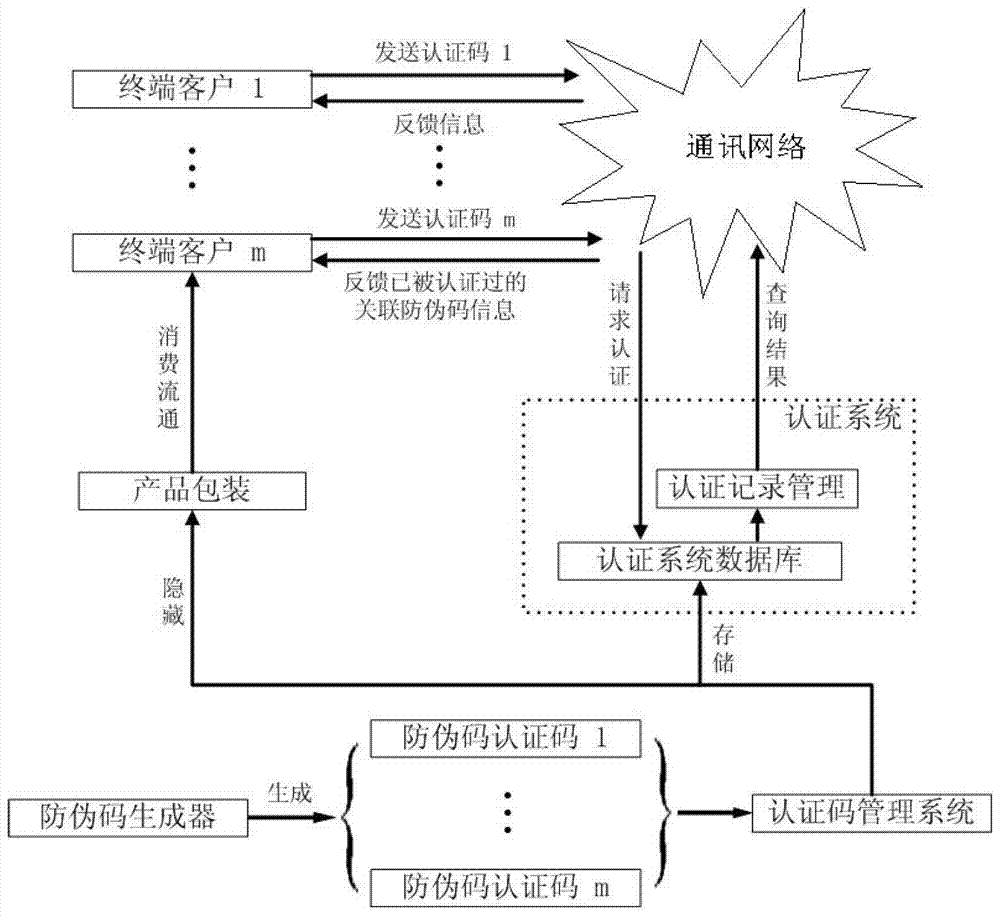
An article anti-counterfeiting method that realizes multiple authentications through associated anti-counterfeiting codes
ActiveCN103400270BStop counterfeitingLow anti-counterfeiting costCommerceComputer terminalCard security code
The invention discloses an article anti-counterfeiting method for realizing multiple authentications through associated anti-counterfeiting sets of codes. The method forms a set of anti-counterfeiting authentication codes with a plurality of random anti-counterfeiting authentication codes according to requirements, and hides the anti-counterfeiting codes in articles and on the package of the item and stored in the database of the authentication system; then when the relevant end customer performs the final anti-counterfeiting certification, the anti-counterfeiting authentication code hidden on the item or item packaging is taken out through an irreversible operation on the item, and the anti-counterfeiting authentication code hidden on the item or item packaging is retrieved by telephone, mobile phone or network query means The obtained anti-counterfeit authentication code is sent to the authentication system through the communication network. The authentication system will feed back the corresponding authentication result to the end customer according to whether the anti-counterfeiting code exists in the system database, the number of times it has been authenticated, and the associated authenticated anti-counterfeiting authentication code information. The anti-counterfeiting method of the invention can effectively prevent counterfeiting and counterfeiting, and can obtain the anti-counterfeiting effect of low anti-counterfeiting cost, easy realization and high anti-counterfeiting ability.
Owner:SHAANXI UNIV OF SCI & TECH
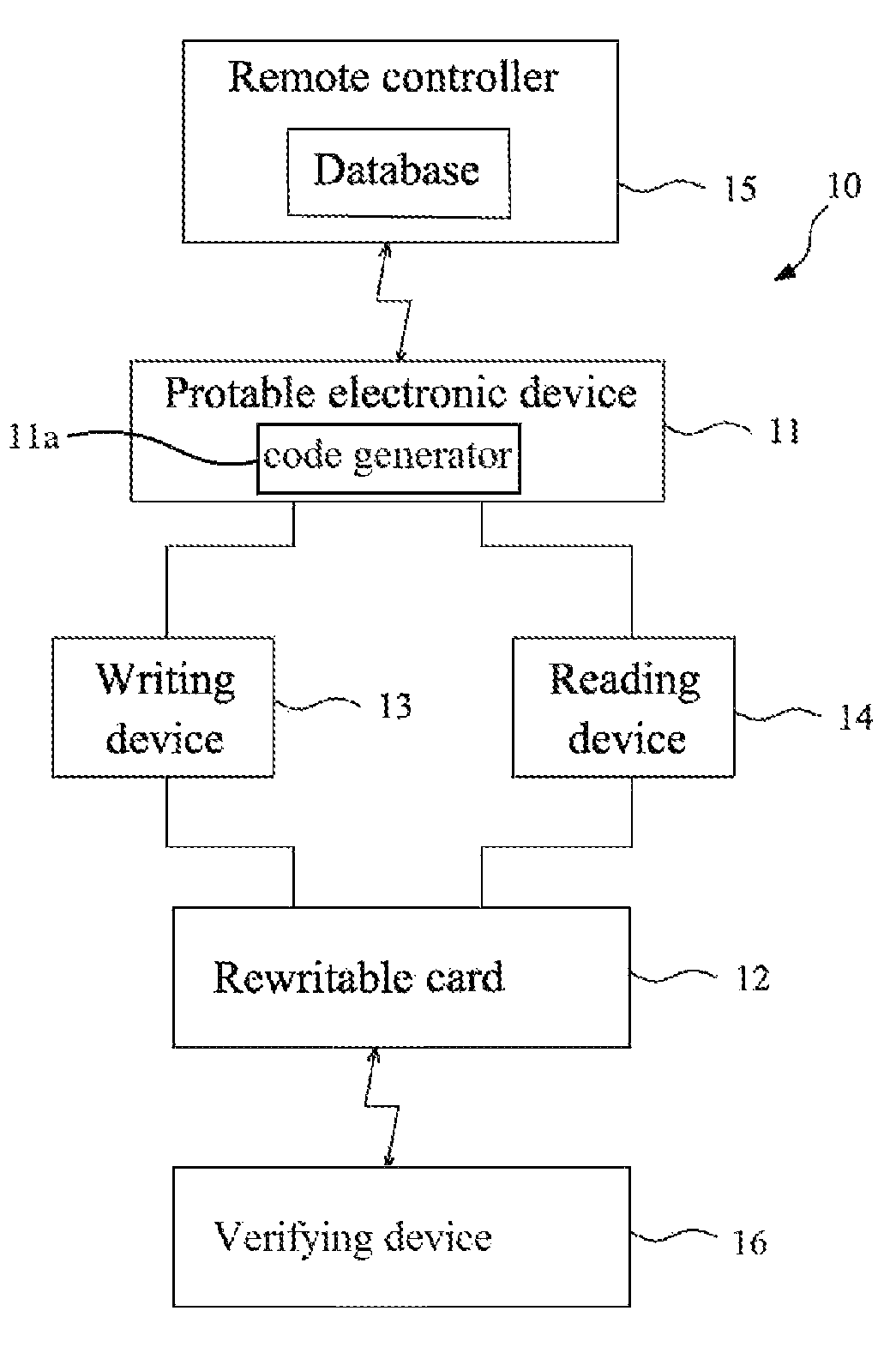
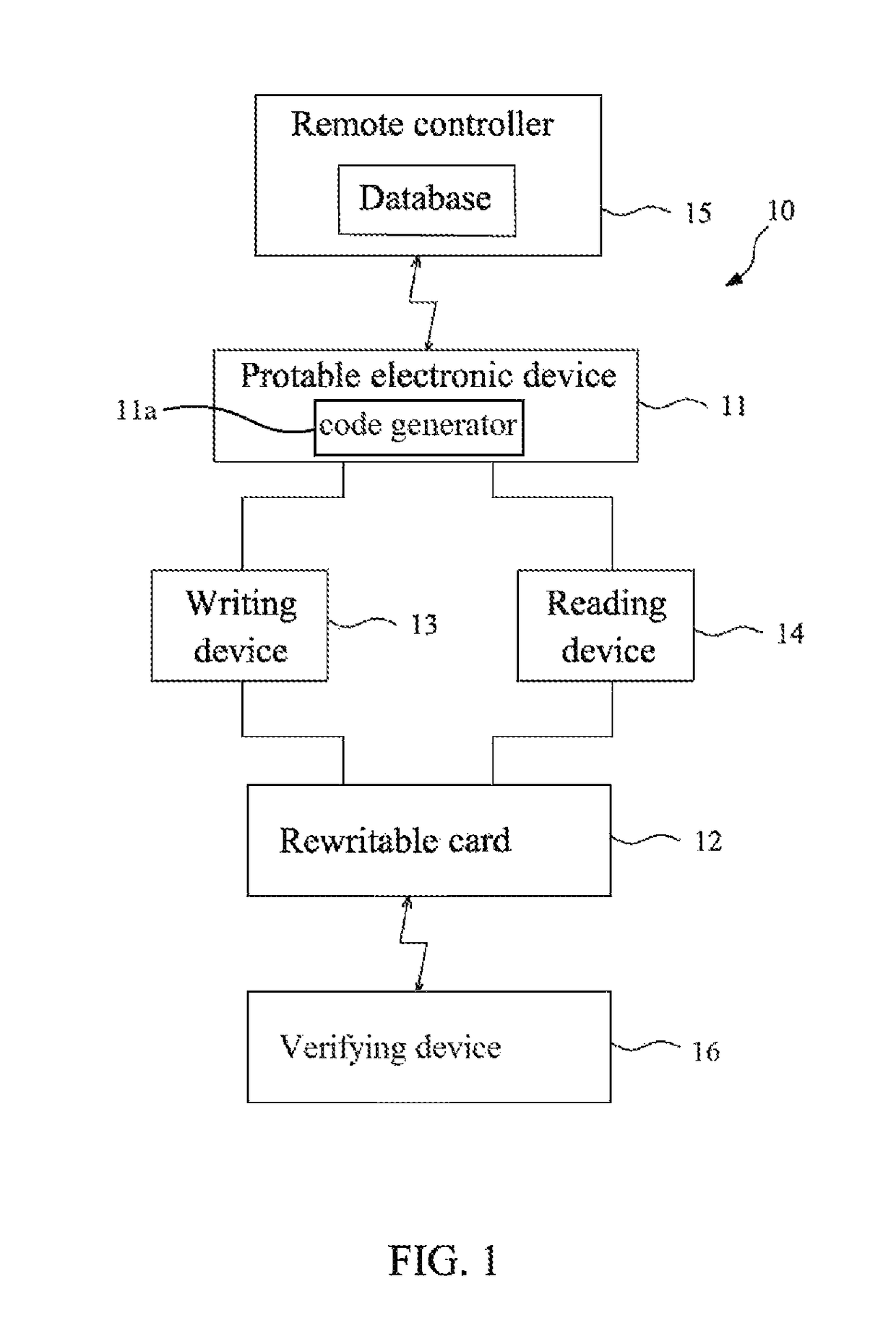
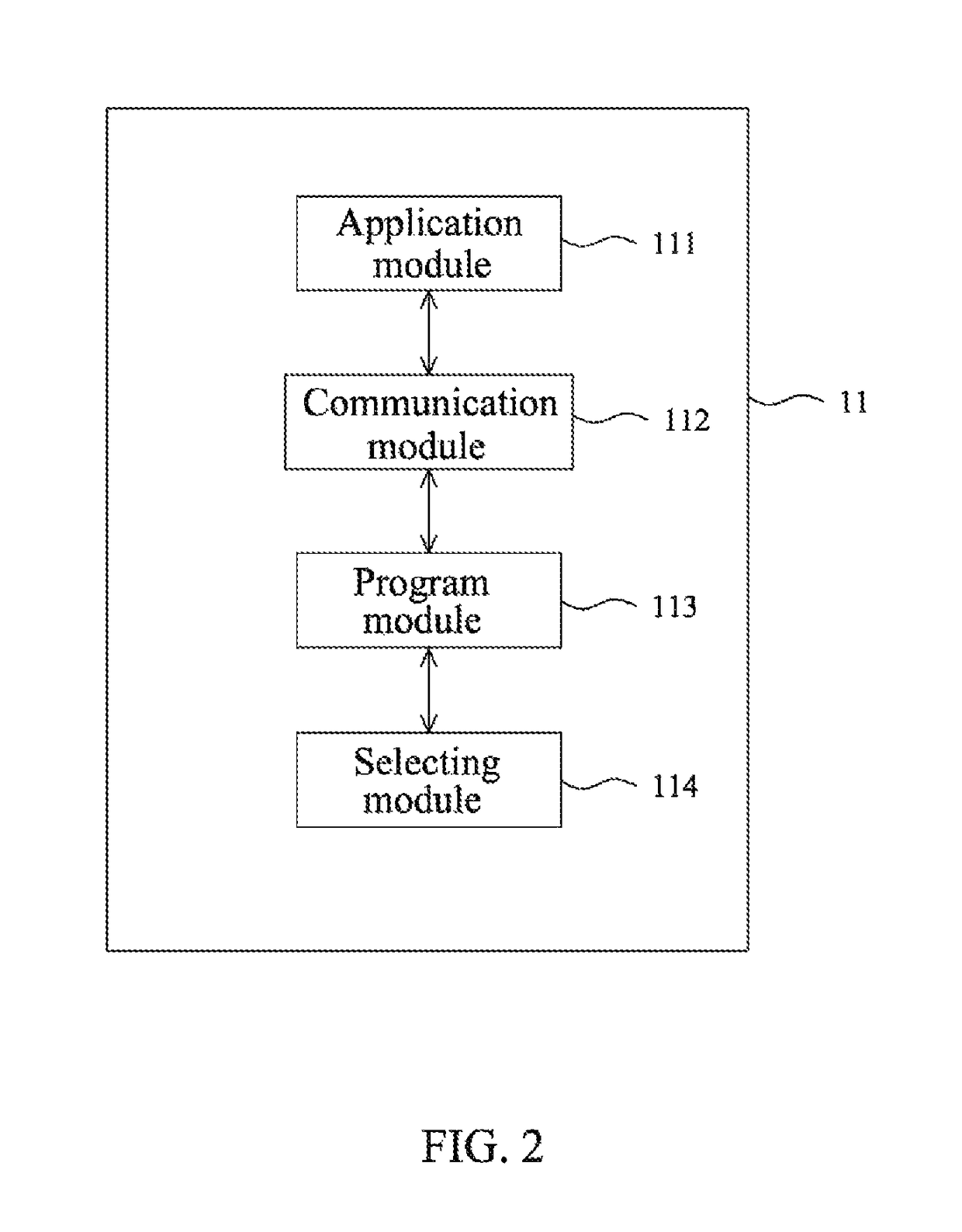
Portable electronic card system and verifying method thereof
A portable electronic card system and a verifying method thereof are provided. The portable electronic card system includes: a portable personal electronic device, a rewritable card, and a writing device. The portable personal electronic device is used for obtaining a certificated code and a personal information from a remote controller. When a bidirectional verifying communication is performed between the remote controller and the portable electronic device to download the personal information, security code stored in the rewritable card be compared with security code stored in the portable electronic device for verifying and writing the personal information into the rewritable card, and another security code is generated to update or replace the original security code stored in the portable electronic device and the rewritable card.
Owner:SUN PINSHENG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com