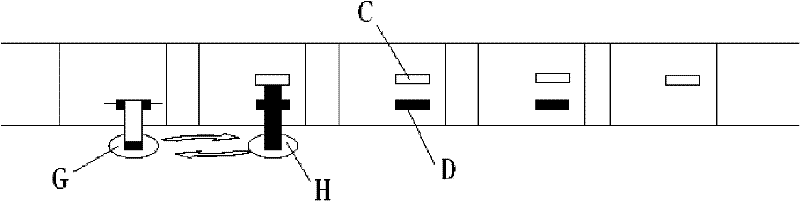
Method for encrypting real-time data into product security codes
A data encryption and anti-counterfeiting code technology, applied in the field of anti-counterfeiting, can solve the problems of large amounts of data, slow query process, hidden dangers of database load, etc., and achieve the effects of wide application, cost reduction and query speed improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0015] Example 1. The application of the present invention on a one-time anti-counterfeit combination lock.
[0016] For products equipped with disposable anti-counterfeiting combination locks, consumers need to inquire about the unlocking password of the one-time anti-counterfeiting combination locks before they can open the packaging of the products. Set the unlock password of the one-time anti-counterfeiting combination lock to instant data D, and encrypt the unlocking password of the one-time anti-counterfeiting combination lock in the anti-counterfeiting code according to the following steps:
[0017] (1) Set the product basic code A according to the product information. Product basic code A is generated according to the requirements of the enterprise, and can be composed of manufacturer code, product serial number or production date, such as 20072800110001, where manufacturer code: 0011, serial number: 0001, date: February 8, 2007. It can also be various codes containi...
Embodiment 2
[0027] Example 2. The application of the present invention in logistics anti-fleeing goods.
[0028] Fleeing goods is to sell the products distributed across regions. Fleeing goods will cause market crowding, price confusion, and seriously affect the reputation of manufacturers. The invention can be used to prevent channeling. Set the dealer (arrival place) code as real-time data D, and follow the steps below to encrypt the product dealer code in the anti-counterfeiting code:
[0029] (1) Set the product basic code A according to the product information. Product basic code A is generated according to the requirements of the enterprise, and can be composed of manufacturer code, product serial number or production date, such as 20072800110001, where manufacturer code: 0011, serial number: 0001, date: February 8, 2007. It can also be various codes containing other information.
[0030] (2) The basic anti-counterfeiting code B is generated by encrypting the product basic code...
Embodiment 3
[0036] Example 3. The application of the present invention in the monitoring of product validity period.
[0037]The production date is generally printed on the product packaging so that consumers can identify whether the product is within the validity period. However, some unscrupulous distributors maliciously alter the production date of expired products or products that are about to expire in order to seek profits, seriously infringing on the rights and interests of consumers. Especially for food and pharmaceutical products, the act of altering the production date will directly pose a threat to the health and life of consumers. The invention can load the production date of the product into the anti-counterfeit code, not only can identify the authenticity of the product, but also can directly identify the production time of the product from the inquired code information, preventing dealers from changing the production date maliciously.
[0038] Set the product production d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com