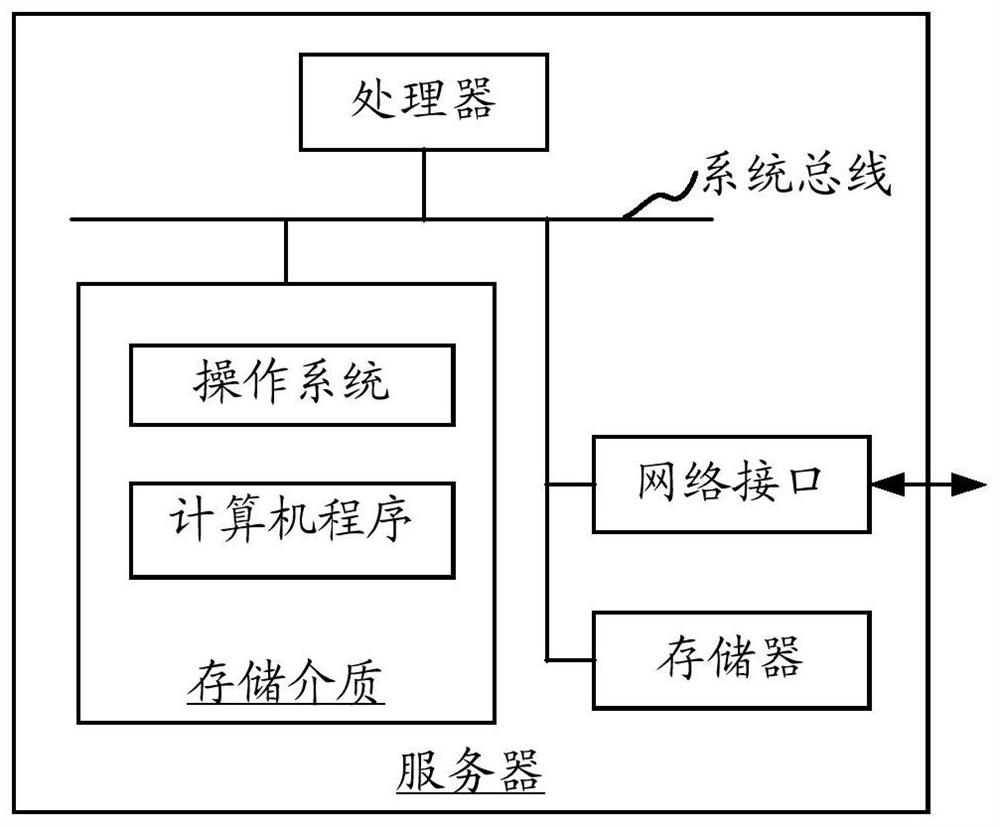
Patents
Literature
127 results about "On-the-fly encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
On-the-fly encryption, also known as real-time encryption and transparent encryption, is a method used by some disk encryption software. "On-the-fly" refers to the fact that data is automatically encrypted or decrypted as it loaded or saved. With on-the-fly encryption, the files are accessible immediately after the key is provided, and the entire volume is typically mounted as if it were a physical drive, making the files just as accessible as any unencrypted ones.No data stored on an encrypted volume can be read without using the correct password/keyfile or correct encryption keys. The entire file system within the volume is encrypted. To be transparent to the end user, on-the-fly encryption usually requires the use of device drivers to enable the encryption process. Although administrator access rights are normally required to install such drivers, encrypted volumes can typically be used by normal users without these rights . In general, every method in which data is transparently encrypted on write and decrypted on read can be called on-the-fly encryption.
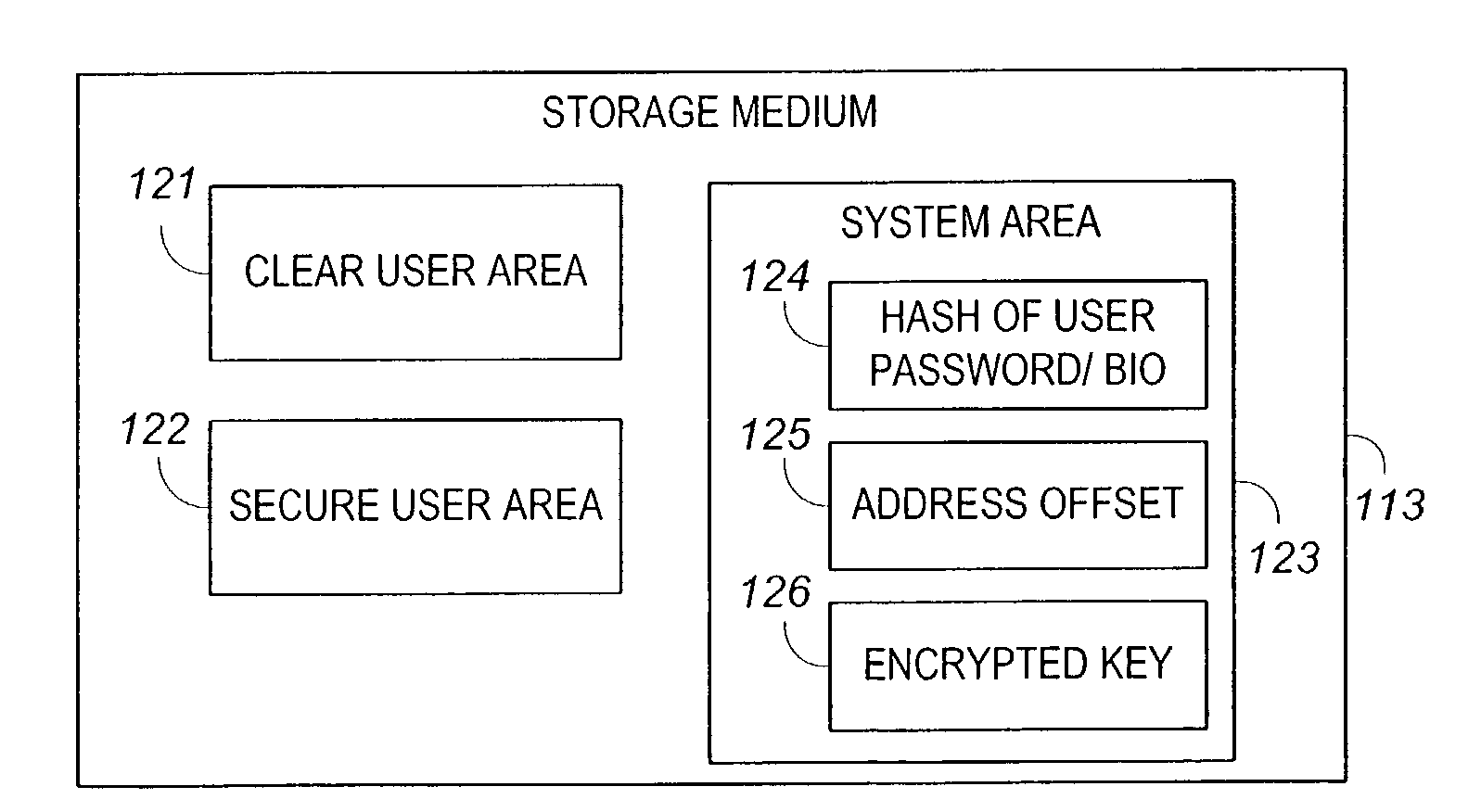
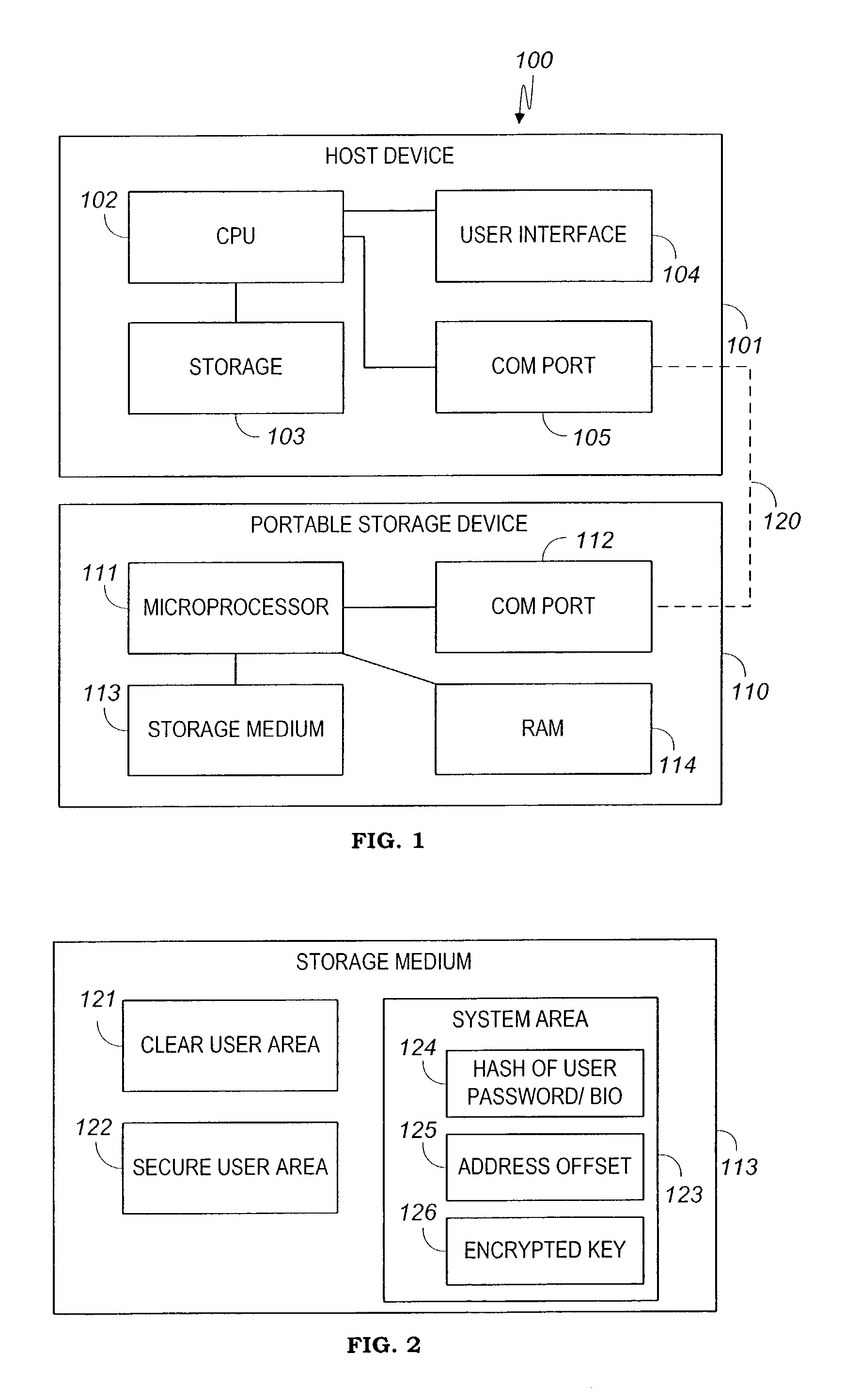
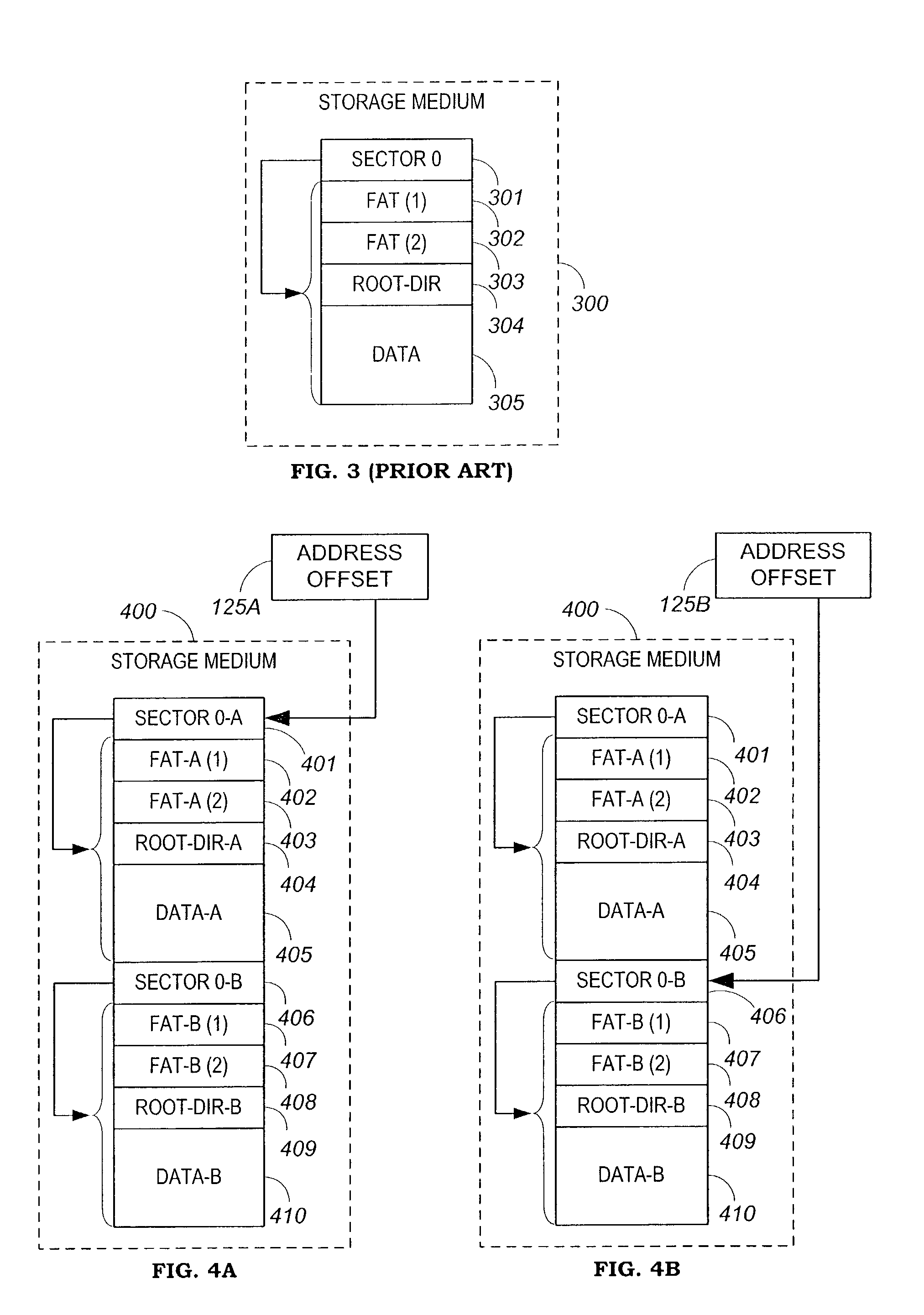
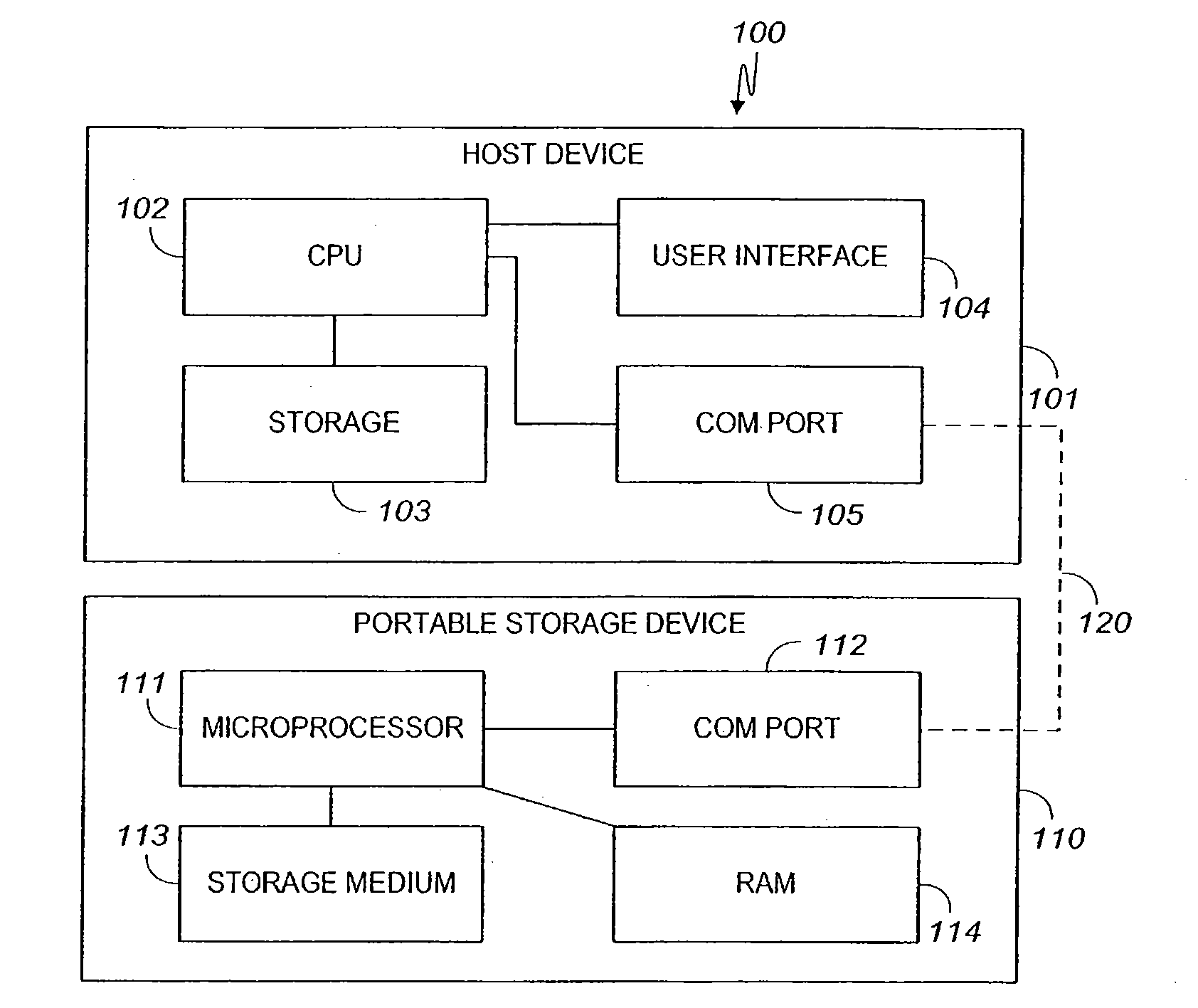
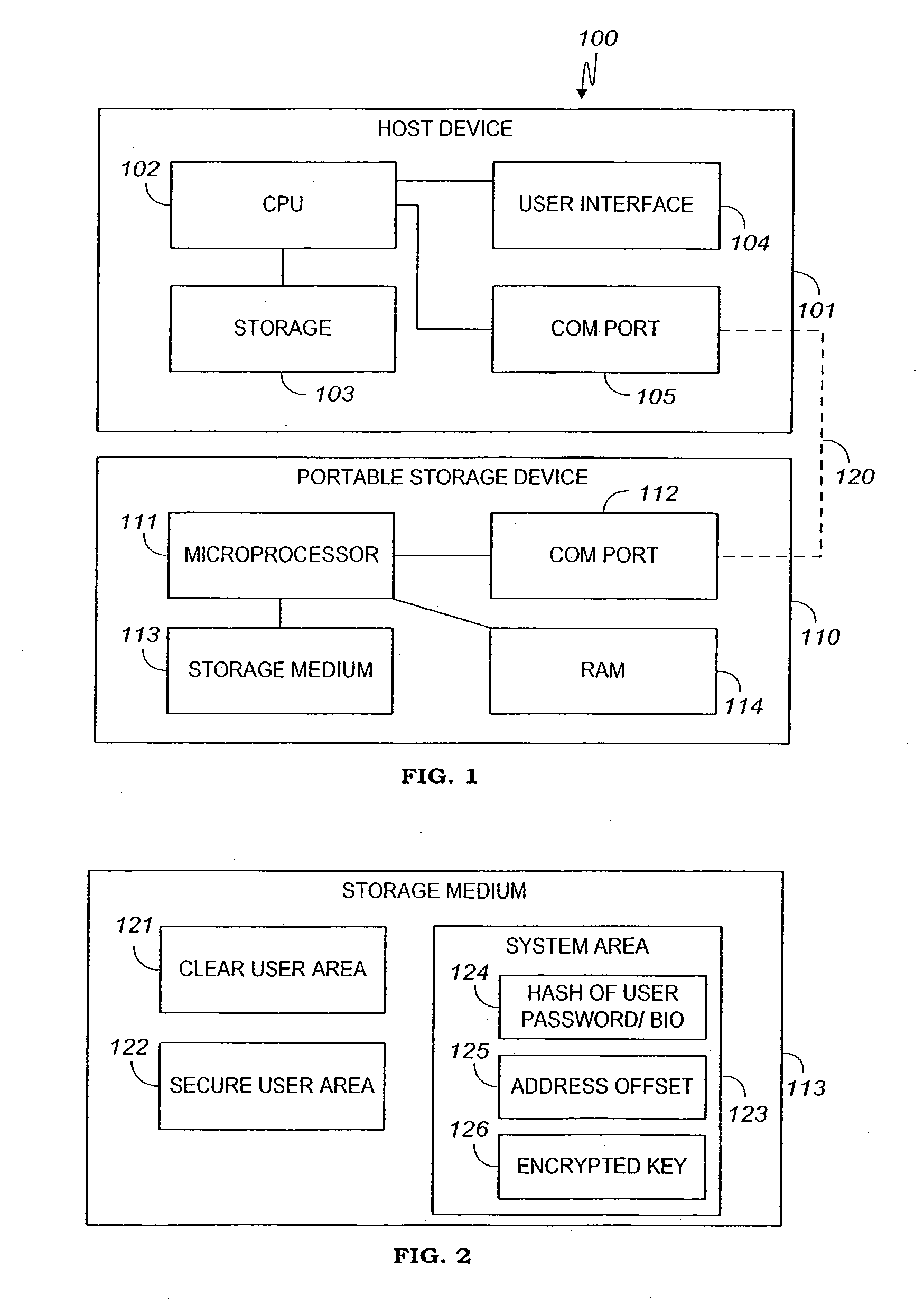
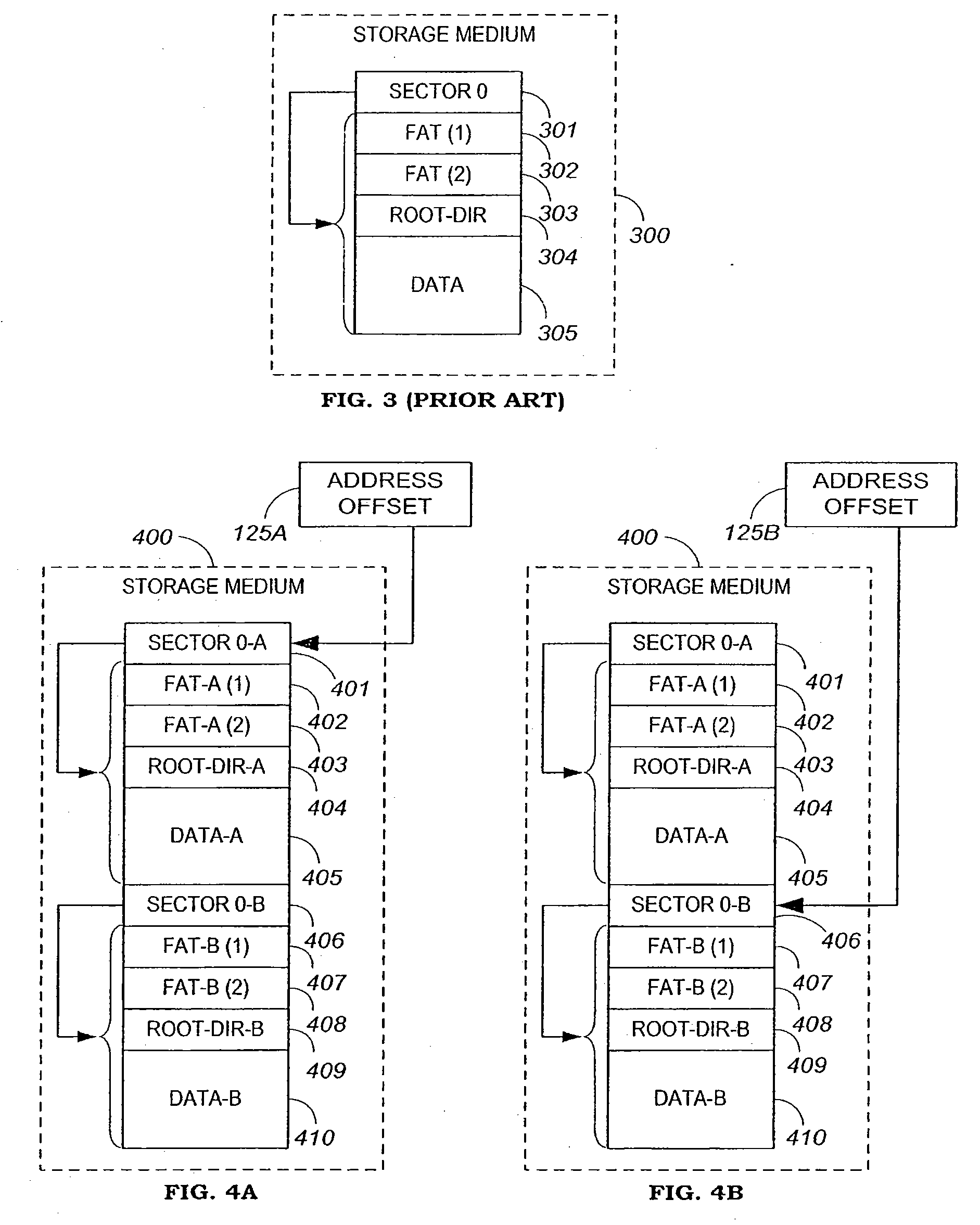
Apparatus and method for securing data on a portable storage device
ActiveUS7478248B2Secure and convenientUnauthorized memory use protectionHardware monitoringPasswordData storing
A portable storage device including a microprocessor and a secure user data area, the microprocessor operable to perform on-the-fly encryption / decryption of secure data stored on the storage device under a user password, the microprocessor also operable to exclude access to the secure user data area unless the user password is provided.
Owner:WESTERN DIGITAL ISRAEL LTD
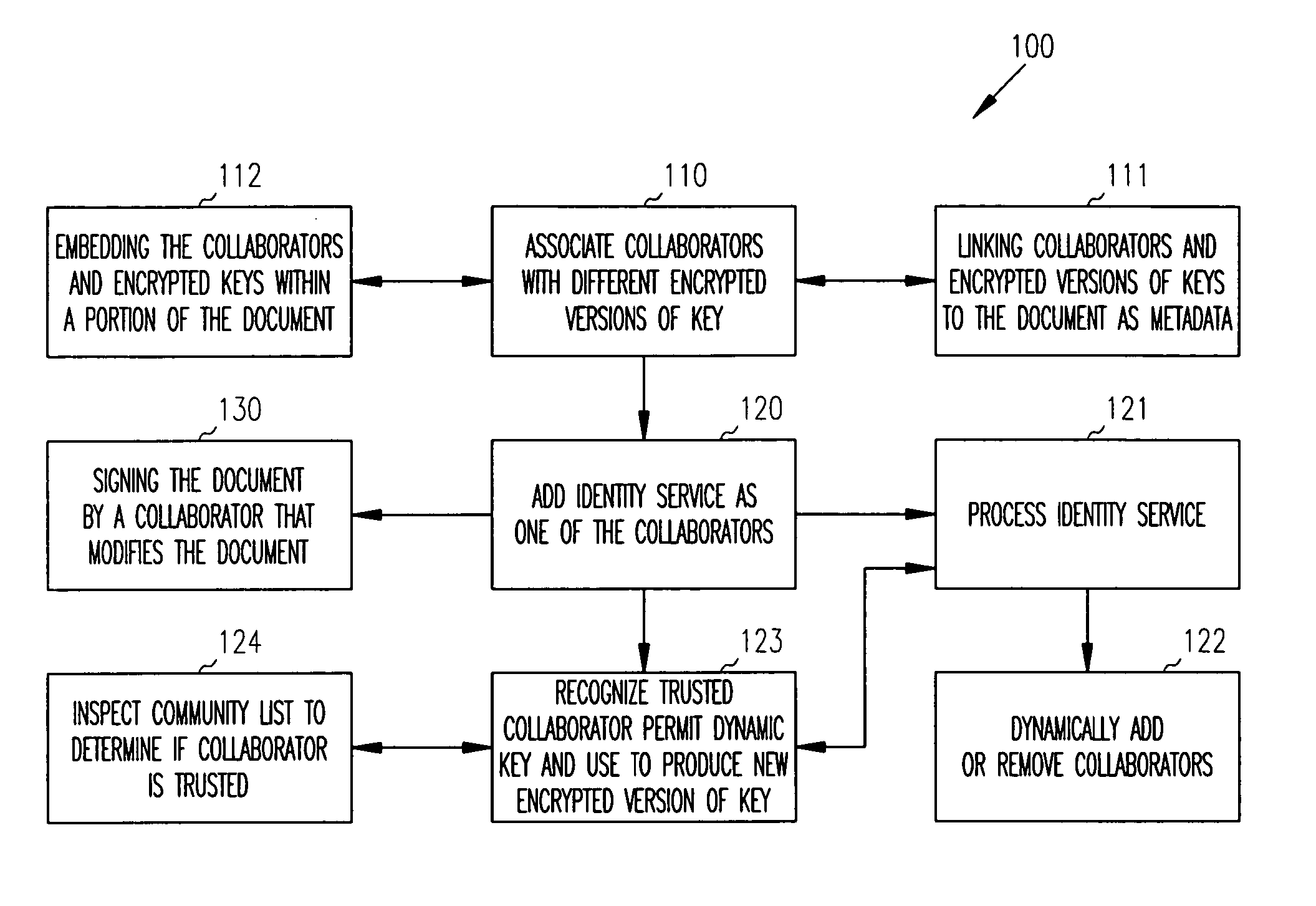
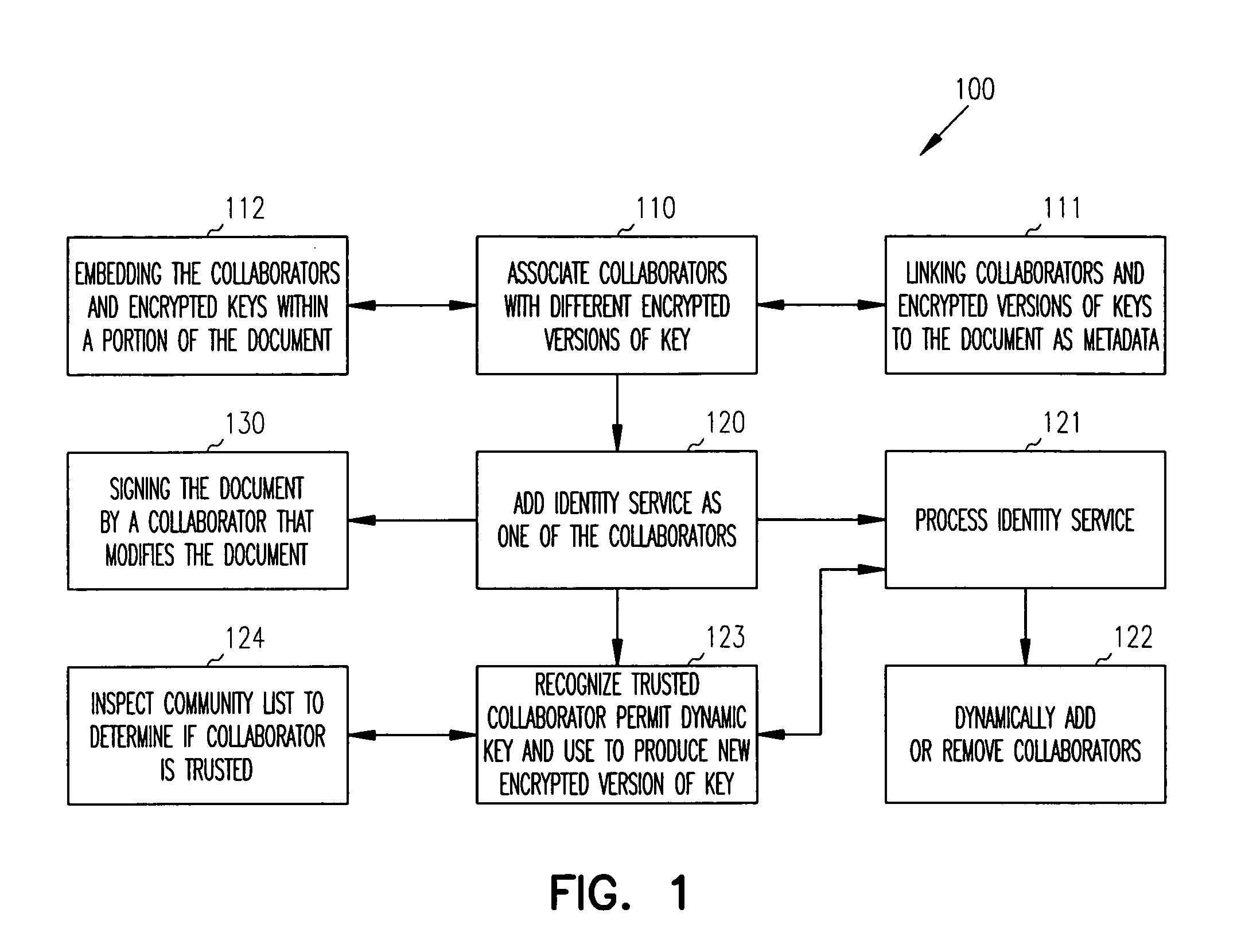
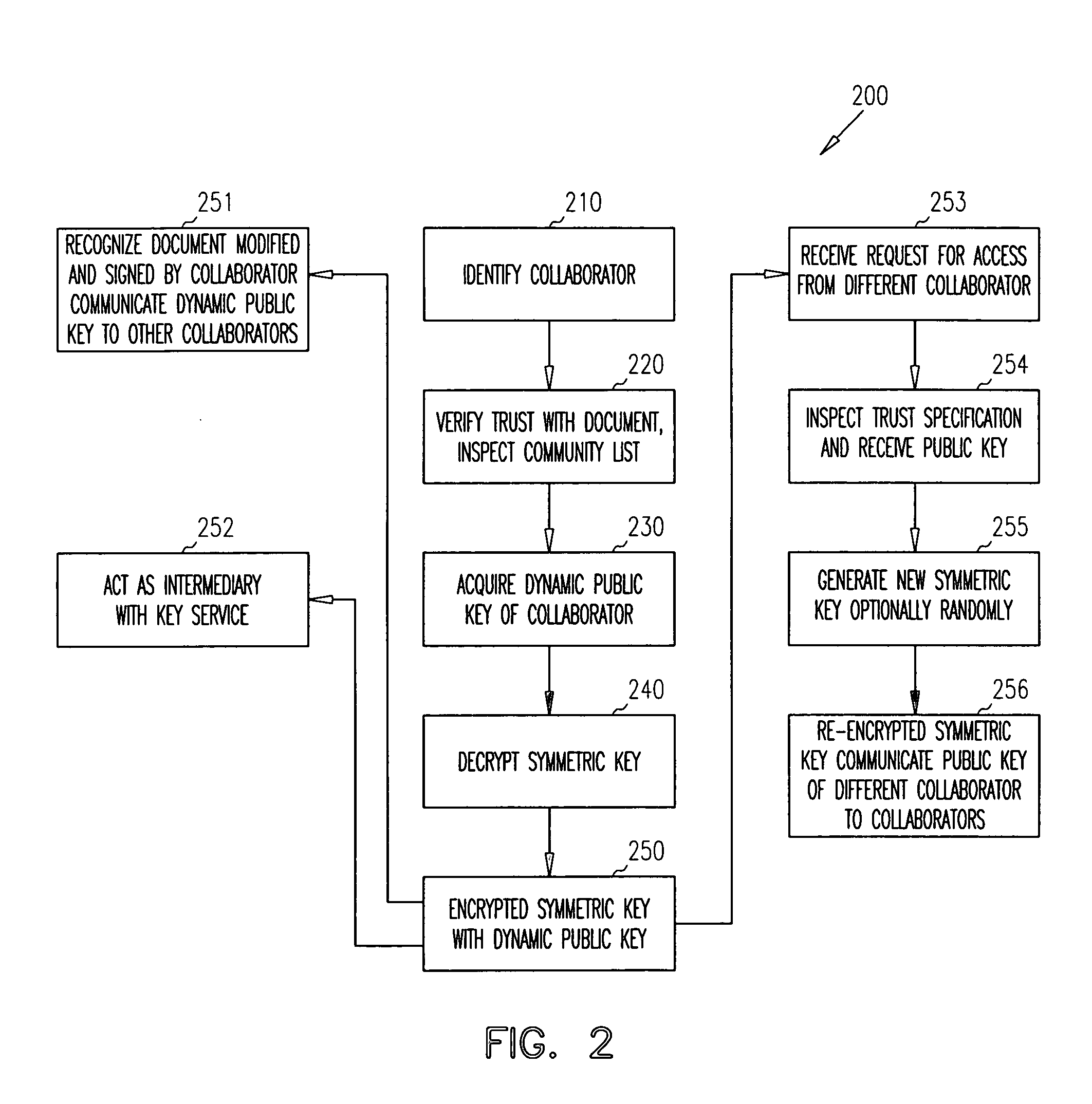
Distributed dynamic security for document collaboration
ActiveUS20050120199A1Digital data processing detailsUser identity/authority verificationPaper documentDynamic management
Techniques are provided for dynamically managing security for document collaboration. A document is associated with a list of collaborators, which can access the document. One collaborator is an identity service. The identity service is capable of dynamically encrypting versions of an access key needed by a collaborator to access the document and capable of dynamically adding or removing collaborators from the list of collaborators.
Owner:ORACLE INT CORP
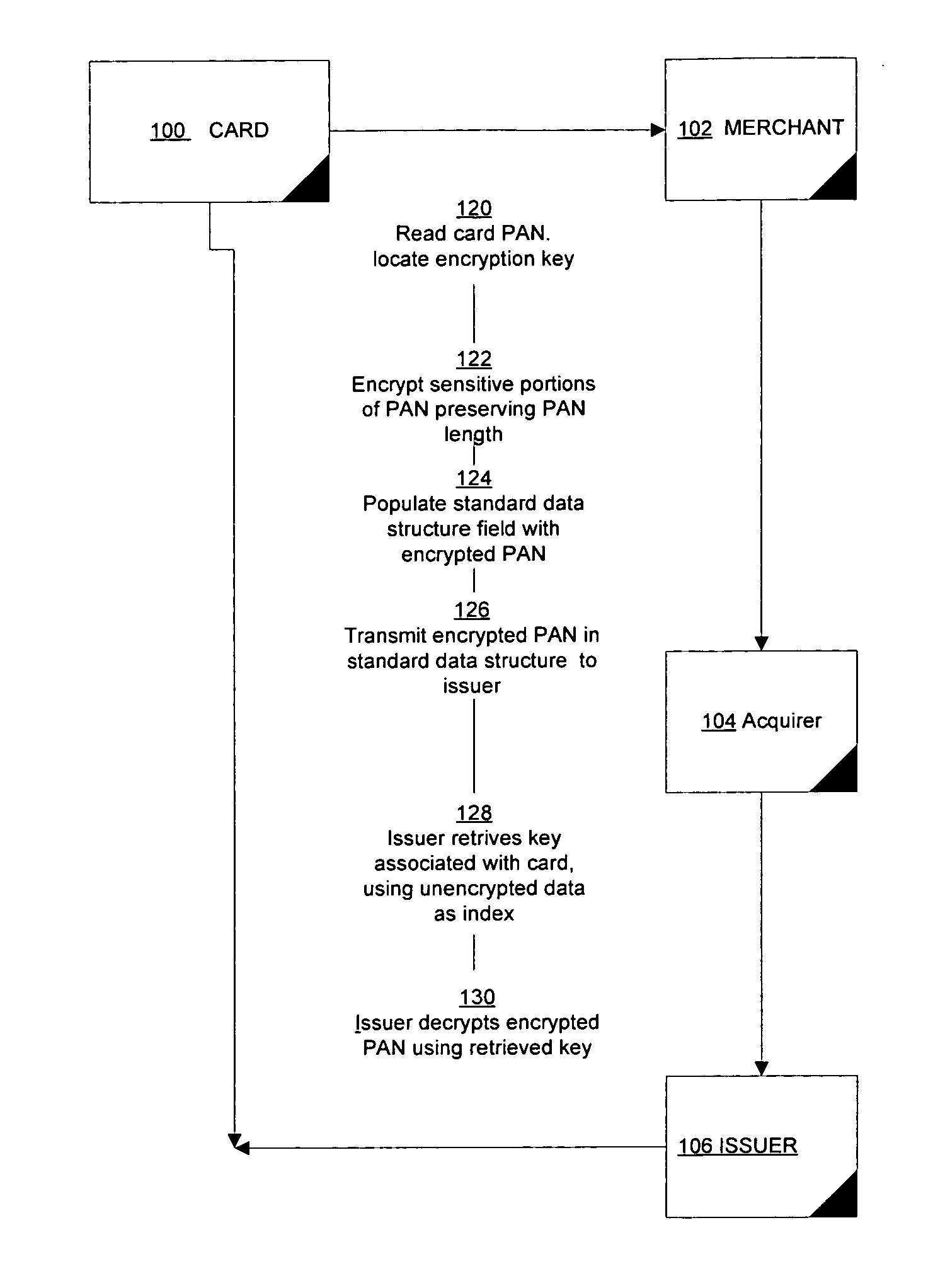
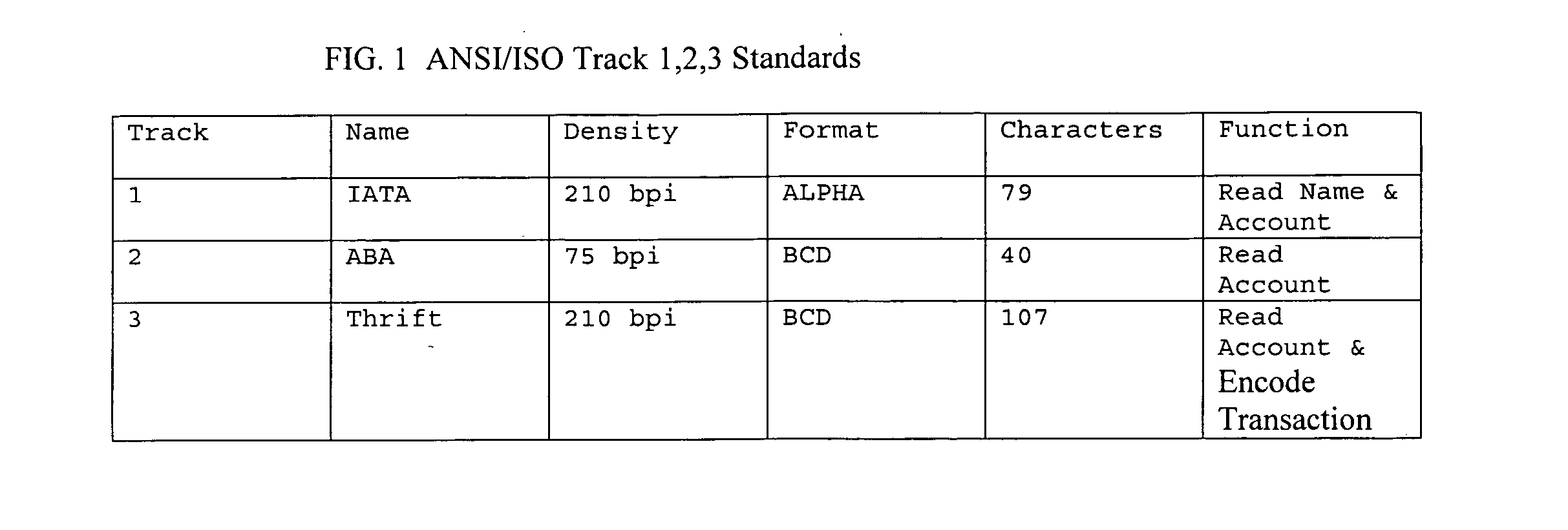
Dynamic encryption of payment card numbers in electronic payment transactions
Systems and methods are provided for secure transmission of information identifying account holders in electronic payment transactions made using payment cards or devices that are based integrated circuit chip technology. Individual cards or devices are associated with a cipher key. Information such as personal account numbers, which may be stored on the cards or devices, is encrypted using a block cipher in a variant of the cipher feedback mode. This manner of encryption preserves the length of the cleartext, and allows the ciphertext to be securely transmitted in standard data structure formats over legacy electronic payment networks.
Owner:MASTERCARD INT INC
Dynamic encryption
ActiveUS20130080772A1Increase flexibilityPreclude need to encryptComputer security arrangementsSecuring communicationService networksEncryption system
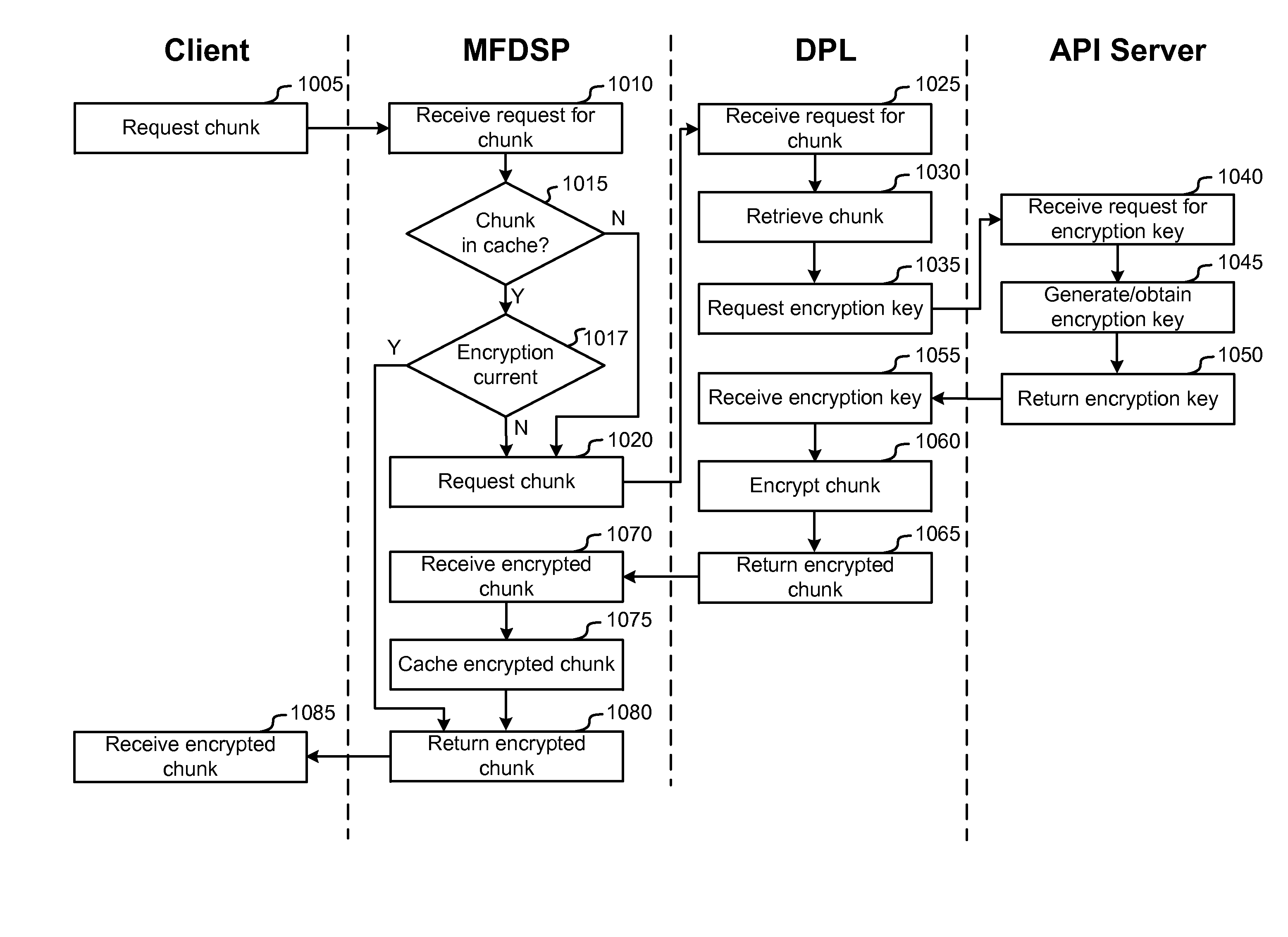
Systems and methods for encrypting a media file for streaming and / or downloading over a network are disclosed. These systems and methods may be part of a larger media servicing network that can be used to, among other things, process uploaded media content, provide it for streaming, and collect metric information regarding the streaming. The disclosed systems and methods provide for receiving requests for a media file or a chunk of a media file and responding to these requests by encrypting the requested chunks dynamically and providing the chunks to the requesting entity. These systems and methods, which can be utilized with a dynamic chunk generation and dynamic index file generation, enable a high degree of flexibility in streaming chunked media files and preclude the need to encrypt the chunks prior to streaming. The systems and methods may also be applied to encrypting files for continuous streaming protocols as well as for progressive download.
Owner:BRIGHTCOVE
System and method for dynamic generation of encryption keys
InactiveUS20060126836A1Secure transmissionMaintain securityMultiple keys/algorithms usageCombined useKey generation
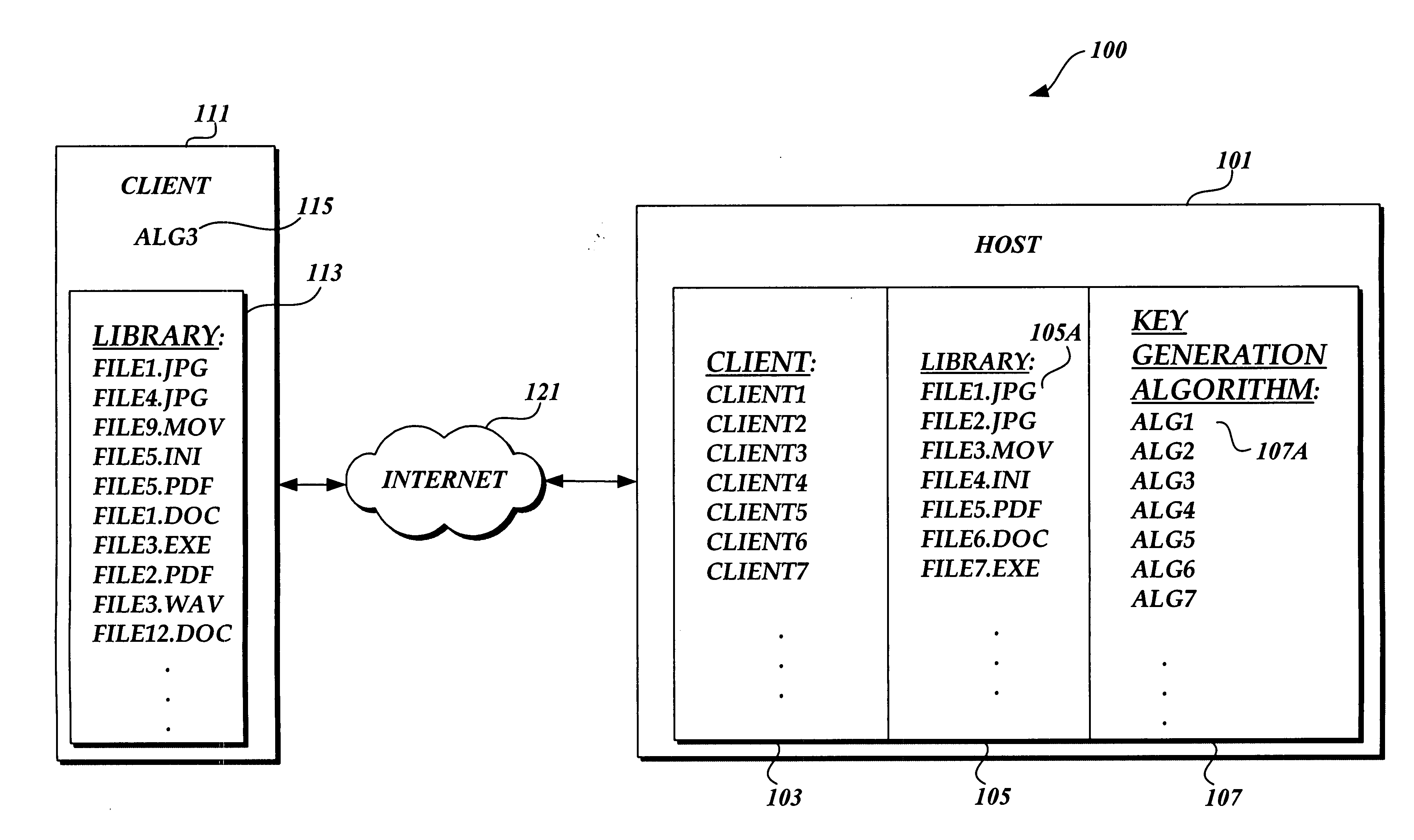
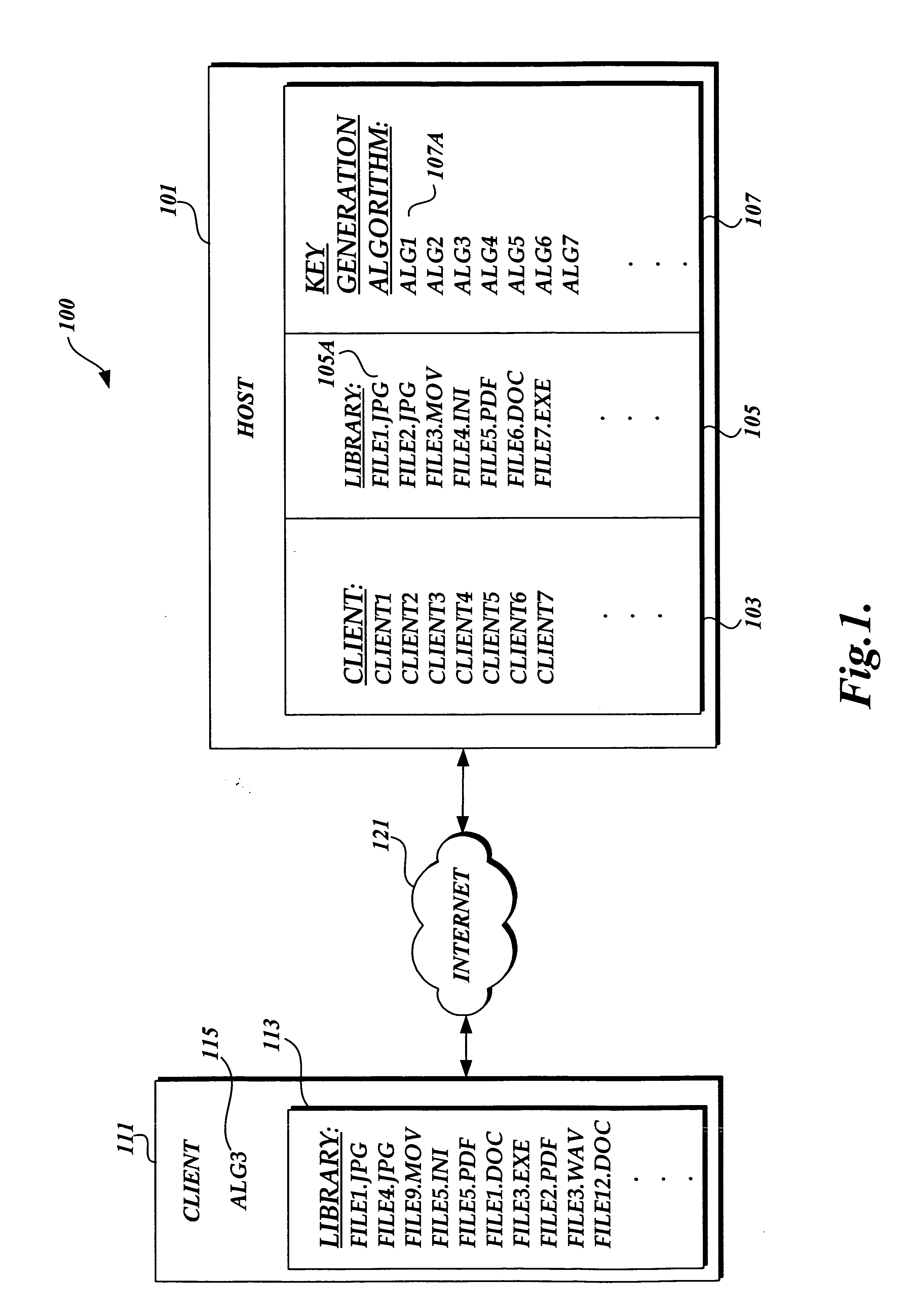
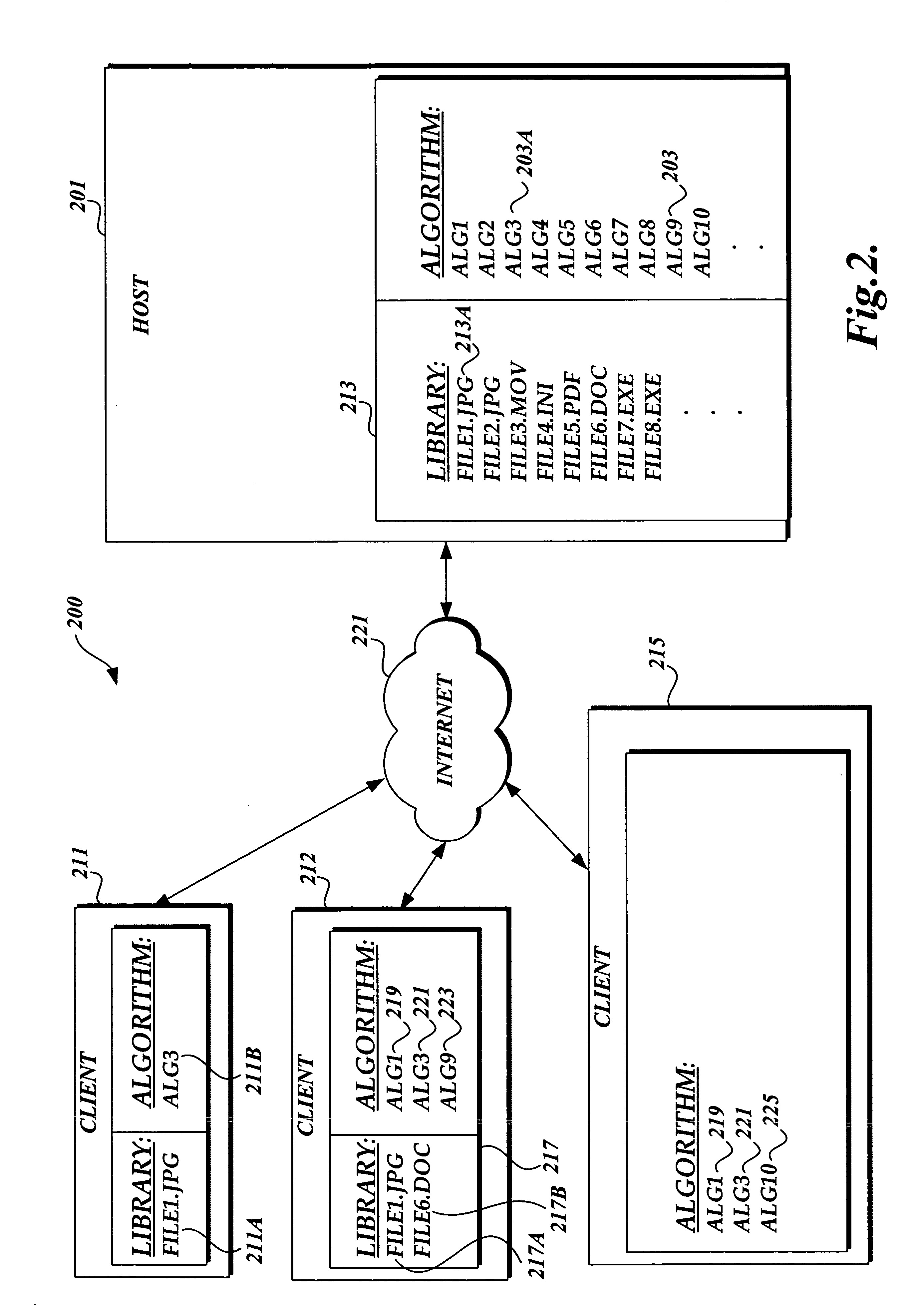
In accordance with an aspect of the present invention, a method for dynamically encrypting and decrypting digital information using a dynamically generated keys is provided. The method includes, obtaining digital information to be encrypted and identifying a file that is to be used in generating a dynamic key. The identified file is used in conjunction with a key generation algorithm to generate a dynamic key and that dynamic key is used with an encryption algorithm to encrypted the digital information. Likewise, to decrypt the encrypted digital information, a file is identified that is to be used to generate a dynamic key. That file and a key generation algorithm are used to generated a dynamic key. The dynamic key is used in conjunction with a decryption algorithm to decrypt the digital information.
Owner:PACCAR INC
Bar-code-based information verification system
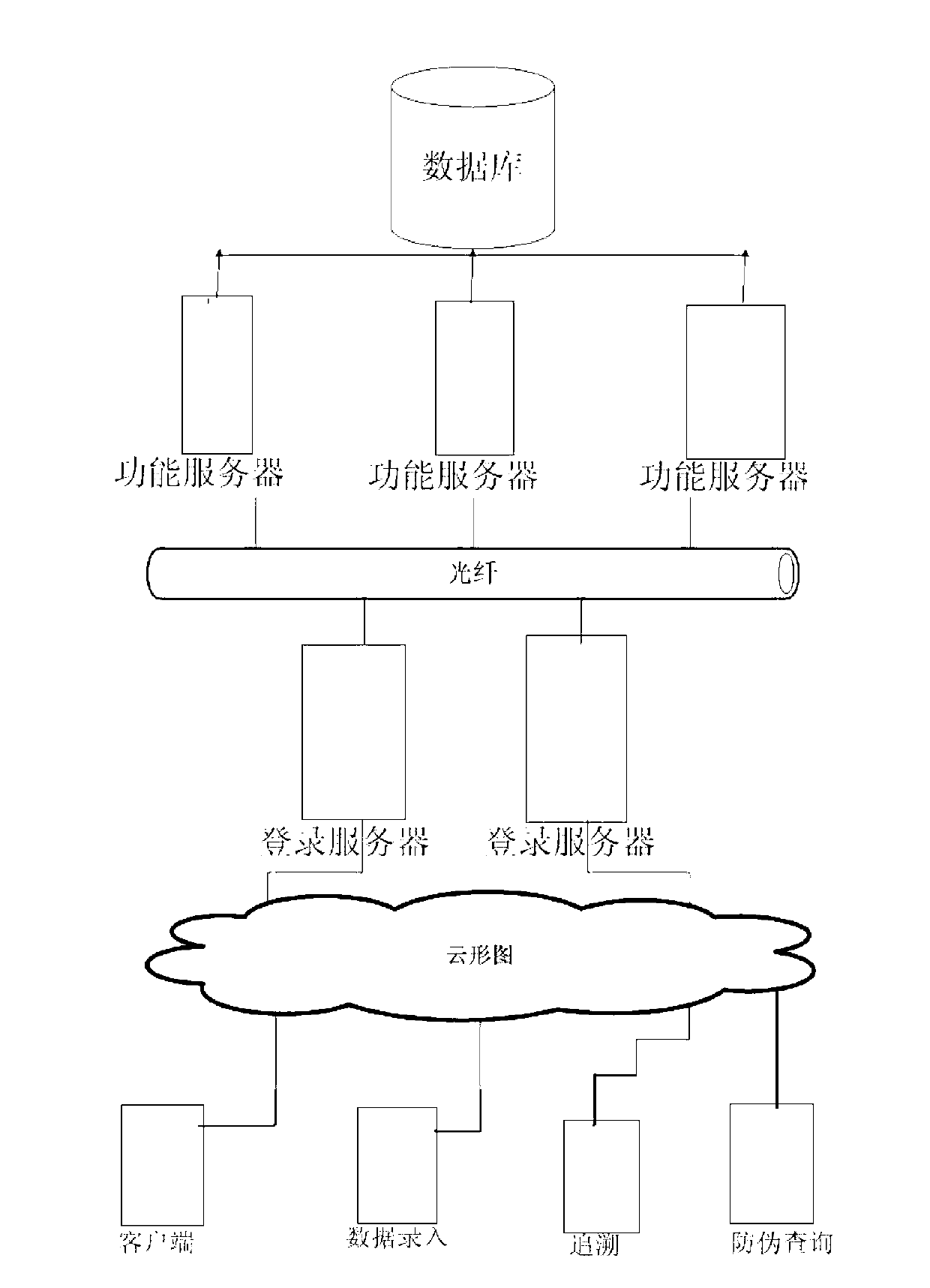
InactiveCN103123709AImprove securityImprove response speedCommerceSensing by electromagnetic radiationProgramming languageEngineering
The invention discloses a bar-code-based information verification system. The information verification system comprises a bar code, a database subsystem, a management subsystem, a server cluster, a fixed terminal and a mobile terminal, wherein the bar code is used for identifying and encoding a product and comprises encrypted product information; the database subsystem is used for storing bar code information and the position information of the terminals; the management subsystem is used for information management and operation maintenance; the server cluster is used for providing support for verification service; the fixed terminal is used for reading the bar code information and sending the bar code information to the server cluster for processing; and the mobile terminal is used for real-time anti-counterfeiting verification. The bar-code-based information verification system has the advantages that (1) system safety is improved by using a dynamic encryption algorithm; (2) the response speed and throughput of the system are increased by using the server cluster; (3) data safety is improved by data backup; and (4) the improved bar code design is suitable for the anti-counterfeiting traceability of commodity.
Owner:广州众码汇信息科技有限公司
Dynamic encryption of a universal resource locator
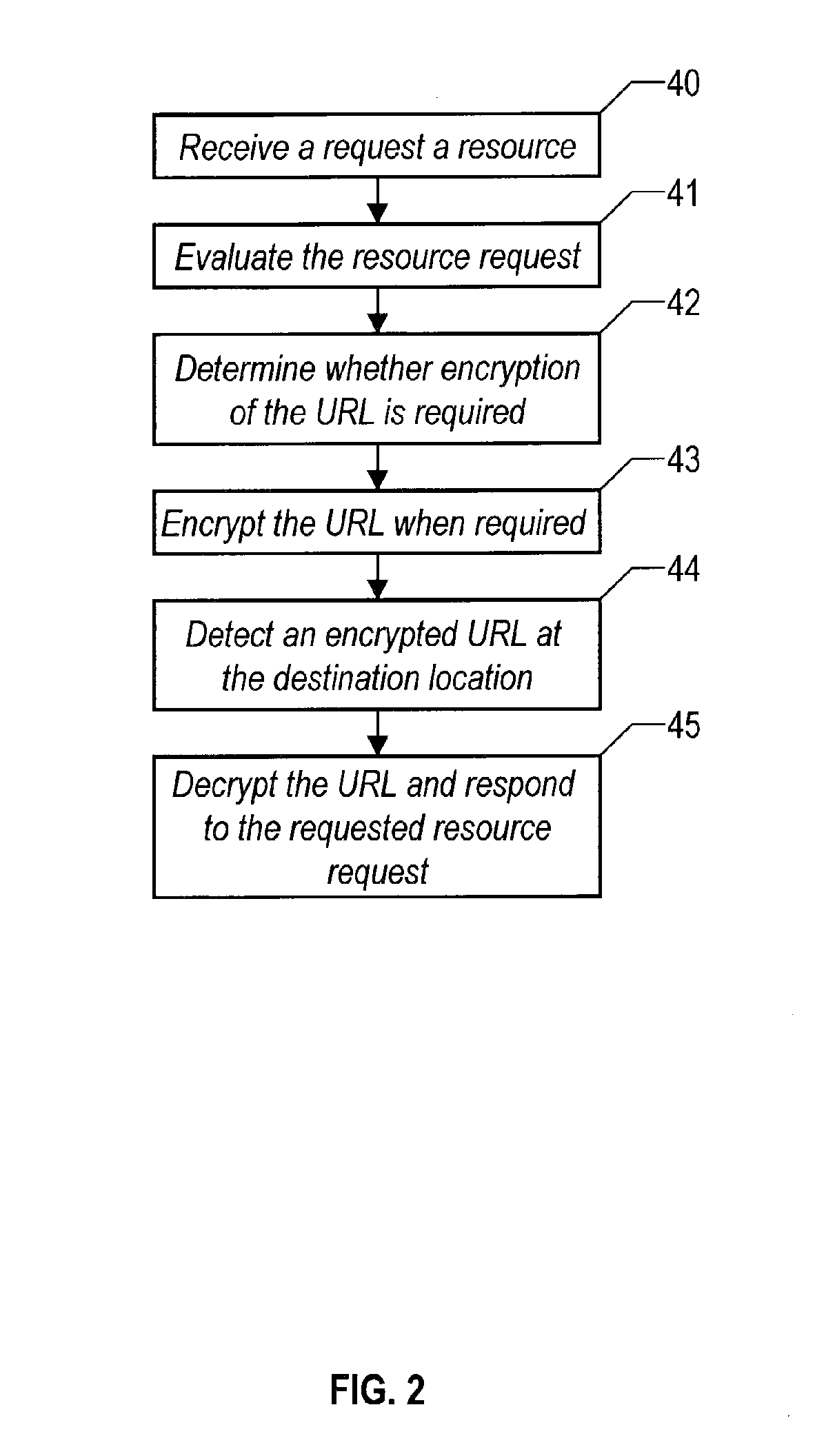
InactiveUS20140317404A1OptimizationSpecial data processing applicationsSecuring communicationAccess to informationResources of a Resource
A system including a computer and a computer readable hardware storage device containing instructions which, upon being executed by the computer, implements a method for restricting access to information transmitted over a computing network. A resource request for a resource to be located is received. The resource request contains a universal resource locator (URL). The URL is evaluated to determine whether encryption of none, part, or all of the URL is required. It is determined that the requested resource is available and in response, the requested resource contained in the resource request is located. It is determined whether encryption is required for none, part, or all of a return URL of the requested resource that is to be returned to a location of the resource request.
Owner:TAASERA LICENSING LLC
Dynamic substitution of USB data for on-the-fly encryption/decryption
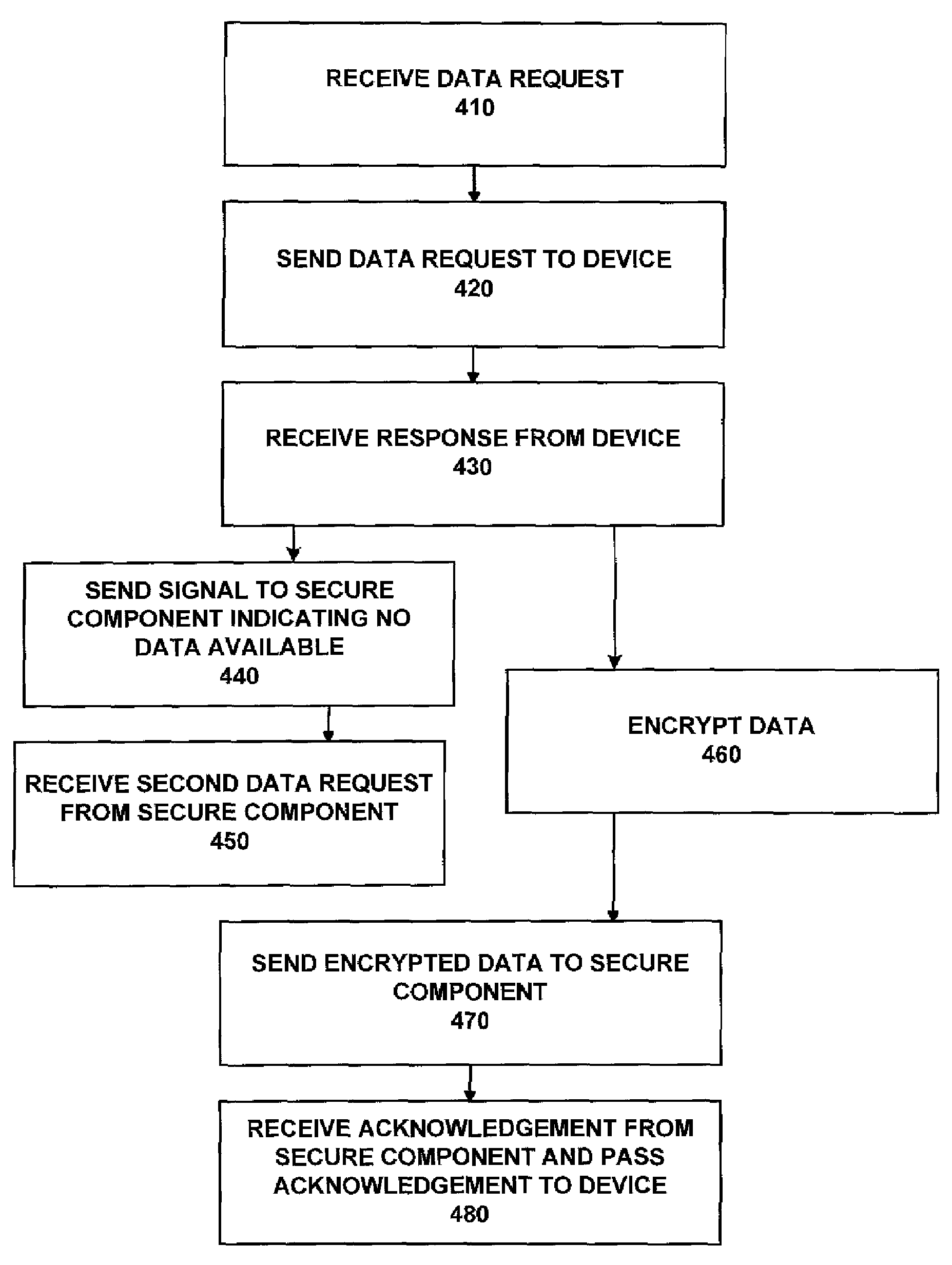
InactiveUS7469343B2Ensure transparencyUnauthorized memory use protectionHardware monitoringComputer moduleProtocol for Carrying Authentication for Network Access
A security module and method implements data requests from a USB or other similar device, in which a secure component can communicate securely with a device without modifying the underlying USB bus protocol, or the device, even where the software controlling the bus is untrusted. A security module (physically separate or integrated into a device or hub) intercepts data being sent from device to secure component in response to a data request. A “not acknowledged” signal is sent to the secure component, and the data is encrypted. The next data request is intercepted, and the encrypted data sent in response. The acknowledgement from the secure component to the device is allowed to reach the device. In order to handle a setup request, an allow command is sent to the security module, which includes the encrypted and unencrypted setup command. If an encryption check is successful, a setup command sent to the device (via the security module) is allowed to reach the device.
Owner:MICROSOFT TECH LICENSING LLC
Apparatus and Method For Securing Data on a Portable Storage Device
InactiveUS20090055655A1Secure and convenientDigital data processing detailsUnauthorized memory use protectionPasswordData storing
A portable storage device including a microprocessor and a secure user data area, the microprocessor operable to perform on-the-fly encryption / decryption of secure data stored on the storage device under a user password, the microprocessor also operable to exclude access to the secure user data area unless the user password is provided.
Owner:WESTERN DIGITAL ISRAEL LTD
VPN system based on dynamic encryption algorithm
ActiveCN1972237AEnhanced defenses against hackers attacking its encrypted systemsImprove efficiencyUser identity/authority verificationNetworks interconnectionRandom combinationPrivate network
This invention relates to VPN system based on dynamic code formula, which uses keys, chips and network technique and designs one set of dynamic symmetric code formula to make each formula with different virtual special networks in each data coding, wherein, each code system only adopts one symmetric code keys such as network keys, pack keys and channel keys through establishing code formula to generate formula and symmetric key generation formula.
Owner:北京中电数安科技有限责任公司
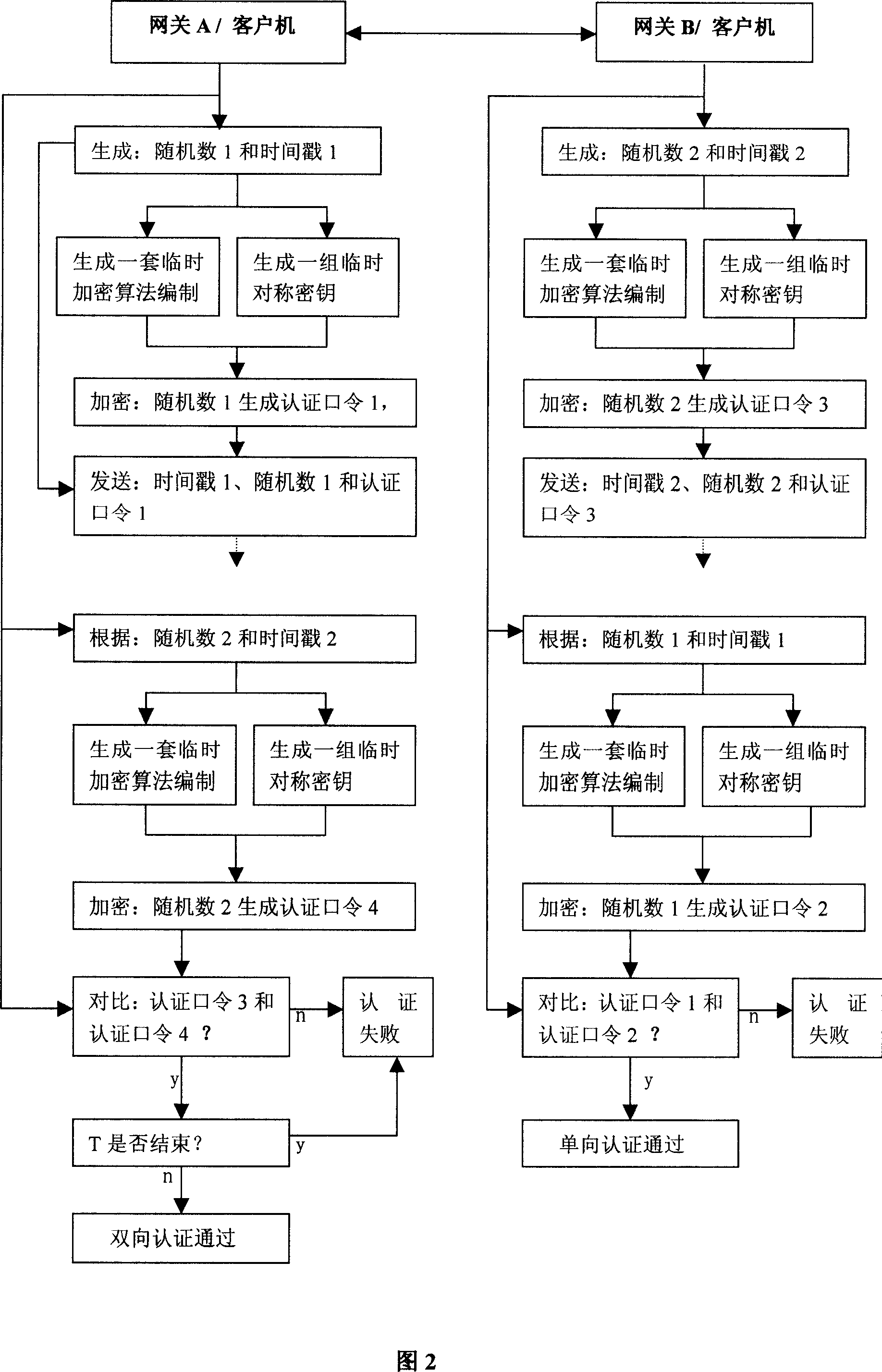
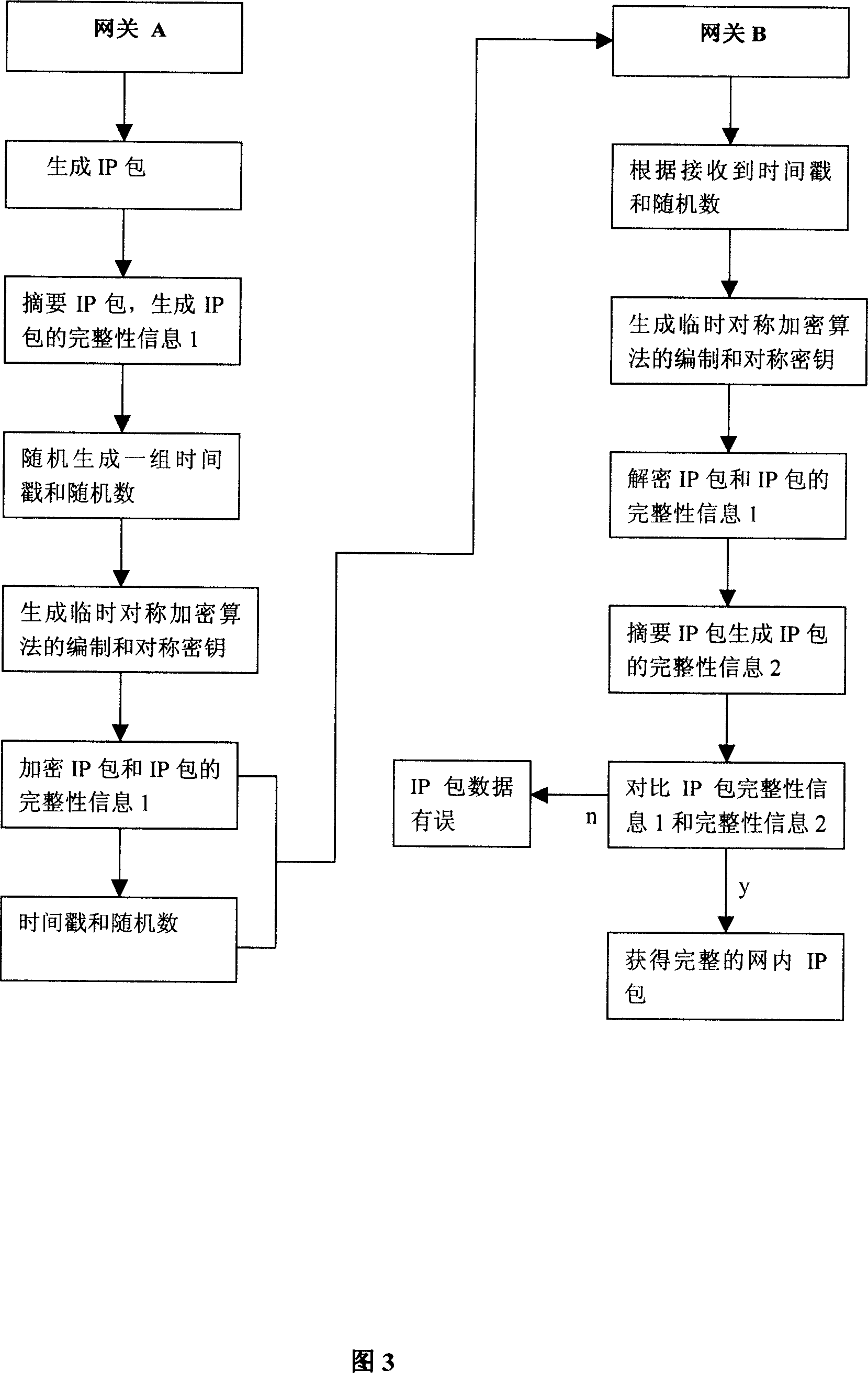
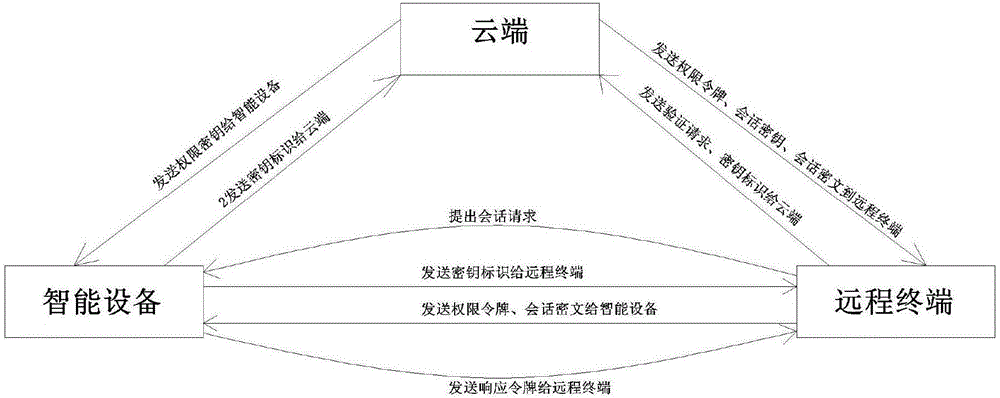
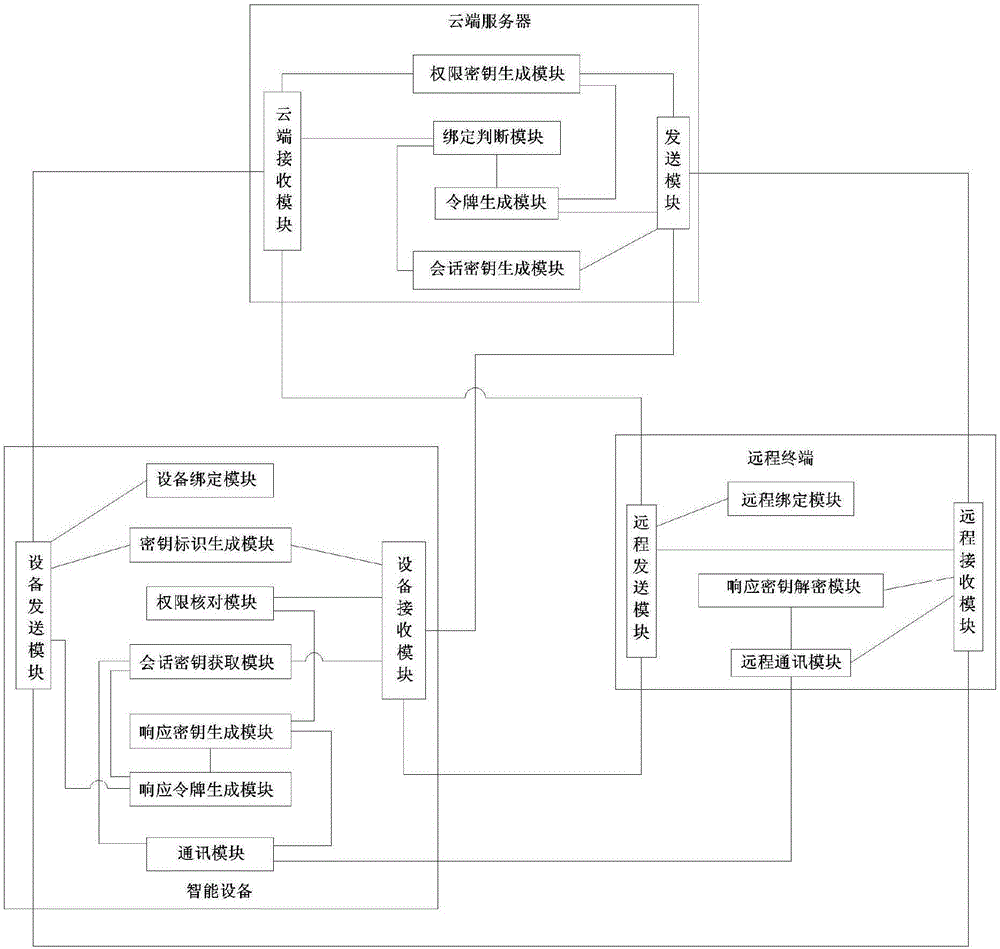
Method and system for implementing dynamic encryption communication between intelligent device and remote terminal
The present invention relates to the technical field of implementing a communication between an intelligent device and a remote terminal using a dynamic key, in particular to a method for implementing a dynamic encryption communication between an intelligent device and a remote terminal. The method includes: a cloud sever respectively establishes communication channels with an intelligent device and a remote terminal, so that the cloud sever, the intelligent device and the remote terminal communicate with each other by the channels; the intelligent device appoints a first-level encryption rule with the cloud sever and the remote terminal; after the remote terminal passes verification according to the first-level encryption rule, the intelligent device appoints a dynamic encryption rule with the cloud sever and the remote terminal; and the intelligent device performs an encryption communication with the remote terminal according to the dynamic encryption rule. A manner of using dynamic keys is disclosed in this method, to facilitate generating a transmission key dynamically according to this protocol when a communication is performed, thereby guaranteeing that keys used during the communication transmission between the intelligent device and different remote terminals are different keys, and avoiding hidden dangers existing in the traditional data transmission process.
Owner:北京同余科技有限公司
Password dynamic enciphering inputmethod of public emipering mode
InactiveCN1599313ARealize dynamic generationNot afraid of leaksMultiple keys/algorithms usageUser identity/authority verificationPasswordComputerized system
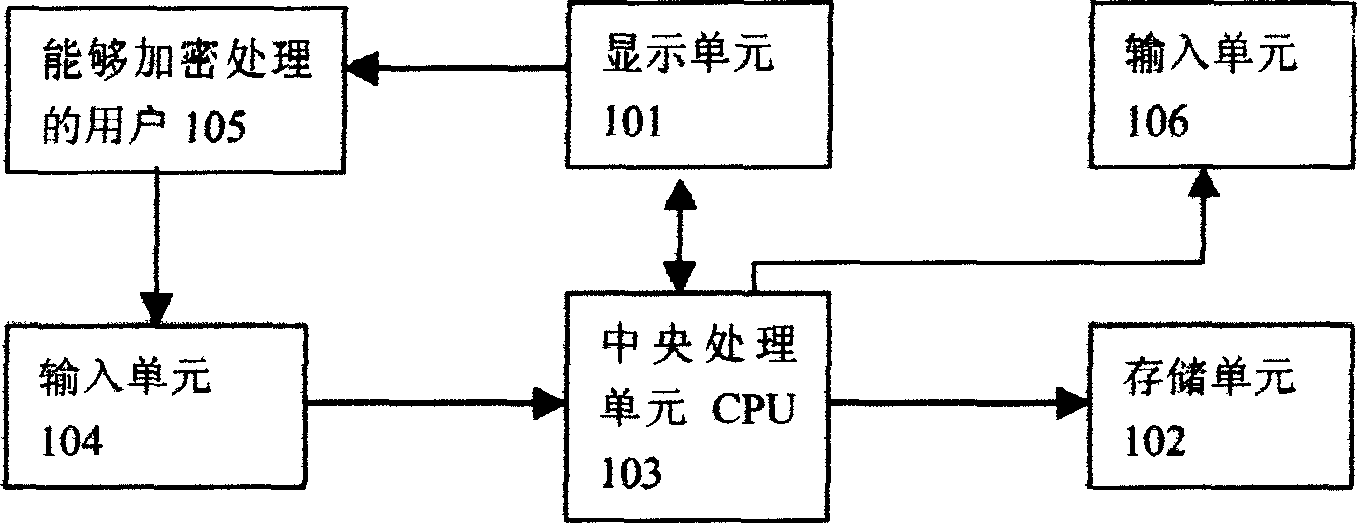
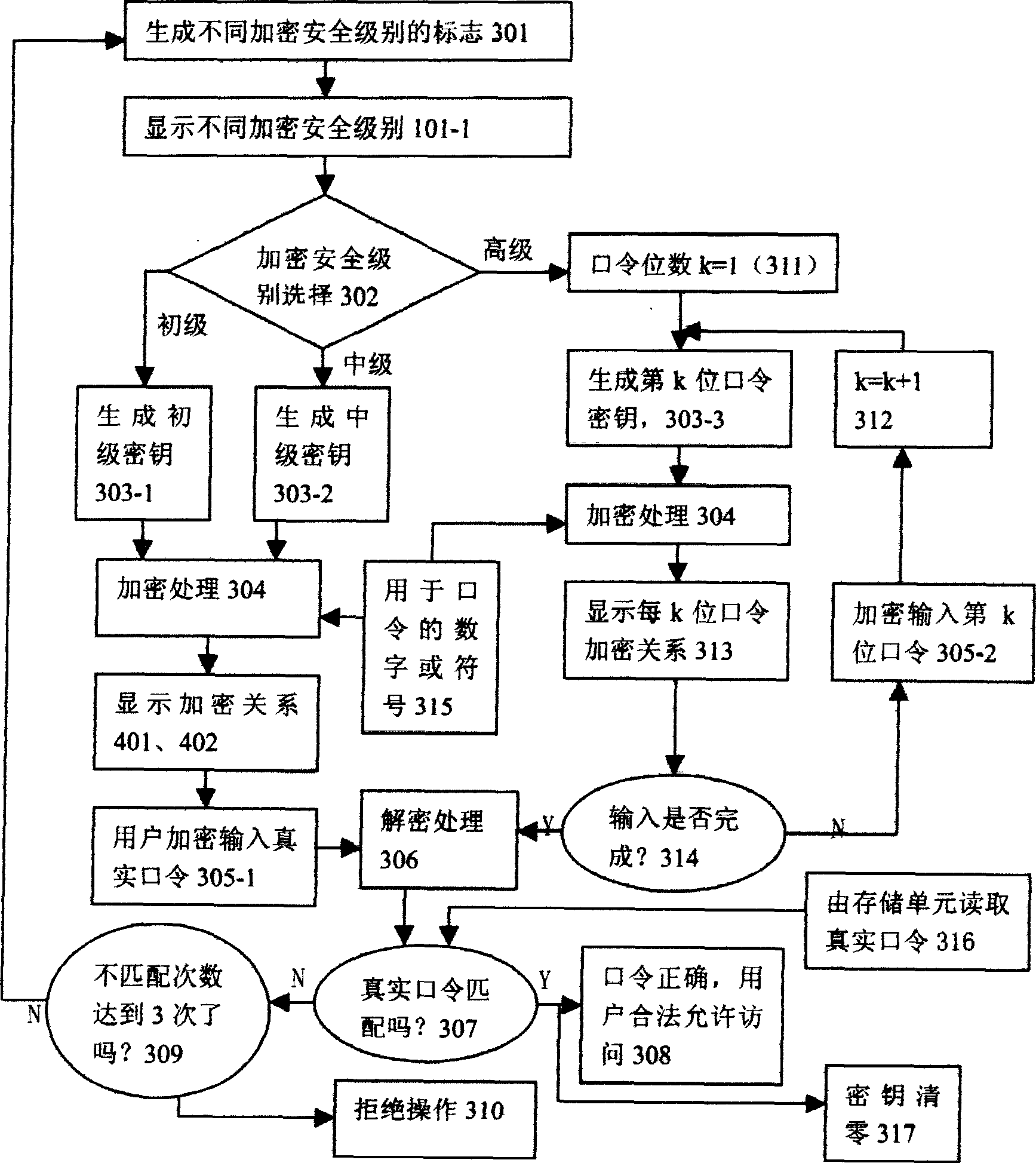
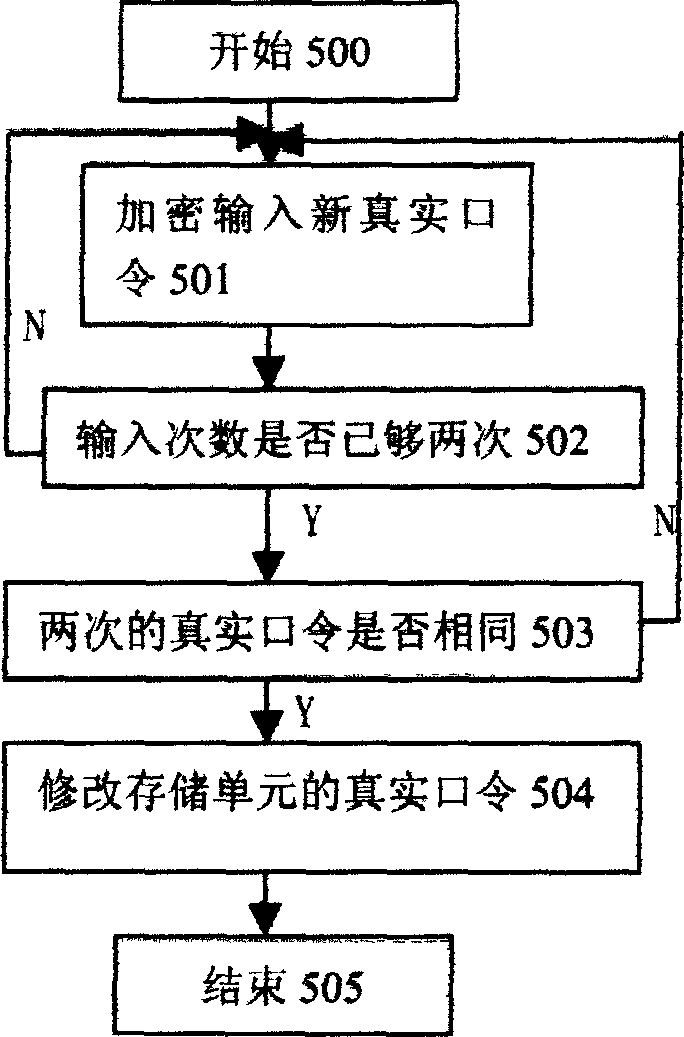
An electronic random numeral generator generates three ciphered safe levels and a random unpredictable dynamic key to be input to the real password, a user selects primary, middle and high three different levels selected by user, an input unit transmits the request information to CPU which generates dynamic key according to the levels and ciphers all numerals and symbols used in the password to be displayed to the user together with the ciphered numerals and symbols in light of this key and their relationship, the user transmits the ciphered real password to the CPU by the input unit to be deciphered and sent out by an output unit. If the password is right, it is allowed to access, if not, it is refused, the memory unit is used for storing real password and corrected real password.
Owner:常志文
Method and device for the secure authentication and execution of programs
ActiveUS20160261592A1Key distribution for secure communicationPlatform integrity maintainanceComputer hardwareData stream
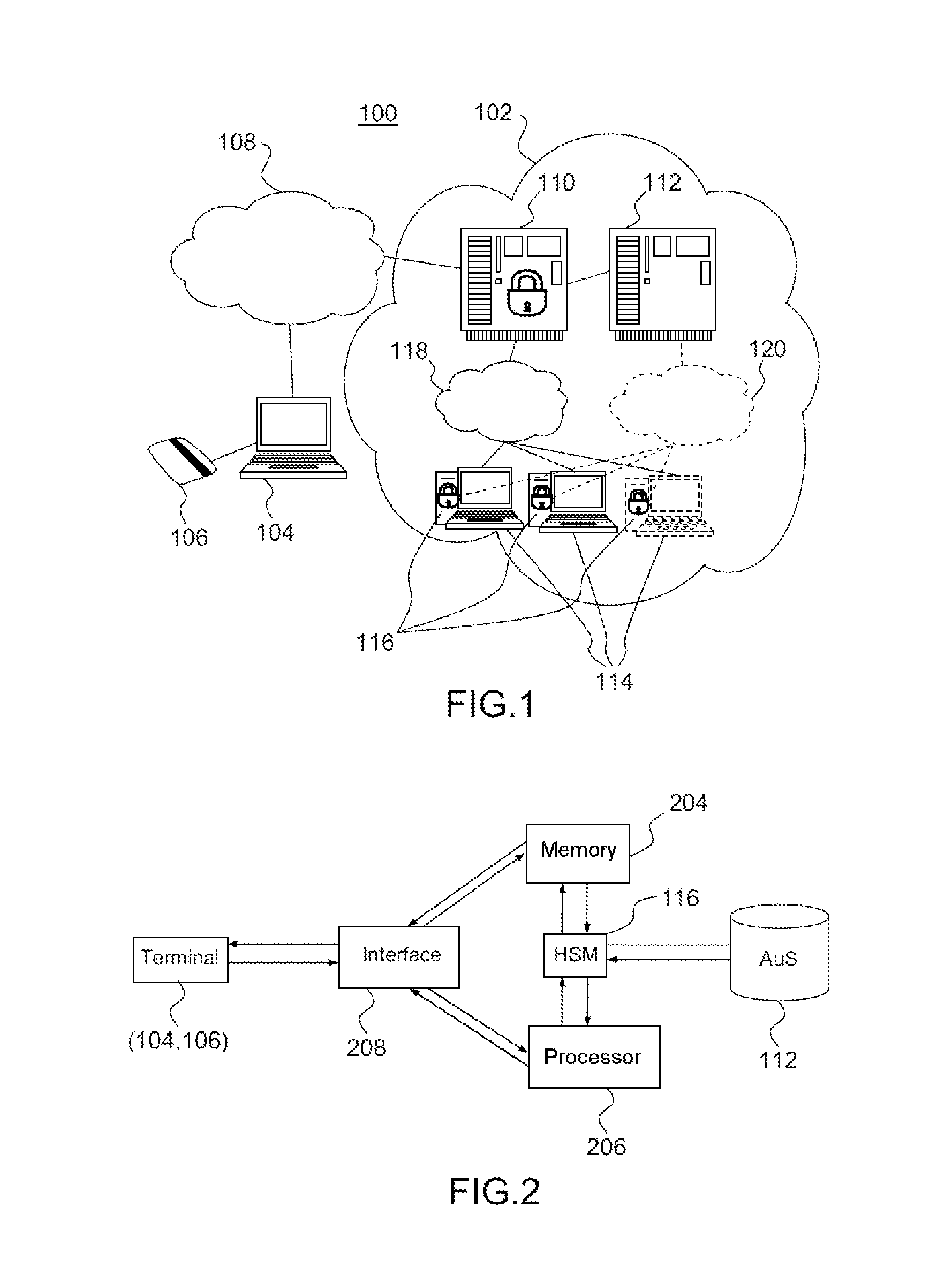
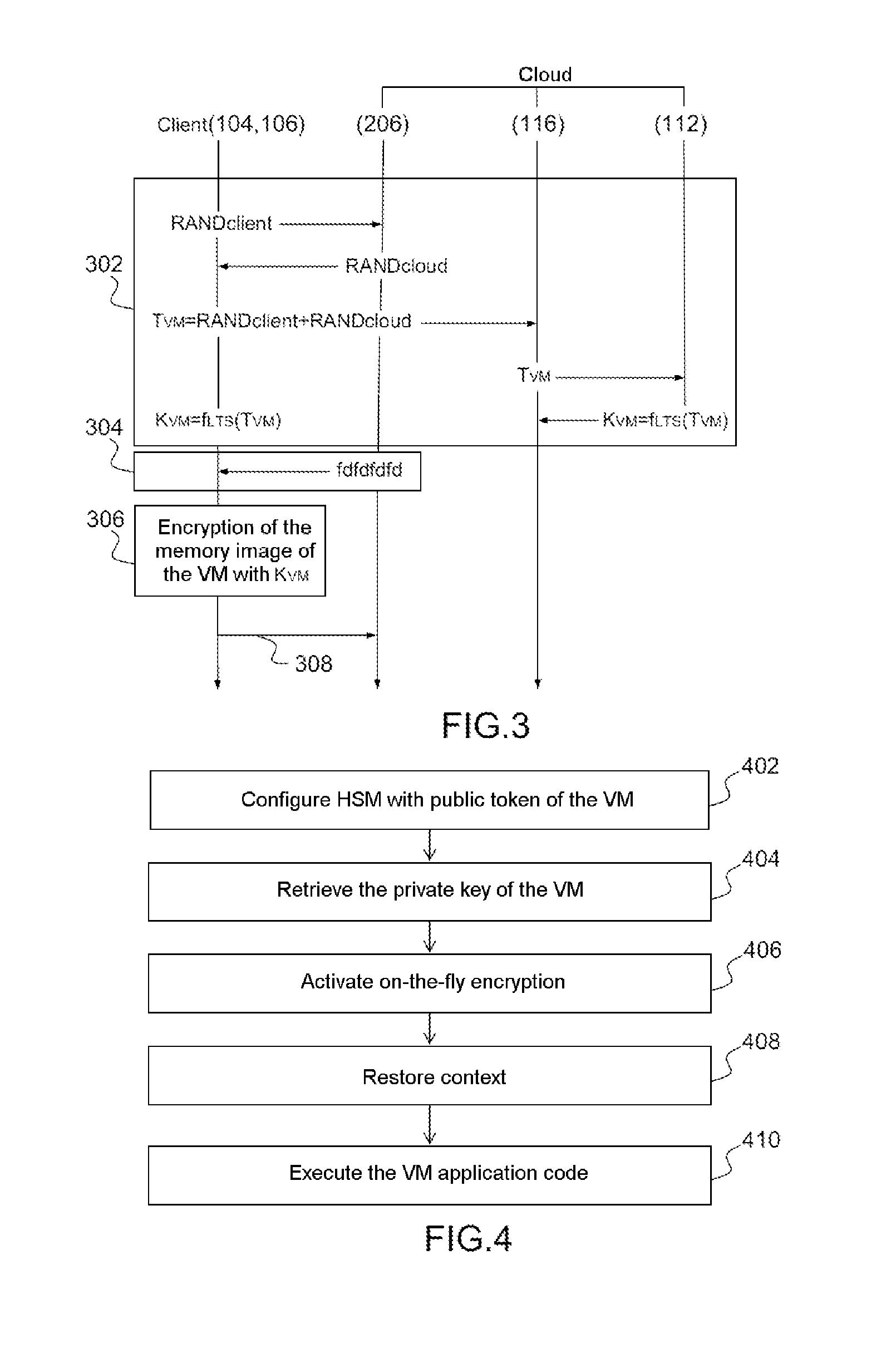
A device and a method for encrypting a virtual machine by on-the-fly encryption and decryption of the memory is described. The device comprises hardware and software elements, including a hardware security module for executing, in response to data read / write requests, on-the-fly encryption and decryption operations of the data stream associated with an encrypted memory image. The device and the method are particularly suited to allowing the secure authentication and execution of programs in the context of the infrastructure as a service layer of the cloud computing model.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
Multi-stage domain protection method and system based on information security level identifiers
ActiveCN102999732ARealize dynamic encryption/decryptionEnable fine-grained accessDigital data protectionInternet privacyDocument Identifier
The invention provides a multi-stage domain protection method and a multi-stage domain protection system based on information security level identifiers. Dynamic encryption / decryption of confidential documents is realized on the basis of security level identifiers including a creator identifier, a document identifier and a domain security level identifier, so that fine-grained access of validated users is realized, and the problem of information disclosure threat existing in a series of processes including generation, access, circulation and destruction of information of different security levels is solved.
Owner:FUCHUN COMM
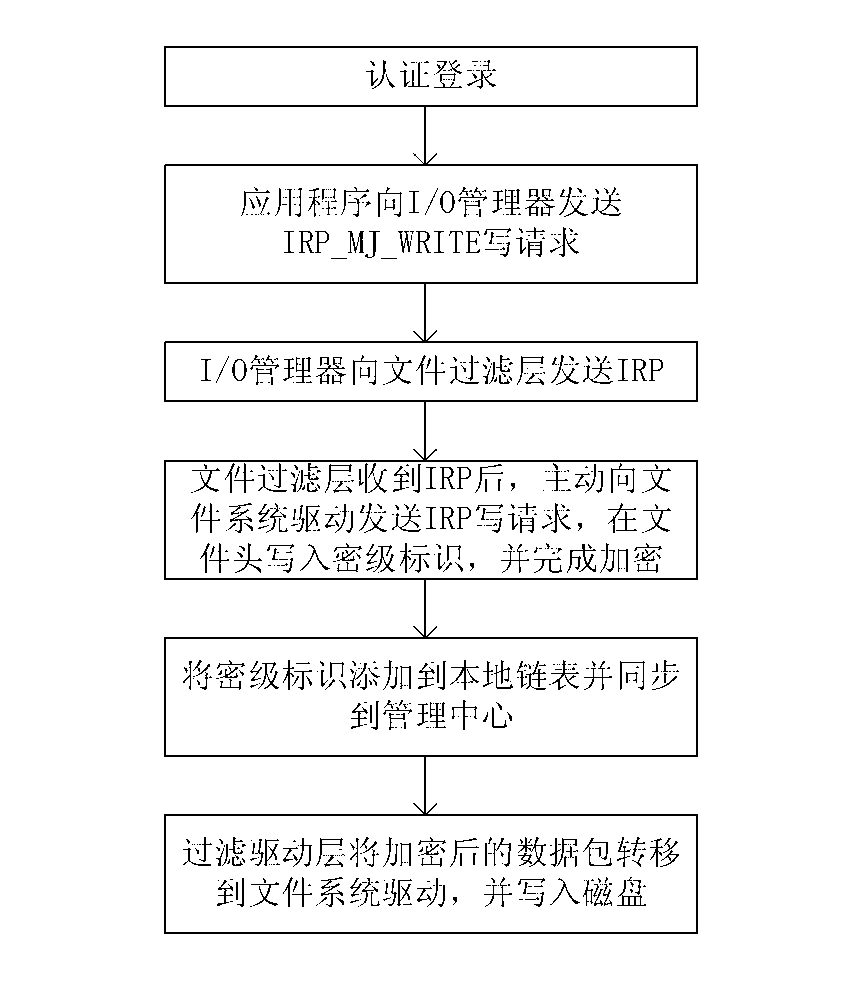
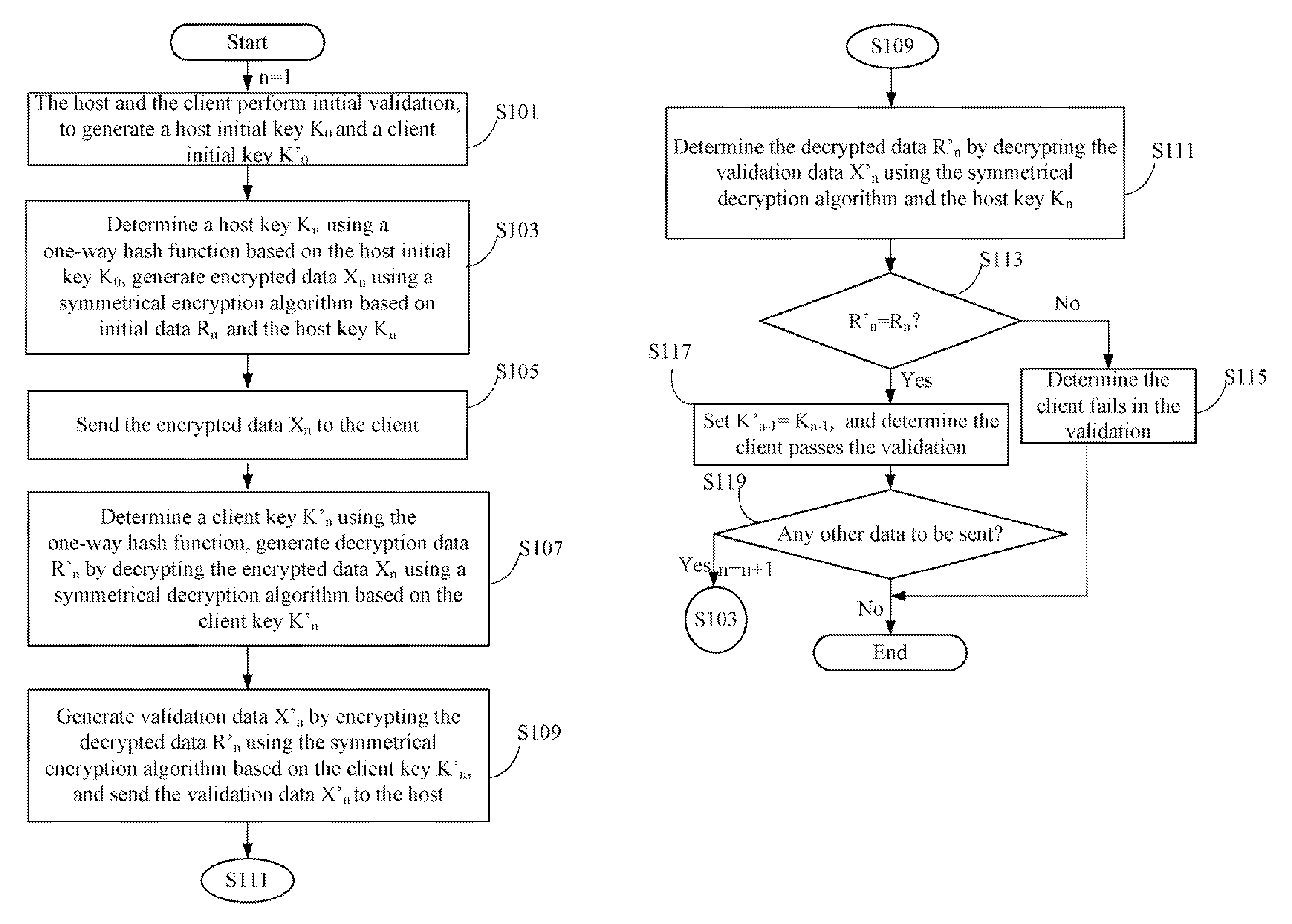
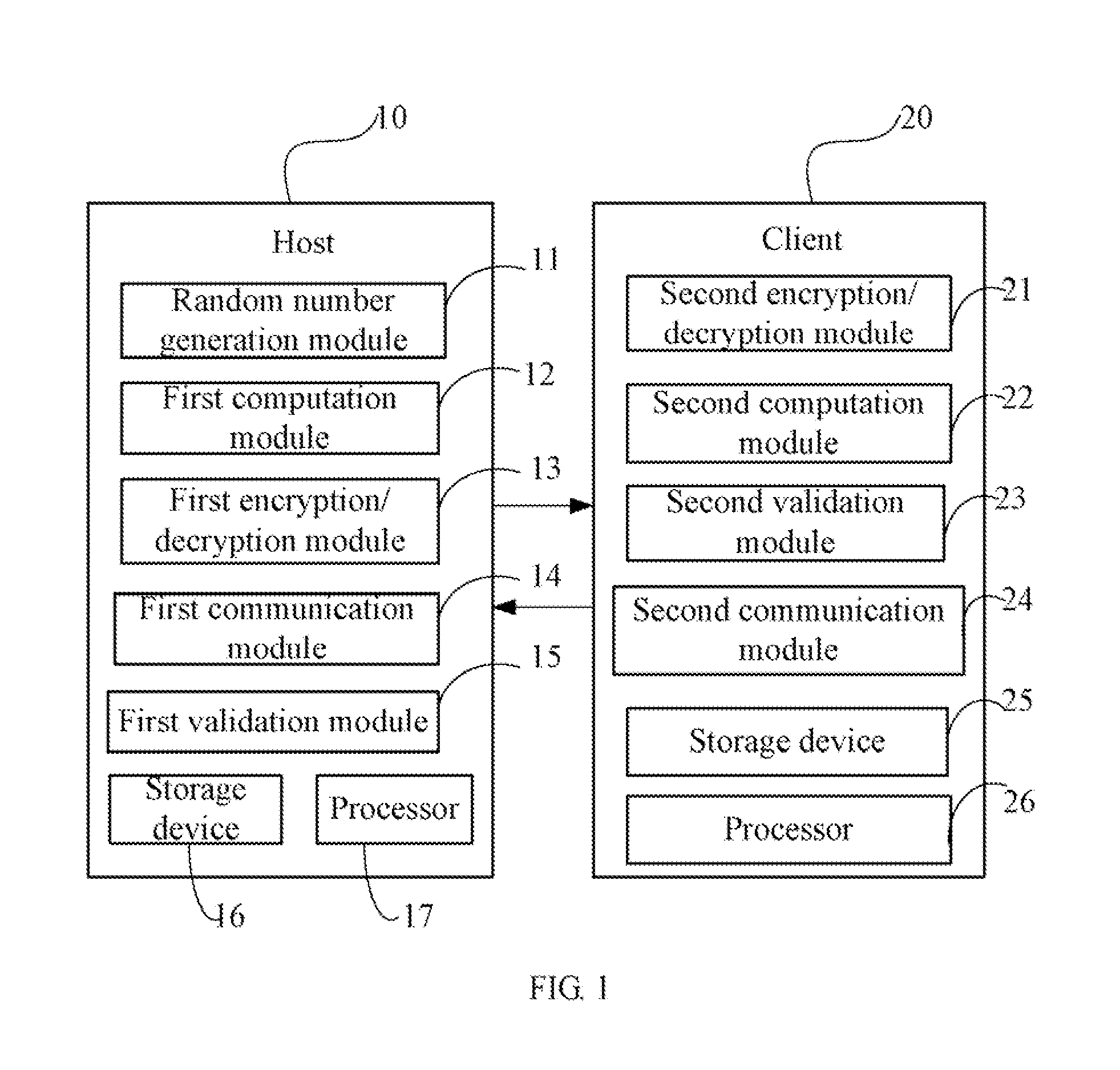
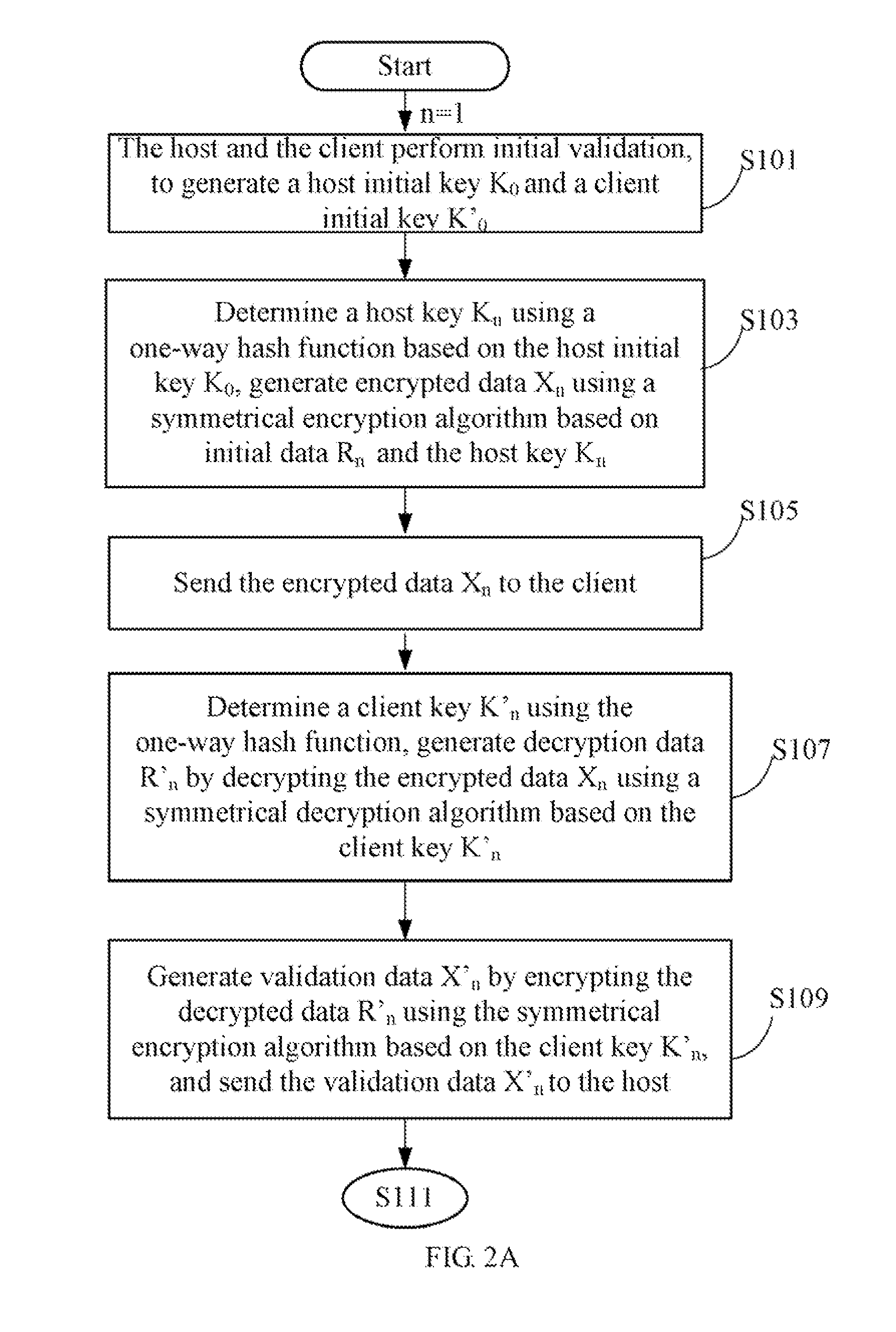
Data security protection method
InactiveUS20120102323A1Digital data processing detailsUser identity/authority verificationHash functionOriginal data
A data security protection method generates dynamic encryption keys and dynamic decryption keys for a host and a client during data transmission between the host and the client. The host stores a host initial key K0, and determines a host key Kn using a one-way hash function based on the host initial key K0. The client stores a client initial key K′0, and determines a client key K′n using the one-way hash function based on the client initial key K′0. Original data Rn is encrypted as encrypted data Xn using the host key Kn before being sent to the client. The client decrypts the encrypted data Xn using the client key K′n, to obtain the original data Rn.
Owner:CLOUD NETWORK TECH SINGAPORE PTE LTD
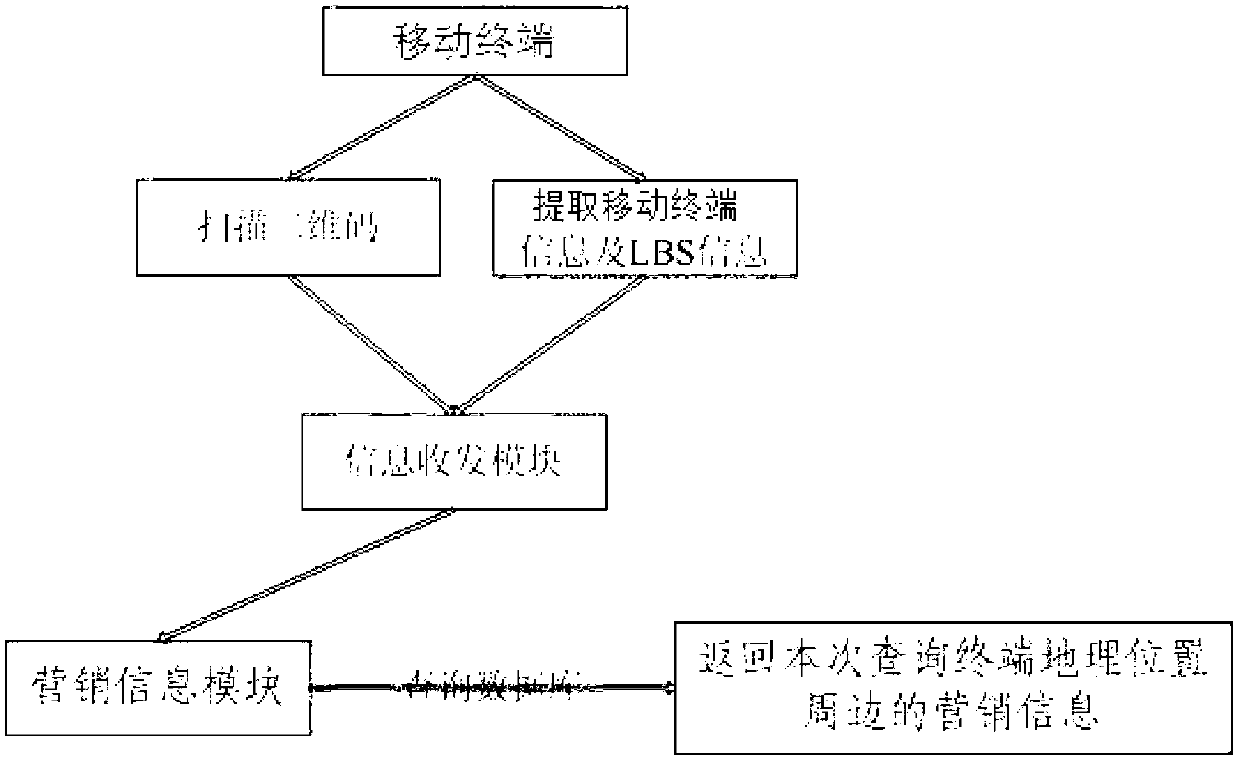
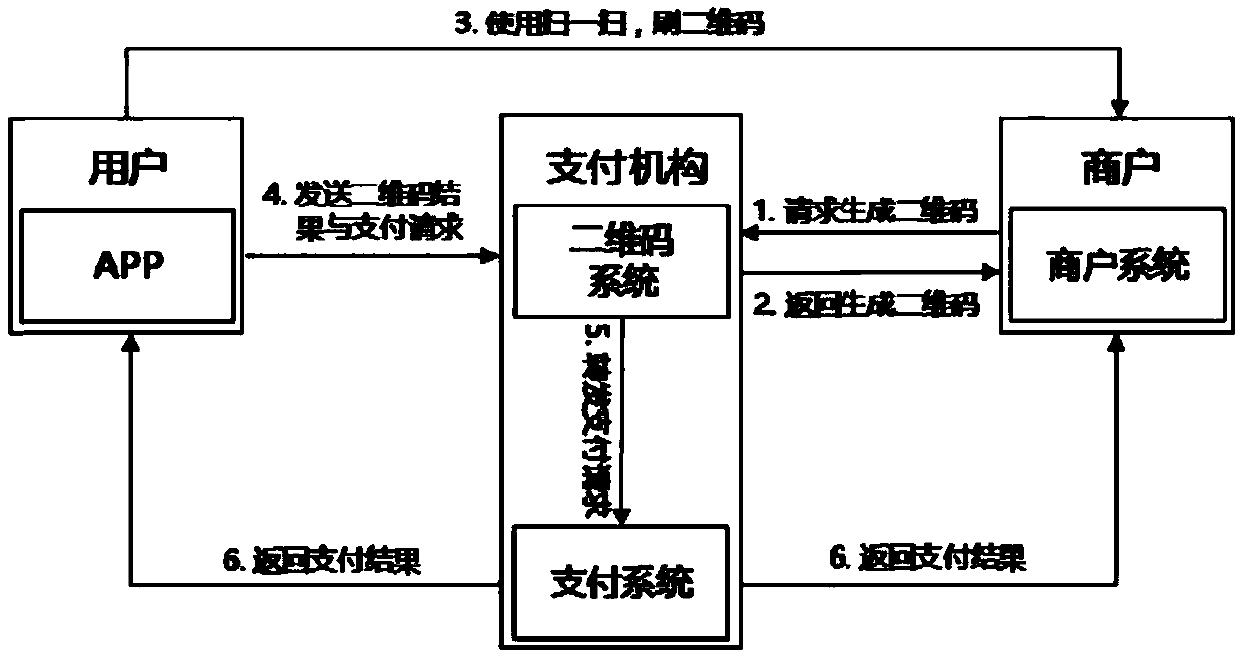
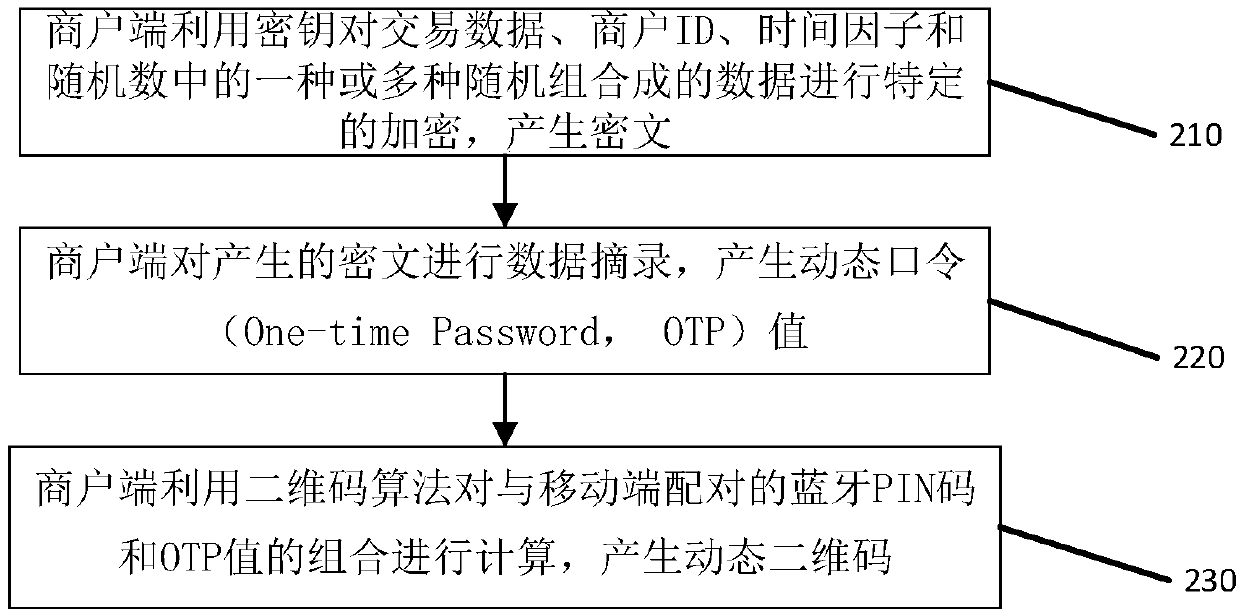
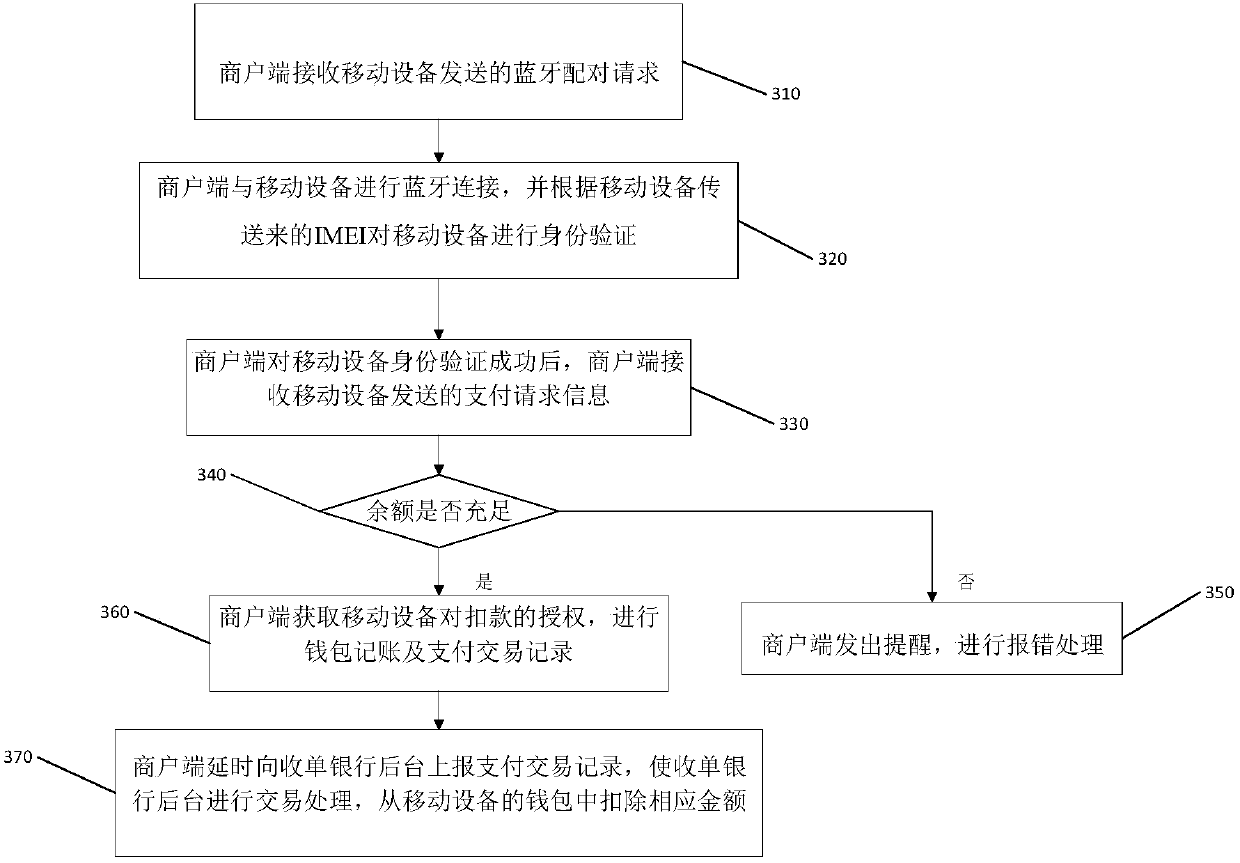
Mobile payment method and checkout terminal thereof
The invention discloses a mobile payment method and a checkout terminal thereof. The method comprises the steps of encrypting the data of one or the combination of more factors including transaction data, merchant ID, time factor and random number by a commercial tenant terminal based on a secret key so as to generate the ciphertext; making the extracts of the ciphertext by the commercial tenant terminal and generating a dynamic password; calculating the bluetooth PIN code and the dynamic password of the commercial tenant terminal by the commercial tenant terminal based on a two-dimensional code algorithm, and generating a dynamic two-dimensional code. According to the invention, the safety degree of the payment is higher. The two-dimensional code adopts the dynamic encryption technology,and is automatically updated once every minute. Therefore, the fund security of commercial tenants is guaranteed. Meanwhile, the commercial tenant terminal and a consumer terminal can adopt the double-offline transaction mode. When the commercial tenant terminal is in the offline state, a consumption bill can be uploaded to a card-issuing single-line background in time. The fund security of commercial tenants is guaranteed.
Owner:HENGBAO
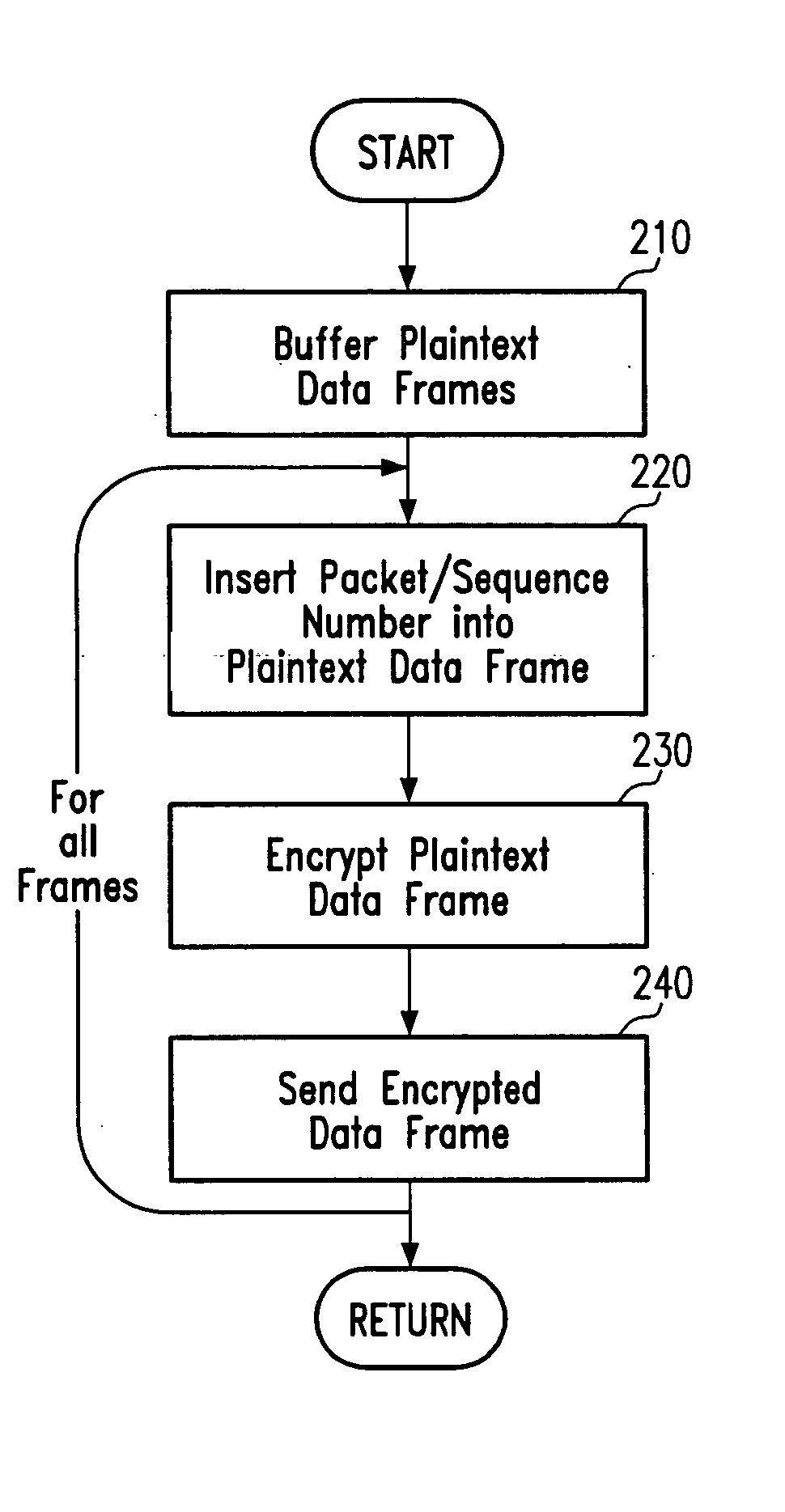
On-the-fly encryption/decryption for WLAN communications
ActiveUS20050190919A1Improve data throughputReduce the cushioning forceUnauthorised/fraudulent call preventionEncryption apparatus with shift registers/memoriesSecure communicationWireless lan
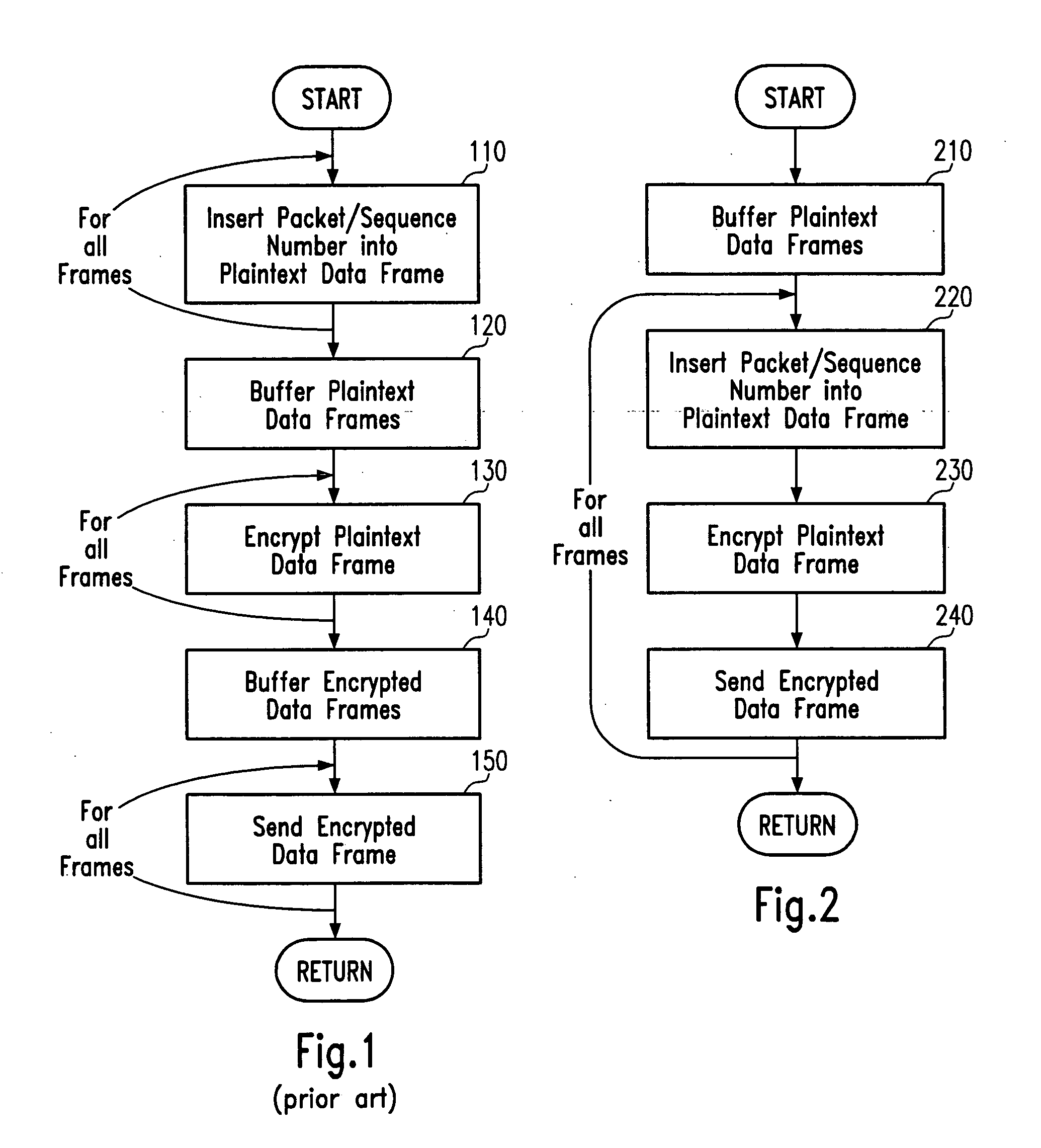
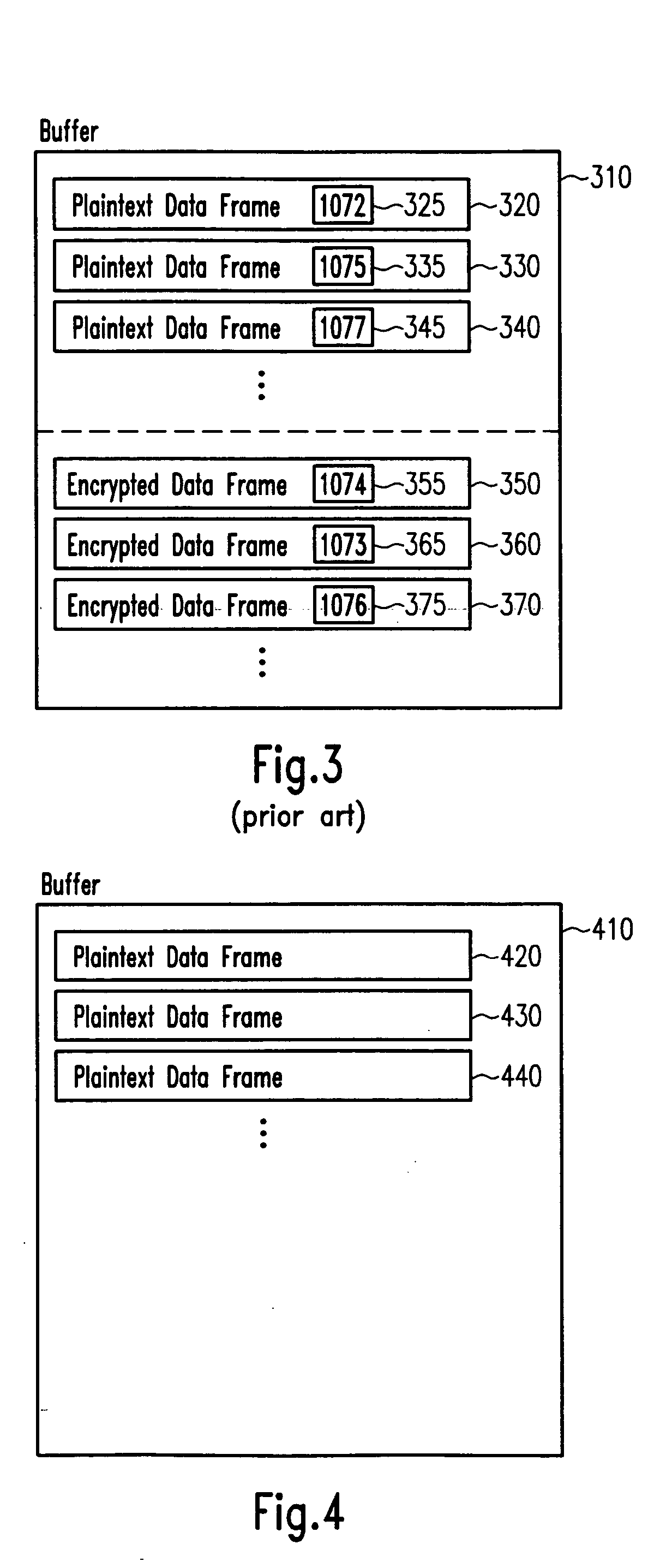
A communication device for performing cryptographically secured communication in a WLAN (Wireless Local Area Network) network is provided that comprises a security enhancement unit and a MAC (Medium Access Control) unit. The security enhancement unit is for encrypting plaintext data frames into encrypted data frames and / or decrypting encrypted data frames into plaintext data frames. The MAC unit is for managing communication between communication devices within the WLAN network by coordinating access to a shared wireless communication medium through which communication signals are transmitted. The security enhancement unit and the MAC unit are adapted to perform an on-the-fly encryption process and / or on-the-fly decryption process thereby exchanging the encrypted data frames without buffering the encrypted data frames after encryption or prior to decryption, respectively. The embodiments may provide an improved encryption / decryption architecture including an on-chip memory for performing on-the-fly encryption and / or on-the-fly decryption in the framework of 802.11i security enhancement.
Owner:GLOBALFOUNDRIES US INC
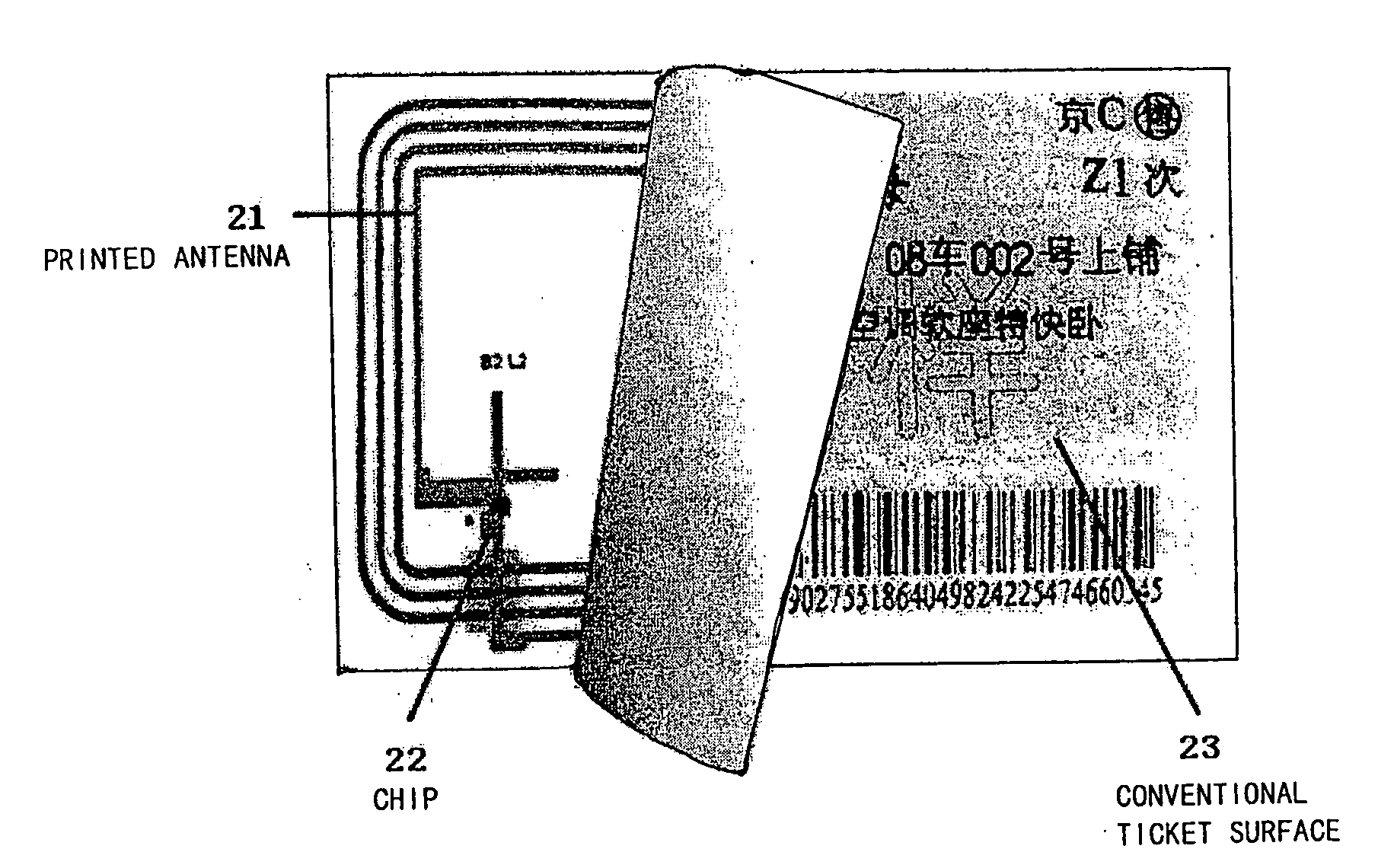
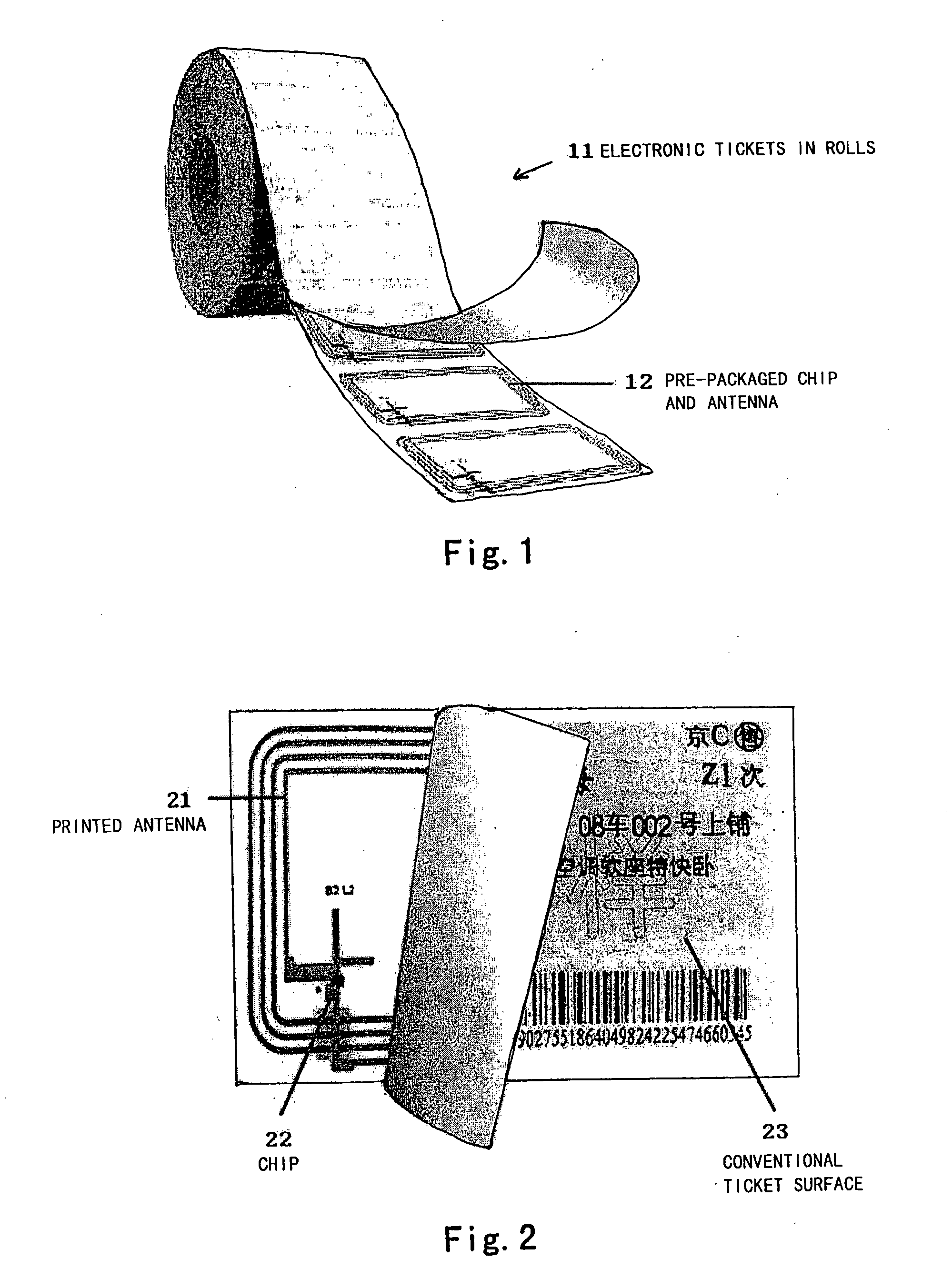
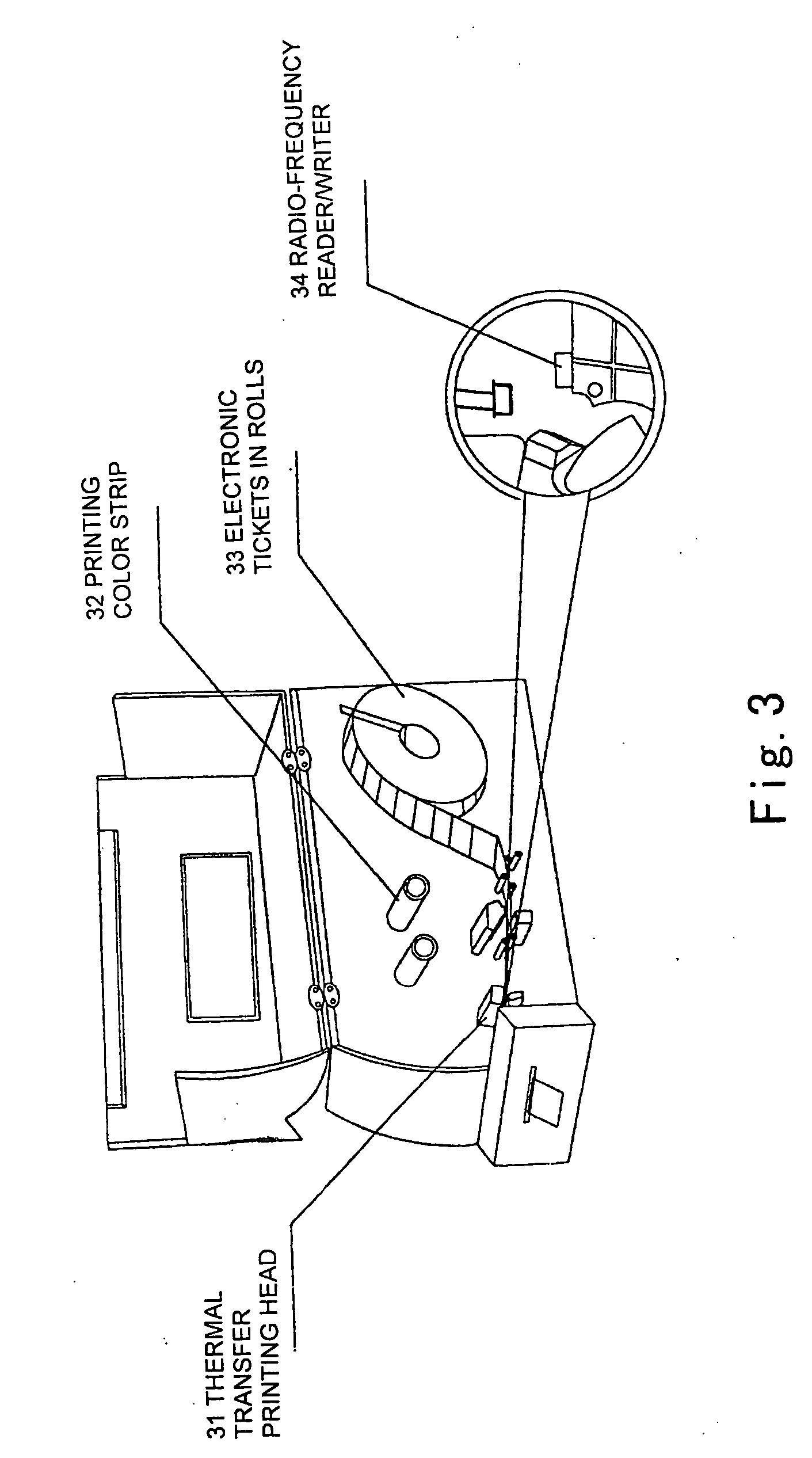
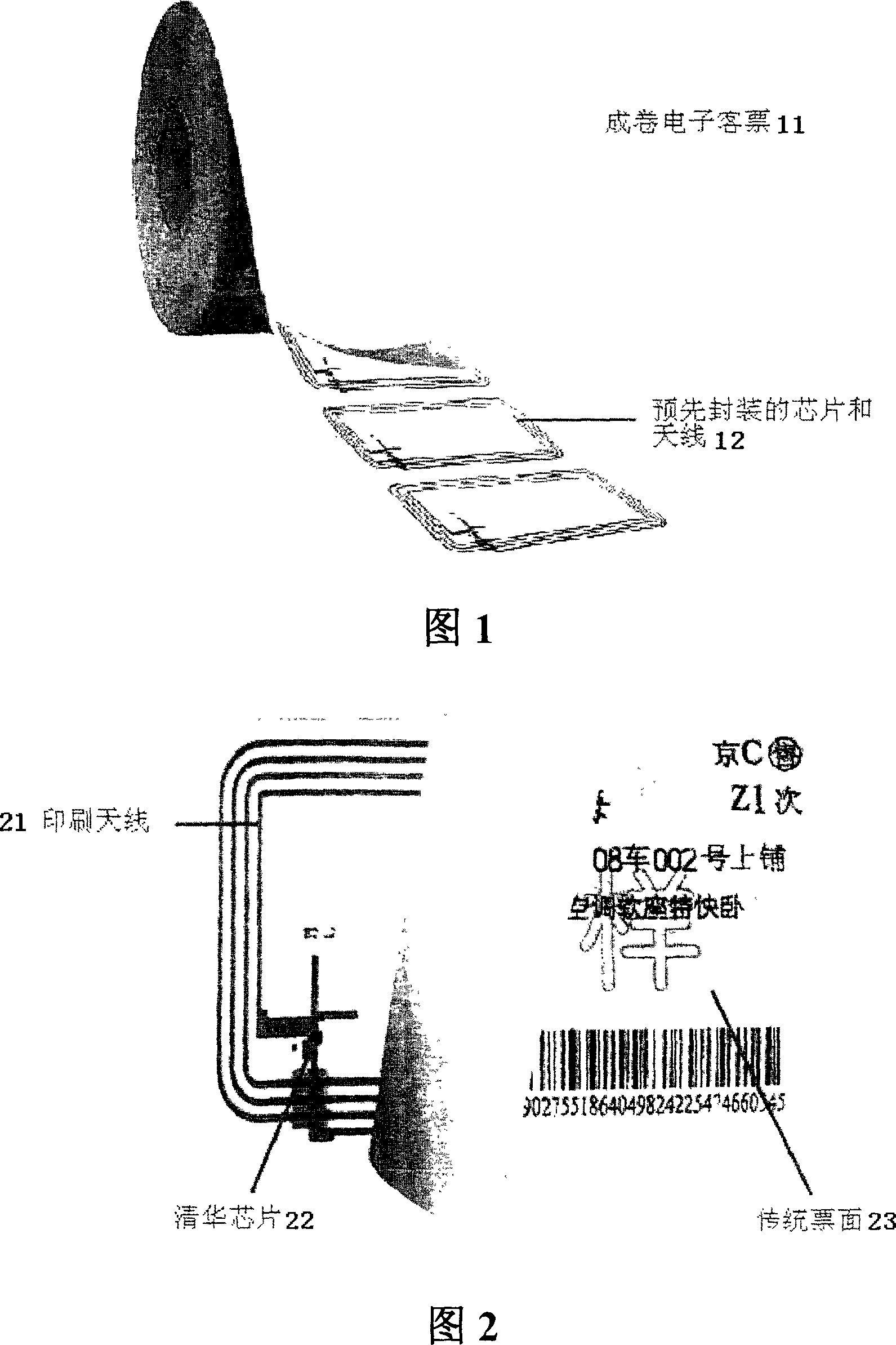
Non-contact paper-based electronic ticket based on electronic tag techniques
InactiveUS20070158412A1Improve sign-in efficiencyImprove anti-counterfeitingCo-operative working arrangementsIndividual entry/exit registersPaper basedComputer science
The present invention provides an electronic ticket compatible with the existing railway paper tickets, which comprises two layers of paper media where an antenna and a chip are buried in advance and is characterized in that dynamic encryption information is written into said chip in advance and has a check code associated with a serial number for anti-counterfeiting; at a ticket selling terminal, ticket information will be written into said chip, and such ticket information in said chip can be rewritten many times; and said antenna is used for receiving RF signals and transmitting them to said chip.
Owner:TSINGHUA UNIV +1
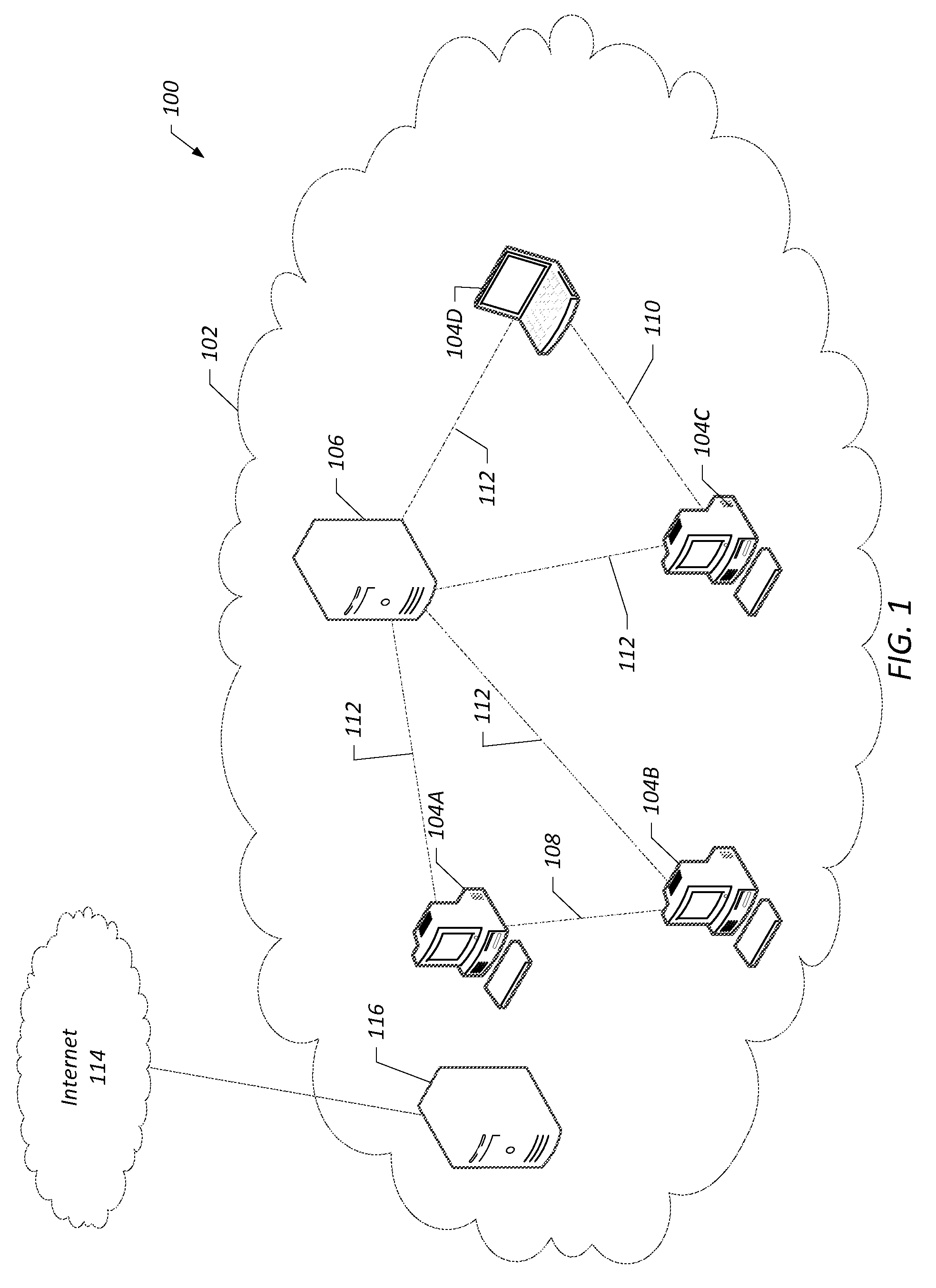
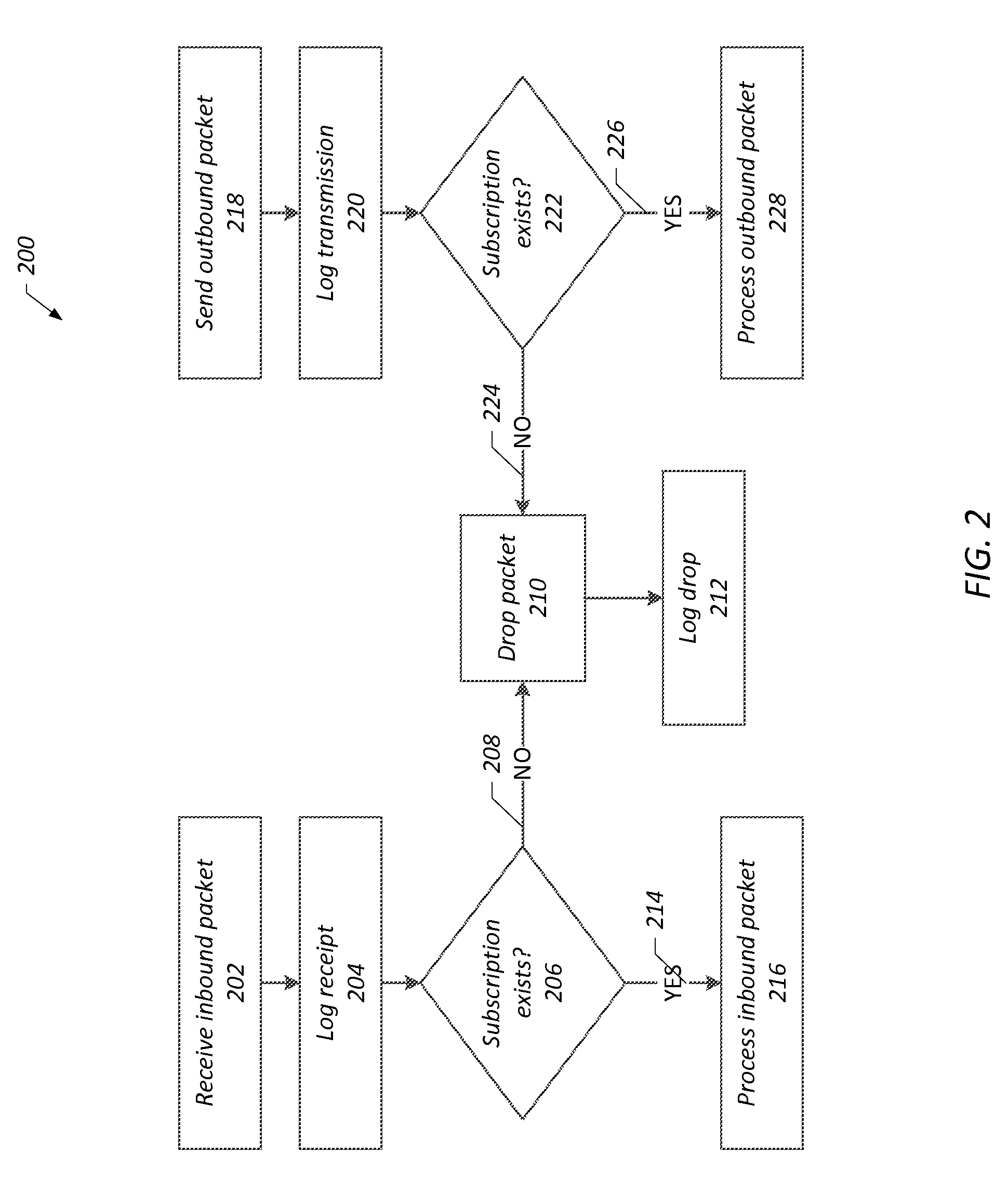
Systems, methods, and computer-readable media for secure digital communications and networks
ActiveUS20130268762A1Multiple keys/algorithms usageUser identity/authority verificationSecure communicationKey size
Provided are system, methods, and computer-readable media for systems, methods, and computer-readable media for secure digital communications and networks. The system provides for secure communication between nodes through the use of a subscription between two nodes based on unique identifiers that are unique to each node, and communication between nodes without a subscription may be blocked. Additionally, secure communications between a node and a remote node are dynamically encrypted using asymmetric and symmetric encryption. The encryption algorithms and key lengths may be changed at each subsequent negotiation between a node and a remote node.
Owner:STT
Non-contact paper base electronic passenger ticket based on electronic label technology
ActiveCN1987903AResistant to foldingWear-resistantDigitally marking record carriersCo-operative working arrangementsTicketEmbedded system
The invention provides an e-ticket compatible with the existing railway votes, it includes: two layers paper medium. An antenna and chip are pre-embedded into the above paper medium, its characteristics lies in that dynamic encryption information is written into the chip in advance and these information have the test code associated with a serial number, to be used in security. In the ticketing terminal, the passenger ticket information will be written to the chip, which can be rewritten many times. The said antenna can receive RF signals and transfer it to the chip.
Owner:TSINGHUA UNIV +1
Network access method and device
ActiveCN113347206AAchieve securityTo achieve the purpose of safetyMultiple keys/algorithms usageAccess methodEngineering
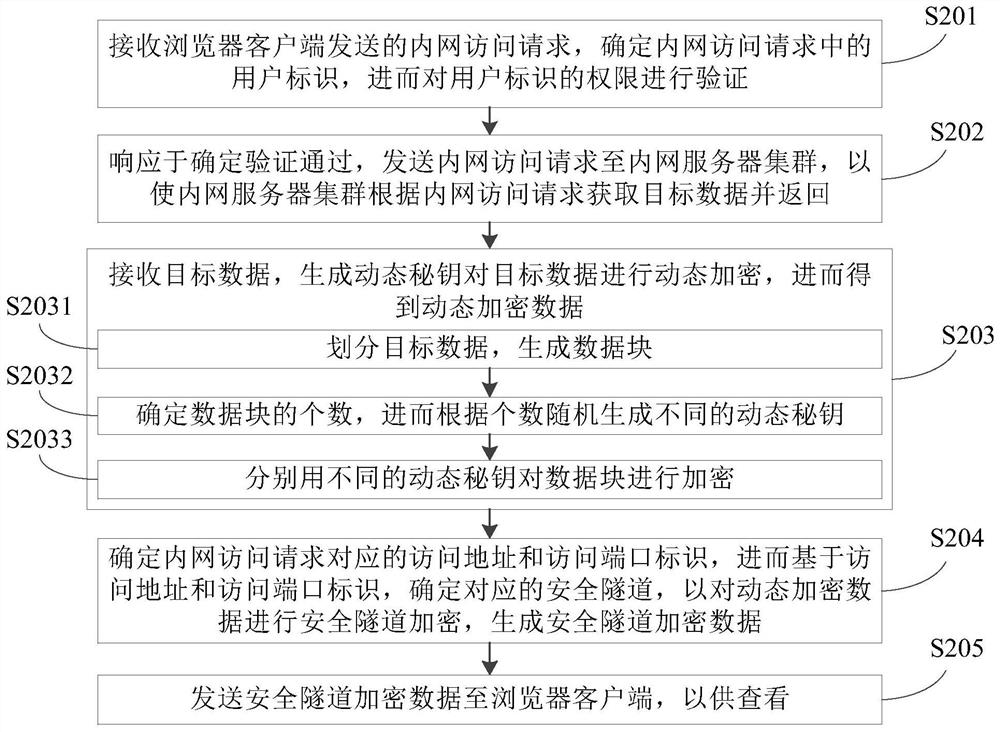
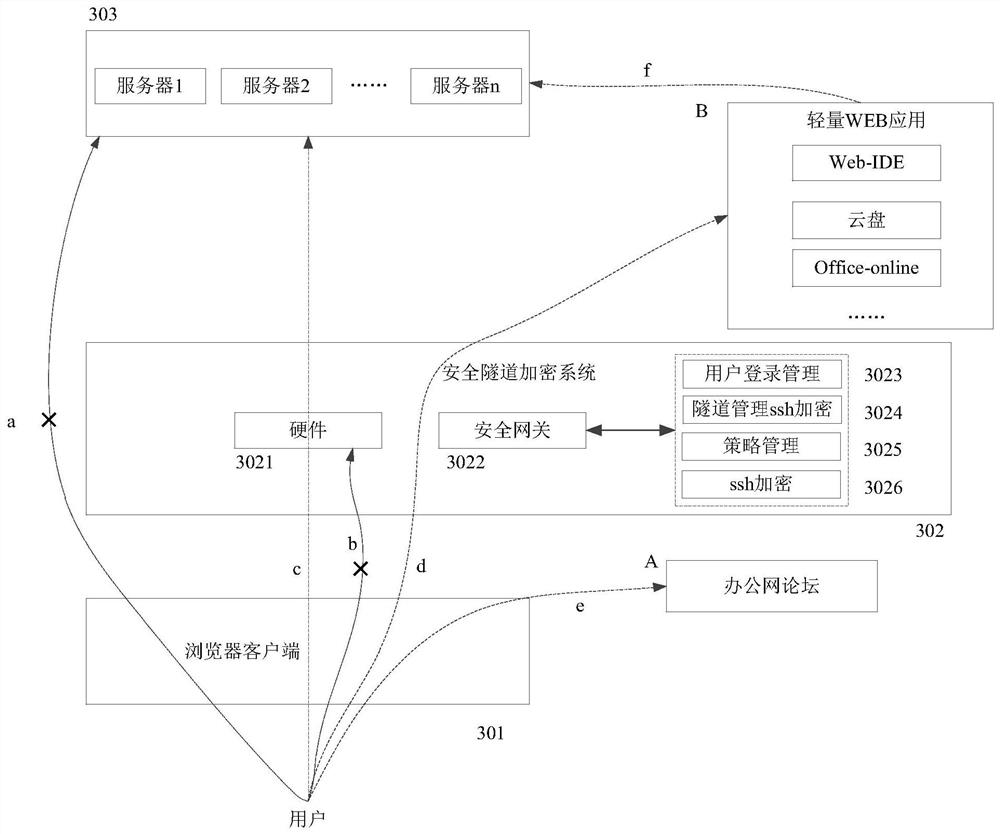
The invention discloses a network access method and device, and relates to the technical field of computers, and the method comprises the steps: receiving an intranet access request, determining a user identifier in the intranet access request, and verifying the authority of the user identifier; in response to determining that the verification is passed, sending an intranet access request to an intranet server cluster, so that the intranet server cluster obtains target data according to the intranet access request and returns the target data; receiving target data, and generating a dynamic secret key to dynamically encrypt the target data to obtain dynamic encrypted data; determining an access address and an access port identifier corresponding to the intranet access request, determining a corresponding secure tunnel based on the access address and the access port identifier, performing secure tunnel encryption on the dynamic encrypted data, and generating secure tunnel encrypted data; and sending the secure tunnel encrypted data to the browser client for viewing. When a user has a frequent internal and external network access requirement, the internal and external networks do not need to be switched frequently, and the purpose of information security is achieved at the same time.
Owner:CCB FINTECH CO LTD
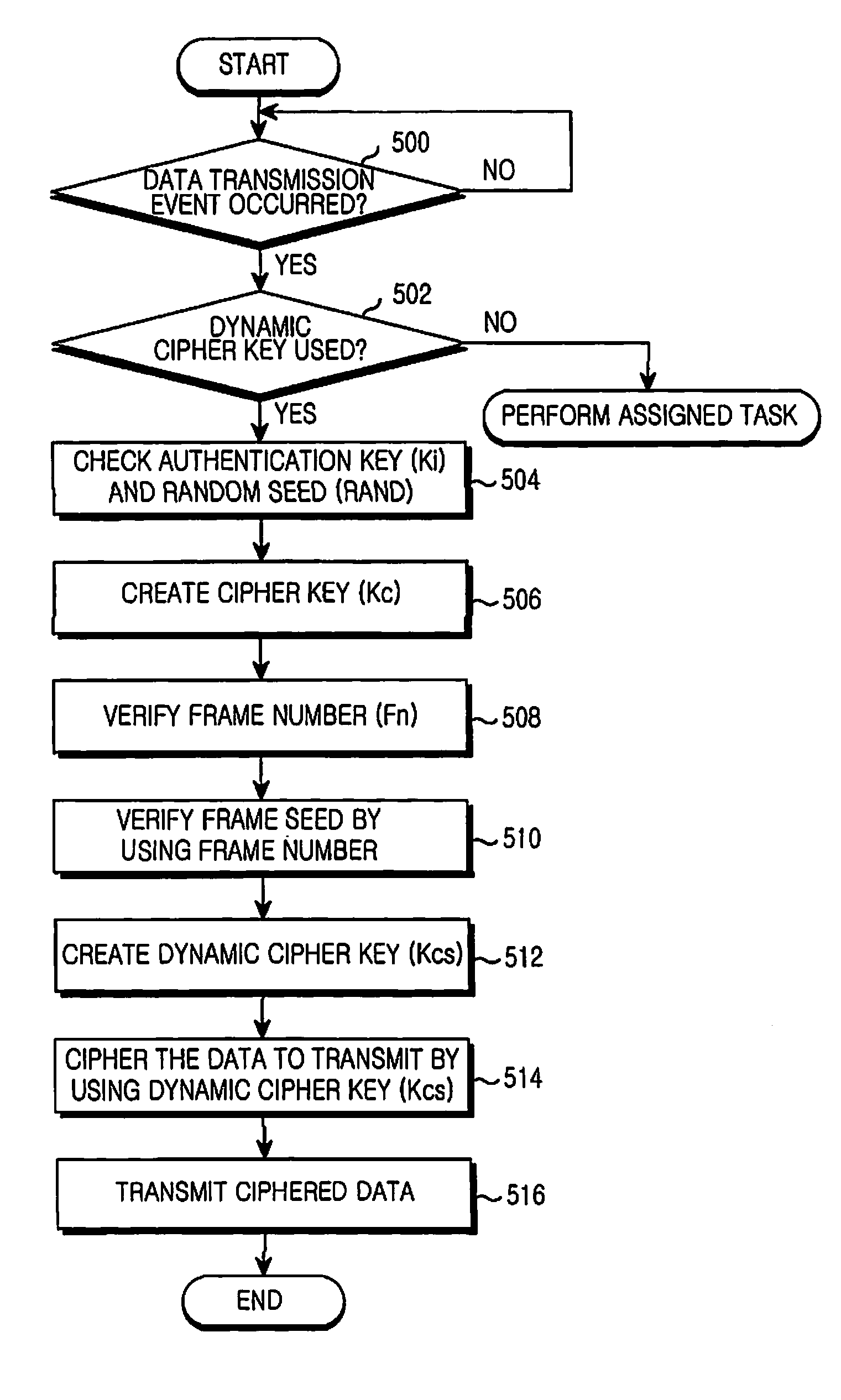
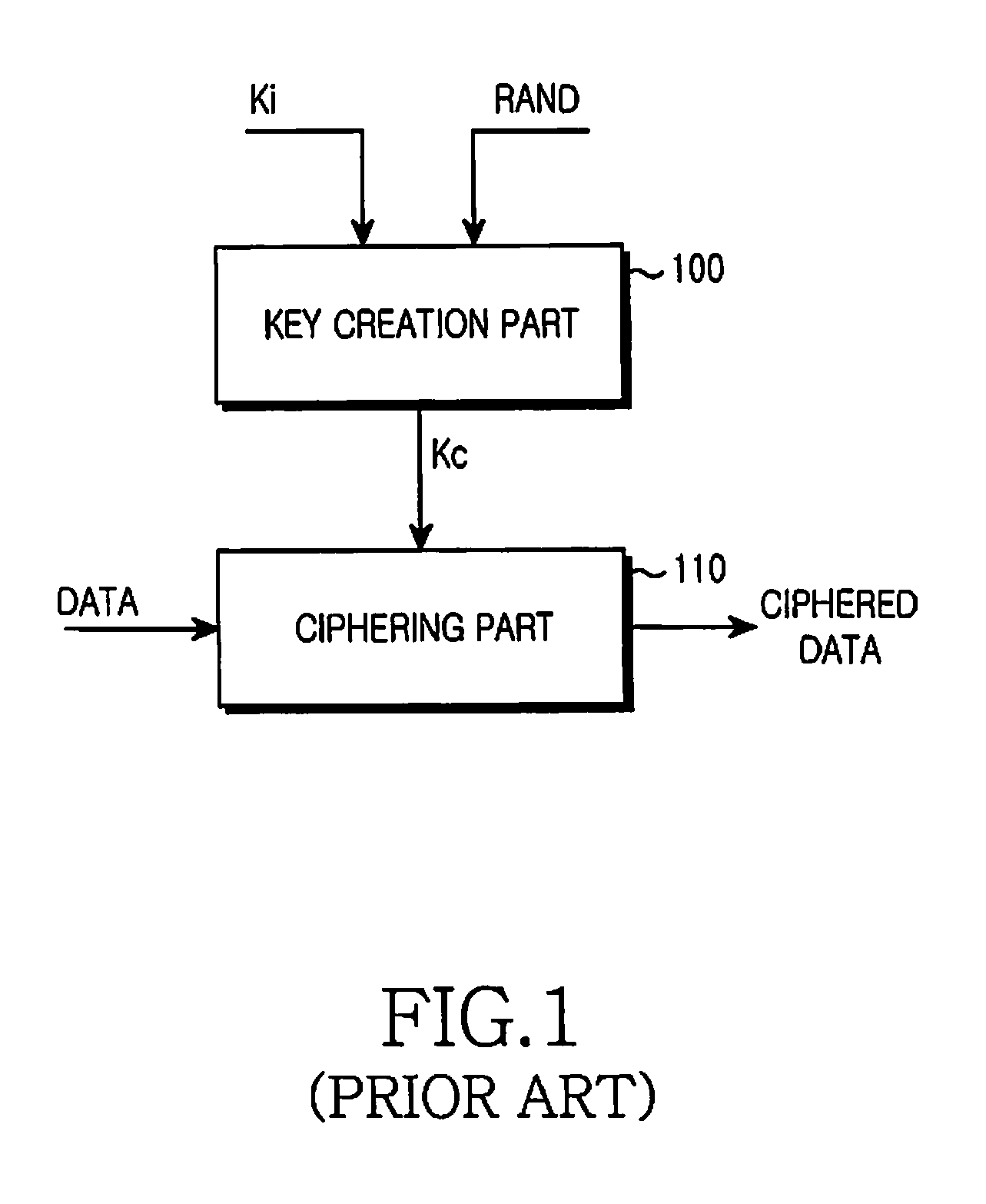
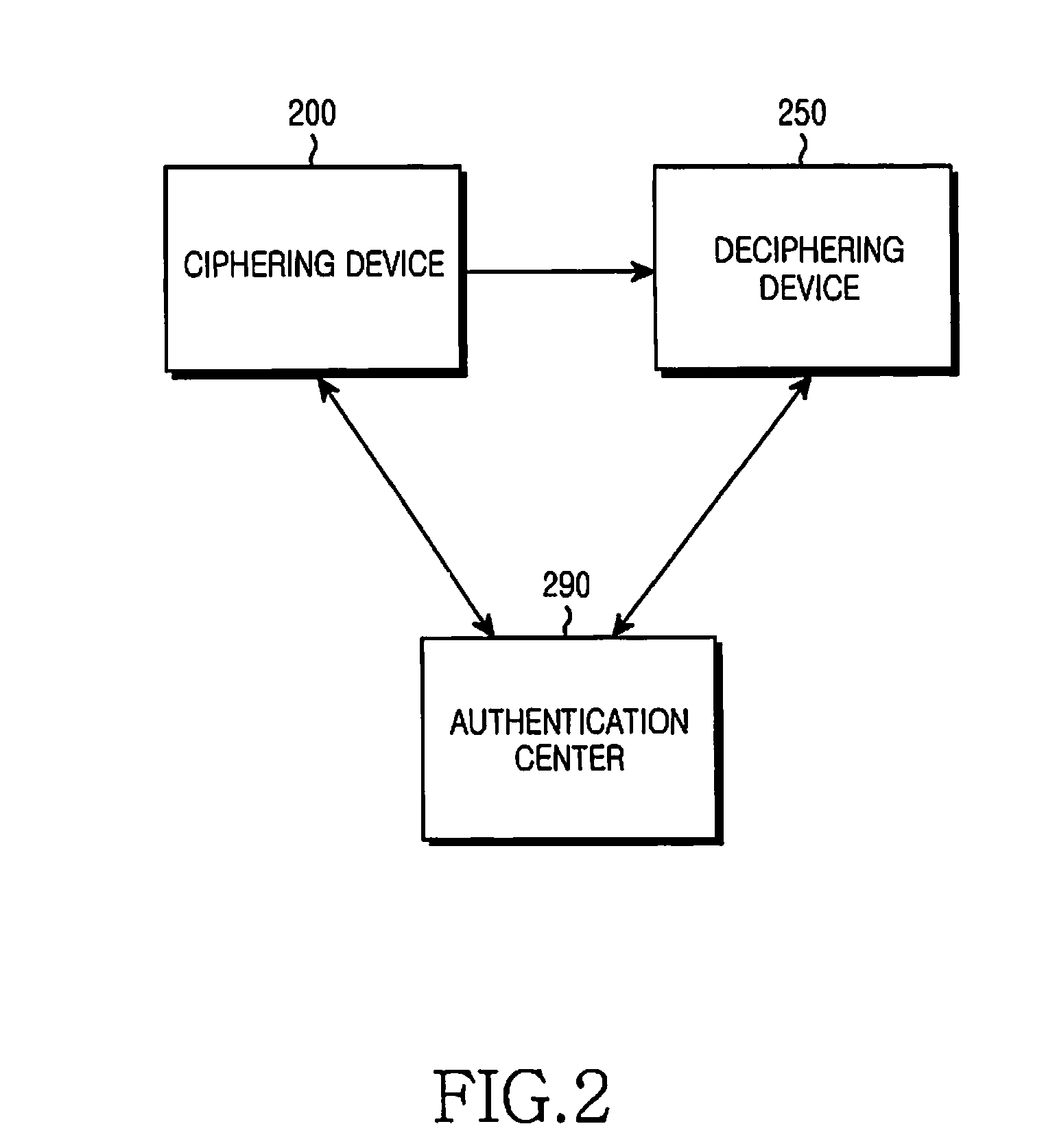
Apparatus and method for dynamic ciphering in a mobile communication system
InactiveUS20080112563A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer hardwareCommunications system
An apparatus and method for dynamic ciphering in a mobile communication system are provided. In a dynamic ciphering mobile communication system, a ciphering apparatus receives the Security Code Table (SCT) in advance and stores it, creates dynamic cipher keys when the data need to be ciphered using the SCT and the frame number of the data, and transmits the frame containing the data ciphered by the created dynamic cipher key, a deciphering apparatus receives the frame, creates the dynamic cipher key using the SCT and the frame number of the received frame, and deciphers the data contained in the frame using the dynamic cipher key created, and an authentication center manages authentication keys which are subscribers' authentication information, and creates and manages the SCTs of subscribers.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and System to Electronically Identify and Verify an Individual Presenting Himself for Such Identification and Verification
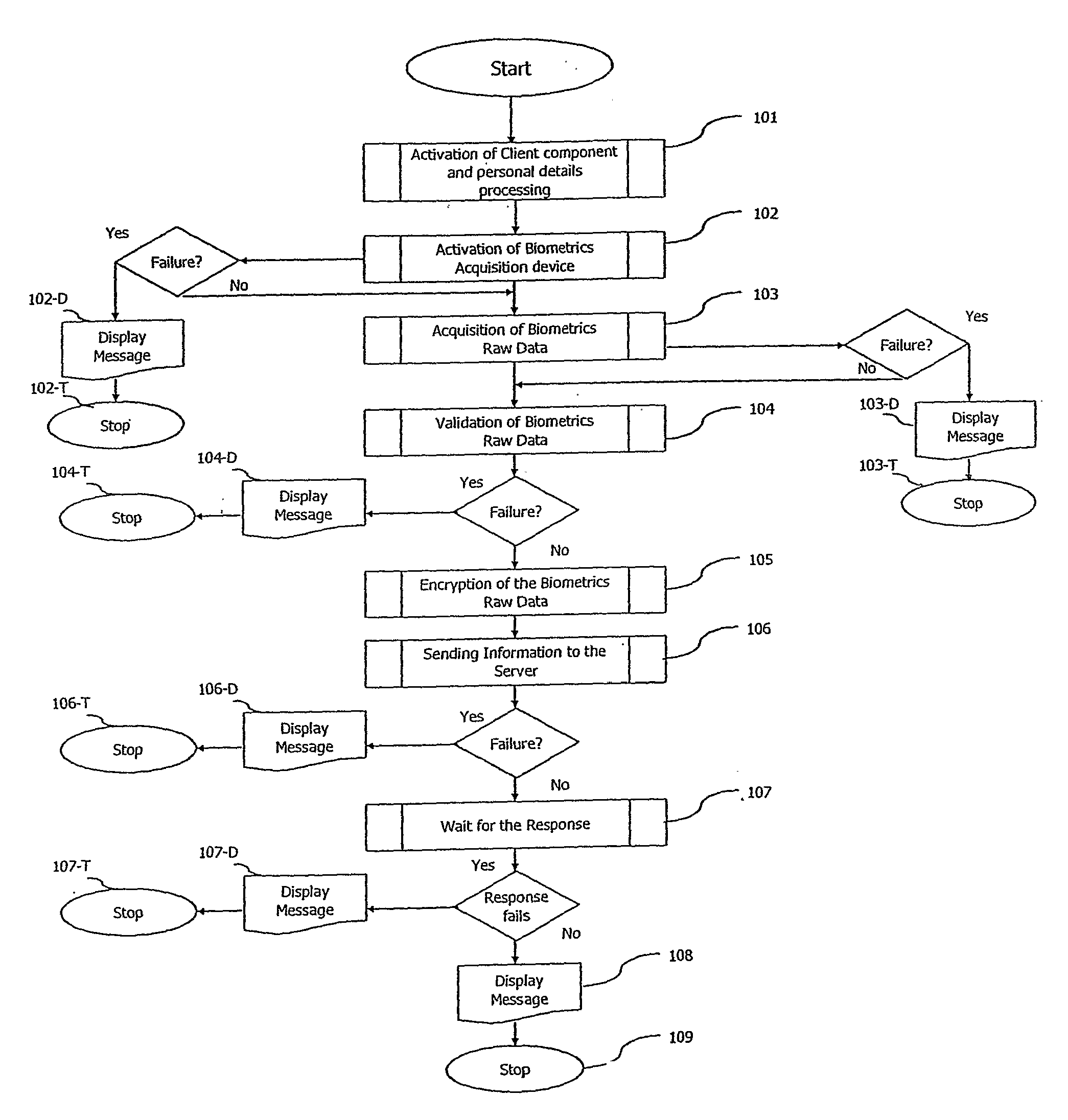
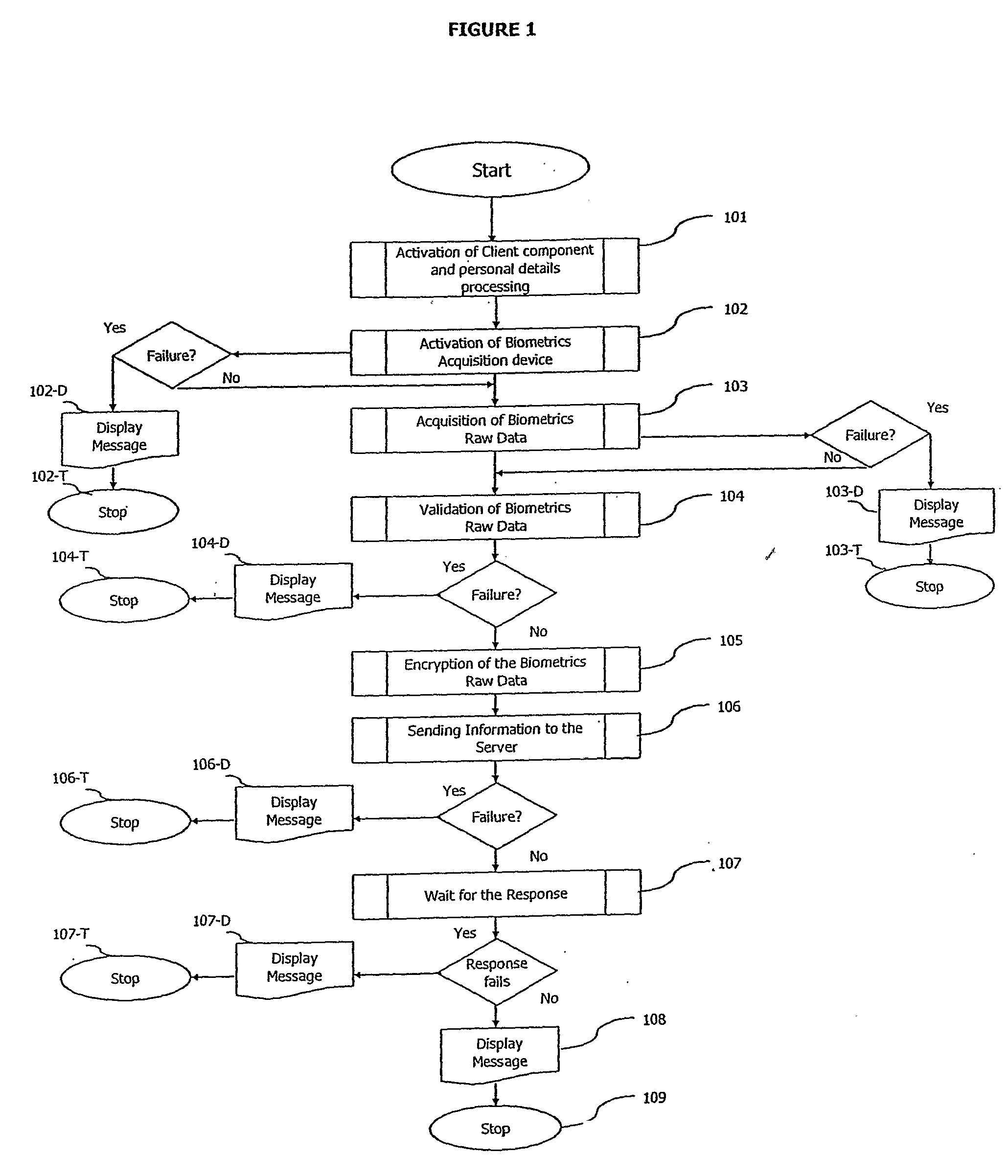
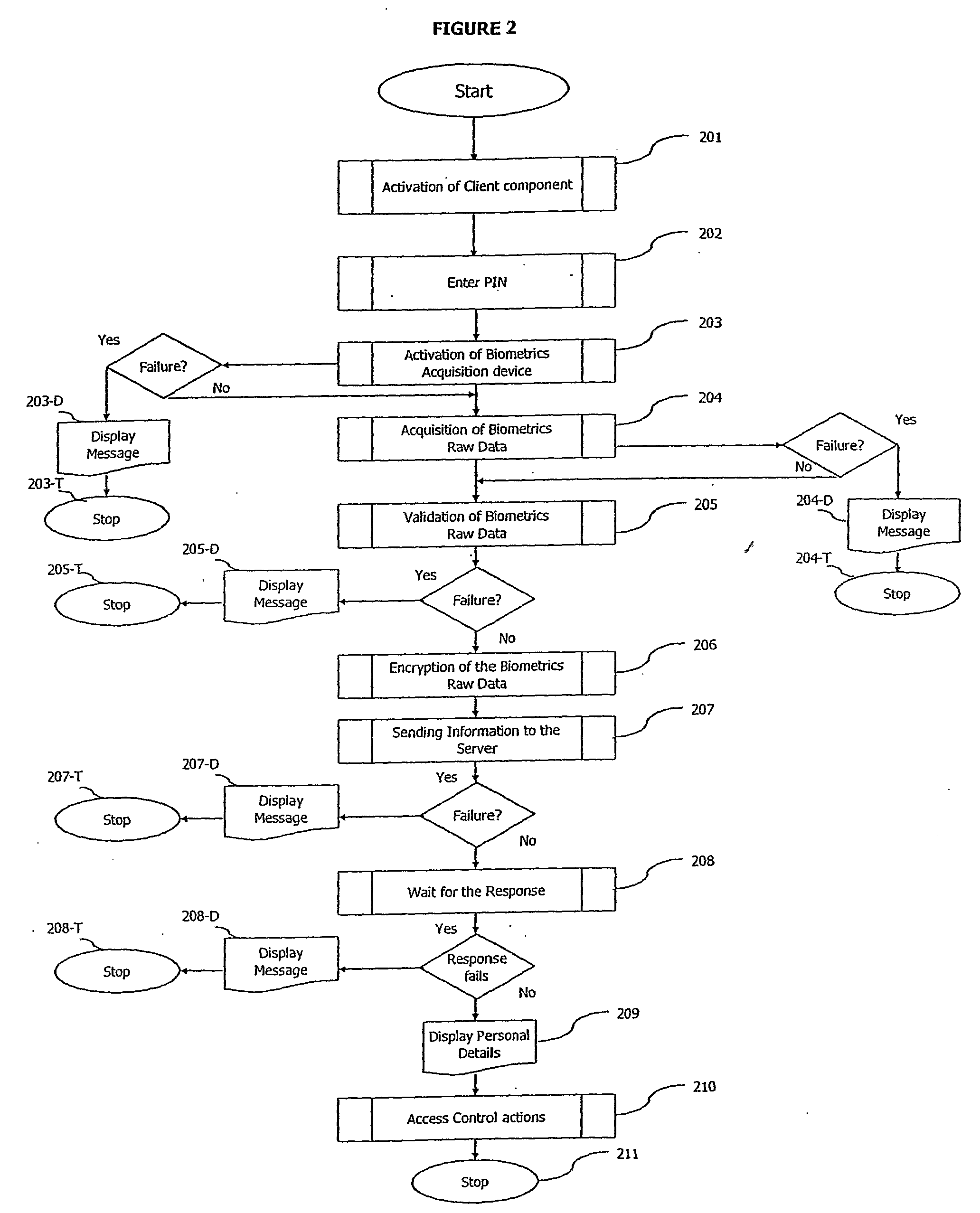
InactiveUS20070253601A1User identity/authority verificationCharacter and pattern recognitionDatabase machineOn-the-fly encryption
A method and a system of electronically identifying and verifying an individual utilising at least one biometric features of the individual is disclosed. The method includes the steps of activating an access apparatus with a means to capture at least one biometric feature of an individual in a secure manner using dynamic encryption, capturing the biometric feature of an individual wherein key features of biometric raw data are extracted, encrypting in a dynamic manner the biometric features, transmitting the encrypted data of the biometric feature to at least one server; and verifying the biometric features captured in the fruit step with a pre-stored biometric feature in the server. Wherein upon positive identification and verification of the individual access is given to an auxiliary means such as but not limited to access to secured doors, database, computer network and servers.
Owner:SURESHWARA
Data transmission method and device, computer device and storage medium
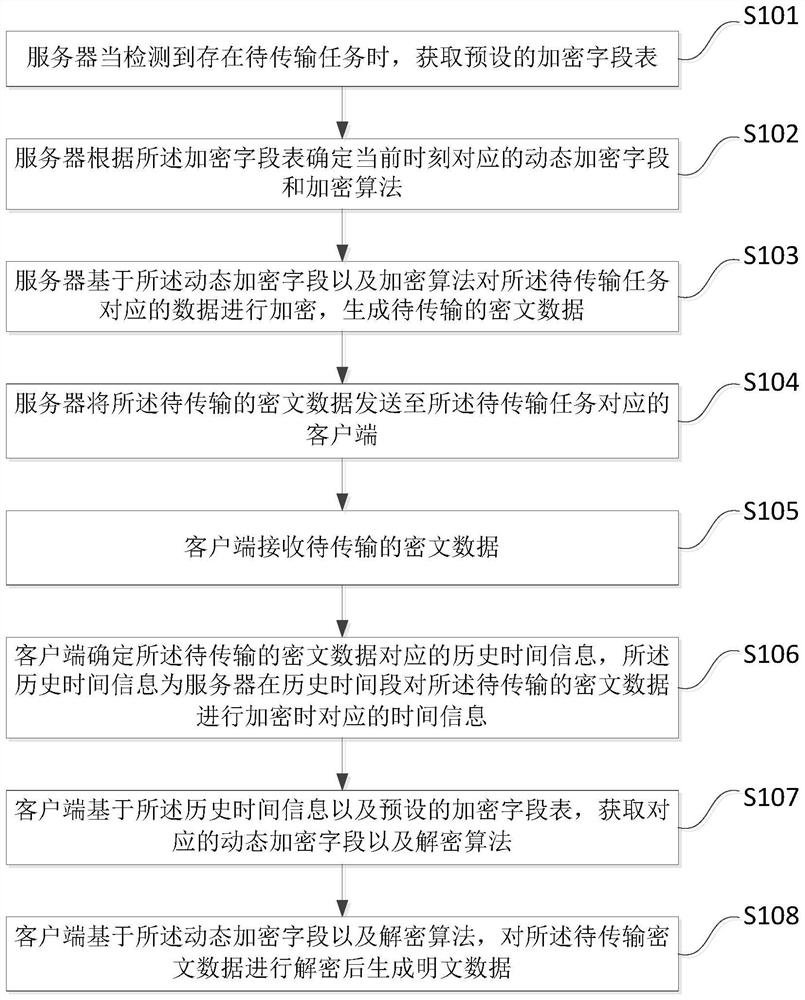
ActiveCN112019541AReduce risk of leakageSolve potential safety hazardsMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesTime informationCiphertext
The invention discloses a data transmission method and device, a computer device and a storage medium, and the method comprises the steps: enabling a server to obtain a preset encryption field table when a to-be-transmitted task is detected to exist; the server determining a dynamic encryption field and an encryption algorithm corresponding to the current moment according to the encryption field table; the server encrypting data corresponding to the to-be-transmitted task based on the dynamic encryption field and an encryption algorithm to generate to-be-transmitted ciphertext data; and the server sending the ciphertext data to be transmitted to the client corresponding to the task to be transmitted; the client receiving ciphertext data to be transmitted; the client determining historicaltime information corresponding to the ciphertext data to be transmitted; the client acquiring a corresponding dynamic encryption field and a decryption algorithm based on the historical time information and a preset encryption field table; and the client decrypting the to-be-transmitted key data based on the dynamic encryption field and a decryption algorithm to generate plaintext data. Therefore,by adopting the embodiment of the invention, the risk of data leakage can be reduced.
Owner:PINGAN INT SMART CITY TECH CO LTD
Data dynamic encryption communication method and system based on two-wire system communication
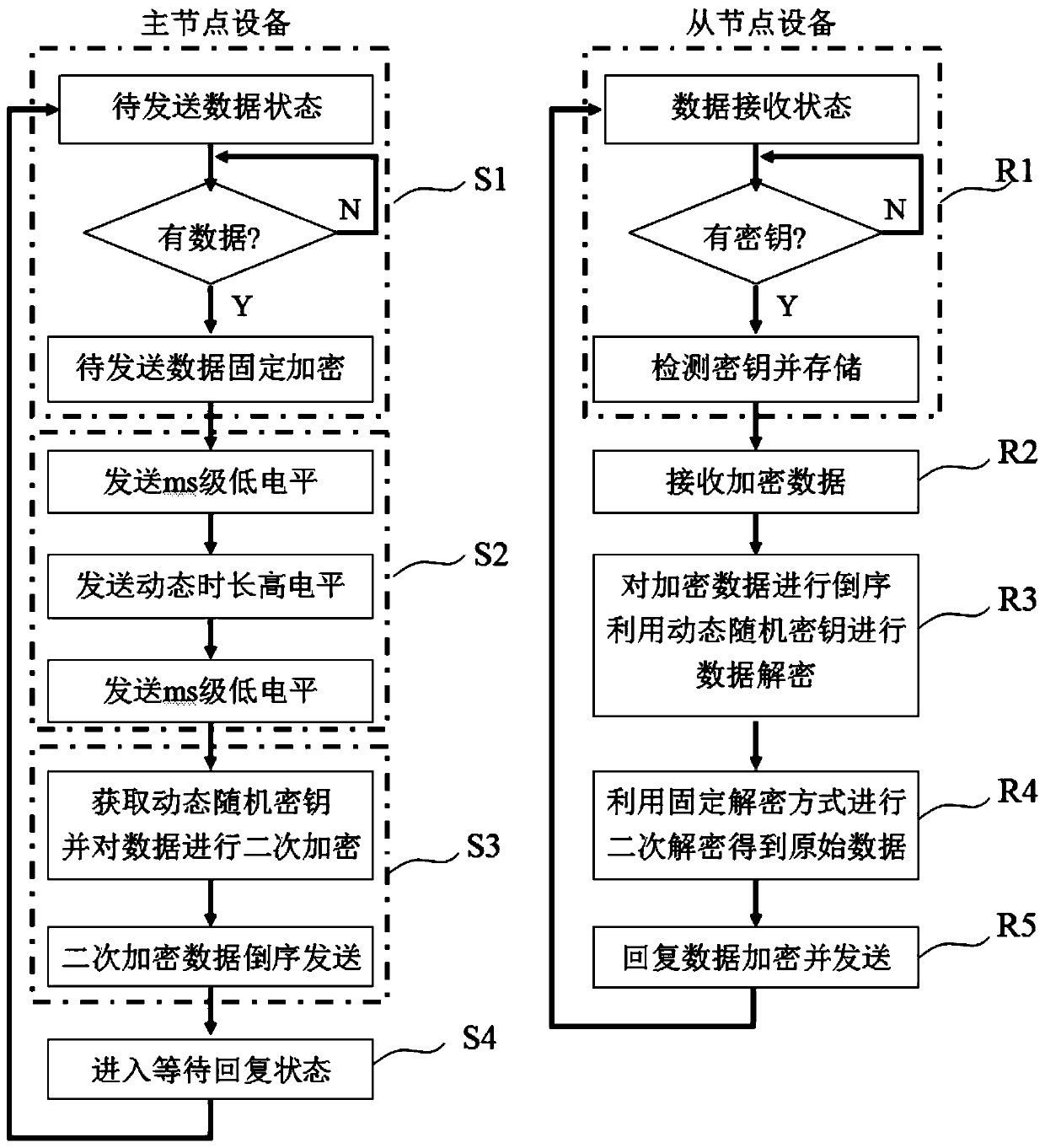
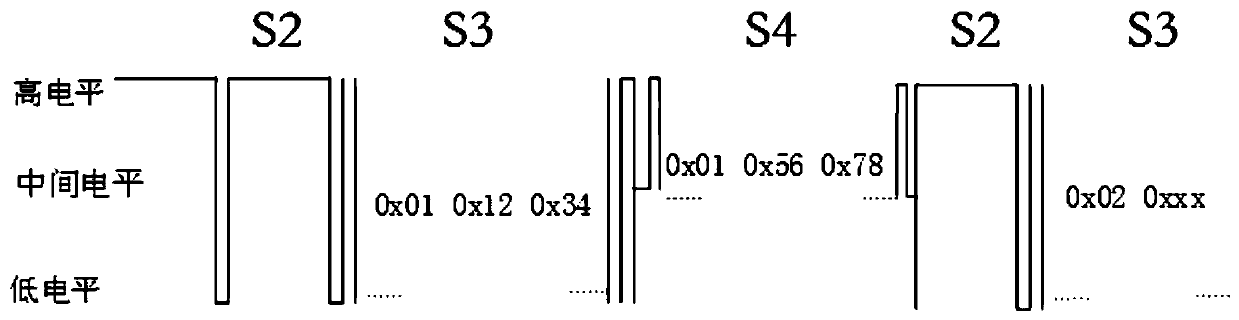
ActiveCN110944009ARealization of dynamic encryptionPrevent brute force attacksTransmissionOriginal dataCarrier signal
The invention discloses a data dynamic encryption communication method based on two-wire system communication. The method comprises main node equipment data encryption sending and slave node equipmentdata receiving and responding, and the main node equipment data encryption sending process comprises the steps that to-be-sent data is encrypted in a fixed encryption mode, then a random dynamic secret key is sent, secondary encryption is conducted on the data through the random dynamic secret key, reverse order sending is conducted, and reply is waited after sending is completed; data receivingand responding processes of the slave node equipment are as follows: when a dynamic random key signal exists on a bus, detecting and storing the dynamic random key signal, then receiving encrypted data, decrypting the encrypted data by utilizing a dynamic random key, then performing reverse processing, finally decrypting by adopting a fixed encryption mode to obtain original data, generating encrypted reply data, and sending the encrypted reply data to the bus. According to the invention, dynamic encryption of two-bus or direct-current carrier data is realized, communication data is effectively prevented from being intercepted by external communication and violently attacked by the outside, and the security of data transmission is ensured.
Owner:WUHAN WUTOS
Encipher apparatus for image and sound transmission
The invention provides an audio-visual transmission and encrypting device, which comprises a playing mechanism and a video signal receiving mechanism, wherein the playing mechanism is capable of processing audio-visual signal, and is at least provided with a drive unit, a dynamic decryption unit and an application program unit which are connected with each other; and the video signal receiving mechanism is connected with the playing mechanism through a connecting interface, and is at least provided with a receiving and demodulating unit capable of receiving external audio-visual signals, and a dynamic encrypting unit connected with the receiving and demodulating unit; and the dynamic encrypting unit can receive a dynamic encrypting string of the drive unit, operate the dynamic encrypting string, encrypt the operated dynamic encrypting string with the audio-visual signal and transmit the encrypted dynamic encrypting string to the drive unit. Therefore, encryption data used in the communication process of the video signal receiving mechanism and the playing mechanism are not easy to decode, and video signal data during the transmission are effectively protected.
Owner:YUAN HIGH-TECH DEV CO LTD
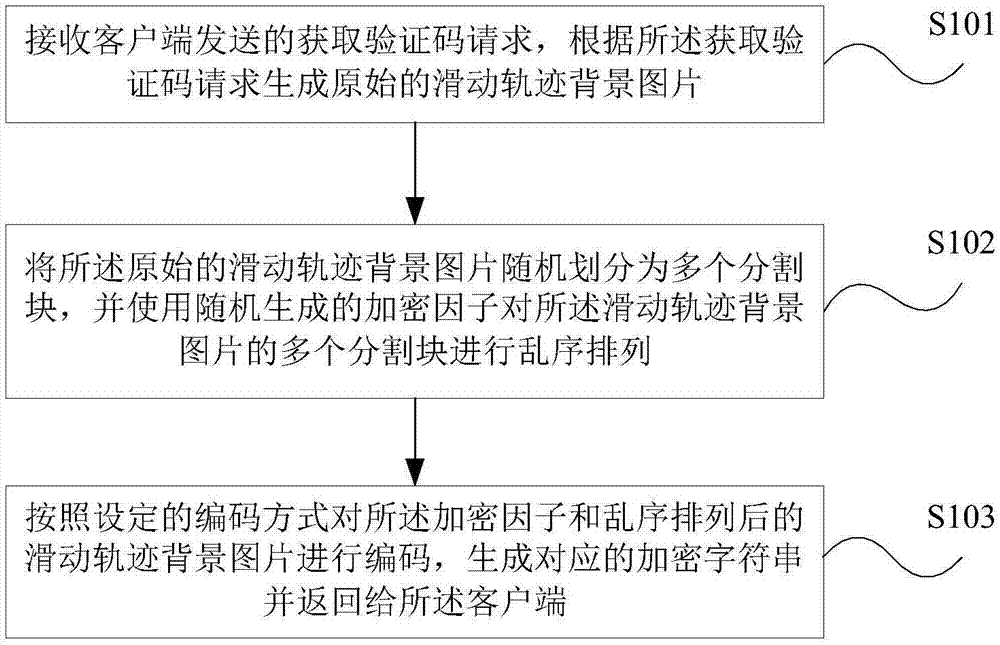
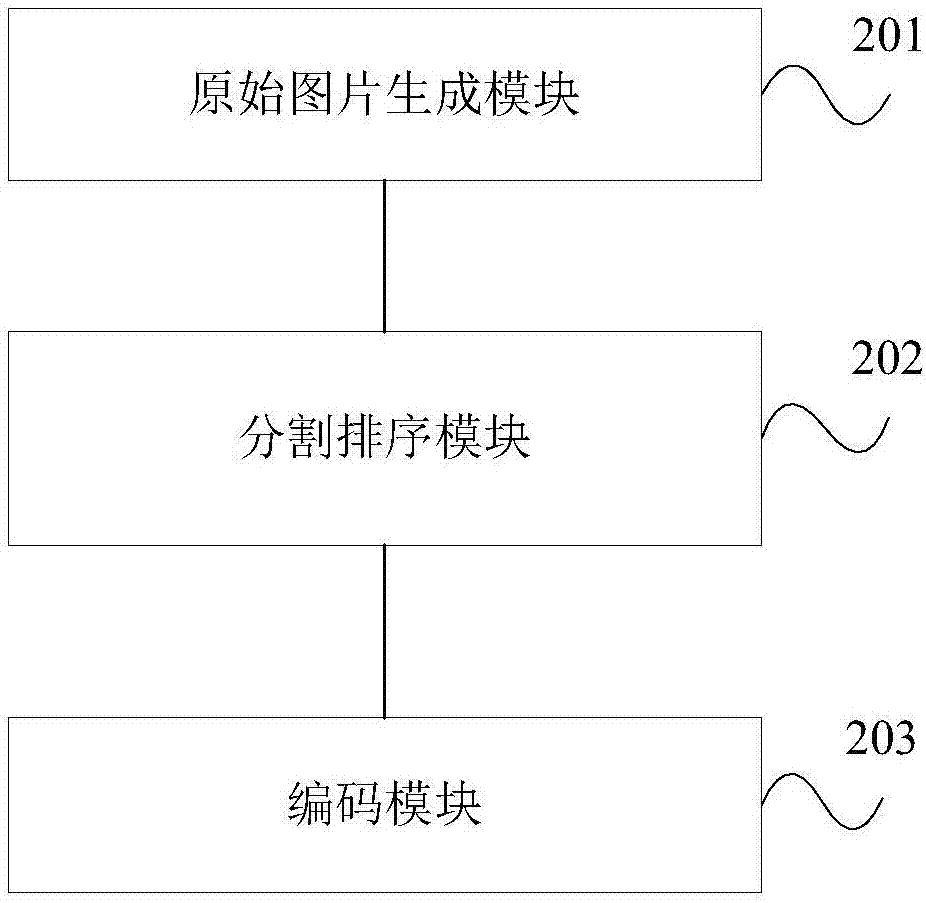
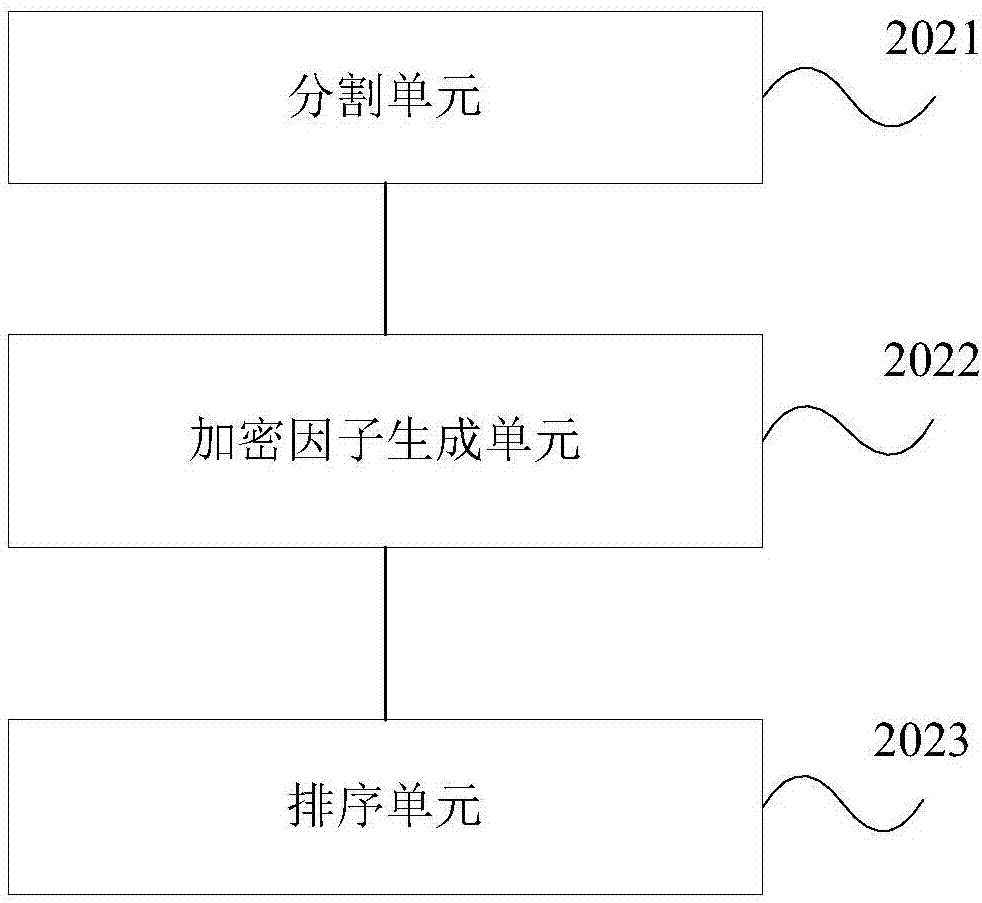
Encryption and decryption methods and devices of sliding track background picture
InactiveCN107491686AReduce complexityIncrease costDigital data authenticationDigital video signal modificationComputer hardwareAlgorithm
The invention provides encryption and decryption methods and devices of a sliding track background picture. The encryption method of the sliding track background picture includes: receiving a verification-code acquisition request sent by a client, and generating the original sliding track background picture according to the verification-code acquisition request; randomly dividing the original sliding track background picture into a plurality of division blocks, and using a randomly generated encryption factor to carry out out-of-order arrangement on the plurality of division blocks of the sliding track background picture; and encoding the encryption factor and a sliding track background image after out-of-order arrangement according to a set encoding mode to generate corresponding encrypted character strings, and returning the same to the client. According to the encryption and decryption methods and devices of the sliding track background picture provided by the embodiment of the invention, track background picture contents can be directly returned, a link form is not used, and server realization complexity is reduced; and the encryption method adopts out-of-order encryption and dynamic encryption, and greatly increases cracking costs and difficulty of a cracker.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
Systems, methods, and computer-readable media for secure digital communications and networks
ActiveUS8880887B2Multiple keys/algorithms usageUser identity/authority verificationSecure communicationKey size
Provided are system, methods, and computer-readable media for systems, methods, and computer-readable media for secure digital communications and networks. The system provides for secure communication between nodes through the use of a subscription between two nodes based on unique identifiers that are unique to each node, and communication between nodes without a subscription may be blocked. Additionally, secure communications between a node and a remote node are dynamically encrypted using asymmetric and symmetric encryption. The encryption algorithms and key lengths may be changed at each subsequent negotiation between a node and a remote node.
Owner:STT
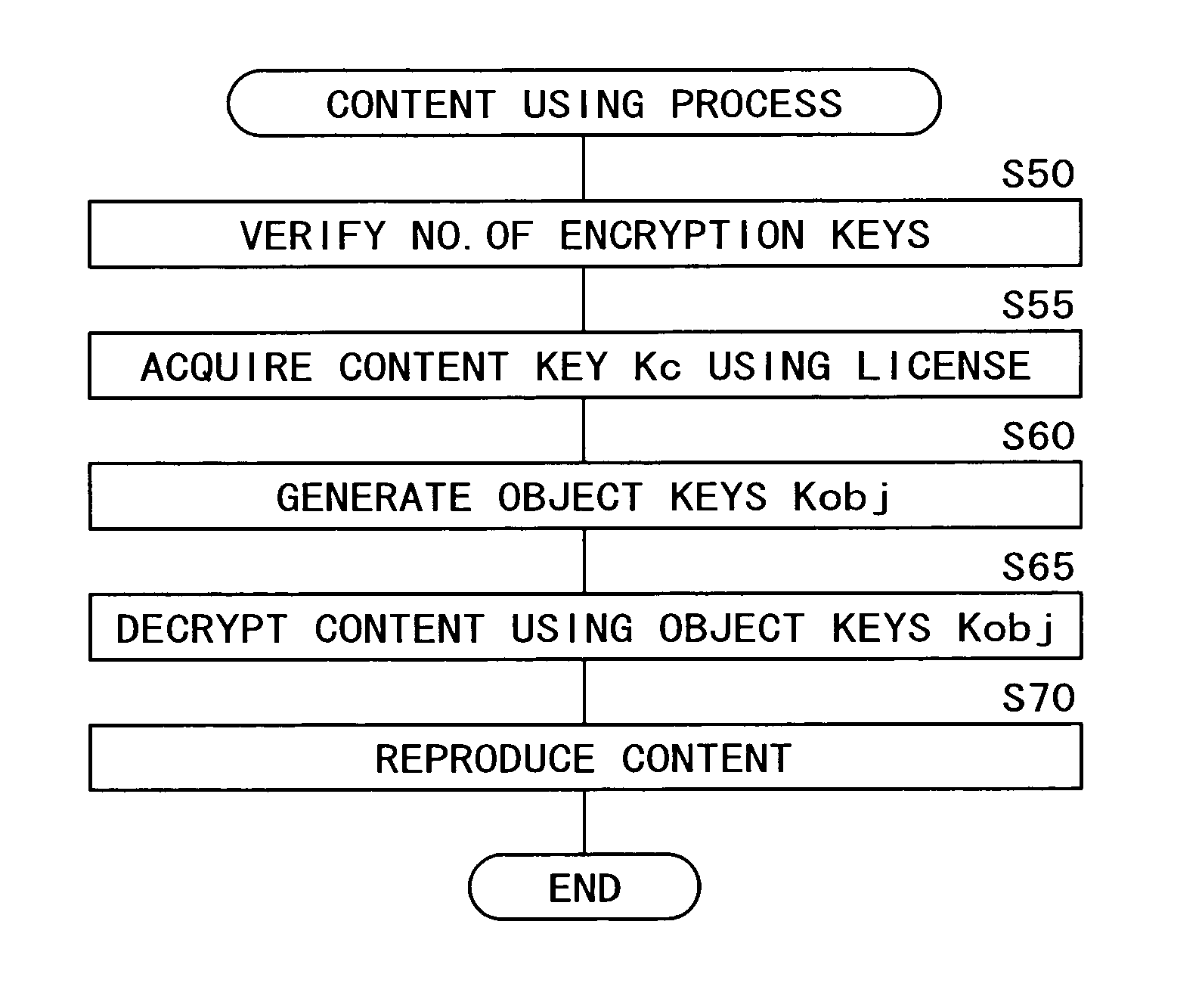
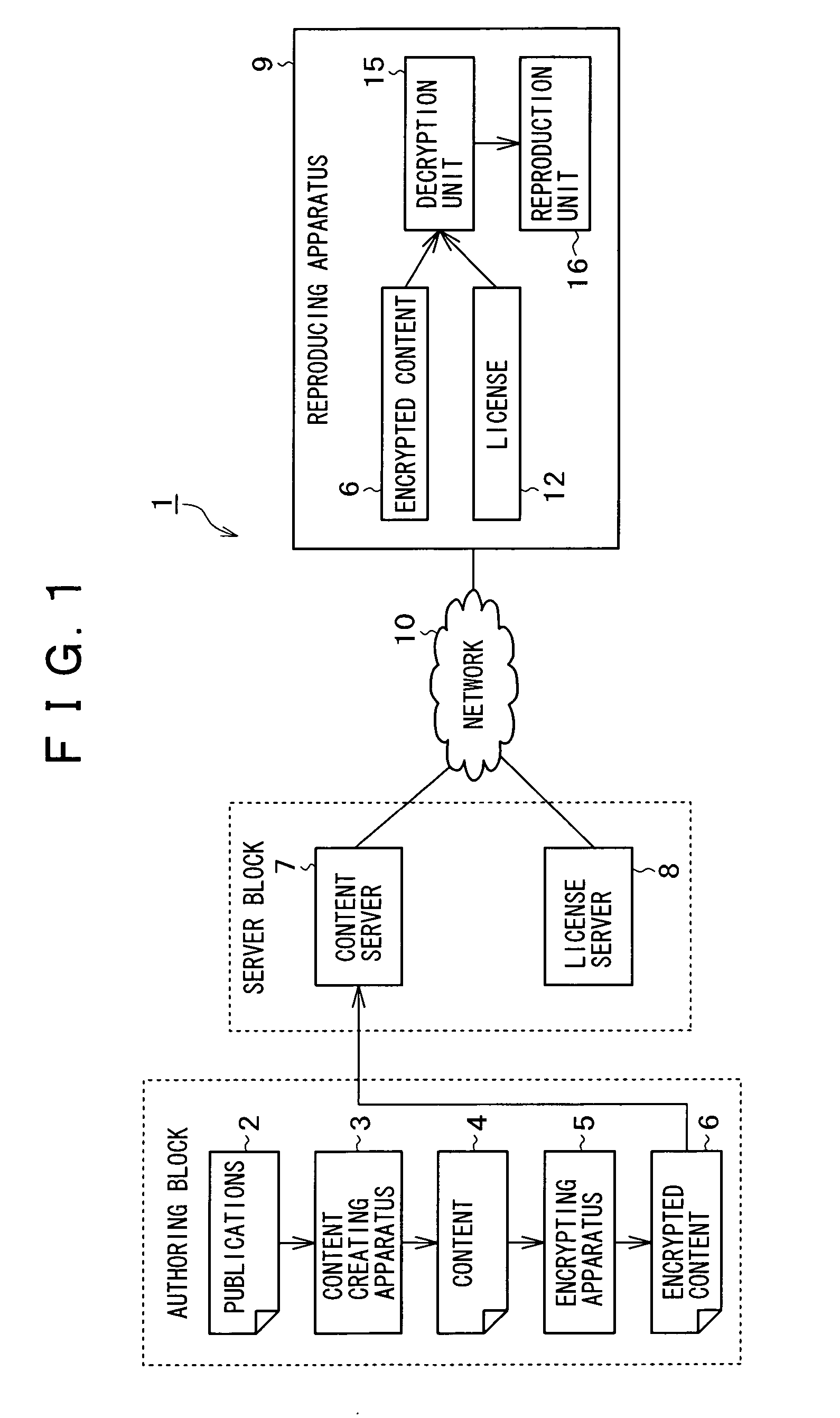
Content distributing system with dynamic encryption keys
InactiveUS8261360B2Key distribution for secure communicationMultiple keys/algorithms usageInternet privacyEngineering
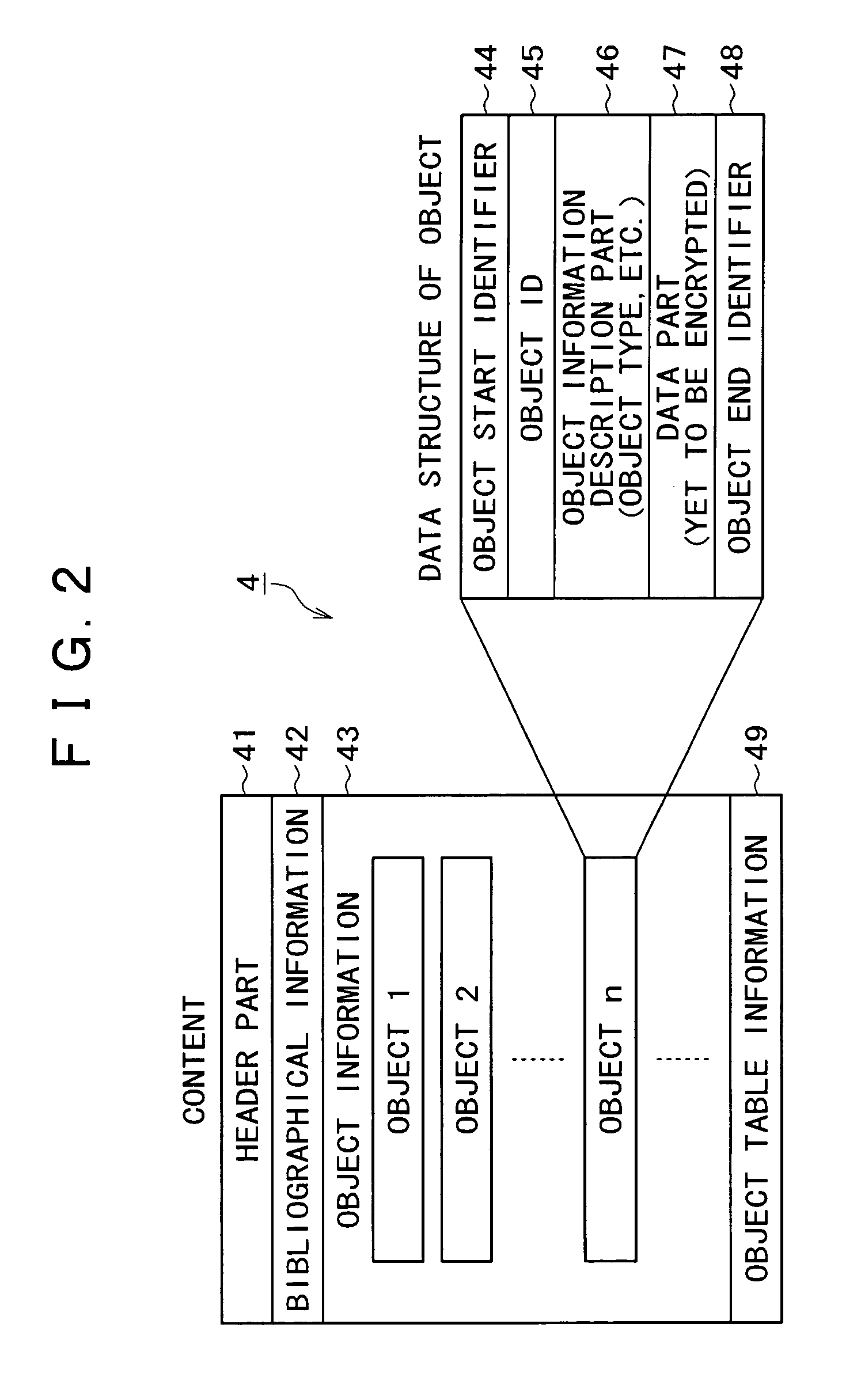
A content distributing system for distributing content disclosed herein is an encrypting apparatus for encrypting each of objects constituting content using a different encryption key, a content offering apparatus for offering the encrypted content to a content reproducing apparatus; a license information offering apparatus for offering license information including information necessary for decrypting the encrypted content, and a content reproducing apparatus for acquiring the encrypted content from the content offering apparatus in order to decrypt and reproduce the acquired content using the license information acquired from the license offering apparatus.
Owner:SONY CORP
Sensing system key protecting method in field of Internet of things and wireless access equipment
ActiveCN104581715AKey distribution for secure communicationUser identity/authority verificationNetwork connectionEncryption
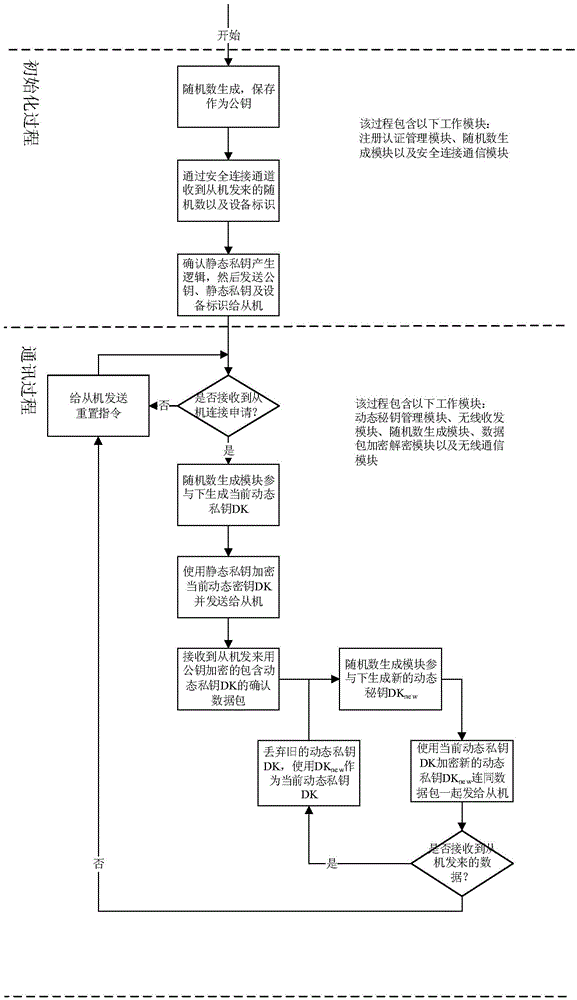
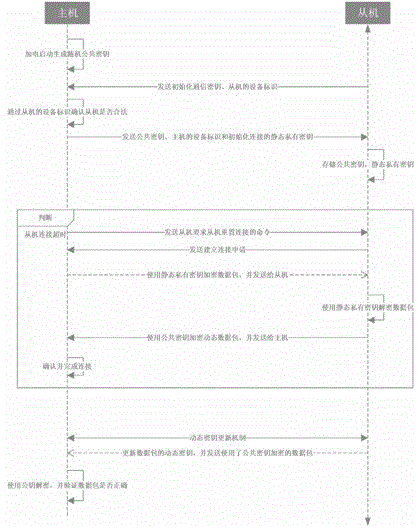
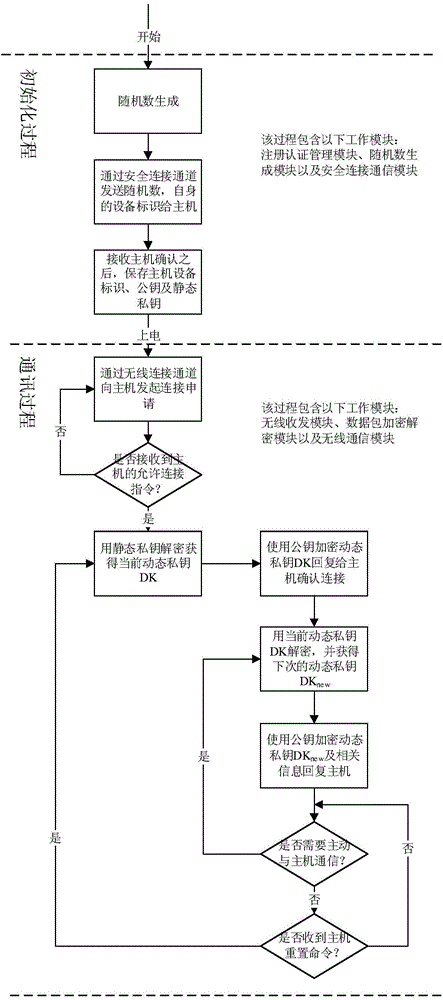
The invention discloses a network security key protecting method in the field of Internet of things. The network security key protecting method comprises the following steps: a public key is randomly generated after a host computer starts up a work; the host computer and a slave computer complete connection initialization through a reliable connection way; equipment identifiers of counterparts are mutually recorded by the host computer and the slave computer, and a static private key during connection establishment is generated under the domination of the slave computer; after accessing to the network, all communications between the host computer and the slave computer have a dynamic encryption mechanism dominated by the host computer. Through application of a safe connection initializing mechanism and a dynamic key mechanism, network connection between the host computer and the slave computer can be quickly and securely realized, so that a user does not need to remember a security key, but secure wireless connection can be quickly and conveniently established; the risk that the key is monitored by a malicious device and the risk that information is copied and faked are avoided.
Owner:杭州木梢科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com