Multi-stage domain protection method and system based on information security level identifiers
A multi-level domain and identification technology, applied in the field of computer security, can solve the problems of inability to implement accountability, information monitoring, interception, and inability to conduct audits, and achieve the effect of achieving access and solving information leakage threats.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
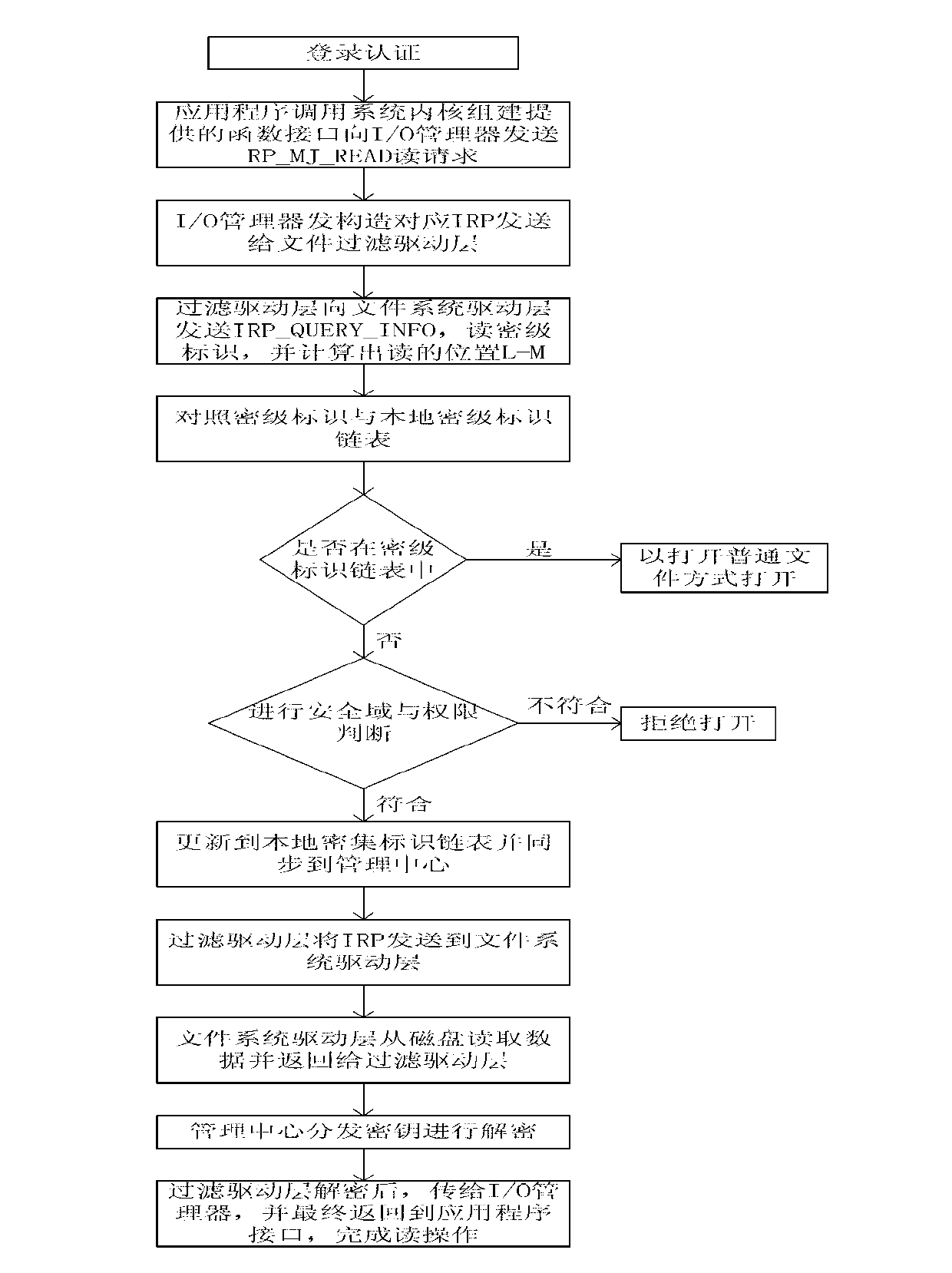
[0041] The ciphertext is created by the authenticated user above, see figure 2 , in one embodiment may specifically include the steps:
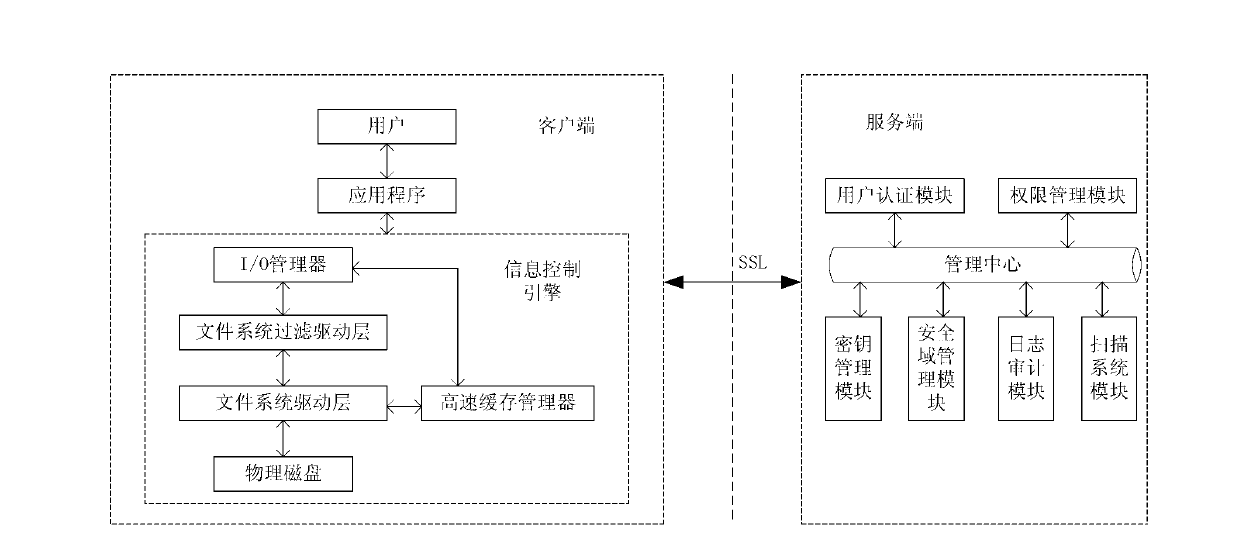
[0042] A1), through page redirection (a common mandatory authentication method), the user is forced to implement handshake authentication through the SSL security mechanism, establish a communication security channel, and connect to the server;
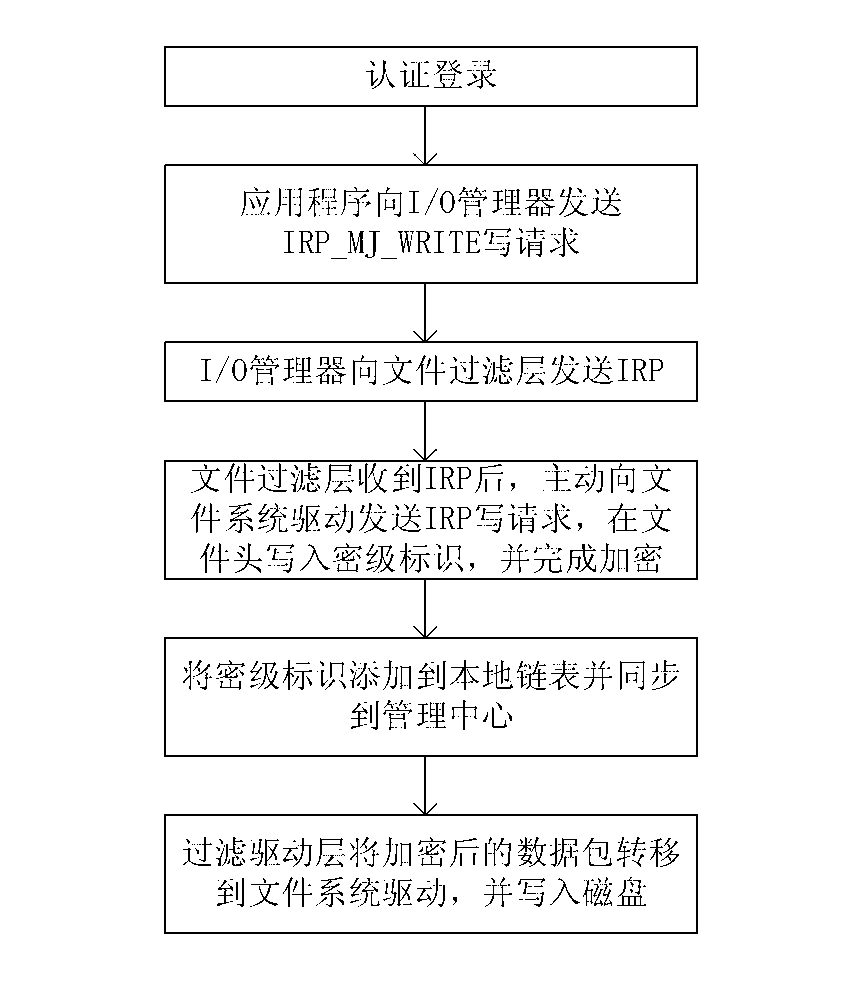
[0043]A2), the client application (the application software used by the user to open confidential information, such as word) calls the operating system to read and write information functions (such as the CreateFile function, which is the function to be called when reading and writing information in the windows framework) Send an IRP_MJ_WRITE write request to the I / 0 manager;
[0044] A3), the I / 0 manager extracts the process name, storage path, start address, data length, data to be stored, etc. to construct an I / 0 request packet (IRP) corresponding to the write request, and sends the IRP to the f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com