Access control method based on image recognition and user level
An access control and user-level technology, applied in the fields of digital image processing and information security, can solve problems such as waste of resources, poor image readability, limited authorization protection, etc., and achieve the effect of precise mining, high security, and guaranteed security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
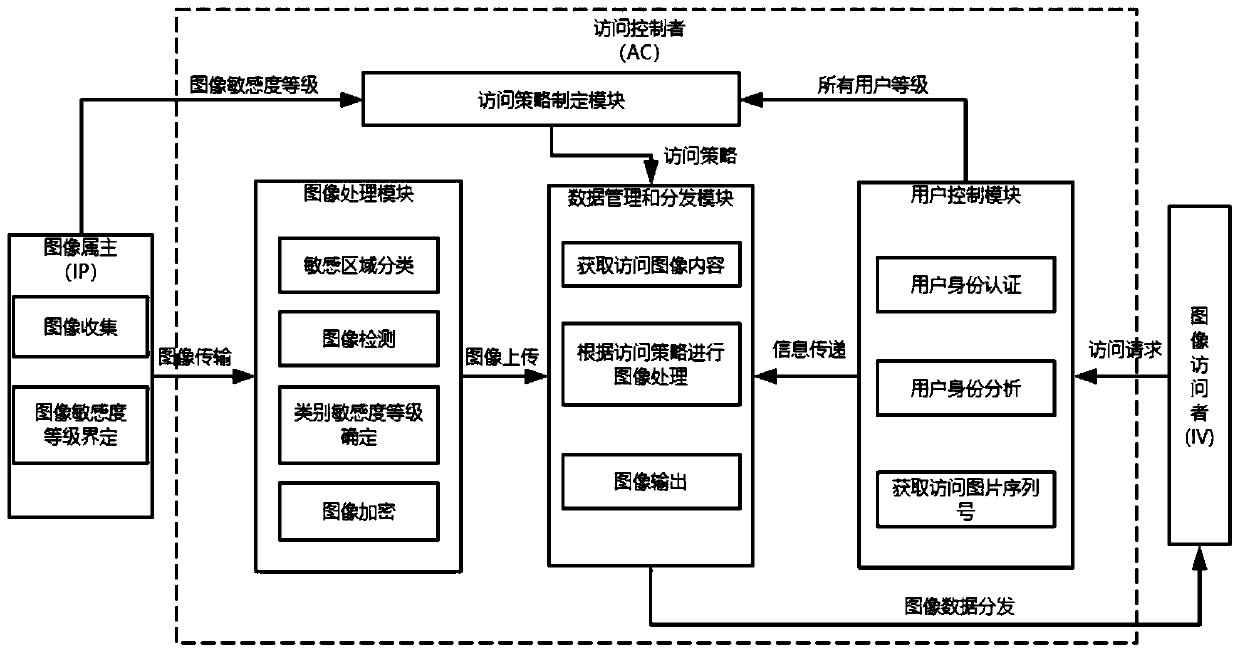
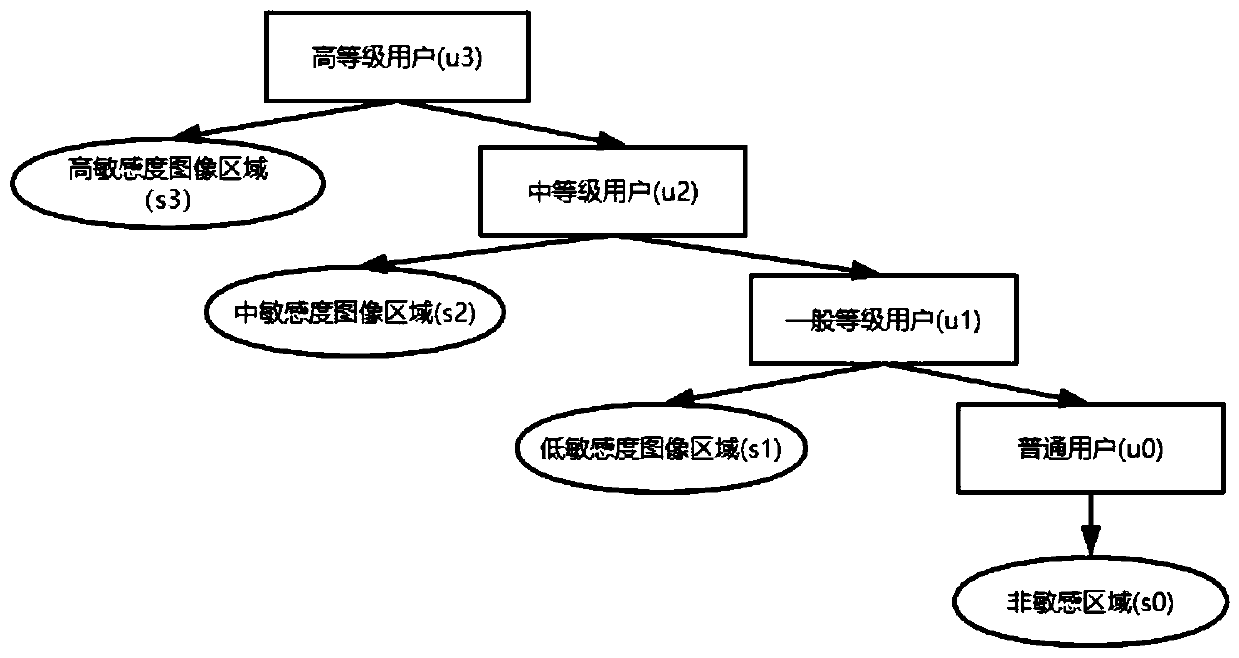
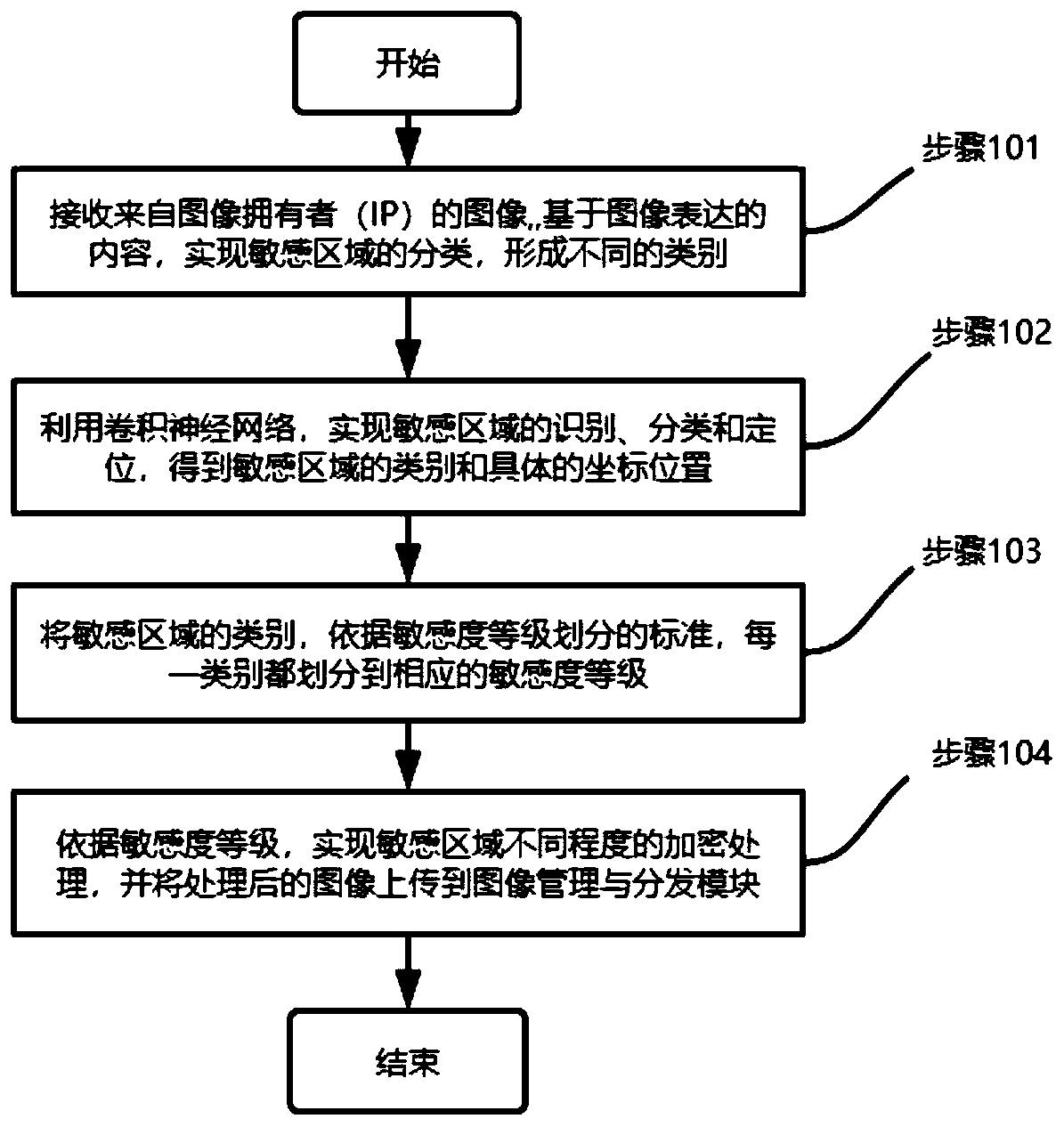
[0072] The student management system stores the image of each student's student ID card, which includes the student's photo, name, student number, place of origin, ID number, enrollment date, degree, validity period, college, major, school year and other information. If the photo, name, place of origin, ID number, and student number in the student ID card are regarded as sensitive information, then there are five categories of sensitive areas: {Face, Name, Birthplace, Identification_number, Student_ID}; image sensitivity is divided into four level: sensitivity_level = {s 3 High sensitivity image area, s 2 Medium sensitivity image area, s 1 low sensitivity image area, s 0 non-sensitive image region}.
[0073] After collecting the image of the student ID card in the system, it is sent to the image processing module; each image of the student ID card is marked with a tool, and based on the five categories and location information, a label text corresponding to the image is for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com