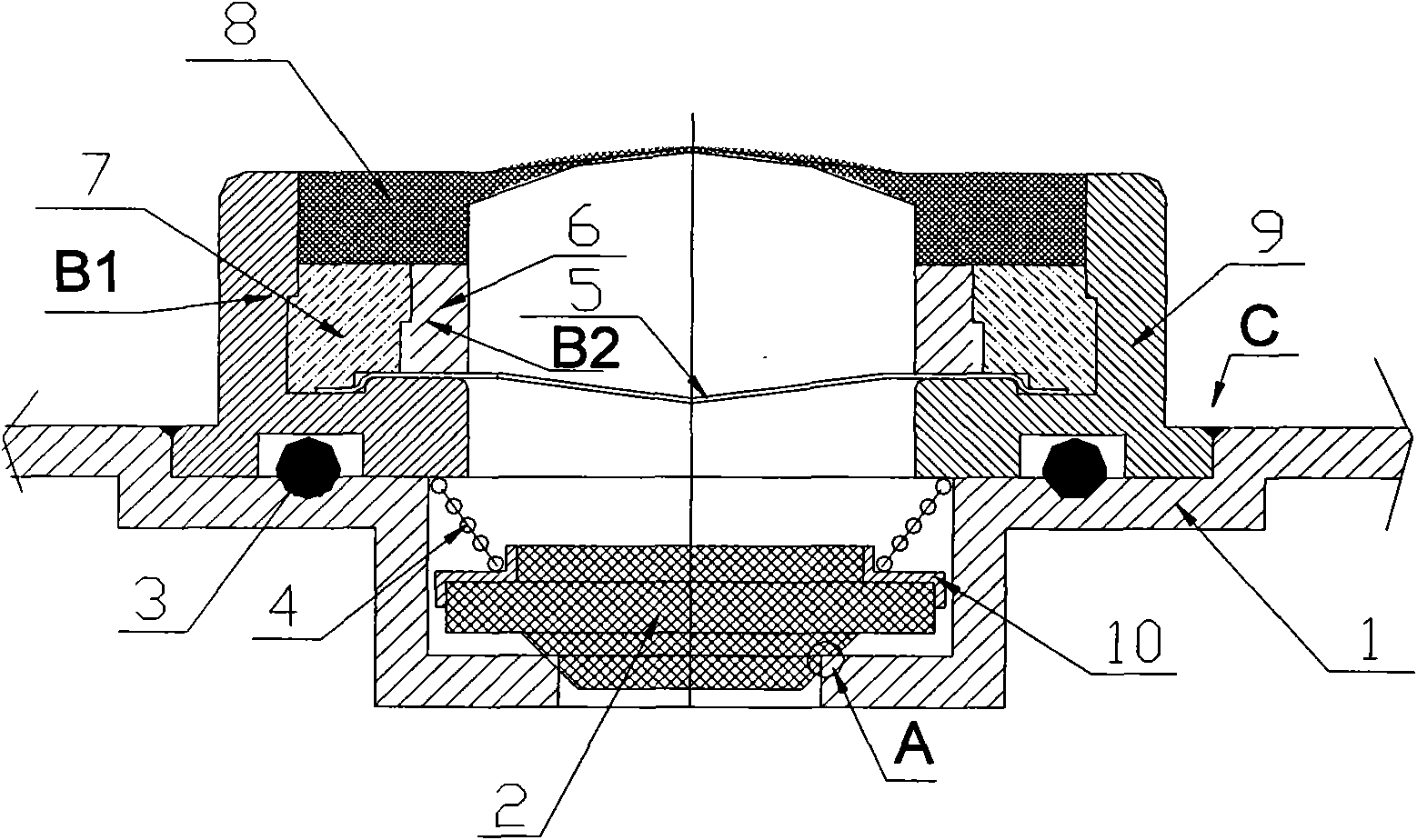
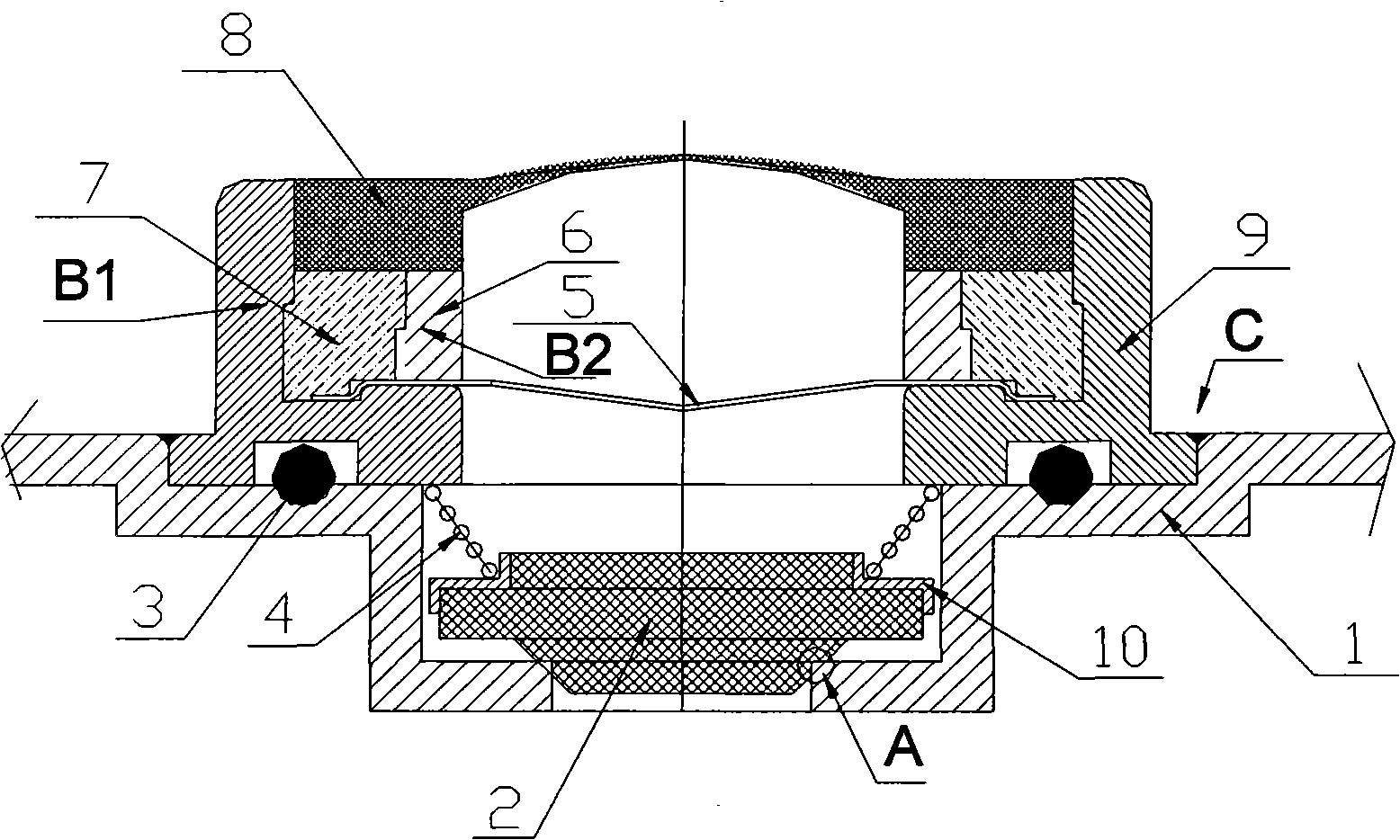
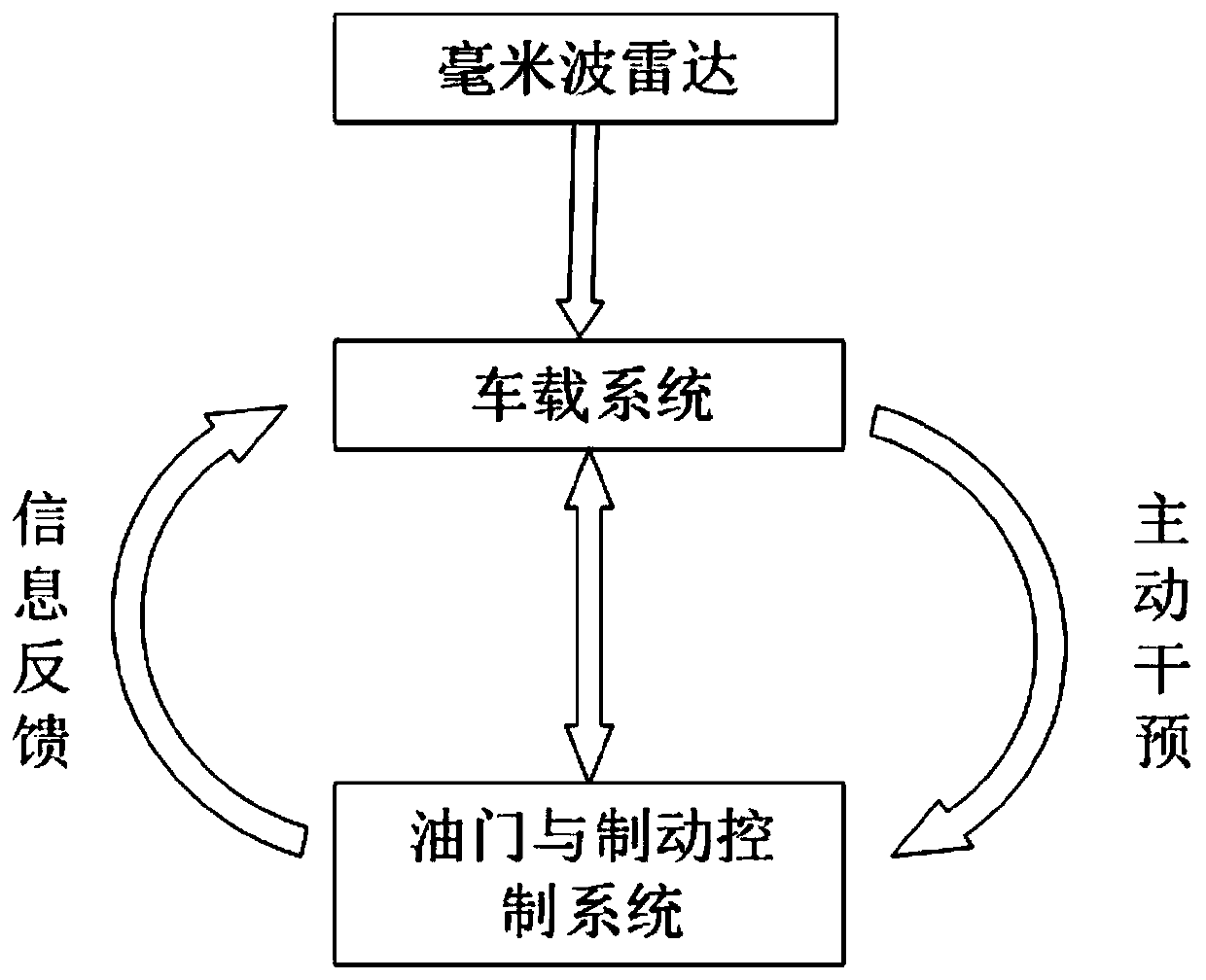
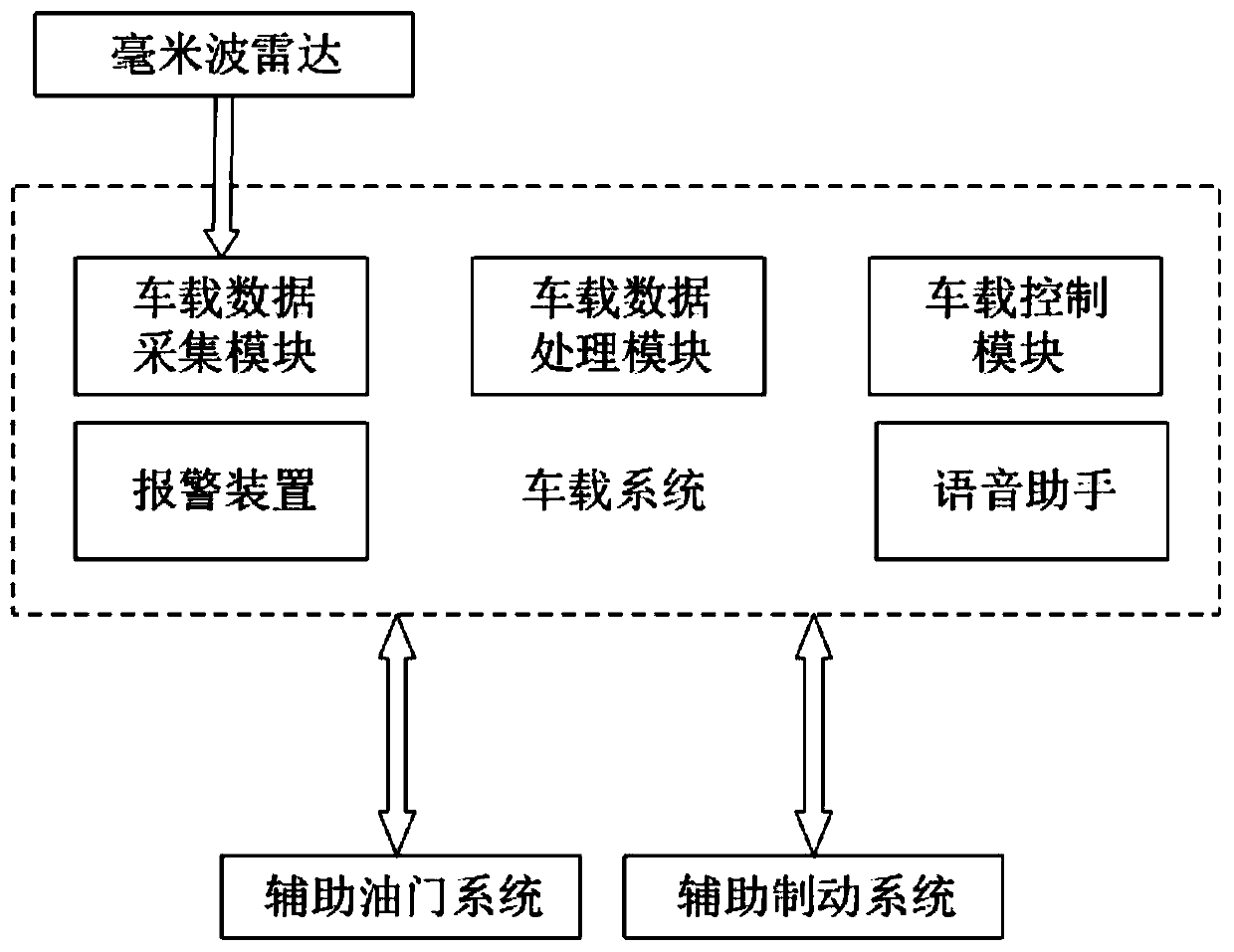
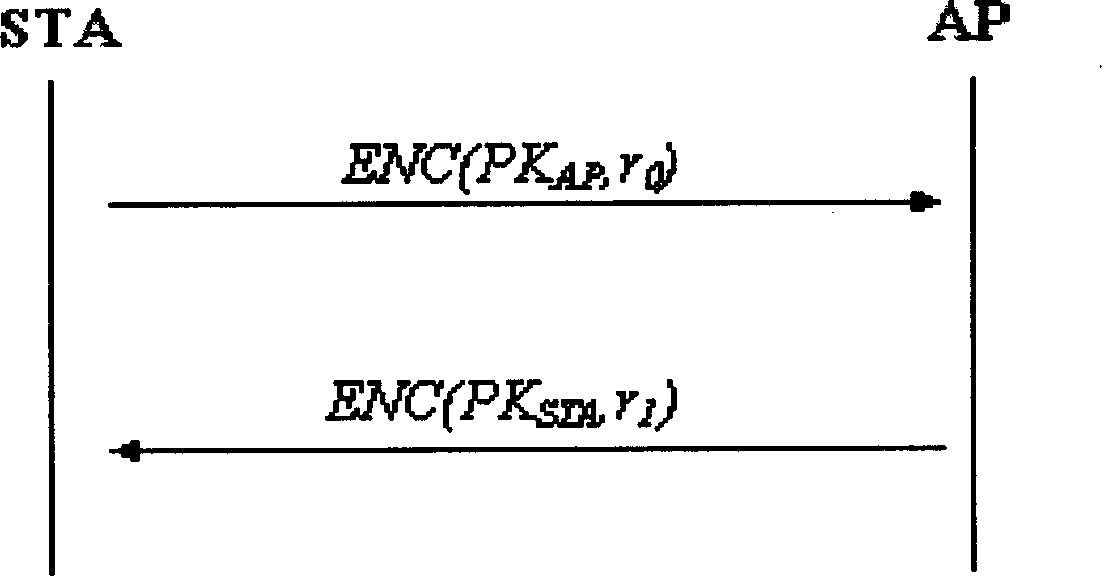Patents
Literature
66results about How to "To achieve the purpose of safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
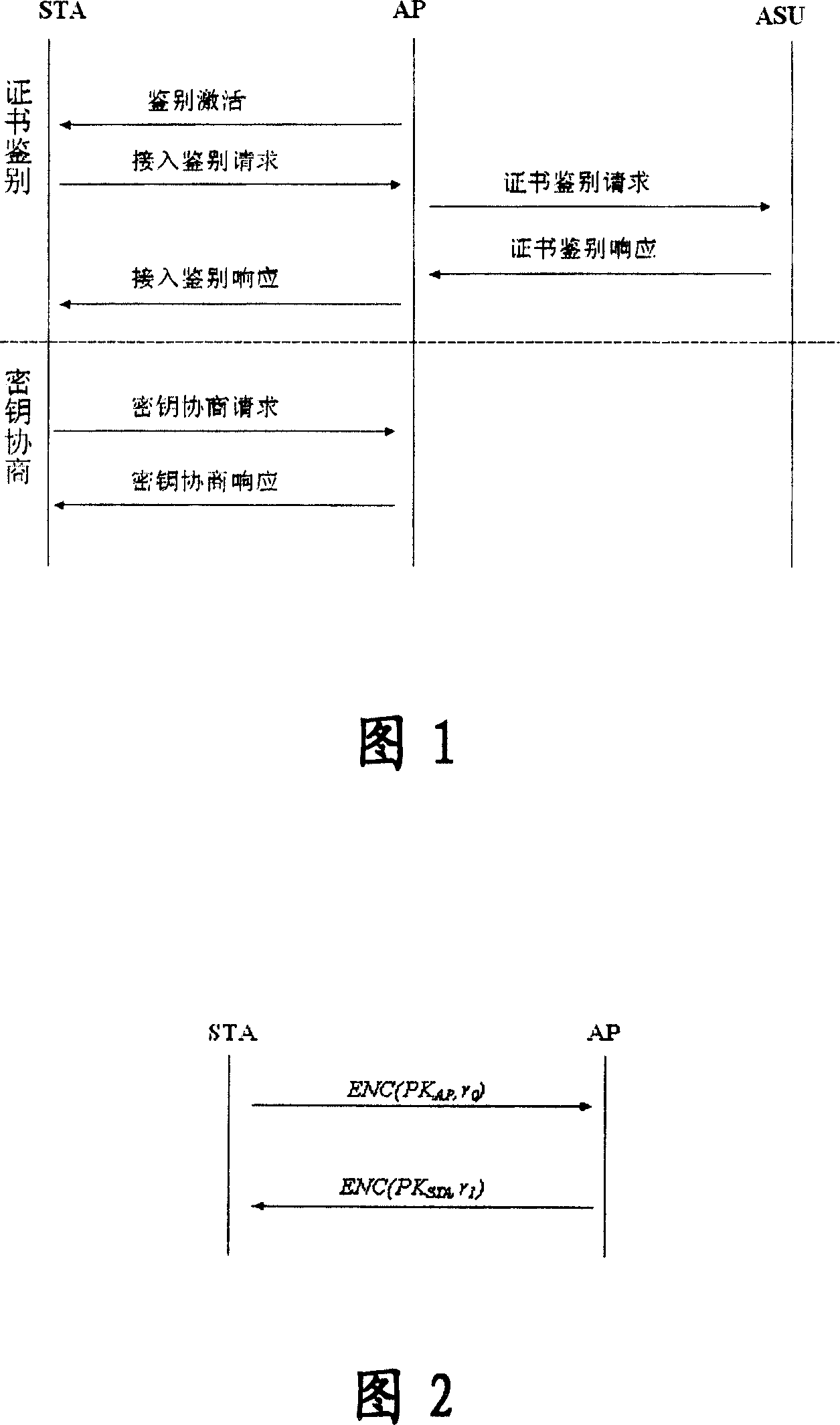
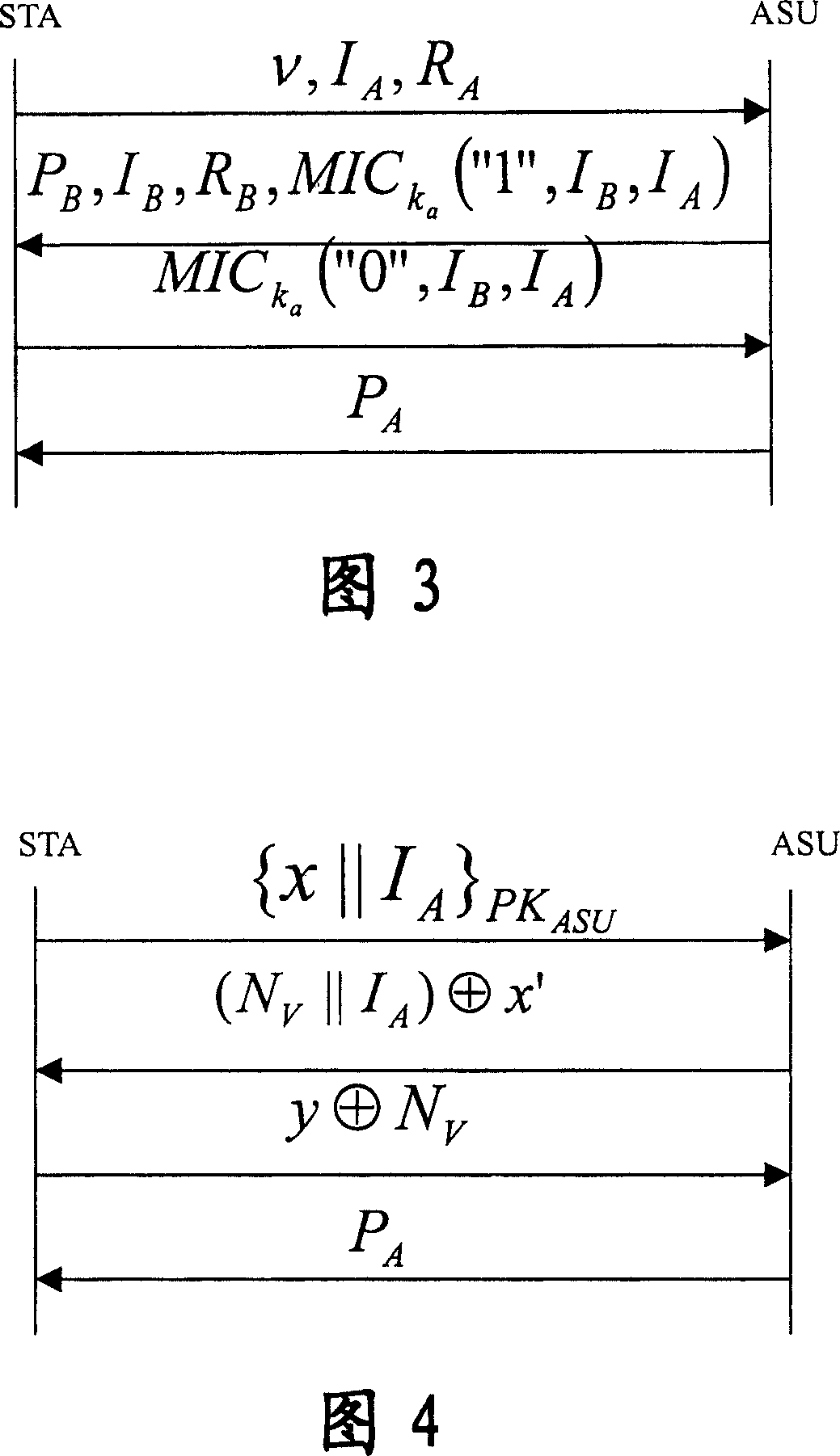
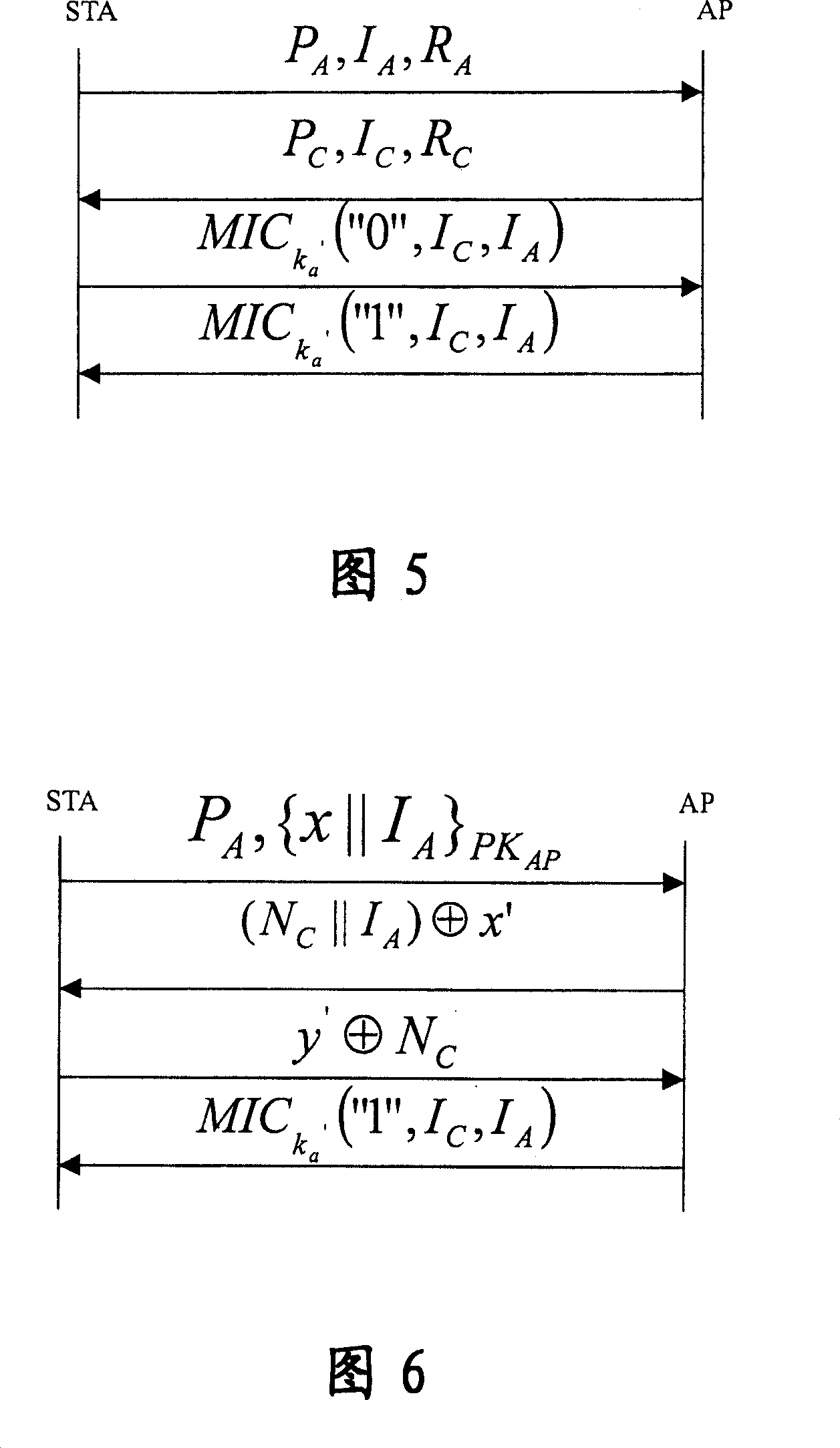
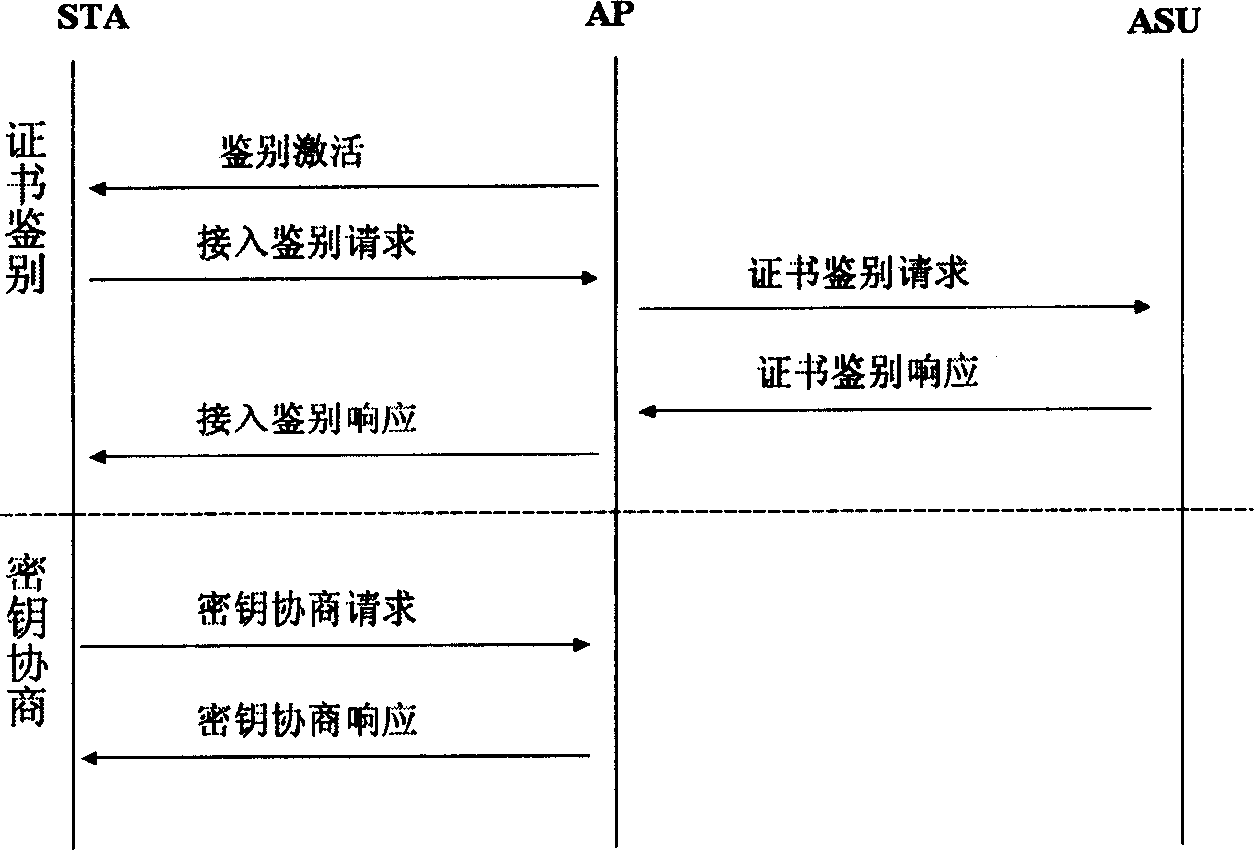
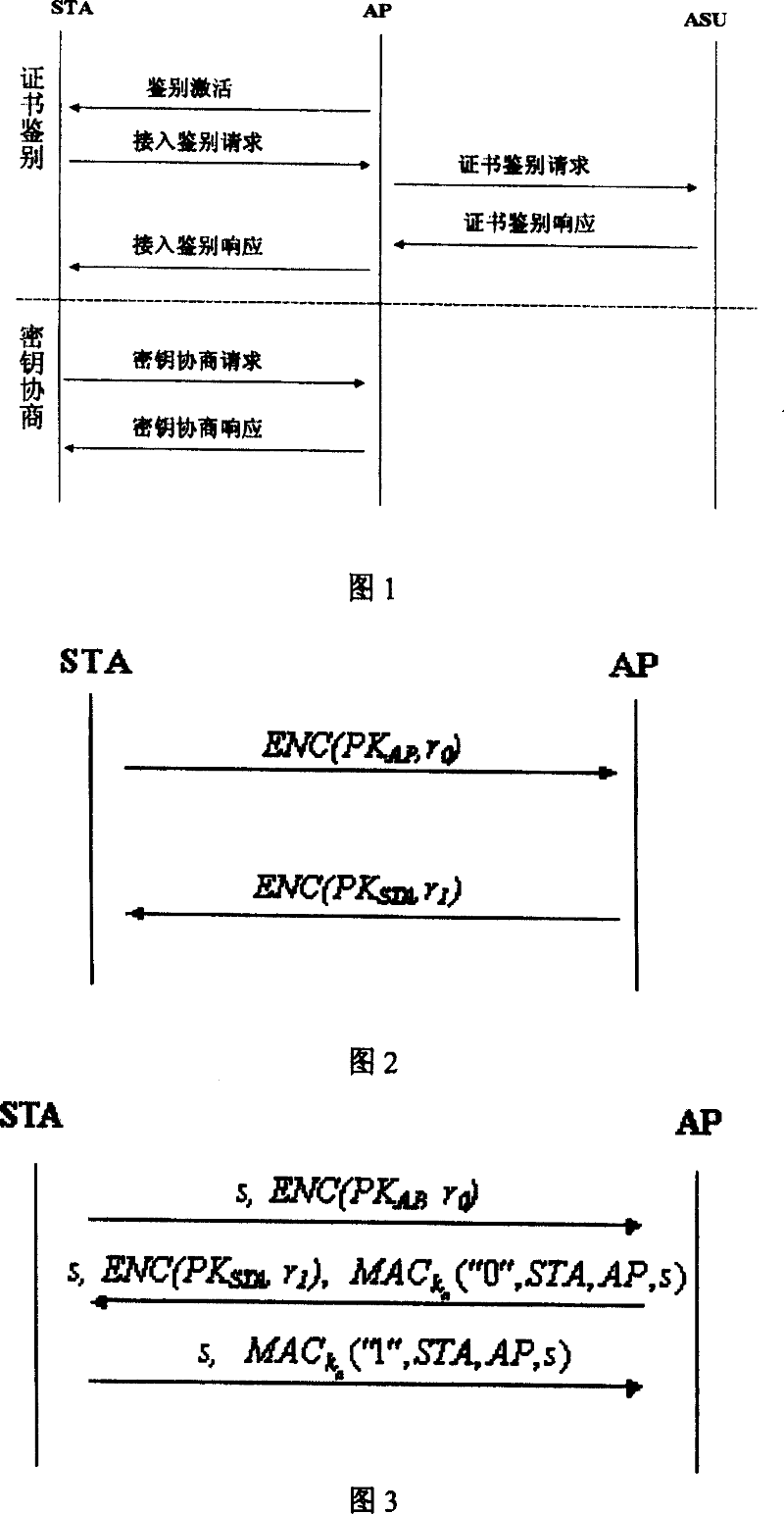
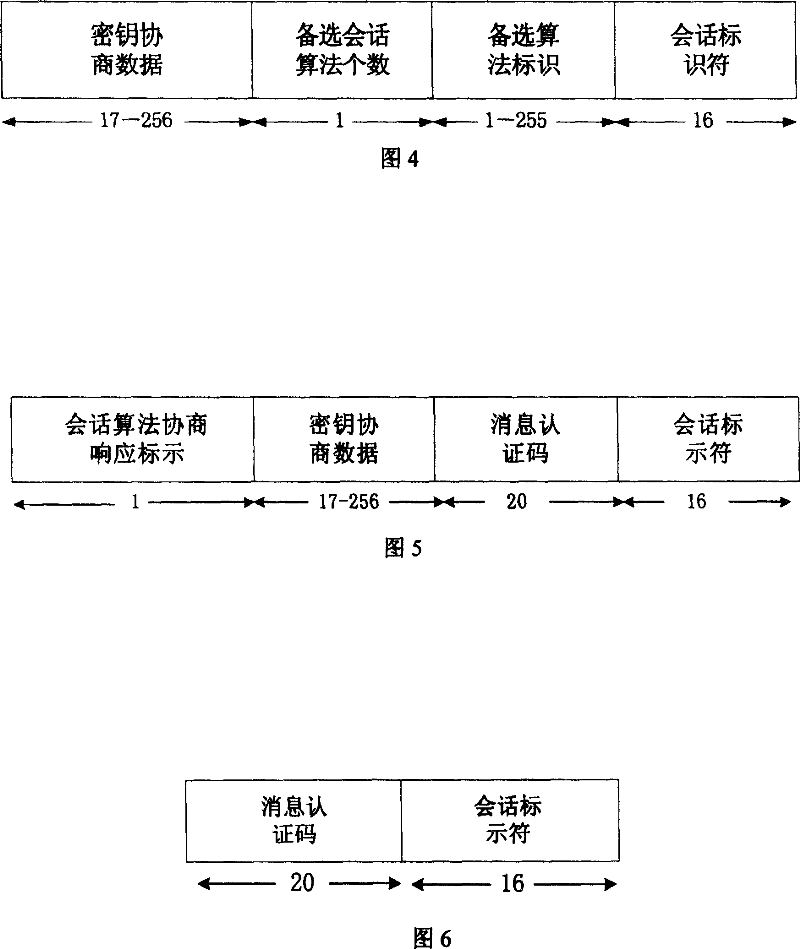
A WAPI authentication and secret key negotiation method and system
InactiveCN101123501ATo achieve the purpose of safetyIncrease flexibilitySynchronising transmission/receiving encryption devicesUser identity/authority verificationClient-sidePublic key certificate
The present invention provides a method and a system for authentication and key negotiation in the WLAN Authentication and Privacy Infrastructure (WAPI), in which an authentication organization is included. The method has two steps. Firstly, a client end and / or an access point apply for a self-verified public key certificate from the authentication organization; and secondly, the identity verification and key negotiation is carried out between the client end and the access point by utilizing the self-verified public key certificate. By the present invention, the quantity of data transmission and on-line calculation is reduced, the security of the authentication sytem is enhanced, and problems exist in the course of identity authentication and key negotiation in the WLAN Authentication and Privacy Infrastructure (WAPI), thus further increasing the security intensity of the WAPI authentication mechanism.
Owner:XIDIAN UNIV +1
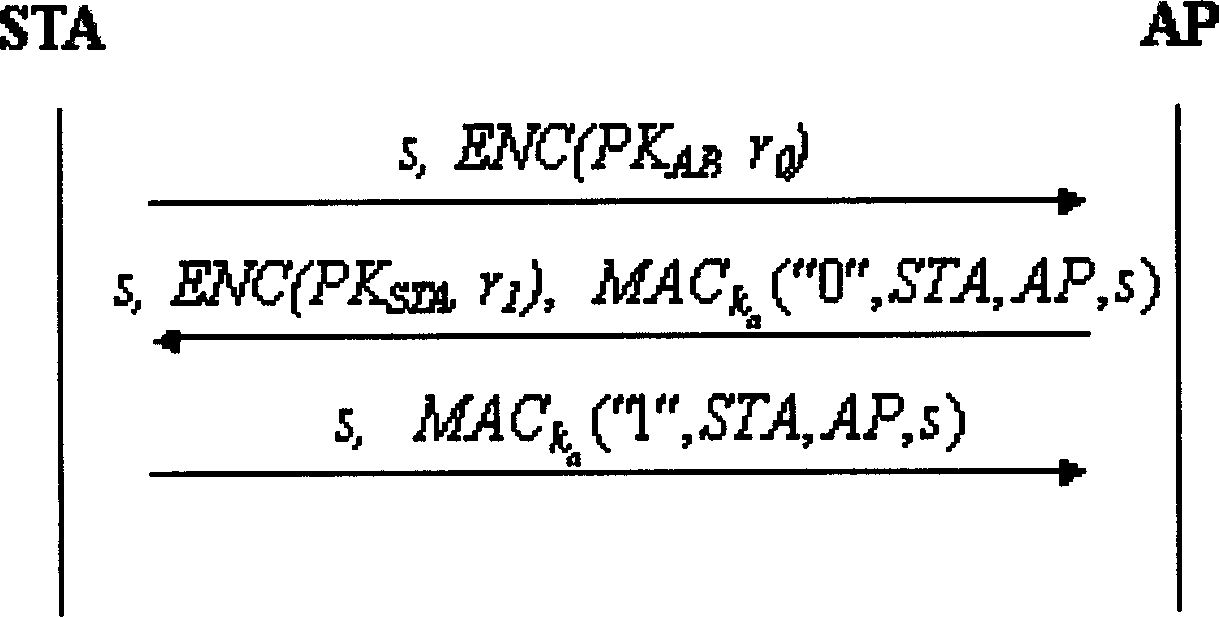
Key agreement method in WAPI authentication mechanism
InactiveCN1665183AThe idea of key agreement has not changedTo achieve the purpose of safetySynchronising transmission/receiving encryption devicesData switching by path configurationMessage authentication codeMobile device
The invention discloses a secret key consulting method in the attestation mechanism of WAPI, solving the problems of ID attestation and secret key consultation of mobile equipment accessing to wireless local-area network. The method arranges three messages: request, response and answer of secret key and their interchanging course: a client-end STA generates a random number r0, encrypts the r0 by the public key of an access point AP and then sends the encrypted r0 and a conversation indication sign s to the AP; the AP decrypts to obtain the r0, selects the other random number r1, and calculates conversation secret key and message attestation code and sends the message attestation code, the indication sign s and the r1 encrypted by public key of the STA; the STA decrypts to obtain the r1 and attests the message attestation code transmitted from the AP to determine to access to the network and output conversation secret key; finally, the STA calculates the other message attestation code and sends it and s together to the AP; the AP attests the message attestation code transmitted by the STA and then outputs conversation secret key and allows the STA to access to the network. The method achieves universal combinable safety strength and implements ID attestation and secret key consultation, able to be used in improving the attestation mechanism in the WAPI.
Owner:XIDIAN UNIV
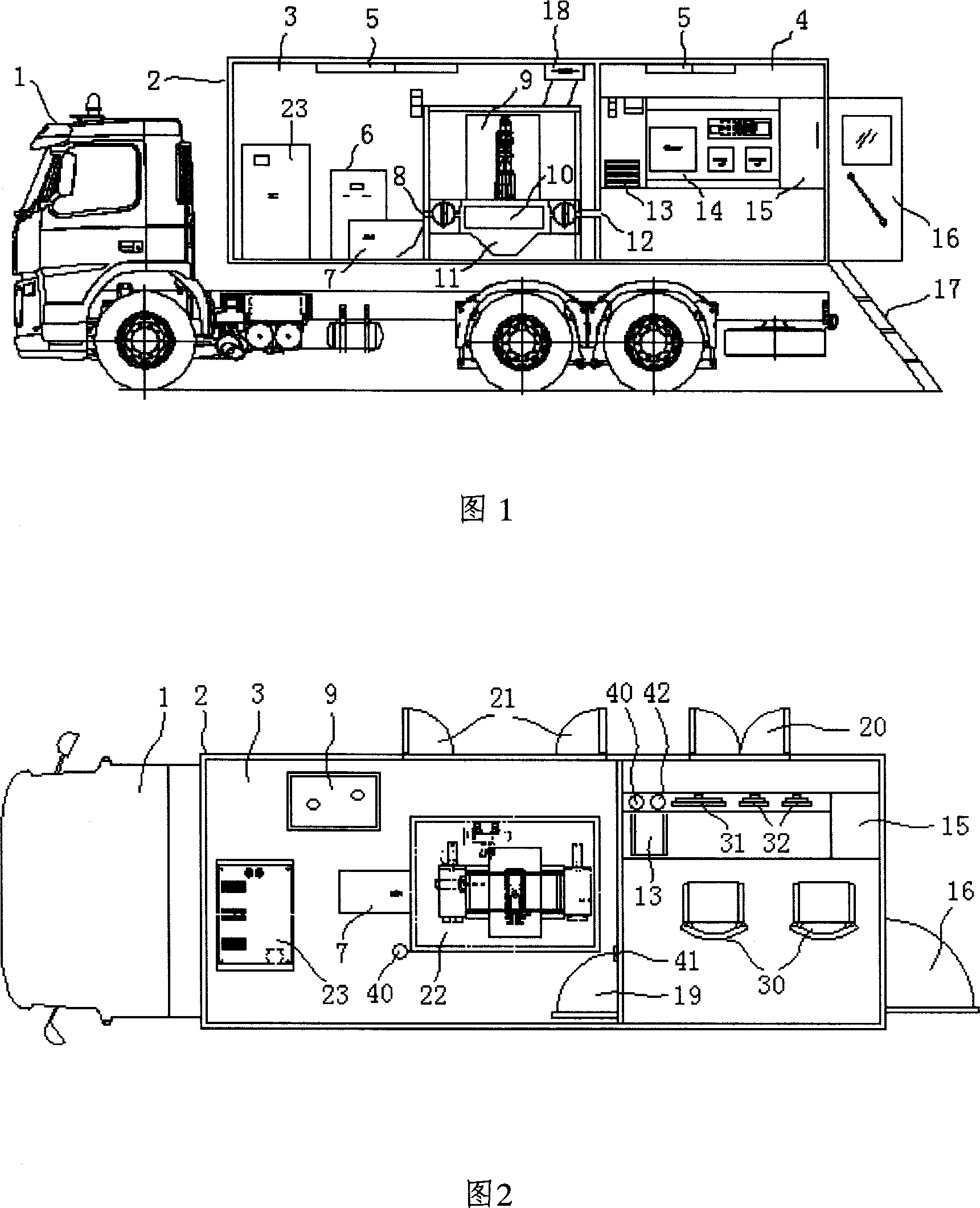
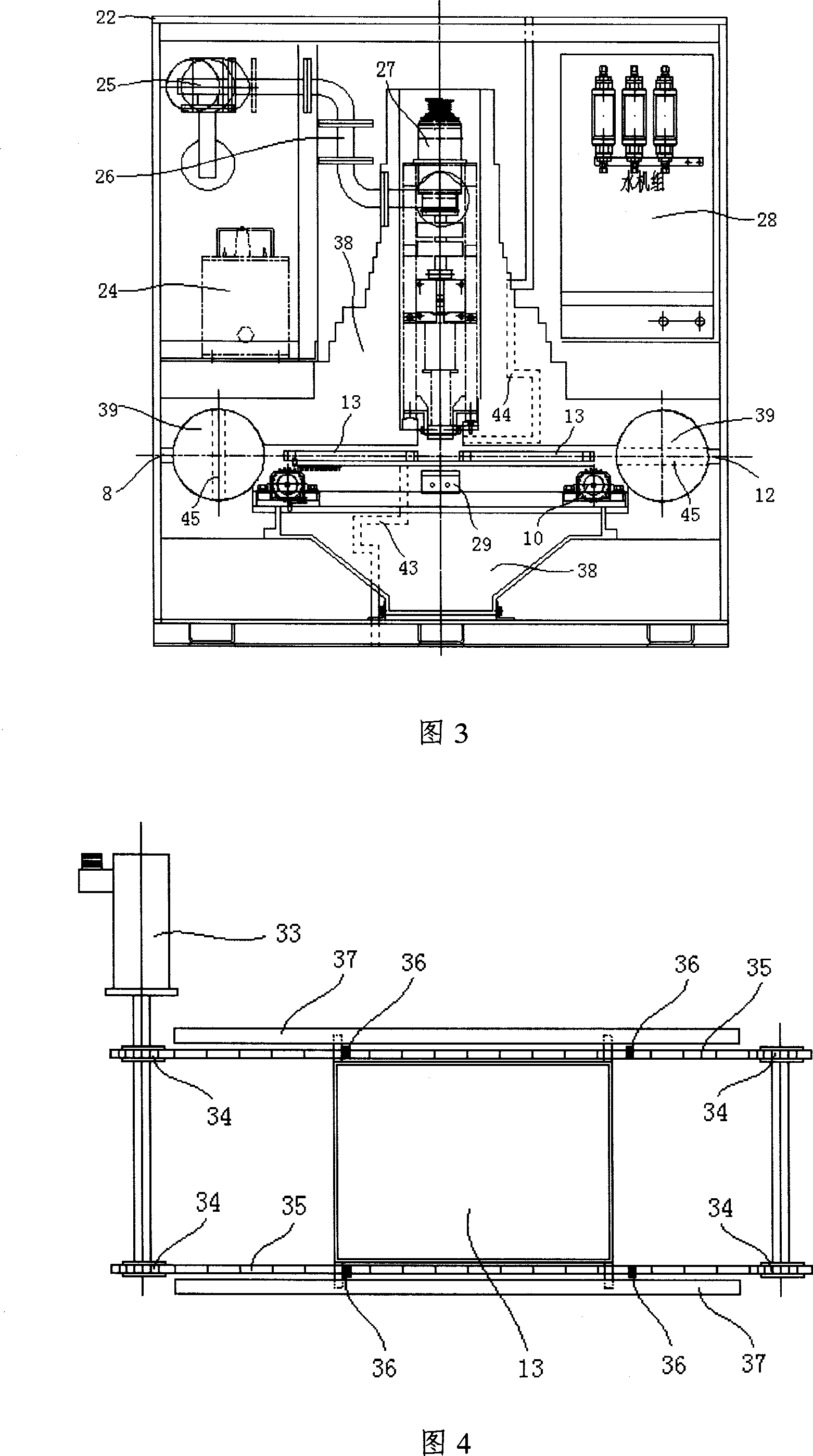
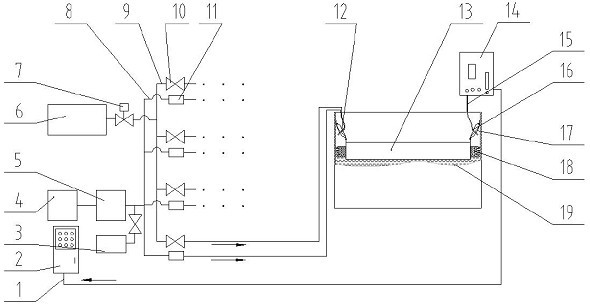
Mobile electron beam irradiation sterilizing installation
The invention relates to an electron beam irradiation sterilization equipment. The movable electron beam irradiation sterilization equipment of the invention consists of an electron beam irradiation accelerator and the control system, a vehicle chassis, a cabin installed on the chassis, an exhaust equipment and a power system installed in the cabin. The electron beam irradiation accelerator is installed in the cabin. The active effects of this invention are that: the electron beam irradiation accelerator and the control system, exhaust equipments and power system are all installed in the cabin of the vehicle chassis with small volume and mobility and flexibility, which can quickly shift in short time and has no special requirements on the applying environment and no extra construction. The invention can rapidly and thoroughly sterilize various kinds of documents and mails to keep them safe, without any damage on the radiated articles or any radiation remaining. Due to high automated integration, easy operation and safety, the invention is suitable to be applied in many domestic and international important organs.
Owner:TSINGHUA UNIV +1
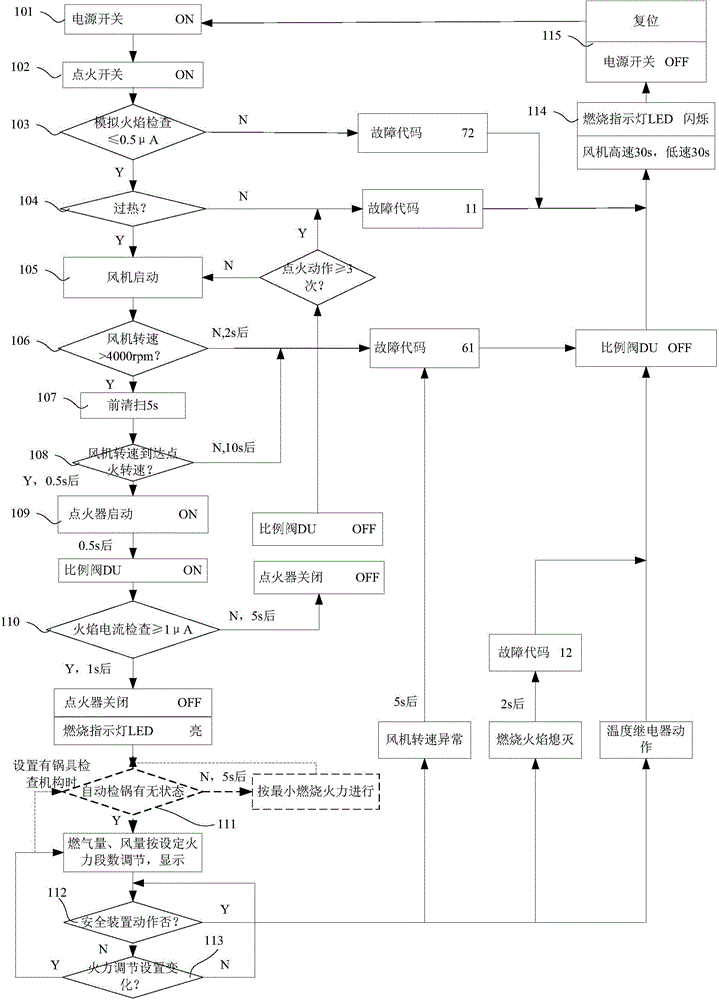
Blowing-type burner control method
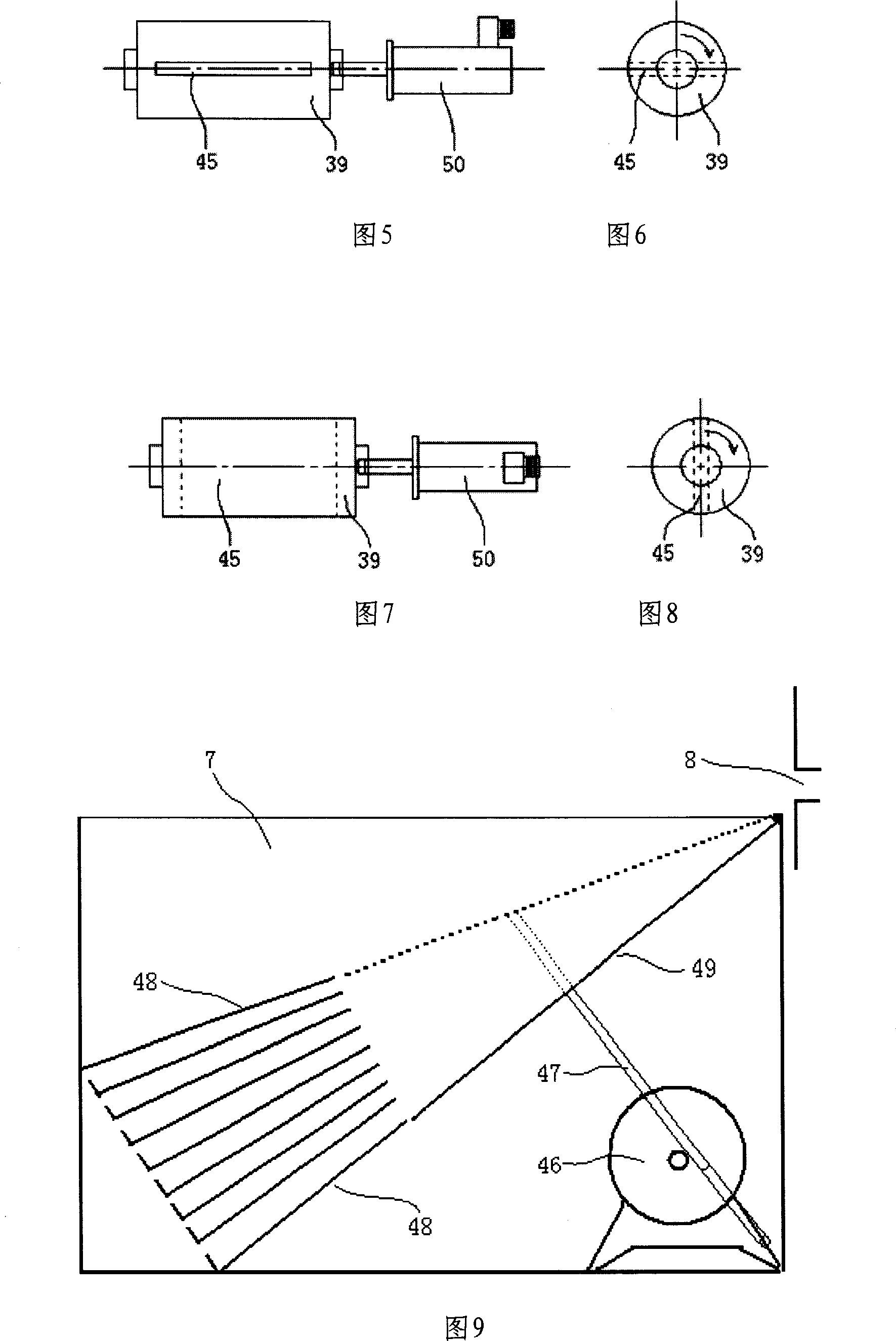
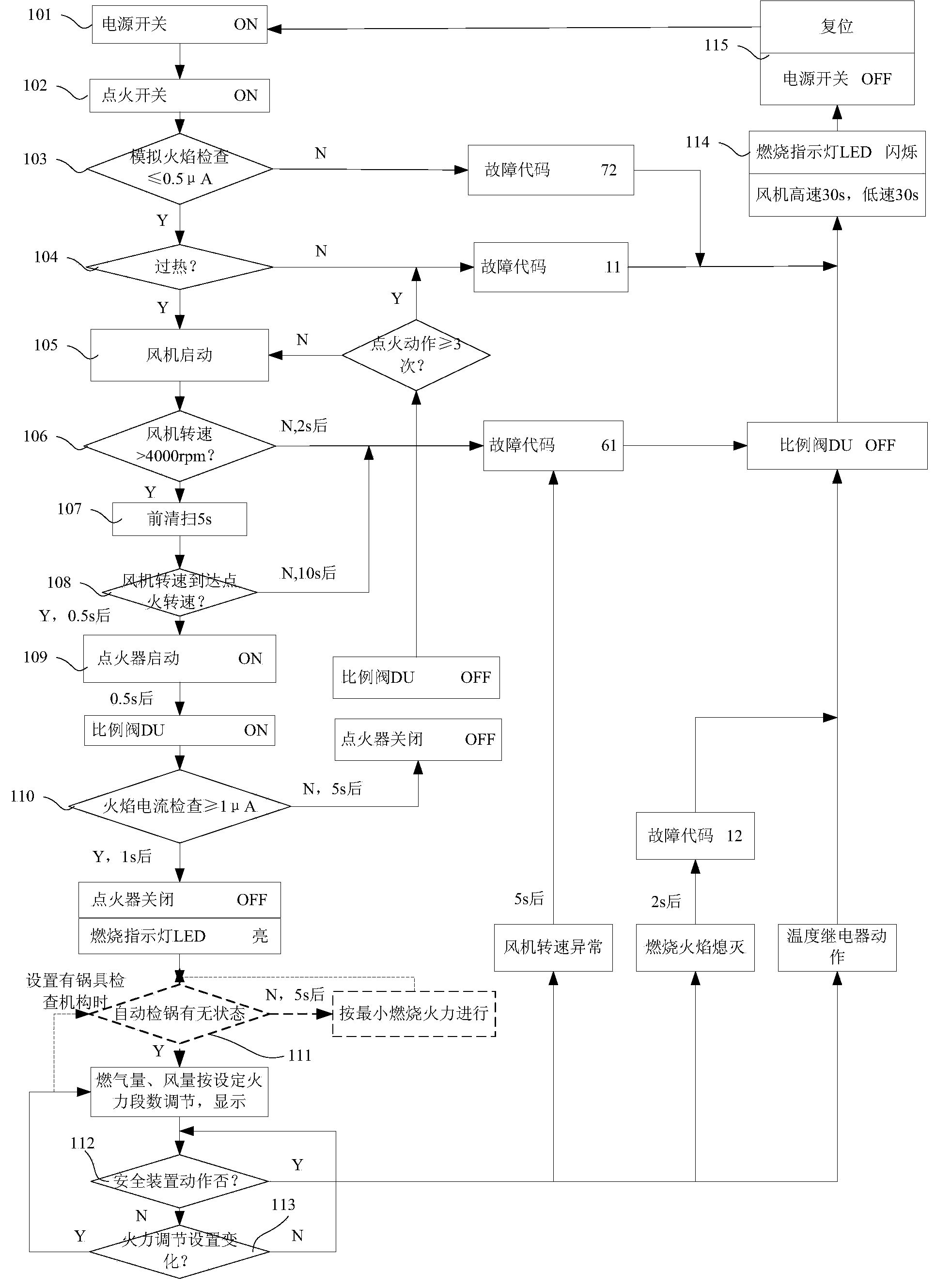
ActiveCN103900103AImprove securityEffectively clean up residueCombustion regulationElectricityStopped work
The invention relates to a blowing-type burner control method which comprises the following steps that an electric controller receives an ignition instruction and conducts slash fire detection, overheat detection and draught fan rotating speed detection sequentially; the electric controller controls an air blower to blow and sweep a combustion box at the rotating speed a; the electric controller controls the rotating speed of the air blower to be a set ignition rotating speed b, an igniter is started, a power shut-off valve on a gas proportion valve assembly is controlled to be opened, and an electric adjustment opening in the gas proportion valve assembly is opened to an ignition opening degree according to a set ignition current; after the successful ignition, the electric controller synchronously controls the opening degree of the electric adjustment opening and the rotating speed of the air blower according to the burning power input by a manipulator; when the electric controller receives a stop work instruction from the manipulator, the gas proportion valve assembly is closed and the air blower continues to run for set period of time. Compared with the prior art, the blowing-type burner control method has the advantages of being high in heat exchange efficiency, high in safety and the like.
Owner:SHANGHAI HESEN ELECTRO MACHINERY
External floating roof petroleum storage tank water mist safe protection system and protection method
ActiveCN102417081AImprove active safety protection performanceControl concentrationLarge containersControl systemEnvironmental engineering
The invention discloses an external floating roof petroleum storage tank water mist safe protection system and a protection method; the external floating roof petroleum storage tank water mist safe protection system comprises a control system, a gas detection analyzer and an inert medium generating system; the control system is connected with the gas detection analyzer; the gas detection analyzer is communicated with a primary sealing space and a secondary sealing space of a petroleum storage tank through a gas pipe for detection and analysis; the inert medium generating system is connected with water mist generators which are arranged in the primary and the secondary sealing spaces of the petroleum storage tank; and the inert medium generating system comprises a water tank which is communicated with the liquid input ends of the water mist generators through high-pressure water pumps and an inert gas storage device which is communicated with the gas input ends of the water mist generators through selection valves. According to the invention, because water mist with inert media is filled into the primary and the secondary sealing spaces of the petroleum storage tank, the petroleum-gas mixture content in the sealing spaces is controlled within a set range, so that the problem that the primary and the secondary sealing spaces of the external floating roof petroleum storage tank are easy to explode.
Owner:VITALONG FIRE SAFETY GRP
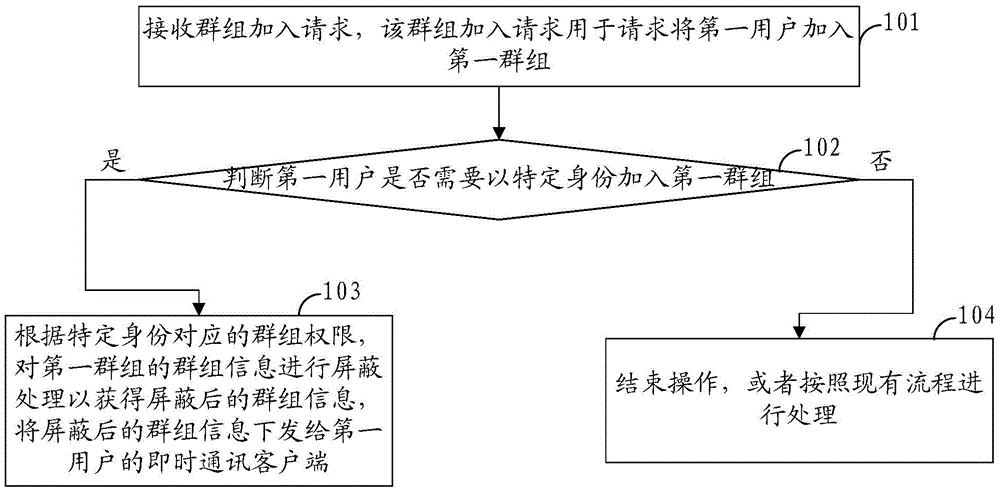
Information processing method based on instant communication and apparatus thereof
ActiveCN105610681ATo achieve the purpose of safetyMeet instant messaging needsDigital data authenticationData switching networksInformation processingUser needs
The invention provides an information processing method based on instant communication and an apparatus thereof. The method comprises the following steps of receiving a group joining request, wherein the group joining request is used to request to join a first user in a first group; determining whether the first user needs to join in the first group as a specific identity mode; and if a determination result is yes, according to a group authority corresponding to the specific identity, carrying out shielding processing on group information of the first group so as to acquire the shielded group information and issuing the shielded group information to an instant communication client of the first user. In the invention, an instant communication demand can be satisfied and simultaneously an information safety problem is solved.
Owner:ALIBABA GRP HLDG LTD
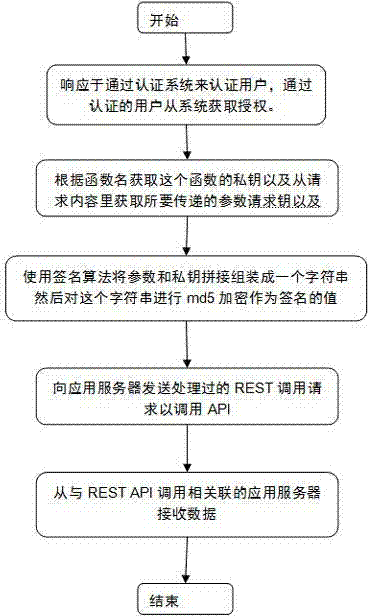
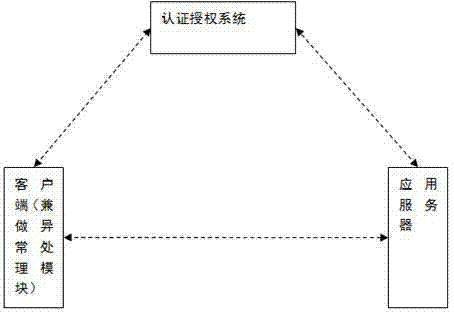
REST security system based on signature mechanism
InactiveCN103095731ATo achieve the purpose of safetyUser identity/authority verificationUsage modelEncryption
The invention provides a REST security system based on a signature mechanism. According to the REST security system, the signature mechanism is used as the core of the system, sessionkey and an md5 encrypted message of a parameter are encapsulated in a http request, hostile attacks such as interception, data tampering and the like carried out by a hacker in transmission are confronted through the transmission of the encrypted data, meanwhile, the encrypted data can also be used for protecting private information of a user, and a safe purpose is achieved. Compared with the prior art, the REST security system based on the signature mechanism has the advantages that a REST usage model which is based on signature is adopted, through certification and authority, an illegal user is limited to access application before an application program interface (API) method is called, then a private key of an application that the API belongs to is obtained after the user passes the certification and the authority to access the API, parameters of a RESTAPL request is obtained in the request, the parameters are organized according to an agreed form of application, namely the parameters and the private key, and then md5 encryption is conducted, the data after being encrypted is placed in the request, and therefore a safe aim is achieved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Strategic location protection radar network detection method adopting forward scattering radar
InactiveCN102680970AEfficient detectionOvercoming detection difficultiesRadio wave reradiation/reflectionForward scatterRadar network
The invention provides a strategic location protection radar network detection method adopting a forward scattering radar, which aims at protecting the safety of the airspace of a strategic location, realizing effective detection of a low-altitude flying small target and forming continuous, stable and precise target track estimation, and belongs to the technical field of radar networking detection. According to the method provided by the invention, the continuous, stable and precise target track estimation is formed and the purpose of protecting the safety of the airspace of the strategic location is achieved by determining a coverage model of the forward scattering radar, selecting a topological structure with optimal topological units based on a genetic algorithm, determining a protection area, comprehensively covering the protection area according to the comprehensive coverage principle and performing target detection, track fusion and other steps.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
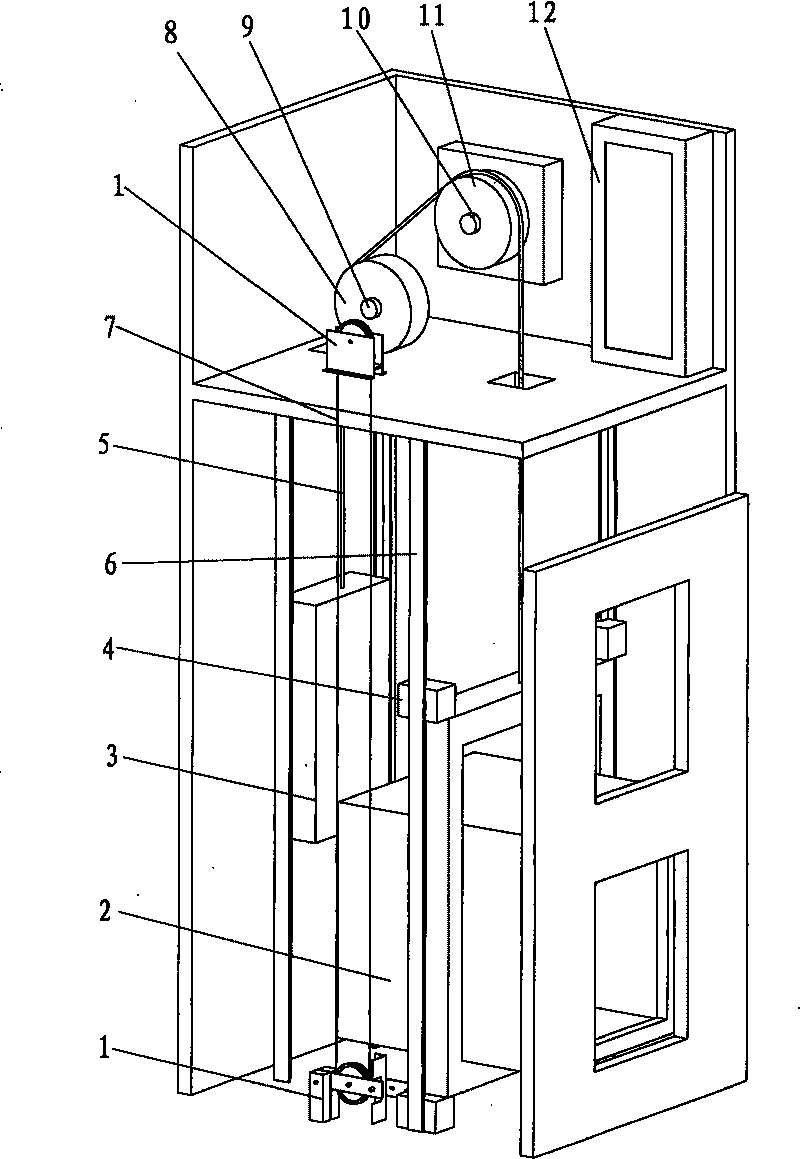
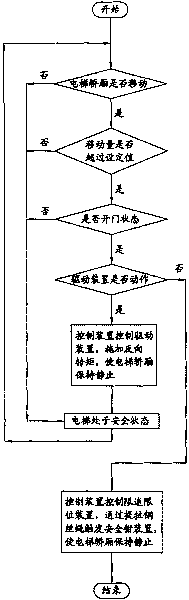
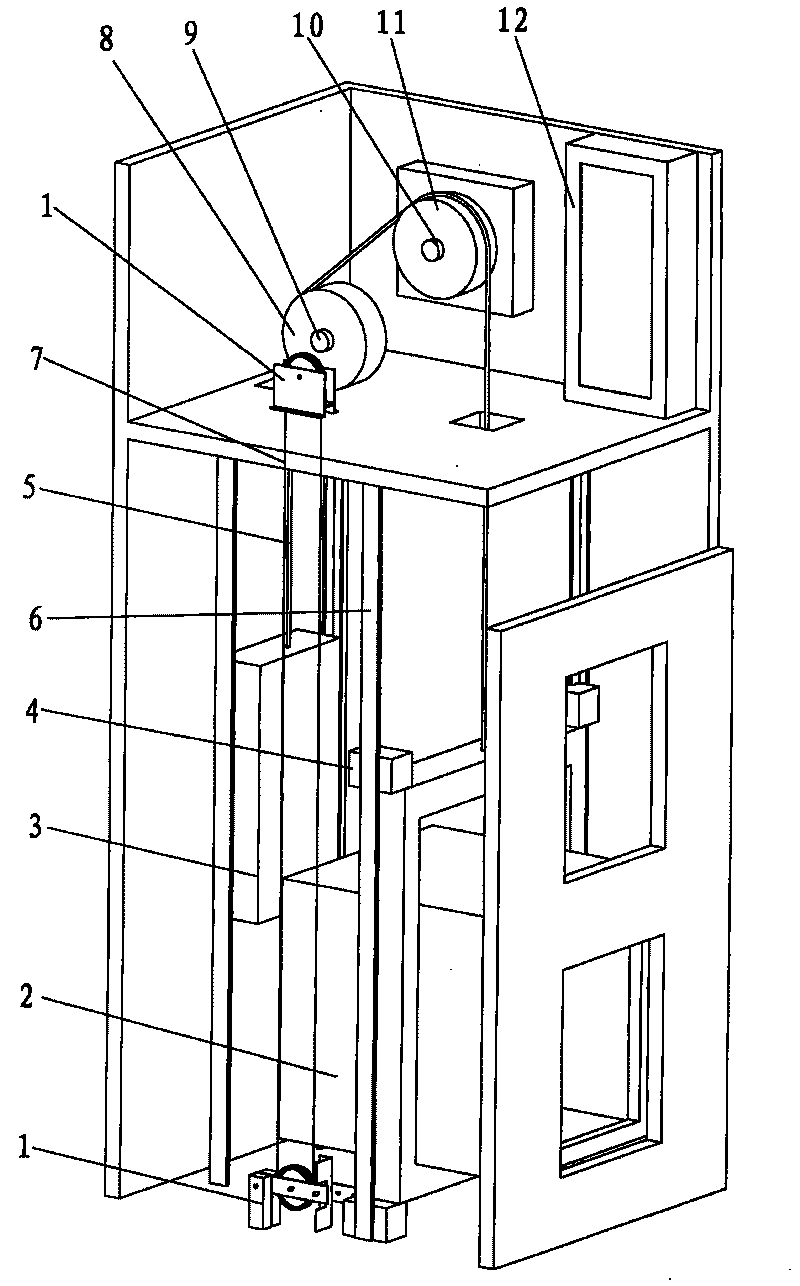
Safety protecting system of elevator door zone
The invention discloses a safety protecting system of an elevator door zone, mainly comprising a control device, a first feedback element arranged on a driving device, and a second feedback element arranged on a rope wheel. When the control device monitors the condition that an elevator is open and the rotating displacement of an active wheel fed back by the first feedback element arranged on the driving device exceeds a set value, the control device sends out a braking command for controlling the driving device to apply reverse force in order to prevent the driving device from rotating; when the control device monitors the condition that the elevator is open and the rotating displacement of the rope wheel fed back by the second feedback element arranged on the rope wheel exceeds the set value, the control device sends out the braking command for controlling a speed restriction spacing device to trigger a safety clamp device to act; and a car of the elevator is firmly clamped on guiding rails. The safety protecting system is used for monitoring slippage and glide when the elevator door zone is open, actively executes a safety protecting function and effectively avoids generating serious accidents of clamping passengers and the like.
Owner:XJ SCHINDLER XUCHANG ELEVATOR
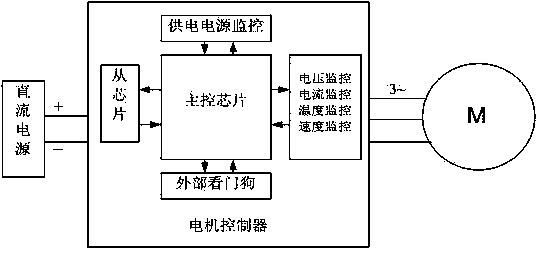
Vehicle motor control system and safety monitoring method
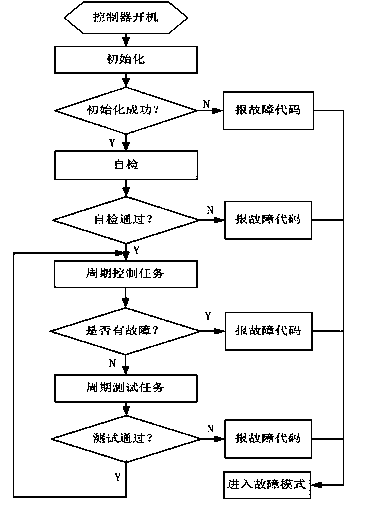
ActiveCN103475300AAdd boot self-testTo achieve the purpose of safetyProgramme controlAC motor controlControl systemComputer module
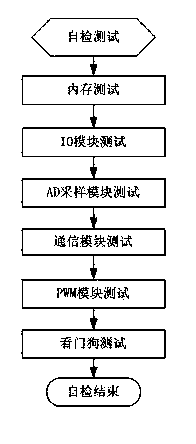
The invention discloses a safety monitoring method of a vehicle motor control system and a system using the method. The safety monitoring method comprises the following steps that 1), all modules of a main control chip are subjected to initialization configuration, 2) all the modules of the main control chip are subjected to self detection, and the self defection comprises testing of an internal storage, an IO module, an AD sampling module, a communication module, a PWM module, and a watchdog module, 3) a system period control task is carried out, and 4) a system period testing task is carried out. According to the safety monitoring method and the system, on the premise of not changing monitoring of hardware and software of an original system, starting self detection of the system and detection and monitoring for the overall operation state in cooperation with a sub chip are added, the purpose of overall system safety can be achieved, the system is slightly changed, cost is low, and safety of system operation can be improved.
Owner:奇瑞新能源汽车股份有限公司
Safety socket
InactiveCN102195218ATo achieve the purpose of safetyWith energy saving effectCoupling device detailsActive safetyComputer module
The invention provides a safety socket comprising a seat body and a circuit module, wherein one or more jacks connected to the inner side are arranged on the surface of the seat body, a relay module connected with a power supply is arranged on a circuit board of the circuit module at the inner side of the seat body and is electrically connected with a single-pole double-throw type active safety protection circuit, the base side edge of the active safety protection circuit connected with the relay module is electrically connected with a switch clamp, the other side of the switch clamp is provided with a first sheet body in contact with the switch clamp after the switch clamp rotates under heating, the first sheet body is electrically connected with an integrated circuit capable of transmitting a signal to the relay module to close the relay module, and the other end of a base inside the active safety protection circuit is electrically connected with one or more sockets. Because high temperature generated due to an abnormal power supply state is utilized to enable the active safety protection circuit to be switched, a power supply only supplies power to the socket(s) or one of a power supply module and the integrated circuit, and thus, the purposes of improving use safety and saving energy by stopping supplying power to the socket(s) are achieved.
Owner:SEEKER
Network access method and device
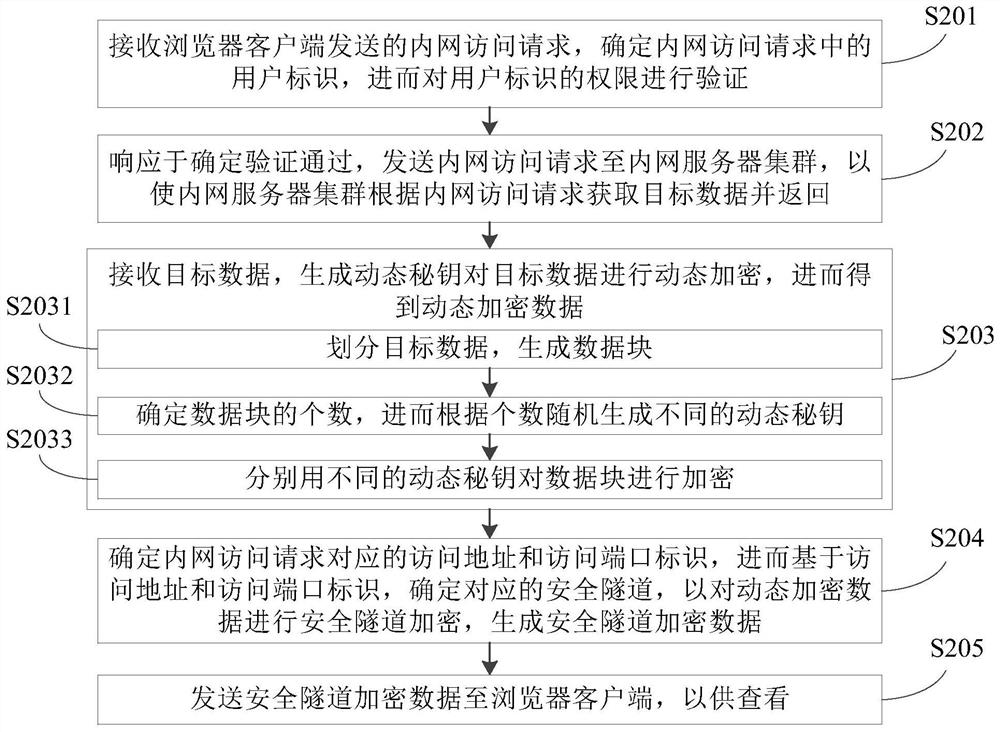
ActiveCN113347206AAchieve securityTo achieve the purpose of safetyMultiple keys/algorithms usageAccess methodEngineering
The invention discloses a network access method and device, and relates to the technical field of computers, and the method comprises the steps: receiving an intranet access request, determining a user identifier in the intranet access request, and verifying the authority of the user identifier; in response to determining that the verification is passed, sending an intranet access request to an intranet server cluster, so that the intranet server cluster obtains target data according to the intranet access request and returns the target data; receiving target data, and generating a dynamic secret key to dynamically encrypt the target data to obtain dynamic encrypted data; determining an access address and an access port identifier corresponding to the intranet access request, determining a corresponding secure tunnel based on the access address and the access port identifier, performing secure tunnel encryption on the dynamic encrypted data, and generating secure tunnel encrypted data; and sending the secure tunnel encrypted data to the browser client for viewing. When a user has a frequent internal and external network access requirement, the internal and external networks do not need to be switched frequently, and the purpose of information security is achieved at the same time.
Owner:CCB FINTECH CO LTD
Logic binding method for preventing PC (personal computer)hard disk information from theft
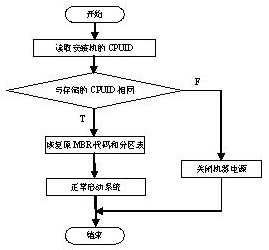
InactiveCN101847130APrevent leakageTo achieve the purpose of safetyUnauthorized memory use protectionMedia access controlPersonal computer
The invention relates to a safety protection method of computer information, in particular to a logic binding method for preventing PC hard disk information from theft, which is characterized in that the hard disks of the computers and computers where the hard disks are located are logically bound by a software mode to enable the hard disks to correspond to the computers where the hard disks are located one to one, and the hard disks which do not correspond to the environments of the computers do not work. The logic binding method can carry out protection by CPUID (Central Processing Unit Identification), and each hard disk corresponds to CPUID information, which ensures that the computers can be started after the hard disks correspond the CPUID. In the invention, a network card MAC (Media Access Control) address judgment procedure is installed, and under the condition that the repeat happens on CPUID, the started computers carry out network card MAC address judgment; the MAC address of each network card is unique, and thereby, the hard disk information of the computers is further protected. The invention logically binds the hard disks and the assorted computers from multiple angles, and thereby ensuring that the hard disk information can not be illegally stolen by computer hard disk crackers, effectively preventing the hard disk information from being revealed, and achieving the goal for information safety.
Owner:DALIAN NATIONALITIES UNIVERSITY
New energy automobile fire early warning control strategy
PendingCN111497743ATo achieve the purpose of safetyFire rescueSignalling/lighting devicesEarly warning systemDriver/operator
The invention relates to the technical field of pure electric vehicle fire early warning system application, in particular to a new energy vehicle fire early warning control strategy, which comprisesa fire early warning system, and the fire early warning system comprises first-level early warning, second-level early warning and third-level early warning. Safety hazards caused by harmful gas leakage, smoke and fire hazards of high-temperature and high-voltage batteries in the running process of the vehicle can be avoided, battery fire early warning is divided into three levels, the whole vehicle is controlled according to the fire alarm level, a driver is reminded to conduct corresponding treatment, and the safety purpose is achieved.
Owner:JIANGXI KAMA BONLUCK BUSINESS BUS
Lithium ion power battery explosion protection cover
InactiveCN101867026ASolution to short lifeLong life, long safety levelCell component detailsPower batteryExplosion protection
The invention relates to a lithium ion power battery explosion protection cover, belonging to the technical field of the lithium ion battery. The lithium ion power battery explosion protection cover comprises a cover plate and an explosion-protection film, wherein the cover plate is provided with an explosion-protection hole. The lithium ion power battery explosion protection cover is characterized in that the explosion-protection hole is provided with a rubber sealing plug, and the rubber sealing plug is connected with a pressure spring. The lithium ion power battery explosion protection cover has novel structure, high safety level and good explosion protection effect, is assembled compactly, is convenient to process and not easy to leak electrolyte and can ensure that the lithium ion power battery has long service life, thereby having wide application range.
Owner:TIANJIN BATTERY ELECTRICAL
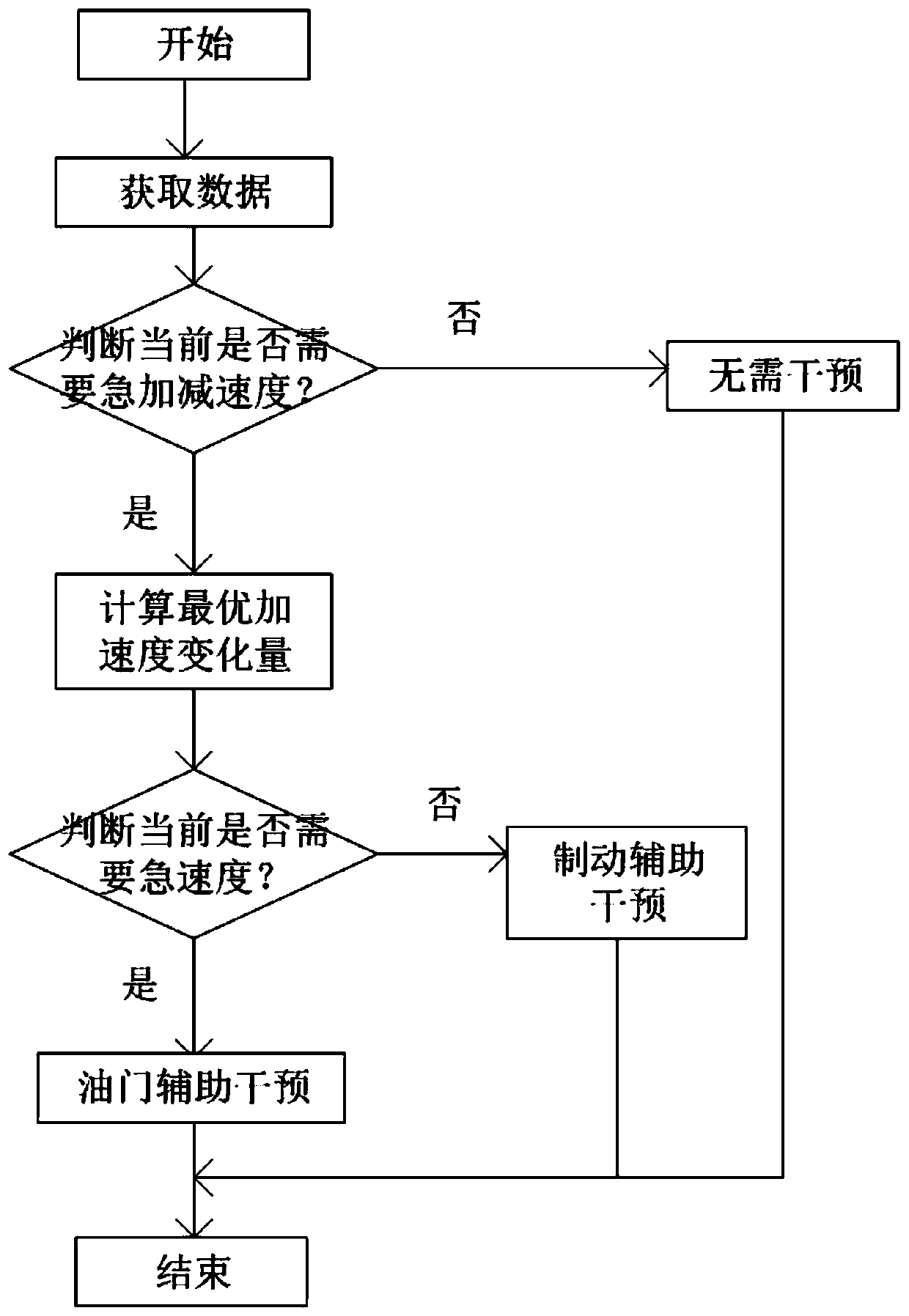
Driving active intervention system and method based on acceleration change rate optimization
ActiveCN111348039AReduce traffic accidentsTo achieve the purpose of safetyExternal condition input parametersControl theoryAutomotive engineering
The invention belongs to the field of automobile energy-saving methods, and discloses a driving active intervention system and method based on acceleration change rate optimization. By obtaining the front vehicle distance and the current vehicle speed, the optimal acceleration variable quantity which is uniformly changed when the current vehicle accelerates and decelerates suddenly under the safety condition is calculated, the accelerator or braking active intervention vehicle acceleration is assisted, the accelerator and pedal opening degree is reasonably adjusted, and active intervention ondriving operation is achieved. According to the method and the system, the purpose of reducing energy consumption can be achieved.
Owner:CHANGAN UNIV
Polishing device for bamboo summer sleeping mat machining
InactiveCN108942555AEasy to useSafe and reliable structural designCane mechanical workingWood working apparatusEngineeringDrive motor
The invention discloses a polishing device for bamboo summer sleeping mat machining. The polishing device for bamboo summer sleeping mat machining comprises a first drive motor, a second drive motor,a polishing machine, a shearing machine, seal doors and a dust collector. The seal doors comprise an inlet door and an outlet door. The seal doors are movably installed on the two sides of equipment through hinges. The dust collector is fixed to the middle of a fixing plate through bolts. The equipment outer wall of the side, close to the inlet door, of the dust collector is provided with a PLC, atouch controller and a rotation speed meter. The polishing machine and the first drive motor are both fixed to the lower end of the dust collector through bolts. The lower end of the portion, betweenthe polishing machine and the inlet door, of the fixing plate is fixedly provide with the shearing machine through bolts. The conveyer belt is arranged below the shearing machine. The conveyer belt is fixedly installed on the base through bolts. The polishing device for bamboo summer sleeping mat machining has the advantages of being reasonable in structural design, safe, convenient to use and the like and can be generally used and popularized.
Owner:湖南奇宏林业股份有限公司
Key agreement method in WAPI authentication mechanism
InactiveCN100358282CThe idea of key agreement has not changedTo achieve the purpose of safetySynchronising transmission/receiving encryption devicesData switching by path configurationMessage authentication codeMobile device
The invention discloses a secret key consulting method in the attestation mechanism of WAPI, solving the problems of ID attestation and secret key consultation of mobile equipment accessing to wireless local-area network. The method arranges three messages: request, response and answer of secret key and their interchanging course: a client-end STA generates a random number r0, encrypts the r0 by the public key of an access point AP and then sends the encrypted r0 and a conversation indication sign s to the AP; the AP decrypts to obtain the r0, selects the other random number r1, and calculates conversation secret key and message attestation code and sends the message attestation code, the indication sign s and the r1 encrypted by public key of the STA; the STA decrypts to obtain the r1 and attests the message attestation code transmitted from the AP to determine to access to the network and output conversation secret key; finally, the STA calculates the other message attestation code and sends it and s together to the AP; the AP attests the message attestation code transmitted by the STA and then outputs conversation secret key and allows the STA to access to the network. The method achieves universal combinable safety strength and implements ID attestation and secret key consultation, able to be used in improving the attestation mechanism in the WAPI.
Owner:XIDIAN UNIV
Kitchen/bathroom basin drainage system and kitchen/bathroom basin drainage system control method
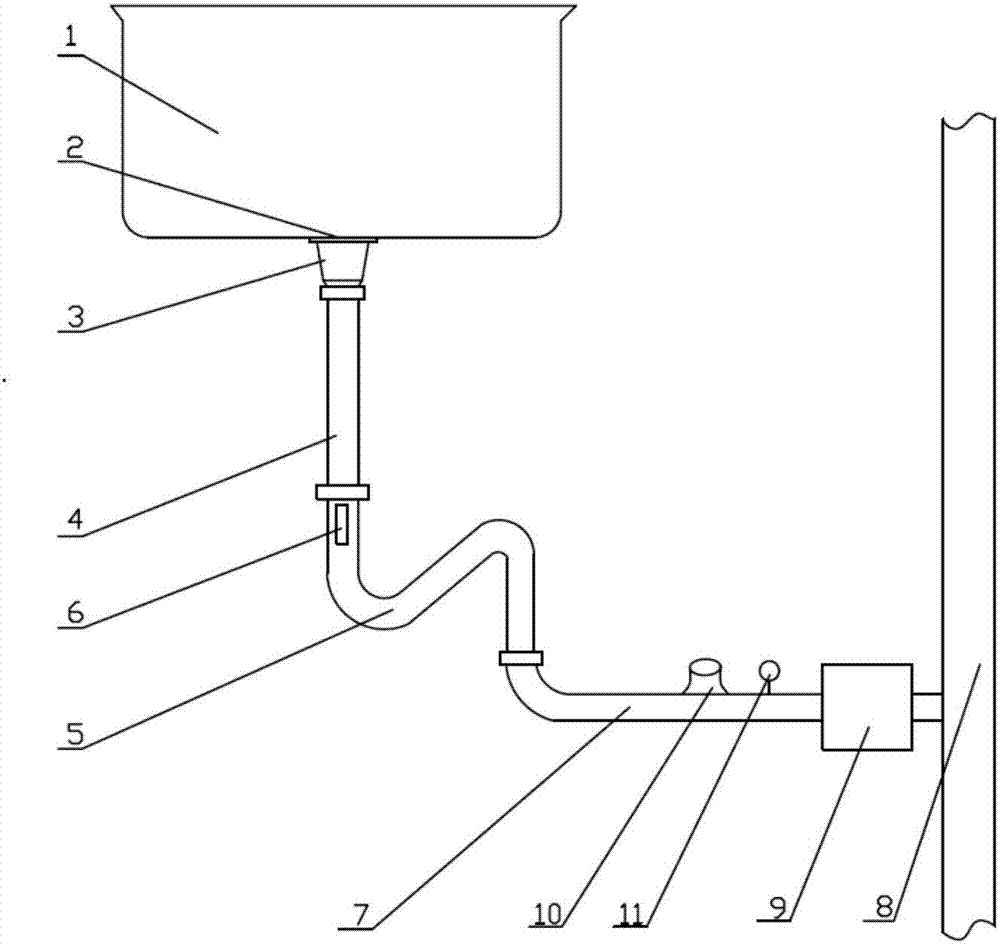
ActiveCN106948433AExplain patencyReal-time monitoring of dredging effectDomestic plumbingEngineeringLiquid level sensor
The invention relates to a kitchen / bathroom basin drainage system for smart home and a kitchen / bathroom basin drainage system control method for smart home. The kitchen / bathroom basin drainage system comprises a basin body, a sewer pipe, a branch drain and a main controller. The basin body has a drain hole positioned at the bottom. A garbage filtration bowl is arranged in the drain hole. A first end of the sewer pipe is connected to the drain hole. The sewer pipe has an odour-isolating elbow. The sewer pipe is provided with a liquid level sensor above the odour-isolating elbow. An initiating end of the branch drain is connected to a second end of the sewer pipe, and a termination end of the branch drain is connected to a main sewer. The branch drain is provided with at least one vibrator. A flow sensor capable of detecting flow velocity of a liquid in the branch drain is also arranged in the branch drain. The liquid level sensor and the at least one vibrator are respectively communicated with the main controller, and the main controller has an alarm function.
Owner:TERMINUSBEIJING TECH CO LTD
Bluetooth-controlled and Freely-opened/closed door and locking magnetic feedback door system
InactiveCN104635587ATo achieve the purpose of safetyEasy to operateProgramme controlComputer controlControl engineeringElectric machinery
The invention provides a Bluetooth-controlled and Freely-opened / closed door and locking magnetic feedback door system. The device is composed of a Bluetooth module, a single microcomputer chip system, magnetic induction modules, a transmission rod motor module, electric mechanical lock modules, an alarming module, a power supply module and an intelligent terminal, and is characterized in that long-distance information interaction is carried out by the intelligent terminal and the Bluetooth module, so that a door is controlled by a single microcomputer chip to be opened and closed by a free angle and is adapted to different user requirements; meanwhile, a door lock is remotely controlled to be locked; on the previous basis of the system, a magnetic induction switch is automatically switched on by the system to detect whether the door is really locked or not after the door is locked; if the door is unlocked, an alarm makes sounds to remind a user of carrying out door locking operation for one time and the safety aim is realized; when the intelligent terminal is met outsides the door or the system has no power, the lock is opened by an original mechanical lock key; when the user stands indoors, the door can be opened by a manual module, so that the emergency effect is realized; the system is simple to operate, convenient and practical and safe.
Owner:桑露萍
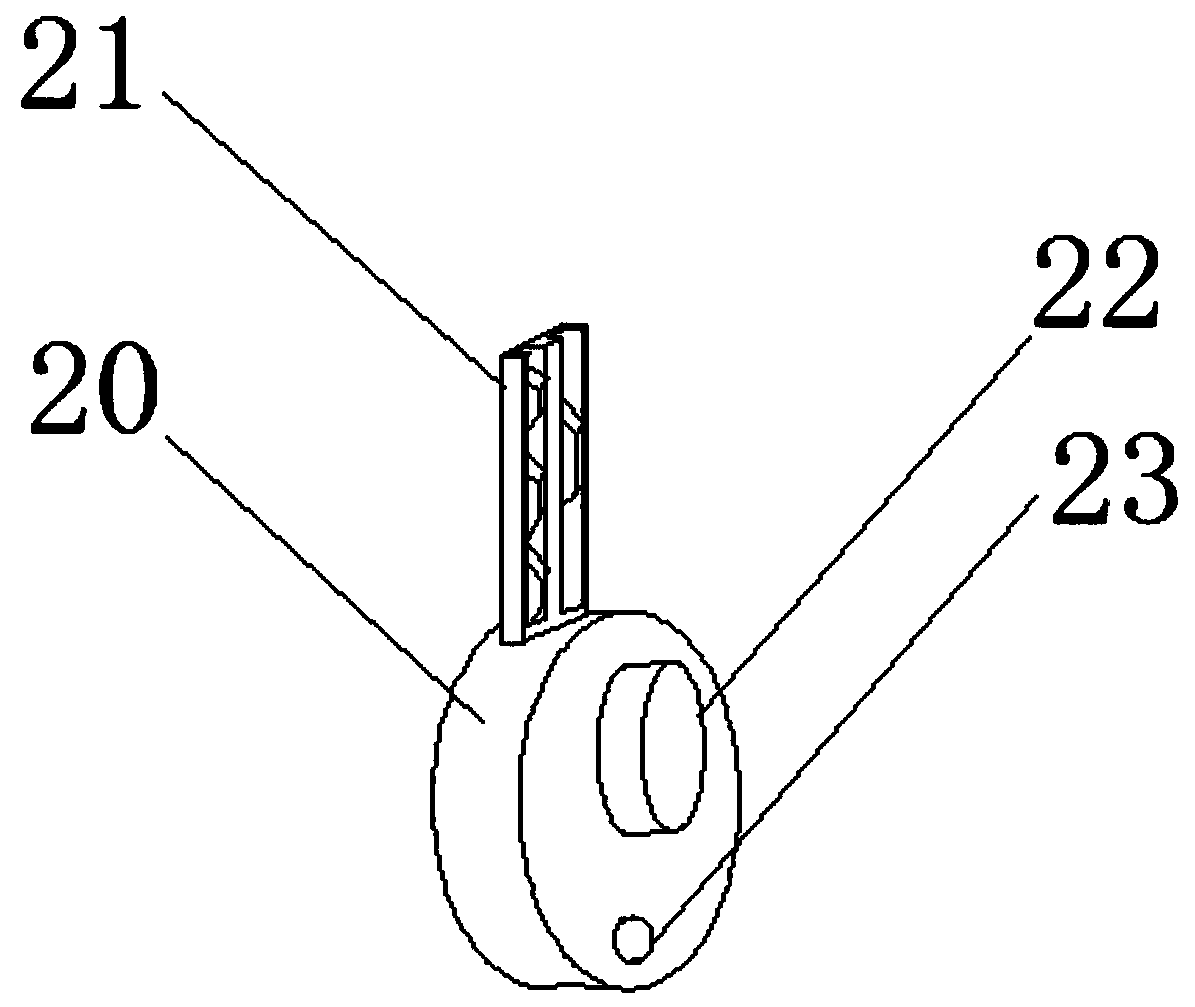
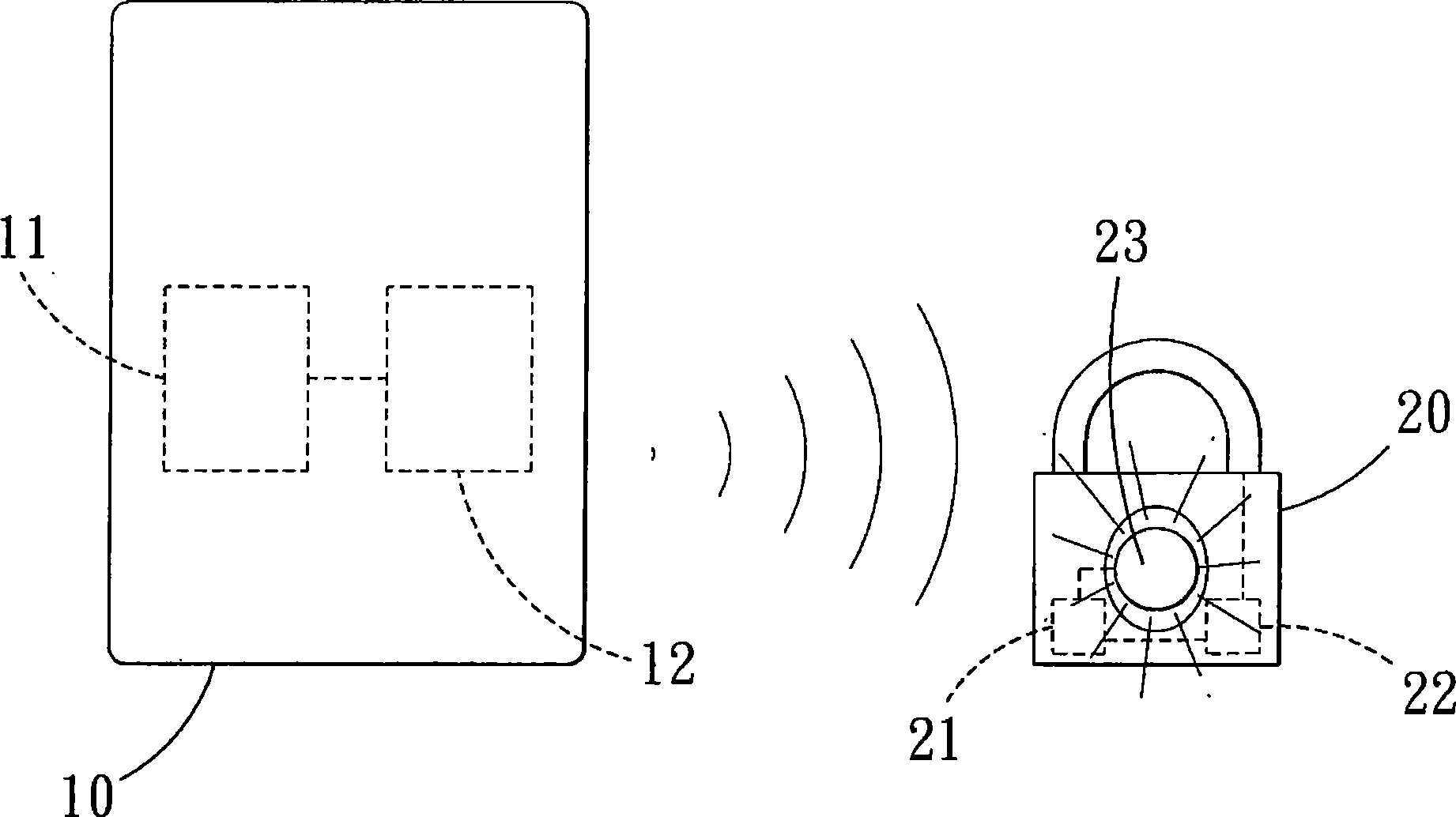
Method and system for illegal invasion identification base on wireless network signal CO complexity
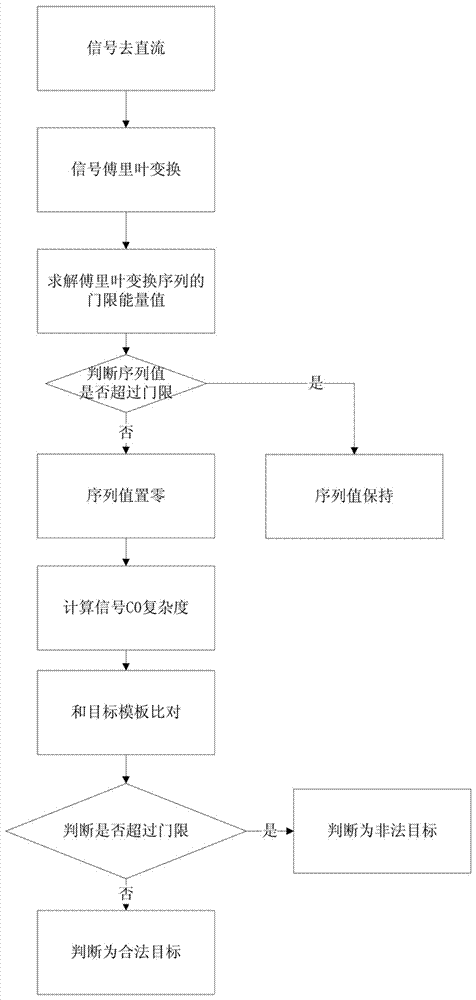
InactiveCN107105431ATo achieve the purpose of safetyImprove discrimination accuracySecurity arrangementNear neighborDigital watermarking
The present invention discloses a method for illegal invasion identification base on wireless network signal CO complexity, and relates to the information safety protection field. The method comprises the following steps: firstly, performing signal direct current subtracting processing of an original wireless network signal sequence, obtaining a direct current subtracting signal sequence, performing signal Fourier transform processing, and obtaining a Fourier transform sequence; secondary, according to a threshold energy value, performing sequence reconstruction of the Fourier transform sequence, and solving the estimation value of the CO complexity; and finally, employing a nearest neighbor method to perform identification of the illegal invasion. Besides, the present invention further discloses a system for illegal invasion identification base on the wireless network signal CO complexity. The method and system for illegal invasion identification base on the wireless network signal CO complexity do not depend on traditional wireless network safety protection means such as passwords, MAC address verification, digital watermarking and the like to thoroughly solve the safety threats such as password leakage, MAC address falsification or digital watermarking and the like; and moreover, the calculation efficiency is high, and processing delay is little.
Owner:NAT UNIV OF DEFENSE TECH
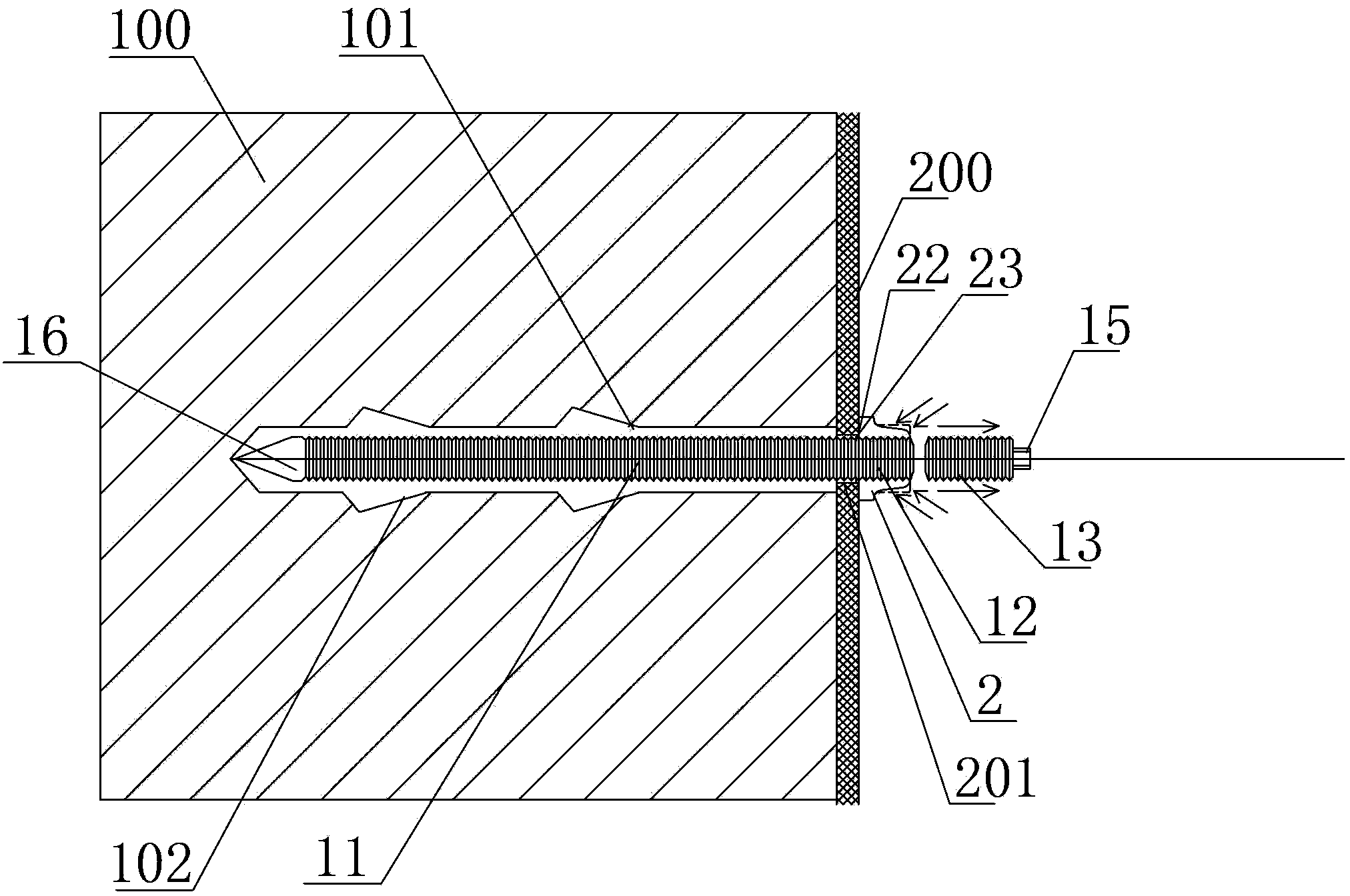
Chemical anchor bolt, connecting structure for fixing building attachment by using chemical anchor bolt and mounting method
InactiveCN103437467AEliminate uncertaintyImprove fastening strengthWallsBuilding material handlingInterference fitUltimate tensile strength
The invention provides a chemical anchor bolt, a connecting structure for fixing a building attachment by using the chemical anchor bolt and a mounting method. A metal anchor rod of the chemical anchor bolt is provided with an anti-loosening anchor section and a fastening sleeve, wherein the fastening sleeve tightly presses a connected part under the action of a tool, and an inner hole is shrunk to tightly wrap the anti-loosening anchor section and simultaneously form a concavo-convex inner hole surface matched with anti-loosening stripes on the surface of the anti-loosening anchor section to form weldless permanent connection; a convex ring or a bump is arranged at the front end of the fastening sleeve, and is squeezed into a gap between the hole wall of a hole, through which the metal anchor rod penetrates, of the building attachment and the metal anchor rod to form squeezing or interference fit. The chemical anchor bolt can be used for realizing permanent firm connection without welding, loosening is avoided, the fastening strength is greatly strengthened, all uncertain factors influencing chemical gum are eliminated, the aim of safety is actually fulfilled, and the mounting labor and the mounting cost can be reduced; a fireproof and heat-resistant solution to the chemical anchor bolt is also disclosed, so that the chemical anchor bolt is applied to various fire zones.
Owner:斯泰科技(杭州)有限公司 +2
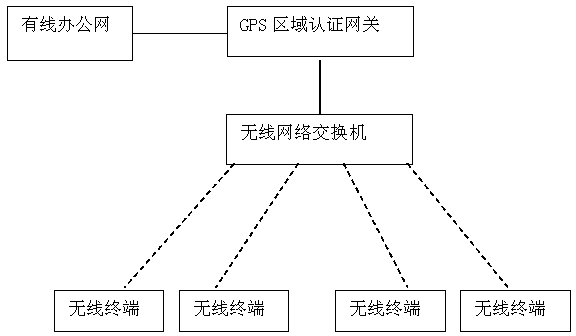
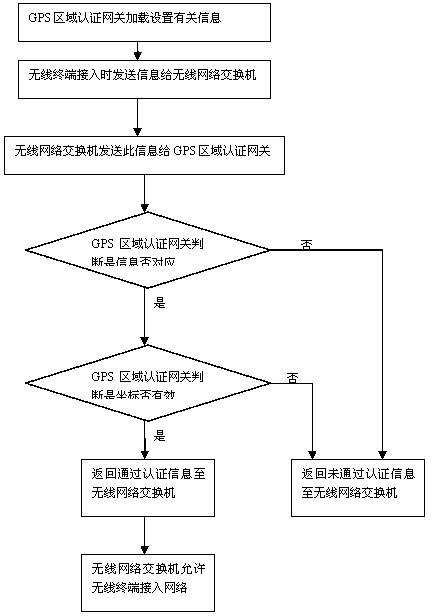
Electric power special wireless network system based on area authentication, and wireless transmission method
InactiveCN103686728AInternet preventionTo achieve the purpose of safetySecurity arrangementHigh level techniquesWireless transmissionNetwork connection
The invention discloses an electric power special wireless network system based on area authentication. The system comprises a GPS area authentication gateway, a wireless network switch and wireless terminals. The wireless network switch is connected with the GPS area authentication gateway in a wired way. The GPS area authentication gateway is connected with a wired office network in the wired way. The wireless network switch is connected with at least one wireless terminal in a wireless way. Each wireless terminal is internally provided with a GPS satellite positioning module. With a wireless transmission method, authentication of the GPS area authentication gateway is required when the wireless terminals are connected with the wireless network switch in the wireless way, the wireless terminals are permitted to be connected with the network within the range and personnel outside the area is prevented from being connected with the network so that an objective of security is achieved, convenient network connection is realized and thus production and working efficiency on electric power aspects are greatly enhanced.
Owner:STATE GRID CORP OF CHINA +3
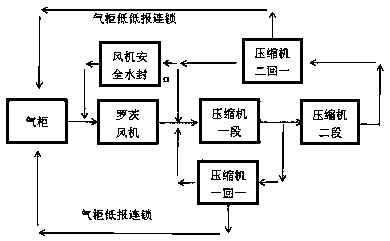
Nitrogen-hydrogen compressor self-adjusting system based on safety and working method thereof
ActiveCN110905783AOptimizing the Shortcut Adjustment ProcessRealize unattendedPump controlPump installationsControl systemGas compressor
The invention discloses a nitrogen-hydrogen compressor self-adjusting system based on safety and a working method thereof. The system comprises a gas holder, a Roots blower and a nitrogen-hydrogen compressor. A first-return first-near path and a second-return first-near path of the nitrogen-hydrogen compressor are in a self-adjusting state, and a first-return first-self-adjusting near path and a second-return first-self-adjusting near path are interlocked with a height of the gas holder. An inlet pipeline and an outlet pipeline of the Roots blower are connected with blower safety water seal. The height of the gas holder is interlocked with the one-return one-near path and the two-return one-near path of the nitrogen-hydrogen compressor according to low alarm and very low alarm. A DCS control system is arranged in the nitrogen-hydrogen compressor, and a gas holder height detector is arranged in the DCS control system to detect the height of the gas holder. In the invention, the near path of the gas compressor is reconstructed, and the safe water seal of the Roots blower is combined for use so that a possibility of ultralow pressure and negative pressure pumping of a gas-making gas holder is avoided, safety of a production process is improved, and a purpose of intrinsic safety is achieved.
Owner:JINYIMENG GRP CO LTD
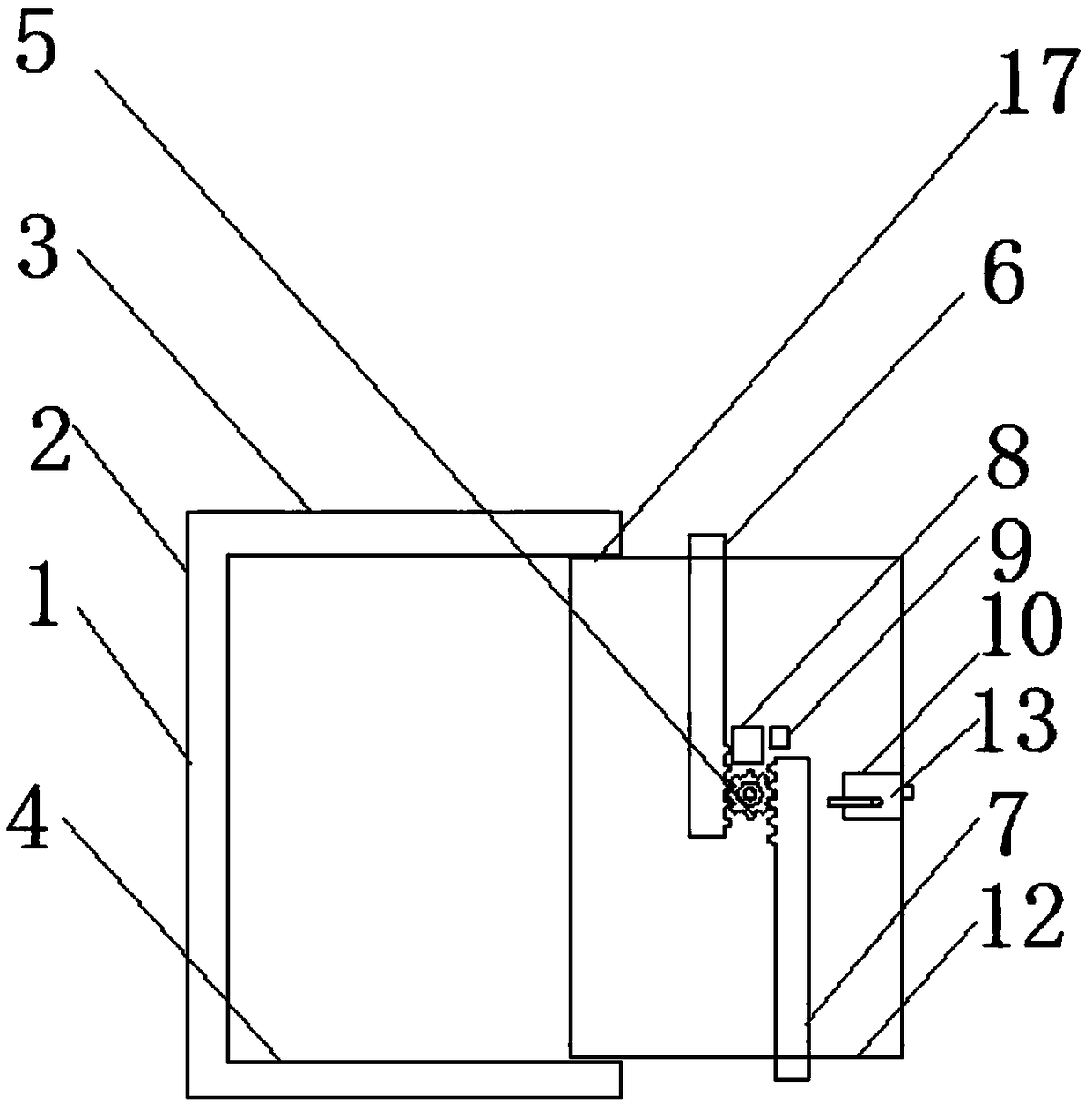
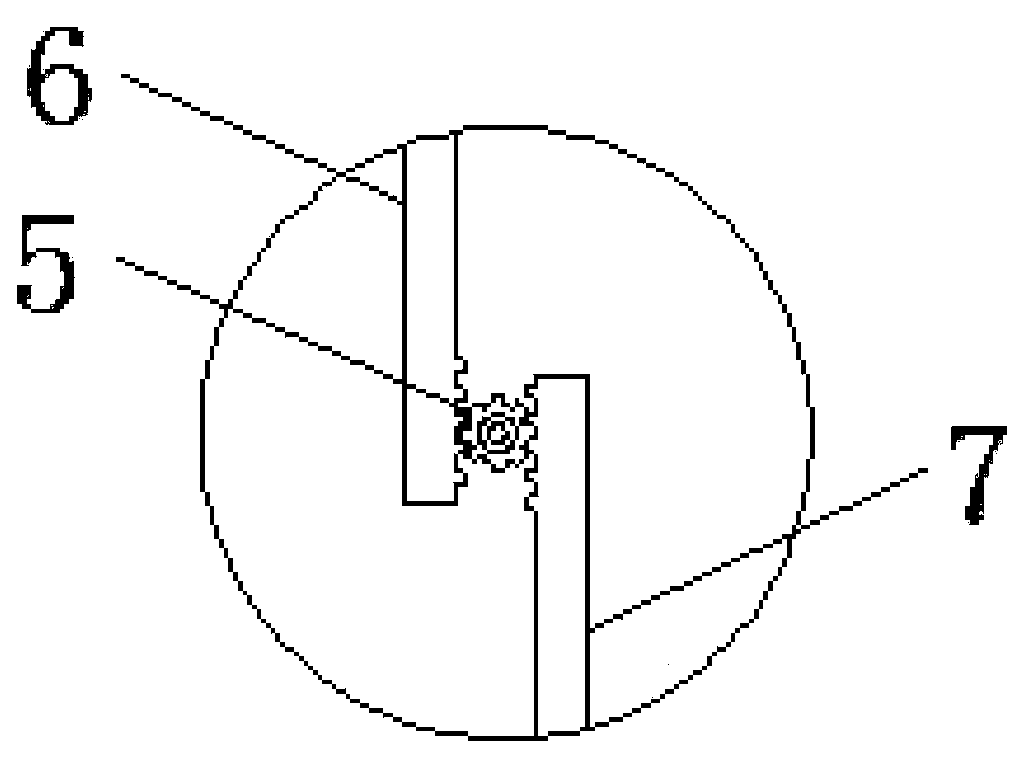
Intelligent chip remote control safeguard door lock
The invention discloses an intelligent chip remote control safeguard door lock which comprises a door frame body and a key. The door frame body is composed of a vertical frame, a top frame and a bottom frame, a door shaft is fixedly connected between the top frame and the bottom frame, and the door shaft is movably connected with a door plate body. A work transmission gear is mounted on the door plate body, two safety locks are mounted in the door plate body, and a chip is mounted on the door plate body. A button is arranged on the surface of the key, and a light-emitting diode is arranged inthe key. According to the intelligent chip remote control safeguard door lock, a special infrared emitting structure on the key and the chip on the door plate body are in communication connection, therefore, the two safety locks mounted in the door plate body are remotely controlled, the door is easily locked and unlocked, the structure is simple, the risk that the intelligent chip remote controlsafeguard door lock is likely to be damaged is avoided, and use is convenient and safe.
Owner:温州中邦知识产权有限公司
Powerless type electric lock piece and method for controlling same
InactiveCN101545337ASimple structureReduce power structure setupTransmission systemsElectric permutation locksEmbedded systemAuthentication
The invention discloses a powerless type electric lock piece which comprises at least one portable type equipment and a plurality of sets of electronic locks; each electronic lock is arranged on a plurality of files or archive cabinets; the electric lock is provided with different authentication codes inside; and a database is provided with authentication codes corresponding to the authentication codes of the electric lock. The invention also discloses a method for controlling the powerless type electric lock piece; the portable type equipment obtains the corresponding authentication code from the database to the electric lock on each archive cabinet or file cabinet for the contact or non-contact with the electric lock; the power supply is provided for the electric lock; the portable type equipment transmits the authentication code stored inside the portable type equipment to the electric lock; if the authentication code of the portable type equipment is tallied with the authentication code of the electric lock, the electric lock is started; therefore, the electric lock is kept in a state without electrical energy in normal times and can reduce the meaningless consumption of the electrical energy; and when the electric lock is arranged on a cabinet body, a complex wire pulling or fixing structure is not needed so as to reduce the cost of the overall setting and improve the efficiency of safeguarding and controlling articles in the cabinet.
Owner:林岱右
Safe pet leash
ActiveCN104026039BSlow down the retraction speedAvoid cutsTaming and training devicesPull forceEngineering
The invention discloses a safety pet leash comprising a housing with a handle, a reel disposed inside the housing, and a leash rope wound on the reel. The housing is provided with a rope outgoing hole admits outgoing of the leash rope. The side of the reel is connected with a moving lock tooth through a tension spring; the moving lock tooth comprises a hinging end and a fastening end; the hinging end is rotatably connected to the side of the reel through a hinge pin; the fastening end is radially abutted to a protruding rib formed on the reel, under the tension action of the tension spring; the housing is provided with a fastening rib matching with the moving lock tooth. When the reel rotates fast, the moving lock tooth rotates around the hinge pin under the centrifugal action of the moving lock tooth; accordingly, the fastening end radially moves out and fastens to the fastening rib. The safety pet leash has the advantages that a pet running away fast can be held back, and accidents are avoided; when the pet moves suddenly in response to external disturbances, the safety pet leash can actively brake to ensure safety of the pet and people.
Owner:SUZHOU PETMATE IND & TRADE
Stopping machine special for low-temperature tanker loading and unloading arm
The invention relates to a stopping machine special for a low-temperature tanker loading and unloading arm. The stopping machine comprises a main plate and an auxiliary plate which are connected with each other in a plane-stacking manner. A cavity capable of containing a flange is formed between a middle protrusion of the auxiliary plate and the main plate, a U-shaped notch allowing the low-temperature tanker loading and unloading arm to enter and to be placed is formed on the auxiliary plate, and the stopping machine further comprises a first flange limiting bolt. The stopping machine is mounted on a tanker loading platform or other utensils provided with loading and unloading arms; after loading and unloading is completed and when the loading and unloading arm is contained, the loading and unloading arm is rotated and the flange at an opening of the loading and unloading arm is pushed or inserted into a space between the main plate and the auxiliary plate, the flange limiting bolt is overturned to fall into an opening bolt groove of the flange, and a butterfly-shaped nut on the flange limiting bolt is screwed to form pressure limiting. A flaring is arranged at an opening of the U-shaped notch on the auxiliary plate, so that the auxiliary plate has a guiding function, and convenience is brought to pushing-into or inserting-into of the loading and unloading arm. In addition, a sealing pad is arranged on the main plate, so that sealing can be quickly realized when the loading and unloading arm stops in place.
Owner:贺耿
A kind of control method of blast type burner
ActiveCN103900103BImprove securityEffectively clean up residueCombustion regulationStopped workElectricity
The invention relates to a blowing-type burner control method which comprises the following steps that an electric controller receives an ignition instruction and conducts slash fire detection, overheat detection and draught fan rotating speed detection sequentially; the electric controller controls an air blower to blow and sweep a combustion box at the rotating speed a; the electric controller controls the rotating speed of the air blower to be a set ignition rotating speed b, an igniter is started, a power shut-off valve on a gas proportion valve assembly is controlled to be opened, and an electric adjustment opening in the gas proportion valve assembly is opened to an ignition opening degree according to a set ignition current; after the successful ignition, the electric controller synchronously controls the opening degree of the electric adjustment opening and the rotating speed of the air blower according to the burning power input by a manipulator; when the electric controller receives a stop work instruction from the manipulator, the gas proportion valve assembly is closed and the air blower continues to run for set period of time. Compared with the prior art, the blowing-type burner control method has the advantages of being high in heat exchange efficiency, high in safety and the like.
Owner:SHANGHAI HESEN ELECTRO MACHINERY
Motorcycle shell production device
InactiveCN106984481AScientific and reasonable structureEasy to useEdge grinding machinesLiquid surface applicatorsImpellerDrive wheel
The invention discloses a motorcycle casing production device, comprising a casing, a controller, a power unit and a working main body. A working indicator light is installed on the upper right of the casing, a base is installed under the casing, and the casing is installed. There is a material outlet on one side, a data processor is installed inside the casing at the upper left, an information collector is installed at the lower end of the data processor, a controller is installed at the lower left of the information collector, and the lower right end of the controller is installed A PLC electronic control unit is installed, the controller is connected with the power unit through the PLC electronic control unit, a clip frame is installed at the lower end of the power device, a conveying crawler is installed under the clip frame, and a conveying crawler is installed above the conveying crawler. A driving wheel, one end of the driving wheel is installed with a working body, and the working body includes a driven wheel, a driving wheel and an edging working wheel. The present invention has the technology of Internet of Things, can control in real time, can achieve the purpose of rapid production to a large extent, and can operate in an integrated manner.
Owner:JIANGSU HENGAI MEDICAL EQUIP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com