Logic binding method for preventing PC (personal computer)hard disk information from theft
A hard disk and logic technology, applied in the field of computer information security protection, can solve the problems of no protection and can not prevent the computer hard disk from reproducing the information in it, and achieve the effect of preventing the leakage of hard disk information and eliminating information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0019] A logical binding method for anti-theft of PC hard disk information, which uses software to logically bind the hard disk of the computer to the computer where it is located, so that the hard disk is in one-to-one correspondence with the computer where it is located, and the hard disk does not work in an uncorresponding computer environment.
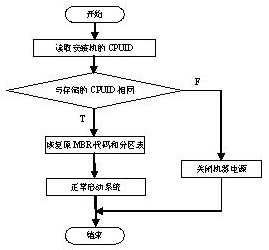
[0020] The software includes a CPUID judging program, which is composed of a binding module, a storage module, a reading module and a judging module. The binding module binds the hard disk with the CPUID, stores the binding information of the hard disk and the CPUID in the storage module, rewrites the MBR code of the hard disk, and the function of the rewritten MBR code is to judge the CPUID and restore the original MBR code and partition table , the original MBR code and partition table are stored in the empty backup sector of the hard disk. The flowchart of the MBR code is as follows figure 1 shown. After the computer is start...
Embodiment 2
[0022] A logical binding method for anti-theft of PC hard disk information, which uses software to logically bind the hard disk of the computer to the computer where it is located, so that the hard disk is in one-to-one correspondence with the computer where it is located, and the hard disk does not work in an uncorresponding computer environment.
[0023] The software includes a CPUID judging program, which is composed of a binding module, a storage module, a reading module and a judging module. The binding module binds the hard disk with the CPUID, stores the binding information of the hard disk and the CPUID in the storage module, rewrites the MBR code of the hard disk, and the function of the rewritten MBR code is to judge the CPUID and restore the original MBR code and partition table , the original MBR code and partition table are stored in the empty backup sector of the hard disk. The flowchart of the MBR code is as follows figure 1 shown. After the computer is start...
Embodiment 3
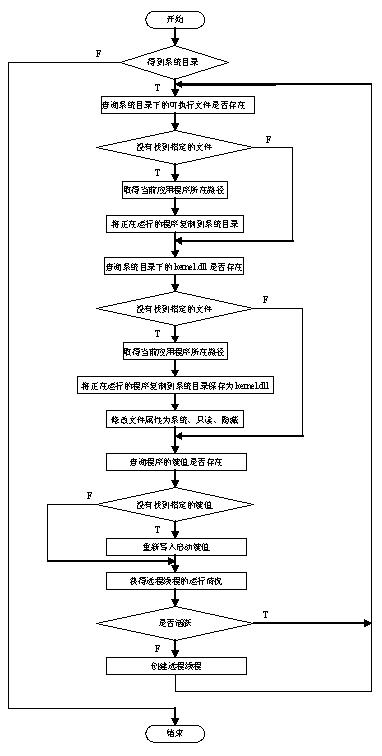
[0086] On the basis of embodiment 2, the hidden hard disk partition table program is added in the software, for preventing the hard disk from being read after being installed with the slave mode (slave machine responds to the master mode), rewrite the MBR (MasterBootRecode master boot sector code) code, and Destroy the partition table, and the original partition table is stored in the backup sector, which will be restored when used, and destroyed after use, ensuring that the hard disk will be visible and unreadable even if it is installed on other machines.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com