REST security system based on signature mechanism
A security system and mechanism technology, applied in the field of web security, can solve the problems of REST not having predefined security methods and being vulnerable to attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The method of the present invention is described in detail below with reference to the accompanying drawings.
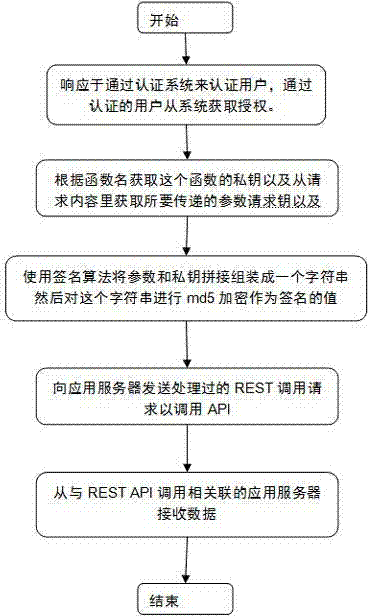
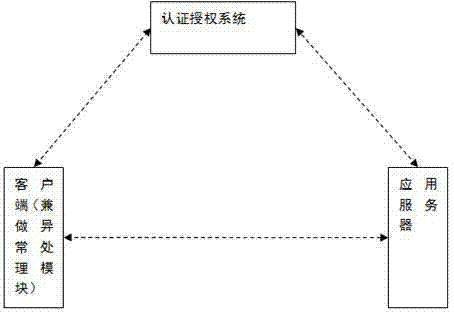
[0026] The first step: verification and authorization, the client application must obtain authorization from the authentication and authorization system before calling the REST API. From a technical point of view, obtaining authorization is to obtain a Session Key;
[0027] The second step: interface call, here we first define a signature algorithm:
[0028] S:{
[0029] Format the request parameters into "key=value" format, namely "k1=v1", "k2=v2", "k3=v3";
[0030] Arrange the above-formatted parameter key-value pairs in ascending order of the dictionary, and splice them together, that is, "k1=v1k2=v2k3=v3";
[0031] Append the private key of the API application at the end of the concatenated string;
[0032] The MD5 value of the above string is the value of the signature;
[0033]}
[0034] Then we use this algorithm to process the request to get the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com