Patents
Literature
202results about How to "Allow access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
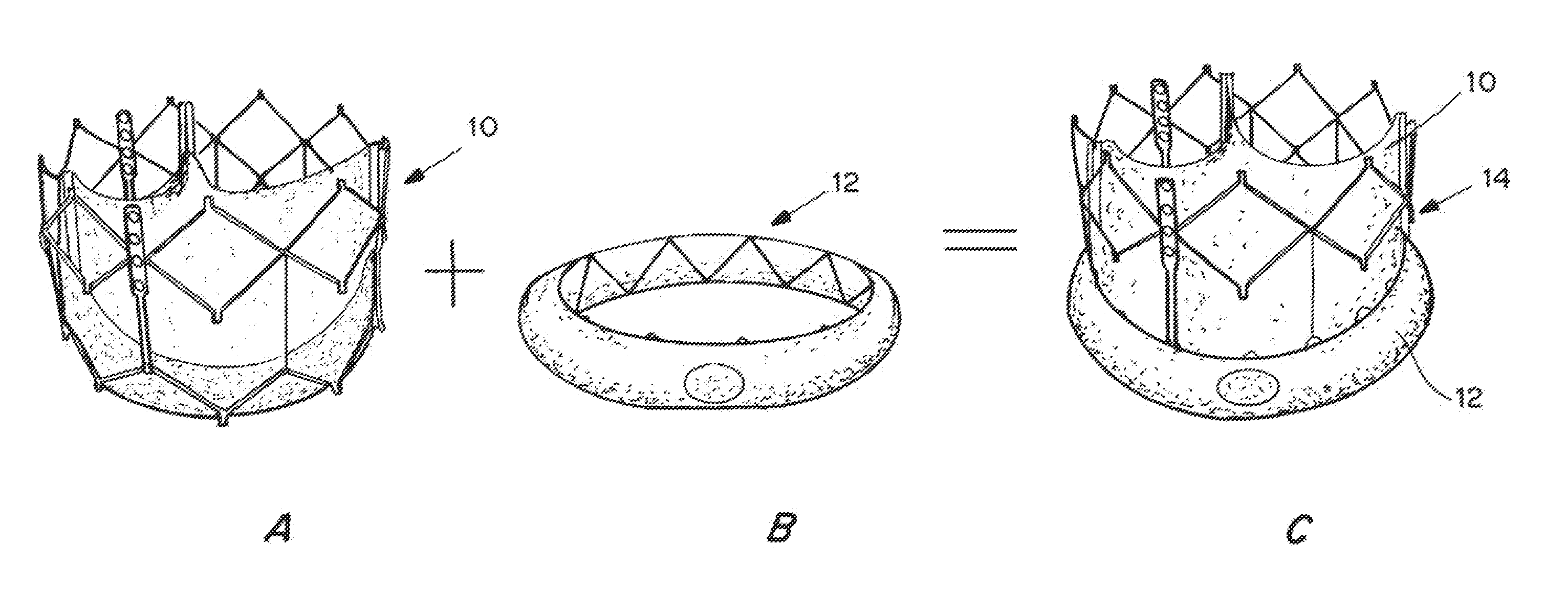
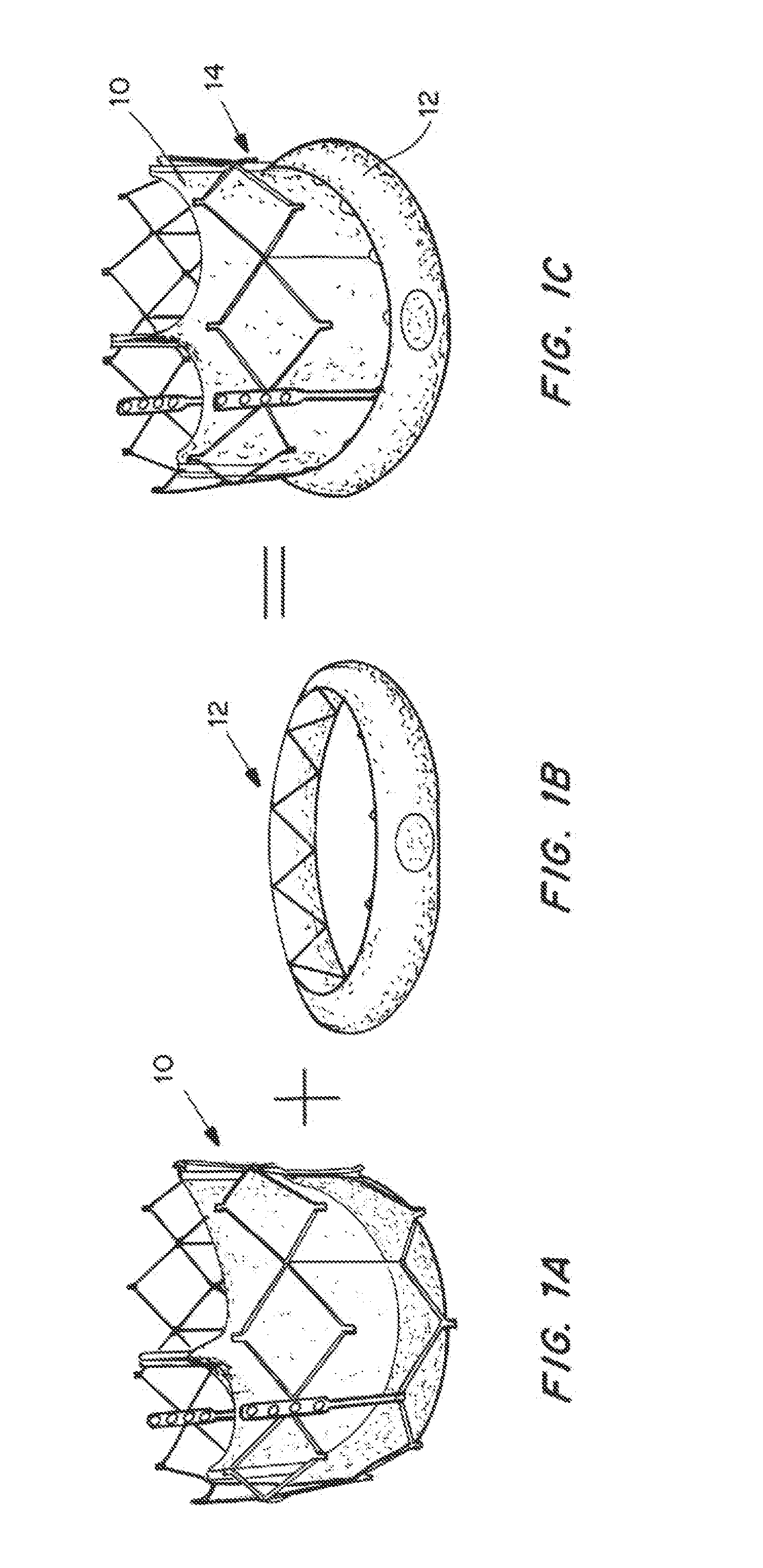
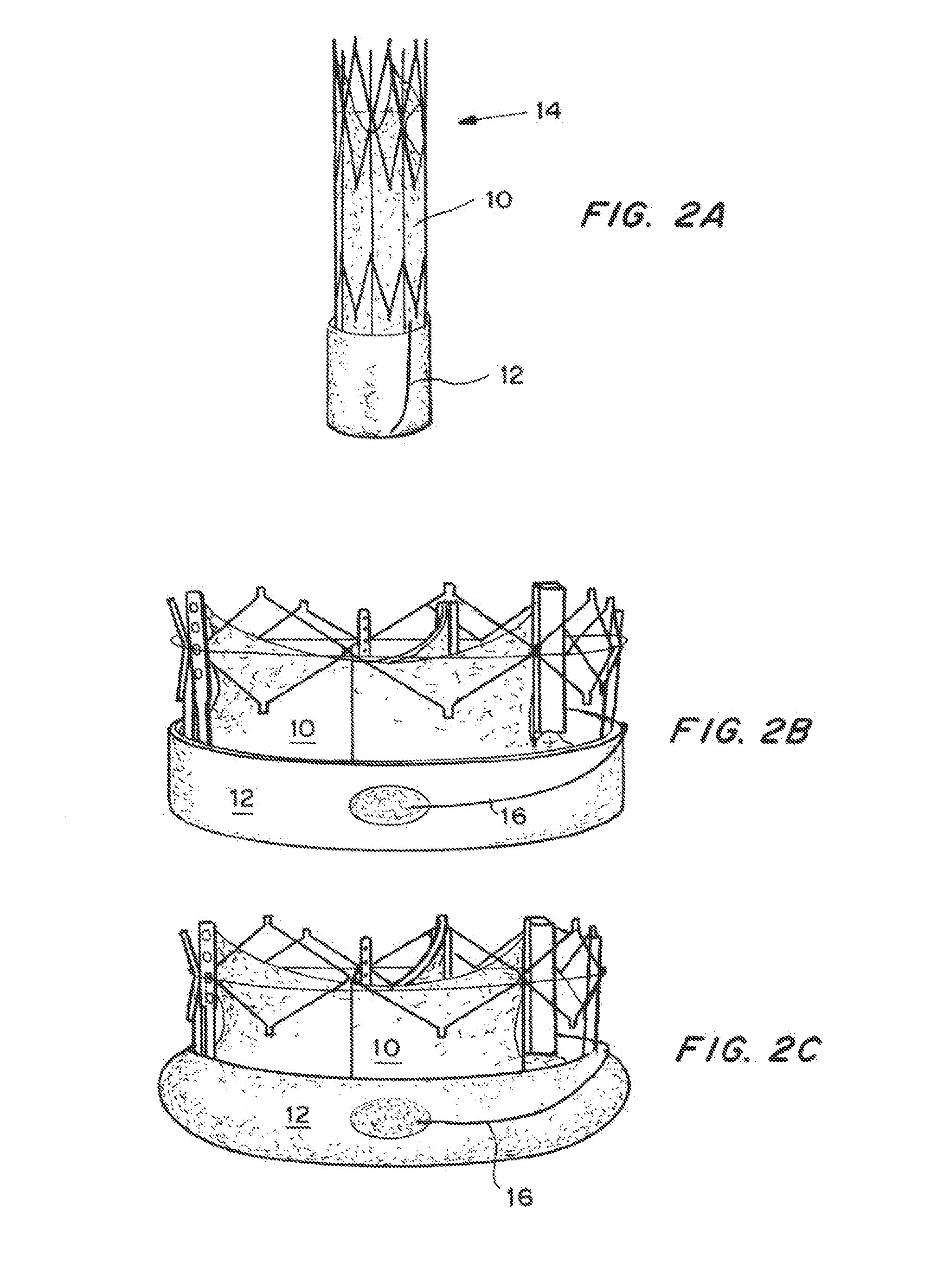
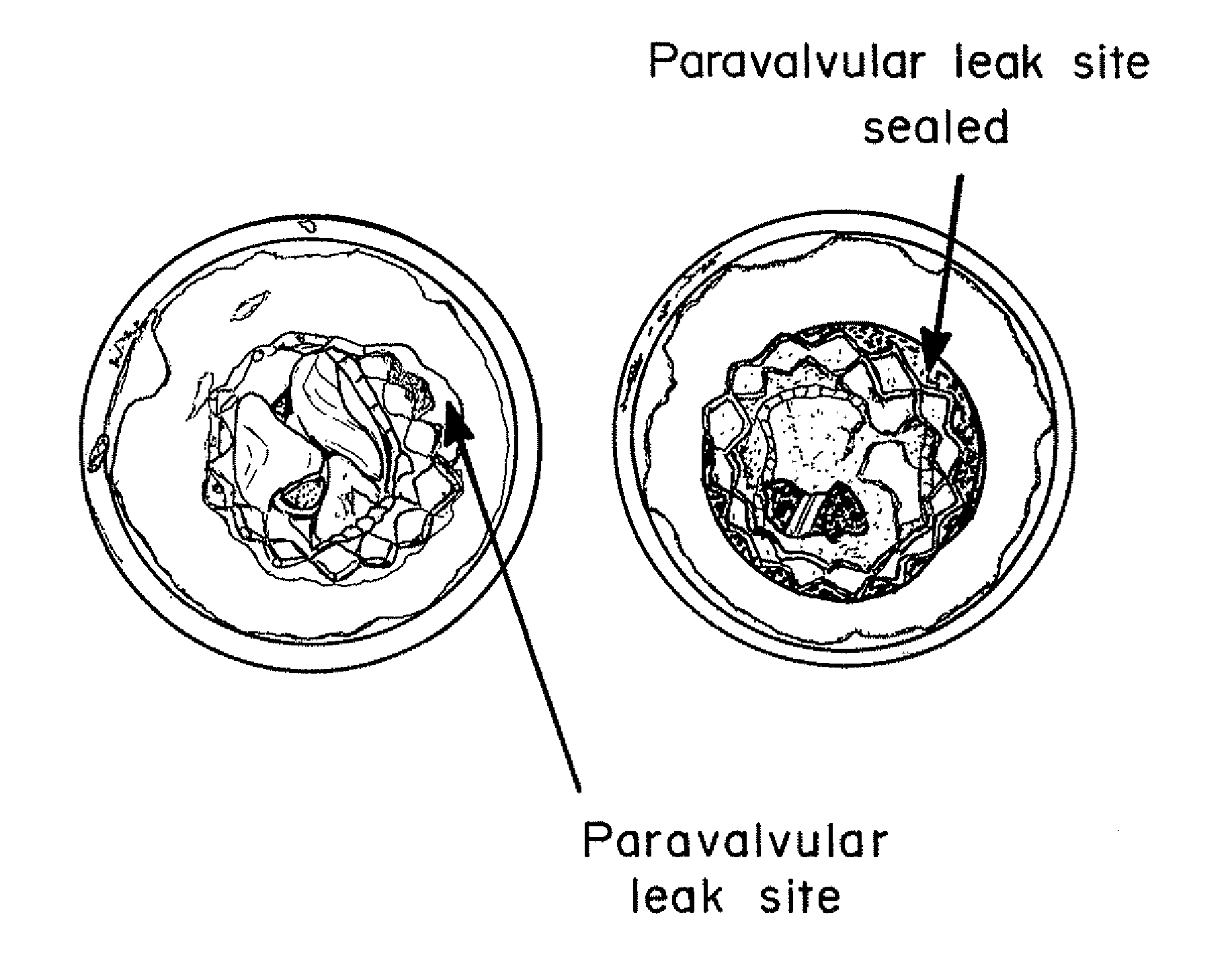
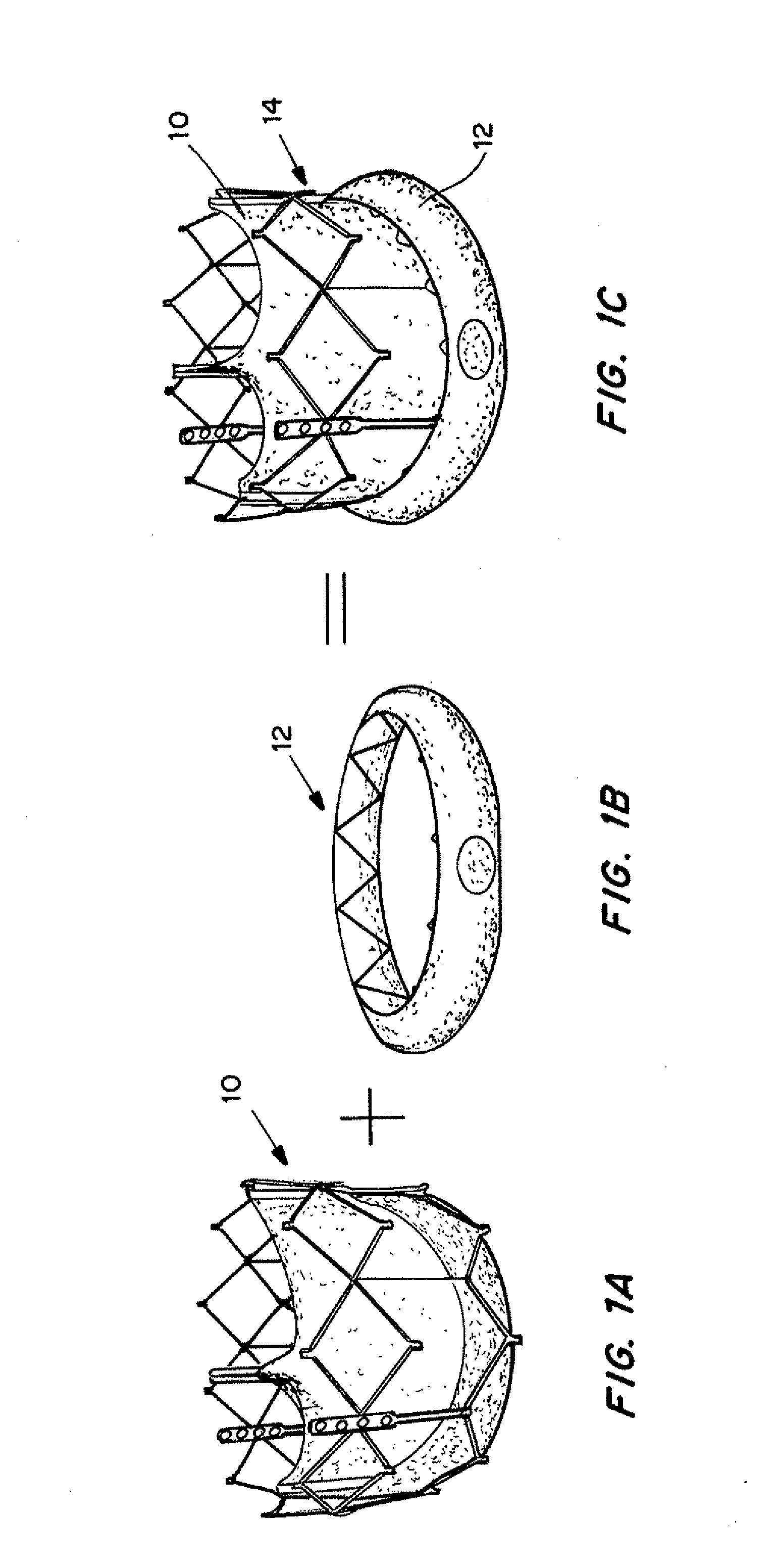
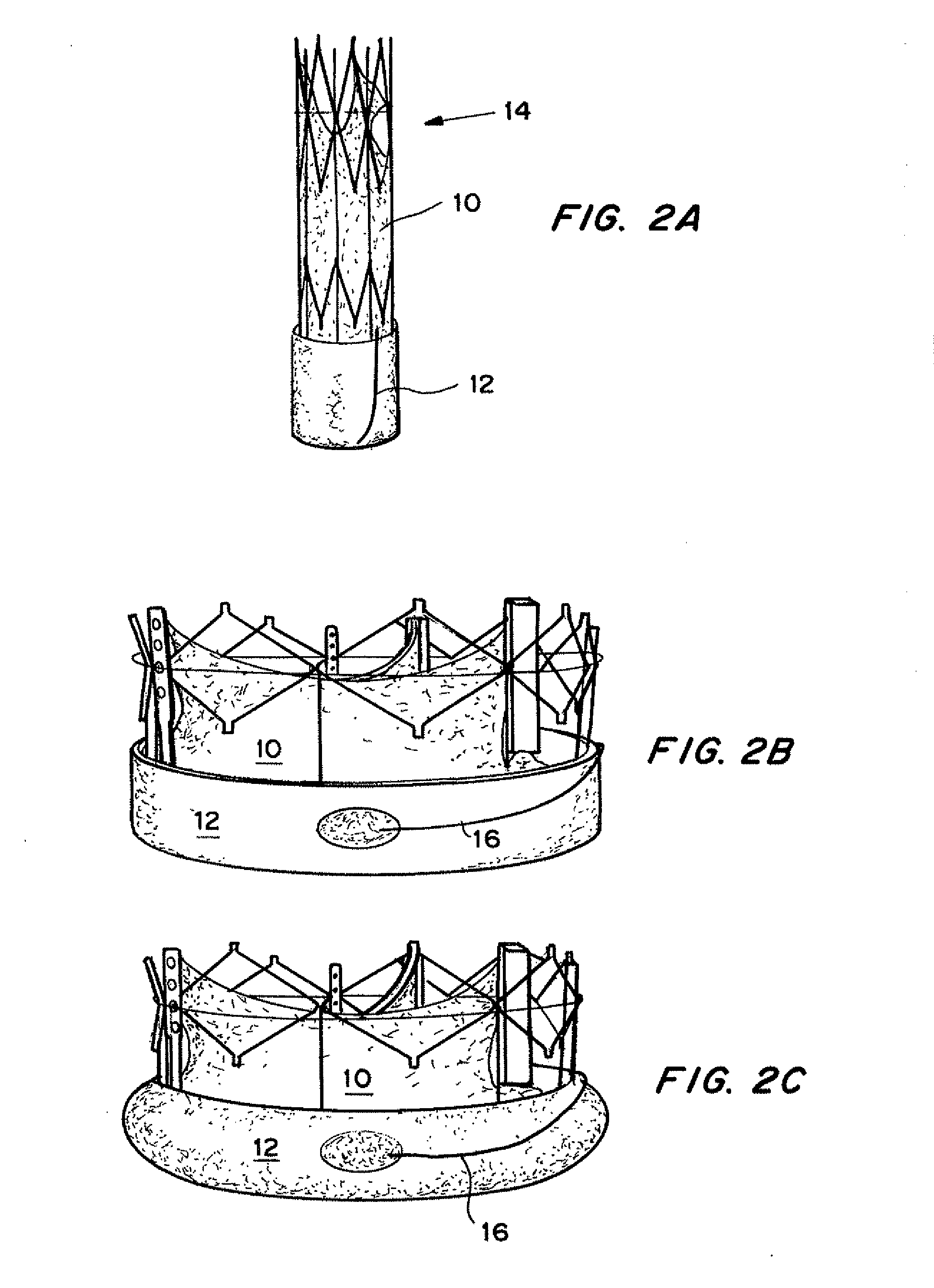
Means for Controlled Sealing of Endovascular Devices
InactiveUS20130331929A1Improve sealingEliminate prosthetic-annular incongruenceSurgical adhesivesHeart valvesProsthesisFunctional integrity
Expandable sealing means for endoluminal devices have been developed for controlled activation. The devices have the benefits of a low profile mechanism (for both self-expanding and balloon-expanding prostheses), contained, not open, release of the material, active conformation to the “leak sites” such that leakage areas are filled without disrupting the physical and functional integrity of the prosthesis, and on-demand, controlled activation, that may not be pressure activated.
Owner:ENDOLUMINAL SCI
Secure, vehicle mounted, surveillance system
InactiveUS6211907B1Allow accessRegistering/indicating working of vehiclesAnti-theft devicesTransceiverData file
A novel system for gathering, analyzing and storing information for the purpose of motor vehicle theft and vandalism investigations. An on board secure vehicle mounted surveillance system, that can monitor the vehicle for brief or extended periods of time that can operate whether the vehicle is on or off, having a video camera for generating video signals of an incident proximate the vehicle, having an audio device for monitoring events proximate the vehicle, motion sensor to activate the system and lights activated by the system to illuminate the area viewed by the camera. The video signals are digitized into a synchronized data file, carrying a unique vehicle identification and a time indicator with other input data occurring on or about the vehicle such as audio recordings and the like. The file is encrypted and stored on a large capacity, code accessible device or transmitted, via a transceiver, real time to authorities and / or an off vehicle storage site. Once written, the encrypted file cannot be altered or corrupted, decrypted without the encryption key, or accessed without the access authorization code. The stored data file can be down loaded to be used as evidence.
Owner:EVICAM INT
System and Method for Managing Data Across Multiple Environments
ActiveUS20080109448A1Allow accessSpecial data processing applicationsProgram managementData management
The present invention discloses a system and method for data management whereby a data management application manages data across a managed service environment, a mail server environment, and a client environment. The present invention allows a customer to optimize data management functions such as archiving, recovering, monitoring, authenticating, synchronizing, transferring, copying, stubbing, chunking, harvesting, and securing.
Owner:MESSAGEONE INC
Encryption apparatus and method for synchronizing multiple encryption keys with a data stream
ActiveUS7242772B1Minimized in sizeImprove distributionKey distribution for secure communicationSynchronising transmission/receiving encryption devicesMultiple encryptionComputer hardware
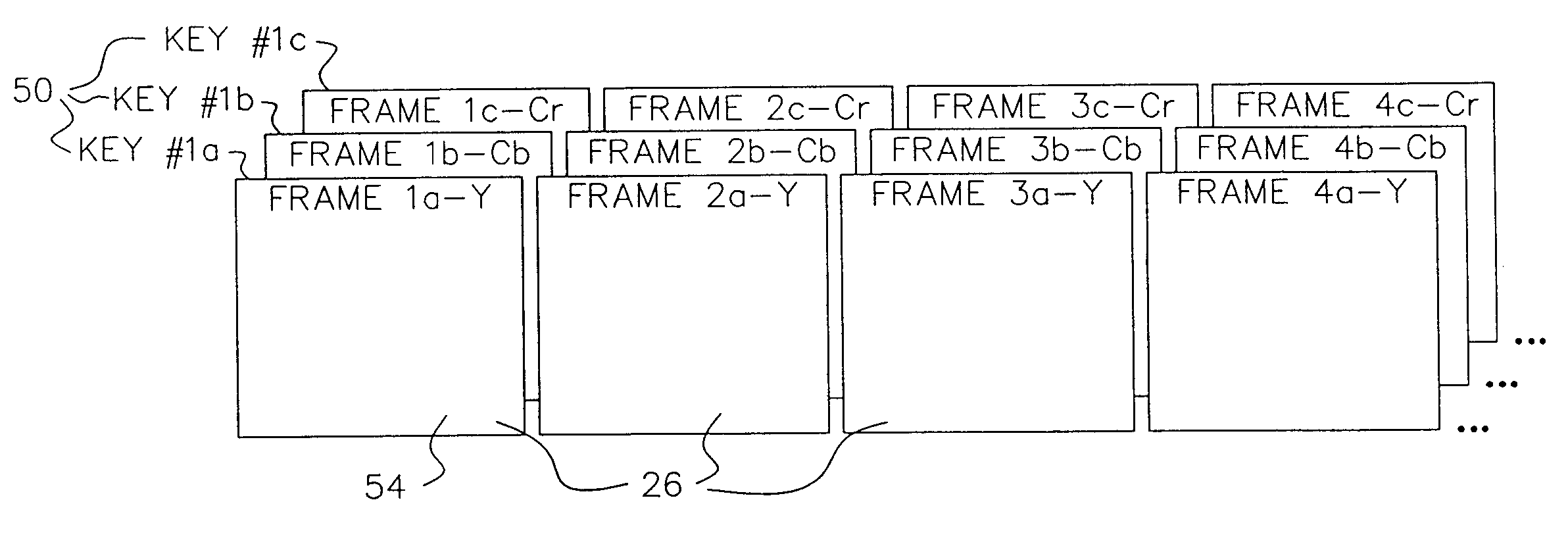
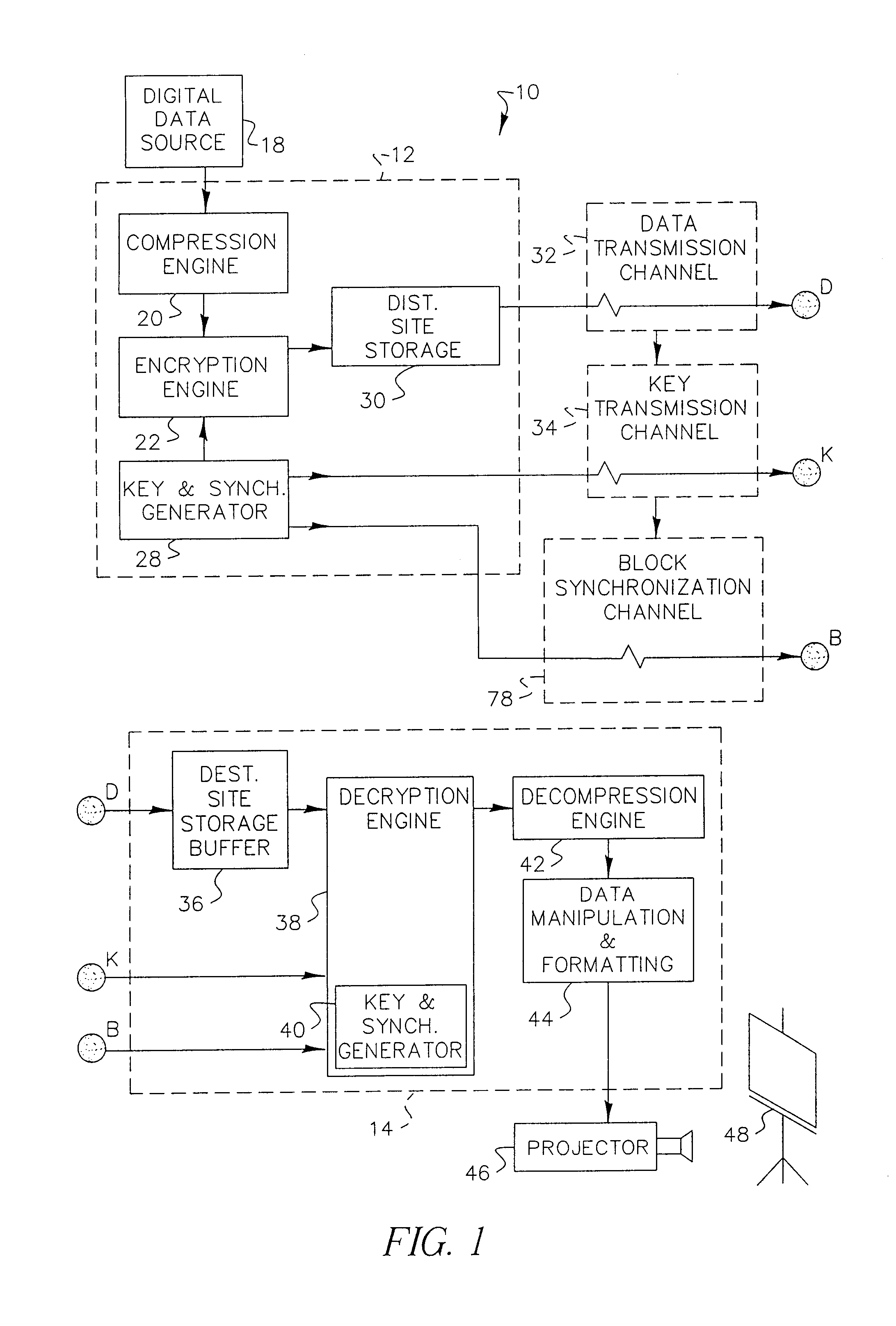
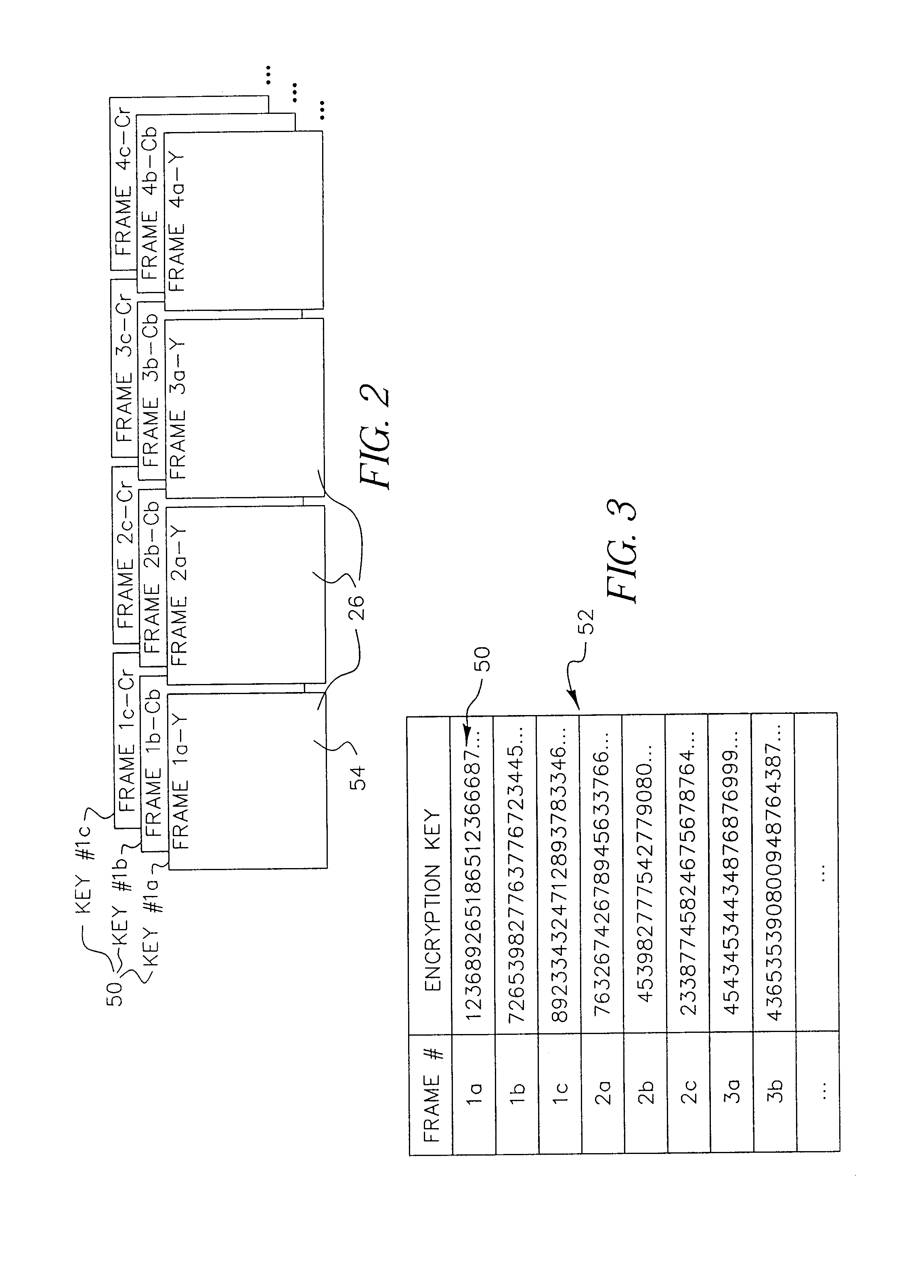
A data stream, such as a digital motion picture, is encrypted in units of one or more blocks, each block having an assigned encryption key. A plurality of encryption keys is assigned to the complete data stream, with a synchronization index provided to map each individual encryption key to its starting data block. Encryption keys and associated synchronization indices are provided separately from the data stream, using one or more additional data transfer mechanisms. An optional offset, randomly generated, allows variation in intervals between data blocks at which encryption by a specific encryption key can be performed.
Owner:MONUMENT PEAK VENTURES LLC
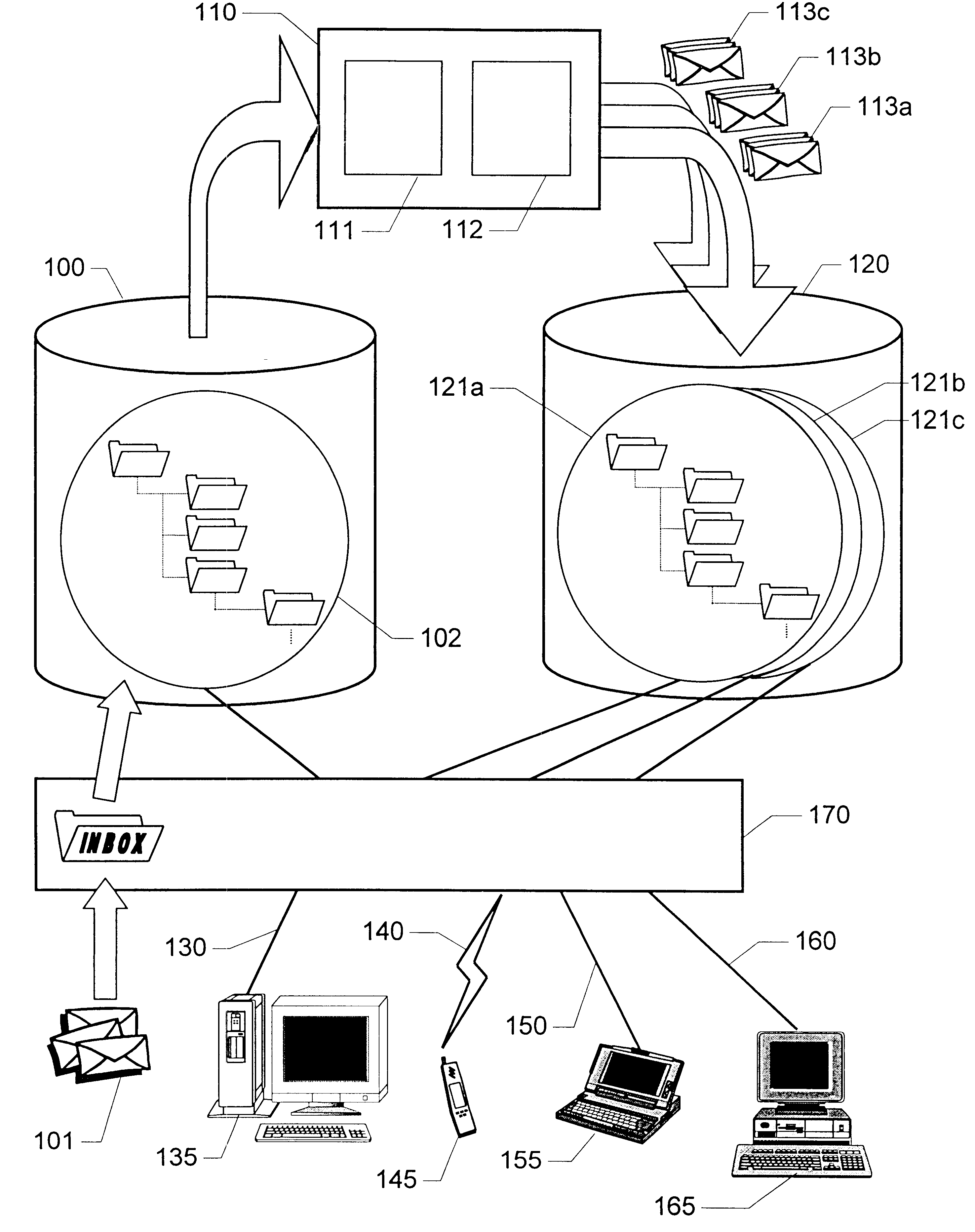
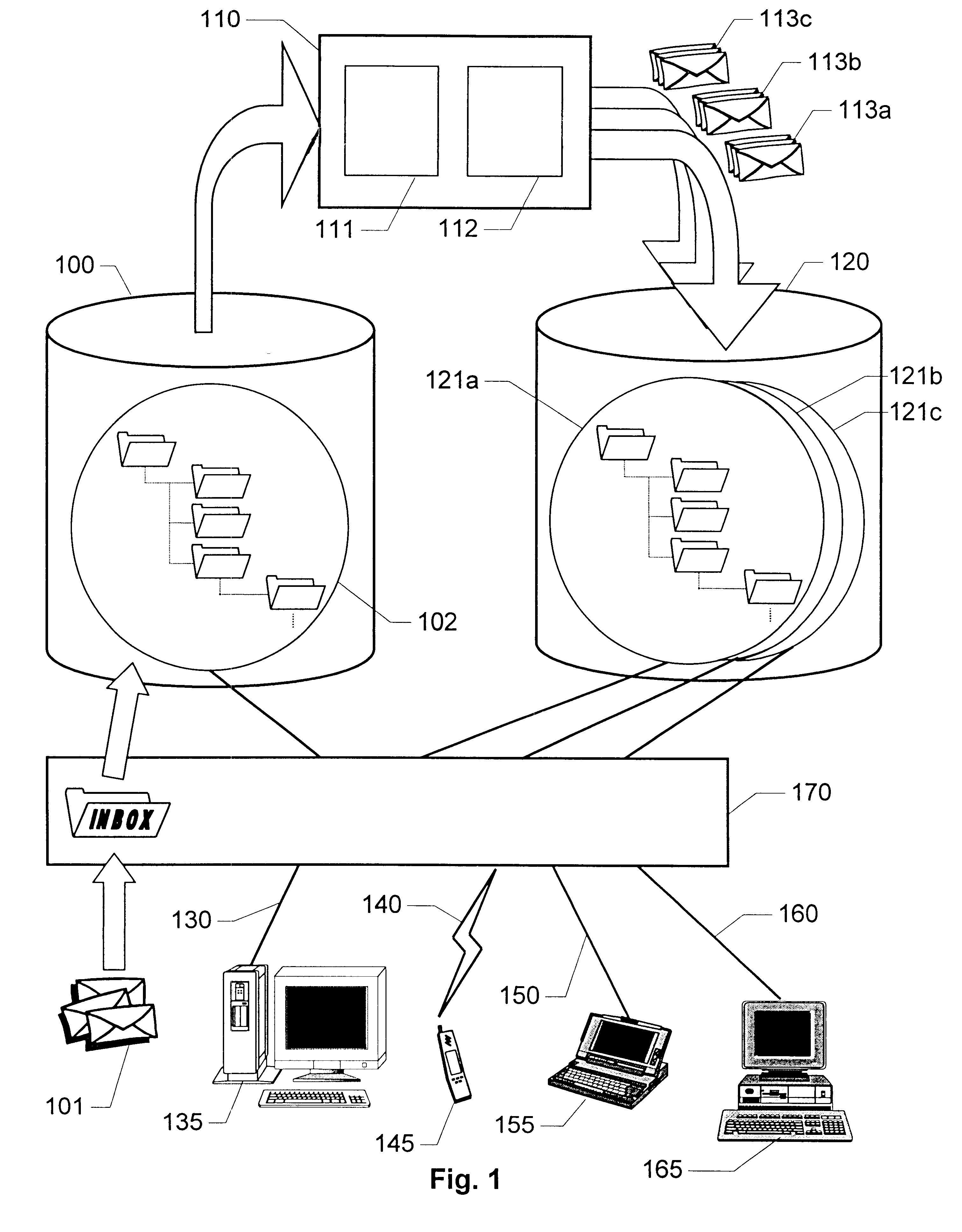
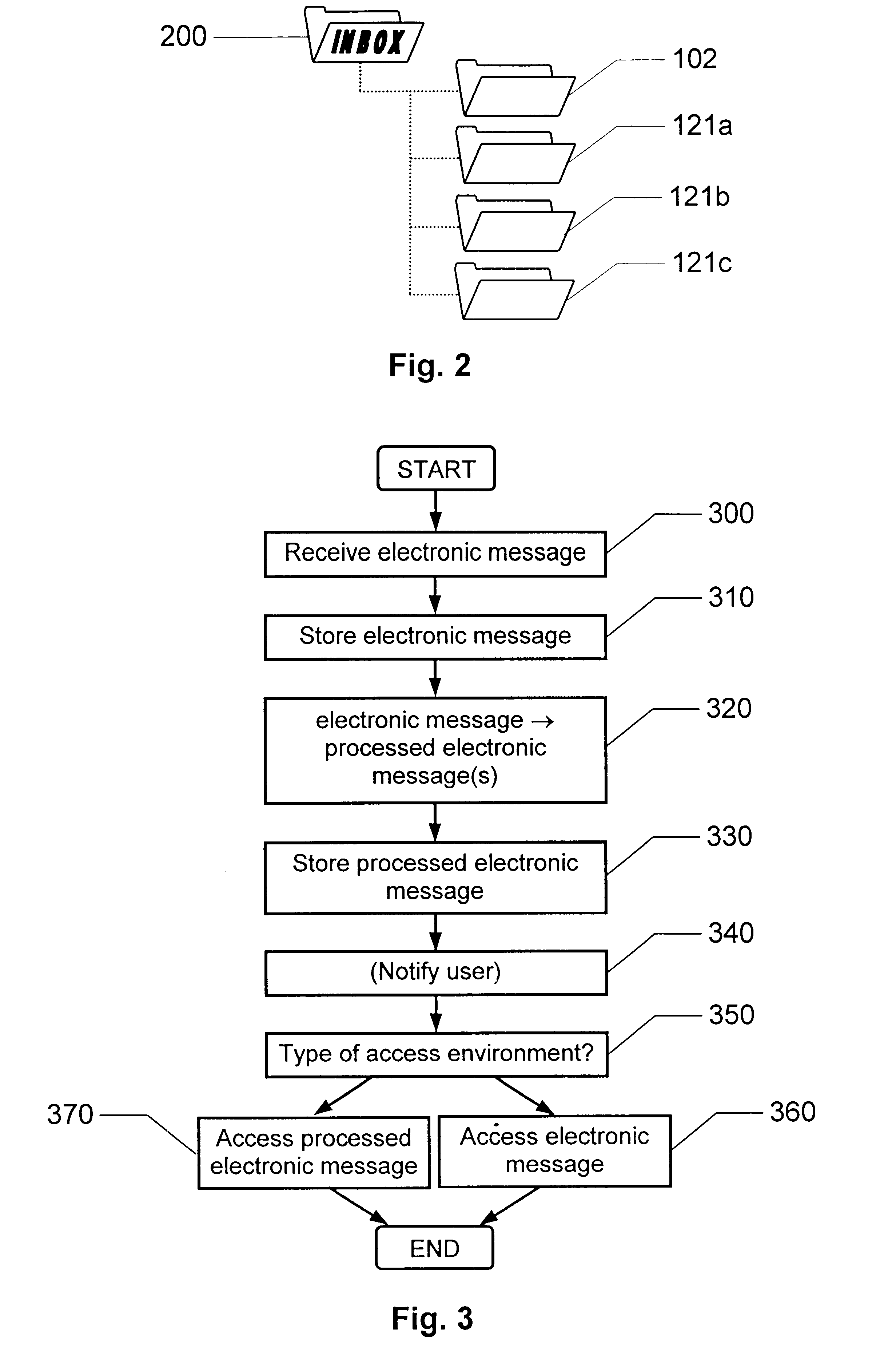
Method and apparatus for organizing and accessing electronic messages in a telecommunications system
InactiveUS6738800B1Reduce communicationImprove efficiencyMultiple digital computer combinationsData switching networksOriginal dataStructure of Management Information
The invention relates to the organization of electronic messages (101) coming in to a user who can access his / her messages via at least two different types of access environments (130-165). A first storage area (100) receives the electronic messages (101), which each has an original data format. The electronic messages (101) are then stored according to a first structure (102). An agent (110) processes the electronic messages (101) into at least one set of processed electronic messages (113a-113c) having data formats, which are at least as adapted to an alternative access environment as the data formats of the corresponding original electronic messages. The processed electronic messages (113a-113c) are then stored according to at least one second structure (121a-121c) that is a mapping of the first structure (102). The user may either access an original electronic message (101) in the first structure (102) or one of the processed electronic messages (113a-113c) in the at least one second structure (121a-121c). The choice of message version is based on the type of access environment (130-165) that the user currently has at his / her disposal.
Owner:IDTP HLDG
Means for controlled sealing of endovascular devices
InactiveUS20130190857A1Improve sealingEliminate prosthetic-annular incongruenceStentsHeart valvesProsthesisFunctional integrity
Expandable sealing means for endoluminal devices have been developed for controlled activation. The devices have the benefits of a low profile mechanism (for both self-expanding and balloon-expanding prostheses), contained, not open, release of the material, active conformation to the “leak sites” such that leakage areas are filled without disrupting the physical and functional integrity of the prosthesis, and on-demand, controlled activation, that may not be pressure activated.
Owner:ENDOLUMINAL SCI
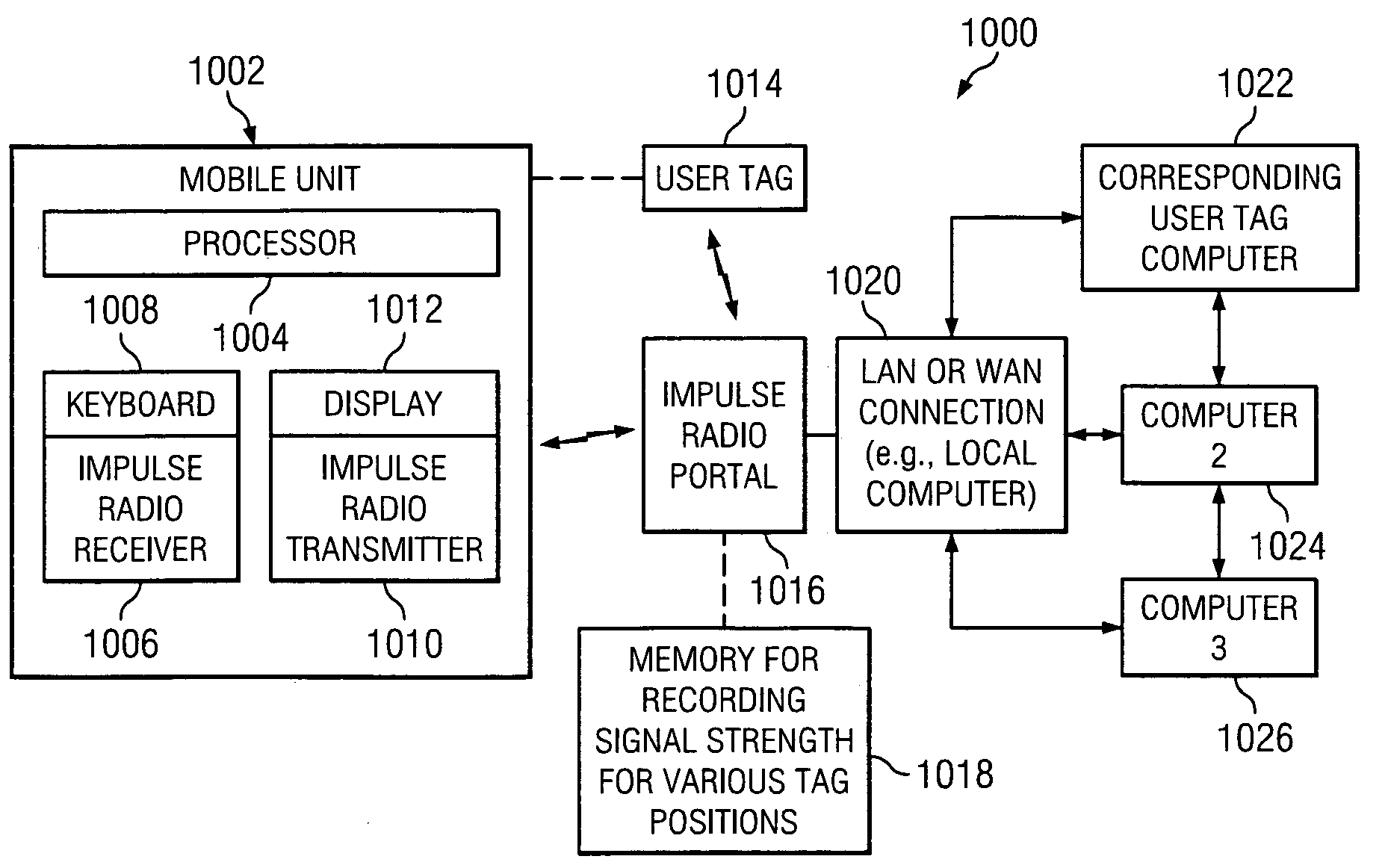
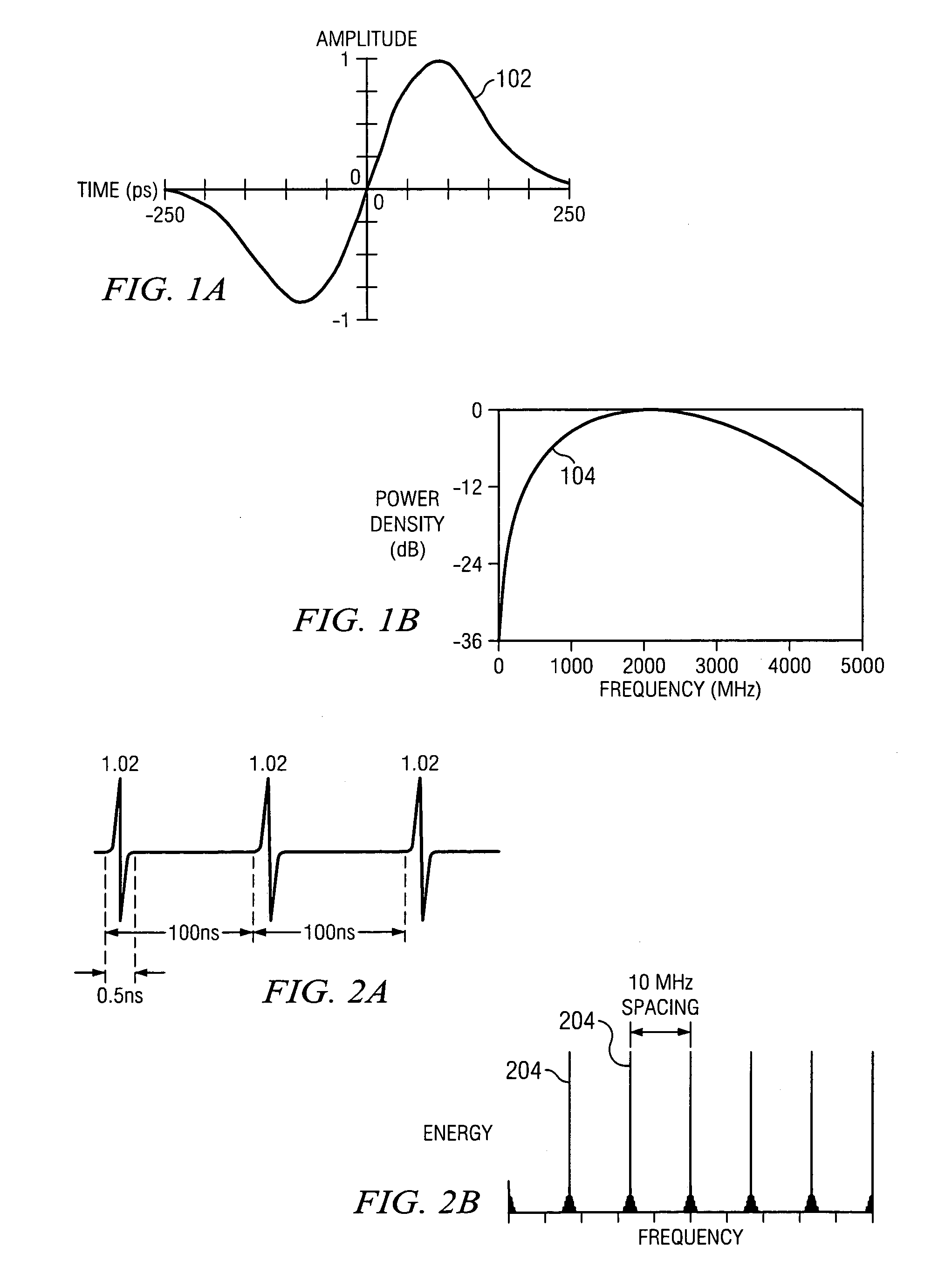
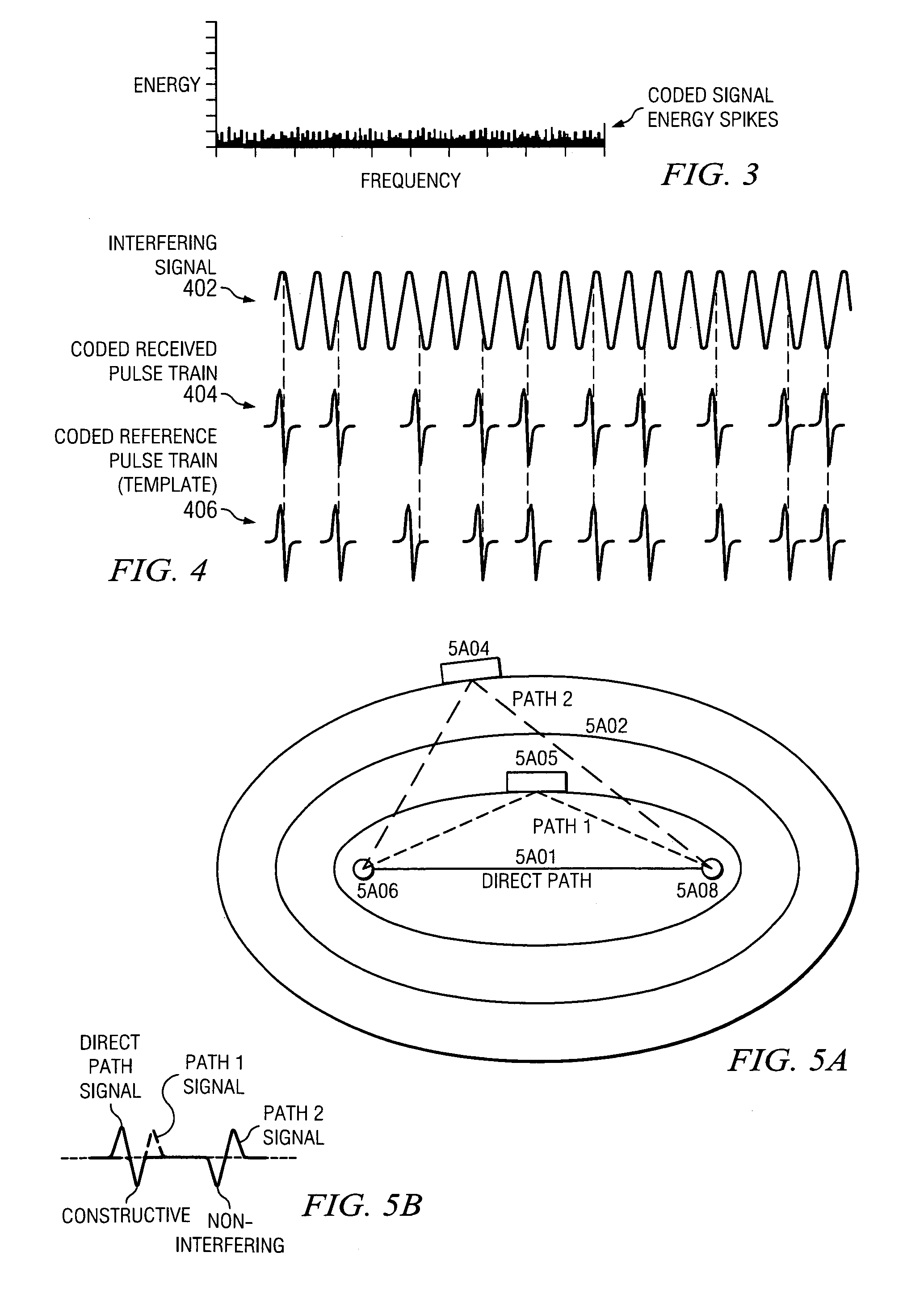
Impulse radio virtual wireless local area network system and method
InactiveUS7027425B1Improve featuresIncrease data rateNetwork traffic/resource managementNetwork topologiesSignal-to-noise ratio (imaging)Engineering
A virtual wireless local area network system and method utilizing impulse radio wherein transmission rates (bit rates) can vary according to the impulse radio transmission quality (signal to noise ratio) and wherein the position of the user can be determined and said user can be directed to an area of greater transmission rates and wherein a plurality of impulse radio portals can be utilized and switched between to maintain high levels of transmission rates while a user is moving within a predetermined area.
Owner:ALEREON
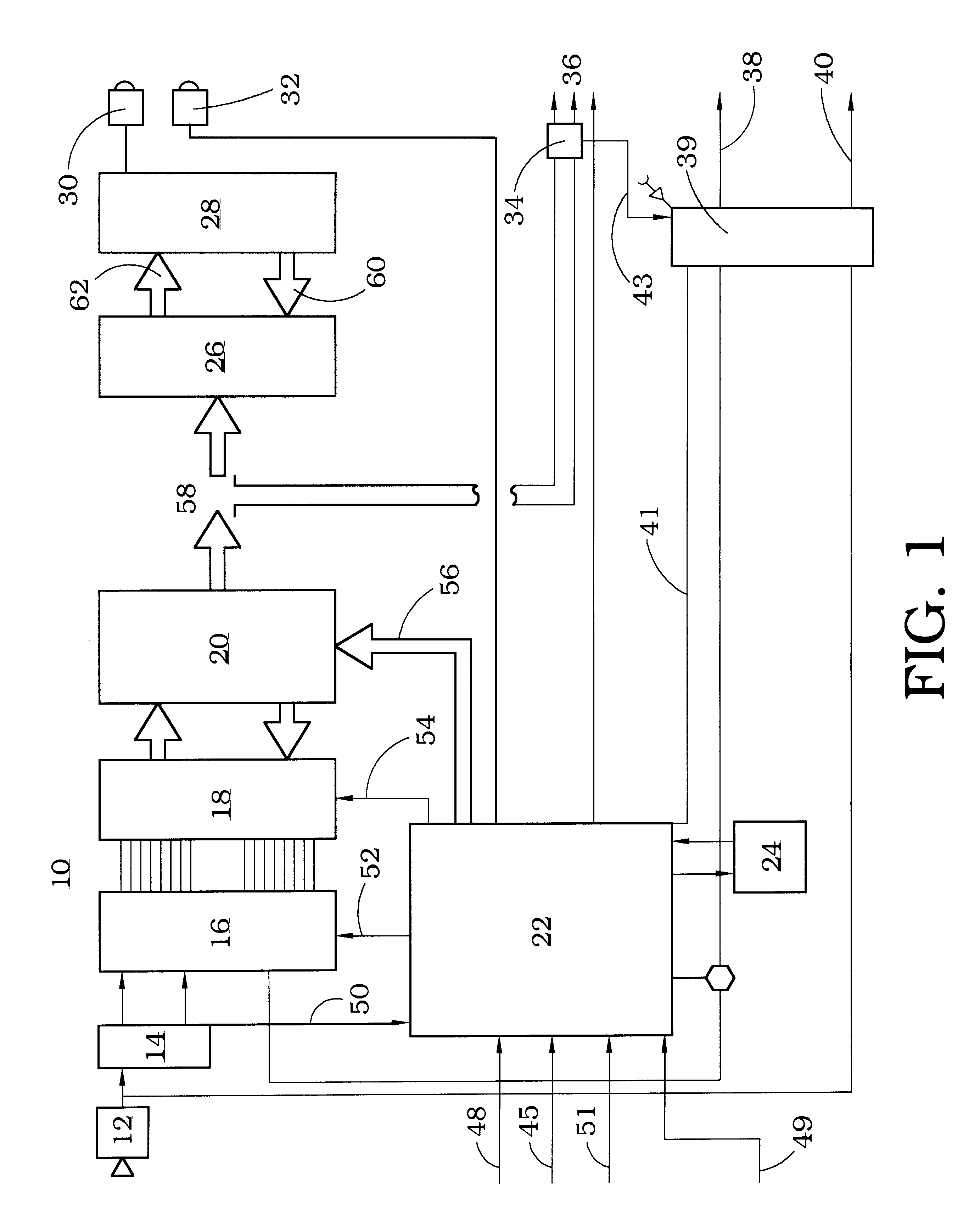
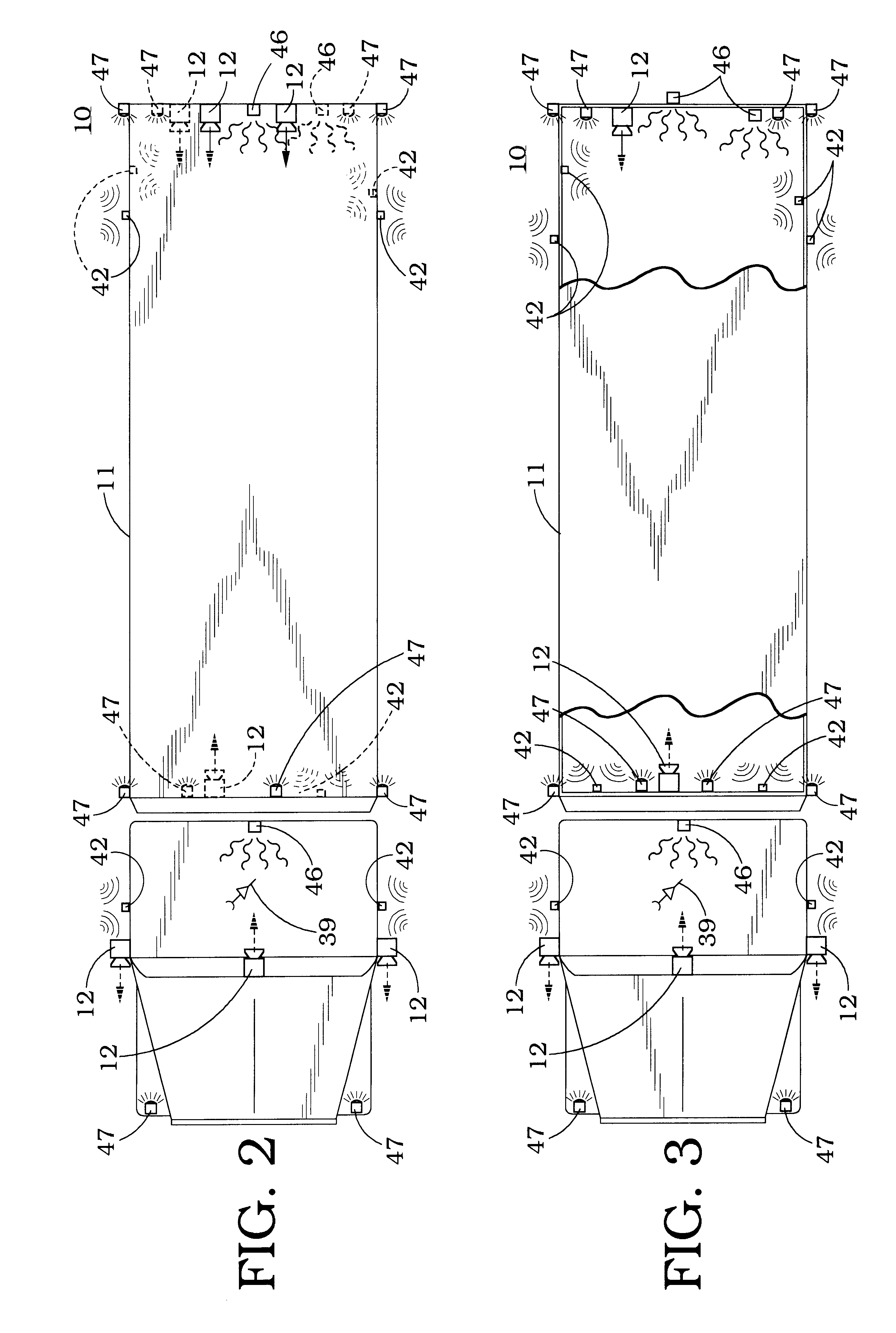
Non-expandable transluminal access sheath
InactiveUS20060253102A1Improved radiopaque characteristicMinimize potential for damageCannulasInfusion syringesFluid transportVisibility
A transluminal sheath is disclosed that permits instrumentation to be passed therethrough. The transluminal sheath comprises a composite structure with an inner layer, an outer layer, and a reinforcing layer. The materials comprising the inner and outer layer are plastically deformable and maintain their shape, once bent into a specific configuration. The reinforcing layer further has radiopacity enhancing coatings to improve visibility under fluoroscopy and a system of flutes running longitudinally, to enhance fluid transport and reduce friction.
Owner:ONSET MEDICAL CORP
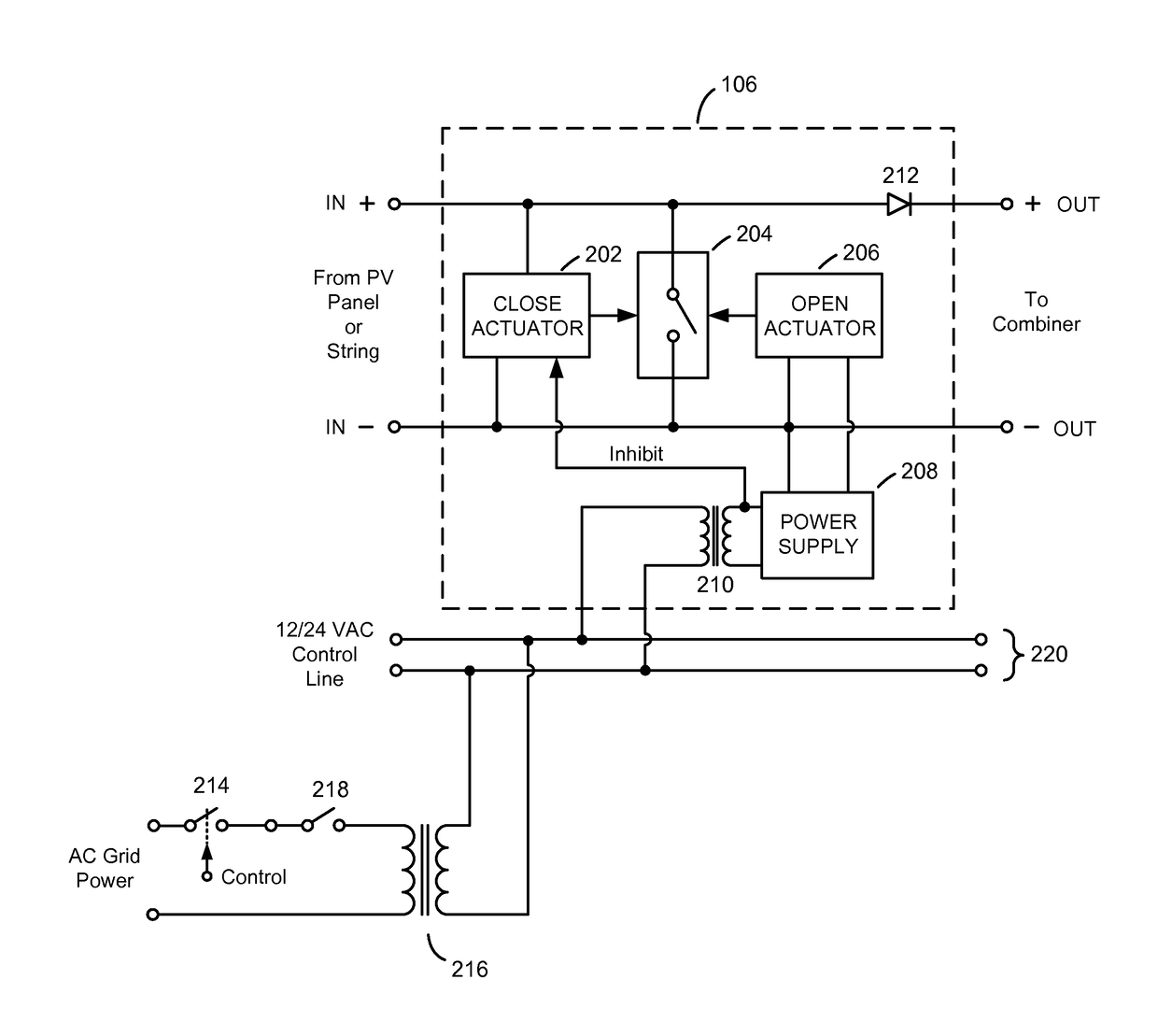
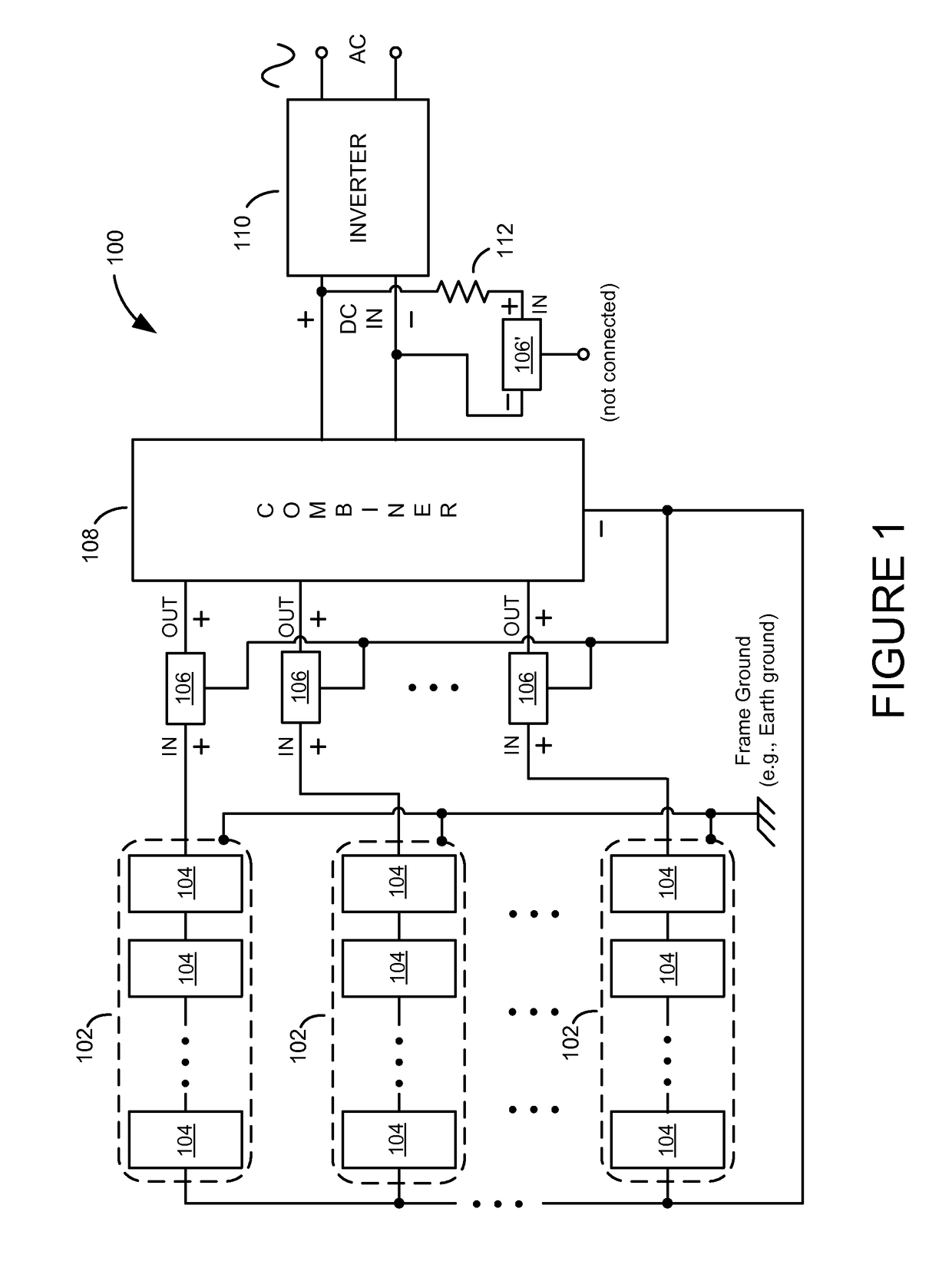
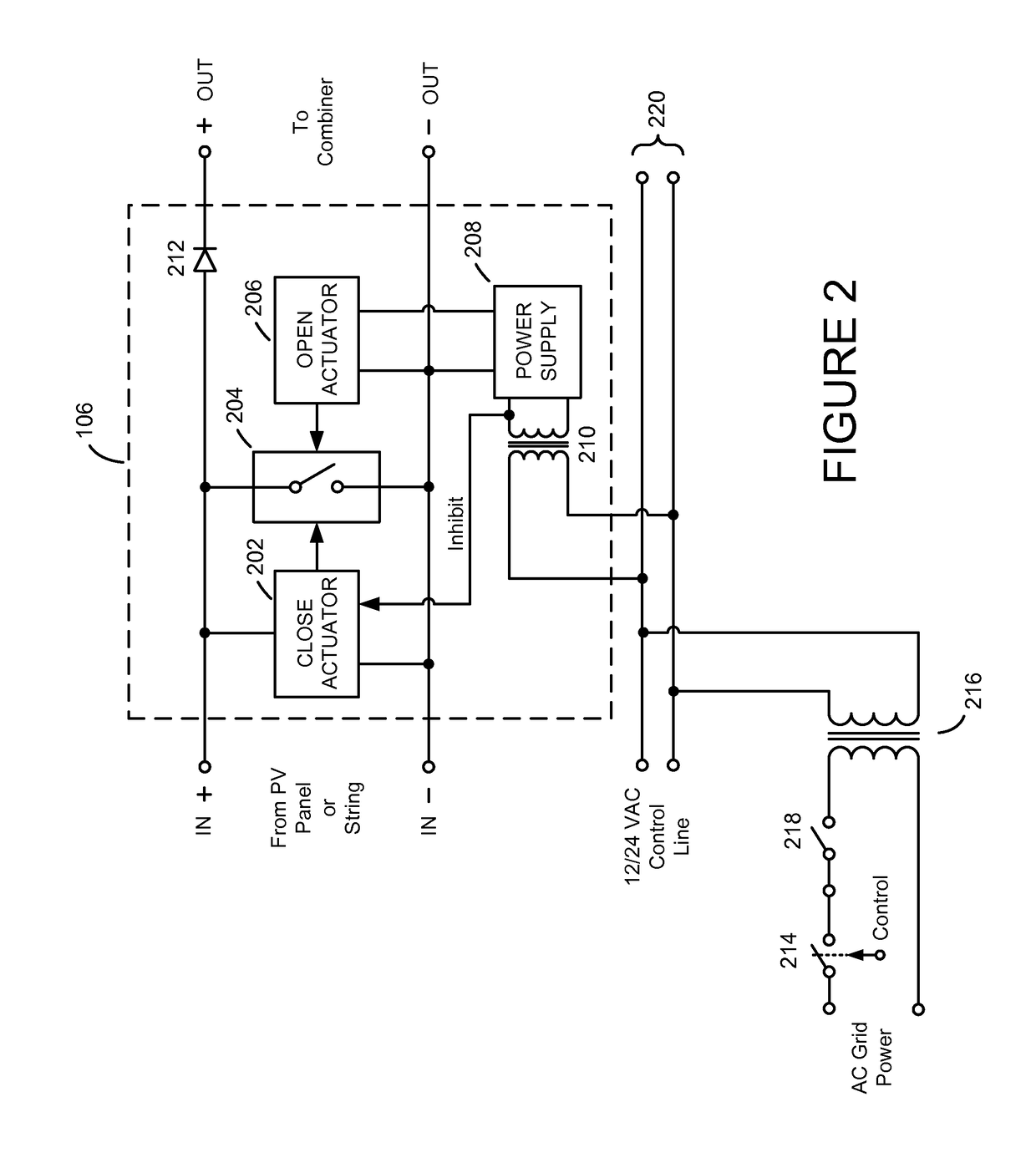
Safety Shutdown System for Photovoltaic Power Generators
ActiveUS20160036235A1Allow accessEasily incorporated into new PVDc network circuit arrangementsBatteries circuit arrangementsPhotovoltaic generatorActuator
A photovoltaic power generator with safety shutdown system includes a plurality of solar panel strings, a combiner, and a plurality of solar safety switches electrically disposed between a plurality of DC outputs of the plurality of solar panels strings and a plurality of DC inputs of the combiner. Each solar safety switch is associated with one of the solar panel strings and includes a solid-state device and a close actuator. The solid-state device of each solar safety switch is connected between the positive and negative terminals of the DC output of its associated solar panel string. The close actuator in each solar safety switch controls whether its associated solid-state device is turned on or is turned off. During normal operating conditions, the close actuators prevent their respective solid-state devices from turning on. However, in the event of a fire, the close actuators cause their associated solid-state devices to turn on, thereby effectively short-circuiting the DC outputs of their associated solar panel strings and preventing the solar panel strings from producing high voltages.
Owner:GETSLA ROBERT
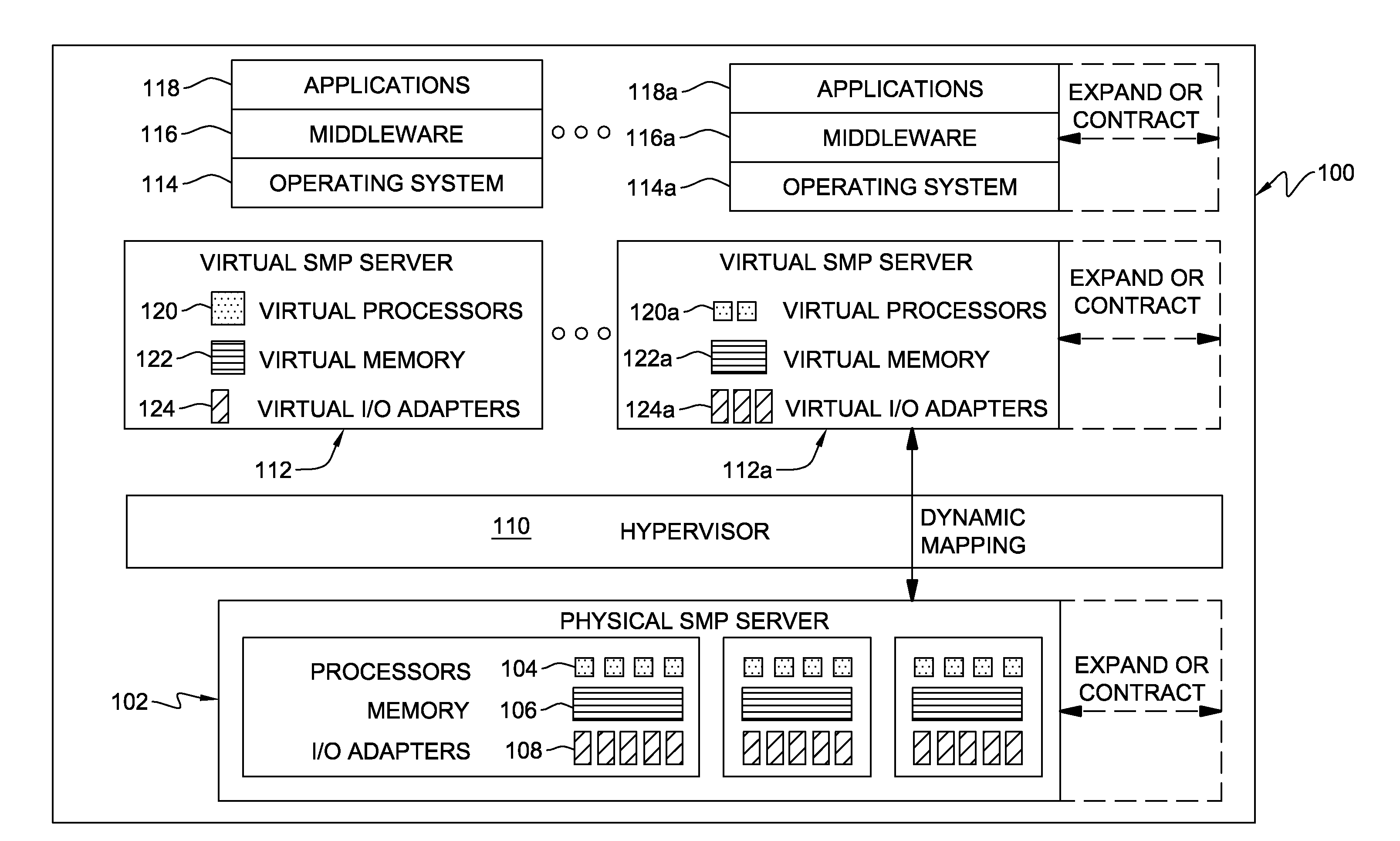
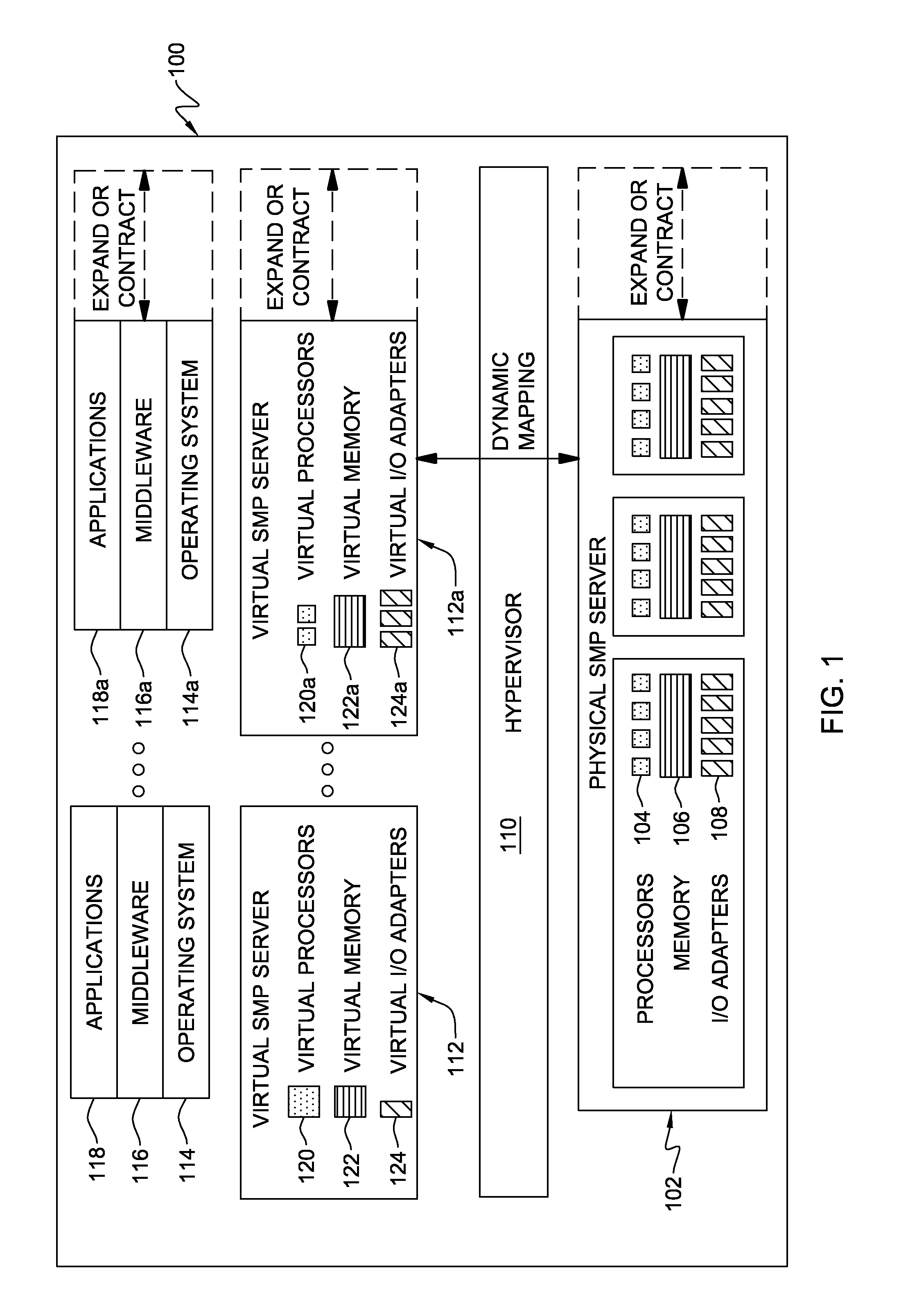
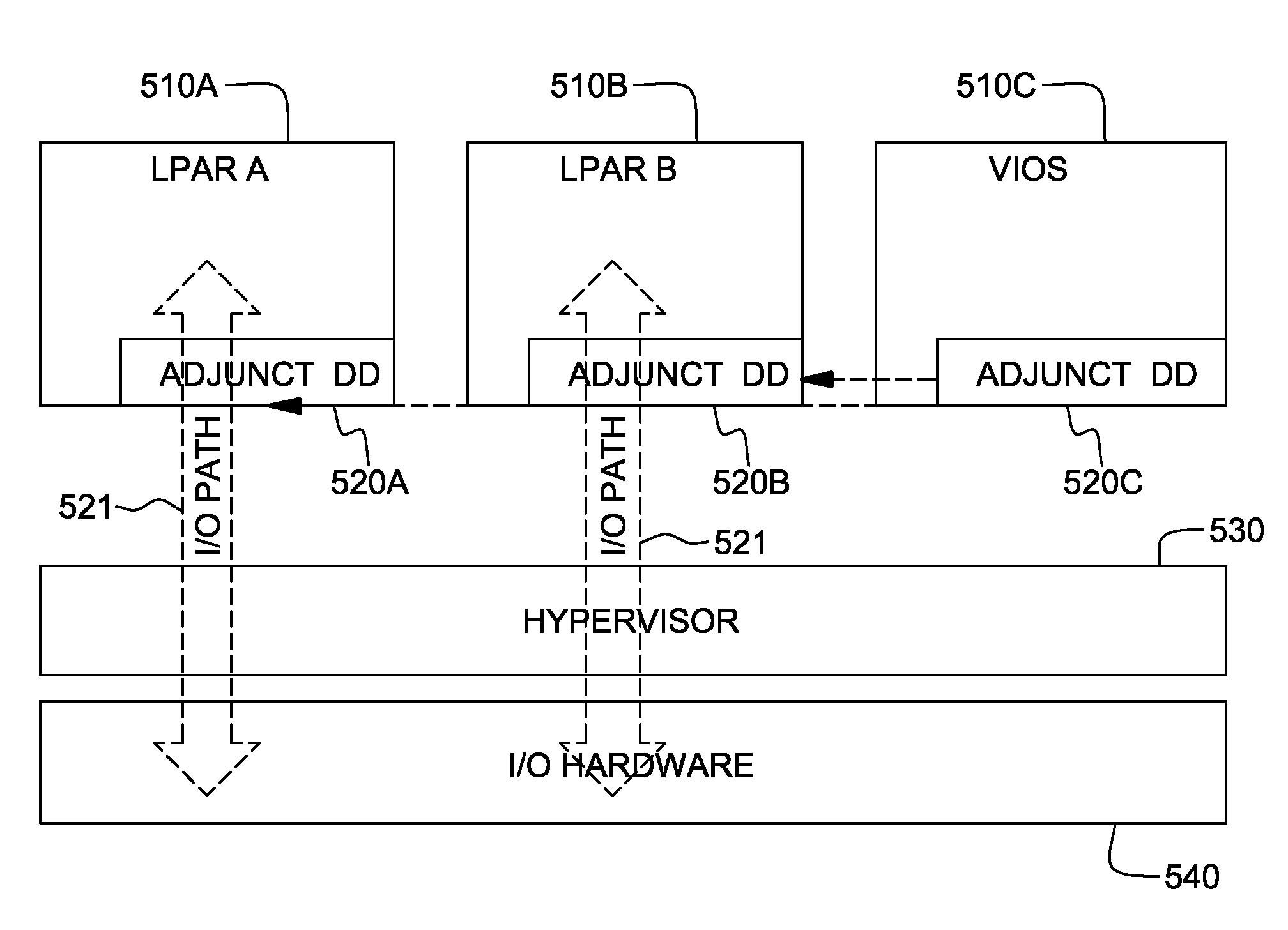
Hypervisor-enforced isolation of entities within a single logical partition's virtual address space
ActiveUS20090037682A1Easy to operateAllow accessMemory architecture accessing/allocationMemory adressing/allocation/relocationData processing systemData treatment
Access control to shared virtual address space within a single logical partition is provided. The access control includes: associating, by a hypervisor of the data processing system, a memory protection key with a portion of a single logical partition's virtual address space being shared by multiple entities, the key preventing access by one of the multiple entities to that portion of the virtual address space, and allowing access by another of the entities to that portion of the virtual address space; and locking by the hypervisor the memory protection key from modification by the one entity, wherein the locking prevents the one entity from modifying the key and thereby gaining access to the portion of the single logical partition's virtual address space with the associated memory protection key. In one embodiment, the one entity is the single logical partition itself, and the another entity is a partition adjunct.
Owner:IBM CORP
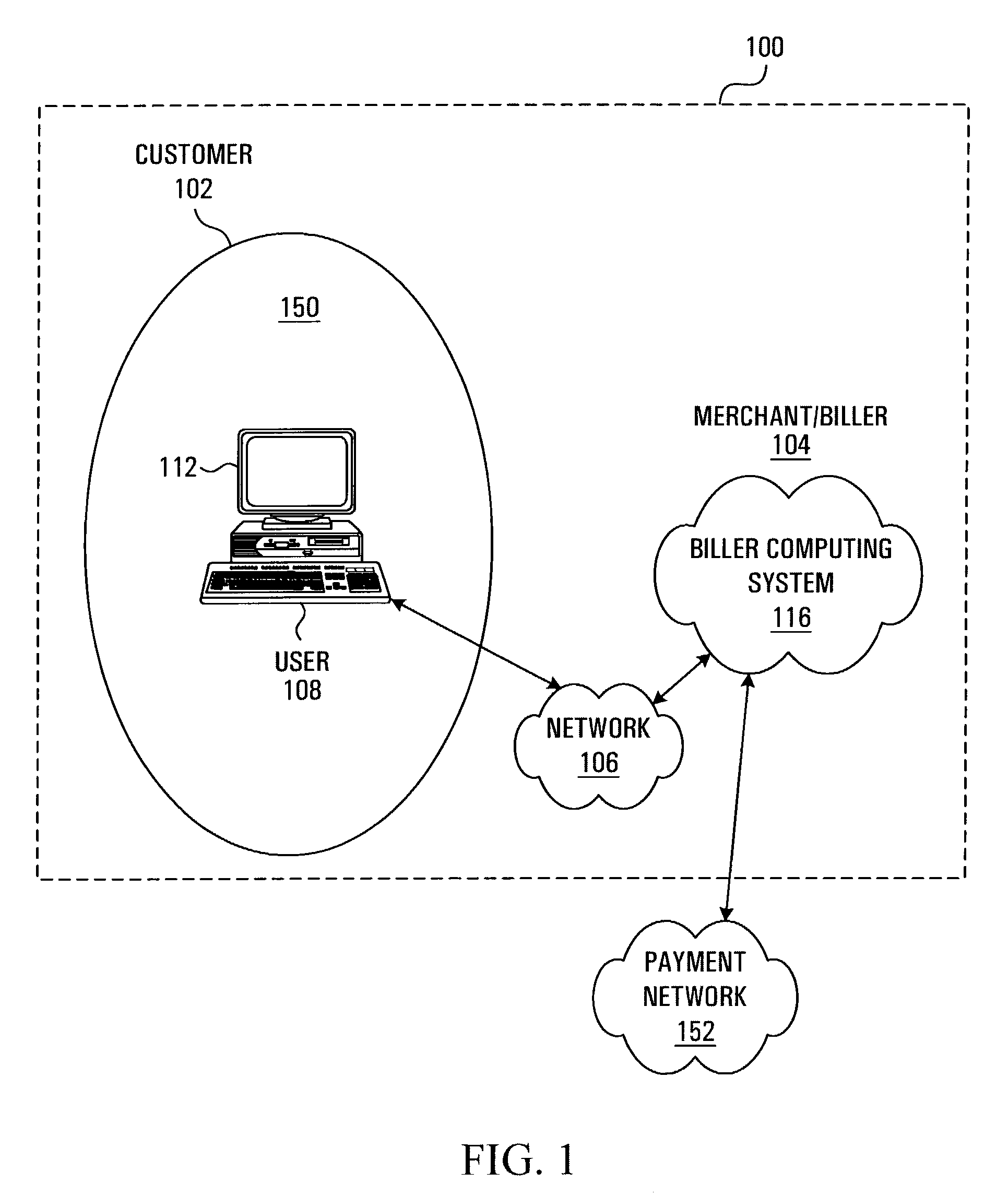
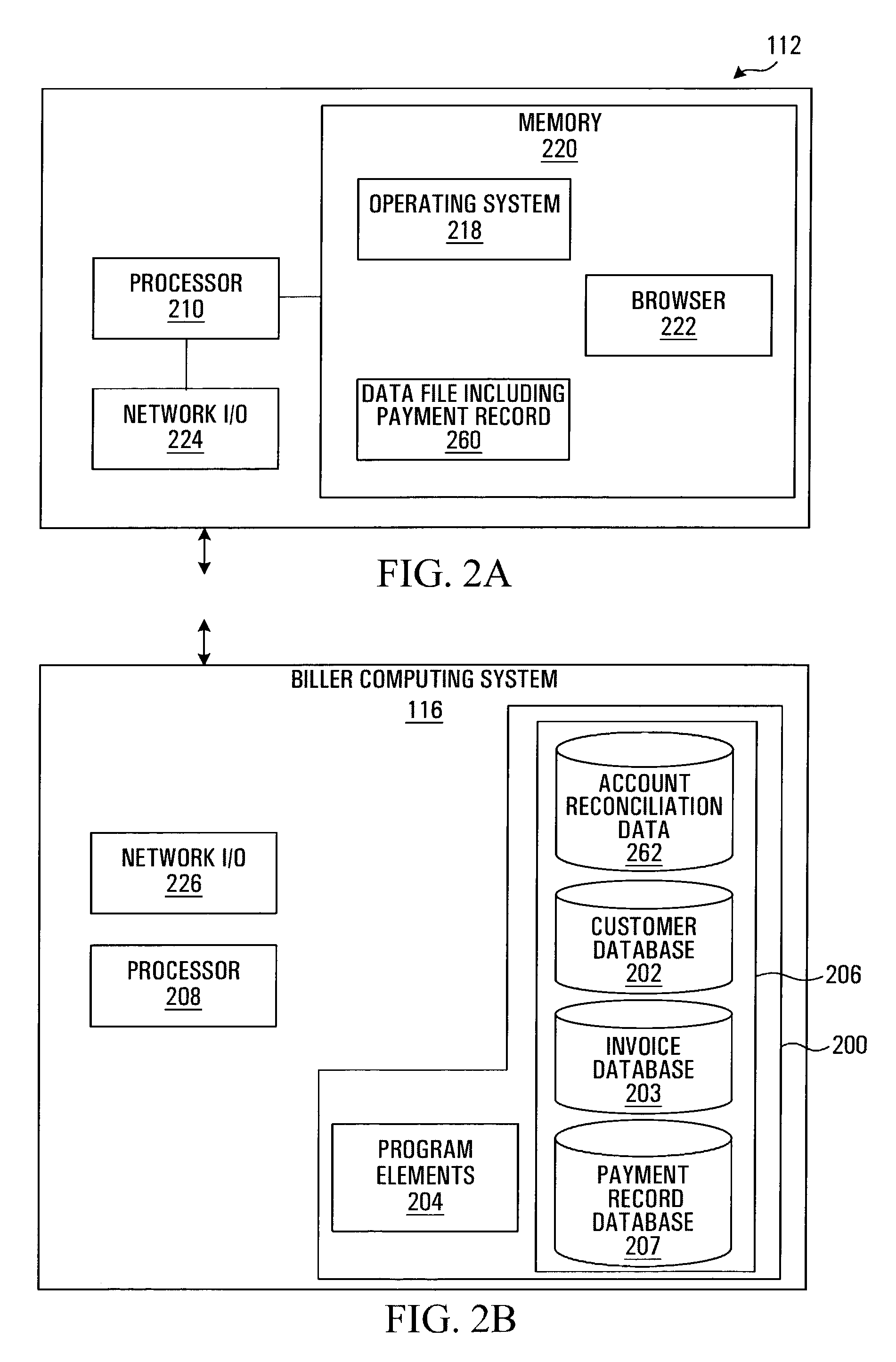
Method and system for generating account reconciliation data
ActiveUS7536325B2Allow accessSaving of time in-houseComplete banking machinesFinancePaymentData export
A method and system for providing information regarding a customer account are provided. The customer account includes a plurality of entries, each entry being indicative of a request for payment where the request for payment is being issued by a biller entity to a customer entity. A payment record including remittance detail data is received over a network account reconciliation data at least in part on the basis of the remittance detail data and the entries in the customer account. A signal suitable for causing information derived from the account reconciliation data to be displayed on a display screen is then transmitted.
Owner:CANADIAN NAT RAILWAY
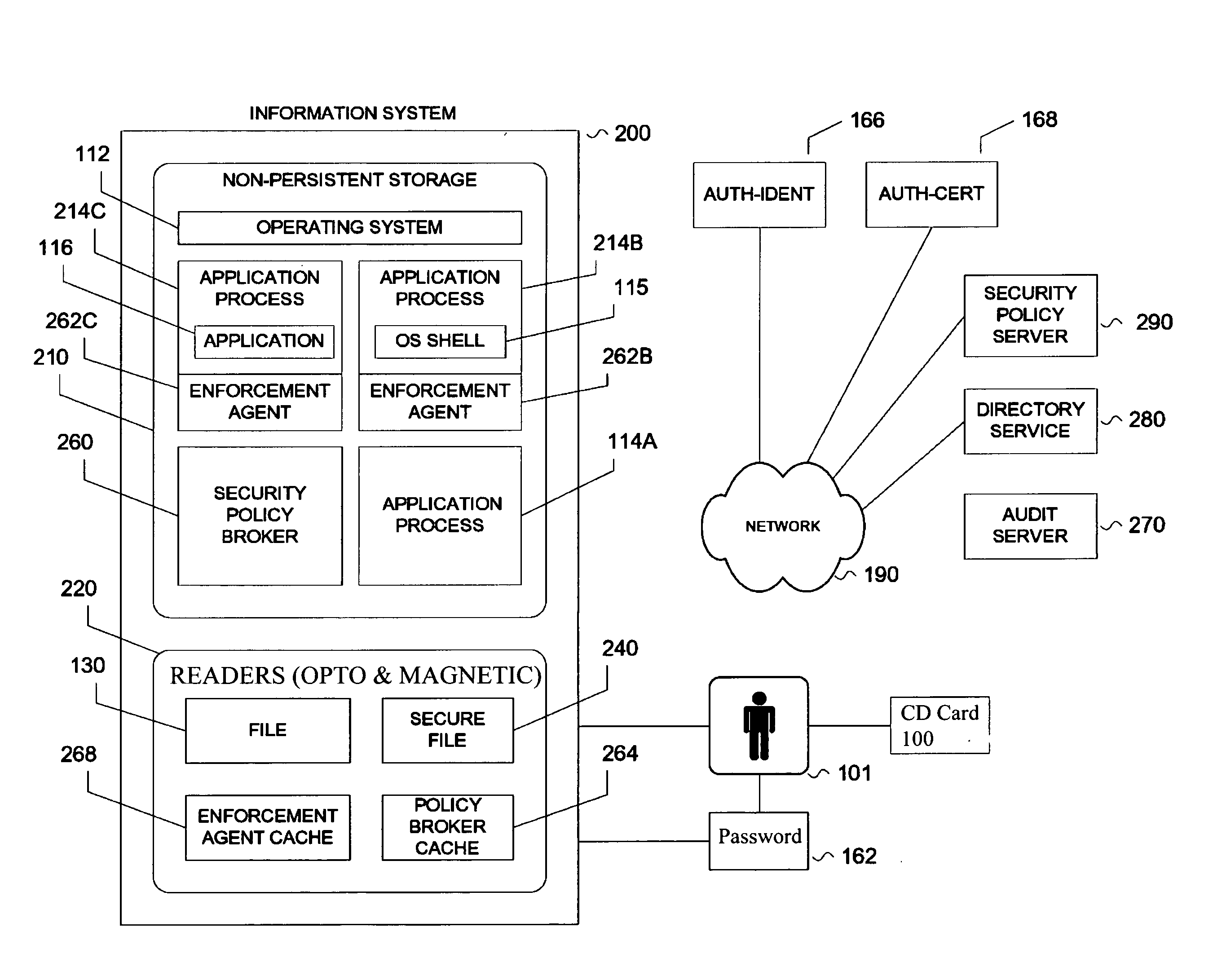
Trusted records using secure exchange
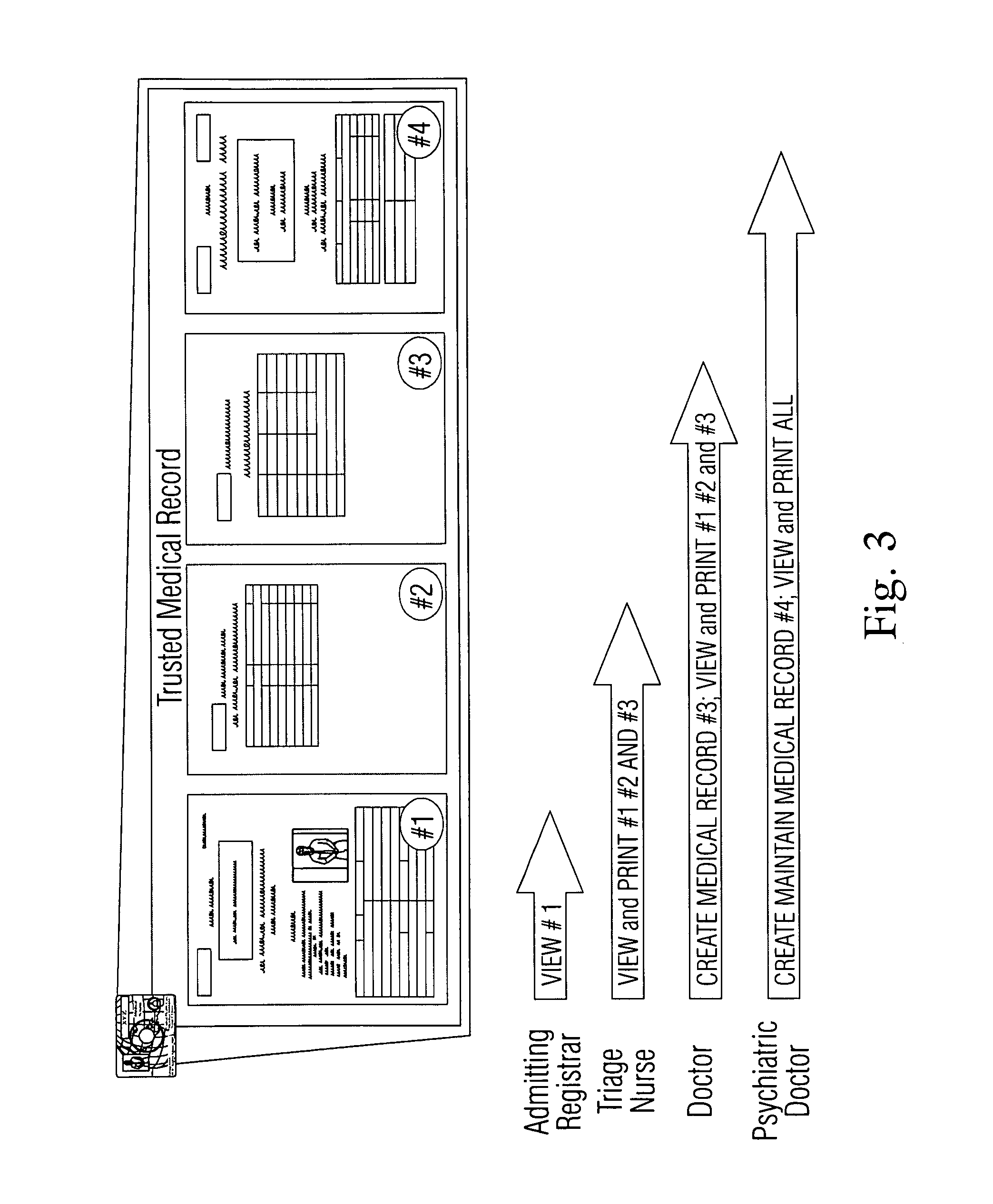
InactiveUS20090055924A1Easy to carryEasy accessDigital data processing detailsUser identity/authority verificationMedical recordThe Internet
A secure method and apparatus for data exchange that allows a client's or patient's financial data, medical records, and other information to be stored on a card-shaped compact disk, with multiple levels of encryption to preserve privacy. The trusted record disc can be read on any computer with a network or internet connection, but access to the information on the disc is restricted according to a password protected hierarchical encryption policy. In order to obtain access to the restricted information, an individual user needs to enter a unique password that is sent to a central server. The server confirms the password and returns an electronic key to the user's computer. The electronic key unlocks the encryption and allow the user to view only the information that is permitted (under federal patient, financial privacy or other laws). Thus, in the medical setting, physicians can review the patient's entire medical record and make changes to it. Nurses, pharmacists, and billing clerks have differing predetermined levels of access.
Owner:SECURE EXCHANGE SOLUTIONS
Method and system for controlling access to data stored on a data storage device
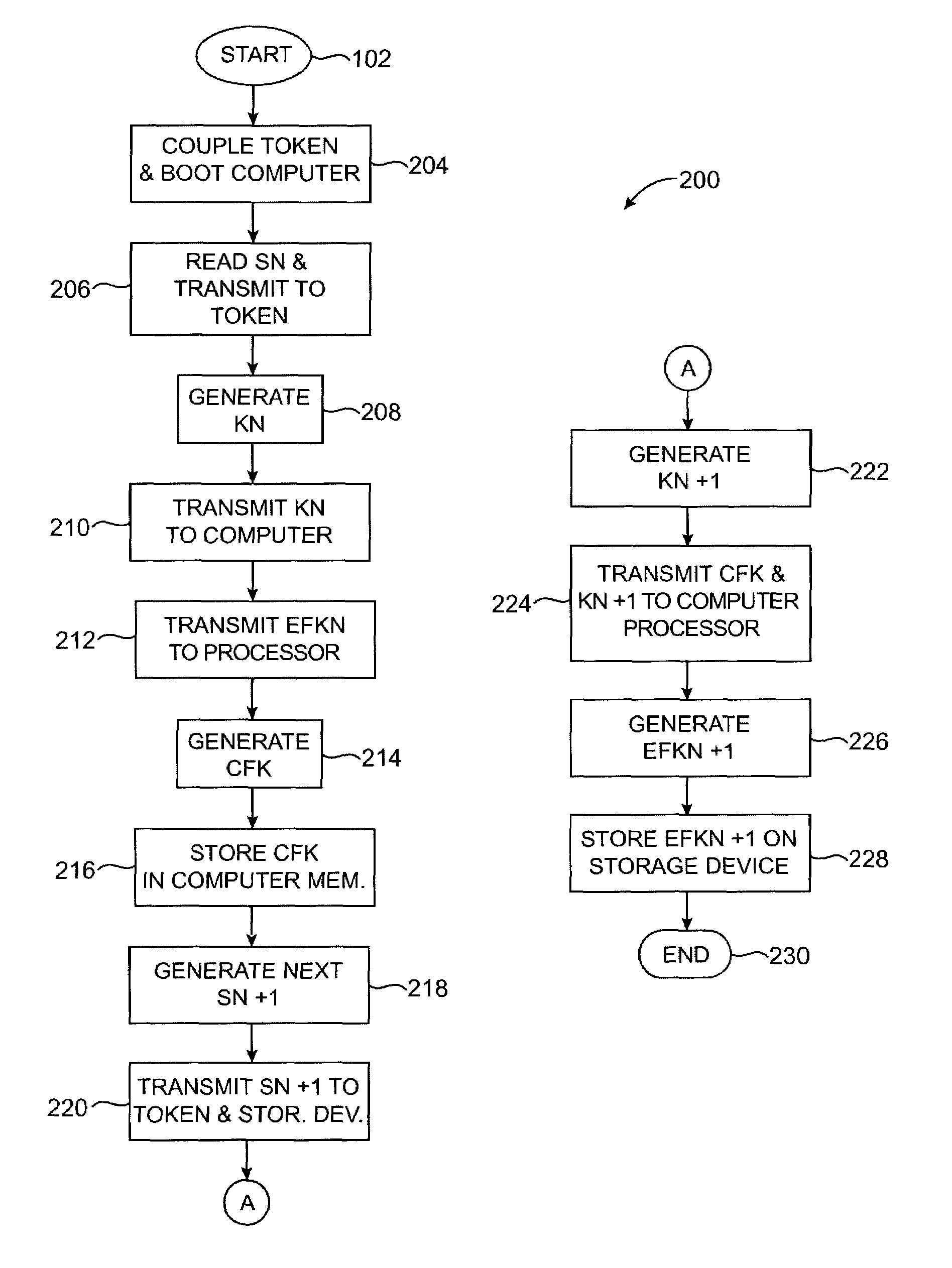
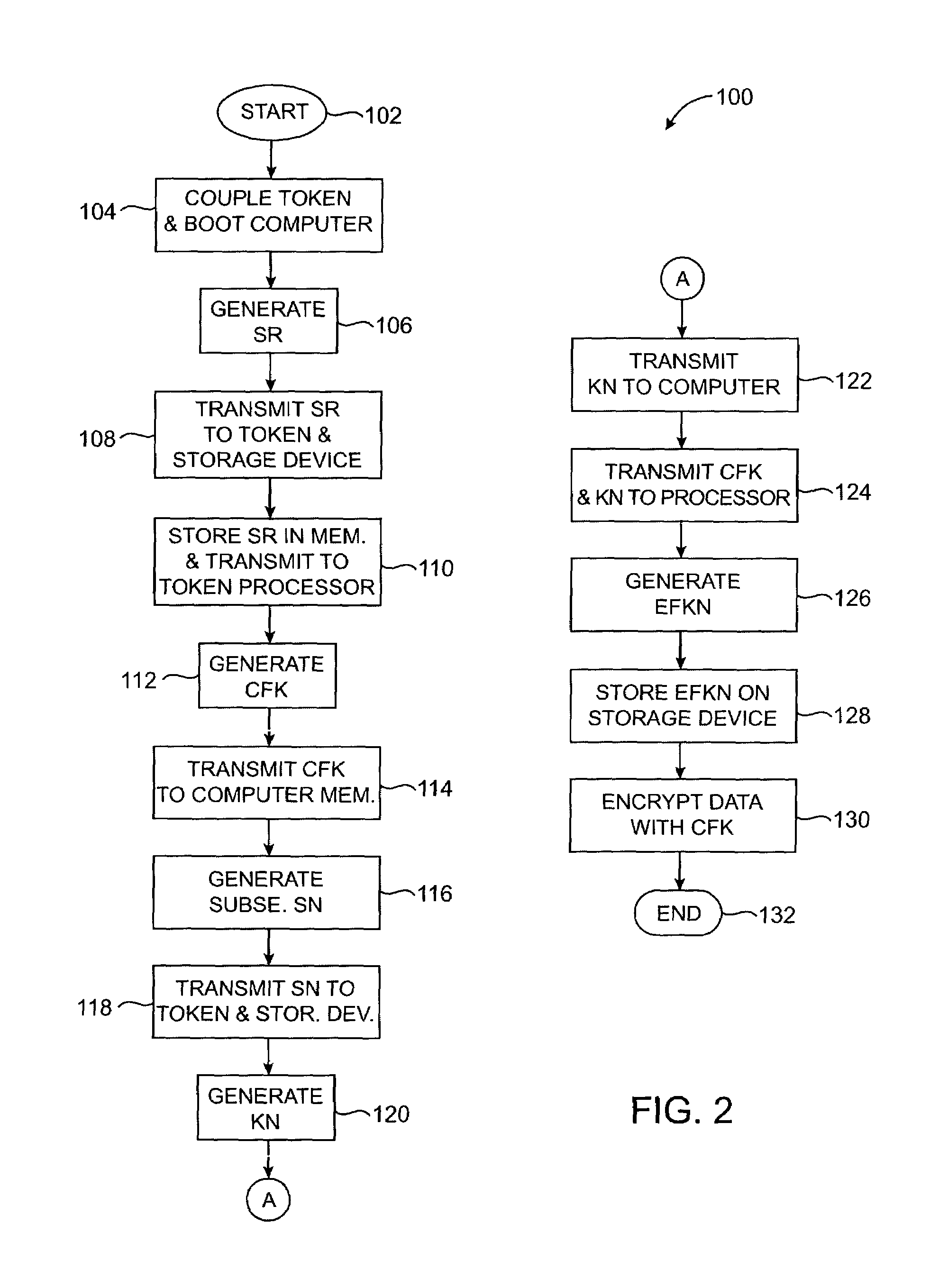
ActiveUS7191344B2Allow accessKey distribution for secure communicationDigital data processing detailsHard disc driveData storing
A system and method of data encryption and decryption for controlling access to a data storage device such as a hard disk drive or optical drive is provided. The invented method utilizes data encryption and decryption techniques, combined with a token device, to control access to data stored on the data storage device.
Owner:AUTHENEX
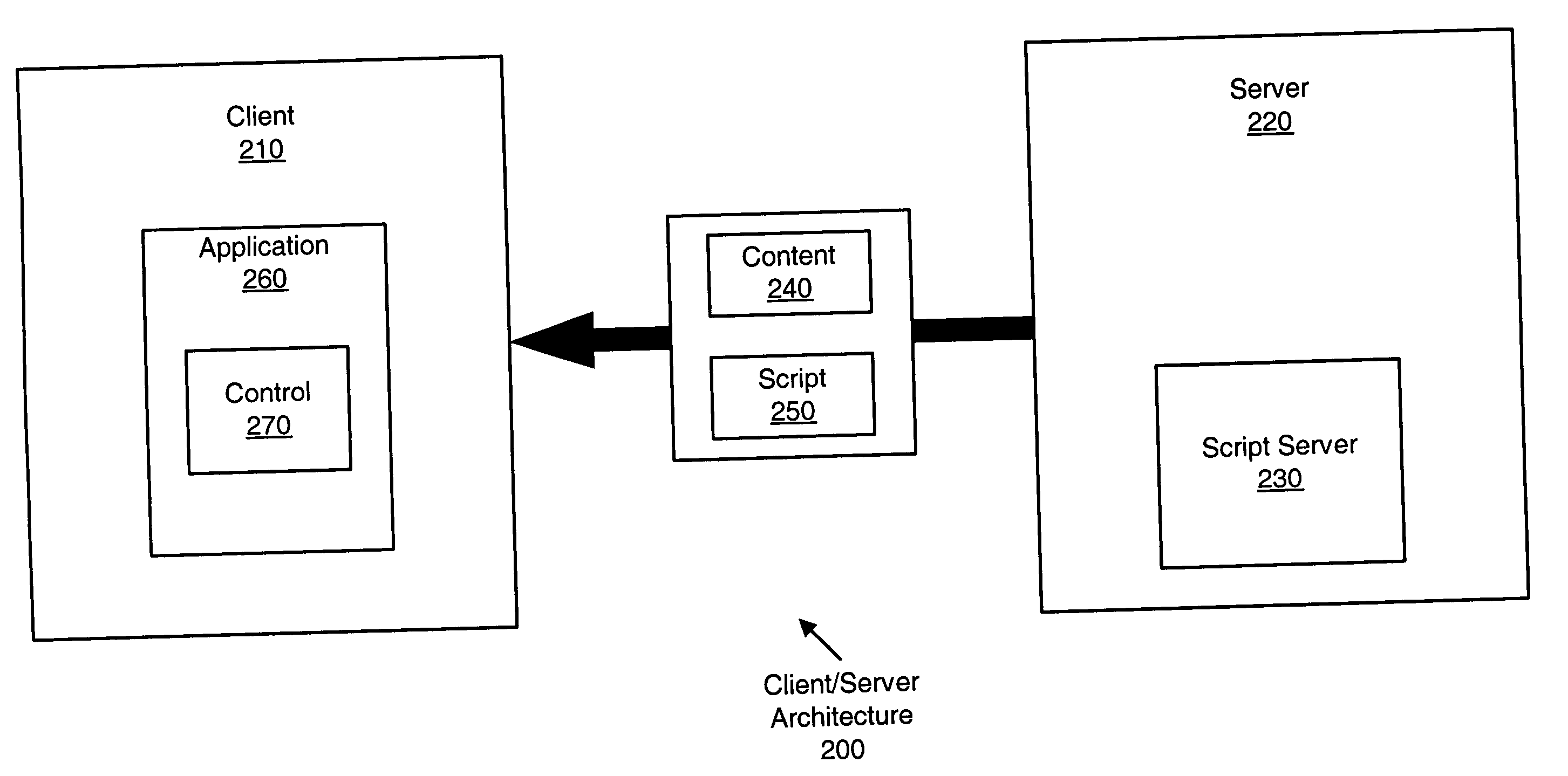
Method and apparatus for providing desktop application functionality in a client/server architecture
InactiveUS20050050547A1Quick and efficient and extensible accessAdversely impacting network resourceMultiprogramming arrangementsStructured data retrievalApplication softwareClient-side
A method and apparatus for synchronizing a client-side information store with a server-side database in a client / server architecture are disclosed. The method includes receiving data and receiving a script. The script defines a function of a control, and the function allows the control to perform an operation using the data.
Owner:R2 SOLUTIONS
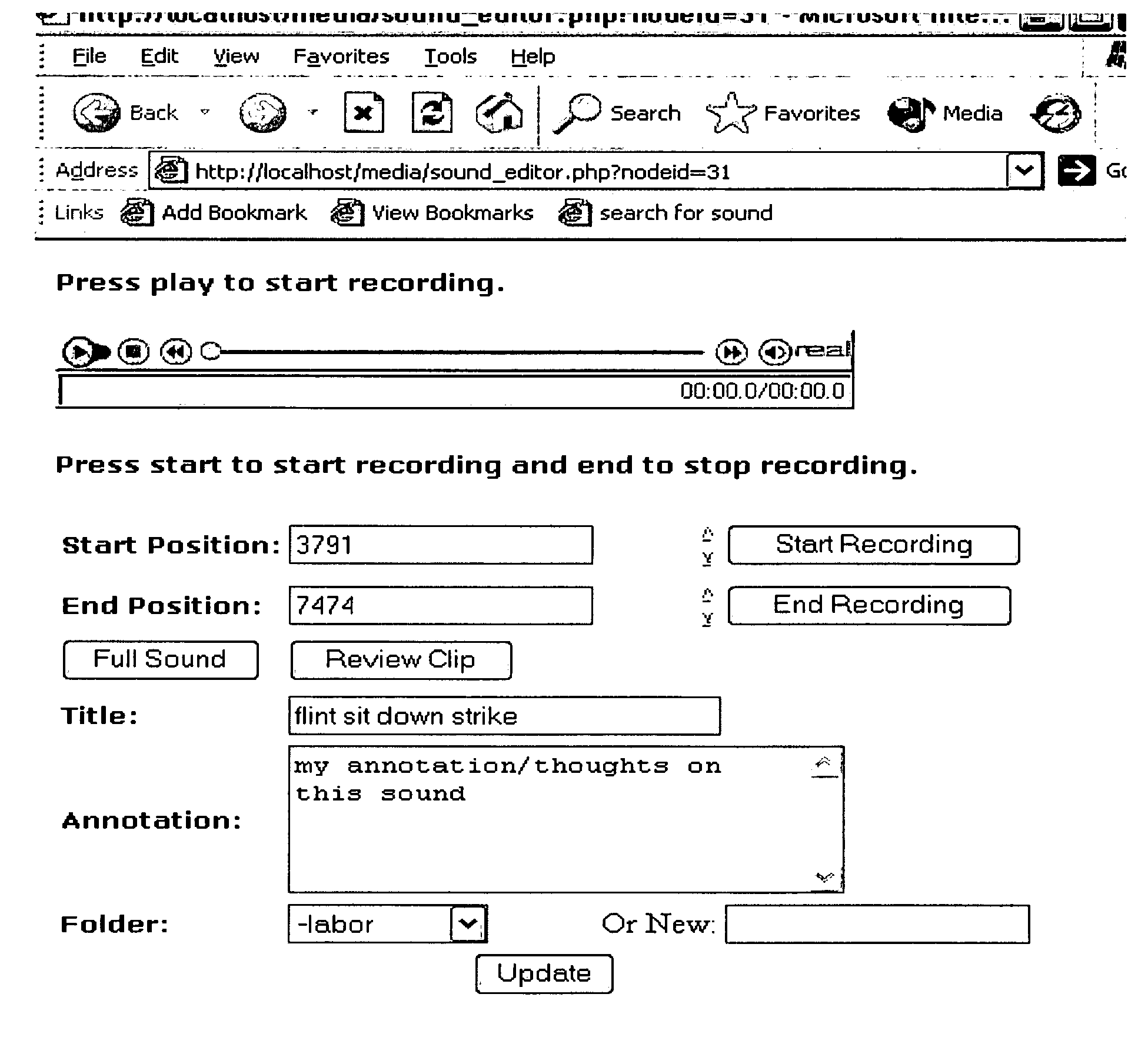
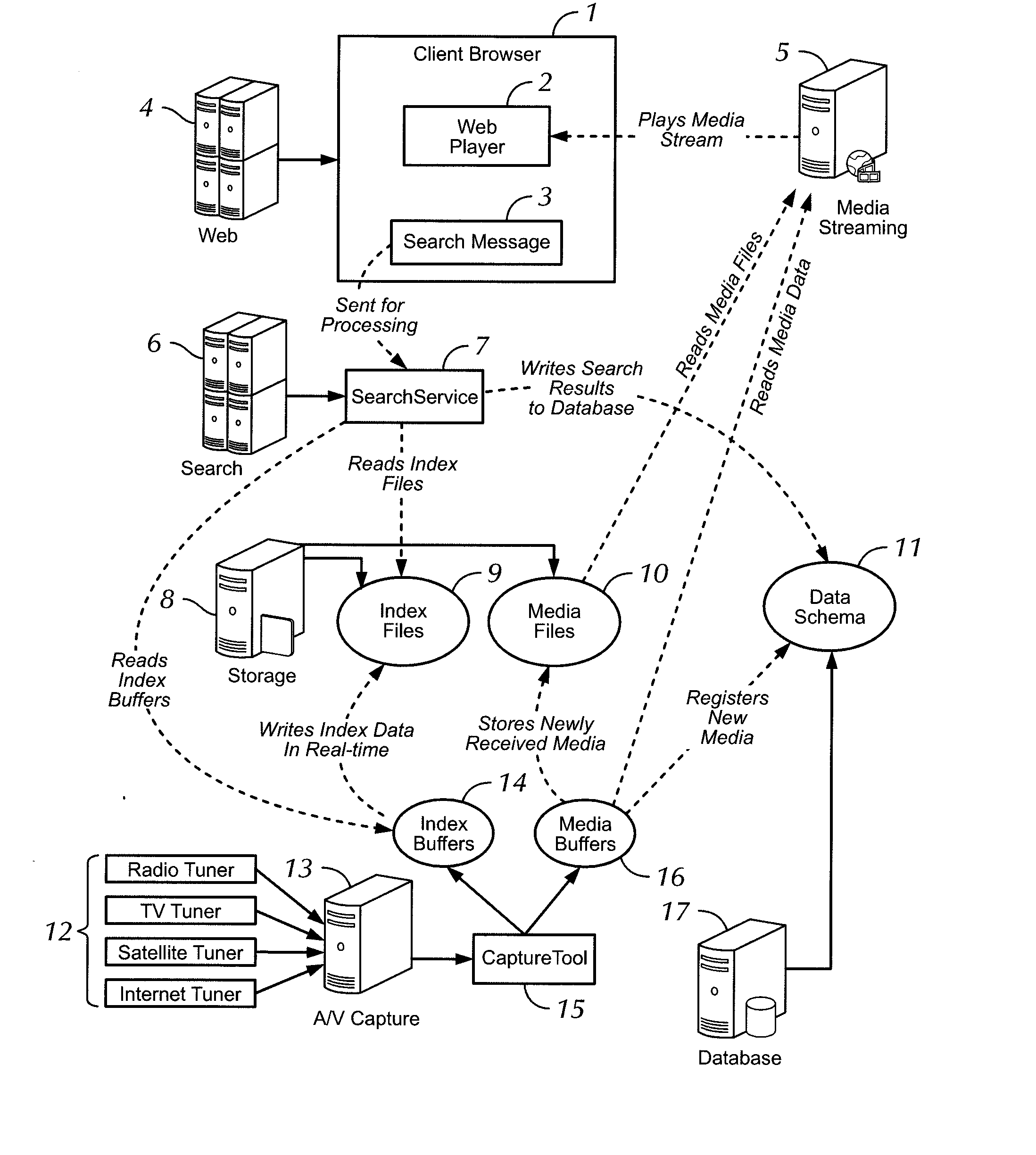
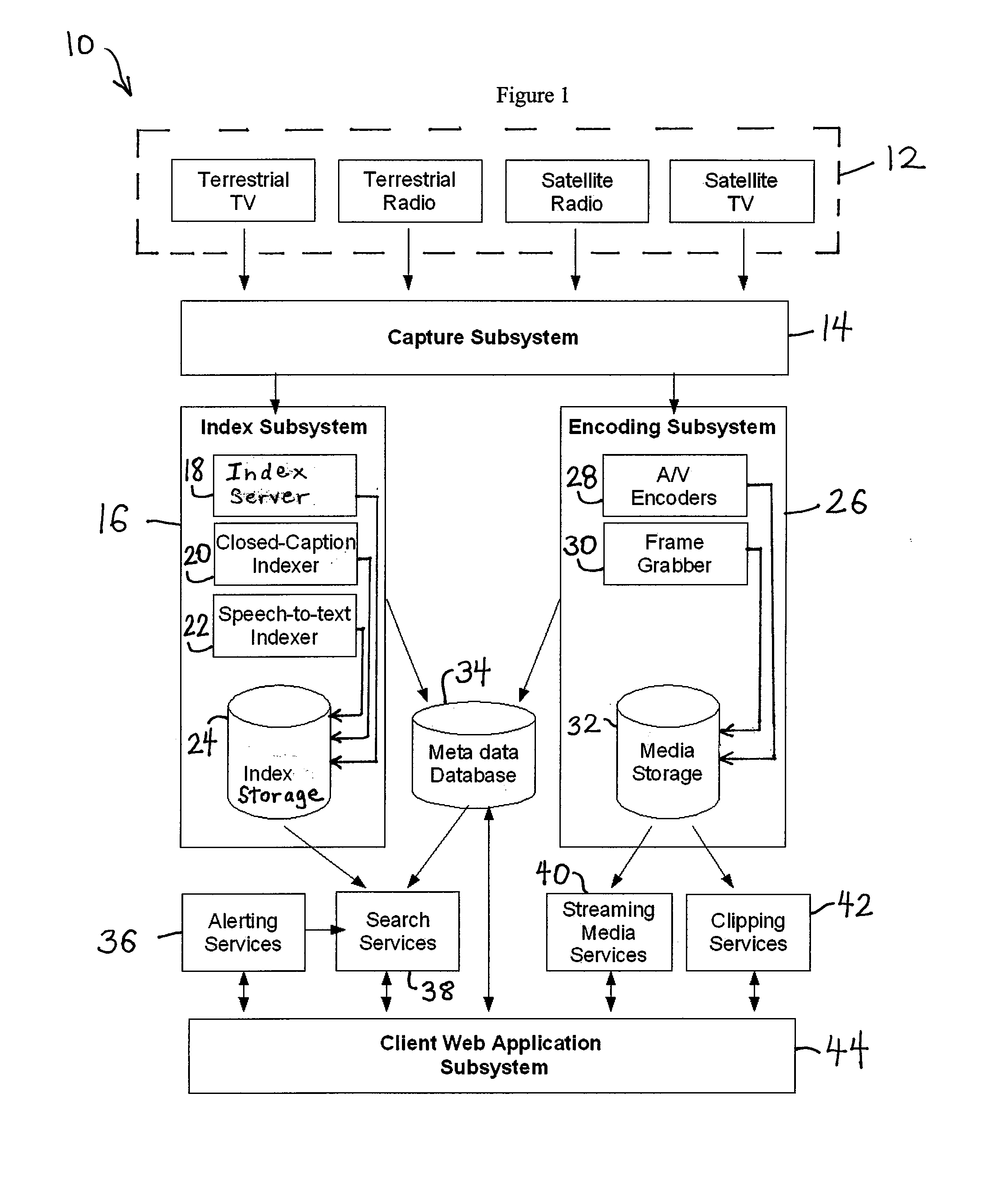
Systems and methods for identifying, segmenting, collecting, annotating, and publishing multimedia materials
InactiveUS20050144305A1Allow accessFlexibility and ease-of-useMultiple digital computer combinationsTransmissionServer-sideAnnotation
The present invention relates to systems and methods for identifying, segmenting, collecting, annotating, and publishing multimedia materials. In some embodiments, the present invention provides a comprehensive server-side system for editing, annotating, managing and presenting multimedia events from a plurality of multimedia sources.
Owner:BOARD OF TRUSTEES OPERATING MICHIGAN STATE UNIV
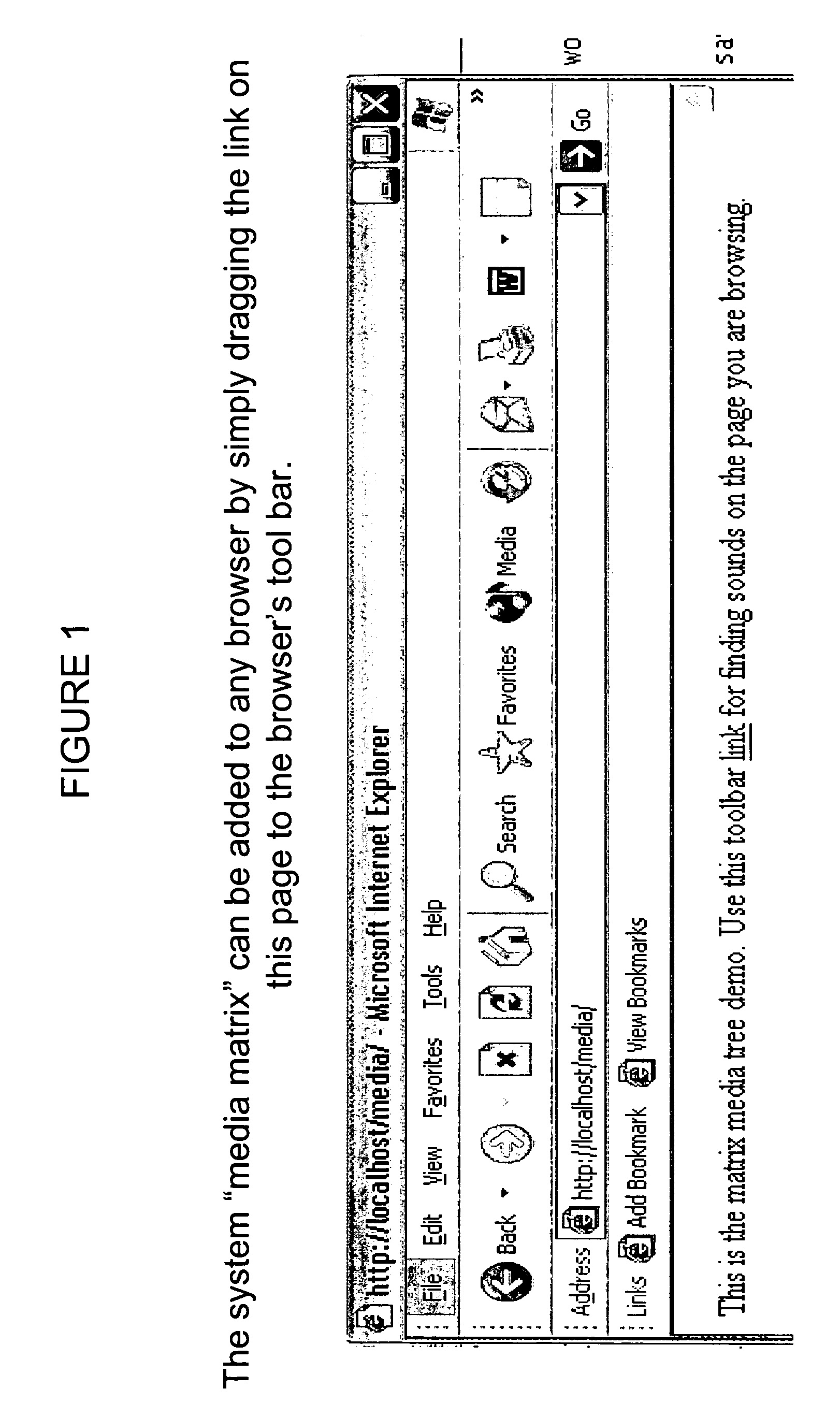
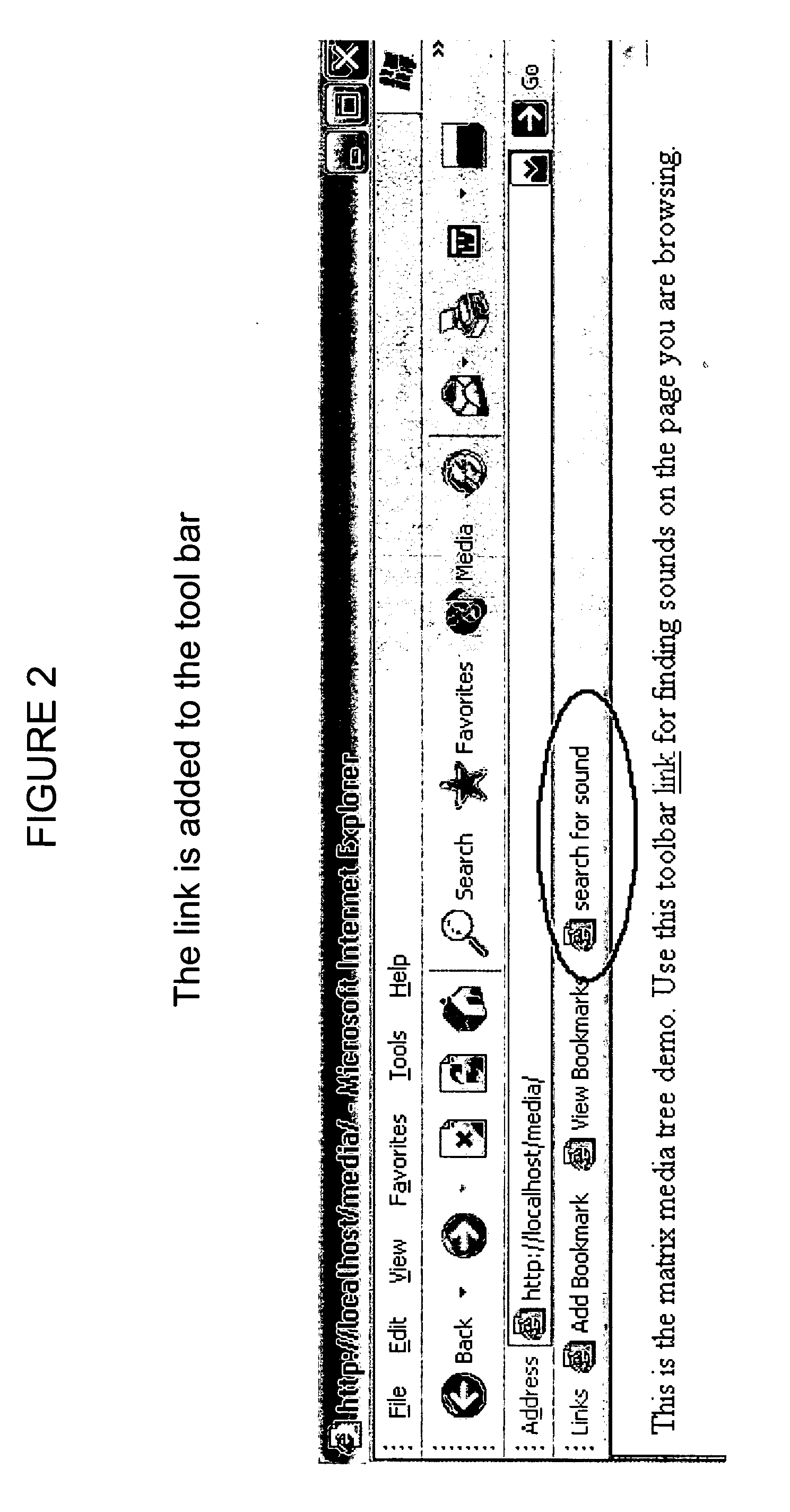
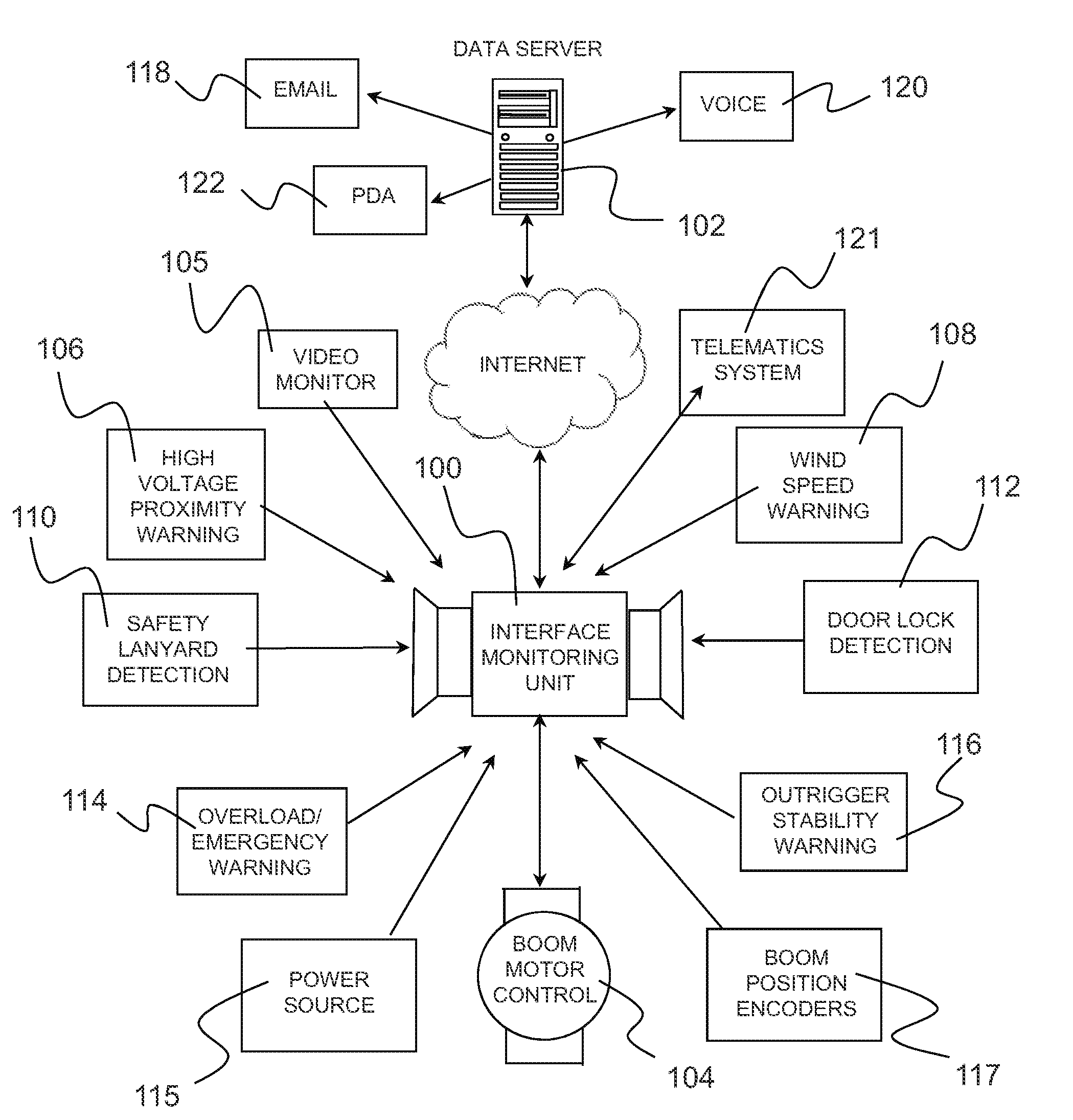
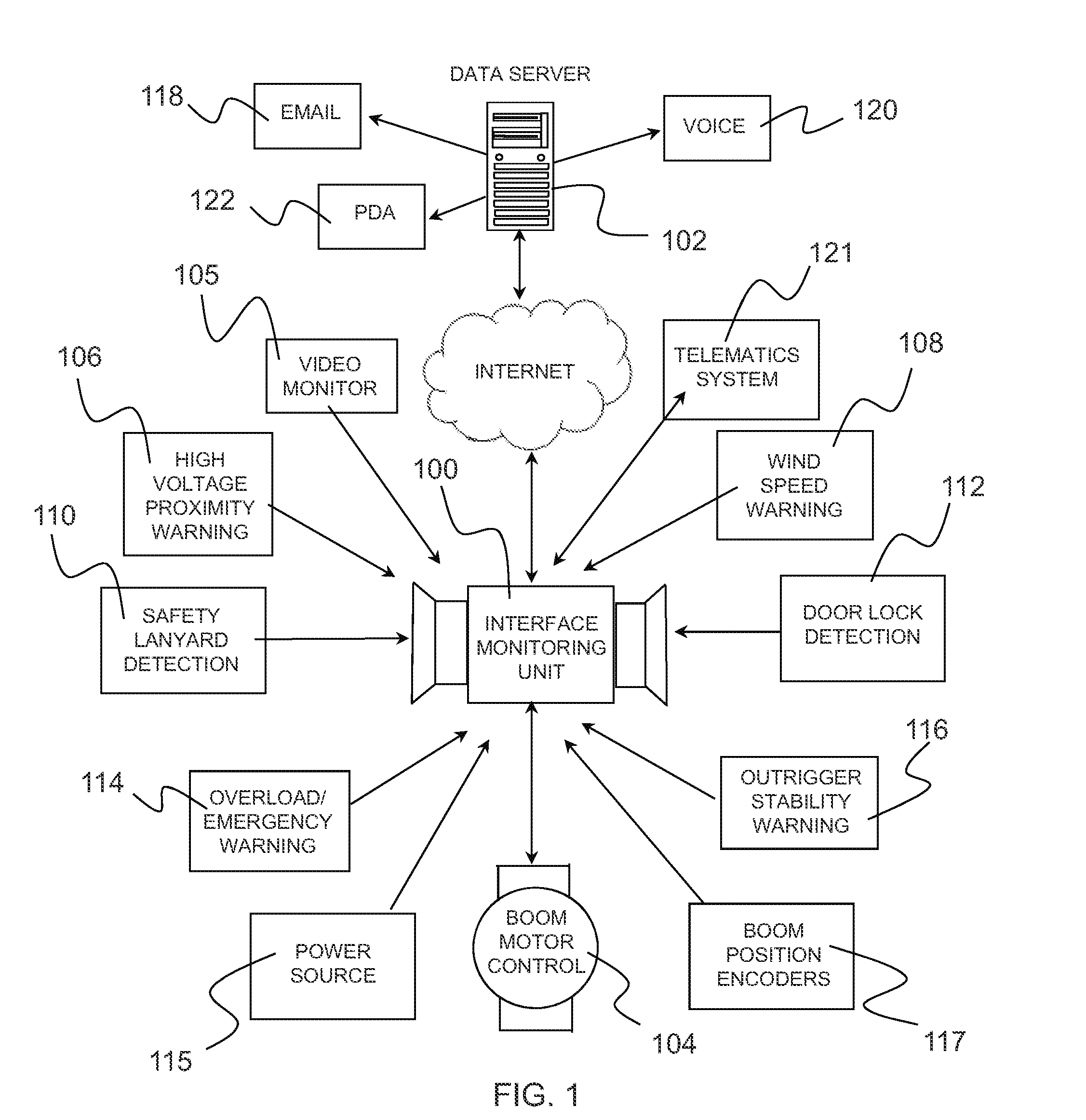
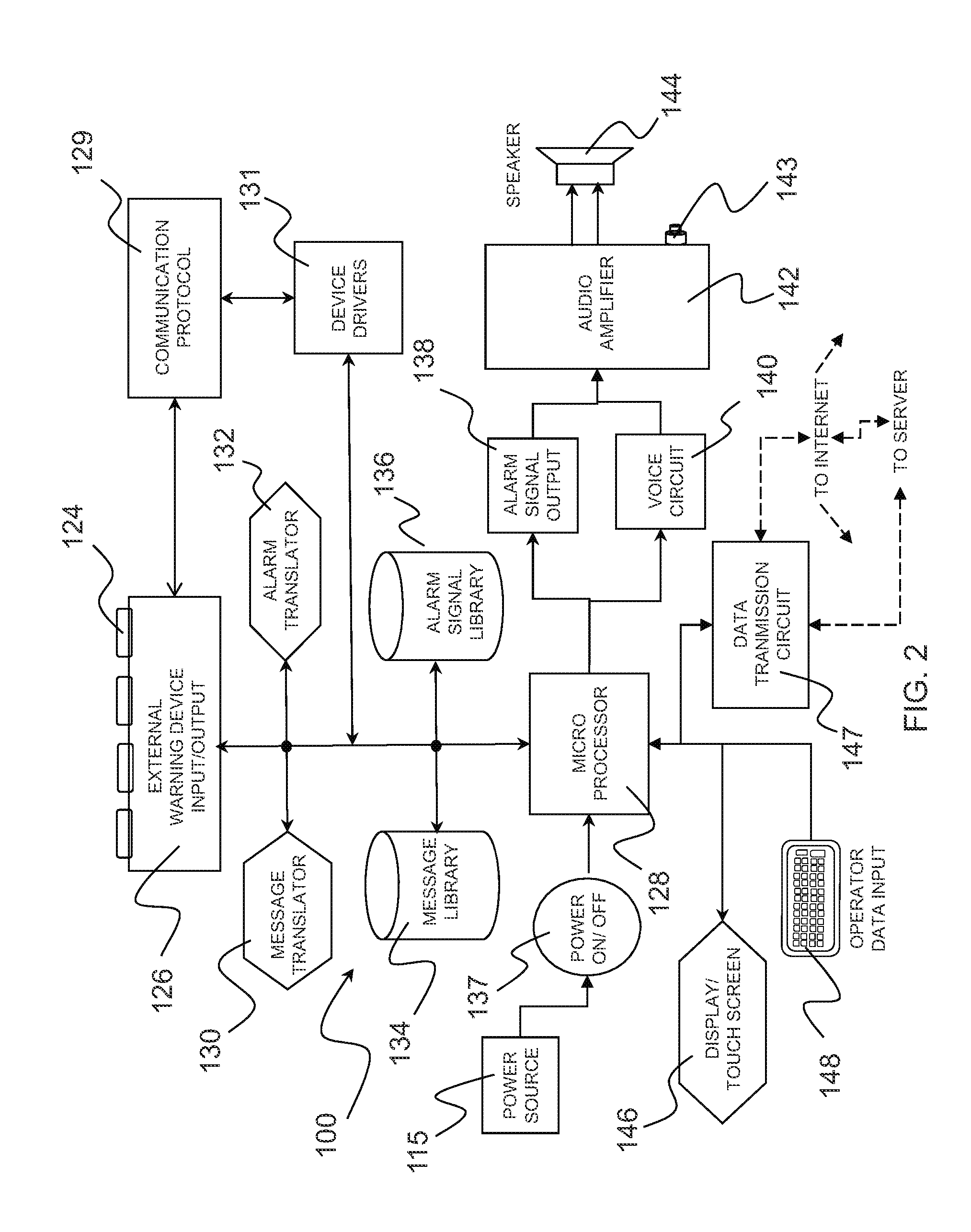
Warning and message delivery and logging system utilizable in the monitoring of fall arresting and prevention devices and method of same
ActiveUS20120217091A1Allow accessEasy to useSafety devices for lifting equipmentsDigital data processing detailsMessage deliveryWarning system
An active interface monitoring and warning system for fall arresting / prevention devices delivering specific fault condition messages to individuals who are subject to accidental falls or other safety hazards when performing construction or the like or when operating elevating construction machinery such as aerialift work platforms and the like. The invention further provides a data logging system to record and transmit operational conditions, fault conditions and safety infractions.
Owner:O E M CONTROLS INC +1
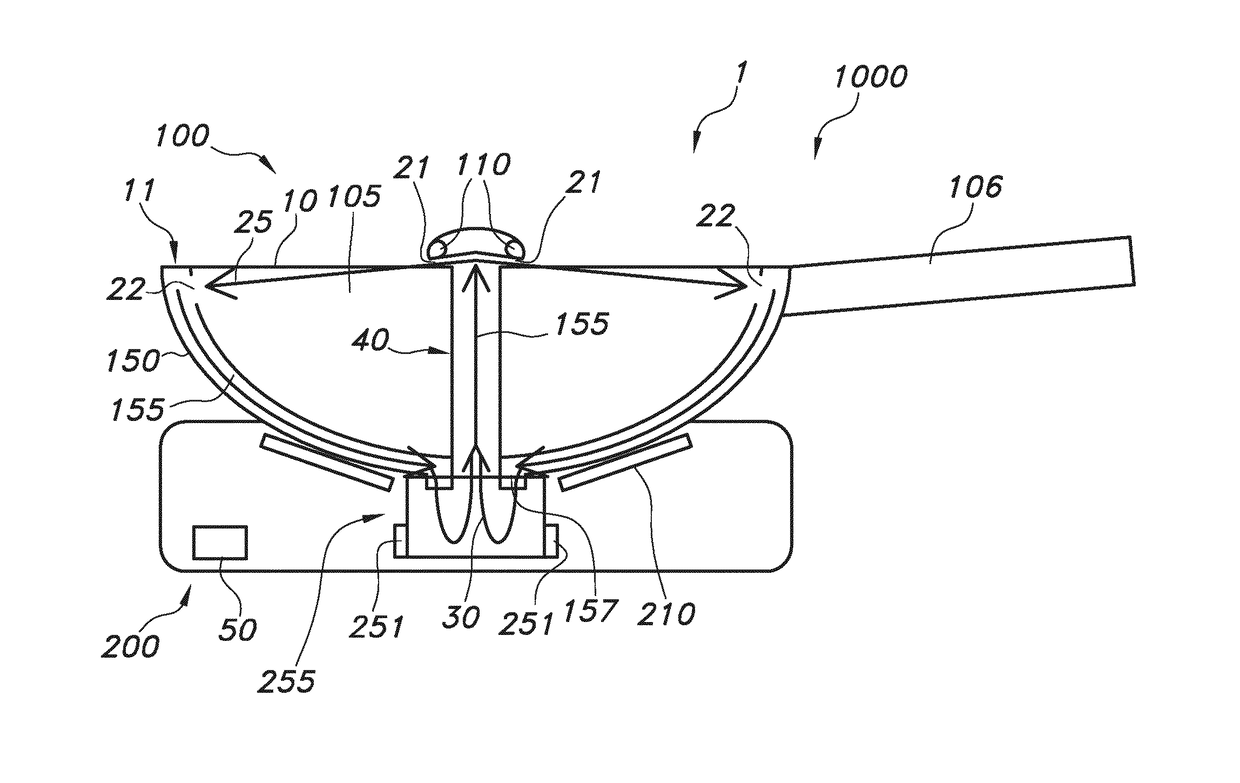
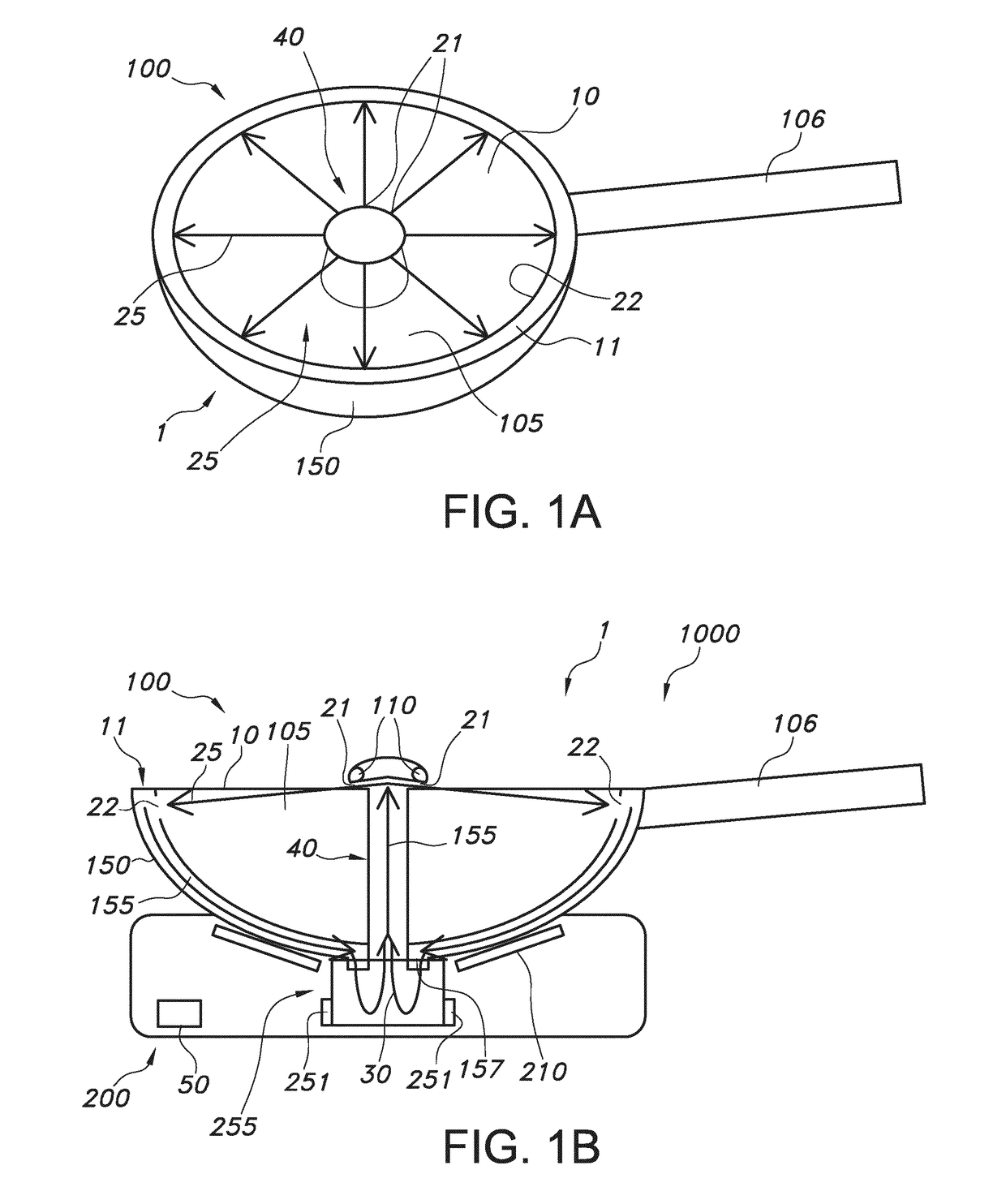
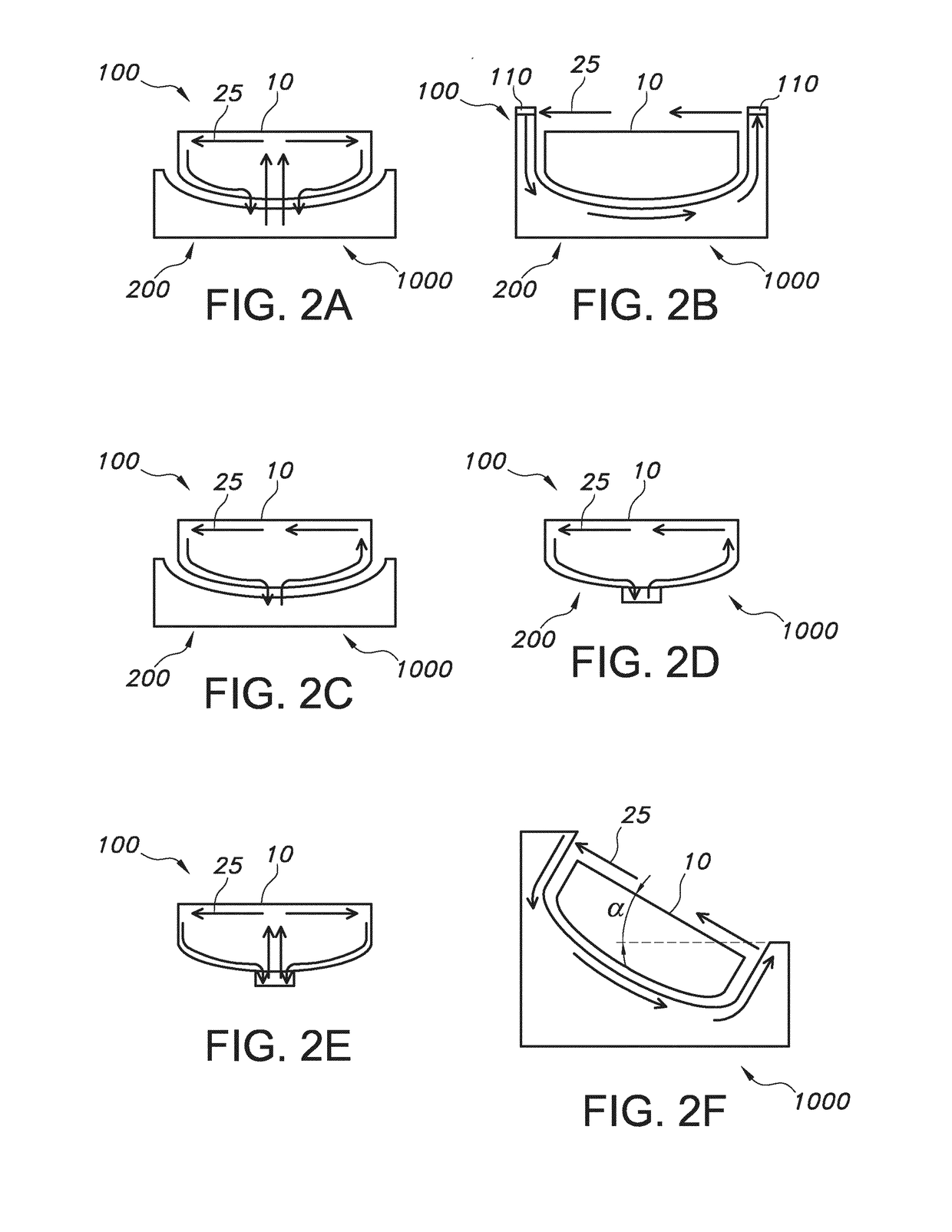
Smokeless air blade wok
InactiveUS20170367514A1Reduce escapeImprove efficiencyFood scienceCooking vessel constructionsEngineeringFood preparation
The invention provides a food preparation vessel (100) comprising a main inlet (10) for introduction of a food material into the food preparation vessel (100), wherein the food preparation vessel (100) comprises a gas flow generator outlet (21) and a gas flow receiver inlet (22), wherein the gas flow generator outlet (21) is configured to provide a gas flow (25) in the direction of the gas flow receiver inlet (22) and having a component parallel to the main inlet (10) when the gas flow generator outlet (21) is functionally coupled with a gas flow generator in operation.
Owner:KONINKLJIJKE PHILIPS NV
Safety shutdown system for photovoltaic power generators
ActiveUS9843193B2Allow accessEasily incorporated into new PVBatteries circuit arrangementsPhotovoltaic monitoringPhotovoltaic generatorActuator
A photovoltaic power generator with safety shutdown system includes a plurality of solar panel strings, a combiner, and a plurality of solar safety switches electrically disposed between a plurality of DC outputs of the plurality of solar panels strings and a plurality of DC inputs of the combiner. Each solar safety switch is associated with one of the solar panel strings and includes a solid-state device and a close actuator. The solid-state device of each solar safety switch is connected between the positive and negative terminals of the DC output of its associated solar panel string. The close actuator in each solar safety switch controls whether its associated solid-state device is turned on or is turned off. During normal operating conditions, the close actuators prevent their respective solid-state devices from turning on. However, in the event of a fire, the close actuators cause their associated solid-state devices to turn on, thereby effectively short-circuiting the DC outputs of their associated solar panel strings and preventing the solar panel strings from producing high voltages.
Owner:GETSLA ROBERT
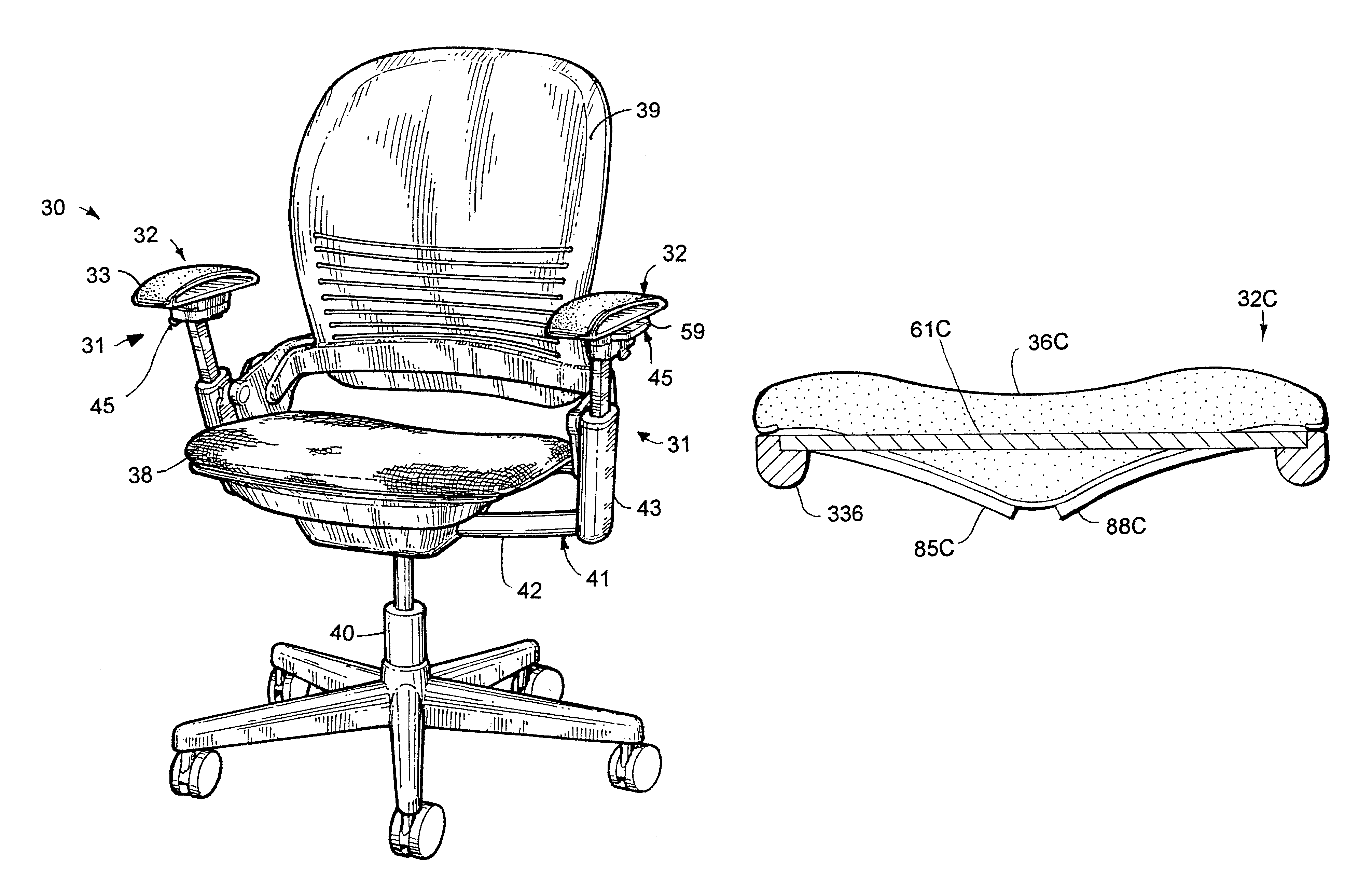
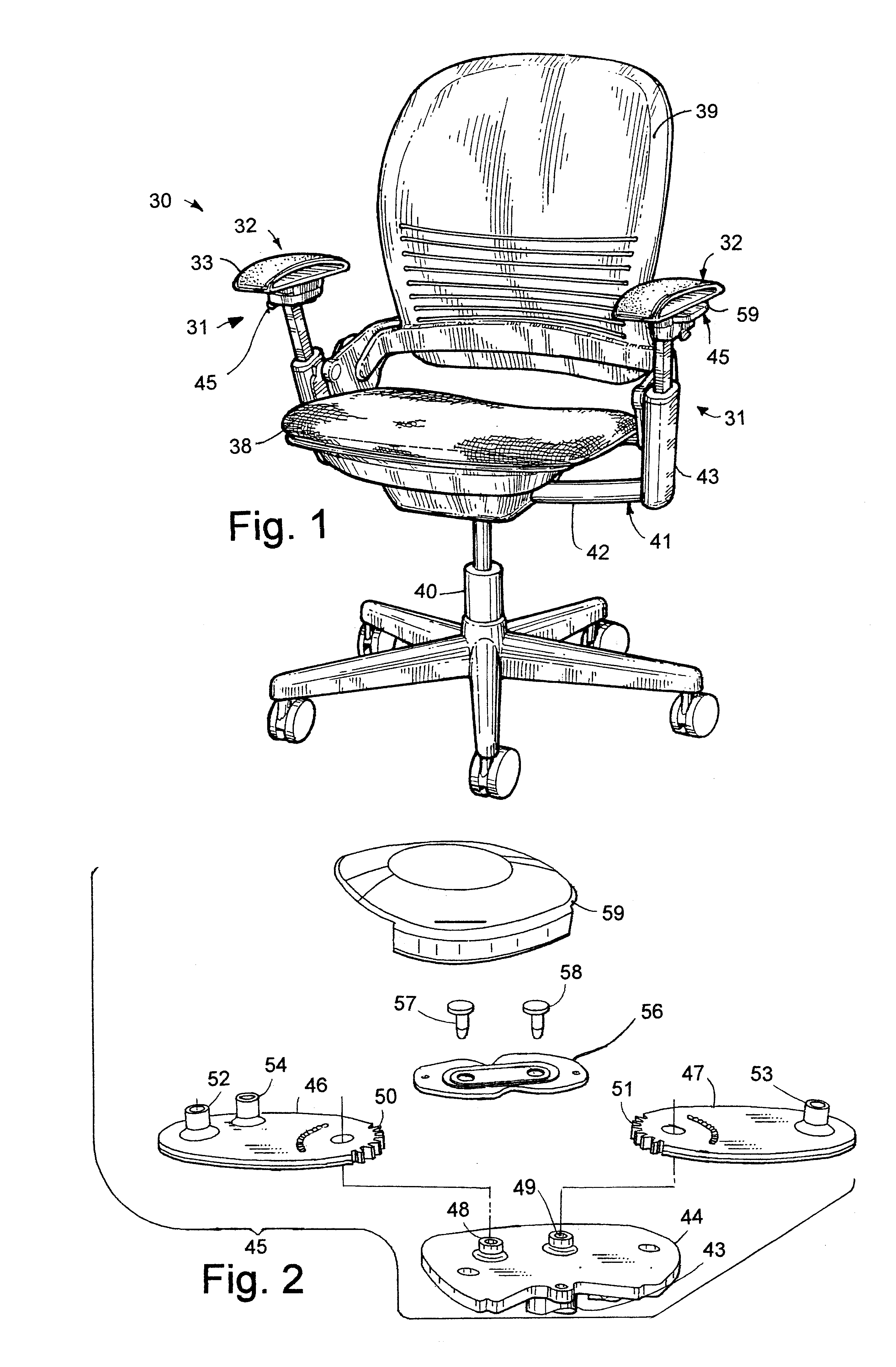
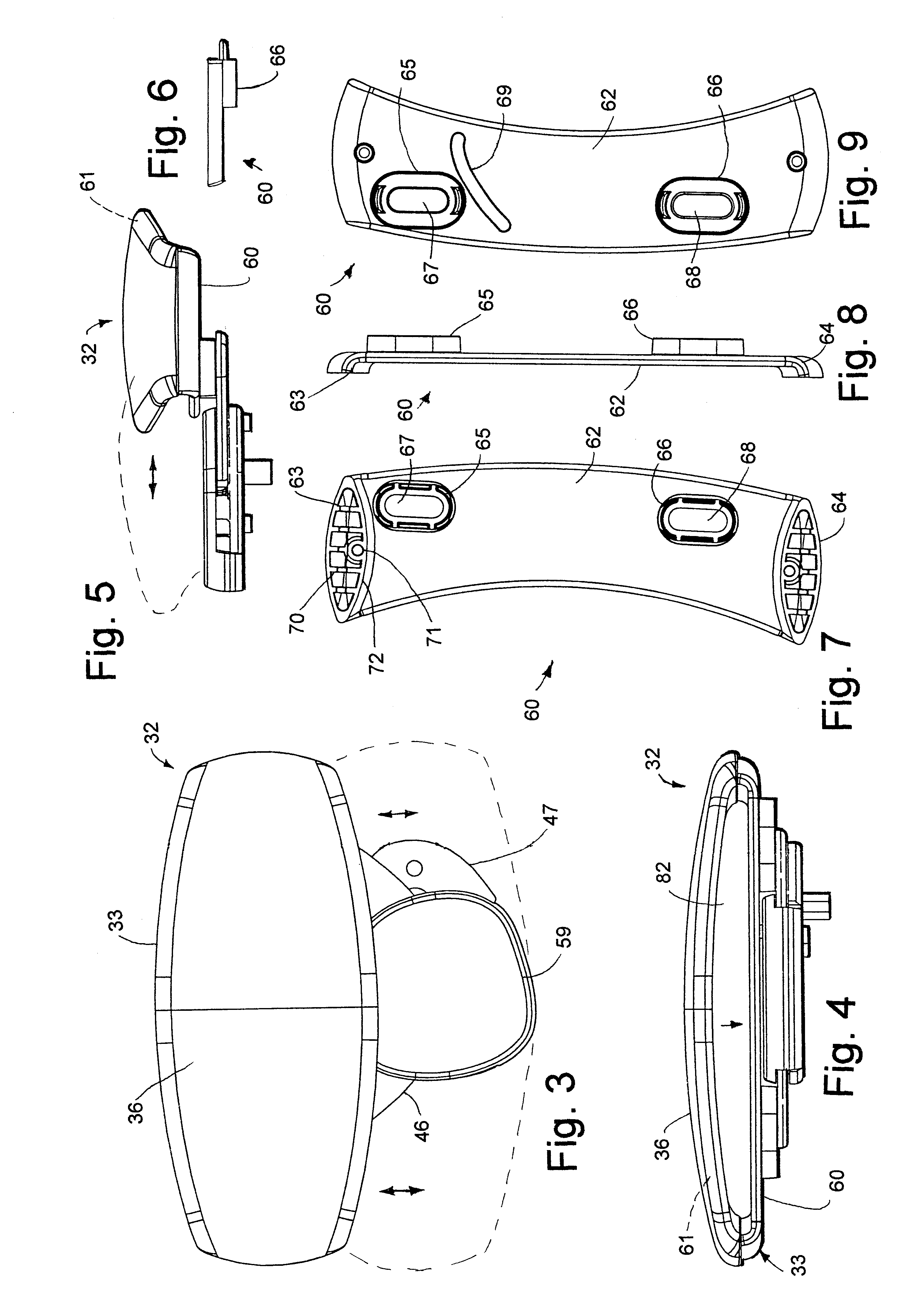
Flexible armrest construction
InactiveUS6343839B1Grasp comfortEvenly distribute stressVehicle seatsFluid mattressesEngineeringHandrail
A component has a support with a stiff section and a flexible section. An incompressible resilient material, such as a gel, is supported on the flexible section. In one form, the component forms an armrest, with the support including upper and lower sections forming a loop. The upper section bridges between ends of the lower section and includes the flexible section, and a section of gel material is positioned on or molded onto the flexible section. In the armrest, the incompressible resilient material is sufficiently thick and resilient to comfortably support a person's forearm on the support yet further is sufficiently flowable and stretchable to at least partially move off a rib on the support and into the non-supporting areas when pressure is applied to the incompressible resilient material.
Owner:STEELCASE DEV INC
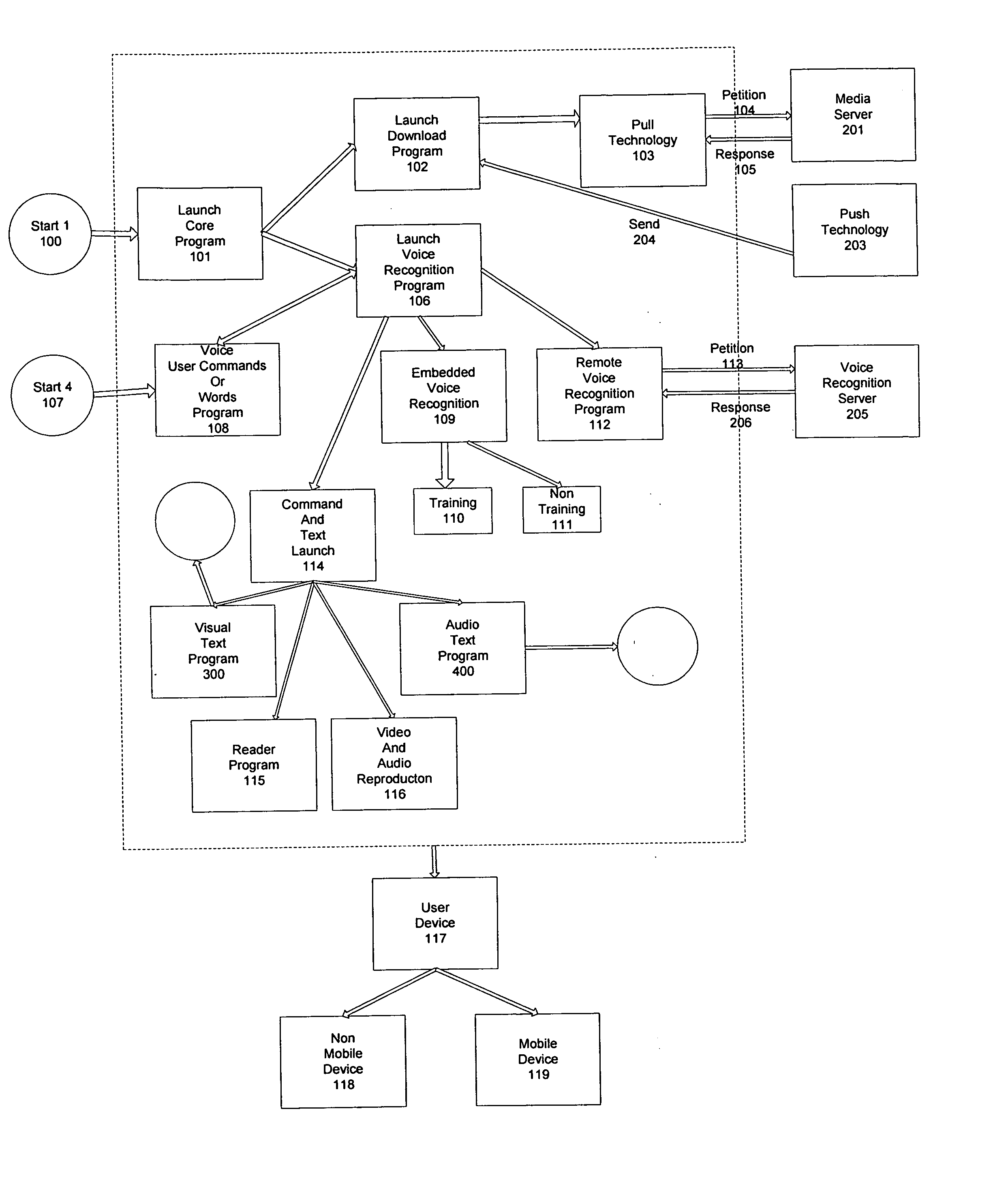
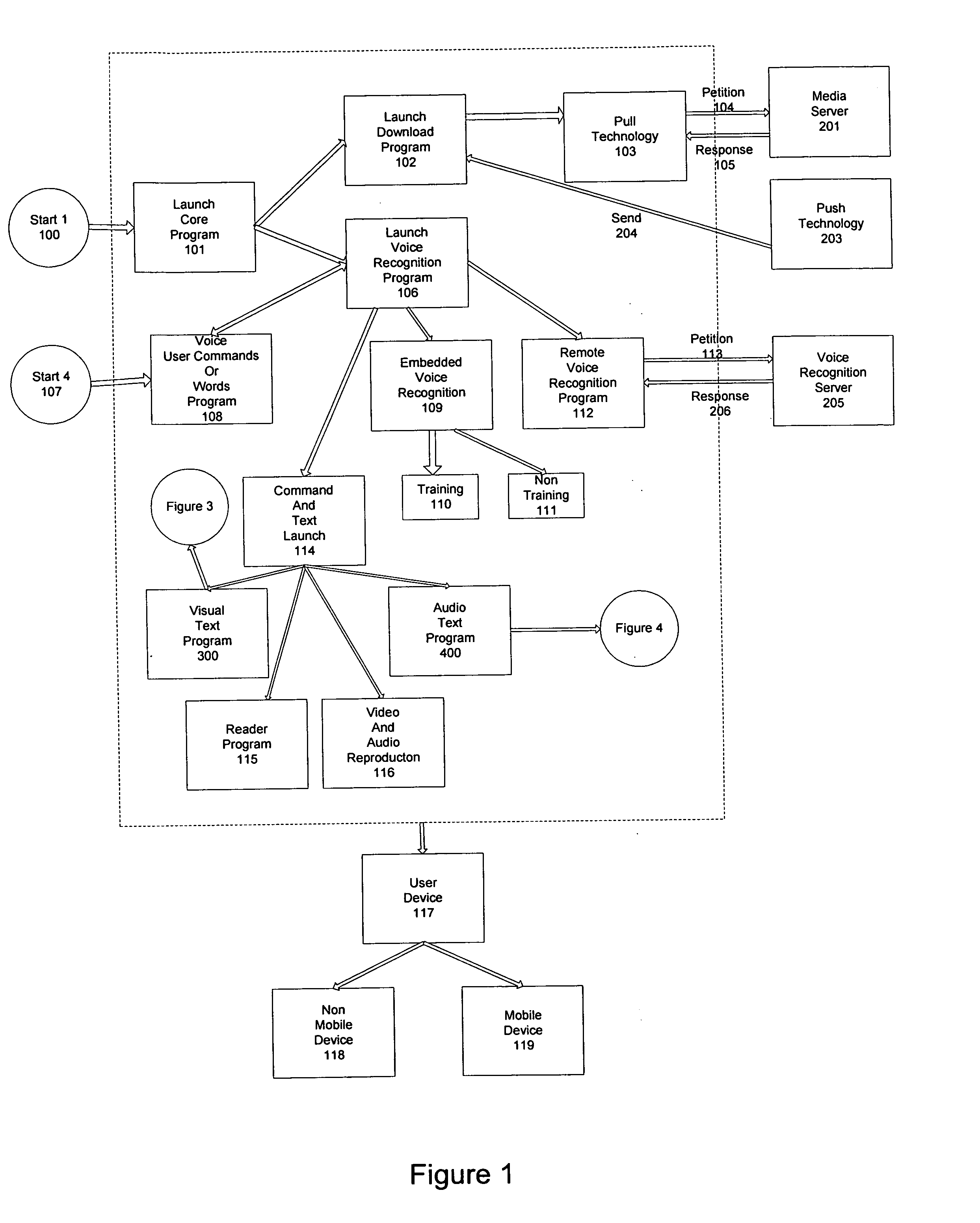
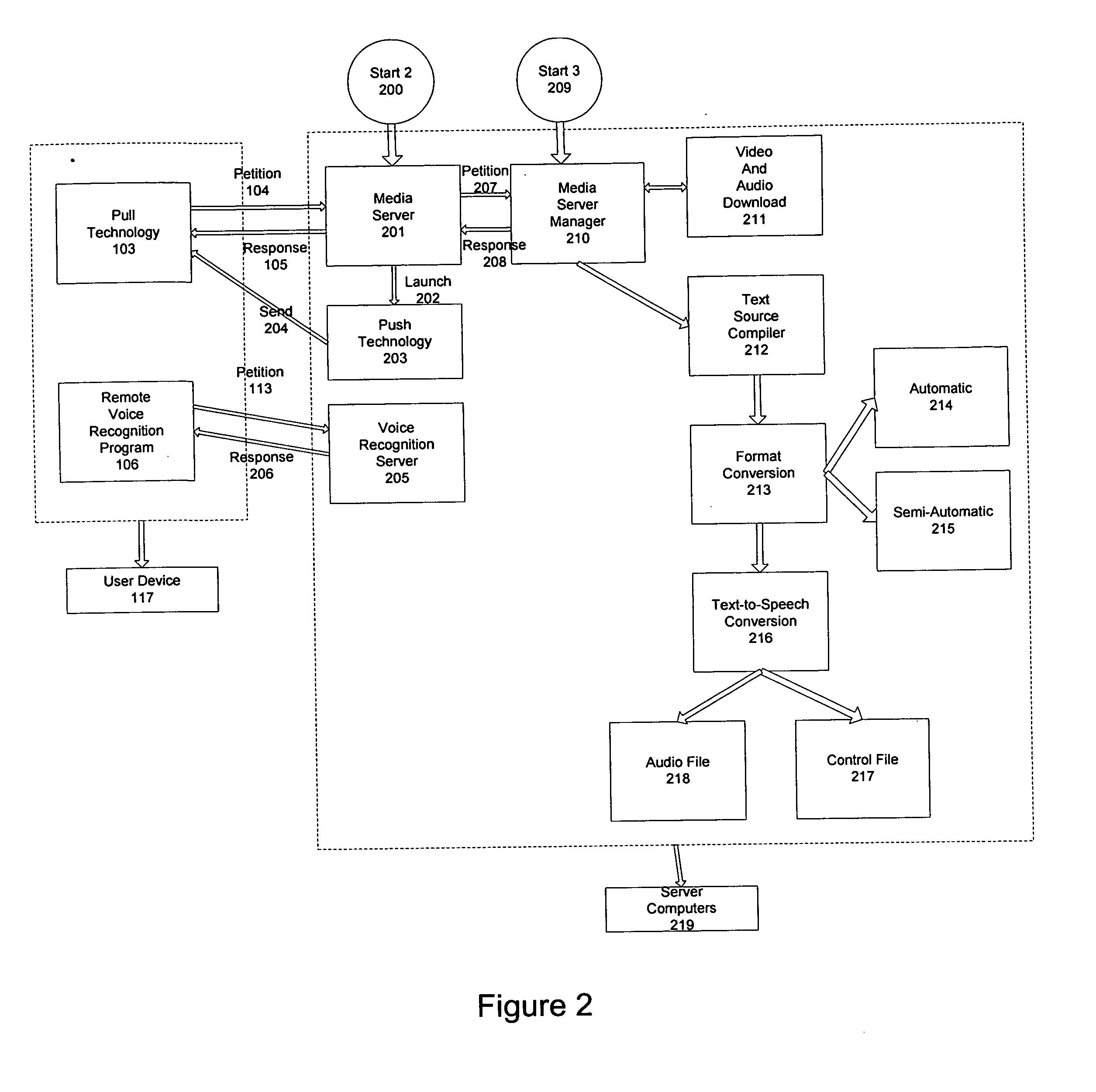
Method of accessing cultural resources or digital contents, such as text, video, audio and web pages by voice recognition with any type of programmable device without the use of the hands or any physical apparatus.
The use of voice as a means of communication with a computer or programmable device (117), as well as, converting text to speech, allows visually or physically disabled people access to texts in any format such as, but not limited to, newspapers, books, Blogs, or web pages accessible through the Internet or other means of communication with their device (117) or computer. Likewise, users are enabled to access other cultural content such as movies, documentaries, music, etc. The invention also allows non-disabled people access to the same, in conditions that prevent them from using their hands, such as driving, or being outside their normal place to live or work.
Owner:MEIVOX
Hypervisor-enforced isolation of entities within a single logical partition's virtual address space
ActiveUS8010763B2Easy to operateAllow accessMemory architecture accessing/allocationSoftware simulation/interpretation/emulationData processing systemVirtual address space
Access control to shared virtual address space within a single logical partition is provided. The access control includes: associating, by a hypervisor of the data processing system, a memory protection key with a portion of a single logical partition's virtual address space being shared by multiple entities, the key preventing access by one of the multiple entities to that portion of the virtual address space, and allowing access by another of the entities to that portion of the virtual address space; and locking by the hypervisor the memory protection key from modification by the one entity, wherein the locking prevents the one entity from modifying the key and thereby gaining access to the portion of the single logical partition's virtual address space with the associated memory protection key. In one embodiment, the one entity is the single logical partition itself, and the another entity is a partition adjunct.
Owner:INT BUSINESS MASCH CORP
RFID tag
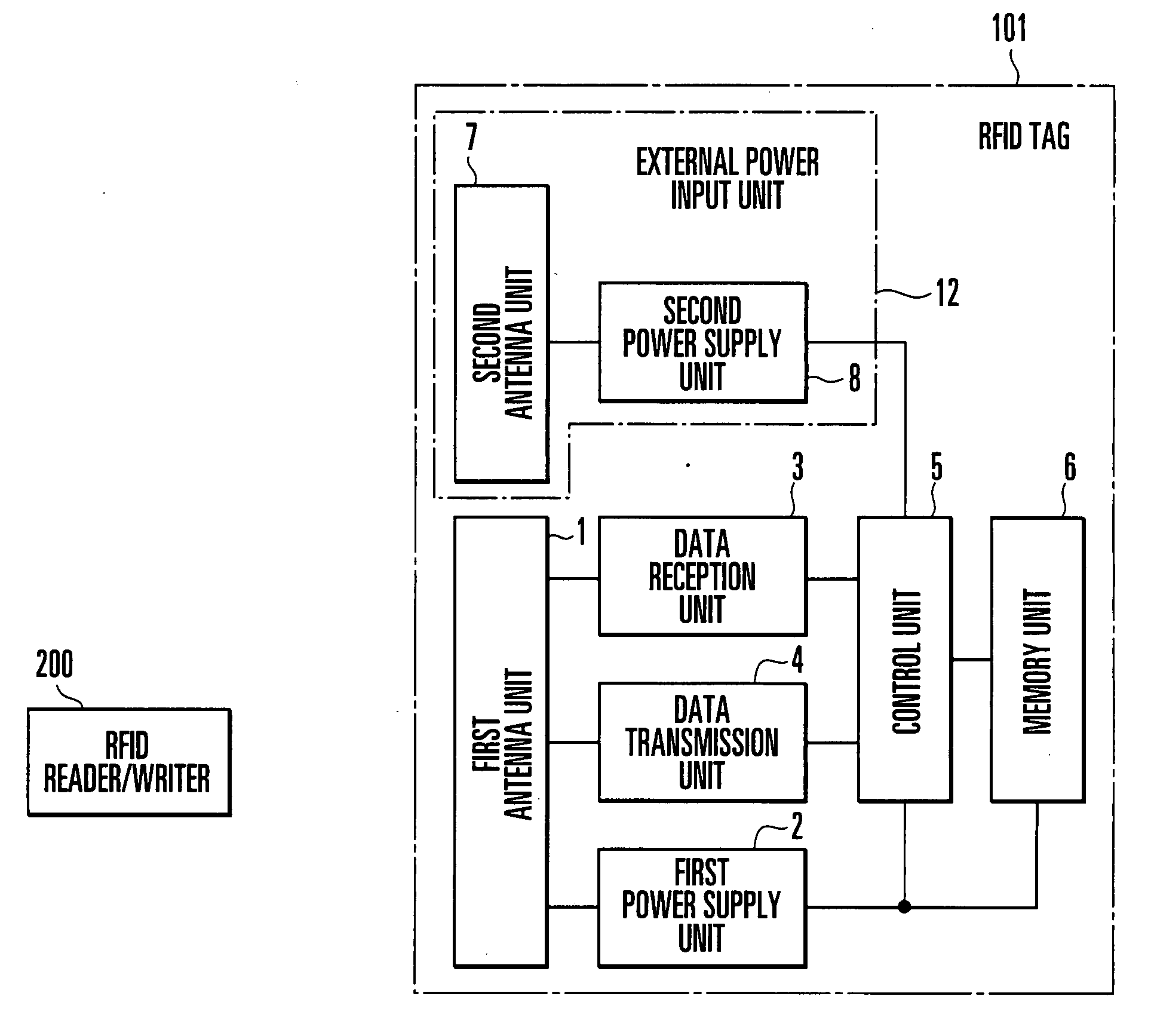
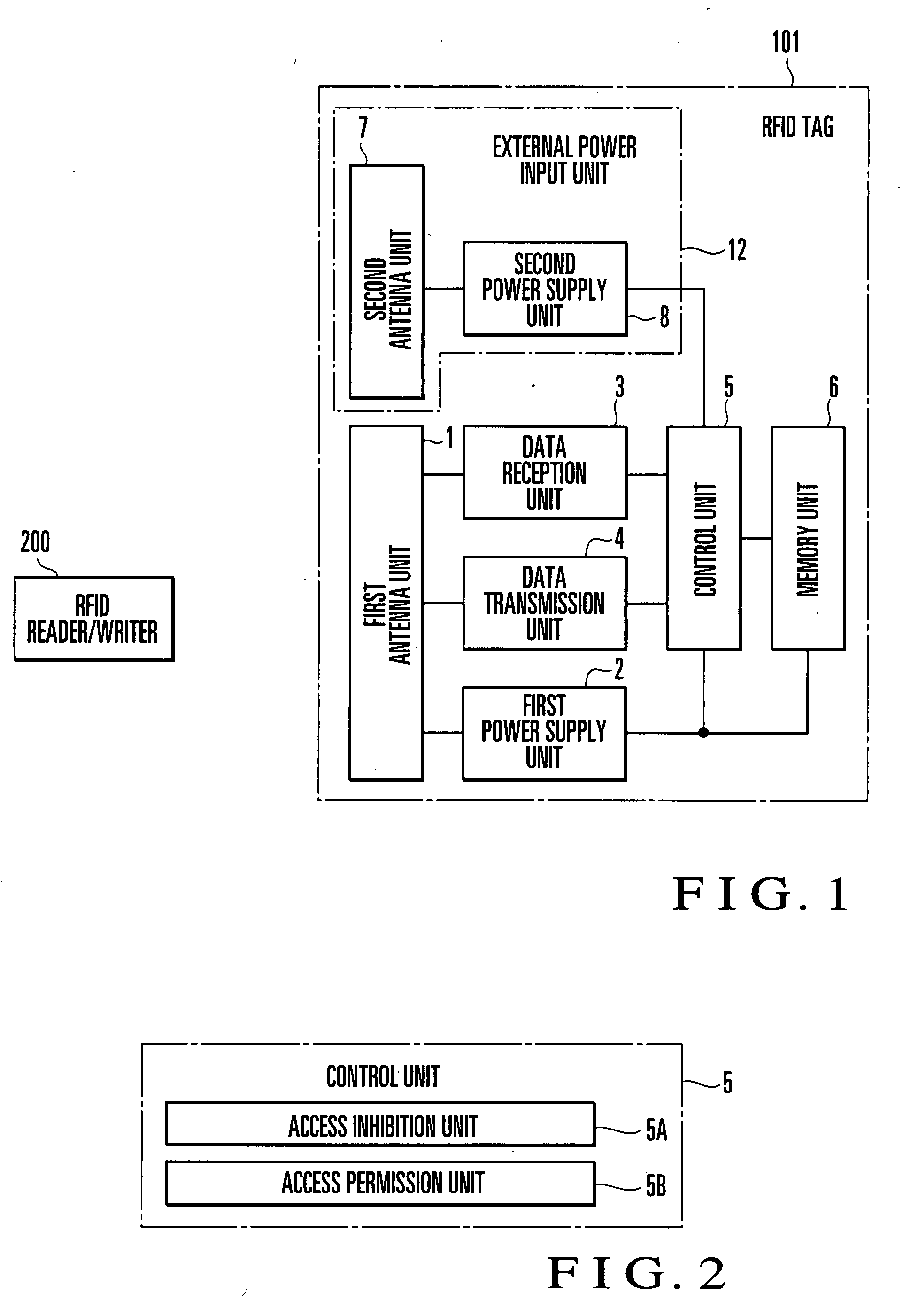
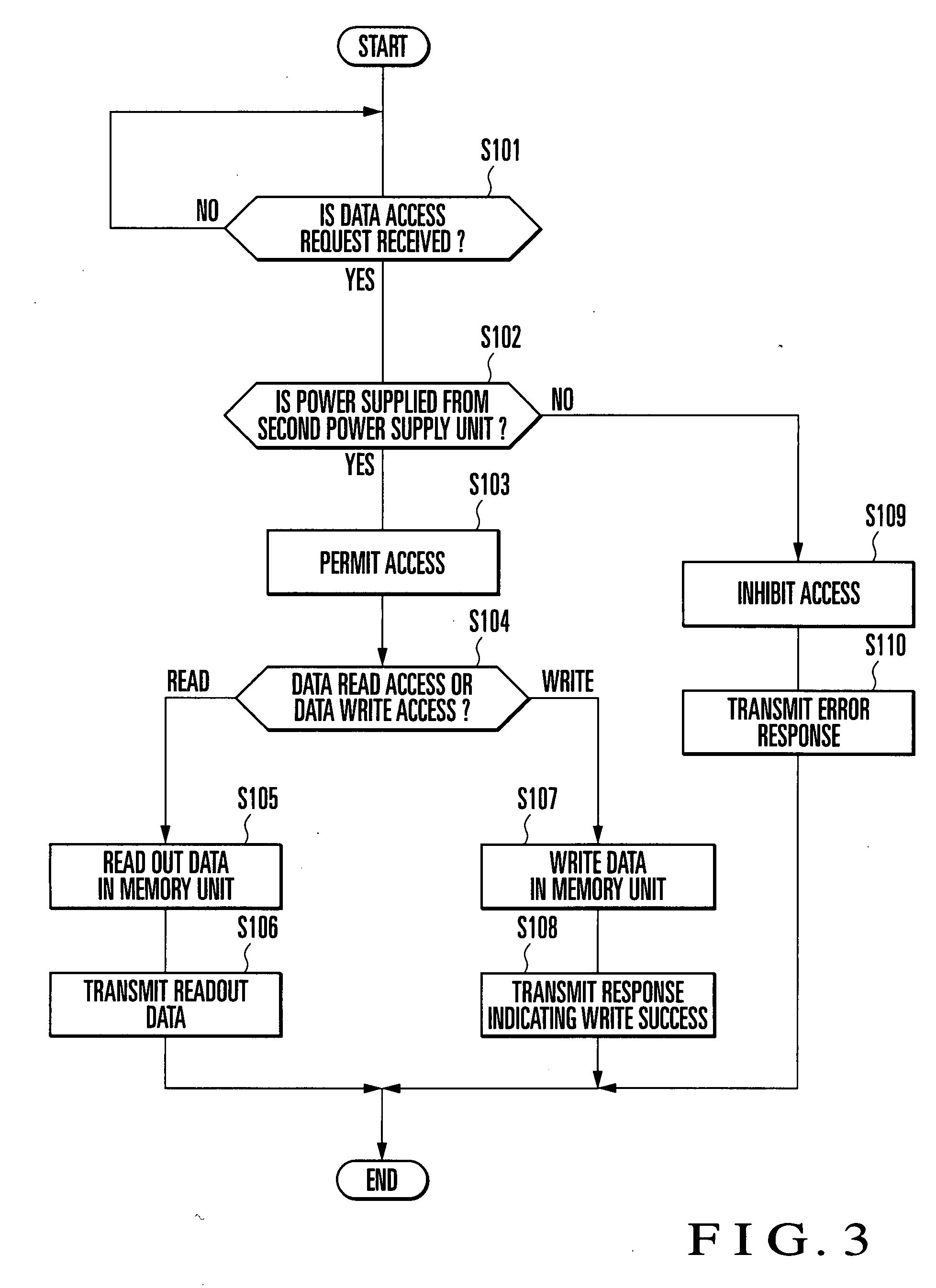
InactiveUS20070222610A1Prevent unauthorized accessFacilitate performance improvementsRecord carriers used with machinesBurglar alarm by hand-portable articles removalRadio waveTelecommunications equipment
An RFID tag includes an external power input unit, first antenna unit, first power supply unit, memory unit, and control unit. The external power input unit inputs external power. The first antenna unit receives power from a communication device. The first power supply unit extracts power from the radio wave received by the first antenna unit. The control unit operates upon receiving power from the first power supply unit and controls permission and inhibition of access from the communication device to the memory unit in accordance with presence / absence of input of power from the external power input unit.
Owner:NEC CORP
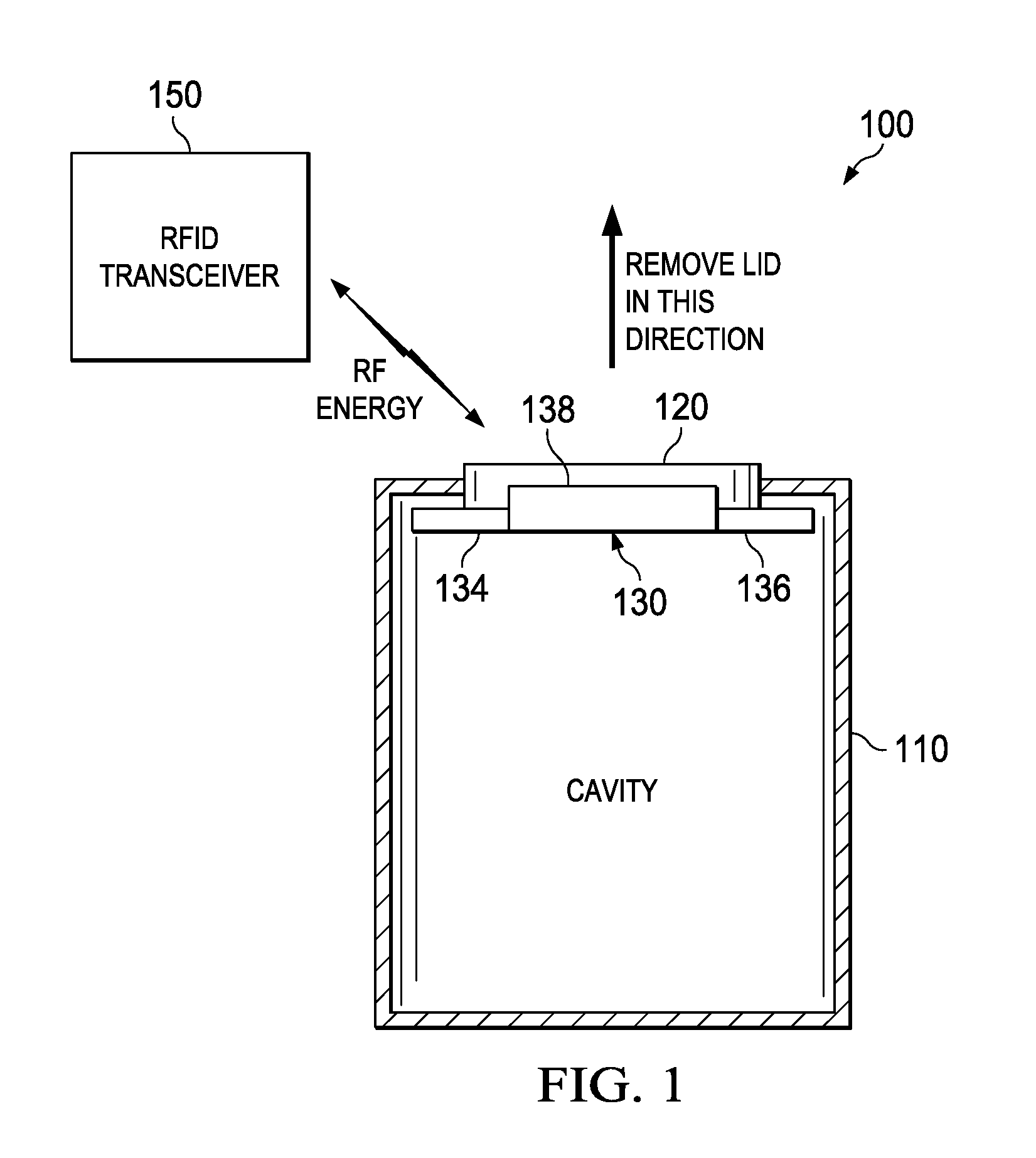
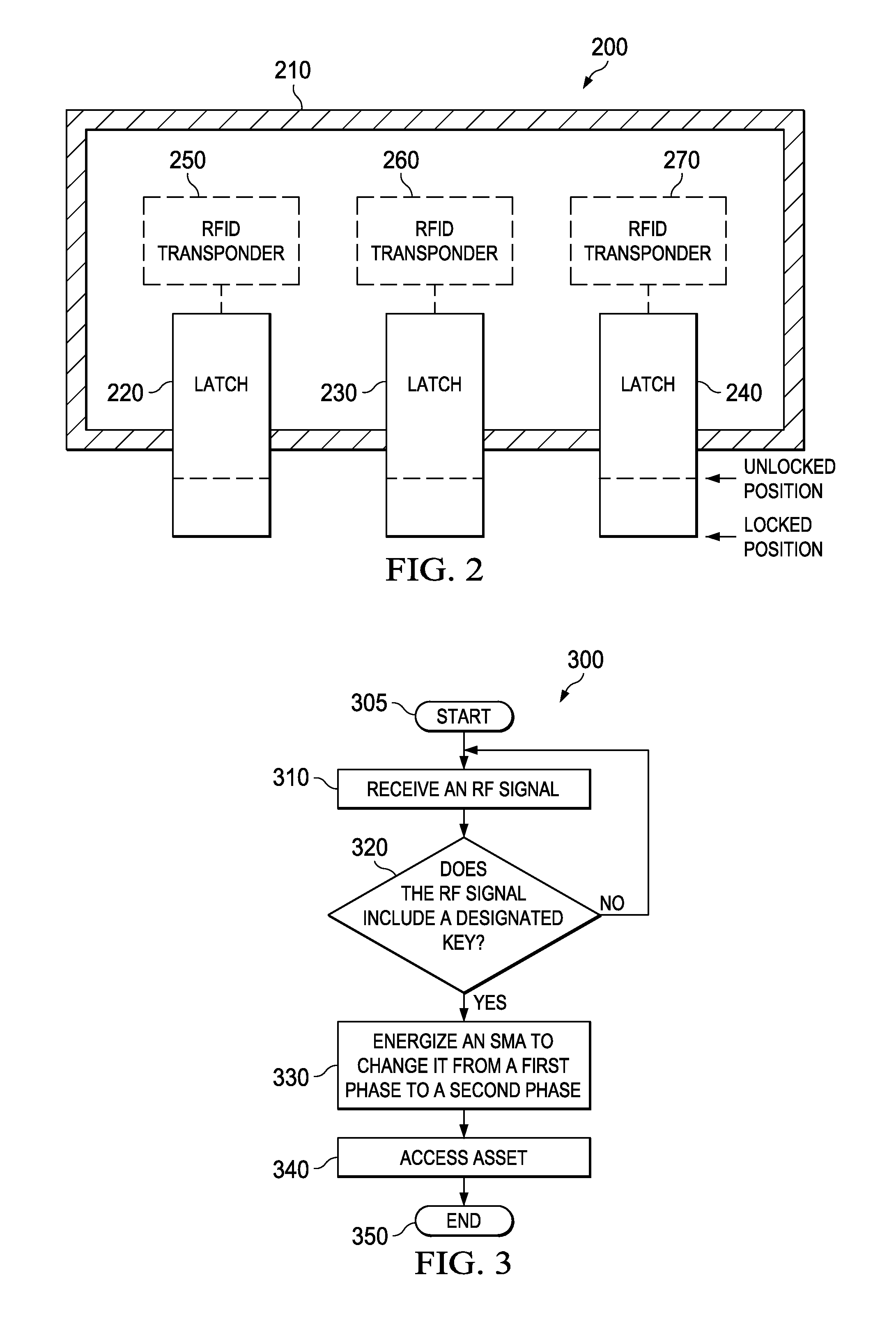
Cryptographic lock, method of operation thereof and secure container employing the same
ActiveUS20090322531A1Avoid accessAllow accessNon-mechanical controlsIndividual entry/exit registersTransceiverShape-memory alloy
Various cryptographic locks for securing assets, secure containers and methods of operating a cryptographic lock. One embodiment of a cryptographic lock includes: (1) a shape memory alloy (SMA) having a first and second phase, wherein the first phase inhibits access to an asset and the second phase allows access to the asset and (2) an RFID transponder, coupled to the SMA, configured to receive an authentication signal from an RFID transceiver and, based thereon, energize the SMA to temporarily change the SMA from the first phase to the second phase.
Owner:TEXAS INSTR INC
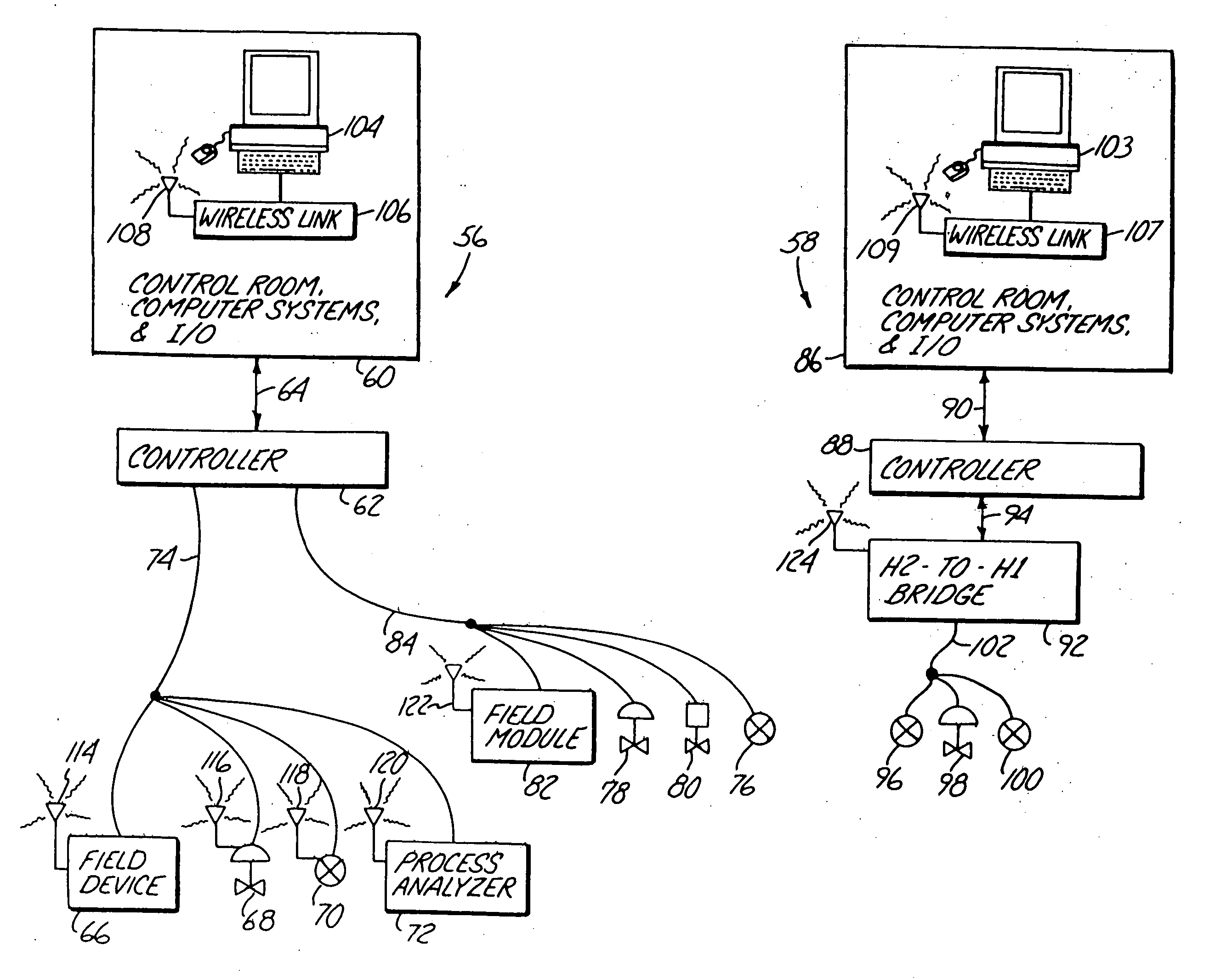
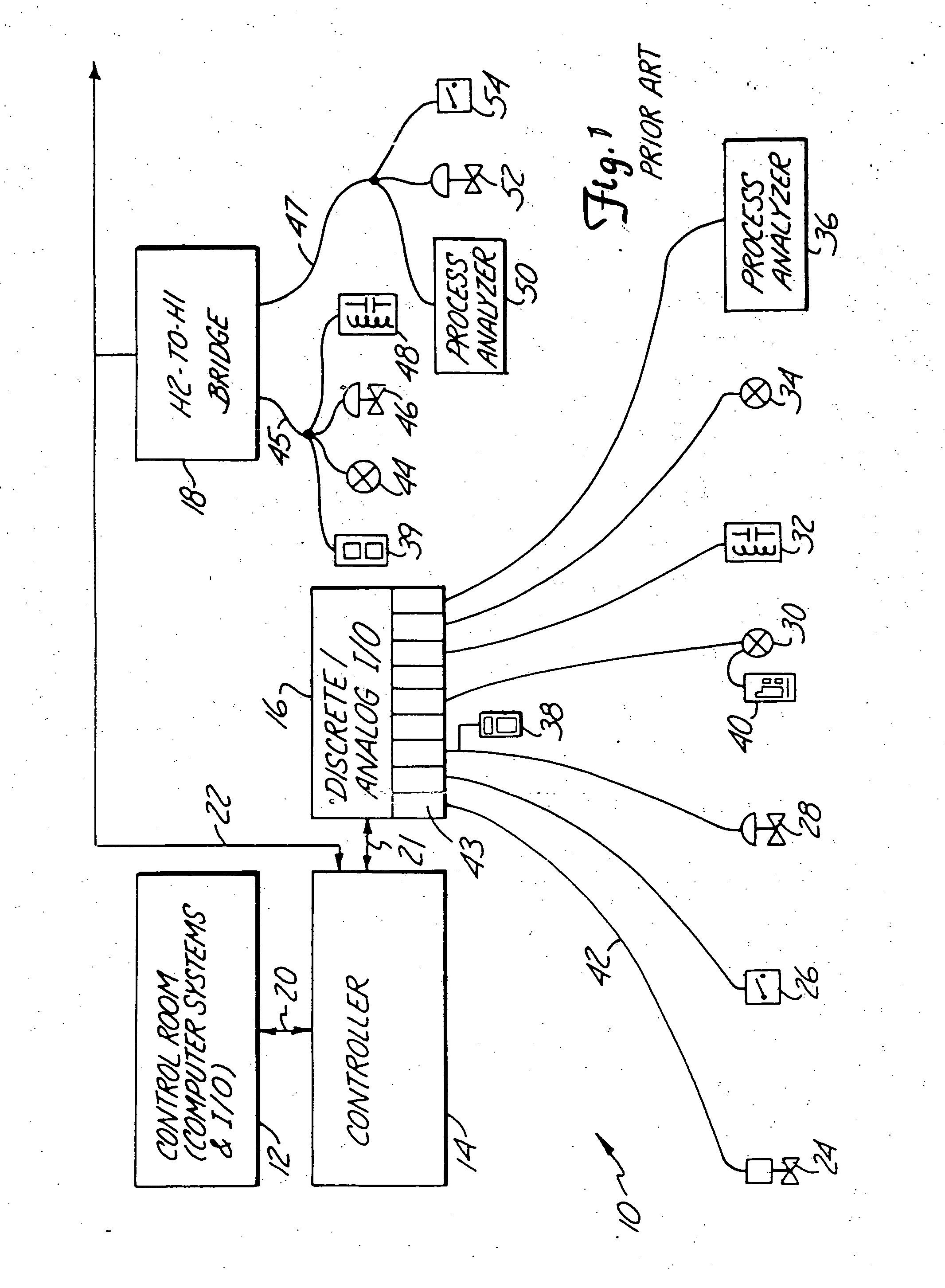
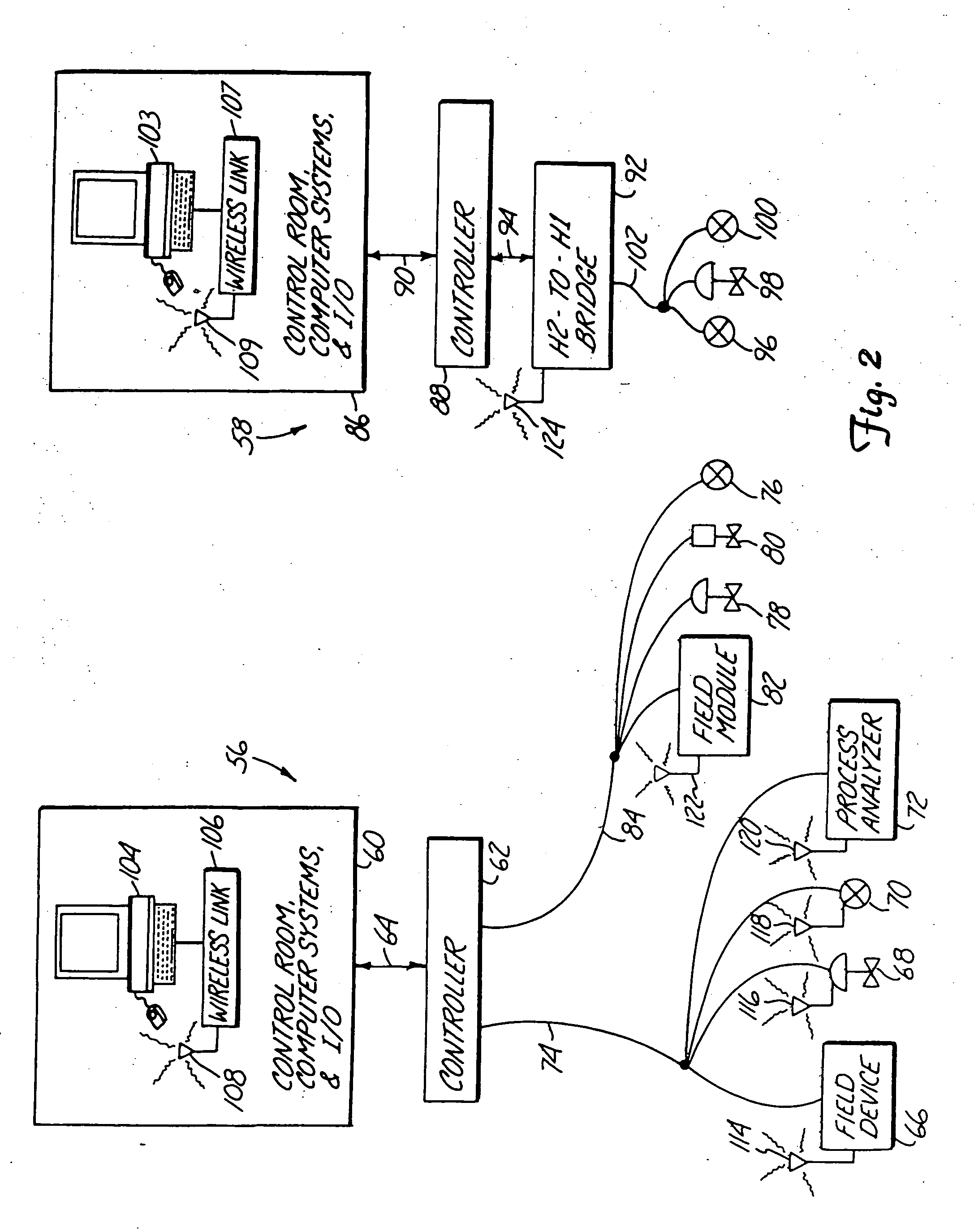
Wireless communications within a process control system using a bus protocol
InactiveUS20050049727A1Allow accessError preventionFrequency-division multiplex detailsEmbedded systemMultiple device
An apparatus provides wireless communication between multiple devices within a process control system, such as between field devices, control units, user terminals, controllers, etc., using a wireless bus protocol. In one embodiment, a process control system for use within a process control environment includes a plurality of process control field devices that operate within the process environment, and a control device adapted to receive a sense signal from or to provide a control signal to one or more of the plurality of process control field devices. First and second wireless transceivers are communicatively connected to different ones of the process control field devices and the control device and communicate with one another using a bus protocol, to thereby provide wireless communications within the process control system.
Owner:FISHER-ROSEMOUNT SYST INC
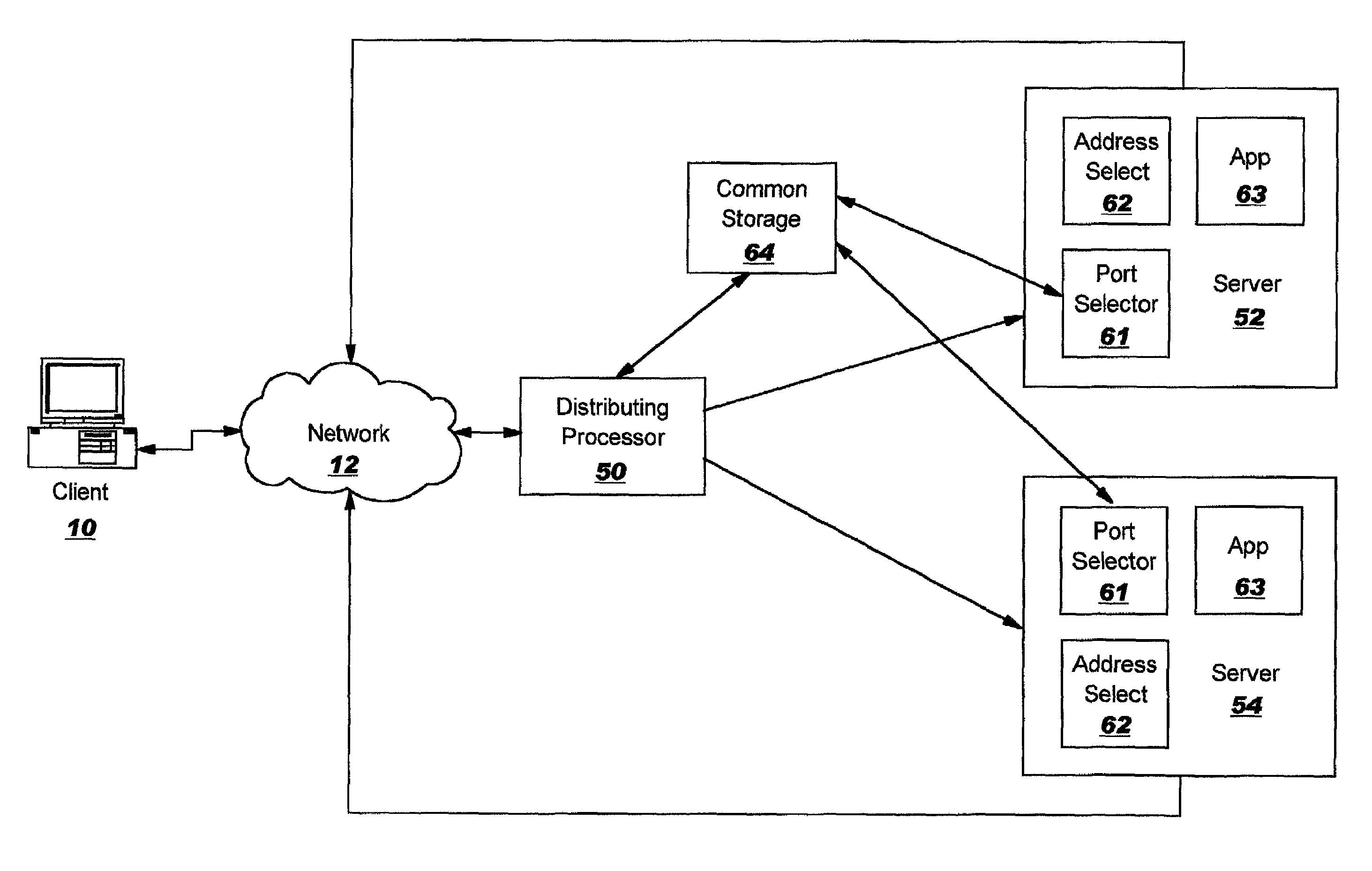
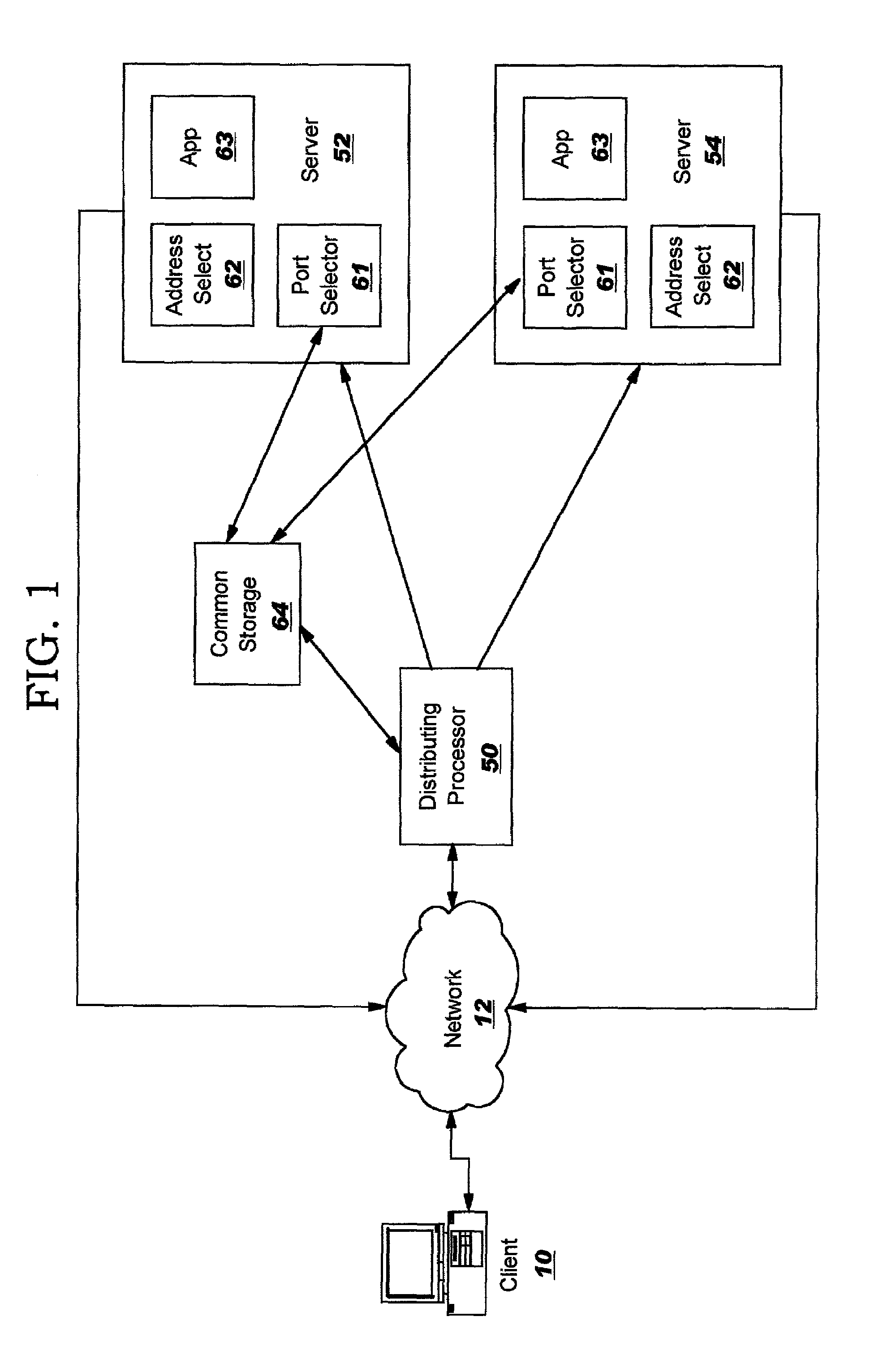
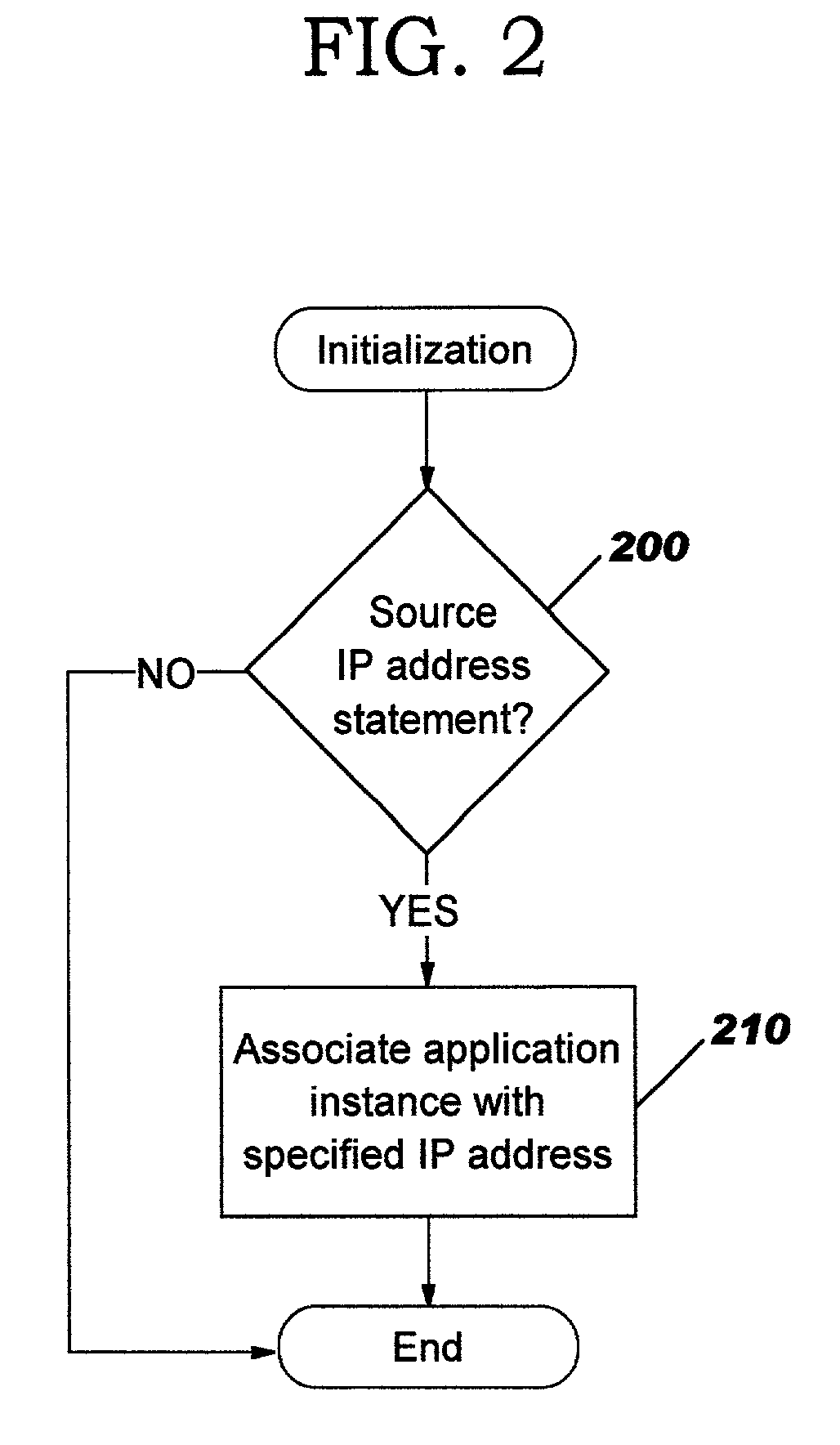
Methods, systems and computer program products for port assignments of multiple application instances using the same source IP address
InactiveUS7120697B2Avoid accessAllow accessMultiple digital computer combinationsElectric digital data processingData processing systemIp address
Methods, systems and computer program products provide assignment of ports for connections originated by multiple application instances executing on different data processing systems utilizing a common network address. An indication of available ports for the common network address is provided to each of the different data processing systems executing the multiple application instances. A port identified as available is selected as a port for a connection utilizing the common network address.
Owner:A10 NETWORKS
Tamper resistant ground fault circuit interrupter receptacle having dual function shutters
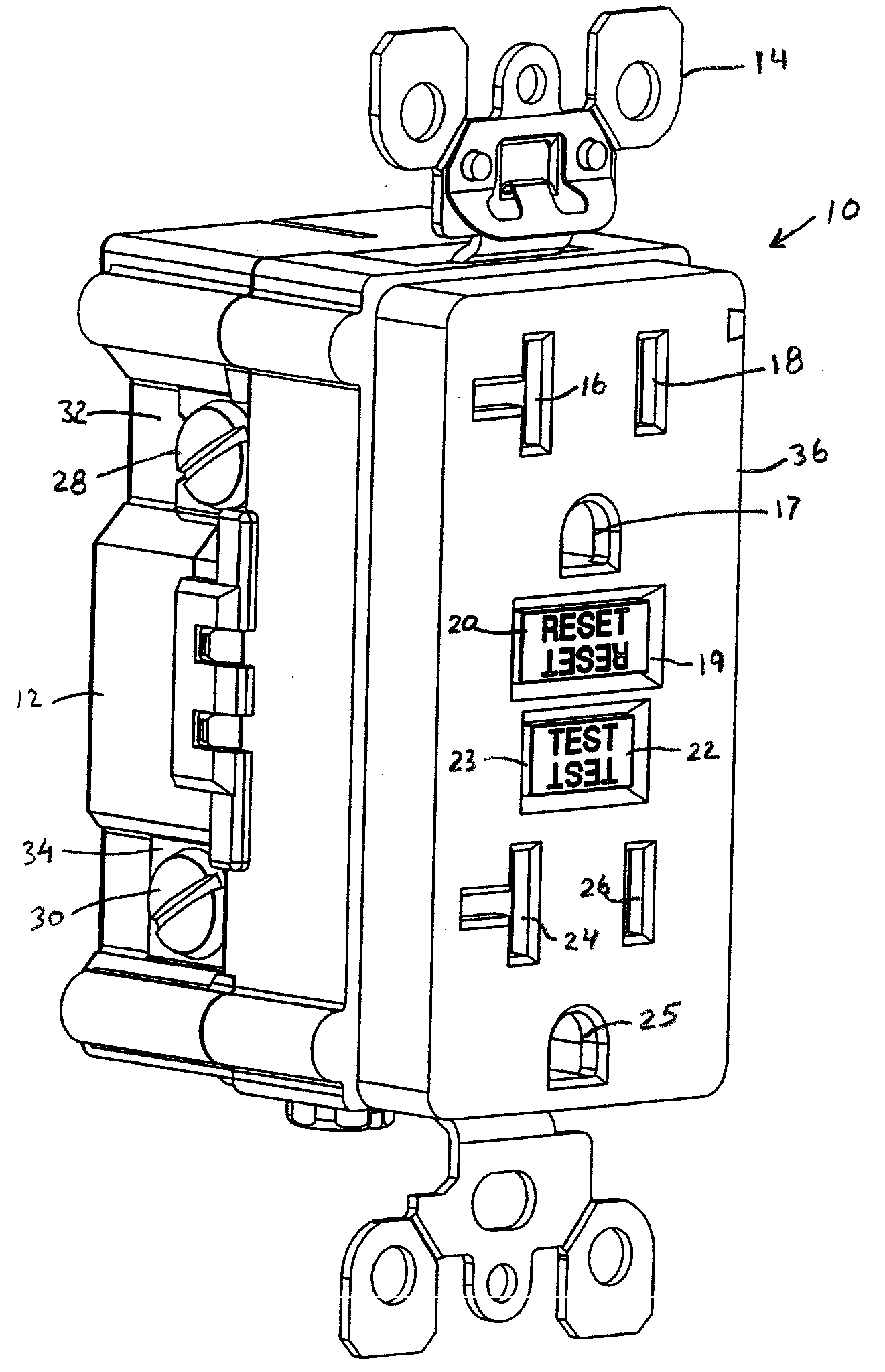
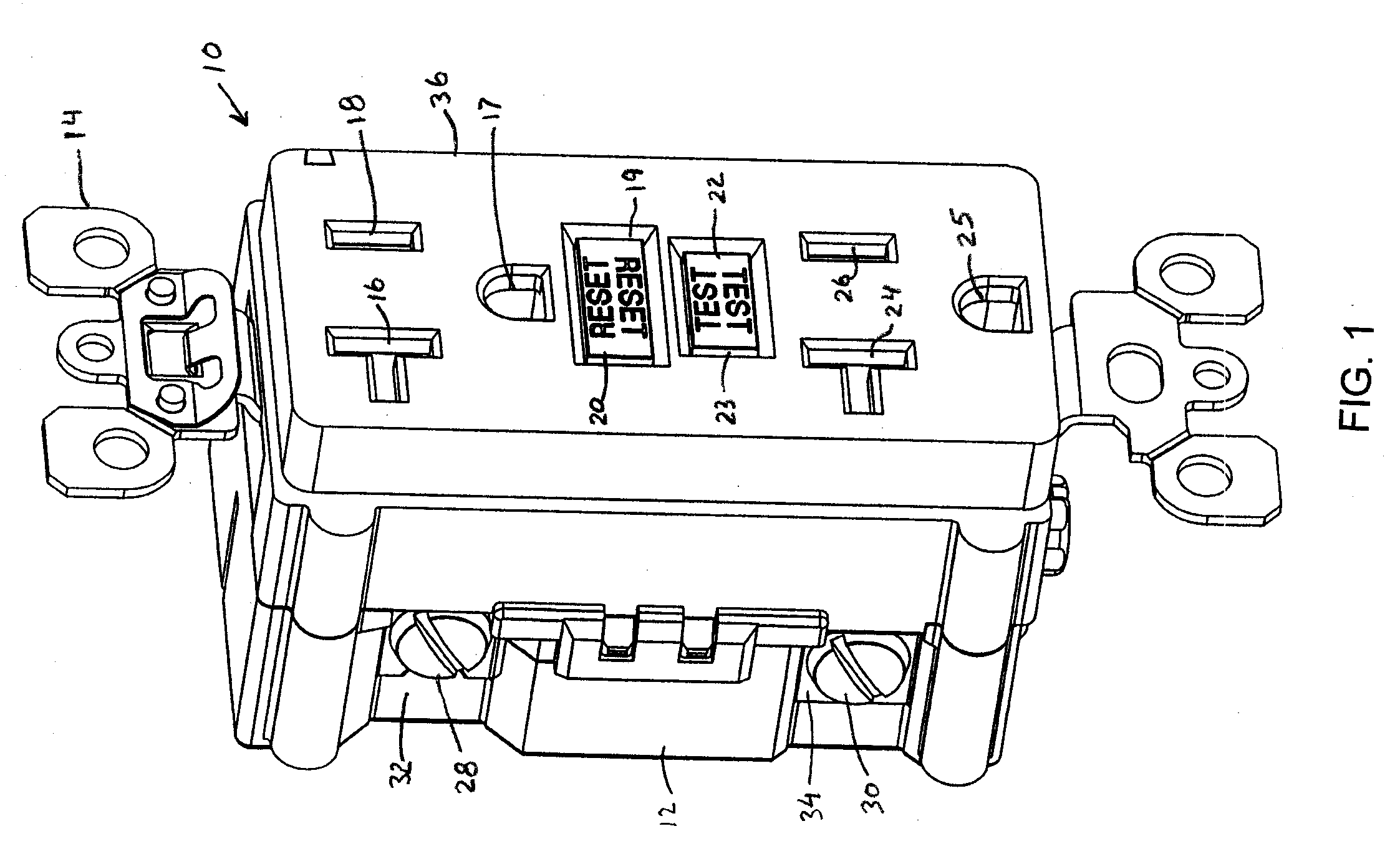
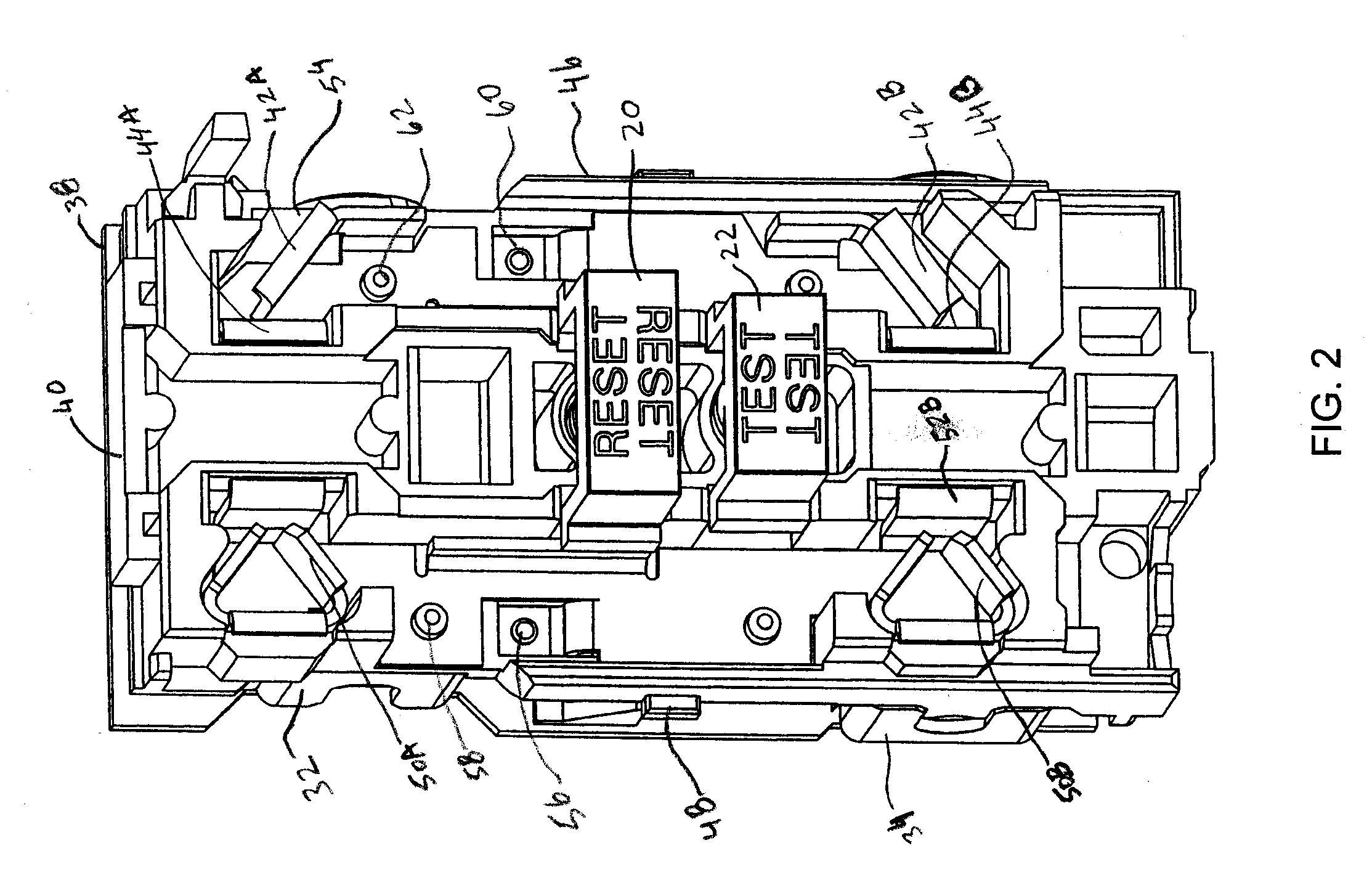
InactiveUS20070211397A1Avoid accessAllow accessCircuit-breaking switches for excess currentsTwo pole connectionsDual functionCircuit breaker
An electrical receptacle having a tamper resistant mechanism is disclosed. In addition, a GFCI can optionally be configured to include the tamper resistant mechanism. Furthermore, the GFCI can be configured so that the GFCI engages the tamper resistant mechanism when the GFCI is tripped or reset. When the GFCI is tripped, the tamper resistant mechanism is engaged such that it prevents user access to the face terminals of the electrical receptacle. When the GFCI is reset the tamper resistant mechanism does not restrict access to the face terminals of the electrical receptacle. The tamper resistant mechanism has one or more shutter positioned with respect to one or more entry ports to the face terminals. The shutter positioning restricts the insertion of prongs of an electrical plug when the GFCI device of the electrical receptacle is tripped. The GFCI device is tripped when it detects a fault. The GFCI device of the electrical receptacle may be shipped in the tripped condition and cannot be reset if the GFCI device is reverse wired. Thus, the tamper resistant mechanism prevents access to a reverse wired GFCI.
Owner:LEVITON MFG
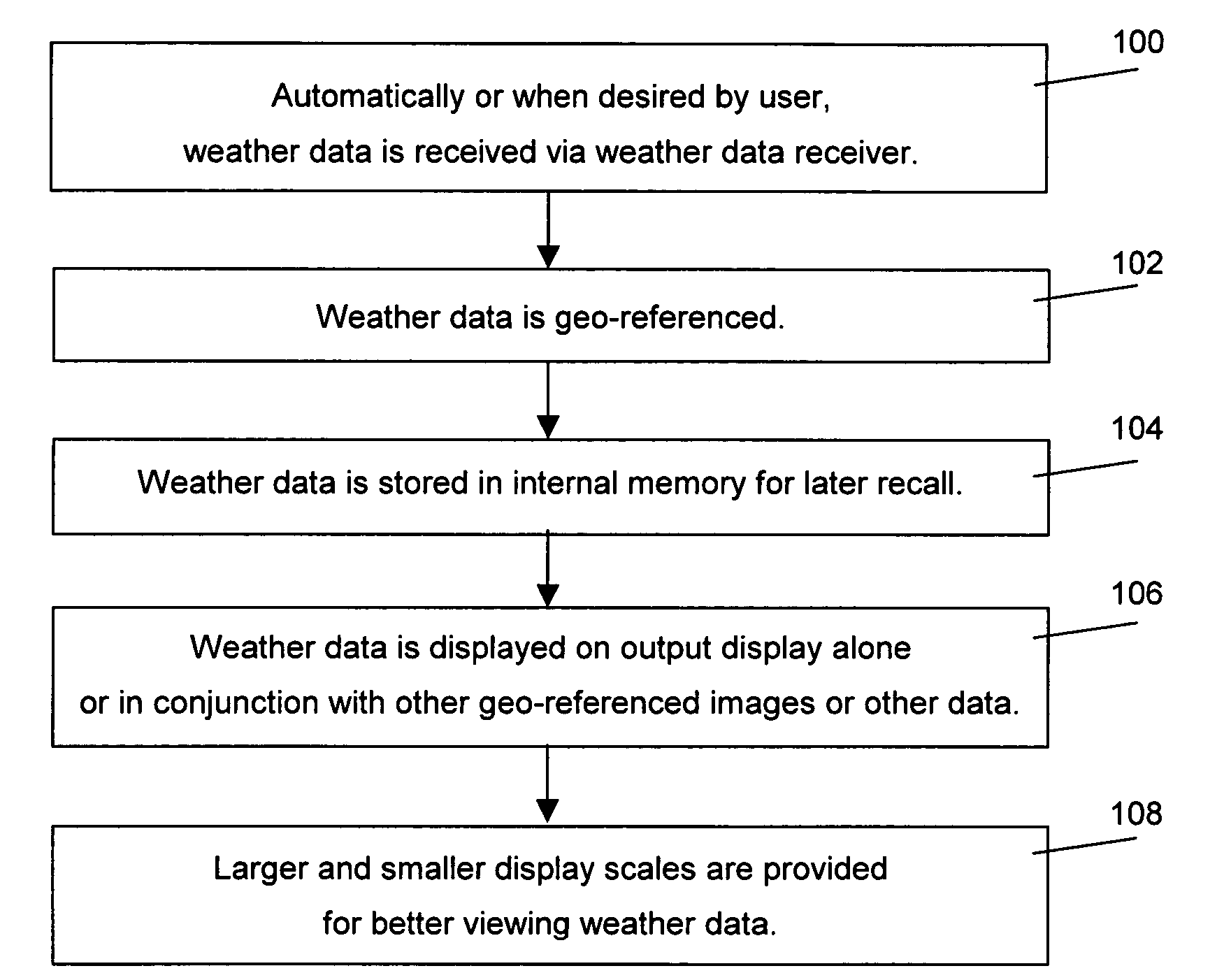
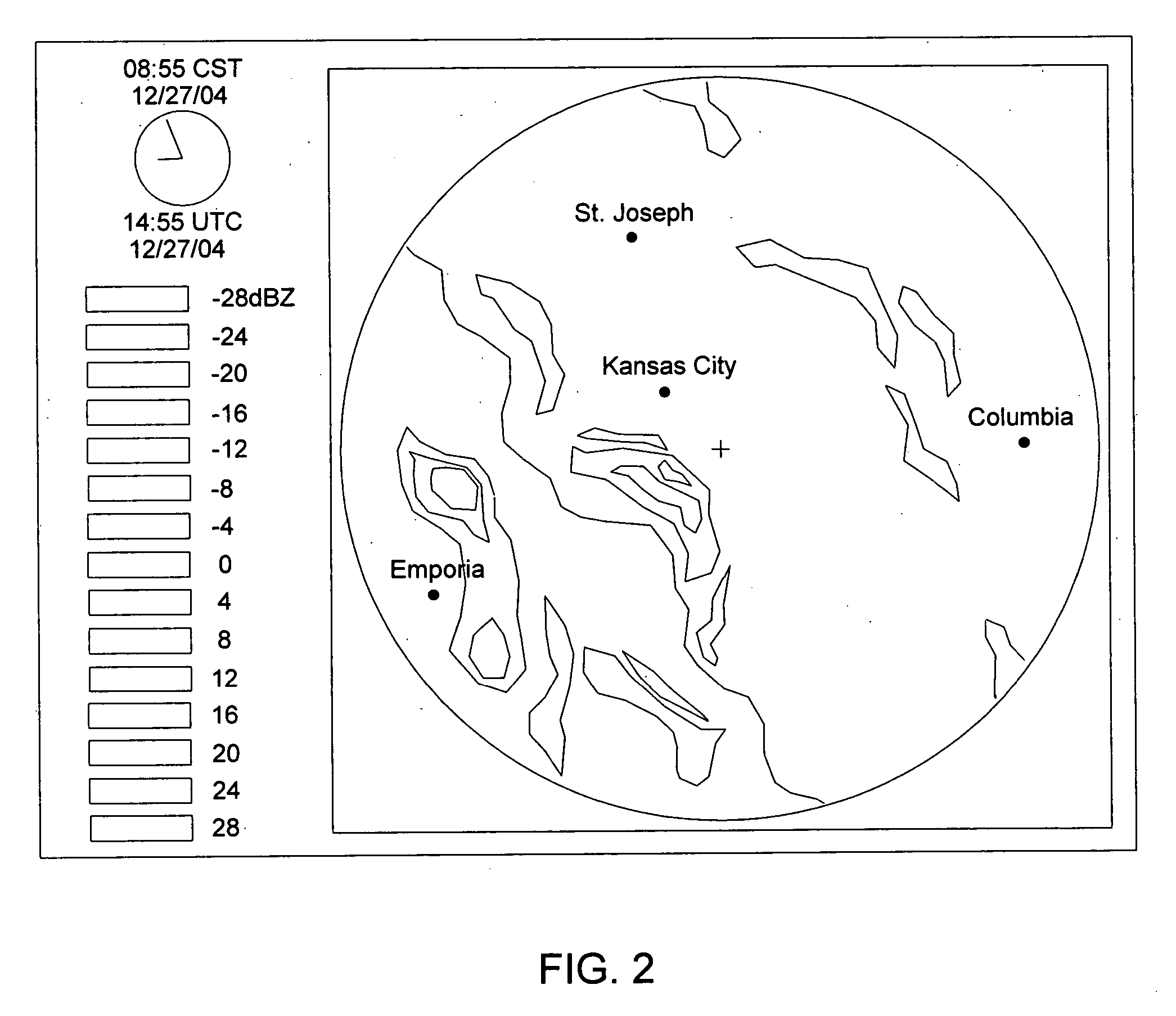
GPS device and method for displaying weather data
InactiveUS20060229810A1Accurately overlayedHigh resolutionNavigational calculation instrumentsWeather condition predictionHand heldAtmospheric sciences
A GPS device and method for associating current and forecasted geo-referenced weather data with location data in a hand-held ruggedized GPS device having an integrated weather data receiver, wherein the weather data can be displayed alone, particularly on larger scales, or in conjunction with the location data.
Owner:BUSHNELL
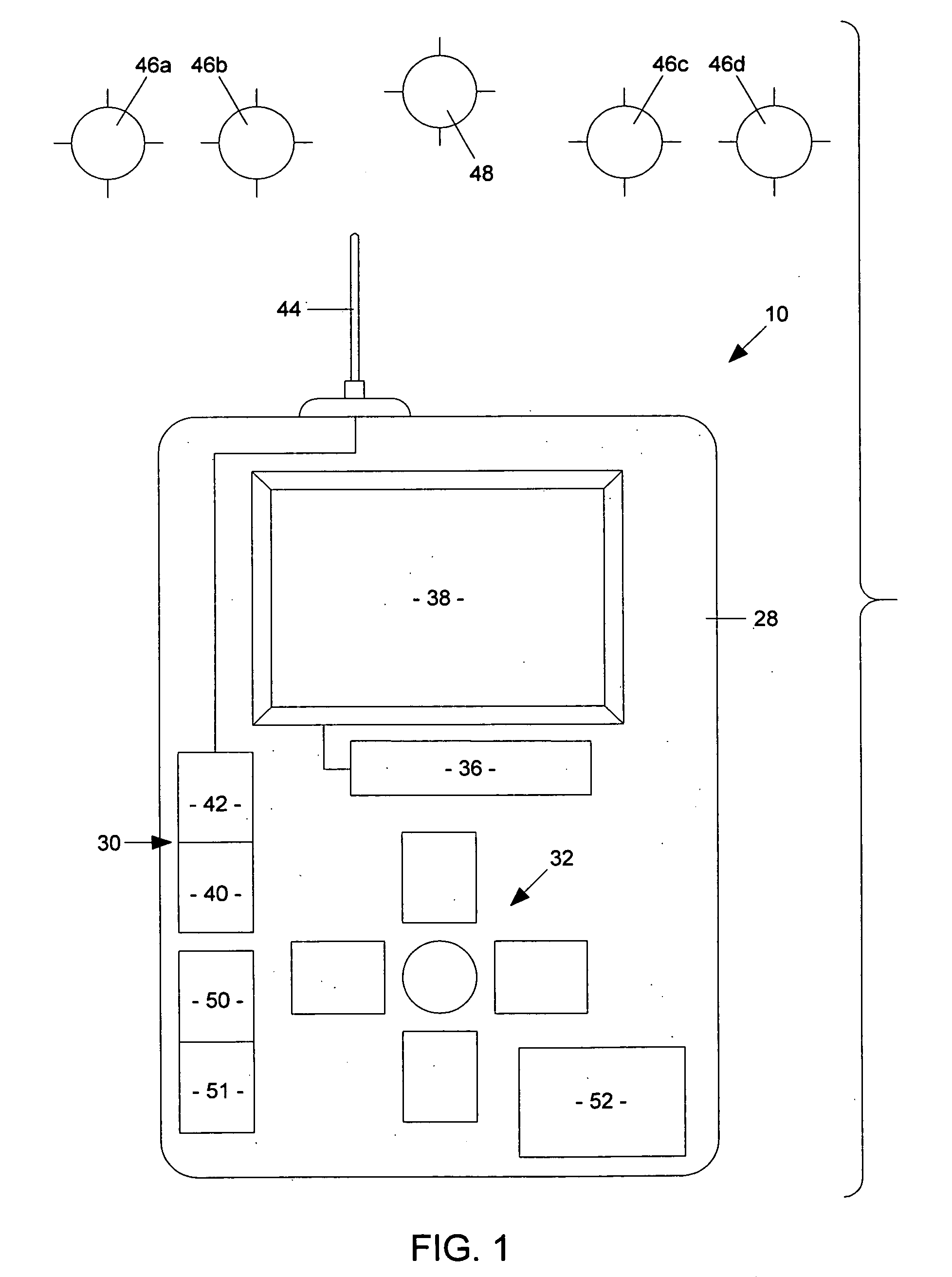
Search engine for audio data
InactiveUS20080033986A1Allow accessMetadata audio data retrievalDigital data processing detailsDistribution systemSpeech recognition
Audio streams are captured and simultaneously indexed in real time from a plurality of audio sources. The captured audio streams and index data of the captured audio streams from the plurality of audio sources are then stored. The storing process operates by temporarily storing the most recently captured audio streams, temporarily storing index data of the most recently captured audio streams, and then periodically loading the temporarily stored audio streams into permanently stored audio streams and periodically loading the temporarily stored index data into the permanently stored index data. A search and media distribution system is connected to the temporarily stored audio streams and the temporarily stored index data for allowing real time search and retrieval access to the captured audio streams.
Owner:REDLASSO CORP
Filtering and Policing for Defending Against Denial of Service Attacks on a Network
ActiveUS20080134327A1Reduce negative affectIncrease numberMemory loss protectionError detection/correctionComputer basedDenial-of-service attack
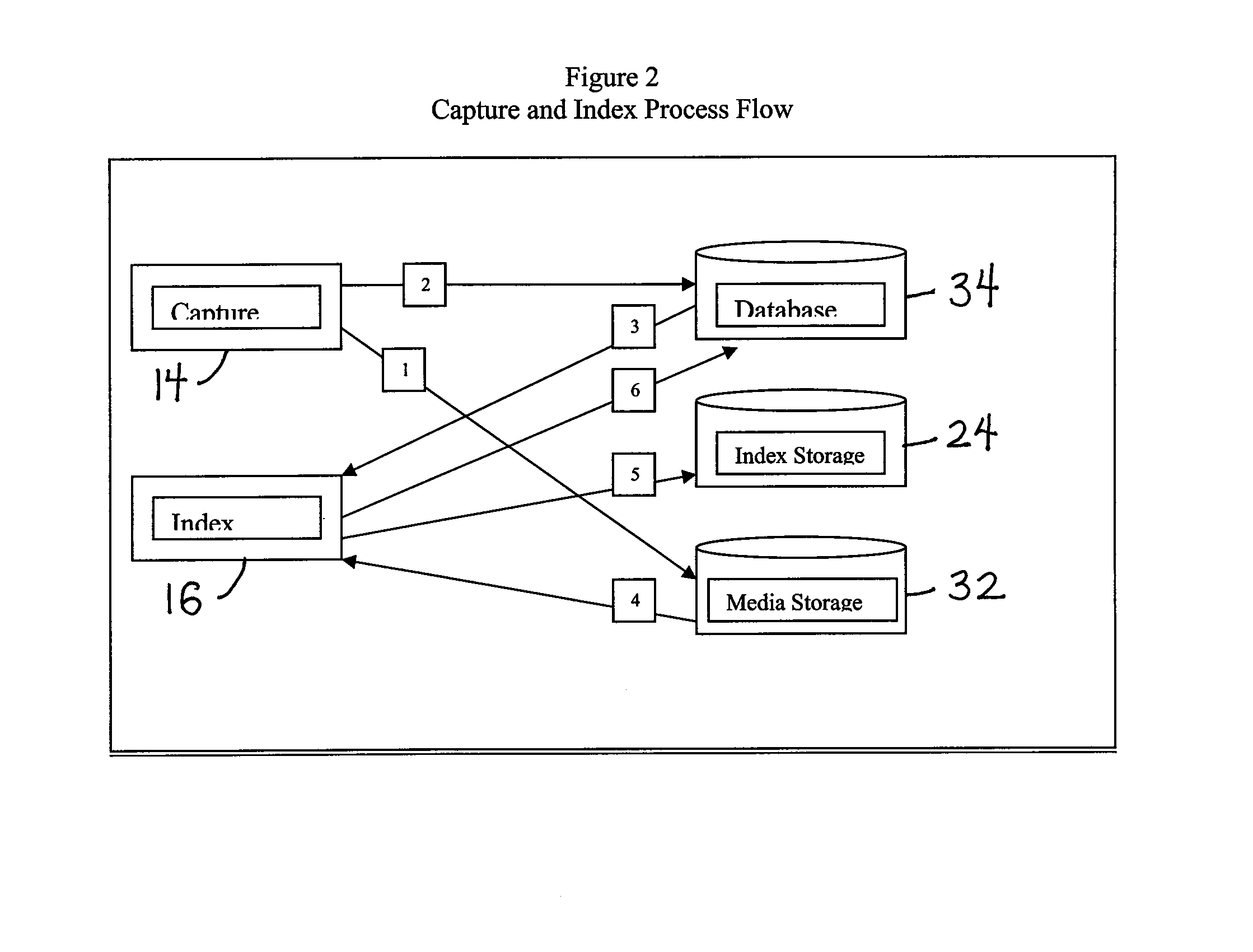
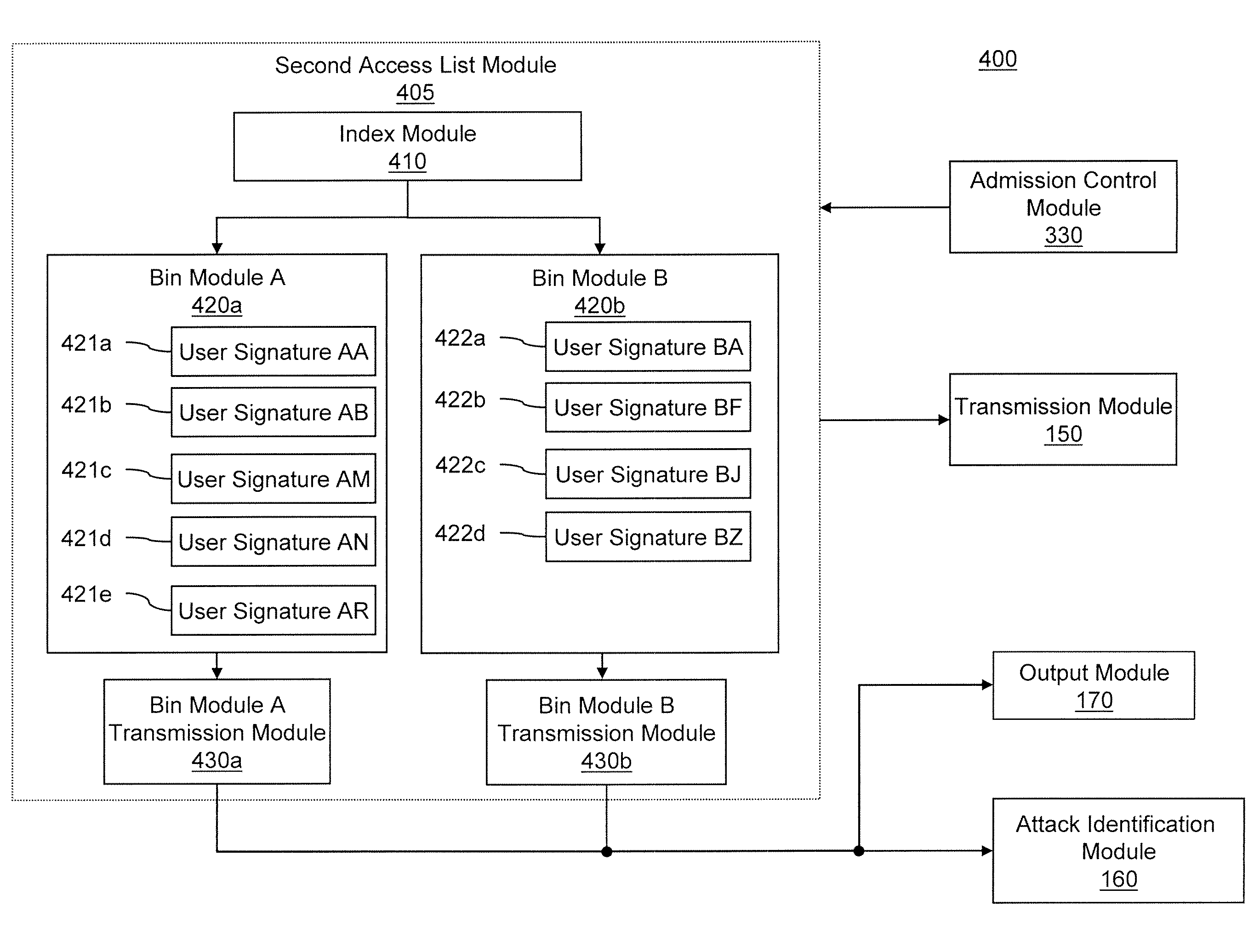
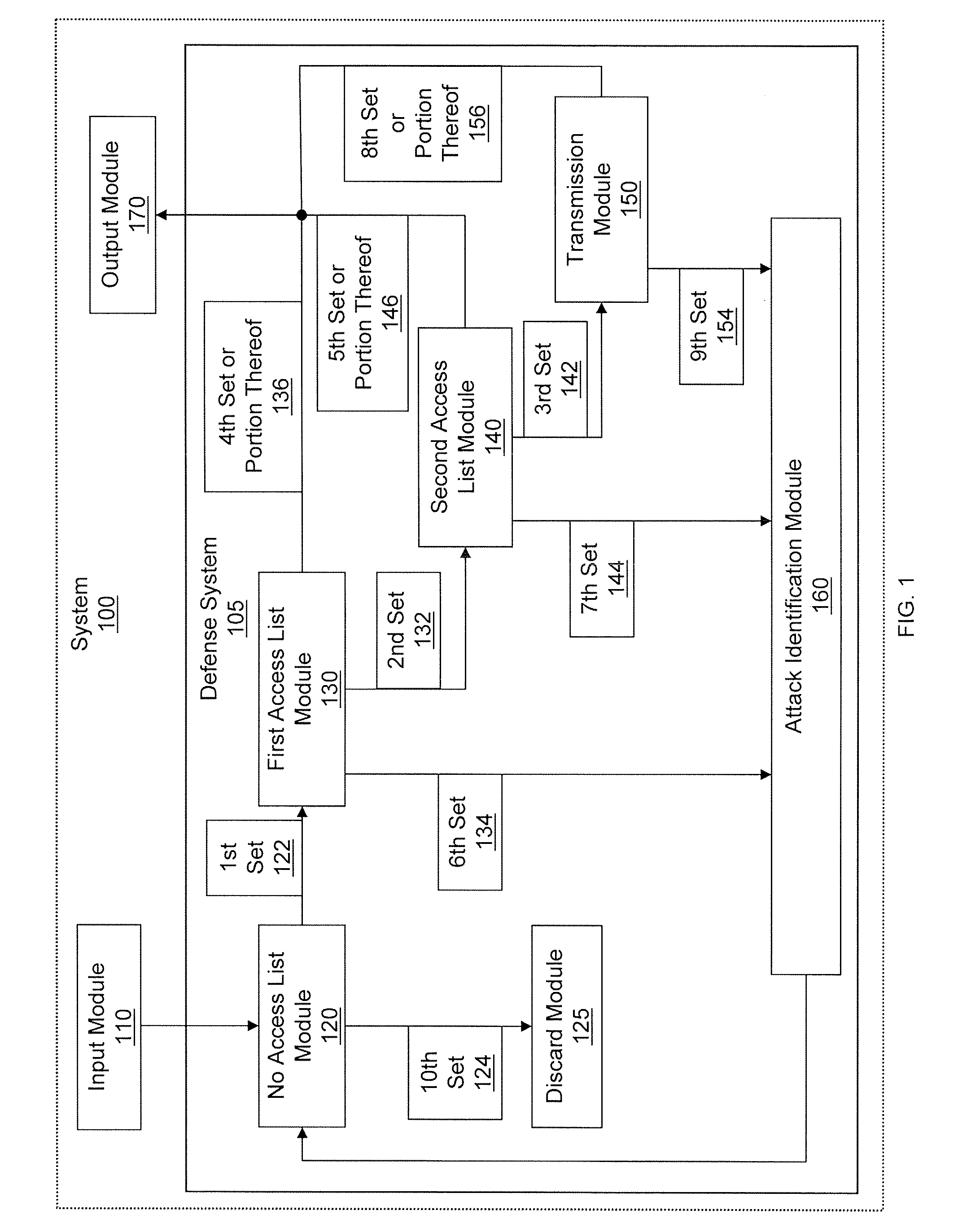
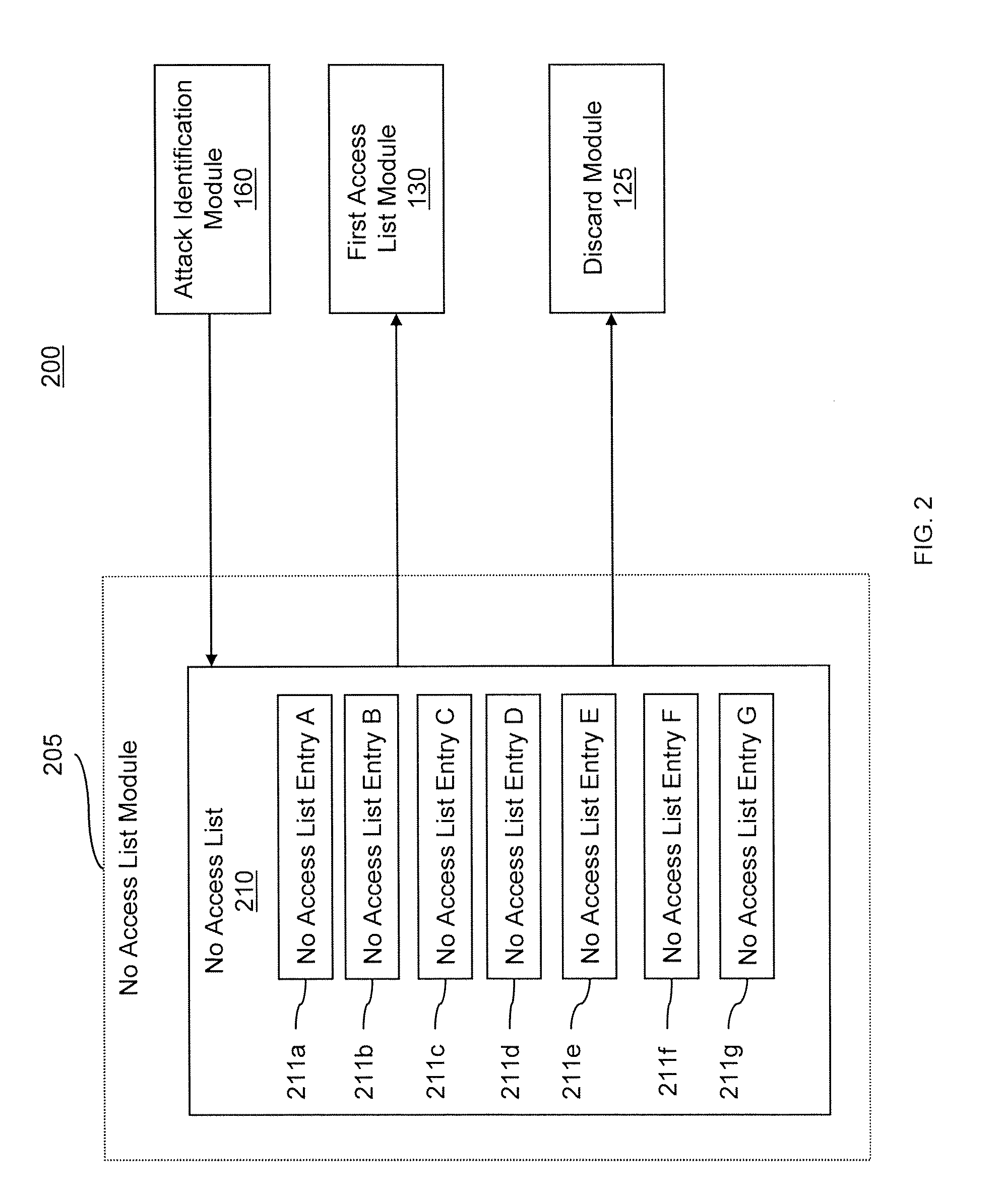
Described are computer-based methods and apparatuses, including computer program products, for filtering and policing for defending against denial of service attacks on a network. A data packet is filtered by a multi-tiered filtering and transmission system. Data packets matching the first tier filter are discarded. Data packets matching the second tier filter are transmitted to an output module based on a criterion. Data packets in the third tier filter are hashed into bins and data packets matching an entry in the bin are transmitted to the output module based on a criterion for the bin. Data packets in the fourth tier transmission system are transmitted to the output module based on a criterion. Data packets that do not meet the criterion for transmission to the output module are transmitted to an attack identification module which analyzes the data packets to identify attacks.
Owner:RIBBON COMM OPERATING CO INC
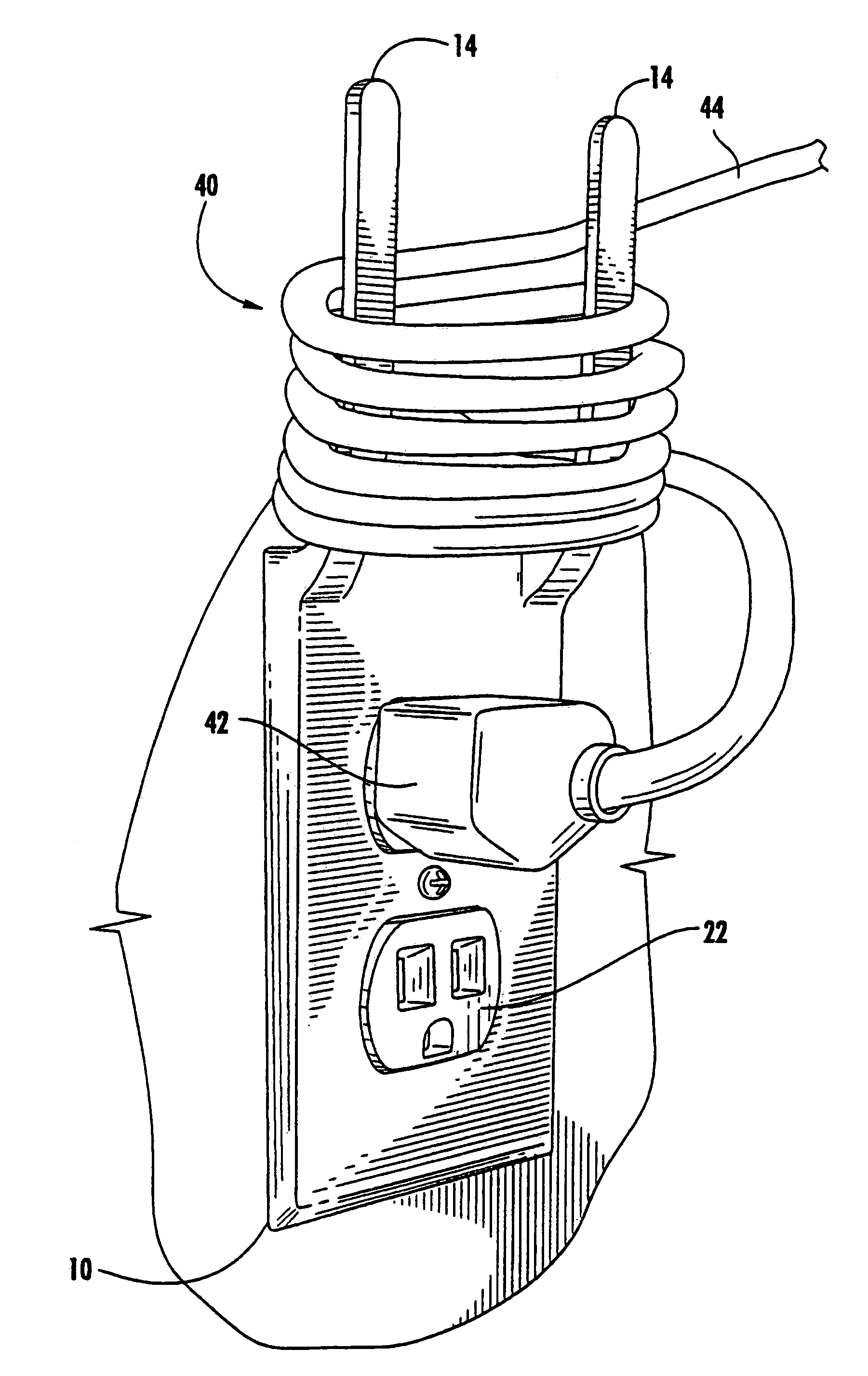
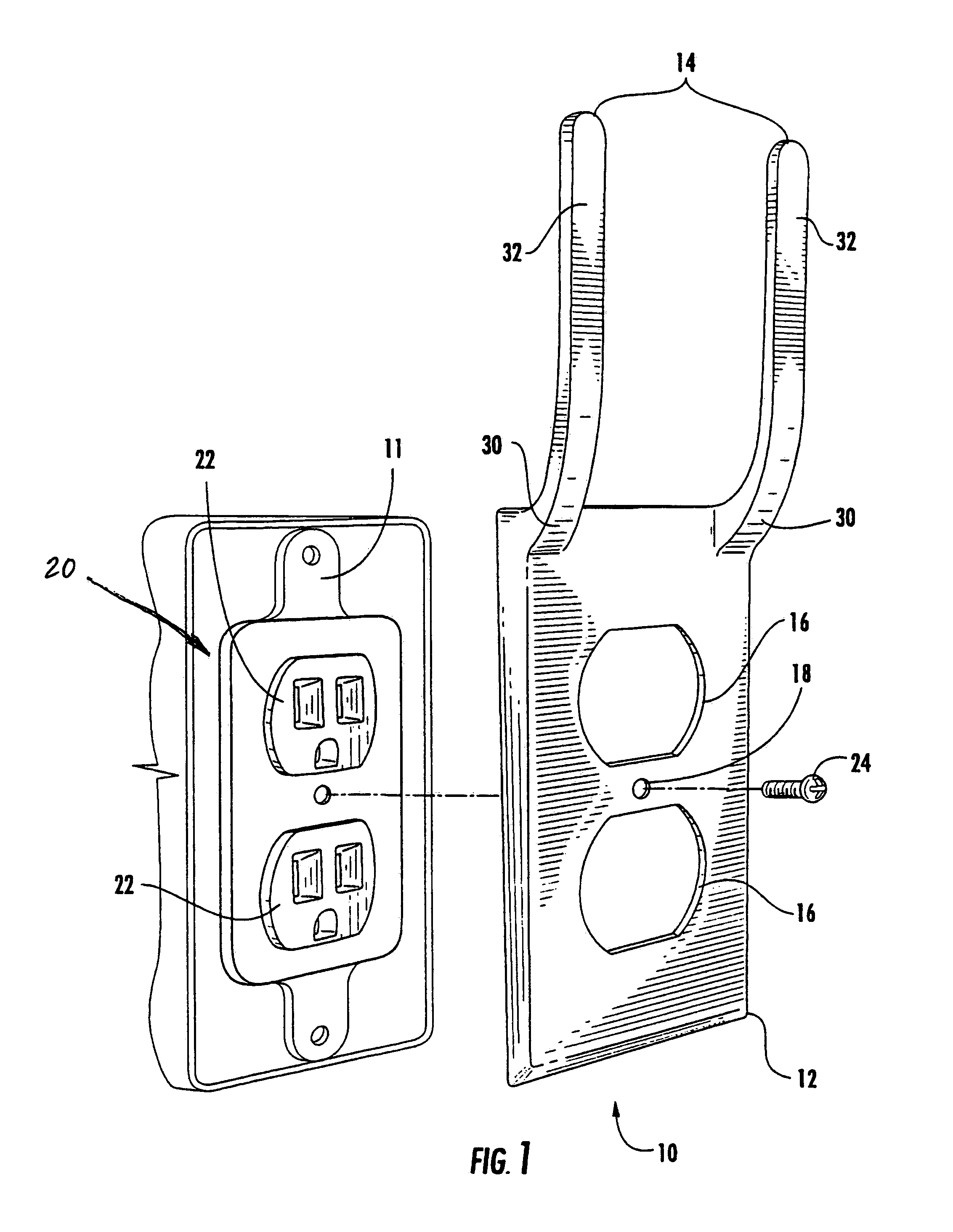
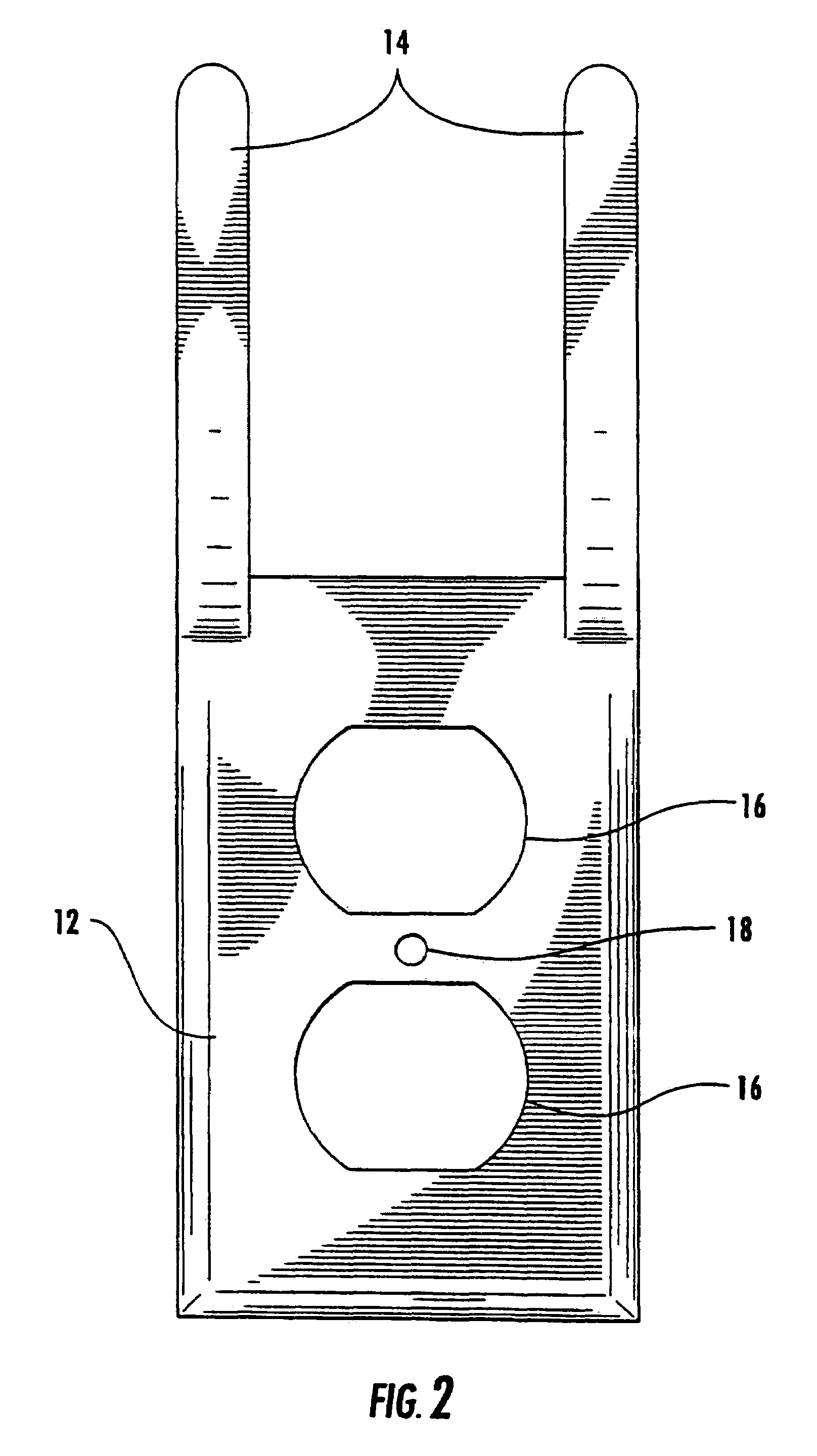
Power cord hanger outlet faceplate
ActiveUS7255588B2Allow accessEasy to receiveEngagement/disengagement of coupling partsTwo pole connectionsSurface platePower cord
Owner:WILDER JACKSON R
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com