Method and system for illegal invasion identification base on wireless network signal CO complexity
A technology of illegal intrusion and identification method, applied in wireless communication, electrical components, security devices, etc., can solve the problems of difficult illegal user intrusion, wireless network security loopholes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
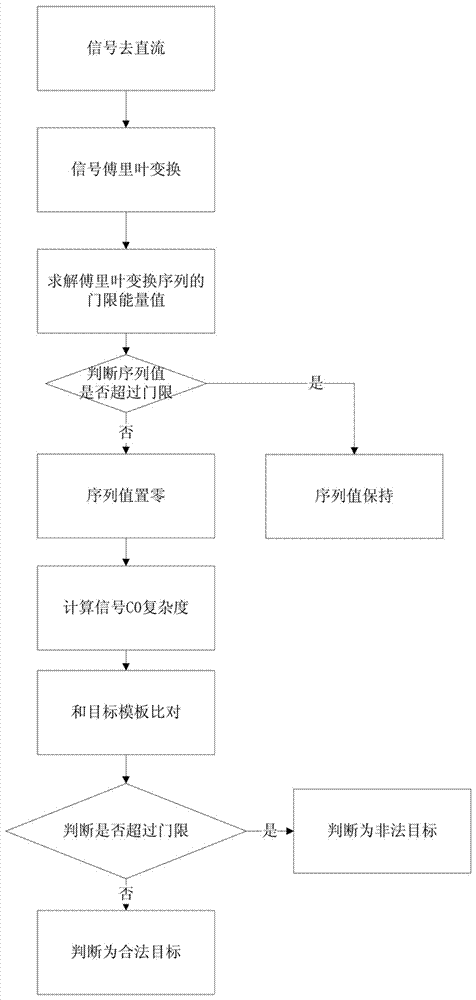
[0062] The present invention will be further described below in conjunction with the accompanying drawings and embodiments. In the present invention, take collecting a wireless network card signal of a DareGlobal DW505USB interface as an example.
[0063] Radiation source fingerprint identification technology can subvert the existing wireless network security mechanism based on keys and digital certificates, and completely solve the huge threat in the field of information security. The invention belongs to the field of wireless network / information security protection, and specifically relates to the "fingerprint" feature extraction technology of wireless network terminal equipment, which refers to the use of the unique "fingerprint" feature contained in the transmitted signals of different terminals connected to the wireless network to distinguish legitimate users from illegal users. user's method.
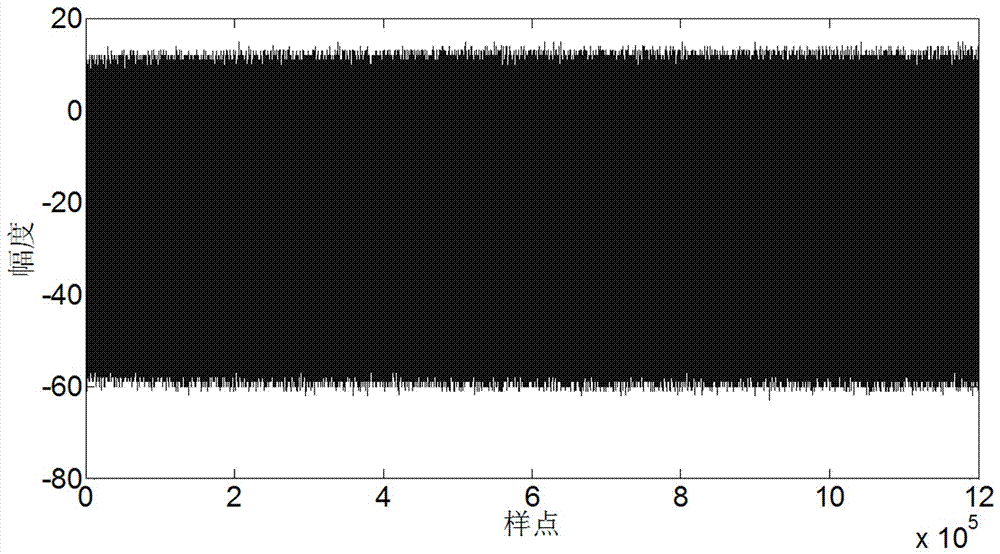
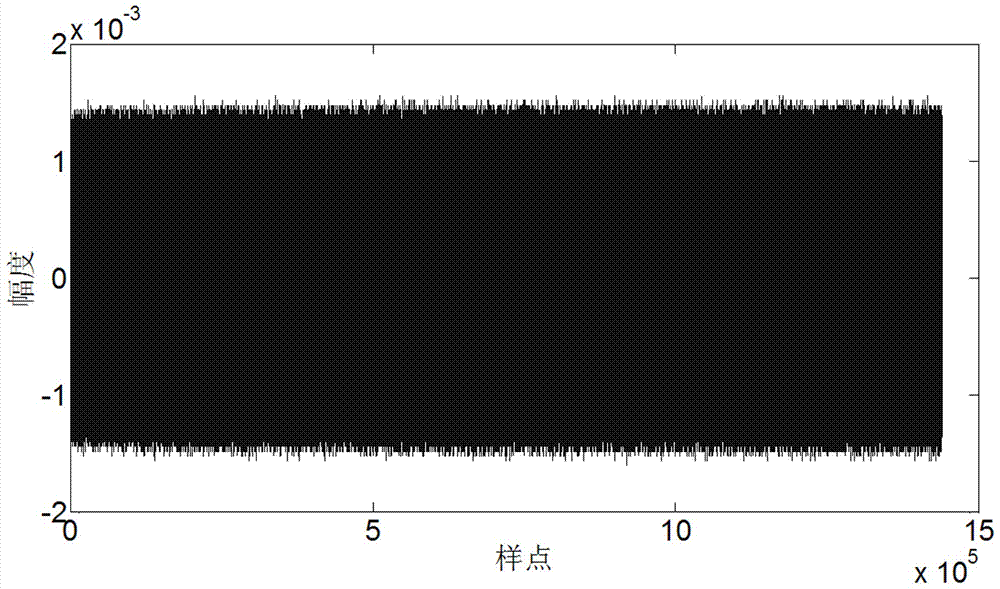
[0064] Such as Figure 1-8 As shown, in the first embodiment of the present...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com