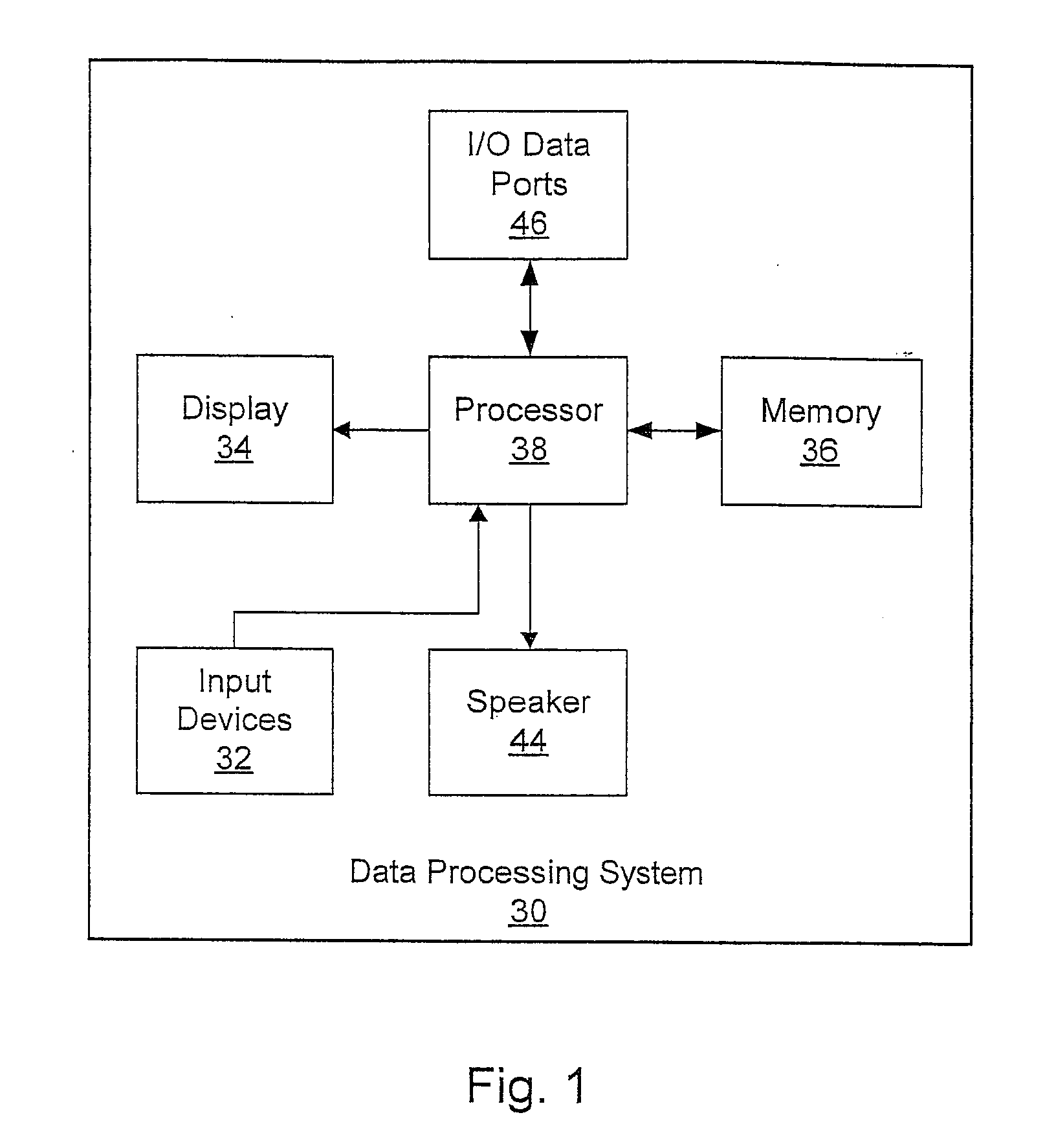
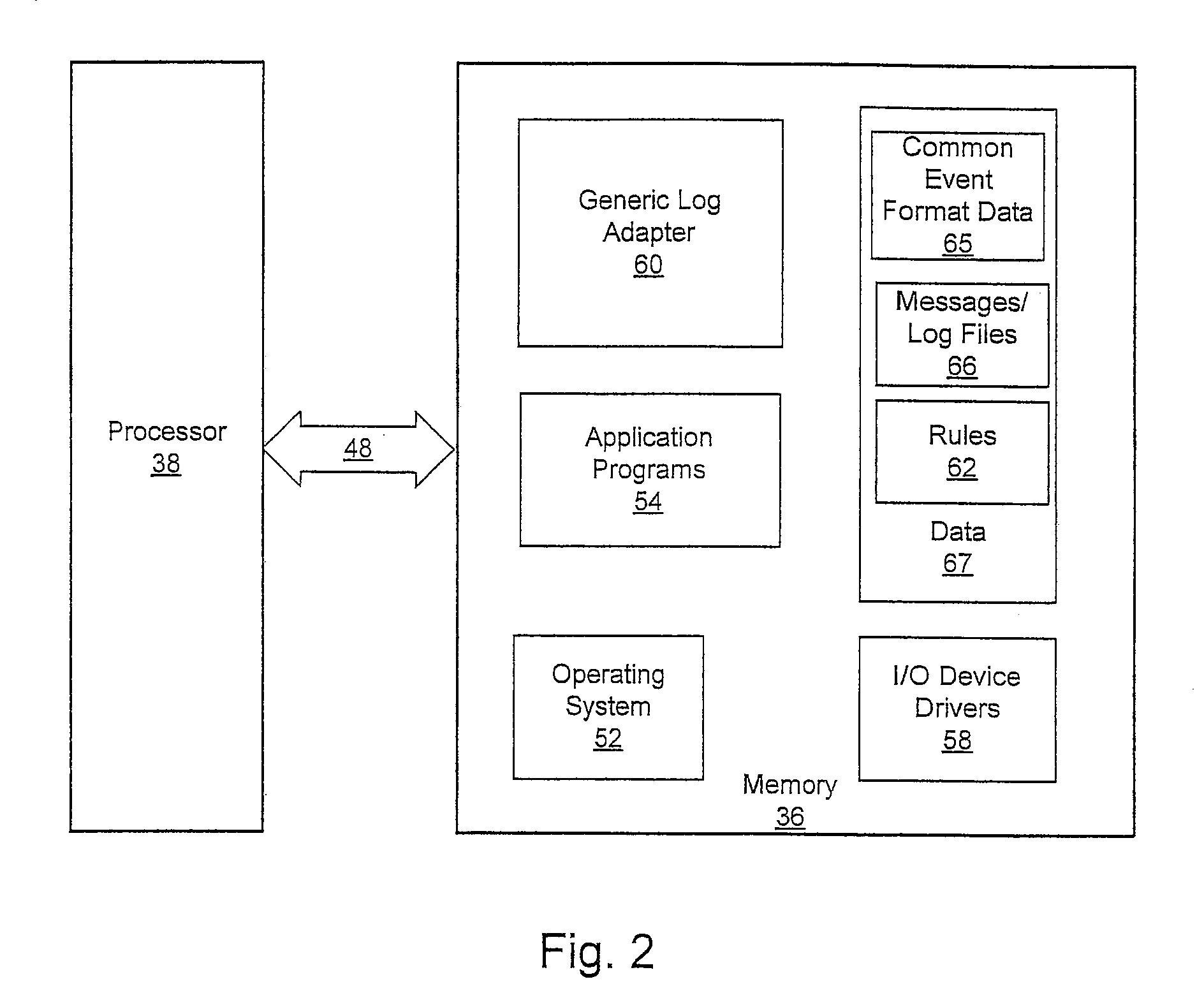
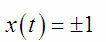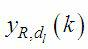Patents
Literature
422 results about "Code acquisition" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Indoor mobile robot positioning system and method based on two-dimensional code
ActiveCN102735235ASolve the speed problemFix the angle problemNavigation instrumentsCommunication interfaceImaging processing
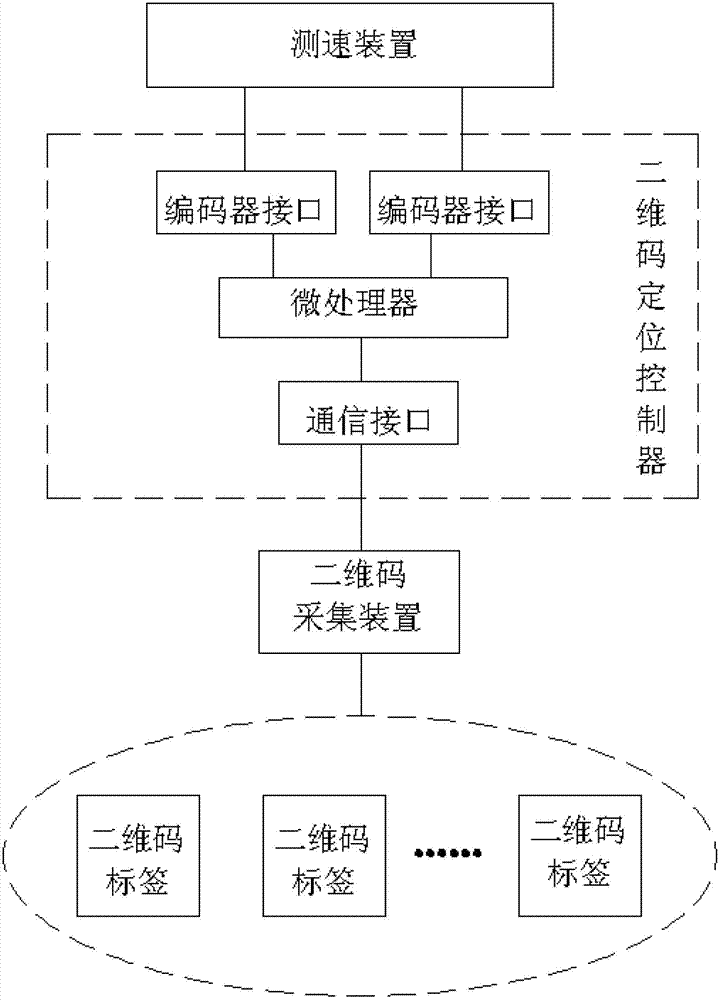
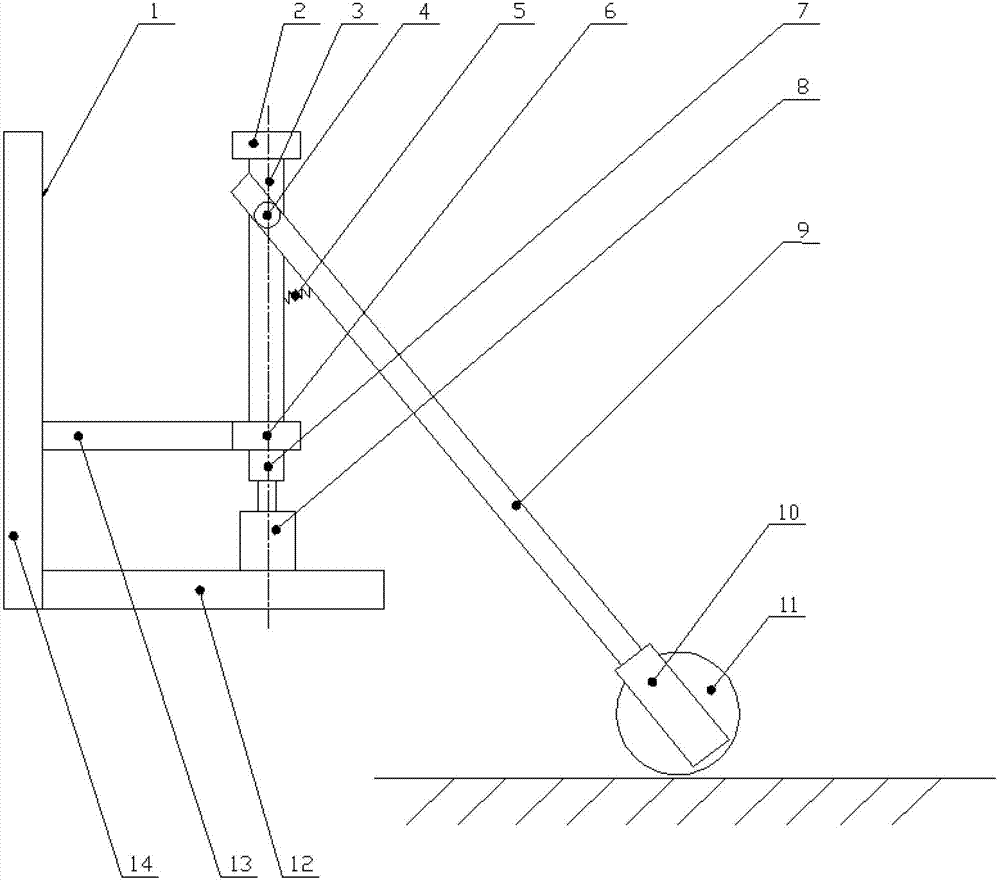
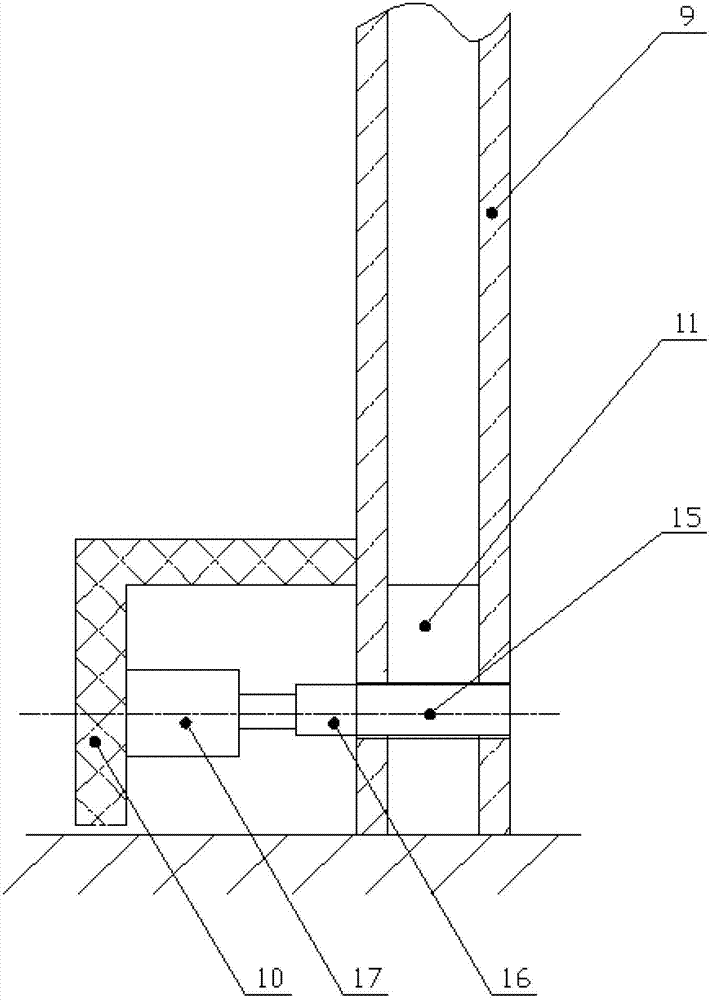
The present invention relates to an indoor mobile robot positioning system and method based on two-dimensional code. The system includes a two-dimensional code positioning controller mounted on a mobile robot, a two-dimensional code acquisition device and a two-dimensional code label distributed in the indoor environment. The two-dimensional code positioning controller is composed of a microprocessor and a communication interface that are connected together. The microprocessor is connected with the two-dimensional code acquisition device through the communication interface and is used for controlling the two-dimensional code acquisition device to acquire two-dimensional code images, receive the two-dimensional code images acquired by the two-dimensional code image acquisition device and realize precise positioning function. The method acquires an actual position of the mobile robot through photographing the indoor two-dimensional code labels, transforming coordinates and mapping code values. The method of the invention organically combines visual positioning technique, two-dimensional code positioning technology and two degree of freedom measuring technology to realize the function of precise positioning of the mobile robot and solve problems of complex image processing and inaccurate positioning of a traditional vision positioning system.
Owner:爱泊科技(海南)有限公司
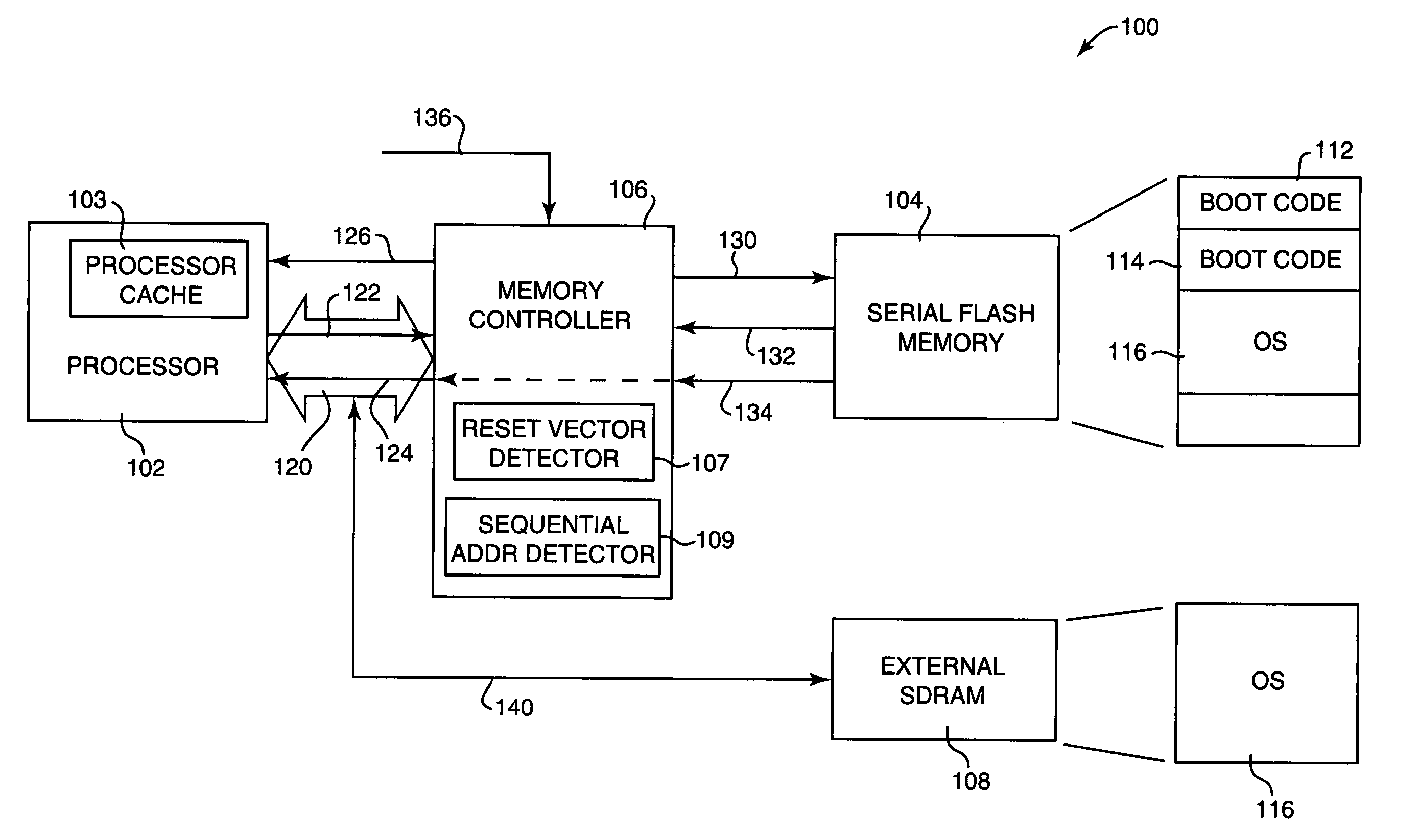
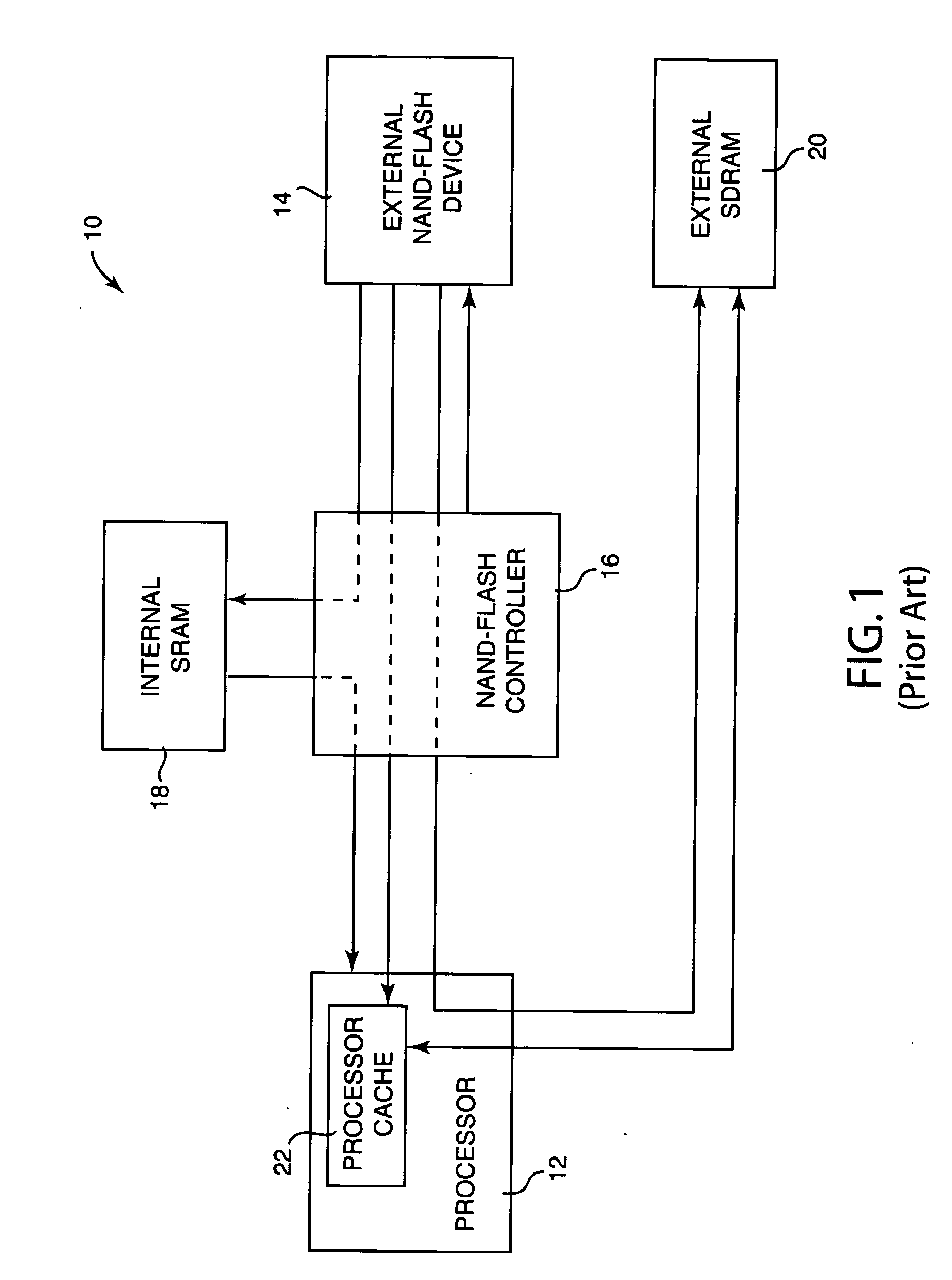
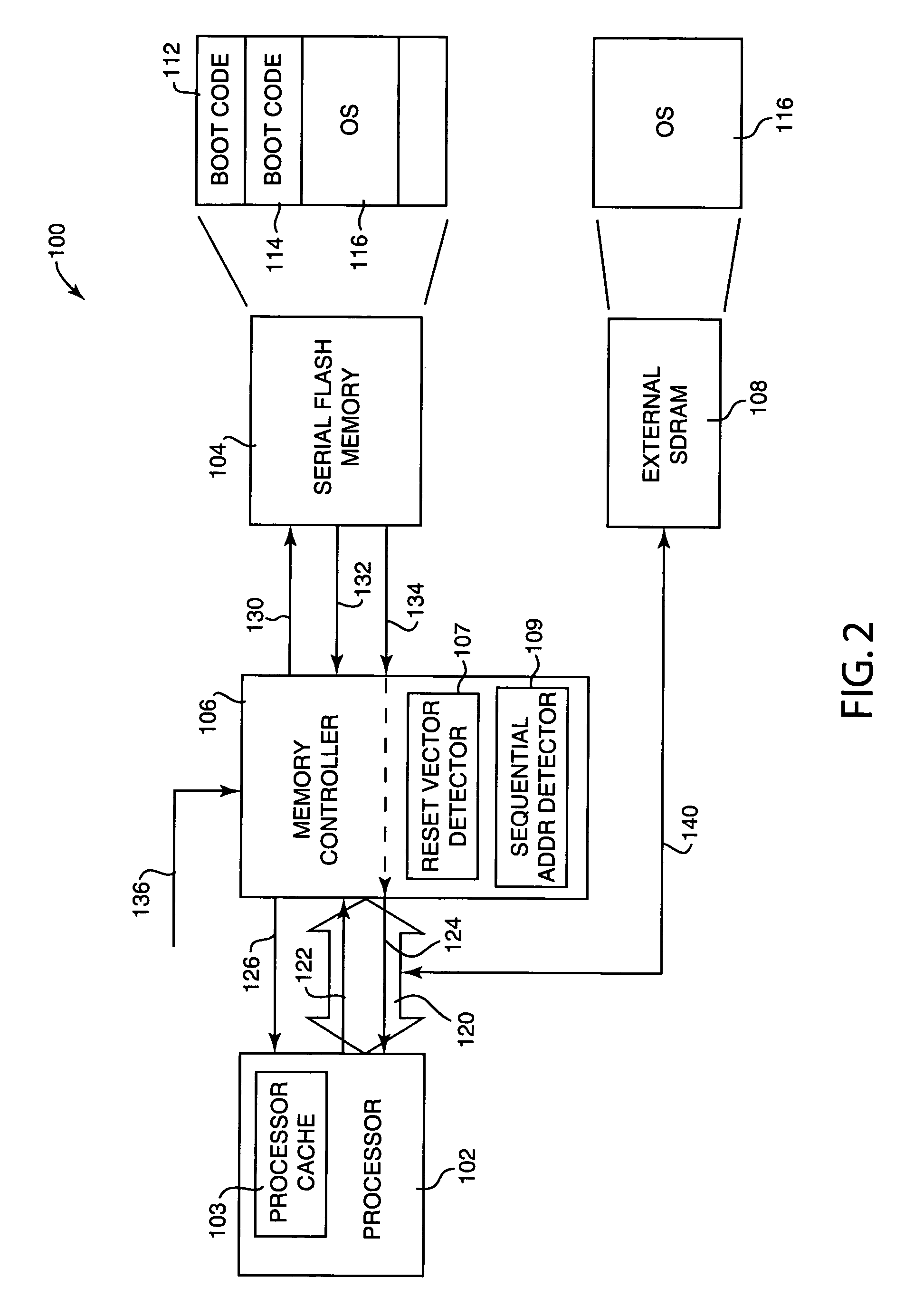
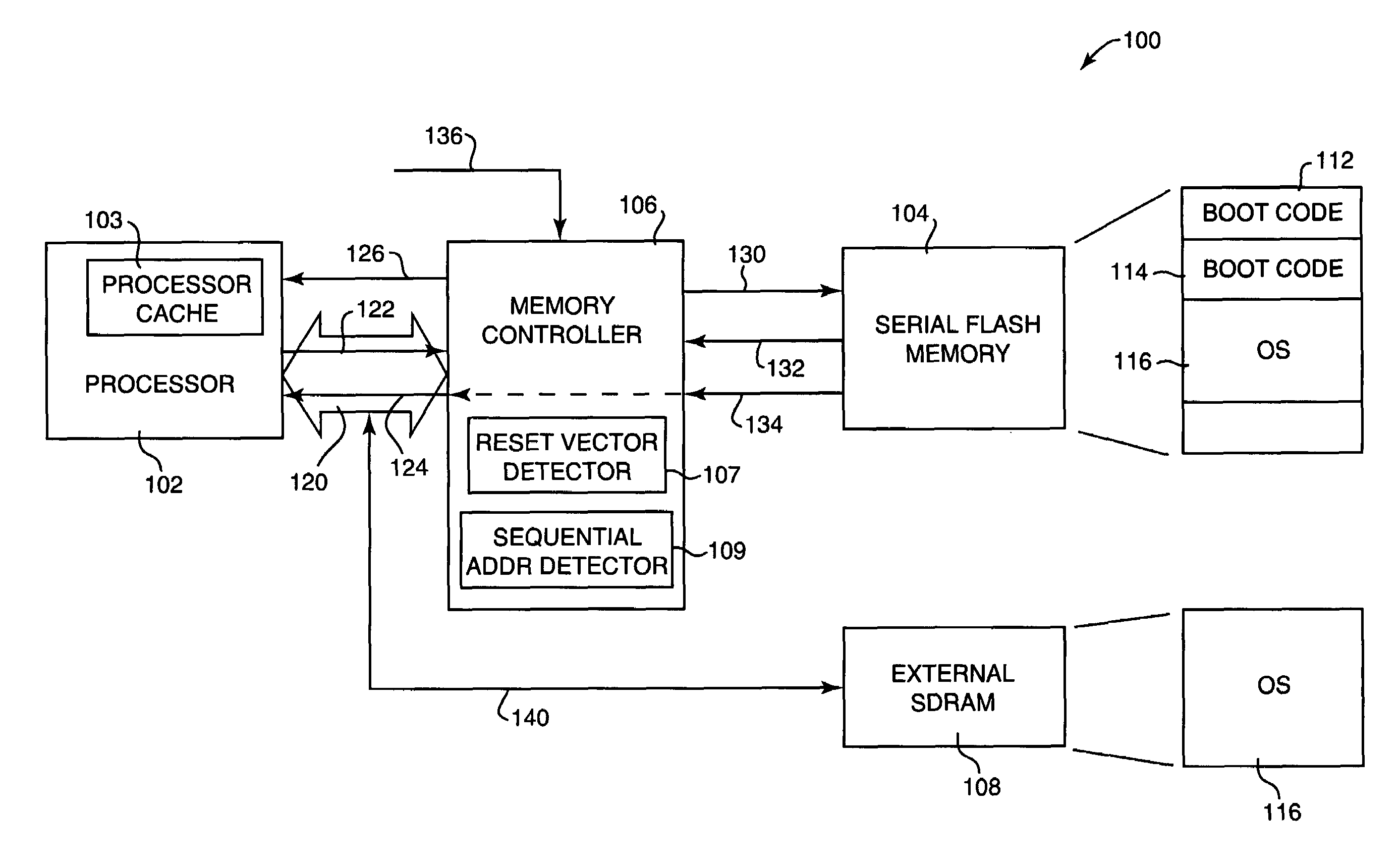
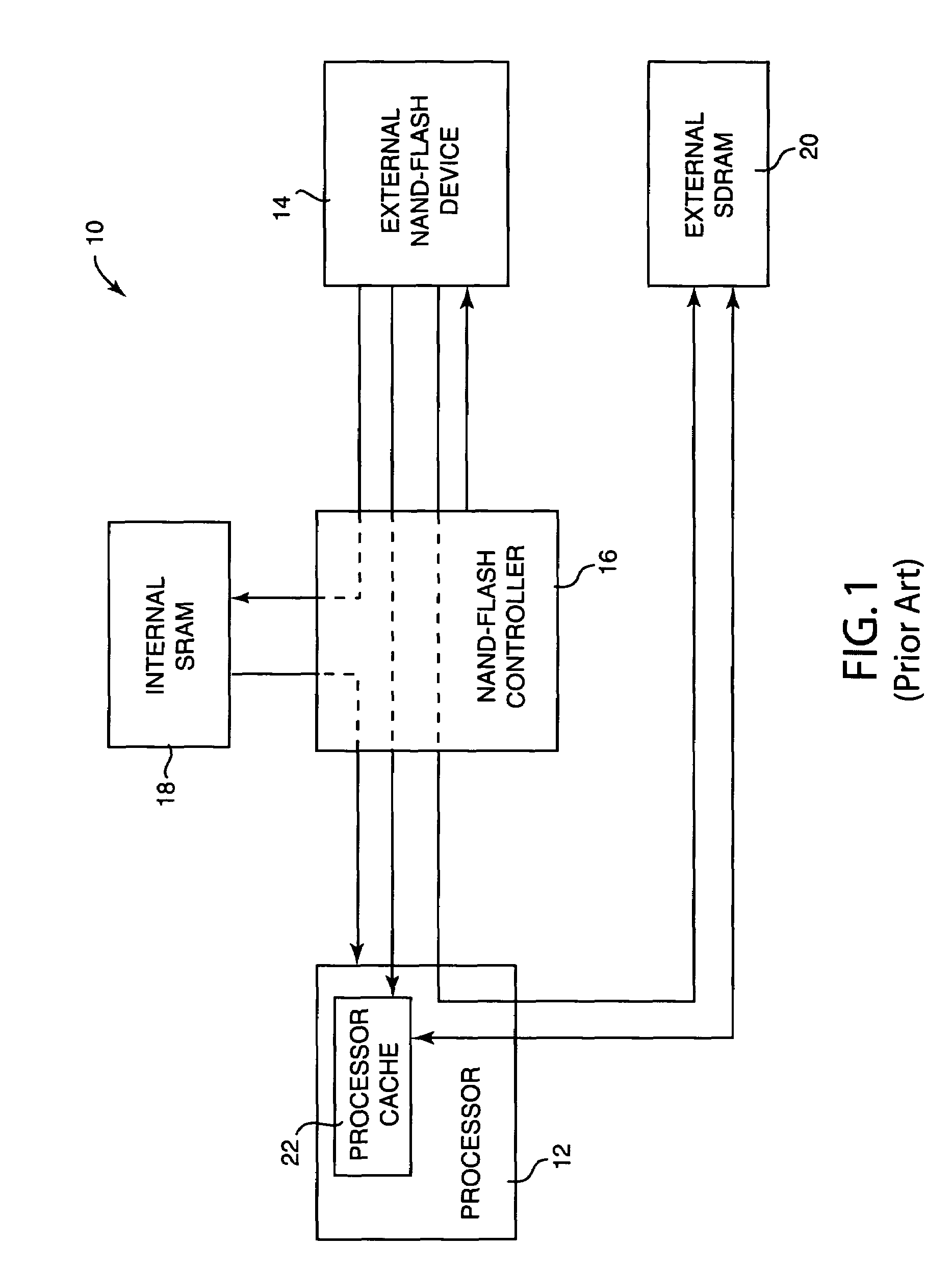
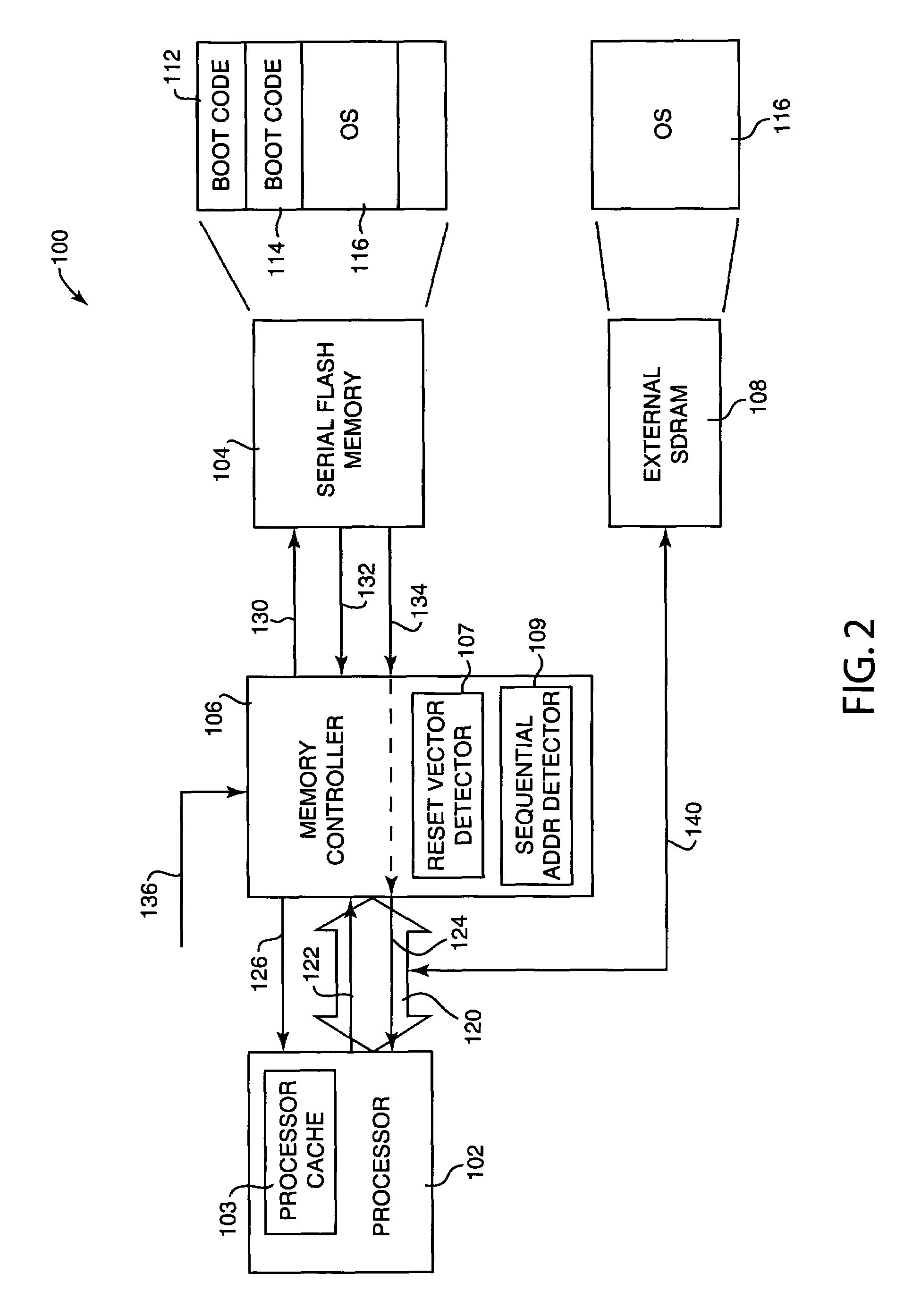
Method and system for loading processor boot code from serial flash memory
ActiveUS20050283598A1Increase storage capacityReduced parts countRead-only memoriesDigital computer detailsCode acquisitionMicroBlaze
Method and system for loading processor boot code from a serial flash memory device. A code fetch request is received from a processor, the code fetch request requesting a portion of boot code to be executed by the processor. The code fetch request is translated into a memory request providing random access to the serial flash memory device, and the memory request is sent to the serial flash memory. The portion of boot code is read from the serial flash memory device and provided to the processor.
Owner:LENOVO PC INT
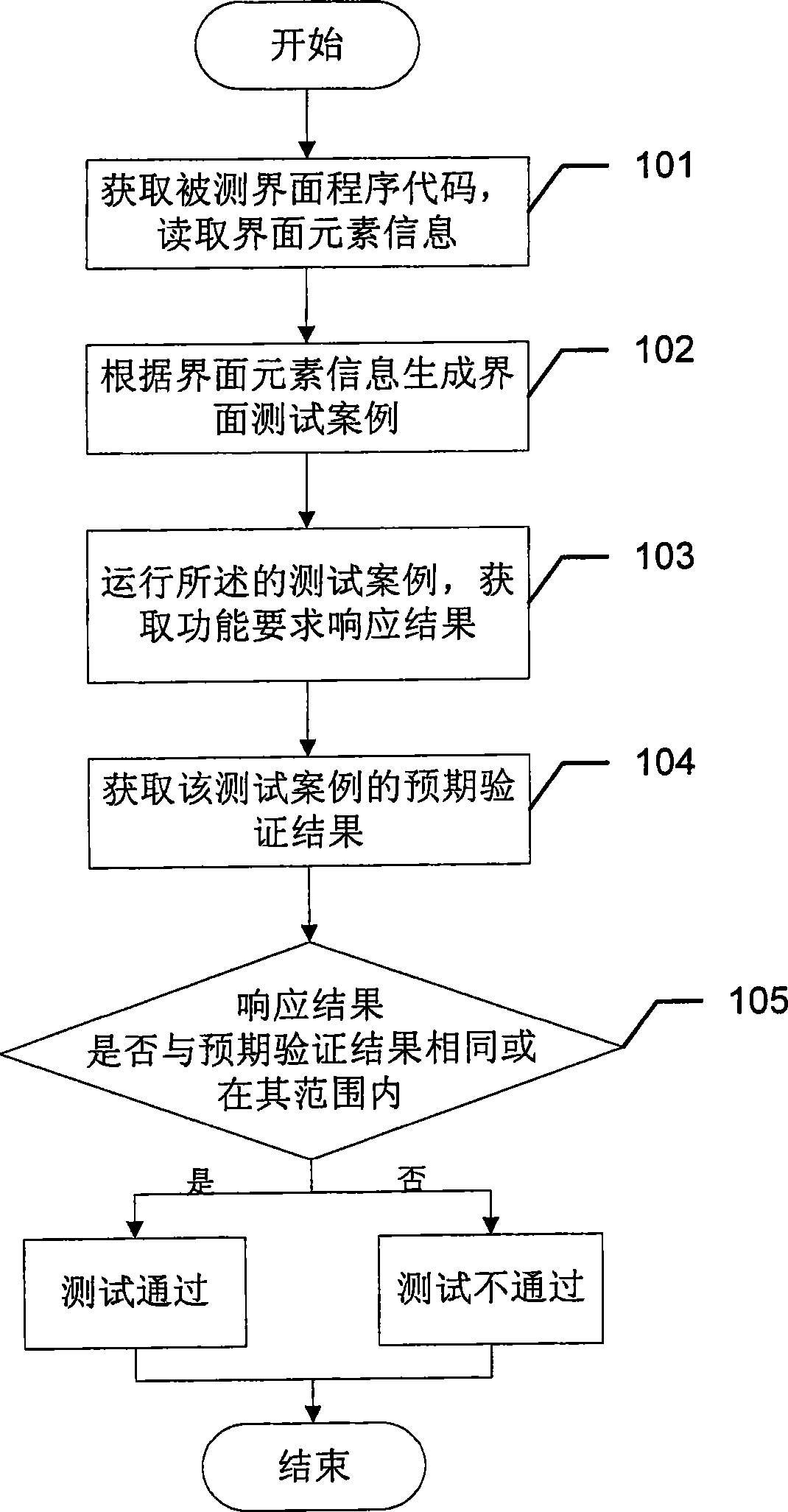
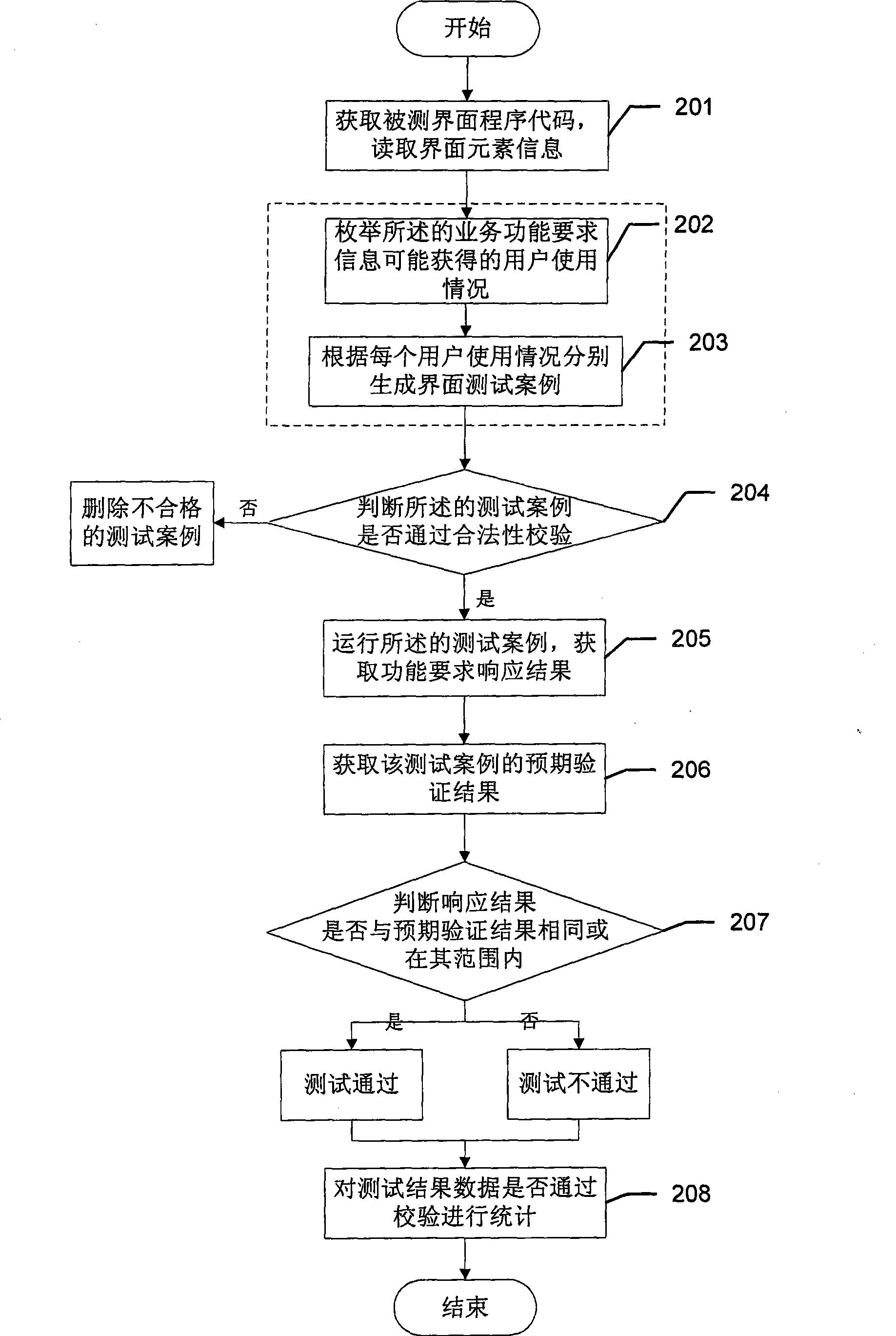
Automatic interface test system
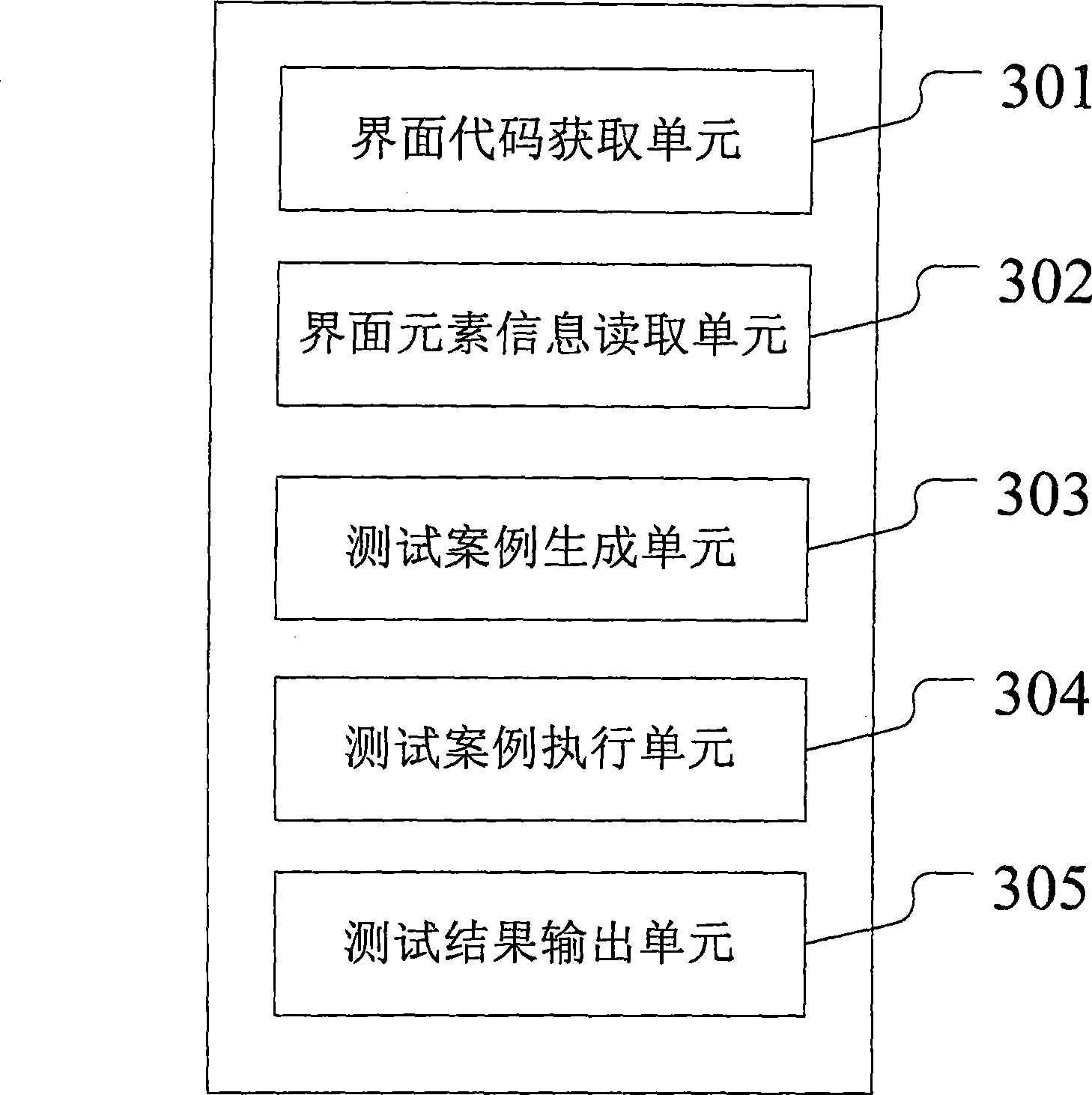
ActiveCN101377759AThe solution cannot be reusedSolve difficult batch case executionSoftware testing/debuggingComputer hardwareTest efficiency
The invention provides an automatic interface test system, which comprises an interface code acquisition unit used for acquiring the codes of tested interface programs; an interface element information read unit used for reading interface element information including interface element names, interface element types and service function requirement information from the codes of the tested interface programs; a test case generation unit used for generating interface test cases according to the business function requirement information; a test case execution unit used for running the test cases and responding to the functional requirements in the running of the test cases as well as acquiring the responding results of the functional requirements; a test result output unit used for acquiring expected verification results of the test cases from the running test cases, comparing the responding results of the functional requirements with the expected verification results for uniformity, and outputting uniform or nonuniform test results. The test efficiency of the automatic interface test system is significantly improved by comparing the test with the automatic interface test system with manual test.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
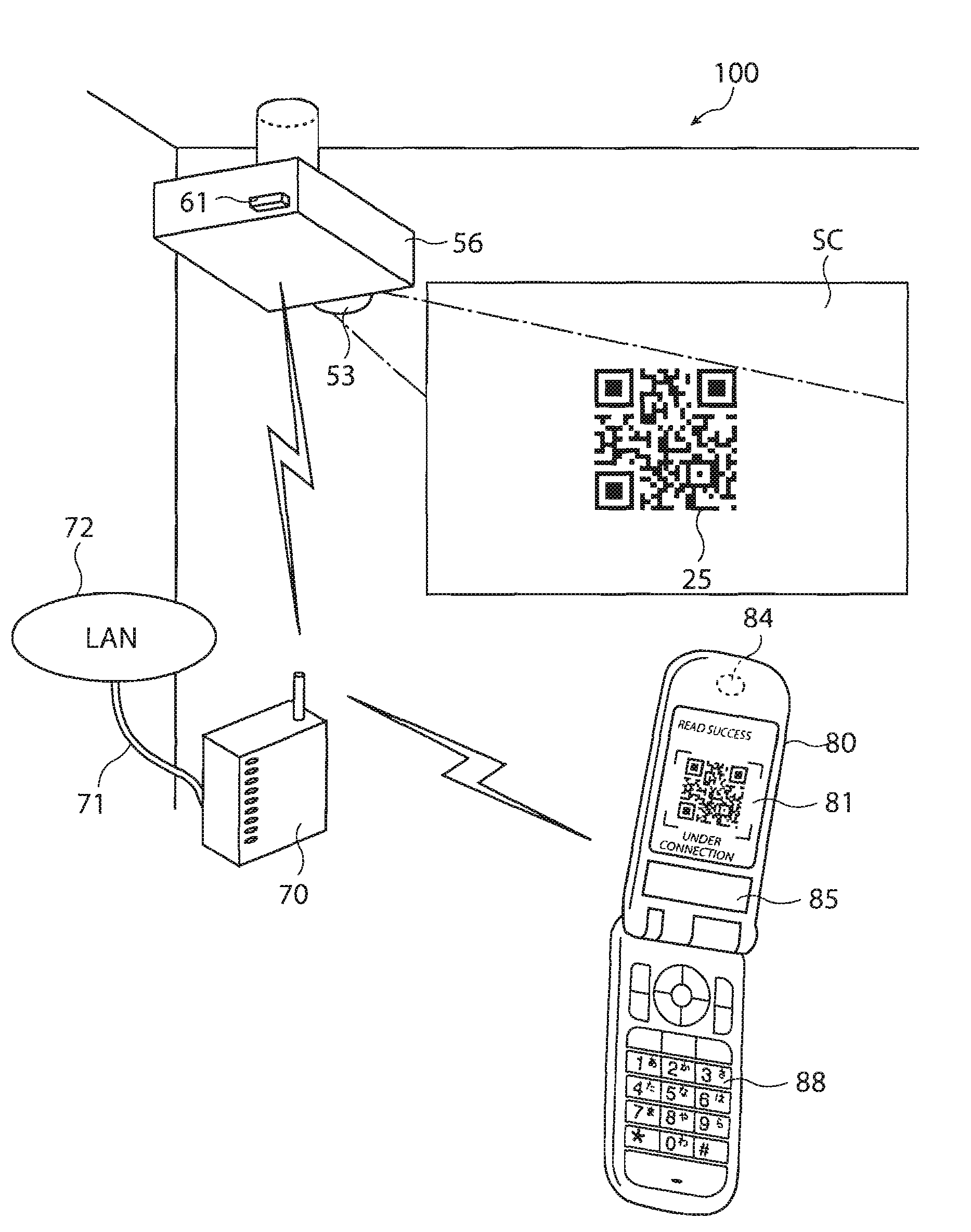
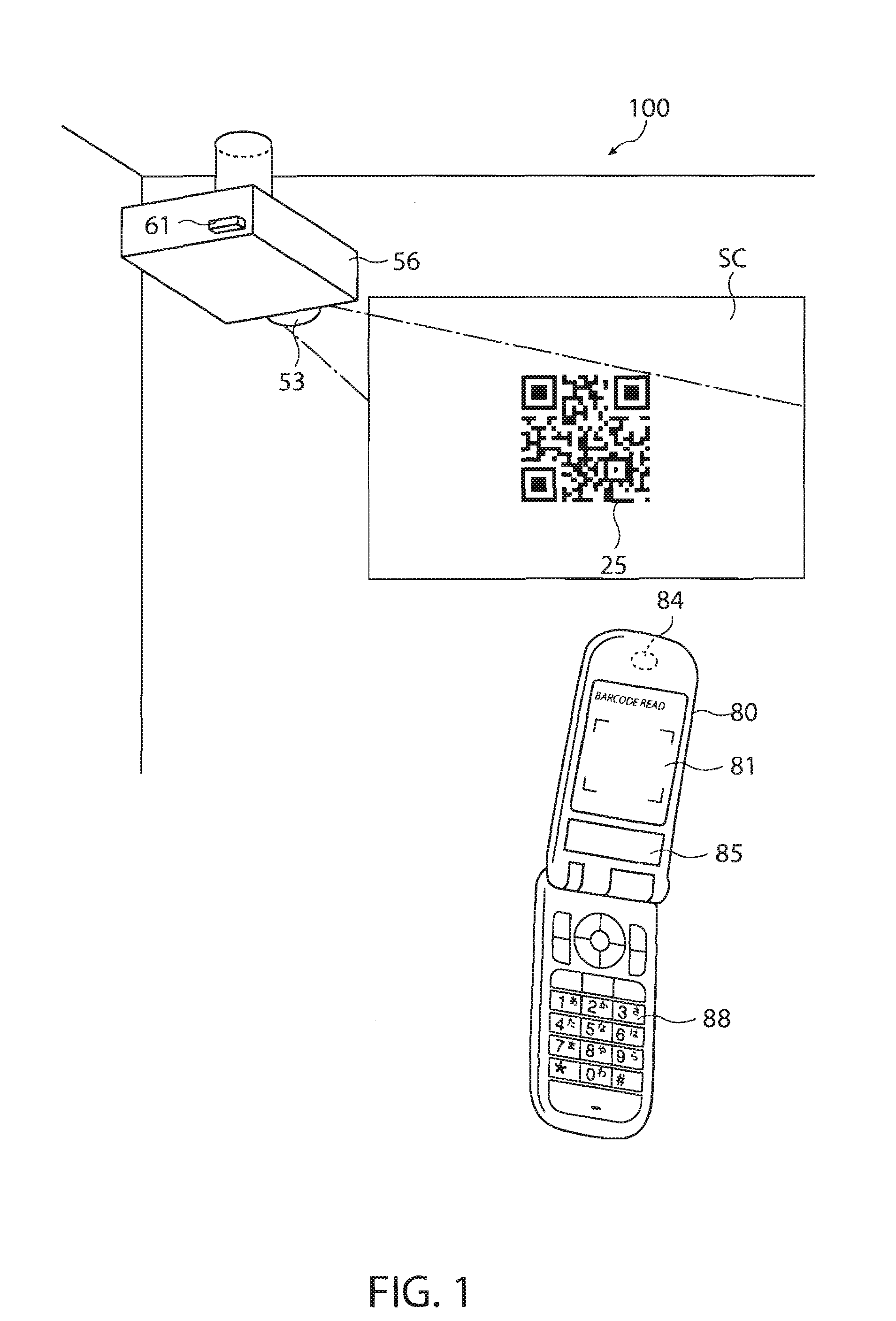
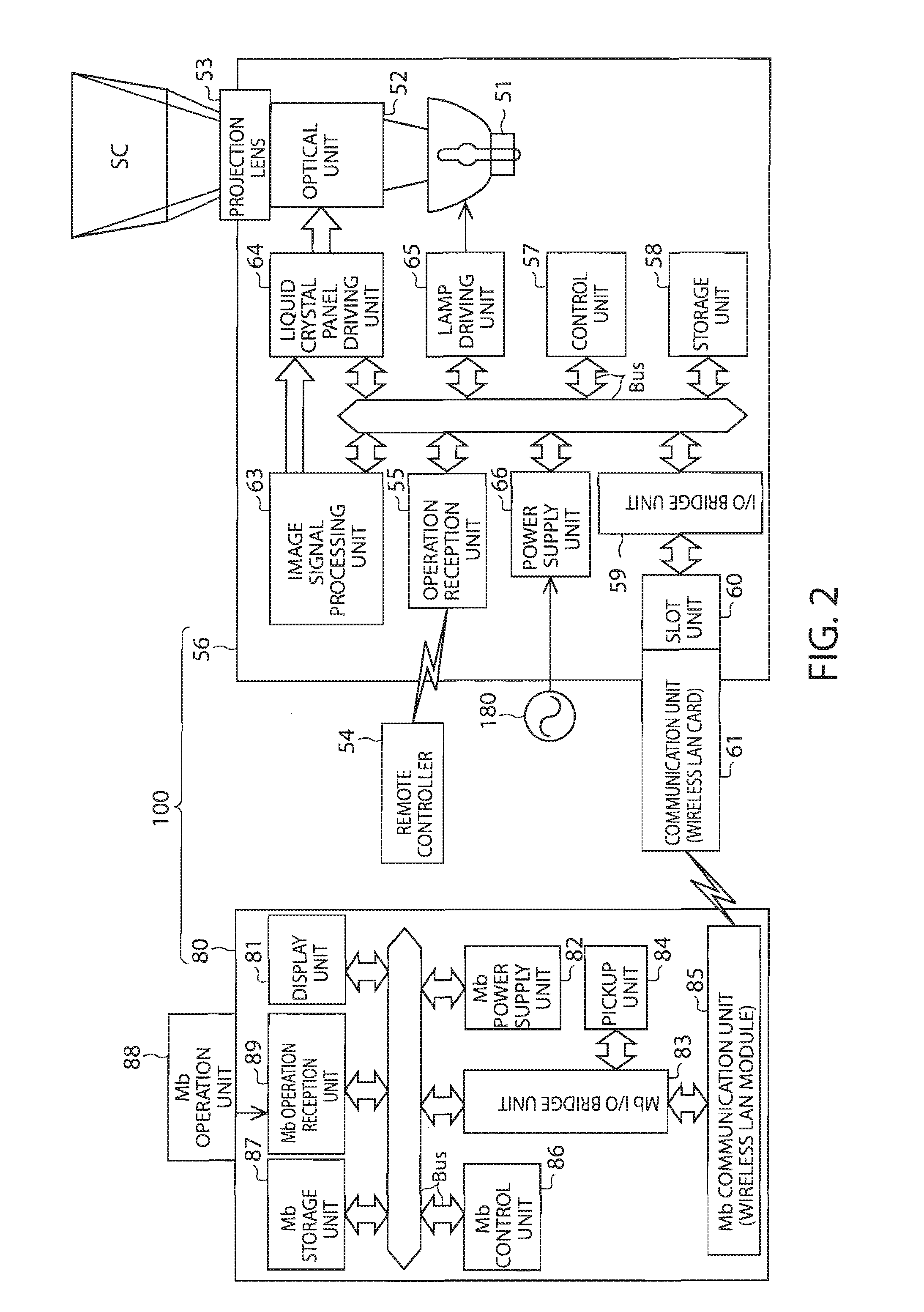
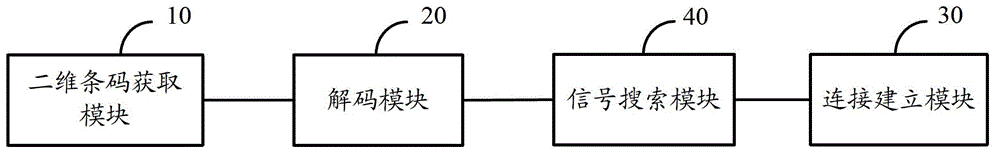
Image display system, image display device of image display system, mobile terminal device, connection establishment method of image display system
ActiveUS20080039063A1Improve connection reliabilityPrevent impossibilityDevices with wireless LAN interfaceMultiple digital computer combinationsDisplay deviceCode acquisition
An image display system is disclosed. The image display system includes an image display device forming an image and a mobile terminal device supplying image information to the image display device over a predetermined network, wherein the image display device includes: a storage unit which stores connection information for connecting to the image display device in the predetermined network; an encoding unit which encodes connection information code including the connection information; and a display unit which displays the connection information code or an image including the connection information code, and wherein the mobile terminal device includes: a code acquiring unit which acquires the connection information code from the displayed connection information code or the image including the connection information code; a code analysis unit which analyzes the connection information from the acquired connection information code; and a network connection establishment unit which establishes network connection with the image display device on the basis of the analyzed connection information.
Owner:SEIKO EPSON CORP
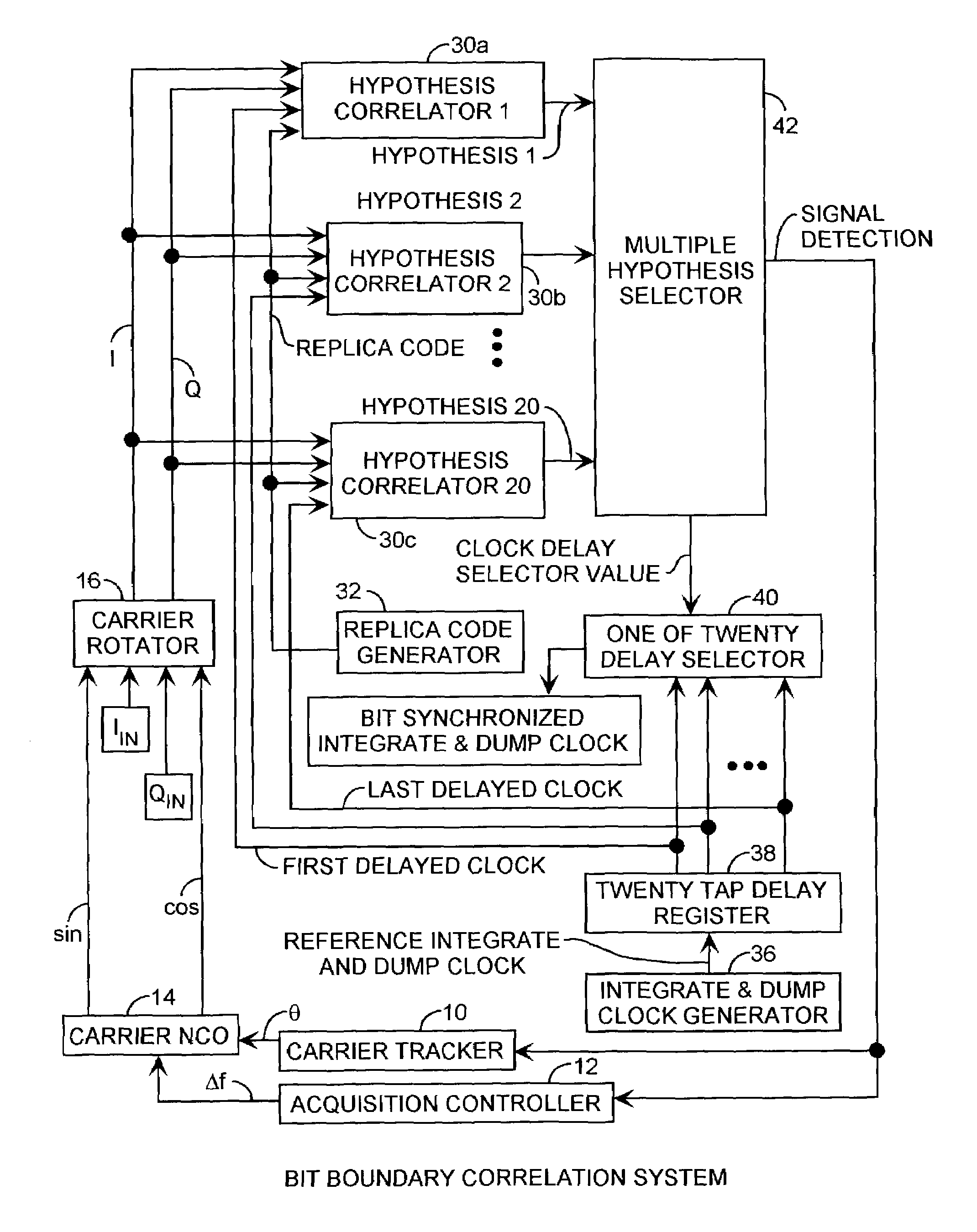
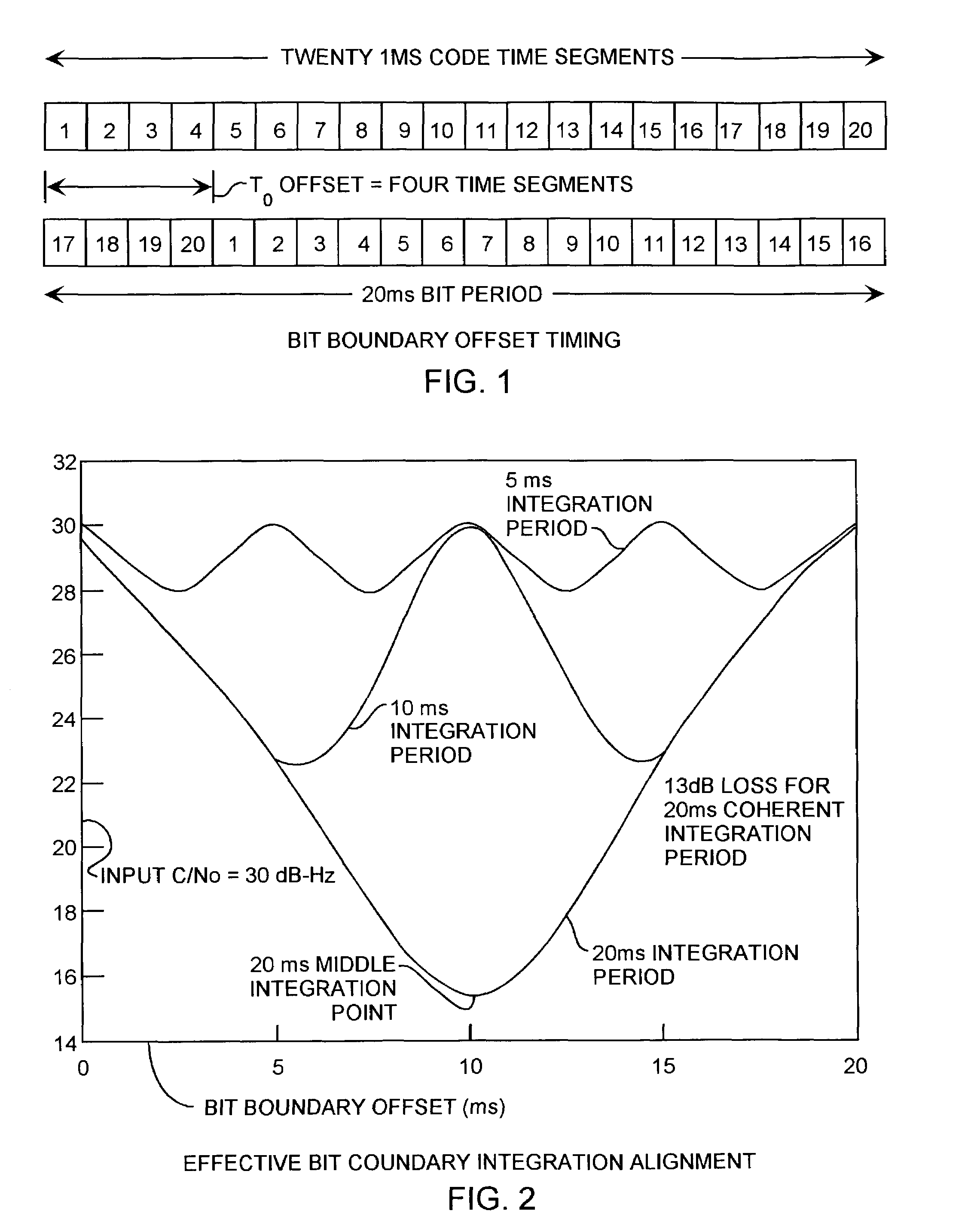
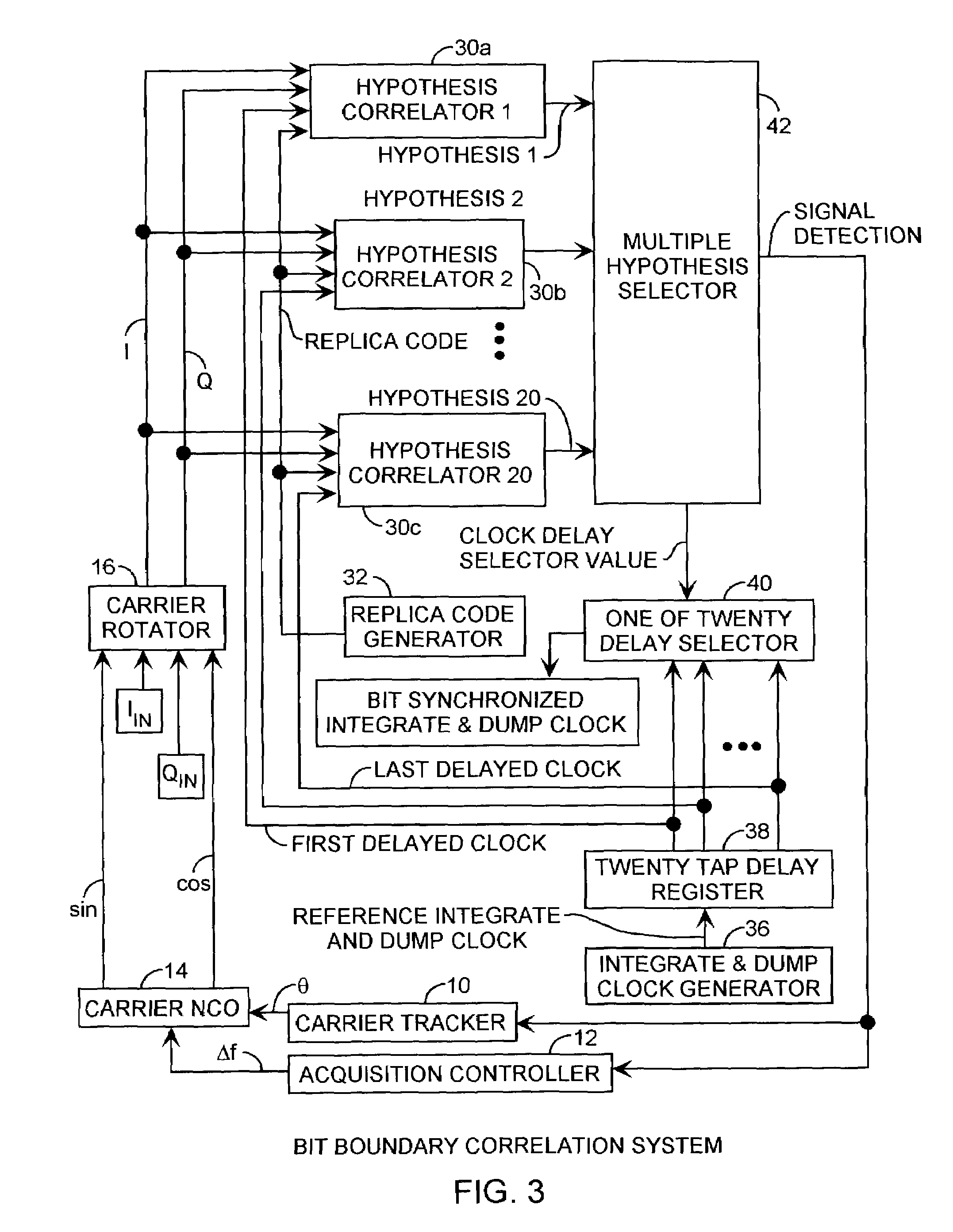
Spread spectrum bit boundary correlation search acquisition system
ActiveUS7042930B2Reduce lossesImproved coherent integrationAmplitude-modulated carrier systemsBeacon systemsHypothesisData acquisition
A multiple integration hypothesis C / A code acquisition system resolves bit boundaries using parallel correlators providing magnitude hypotheses during acquisition to reduce losses over the 20 ms integration period to improve the performance and sensitivity of C / A code receivers to achieve low C / No performance using inexpensive, imprecise oscillators and long noncoherent dwell periods, well suited for in-building, multipath, and foliage attenuated GPS signaling applicable to E911 communications with several dB of additional improvement in receiver sensitivity due to the ability to detect bit synchronization during acquisition.
Owner:THE AEROSPACE CORPORATION
Factory intelligent workshop real-time scheduling system
ActiveCN106056298AIntelligent Management ScienceManagement scienceResourcesProduction control systemStorage garage
The invention relates to a factory intelligent workshop real-time scheduling system, and is designed to solve the technical problem that a management system of an existing factory intelligent workshop needs further improvement. The system is mainly characterized in that an intelligent processing production line of the scheduling system finishes research and purchase as well as installation and debugging of workshop machining equipment; an intelligent warehouse and logistics transportation system carries out scientific classification, storage and transportation on raw materials and substances, management of finished and semi-finished products, and analysis and management on storage data of the raw materials, the semi-finished products and the finished products; an intelligent production control system, by fully utilizing information technology, carries out control in multiple dimensions of production plan issuing, material delivery, production scheduling, completion confirmation, standard operation guidance, quality control and finished product bar code acquisition, and accurately conveys on-site information to a production manager and a decision maker in real time through a network; and an intelligent alarm system is used for monitoring environment and temperature and reminding a transfer robot to return, avoid obstacles and charge.
Owner:宁波赛夫科技有限公司
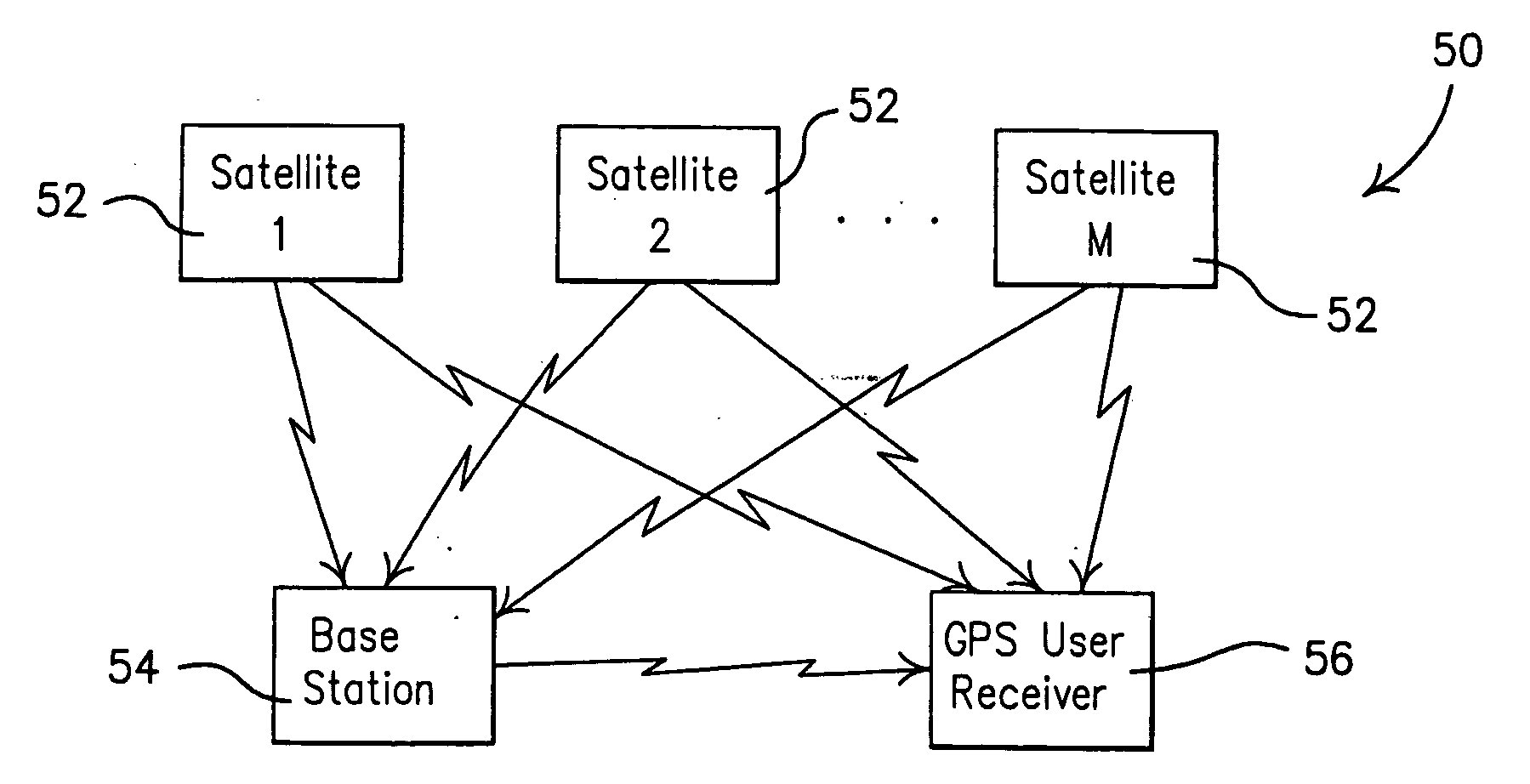
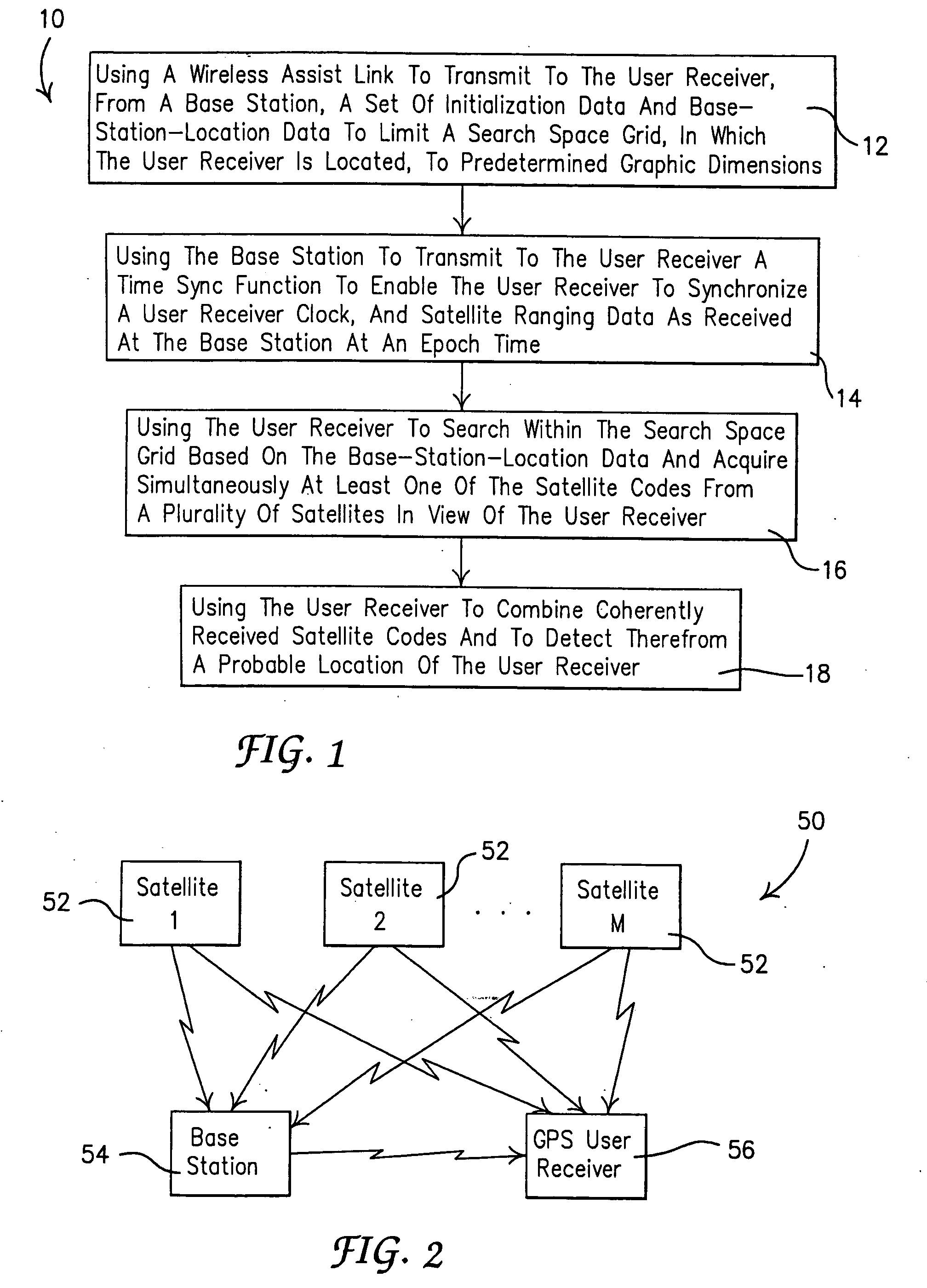
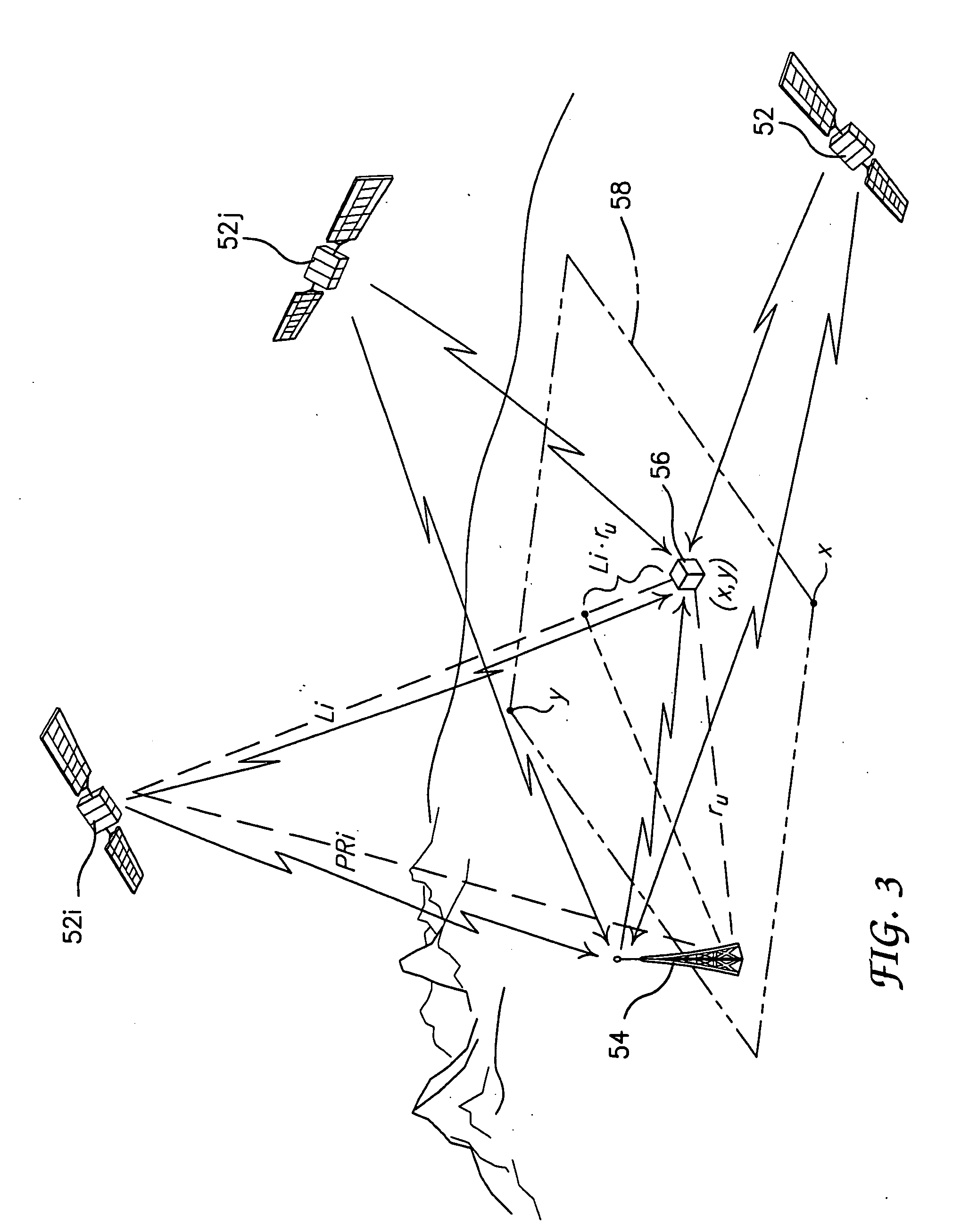
Method and system for all-in-view coherent GPS signal prn codes acquisition and navigation solution determination
ActiveUS20090262014A1Robust detectionImprove signal-to-noise ratioPosition fixationBeacon systemsOperation modeHot start
A method and system for enabling more robust detection, positioning and time solution using GPS satellite ranging signals based on a simultaneous, all-in-view coherent PRN code signal processing scheme rather than acquisition of GPS signals one at a time. Additionally, a plurality of signal processing operating modes are provided that include a Factory Start mode, a Hot Start mode, a Subsequent Fix mode and a Reacquisition mode. Each mode provides a user receiver with an ability to quickly determine its current probable location without undue delay when a prior probable location has been obtained. Preventing undue delay of predicting a probable location of the user can be especially valuable in conditions where weak signals are being received, or in high interference environments, or when signal jamming conditions are being experienced, or when a combination of such environments is present.
Owner:THE BOEING CO
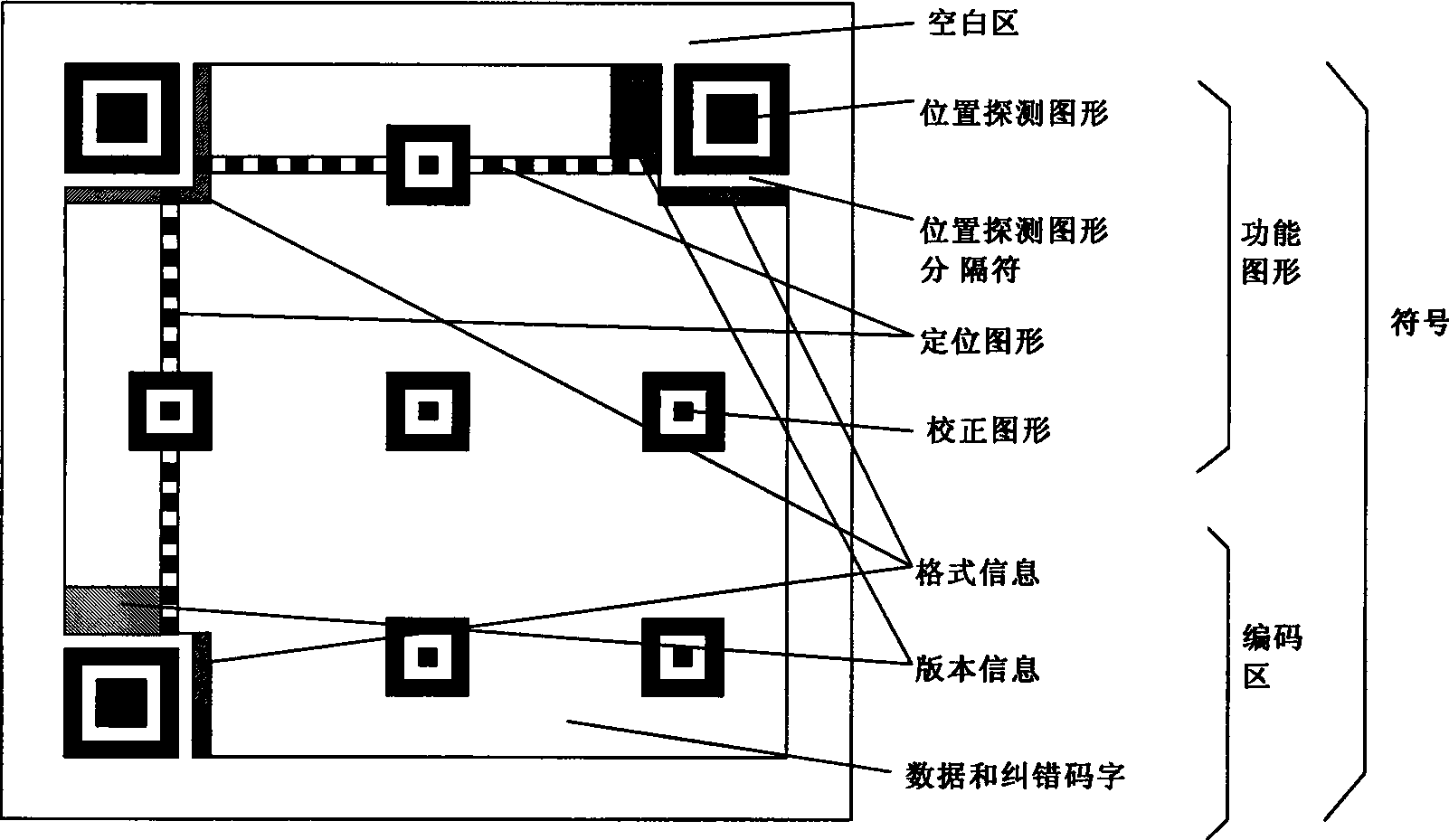
QR two-dimension bar code recognition method and system based on field programmable gate array
InactiveCN101504716AHigh resolutionImprove claritySensing by electromagnetic radiationLiquid-crystal displayReal time display
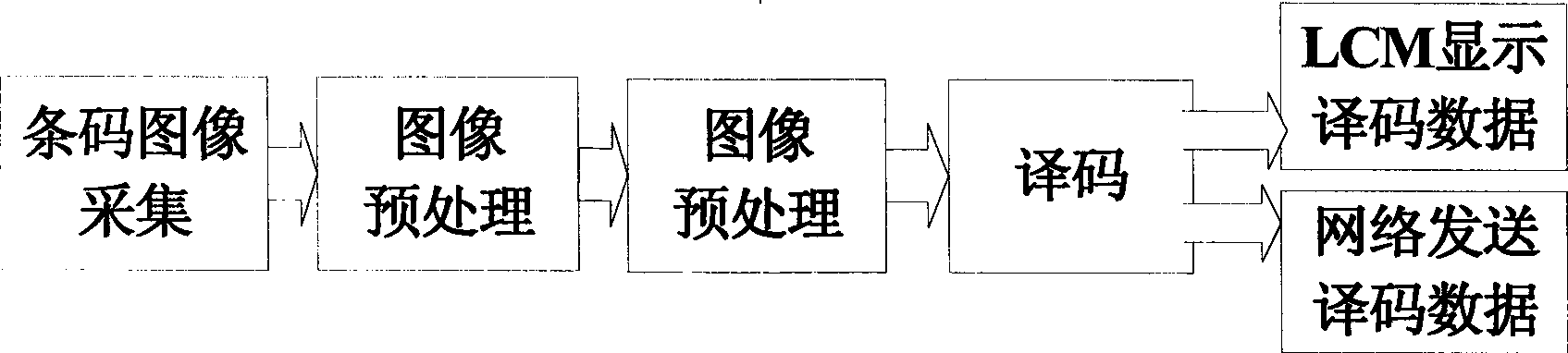
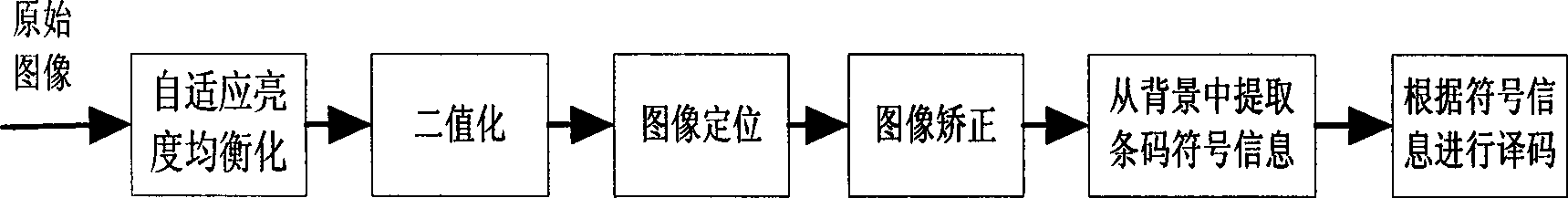
The invention provides a two-dimensional bar code recognition system based on a field programmable gate array (FPGA) and a realization method thereof. An FPGA core chip, a bar code acquisition camera and a liquid crystal display screen are adopted to construct a hardware platform of the bar code recognition system. Functions realized by the whole system comprise the acquisition of a two-dimensional bar code image, the displaying of the bar code image, the decoding of a bar code, the real-time displaying of decoding data on the liquid crystal display screen, and the sending of the decoding data through a network. The whole bar code recognition system is realized under an embedded system based on the FPGA, and provides a simple and quick symbolic information extraction method.
Owner:CHONGQING UNIV
Mobile terminal and WiFi (wireless fidelity) connection method for same
InactiveCN102883322AFirmly connectedSafe and efficient connectionConnection managementSecurity arrangementComputer moduleComputer terminal
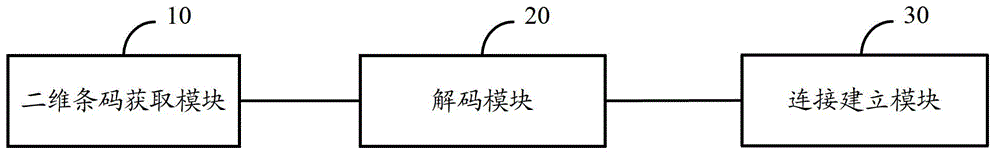
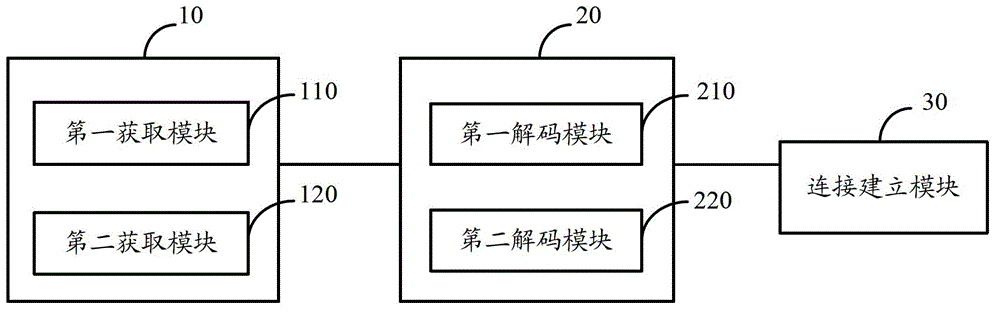
The invention discloses a mobile terminal and a WiFi (wireless fidelity) connection method for the same. The mobile terminal comprises a two-dimensional bar code acquisition module, a decoding module and a connection establishment module, wherein the two-dimensional bar code acquisition module is used for acquiring two-dimensional bar code information of WiFi connection information, the decoding module is used for decoding the two-dimensional bar code information according to preset rules and obtaining the WiFi connection information, and the connection establishment module is used for performing WiFi connection with a wireless access point according to the WiFi connection information. The mobile terminal and the WiFi connection method have the advantage that WiFi connection is facilitated, and is speedy and safe.
Owner:DONGGUAN YULONG COMM TECH +1
Method and system for loading processor boot code from serial flash memory
ActiveUS7296143B2Increase storage capacityReduce the number of partsRead-only memoriesDigital computer detailsCode acquisitionMicroBlaze
Owner:LENOVO PC INT
Data transmitter and receiver of a spread spectrum communication system using a pilot channel
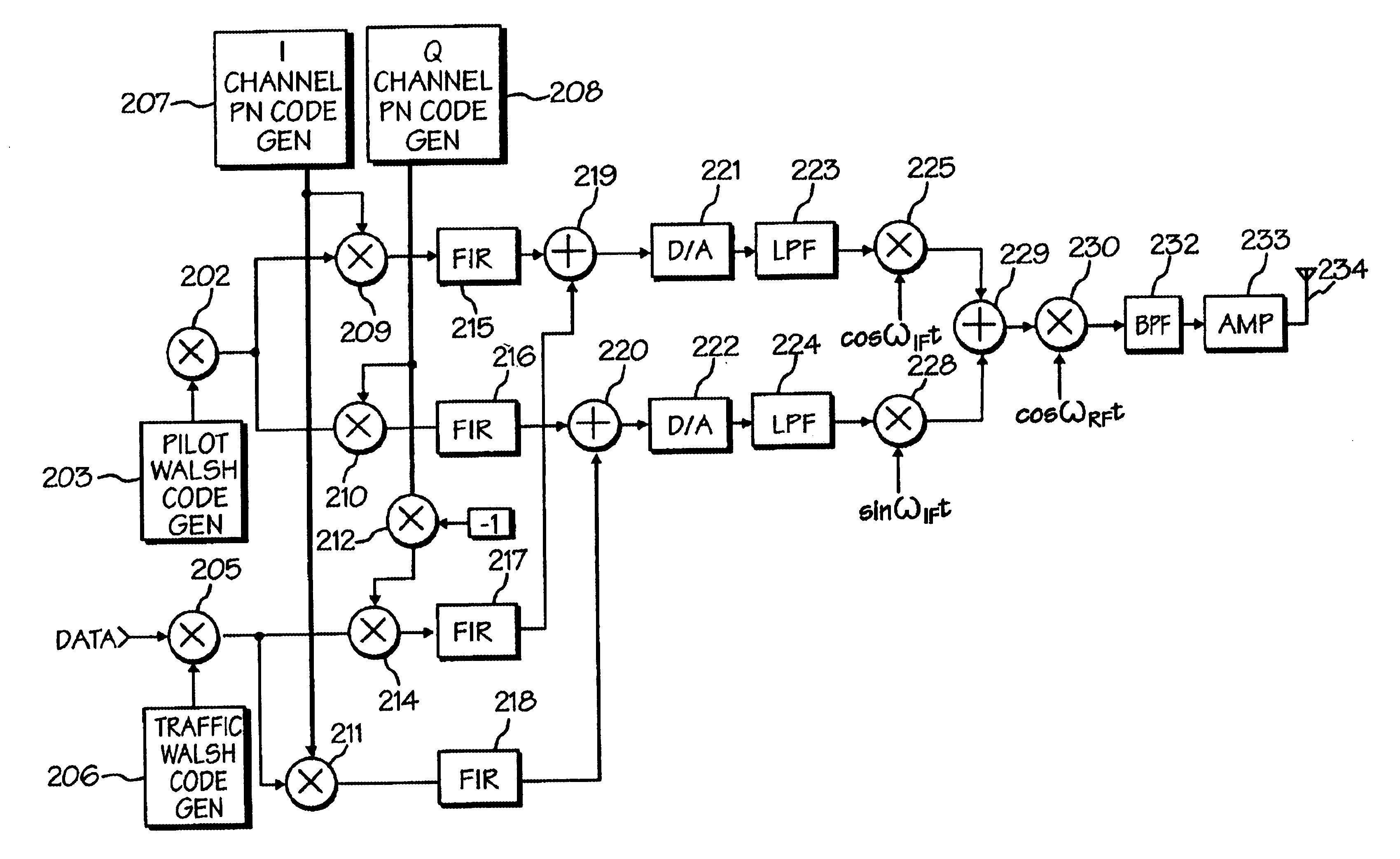
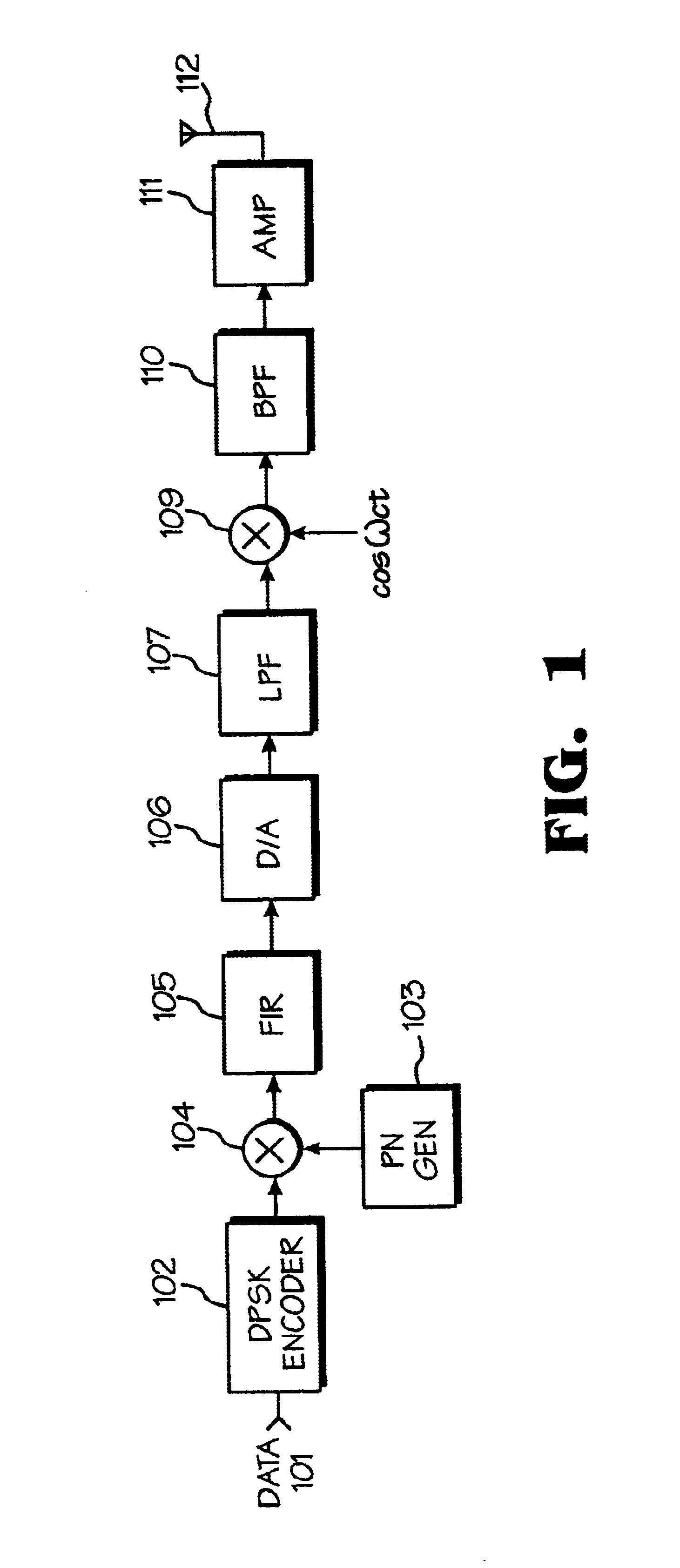
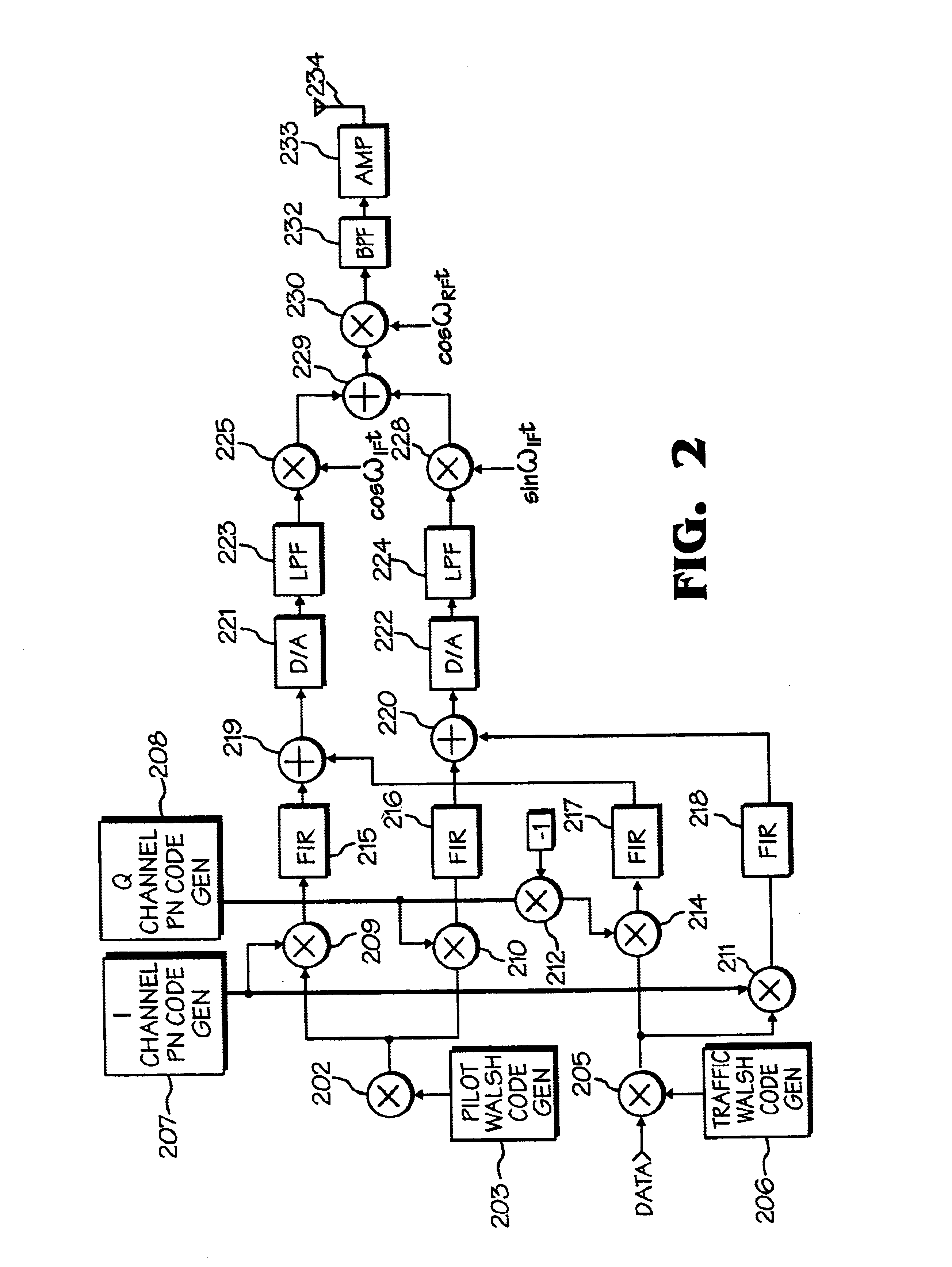
InactiveUSRE38603E1The synchronization process is simpleMinimizing PN code acquisition timeSynchronisation information channelsMultiplex code generationFinite impulse responseIntermediate frequency
An improved spread spectrum communication system includes a transmitter and a receiver utilizing a pilot channel for the transmission of pure rather than modulated PN codes for code acquisition or tracking purposes with a lower bit error rate. The pilot signal is used to obtain initial system synchronization and phase tracking of the transmitted spread spectrum signal. At the transmitter side, a Walsh code generator, a Walsh modulator, a first PN code generator, a first band spreader, a second band spreader, finite impulse response filters, digital-analog converters, low-pass filters, an intermediate frequency mixer, a carrier mixer, a band-pass filter are used to transmit a spread spectrum signal. At the receiver side, a corresponding band-pass filter, a carrier mixer, an intermediate-frequency mixer, low-pass filters, analog-digital converters, a second PN code generator, an I channel despreader, a Q channel despreader, a PN code synchronization controller, a Walsh code generator, a first Walsh demodulator, a second Walsh demodulator, accumulator & dump circuits, a combiner, and a data decider are used to demodulate a received spread spectrum signal
Owner:SAMSUNG ELECTRONICS CO LTD
Short-term burst spread spectrum signal transmitting and receiving method
The invention provides a short-term burst spread spectrum signal transmitting and receiving method which comprises the following steps of: 1) enabling unique codes and carrying data to constitute a burst spread spectrum signal frame structure, wherein the unique codes play a role of a leader sequence; and 2) enabling a receiving machine to adopt a burst signal receiving method based on differential operation, and simultaneously and quickly completing burst signal detection, PN (pseudo noise) code acquisition, frequency offset estimation, frame synchronization detection and symbol timing acquisition tasks. In the method provided by the invention, only the unique codes are used in the burst leader sequence, and the all-1 or all-0 sequence is not used, so that the transmission efficiency is improved. Simultaneously, the invention further provides a burst signal receiving method based on the differential operation, which can simultaneously and quickly complete the burst signal detection, PN code acquisition, frequency offset estimation, frame synchronization detection, symbol timing acquisition and other tasks.
Owner:SHANGHAI JIAO TONG UNIV
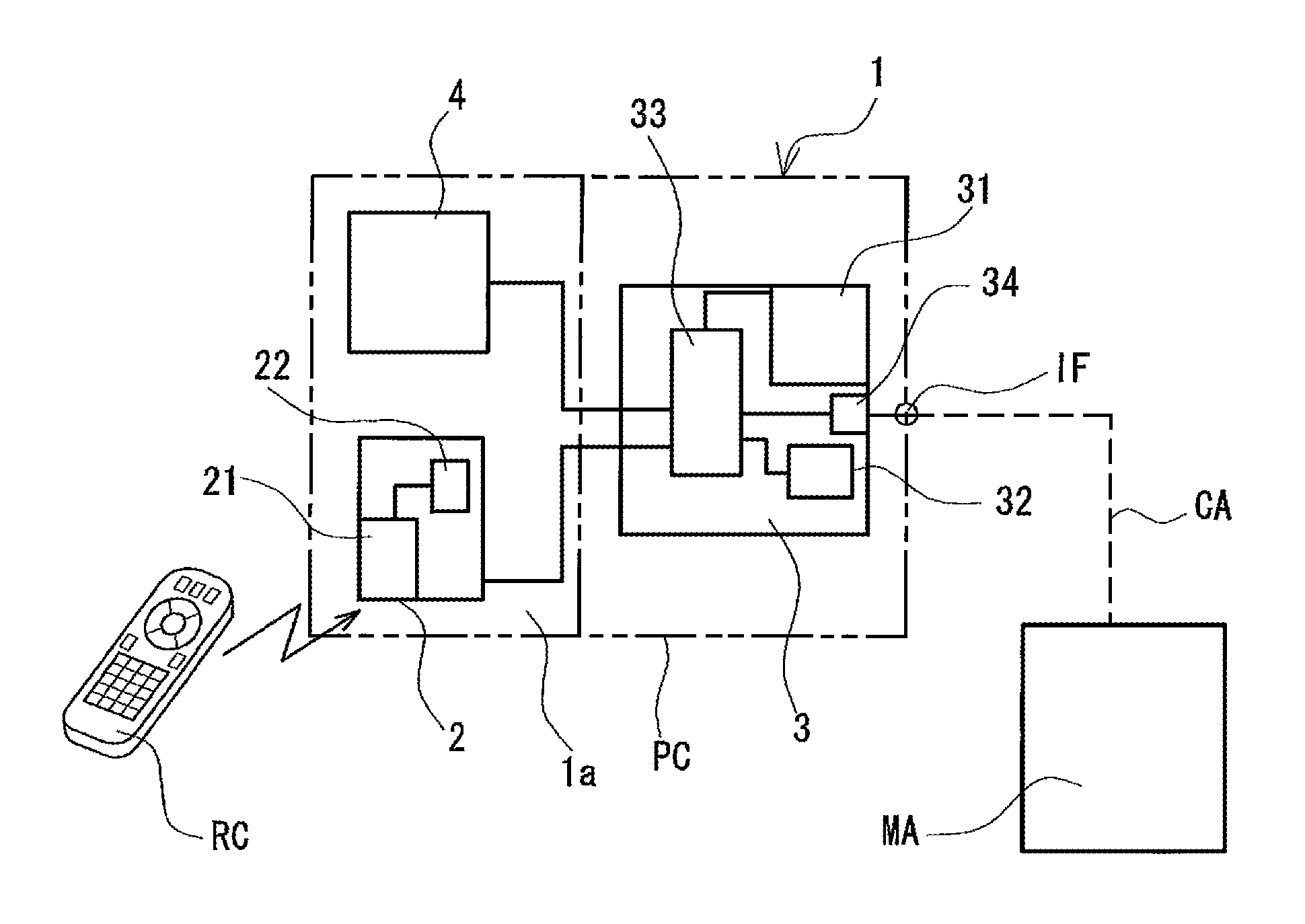
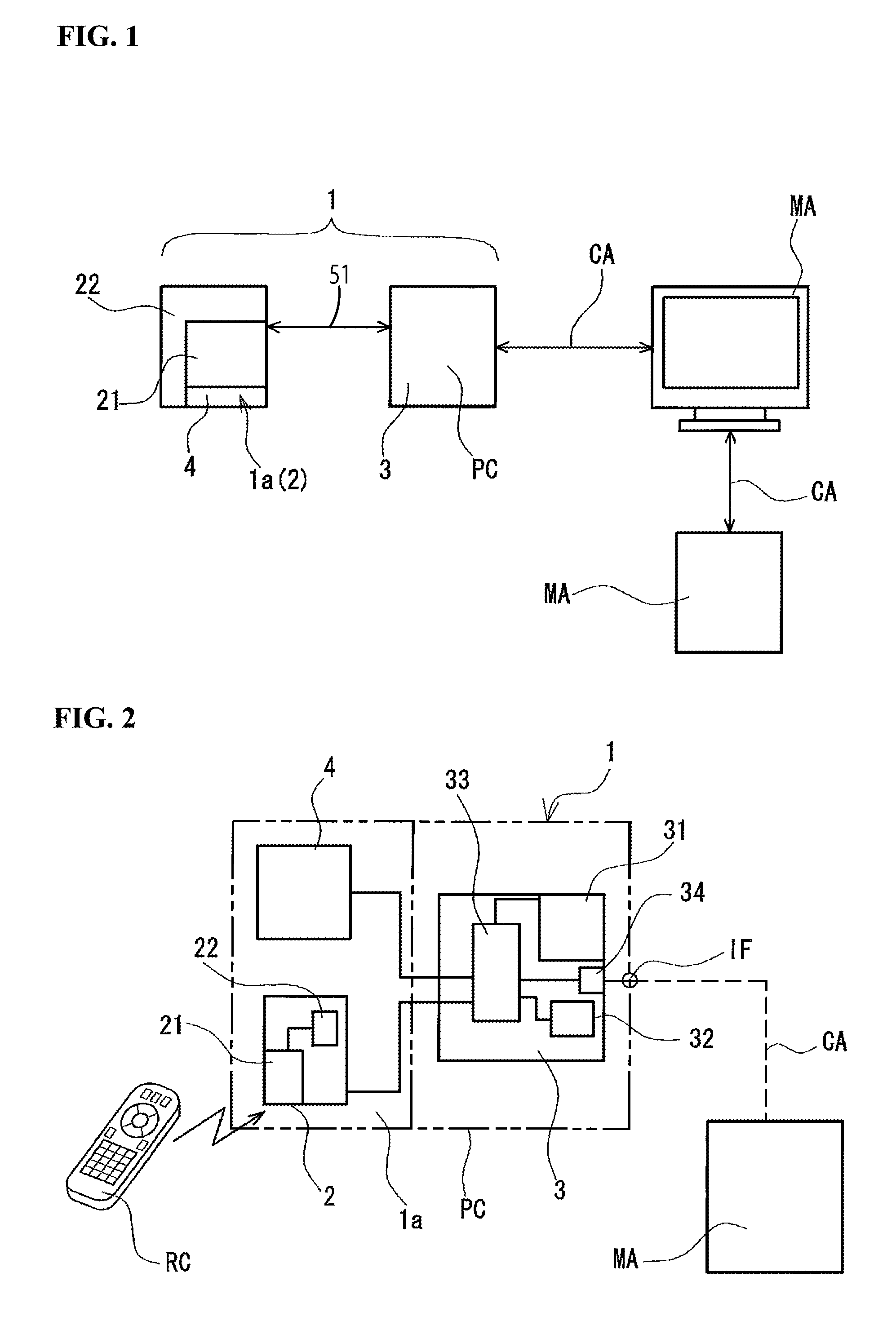
Cec control apparatus
InactiveUS20090207039A1Television system detailsTelemetry/telecontrol selection arrangementsInformation controlInstruction unit
A Consumer Electronics Control (CEC) control apparatus includes a vendor code acquisition instruction unit that queries a CEC device for a vendor code when connected to a CEC device, a control part provided with a storage unit capable of storing the reference location of stored CEC control information that corresponds to the acquired vendor code, a control information storage part which, for each vendor, pre-stores CEC control information corresponding to a plurality of vendors, and a photoreceptor unit having a received signal demodulation unit capable of receiving a signal from a remote control RC and demodulating the signal to acquire a CEC control signal. Based on the acquired vendor information, the control part acquires from the control information storage part control information corresponding to the vendor corresponding to the control signal transmitted from the remote control RC, and outputs the CEC control signal to the externally connected CEC device.
Owner:SMK CORP
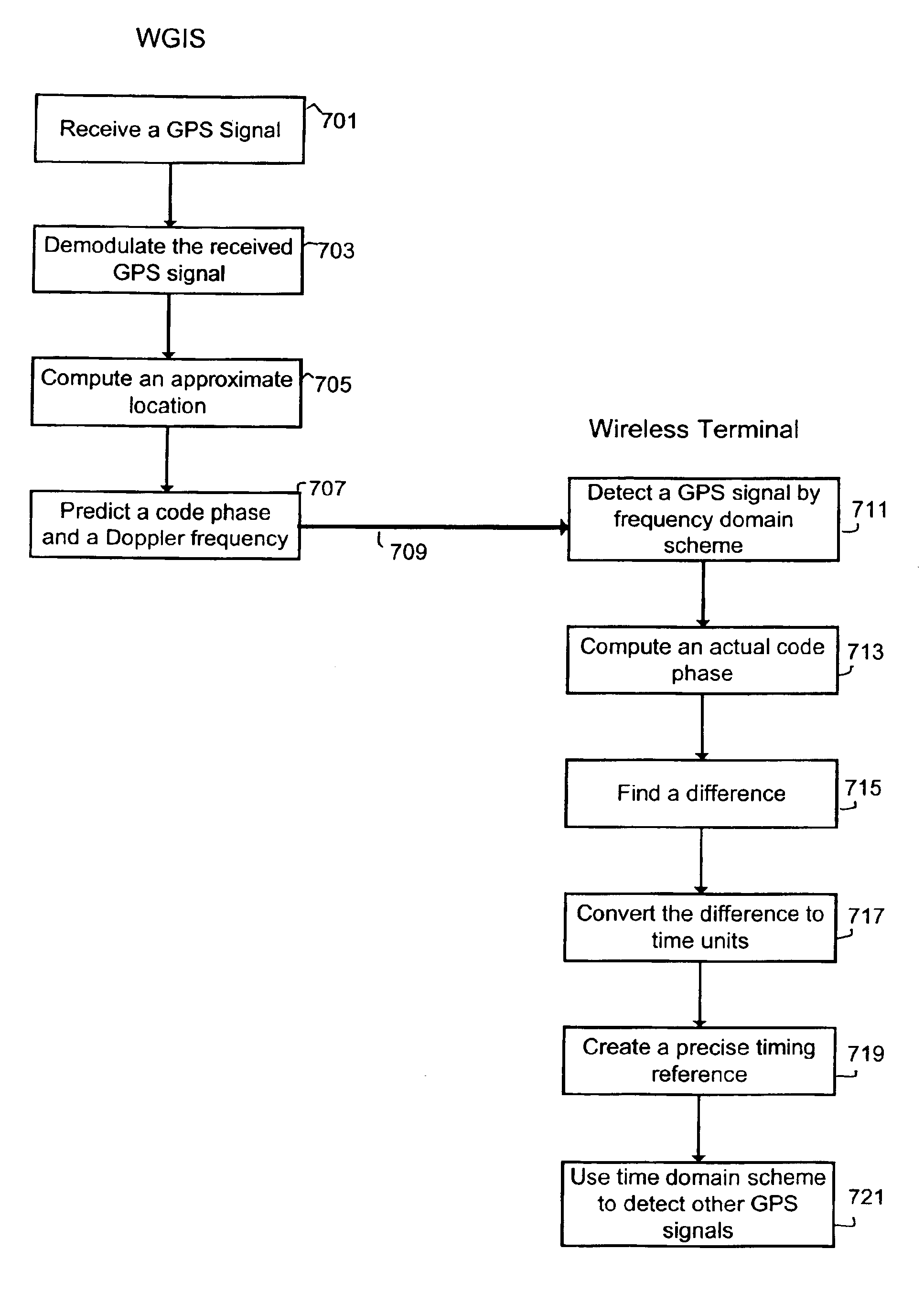
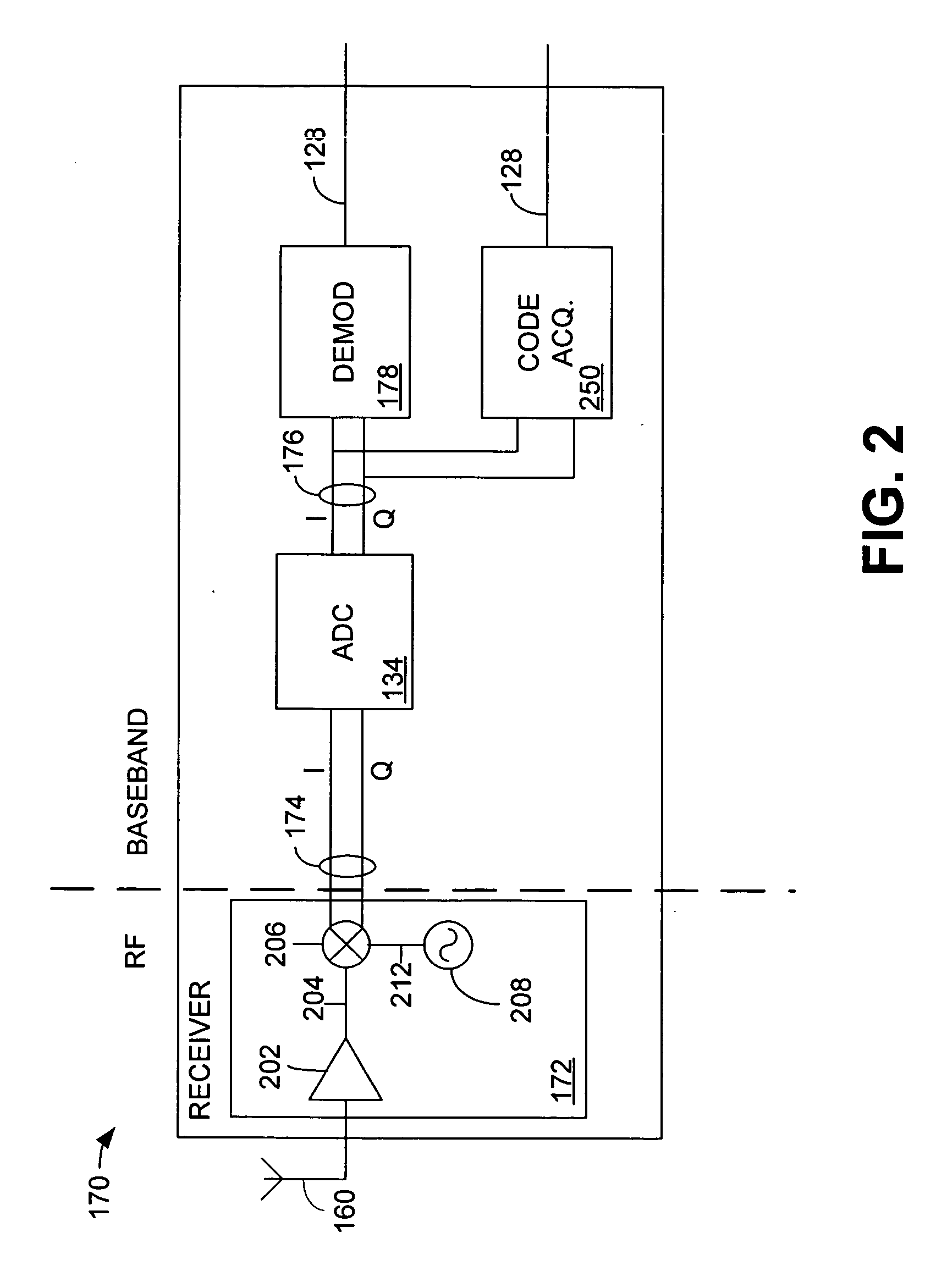
GPS signal acquisition based on frequency-domain and time-domain processing
InactiveUS6922546B1Easy accessQuick checkDirection finders using radio wavesActive radio relay systemsTime domainCommunications system
An improved code acquisition scheme for faster acquisition of GPS “coarse acquisition” (C / A) codes leads to faster detection of GPS signals, and thereby a wireless terminal may determine its position in a shorter period of time. The scheme is a combination of a frequency-domain and time-domain code acquisition techniques. The scheme utilizes a frequency-domain code acquisition technique to detect one GPS signal and to create a precise timing reference at the wireless terminal, and then utilizes time-domain code acquisition techniques to detect other GPS signals from the same satellite or other satellites faster. The scheme has the advantage of being able to be used for any wireless communications system without the requirement of maintaining a precise timing reference in the wireless terminals, and without the requirement of heavy computational resources that are usually needed in systems that utilize frequency-domain code acquisition techniques.
Owner:ALCATEL-LUCENT USA INC
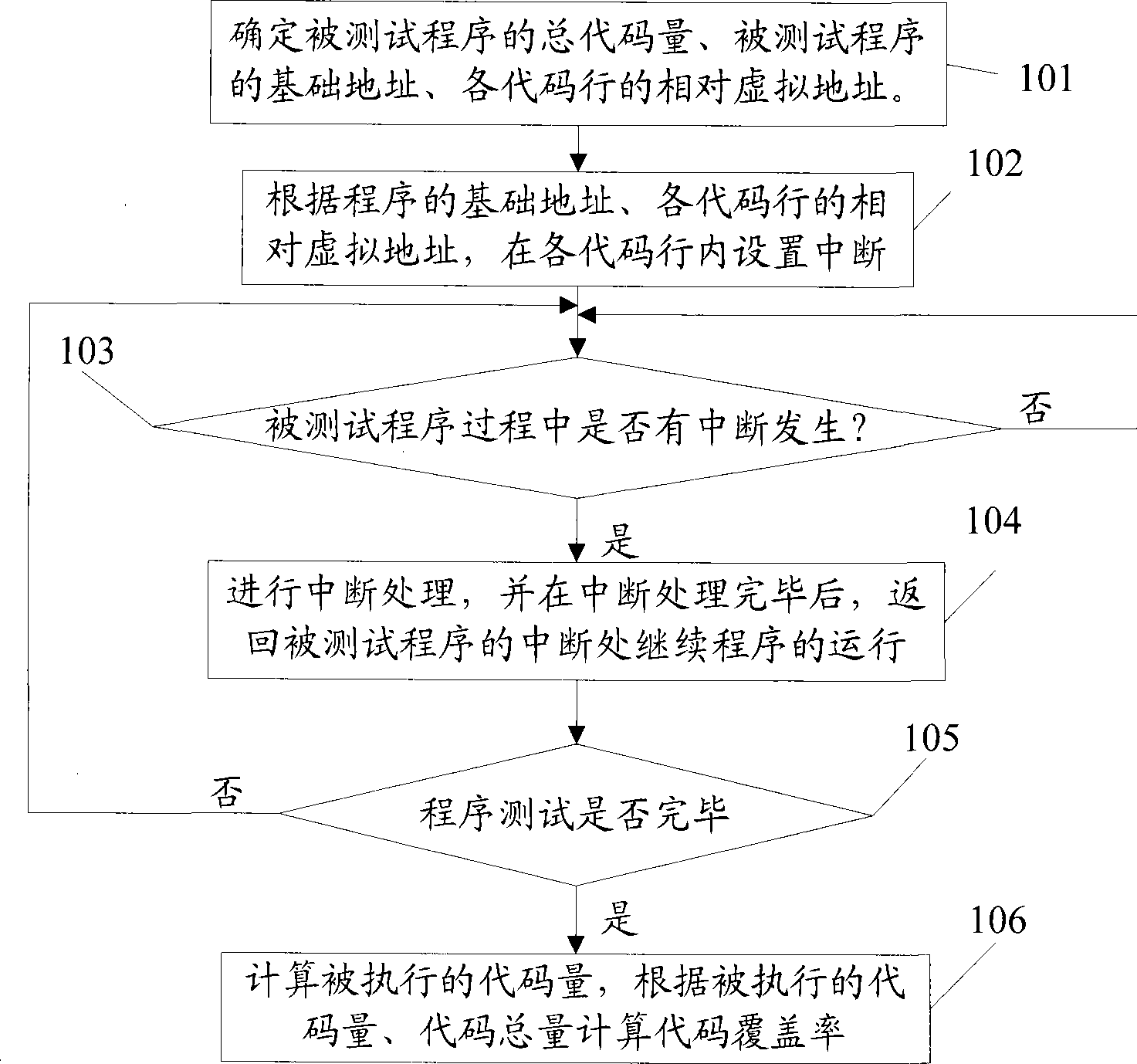
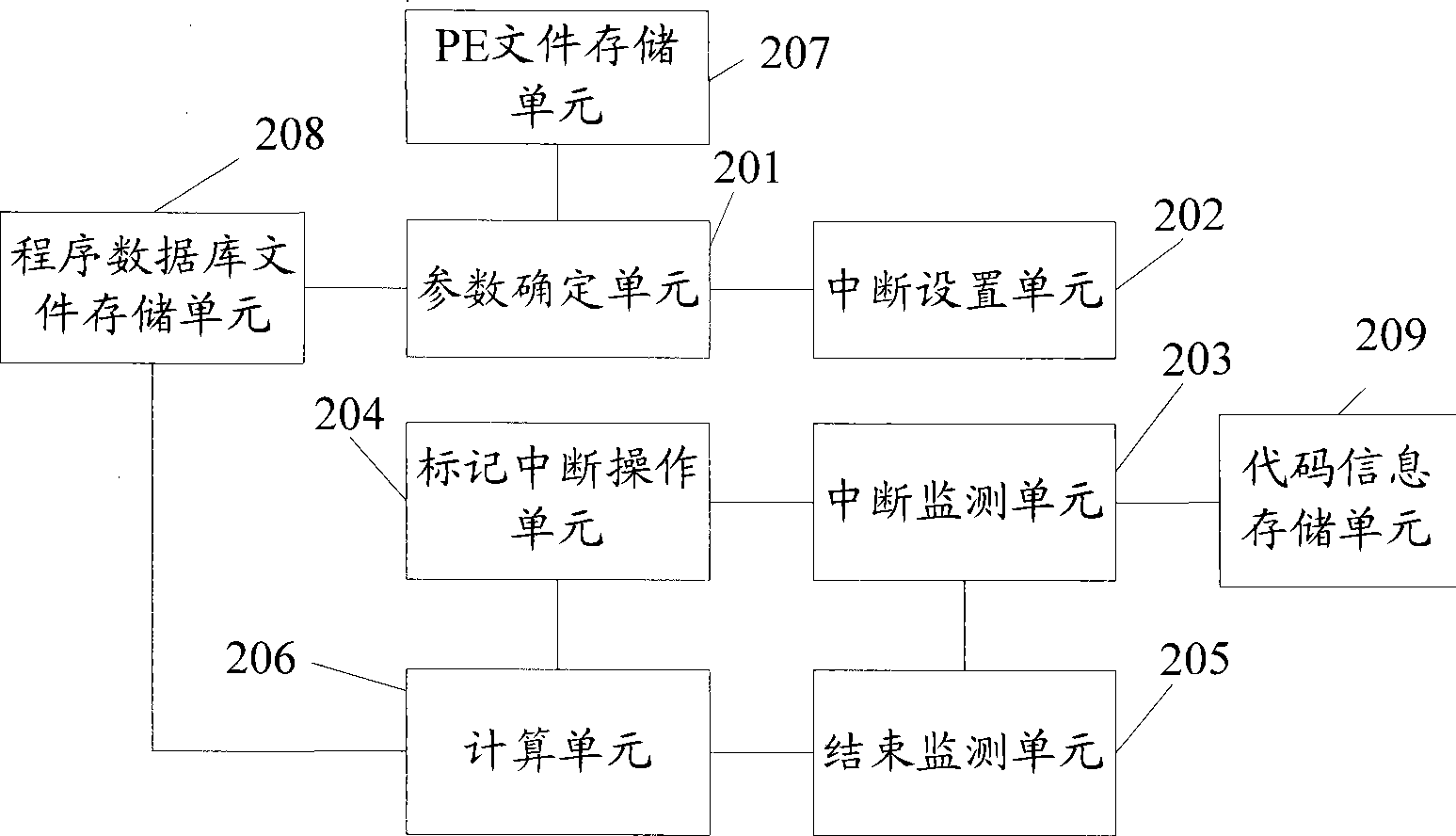
Method and test device for confirming code coverage rate
ActiveCN101464829AGuaranteed stabilityGet detailsSoftware testing/debuggingCode coverageTest fixture
The invention relates to the computer field. The embodiment of the invention discloses a method for confirming code coverage and a test method thereof. The test method comprises the following steps: confirming the total code amount and the basic address of a tested program, as well as relative virtual addresses of all code lines; setting interruption in the code lines according to the basic address and the virtual addresses of the code lines; detecting whether interruption takes place in the process of the tested program, if yes, marking the code line the interruption belongs; detecting whether the test is completed, if no, returning to the step of detecting whether interruption takes place, and if yes, accumulating marked total code in the code lines to acquire executed total code amount; and obtaining the code coverage of a tested program according to the executed total code amount and the total code amount thereof. By adopting the technical scheme of the embodiment of the invention, the code coverage of the tested program can be accurately obtained and the stability of the tested program can be guaranteed.
Owner:ZHUHAI KINGSOFT SOFTWARE CO LTD
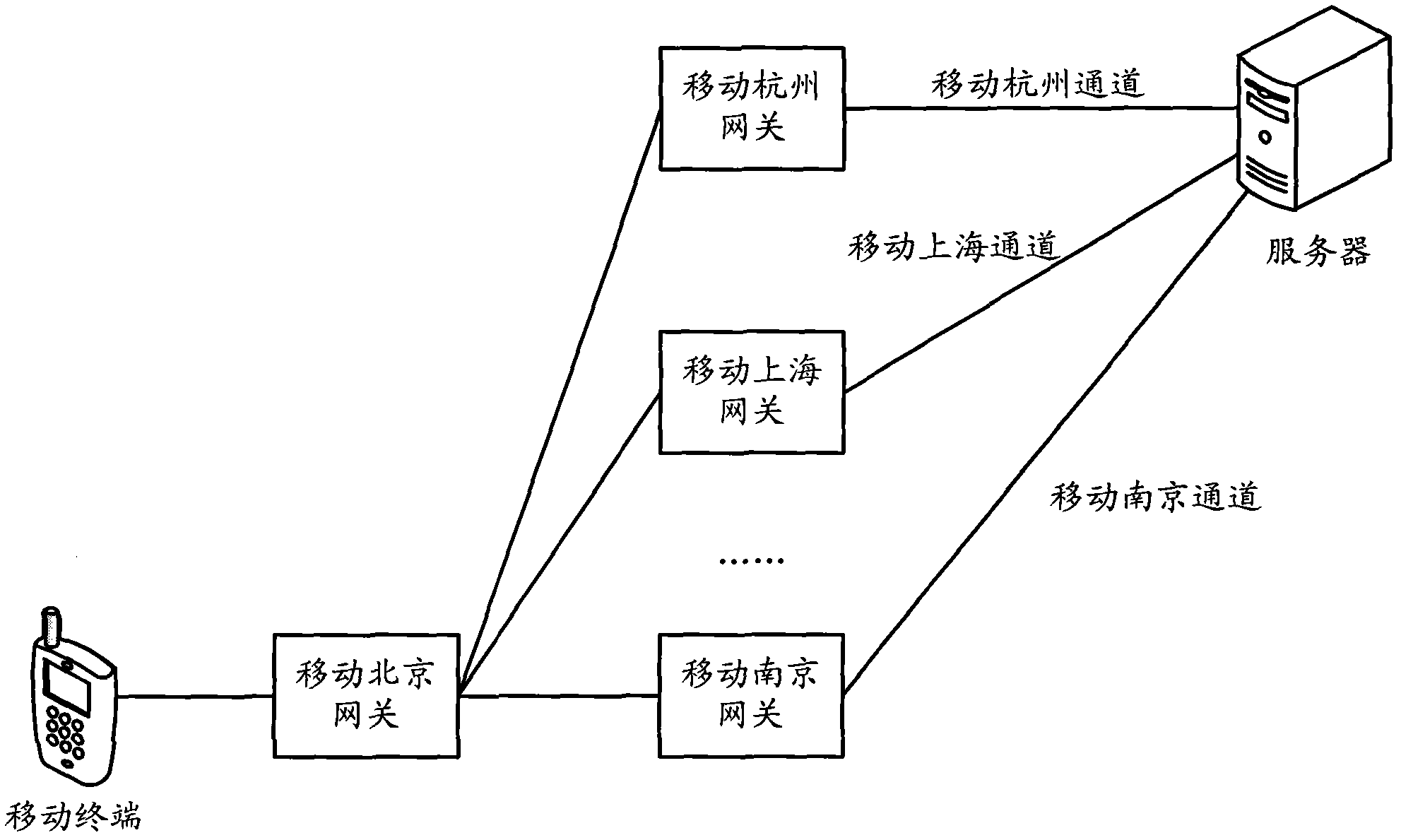
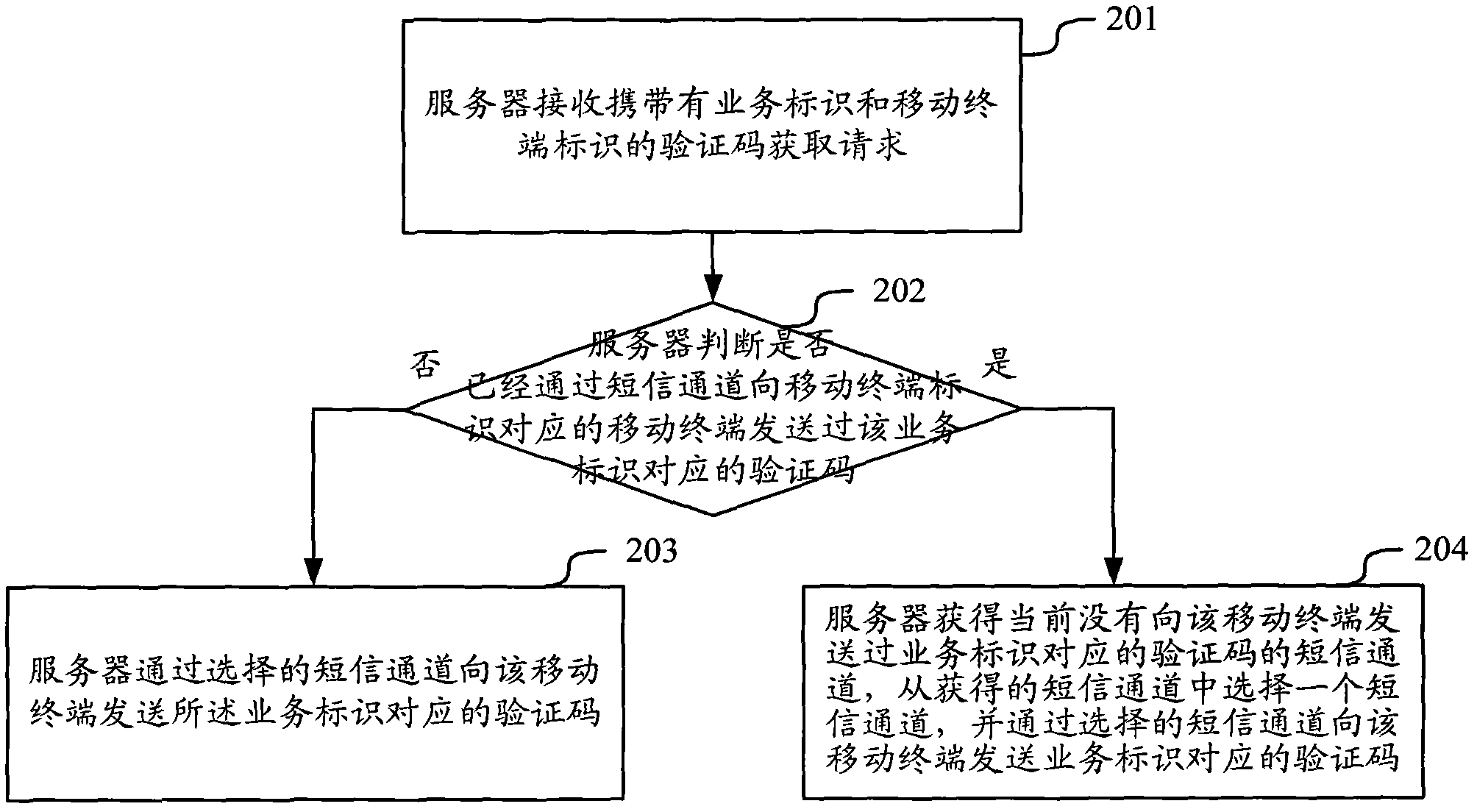
Method and device for transmitting verification codes via short messages
ActiveCN103002415AIncrease reachReduce the number of interactionsMessaging/mailboxes/announcementsComputer hardwareCode acquisition
The invention discloses a method and a device for transmitting verification codes via short messages. The method includes that a server receives a verification code acquisition request carried with service identification and mobile terminal identification; the server judges whether a verification code corresponding to the service identification is previously transmitted to a mobile terminal via a short message channel or not, and the mobile terminal corresponds to the mobile terminal identification; the server transmits the verification code corresponding to the service identification to the mobile terminal via a selected short message channel if the verification code is not previously transmitted to the mobile terminal; and the server acquires short message channels which do not previously transmit the verification code corresponding to the service identification to the mobile terminal, selects a short message channel from the acquired short message channels and transmits the verification code corresponding to the service identification to the mobile terminal via the selected short message channel. The method has the advantage that the short message arrival rate can be increased when the verification codes are transmitted via the short messages.
Owner:ALIBABA GRP HLDG LTD
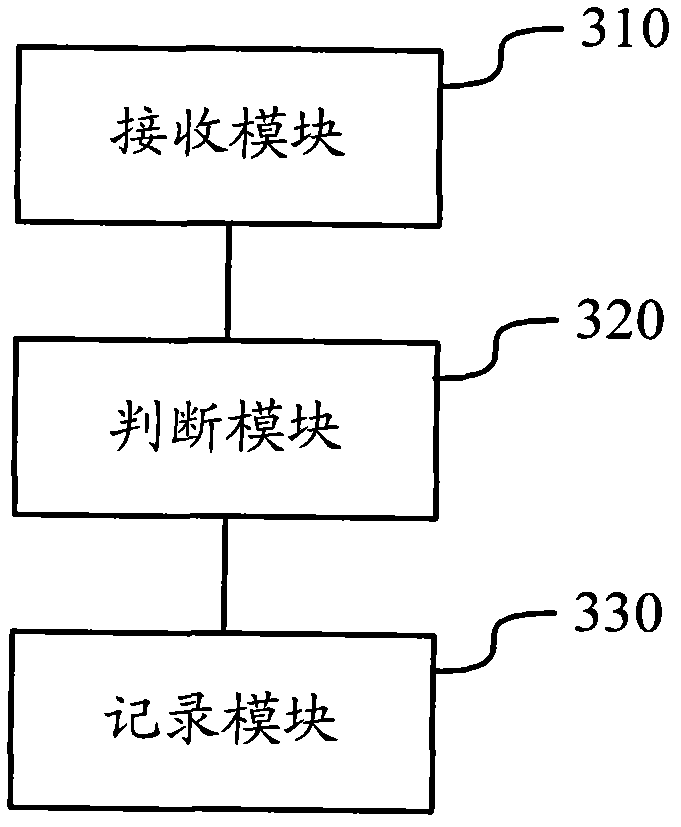
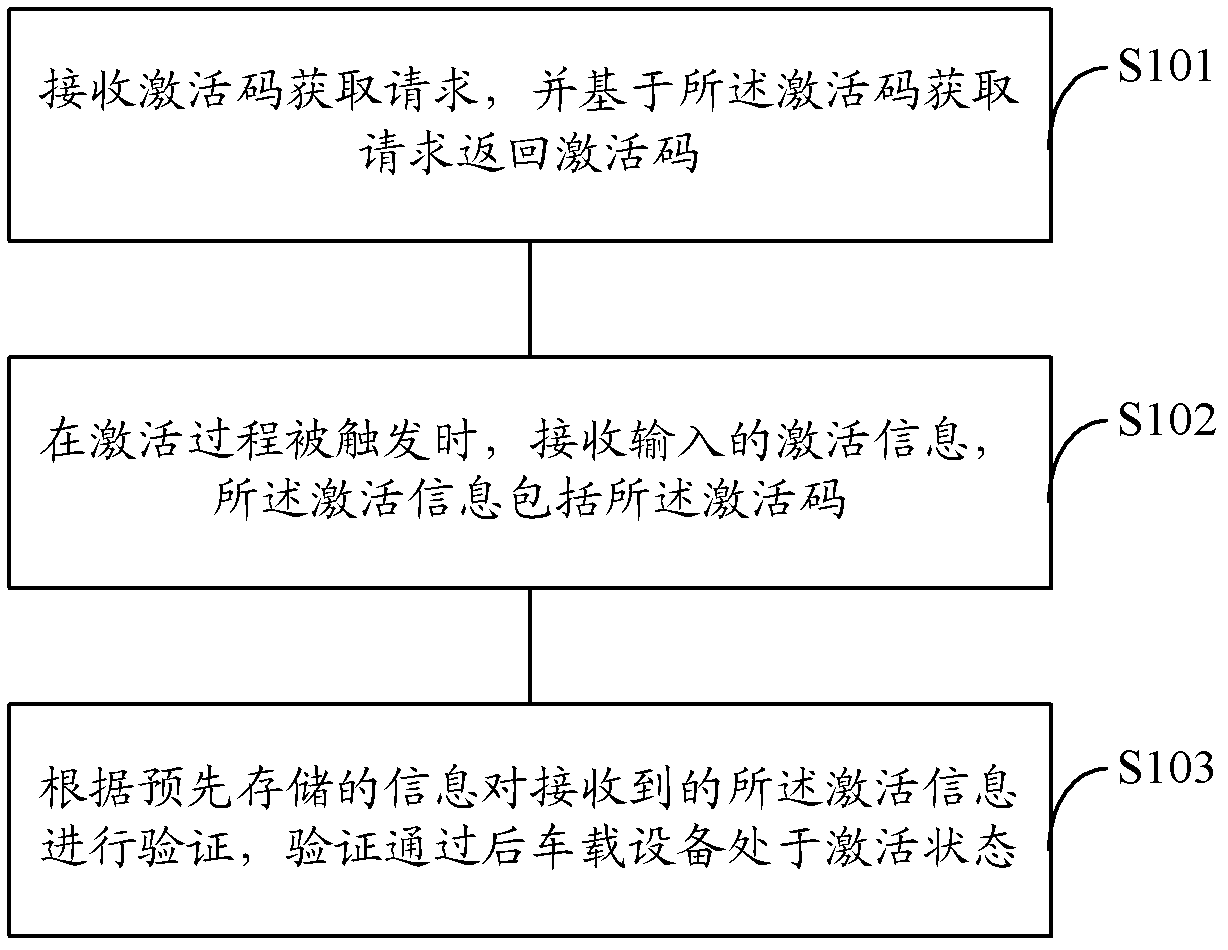
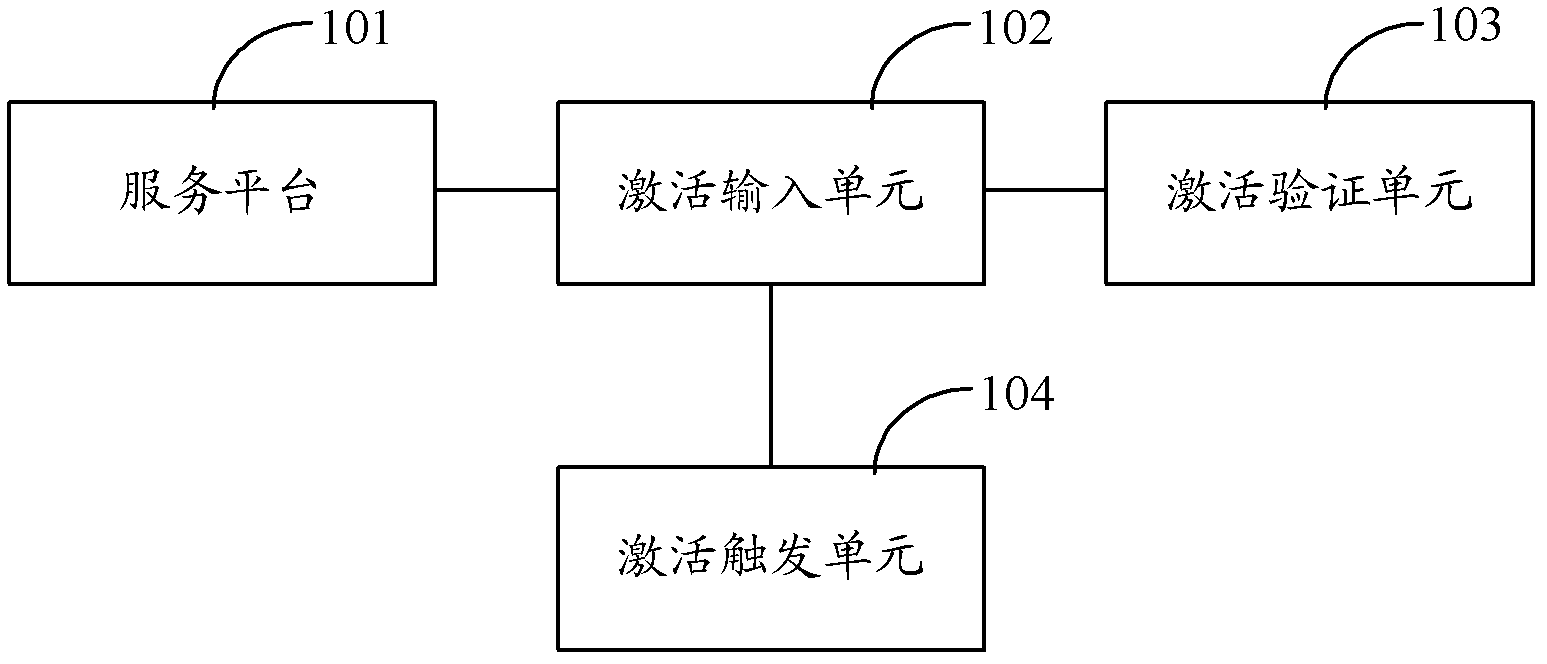
Activation method and activation system for vehicle-mounted equipment
ActiveCN103029648AEfficient activationPromote activationElectric/fluid circuitActivation methodBiological activation
The invention discloses an activation method and an activation system for vehicle-mounted equipment. According to the activation method, an activation code acquisition request is received, and an activation code is returned based on the activation code acquisition request; when an activation process is triggered, input activation information is received, and the activation information comprises the activation code; the received activation information is verified according to pre-stored information, and after the verification is passed, the vehicle-mounted equipment is in an activation state. The activation method and the activation system for the vehicle-mounted equipment can activate the vehicle-mounted equipment efficiently and conveniently, and achieves starting of the vehicle-mounted equipment and effective management of replacement.
Owner:SHANGHAI PATEO INTERNET TECH SERVICE CO LTD
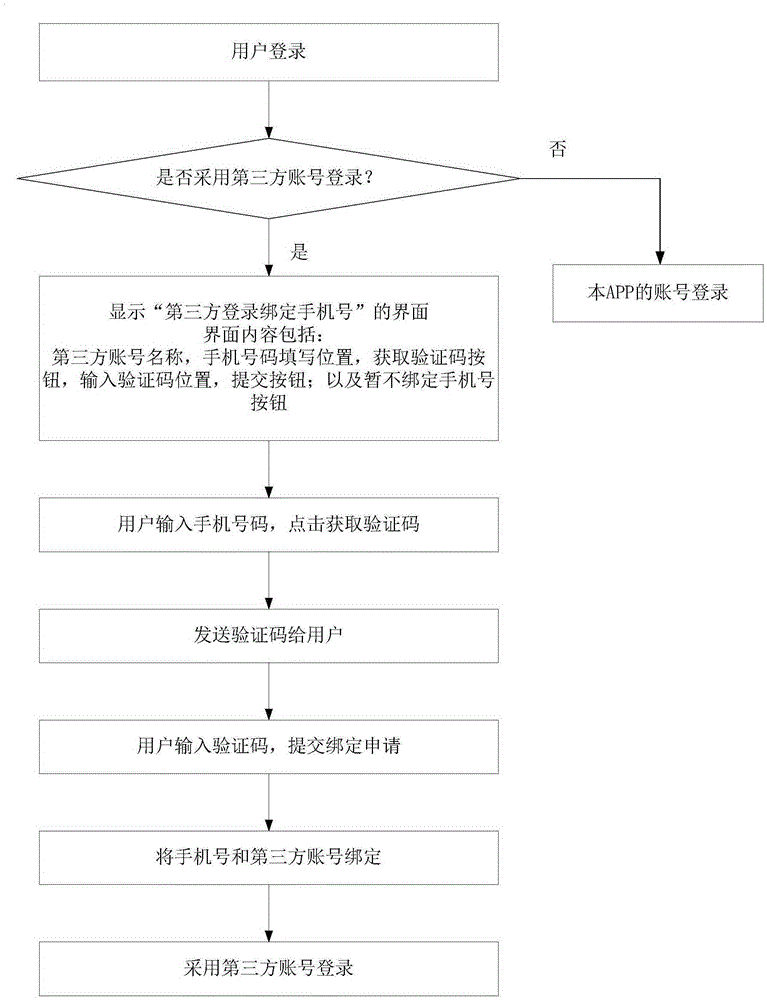
Third-party login mobile phone number binding method based on mobile phone APP
ActiveCN105306733AAvoid damageTelephone sets with user guidance/featuresTransmissionThird partyPassword
The invention relates to an APP login method, and specifically relates to a third-party login mobile phone number binding method based on a mobile phone APP. The method provided by the invention comprises the following steps that: a login request of a client is received and an option is returned back, wherein the option is whether to log in with a third-party account or not; when a user selects to log in with the third-party account, the client enters into a third-party login mobile phone number binding page; after the client clicks a verification code acquisition button, a server automatically generates a verification code and transmits the verification code to a mobile phone number; after the verification code is received by the mobile phone number, the verification code is input through a verification code input position of the client, and then, the verification code is submitted. In method provided by the invention, a step of binding the mobile phone number is added before logging in of the third-party account in the existing technical scheme, thus, the method solves a technical problem of failure in logging in to the APP with the third-party account again caused by forgetting the third-party account or forgetting passwords of the third-party account after logging in with the third-party account.
Owner:SHENZHEN GENUINE INNOVATIVE TECH CO LTD
Two-dimensional code management system for online products on production line
InactiveCN103049828AEffective associationSimple structureResourcesSensing by electromagnetic radiationProduction lineComputer module
The invention discloses a two-dimensional code management system for online products on a production line, which comprises a product tagging module, a two-dimensional code acquisition module and a server, wherein the product tagging module is used for giving each product a unique two-dimensional code identity in a code spraying, code adhering and laser code printing manner; the server is used for carrying out decoding analysis on two-dimensional code images and carrying out related management on two-dimensional code values and product information; the product tagging module and the two-dimensional code acquisition module are sequentially arranged along the movement direction of a conveying belt of the production line; and the product tagging module and the two-dimensional code acquisition module are respectively connected with the server. The two-dimensional code management system is characterized in that the two-dimensional code management system can be implemented by carrying out small-scale reconstruction on an existing production line, has high automation degree and has a simple structure.
Owner:GUANGZHOU WIDTH INFORMATION TECH
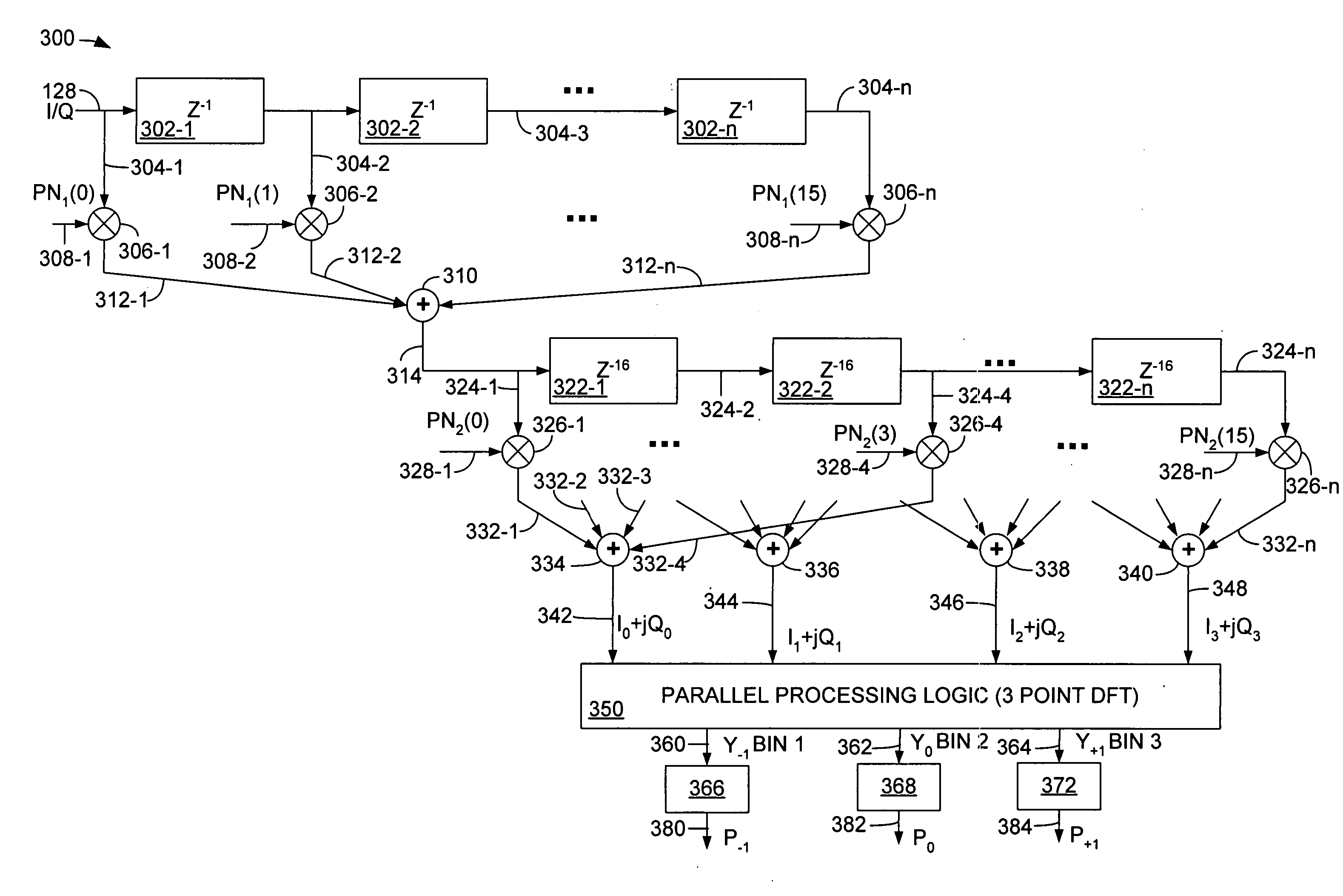
Multiple simultaneous frequency and code acquisition for a code division multiple access (CDMA) communication system
ActiveUS20050238087A1Reduce process complexityLow costDigital technique networkAmplitude-modulated carrier systemsCommunications systemParallel processing
A multiple stage matched filter for a wireless receiver comprises a receiver configured to develop a received signal, the received signal comprising a bit stream of signal samples, and a multiple stage matched filter configured to parallel process the received signal such that multiple codes are analyzed simultaneously to determine a frequency offset and code location.
Owner:MEDIATEK INC
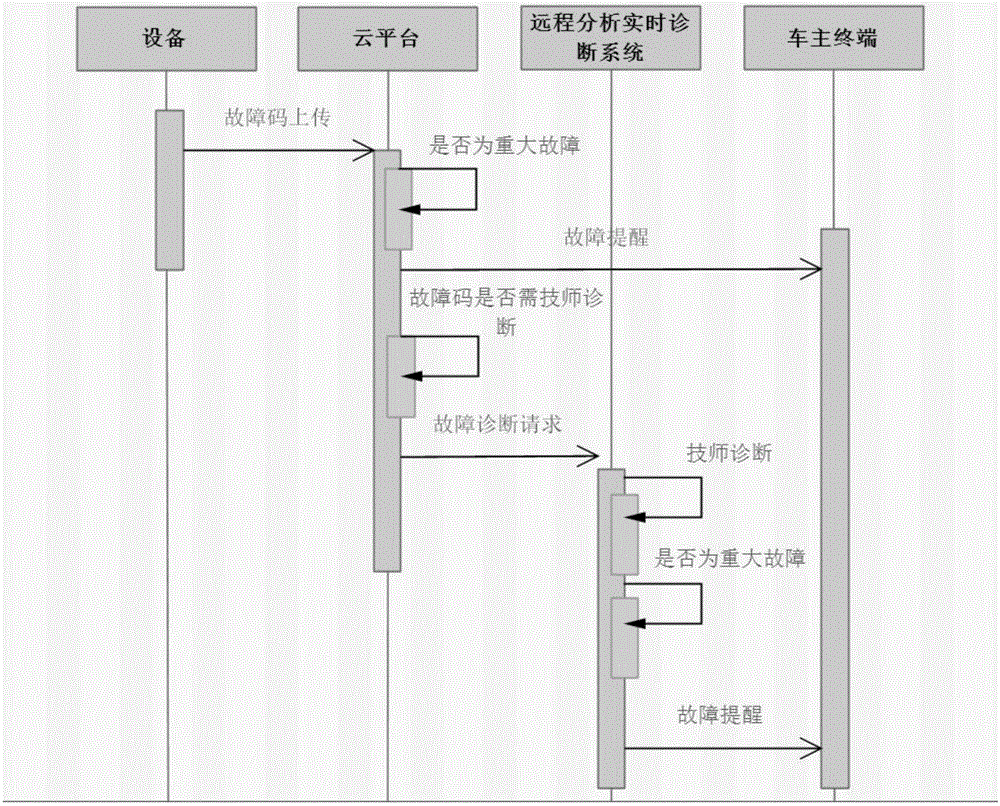
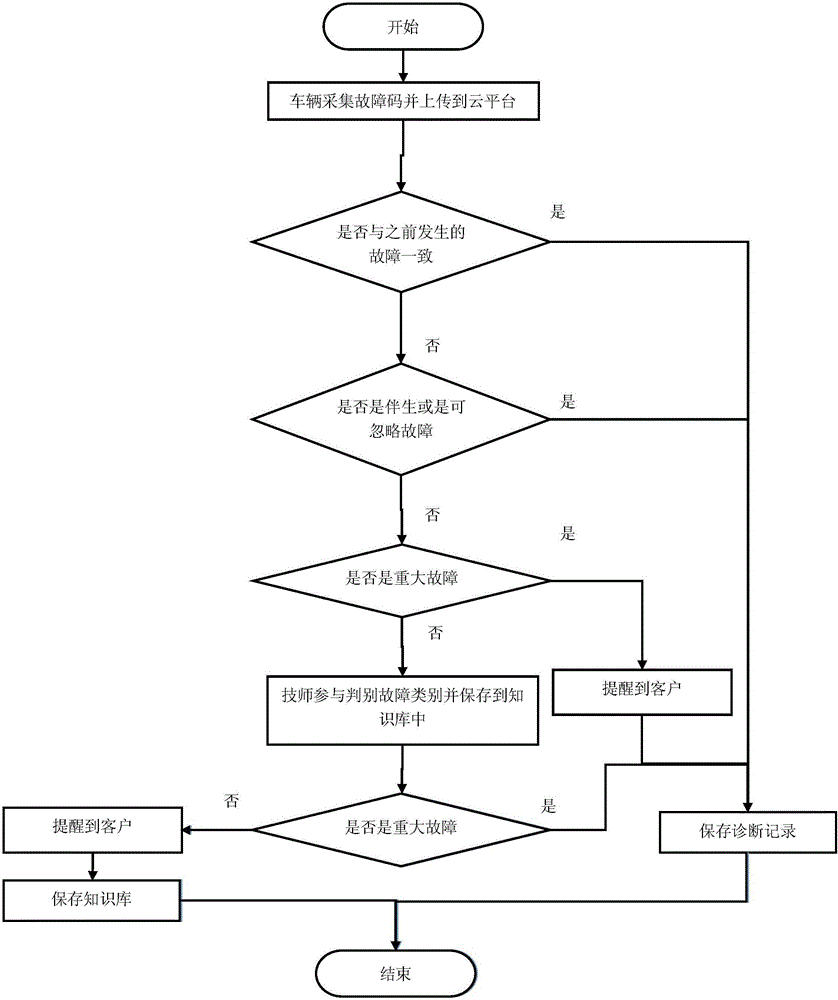
Vehicle fault code real-time acquisition and historical data analysis and diagnosis method and device
ActiveCN105867351AReal-timeRealize upload storageProgramme controlElectric testing/monitoringData acquisitionData store
The invention provides a vehicle fault code real-time acquisition and historical data analysis and diagnosis method and device and belongs to the field of fault code acquisition. The method and device solve the problem about classified warning. The method is characterized by including the steps that each time a vehicle is started, a device collects a fault code, the device collects the fault code on the vehicle in real time, the fault code is uploaded to a cloud platform by a mobile communication network, the cloud platform receives fault code data, the fault code data is stored in a database, the cloud platform combines fault data uploaded last time and stored historical fault data for big data analysis, faults obtained by analyzing and diagnosing the fault code data are classified, and fault reminding is decided according to classification. The method has the effects that warning decisions are determined according to classification, and the phenomenon that warning creditability is reduced because of all warnings can be avoided.
Owner:DALIAN ROILAND SCI & TECH CO LTD
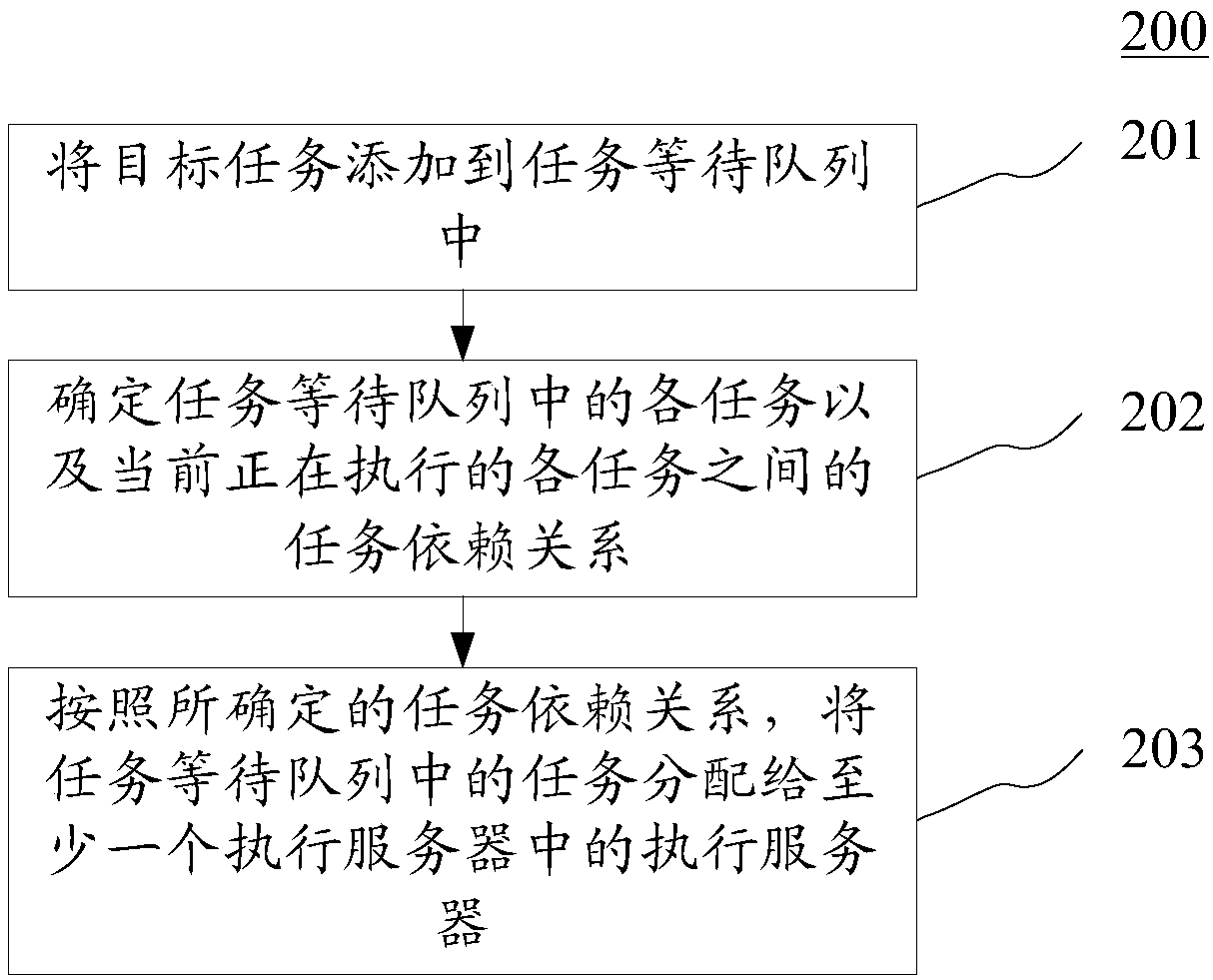
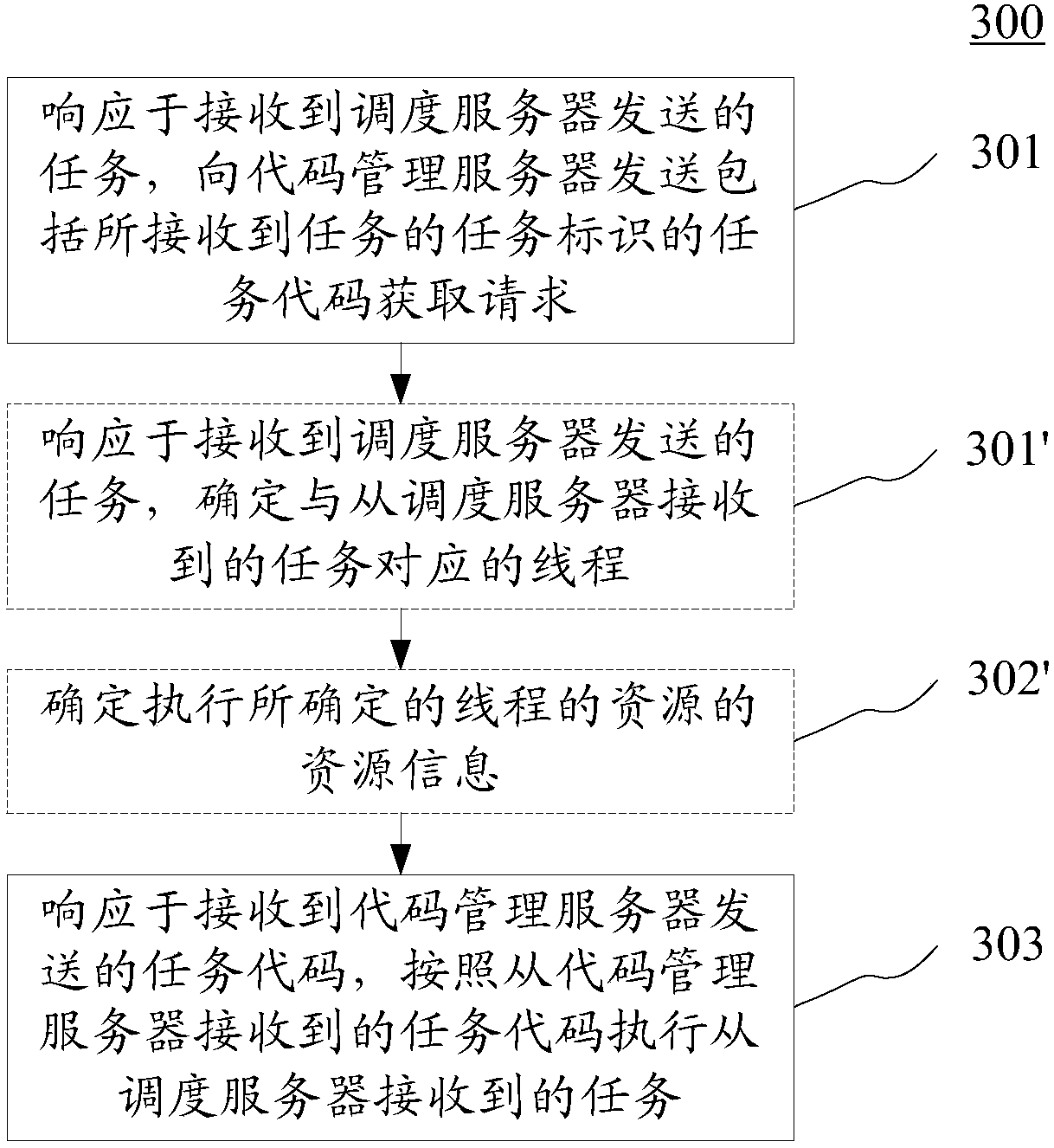
Task scheduling system, method and device
ActiveCN108182111AImprove versatilityAchieve horizontal expansionProgram initiation/switchingResource allocationOperating systemCode acquisition
The embodiment of the invention discloses a task scheduling system, method and device. The task scheduling system comprises a scheduling server, at least one execution server and a code management server, wherein the scheduling server is used for determining task dependence relations between all tasks which are currently in execution and all tasks in a task waiting queue, and according to the determined task dependence relations, the tasks in the task waiting queue are distributed to the execution servers; the execution servers receive the tasks sent by the scheduling server and then sends task code acquiring requests to the code management server, and according to task codes received from the code management server, tasks received from the scheduling server are executed; the code management server is in response to the received task code acquiring requests sent by the execution servers, and then the task codes corresponding to the task code acquiring requests are sent to the executionservers which send the task code acquiring requests. In this way, the universality and horizontal scaling of the task scheduling system are achieved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
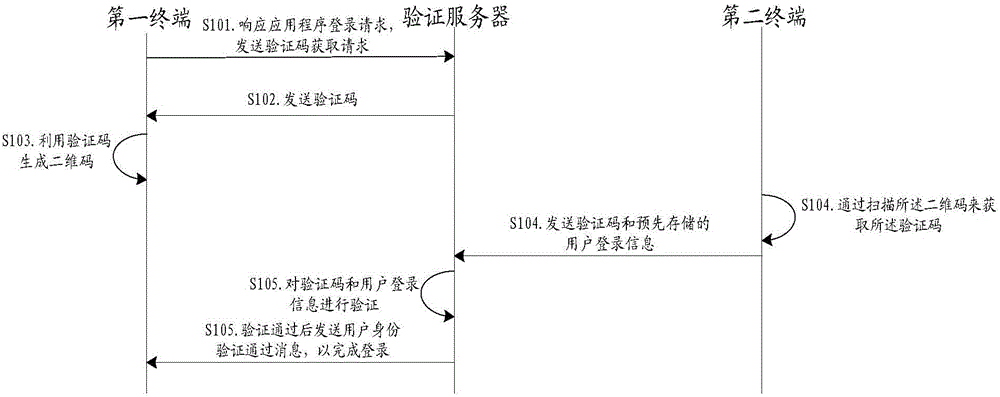
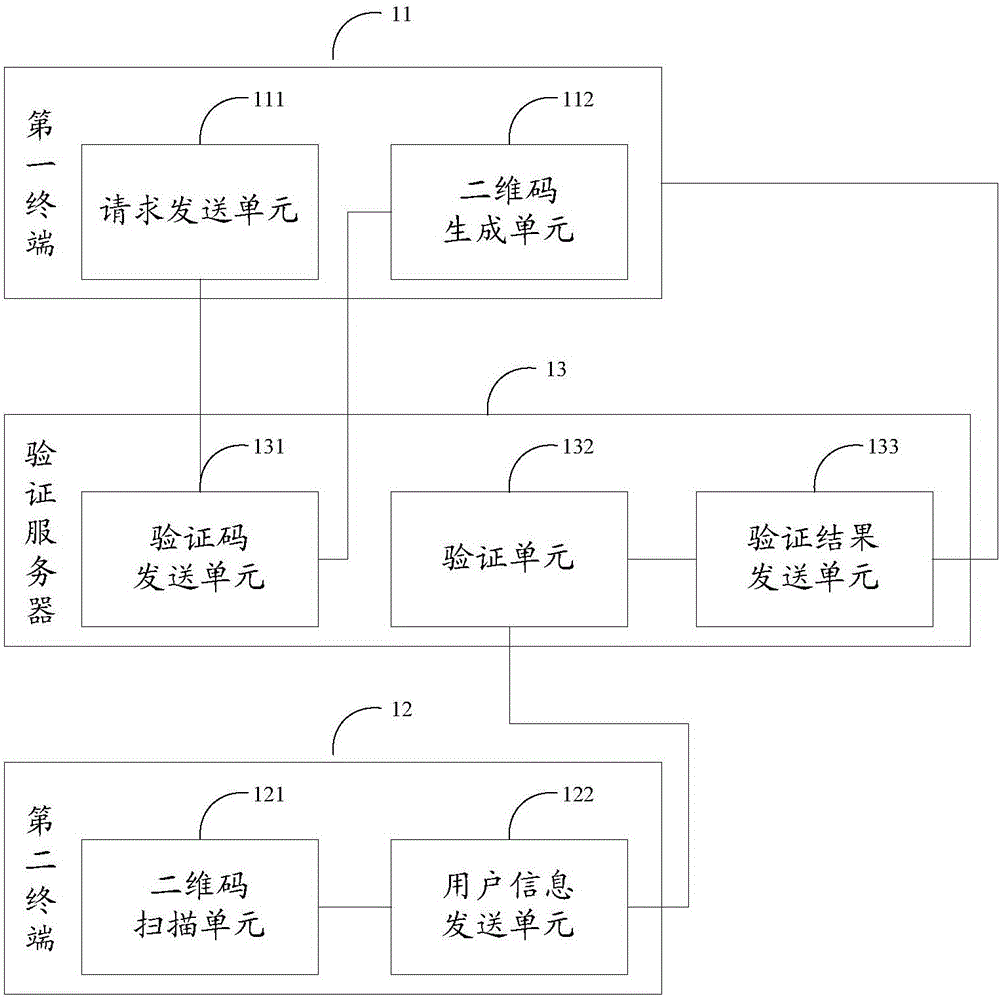
Logging-in method and system
ActiveCN106209763AImprove experienceImprove login efficiencyTransmissionDimensional modelingUser authentication
The embodiment of the invention discloses a logging-in method and system, and improves logging-in efficiency and user experience. The method comprises the steps that: in response to a triggered application logging-in request, a first terminal sends a verification code acquisition request to a verification server; the verification server sends a verification code to the first terminal according to the verification code acquisition request; the first terminal generates a two-dimensional code by utilizing the verification code and displays the two-dimensional code; a second terminal acquires the verification code by scanning the two-dimensional code, and sends the verification code and user logging-in information pre-stored in the second terminal to the verification server, wherein the user logging-in information corresponds to an application; and the verification server verifies the verification code and the user logging-in information from the second terminal, and sends a user identity verification passed message to the first terminal after verification on both the verification code and the user logging-in information is passed, so that logging-in on the application is completed.
Owner:BEIJING AMAZGAME AGE INTERNET TECH CO LTD
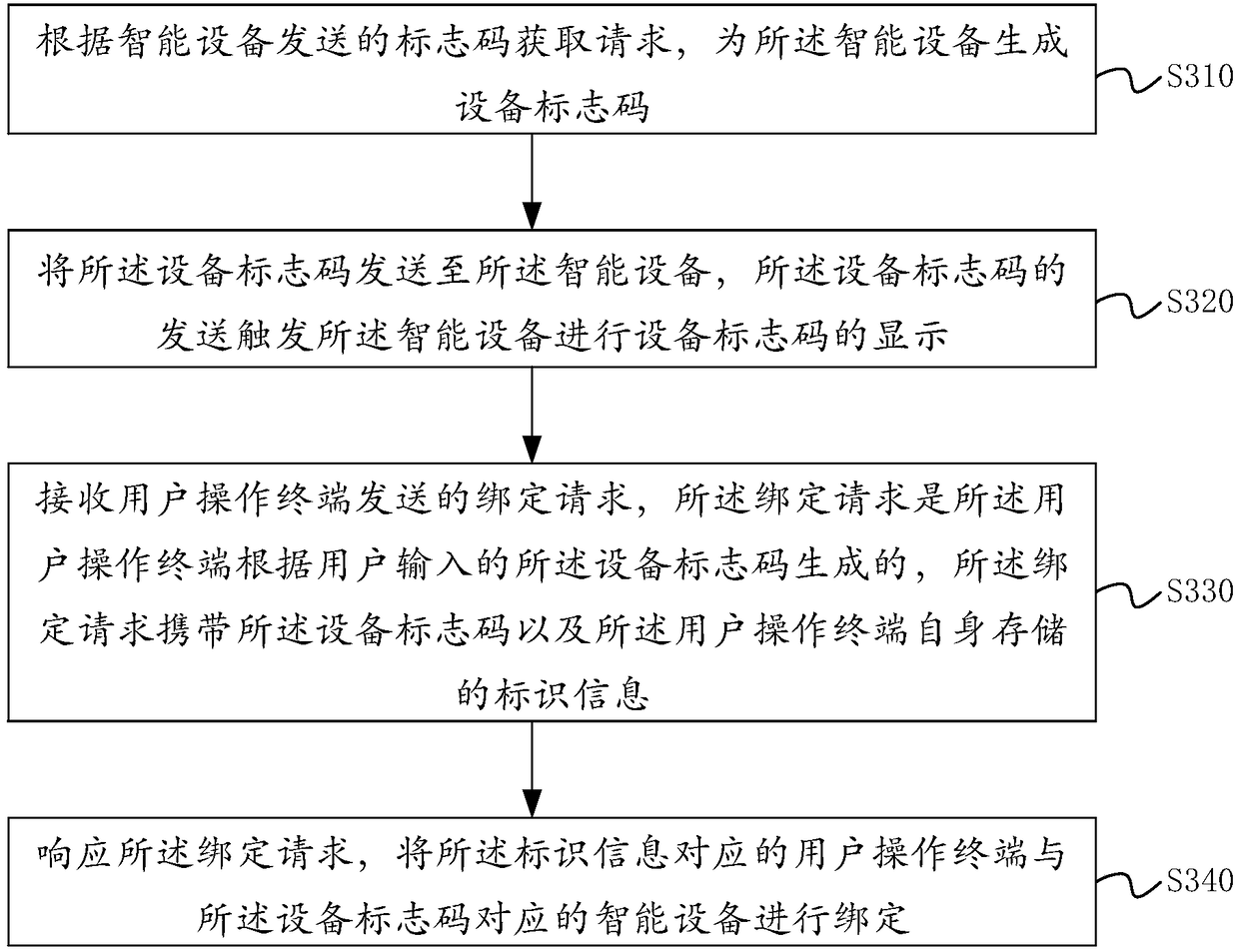
Binding method and device for intelligent equipment and user operation terminal, and electronic equipment
ActiveCN108259643AReduce the risk of bindingImprove securityTransmissionSoftware engineeringComputer terminal
The invention discloses a binding method and a binding device for intelligent equipment and a user operation terminal, electronic equipment and a computer readable storage medium. The method comprisesthe steps of generating an equipment identification code for intelligent equipment according to an identification code acquisition request sent by the intelligent equipment; sending the equipment identification code to the intelligent equipment, wherein the sending of the equipment identification code triggers the intelligent equipment to display the equipment identification code; receiving a binding request sent by the user operation terminal, wherein the binding request is generated by the user operation terminal according to the equipment identification code input by a user, and the binding request carries the equipment identification code and identification information stored in the user operation terminal; and in response to the binding request, binding the user operation terminal corresponding to the identification information with the intelligent equipment corresponding to the equipment identification code. According to the scheme provided by the invention, a two-dimensional code is not needed to be printed and pasted onto the intelligent equipment, so that the problems that the wrong two-dimensional code is pasted and the two-dimensional code is leaked are avoided, the risk of binding the intelligent equipment by unreal users can be reduced and the security of the intelligent equipment is improved.
Owner:MIDEA SMART TECH CO LTD +1
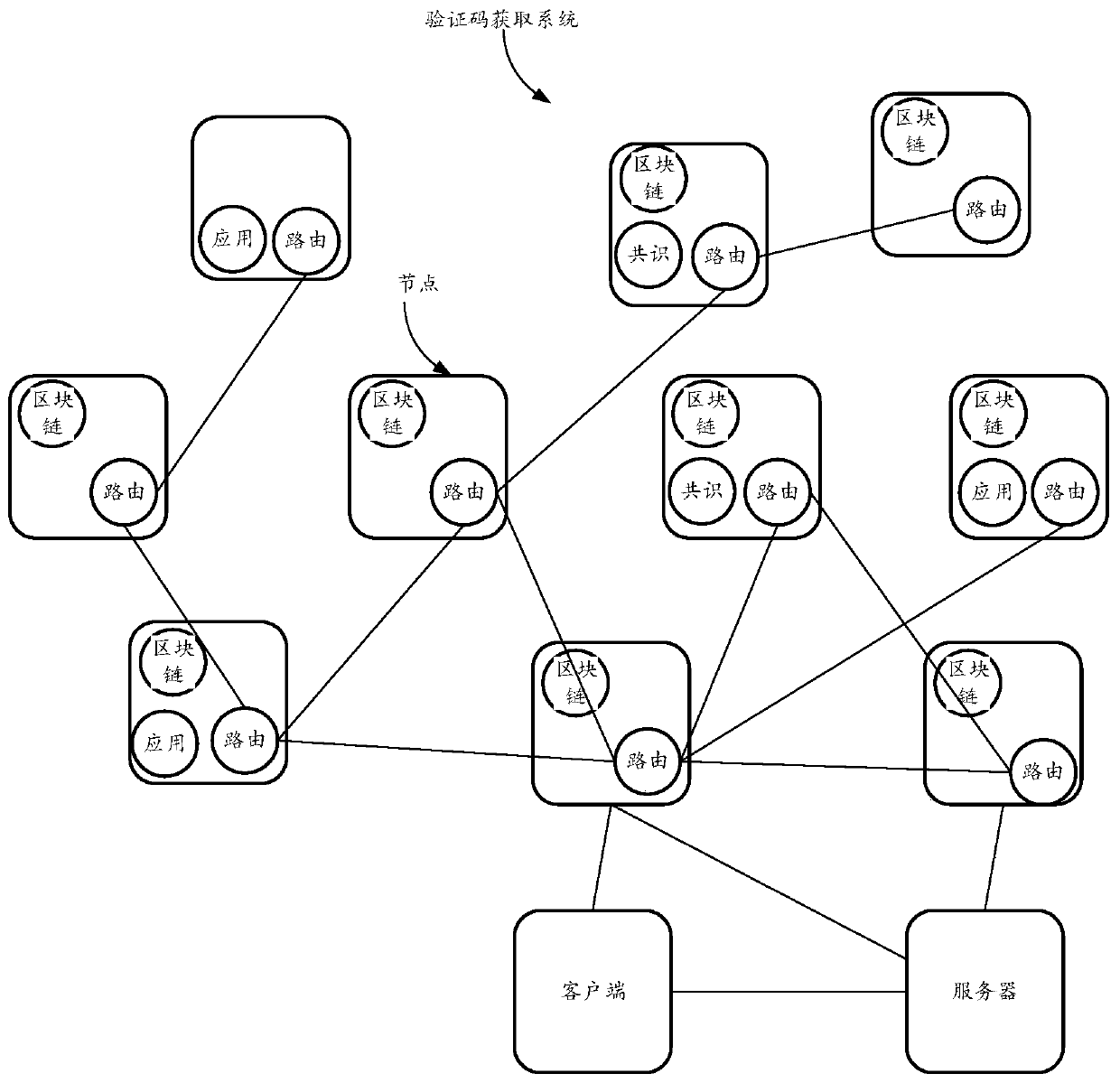
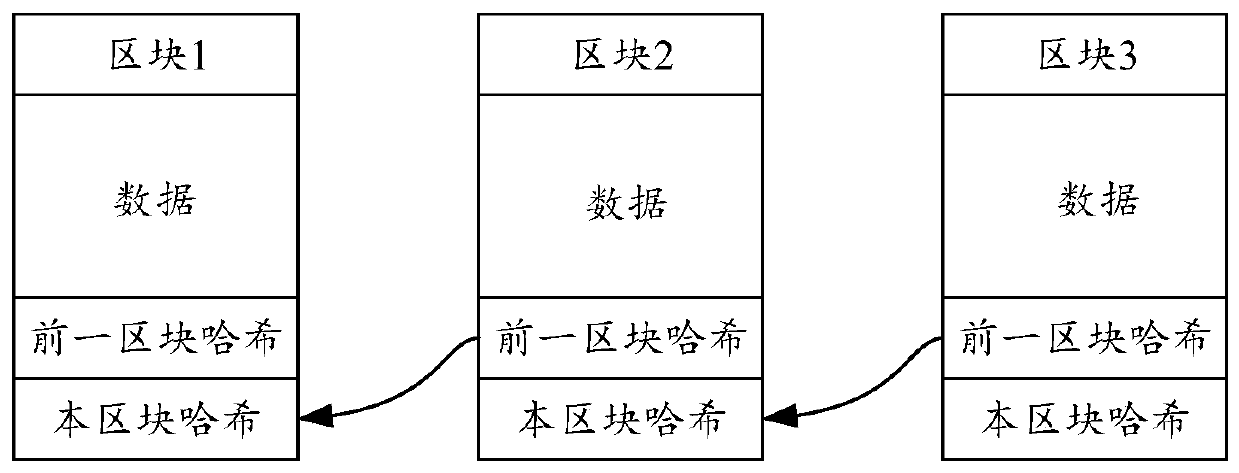
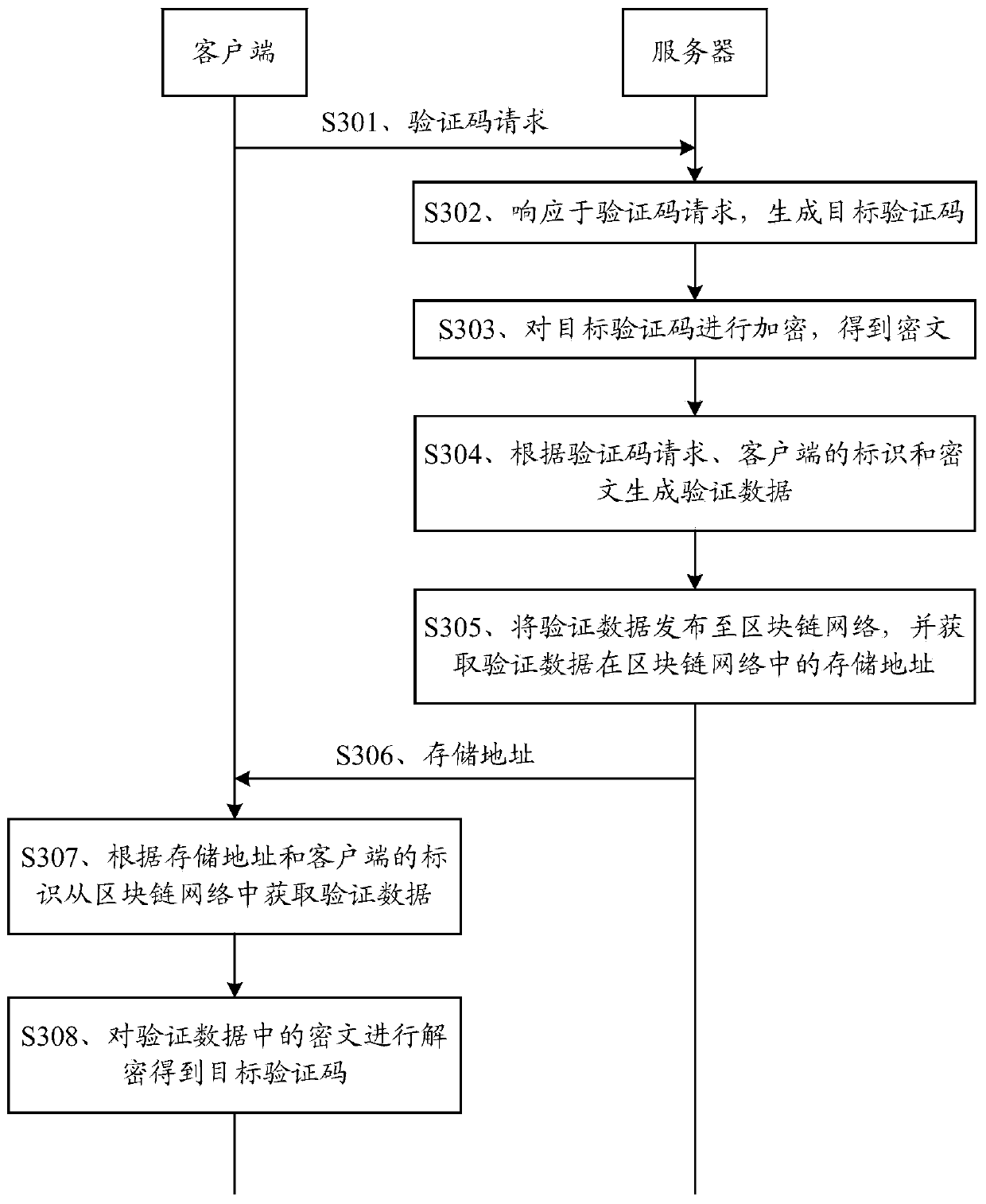
Block chain-based verification code acquisition method, client, server and storage medium
ActiveCN110493261AImprove securityRealize transmissionKey distribution for secure communicationCiphertextOperating system
The embodiment of the invention provides a block chain-based verification code acquisition method, a client, a server and a storage medium. The method comprises the following steps: sending a verification code request to a server, wherein the verification code request carries an identifier of the client and is used for enabling the server to generate a target verification code, encrypting the target verification code to obtain a ciphertext, generating verification data according to the verification code request, an identifier of the client and the ciphertext, publishing the verification data to the blockchain network, and obtaining a storage address of the verification data in the blockchain network; receiving a storage address sent by the server, and obtaining verification data from the blockchain network according to the storage address and the identifier of the client; and decrypting the ciphertext in the verification data to obtain the target verification code. Through the embodiment of the invention, the transmission of the verification code can be realized based on the blockchain network without using an SIM card. The evidence storage of the verification code verification event can also be realized.
Owner:TENCENT TECH (SHENZHEN) CO LTD
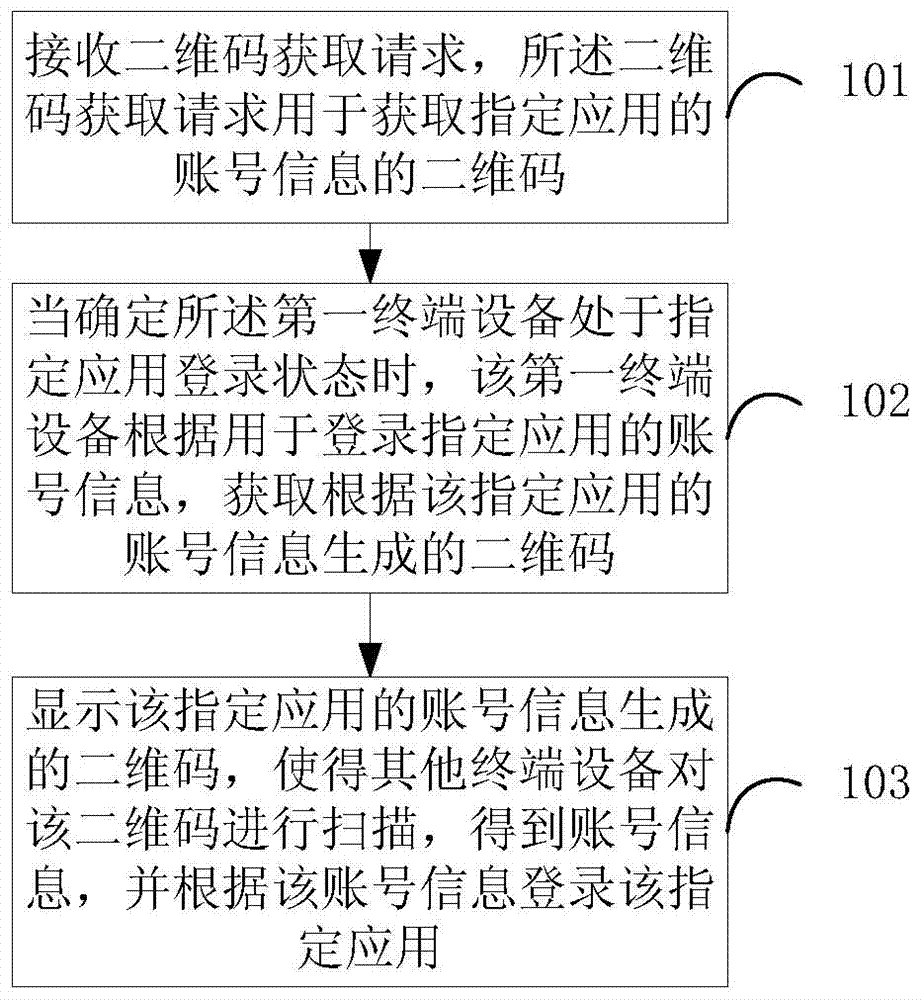
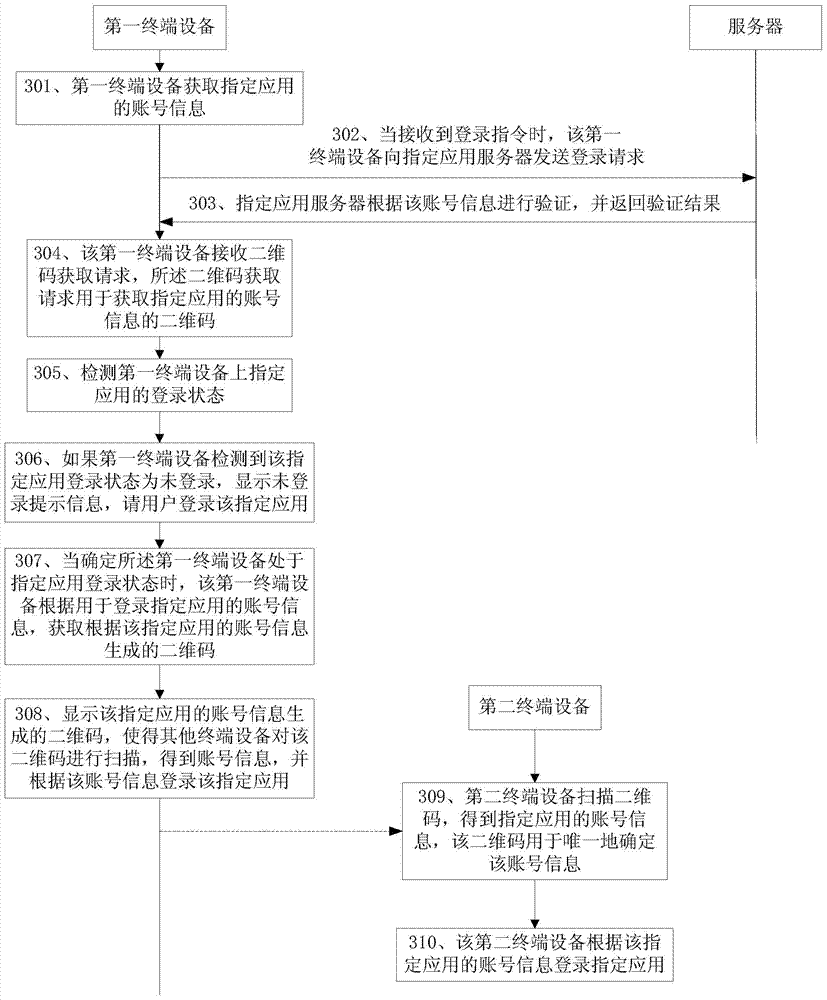
User login method, user login device and terminal devices
InactiveCN104519197AAvoid multiple re-typingLess typingUser identity/authority verificationSubstation equipmentPasswordTerminal equipment
The invention discloses a user login method, a user login device and terminal devices, and belongs to the technical field of terminal devices. The user login method includes receiving two-dimensional code acquisition requests for acquiring two-dimensional codes of account number information of specified application; acquiring the two-dimensional codes according to the account number information for logging users in the specified application when the first terminal devices are determined to be in specified application login states; displaying the two-dimensional codes generated according to the account number information of the specified application, allowing the other terminal devices to scan the two-dimensional codes to obtain the account number information and logging the users in the specified application according to the account number information. The two-dimensional codes are generated according to the account number information of the specified application. The user login method, the user login device and the terminal devices have the advantages that the two-dimensional codes corresponding to the account number information can be generated according to the account number information of the logged specified application by the terminal devices and can be displayed, so that the other terminal devices can obtain the account number information by means of scanning the two-dimensional codes, the users can log in the specified application according to the account number information, account numbers and passwords do not need to be repeatedly inputted, and the time can be saved to a great extent.
Owner:TENCENT TECH (SHENZHEN) CO LTD
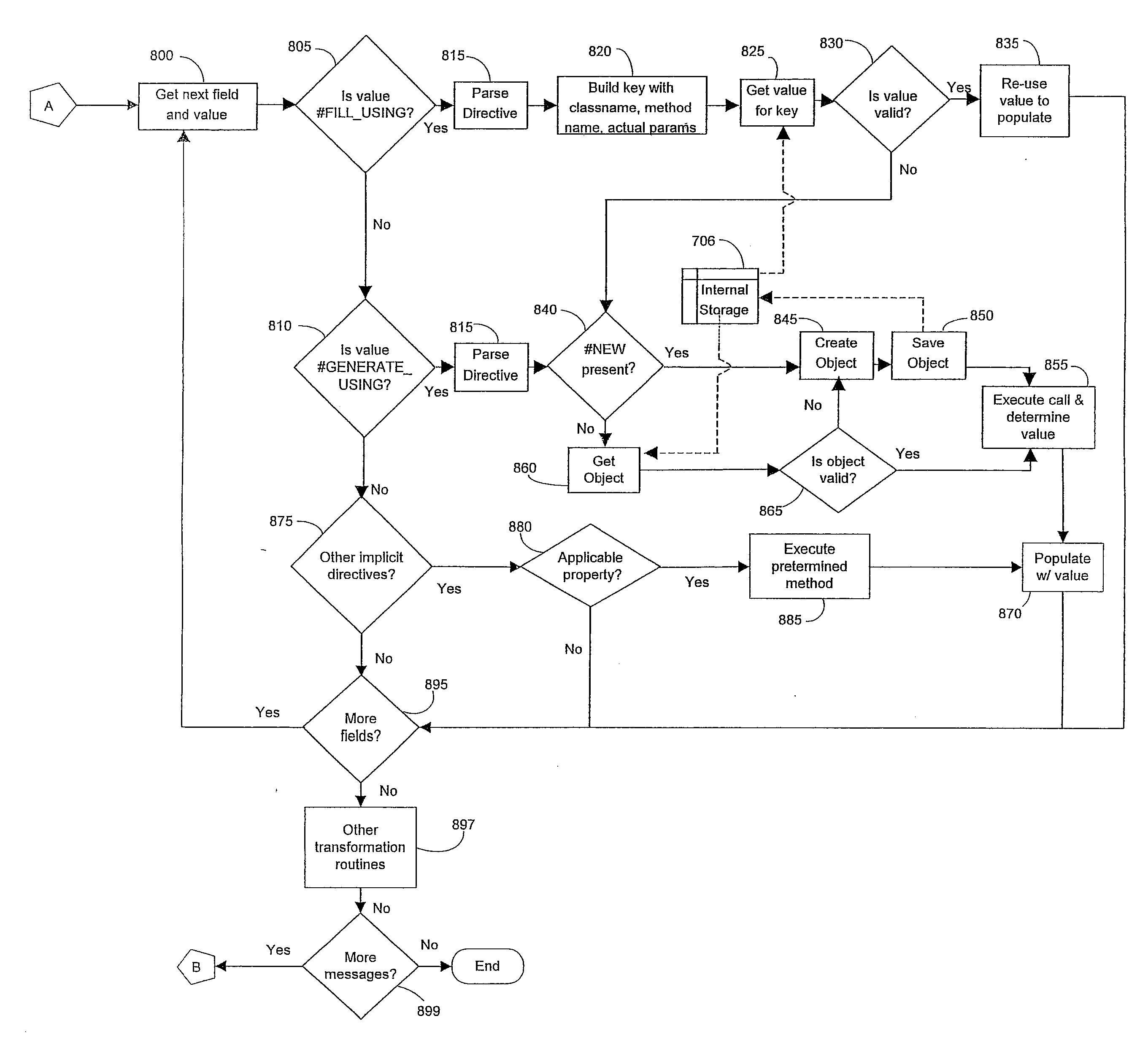
Event decomposition using rule-based directives and computed keys
InactiveUS20080294740A1Multiple digital computer combinationsNon-redundant fault processingDecompositionProperty value
Methods, systems, and computer program products for generating a common event format representation of information from a plurality of messages include parsing a rule associated with a current message to determine if a property of a common event format representation for the current message is to be populated with a property value from a previous message. If the rule specifies to obtain the property value from the previous message, the property value is obtained from the previous message and the common event format representation for the current message is populated with the obtained property value from the previous message. The property value may be obtained by generating a computed key based on properties of the current message that are common to the previous message, and identifying the previous message based on the key of the current message. The rule associated with the current message may also be parsed to determine if the property of the common event format representation for the current message is to be populated with a property value determined by specified code. If the rule specifies to obtain the property value using the specified code, the property value is obtained using the specified code and the common event format representation for the current message is populated with the obtained property value obtained using the specified code.
Owner:INT BUSINESS MASCH CORP
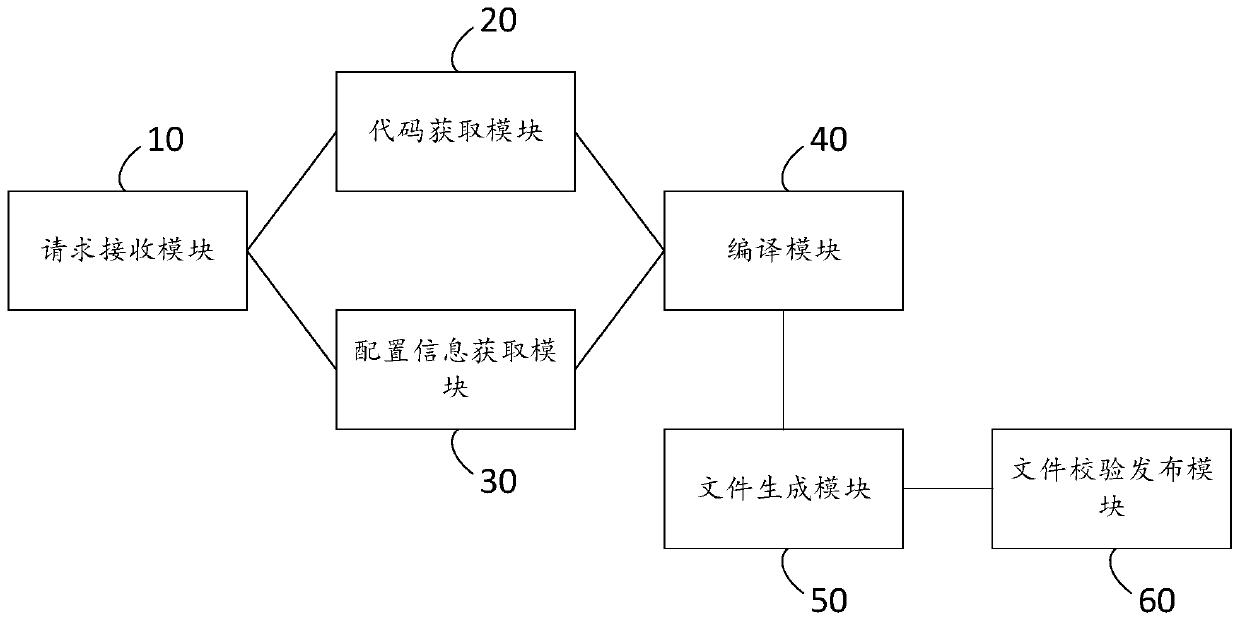
Automatic construction and uploading method and device for application program, computer equipment and storage medium
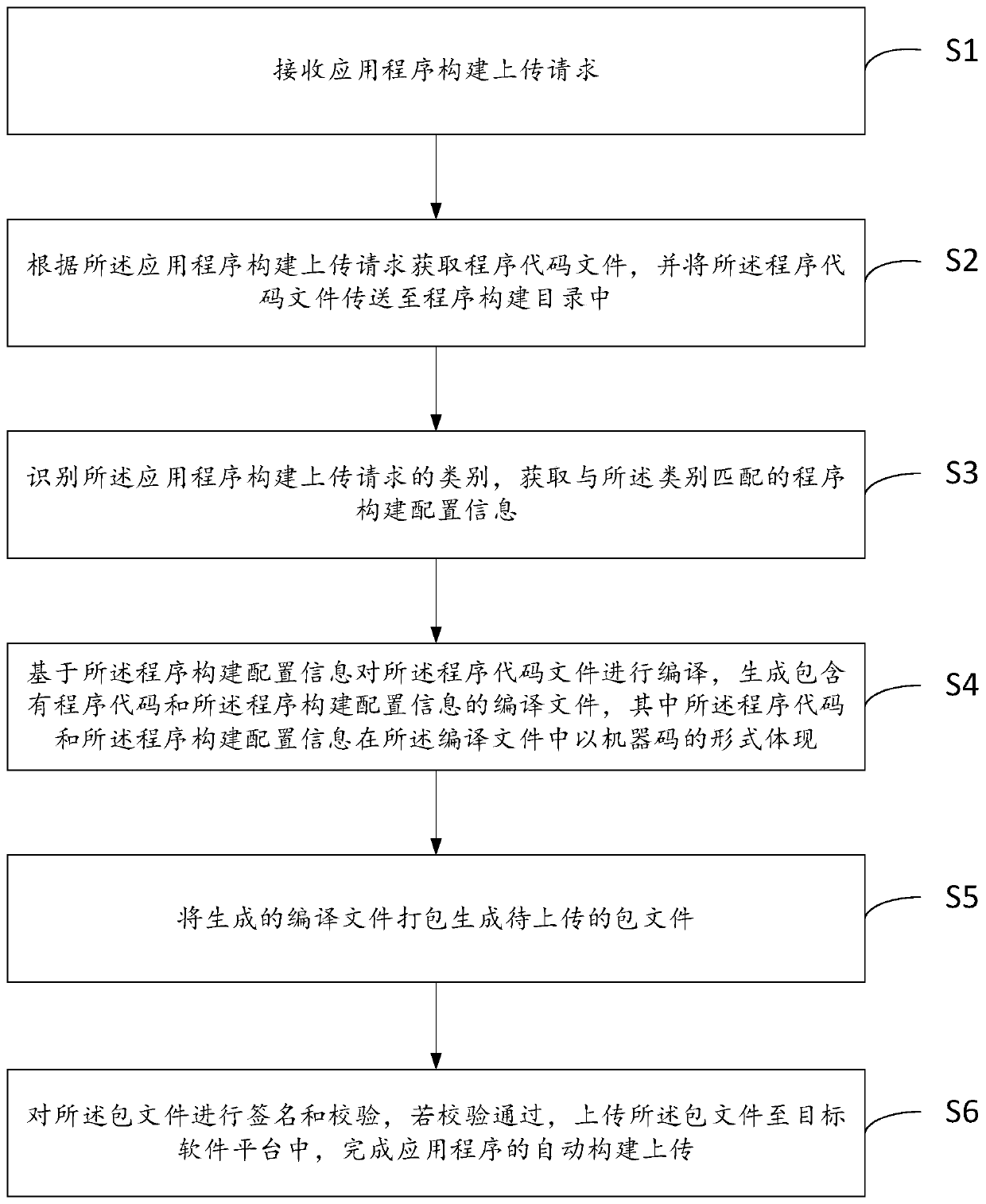
PendingCN110851135AReduce build timeImprove work efficiencyVersion controlProgram documentationContinuous integrationSoftware engineering
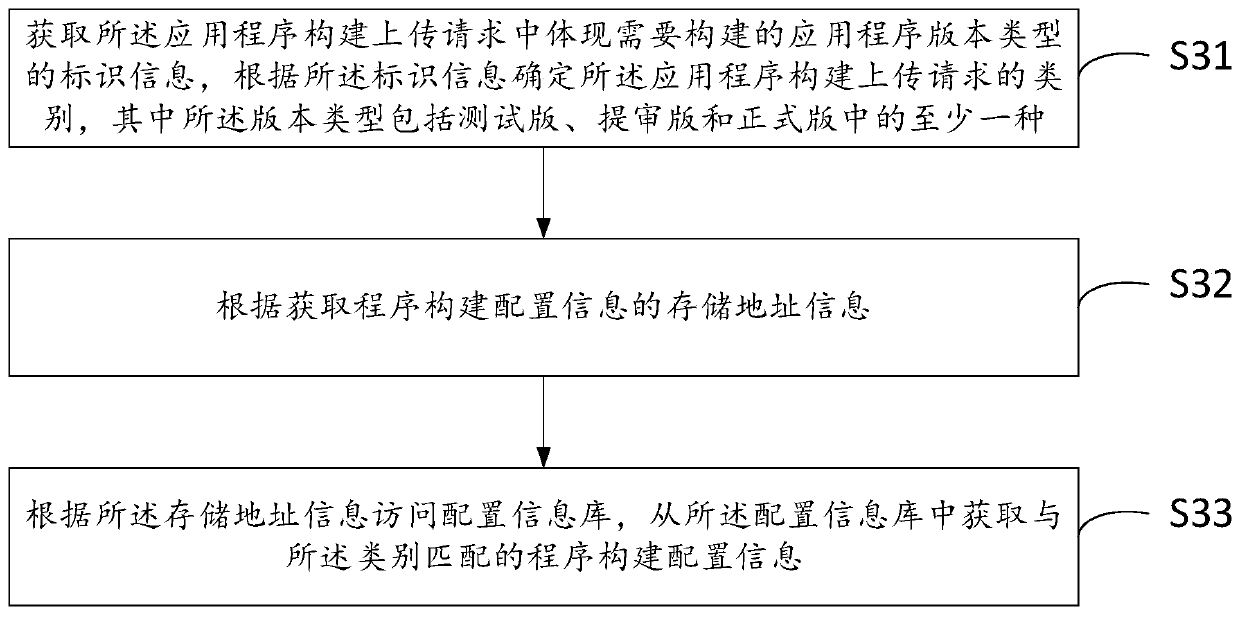
The invention belongs to the field of computers, and relates to an automatic construction and uploading method and a device for an application program, computer equipment and a storage medium. The method comprises the steps of receiving an application program construction uploading request; acquiring a program code file according to the application program construction uploading request and transmitting the program code file to a program construction directory; acquiring program construction configuration information matched with the category of the application construction uploading request,and compiling a program code file according to the program construction configuration information to generate a compiled file; packaging the compiled file to generate a package file to be uploaded; and signing and verifying the package file, and uploading the package file to a target software platform after the package file passes the verification, thereby finishing automatic construction and uploading of the application program. According to the method provided by the invention, the links of code acquisition, compiling construction, uploading review and the like are connected in series and integrated together, operation is carried out in an automatic mode, continuous integration can be accessed, the application program construction time can be greatly saved, and the working efficiency isimproved.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
Method for matching vehicle CAN protocol and correlation equipment
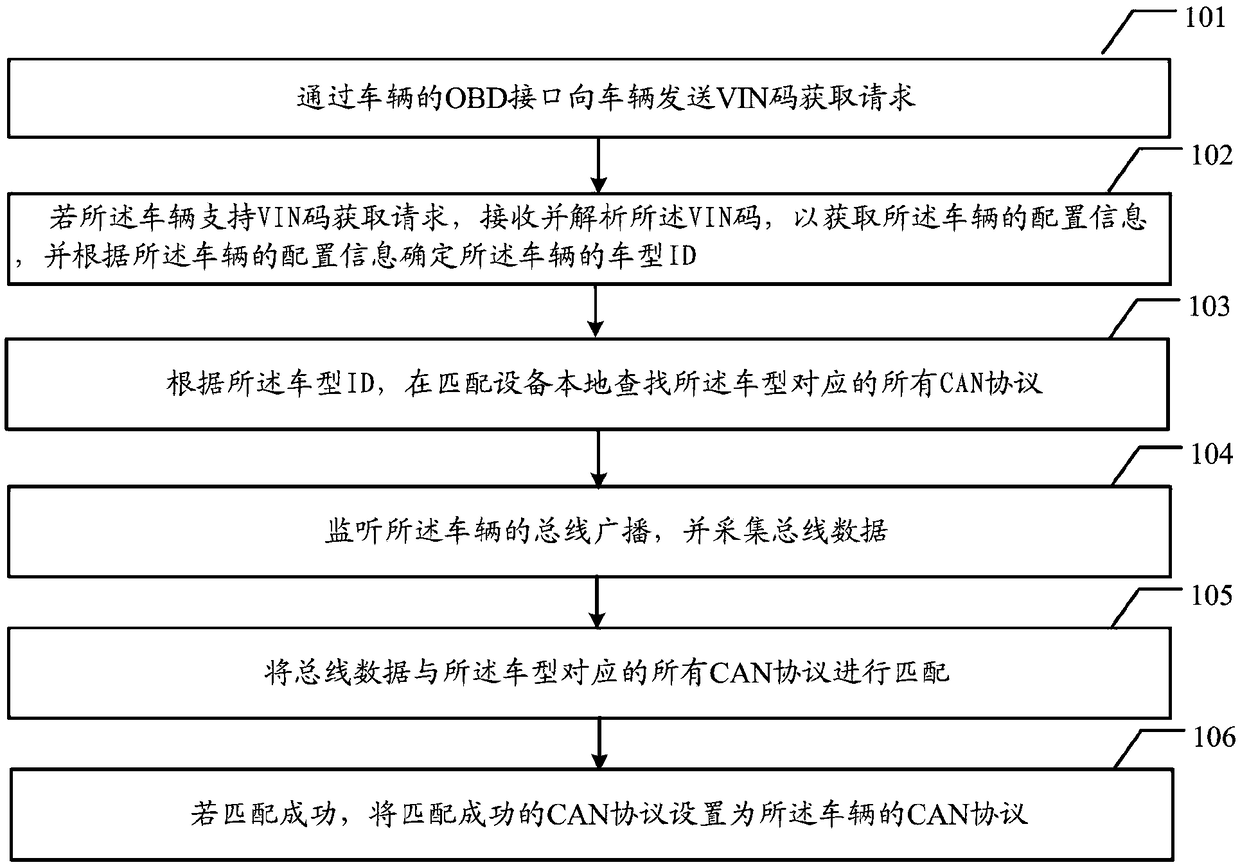
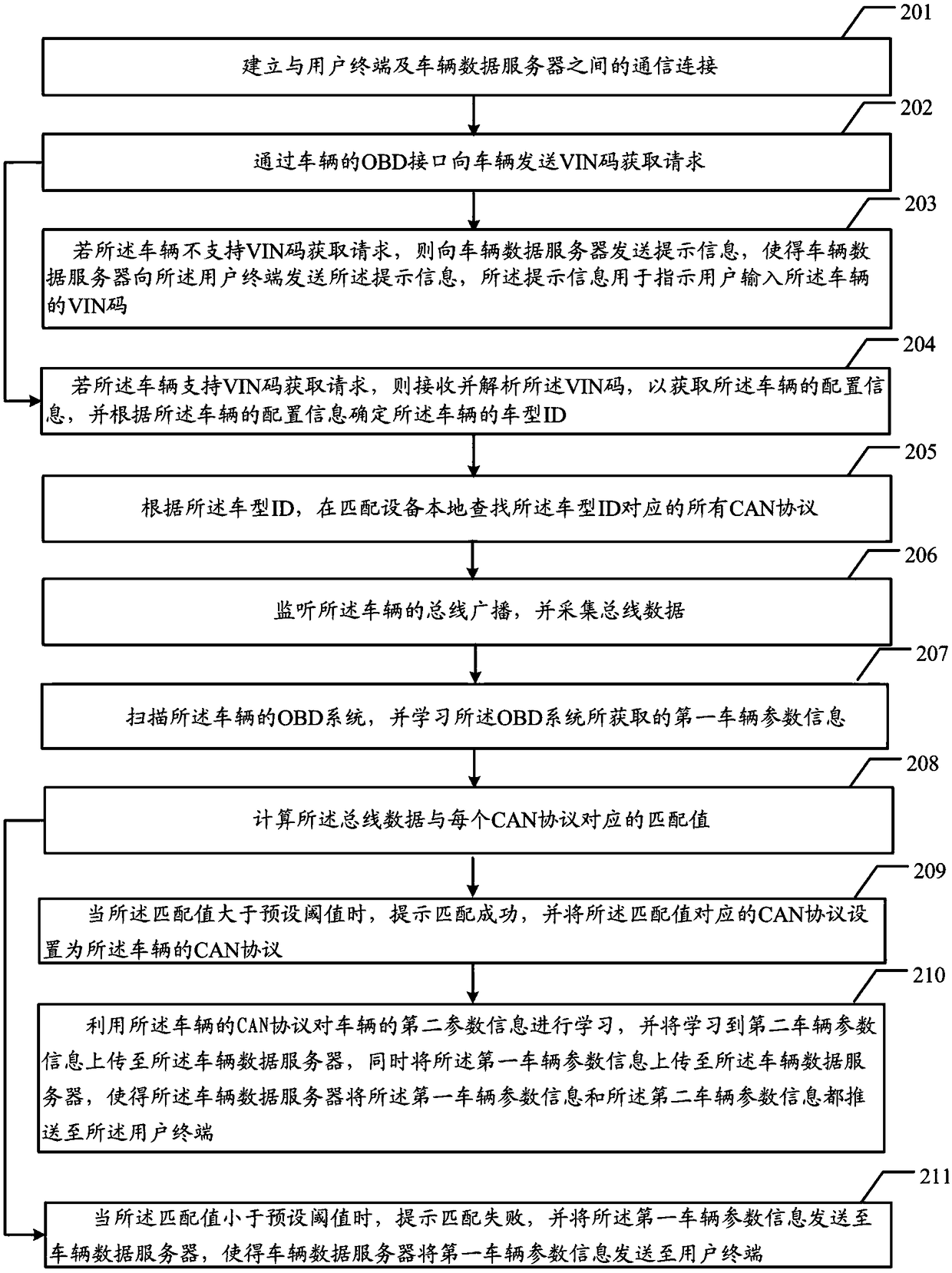
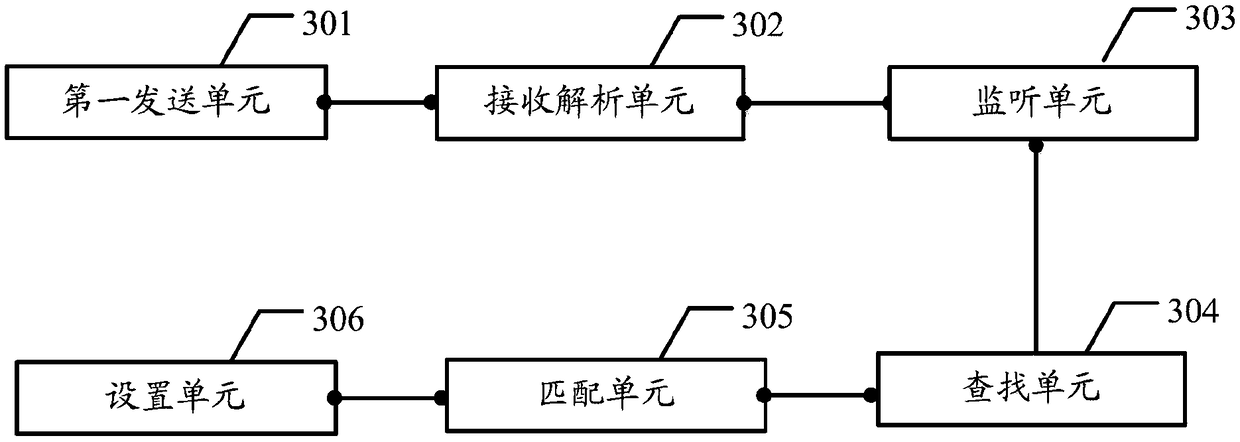
ActiveCN108803580ARealize automatic matchingImprove user experienceProgramme controlElectric testing/monitoringProtocol for Carrying Authentication for Network AccessReal-time computing
The embodiments of the invention provide a method for matching a vehicle CAN protocol and correlation equipment. The method and the equipment are used for automatically matching the vehicle CAN protocol so as to increase the convenience of vehicle parameter acquisition and the diversity of vehicle parameters. The method comprises the following steps of sending a VIN code acquisition request to a vehicle through the OBD interface of the vehicle; when the vehicle supports the VIN code acquisition request, receiving and parsing a VIN code to obtain the configuration information of the vehicle, and determining the vehicle model ID of the vehicle according to the configuration information of the vehicle; locally finding all CAN protocols corresponding to the vehicle model ID in matching equipment according to the vehicle model ID; monitoring the bus broadcast of the vehicle and collecting bus data; matching the bus data with all the CAN protocols corresponding to the vehicle model ID; and if the matching is successful, setting the successfully-matched CAN protocol to be the CAN protocol of the vehicle.
Owner:LAUNCH TECH CO LTD
Control method and system for dynamic configuration of HTML template
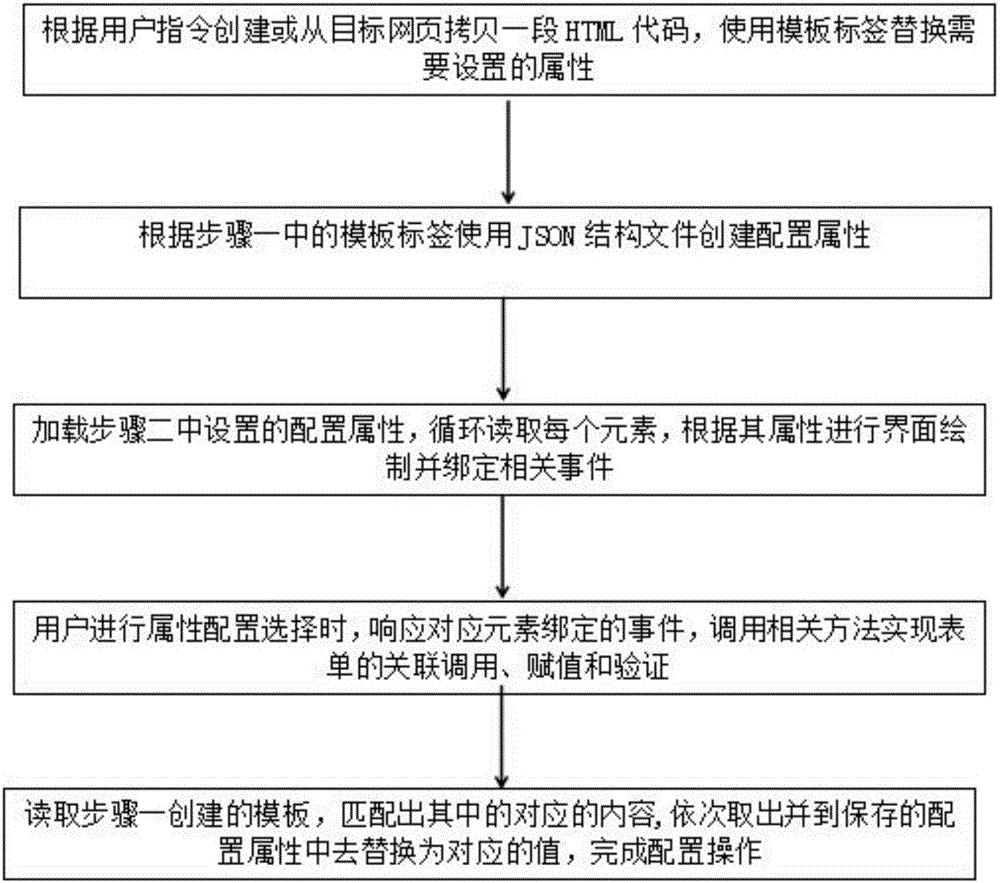
ActiveCN105824787AOptimizationEasy to addNatural language data processingSpecial data processing applicationsLoad stepConfiguration selection
The invention provides a control method for dynamic configuration of an HTML template. The control method comprises the following steps: 1, acquiring an HTML code, and replacing an attribute to be set by a template label; 2, establishing a configuration attribute with a JSON structural file according to the template label in the step 1; 3, loading the configuration attribute set in the step 2, cyclically reading each element, performing interface drawing and binding relevant events; 4, in the process of attribute configuration selection, calling a relevant method in response to events bound to corresponding elements; 5, reading the template established in the step 1, matching corresponding contents, extracting the contents, and replacing corresponding values in the saved configuration attribute. A system applying the method comprises a code acquisition unit, a JSON configuration attribute unit, a reading unit, an event proxy server and an interface generator. The control method is easy for adding, operation of html and js is avoided, and a user unfamiliar with codes can configure a template and an attribute conveniently.
Owner:JIANGSU ZHONGWEI TECH SOFTWARE SYST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com