Third-party login mobile phone number binding method based on mobile phone APP
A mobile phone number, mobile phone number technology, applied in the field of APP login, to achieve the effect of reducing damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
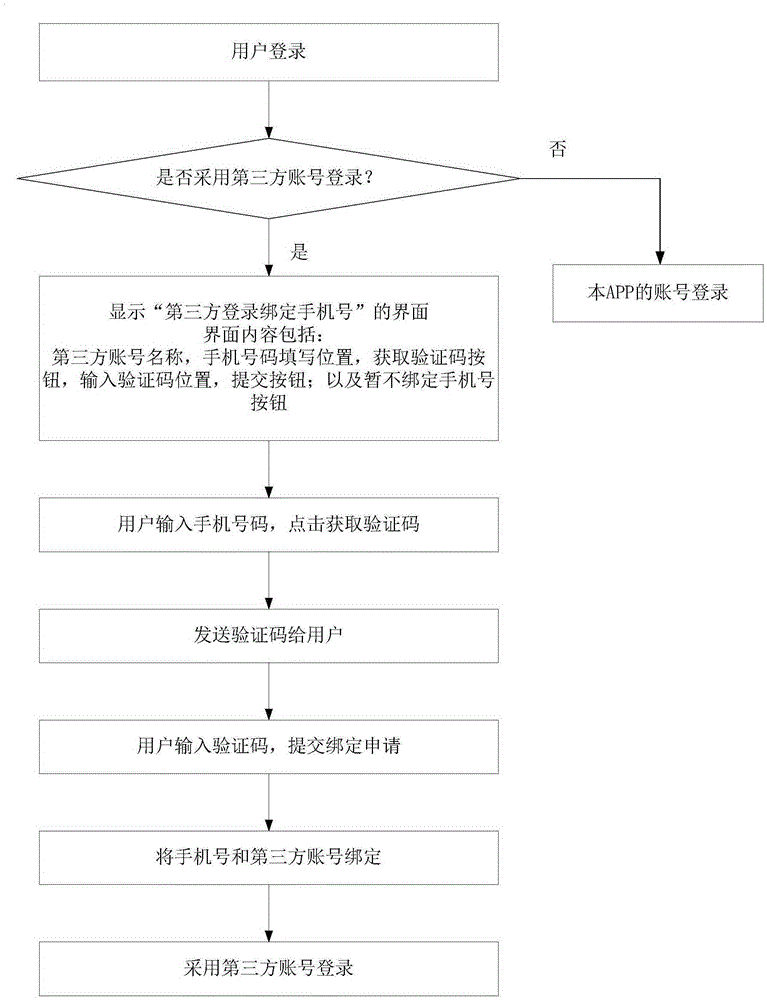
[0021] Such as figure 1 As shown, the third-party login and binding mobile phone number method based on the mobile phone APP includes the following steps:
[0022] Step 1: Receive the login request from the client and return the selection item, the selection item is whether to use a third-party account to log in;
[0023] Step 2, when the user chooses not to use a third-party account to log in, the client enters the APP account and password input page;
[0024] When the user chooses to use a third-party account to log in, the client enters the third-party login binding mobile phone number page; the third-party login binding mobile phone number page is at least provided with a third-party account name input box, a mobile phone number filling position, and a verification code button, enter the location of the verification code, the submit button, and the button of not binding the mobile phone temporarily, and the client clicks the button of not binding the mobile phone temporar...
Embodiment 2
[0028] The specific method of the third-party account login in the steps 1, 2, and 4 is: the open platform enters the page to receive the authorization instruction of the user terminal to the third-party site; when the user terminal is authorized to connect successfully, log back in according to the predetermined open platform. Skip protocol, transfer the first login identifier OpenID and the first login key OpenKey of the user terminal to the third-party site; the third-party site performs a process based on the user based on the first OpenID and the first OpenKey. Authorized login for terminal.
[0029] Other steps of embodiment 2 are the same as embodiment 1.
Embodiment 3
[0031] In the step 4, after the verification code is input, verification is required. The verification method is: first, before the verification code is sent, the server sets up a pairing verification module for the mobile phone number, and the pairing verification module records the number of verification codes currently sent. When the server returns the input verification code number, the pairing verification module compares the two sets of verification code numbers, if the comparison is successful, the binding is performed, and if the comparison fails, a failure message is returned.
[0032] Other steps of embodiment 3 are the same as embodiment 2.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com