Patents
Literature
287 results about "Code line" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
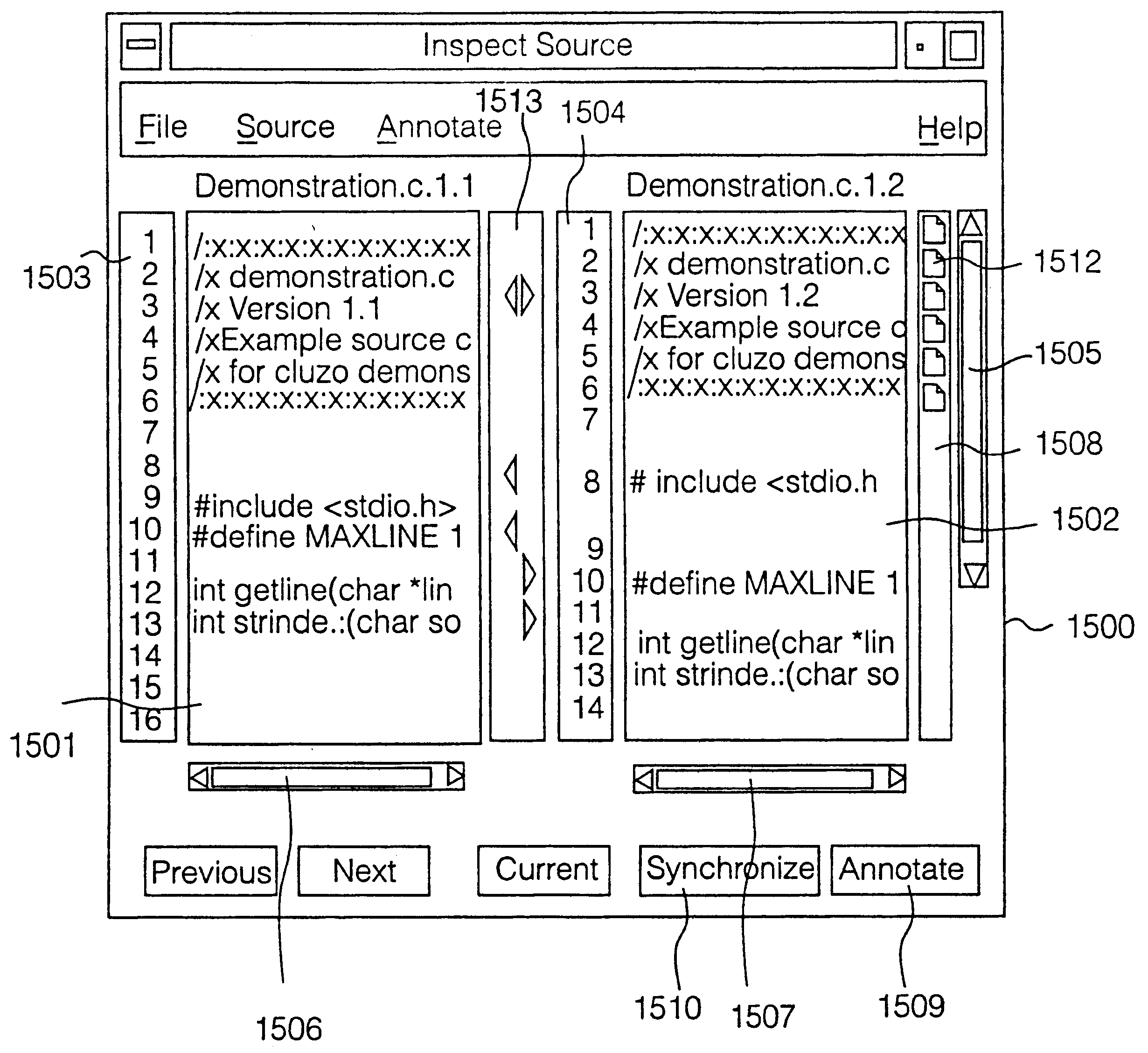
Interactive on line code inspection process and tool
InactiveUS6275223B1Data processing applicationsSpecific program execution arrangementsOnline codesDisplay device
A code inspection tool comprises a plurality of physical computing resources connected by a network facility, eg an LAN, intranet or internet, and a voice conferencing communications facility. The code inspection tool interfaces with a known configuration management system to load a quantity of original source code. A group of developers use a plurality of graphical user interfaces to inspect the code. All graphical user interfaces log into display views generated on a main graphical user interface, which is operated by a human controller of a code inspection session. The code inspection tool comprises means for allowing developers to compile annotation data and forward the annotation data from their respective graphical user interfaces to a centralized data store. Internal algorithms of the code inspection tool compile markers relating the annotation data files to individual lines of source code. During a code inspection session, all developers view a same display, which sets out original source code, side by side with new source code on a line by line basis, matching the line numbers of the original source code with those of the new source code. Changes to the original source code and new source code are visually identified by automatic generation of icons next to the appropriate source code lines on the display. Annotations to the source code lines are indicated by further icons next to the appropriate lines. The tool automatically generates data describing statistics of a code inspection process, for example number of lines inspected, during of a code inspection session, proportion of original and new code lines inspected. Code inspection reports may be generated in a variety of formats, eg plain text or HTML, and automatically distributed to individual developers over the networked facility.
Owner:RPX CLEARINGHOUSE
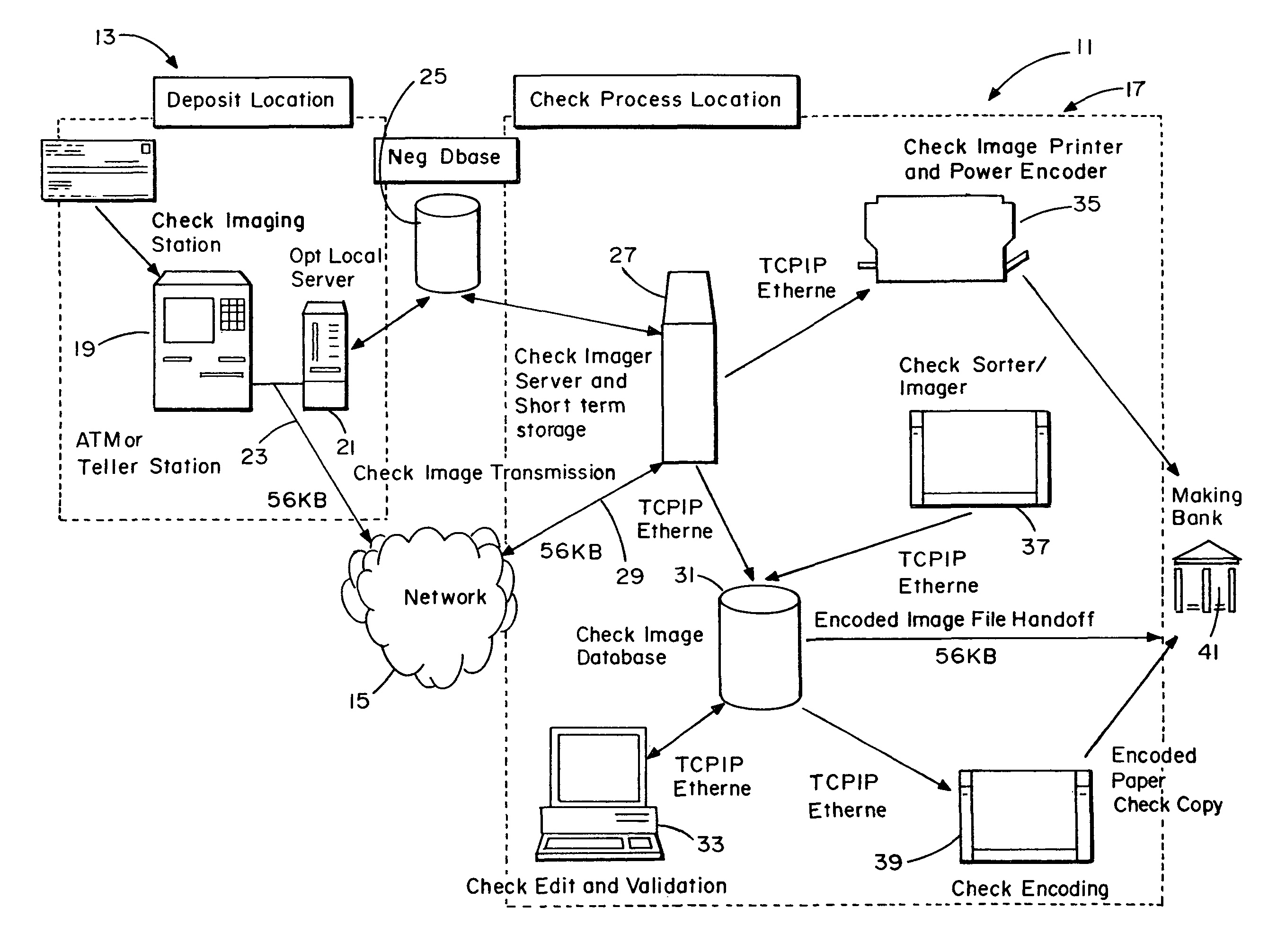
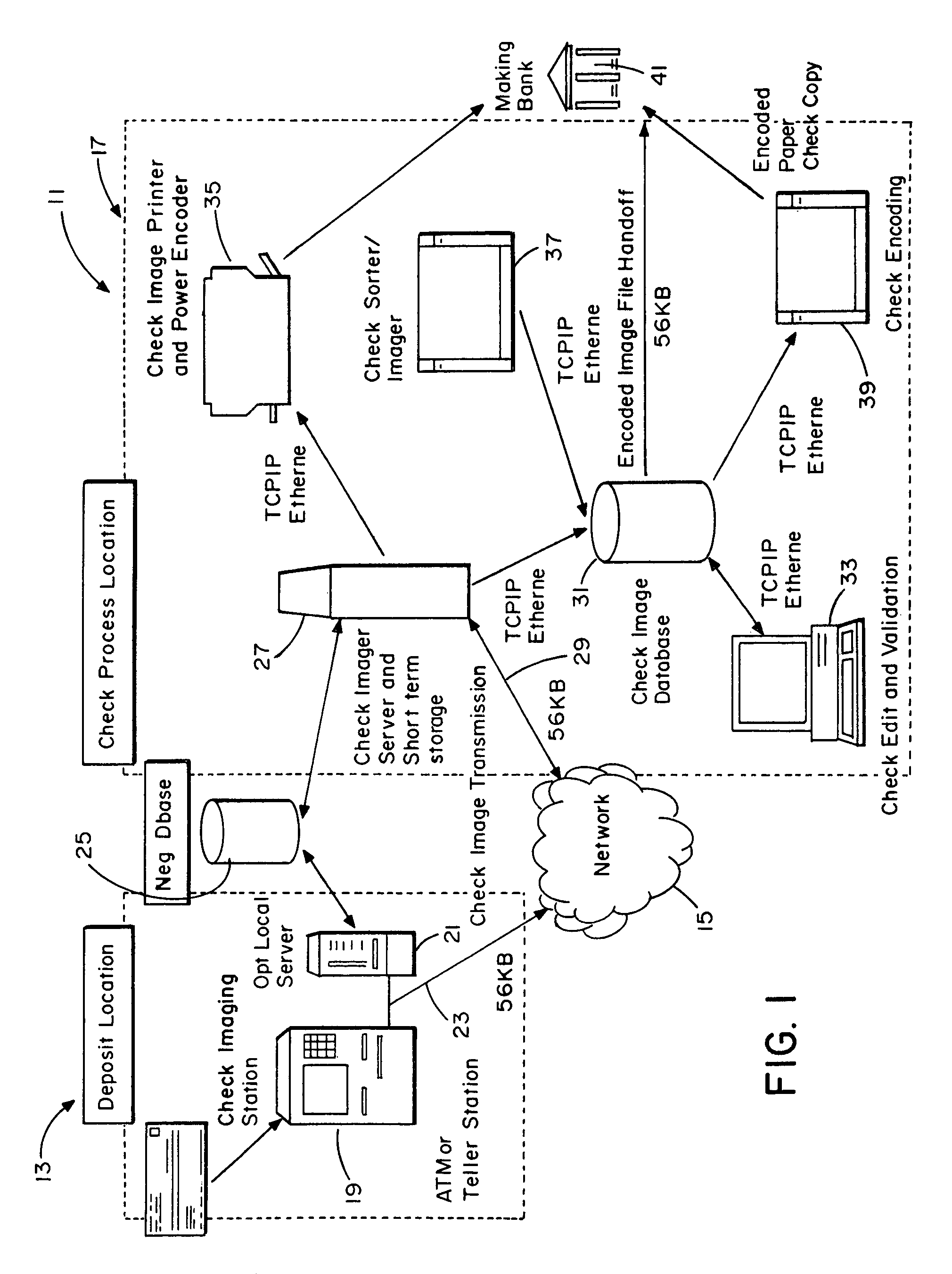
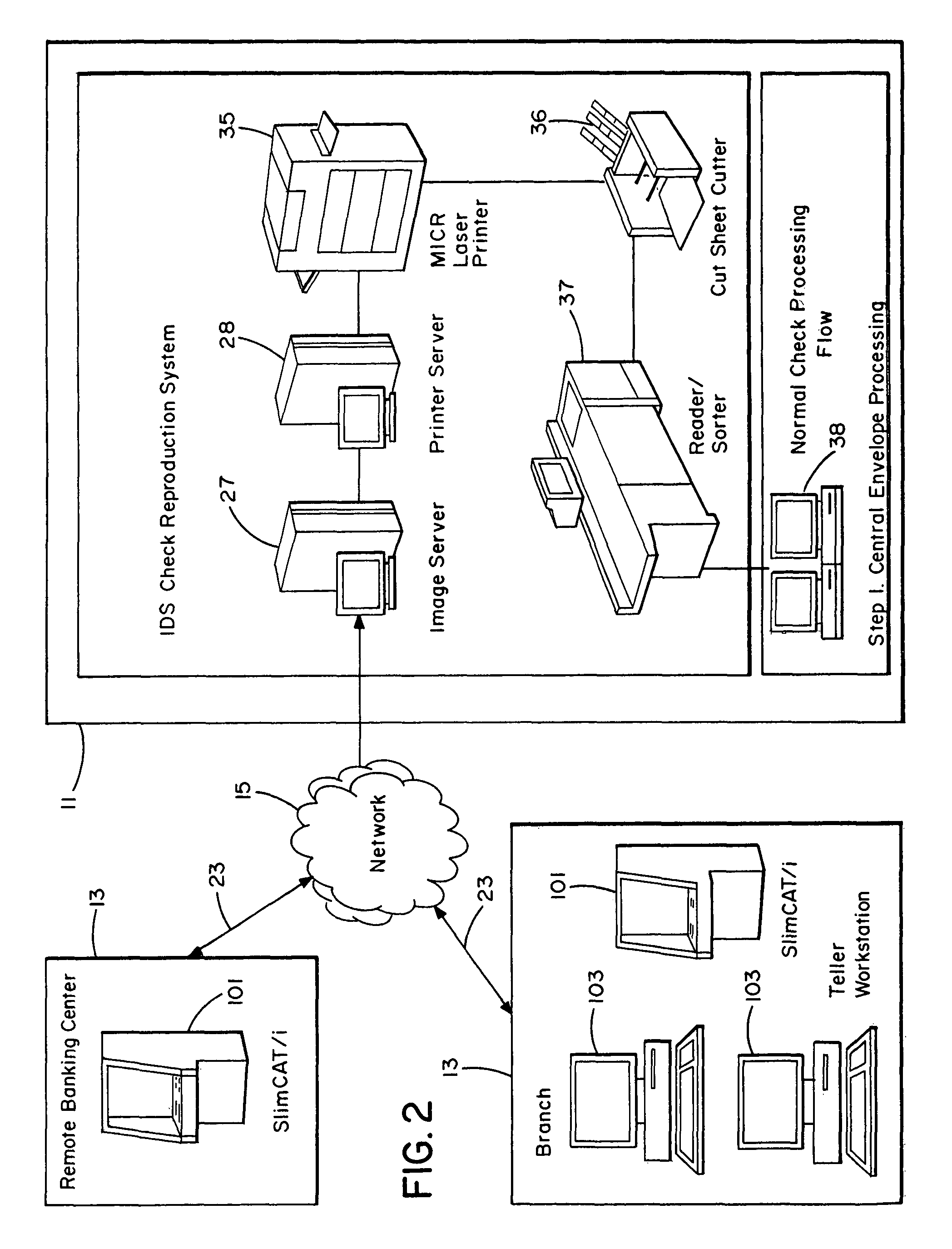
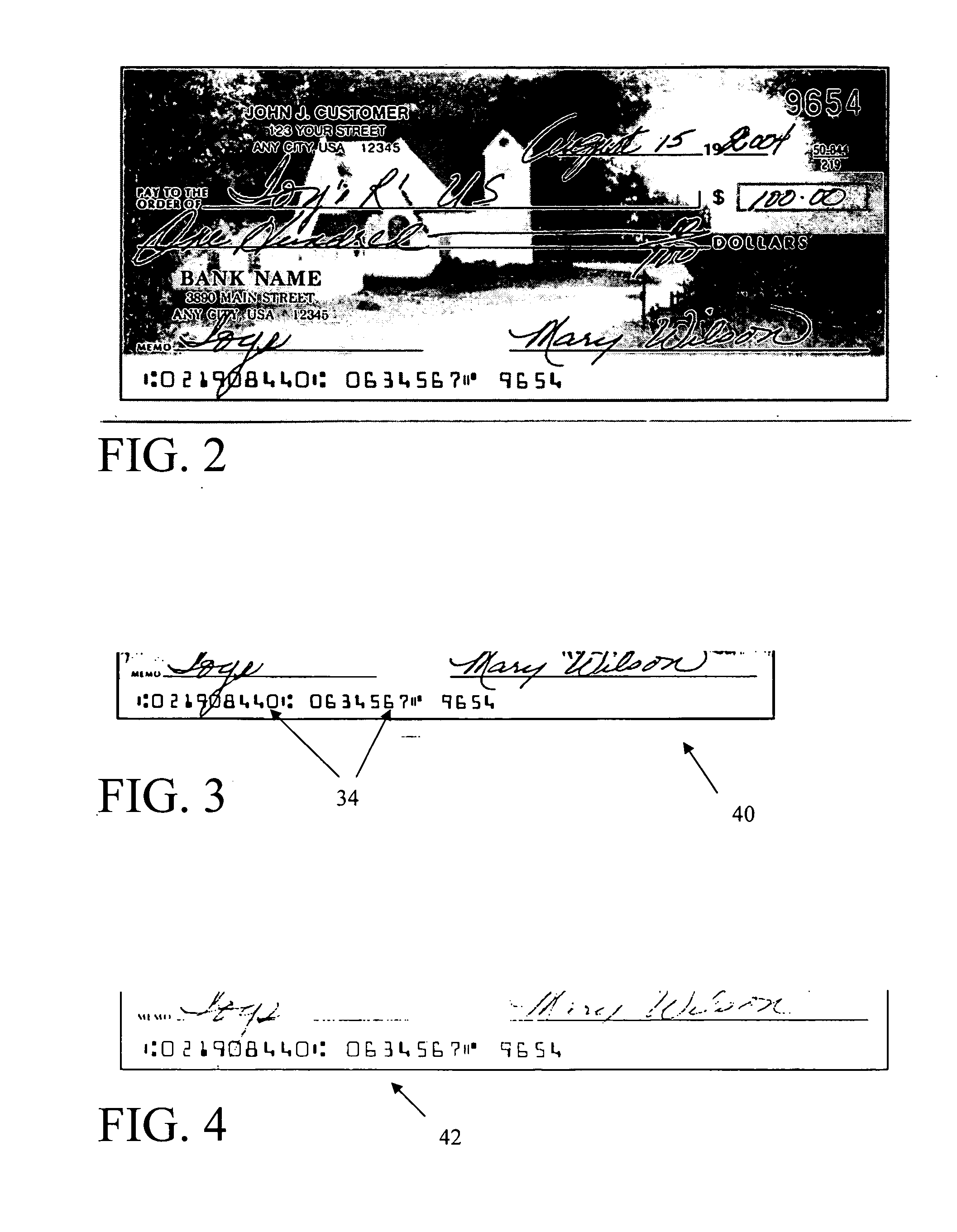
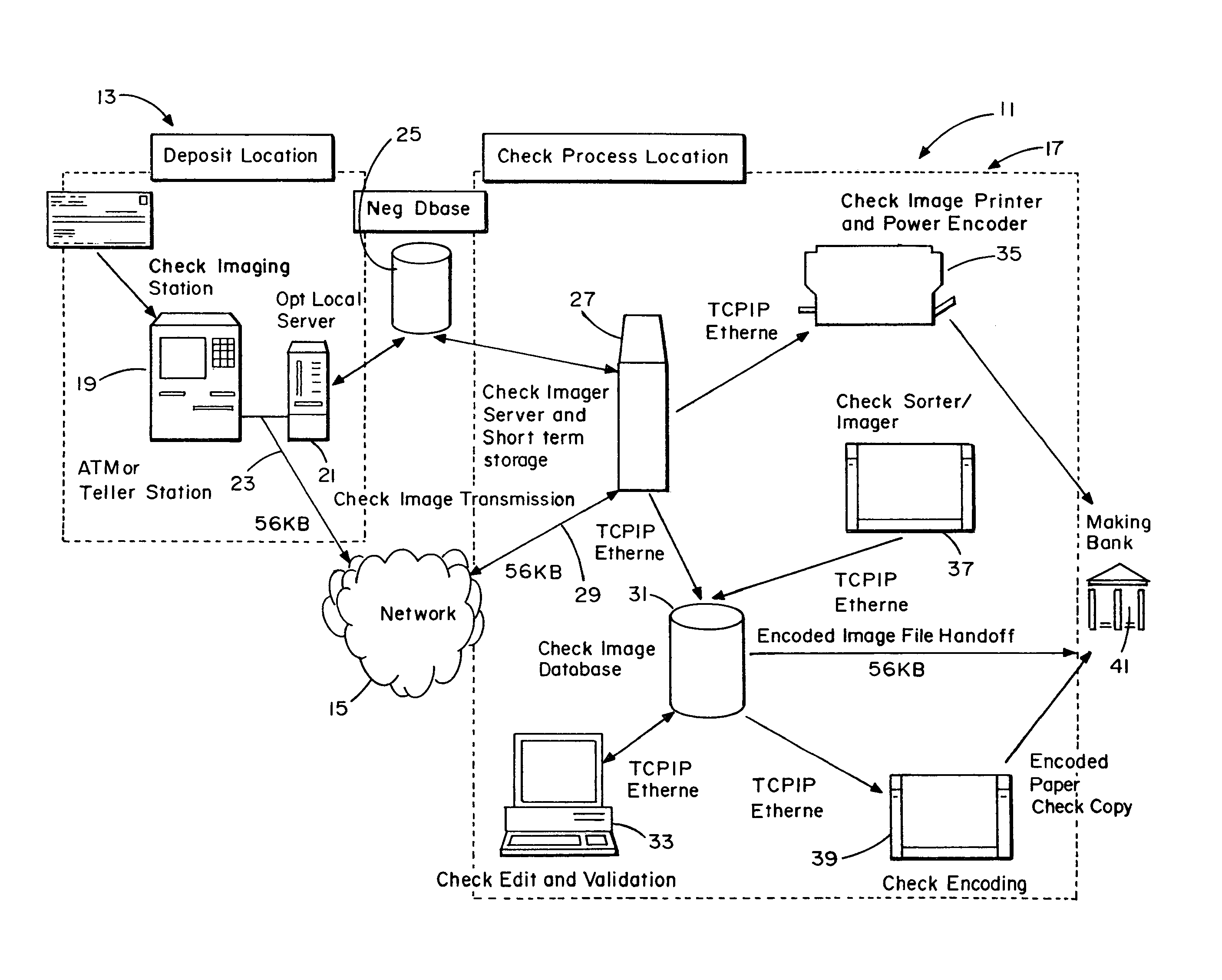
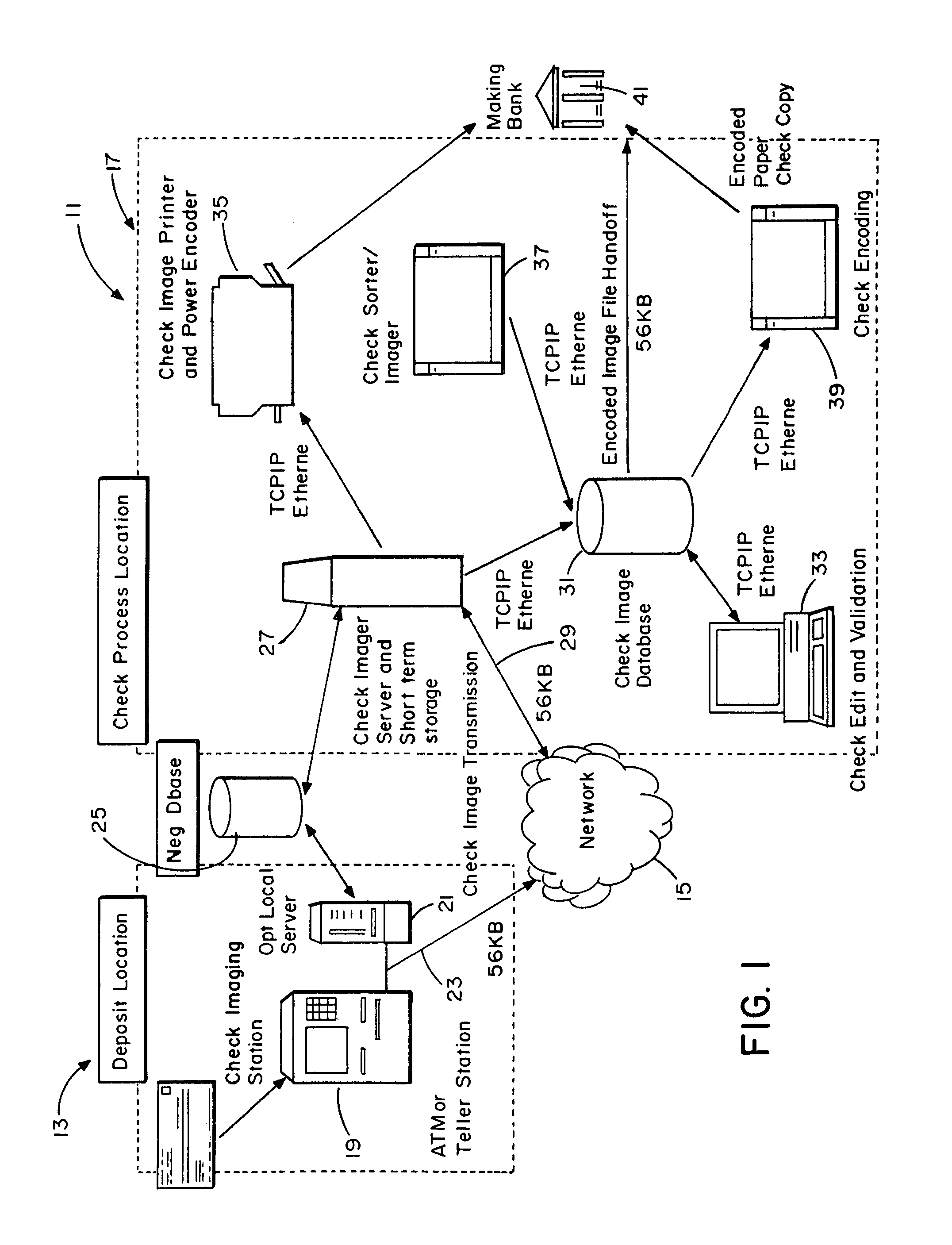
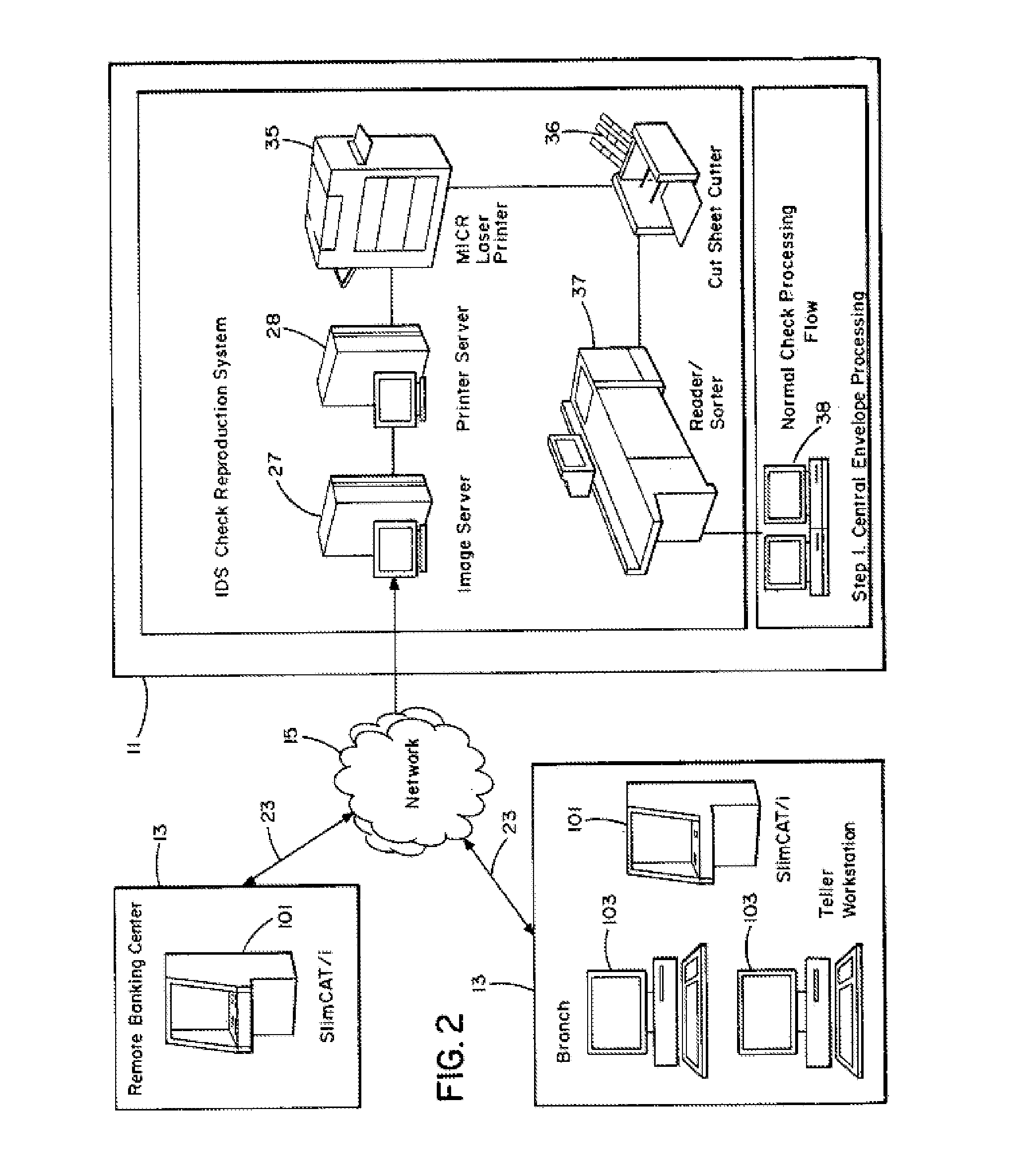
System and method for image depositing, image presentment and deposit taking in a commercial environment
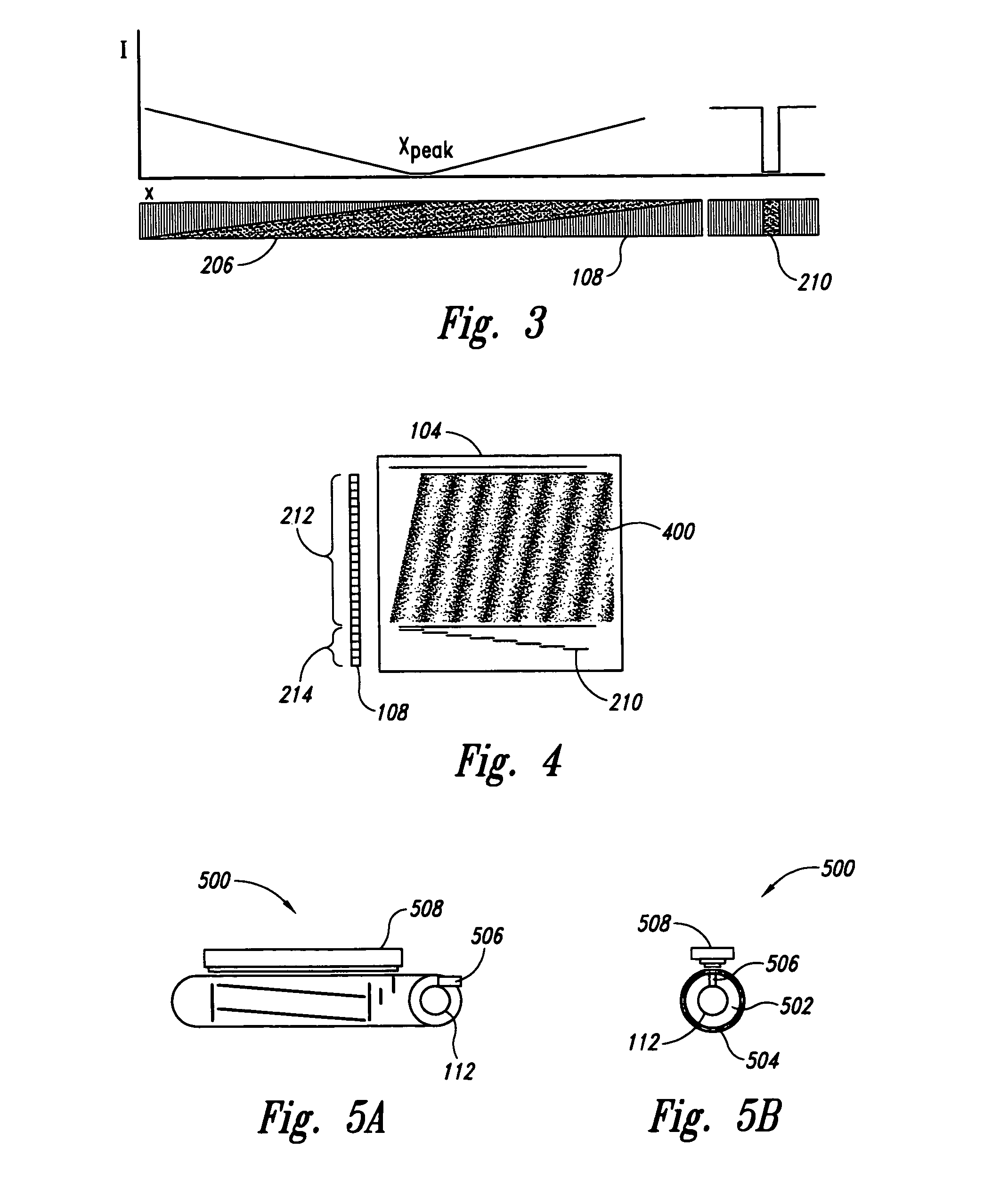
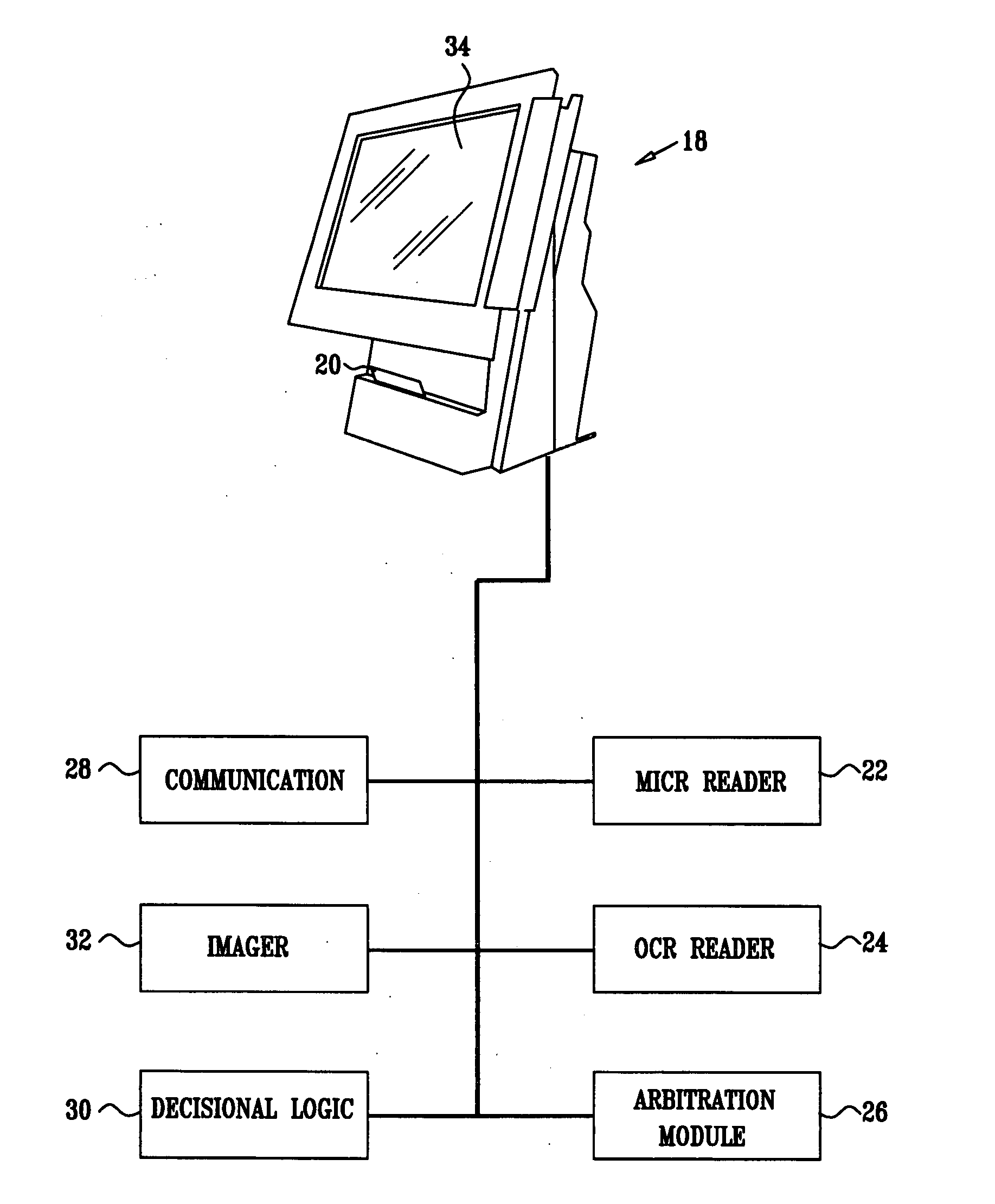
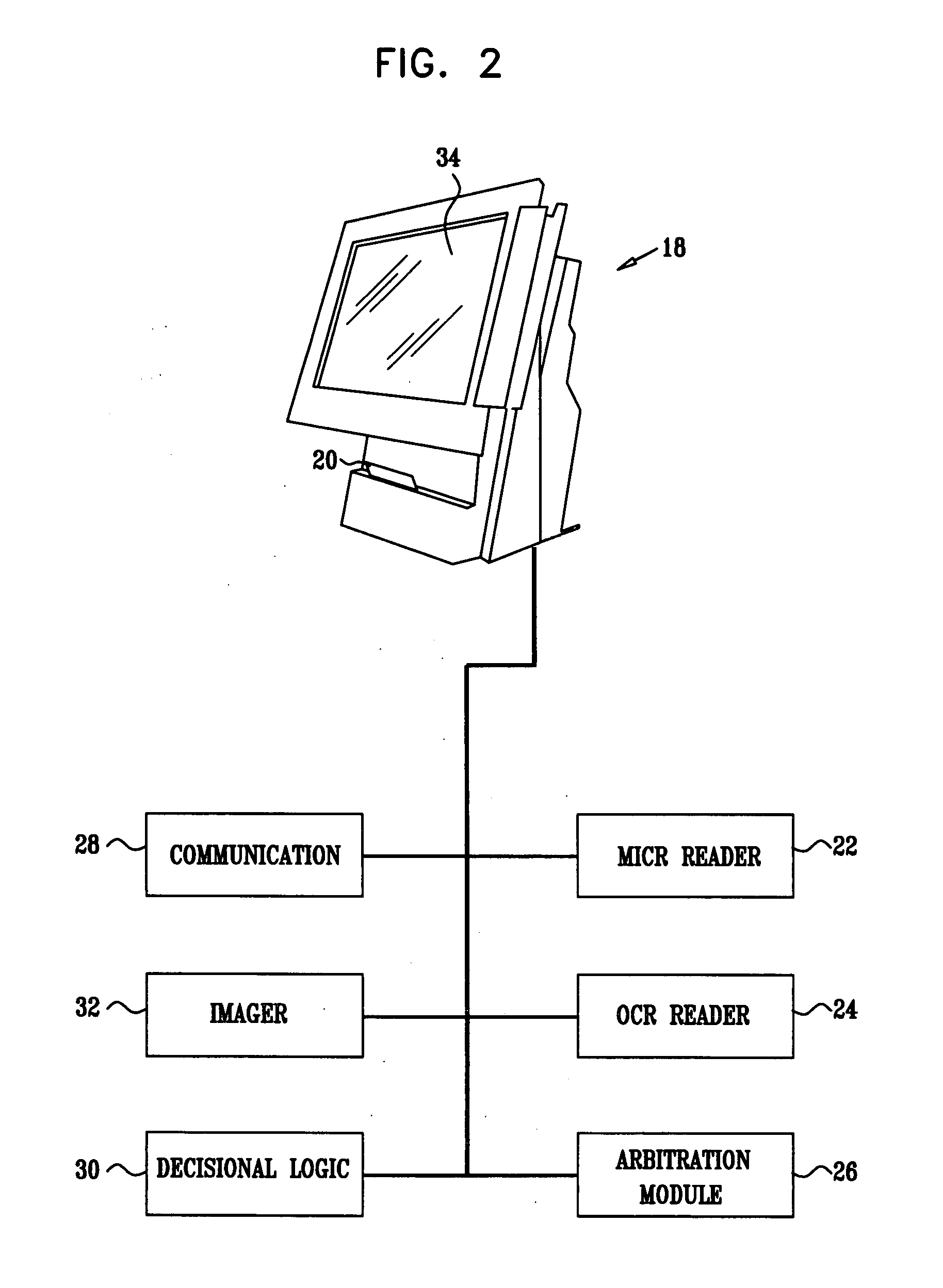
InactiveUS7792753B1Improvement in payment settlement timeLow costComplete banking machinesFinanceChequeDatabase
A method and system provides for scanning a check and / or cash to create an electronic image of the front and the back of the check and / or cash. The image is then processed and transmitted electronically to a central location. The image may be recreated into a paper form at the central location, resembling the original paper check or cash, including a machine-readable regeneration of the MICR code line data captured from the original instrument. Paperless processing of checks and cash is thus provided, including local voiding and storage of the check without requiring immediate pickup, while still allowing the transaction to be process.
Owner:CITIBANK +1
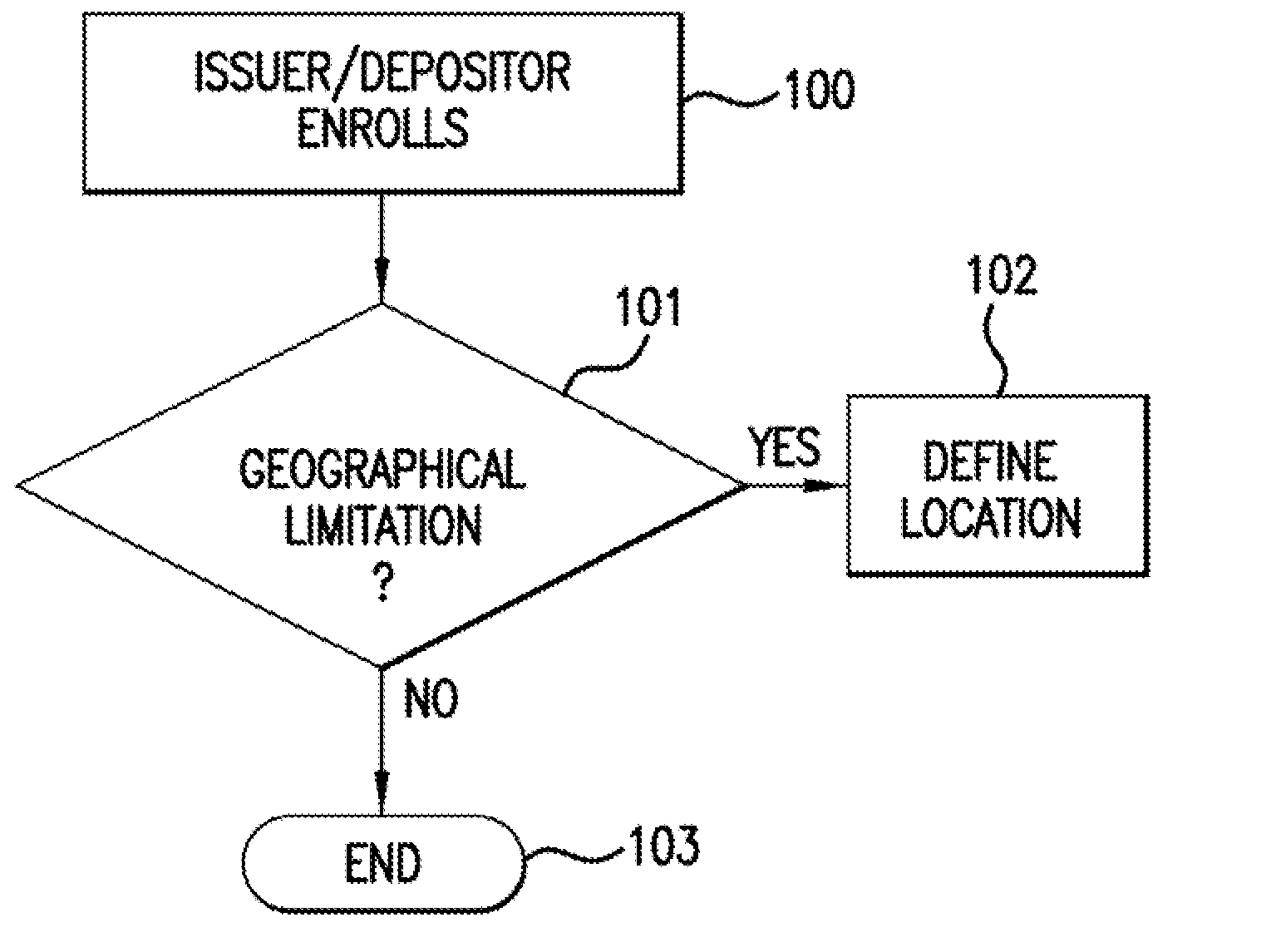
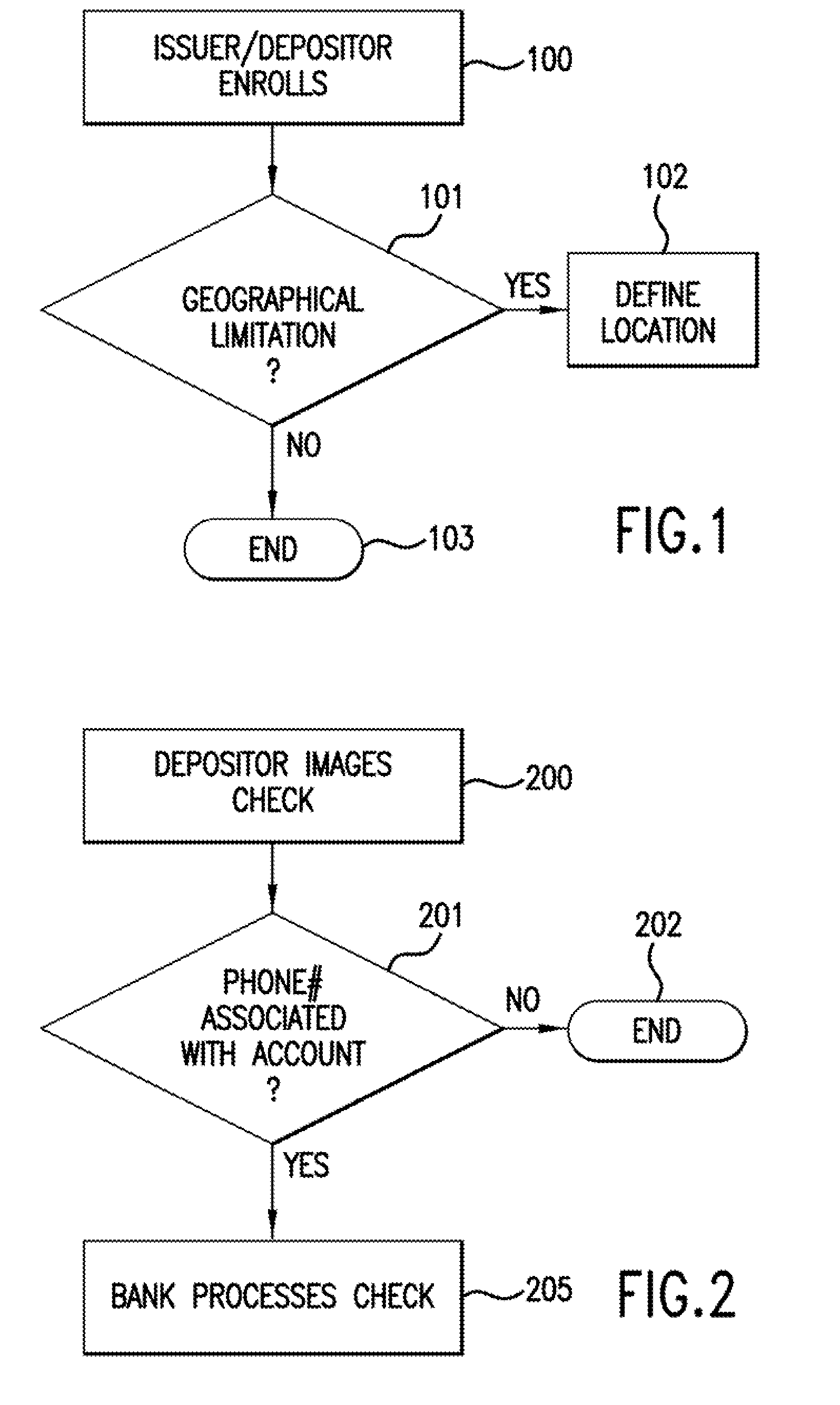
Method for remote check deposit
InactiveUS20100082470A1Without usingReduce operating costsFinancePayment architectureImaging qualityBank account
A method and system for depositing a negotiable instrument, such as a check, using a cellular phone camera. The customer images the check for deposit by taking a photograph of the check with his cellular phone camera and sends the photograph as a MMS to the customer's bank. The system enables validating image quality, automatically recognizing code line, confirming geographical location of the deposit and verifying a courtesy amount of the check so that the check is deposited into the customer's bank account remotely.
Owner:IBM CORP
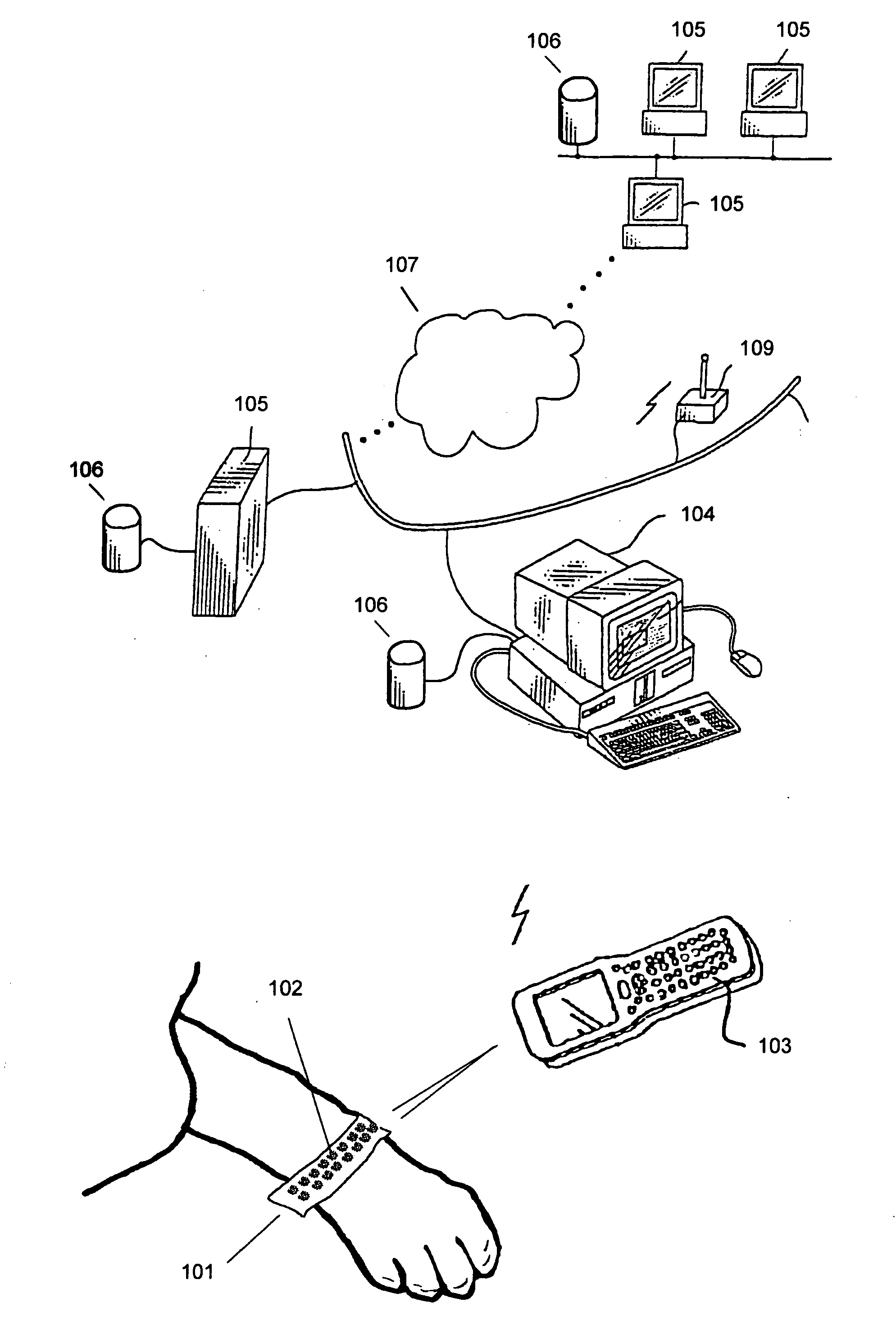
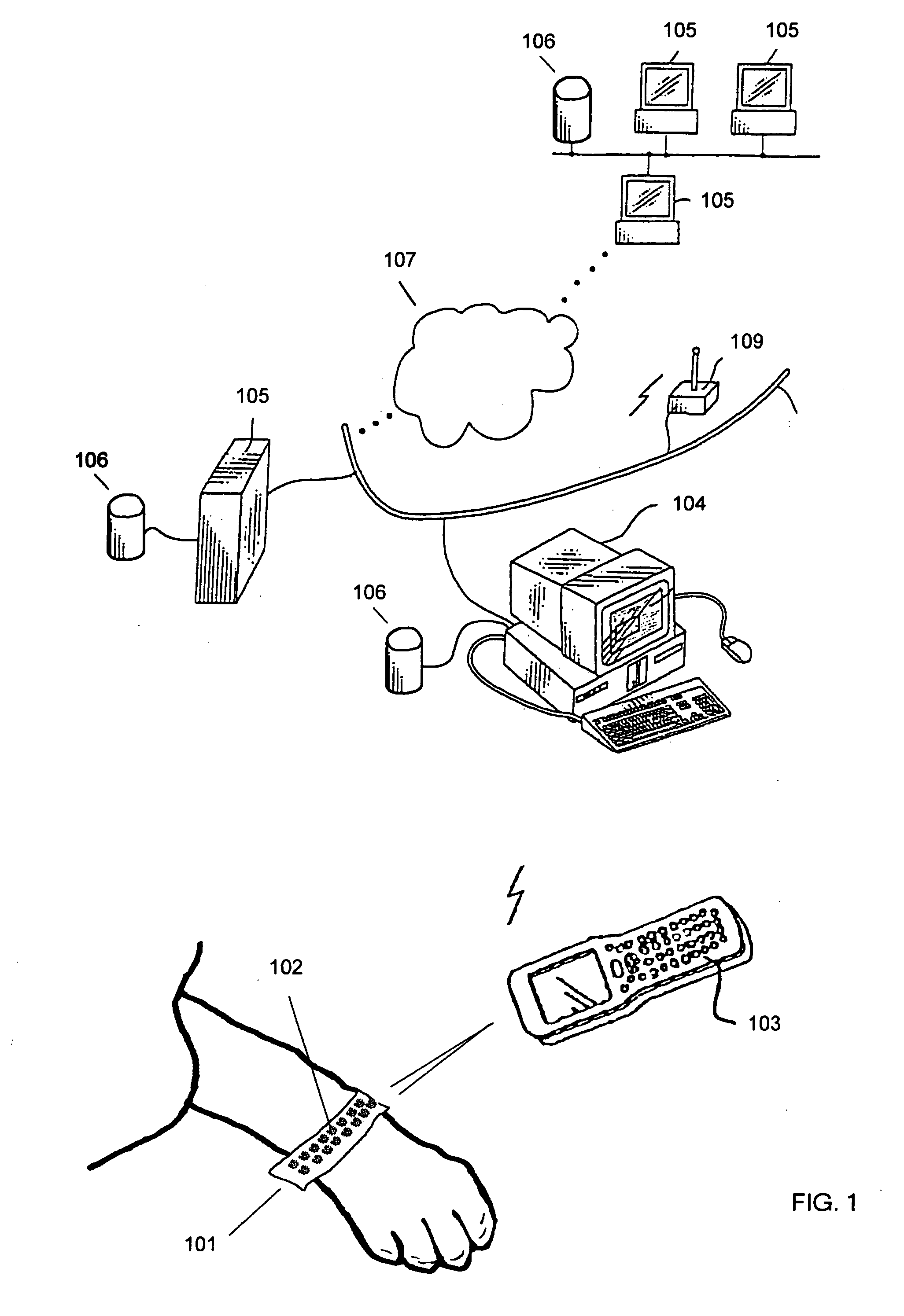
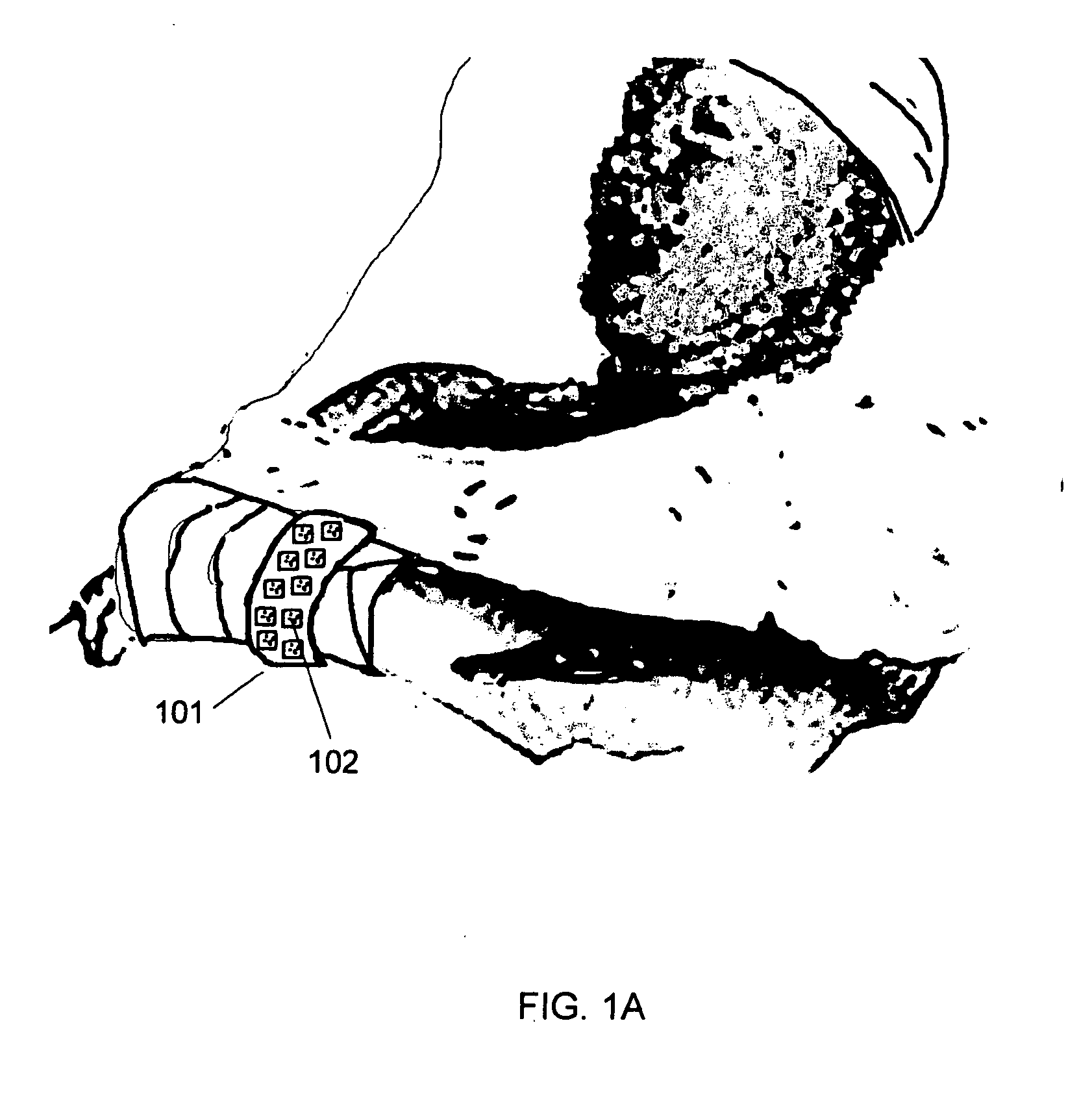
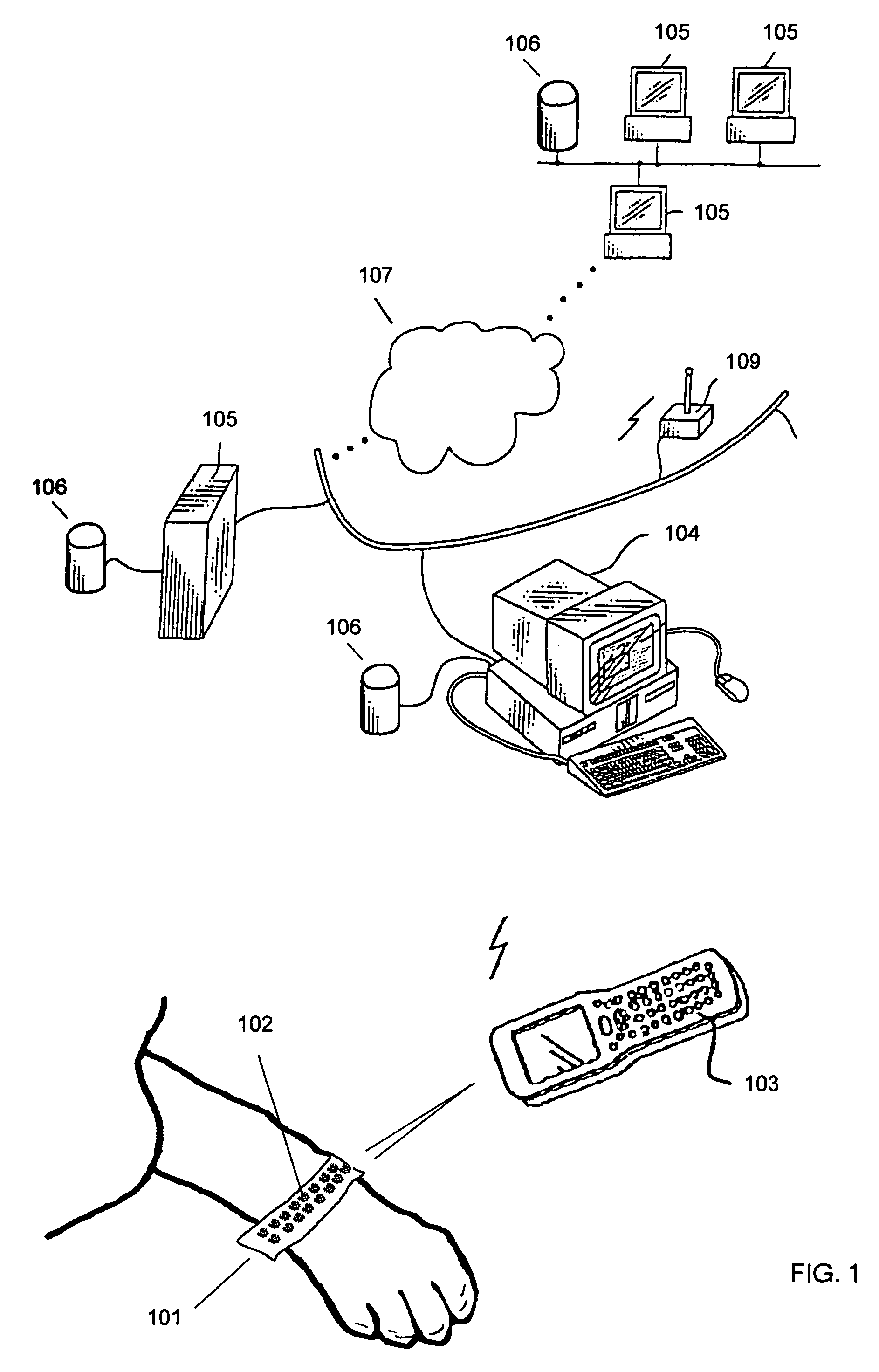
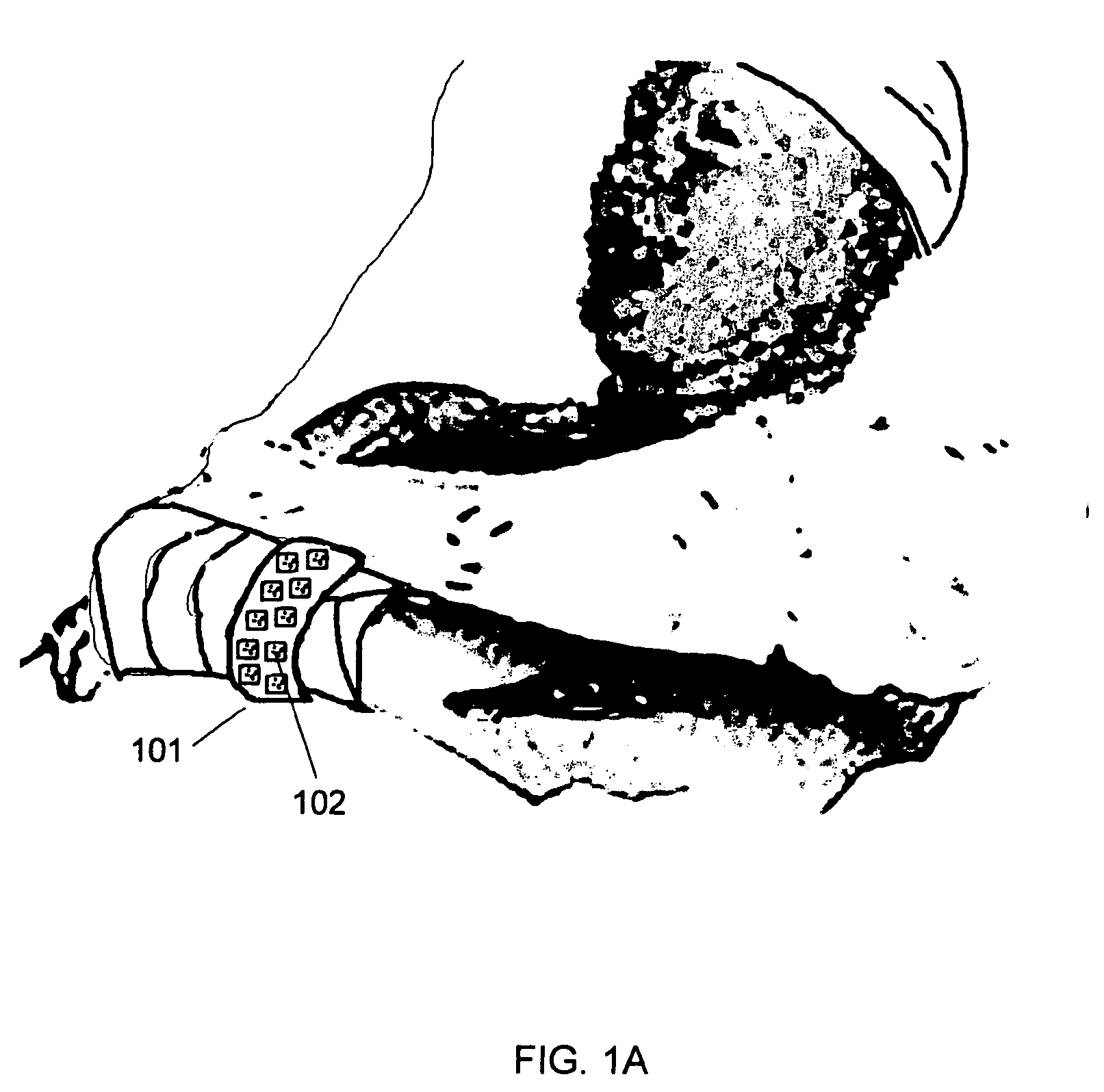
Bar coded wristband
A bar coded patient wristband identifies a patient wearing the wristband. The system comprises a bar code reader to read the bar coded wristband. A host computer is connected to the digital link to receive the segment of data from the bar code reader. A database correlates the segment of data to a patient to identify the patient. The patient wristband comprises a plurality of bar code symbols. A computer then retrieves a patient record from the database to identify the patient wearing the wristband. In one embodiment, a patient wristband for identifying a patient accepts a plurality of markings of 2 D bar codes distributed along the strip. In another embodiment, the wristband comprises a plurality of linear bar code lines and spaces distributed along the strip. The lines and spaces form a 1 D bar code.
Owner:HAND HELD PRODS
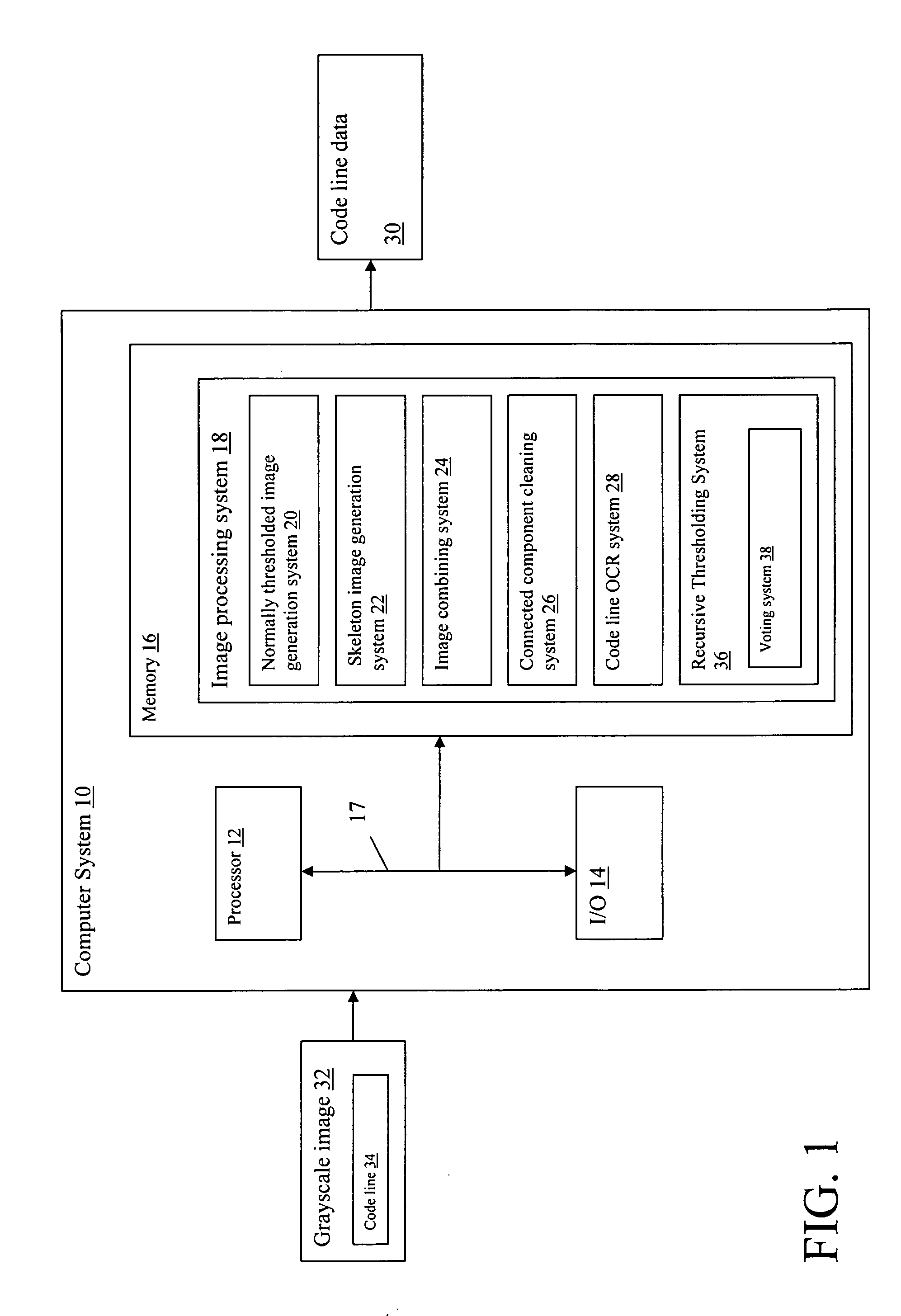
Gray scale image cleaning system and method
ActiveUS20070041629A1Improved check code line OCRRaise the thresholdCharacter recognitionImaging processingComputer science
A gray scale image cleaning algorithm for improved check code line OCR. An image processing system for processing a gray scale image is provided that includes: a system for generating a first thresholded black white image from the gray scale image; a system for generating a second thresholded black white image from the gray scale image, wherein the second thresholded black white image is generated with a higher threshold value than the first thresholded black white image; and a system for logically combining the first and second thresholded black white images to generate a composite image.
Owner:IBM CORP
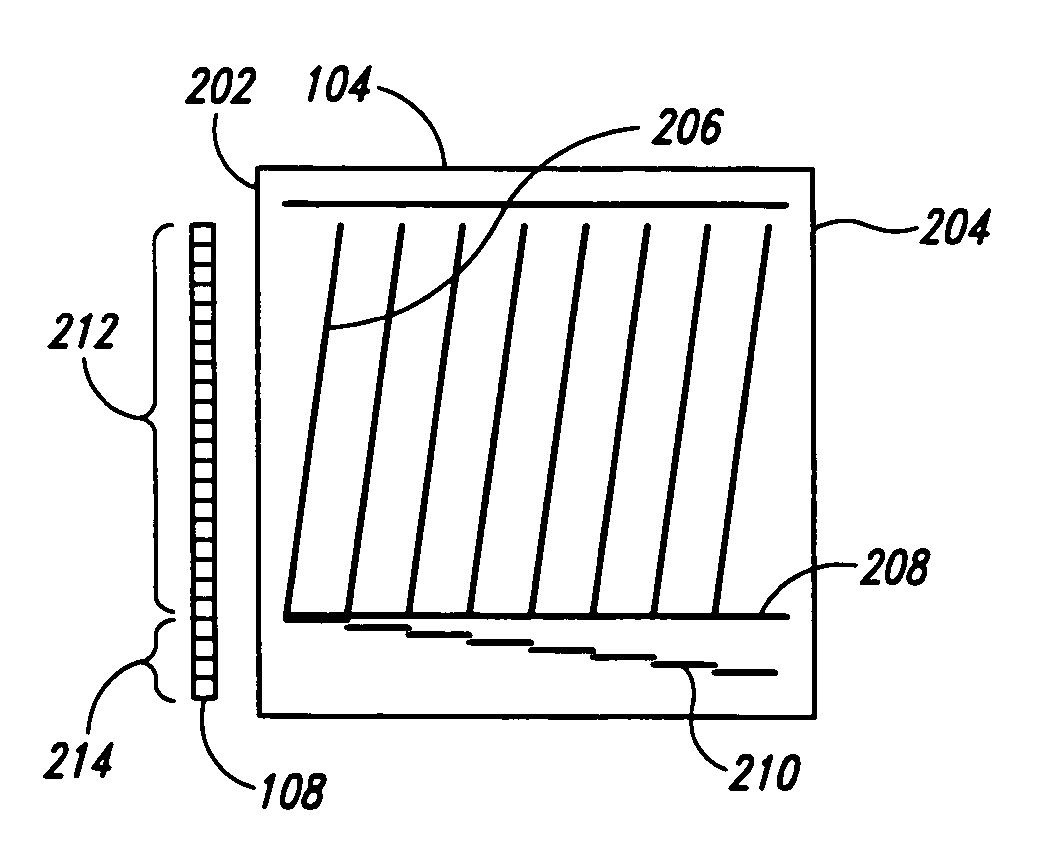
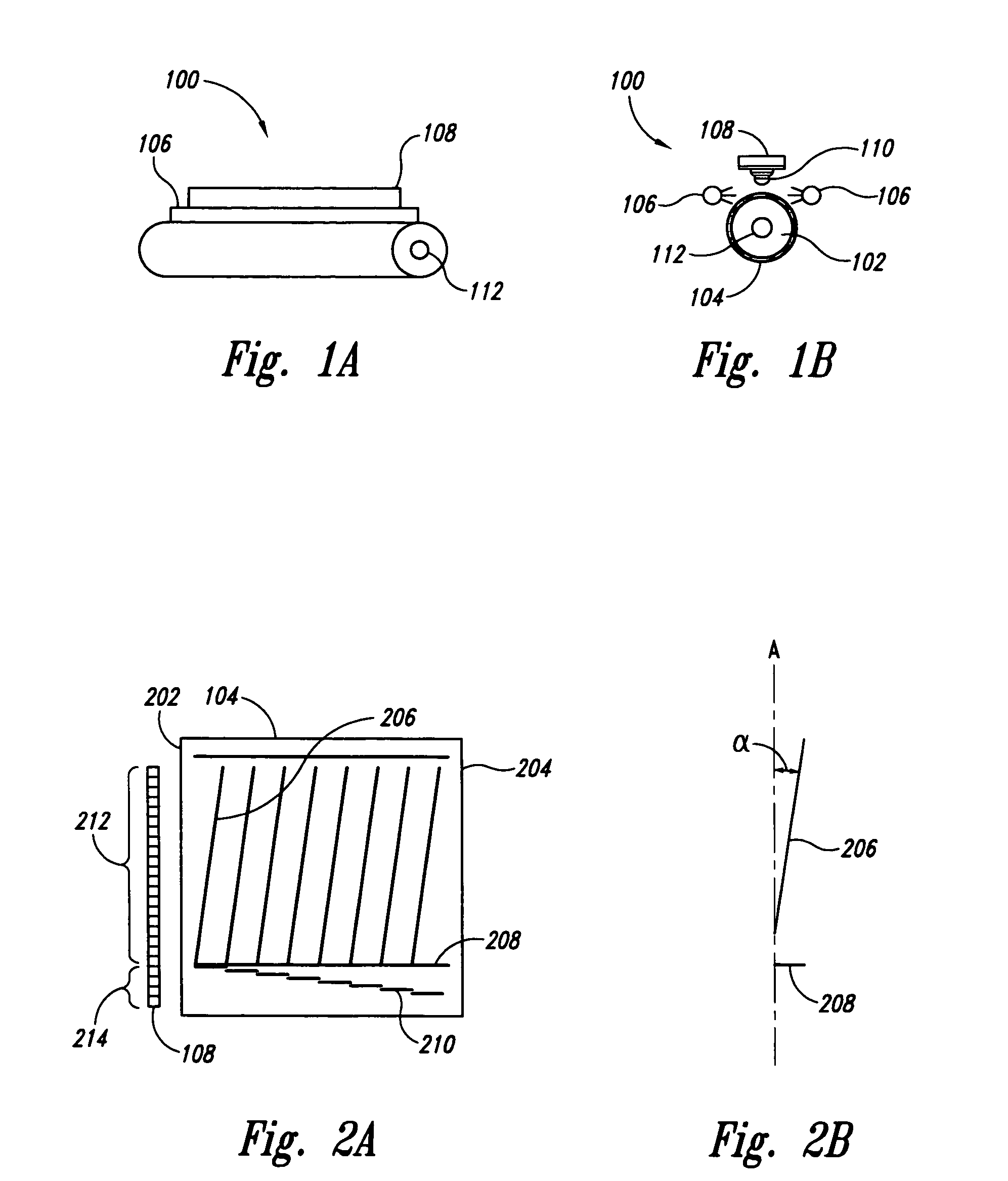
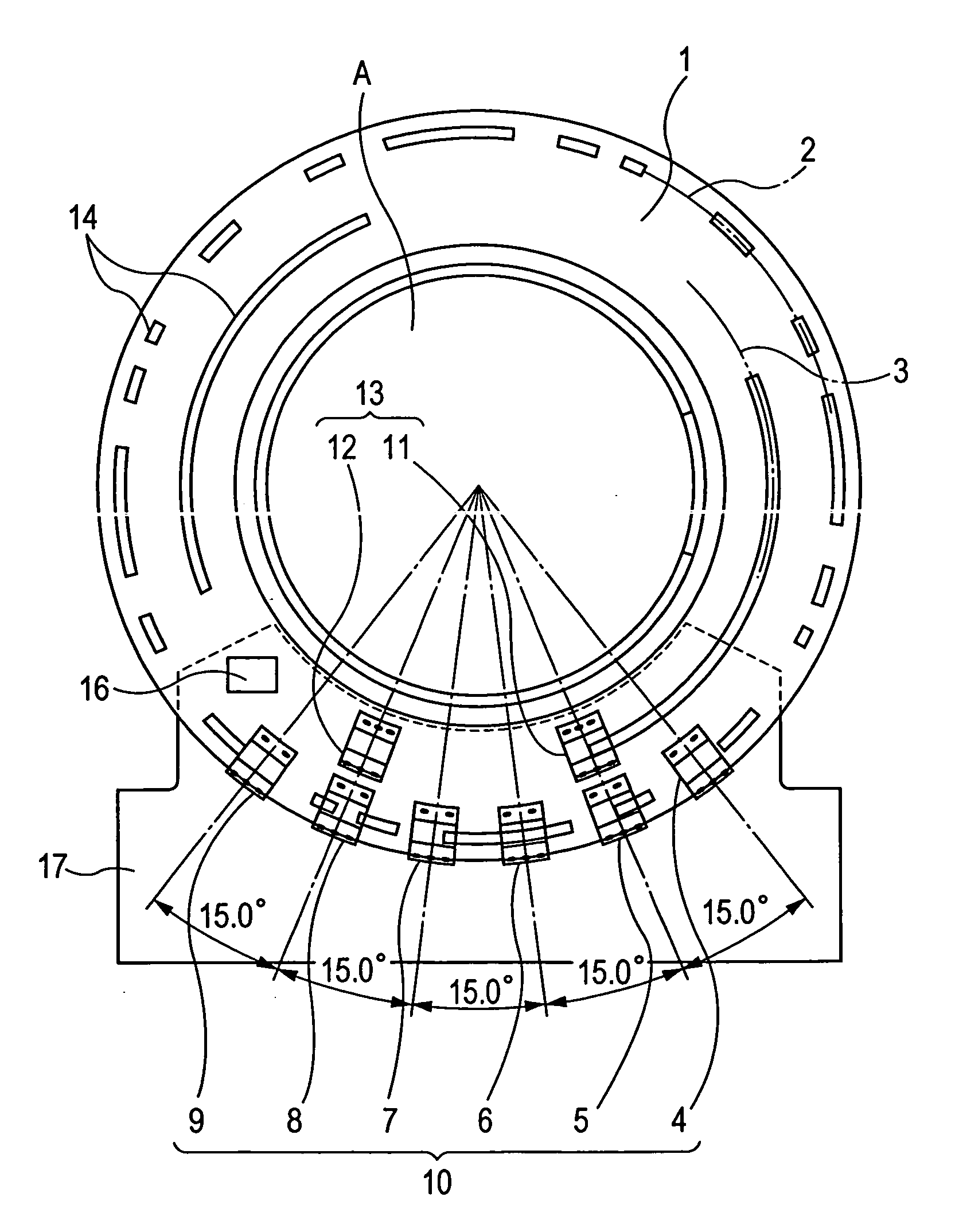
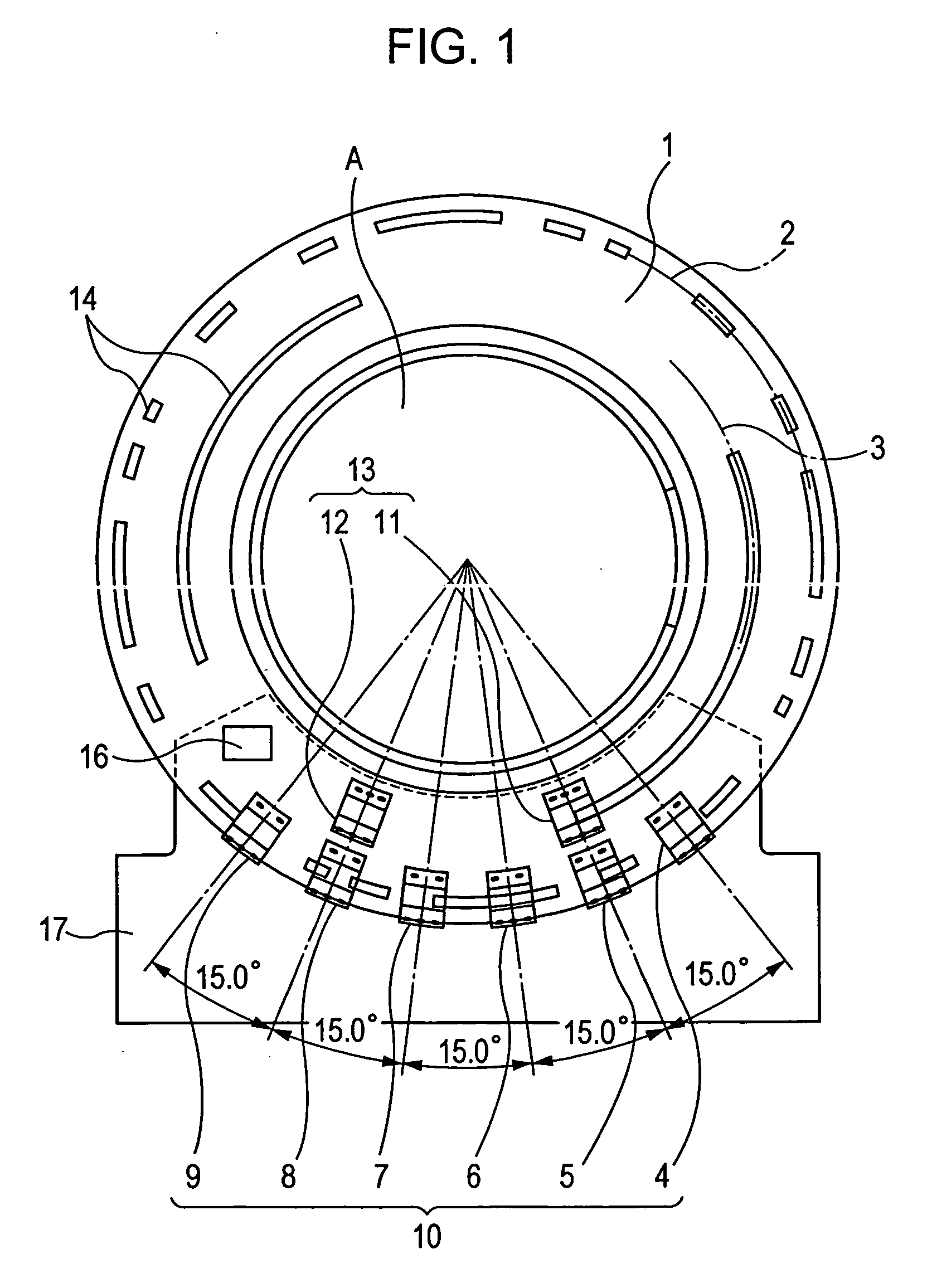
Imaging rotation angle absolute encoder
ActiveUS7135673B2Accurate measurementImprove accuracyOptical measurementsMaterial analysis by optical meansImage rotationEncoder
An angle absolute encoder comprises an encoded code rod that has code marks, such as pairs of fine code lines and coarse code lines. Light is reflected from or transmitted through the code marks and detected by a light detector to determine absolute angle position.
Owner:THE BOEING CO
On-line correction of check code line recognition in point-of-sale stations
InactiveUS20060144937A1Rapid and reliable check code line recognitionHigh quality character recognitionCo-operative working arrangementsCash registersData entryCode line
Methods and systems are provided for check code line recognition at a point-of-sale terminal having OCR and MICR capabilities. Images of problematic characters are extracted and automatically transmitted to a remote location for on-line manual validation or data entry. Video coding of problematic characters is performed for the correction of either or both MICR and OCR results. The correctly encoded characters are returned to the point of sale within a few seconds, and combined as necessary with locally recognized characters, to assemble a correct code line for entry into a payment system.
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
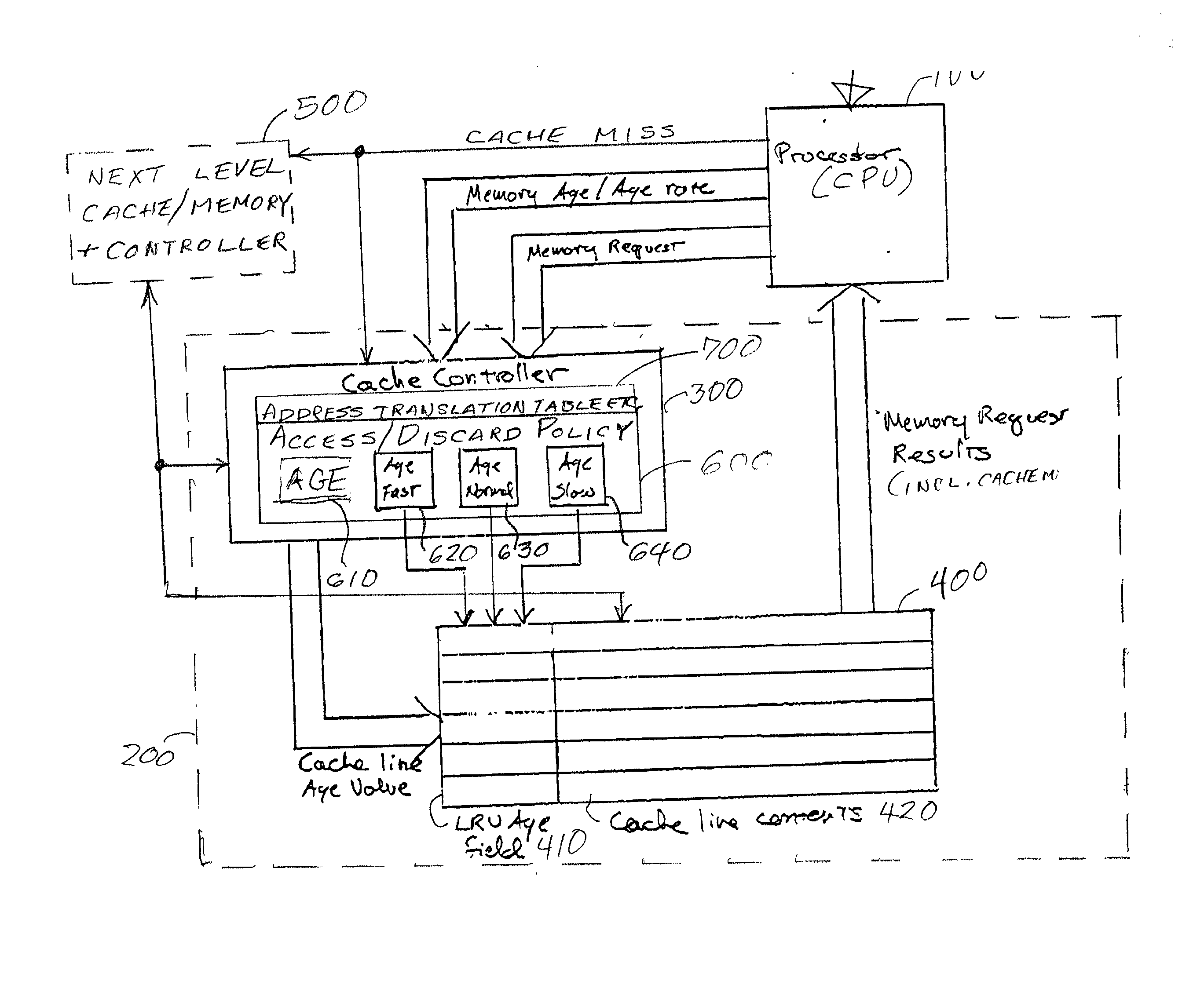
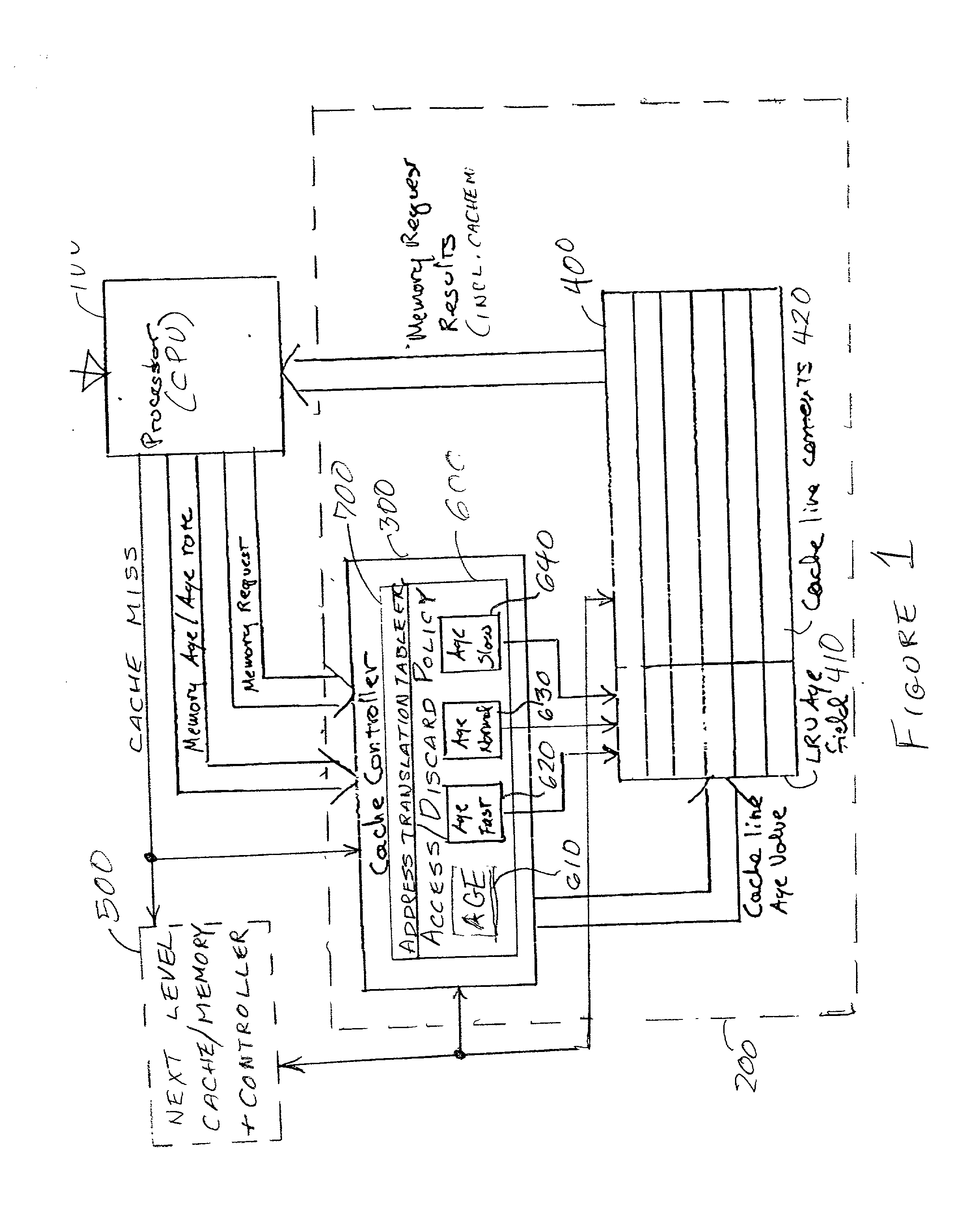
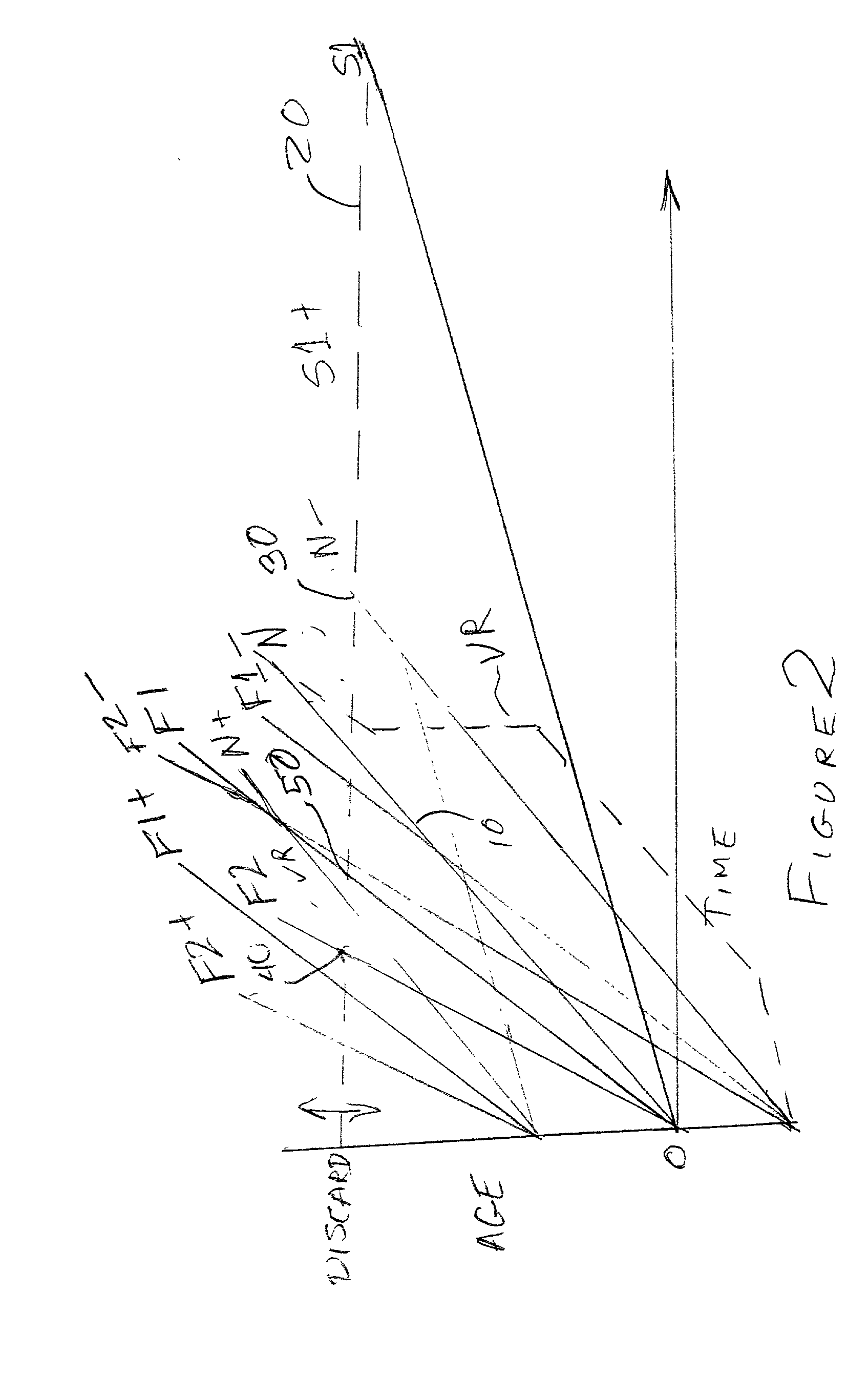
Directed least recently used cache replacement method
InactiveUS20020152361A1Performance maximizationImprove cache hit ratioEnergy efficient ICTMemory adressing/allocation/relocationParallel computingLeast recently frequently used
Fine grained control of cache maintenance resulting in improved cache hit rate and processor performance by storing age values and aging rates for respective code lines stored in the cache to direct performance of a least recently used (LRU) strategy for casting out lines of code from the cache which become less likely, over time, of being needed by a processor, thus supporting improved performance of a processor accessing the cache. The invention is implemented by the provision for entry of an arbitrary age value when a corresponding code line is initially stored in or accessed from the cache and control of the frequency or rate at which the age of each code is incremented in response to a limited set of command instructions which may be placed in a program manually or automatically using an optimizing compiler.
Owner:IBM CORP
System and Method For Image Depositing, Image Presentment and Deposit Taking in a Commercial Environment
InactiveUS20100306111A1Low costExtension of timeComplete banking machinesDigitally marking record carriersChequeDatabase
Owner:CITIBANK +1
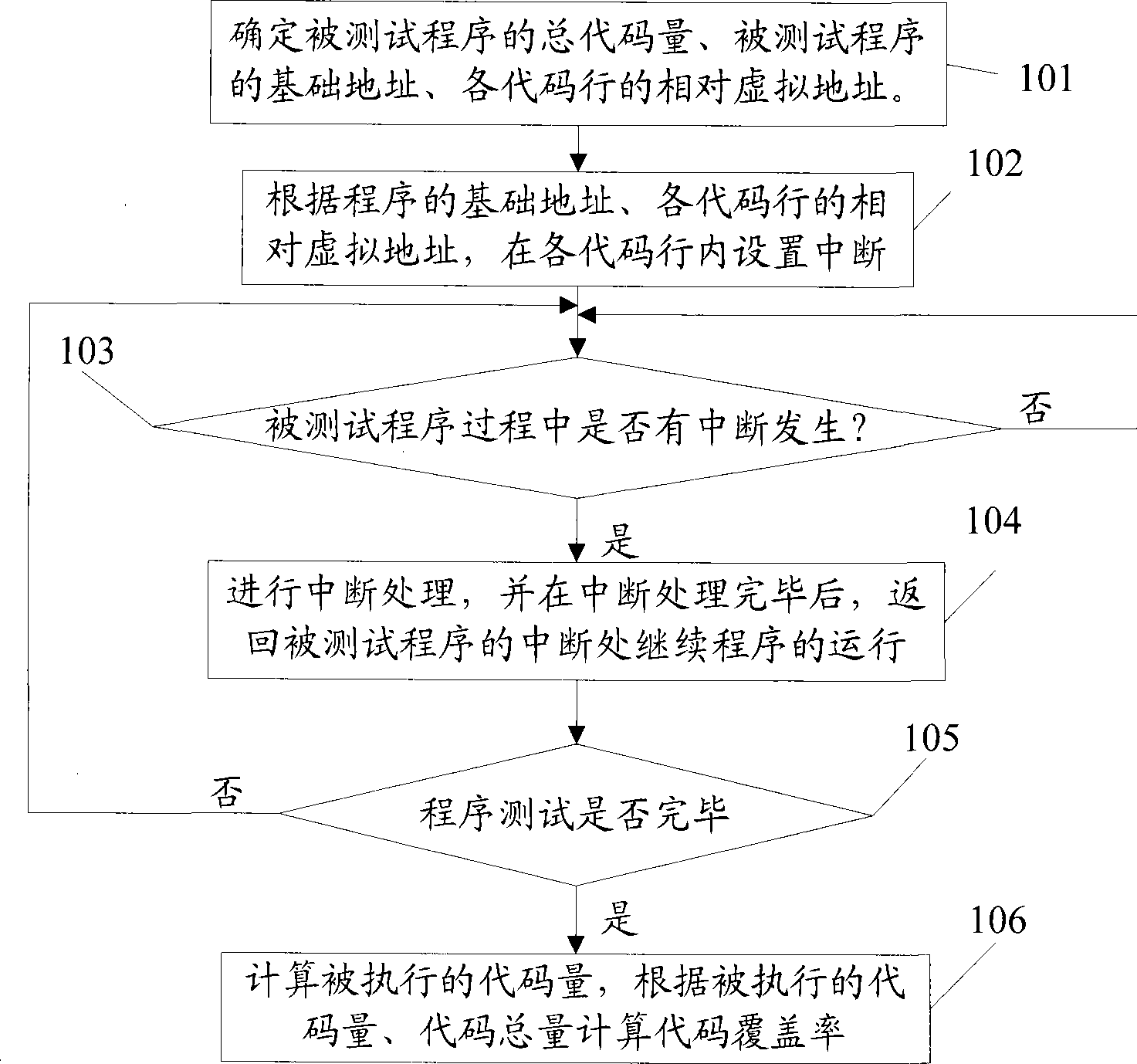
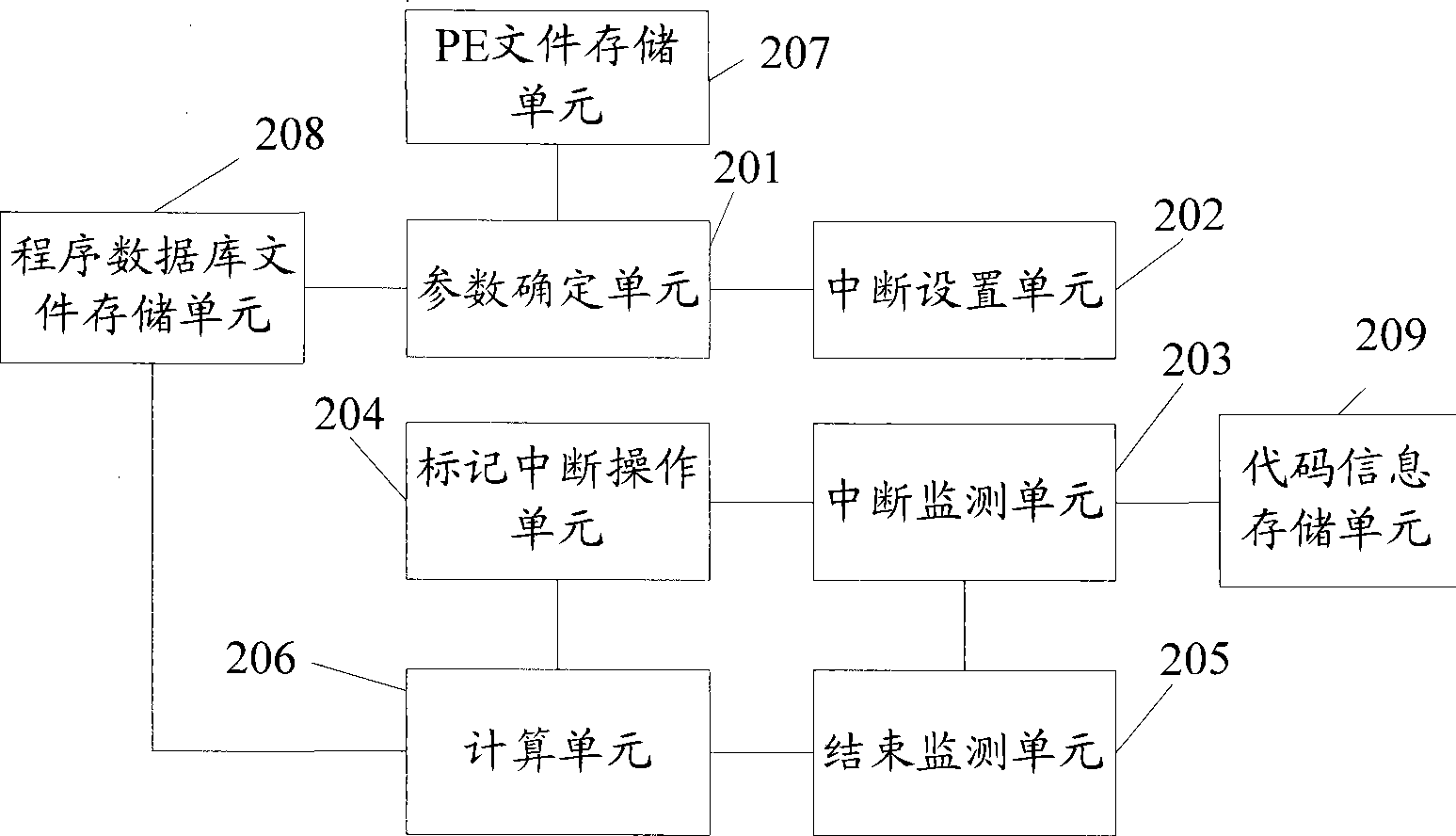
Method and test device for confirming code coverage rate
ActiveCN101464829AGuaranteed stabilityGet detailsSoftware testing/debuggingCode coverageTest fixture
The invention relates to the computer field. The embodiment of the invention discloses a method for confirming code coverage and a test method thereof. The test method comprises the following steps: confirming the total code amount and the basic address of a tested program, as well as relative virtual addresses of all code lines; setting interruption in the code lines according to the basic address and the virtual addresses of the code lines; detecting whether interruption takes place in the process of the tested program, if yes, marking the code line the interruption belongs; detecting whether the test is completed, if no, returning to the step of detecting whether interruption takes place, and if yes, accumulating marked total code in the code lines to acquire executed total code amount; and obtaining the code coverage of a tested program according to the executed total code amount and the total code amount thereof. By adopting the technical scheme of the embodiment of the invention, the code coverage of the tested program can be accurately obtained and the stability of the tested program can be guaranteed.
Owner:ZHUHAI KINGSOFT SOFTWARE CO LTD
Method and device for display stream compression
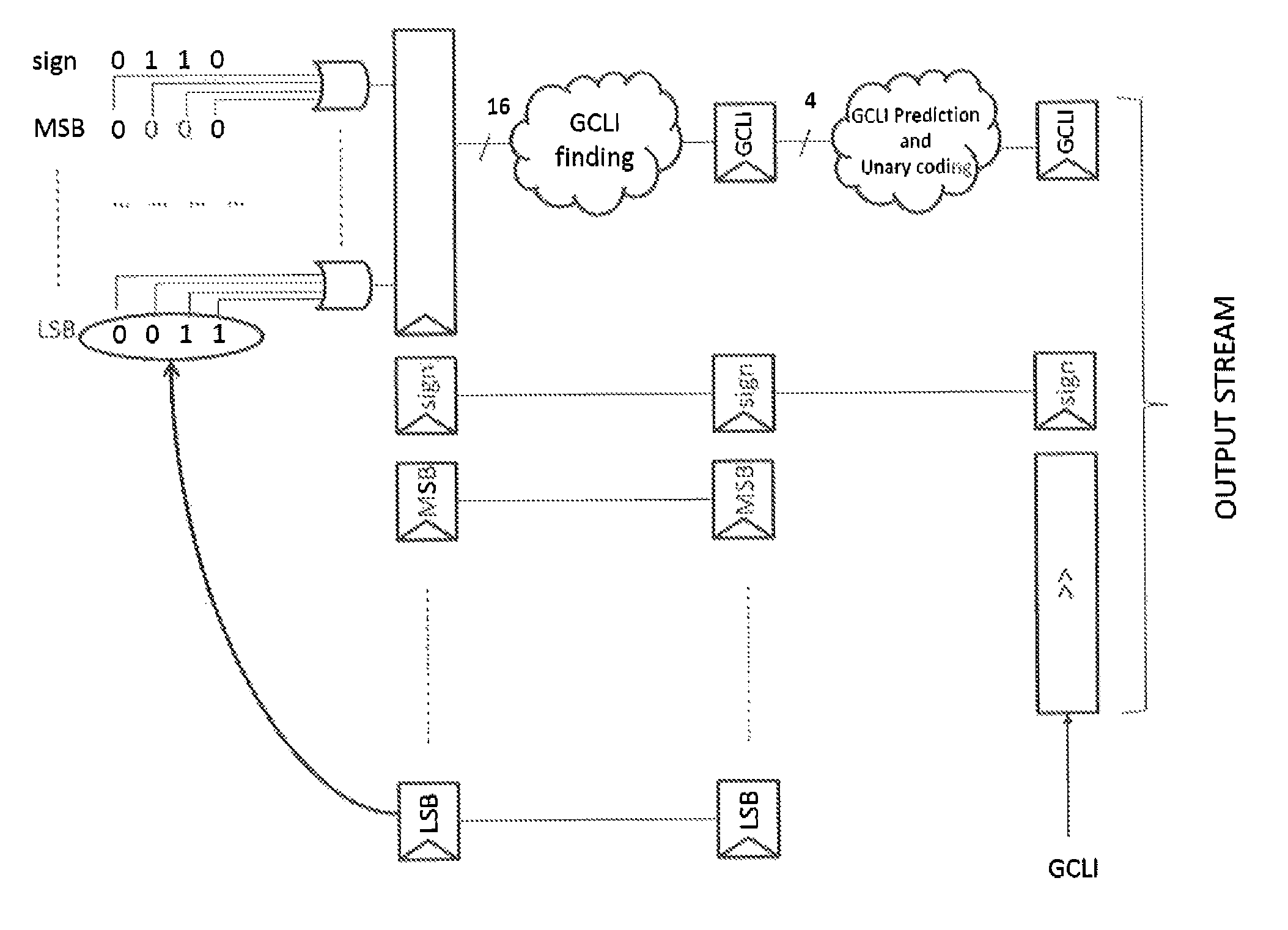
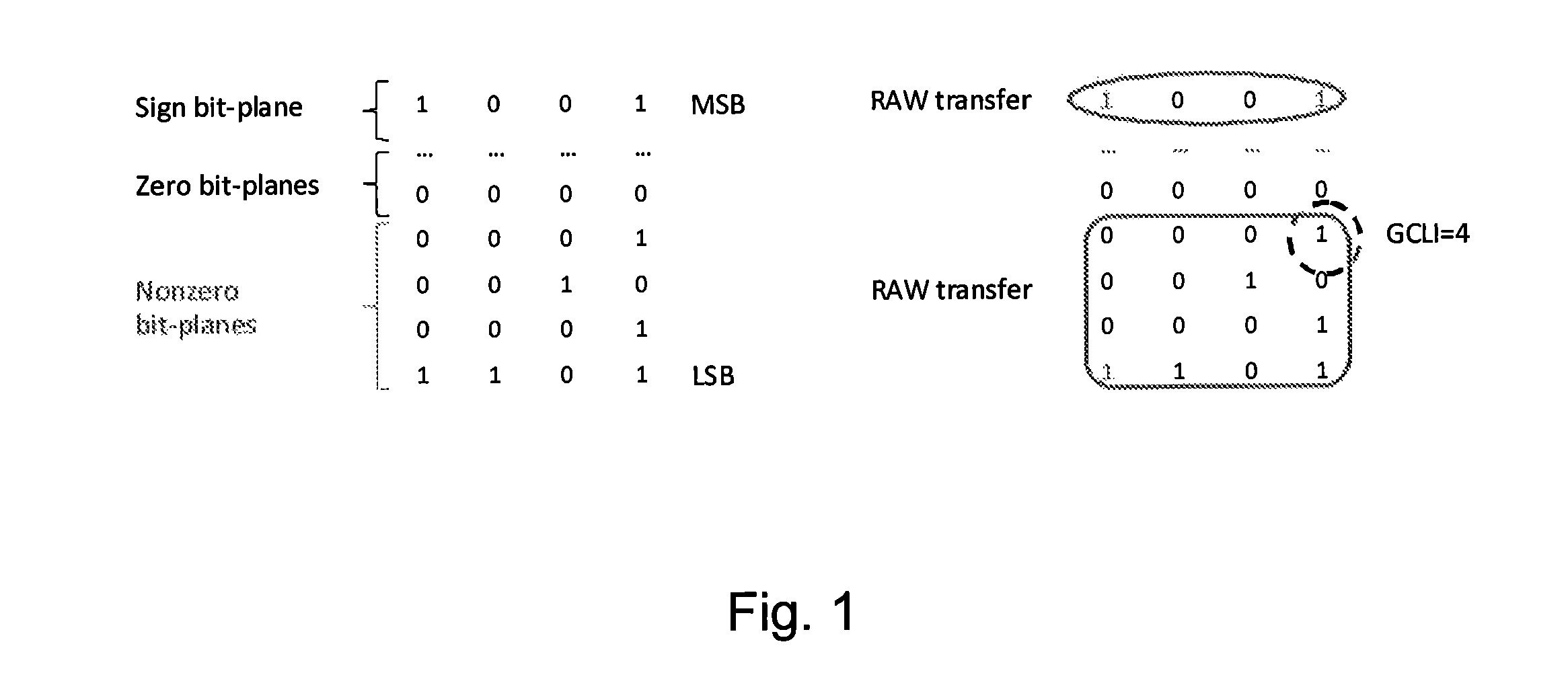
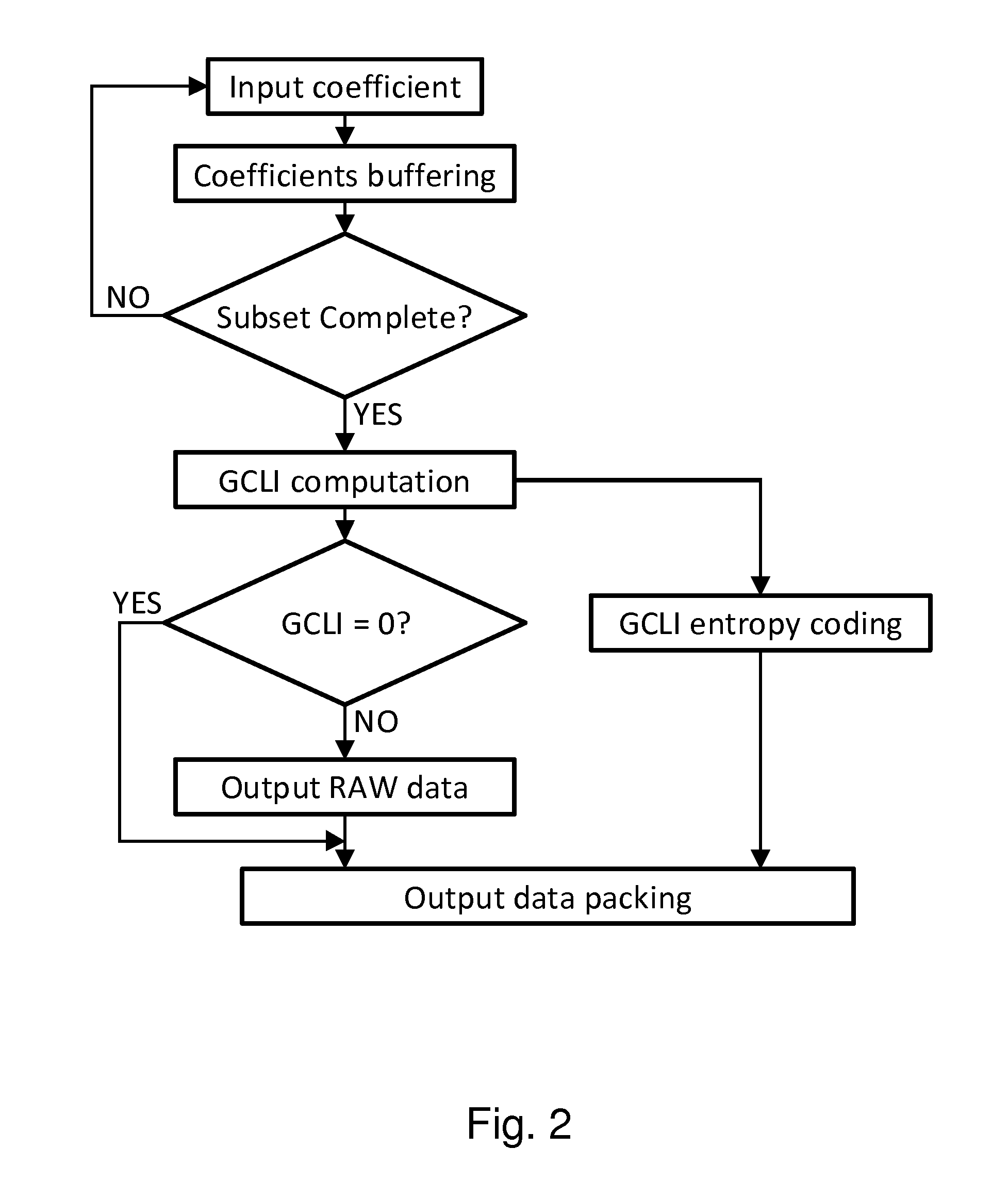
ActiveUS9332258B2Efficient compressionMinimize complexityCharacter and pattern recognitionDigital video signal modificationComputer engineeringCode line
A method and a device compress a display stream wherein coefficients are grouped, for each group, the greatest coded line index (GCLI) is determined and only the GCLI lowest weight bits of the coefficients are copied into the output stream together with the value of the GCLI. The method and device provide a good compression efficiency together with a simple hardware.
Owner:INTOPIX
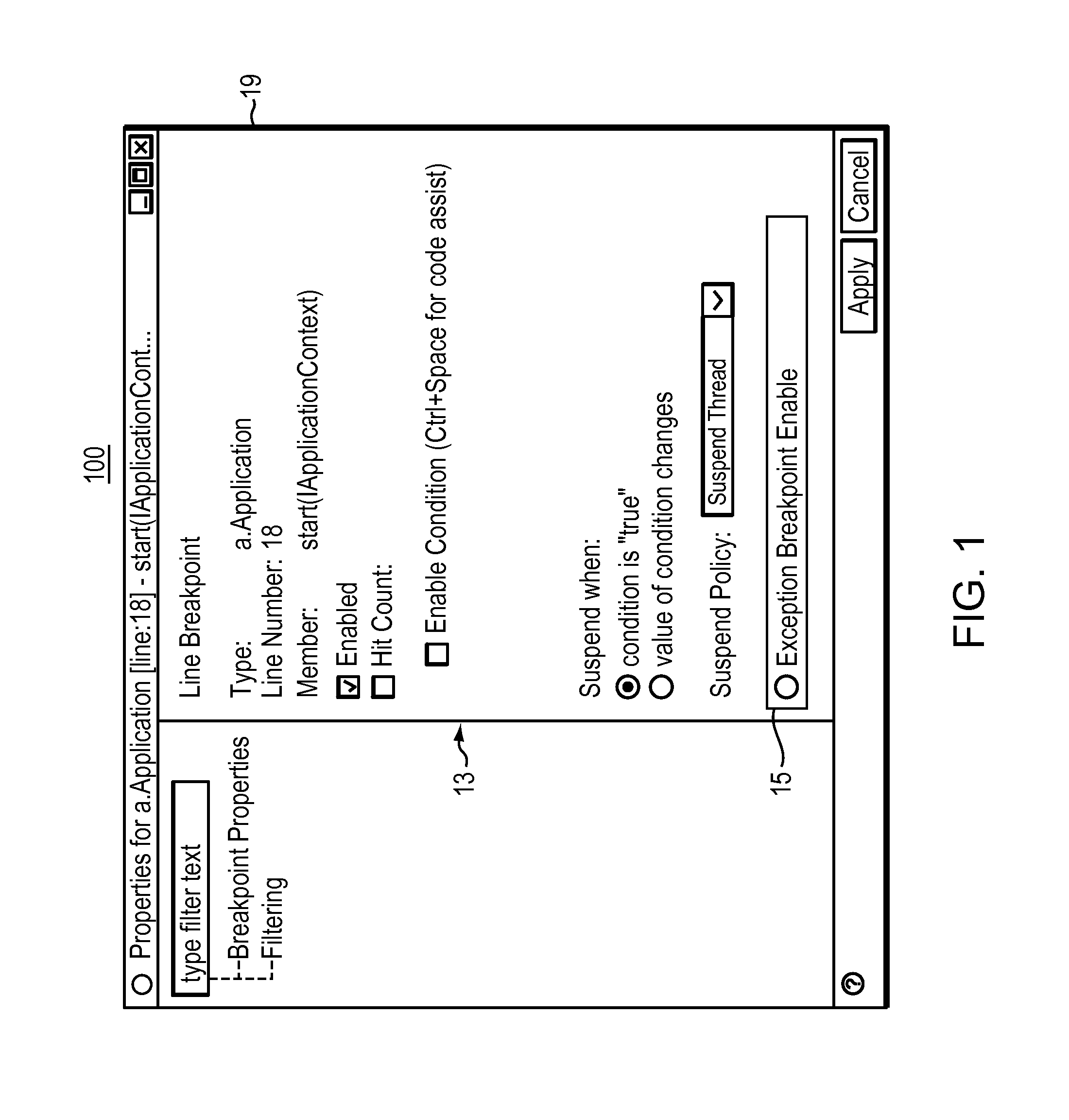
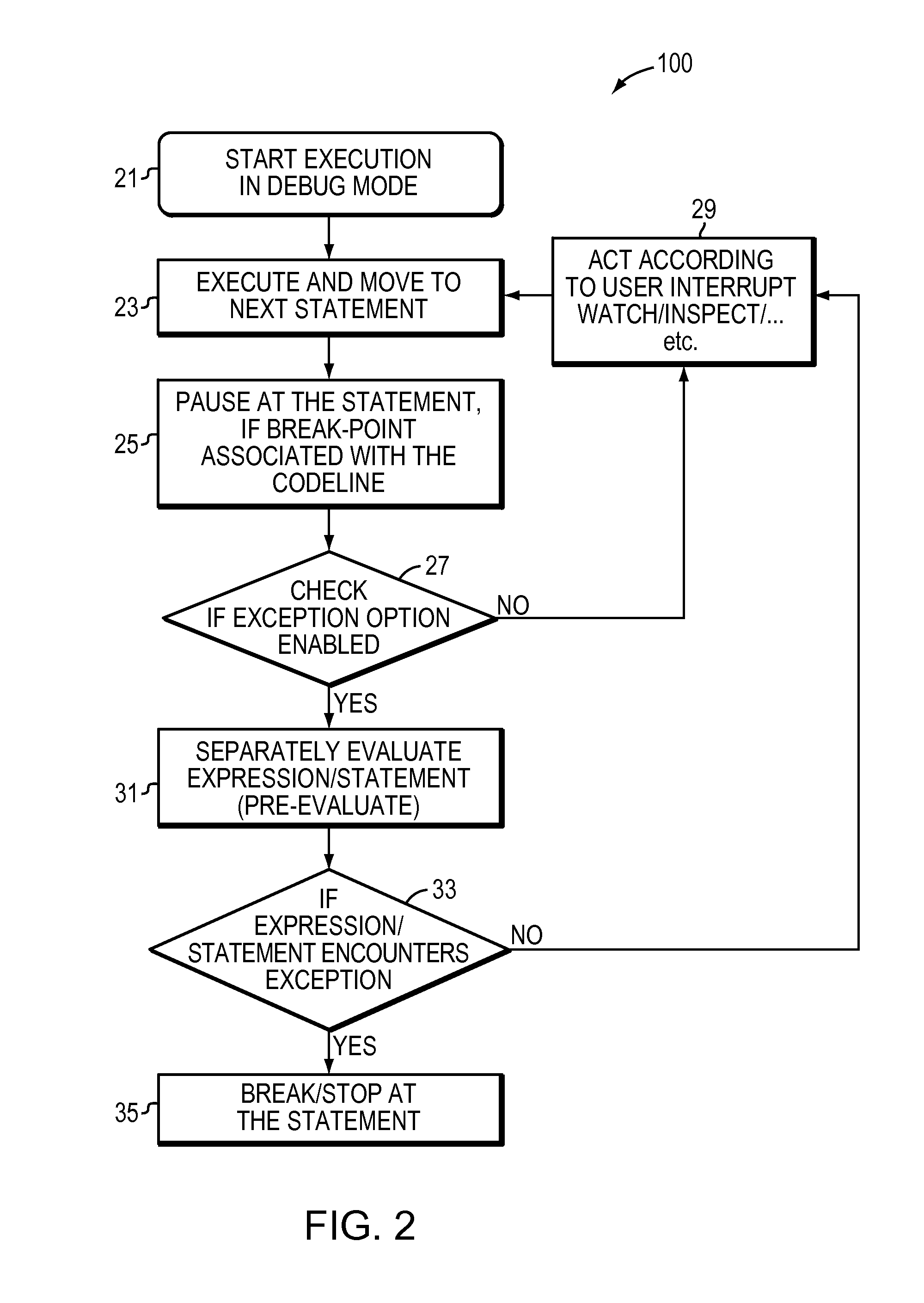
Computer code debugging method and apparatus providing exception breakpoints
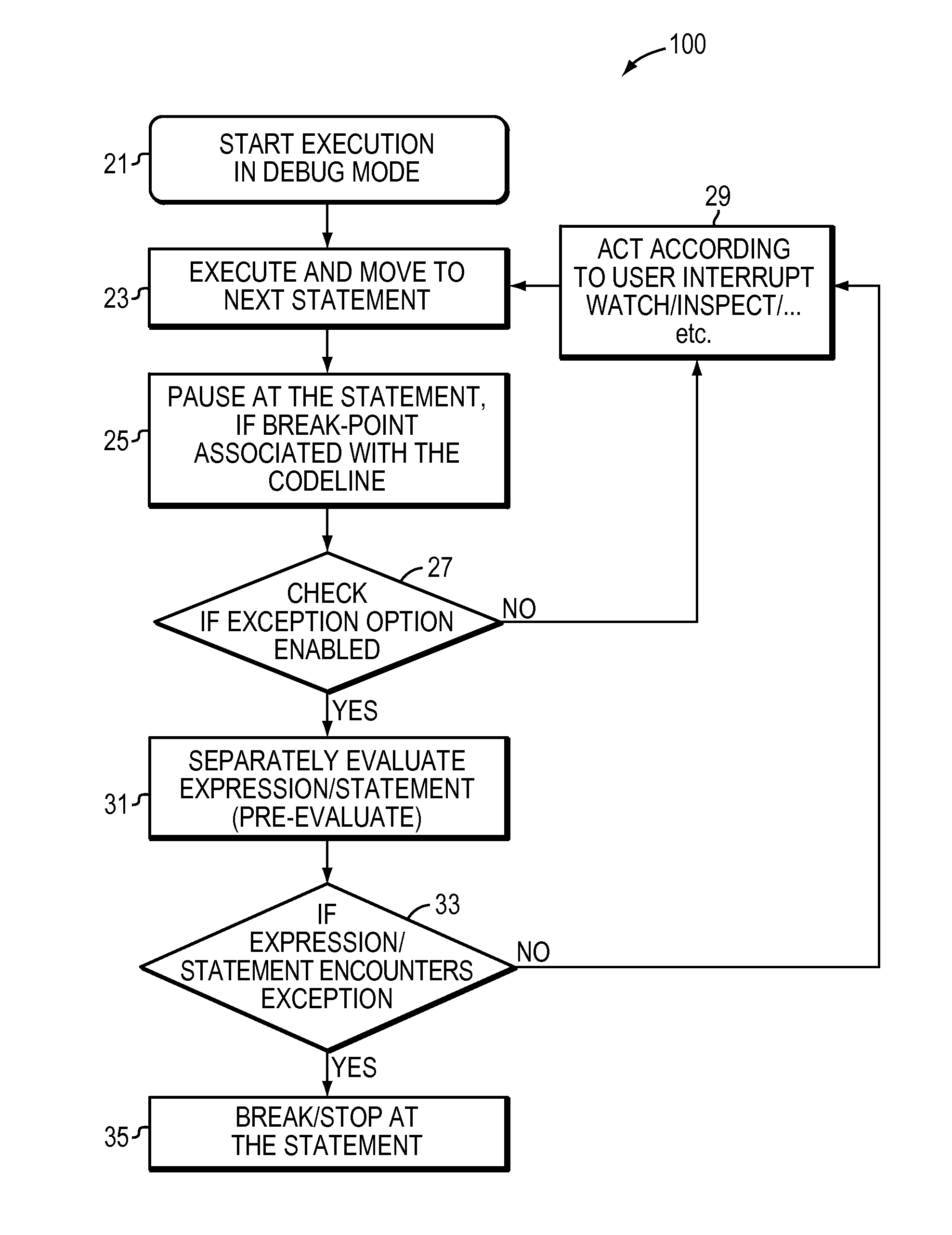
InactiveUS20110321017A1Stop executionSoftware testing/debuggingSpecific program execution arrangementsRunning timeUser interface
A computer method and apparatus for debugging program code provides exception breakpoints with exception notification. Through a user interface, a user associates one or more exception breakpoints with respective different certain lines of code. A computer processor is configured to execute the subject program code in debug mode. During the executing, for each of the different certain lines of code, the processor: (a) pauses to pre-evaluate and determine tendency to throw an exception or spawn an interrupt, and (b) at the certain line of code, stops execution of the subject program code only if the pre-evaluating determined existence of a would-be exception or run-time interrupt.
Owner:IBM CORP
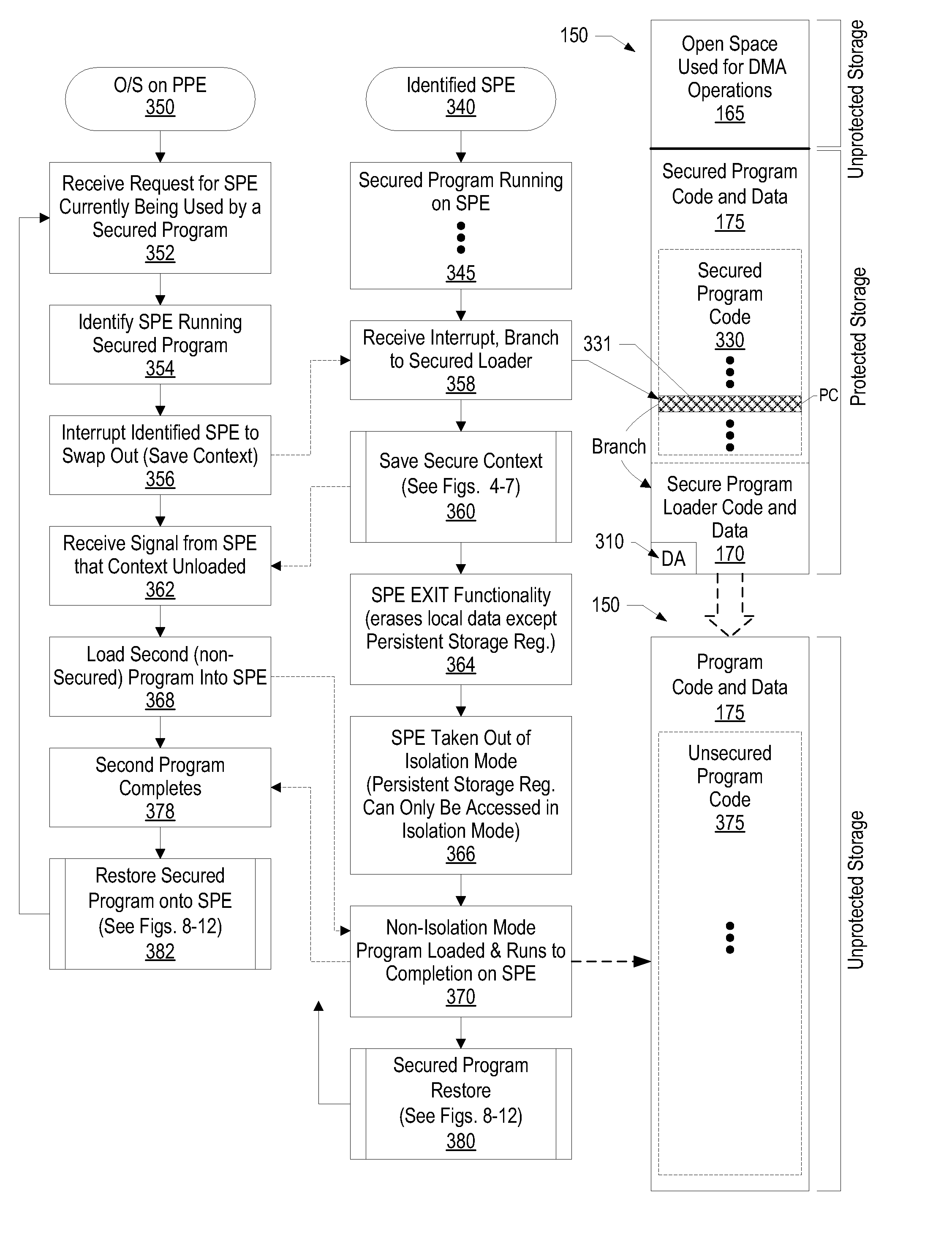
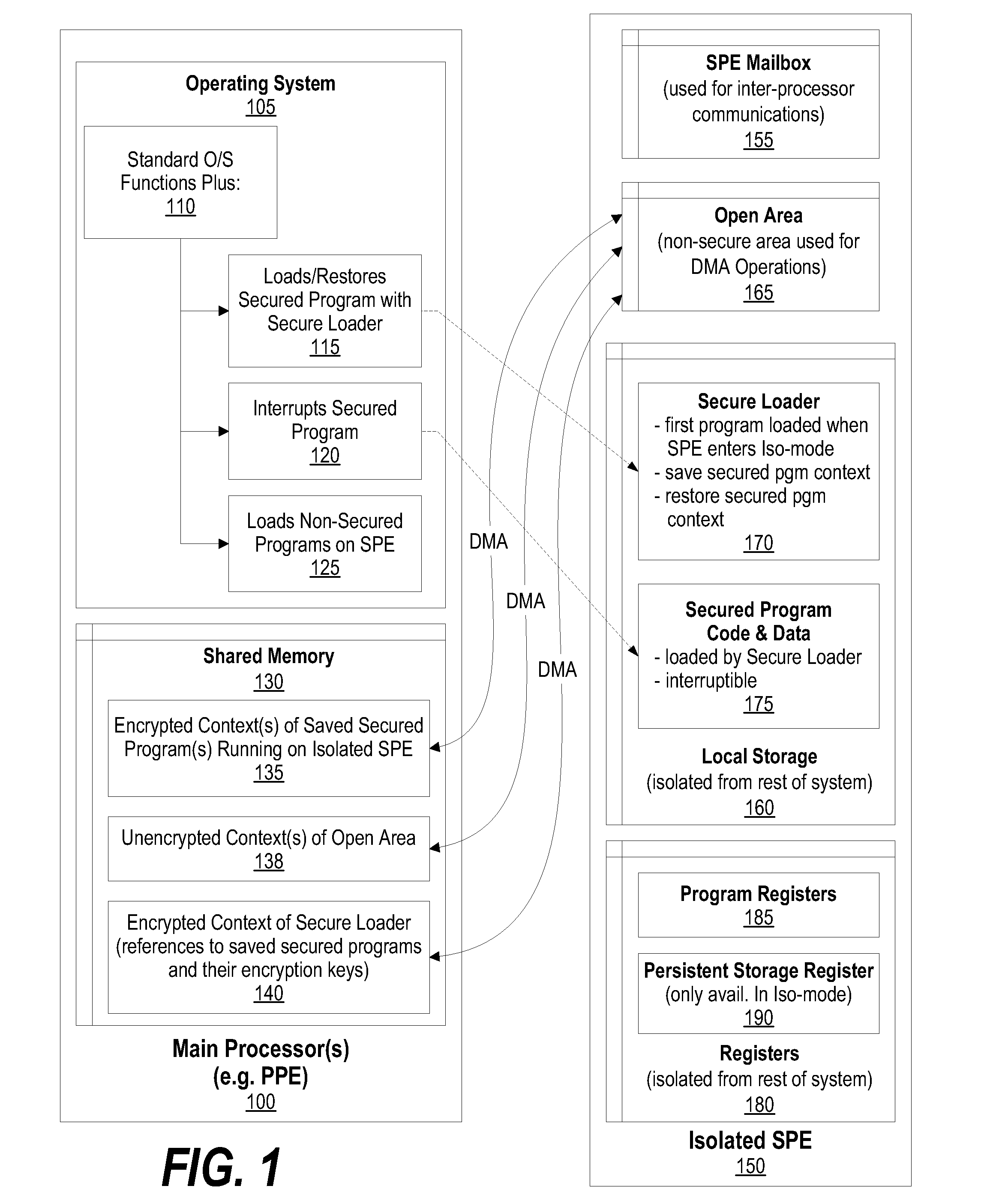
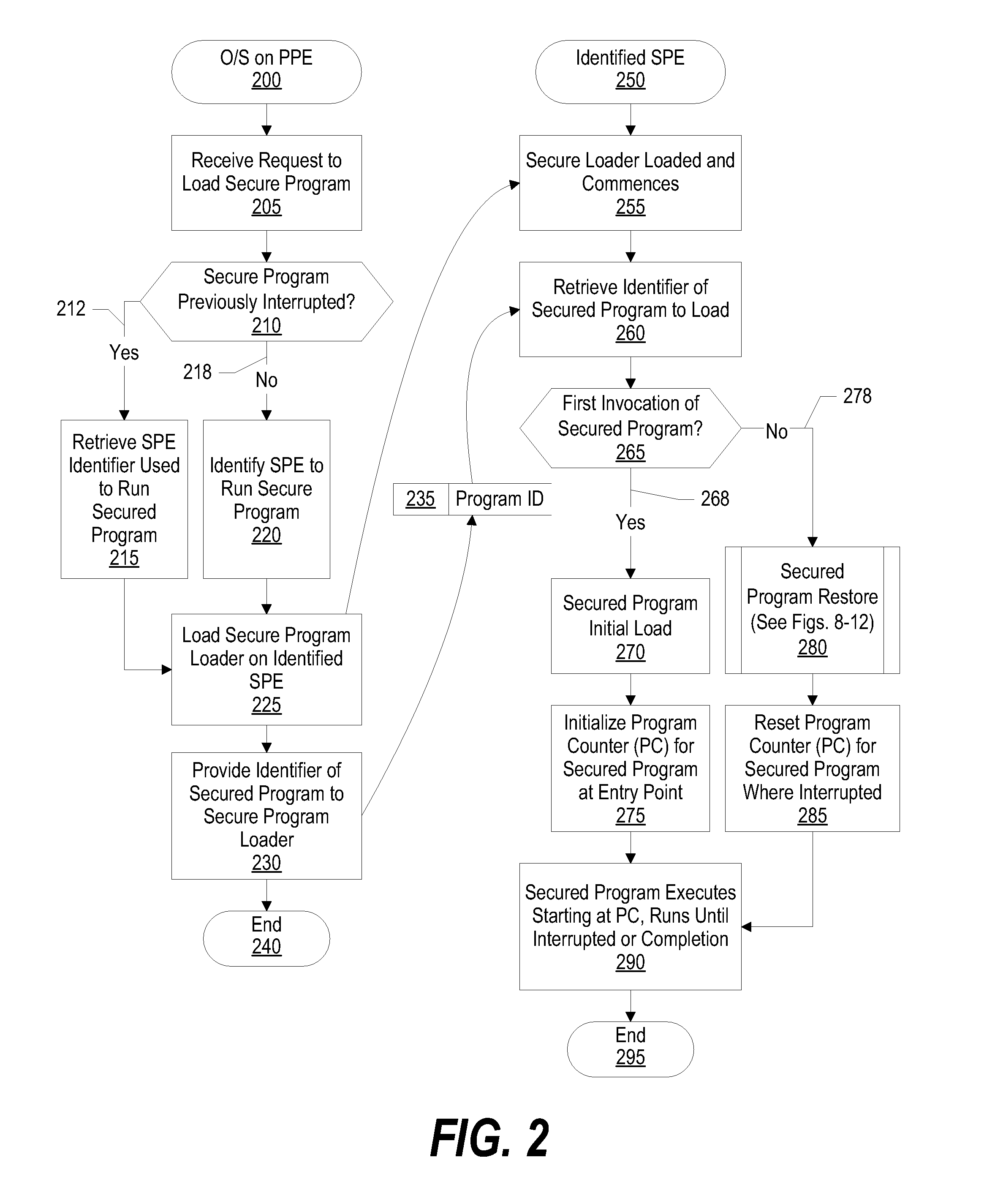
System and Method for Securely Saving a Program Context to a Shared Memory
ActiveUS20080066074A1Program control using stored programsUnauthorized memory use protectionGeneral purposeData value
A system, method and program product for securely saving a program context to a shared memory is presented. A secured program running on an special purpose processor core running in isolation mode is interrupted. The isolated special purpose processor core is included in a heterogeneous processing environment, that includes purpose processors and general purpose processor cores that each access a shared memory. In isolation mode, the special purpose processor core's local memory is inaccessible from the other heterogeneous processors. The secured program's context is securely saved to the shared memory using a random persistent security data. The lines of code stored in the isolated special purpose processor core's local memory are read along with data values, such as register settings, set by the secured program. The lines of code and data values are encrypted using the persistent security data, and the encrypted code lines and data values are stored in the shared memory.
Owner:IBM CORP
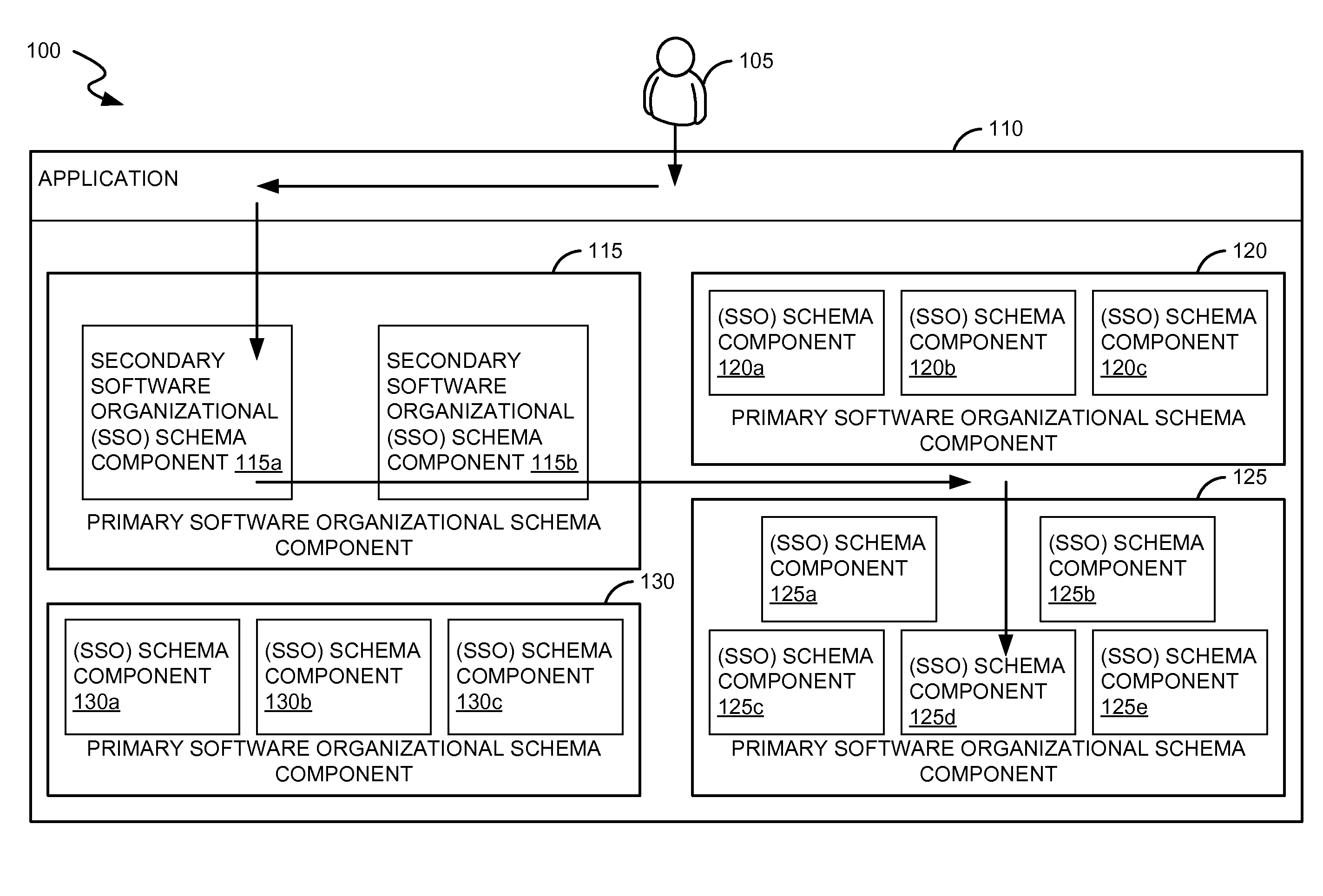
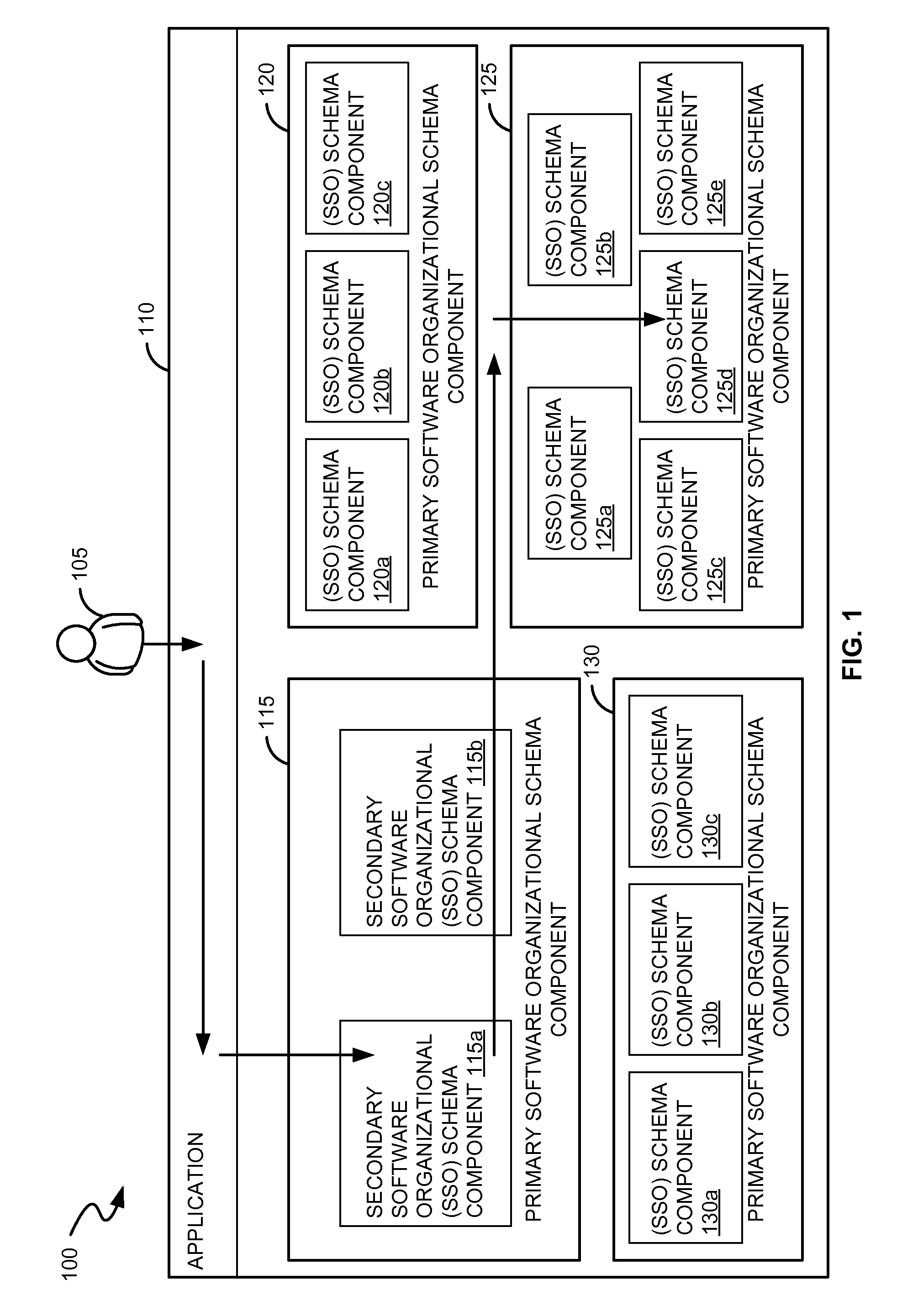
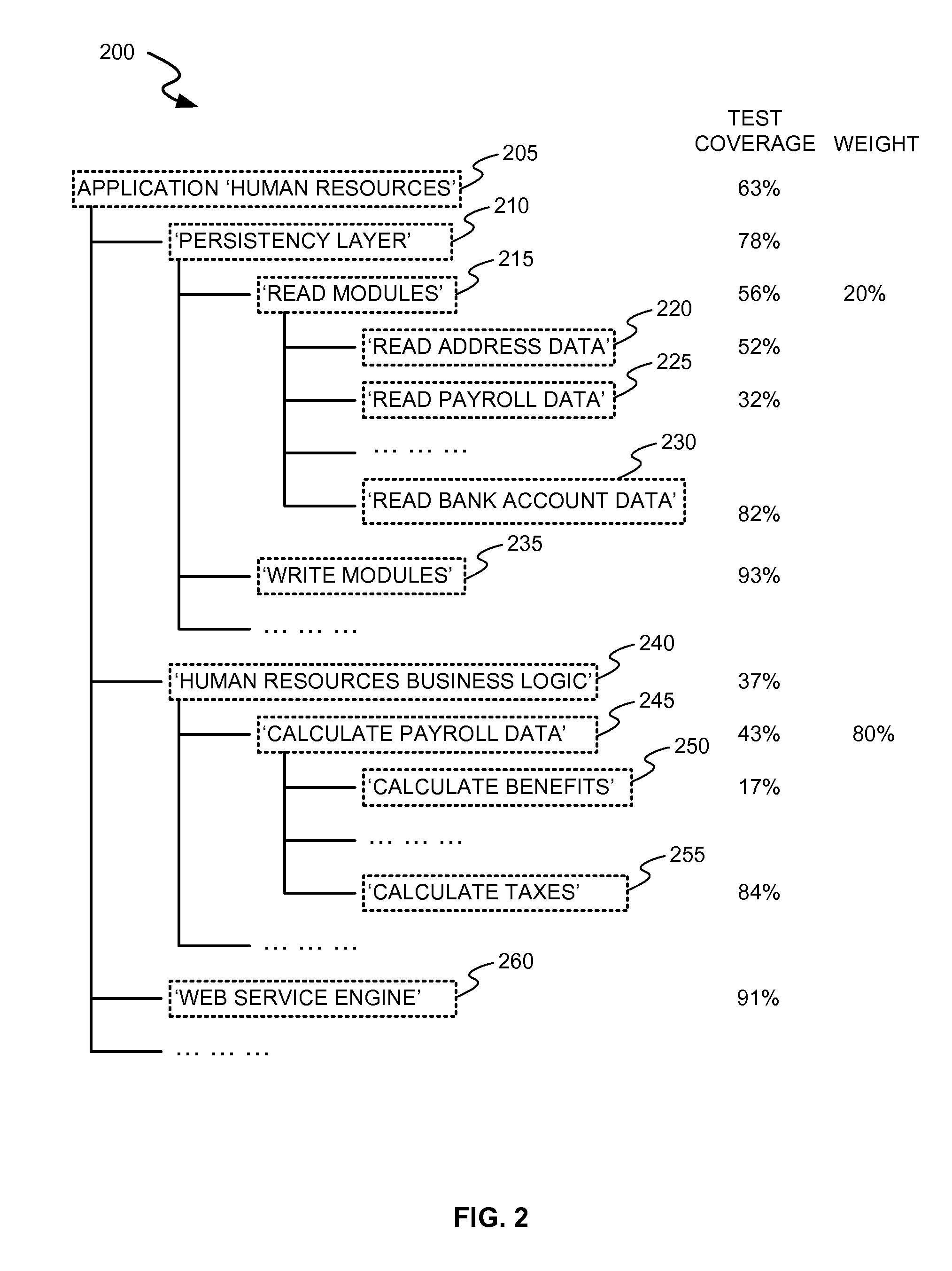
Systems and methods for analyzing test coverage at an organizational level
ActiveUS20110138358A1Software testing/debuggingSpecific program execution arrangementsSoftware engineeringOrganizational space
Disclosed are methods and systems for calculating test coverage of a software organizational schema. The method and systems involve retrieving the software organizational schema associated with an application, receiving an assigned weight factor to the one or more software organizational schema components associated with the application, determining a number of processed code lines and a total number of the code lines associated with the one or more software organizational schema components, calculating a test coverage for the one or more software organizational schema components based on the weight factor, the number of processed code lines and the total number of code lines of the software organizational schema component.
Owner:SAP AG
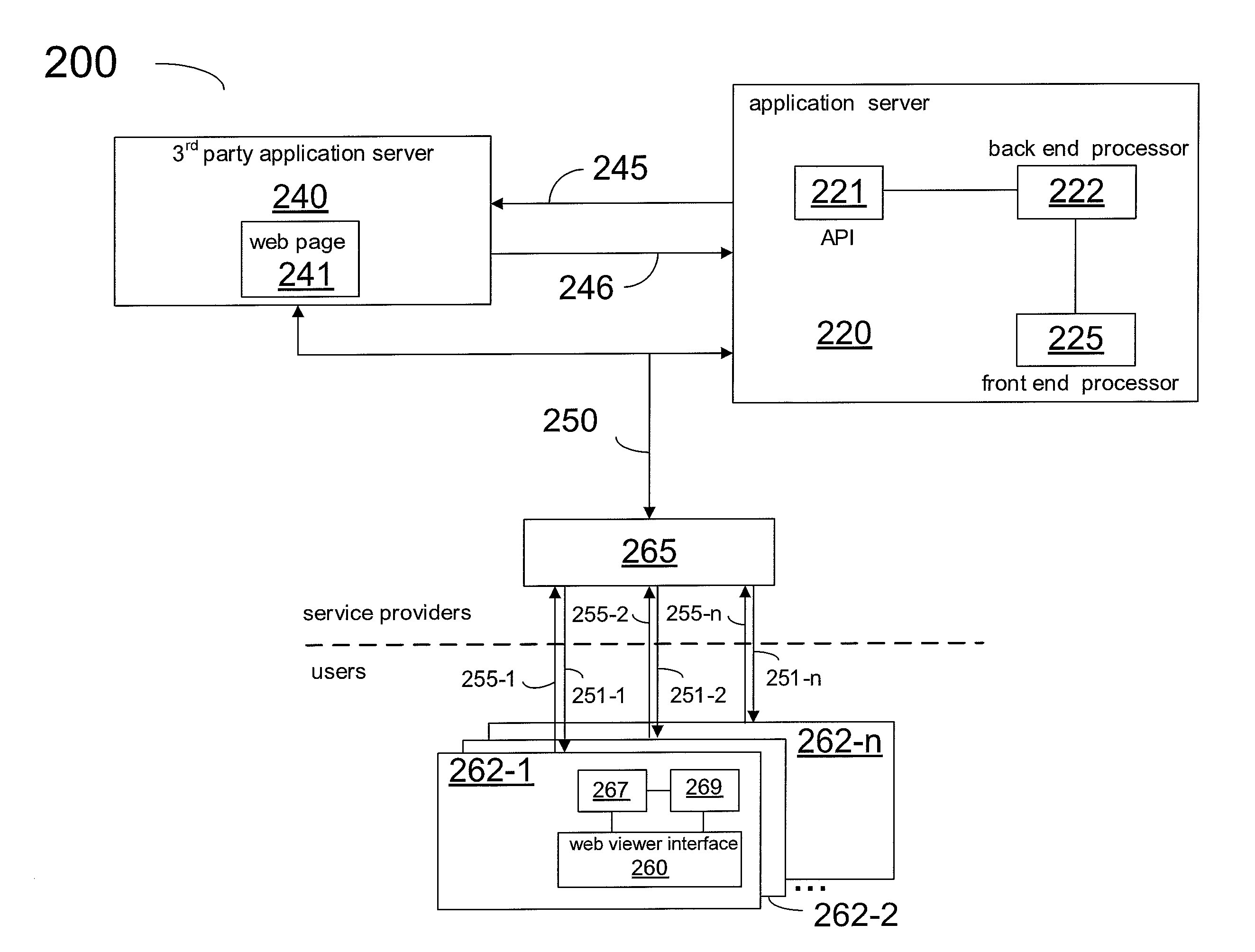
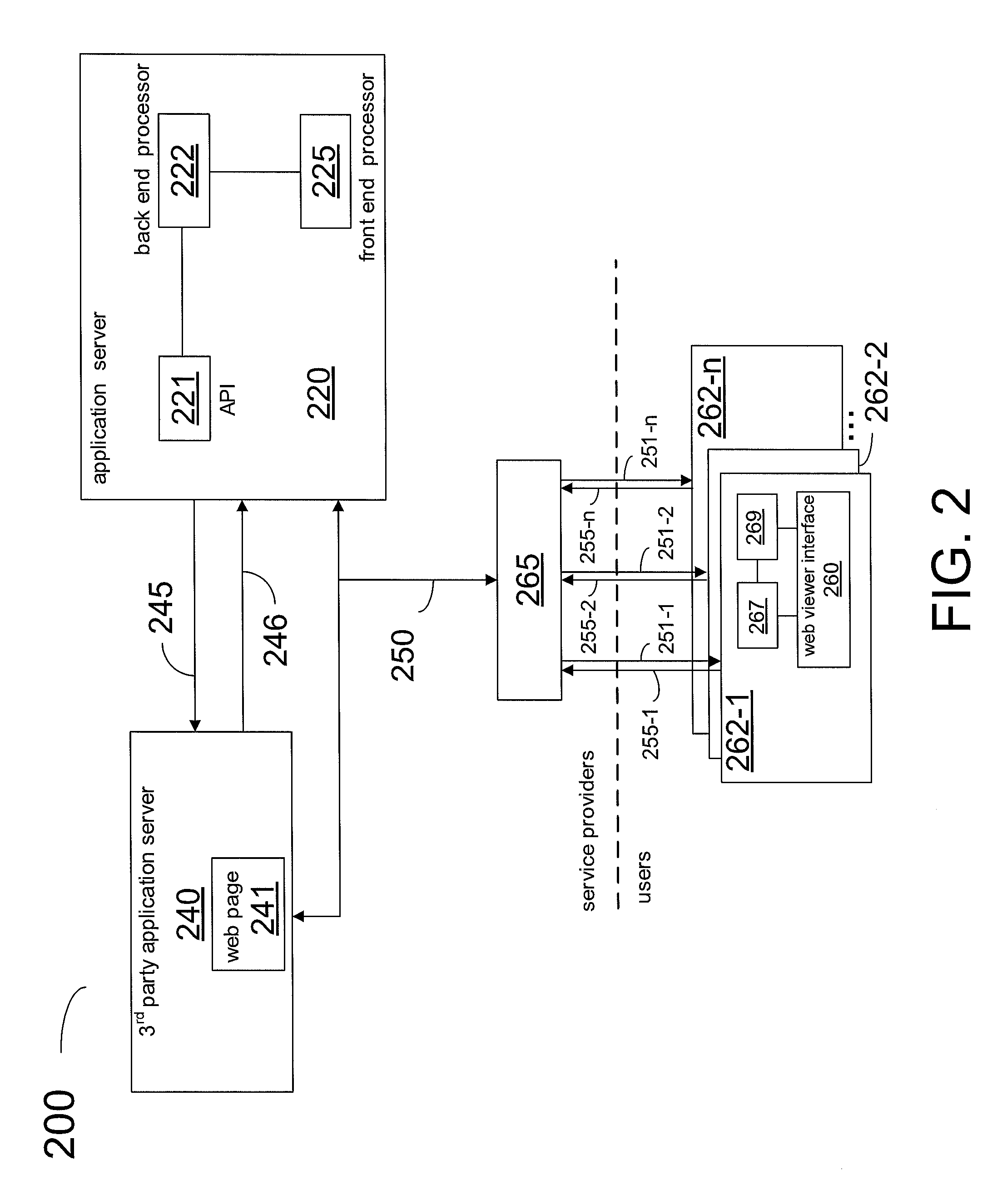
Method and system for an advanced player in a network of multiple live video sources
InactiveUS20120265621A1Transmission easilyInput/output for user-computer interactionMultiple digital computer combinationsVideo playerWeb browser
A method for providing a video player for a network of multiple live video sources includes: causing to be included in a webpage a first program line embedding a universal resource locator wherein, when the webpage is received into a web browser running on a computing device, the first code line causes the web browser to retrieve a file specified by the universal resource locator, the file executed within the web browser; including in the file a program code wherein, when the program code is executed at the web browser, the program code provides in the web browser a video player having capability to communicate messages between the video player and an application server; serving the file to the web browser when the web browser retrieves the executable file at the universal locator; and at the application server, handling message communication between the video player and the application server.
Owner:NEXT VENTURES
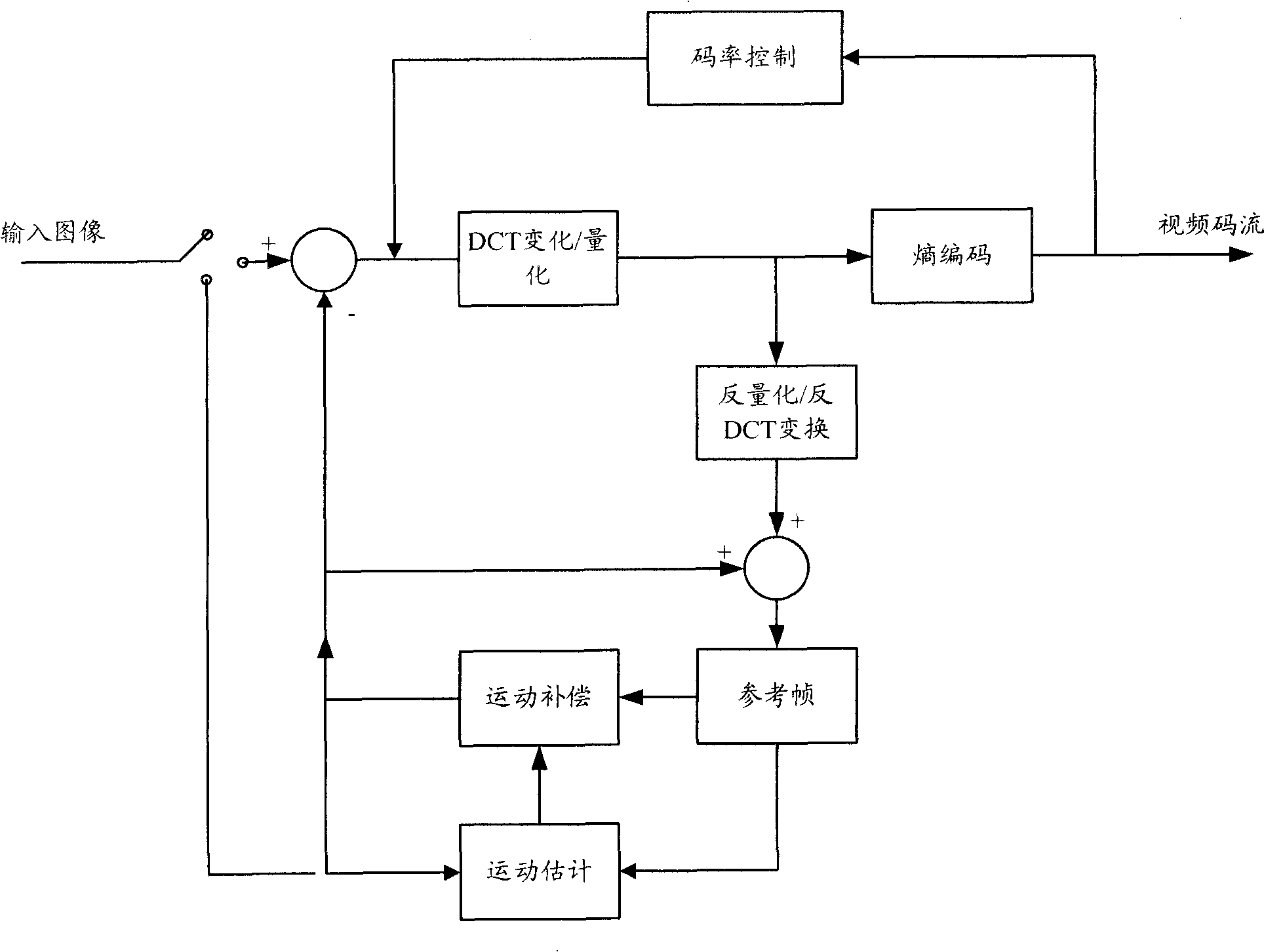
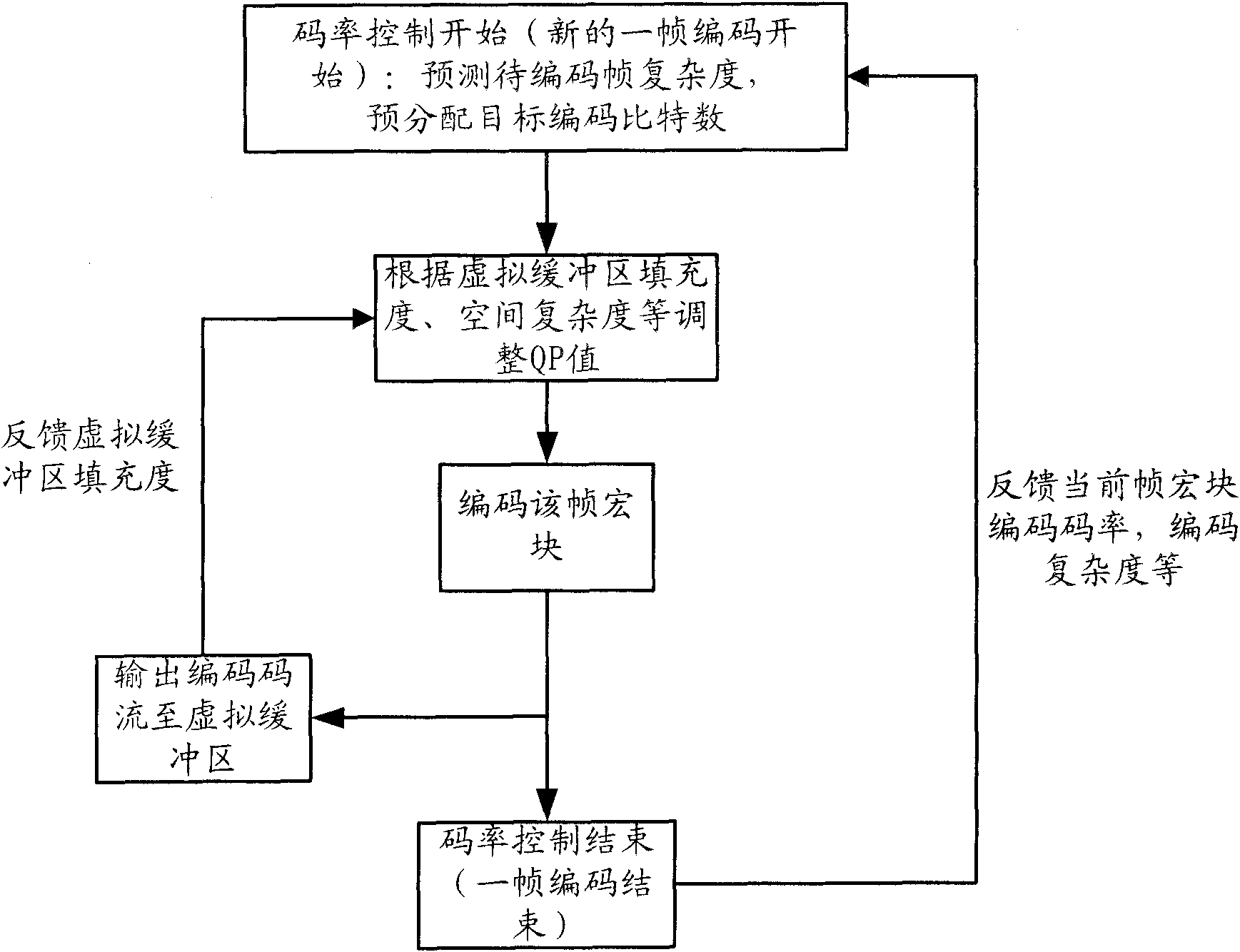
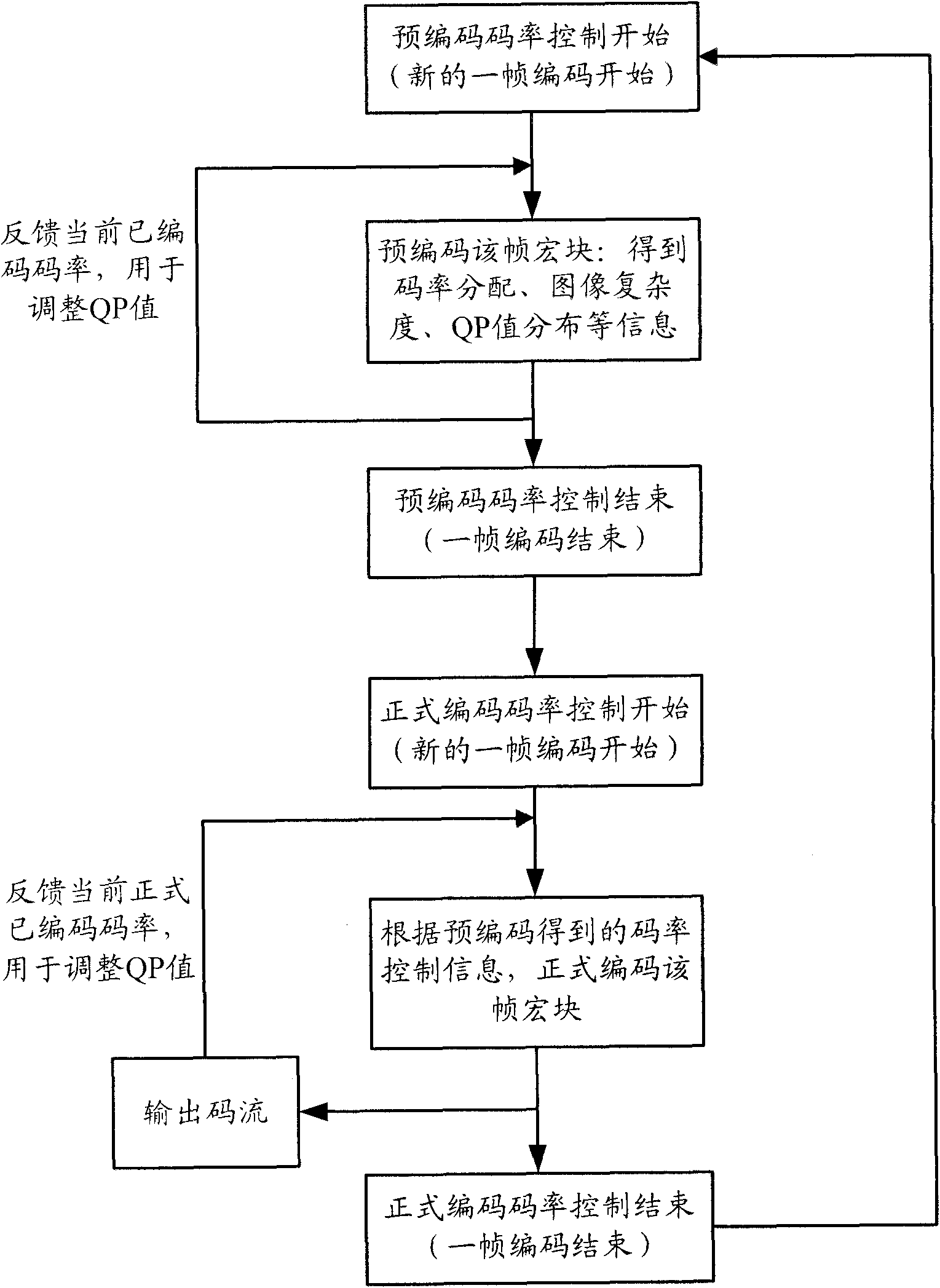
Method and device for controlling code rate in video coding
ActiveCN101795415AImprove image qualityReduce computational complexityPulse modulation television signal transmissionDigital video signal modificationComputer architectureBlock code
The invention discloses a method and a device for controlling code rate in video coding, which is used in the code rate control process using a line macro block as the minimum arithmetic element. Aiming at the current line macro block, the method comprises the following steps: acquiring the initial code rate control parameter of the current frame; determining the QP value of the current line according to the initial code rate control parameter of the current frame, the coding result feedback information of the coded line macro block and a coding scene; and tickling the coding result information obtained after carrying out macro block coding on the current line according to the QP value of the current line. The invention can enhance the quality of the coded image as far as possible on the premise of accurately controlling the code rate.
Owner:NEW H3C TECH CO LTD
Method for partial flashing of ecus
A system and method for compartmentalizing memory sections in a controller to allow compartments to be individually reprogrammed without affecting files in other compartments. The method includes defining a main memory in the controller that stores a plurality of different types of content files that each include lines of code, where the main memory includes compartments having memory slots for lines of code that have been programmed and empty memory slots where lines of codes can be written into. The main memory is initially programmed to store desired content files in the memory compartments. Subsequently, if it is determined that code stored in the main memory needs to be reprogrammed, the reprogramming is performed to flash only the memory compartments that include the code that needs to be reprogrammed and those memory compartments that include code that is linked to the code that needs to be reprogrammed.
Owner:GM GLOBAL TECH OPERATIONS LLC
Imaging rotation angle absolute encoder
ActiveUS20060091304A1Improve accuracyHigh resolutionOptical measurementsMaterial analysis by optical meansImage rotationLight detector
An angle absolute encoder comprises an encoded code rod that has code marks, such as pairs of fine code lines and coarse code lines. Light is reflected from or transmitted through the code marks and detected by a light detector to determine absolute angle position.
Owner:THE BOEING CO
Method for generating reusable behavioral code
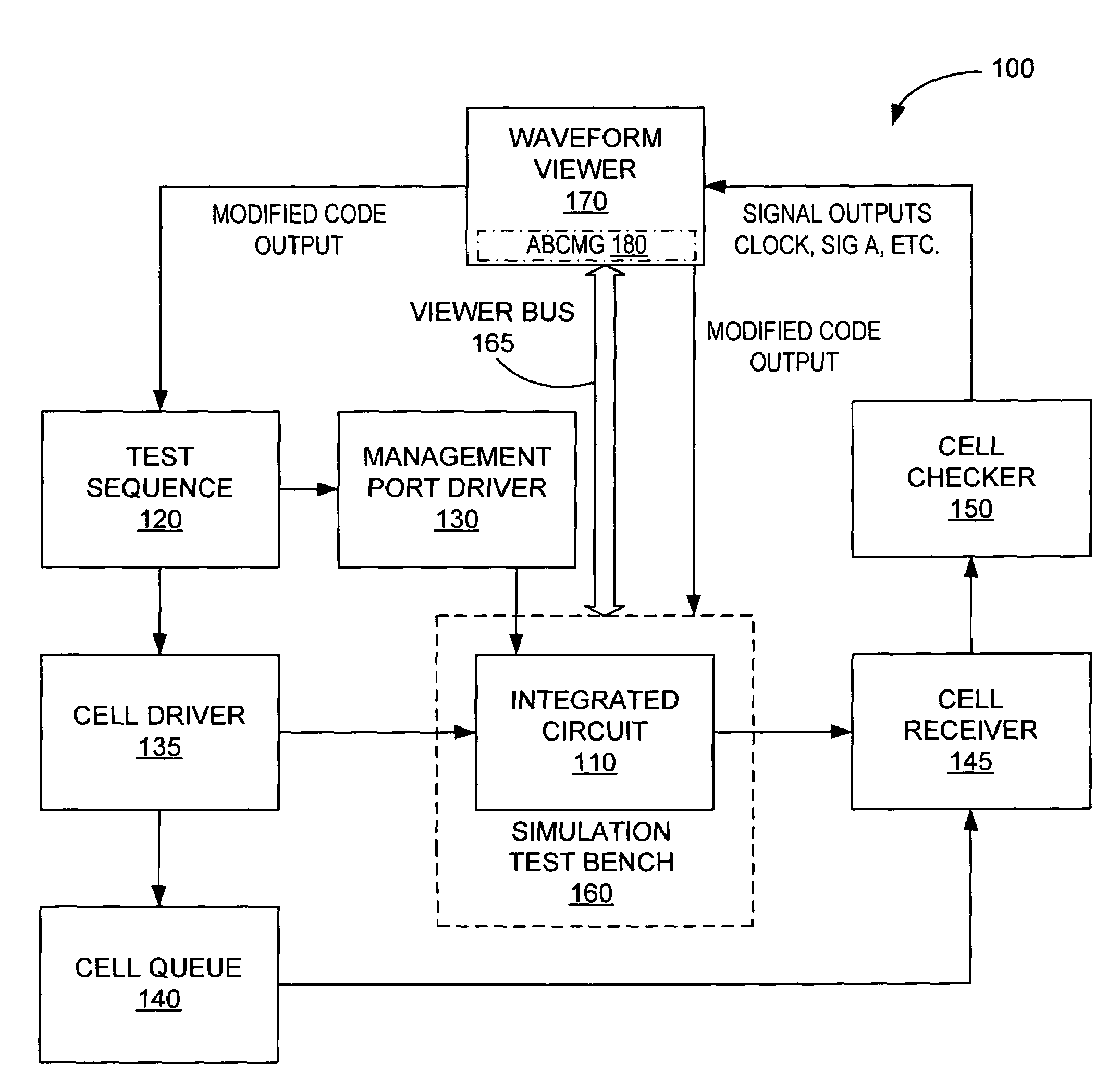
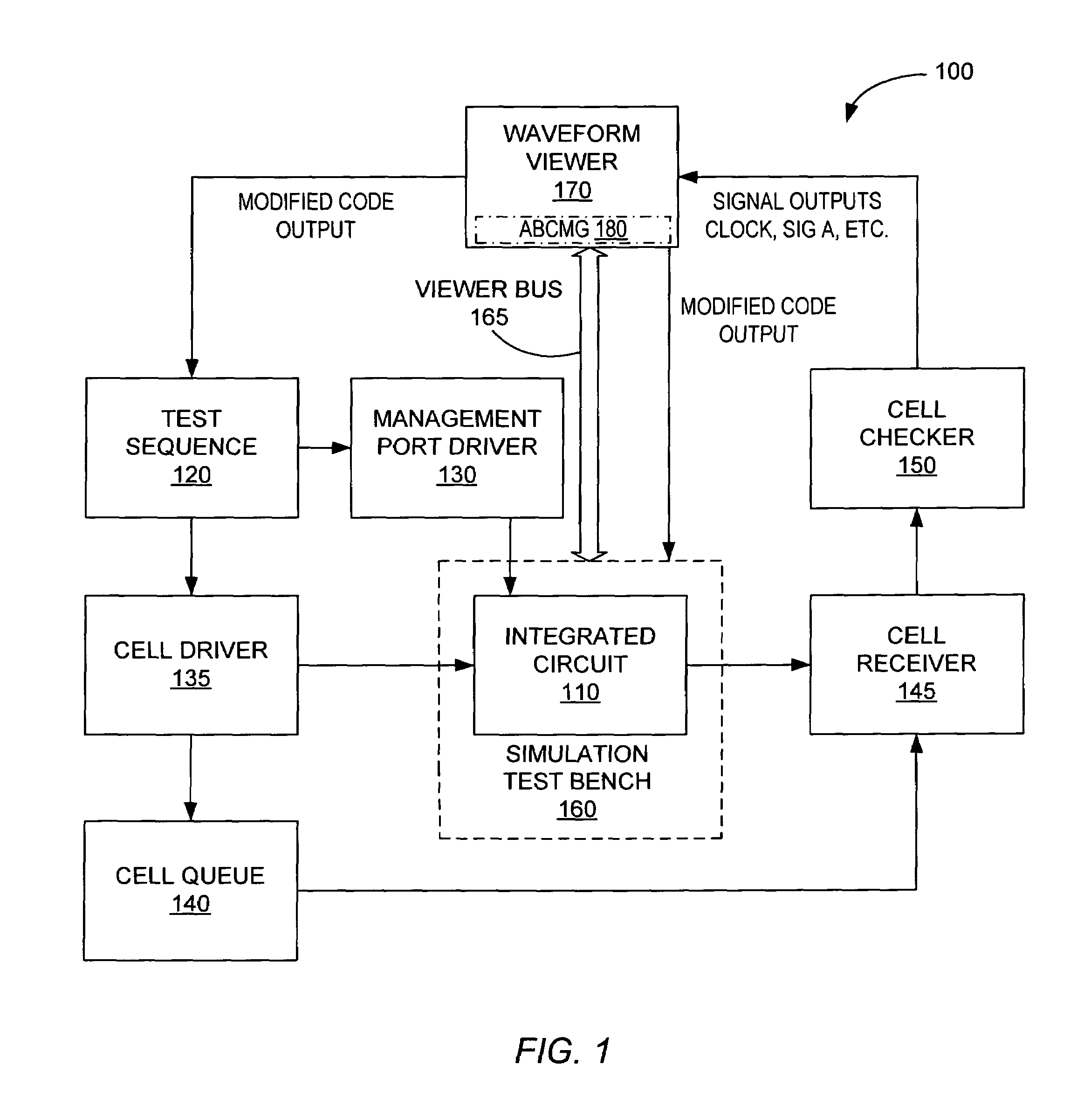
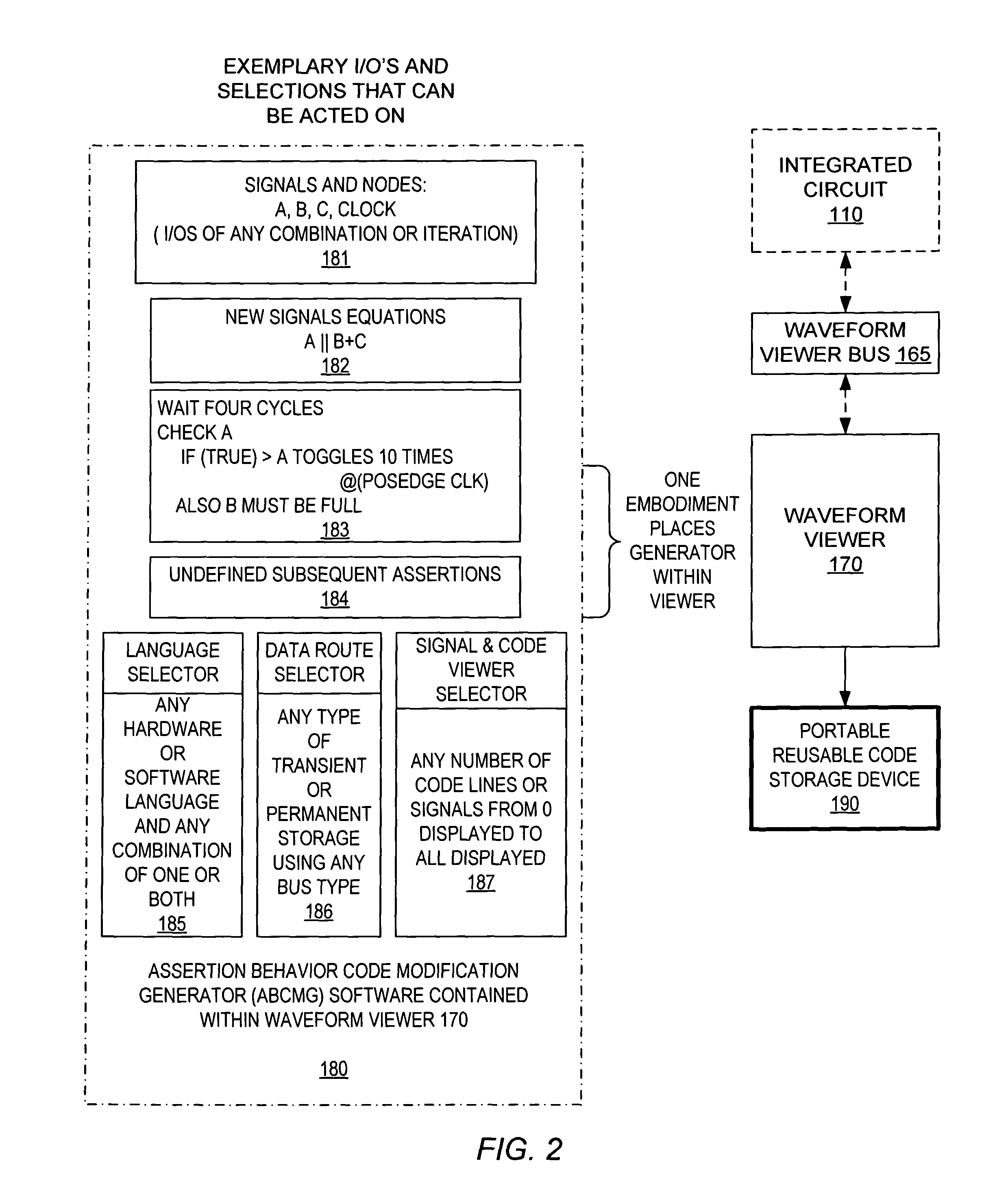
A waveform viewer implemented method of generating and manipulating user specified language simulation code such that an integrated circuit digital design can be modified. The visual capabilities of the waveform viewer allow a plurality of inputs for processing. The previous test's user specified language lines and the original signal waveforms are viewable on the same screen as the new code lines and waveforms. The waveform viewer also displays the contents of the portable reusable code portable reusable coded storage device. Each line of code and every signal can be manipulated by the user within the waveform viewer. The modified code output is applied to the test sequence through the waveform viewer, and the integrated circuit is retested with the new code. After modifications to the integrated circuit are complete, the proved device's stored user specified language can be transported to and inserted in other device architectures.
Owner:INT BUSINESS MASCH CORP
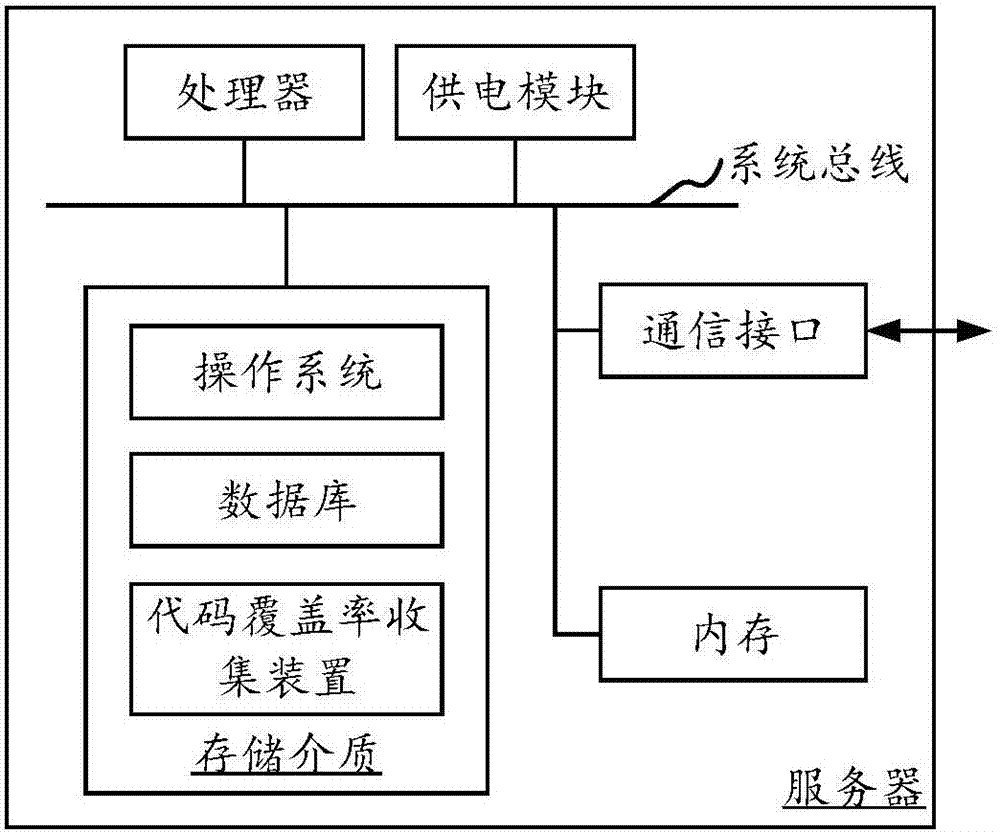
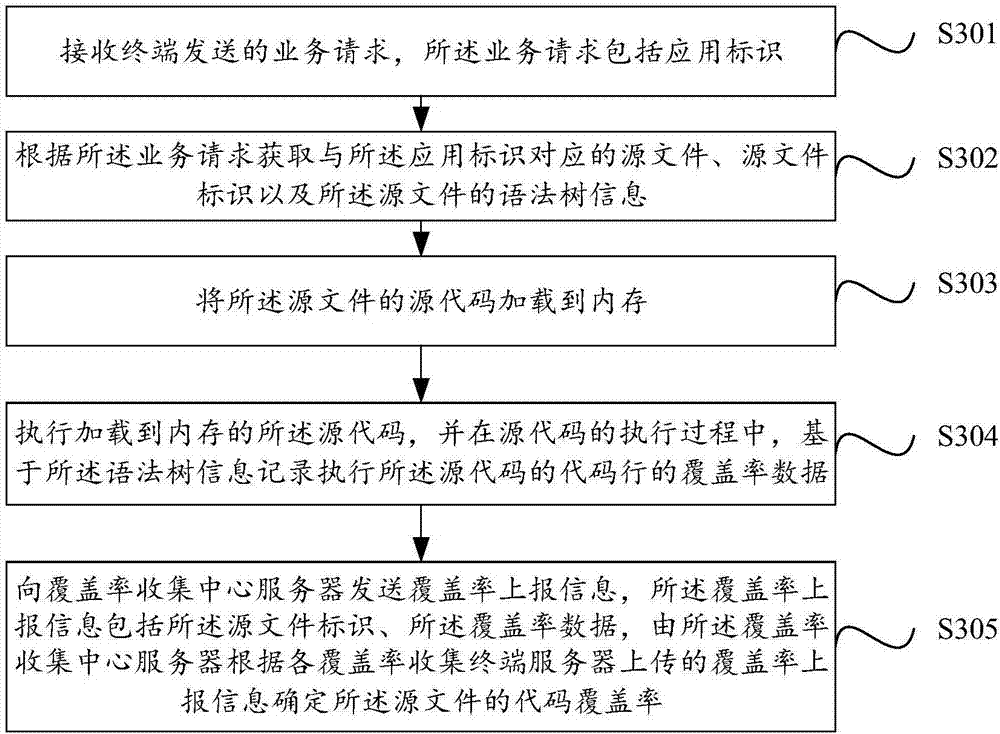
Code coverage rate collection method and device
The invention provides a code coverage rate collection method and a code coverage rate collection device. The method of one embodiment comprises the following steps: receiving a service request sent by a terminal, wherein the service request contains an application identifier; acquiring a source file corresponding to the application identifier, a source file identifier and syntax tree information of the source file according to the service request; loading a source code of the source file into an internal memory; executing the source code loaded into the internal memory and recording code coverage rate data of a code line for executing the source code based on the syntax tree information in an executing process of the source code; sending code coverage rate reporting information to a code coverage rate collection central server, wherein the code coverage rate reporting information contains the source file identifier and the code coverage rate data; and determining the code coverage rate of the source file according to the code coverage rate reporting information, which is unloaded by code coverage rate collection terminal servers, by the code coverage rate collection terminal servers. According to the code coverage rate collection method and device, the collection of the code coverage rates of the servers is realized, and the source code does not need to be modified; and reediting on the source code of developers is not influenced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
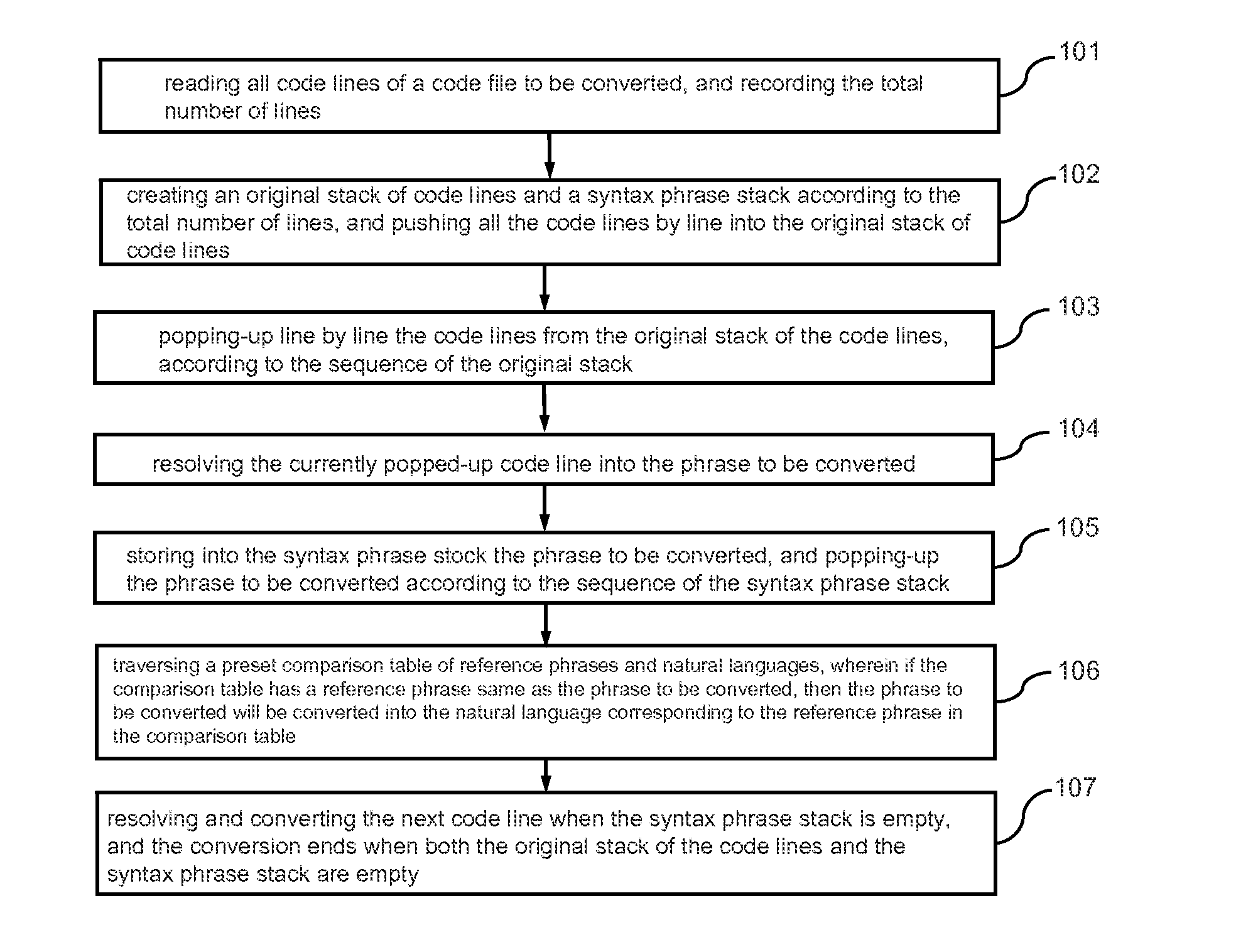
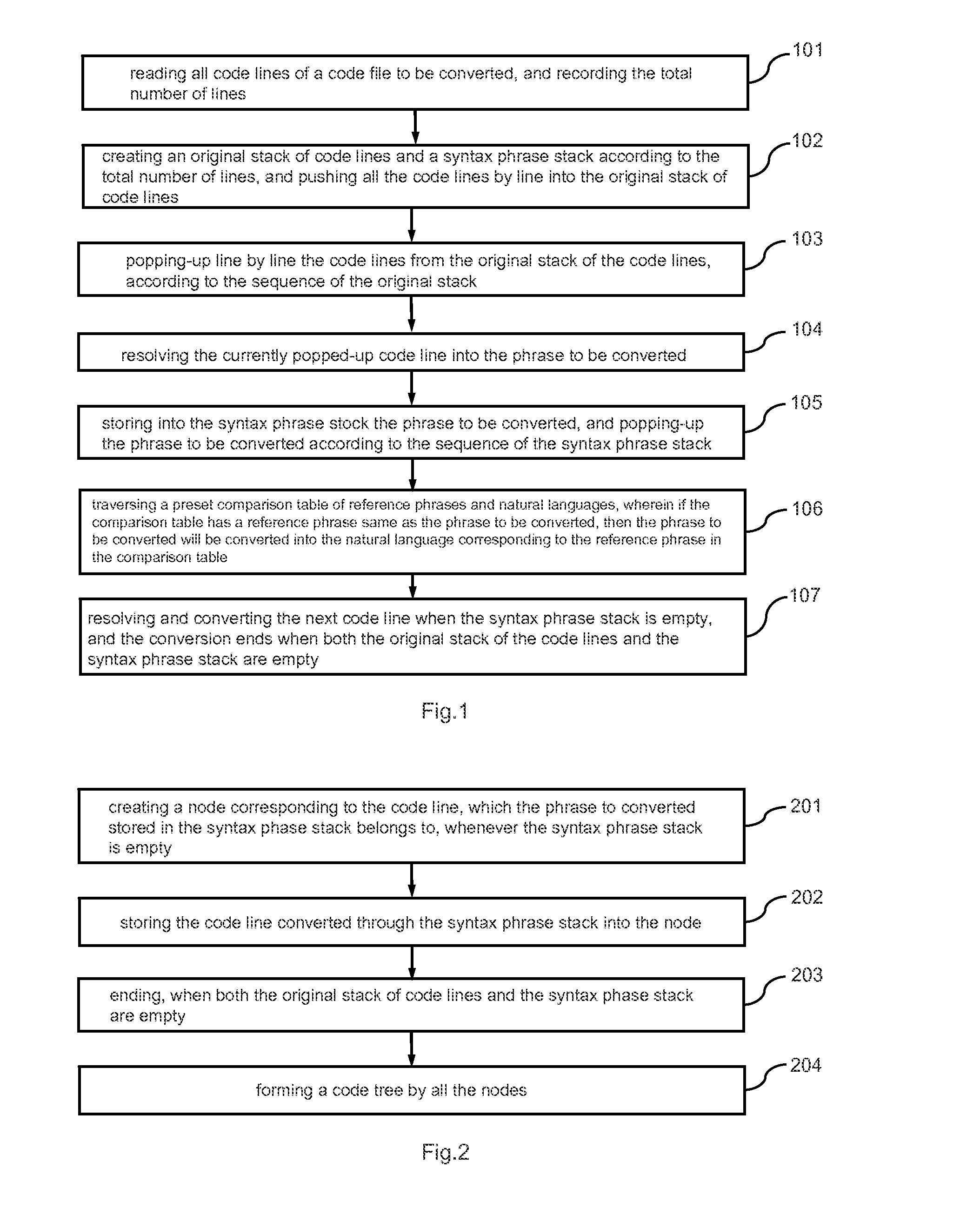
Method and apparatus for code conversion
ActiveUS20150363176A1Increase workloadReduce workloadCode refactoringProgram controlTheoretical computer scienceSoftware engineering
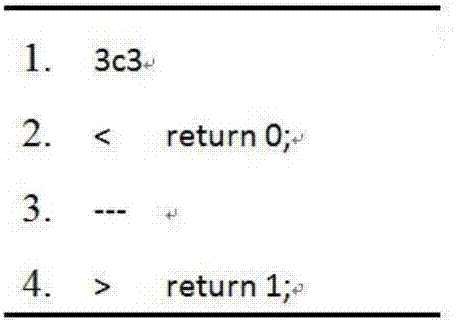
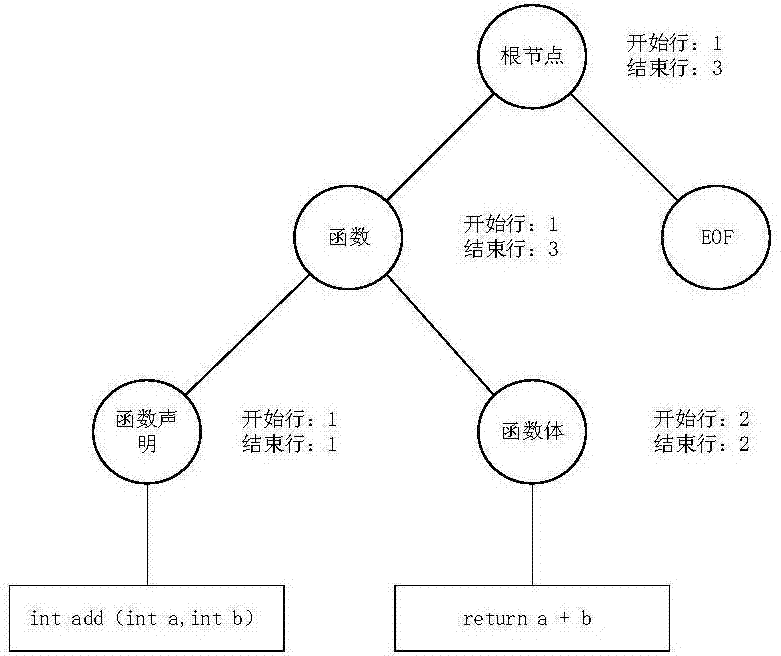
The present invention relates to the field of computer programming, in particular, to a method and apparatus for code conversion in which the codes in the code file to be converted or the code tree to be converted is read and stored into the stack and popped up in the last-in first-out sequence of the stack, and then the code line or the child node currently popped up is resolved into the file to be converted, and lastly the natural semantics comparison table is traversed, and the inter-conversion between the codes and the natural language is automatically carried out, so as to avoid the programmers from manually adding the marks and notes for the codes, which greatly decreases workload of the programmers, and can intuitively display the direct logical relationship of the codes, and at the same time, depending on different situations, the codes can be represented selectively in different forms, facilitating the creating, searching and maintaining of the codes.
Owner:SHENG JIE
Software version evolution comparison analysis method based on AST
ActiveCN107203468ALow efficiencyImprove accuracyVersion controlSoftware testing/debuggingUnixSoftware engineering
The invention provides a software version evolution comparison analysis method base on AST. Two software version source codes are compared and analyzed by a Diff order of a Unix, and changed source codes are divided into three source codes; AST information of the two software version source codes are obtained by a syntactic parser, and corresponding AST information of each line of code of each source code block is analyzed and obtained; obtained syntax node information is combined into combined information, and adjacent code lines with same identifications are combined into a module; identification information of the two source code blocks are compared and analyzed under the condition that modules are used as units, the identification information is subjected to classification analysis according to module evolution conditions, each evolution condition is processed by a preprocessing method and a secondary processing method, and evolution information is stored into a database and transformed into HTML codes. Compared with evolution comparison analysis methods of other software versions, the software version evolution comparison analysis method base on the AST can improve the accuracy rate of the obtained evolution information and improve the efficiency of software version evolution and analysis.
Owner:HARBIN ENG UNIV
Techniques for application security
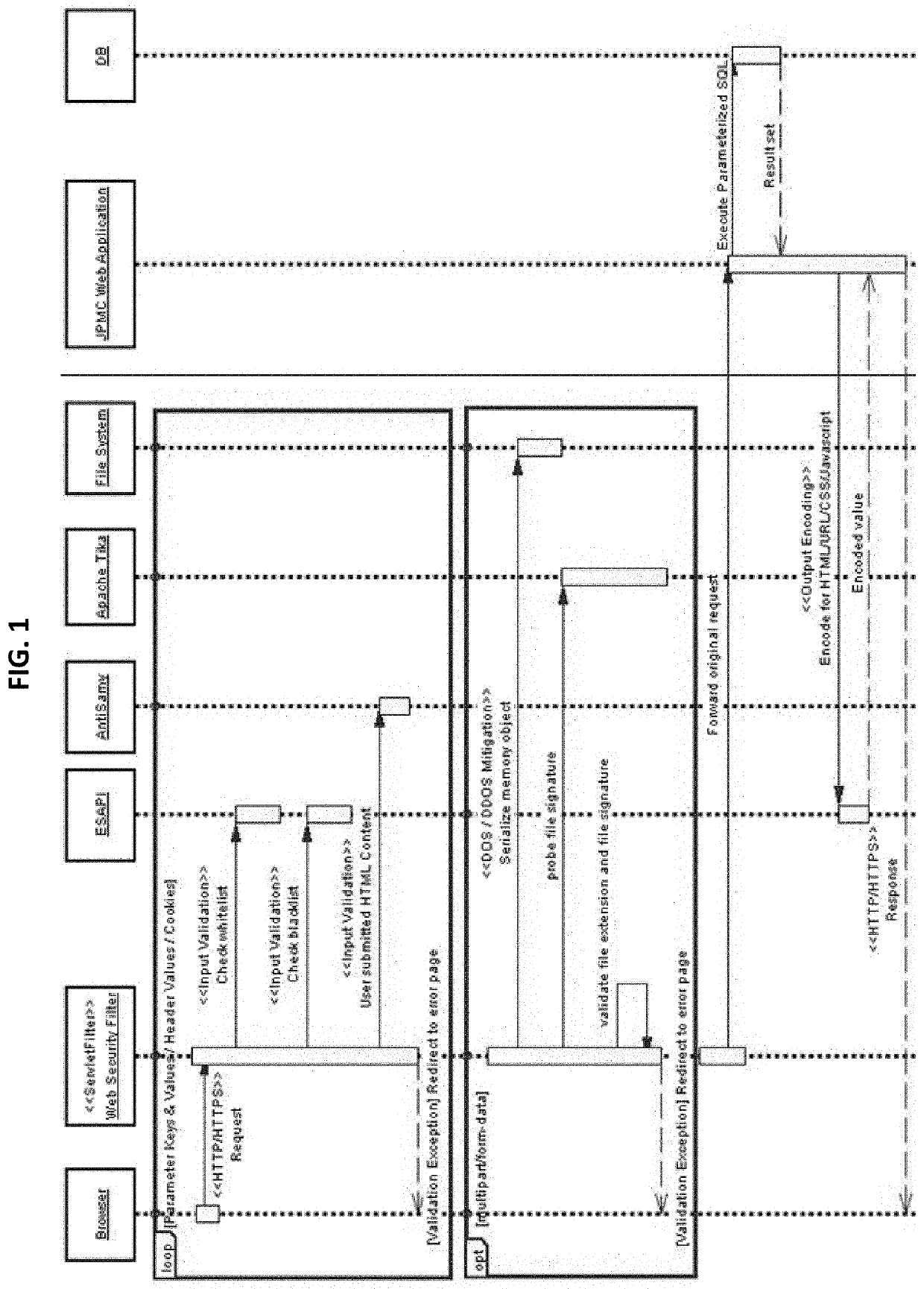
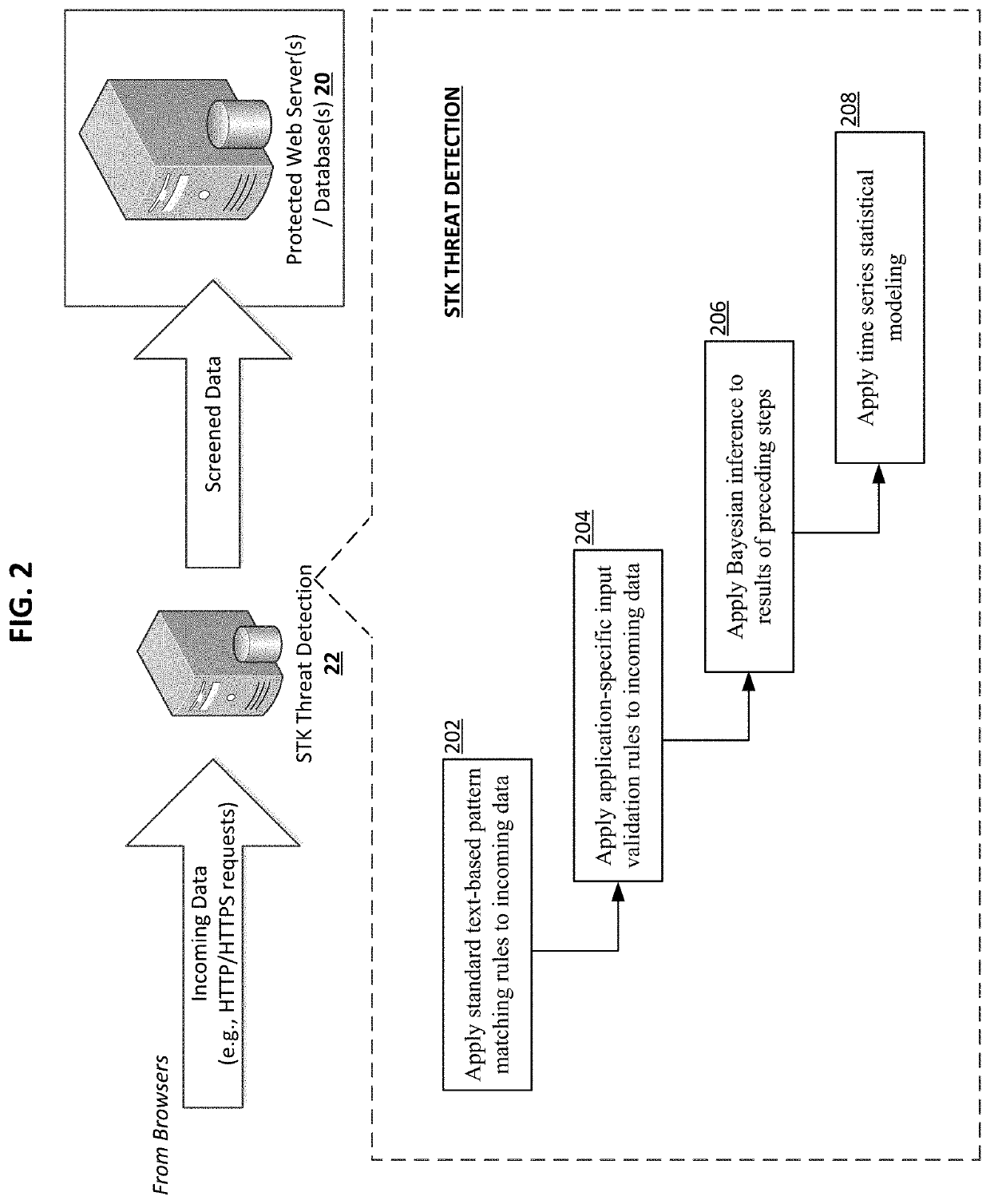
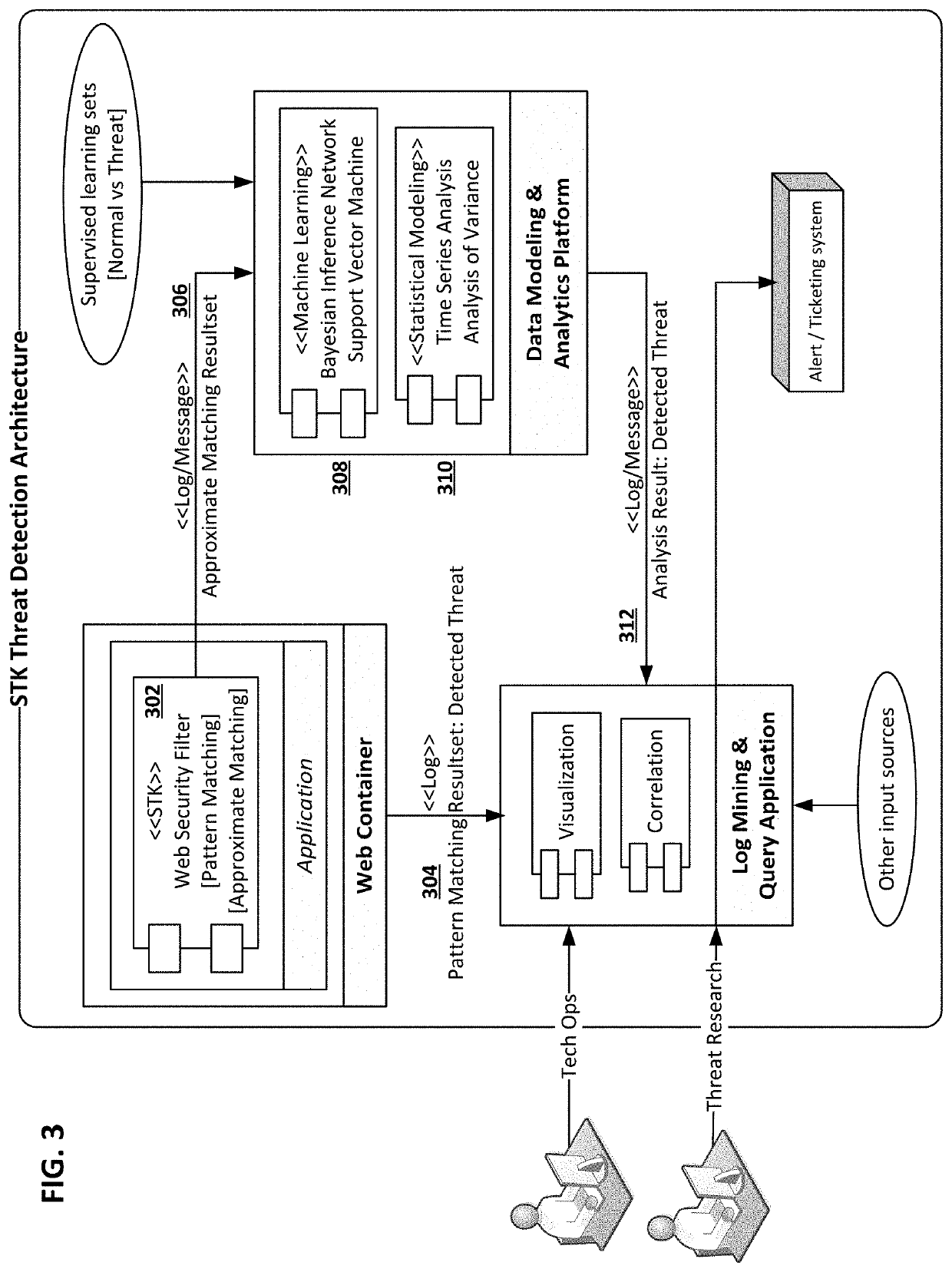
Software developers previously dealt with each security threat by incorporating a corresponding set of code lines into individual web applications, which required significant amount of time and code lines for each security threat and the resulting code was hard to maintain or modify. One aspect of the present invention addresses common security concerns in a standardized and centralized approach. All user requests for web applications are centralized to a single input and validated by a Web Security Filter. Selected layers of validation filters (e.g., ESAPI and AntiSamy) could be sequentially applied to the user requests, and those filters can be individually maintained / modified as discrete modules. Not only is this centralized, holistic approach to application security effective against a majority of malicious attacks, it is also saves a lot of time and costs in code development and maintenance.
Owner:JPMORGAN CHASE BANK NA
Test coverage statistical method and system based on JVM
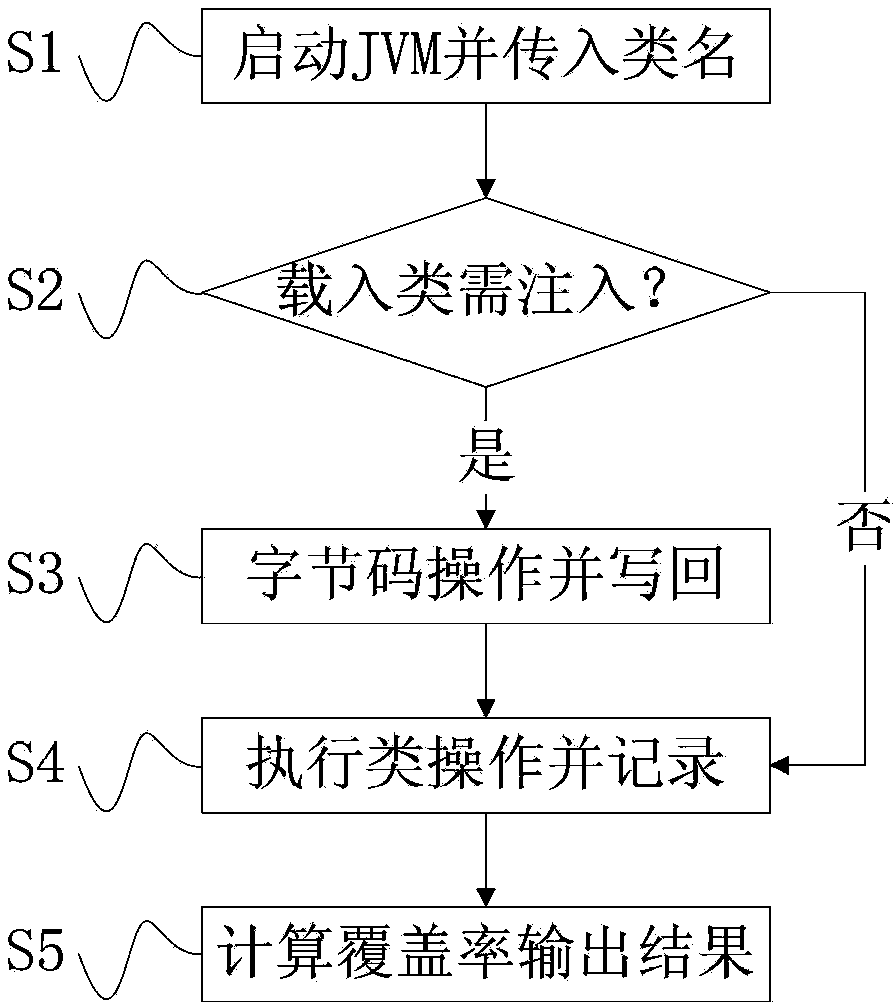
The invention relates to the technical field of software test, and provides a test coverage statistical method and a test coverage statistical system based on JVM. The method comprises the steps of: S1, introducing taxons needing subjecting to statistics as parameters while starting JVM; S2, judging whether classes loaded into a virtual machine need to be injected, if yes, executing a step S3, otherwise, directly executing a step S4; S3, implementing bytecode operation to the classes needing subjecting to statistics and writing back into the virtual machine; S4, normally executing the operation of the classes and automatically recording statistical information in the execution by the virtual machine; S5, when the virtual machine exits, computing test coverage according to the statistical information and outputting result. According to the test coverage statistical method and system based on JVM, the bytecode is injected without changing original program structure, the test coverage of the code line level can be obtained in a black-box testing manner, the test coverage of the software code can be quantitatively evaluated, and a forceful reference index can be provided for the sufficiency of the test and the execution efficiency of a test case.
Owner:AEROSPACE INFORMATION
Weak software watermark method used for software configuration management
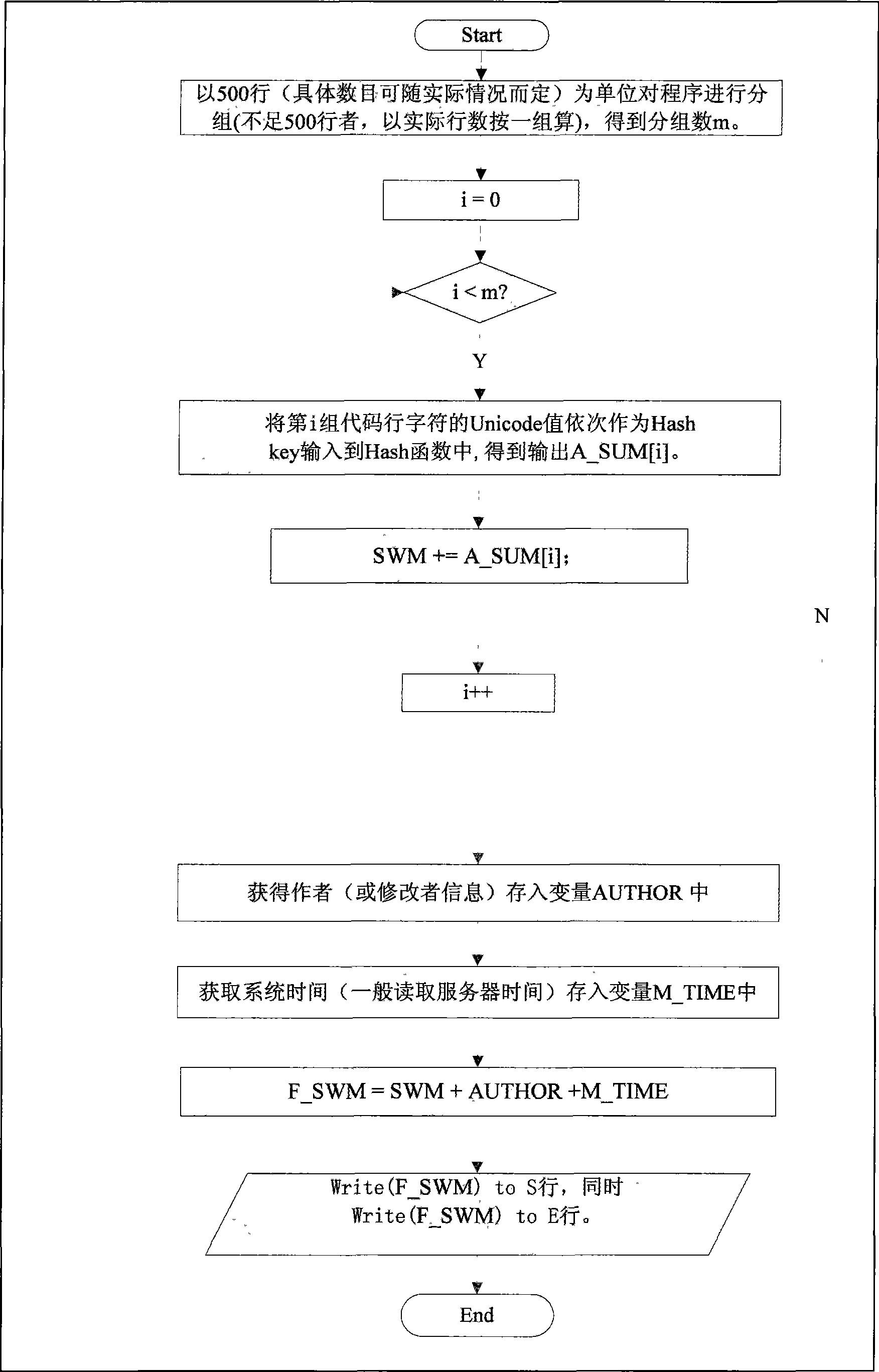
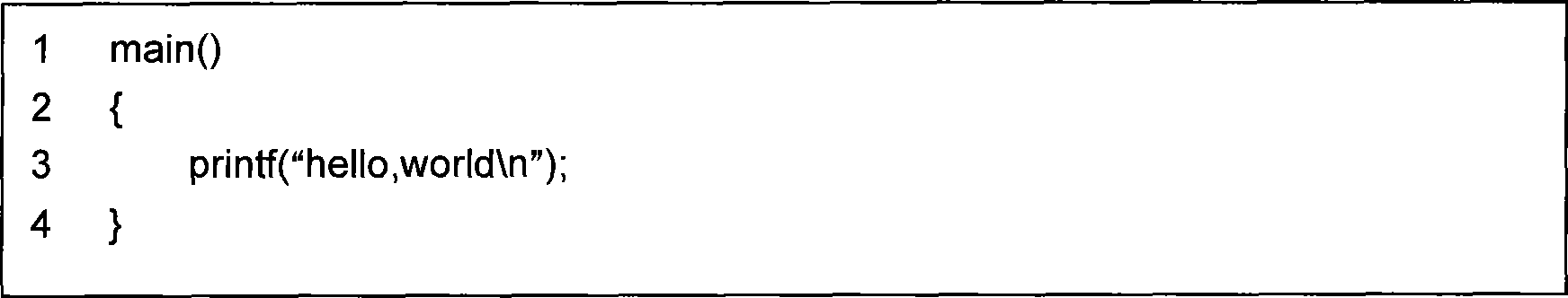
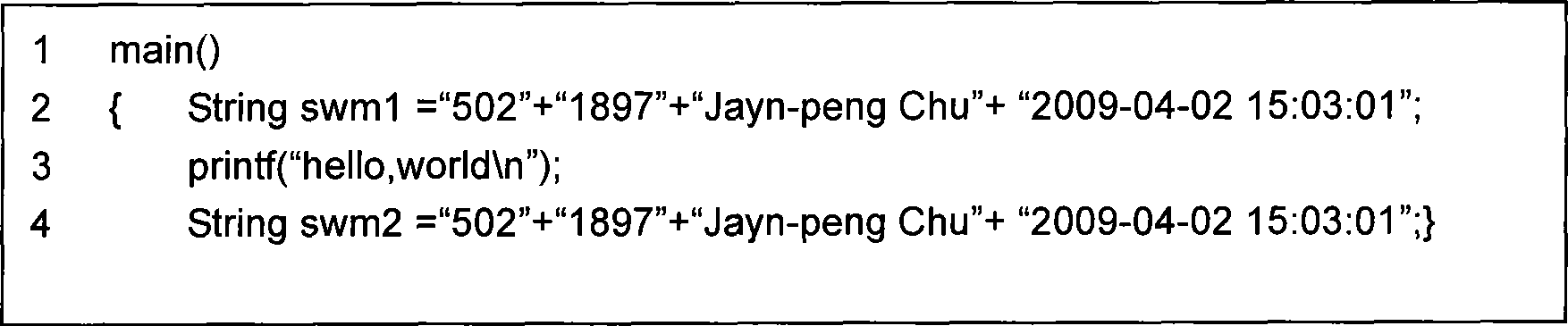
The invention provides a novel fragile software watermarking method for software configuration management. The basic thought of the method is to fully utilize the frangibility of software watermarking to identify the version alteration of software and take watermarking information as an evidence of version identification and retrieval. The method comprises the following steps of: firstly, grouping program codes; secondly, generating various groups of code program information according to various groups of the program codes; thirdly, splicing the groups of the code program information to obtain integral program information; fourthly, splicing the integral program information, author information and time information to obtain final watermarking information; and finally embedding the watermarking information into a first code line containing a program start character of a first group of programs and a final code line containing a program end character of a final group of programs in a write file mode to obtain a program containing the watermarking information. The proposal can effectively overcome and solve the disadvantages and problems existing in the prior software version control method in the software configuration management, and can also be applied to technology such as software tamper resistance and content authentication at the same time.
Owner:GRADUATE SCHOOL OF THE CHINESE ACAD OF SCI GSCAS
Bar coded wristband
A bar coded patient wristband identifies a patient wearing the wristband. The system comprises a bar code reader to read the bar coded wristband. A host computer is connected to the digital link to receive the segment of data from the bar code reader. A database correlates the segment of data to a patient to identify the patient. The patient wristband comprises a plurality of bar code symbols. A computer then retrieves a patient record from the database to identify the patient wearing the wristband. In one embodiment, a patient wristband for identifying a patient accepts a plurality of markings of 2 D bar codes distributed along the strip. In another embodiment, the wristband comprises a plurality of linear bar code lines and spaces distributed along the strip. The lines and spaces form a 1 D bar code.
Owner:HAND HELD PRODS
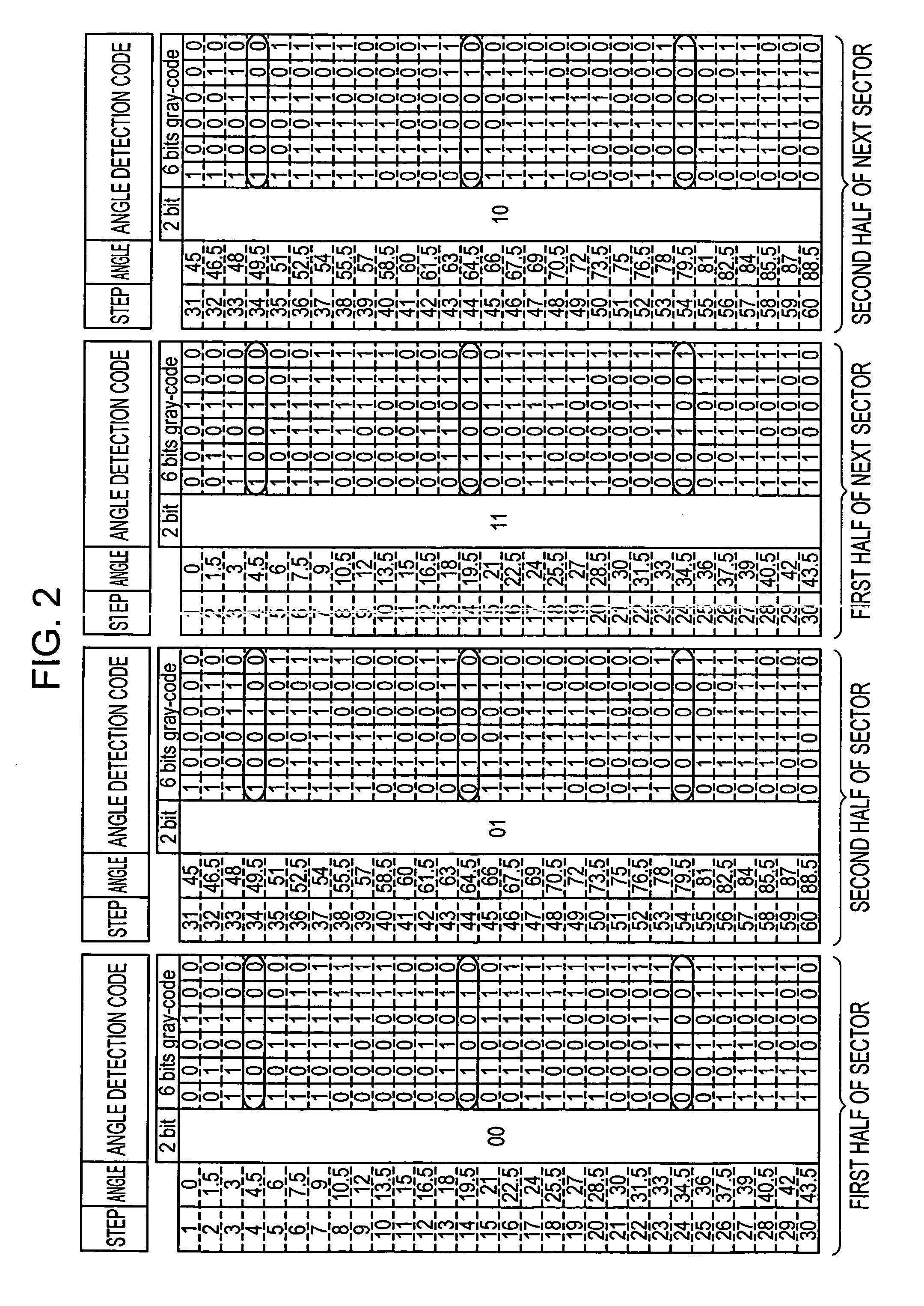
Absolute angle detection apparatus
InactiveUS20060249665A1Accurate detectionIncrease the number ofElectric signal transmission systemsMaterial analysis by optical meansComputer hardwareGray code
In an absolute angle detection apparatus, sectors are obtained by dividing 360° by an even number, each sector having combinations of first and second code lines. The first code lines are Gray codes including third code lines that do not appear the same even when a digit from which they are read is changed and fourth code lines that appear the same when a digit from which they are read is changed. The first code lines at adjacent steps and the first code lines at the first and last steps differ from each other at one bit. Each first code line is shifted by one digit at every predetermined number of steps, and the first code line without shift is obtained when the first code line corresponding to the maximum shift is further shifted by one digit. The second code lines identify the fourth code lines.
Owner:ALPS ALPINE CO LTD
Coding and printing line for lead storage batteries
ActiveCN108128030AFully automatedImprove work efficiencyRotary pressesConveyor partsScreen printingElectrical battery
The invention discloses a coding and printing line for lead storage batteries. The coding and printing line for the lead storage batteries comprises a laser coding line, a battery overturning device and a screen printing line which are sequentially connected. According to the coding and printing line for the lead storage batteries, the battery overturning device automatically converts the batteries the top surfaces of which are coded by the laser coding line into a horizontal placement state from a vertical placement state, then the batteries are input to a third conveyor belt for screen printing to achieve automation, the work efficiency is improved, and the labor cost is saved. By separately arranging a working table above which a laser coding device is arranged on the laser coding lineand clamping and pushing the batteries transported on a first conveyor belt to the working table one by one by a mechanical arm to perform coding, the impact of vibration on the coding process duringrunning of the first conveyor belt is avoided, and two-dimensional codes coded on the batteries are clear without ambiguous images or double images.
Owner:ZHEJIANG TIANNENG POWER ENERGY
Software vulnerability detection method and device based on graph convolution network
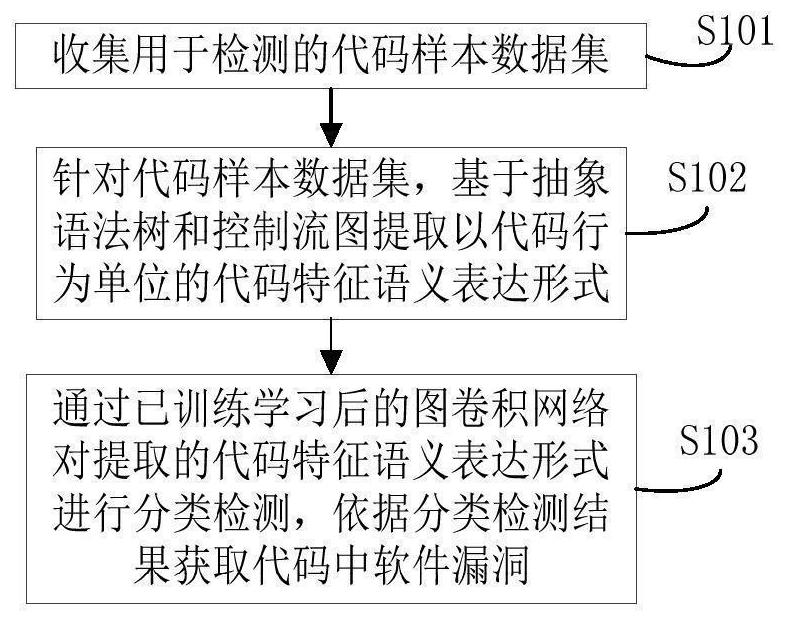
ActiveCN111611586AImprove efficiencyQuality improvementPlatform integrity maintainanceData setData stream
The invention belongs to the technical field of computer security, and particularly relates to a software vulnerability detection method and device based on a graph convolution network, and the methodcomprises the steps: collecting a code sample data set; for the code sample data set, based on the abstract syntax tree and the control flow graph, extracting a code feature semantic expression formin code behavior units; and performing classification detection on the extracted code feature semantic expression form through the trained and learned graph convolutional network, and obtaining software vulnerabilities in the code according to a classification detection result. According to the invention, through extracting the abstract syntax tree, the control flow and the data flow information of the code, a code feature semantic expression mode taking a code as a unit is formed. The possibility that the vulnerability exists in the code is analyzed by using the graph convolution network in deep learning and the characteristics analyzed by the data flow extracted based on the abstract syntax tree, so that the vulnerability detection efficiency and accuracy are effectively improved, the software code reliability is ensured, the software quality is improved, and the method has important significance for software security application.
Owner:上海信息安全工程技术研究中心
Process for measuring coding productivity
InactiveUS7093235B2Error detection/correctionSpecific program execution arrangementsProduction rateComputer science
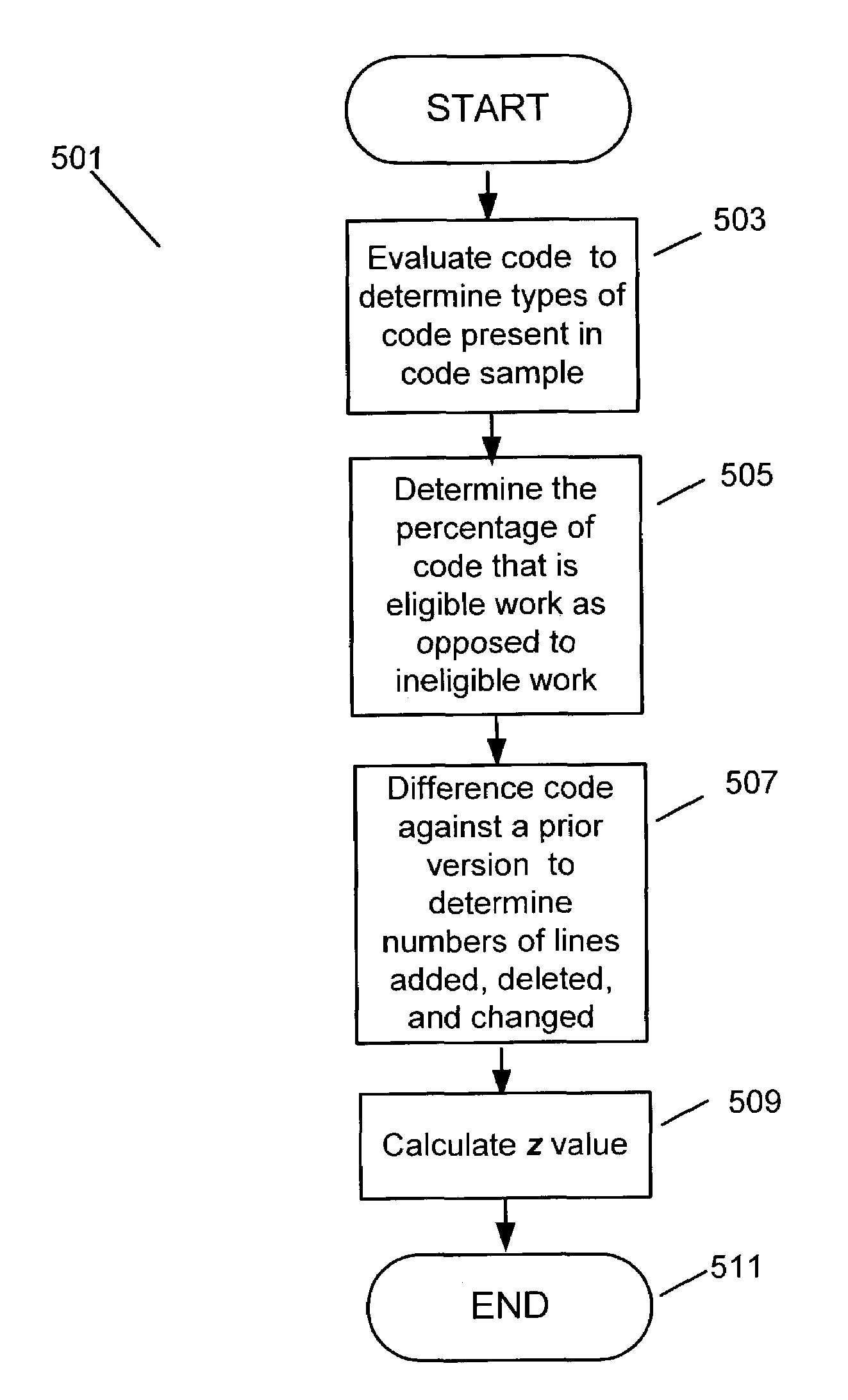
A novel system and method provides a concrete relative measure for evaluating coding quality. The novel system and method do not rely on bug counting. Instead, the number of defective lines of code is compared to a total number of opportunities to create such defects. A defective line is a line that is deleted, added or changed subsequent to drafting of the prior version of the code. In an embodiment, a deletion and an addition are each treated as single defects, while modification of a line of code is treated as two defects. In this way, regardless of whether modification is viewed as deletion followed by addition, or rather simply a single step of modification, the number of defects in either case is the same.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com