Weak software watermark method used for software configuration management
A technology for software configuration management and software watermarking, which is used in electrical digital data processing, computer security devices, instruments, etc., to solve the problems of no version change, new programs not being submitted normally, and abnormal changes in program version numbers. The effect of high return on investment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Various details involved in the method provided by the present invention will be described in detail below in conjunction with the accompanying drawings.
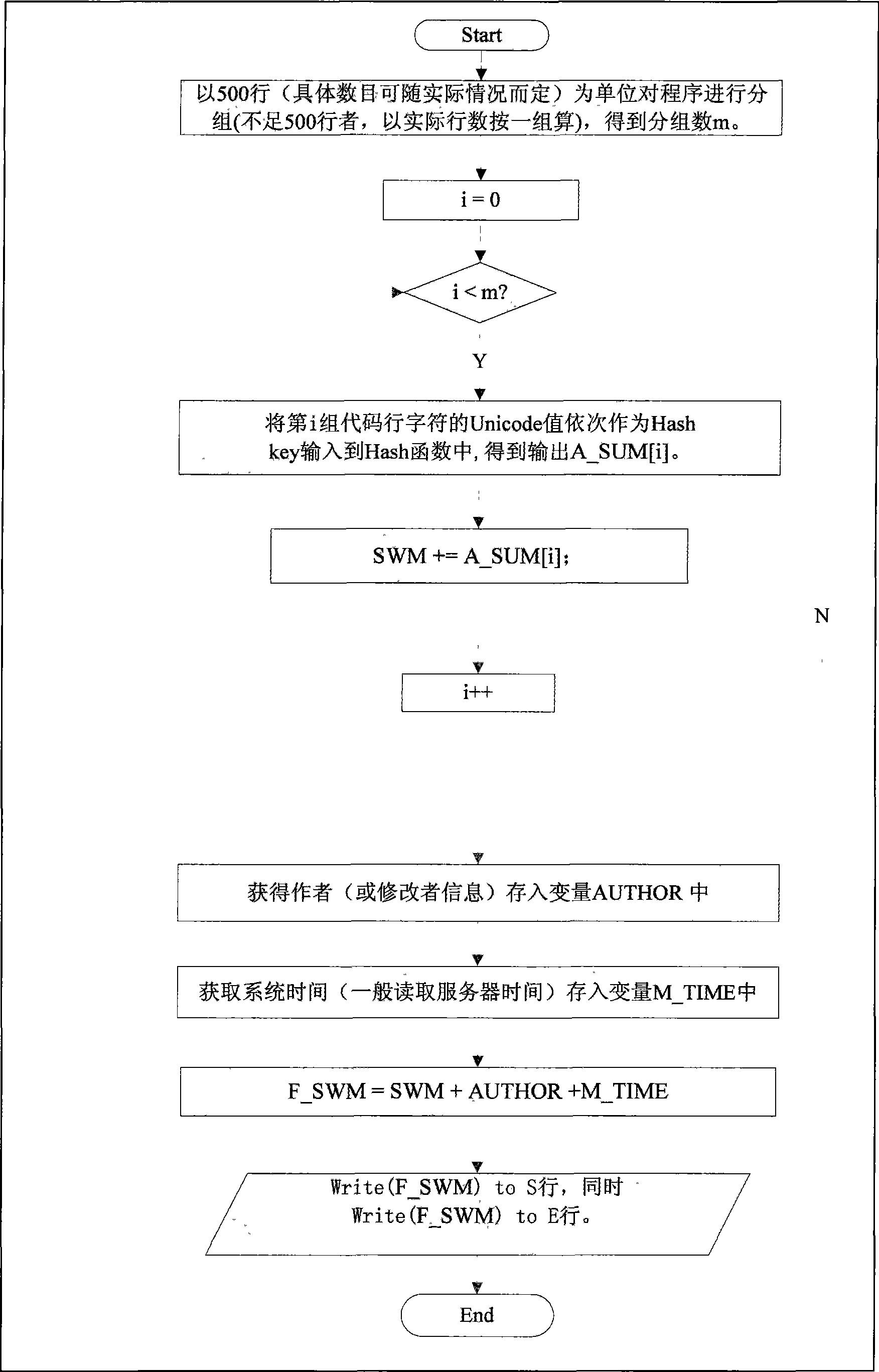
[0034] Such as figure 1 Shown, the specific implementation steps of the inventive method are as follows:
[0035] The first step: program grouping. Group the program code (including comments) in units of 500 lines (the number can be adjusted according to actual needs);
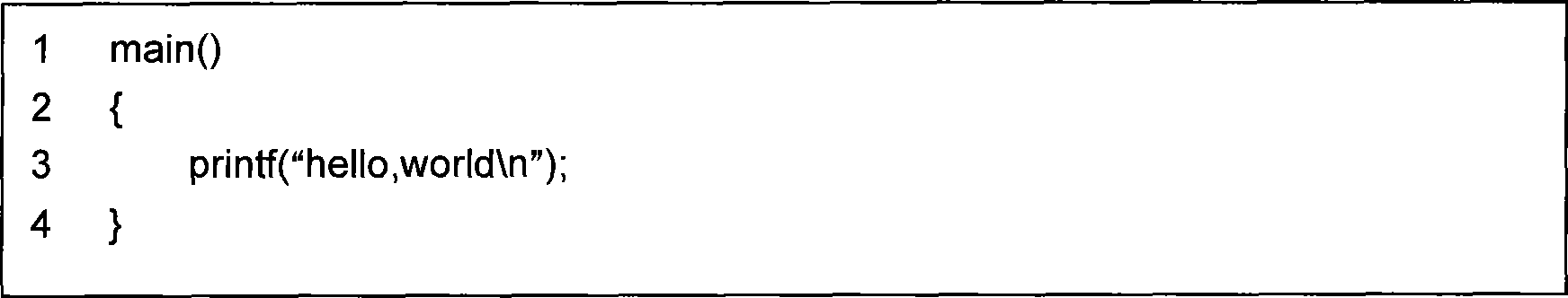
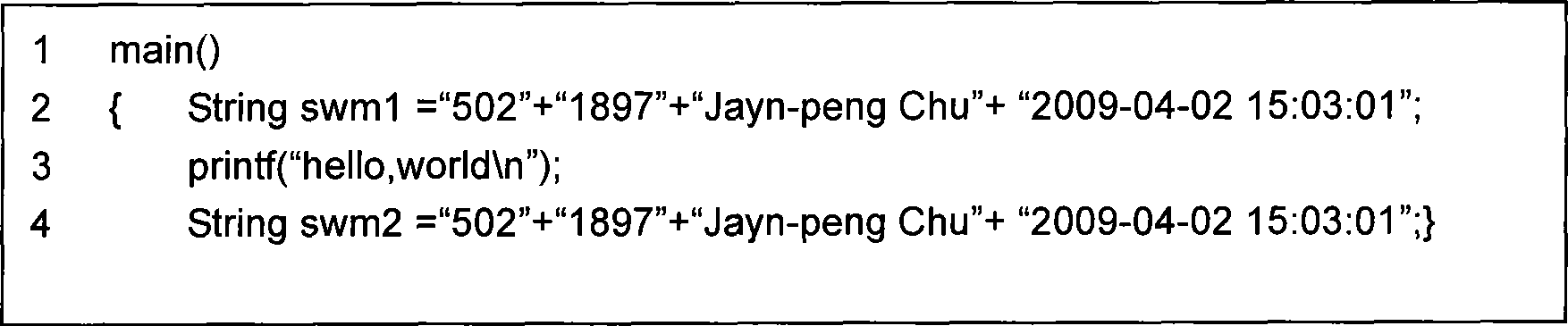
[0036] The second step: generation of watermark information. The watermark information includes program information, author information and modification time, where the author information is the machine name or the physical address of the machine, which is recorded as AUTHOR; the time information is the current time of the system, which is recorded as M_TIME; and the program information can be generated in two ways: One is to calculate the ASCII code sum of program code characters; the second ( figure 1 This is the way) to calculate the Hash valu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com