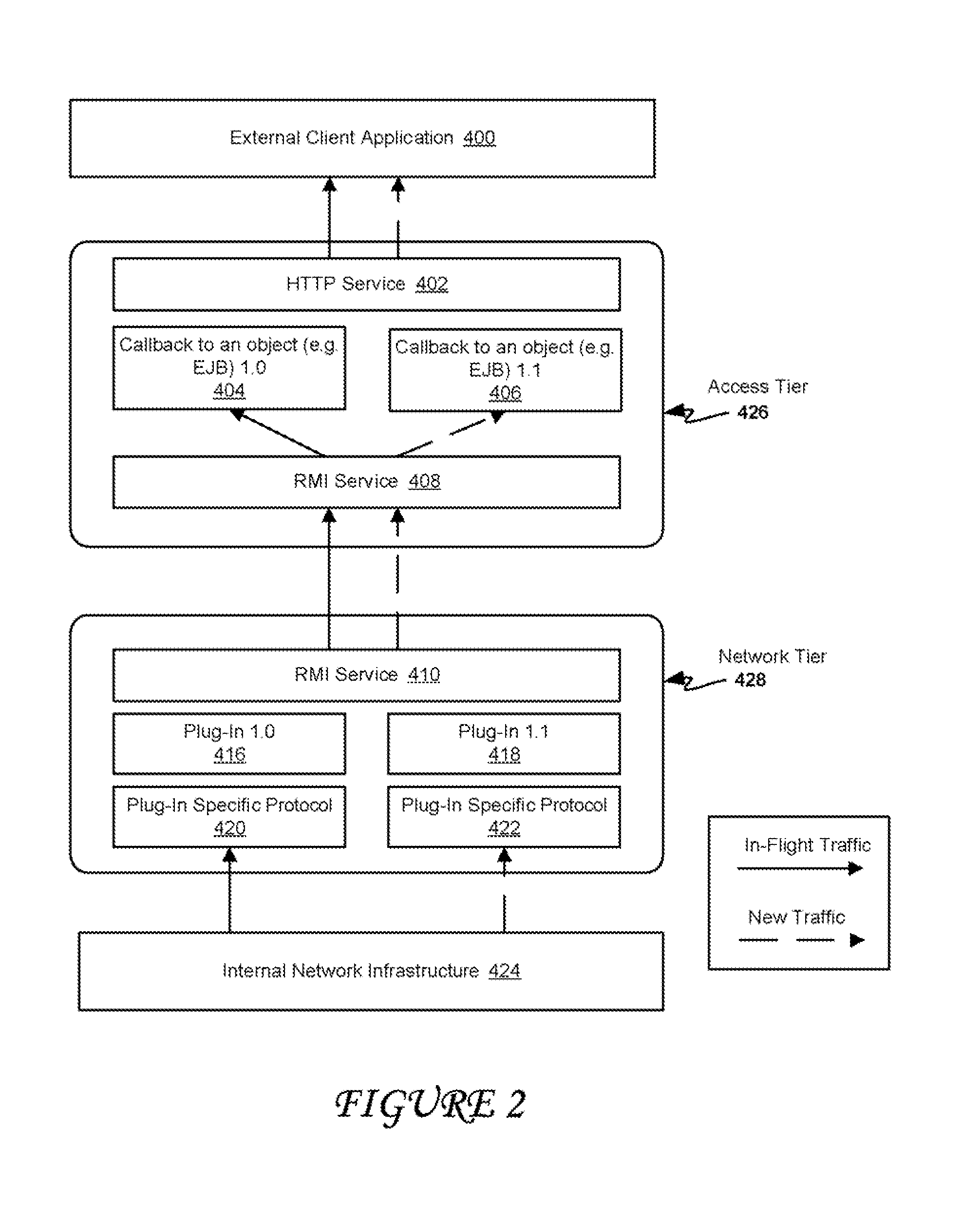
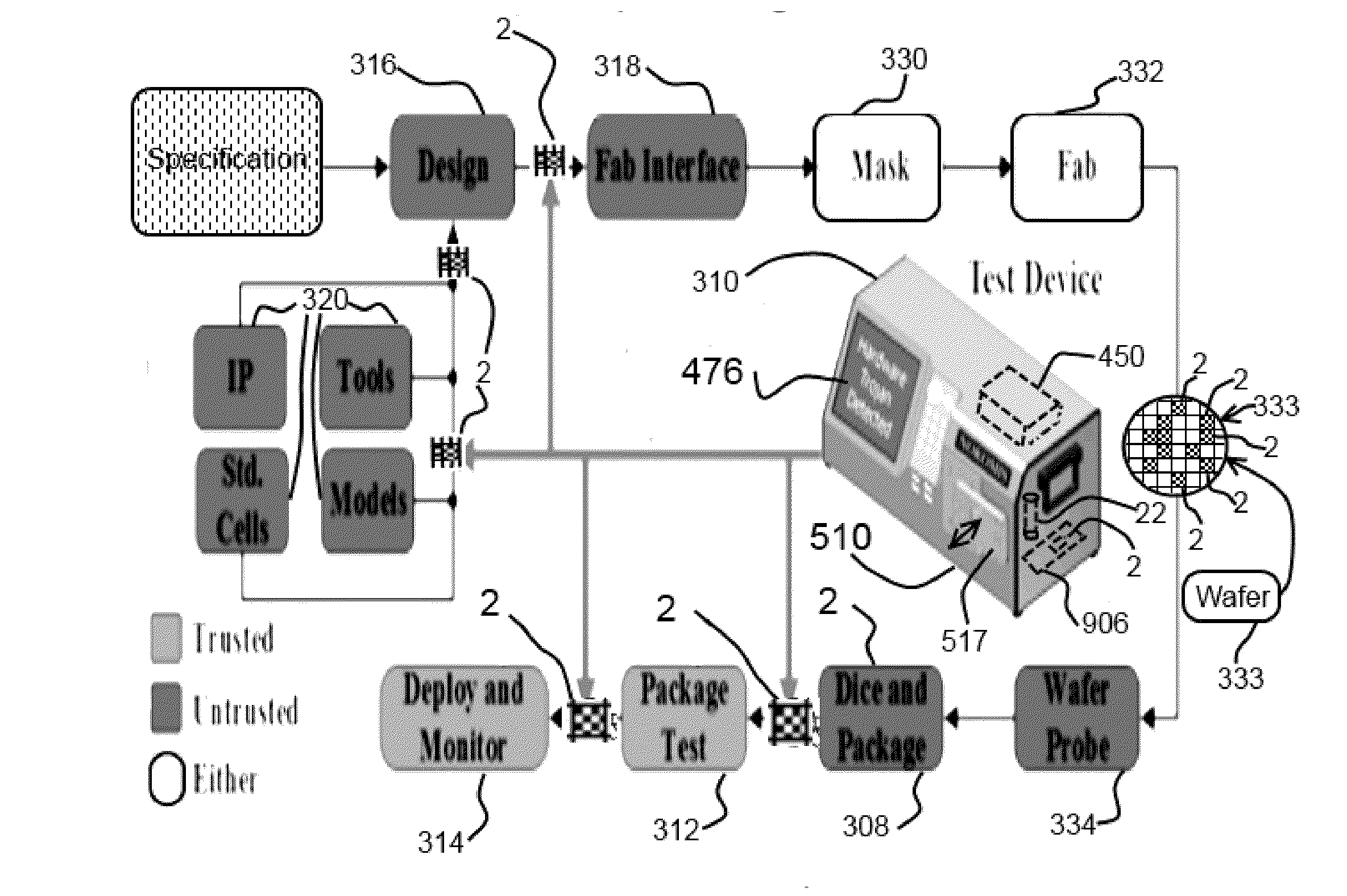
Patents
Literature
869 results about "Revision control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
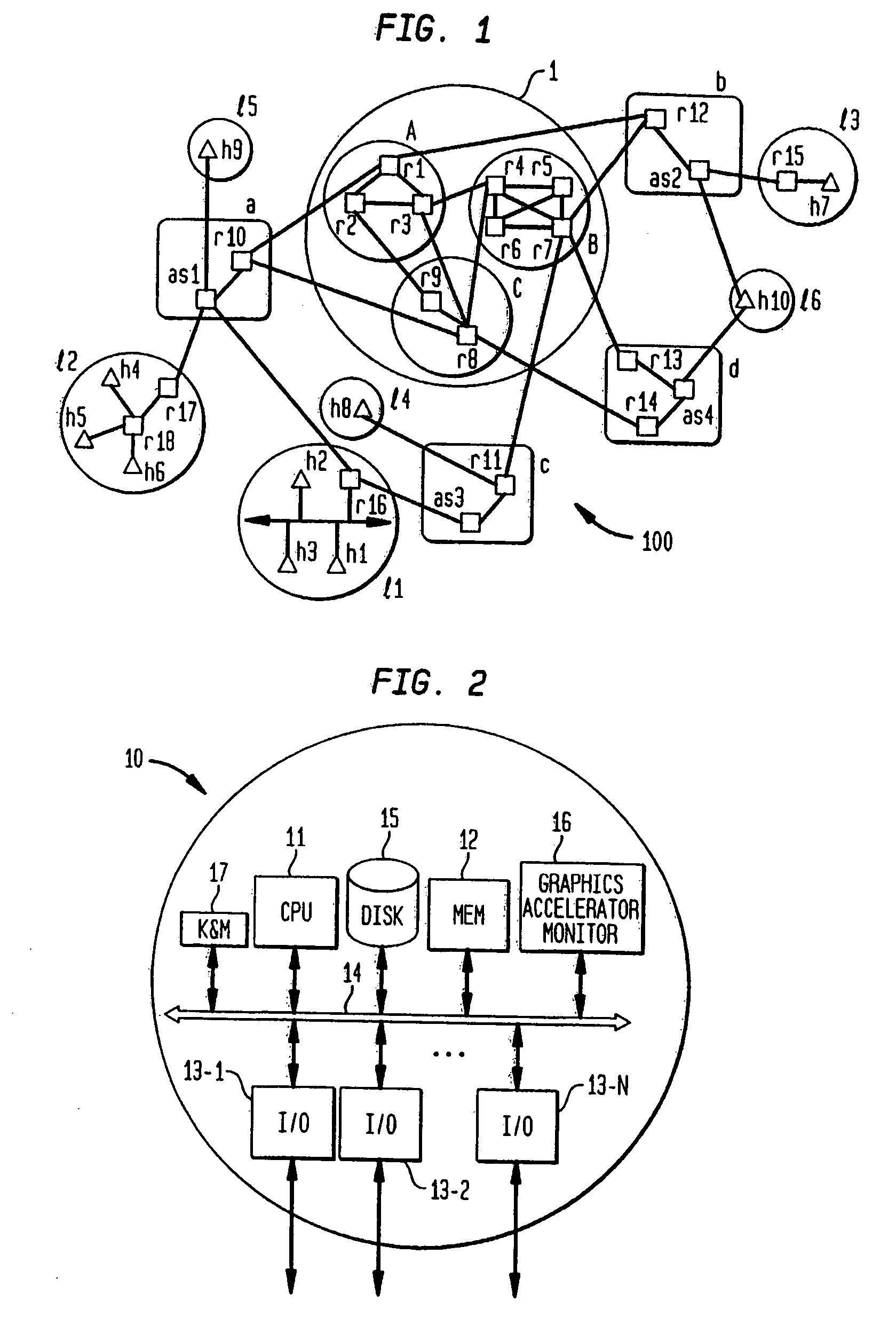
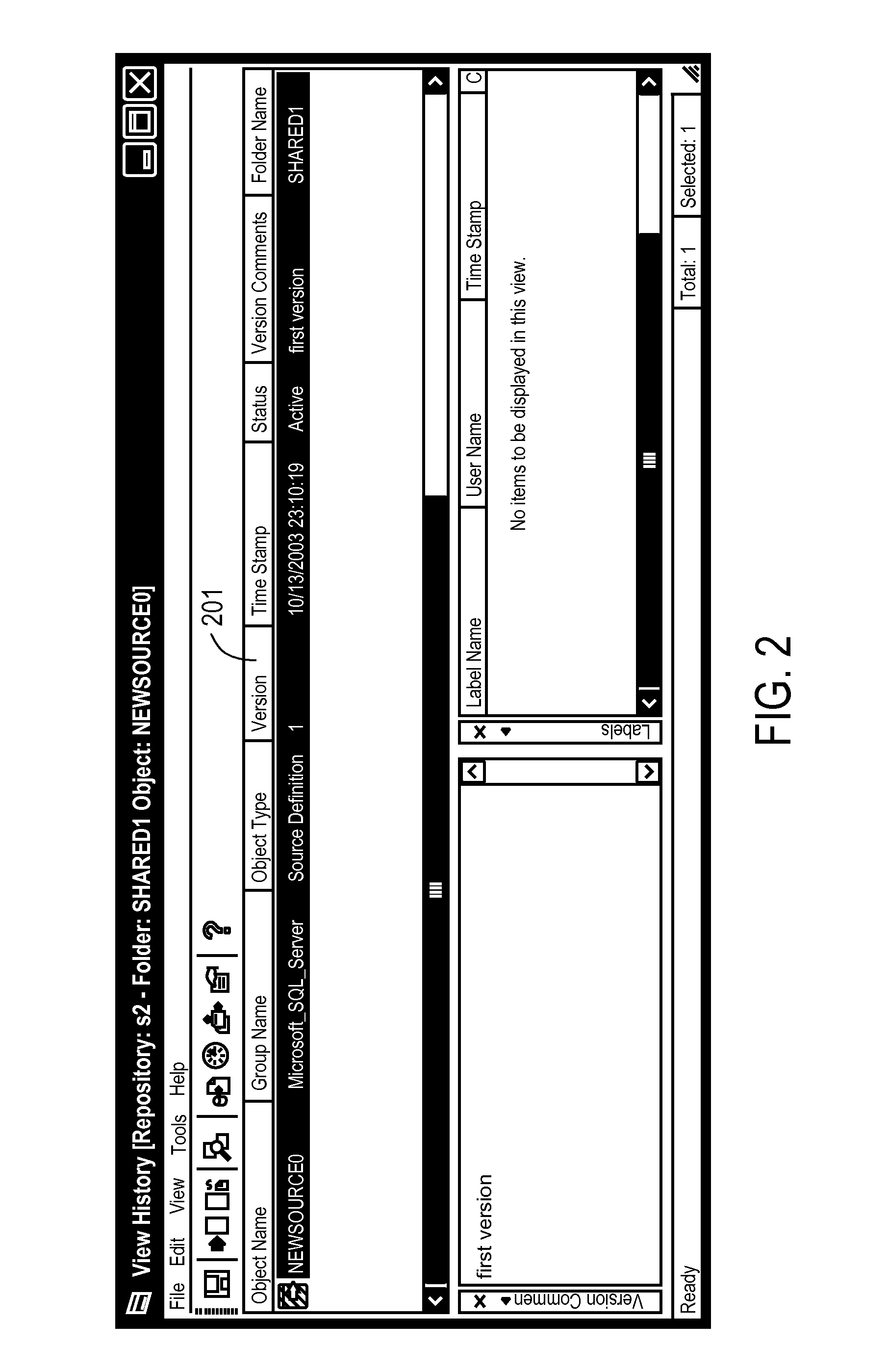
A component of software configuration management, version control, also known as revision control or source control, is the management of changes to documents, computer programs, large web sites, and other collections of information. Changes are usually identified by a number or letter code, termed the "revision number", "revision level", or simply "revision". For example, an initial set of files is "revision 1". When the first change is made, the resulting set is "revision 2", and so on. Each revision is associated with a timestamp and the person making the change. Revisions can be compared, restored, and with some types of files, merged.
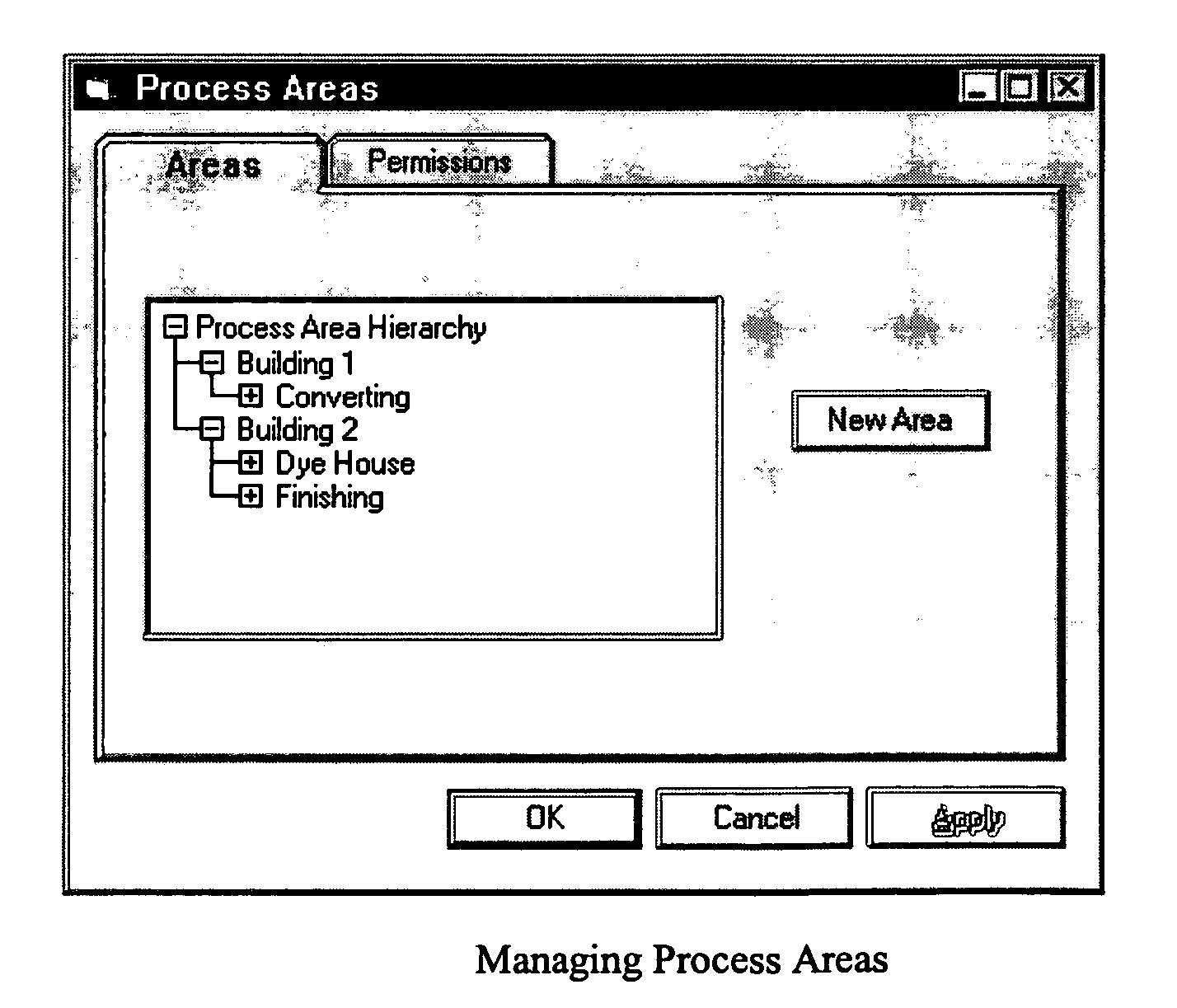
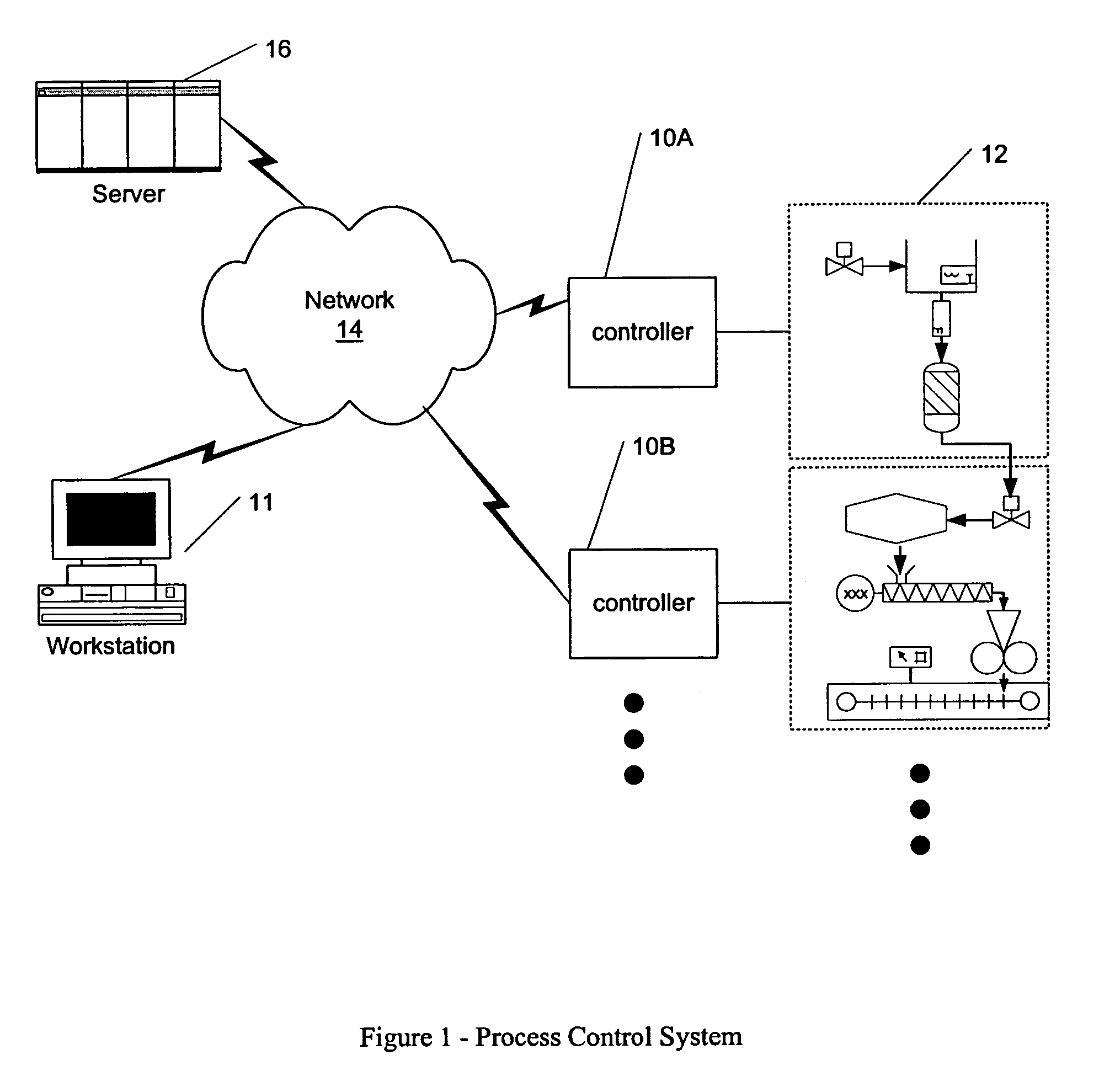
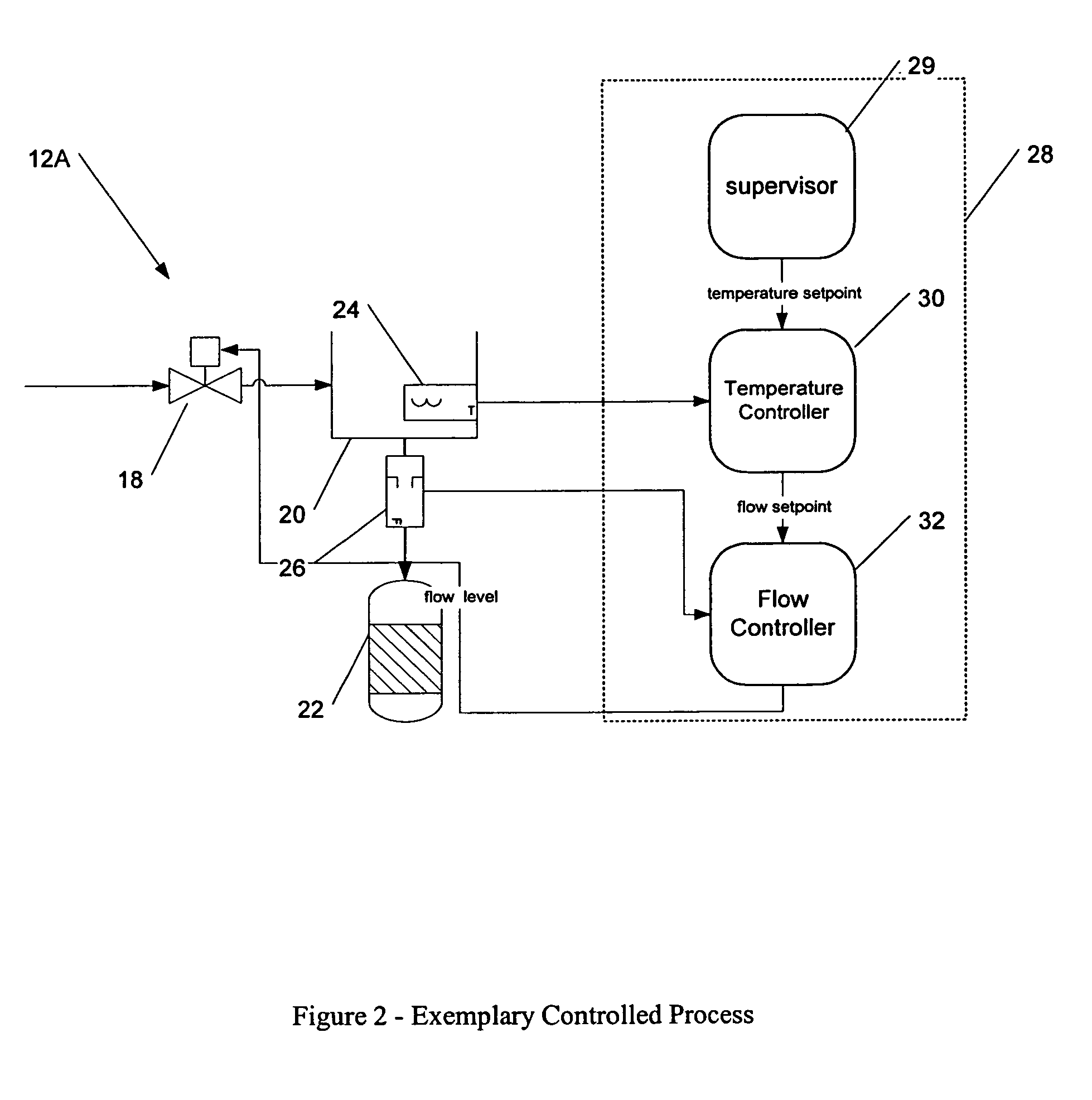
Methods and apparatus for control configuration with versioning, security, composite blocks, edit selection, object swapping, formulaic values and other aspects
InactiveUS7272815B1OptimizationOptimize system configurationData processing applicationsDigital data processing detailsGraphical user interfaceComposite object
Methods and apparatus for configuring process, environmental, industrial and other control systems generate and / or utilize models representing configurations of control systems and / or the systems controlled by them. Records of changes to the models or the configurations represented by them are maintained, thereby, for example, providing bases for determining current states, prior states and histories of changes. Objects in the model have characteristics, such as an object type characteristic and an area characteristic. Users can have corresponding permissions. A security mechanism apparatus controls access by users to the objects. Composite objects are defined by definition objects and are displayed in encapsulated or expanded formats. Objects can include an edit control type identifier that determines how they are presented for editing. Functionality responds to user commands by transferring characteristics of a first object depicted by the graphical user interface to a second object. Configuration-time formulas contained objects are evaluated to constants prior to downloading to the control system.
Owner:SCHNEIDER ELECTRIC SYST USA INC
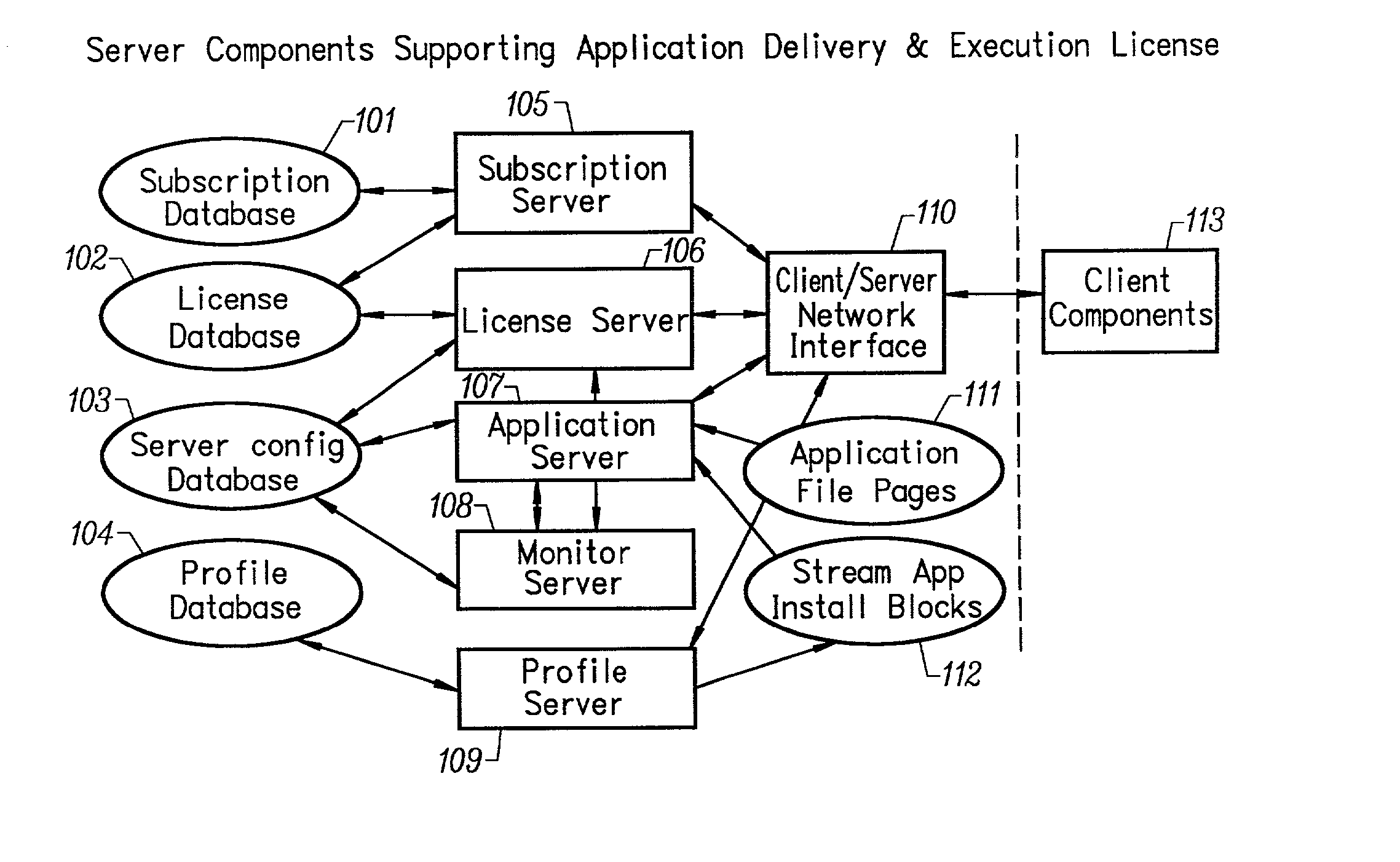
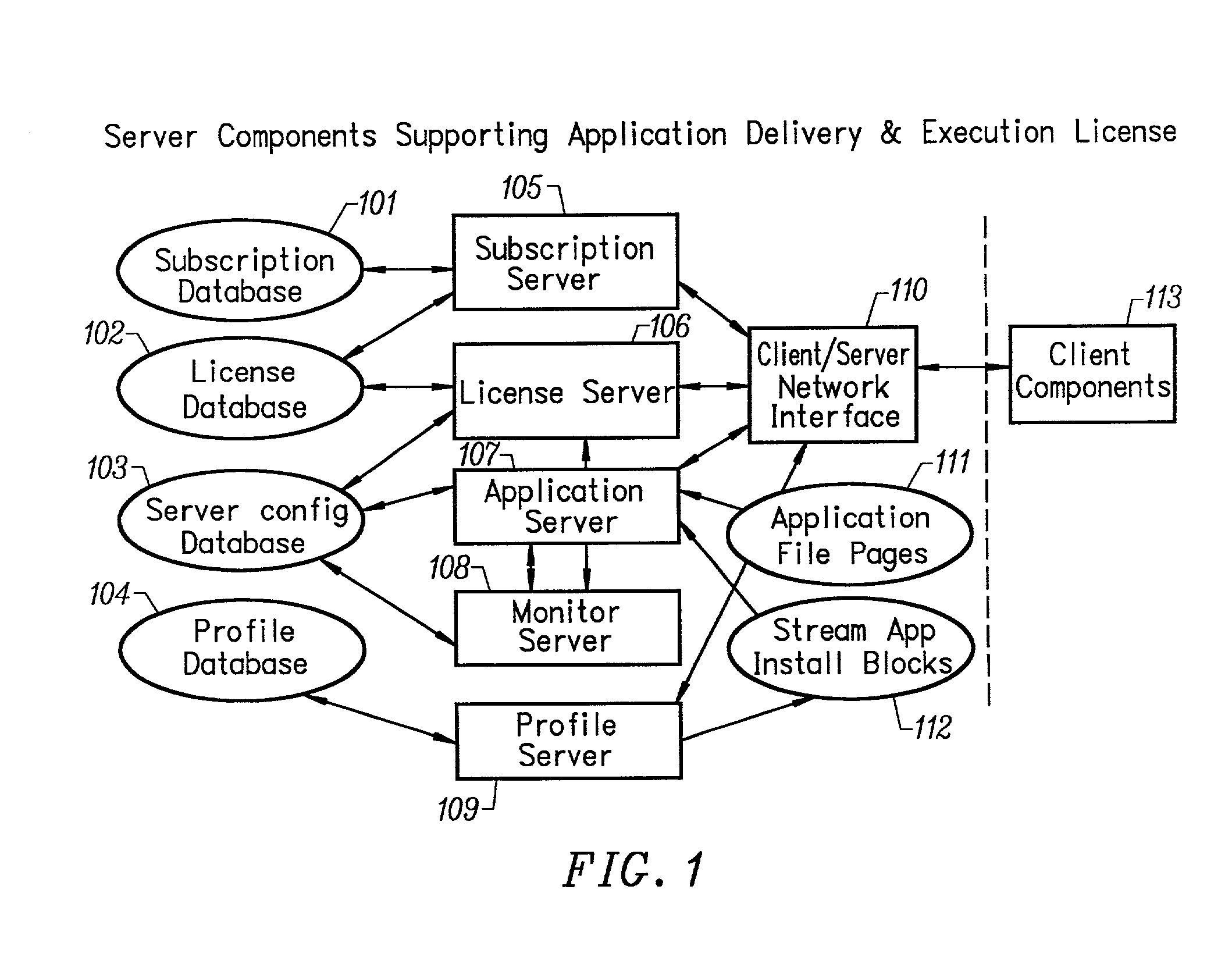
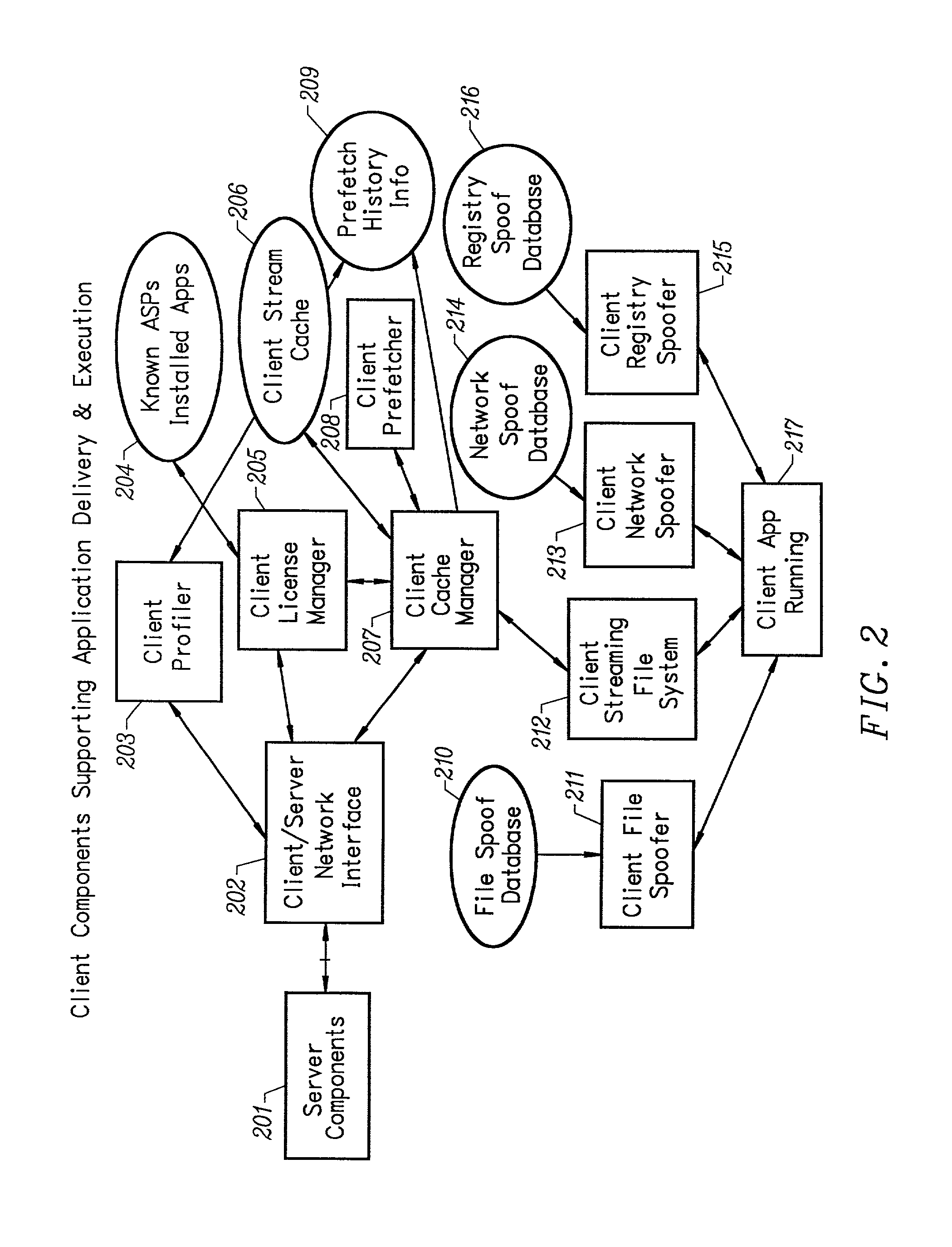
Conventionally coded application conversion system for streamed delivery and execution
InactiveUS20020083183A1Multiple digital computer combinationsProgram loading/initiatingData setMonitoring system
A conventionally coded application conversion system for streamed delivery and execution converts locally installable applications into a data set suitable for streaming over a network. The invention monitors two classes of information during an application installation on a local computer system. System registry modifications are monitored and the modification data are recorded when the installation program writes to the registry of the local computer system. File modification data are logged each time an installation program modifies a file on the system. This data is used to create an initialization data set which is the first set of data to be streamed from the server to the client and contains the information captured needed by the client to prepare the client machine for streaming a particular application. A runtime data set is also created that contains the rest of the data that is streamed to the client once the client machine is initialized for a particular application. A versioning table contains a list of root file numbers and version numbers which are used to track application patches and upgrades. The invention monitors a running application that is being configured for a particular working environment on the local computer system. The data acquired are used to duplicate the same configuration on multiple client machines.
Owner:CREDIT MANAGERS OF CALIFORNIA
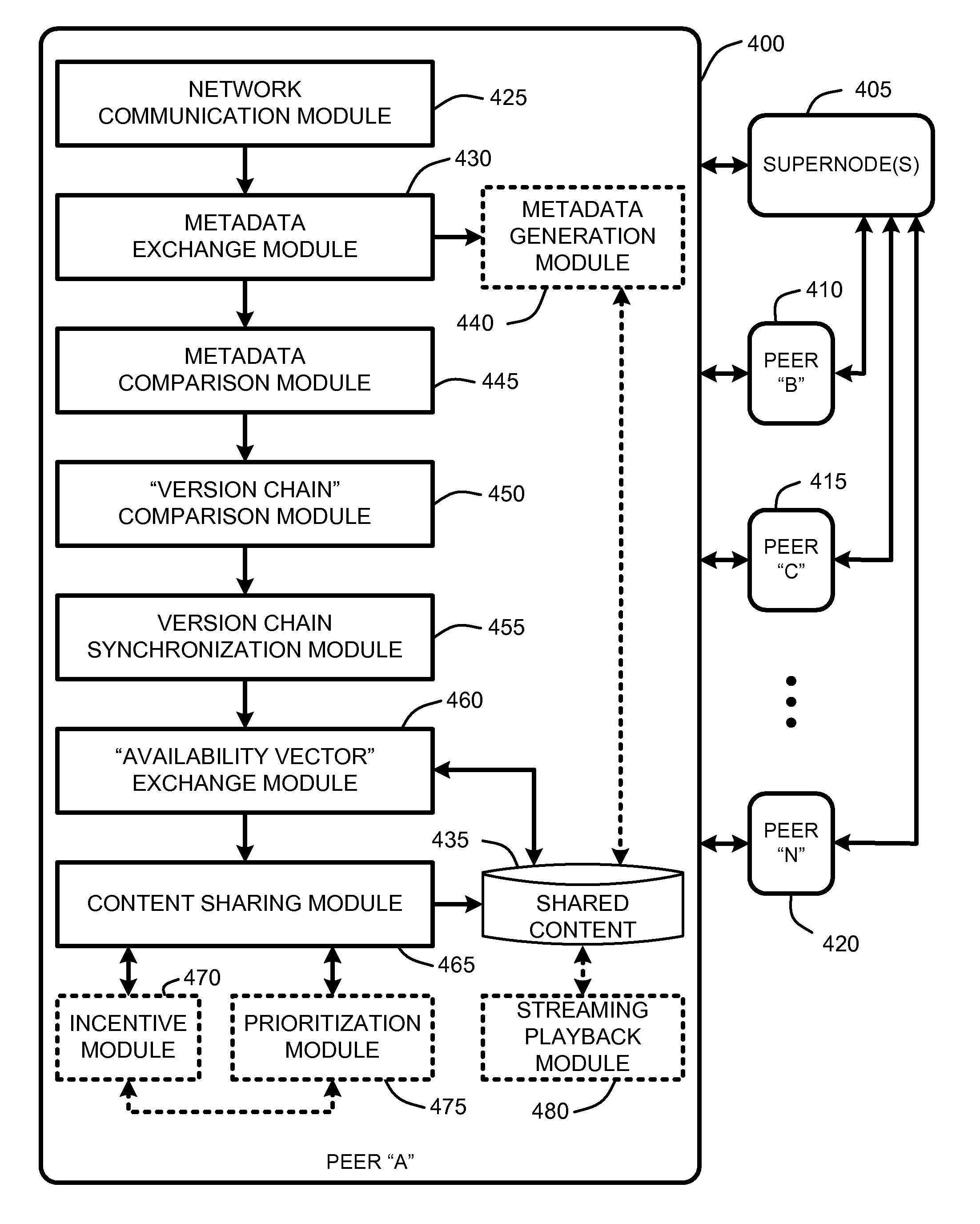
Versioning synchronization for mass p2p file sharing
InactiveUS20080005195A1Digital data information retrievalSpecial data processing applicationsDirectory structureFile sharing
A “Mass File Sharer” (MFS) provides a mass P2P file sharing protocol with optional on-demand file access across a P2P network. Unlike conventional P2P file sharing, the MFS simultaneously asynchronously shares large numbers of files, while providing optional on-demand (synchronous) access to shared files. The MFS uses a unique metadata structure in combination with an inter-peer file / folder version analysis and an inter-peer file / folder availability analysis to share complex directory structures that may include any number of folders, sub-folders, and files. Sharing may be asynchronous and / or synchronous. Specifically, file sharing is generally accomplished as an asynchronous distribution across the network. However, when a particular peer wants direct access particular files, an on-demand access mode is used to enable synchronous delivery of shared files. This combination of asynchronous and synchronous file distribution enables the MFS to support a number of applications, such as on-demand movie viewing, file / folder browsing, etc.
Owner:MICROSOFT TECH LICENSING LLC
Digital photo organizing and tagging method
InactiveUS20110307491A1Digital data processing detailsStill image data indexingDocumentation procedureThe Internet
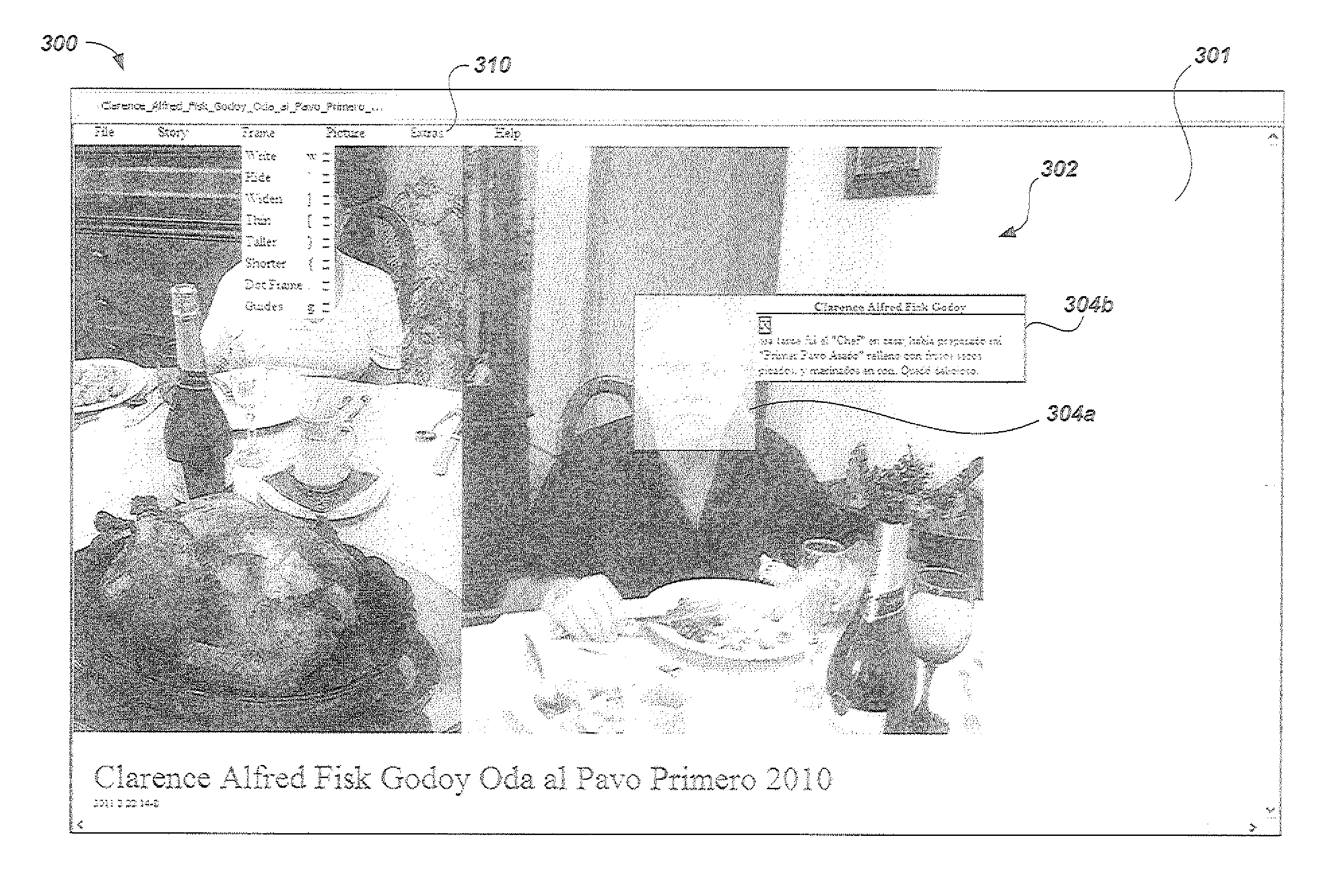
The digital photo organizing and tagging method includes software and a database that organizes digitized versions of dispersed collections of images such as photographs, pictures and other graphical objects from a variety of sources. The method facilitates describing, resizing, indexing, and sorting the different aspects contained in images. Features include documentation, e-mail, updating, version control, inclusion of video, embellishment, sound, animation, text to speech and, dynamic search. An Internet application facilitates annotation, organization, researching and sharing images and corresponding information collected at different times and places. Desktop / Internet applications link and relate images that share common elements. The same person found as a child in one image, as an adult in another, and referenced in a newspaper article is a relation example. The method collects the knowledge embedded in multiple images and produces well documented, organized, and clearly explained printable images, as well as dynamic albums of related images.
Owner:FISK CHARLES M
System and method for migrating processes on a network
InactiveUS6934755B1Prolong lifeMinimize the numberResource allocationDigital computer detailsApplication softwareNetwork service
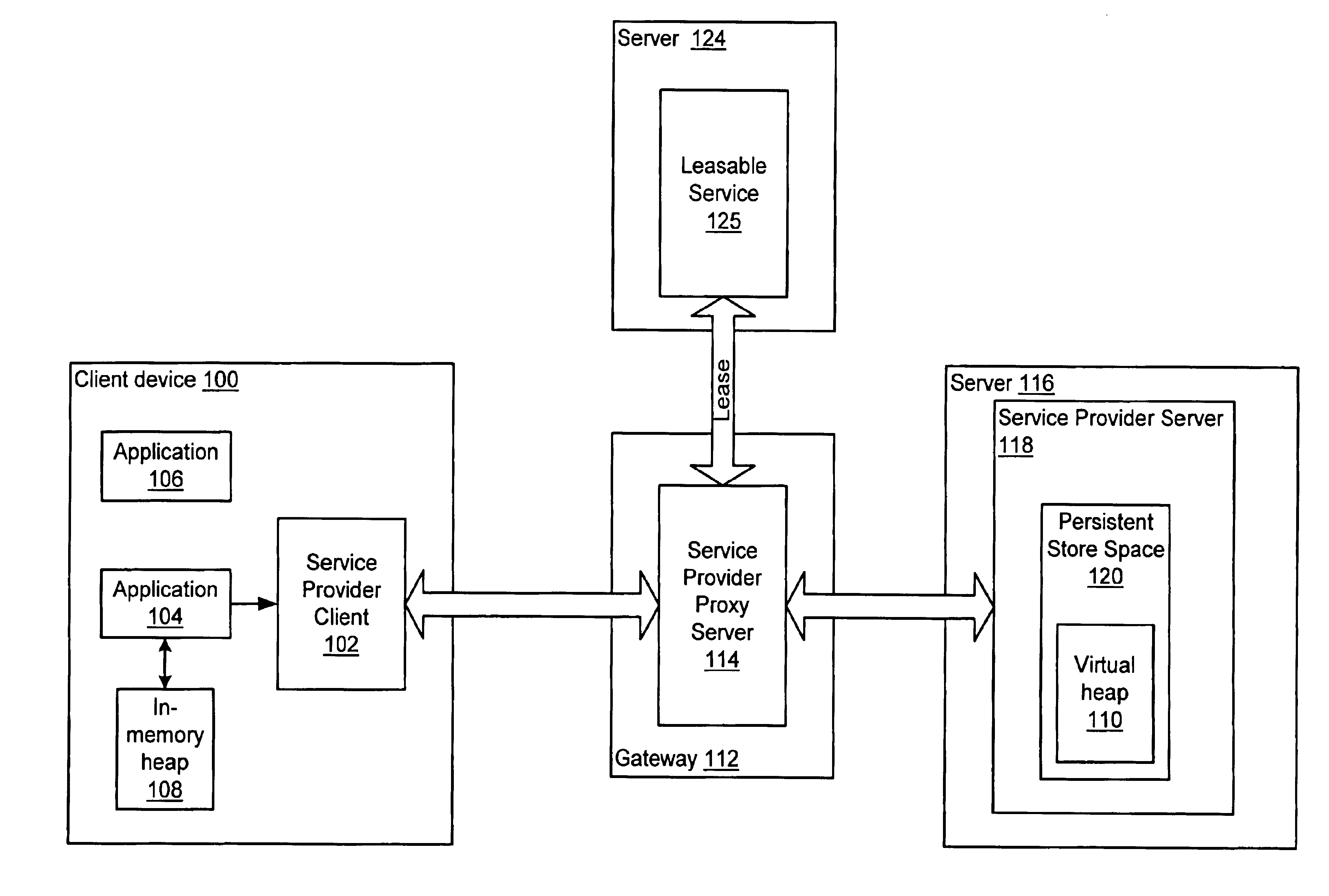
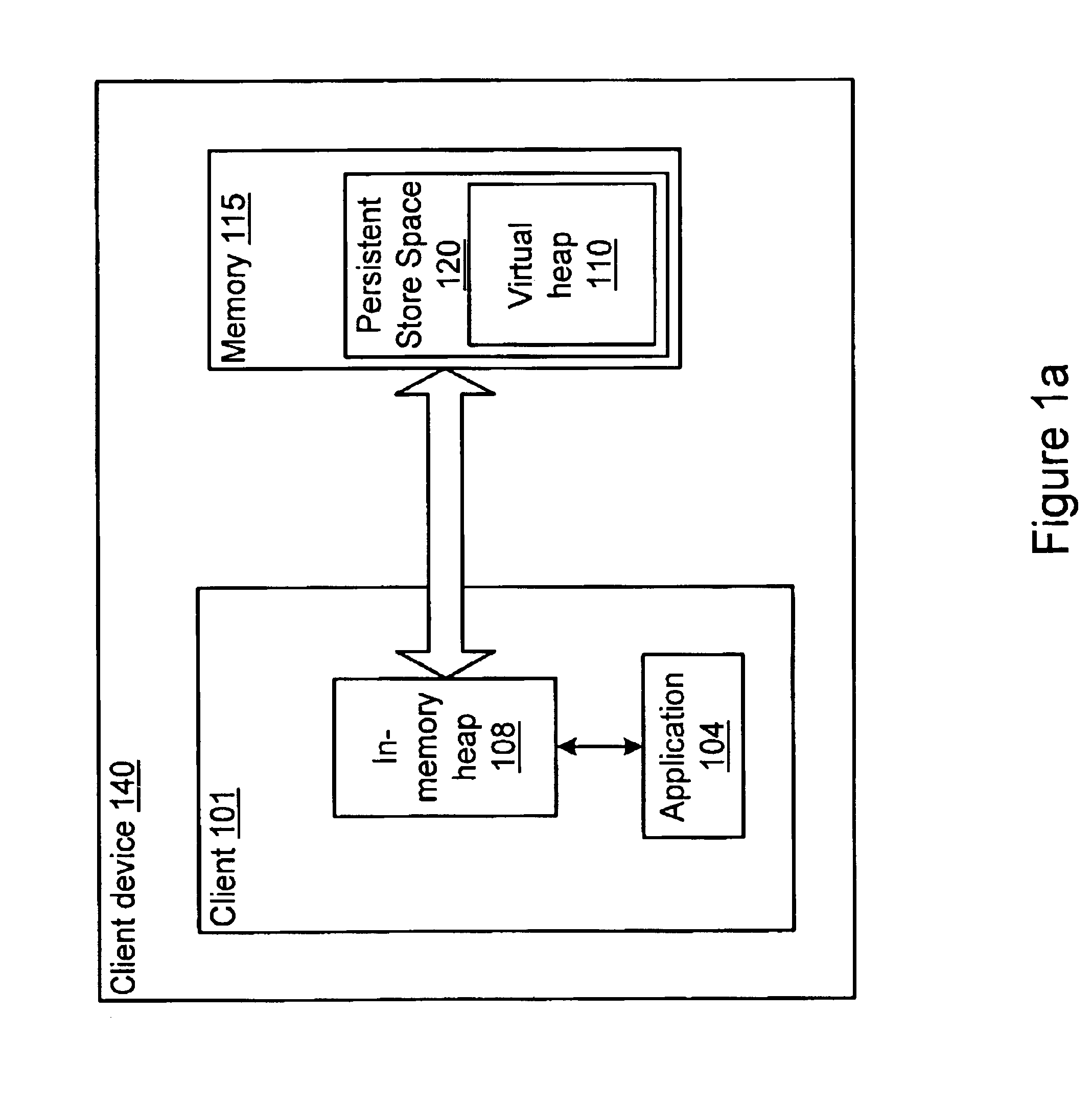
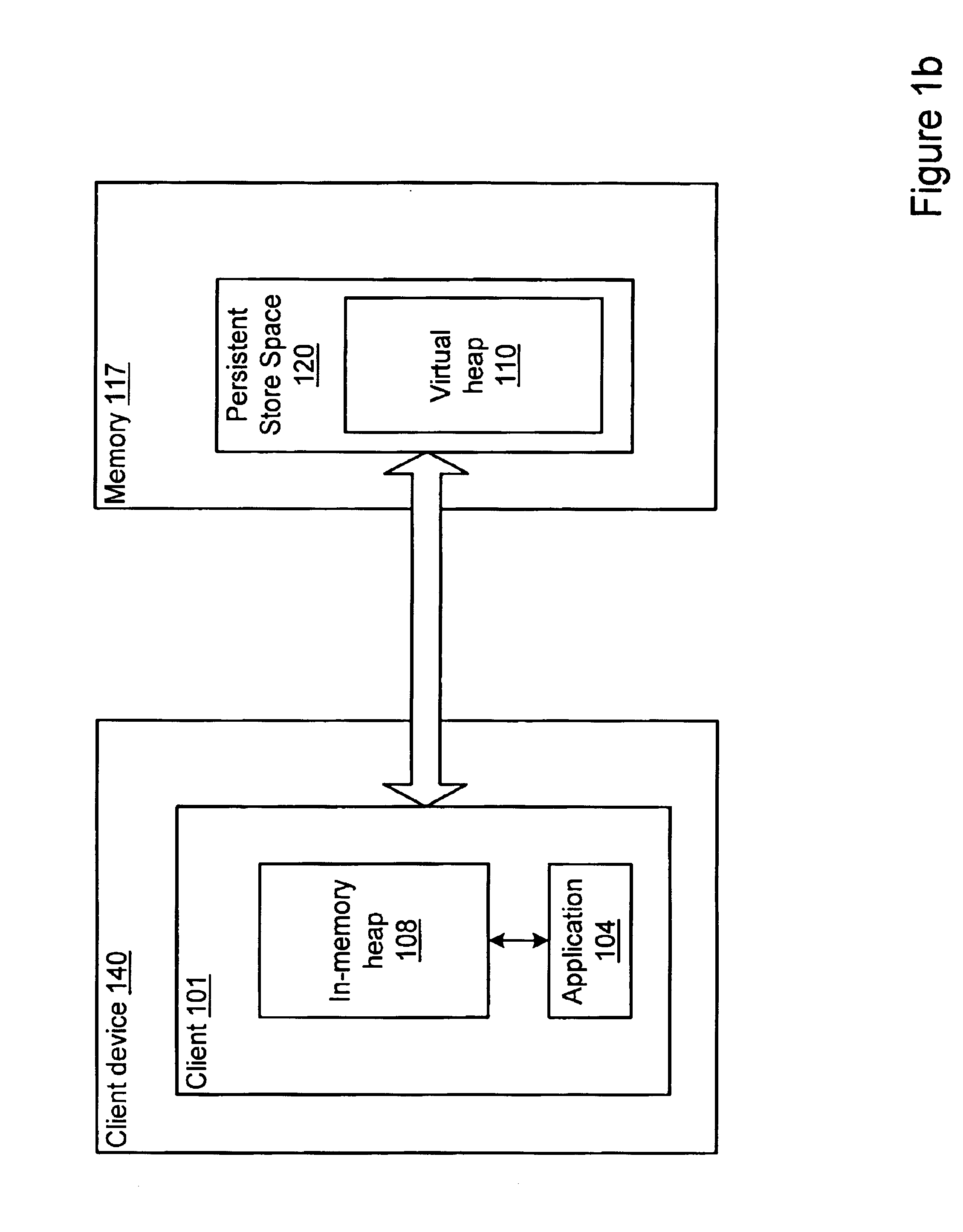
A method and system is provided for migrating processes from one virtual machine to another on a network. To migrate the external state of a process, the process may use a network service connection system or a compact network service connection system for accessing resources external to the virtual machine. A process may be migratable separately from other processes. A process may have an in-memory heap used for the execution of the process, a virtual heap that may include the entire heap of the process including at least a portion of the runtime environment, and a persistent heap where the virtual heap may be checkpointed. In one embodiment, the virtual heap may serve as the persistent heap. In another embodiment, the virtual heap may be checkpointed to a separate, distinct persistent heap. The combination of the in-memory heap, the virtual heap, and the persistent store may be referred to as a virtual persistent heap. One embodiment of a method for migrating an application may include checkpointing the application to a persistent heap. Current leases to local and / or remote resources may be expired. The persistent state of the process may be packaged in the persistent heap and sent to the node where the process is to migrate. A transaction mechanism may be used, where the process's persistent state is copied and committed as having migrated on both the sending and receiving nodes. The state of the process may then be reconstituted into a new virtual persistent heap on the node where the application migrated. Leases to local and / or remote resources for the process may be re-established. The process may then resume execution on the node where it migrated. In one embodiment, a versioning mechanism may be used whereby nodes where a process once lived may cache a previous state. In addition, a user interface (UI) may be provided to manage process checkpoints.
Owner:ORACLE INT CORP
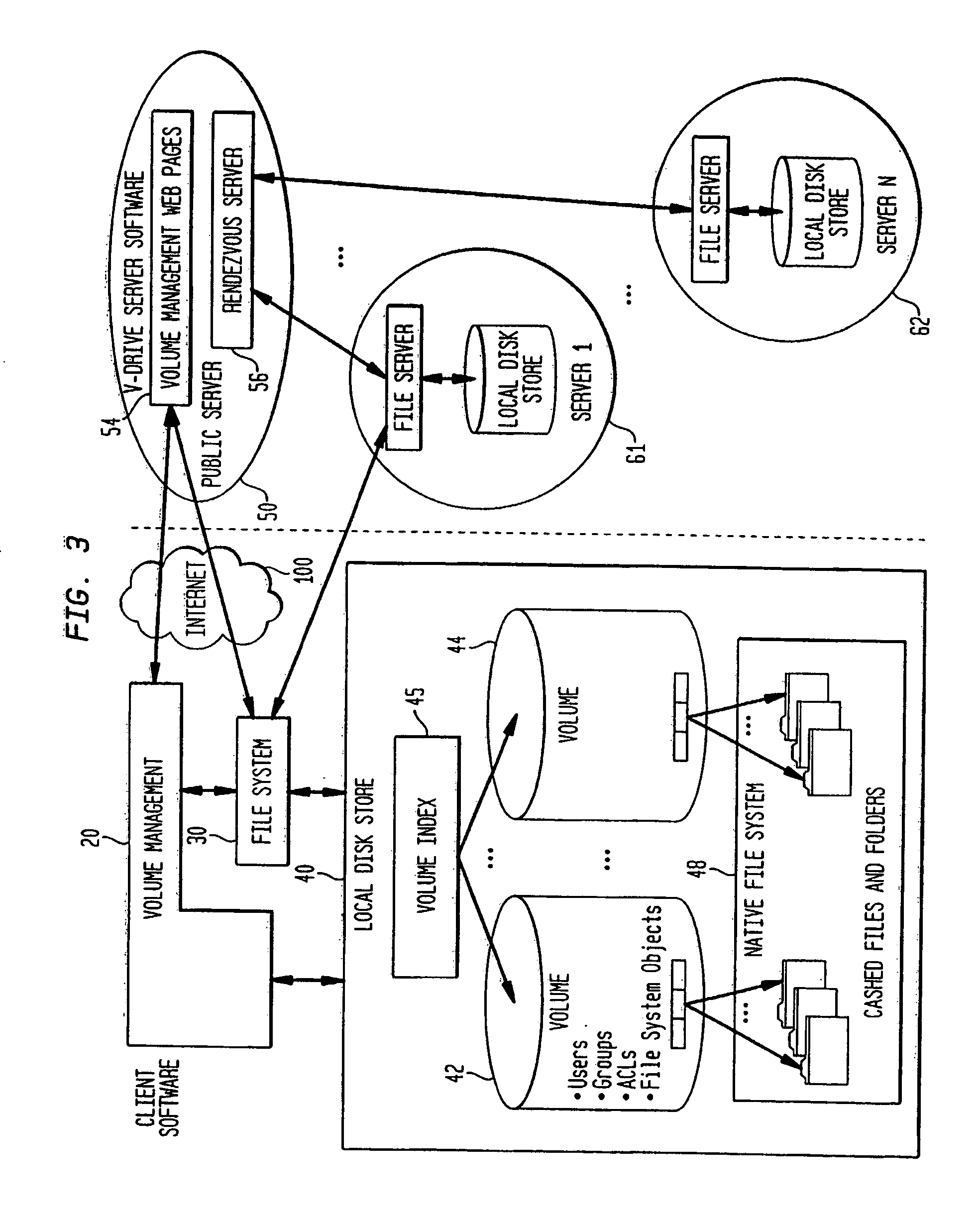
Internet-based shared file service with native PC client access and semantics and distributed version control
InactiveUS20060129627A1Multiple digital computer combinationsTransmissionOperational systemWide area network
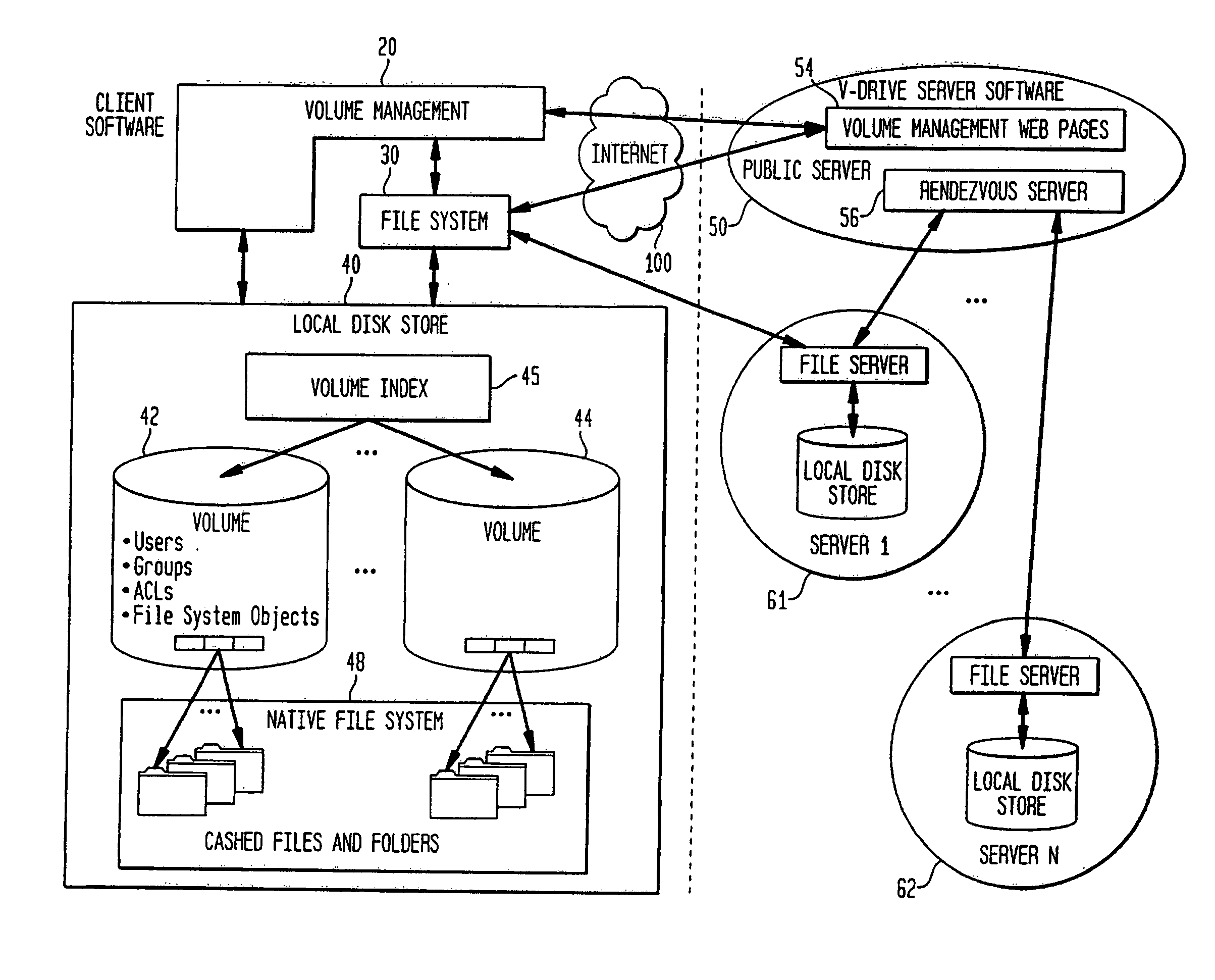
A multi-user file storage service and system enable each user of a pre-subscribed user group to operate an arbitrary client node at an arbitrary geographic location, to communicate with a remote file server node via a wide area network and to access the files of the file group via the respective client node in communication with the remote file server node via the wide area network. More than one user of the pre-subscribed user group is permitted to access the file group at the remote file server node simultaneously. Illustratively, the integrity of the files at the remote file server node are maintained by controlling each access to each file at the remote file server node so that each access to files at the remote file server is performed, if at all, on a respective portion of each file as most recently updated at the remote file server node. Thus, all native operating system application programming interfaces operate as if all multi-user applications accessing the files function as if the remote server and client nodes were on the same local area network. Illustratively, an interface is provided for adapting file access one of the client nodes. The interface designates at the client node each accessible file of the group as stored on a virtual storage device. The interface enables access to the designated files in a fashion which is indistinguishable, by users of, and applications executing at, the client node, with access to one or more files stored on a physical storage device that is locally present at the client node. Illustratively, an encrypted key is transferred from the remote file server node to one of the client nodes via a secure channel. The key is encrypted using an encryption function not known locally at the remote file server node. The transferred key is decrypted at the client node. The key is used at the client node to decrypt information of the files downloaded from the remote file server node or to encrypt information of the files prior to uploading for storage at the remote file server node. Access control to a particular one of the files of the group can be delegated to an access control node.
Owner:GOOGLE LLC
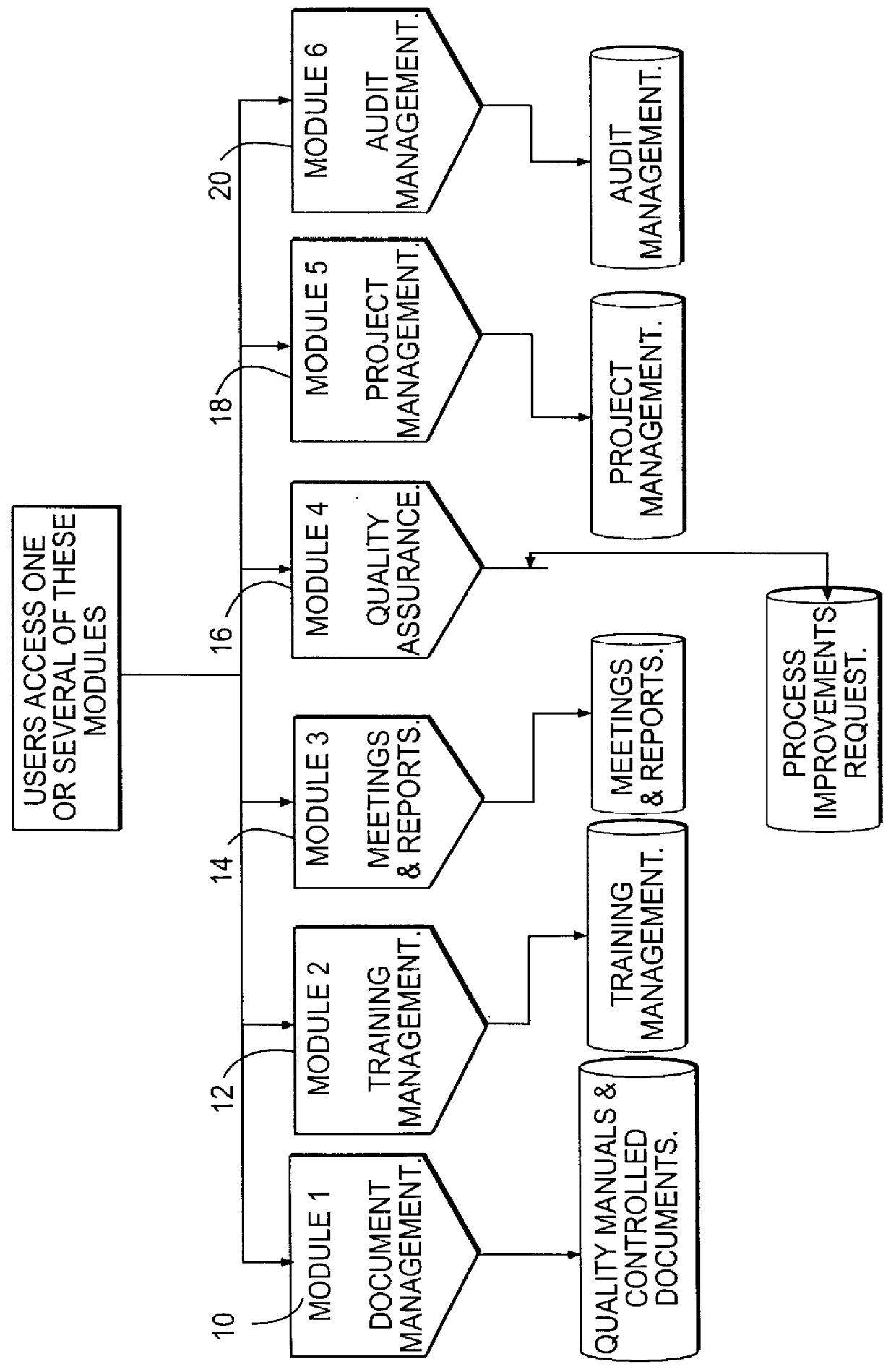
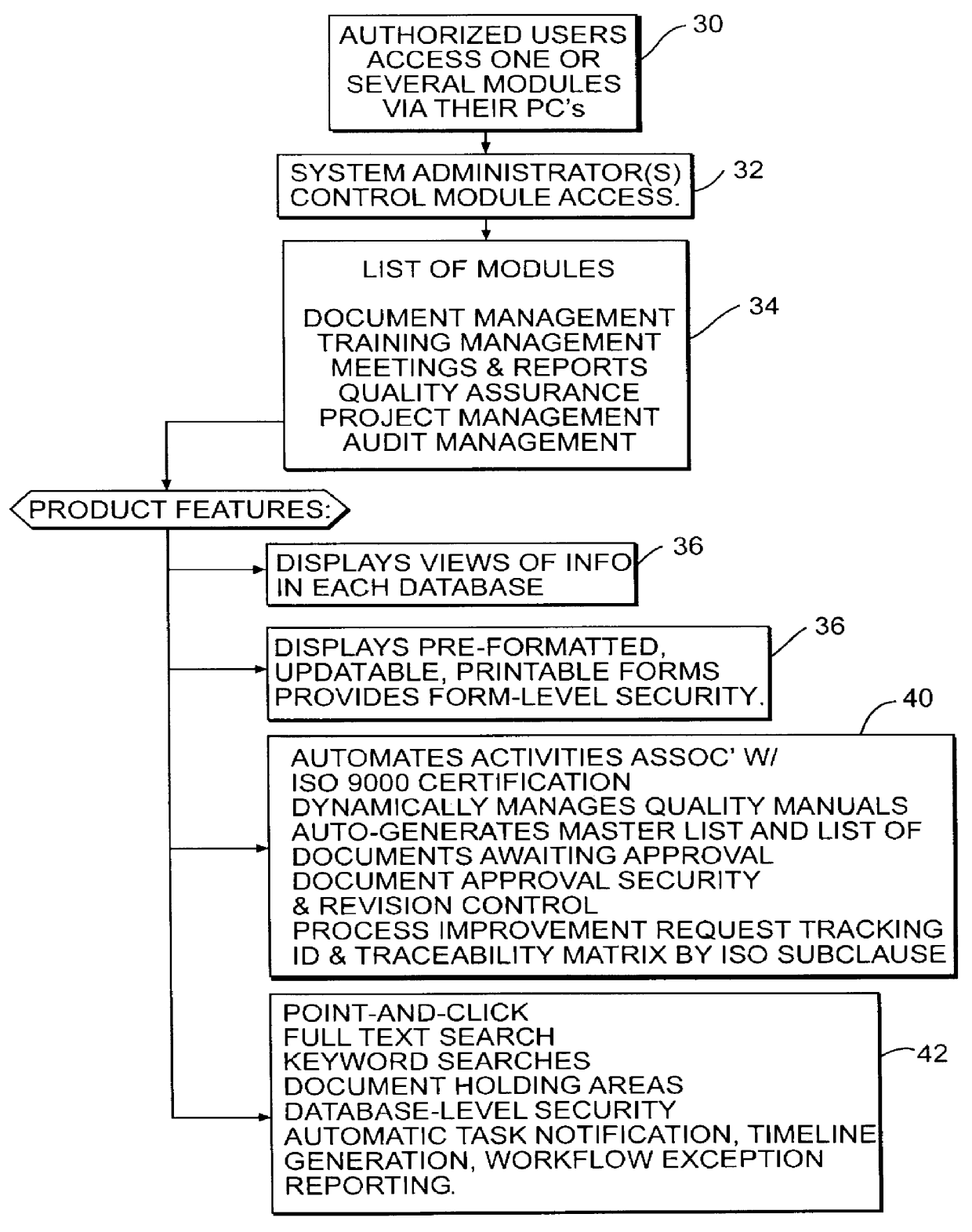
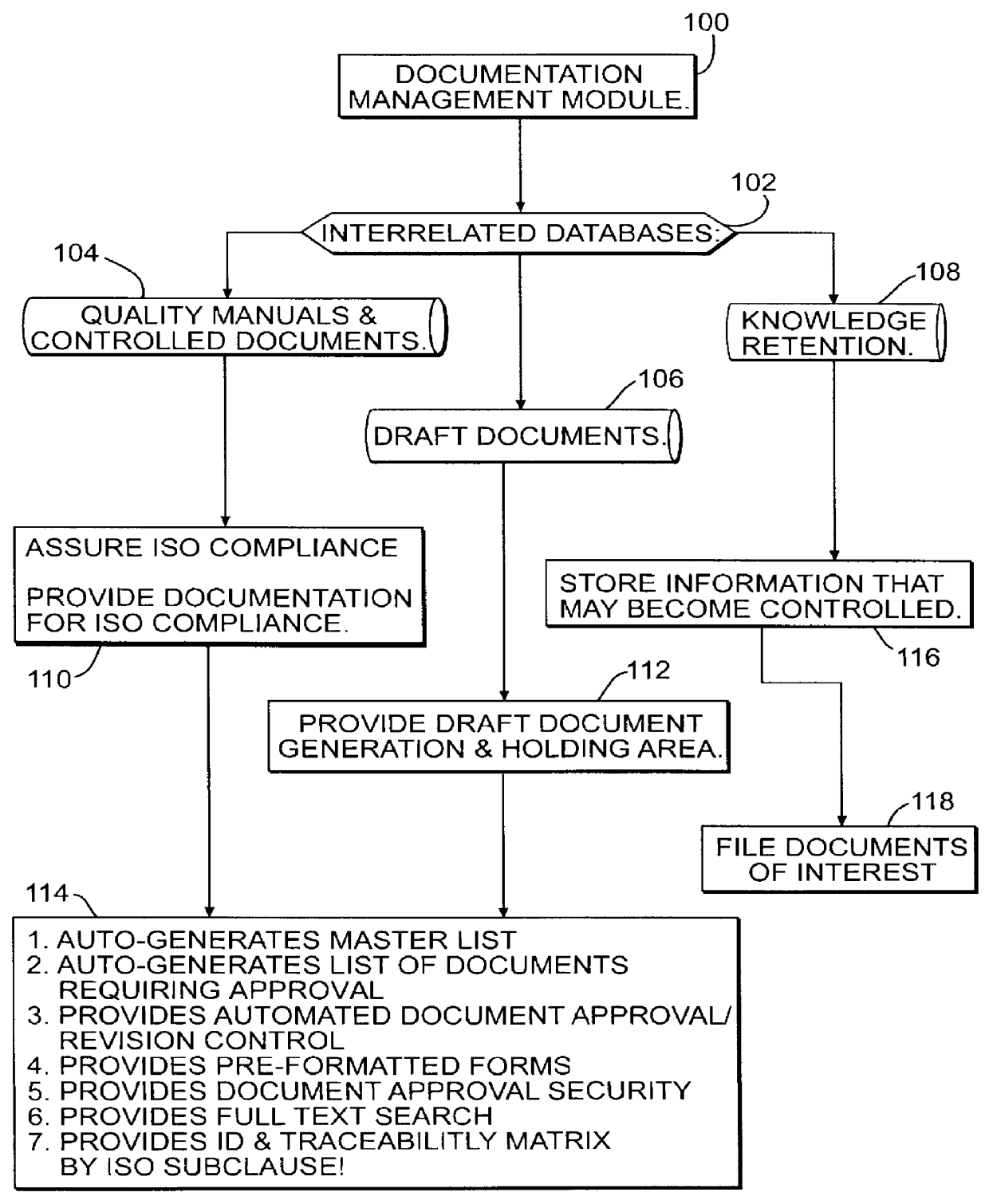
Document management system and method for business quality modeling
InactiveUS6154753AOffice automationSpecial data processing applicationsDocumentation procedureProject management
A computer implemented system and method and a computer readable medium for complying with the requirements of a quality standard known as ISO 9000. The areas covered include controlled documentation, training management, meetings and reports, process improvement requests, project management, and audit management. All controlled documents have a security and revision control portion that controls the access and approval capabilities of the documents. The system is form controlled. Certain individual fields of the forms require the entry of data, and field's control are controlled by certain fields of other forms, with the fields being updated by other fields in the system, operator entry of data, and a combination of control by both the system and operator entry. The system includes an ISO matrix relating each document to an ISO clause. The system has a controlling document for each delineated activity, and all other documents relating to such activity are linked as a child of the controlling document. An audit trail is created by storing and making available previous iterations of current documents as child documents, insuring that the first issue, subsequent changes to content, movement to draft status, reprieval, and reissue are available for auditing the activities of the business.
Owner:CABLE & WIRELESS INC +1
Method and apparatus for content repository with versioning and data modeling
InactiveUS6904454B2Lower requirementData processing applicationsDigital computer detailsData modelingData entity
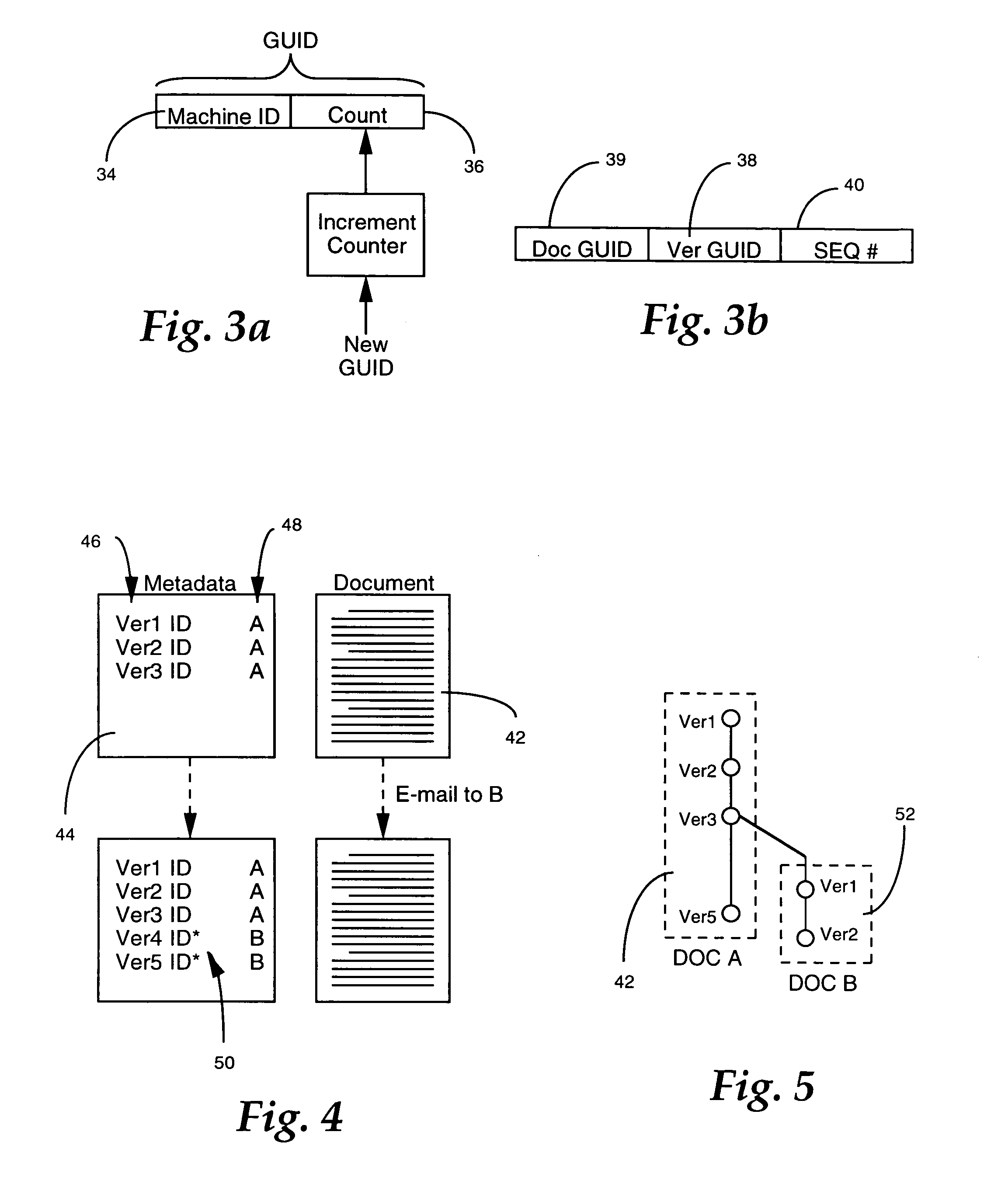
The present invention is related to method and apparatus for versioning. Versioning information is stored as metadata associated with data entities. A hierarchical relationship between the entities allows the definition of an editorial sequence and separate revisions within that sequence as well as relationships between sequences in a self-contained format.
Owner:III HLDG 3
System and method for managing information technology models in an intelligent workload management system
ActiveUS20110126047A1Free computational resourceAgile and flexible managementFault responseDigital computer detailsPlanned changeService-oriented architecture
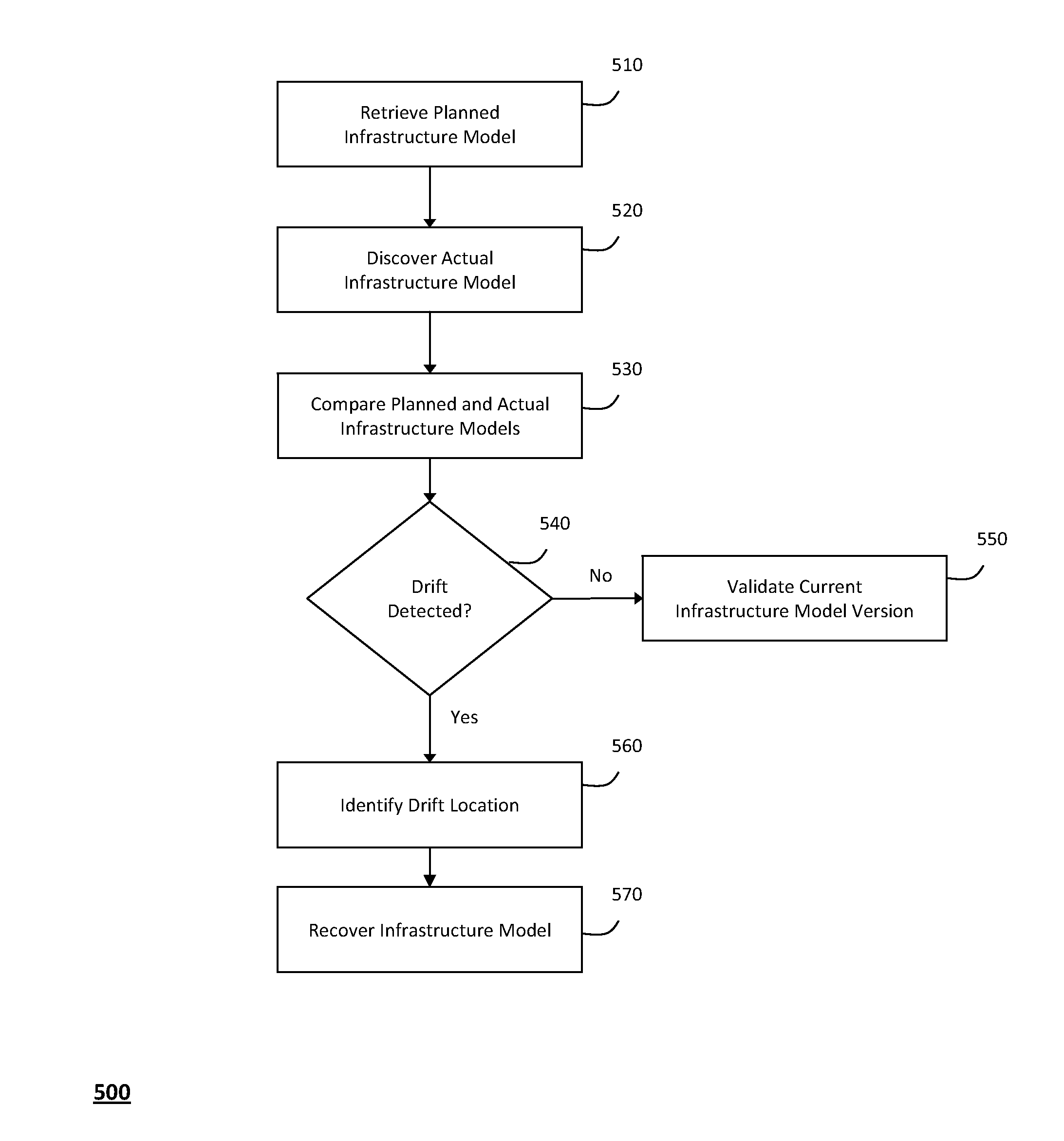
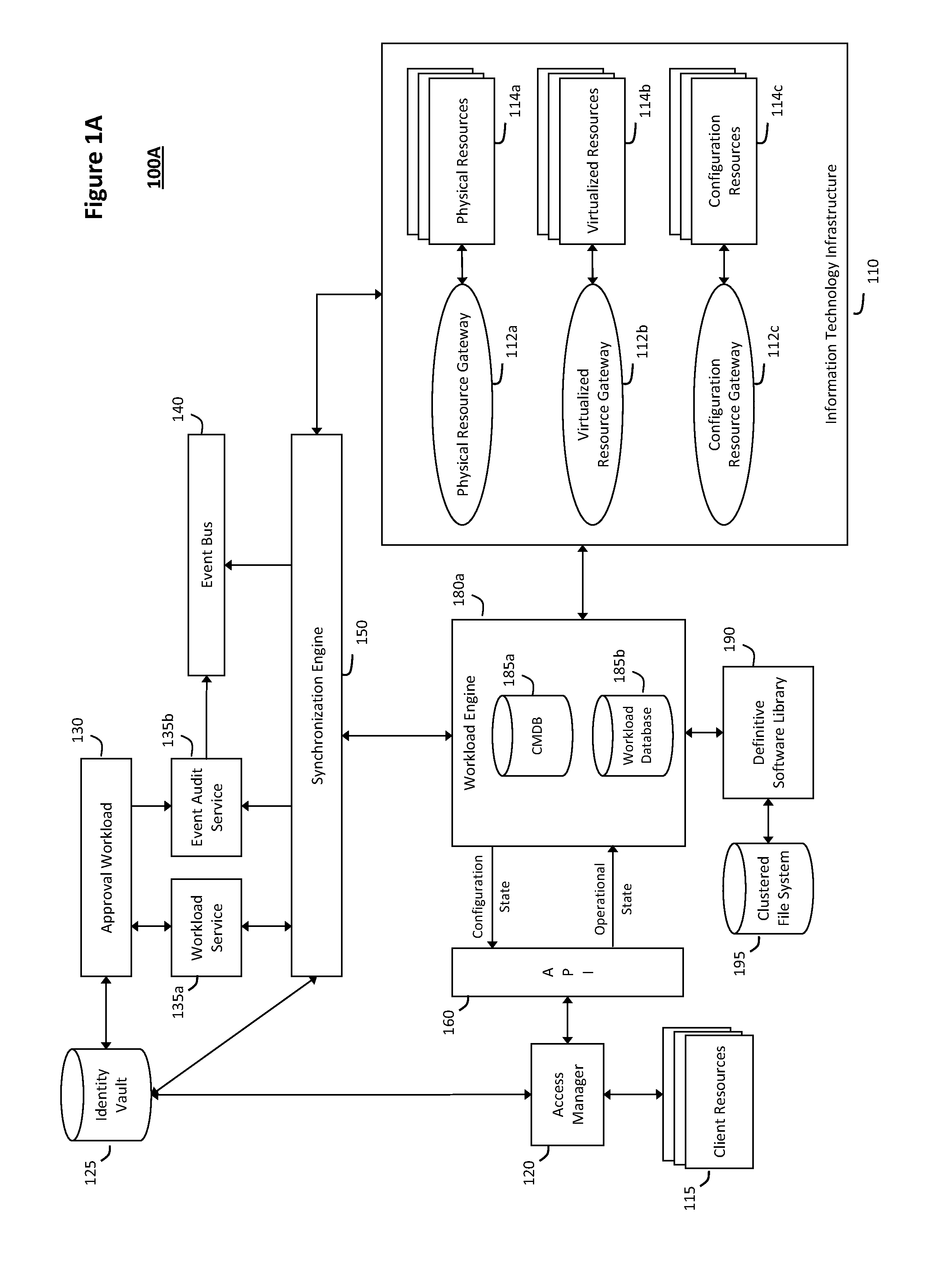
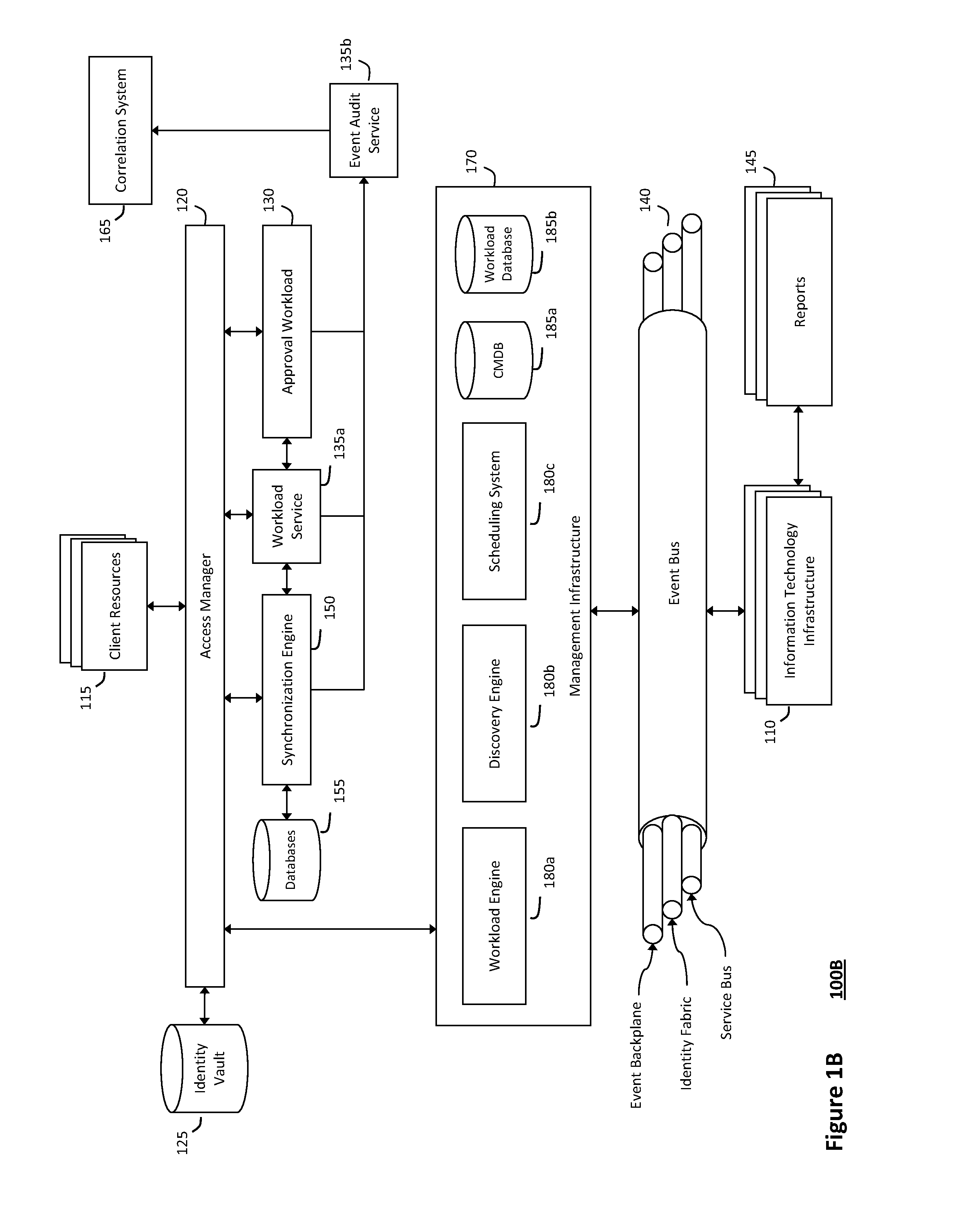
The system and method described herein for managing information technology models in an intelligent workload management system may include a computing environment having a model-driven, service-oriented architecture for creating collaborative threads to manage workloads. In particular, the management threads may converge information for managing planned changes and recovery processes for version-controlled snapshots of the information technology models. For example, a discovery engine may enrich models of an infrastructure with identity information obtained from an identity vault and the infrastructure itself, and a management infrastructure may then manage planned changes to the infrastructure model. In particular, the management infrastructure may construct implementation plans that coordinate interaction between managed entities to implement the planned changes, and may further detect drifts between operational states and planned states for the infrastructure models.
Owner:MICRO FOCUS SOFTWARE INC
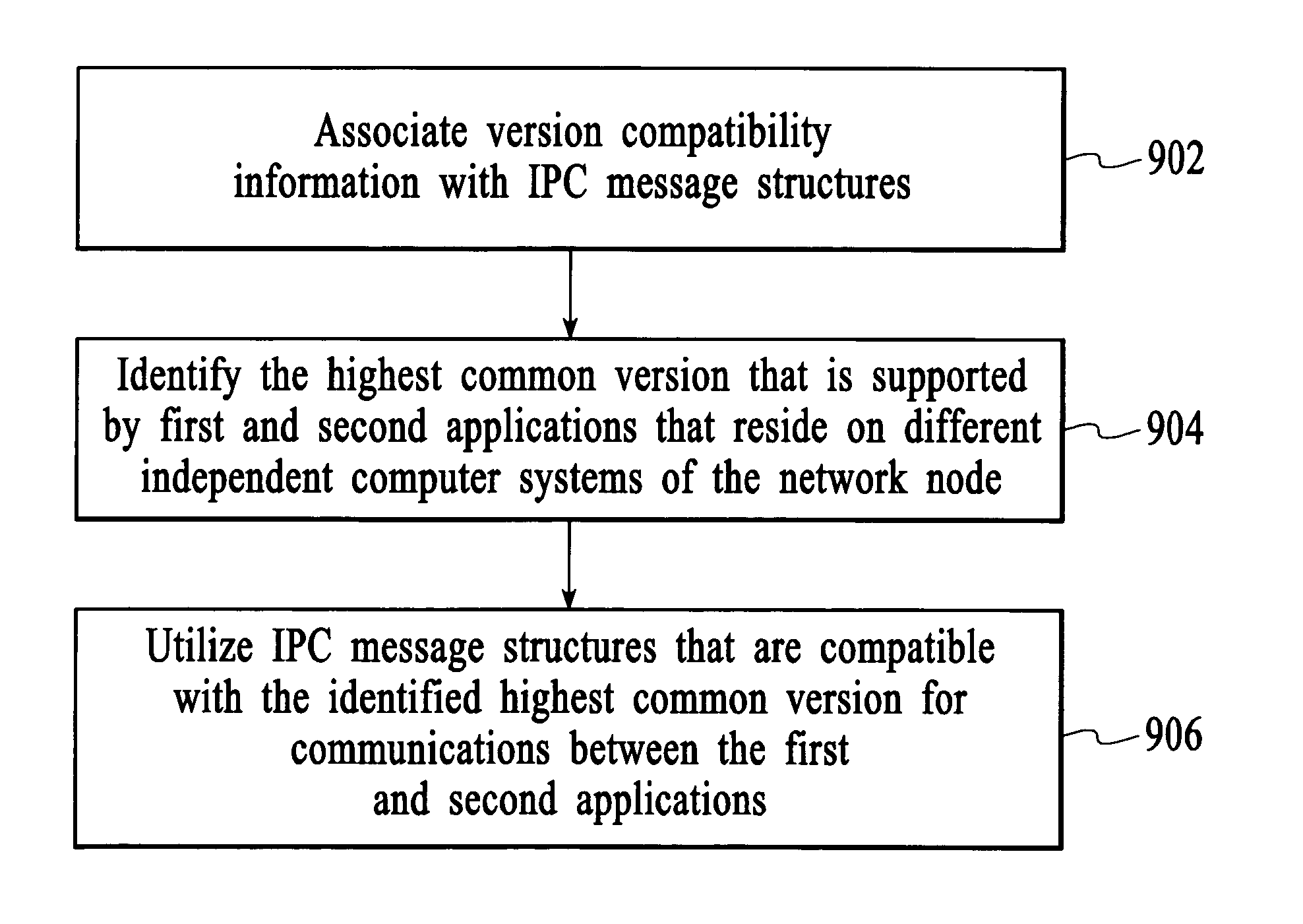
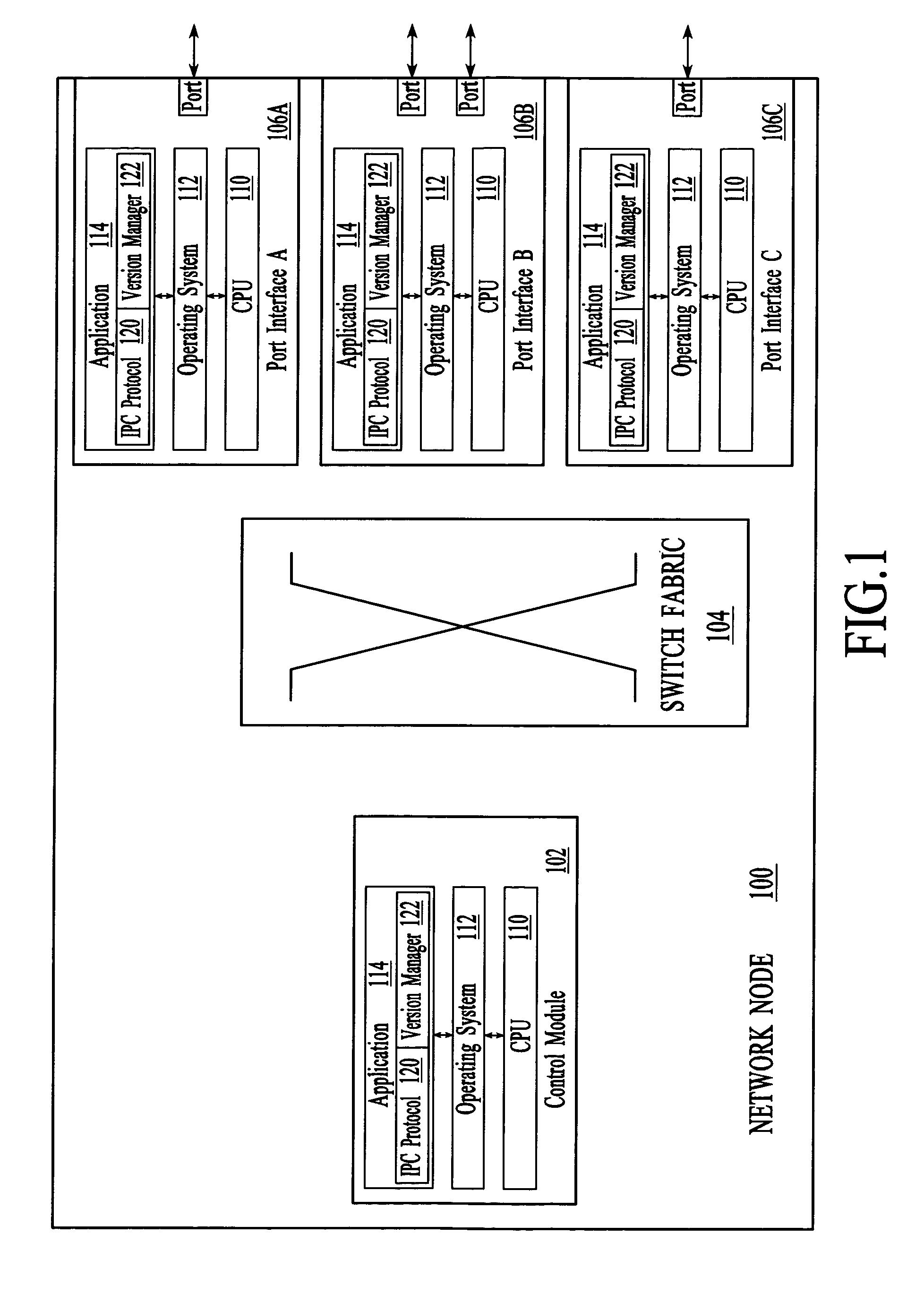
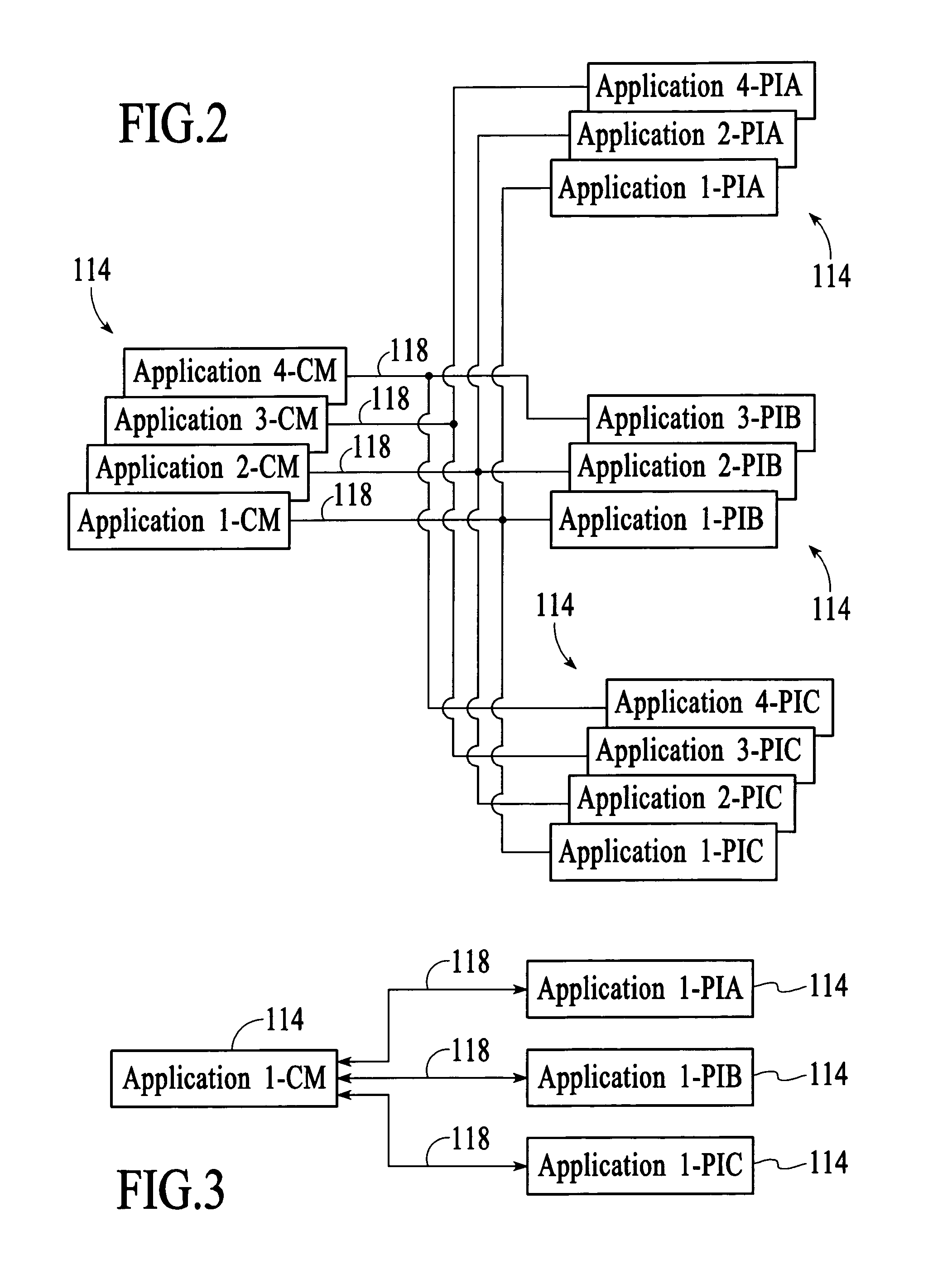
Implicit interprocess communications (IPC) versioning support
InactiveUS7653911B2Maintain compatibilityMultiprogramming arrangementsSpecific program execution arrangementsComputer compatibilityMessage structure
Owner:WSOU INVESTMENTS LLC
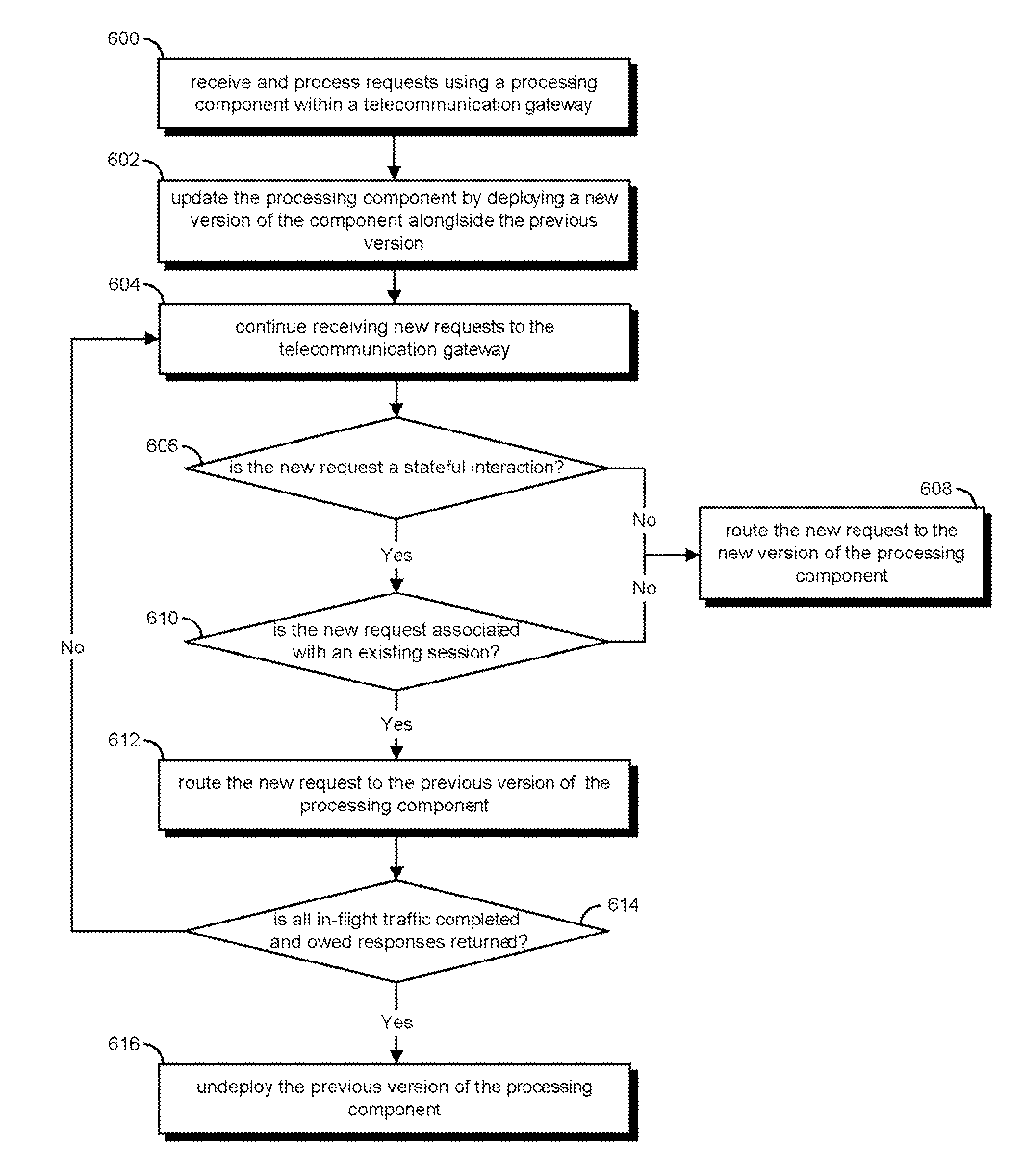
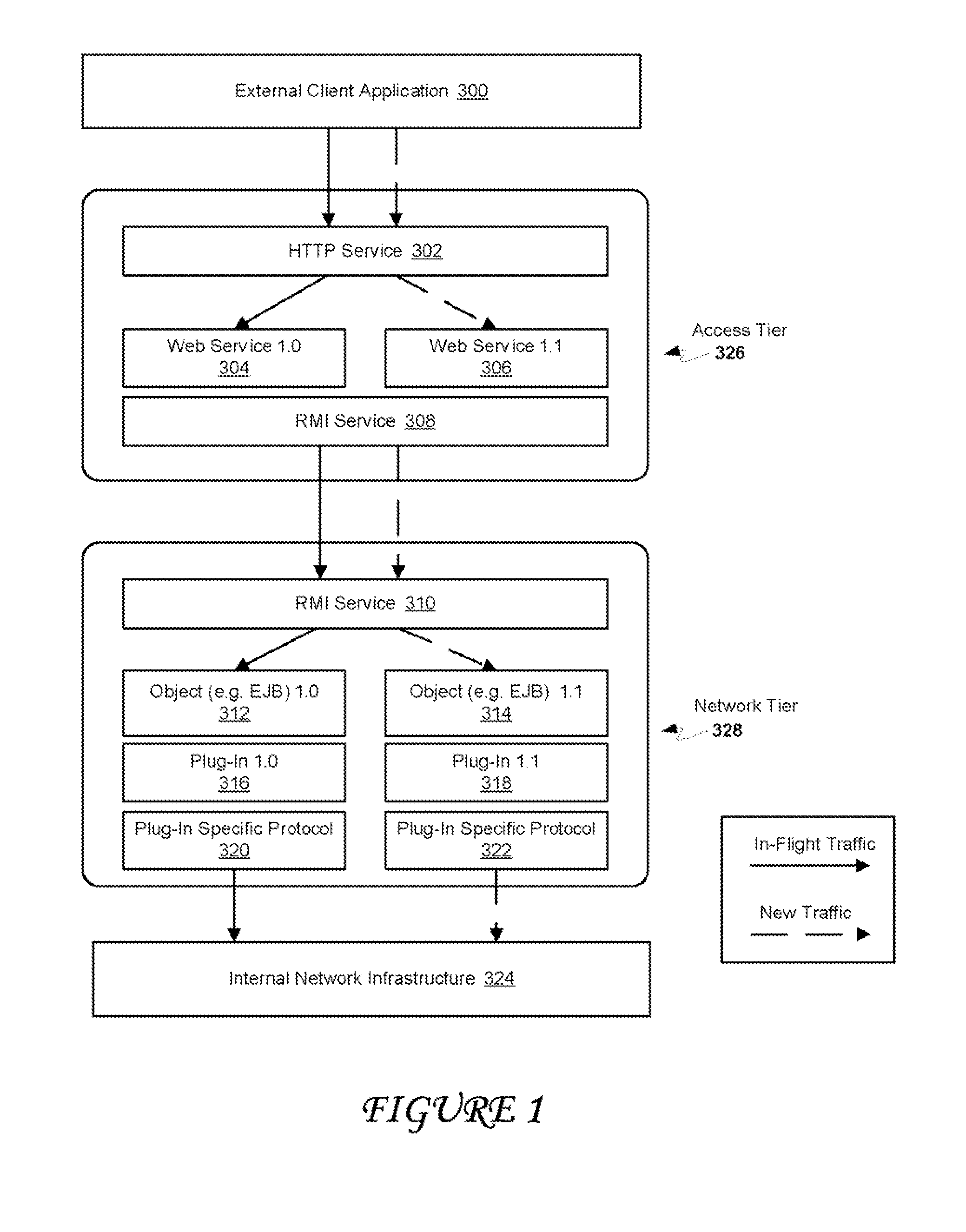
System and method for providing a production upgrade of components within a multiprotocol gateway
ActiveUS8863111B2Automatic exchangesData switching networksTraffic capacityProtocol for Carrying Authentication for Network Access
A production upgrade is described for a multiprotocol gateway. This upgrade allows various modules and components within the gateway to be upgraded independently without impacting traffic flow in the gateway. The upgrade can be performed by deploying a new version of the module alongside an older version of the same module. New client requests can then be directed to the new version, while requests requiring the older module can be continued to be serviced by the prior version. A distinction is made between stateless and stateful conversation during the upgrade of various components. For stateful conversations, request traffic can be versioned according to the session to which each request belongs. A highly available state storage scheme allows new versions of the module to consume state information used by the older versions. For stateless conversations, all new requests can be immediately routed to the new version of the module.
Owner:ORACLE INT CORP
Detection of malicious software, firmware, IP cores and circuitry via unintended emissions
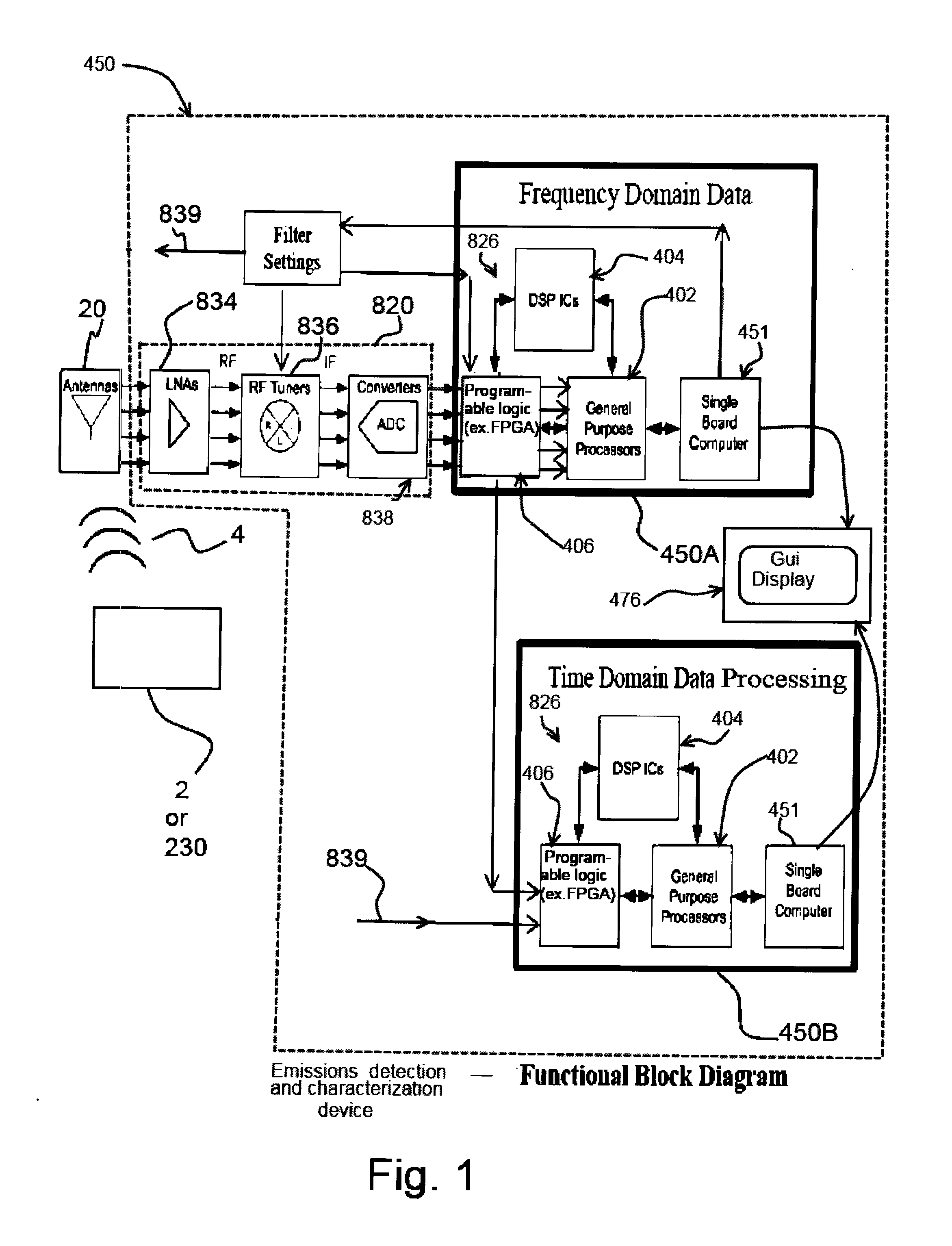
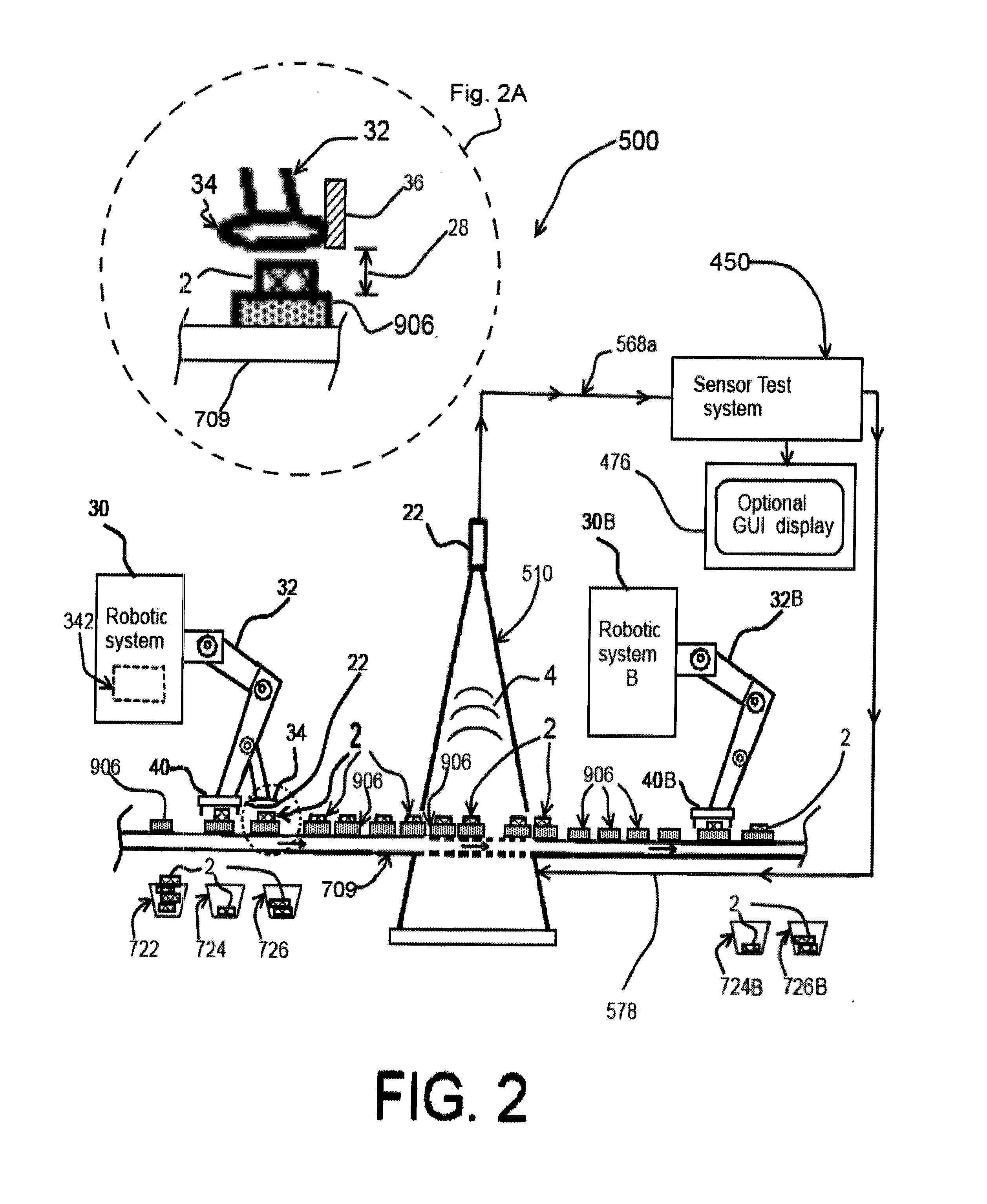
An apparatus for testing, inspecting or screening an electrically powered device for modified or unmodified hardware, firmware or software modifications including Malware, Trojans, adware, improper versioning, worms, or virus and the like, includes an antenna positioned at a distance from the electrically powered device and a signal receiver or sensor for examining a signal from the electrically powered device. The receiver or sensor collects unintended RF energy components emitted by the electrically powered device and includes one or more processors and executable instructions that perform analysis in a response to the acquired signal input while the electrically powered device is active or powered. The characteristics of the collected RF energy may be compared with RF energy characteristics of an unmodified device. The comparison determines one of a modified, unmodified or score of certainty of modified condition of the electrically powered device.
Owner:NOKOMIS
Storage-and transport-independent collaborative document-management system
ActiveUS20060136511A1Digital data processing detailsNatural language data processingUnique identifierPaper document
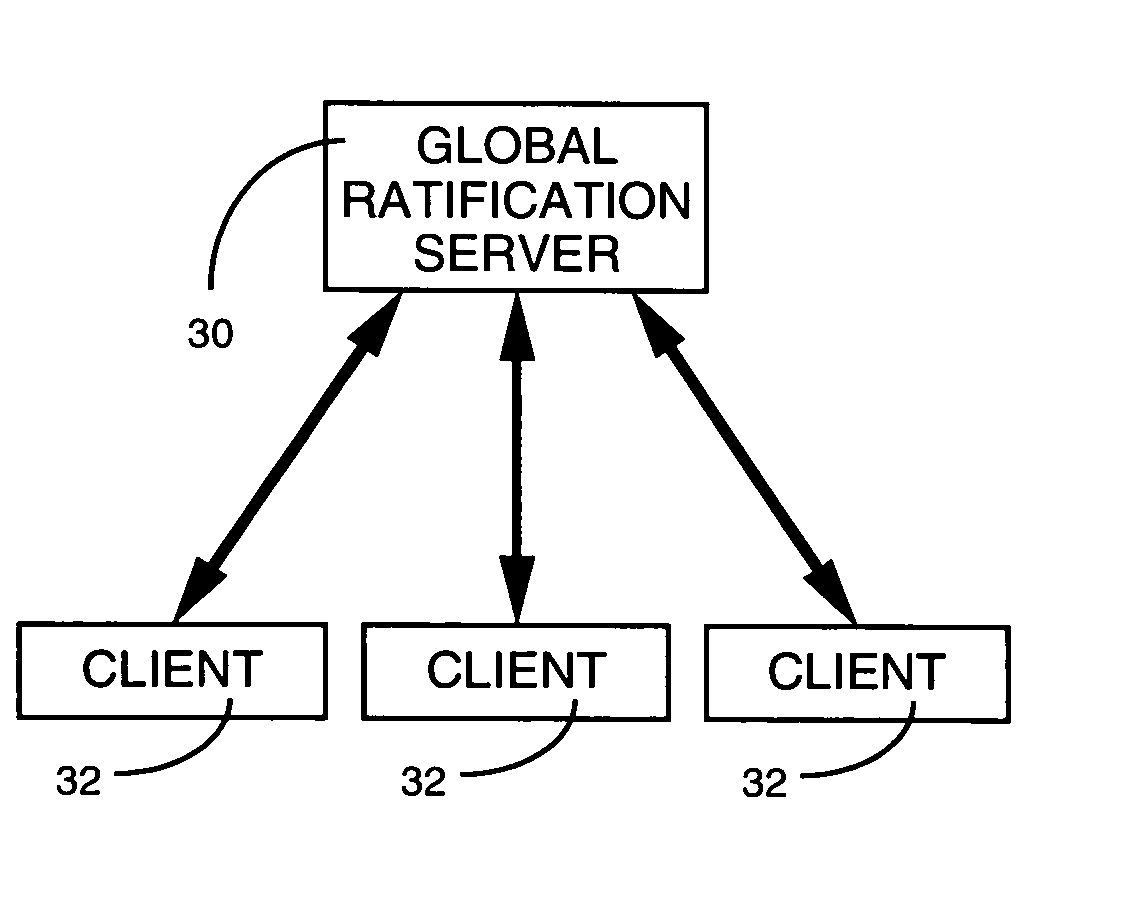
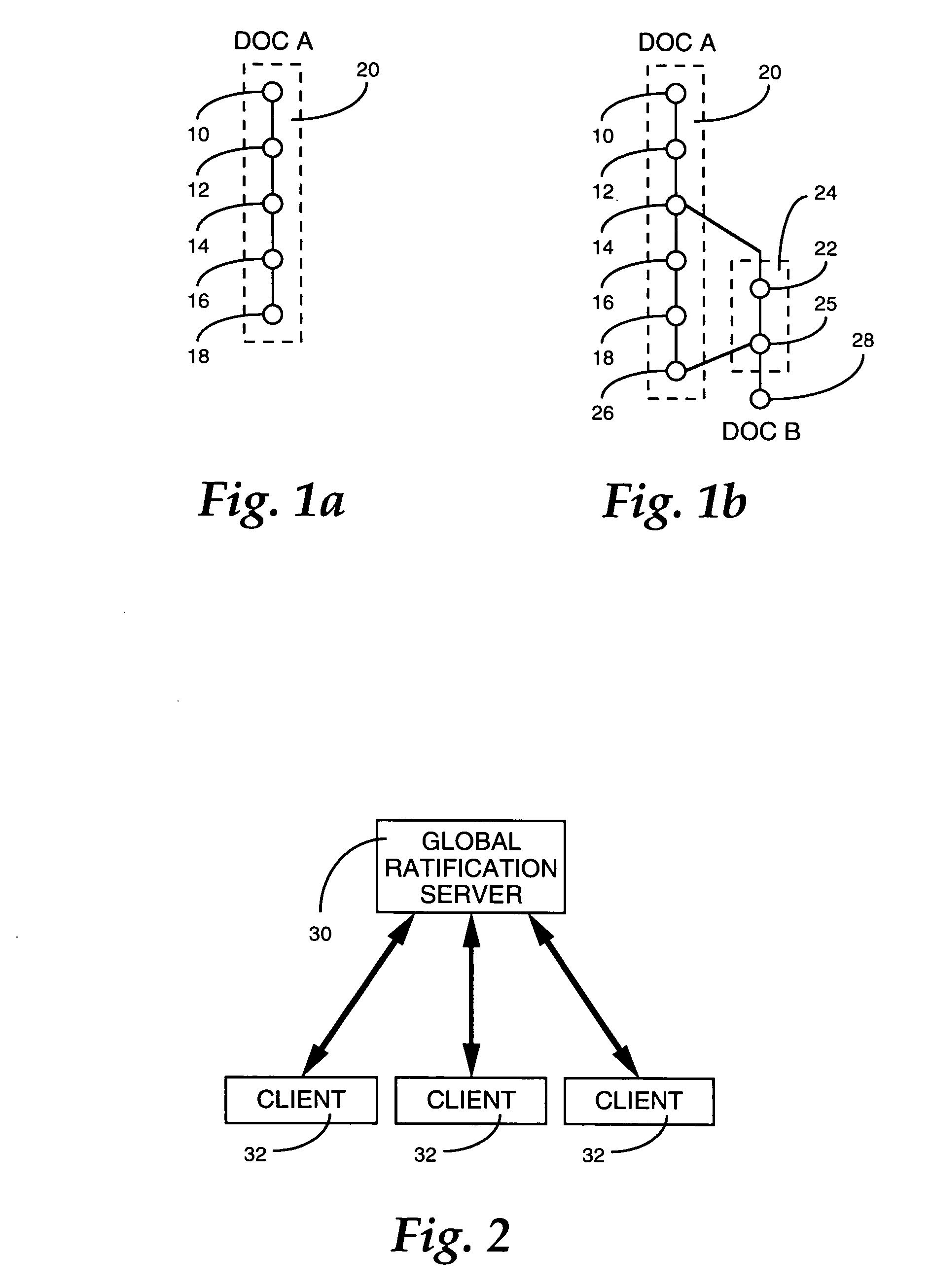
A document management system enables multiple users to collaboratively contribute to the contents of a document via any suitable medium for transporting and storing documents, including email, shared drives, replicated work spaces and centralized storage systems. A tracking strategy is employed, in lieu of a central repository, that is based upon medium-independent versioning. Each version of a document that is created and saved by a user is given a unique identifier. The versions are submitted to a global service for ratification as the next authoritative version of a document. A submitted version that forms the next step in a linear sequence is ratified as the authoritative version of the document, whereas the version which does not meet this criterion becomes identified as a new document. Support is provided for users who create versions off-line, as well as users who are not subscribers to the system.
Owner:PROOFPOINT INC
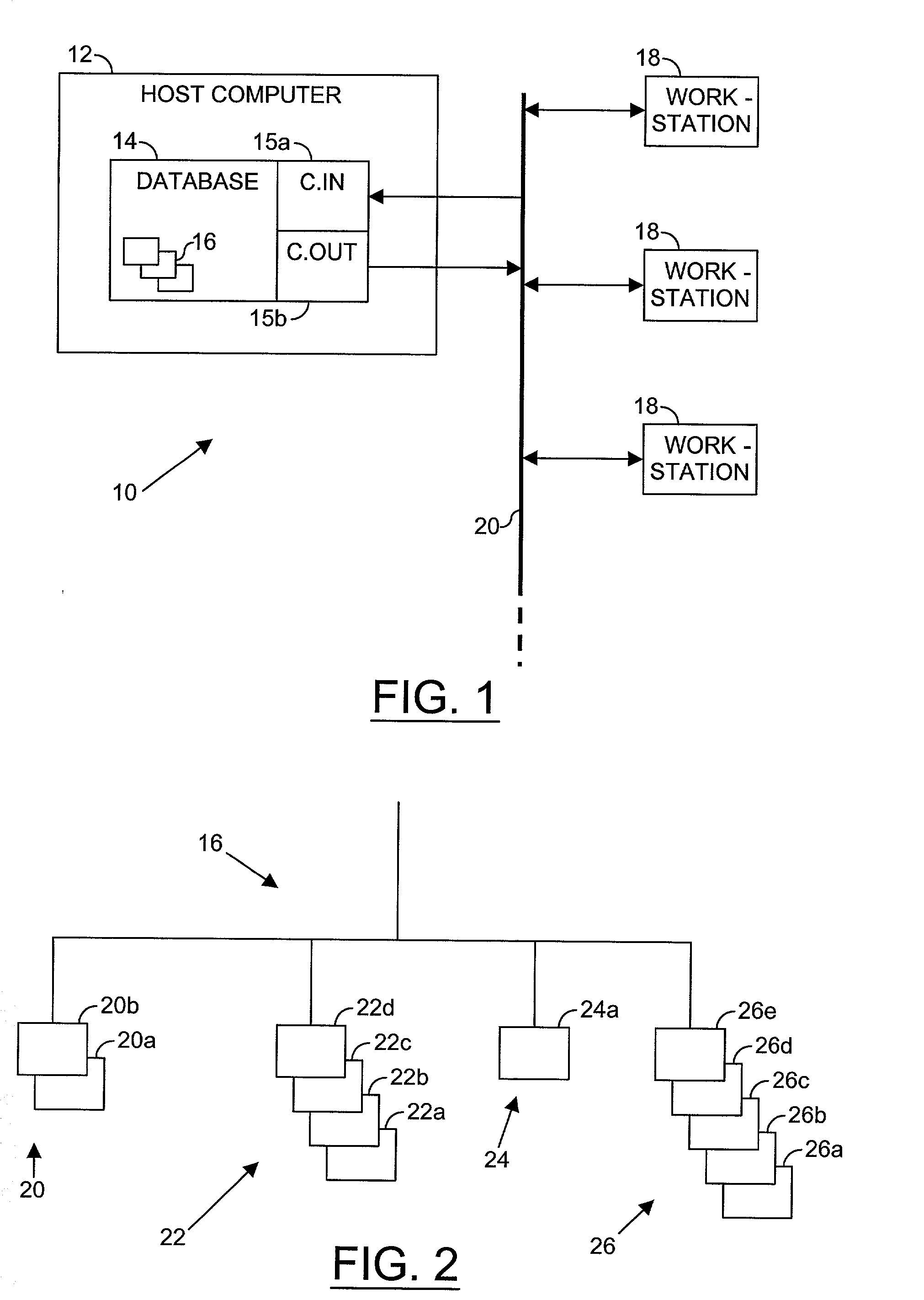
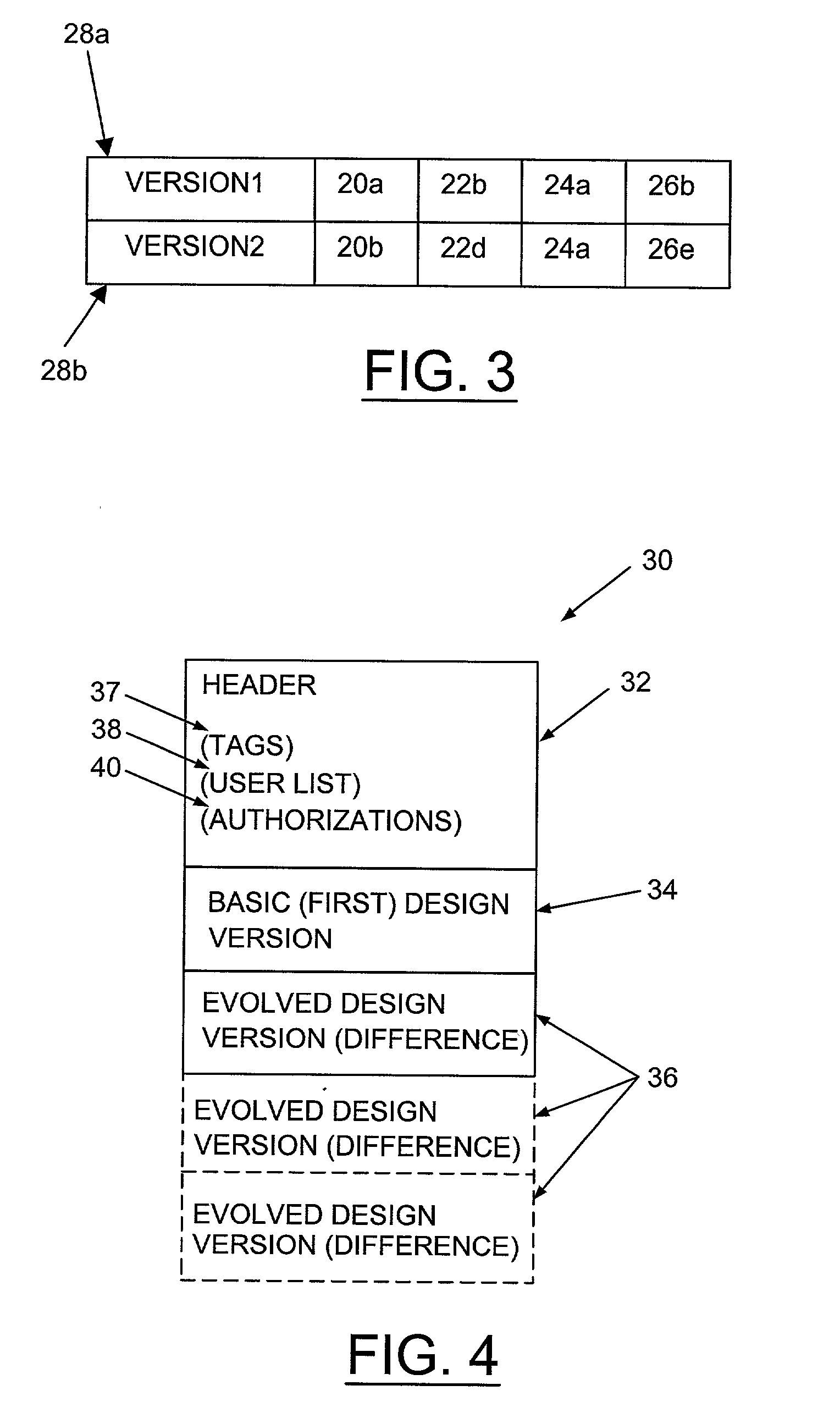
Revision control for database of evolved design
InactiveUS20030212718A1Data processing applicationsComputer security arrangementsAuthorizationDatabase
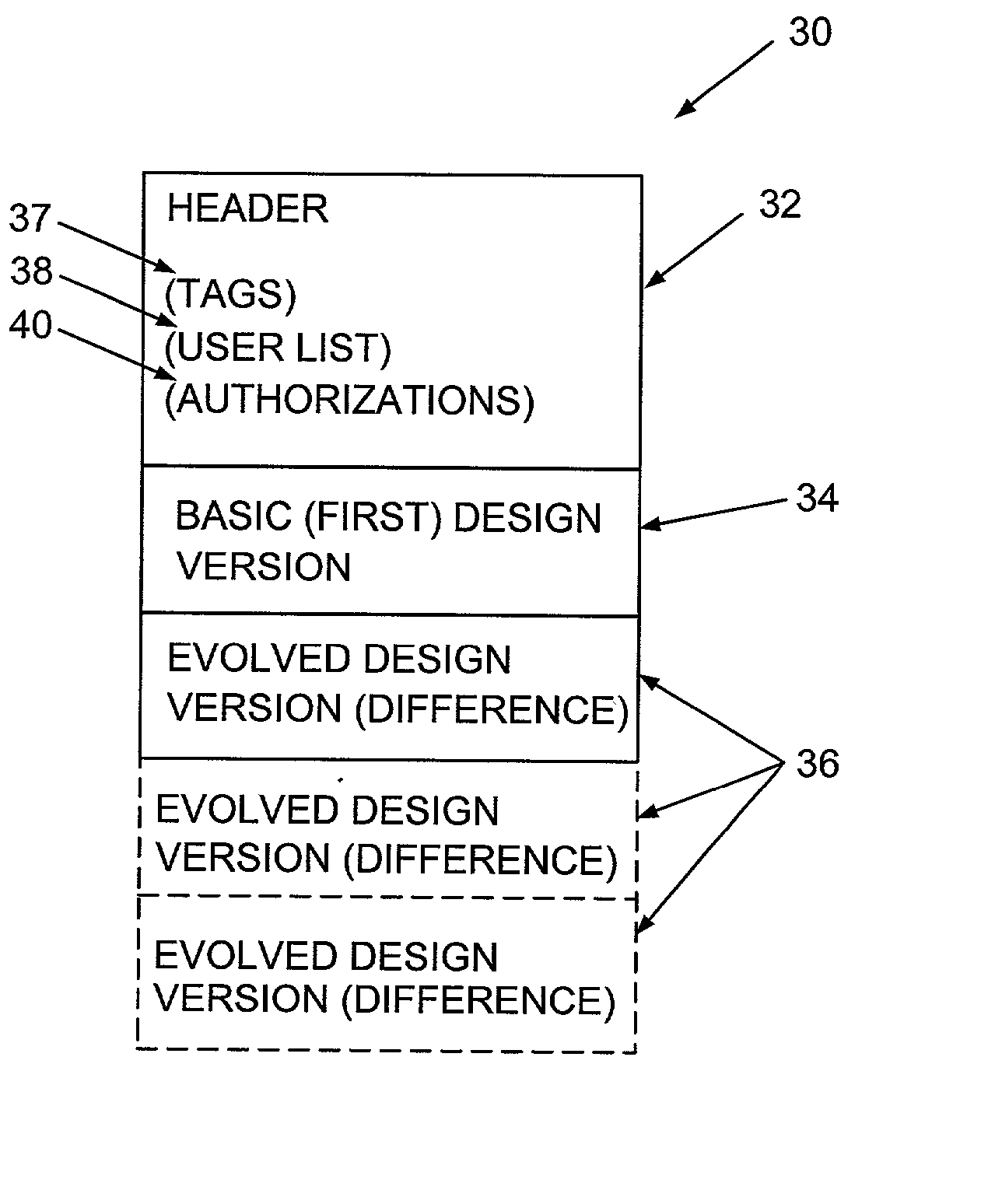
The invention relates to a method of controlling access to a database of a design. The method may comprise the step of identifying a version of the design by a first identifier, allocating first authorization information to the first identifier, and controlling access to the database. The first authorization information may indicate a permission of one or more users to access information in the database in respect of the first identifier. The access may be controlled in accordance with the first authorization information.
Owner:BELL SEMICON LLC
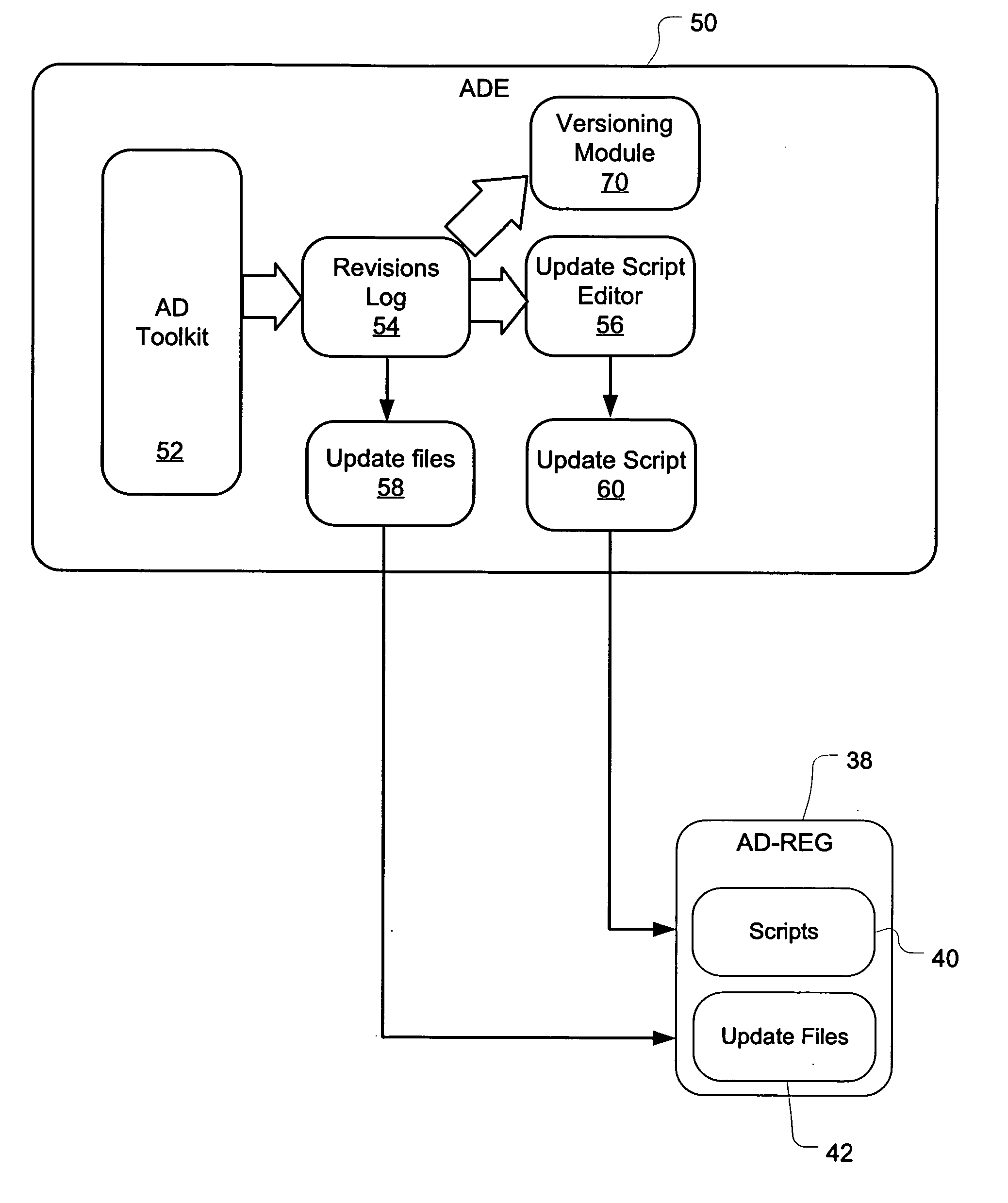
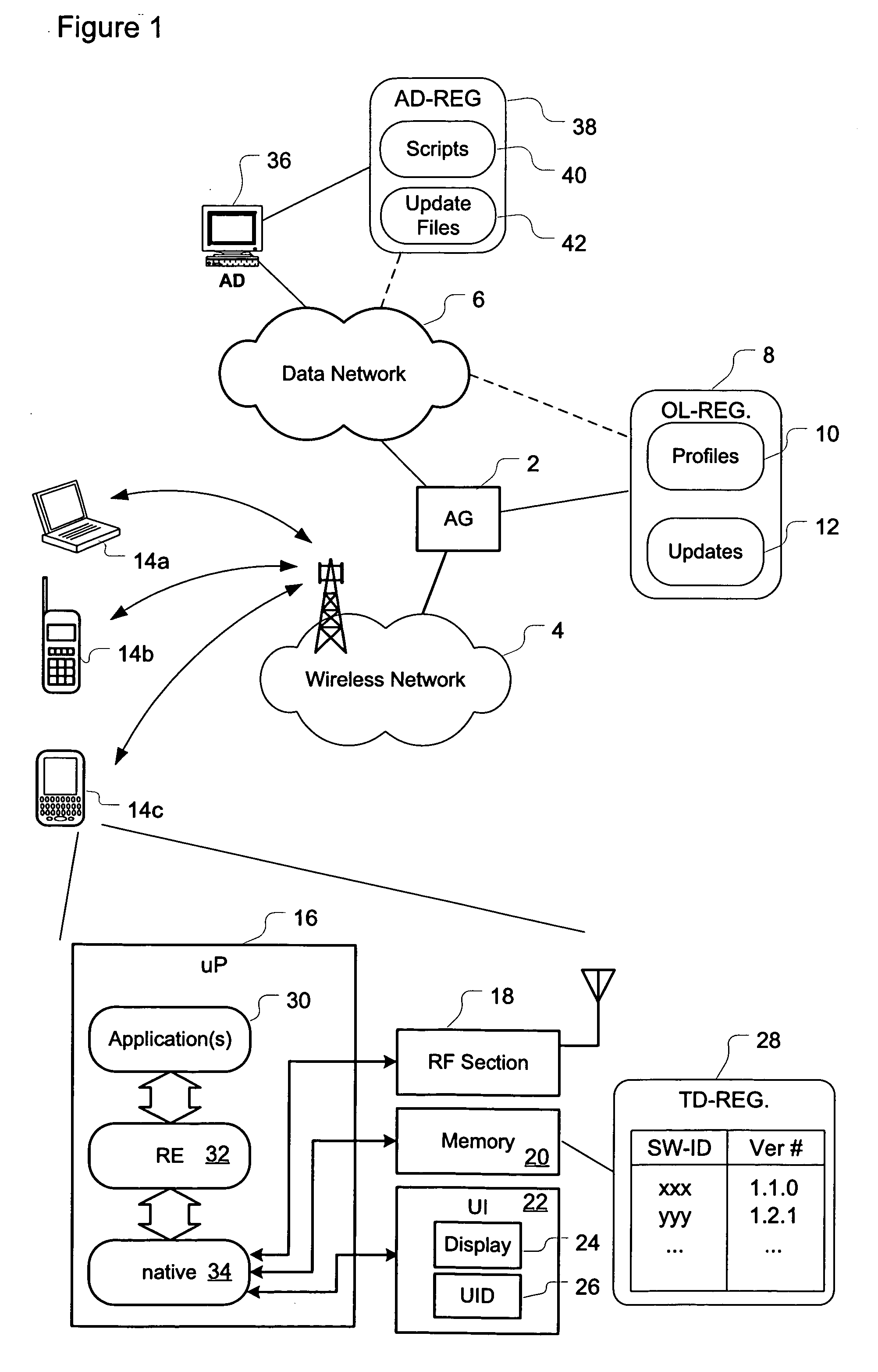
Method and system for controlling software version updates
ActiveUS20060236083A1Restricts distributionDigital computer detailsTransmissionSoftware updateSoftware engineering
Methods and systems are provided for controlling asynchronous distribution and installation of software updates affecting applications installed on terminal devices of a wireless network. A versioning schema enforced by the application development environment enables the runtime environment of a terminal device to evaluate a software update to identify potential compatibility issues and control installation of the update.
Owner:MALIKIE INNOVATIONS LTD
Automated Publishing System That Facilitates Collaborative Editing And Accountability Through Virtual Document Architecture
ActiveUS20080028300A1Decrease to publicationAvoid excessive errorDigital data processing detailsDigital computer detailsDocumentation procedureDocument preparation
The present invention automates the publishing of financial, legal, and governmental documents and any other publications that are structured and require compliance with corporate or external standards and may share content elements. It gives users control in an always-on, familiar environment: the Internet. Due to its virtual document architecture and ability to operate over the Internet and intranets, the system facilitates collaborative work and traces accountability. The key concept behind automating publishing is to control scheduling and costs by better content management. The present invention handles document content as small, reusable components, down to the paragraph and table cell level. The interface helps users assemble documents from these version-controlled components with automated support. The system applies context and filtering criteria stored with each component to locate and apply content fragments to a current document. The system of the present invention can apply structural rules and content requirements to ensure compliance with regulatory requirements and company business rules. A working virtual document within the system always incorporates the current version of all constituent elements.
Owner:US LYNX LLC
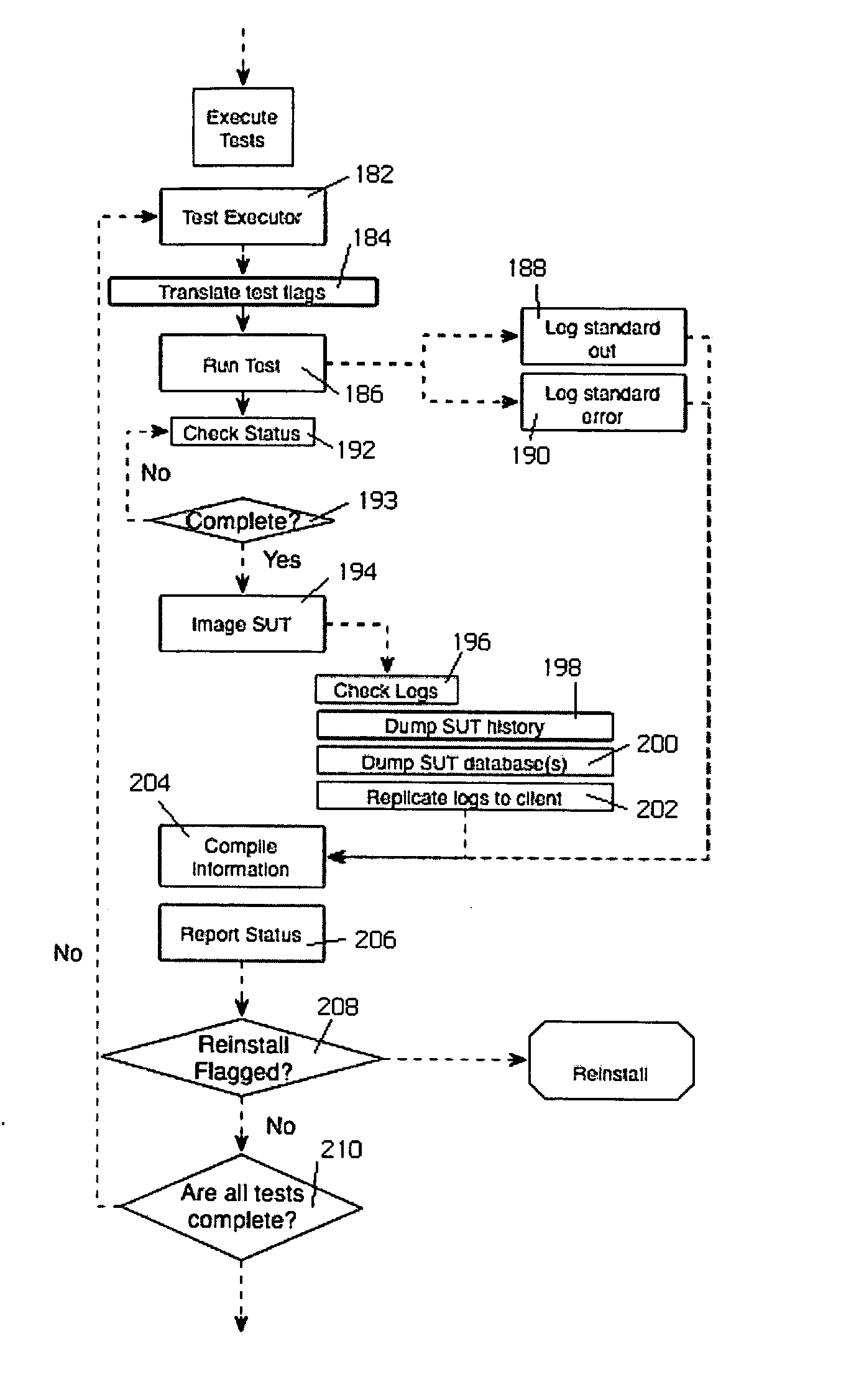
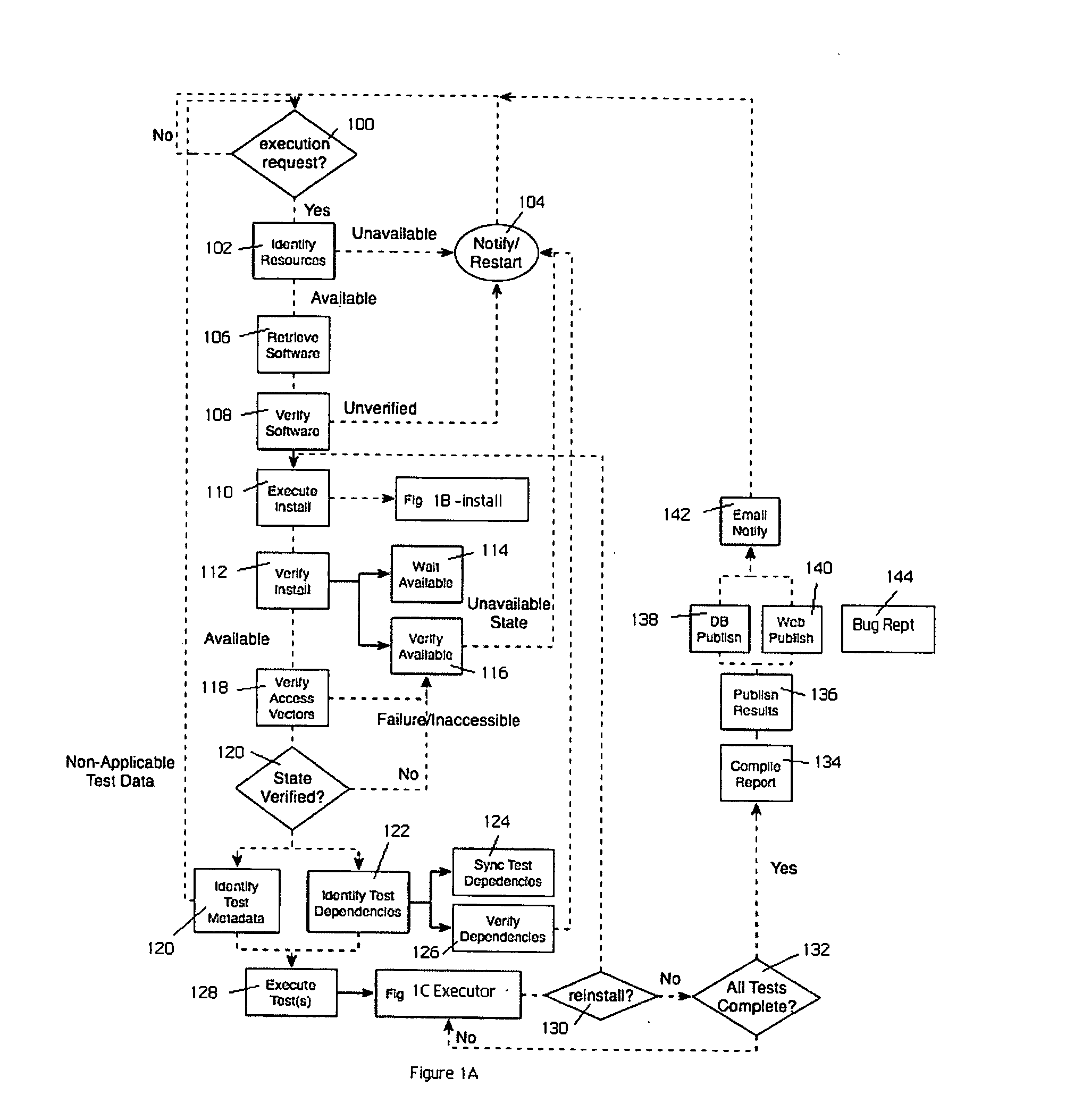
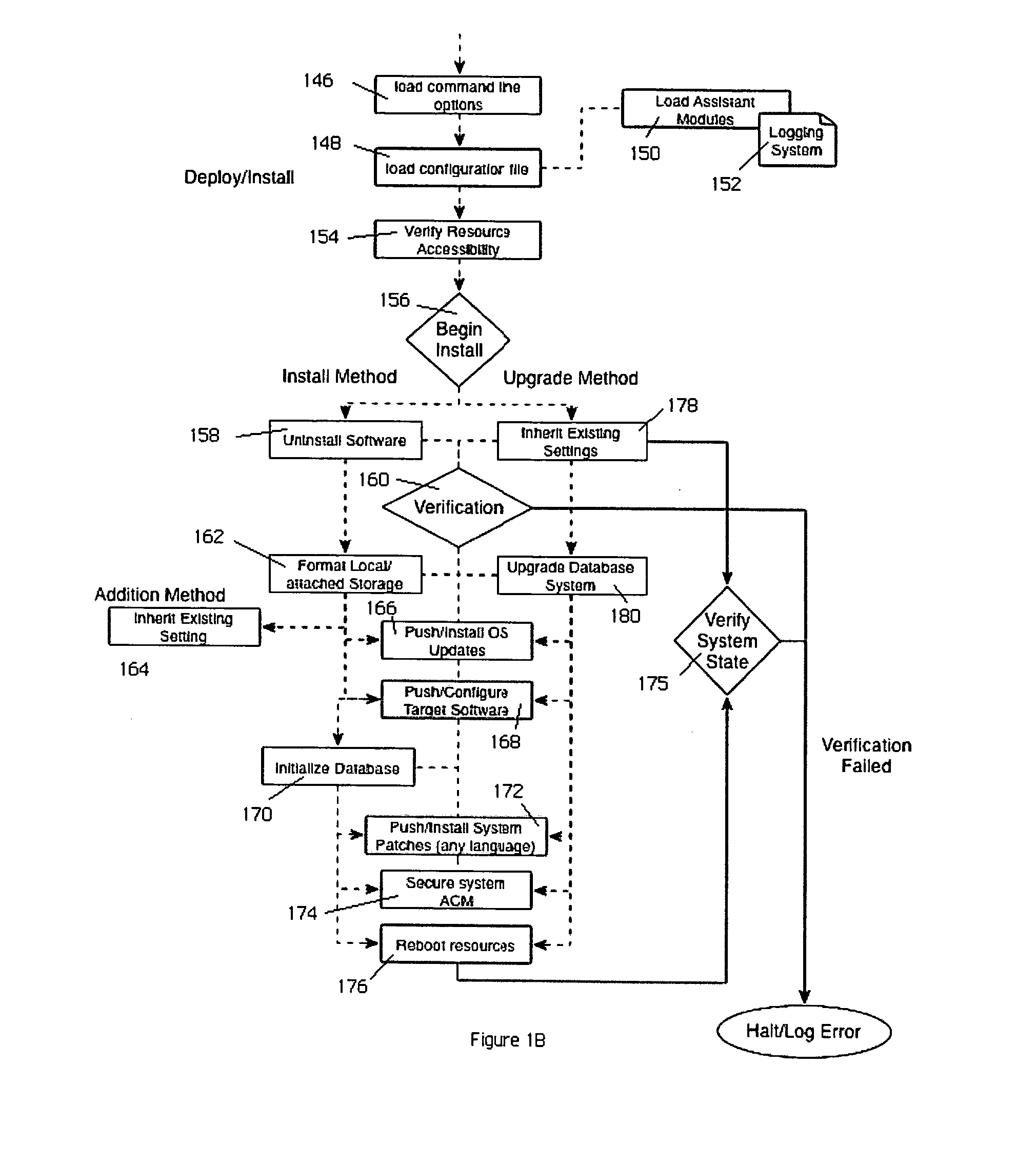
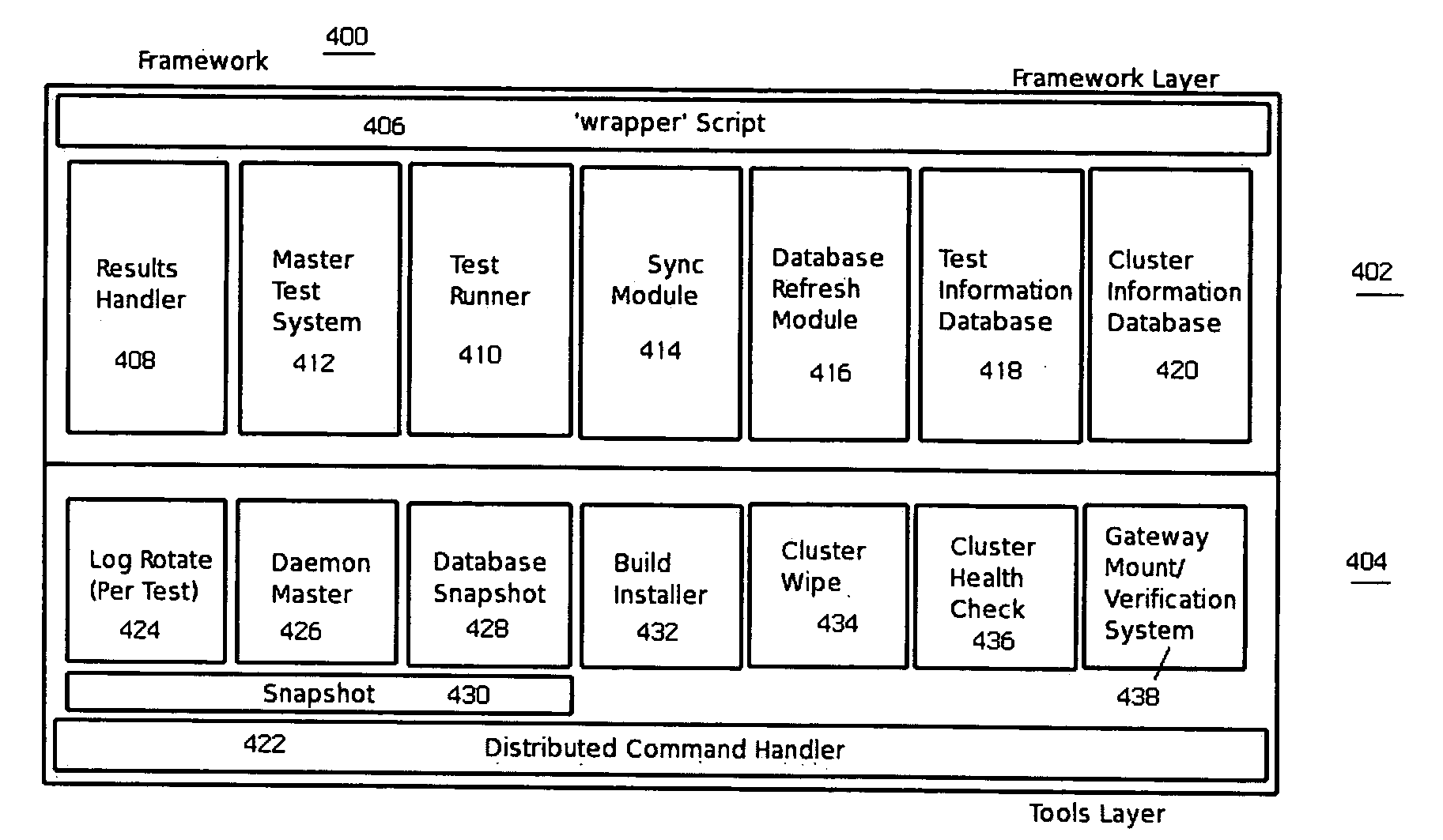
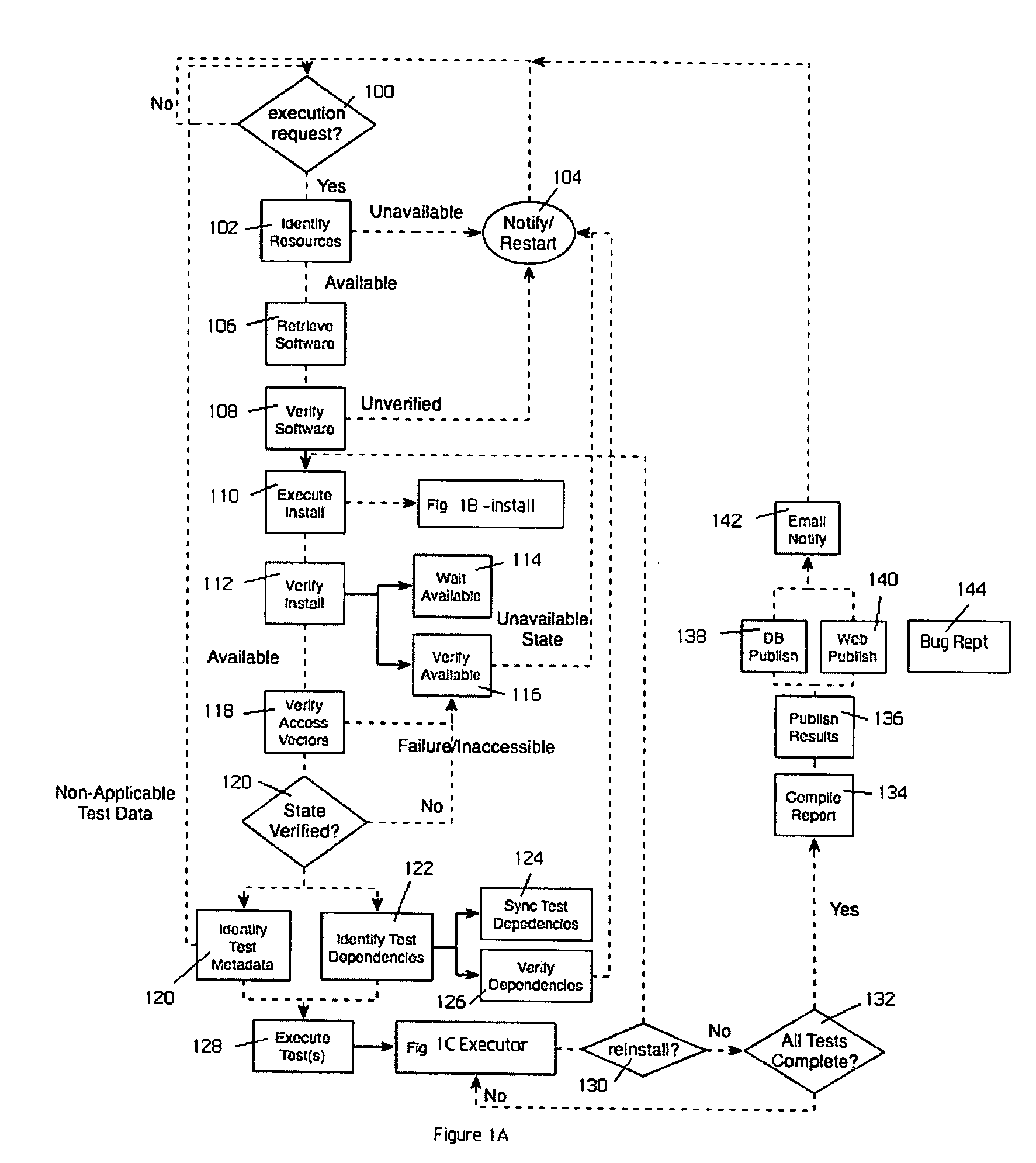
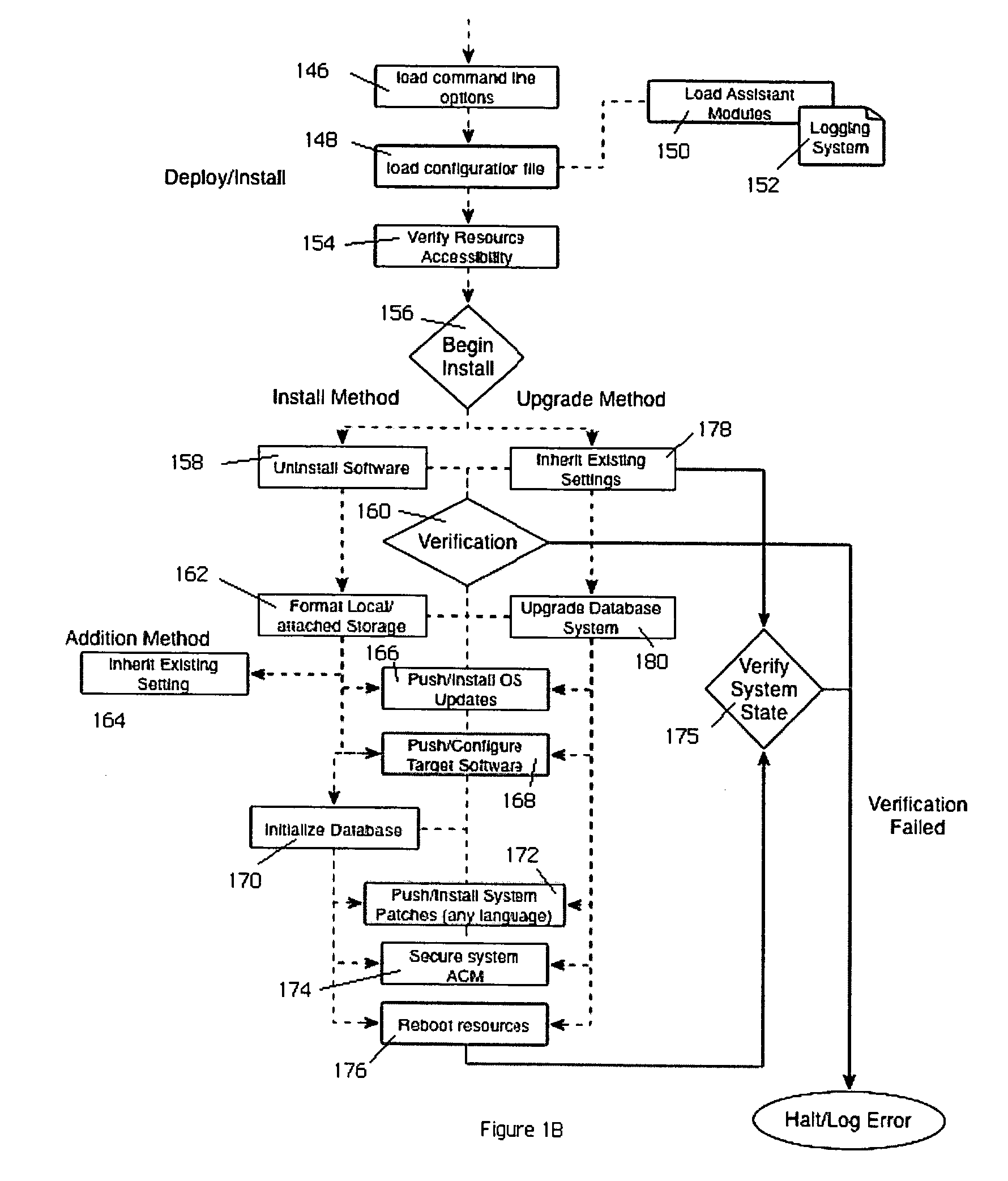
Automated software testing framework
InactiveUS20070234293A1Improve scalabilitySimple and efficientError detection/correctionSpecific program execution arrangementsSpecific testWeb service
A generic testing framework to automatically allocate, install and verify a given version of a system under test, to exercise the system against a series of tests in a “hands-off” objective manner, and then to export information about the tests to one or more developer repositories (such as a query-able database, an email list, a developer web server, a source code version control system, a defect tracking system, or the like). The framework does not “care” or concern itself with the particular implementation language of the test as long as the test can issue directives via a command line or configuration file. During the automated testing of a given test suite having multiple tests, and after a particular test is run, the framework preferably generates an “image” of the system under test and makes that information available to developers, even while additional tests in the suite are being carried out. In this manner, the framework preserves the system “state” to facilitate concurrent or after-the-fact debugging. The framework also will re-install and verify a given version of the system between tests, which may be necessary in the event a given test is destructive or otherwise places the system in an unacceptable condition.
Owner:HITACHI DATA SYST CORP
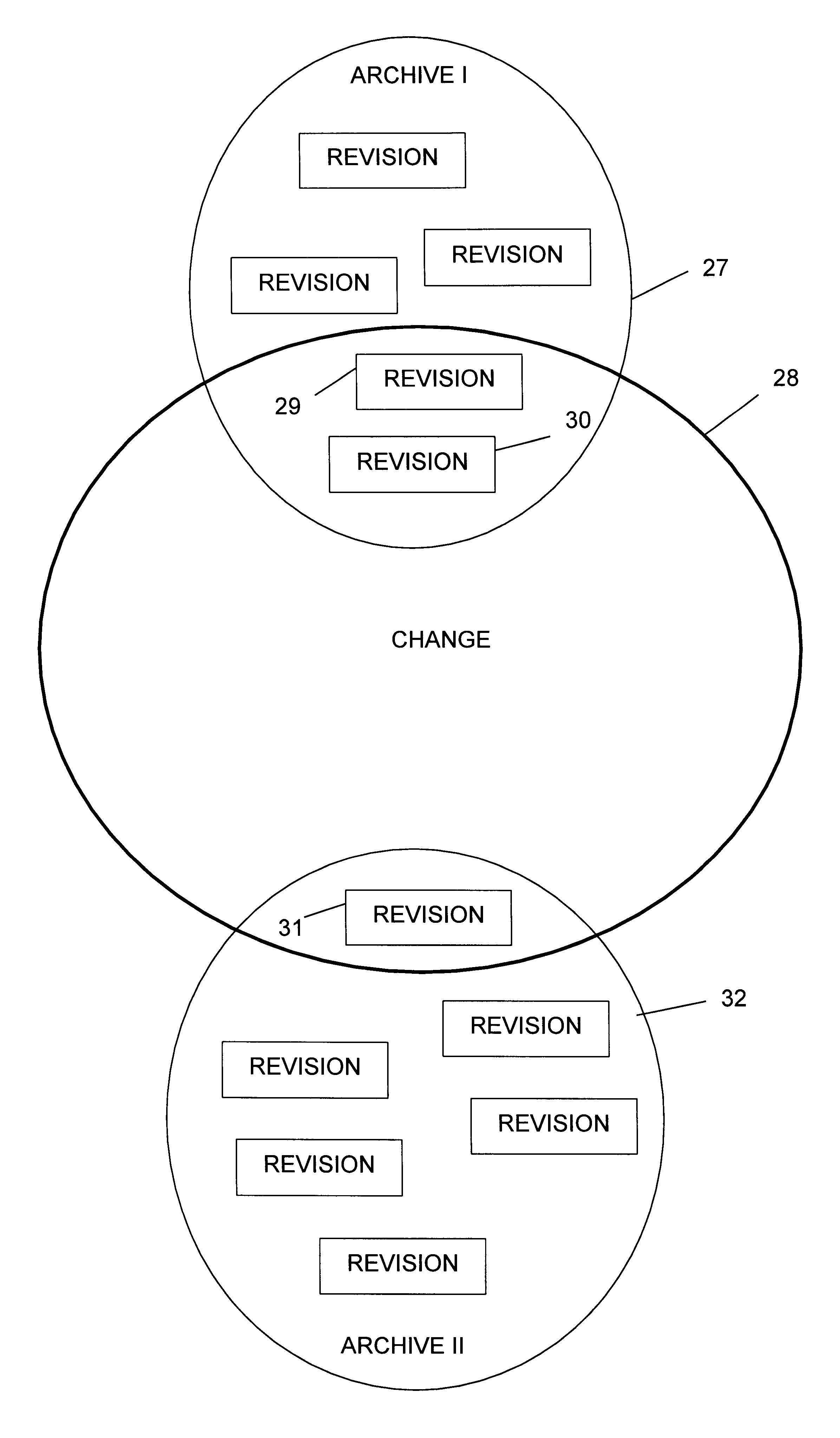
System and method for incorporating changes as a part of a software release
InactiveUS6385768B1Save storage spaceEliminate needData processing applicationsVersion controlComputerized systemDatabase
Disclosed is a method in a computer system capable of executing a version control program, wherein the method operates within the version control program for incorporating changes to software releases. The method creates a project archive object that manages all resources for each of the software releases and then creates a branch in the project archive object in order to establish a new project revision object of the project archive objects. Next, a project revision object is established and is disposed on the branch for incorporating a revision of the project archive object. After this, archive objects are added to the project revision object and revisions are received from a user to each of the archive objects. A change object is established for the project revision, which logically groups a set of revisions to be released. A stream is then created from the project revision object in order to establish a new project revision object of the project archive object, thereby establishing the new project revision object as a software release object. The software release object is then disposed on the stream for incorporating a revision of the project archive object. Finally, the change object is applied to the software release object after it is determined that a change is ready for release.
Owner:UNISYS CORP
Querying, versioning, and dynamic deployment of database objects
InactiveUS7421458B1Save storage spaceEliminate needData processing applicationsObject oriented databasesData warehouseDatabase object
In various embodiments, the present invention provides methods and systems for creating version-stamps of database objects and for tracking, querying, retrieving, and deploying such versioned database objects in enterprise databases, data marts, or data warehouses. The database objects may be interrelated and may reference one another according to their accurate versions.
Owner:INFORMATICA CORP
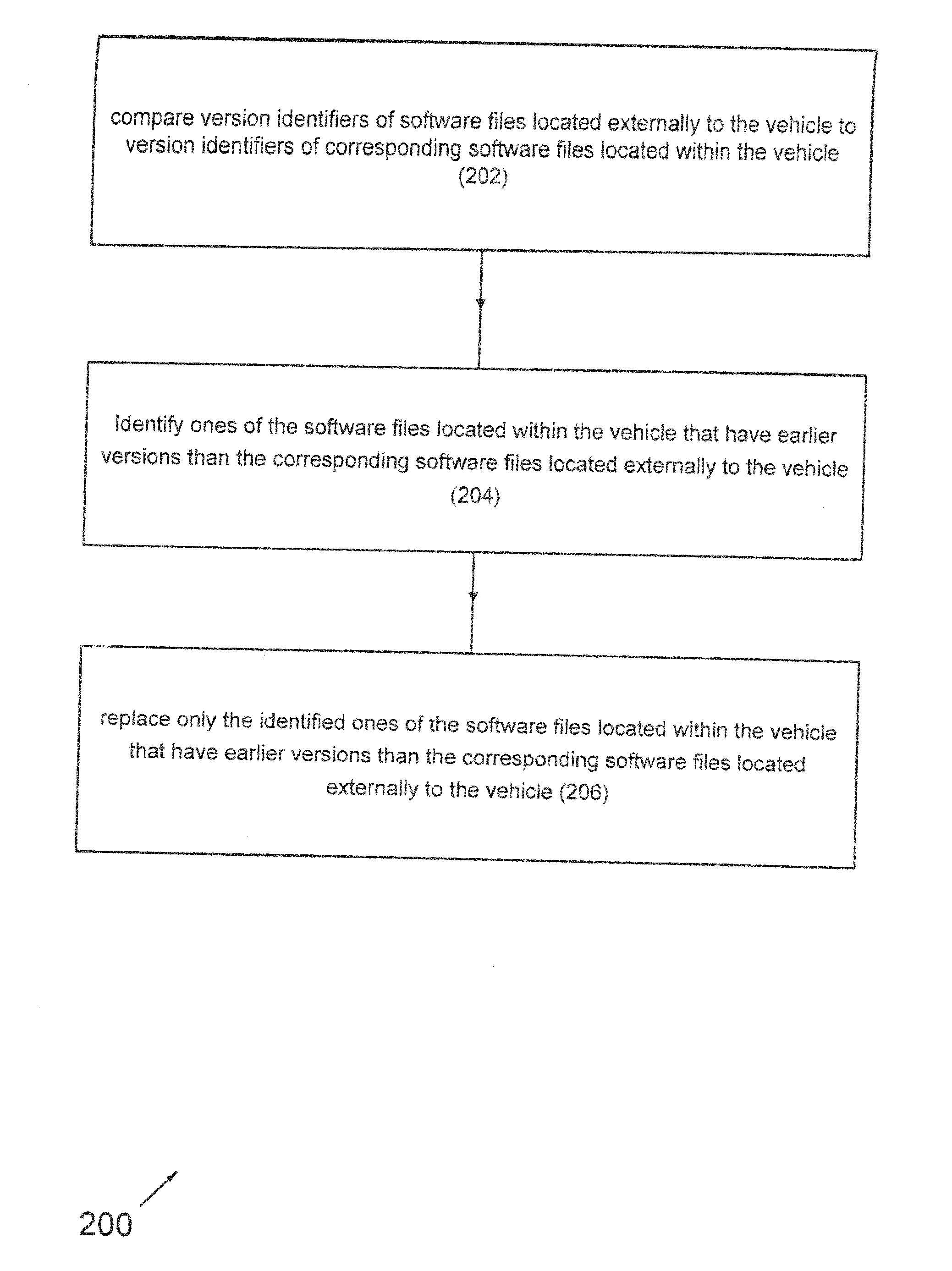
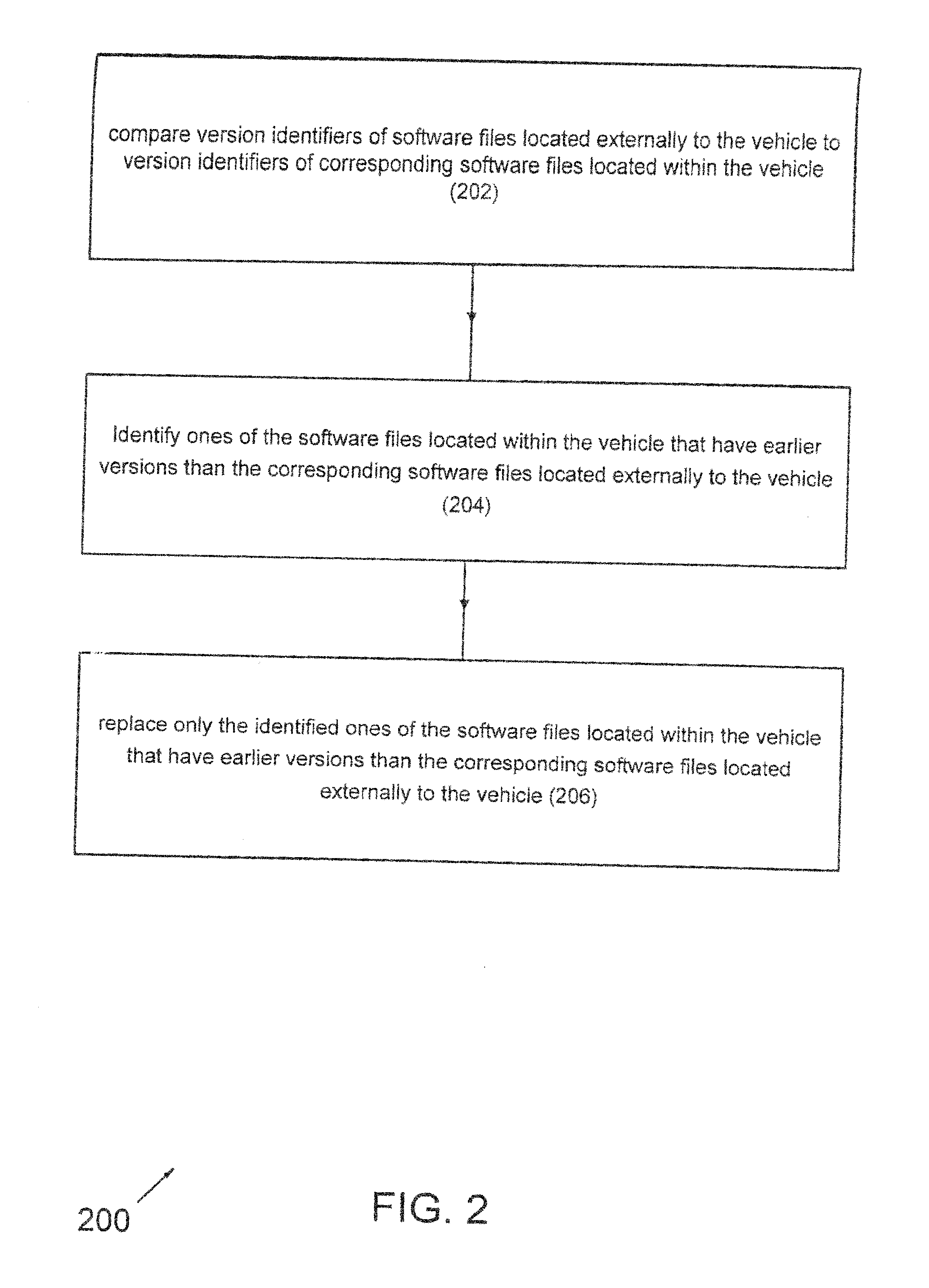
Automotive component self update via software version control
InactiveUS20140245278A1Reduces necessary sizeReduce wearVersion controlProgram loading/initiatingMobile vehicleSoftware engineering
A method of updating software files in a motor vehicle includes comparing version identifiers of software files located externally to the vehicle to version identifiers of corresponding software files located within the vehicle. Ones of the software files located within the vehicle that have earlier versions than the corresponding software files located externally to the vehicle are identified. Only the identified ones of the software files located within the vehicle that have earlier versions than the corresponding software files located externally to the vehicle are replaced. The identified ones of the software files located within the vehicle are replaced with the corresponding software files located externally to the vehicle.
Owner:PANASONIC AUTOMOTIVE SYST OF AMERICA
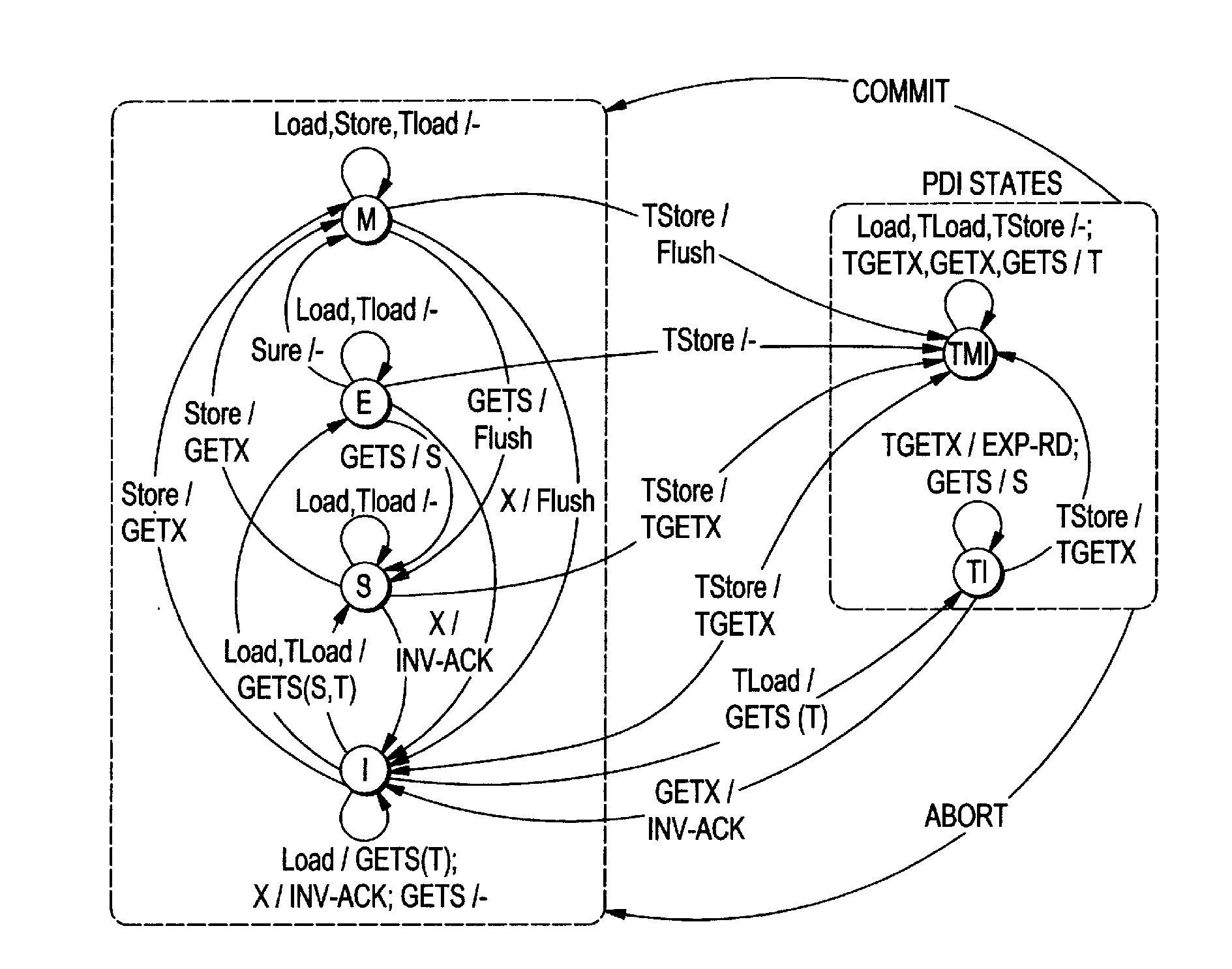
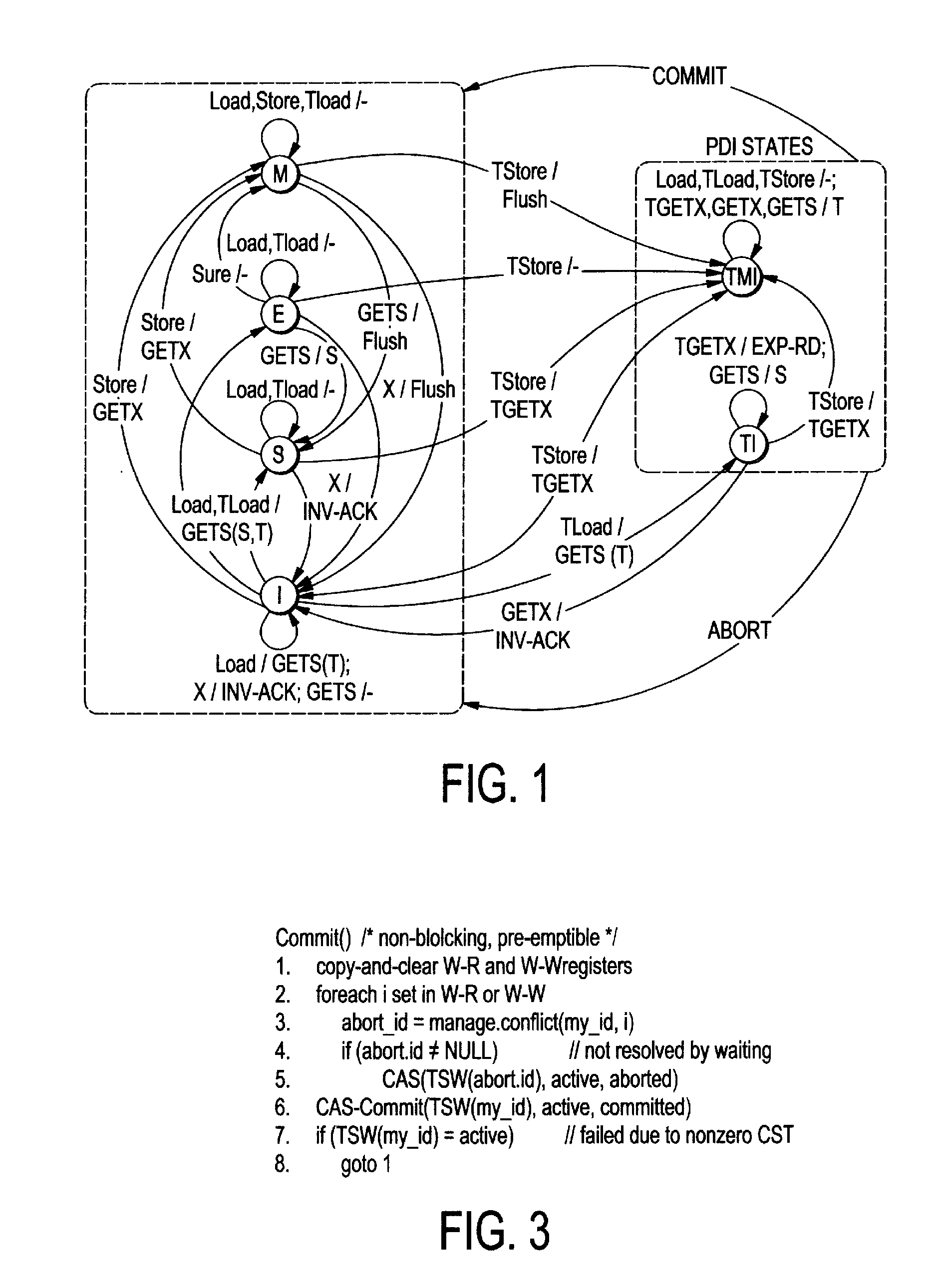
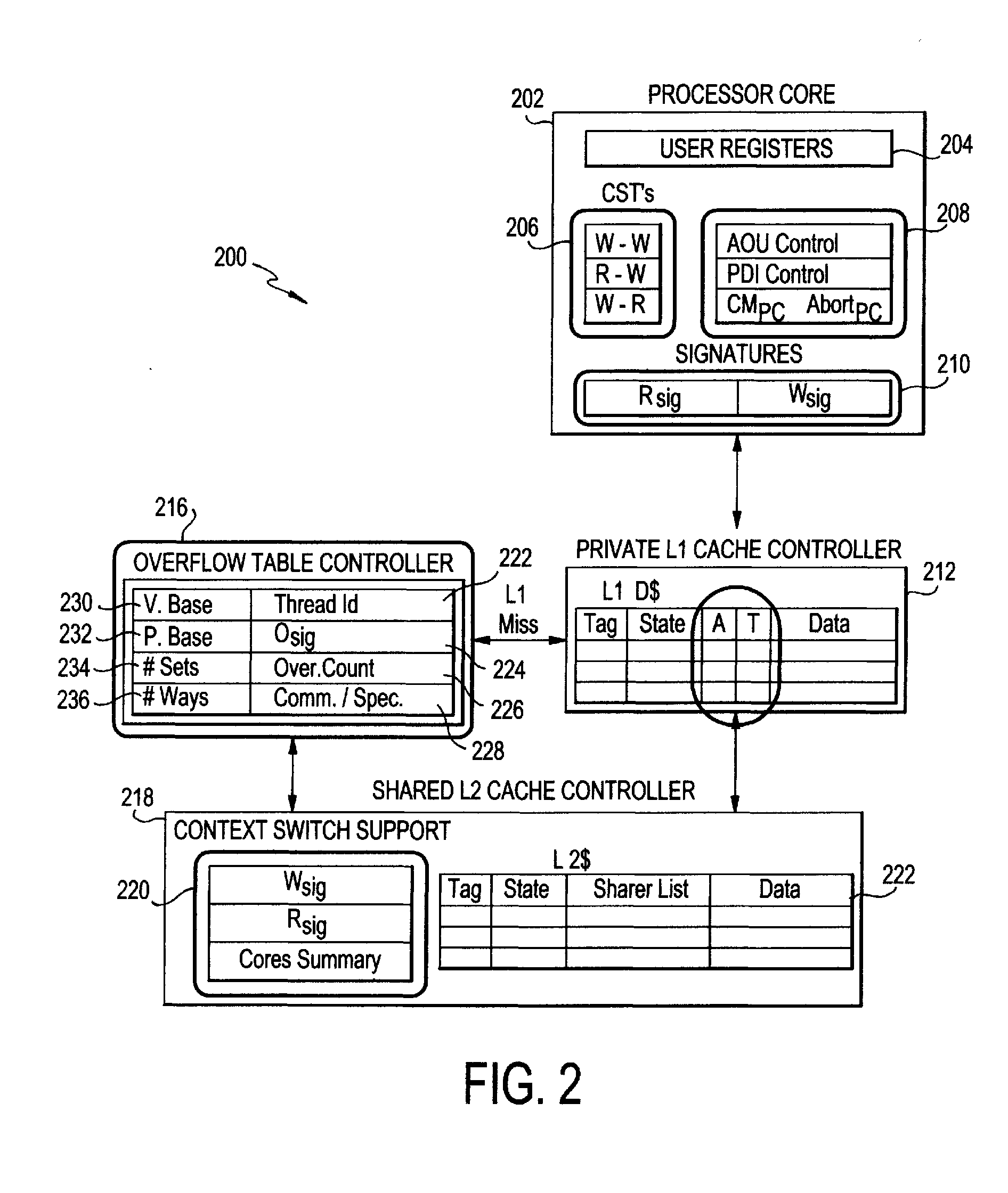
Mechanism to support flexible decoupled transactional memory
ActiveUS20120179877A1Maximize concurrencyEncourages forward progressMemory adressing/allocation/relocationProgram controlVirtual memoryVirtualization
The present invention employs three decoupled hardware mechanisms: read and write signatures, which summarize per-thread access sets; per-thread conflict summary tables, which identify the threads with which conflicts have occurred; and a lazy versioning mechanism, which maintains the speculative updates in the local cache and employs a thread-private buffer (in virtual memory) only in the rare event of an overflow. The conflict summary tables allow lazy conflict management to occur locally, with no global arbitration (they also support eager management). All three mechanisms are kept software-accessible, to enable virtualization and to support transactions of arbitrary length.
Owner:UNIV OF ROCHESTER OFFICE OF TECH TRANSFER
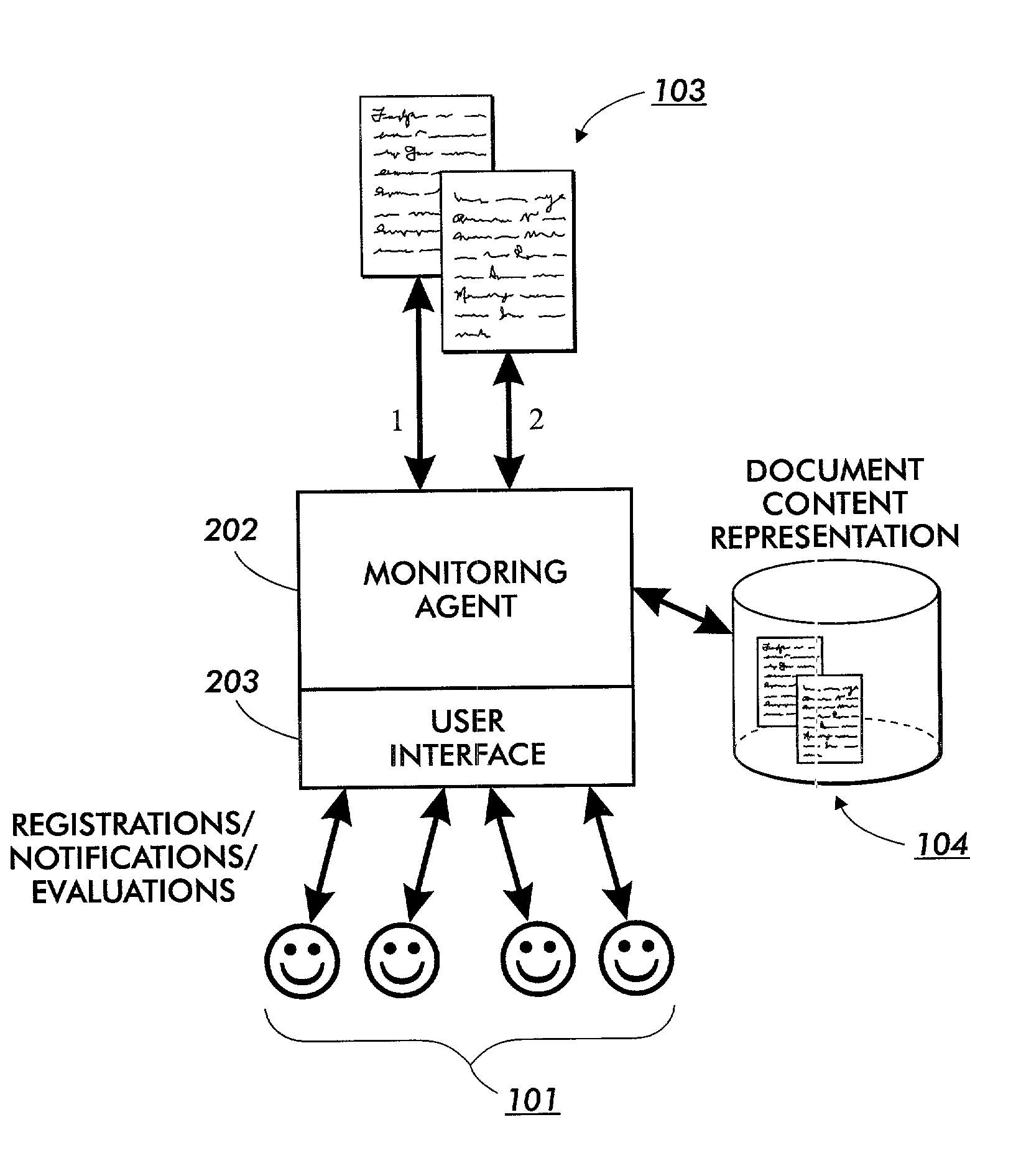
Method and apparatus for collaborative document versioning of networked documents
ActiveUS7174377B2Multiple digital computer combinationsOffice automationDocumentation procedureUniform resource locator
The system comprises an improved document monitoring agent in which user evaluations are used to decide whether a changed document should be saved in the system or not. The evaluation of importance of the change in a document is performed by one or more users who collaboratively monitor a networked document, typically identified by a URL. By providing a user evaluation interface, it is possible for users to indicate their evaluation of the significance of the change. As such, only significantly changed documents, as indicated by the users themselves, are saved. Thus, a more efficient saving is obtained while at the same time reducing the risk of discarding potentially interesting changed documents which would have been discarded by conventional monitoring agents.
Owner:XEROX CORP
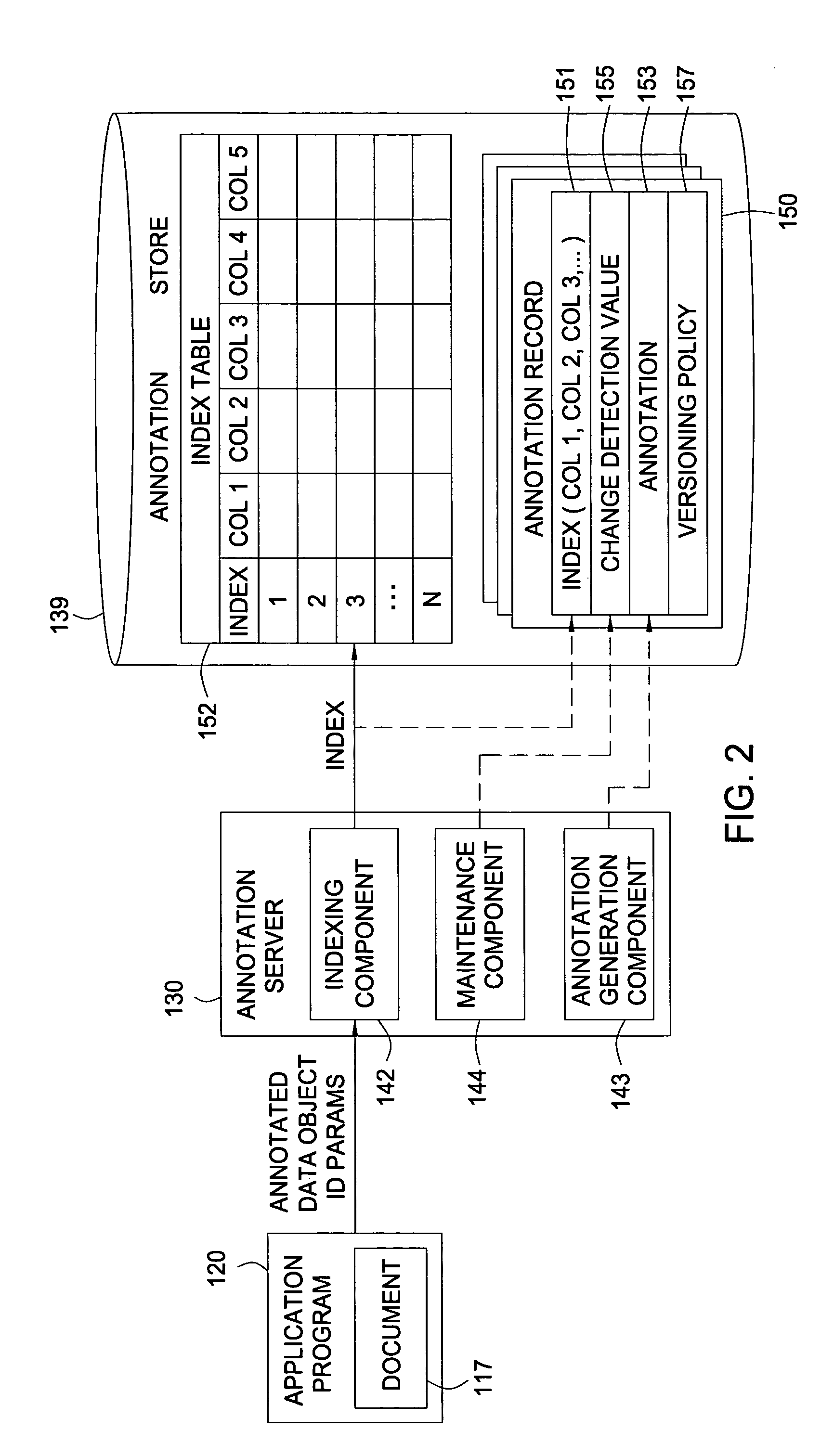
Dealing with annotation versioning through multiple versioning policies and management thereof
ActiveUS20050160356A1Natural language data processingSpecial data processing applicationsRevision controlAnnotation
Methods, systems, and articles of manufacture for maintaining annotations for changing source documents are provided. For some embodiments, an annotation system may support multiple policies, with each policy dictating how (or if) an annotation created for a version of a source document should be applied to subsequent versions of the source document. For some embodiments, a user creating an annotation may select from a group of available policies to be applied to the annotation.
Owner:TWITTER INC
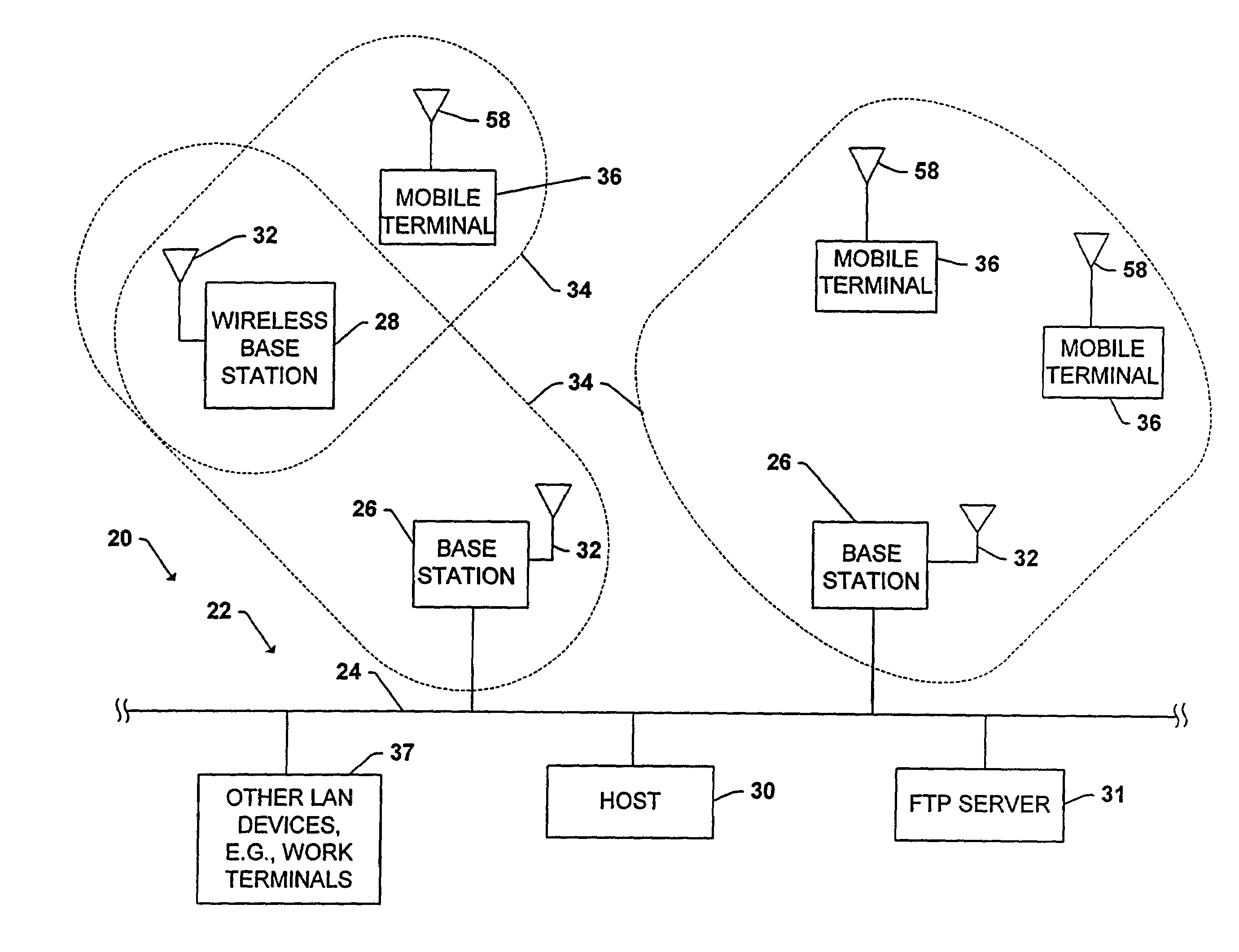
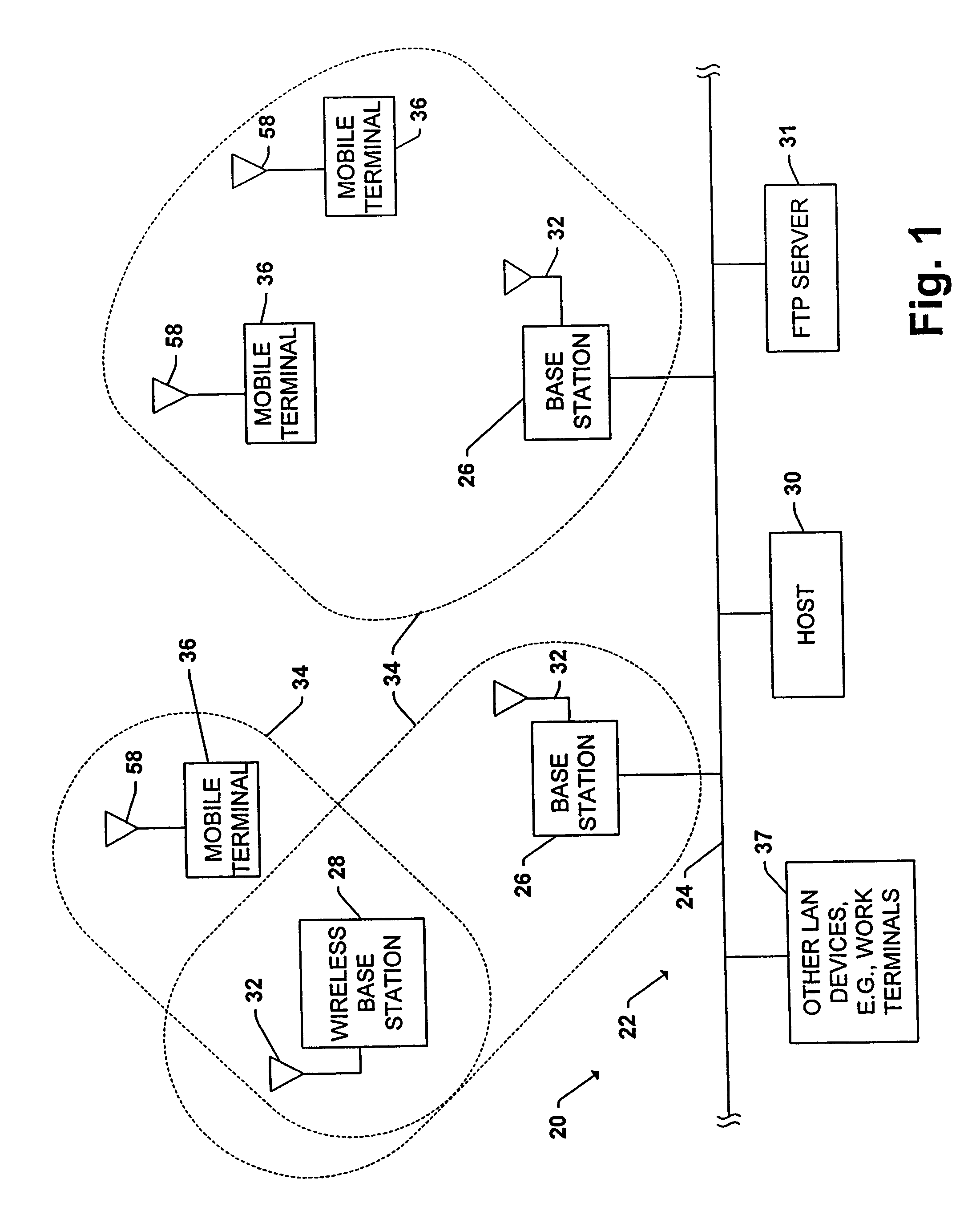
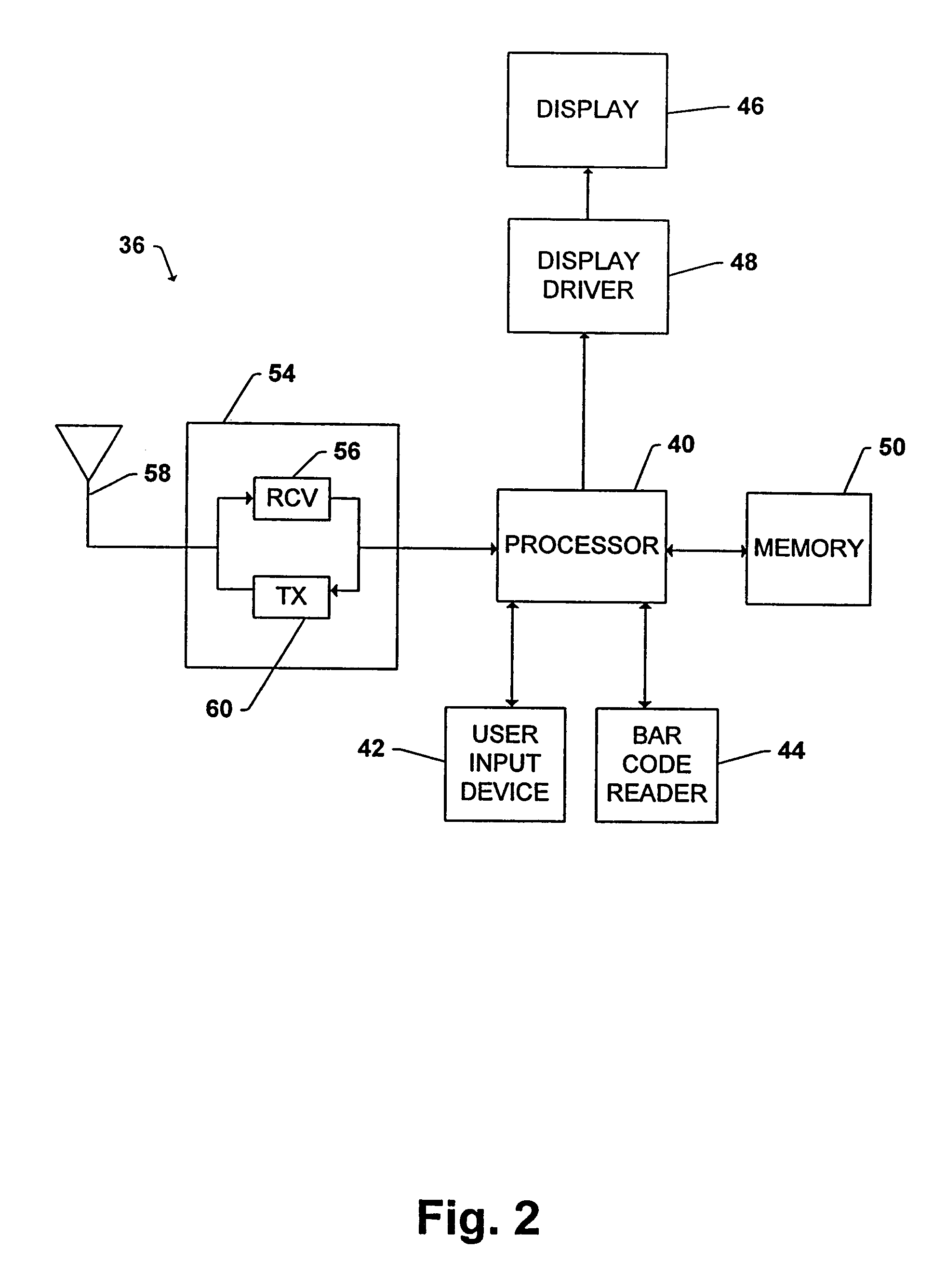
Wireless software upgrades with version control
InactiveUS6968184B2Distribute quicklyData switching by path configurationSubstation equipmentCommunications systemTransceiver
A wireless communication system includes a system backbone, a host computer coupled to the system backbone, at least one base station coupled to the system backbone, the at least one base station including a base station transceiver for communicating wirelessly with mobile devices within the system, and at least one mobile device having a mobile device transceiver for communicating wirelessly with the host computer on the system backbone via the at least one base station. A method of operation includes the steps determining whether a version of operating software stored in the at least one mobile device is a current version of the operating software, and wirelessly updating the operating software stored in the at least one mobile device if it is determined that the operating software stored in the at least one mobile device is not the current version.
Owner:TELXON
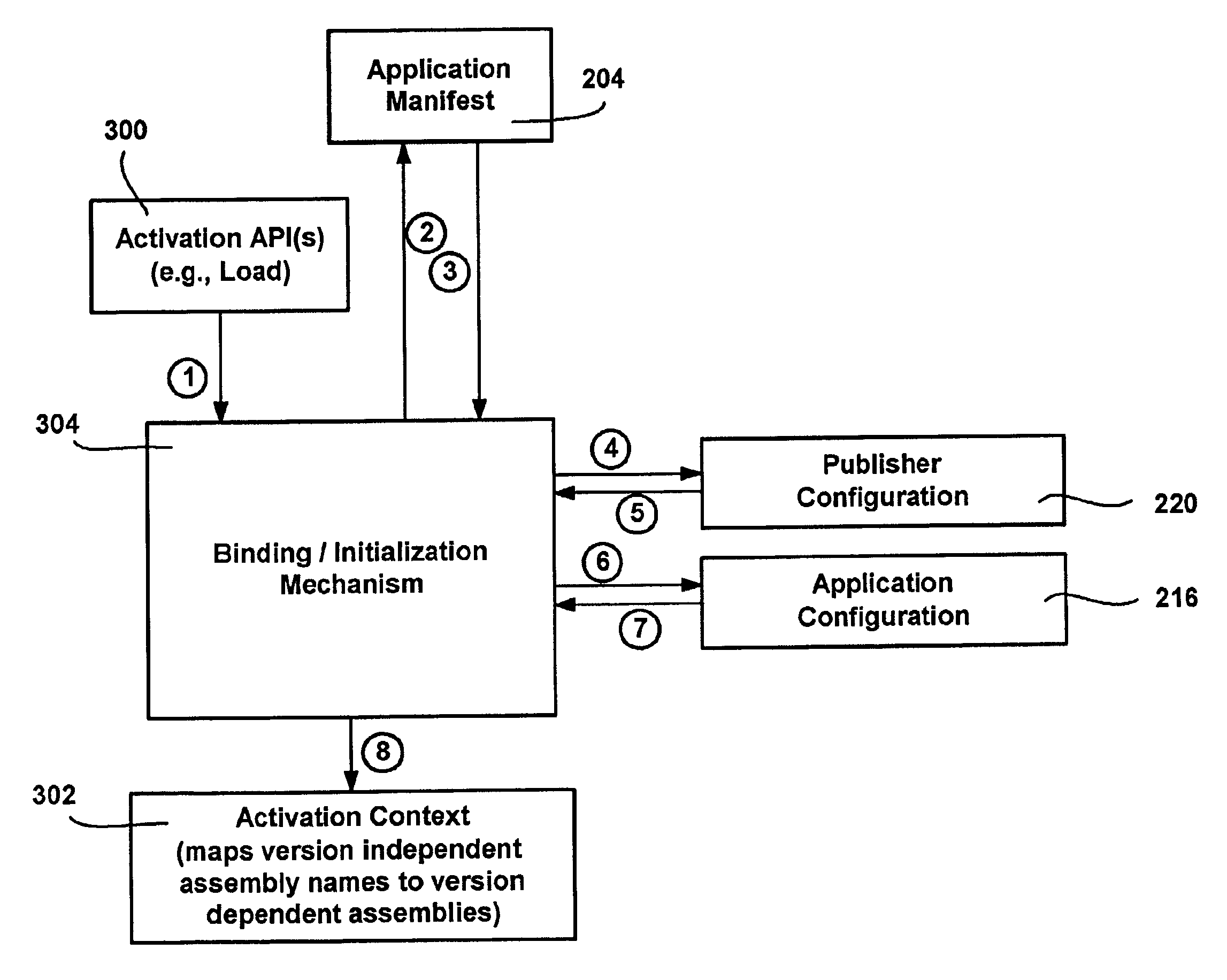
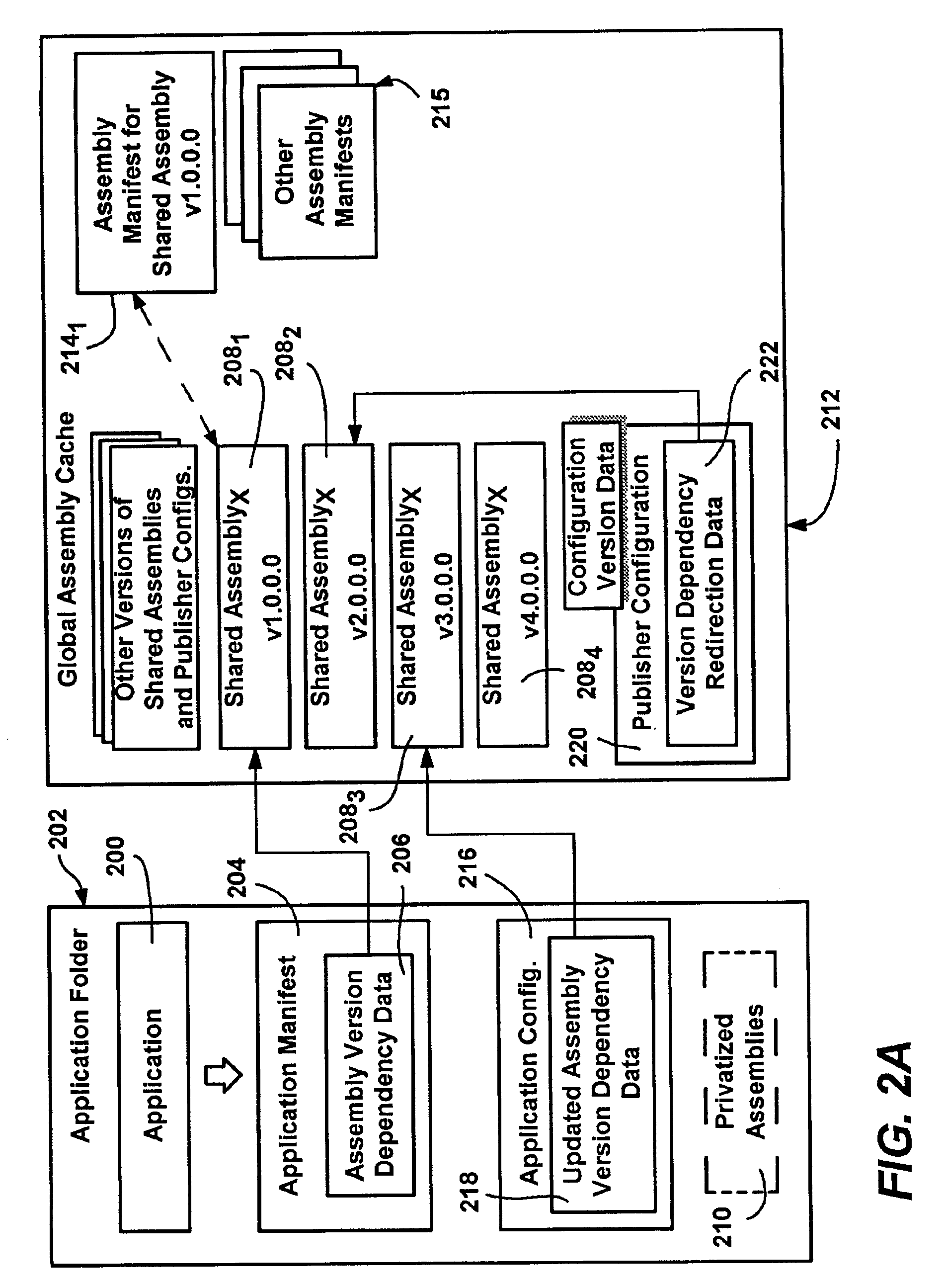
Configurations for binding software assemblies to application programs
A method, system and infrastructure that allow an application to run with specified versions of assemblies bound thereto, while allowing the application author, assembly publisher and / or an administrator to change the originally-specified version as desired. Each assembly may exist and run side-by-side on the system with other versions of the same assembly being used by other applications. An application manifest specifies any desired assembly versions, which may be redirected to another version (overridden) by an application configuration. A publisher configuration provided by an assembly publisher can similarly override the specified version. Lastly, an administrator configuration is capable of overriding other configuration versioning information. A table built from the manifest and any configuration redirection may be accessed during execution to quickly locate the appropriate version. The various configuration data structures themselves may be wrapped as assemblies, thereby enabling versioning of configurations.
Owner:MICROSOFT TECH LICENSING LLC
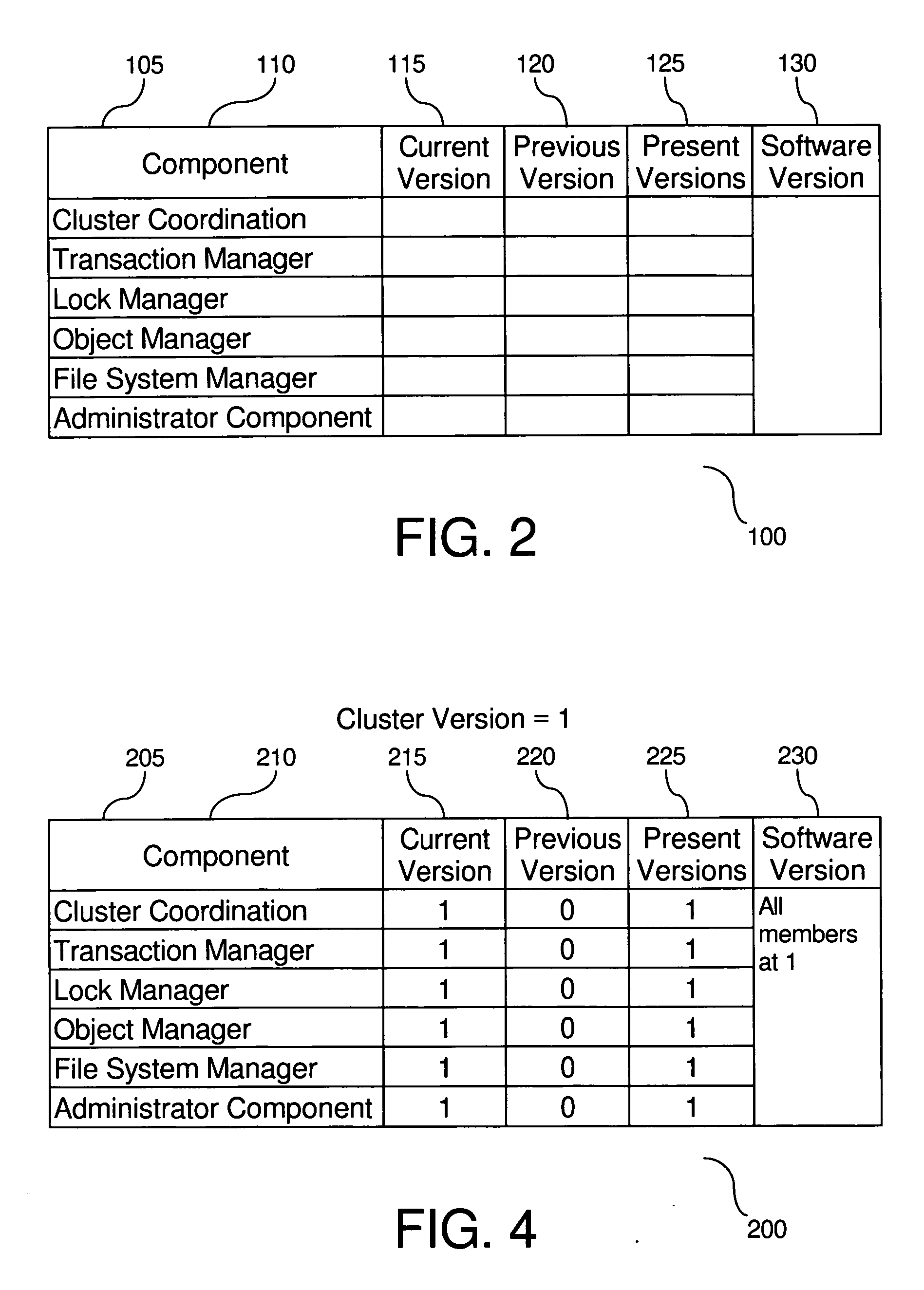
Fault tolerant rolling software upgrade in a cluster
A method and system are provided for conducting a cluster software version upgrade in a fault tolerant and highly available manner. There are two phases to the upgrade. The first phase is an upgrade of the software binaries of each individual member of the cluster, while remaining cluster members remain online. Completion of the first phase is a pre-requisite to entry into the second phase. Upon completion of the first phase, a coordinated cluster transition is performed during which the cluster coordination component performs any required upgrade to its own protocols and data structures and drives all other software components through the component specific upgrade. After all software components complete their upgrades and any required data conversion, the cluster software upgrade is complete. A shared version control record is provided to manage transition of the cluster members through the cluster software component upgrade.
Owner:IBM CORP
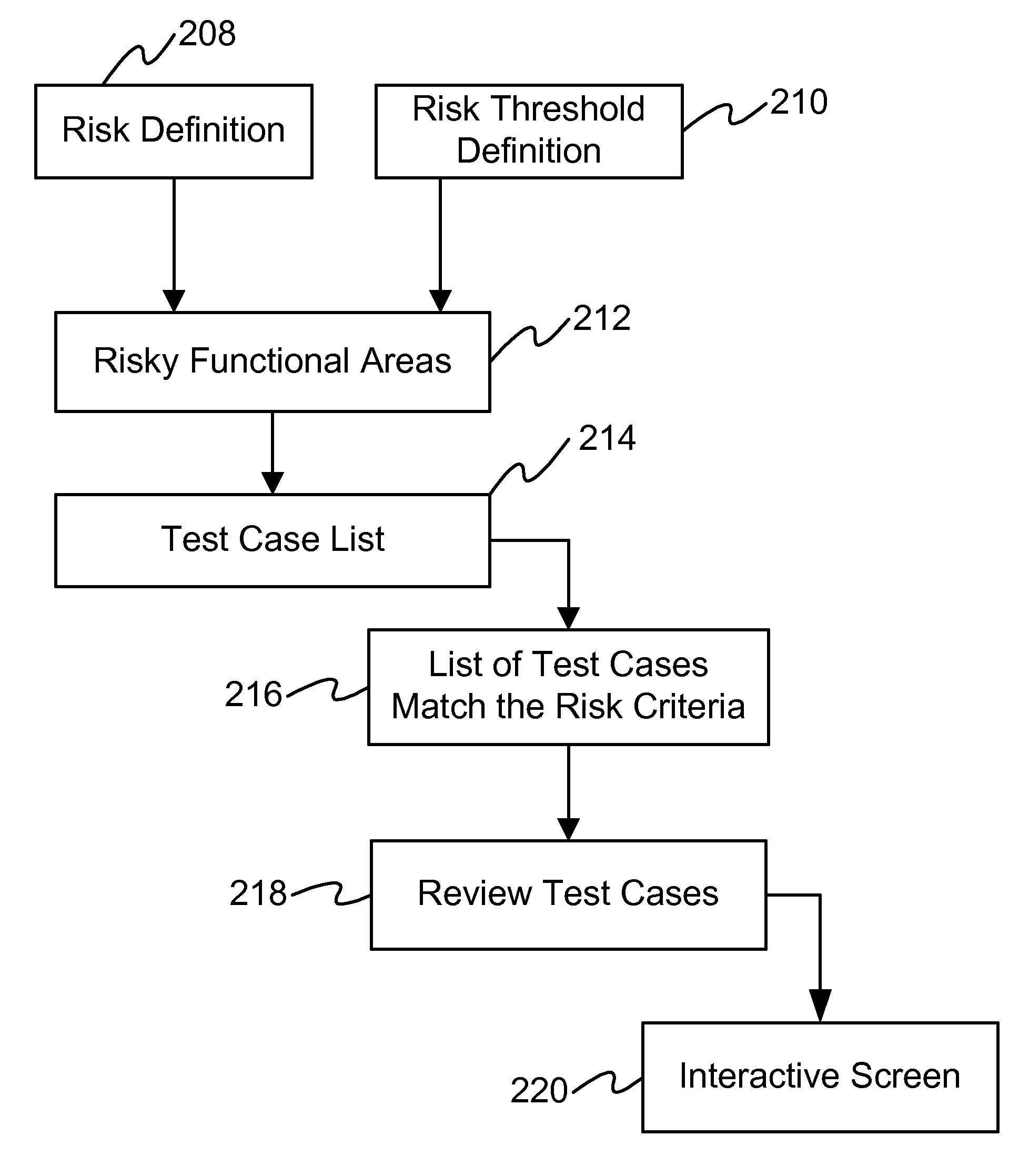
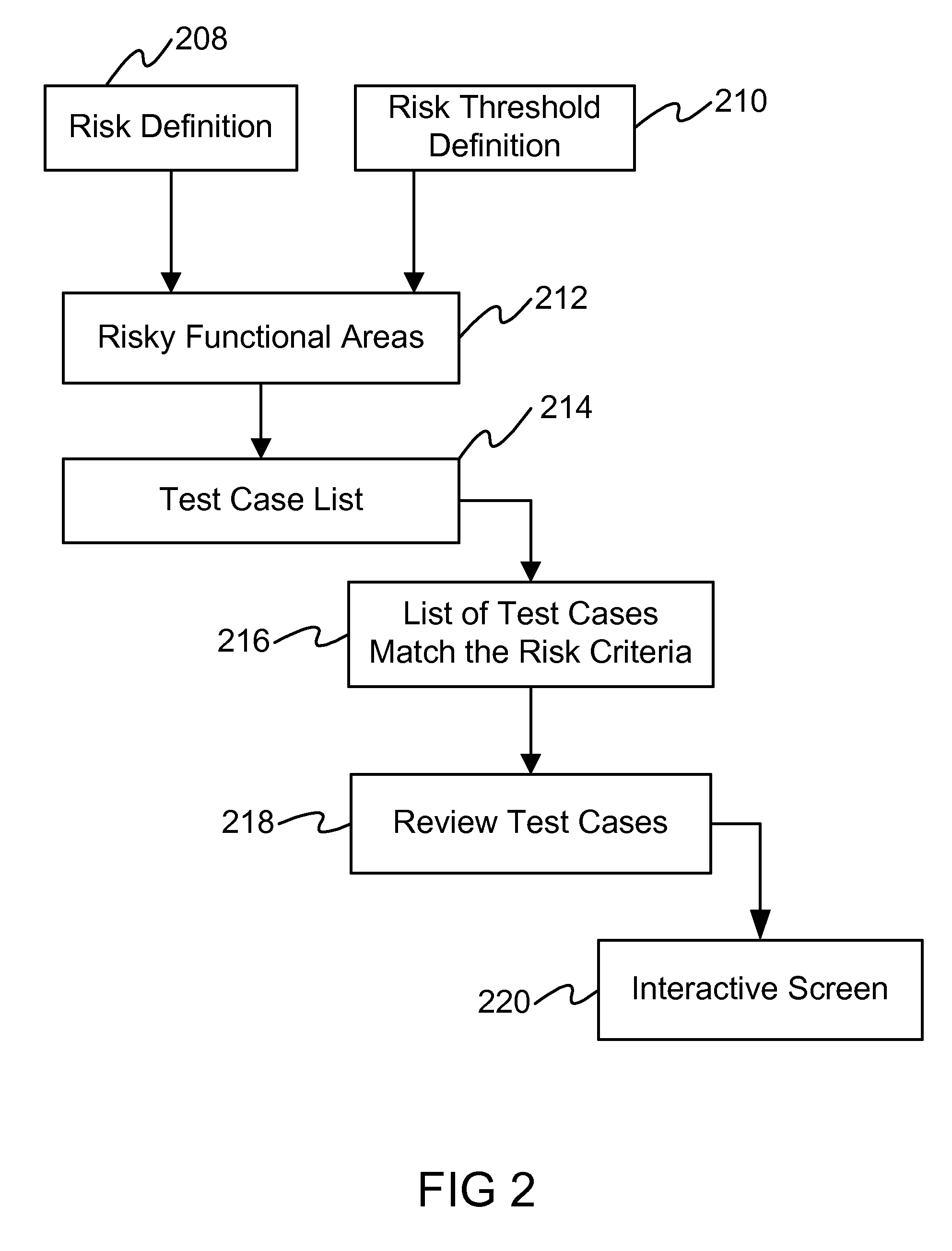
Method and system for automatically determining risk areas to retest
InactiveUS7506312B1Improved oddsVersion controlReliability/availability analysisChange managementManagement tool
In software development, risks can be quantified and defined by certain attributes. For instance, a risky area will have a large number of defects / changes for that area, a large number of high severity defects for that area, or a large number of coders / authors for that same area. All these metrics are already captured in Unified Change Management tools, version control tools and bug tracking tools. By taking the appropriate data and associating them with certain triggers and thresholds, an embodiment of the invention automatically identifies which test cases to run for regression. Through historical and previous test data and test runs, an embodiment of the invention forecasts how long it will take to run these regression suites.
Owner:IBM CORP
Automated software testing framework
InactiveUS7694181B2Simple and efficientEasy to exportError detection/correctionSpecific program execution arrangementsWeb serviceSystem under test
A generic testing framework to automatically allocate, install and verify a given version of a system under test, to exercise the system against a series of tests in a “hands-off” objective manner, and then to export information about the tests to one or more developer repositories (such as a query-able database, an email list, a developer web server, a source code version control system, a defect tracking system, or the like). The framework does not “care” or concern itself with the particular implementation language of the test as long as the test can issue directives via a command line or configuration file. During the automated testing of a given test suite having multiple tests, and after a particular test is run, the framework preferably generates an “image” of the system under test and makes that information available to developers, even while additional tests in the suite are being carried out. In this manner, the framework preserves the system “state” to facilitate concurrent or after-the-fact debugging. The framework also will re-install and verify a given version of the system between tests, which may be necessary in the event a given test is destructive or otherwise places the system in an unacceptable condition.
Owner:HITACHI DATA SYST CORP
Non-volatile memory-based mass storage devices and methods for writing data thereto
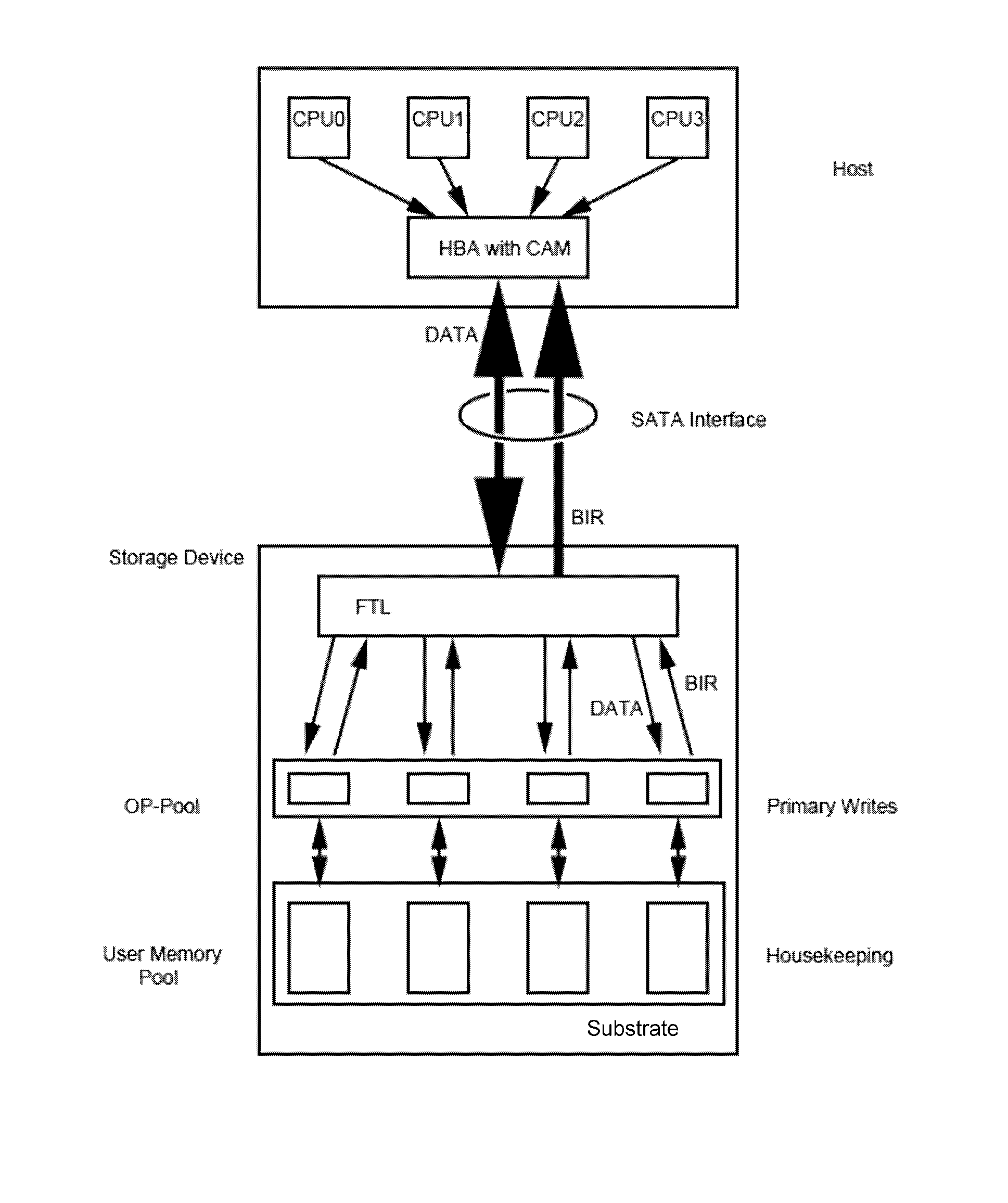
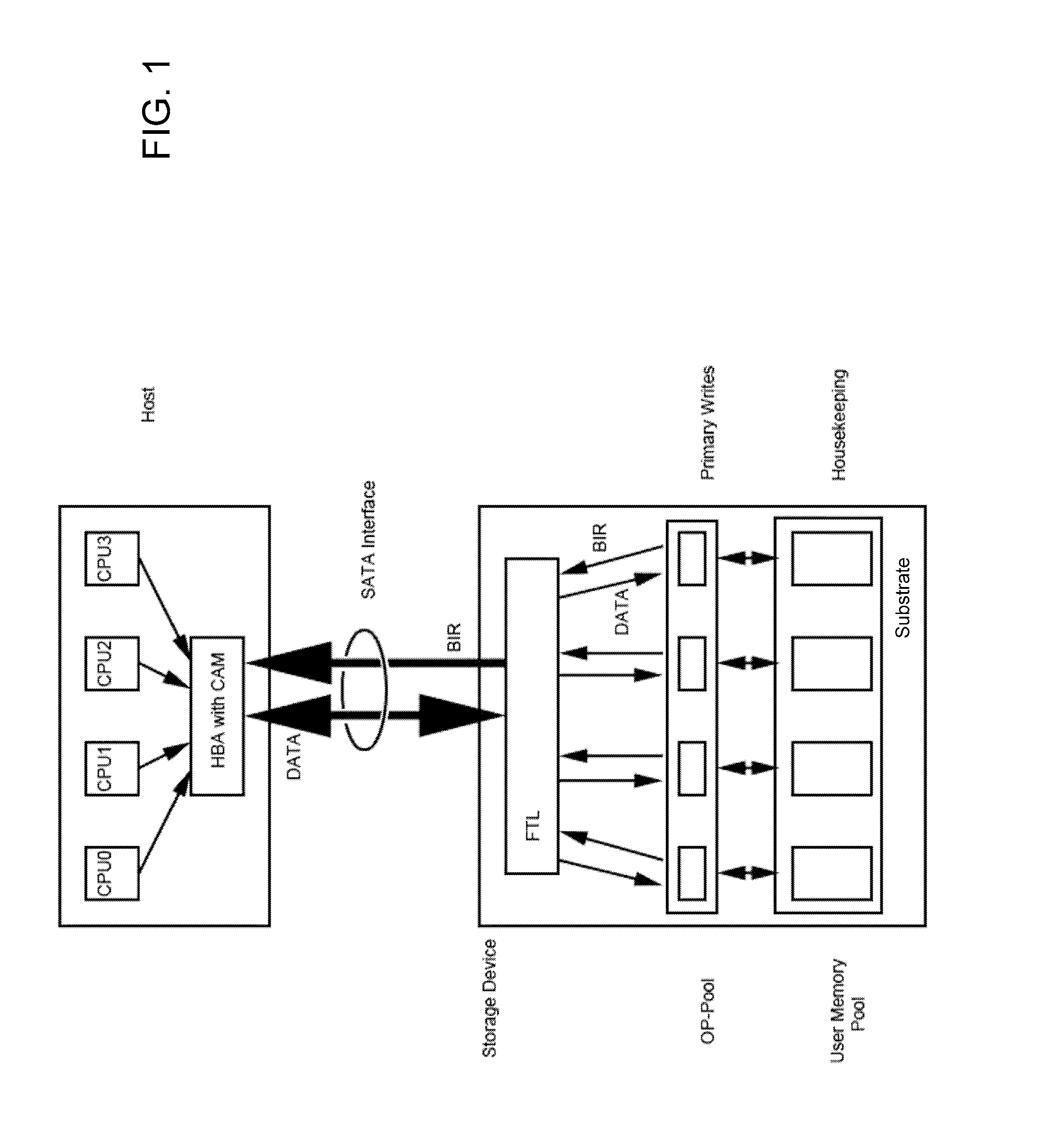
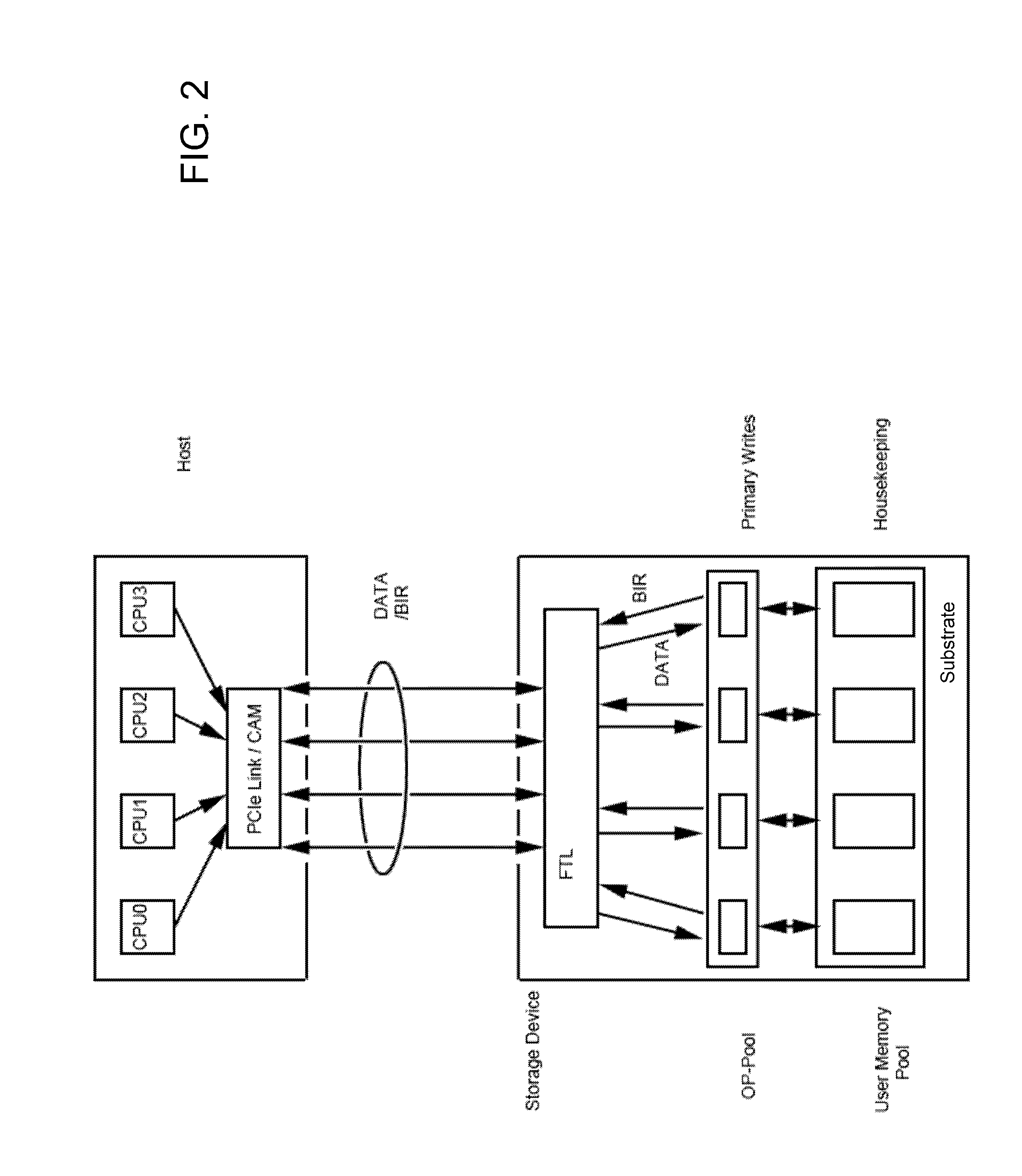
ActiveUS20130067138A1Need for goodMemory architecture accessing/allocationRead-only memoriesMass storageComputer science
A non-volatile solid state memory-based mass storage device having at least one non-volatile memory component and methods of operating the storage device. In one aspect of the invention, the one or more memory components define a memory space partitioned into user memory and over-provisioning pools based on a P / E cycle count stored in a block information record. The storage device transfers the P / E cycle count of erased blocks to a host and the host stores the P / E cycle count in a content addressable memory. During a host write to the storage device, the host issues a low P / E cycle count number as a primary address to the content addressable memory, which returns available block addresses of blocks within the over-provisioning pool as a first dimension in a multidimensional address space. Changed files are preferably updated in append mode and the previous version can be maintained for version control.
Owner:KIOXIA CORP
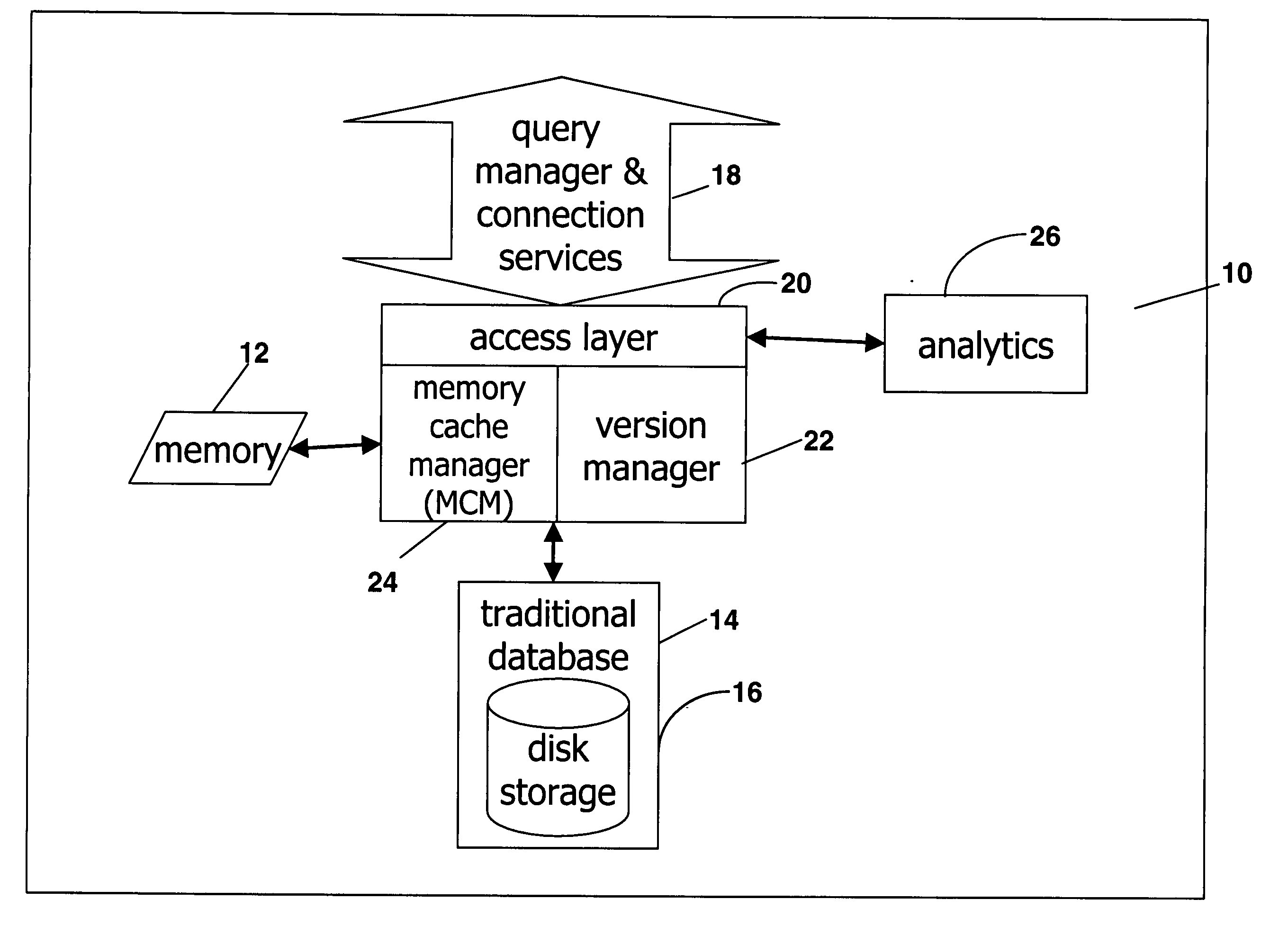
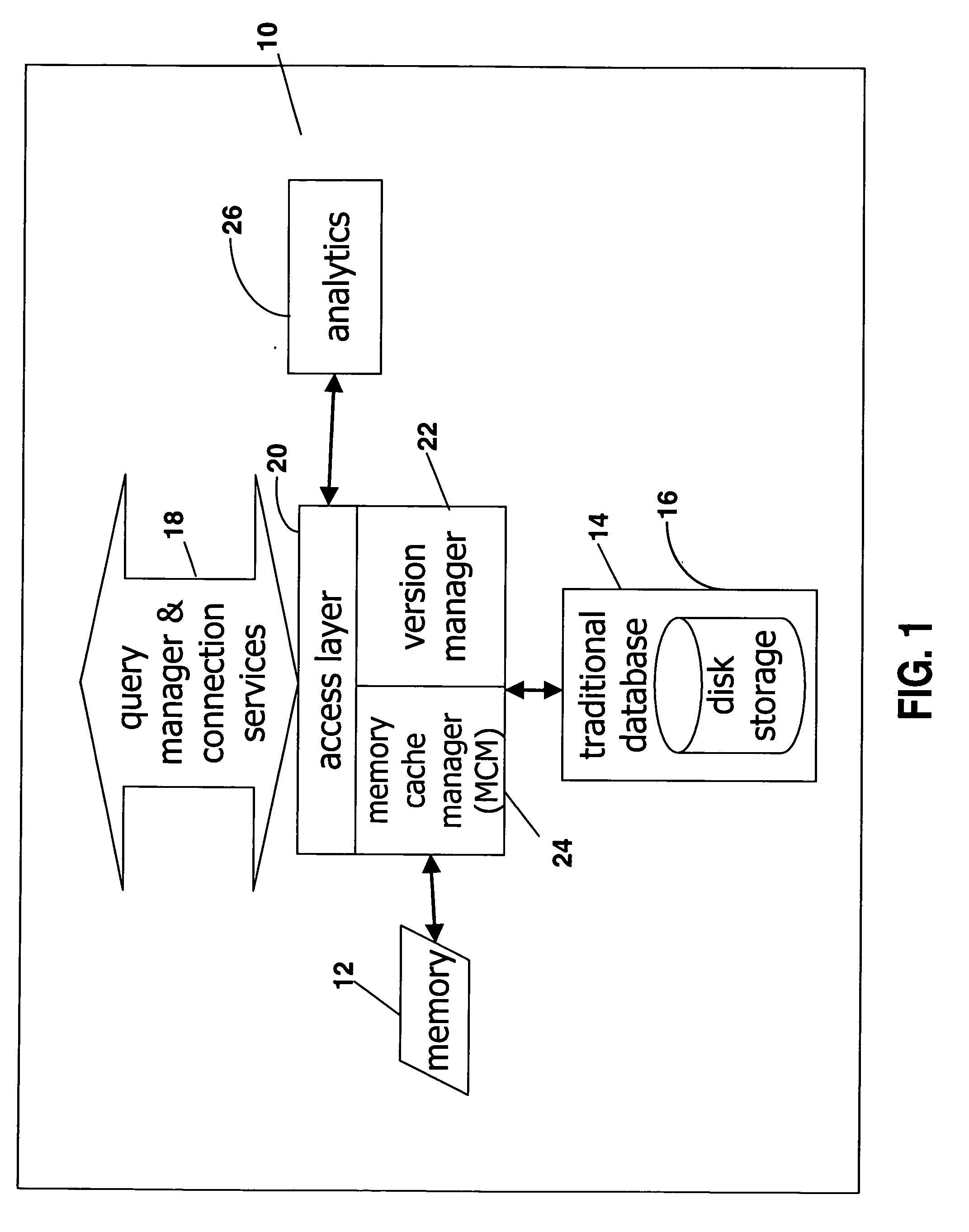
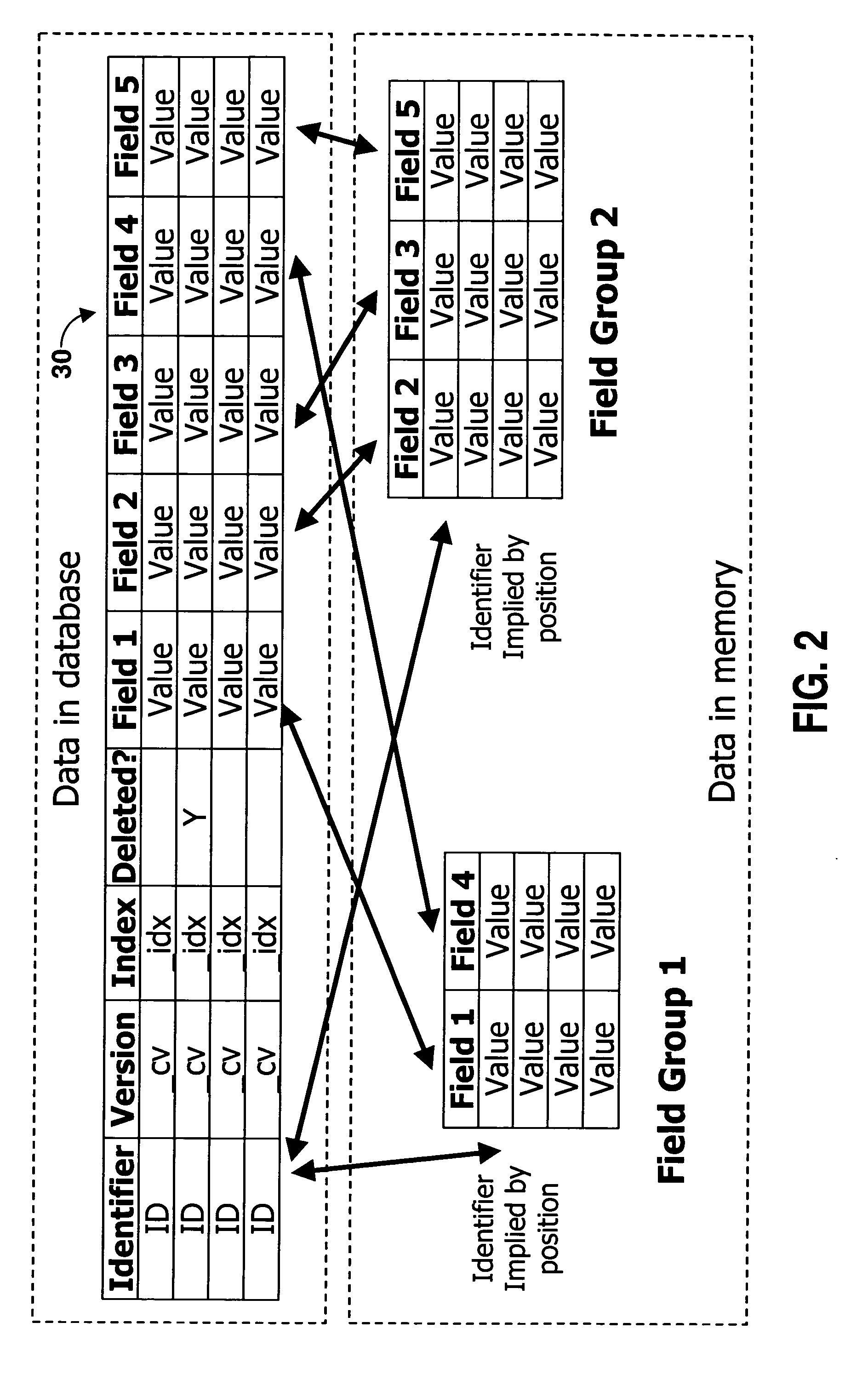
Extended database engine providing versioning and embedded analytics
ActiveUS20050138013A1Increase valueEfficient methodDigital data information retrievalDigital data processing detailsRelational databaseDatabase engine
A system for calculating analytics uses a relational database to store inputs, calculates results, and stores them in cache. The system also includes an access layer that provides a unified view of the data in server. A dynamic access layer is generated at runtime to run an analytic to provide a flexible framework for creating business logic.
Owner:KINAXIS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com