Patents
Literature
77 results about "High severity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
High Priority, High Severity :- An error which occurs on the basic functionality of the application and will not allow the user to use the system (E.g. user is not able to login to the application)
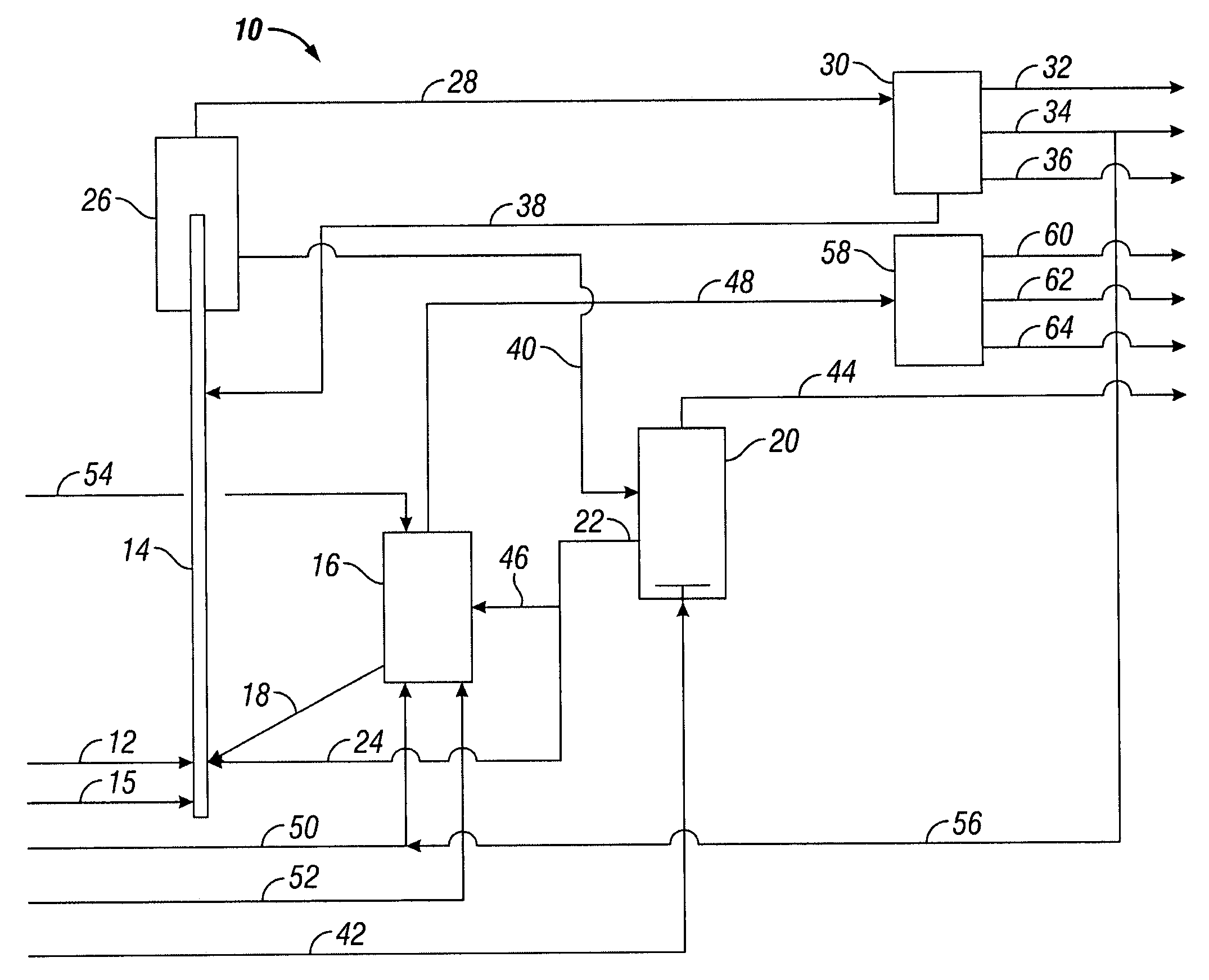
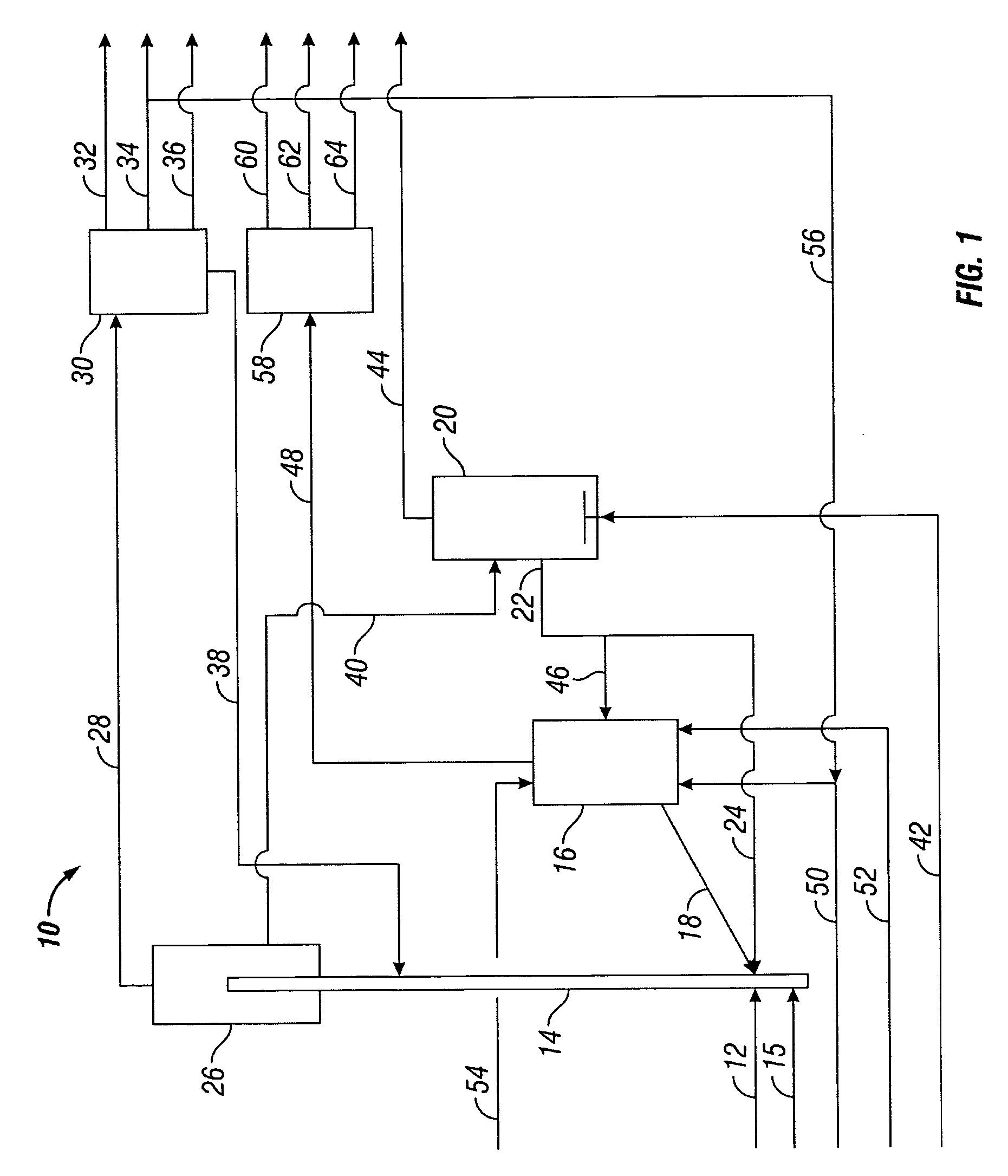
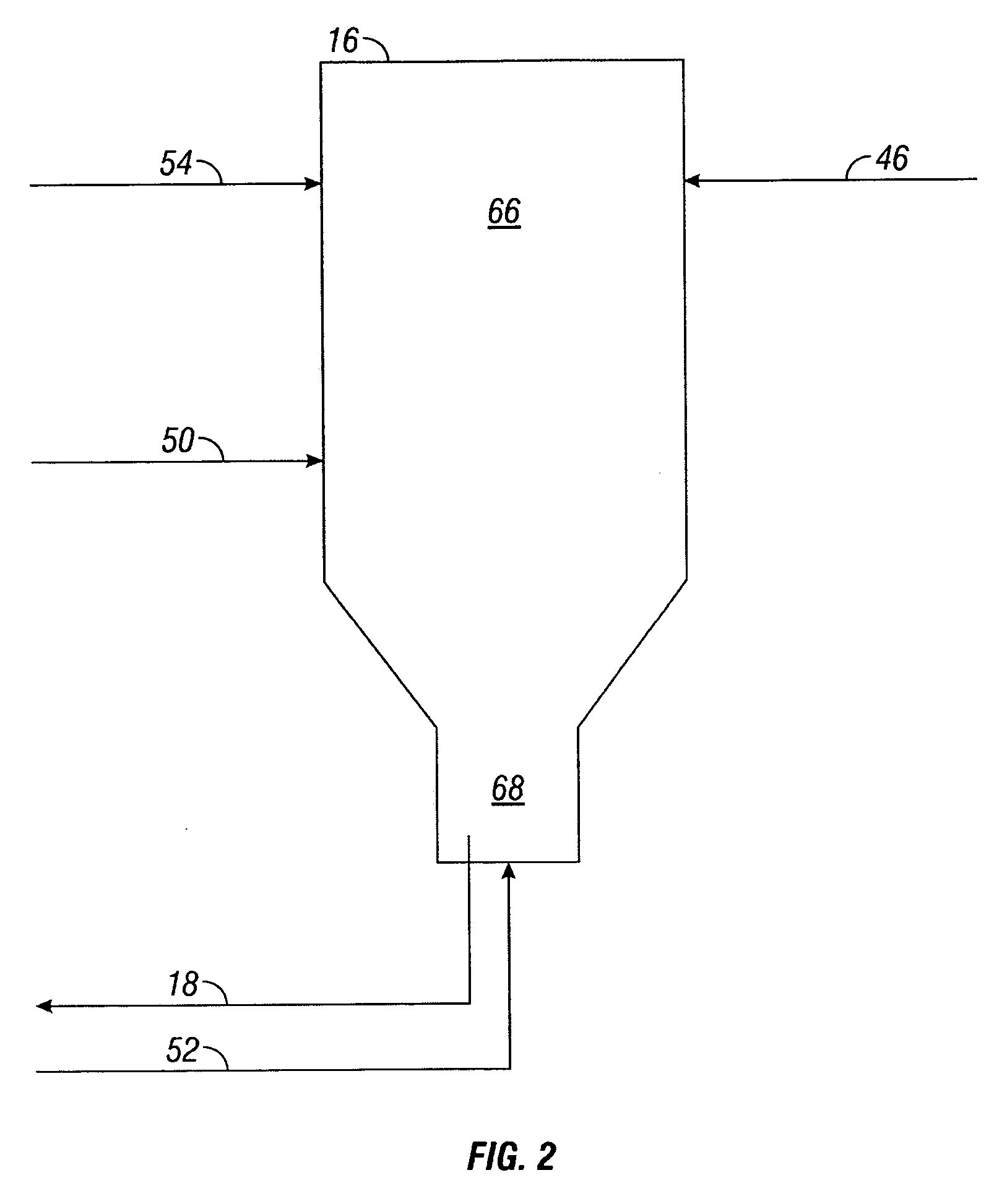
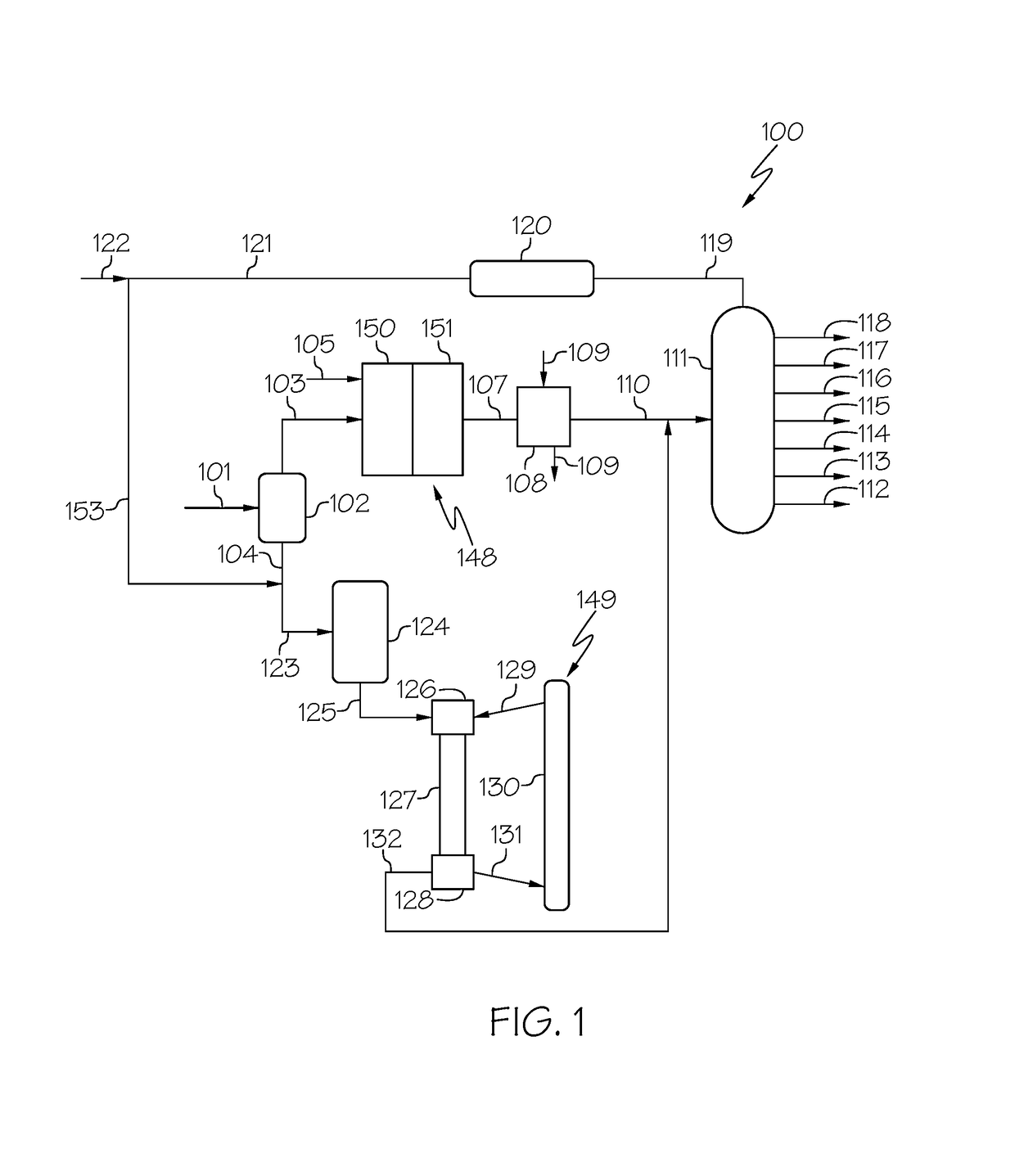
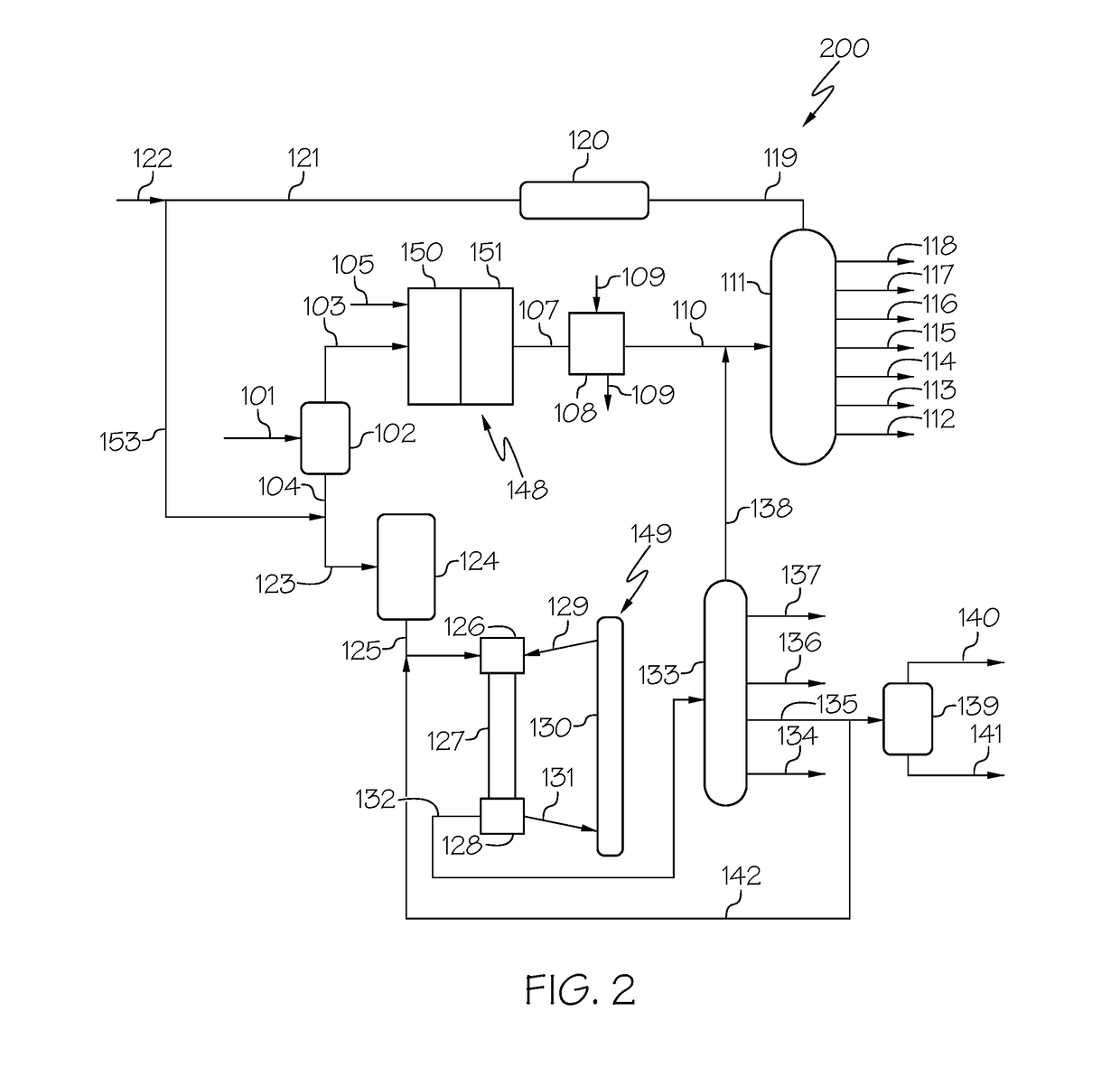
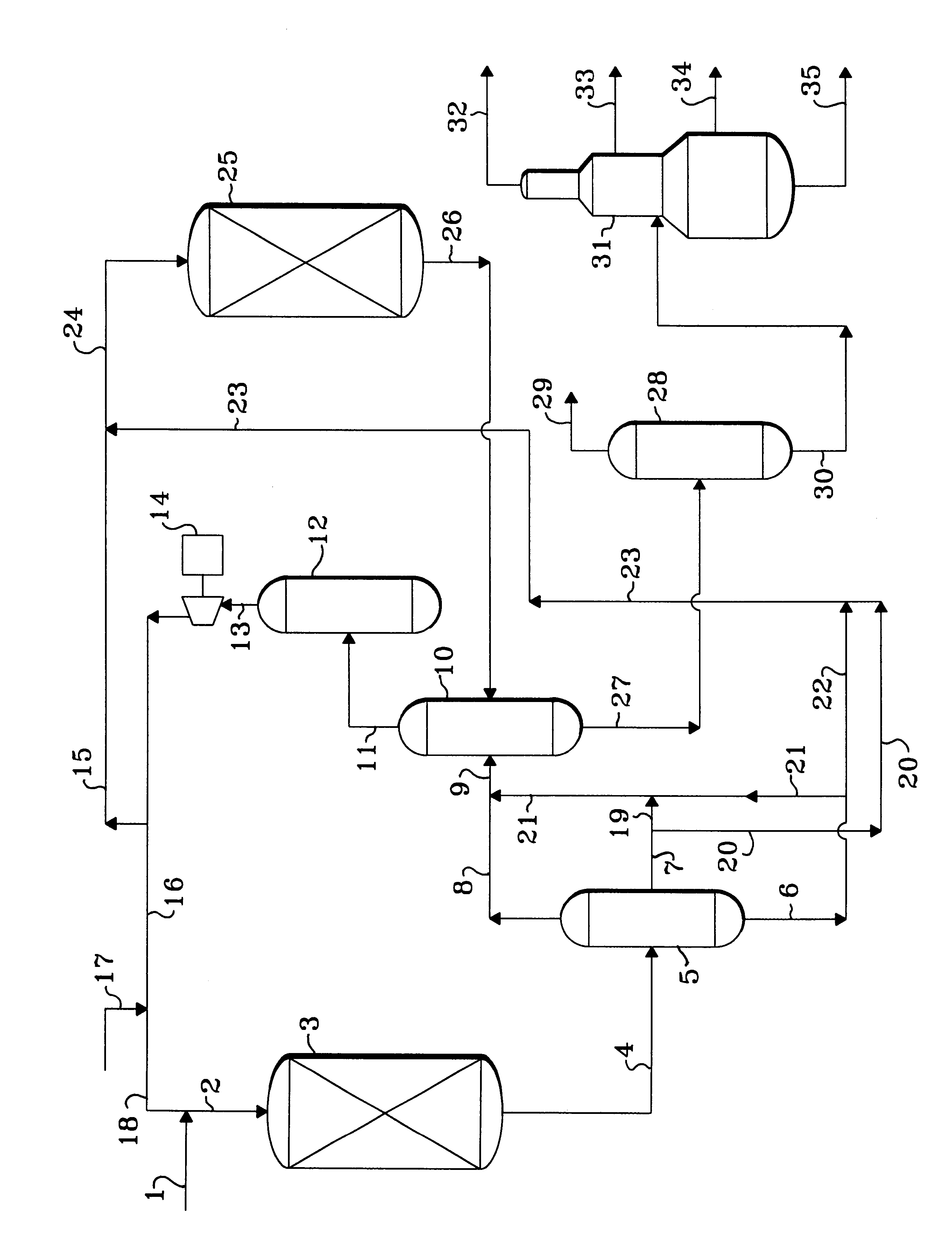
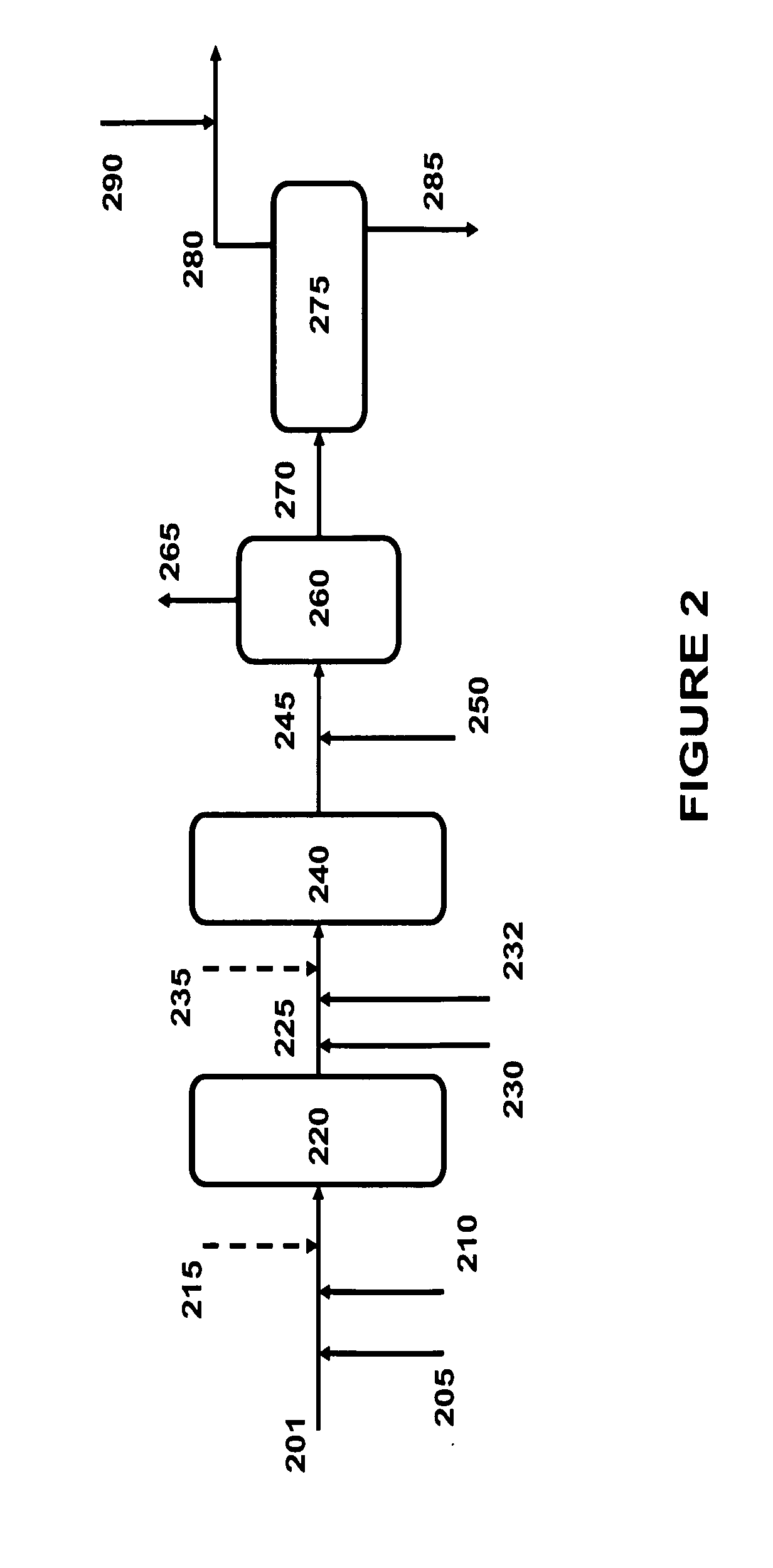
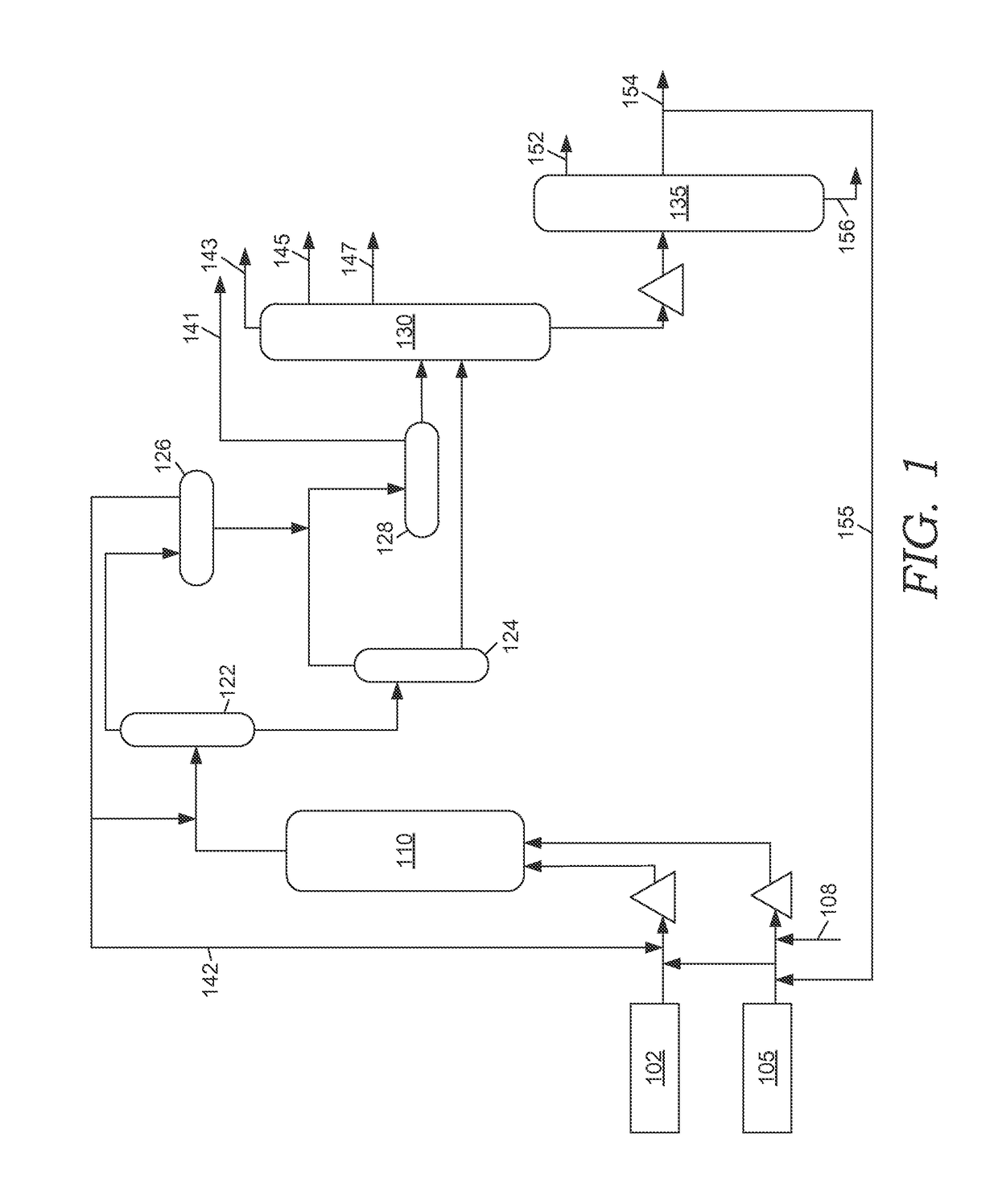
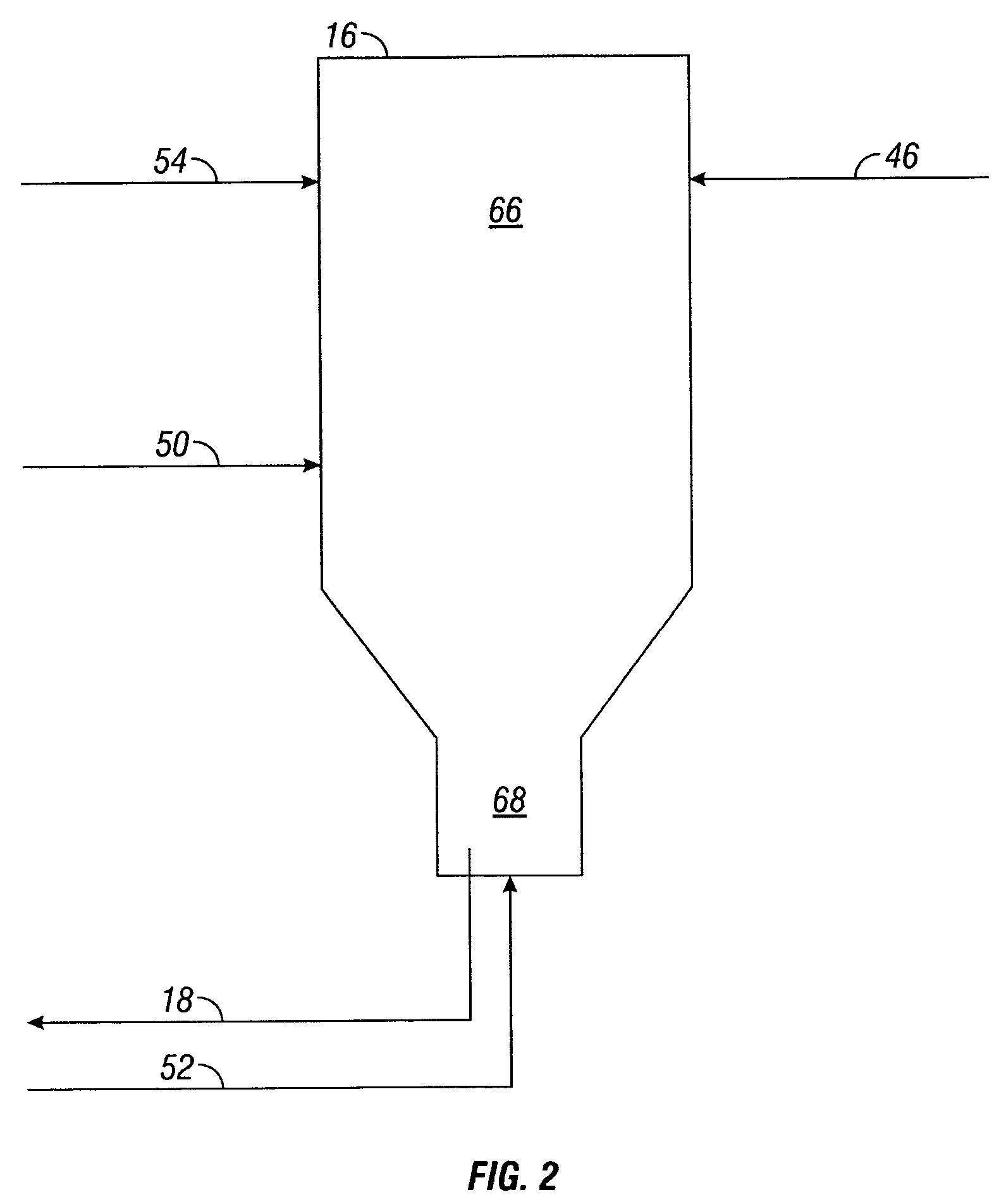
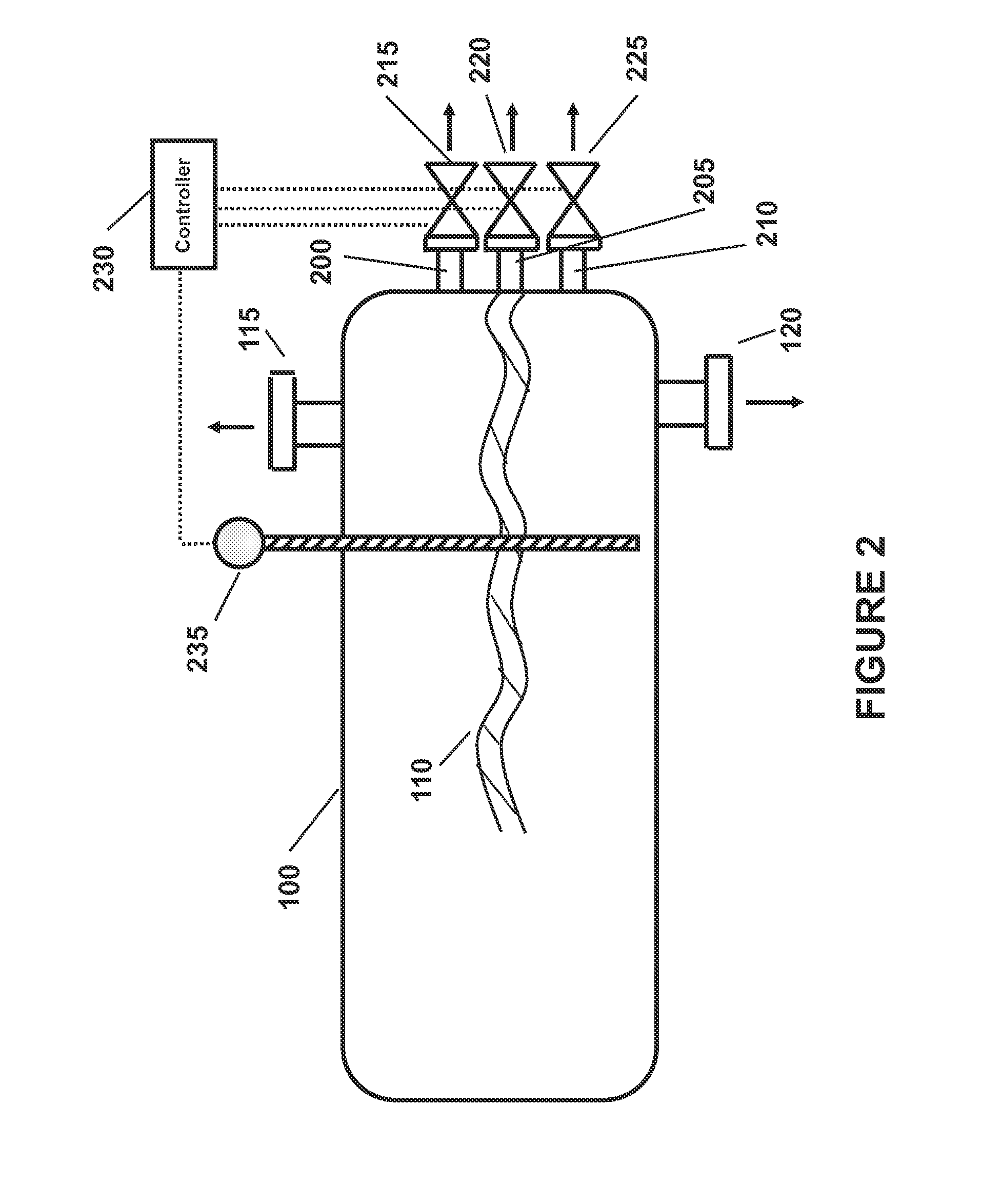
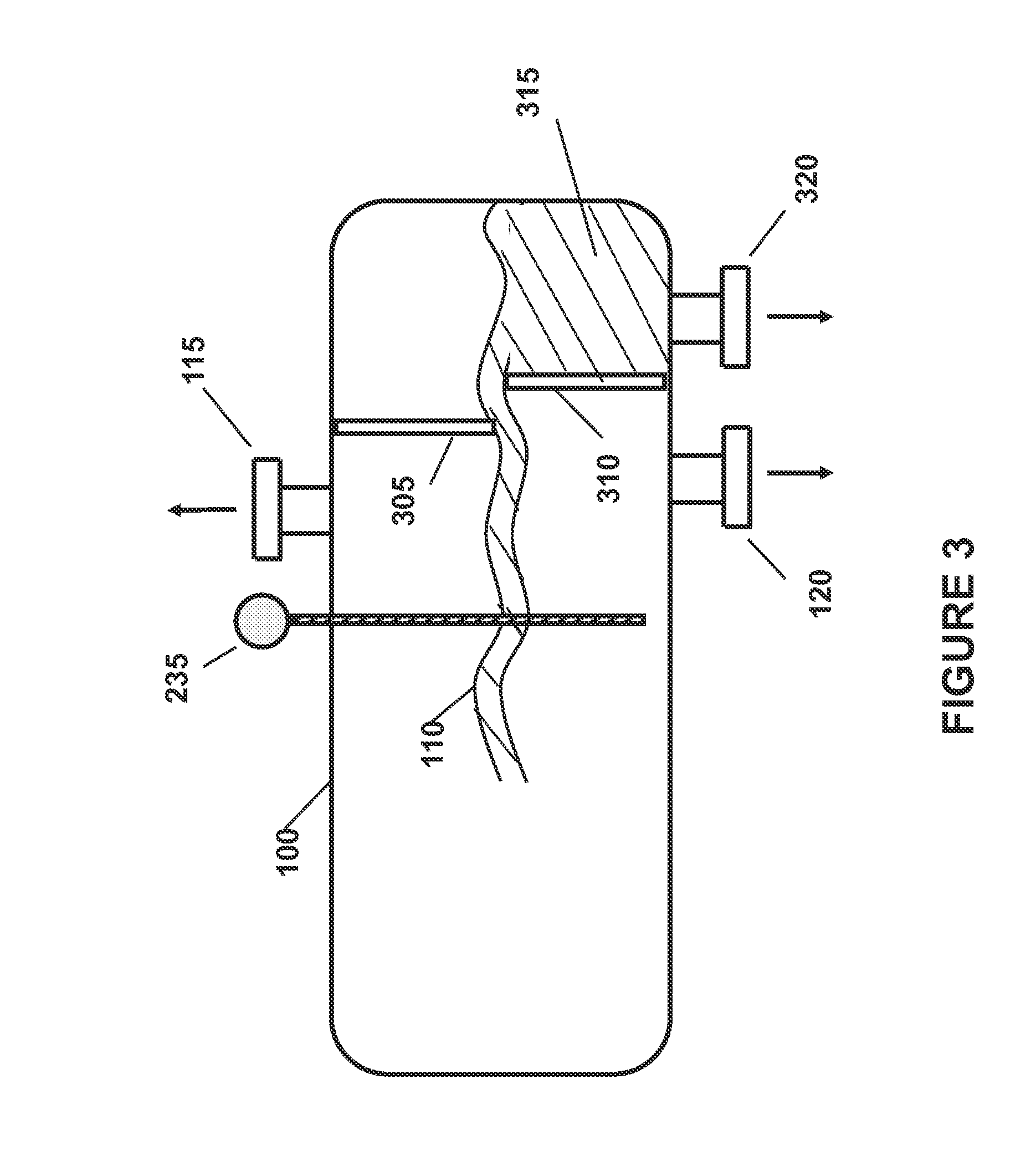
Method and apparatus for making a middle distillate product and lower olefins from a hydrocarbon feedstock
ActiveUS20060178546A1Yield maximizationCatalytic crackingCatalytic naphtha reformingPetroleum productGasoline
Disclosed is a process for making middle distillate and lower olefins. The process includes catalytically cracking a gas oil feedstock within a riser reactor zone by contacting under suitable catalytic cracking conditions within the riser reactor zone the gas oil feedstock with a middle distillate selective cracking catalyst that comprises amorphous silica alumina and a zeolite to yield a cracked gas oil product and a spent cracking catalyst. The spent cracking catalyst is regenerated to yield a regenerated cracking catalyst. Within an intermediate cracking reactor such as a dense bed reactor zone and under suitable high severity cracking conditions a gasoline feedstock is contacted with the regenerated cracking catalyst to yield a cracked gasoline product and a used regenerated cracking catalyst. The used regenerated cracking catalyst is utilized as the middle distillate selective catalyst.
Owner:SHELL USA INC
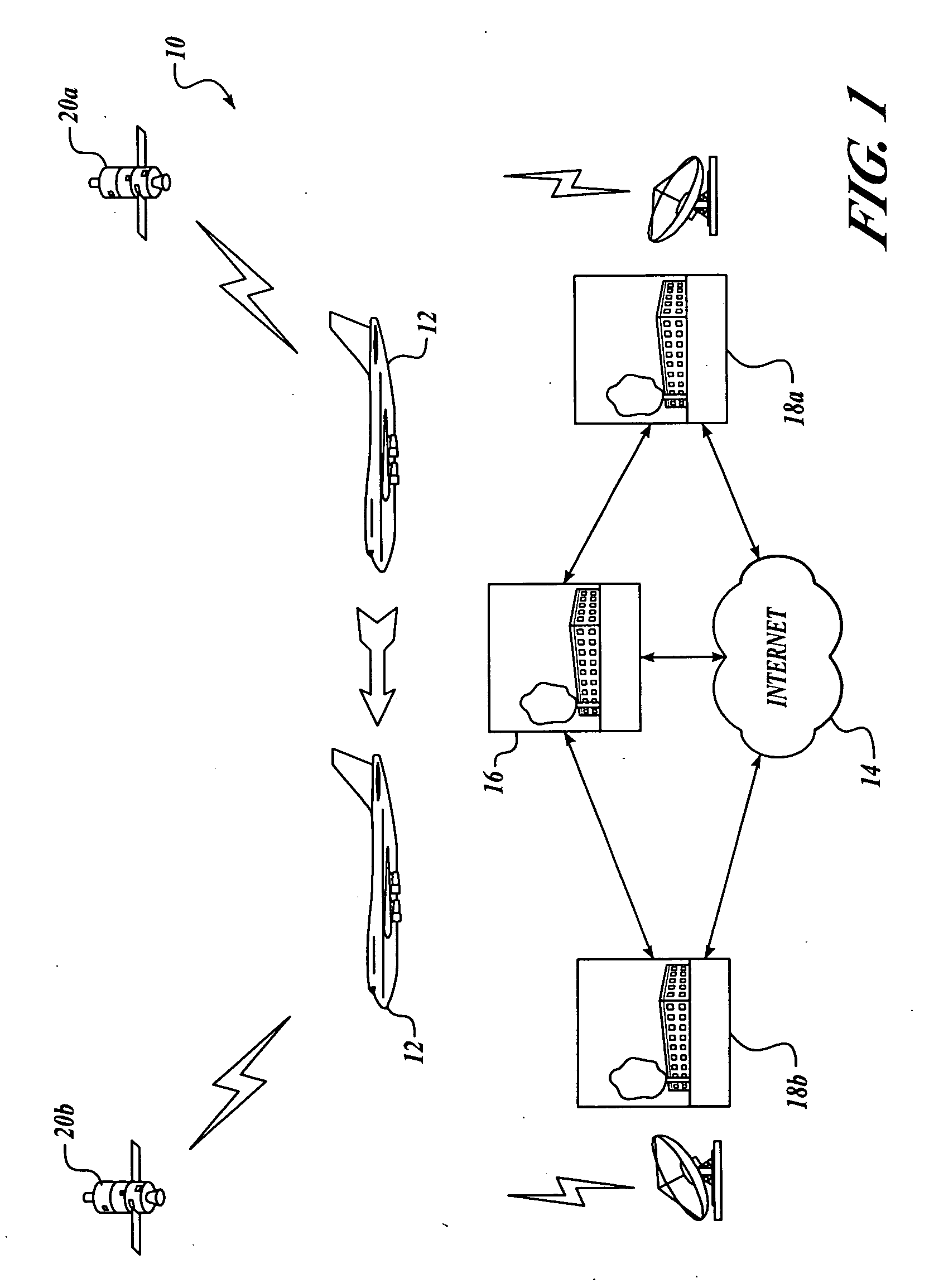
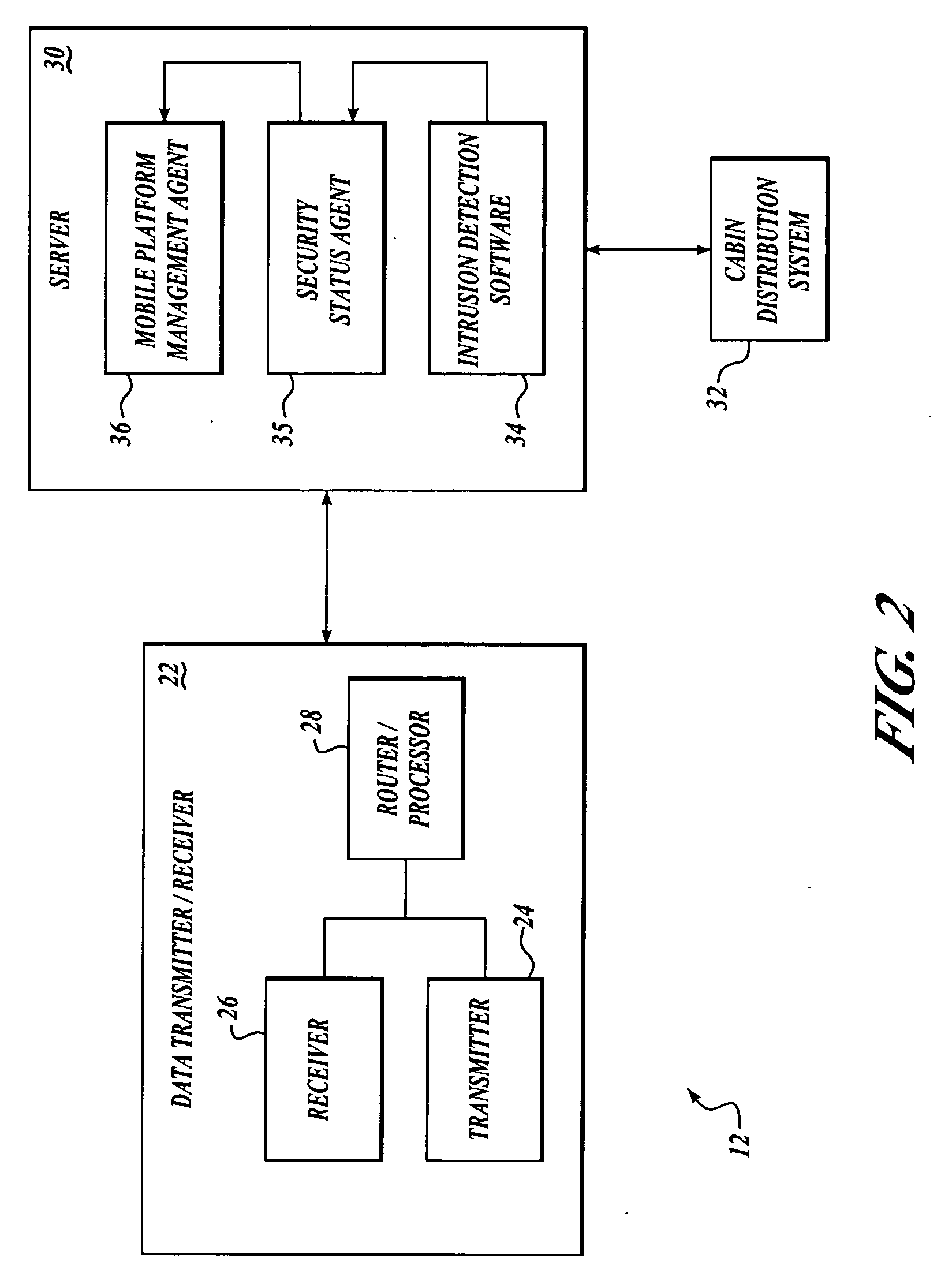
Security state vector for mobile network platform
ActiveUS20050254654A1Minimal amountMemory loss protectionError detection/correctionRolloverCyber operations
State of security in a mobile communications network is communicated. Data regarding nature and severity of security events onboard at least one mobile platform is generated and processed. A message that includes the processed data is generated and transmitted periodically. The processed data makes up a security state vector that includes the number of security events detected since power-up of the mobile platform node, sum of highest severity security events since power-up or counter rollover, sum of the second highest severity security events detected since power-up or counter rollover, sum of the third highest severity security events detected since power-up or counter rollover, highest security event classification, second-highest security event classification, and third-highest security event classification. The processed data may be used in a network operations center to prioritize mobile platforms from which logged data should be retrieved for further investigation and monitoring.
Owner:THE BOEING CO
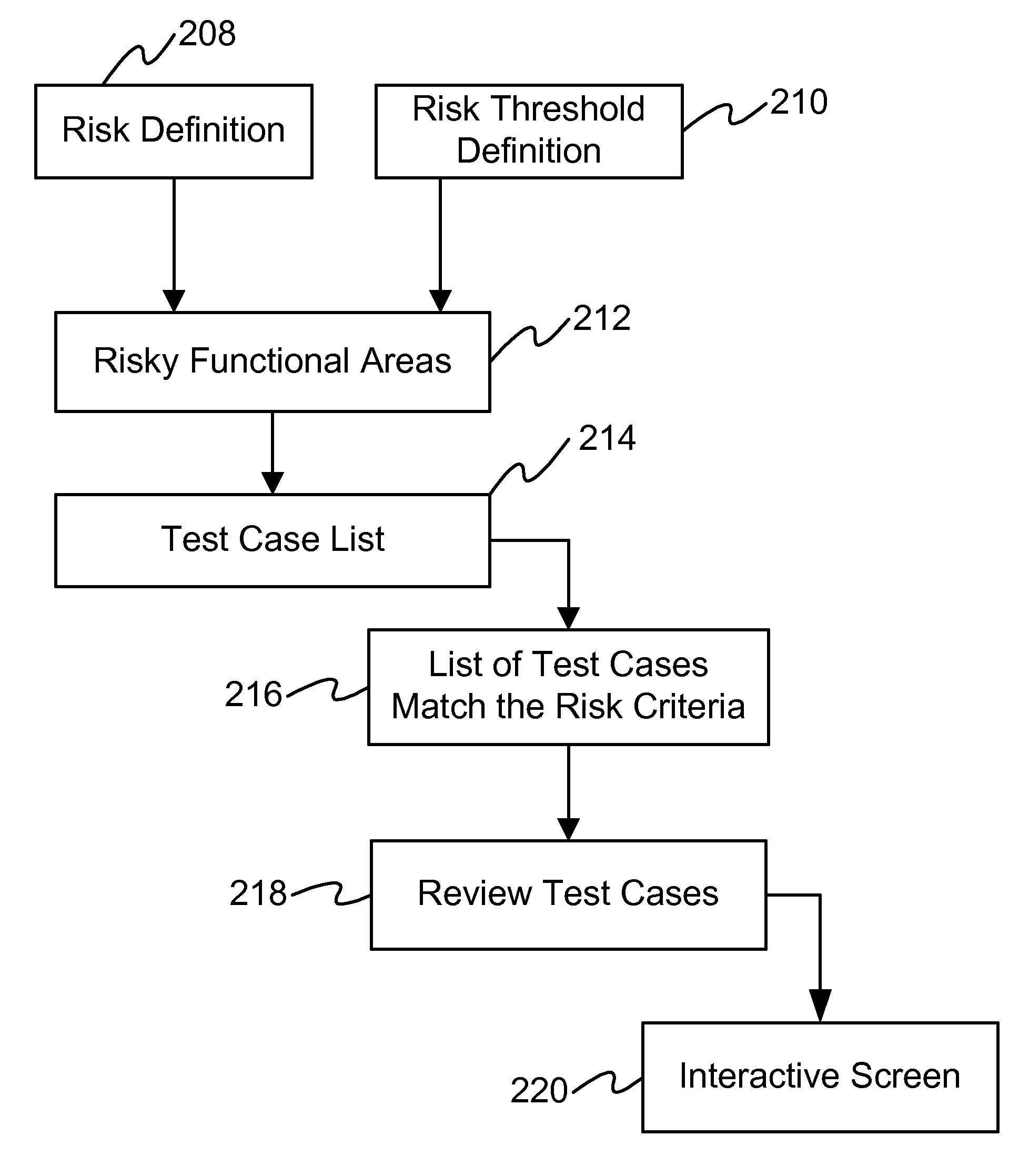
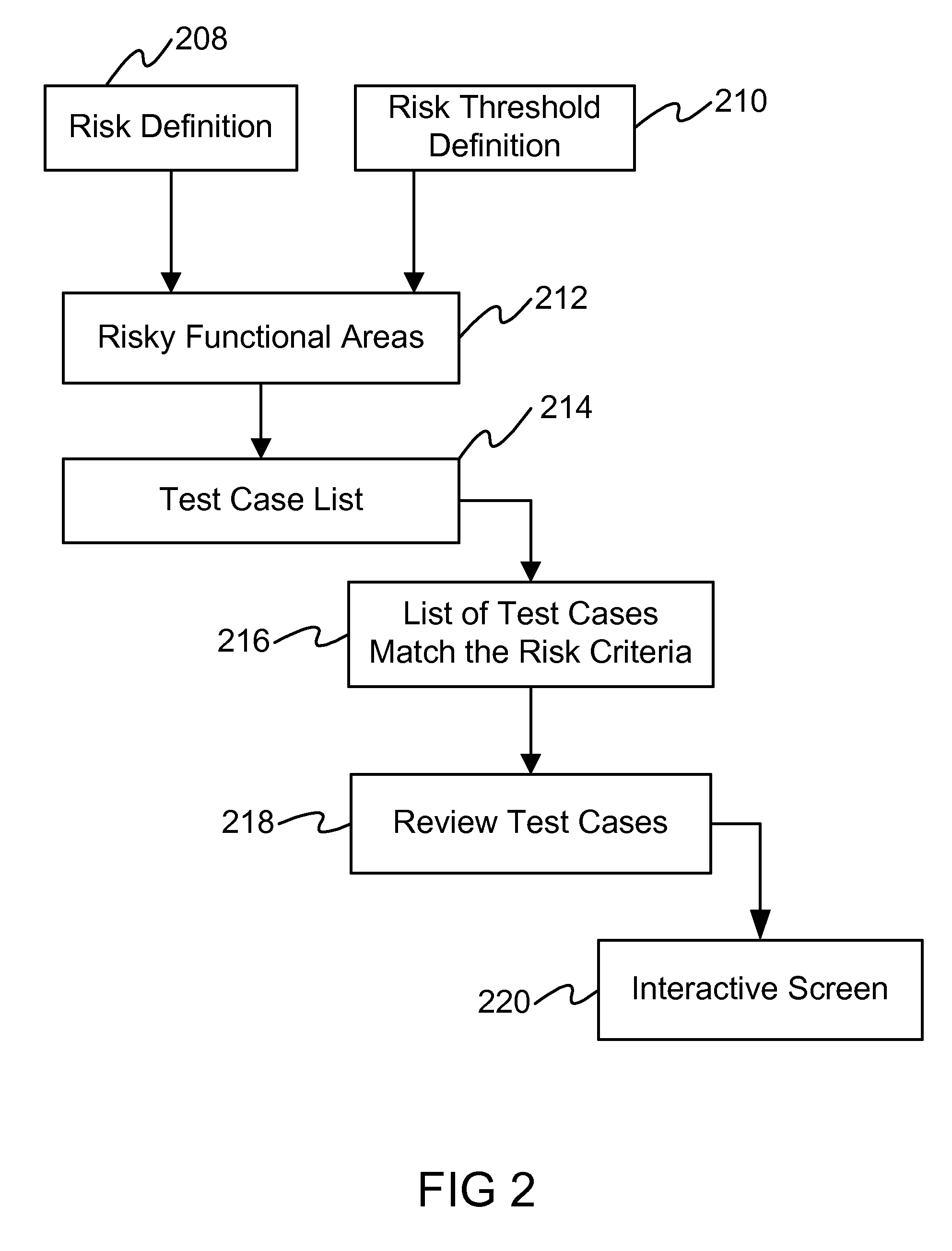
Method and system for automatically determining risk areas to retest
InactiveUS7506312B1Improved oddsVersion controlReliability/availability analysisChange managementManagement tool
In software development, risks can be quantified and defined by certain attributes. For instance, a risky area will have a large number of defects / changes for that area, a large number of high severity defects for that area, or a large number of coders / authors for that same area. All these metrics are already captured in Unified Change Management tools, version control tools and bug tracking tools. By taking the appropriate data and associating them with certain triggers and thresholds, an embodiment of the invention automatically identifies which test cases to run for regression. Through historical and previous test data and test runs, an embodiment of the invention forecasts how long it will take to run these regression suites.
Owner:IBM CORP
Process to produce synthetic fuels and lubricants
InactiveUS20050183988A1Yield maximizationEquipment cost can be minimizedThermal non-catalytic crackingCatalytic crackingBase oilPetroleum
A process utilizing a low severity hydrocracker prior to a high severity hydrocracker for the processing of petroleum based and synthetic hydrocarbon feedstocks into distillate fuels and high quality lubricant base oils. The process minimizes the size and conditions required by the high severity hydrocracker by closely matching such configuration with the desired product slate.
Owner:REG SYNTHETIC FUELS LLC
Systems and methods for the conversion of feedstock hydrocarbons to petrochemical products
ActiveUS20180057758A1Low costLess expensiveThermal non-catalytic crackingCatalytic crackingBoiling pointPetrochemical
According to an embodiment disclosed, a feedstock hydrocarbon may be processed by a method which may include separating the feedstock hydrocarbon into a lesser boiling point hydrocarbon fraction and a greater boiling point hydrocarbon fraction, cracking the greater boiling point hydrocarbon fraction in a high-severity fluid catalytic cracking reactor unit to form a catalytically cracked effluent, cracking the lesser boiling point hydrocarbon fraction in a steam cracker unit to form a steam cracked effluent, and separating one or both of the catalytically cracked effluent or the steam cracked effluent to form two or more petrochemical products. In one or more embodiments, the feedstock hydrocarbon may include crude oil and one of the petrochemical products may include light olefins.
Owner:SAUDI ARABIAN OIL CO
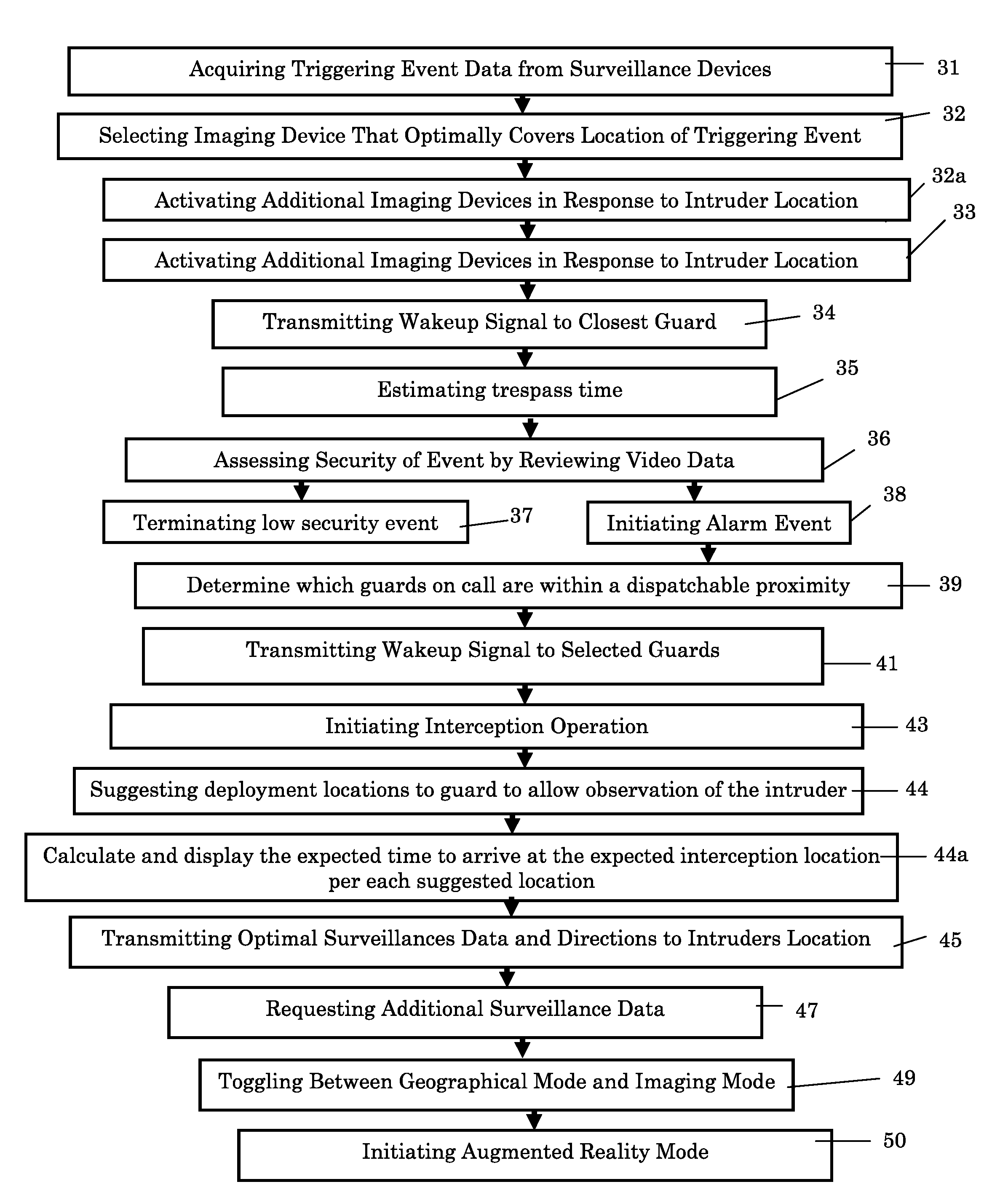
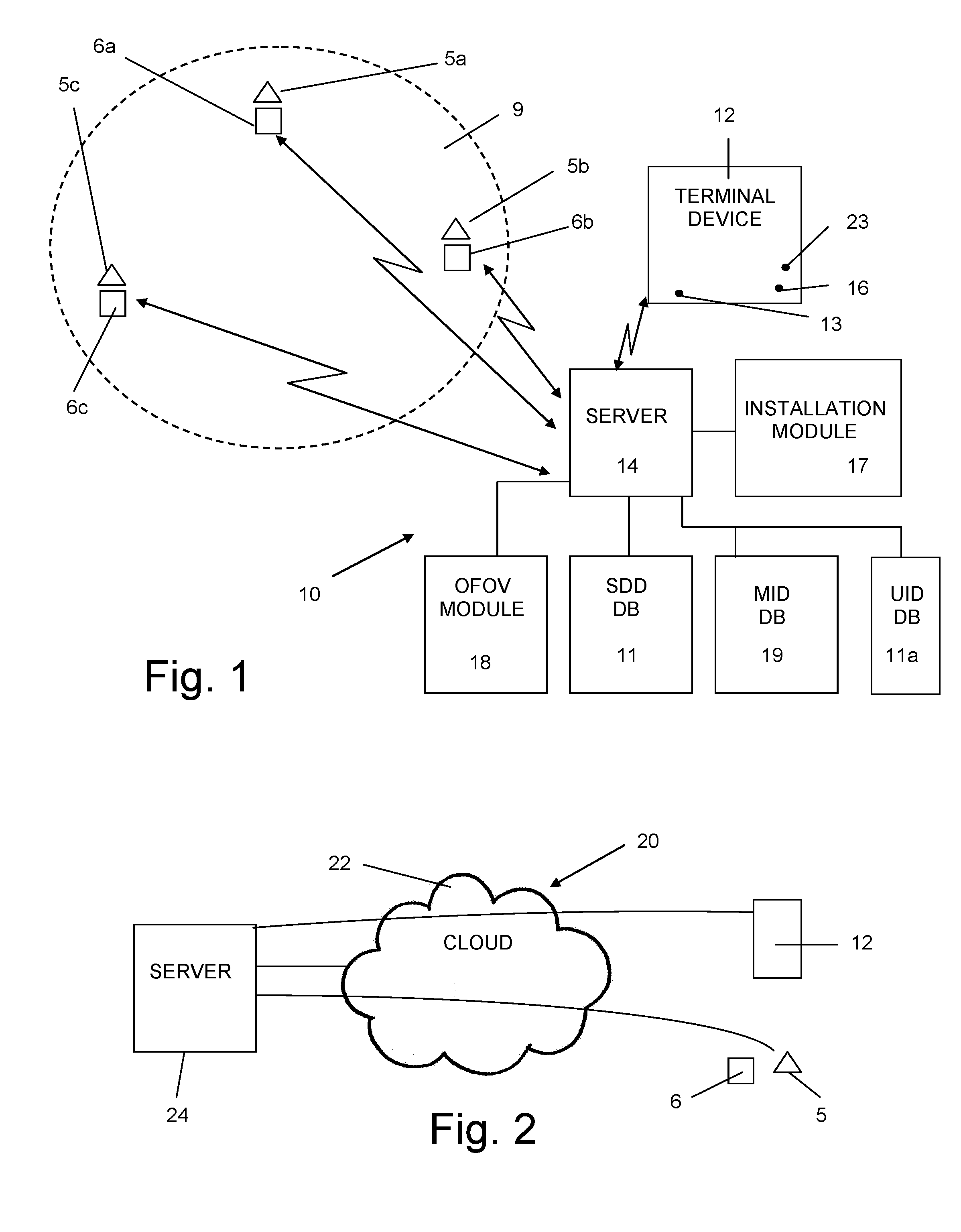
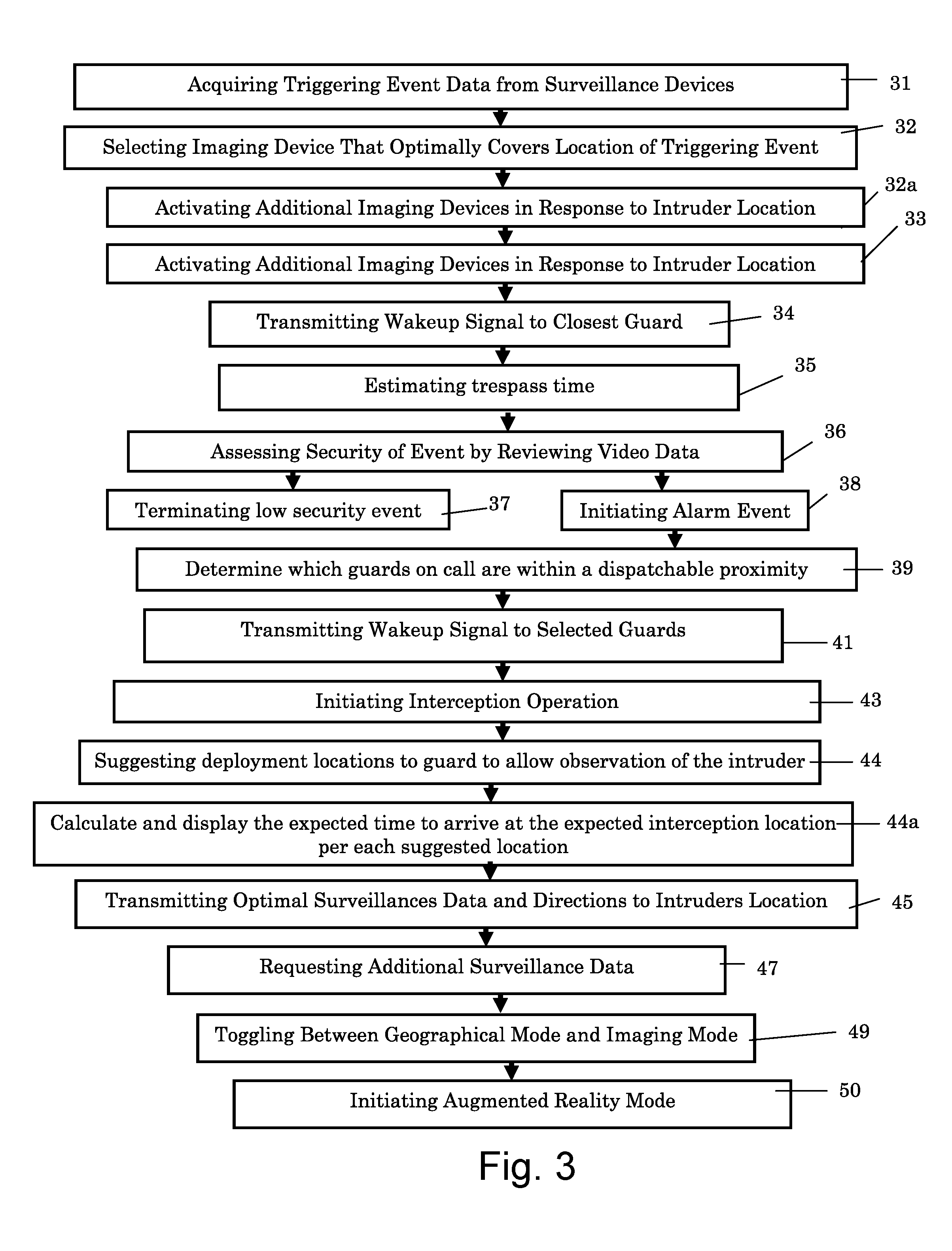
Integrative security system and method
ActiveUS20160232777A1Facilitate quick understandingEasy to understand quicklyClosed circuit television systemsBurglar alarm mechanical actuationSecurity systemSurveillance data
A method for monitoring and securing a facility without employing a manned control center, according to which a server acquires surveillance data from each of a plurality of distributed surveillance devices deployed within or adjacent to a given security sensitive facility. Then the server receives an intrusion alert from a guard, or from one or more of the plurality of surveillance devices to initiate a triggering event, if the acquired surveillance data is indicative of activity that has been detected at an indicated location. A first guard is alerted and presented with a full situational awareness image to assess the severity of the detected activity and the triggering event is terminated if found by the first guard to be of a low severity, or an interception operation initiated by self-dispatching or dispatching one or more additional guards to a close by location that holds tactical advantage relative to the indicated location if the triggering event was found by the first guard to be of a high severity.
Owner:LIQUID 360 LTD
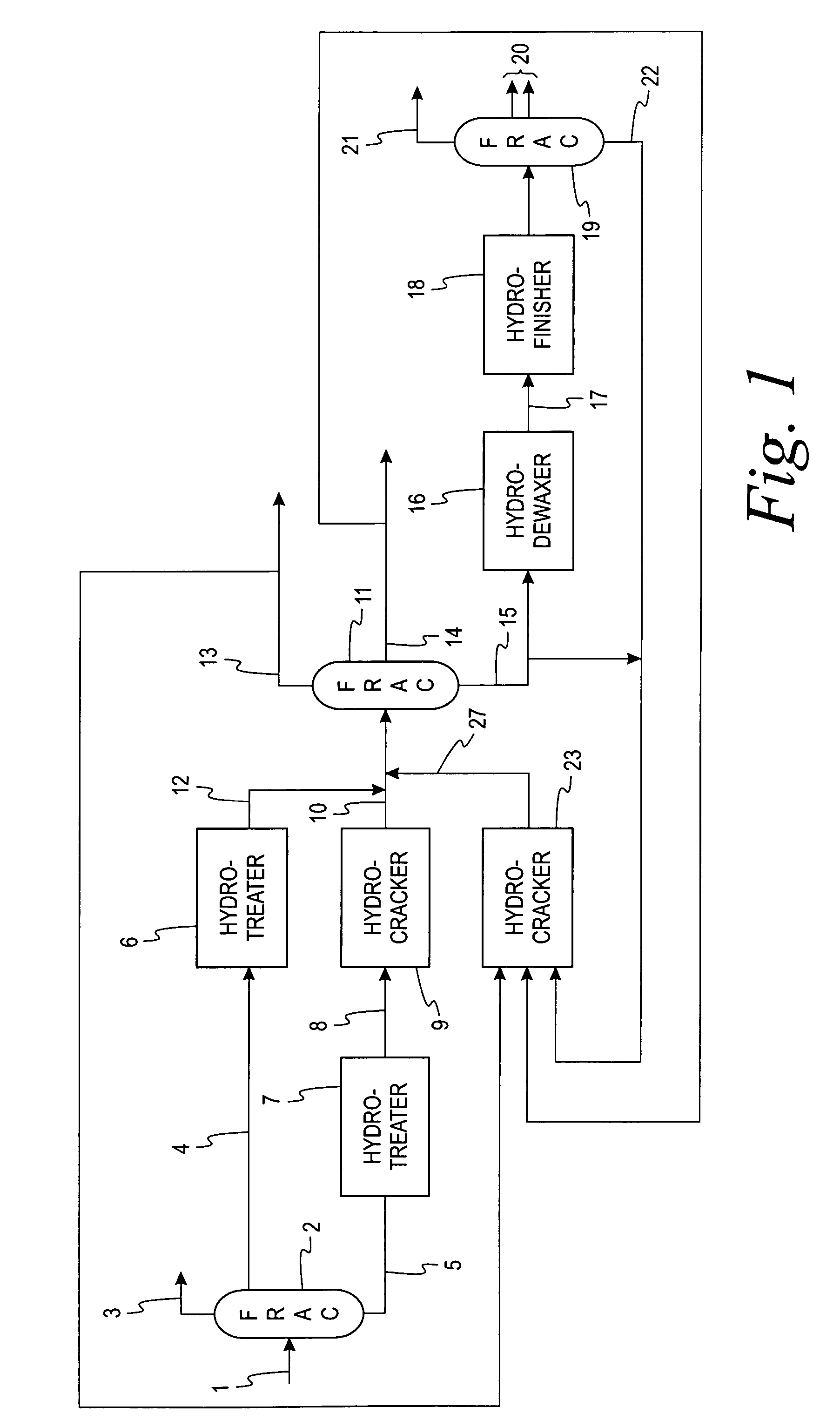
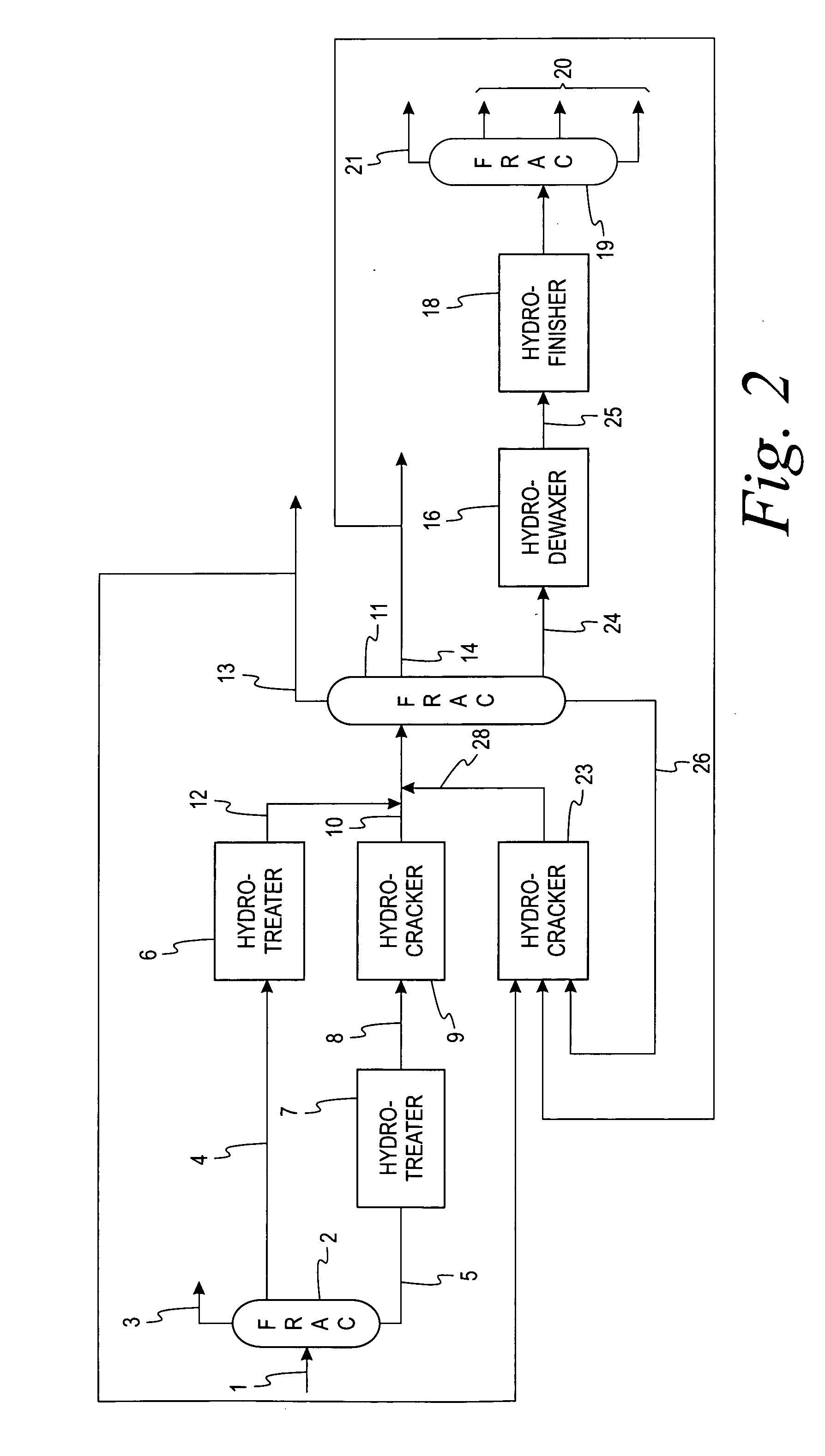
High severity, low conversion hydrocracking process
InactiveUS6294079B1Hydrocarbon oil crackingTreatment with hydrotreatment processesReaction zoneHigh pressure
A feed stream is first processed in a hydrotreating reaction zone and then the effluent is separated into three fractions in an augmented first high pressure separator. Controlled portions of the middle and heavy hydrocarbon fractions are passed into a high severity hydrocracking zone, while the remaining portions of these two fractions are passed into a second high pressure separator for recovery. The effluent of the hydrocracking zone is also fed to the second high pressure separator.
Owner:UOP LLC
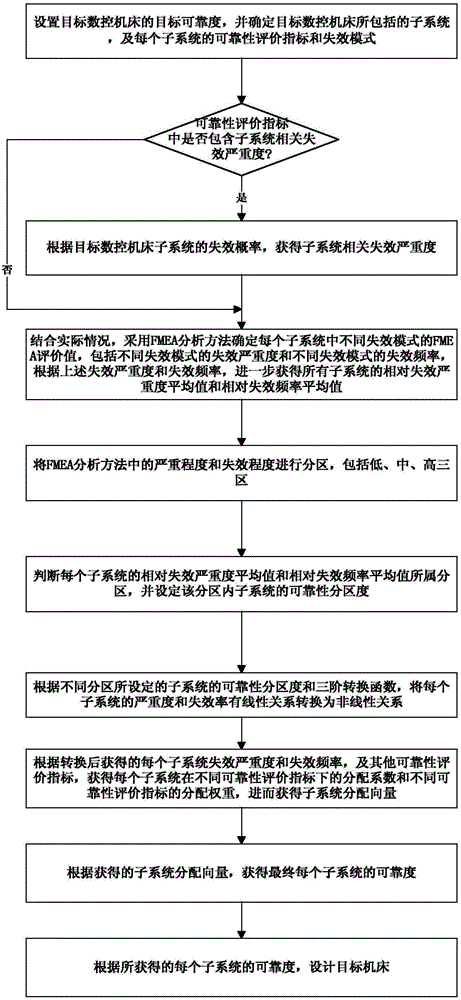
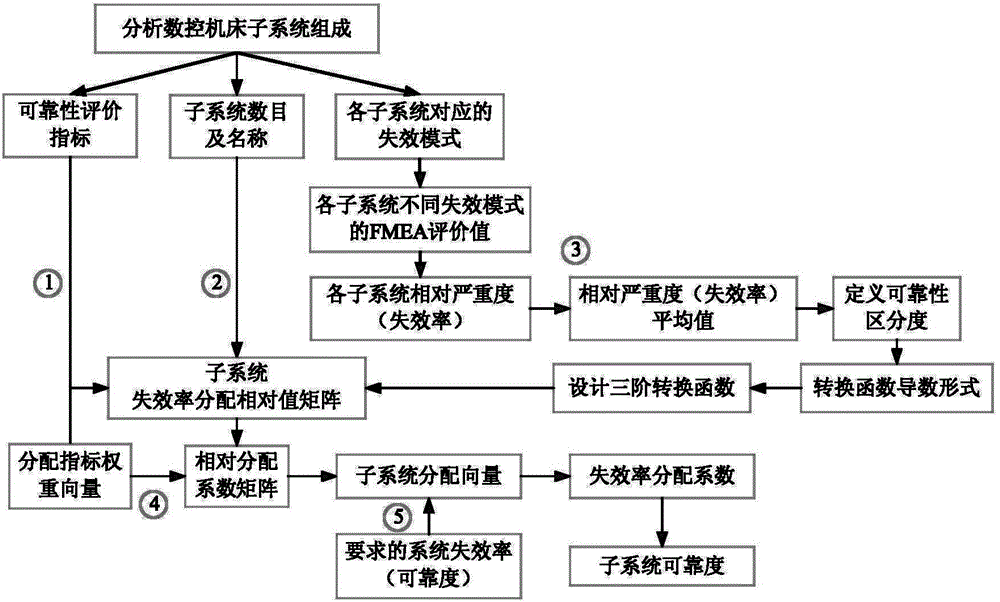
FMEA analysis based comprehensive reliability allocation method for numerical control machine tool
ActiveCN104992011AWell formedEasy to understandSpecial data processing applicationsNumerical controlDistribution method
The invention discloses an FMEA analysis based comprehensive reliability allocation method for a numerical control machine tool, and belongs to the field of mechanical system reliability analysis. According to the method, the comprehensive reliability allocation for a system is carried out based on an FMEA three-order conversion function and a Copula function, so that the problems of a single consideration factor, only capability of regulating reliability differentiation degree of high severity or failure frequency, and the like in an existing machine tool reliability allocation method are solved; the conversion function in the method is simple in form and easy to understand and operate, covers the advantages of a conventional index conversion function and extends reliability differentiation degree regulation capability of a low interval and a medium interval of an FMEA analysis result; the method considers influence of various allocation indexes and fault correlation effects at the same time, and has the characteristics of good integrity and convenience for engineering application; and compared to a conventional method, the subsystem reliability obtained by analysis with the method is lower, the manufacturing and processing cost requirements can be better lowered, and very important engineering value is achieved.
Owner:NORTHEASTERN UNIV
FCC process combining molecular separation with staged conversion
InactiveUS20060231459A1Thermal non-catalytic crackingSemi-permeable membranesReaction zoneDiesel fuel
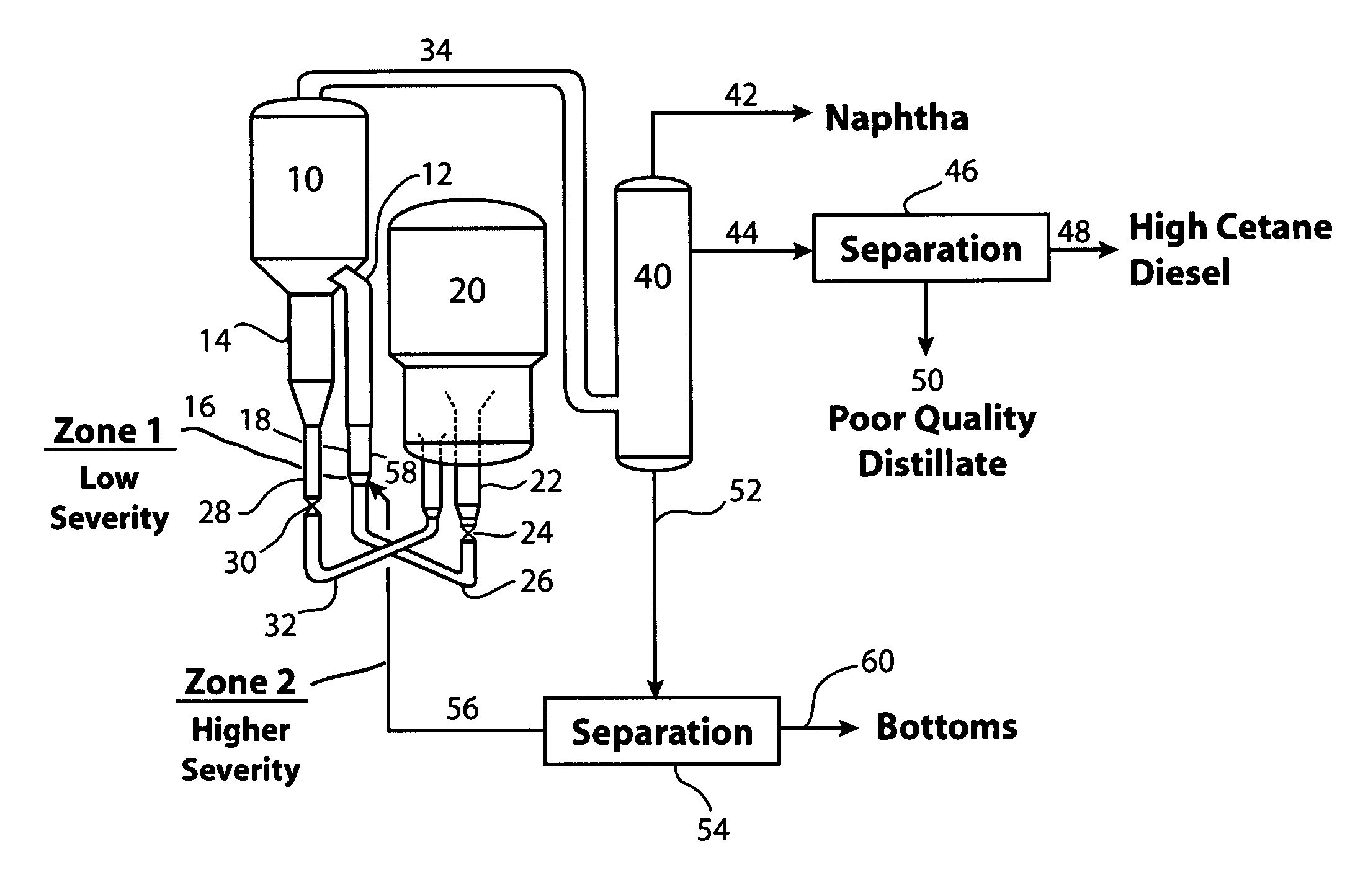
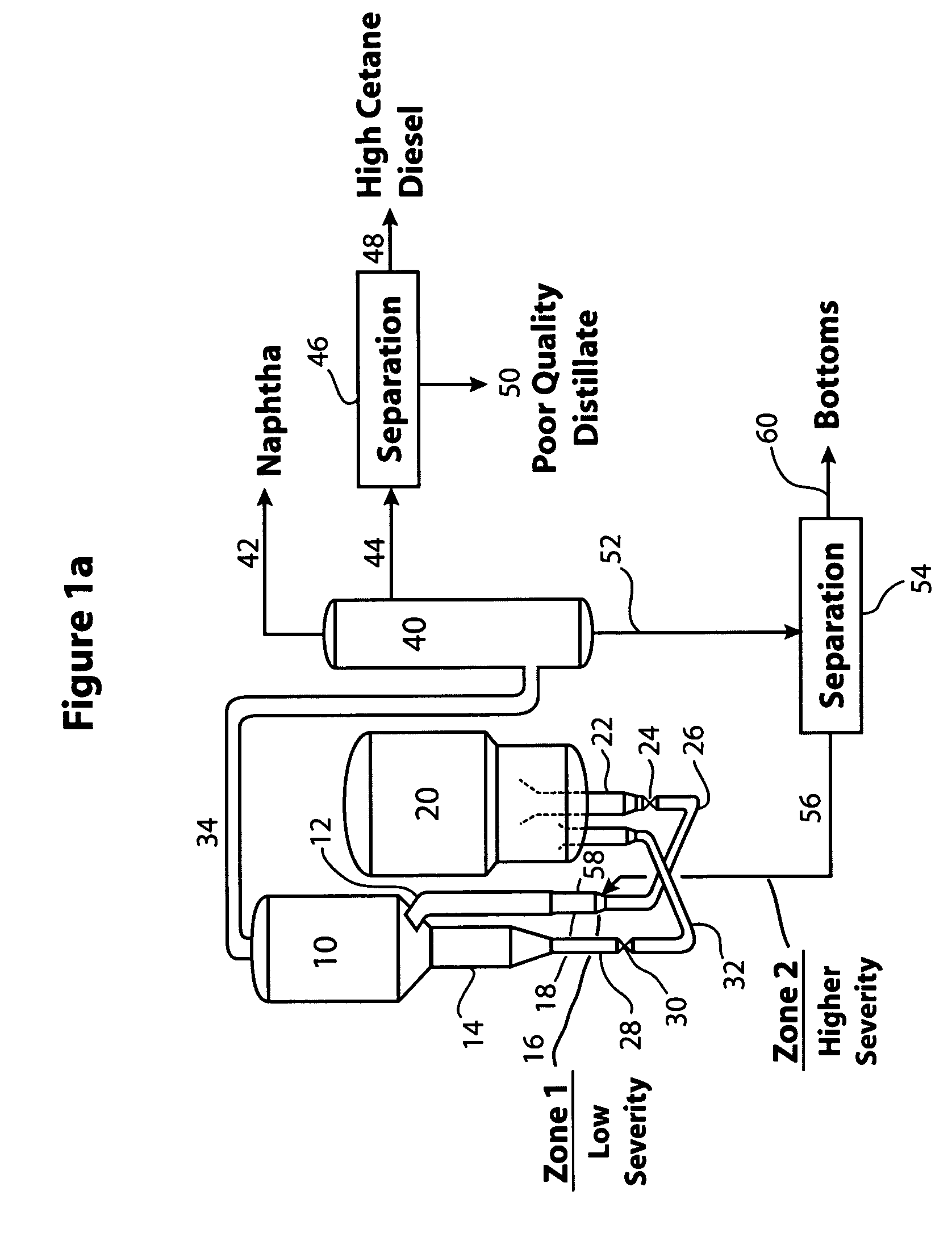
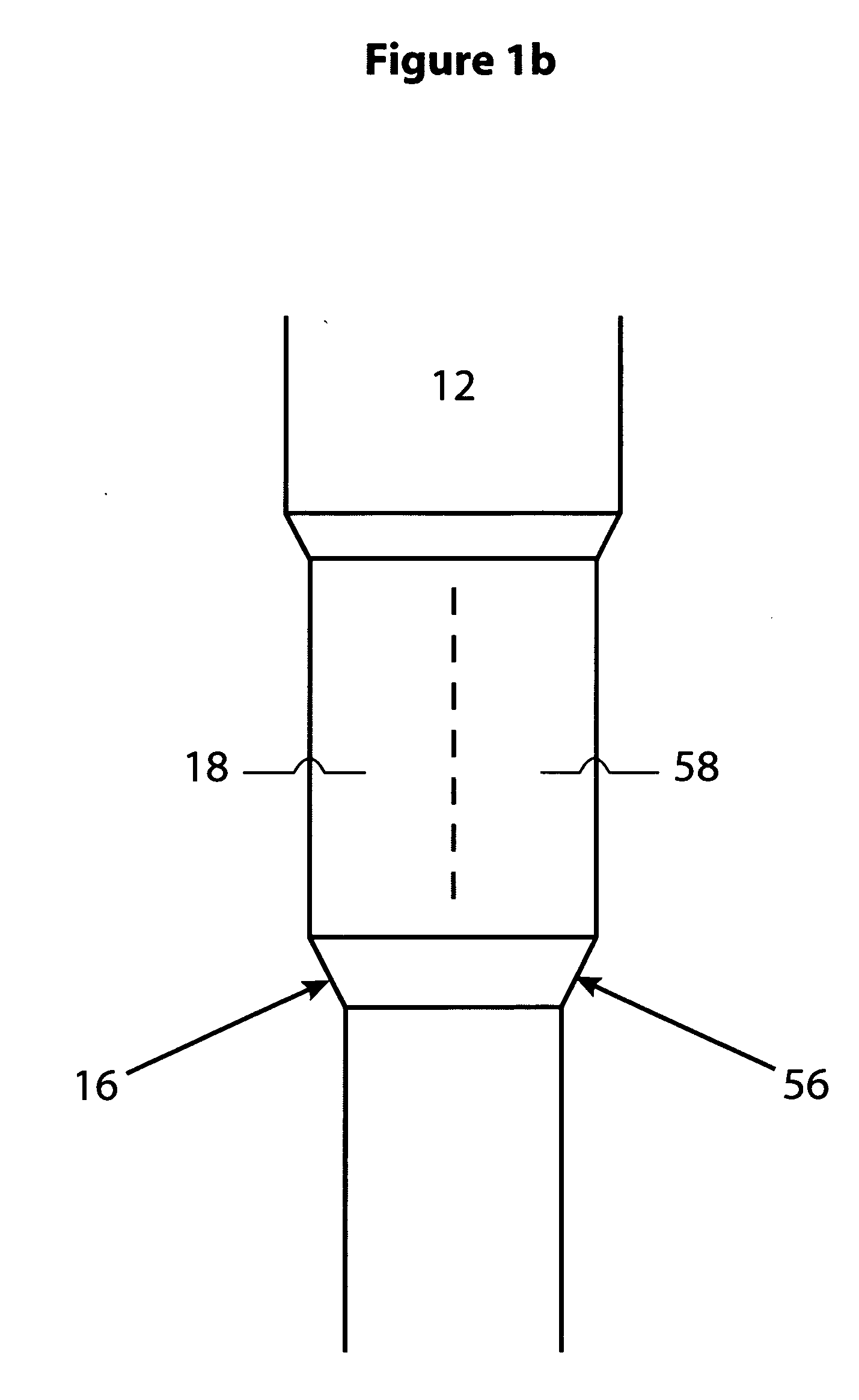
This invention relates to fluid catalytic cracking (FCC) process for improving the quality of distillates suitable as blend stocks for diesel fuels. The FCC process combines staging the FCC conversion process with interstage molecular separation of multi-ring aromatic species. Lower and higher severity reaction zones in the riser of the FCC reactor are combined with selective molecular separations to improve the production of diesel quality distillates.
Owner:EXXON RES & ENG CO
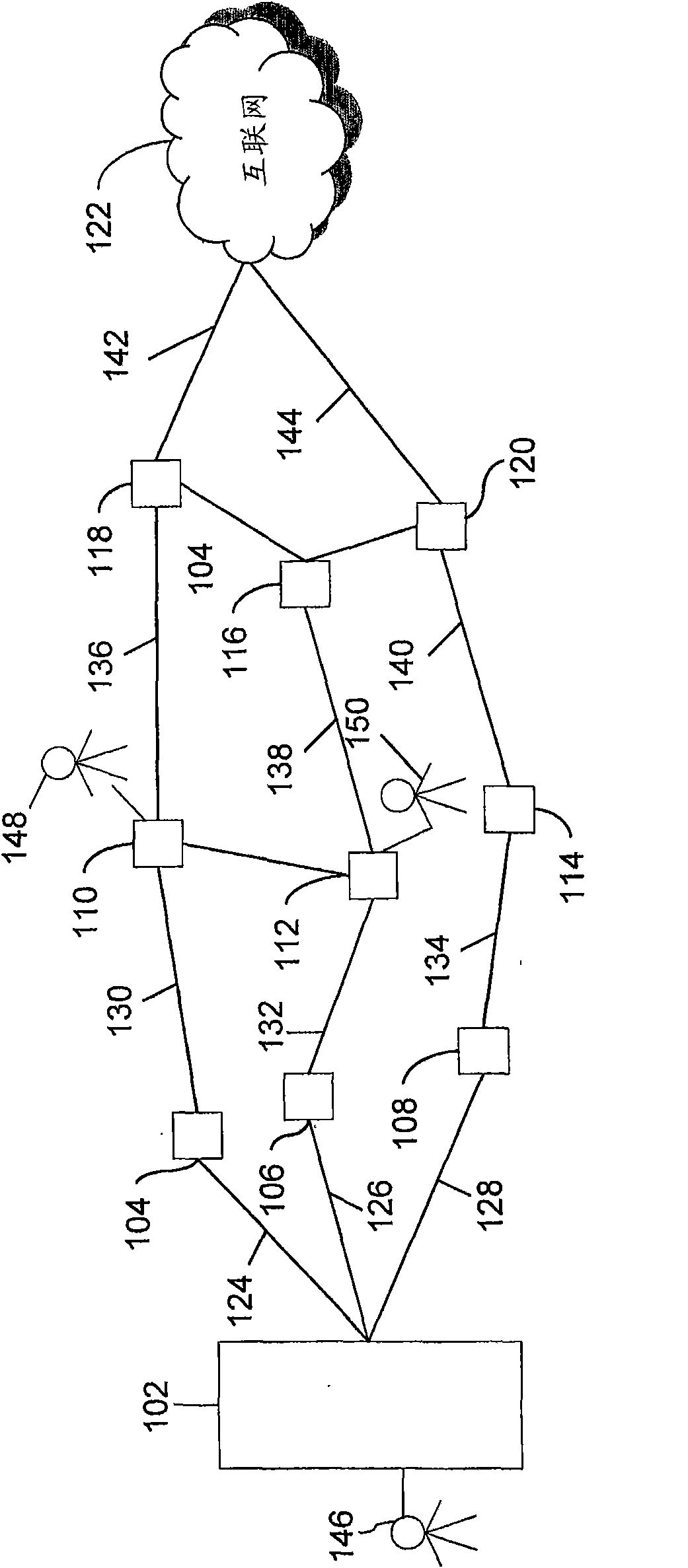
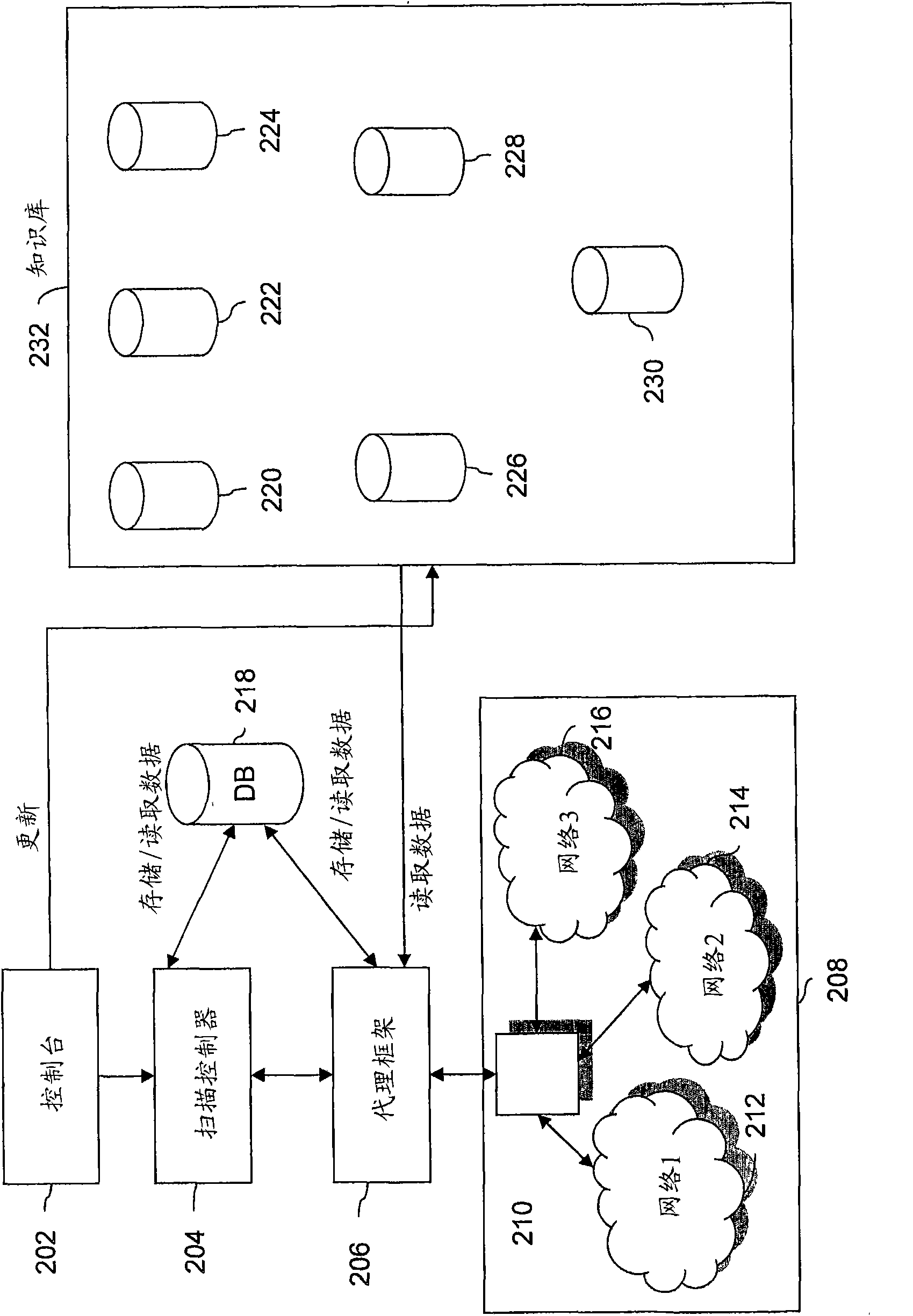
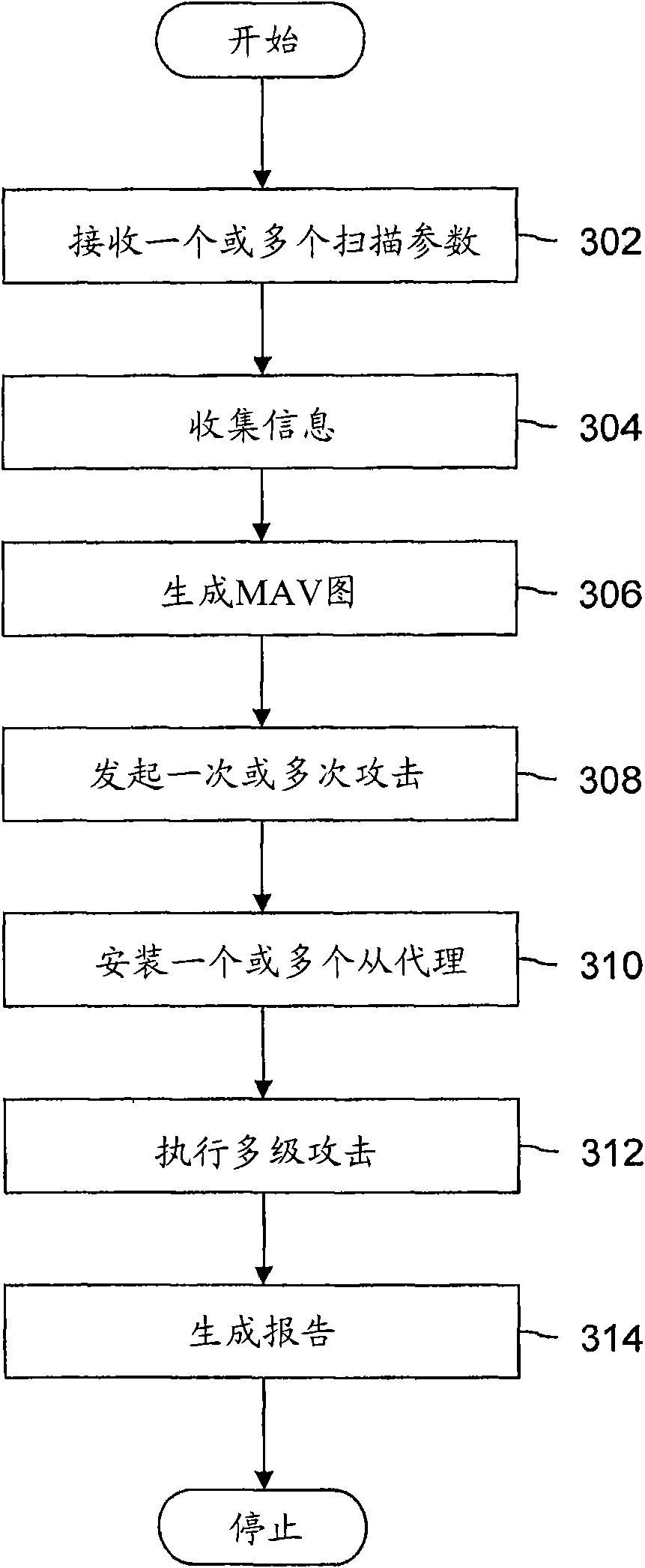
Method and system for simulating a hacking attack on a network
InactiveCN101682626AComputer security arrangementsTransmissionCommunication linkDistributed computing
The present invention describes a method for simulating a hacking attack on a Network, wherein the Network comprises at least one of a plurality of data processing units (DPUs), a plurality of users and a plurality of communication links, to assess vulnerabilities of the Network. The method includes receiving one or more scan parameters for the Network. Further, the method includes creating at least one master agent by a system to gather information about the Network, wherein the information pertains to critical and non-critical information about the Network. The method includes creating an Information Model and then incrementally updating the Information Model during the hacking attack. The Information Model is the abstract representation of information collected by the system. Furthermore, the method includes generating a Multiple Attack Vector (MAV) graph based on one or more scan parameters and the Information Model. MAV has the ability to combine plurality of low and medium severity vulnerabilities associated with the data processing units (DPUs), users and communication links, correlate vulnerabilities in combination with Information Model and generate high severity attack paths that can lead to compromise of the Network. Moreover, the method includes launching one or more attacks based on the MAV graph to compromise the Network. The method further includes installing atleast one slave agent on the compromised Network to perform the one or more attacks in a distributed manner. Moreover, the method includes performing a multi stage attack by using the at least one slave agent and the at least one master agent by repeating above steps. Finally, the method includes generating a report by the scan controller, wherein the report contains details about the compromisedNetwork and the vulnerabilities of the Network.
Owner:IVIZ TECHNO SOLUTIONS PVT
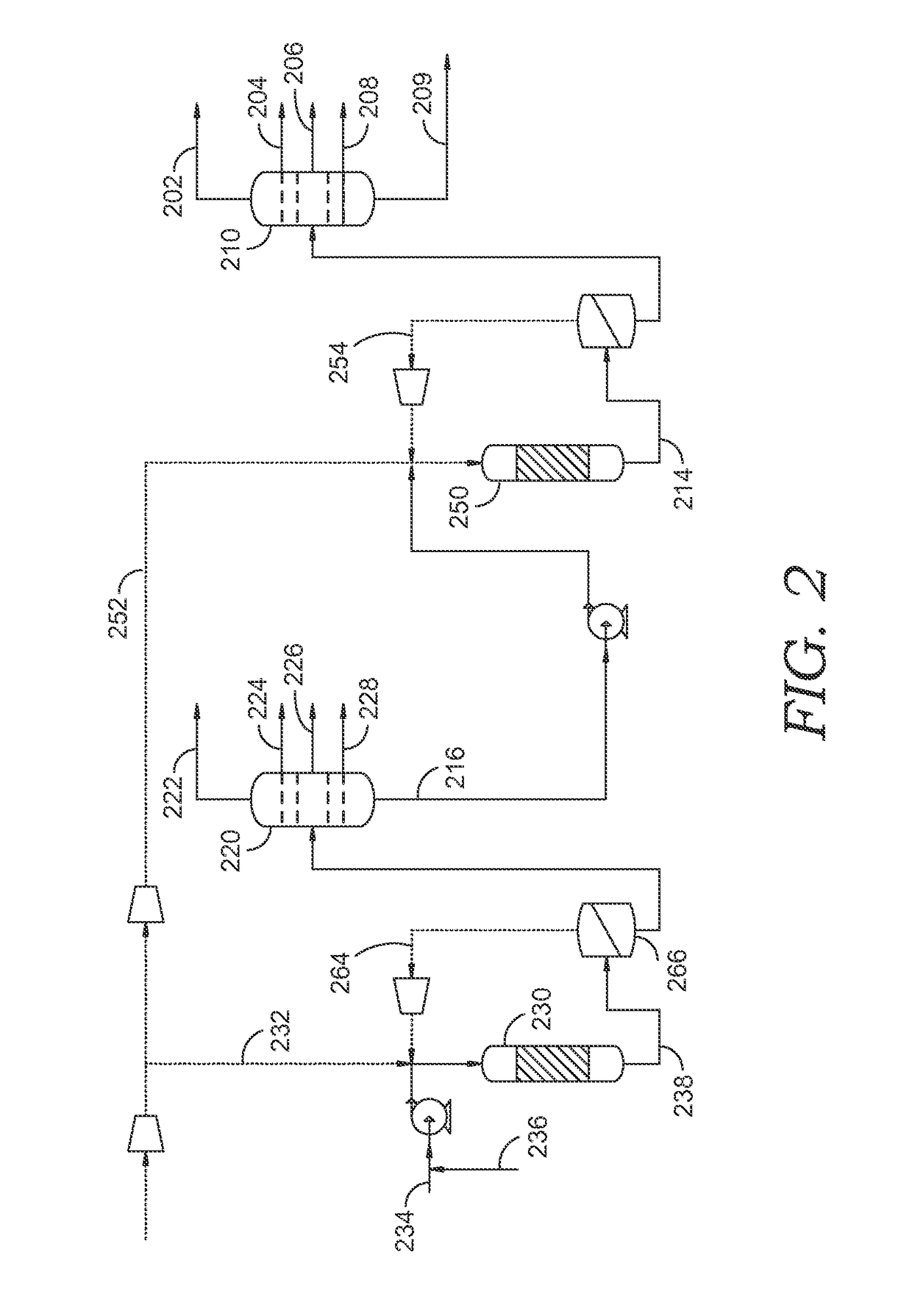
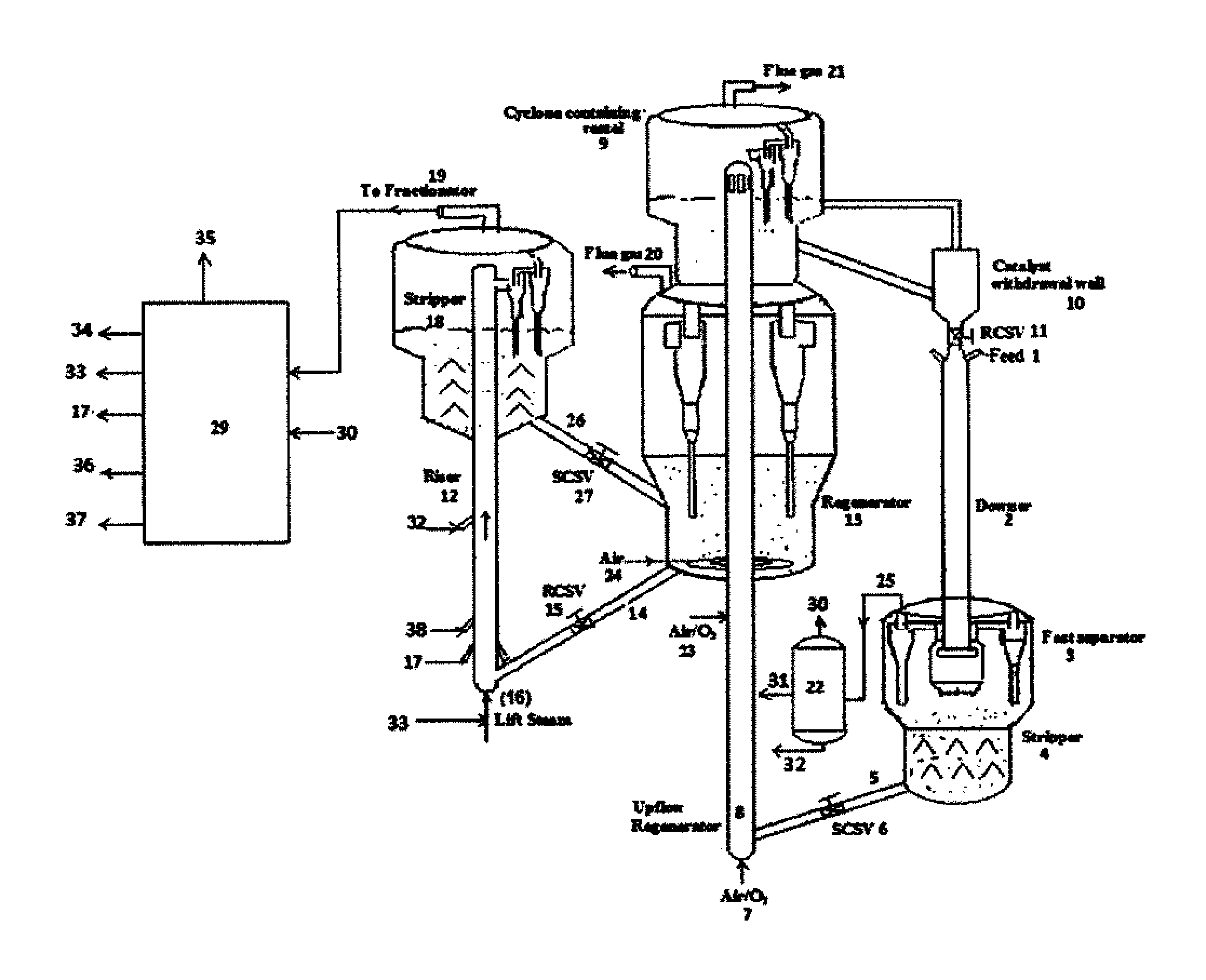
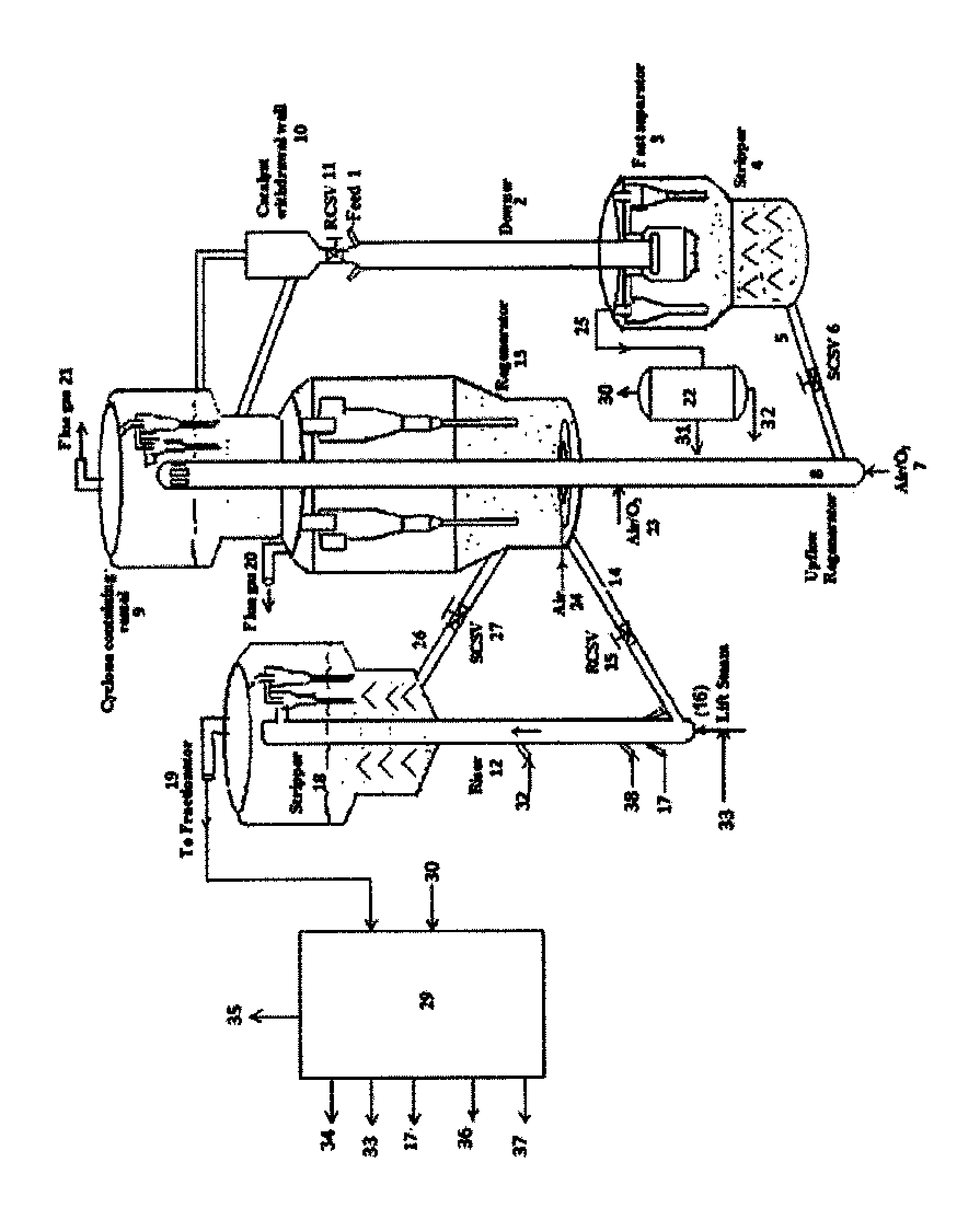
Process for high severity catalytic cracking of crude oil
ActiveUS9290705B2Maximize productionCatalytic crackingTreatment with plural parallel cracking stages onlyBoiling pointChemistry
In an FCC process and system, a whole crude oil feedstock is directly converted into light olefins and other products. The feed is separated into a high boiling fraction and a low boiling fraction, and each fraction is processed in separate FCC downflow reactors. The catalyst, combined from both downflow reactors, is regenerated in a common vessel. The low carbon content in the catalyst particles from the low boiling fraction downflow reactor is insufficient to provide the necessary heat. By combining catalyst particles from the high boiling fraction having high carbon content helps to provide additional heat for regeneration.
Owner:SAUDI ARABIAN OIL CO
Process for maximum distillate production from fluid catalytic cracking units (FCCU)
InactiveUS20130130889A1Easy to crackIncrease severityCatalytic crackingLiquid hydrocarbon mixture productionNaphthaHydrocarbon
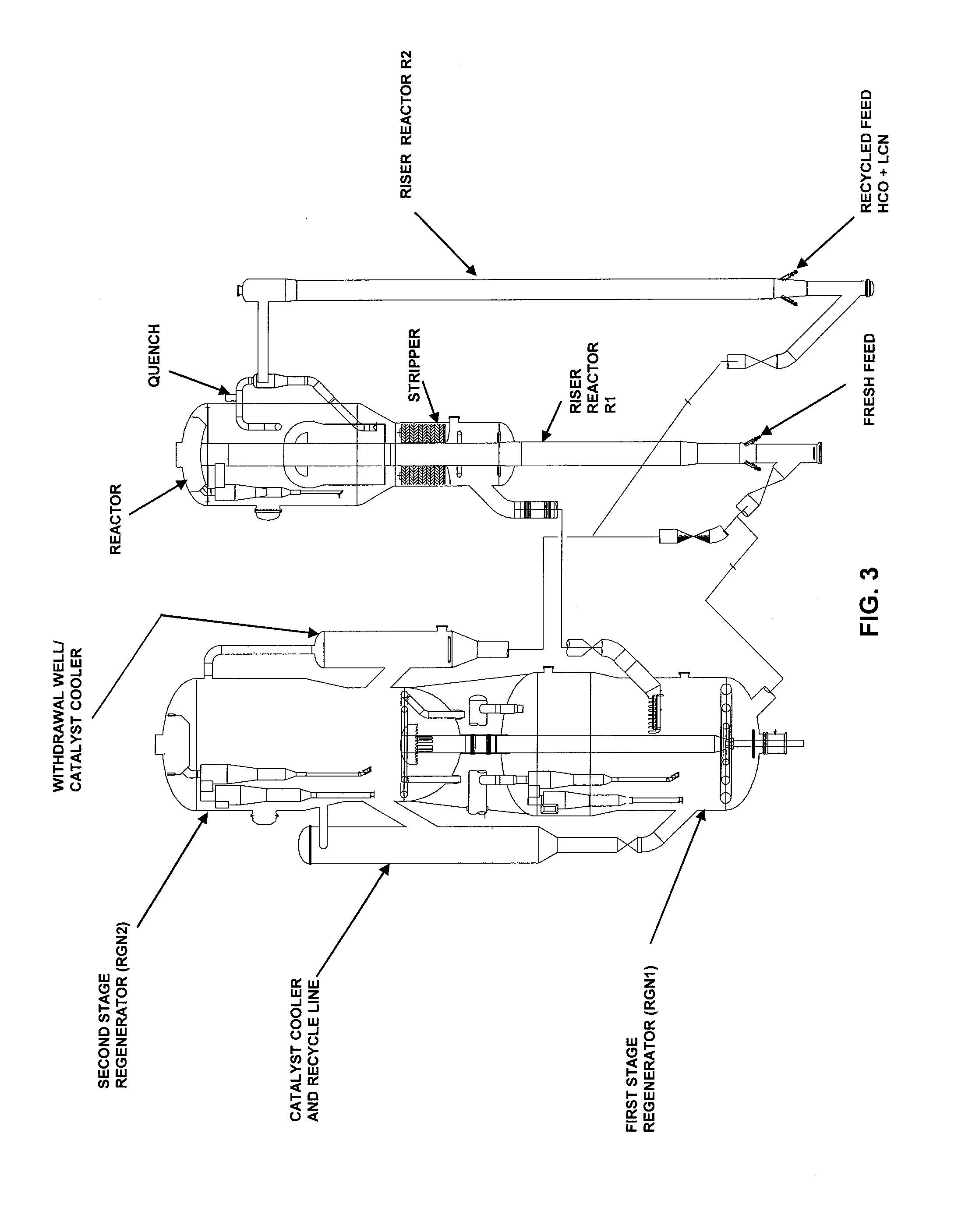
The present invention provides an improved fluidized catalytic cracking process coupled with a two stage regeneration process in which the activity of the circulating catalyst is independently controlled for cracking hydrocarbon feedstocks or the vapors at low severity to produce maximum light cycle oil / distillate in one riser whilst cracking recycle streams comprising heavy cycle oil (HCO), light cracked naphtha (LCN) etc. in a second riser operating at high severity to produce LPG.
Owner:TECH PRECESS TECH INC
Dynamic adaptation to congestion in connection-oriented networks
InactiveUS7127056B2Network resources are more efficiently utilizedAvoid areaError preventionTransmission systemsDistributed computingNetwork congestion
Dynamic adaptation of connection-oriented networks is introduced wherein, once congestion is encountered, dynamic adaptation steps may be performed. Four adaptation steps are proposed for reacting to various network congestion scenarios. It is further recommended that the steps are performed in a particular order such that the higher severity and longer sustentation of the network congestion the more strict step is performed to alleviate the network congestion. At a switch in the connection-oriented network, utilization of a trunk carried on a link connected to the switch is monitored and, if said utilization of said trunk exceeds a first threshold, a first degree of adaptation is initialized wherein use of the trunk by further connections is prevented. Subsequent degrees of adaptation are triggered when high utilization continues and surpasses higher thresholds. The subsequent degrees of adaptation involve rerouting connections that make use of the trunk.
Owner:CIENA
Systems and methods for making a middle distillate product and lower olefins from a hydrocarbon feedstock
InactiveUS20100163455A1Speed up the conversion processTreatment with plural serial cracking stages onlyCatalytic crackingHydrocarbonChemistry
A system comprising a riser reactor comprising a gas oil feedstock and a first catalyst under catalytic cracking conditions to yield a riser reactor product comprising a cracked gas oil product and a first used catalyst; a intermediate reactor comprising at least a portion of the cracked gas oil product and a second catalyst under high severity conditions to yield a cracked intermediate reactor product and a second used catalyst; wherein the intermediate reactor feedstock comprises at least one of a fatty acid and a fatty acid ester.
Owner:SHELL OIL CO
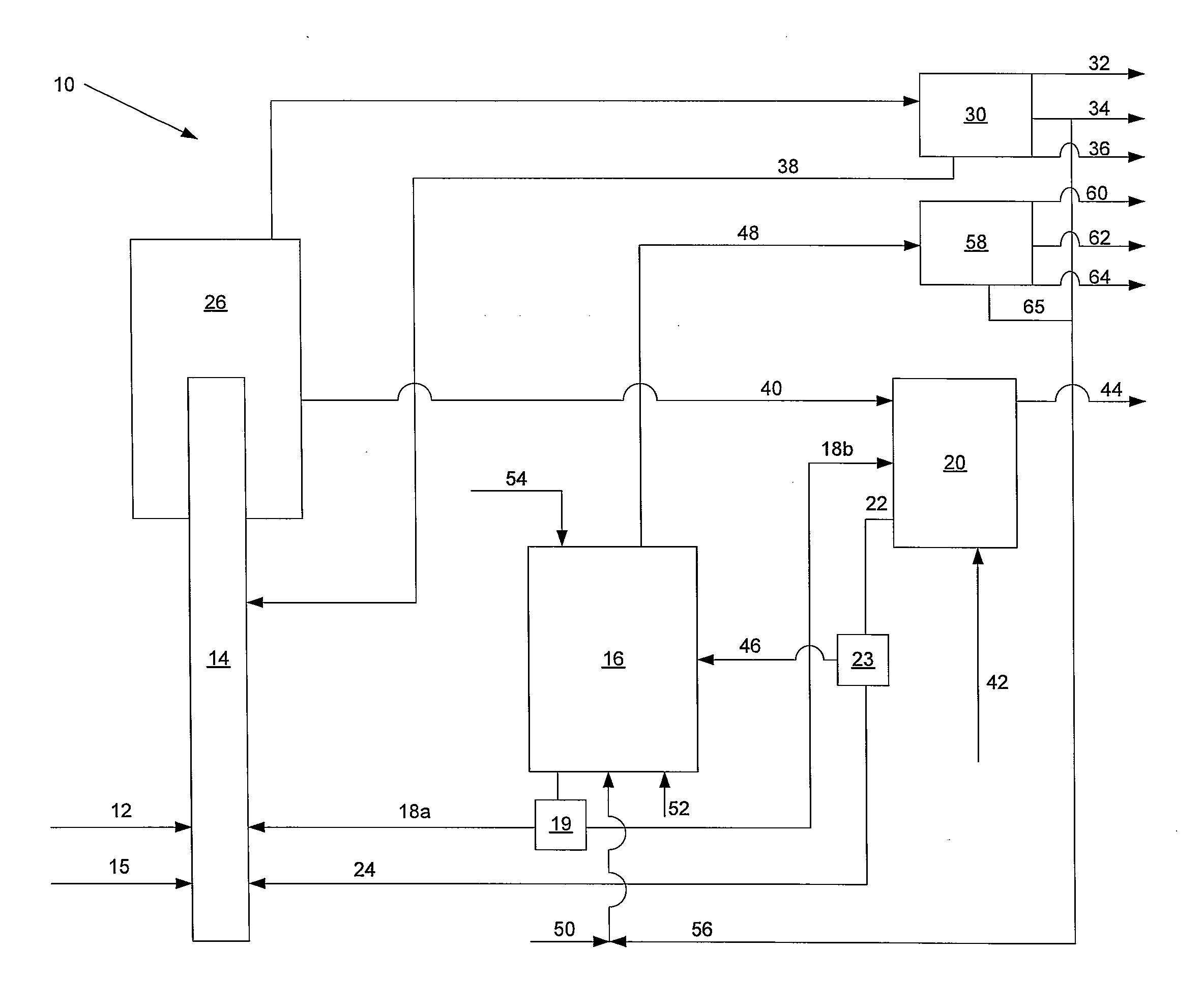
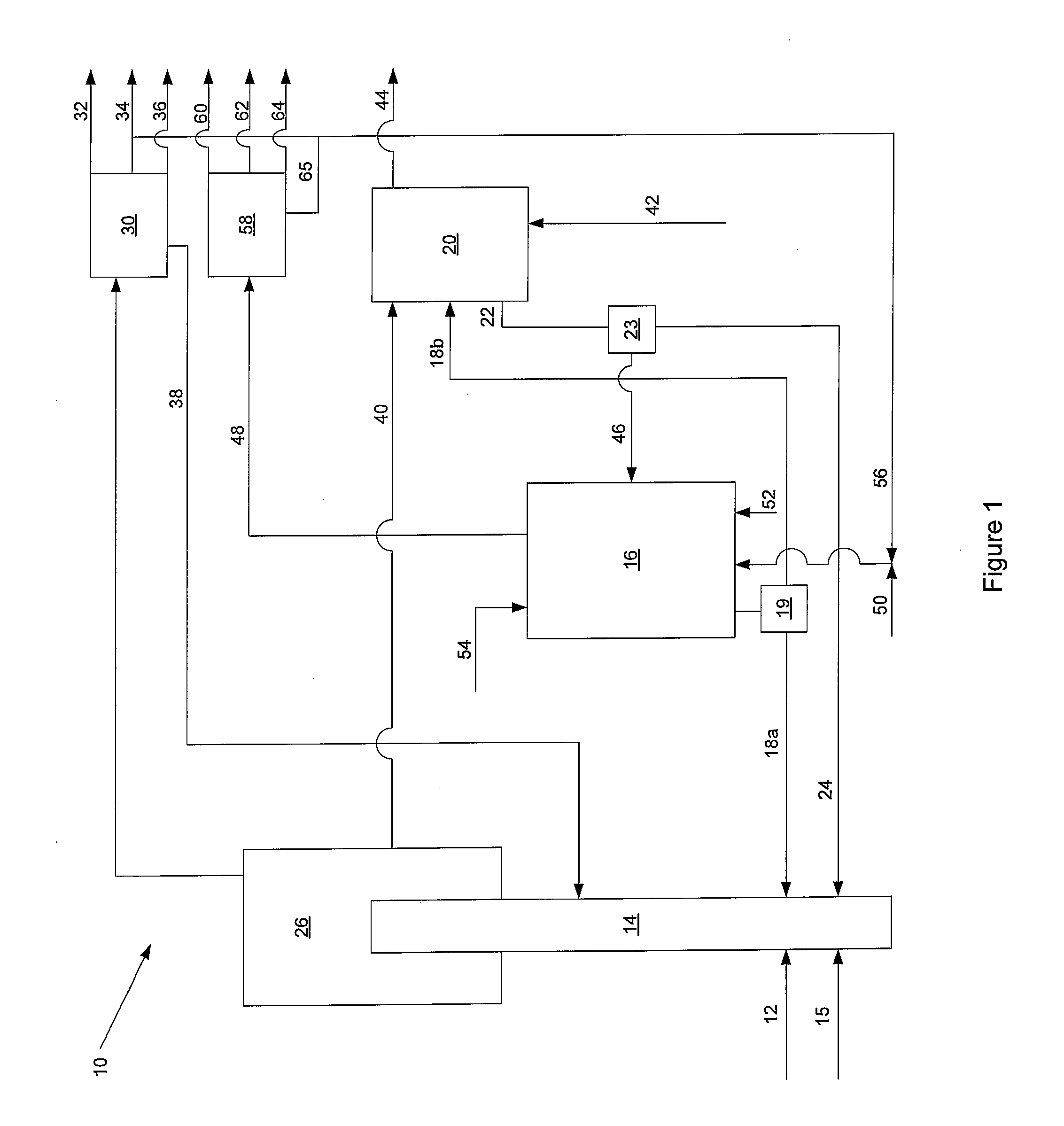
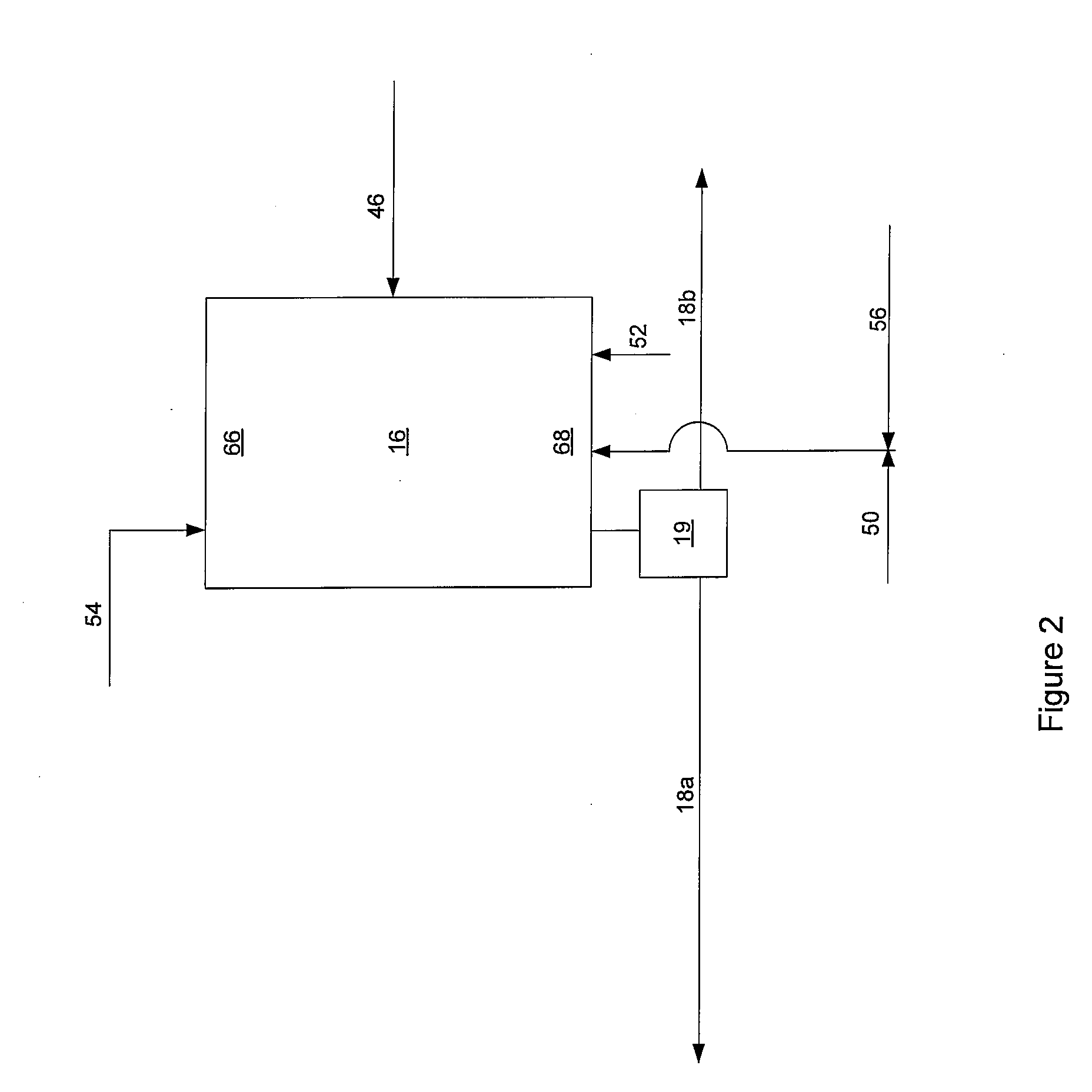
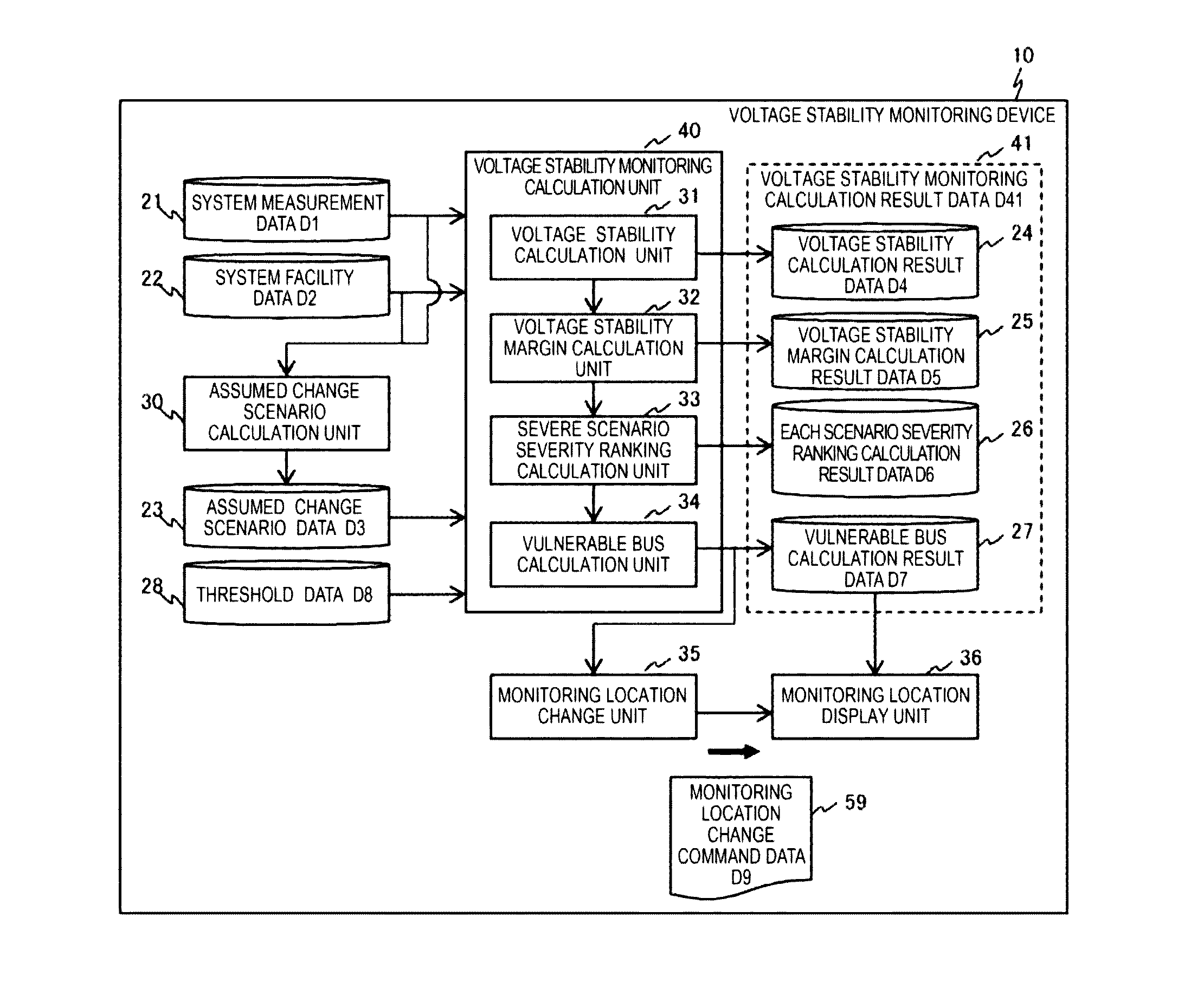
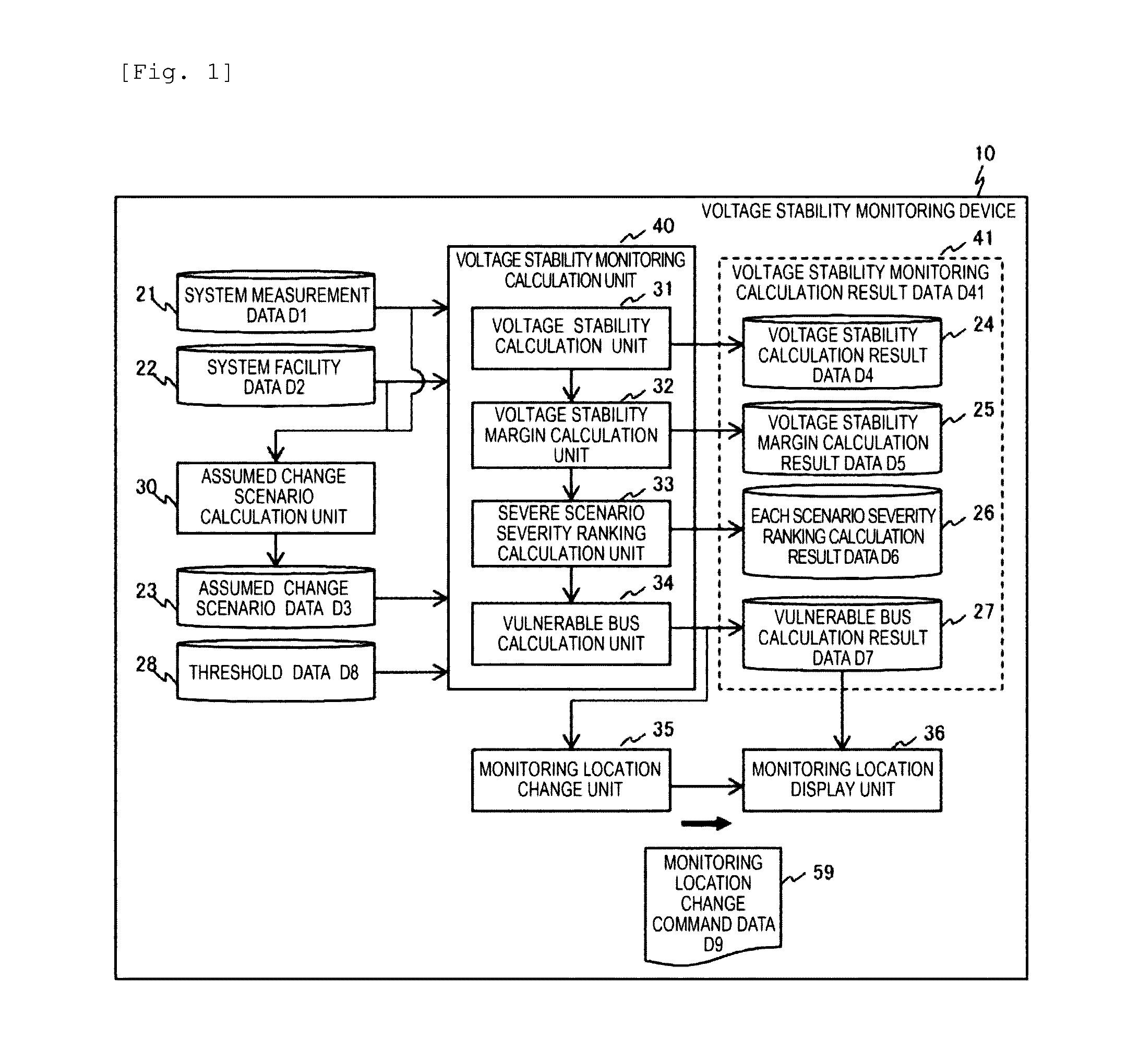
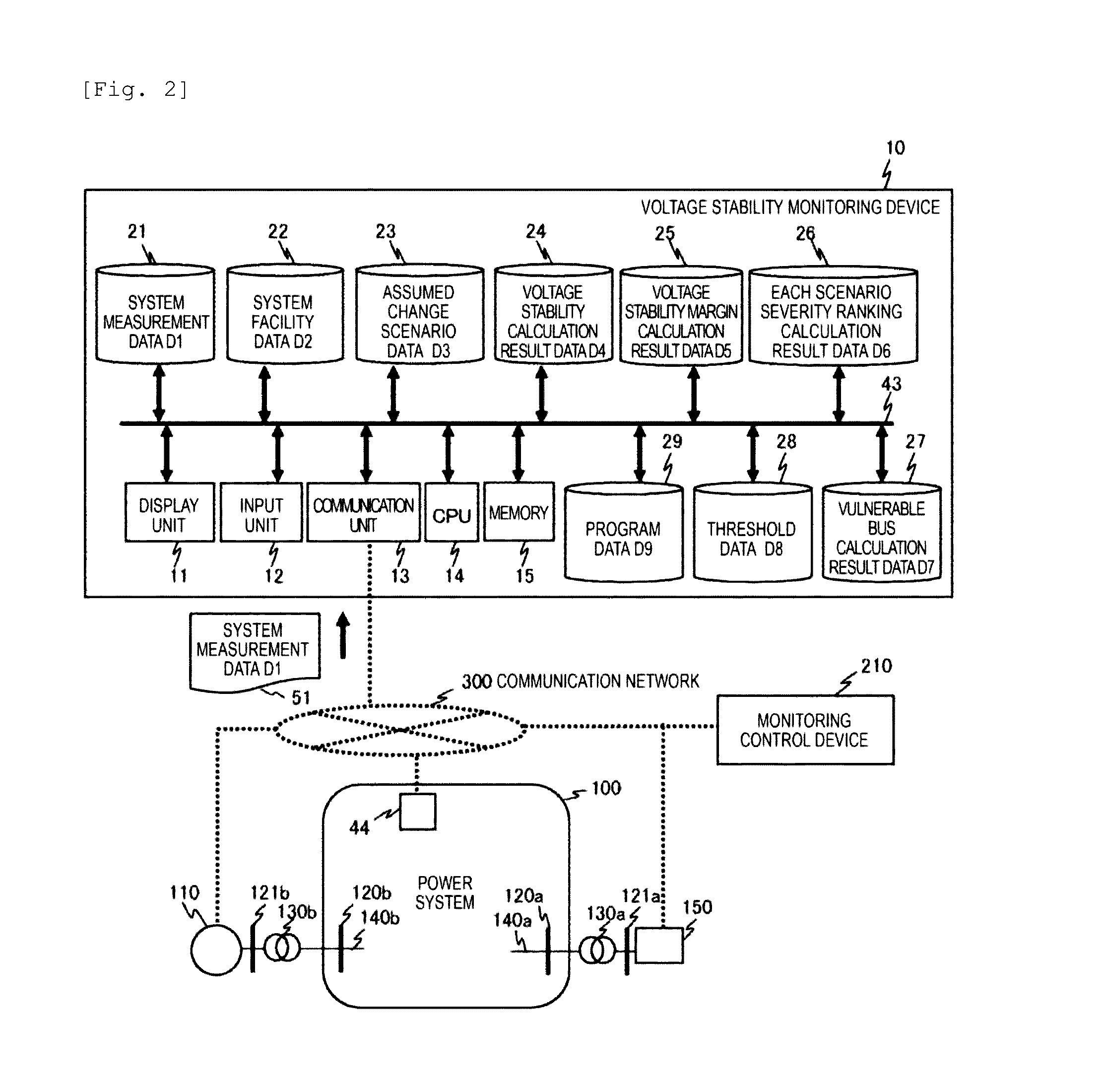
Voltage Stability Monitoring Device and Method
ActiveUS20170045558A1Accurate monitoringReduce effortPower oscillations reduction/preventionVoltage measurements onlyElectric power systemEngineering
An object is to accurately monitor deterioration of current or future voltage stability, by dynamically changing a bus in which current or future voltage stability deteriorates, in stability monitoring calculation of a power system. Hence the present invention provides a voltage stability monitoring device, which monitors voltage stability of a power system, including an assumed change scenario calculation unit which produces a plurality of assumed change scenarios indicating a scenario of a change that is assumed based on at least one of a system configuration of the power system and a change of a tide state; a voltage stability calculation unit which calculates the voltage stability using the assumed change scenario; a voltage stability margin calculation unit which calculates a voltage stability margin indicating margin degree of the voltage stability, based on the voltage stability; an each scenario severity ranking calculation unit which selects an assumed change scenario with high severity of the voltage stability for each assumed change scenario, based on the voltage stability margin; a vulnerable bus calculation unit which calculates which of buses in the power system is a vulnerable bus that decreases voltage stability, based on the assumed change scenario which is selected; and a monitoring location change unit which changes a monitoring target of the voltage stability, based on information of the vulnerable bus.
Owner:HITACHI LTD
Process for producing a high stability desulfurized heavy oils stream
InactiveUS20100155298A1Improve desulfurizationImprove solubilityRefining with metalsTransportation and packagingFuel oilMetal
The present invention relates to a process for desulfurizing heavy oil feedstreams with alkali metal compounds and improving the compatibility of the to stream components in either the feed stream, an intermediate product stream, and / or the reaction product stream in the desulfurization process. The present invention utilizes a high stability aromatic-containing stream that is preferably added to the heavy oil prior to reaction with the alkali metal compounds. The resulting stream resists precipitation of reaction solids in the desulfurization reactors. Even more preferably, the desulfurization system employs at least two desulfurization reactors in series flow wherein the high stability aromatic-containing stream is contacted with the reaction product from the first reactor prior to the second reactor, wherein the first reactor can be operated at a higher severity than without the use of the high stability aromatic-containing component stream.
Owner:EXXON RES & ENG CO
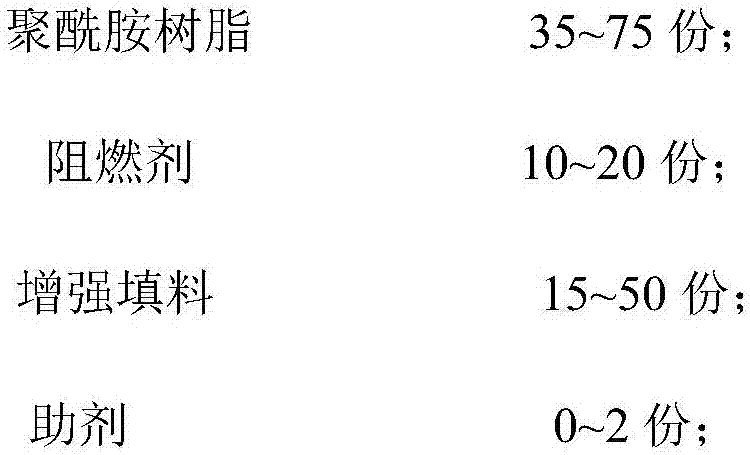
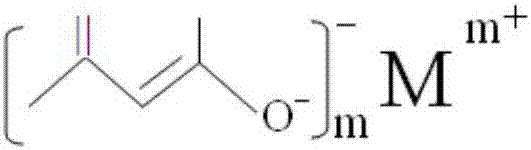
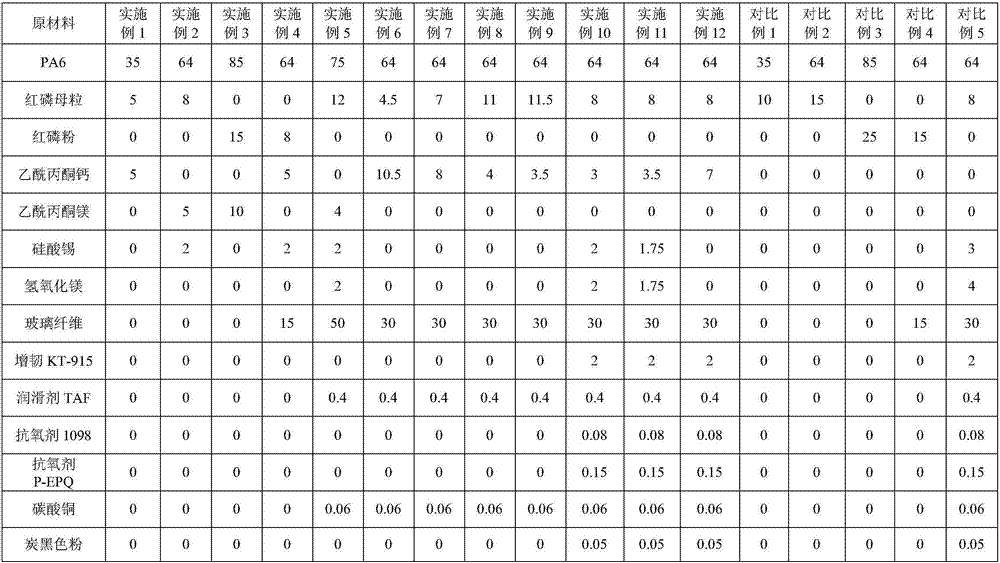
Flame-retardant polyamide composite material
The invention relates to the field of high-molecular materials, in particular a flame-retardant polyamide composite material. The flame-retardant polyamide composite material provided by the invention is prepared from the following components in parts by weight: 35 to 85 parts of polyamide resin and 10 to 25 parts of flame retardant, wherein the flame retardant is prepared from a red phosphorus flame retardant and a synergistic flame retardant; the synergistic flame retardant is an acetylacetone metal salt or a mixture of the acetylacetone metal salt and magnesium hydrate or / and silicate; the acetylacetone metal salt accounts for more than or equal to 40 percent by weight of the mixture. The flame-retardant polyamide composite material provided by the invention has excellent flame retardance security: the flame retardant rating can reach a 0.8mm UL94V-0 level; the ignition risk is low, the glowing filament combustion index can reach a highest severity level (960 / 0.75), and the glowing filament time is less than or equal to 15s; meanwhile, the initiation temperatures of glowing filaments of three thicknesses (3.0mm, 1.5mm and 0.75mm) can be up to the severity level of 750 DEG C.
Owner:BENSONG ENG PLASTICS HANGZHOU
State evaluation method of hydropower plant computer monitoring system
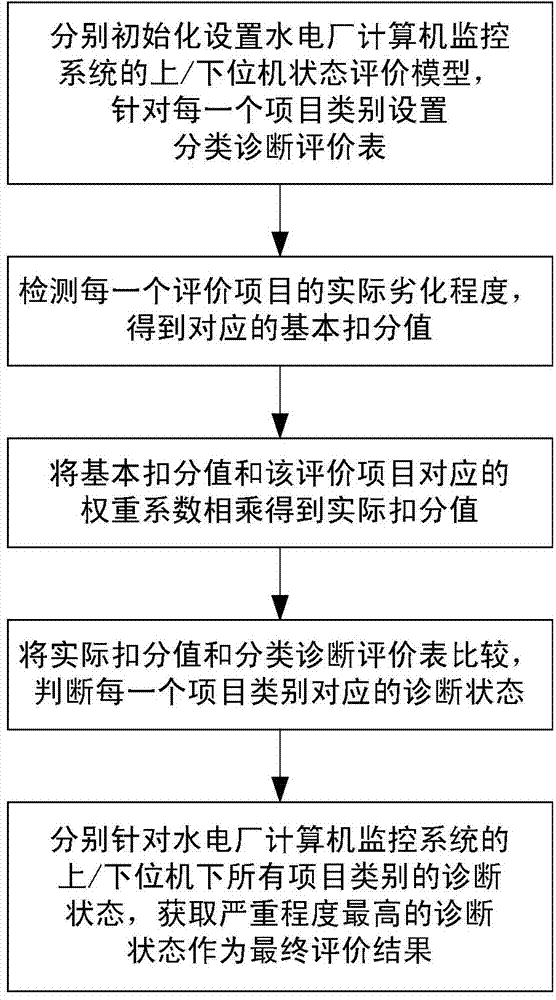
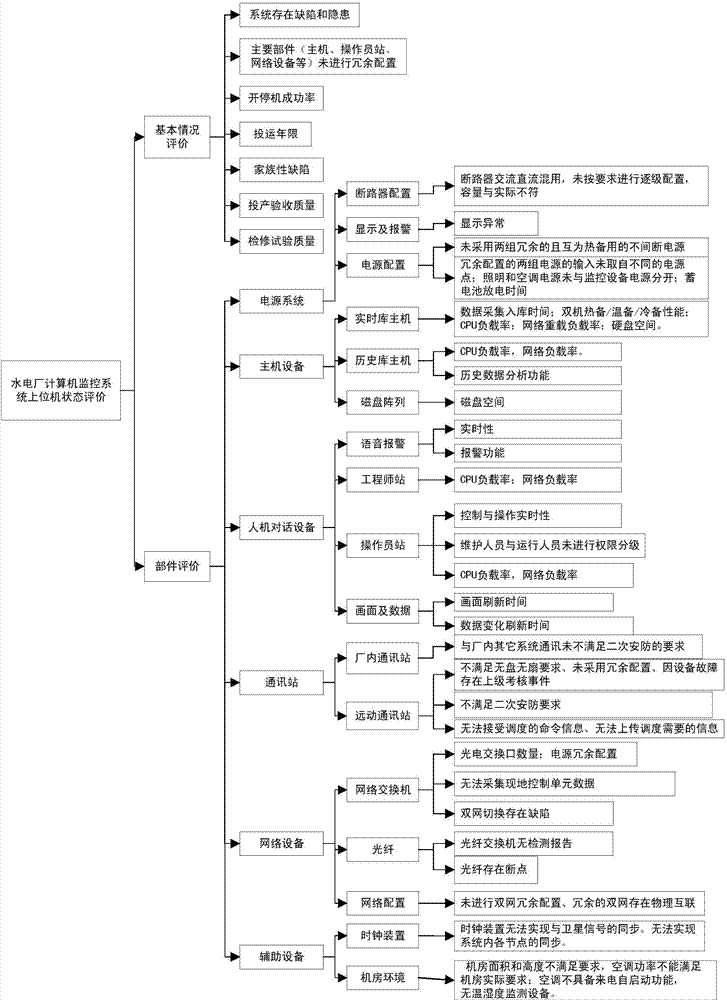
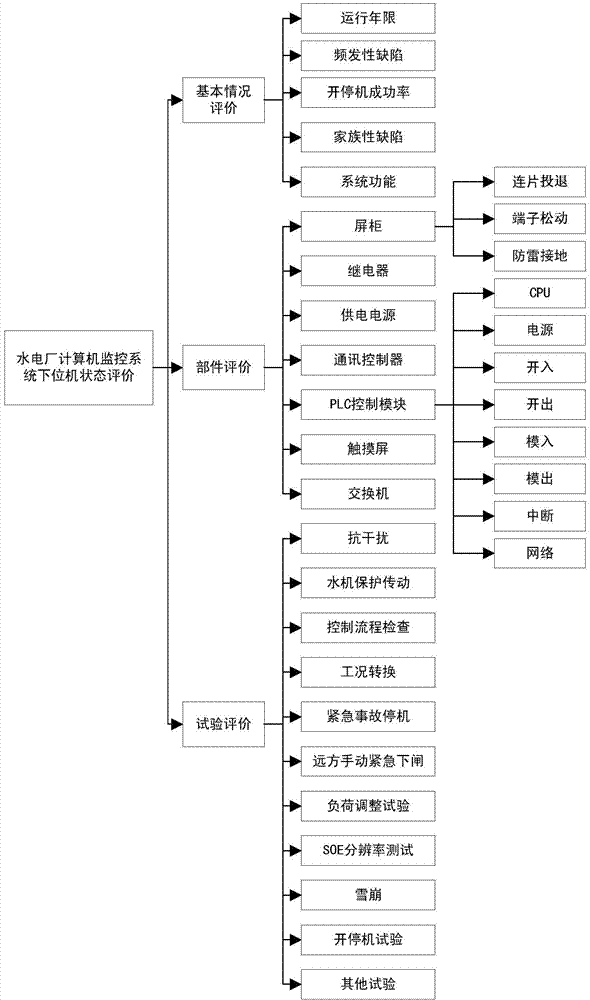
ActiveCN104331042AComprehensive evaluation of operating statusSafe and stable operationTesting/monitoring control systemsTotal factory controlEvaluation resultWeight coefficient
The invention discloses a state evaluation method of a hydropower plant computer monitoring system. The method comprises a step of respectively initiating an upper computer state evaluation model and a lower computer state evaluation model which are provided with hydropower plant computer monitoring systems and establishing the corresponding classification diagnosis evaluation table, respectively detecting the actual degradation degree of each evaluation program and obtaining a basic deduction value, and multiplying the basic deduction value with the weight coefficient corresponding to the evaluation program to obtain the actual deduction value of the evaluation program, a step of comparing the actual deduction value of each evaluation program in each program classification with the classification diagnosis evaluation table and judging the diagnosis state corresponding to each program classification, and a step of obtaining the diagnosis state with the highest severity degree as the final evaluation result of the upper computer / lower computer of the hydropower plant computer monitoring system. According to the state evaluation method, the running state of the hydropower plant computer monitoring system can be comprehensively evaluated, the influence on a hydropower plant and even the stable operation of a power system by fault expansion is prevented, and the examination and maintenance cost can be greatly reduced.
Owner:STATE GRID CORP OF CHINA +2
Rubber composition for tire, and pneumatic tire
InactiveUS20140005319A1Balanced improvement in abrasion resistanceReduce the heating effectHeavy duty tyresHeavy duty vehiclePolymer scienceWear resistance
The invention aims to provide a rubber composition for a tire which achieves a balanced improvement in the abrasion resistance under both low and high severity abrasion conditions, low heat build-up properties, and chipping resistance. The invention relates to a rubber composition for a tire, including: a rubber component containing 60% by mass or more of a natural rubber component; and a carbon black having a cetyltrimethylammonium bromide (CTAB) specific surface area of 140-160 m2 / g, a ratio (CTAB / IA) of the cetyltrimethylammonium bromide specific surface area to an iodine adsorption number (IA) of 0.85-1 m2 / g, and a ratio (ΔD50 / Dst) of a half width (ΔD50) of Stokes' diameter distribution of aggregates to a Stokes' diameter (Dst) of aggregates, as determined by a centrifugal sedimentation method, of 0.9-0.99, the natural rubber component containing 20% by mass or more of highly purified natural rubber per 100% by mass of the natural rubber component.
Owner:SUMITOMO RUBBER IND LTD
Gasoline production by olefin polymerization
InactiveUS20070185359A1Reduce over-polymerizationEasy to convertMolecular sieve catalystsLiquid hydrocarbon mixtures productionButeneFractionation
A process unit for the zeolite-catalyzed conversion of light refinery olefins from an FCC unit such as ethylene, propylene, and butylene to gasoline boiling range motor fuels comprises at least two sequential, serially connected reactors connected in parallel to a fractionation section with at one or two fractionators for separating the reactor effluents into product fraction with an optional recycle stream or streams. The configurations according to this scheme allow the adjustment of reactor temperature and / or pressure and / or space velocity to be based on the reactivities of the olefin compounds present in the LPG streams so that the gasoline produced in each reactor will be separated immediately, to reduce over-polymerization of the gasoline in the low severity reactor and to ensure that gasoline formed in the low severity reactor will not be sent to the higher severity reactor e.g. with a higher reactor temperature, where excessive polymerization to undesirable higher molecular with products may take place.
Owner:EXXON RES & ENG CO
Bio-oil production with optimal byproduct processing
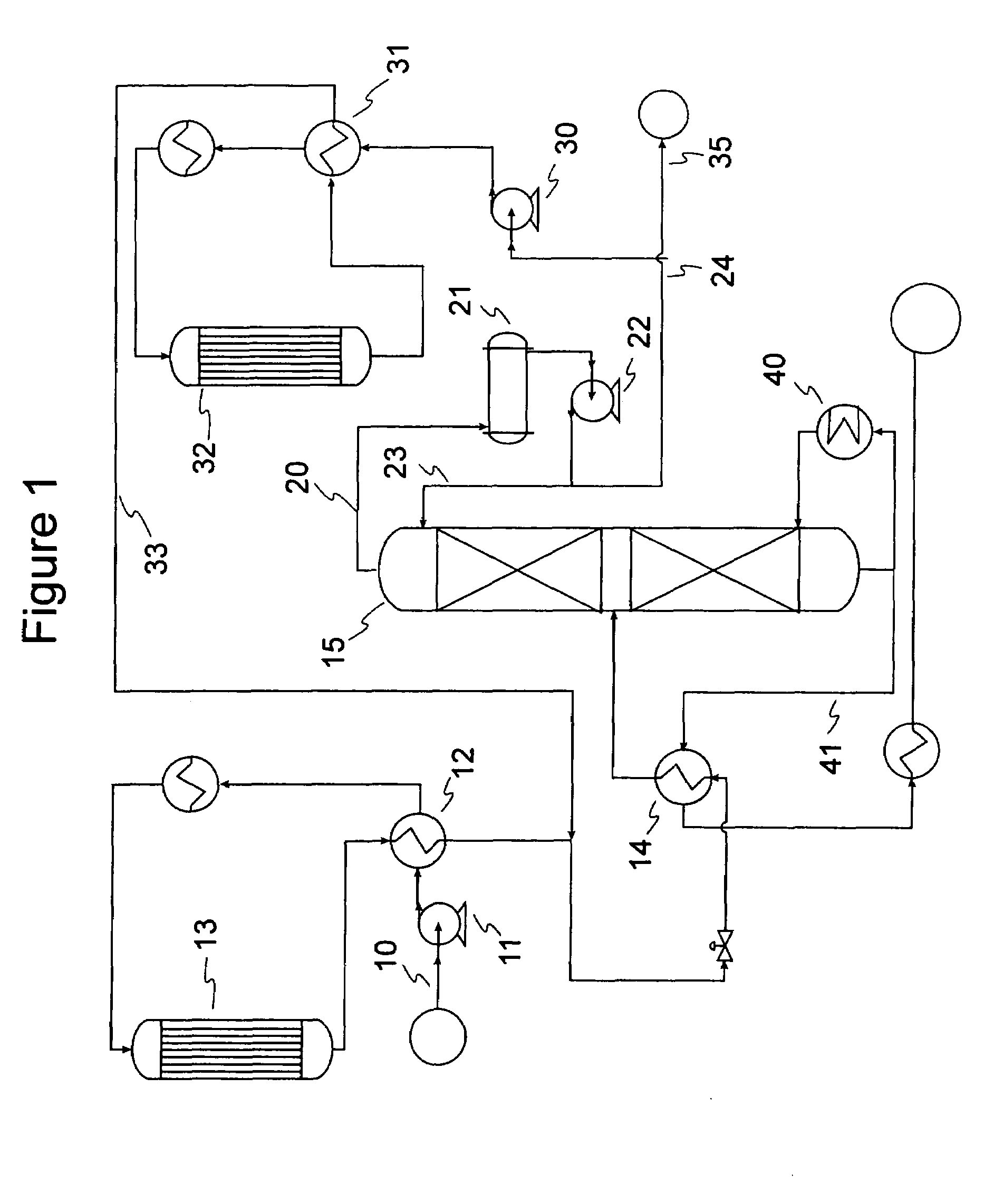
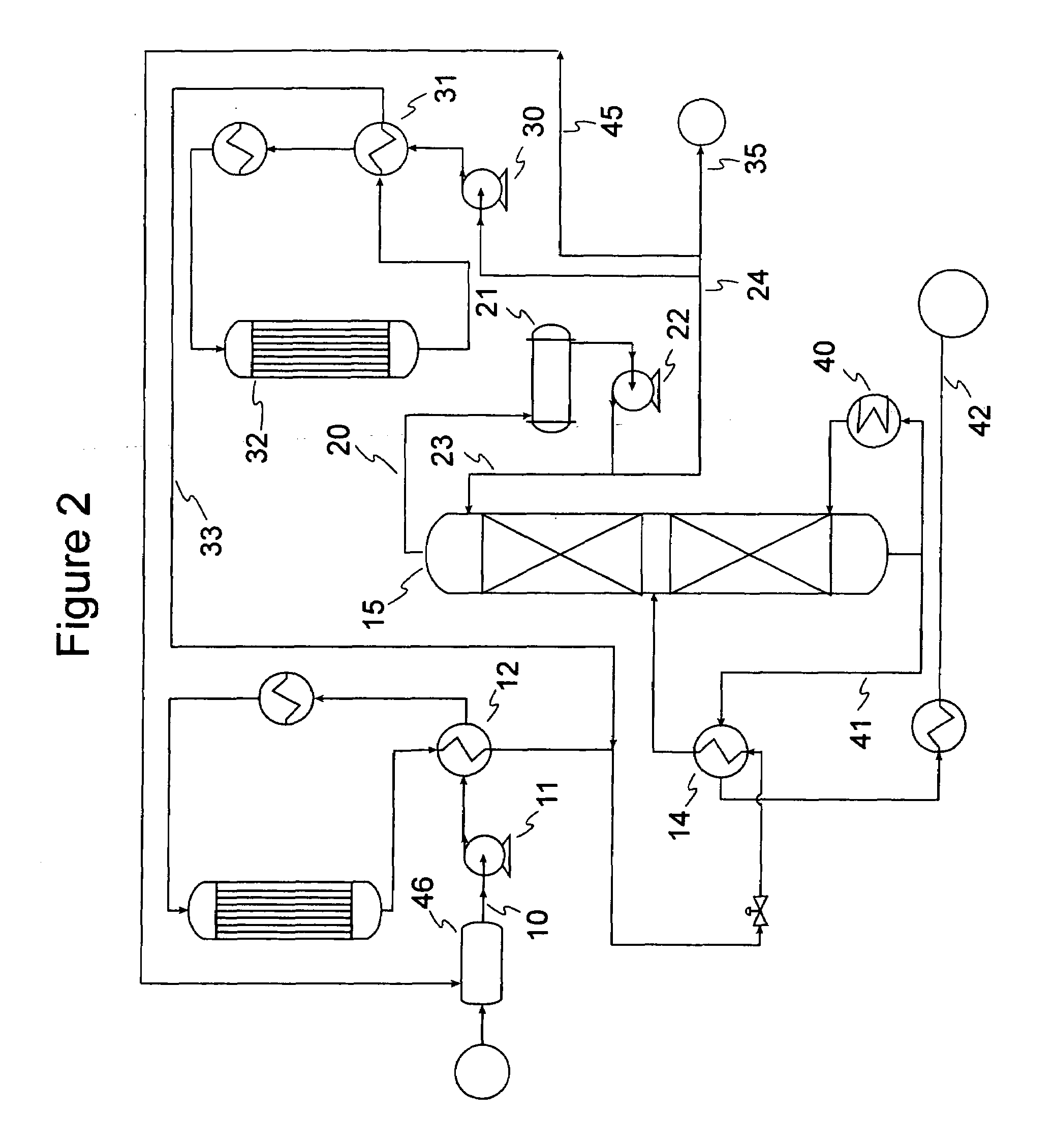
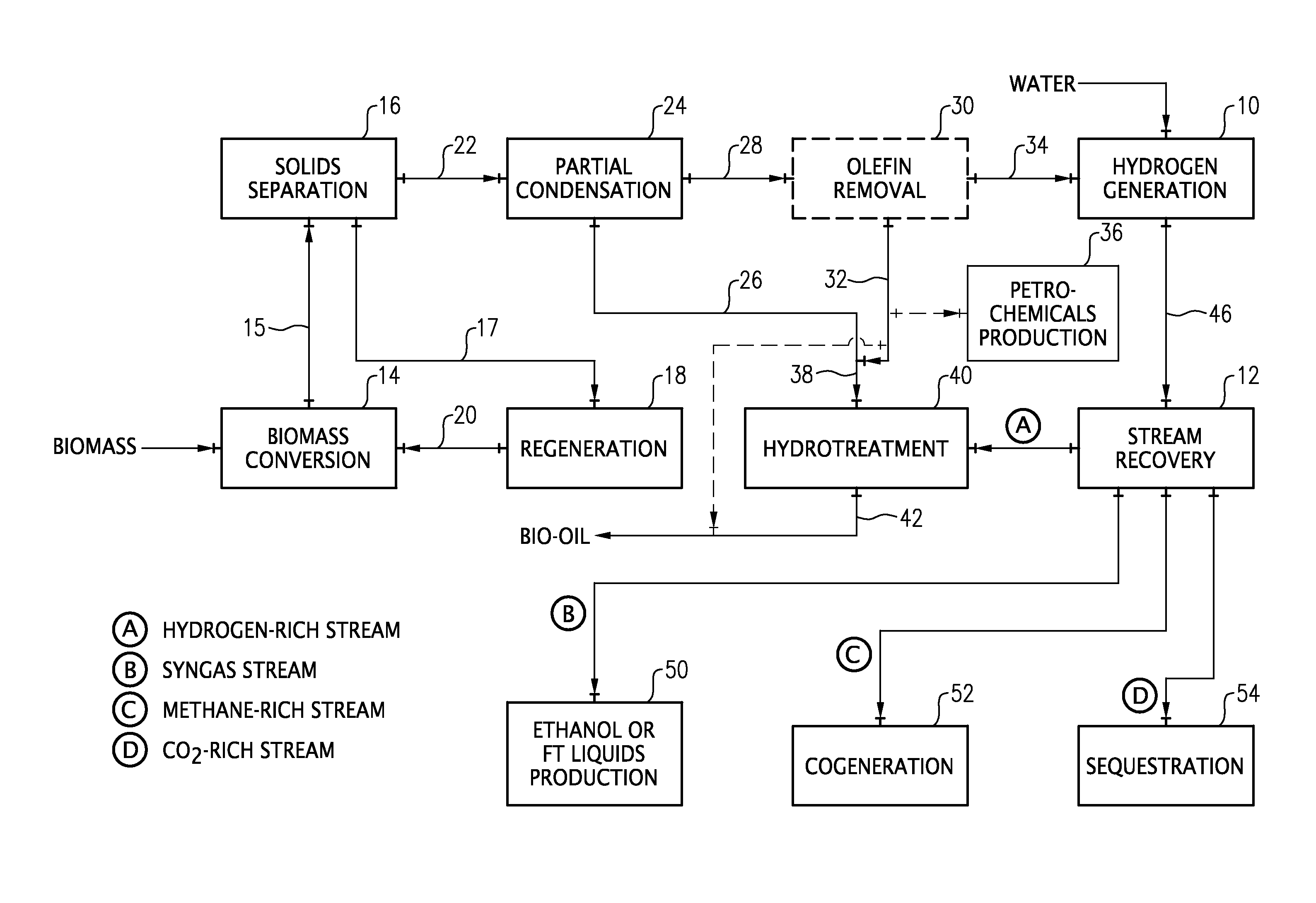
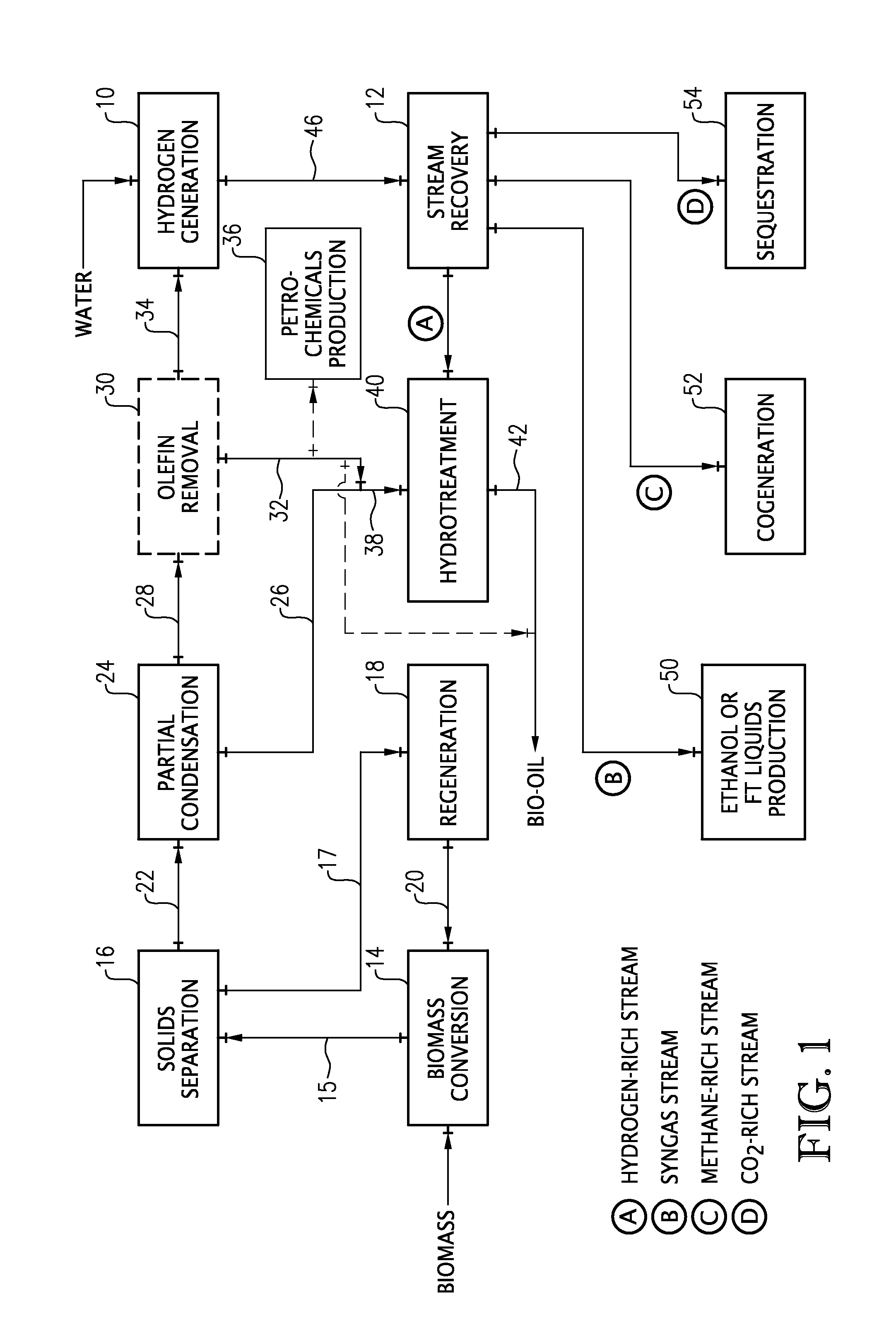
A process and system for the conversion of biomass under high severity in the presence of a catalyst to produce a bio-oil, olefins, methane, and carbon monoxide (CO). The methane and / or CO can be used to generate hydrogen and the generated hydrogen can be used for hydrotreating the bio-oil. Additionally, or alternatively, a syngas stream, a carbon dioxide-rich stream, and / or a methane-rich stream can be recovered for use in the bio-oil production process and / or for use in a conventional petroleum refinery and / or petrochemical plant.
Owner:MARD INC
Rubber composition for tire, and pneumatic tire
InactiveUS8658730B2Balanced improvement in the abrasion resistanceReduce the heating effectHeavy duty tyresHeavy duty vehiclePolymer scienceWear resistance
The invention aims to provide a rubber composition for a tire which achieves a balanced improvement in the abrasion resistance under both low and high severity abrasion conditions, low heat build-up properties, and chipping resistance. The invention relates to a rubber composition for a tire, including: a rubber component containing 60% by mass or more of a natural rubber component; and a carbon black having a cetyltrimethylammonium bromide (CTAB) specific surface area of 140-160 m2 / g, a ratio (CTAB / IA) of the cetyltrimethylammonium bromide specific surface area to an iodine adsorption number (IA) of 0.85-1 m2 / g, and a ratio (ΔD50 / Dst) of a half width (ΔD50) of Stokes' diameter distribution of aggregates to a Stokes' diameter (Dst) of aggregates, as determined by a centrifugal sedimentation method, of 0.9-0.99, the natural rubber component containing 20% by mass or more of highly purified natural rubber per 100% by mass of the natural rubber component.
Owner:SUMITOMO RUBBER IND LTD
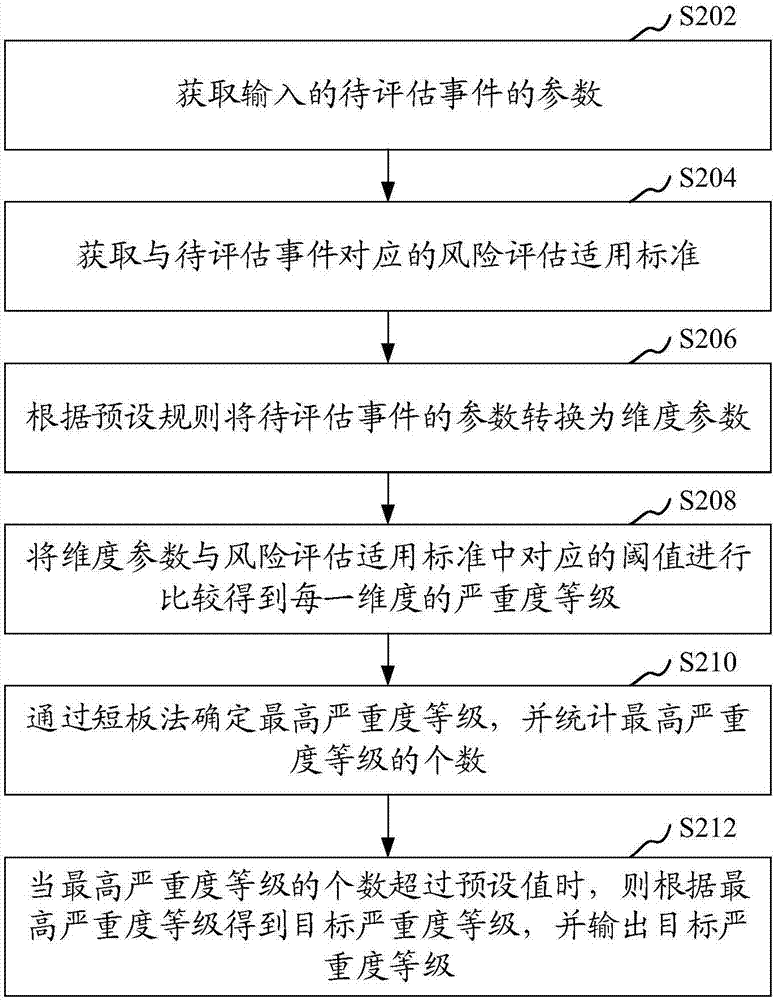
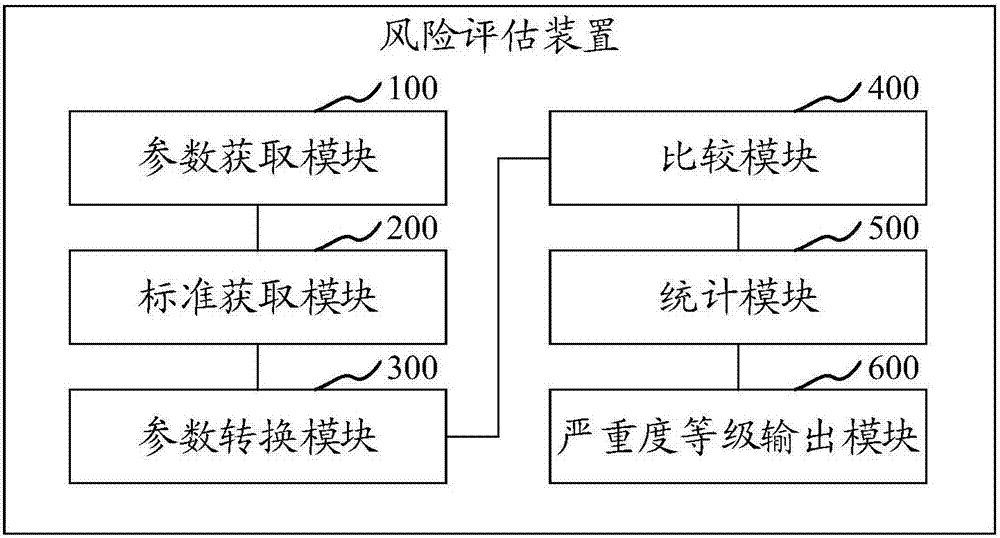
Risk assessment method and device, computer equipment and readable storage medium
The invention relates to a risk assessment method and device, computer equipment and readable storage medium. The method includes a step of obtaining inputted parameters of an event to be evaluated, astep of obtaining a risk assessment applicable standard corresponding to the event to be evaluated, a step of converting the parameters of the event to be evaluated into dimension parameters according to a preset rule, a step of comparing the dimension parameters and a corresponding threshold in the risk assessment applicable standard to obtain a severity level of each dimension, a step of determining highest severity levels by a short board method and counting the number of the highest severity levels, and a step of obtaining a target severity level according to the highest severity levels when the number of the highest severity levels exceeds a preset value and outputting the target severity level. According to the risk assessment method and device, the computer equipment and the readable storage medium, manual intervention is not needed, the efficiency is high, the risk assessment applicable standard is set in advance, and the accuracy of risk assessment is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
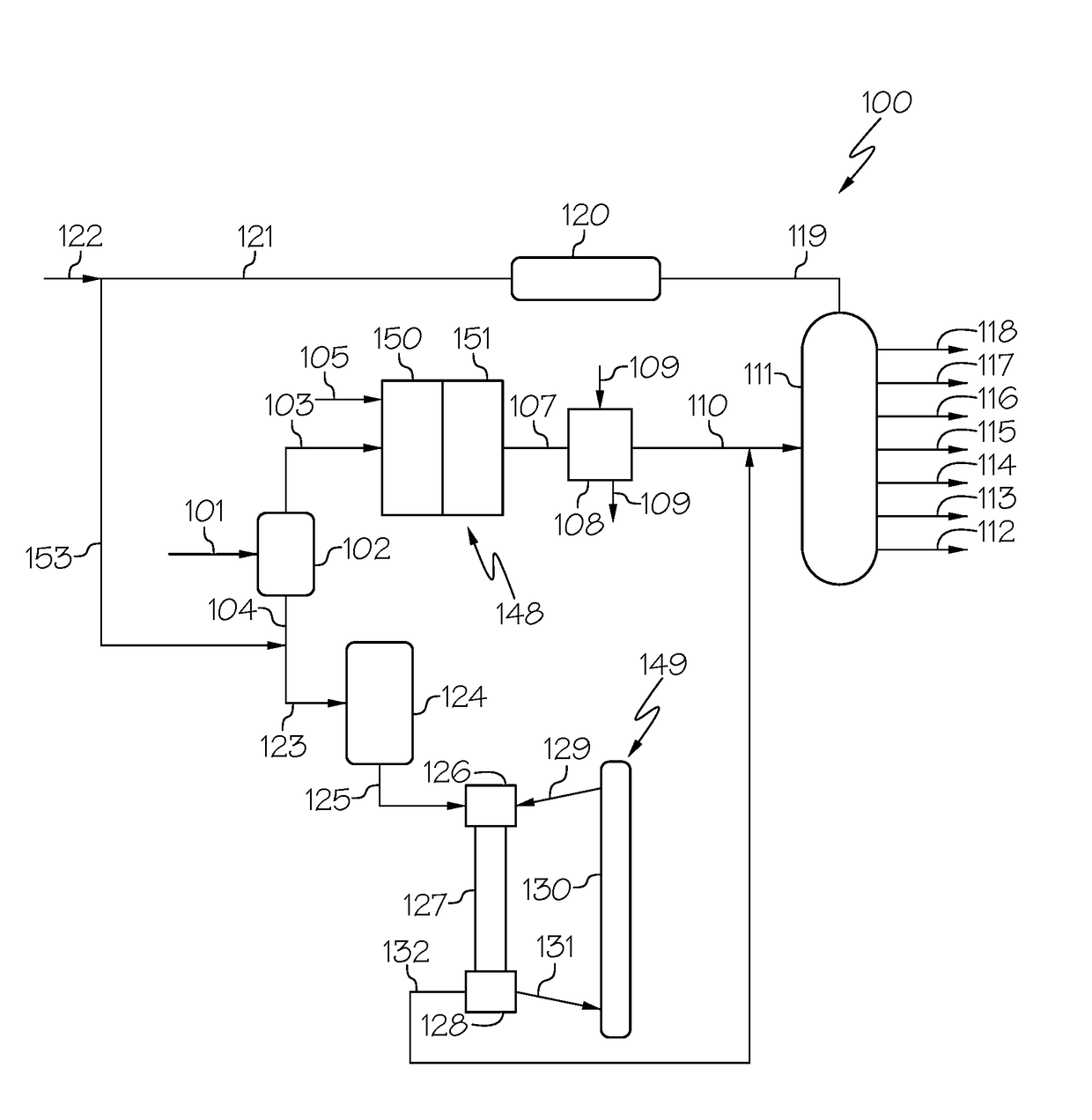
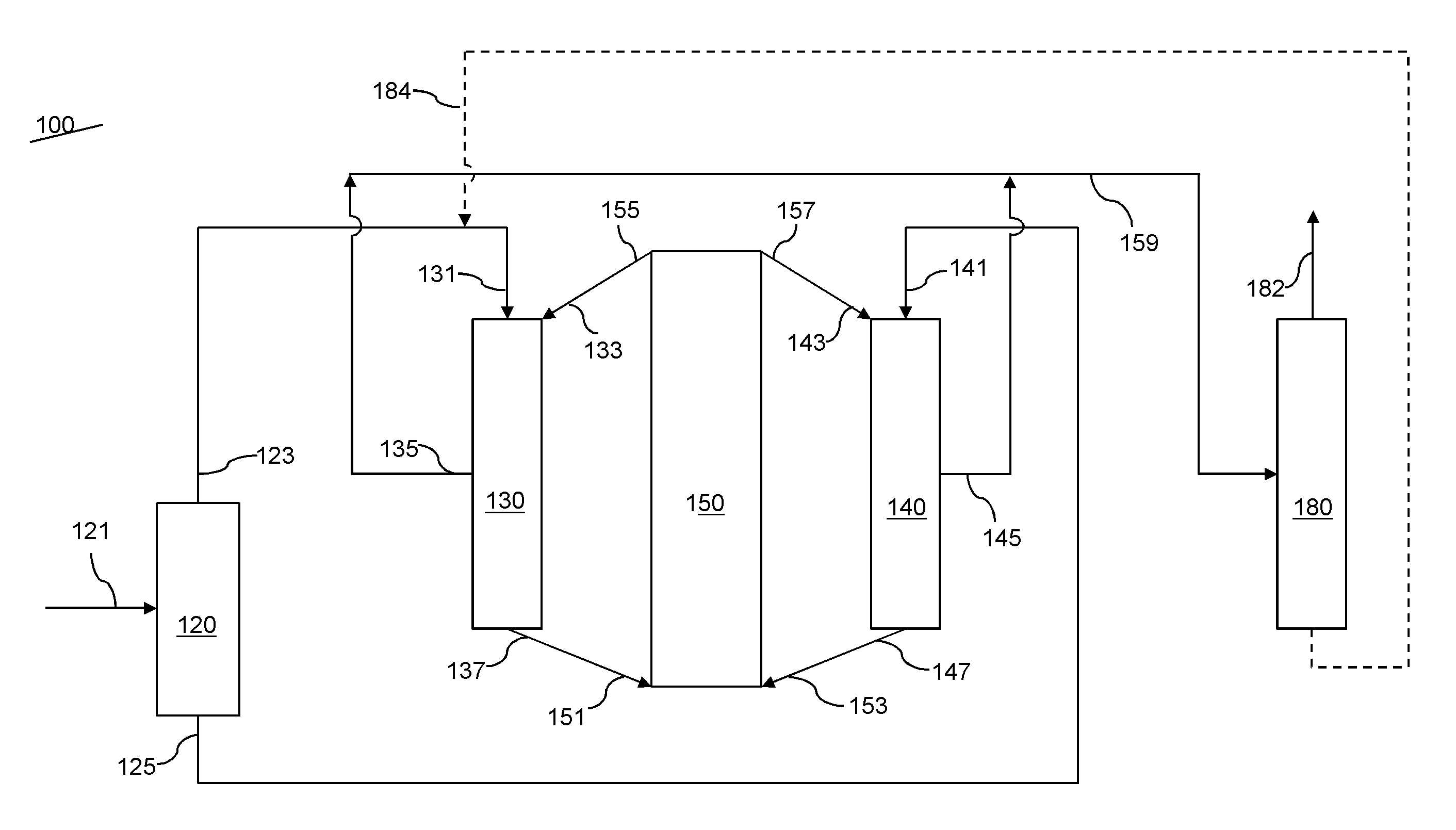
Staged solvent assisted hydroprocessing and resid hydroconversion
Systems and methods are provided for processing a heavy oil feed, such as an atmospheric or vacuum resid, using a combination of solvent assisted hydroprocessing and slurry hydroconversion of a heavy oil feed. The systems and methods allow for conversion and desulfurization / denitrogenation of a feed to form fuels and gas oil (or lubricant base oil) boiling range fractions while reducing the portion of the feed that is exposed to the high severity conditions present in slurry hydroconversion.
Owner:EXXON RES & ENG CO
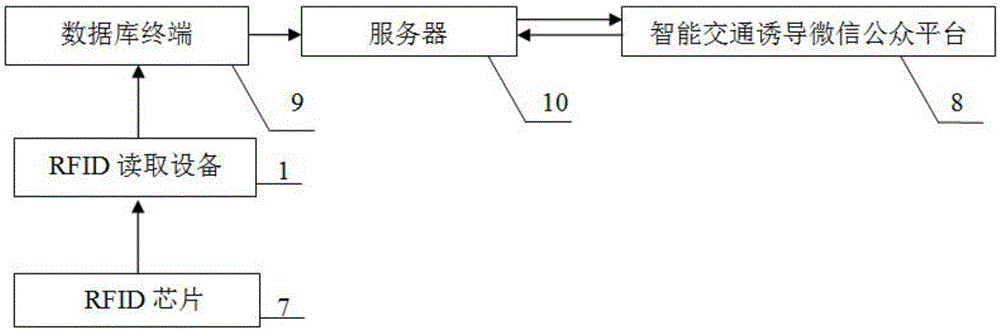
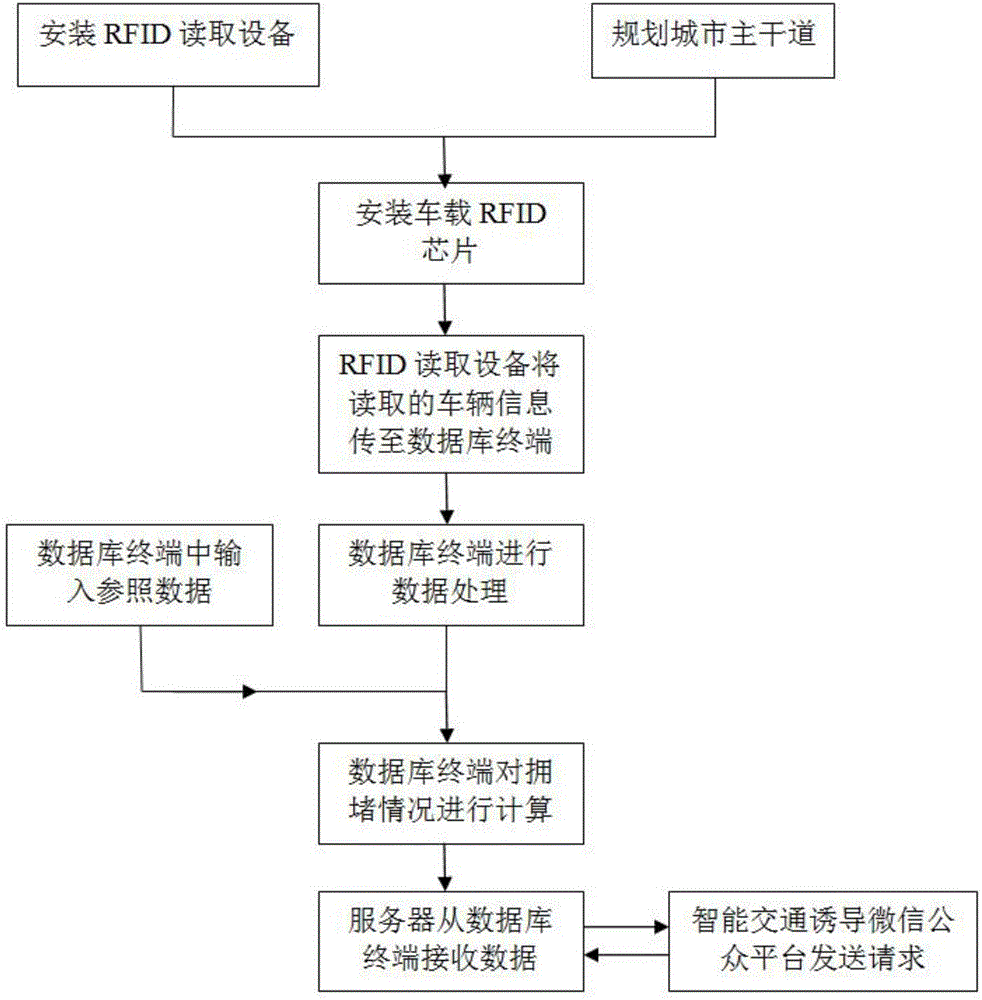
City intelligent traffic induction method based on RFID and WeChat platform
InactiveCN106601005AEffective monitoring of traffic congestionSimple structureRoad vehicles traffic controlIn vehicleRoad traffic
The present invention belongs to the real-time traffic status navigation technology field, and relates to a city intelligent traffic induction method based on a RFID and a WeChat platform. The concrete technology comprises: a RFID reading device reads the information of RFID chips in vehicles and sends the information to a database terminal for calculation and processing, the passing time T(N) of each time on a road section is monitored to evaluate the jamming condition of the road section, if T(N)<1.5T(S), the jamming condition is evaluated as the low-severity jamming, if 2.0T(S)> T(N)>=1.5T(S), the jamming condition is evaluated as the mid-severity jamming, and if T(N)>=2.0T(S), the jamming condition is evaluated as the high-severity jamming, the vehicle jamming quantity S(N) and the vehicle jamming quantity growth rate F(N1) on the road section are employed to evaluate the condition changing trend, and a server calls corresponding information and send the corresponding information to the official account of a user phone terminal according to the query request received by an intelligent traffic induction WeChat public platform. The city intelligent traffic induction method based on the RFID and WeChat platform is simple in structure, reliable in principle and low in installation, can effectively monitor the road traffic jamming condition, can perform effective induction, and is friendly in application environment and wide in the market prospect.
Owner:QINGDAO UNIV
Method and apparatus for making a middle distillate product and lower olefins from a hydrocarbon feedstock
ActiveUS7632977B2Yield maximizationCatalytic crackingCatalytic naphtha reformingGasolineSilicon dioxide
Disclosed is a process for making middle distillate and lower olefins. The process includes catalytically cracking a gas oil feedstock within a riser reactor zone by contacting under suitable catalytic cracking conditions within the riser reactor zone the gas oil feedstock with a middle distillate selective cracking catalyst that comprises amorphous silica alumina and a zeolite to yield a cracked gas oil product and a spent cracking catalyst. The spent cracking catalyst is regenerated to yield a regenerated cracking catalyst. Within an intermediate cracking reactor such as a dense bed reactor zone and under suitable high severity cracking conditions a gasoline feedstock is contacted with the regenerated cracking catalyst to yield a cracked gasoline product and a used regenerated cracking catalyst. The used regenerated cracking catalyst is utilized as the middle distillate selective catalyst.
Owner:SHELL USA INC
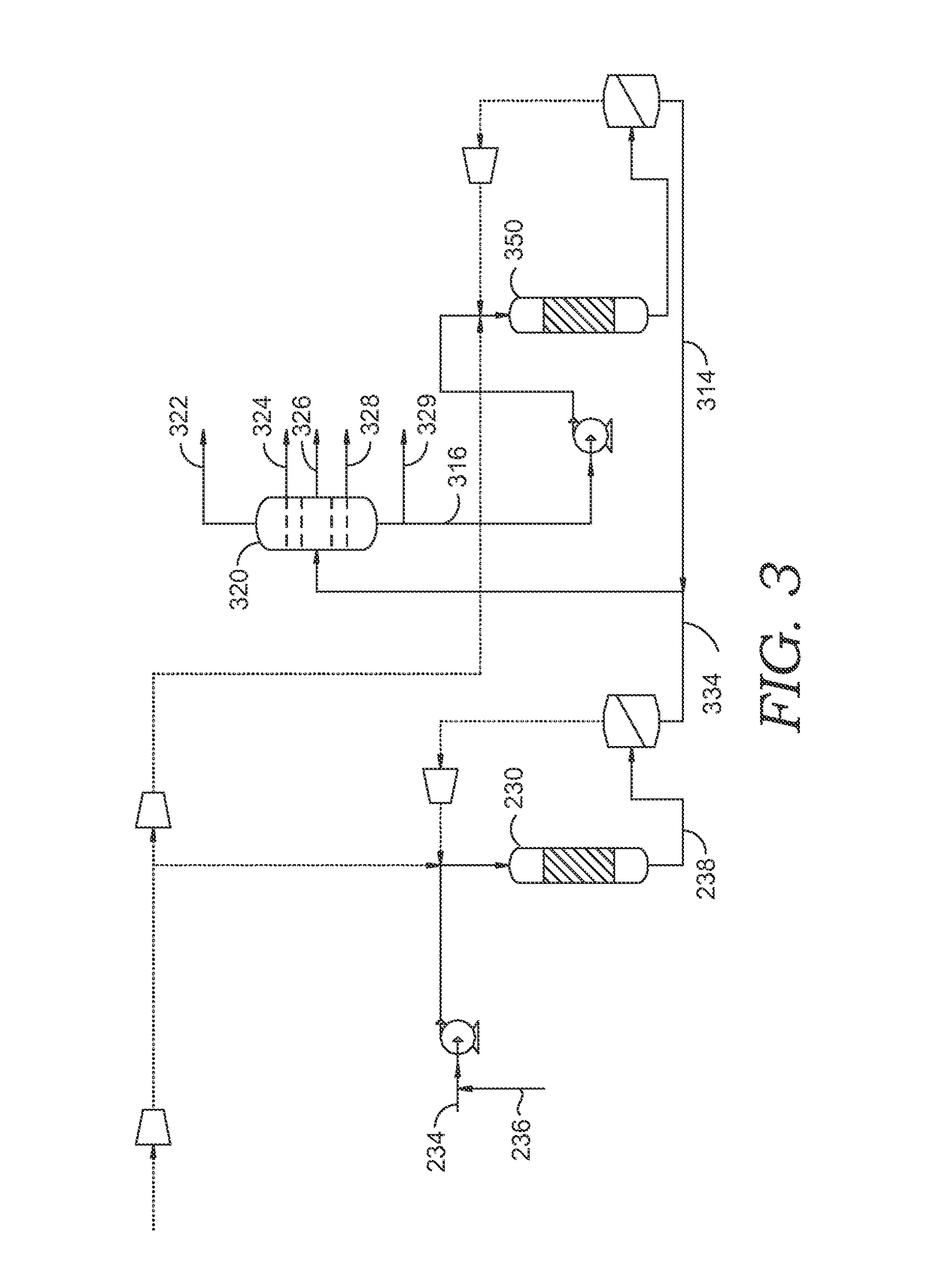
Two stage fluid catalytic cracking process and apparatus
ActiveUS9434892B2Treatment with plural serial cracking stages onlyCatalytic crackingNaphthaResidence time
A two stage Fluid Catalytic Cracking process and an apparatus for simultaneous production of light olefins such as ethylene and propylene and middle distillate range hydrocarbons, wherein a first flow reactor, preferably a downer and a second flow reactor, preferably a riser are operating at varying reaction severities using different catalyst systems with the regenerated catalyst entering the reactors inlet through independent regenerators. Mild cracking of the fresh feedstock is carried out in the first flow reactor of short residence time and the effluent of first flow reactor is separated in an intermediate separator / fractionator followed by re-cracking of the C4 hydrocarbons and naphtha range hydrocarbons, preferably C5-150° C. from the second product separation section and unconverted hydrocarbons (370° C.+) of first flow reactor, in the second flow reactor at higher severity employing different catalyst system.
Owner:INDIAN OIL CORPORATION
Alkali Metal Hydroprocessing of Heavy Oils with Enhanced Removal of Coke Products
InactiveUS20130161234A1Simple and low-cost and efficientSimple and low-cost and efficient methodTreatment with plural serial refining stagesRefining with aqueous alkaline solutionsHydrogenAlkali metal
Hydrocarbon feedstreams are desulfurized using an alkali metal reagent, optionally in the presence of hydrogen. Improved control over reaction conditions can be achieved in part by controlling the particle size of the alkali metal salt and by using multiple desulfurization reactors. The processes herein allow a simple and effective method for removing the majority of coke formed in the alkali metal reagent reactions with the hydrocarbon feedstreams. This makes it cost effective to run such processes at higher severities (which result in higher coke production) thereby resulting in increased amounts of valuable converted hydrocarbon product yields. The process improvements herein may also be used to increase total throughput through a unit due to the ability to effectively manage higher coke content in the reaction products.
Owner:EXXON RES & ENG CO
Visbreaking yield enhancement by ultrafiltration
InactiveUS7837879B2Quality improvementIncrease severityThermal non-catalytic crackingSemi-permeable membranesVisbreakerUltrafiltration
Ultrafiltration may be effectively used to produce visbreaker feeds of improved quality which enable the visbreaker to be operated at higher severity with higher yields of distillable products. A heavy oil feed stream is separated by ultrafiltration or membrane separation into a permeate fraction and a retentate fraction by contacting the heavy oil feed with the first side of a porous membrane separation element in a membrane separation zone. The permeate fraction, comprised of materials which pass selectively through the porous membrane element, is retrieved and at least a portion of it is subjected to visbreaking with the improved liquid yield, especially of lighter distillate fractions. The retentate fraction can be retrieved from the first side of the porous membrane and can also be subjected to visbreaking.
Owner:EXXON RES & ENG CO
Wind power generator set fault overhaul method
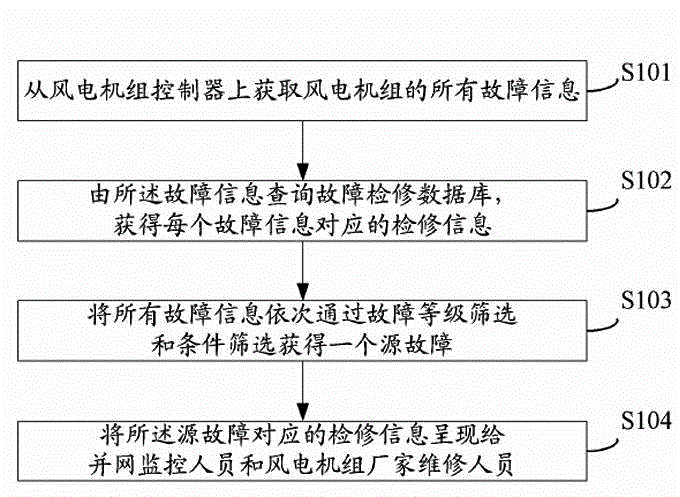
InactiveCN104977923AEasy to operateShorten the timeElectric testing/monitoringElectricityEngineering
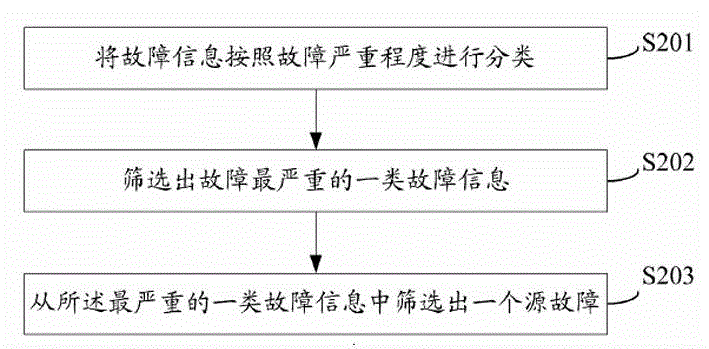
The invention discloses a wind power generator set fault overhaul method comprising the following steps: acquiring all fault information of a wind power generator set from a wind power generator set controller; querying a fault overhaul database according to the fault information to obtain overhaul information corresponding to each piece of fault information, wherein the fault overhaul database includes fault information and overhaul information, each piece of fault information corresponds to a fault code, and each fault code corresponds to a piece of overhaul information; obtaining a source fault through fault level screening and condition screening on all the fault information, wherein fault level screening specifically refers to classifying the fault information according to severity and screening out the fault information with the highest severity, and condition screening specifically refers to screening out a source fault from the fault information with the highest severity; and presenting the overhaul information corresponding to the source fault to grid-connection monitoring personnel and wind power generator set manufacturer maintenance personnel.
Owner:黄染之
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com