Password dynamic enciphering inputmethod of public emipering mode
A dynamic encryption and input method technology, which is applied to the usage of multiple keys/algorithms, user identity/authority verification, etc., can solve problems such as poor practicability, inability to modify passwords, and inability to guarantee system user identification, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
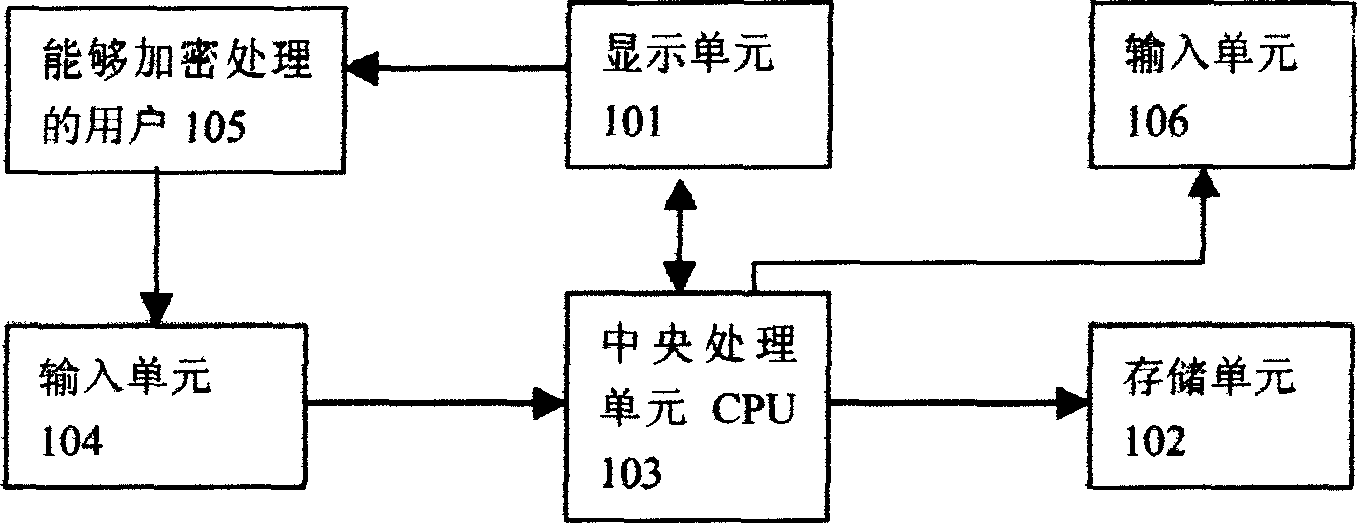
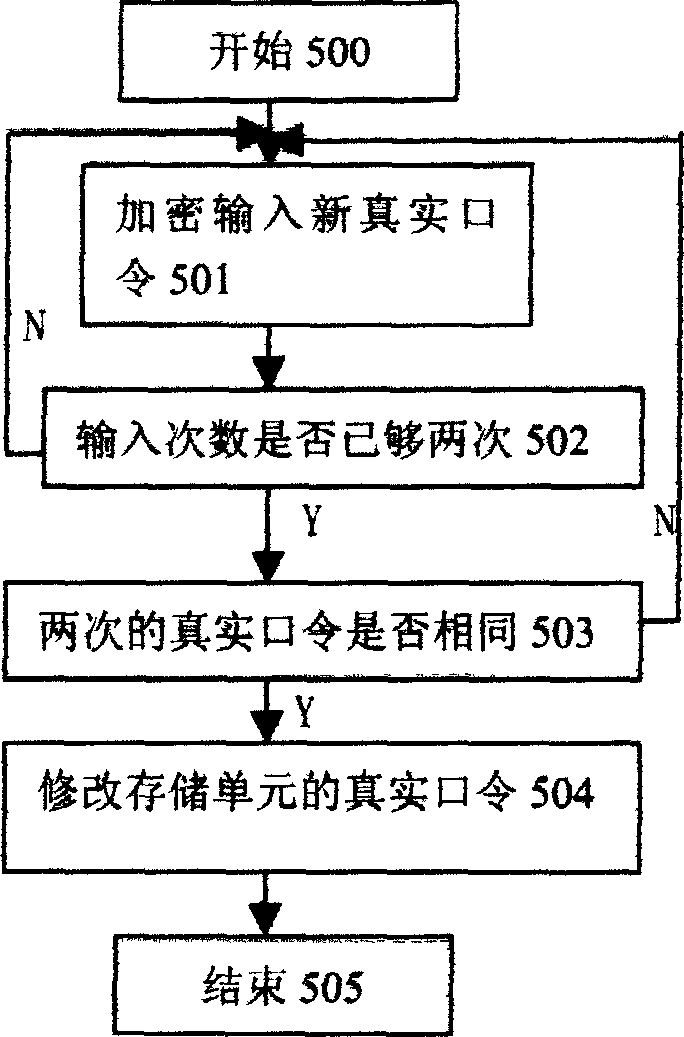
[0063] In the original system, the password is to directly input the real password, and the corresponding program method of the present invention can replace the interface and the module corresponding to the password input, and other parts can be unchanged, and can be run after compiling.
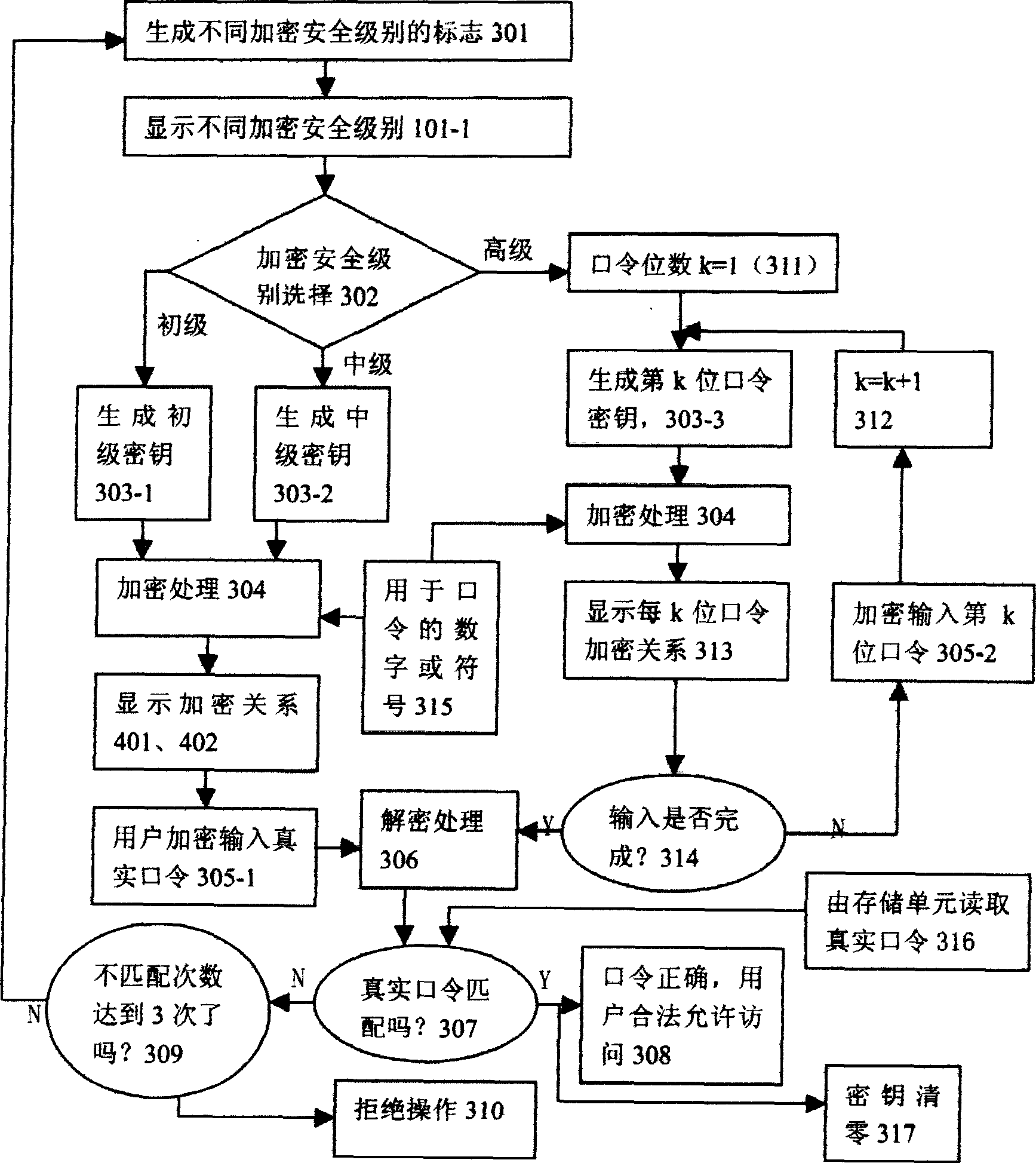
[0064] After the user enters the operation interface by swiping the card or in other ways, first enter such as figure 1 As shown in the selection interface 101-1, the user is required to select the level of difficulty, and the level uses three random numbers in the 10 numbers from 0 to 9 to represent three levels of the encryption security level respectively. The user must select a certain level. One level, if not selected, it can automatically enter the default encryption security level, such as primary, in a few seconds (such as three seconds).
[0065] When the user selects the primary or default security level as the encryption security standard, the user's input method is consistent with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com