Sensing system key protecting method in field of Internet of things and wireless access equipment
A key protection, Internet of Things technology, applied in transmission systems and key distribution, can solve problems such as increasing the burden on nodes and gateways, increasing energy consumption, and entering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
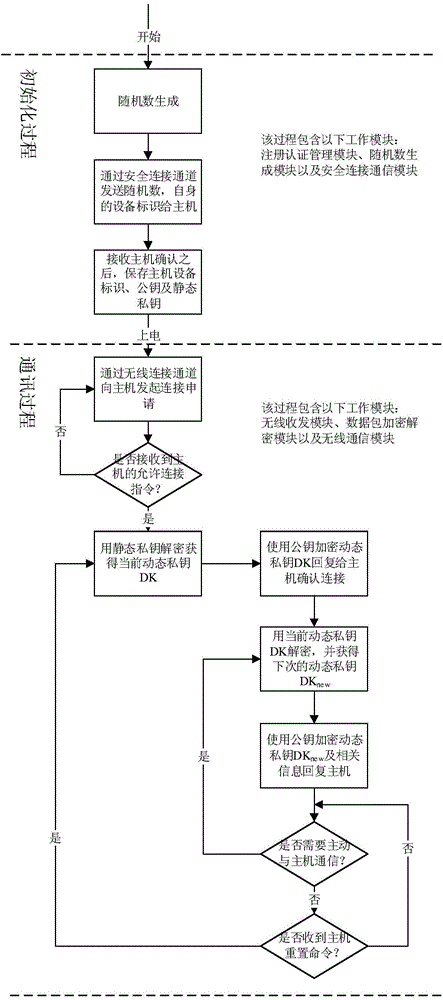
[0040] The workflow of the slave machine includes two main processes: initialization process and communication process.
[0041] The initialization process is that after the slave is powered on, it is connected to the master through a secure connection to initialize various parameters required for the subsequent communication process, mainly including device identification, public key and static private key. Participating modules include: registration authentication management module, random number generation module and secure connection communication module.
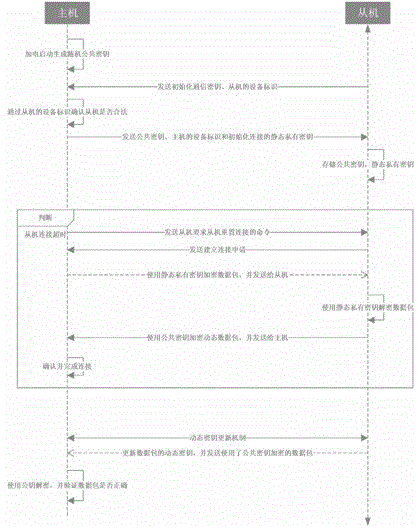
[0042] The communication process is divided into two parts: the wireless connection establishment process and the dynamic key communication process. During the establishment of wireless communication, the slave sends a connection application and waits for the host to confirm. After the host confirms, the slave obtains the current dynamic private key, and then enters the dynamic encryption communication link. The partic...
Embodiment 2
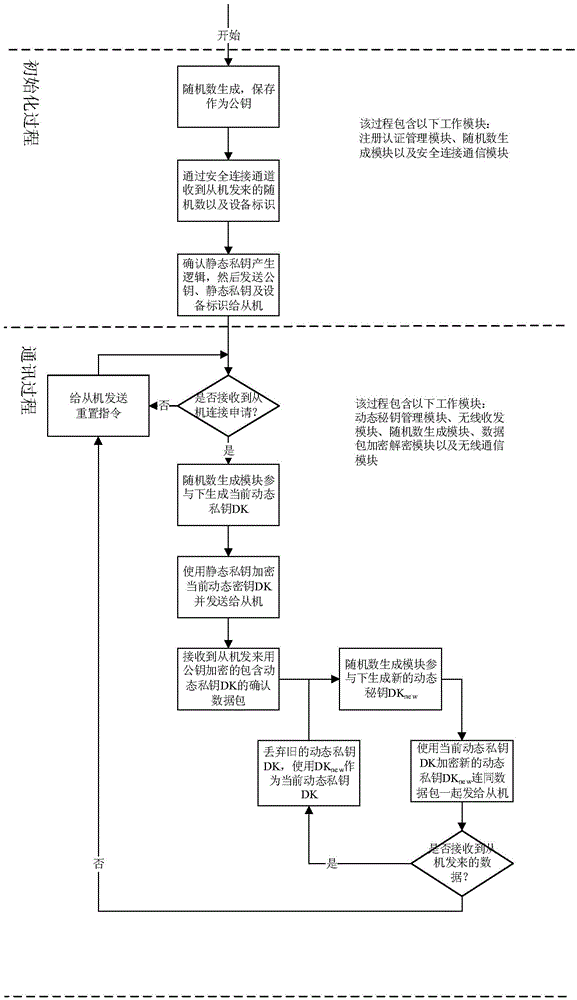
[0069] The workflow of the host includes two main processes: the initialization process and the communication process.
[0070] The initialization process is the public key initialization process after the master is powered on, and through a secure connection with the slave, it is used to initialize various parameters required for the subsequent communication process, mainly including device identification, public key and static private key. Participating modules include: registration authentication management module, random number generation module and secure connection communication module.
[0071] The communication process is divided into two parts: the wireless connection establishment process and the dynamic key communication process. During the establishment of wireless communication, the host computer confirms the connection application of the slave computer, passes the current dynamic private key to the slave computer, and then enters the dynamic encryption communicat...
Embodiment 3
[0096] image 3 It is a schematic diagram of the device structure of the slave device in the network security key protection method provided by Embodiment 3 of the present invention. The slave device is mainly composed of six modules: a random number generation module, a registration authentication management module, a secure communication module, and a wireless transceiver Module, data packet encryption and decryption module and wireless communication module. Wherein, the registration authentication management module is connected with the random number generation module, the secure communication module and the wireless transceiver module; the wireless transceiver module is connected with the data packet encryption and decryption module; the data packet encryption and decryption module is also connected with the wireless communication module. The functions of each module are as follows:
[0097] Wherein, the random number generating module is used for generating random number...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com