Goods false proof method and system based on Internet safety lock
A security lock and Internet technology, applied in computer security devices, commerce, instruments, etc., can solve problems such as the lack of commodity anti-counterfeiting systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
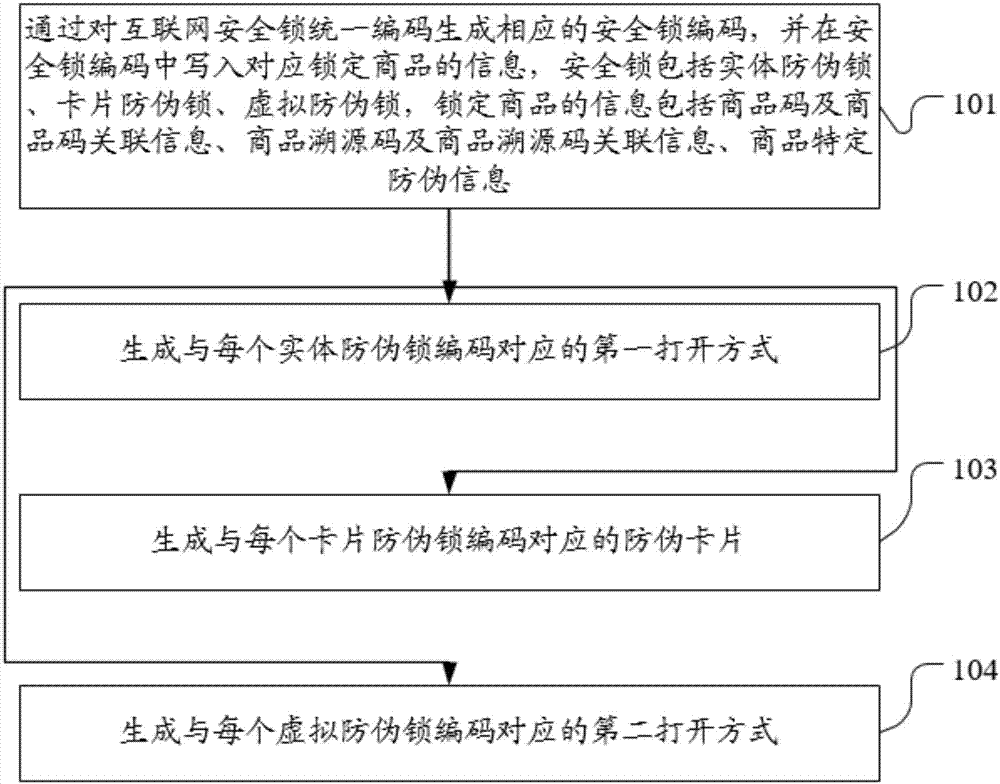
[0049] see figure 1 , the embodiment of the present invention provides a first embodiment of an Internet security lock-based commodity anti-counterfeiting method, including:
[0050] 101. Generate a corresponding security lock code by uniformly coding Internet security locks, and write the information of the corresponding locked product in the security lock code. Security locks include physical anti-counterfeiting locks, card anti-counterfeiting locks, and virtual anti-counterfeiting locks. The information on locked products includes Commodity code and commodity code-related information, commodity traceability code and commodity traceability code-related information, commodity-specific anti-counterfeiting information;
[0051] In the embodiment of the present invention, it is first necessary to uniformly encode the Internet security lock to generate a corresponding security lock code, and write the information of the corresponding locked product in the security lock code. The ...
no. 2 example
[0059] see figure 2 , the embodiment of the present invention provides a second embodiment of an Internet security lock-based commodity anti-counterfeiting method, including:
[0060] 201. Obtaining information on several commodities through the user management system, commodity resource management system, commodity traceability system, and commodity anti-counterfeiting information system, and correcting the accuracy of the information on several commodities by obtaining the national Internet of Things logo;
[0061] In the embodiment of the present invention, it is first necessary to obtain the information of several commodities through the user management system, commodity resource management system, commodity traceability system, and commodity anti-counterfeiting information system, and correct the accuracy of the information of several commodities by obtaining the national Internet of Things logo to ensure The product information written in the security lock code is accur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com