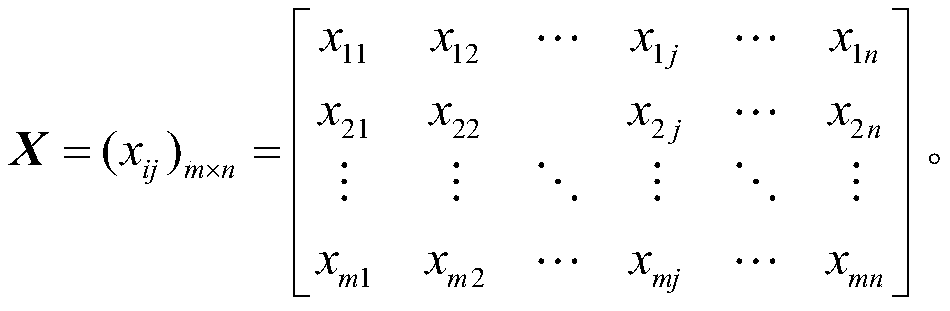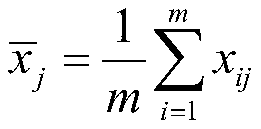Patents
Literature
131 results about "Internet safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Internet safety or online safety or cyber safety is trying to be safe on the internet and is the knowledge of maximizing the user's personal safety and security risks to private information and property associated with using the internet, and the self-protection from computer crime. One key element of internet safety is the ability to maintain privacy. Internet privacy involves the right or mandate of personal privacy concerning the storing, repurposing, provision to third parties, and displaying of information pertaining to oneself via the Internet. Internet privacy is a subset of data privacy. Privacy concerns have been articulated from the beginnings of large-scale computer sharing.
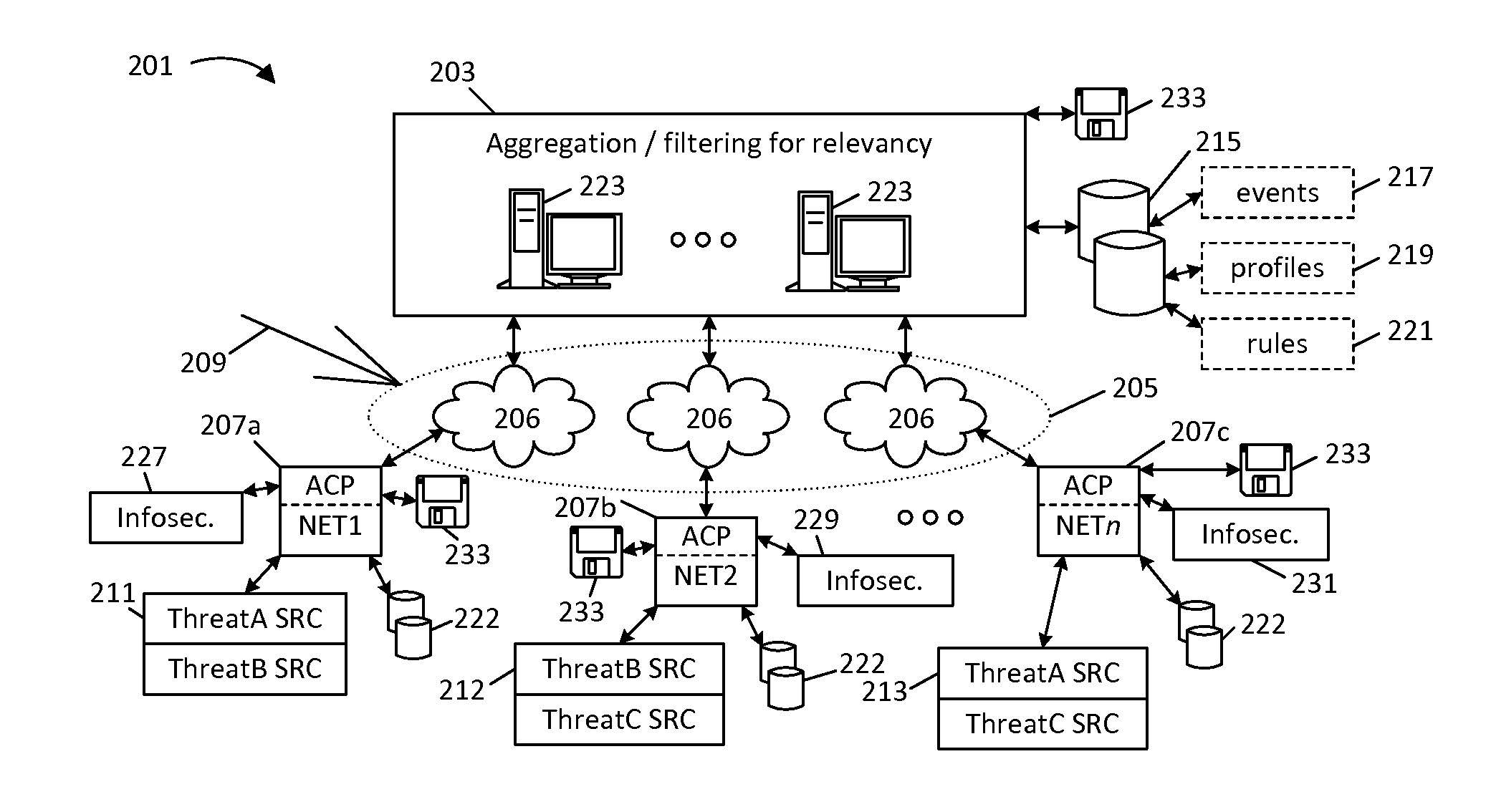
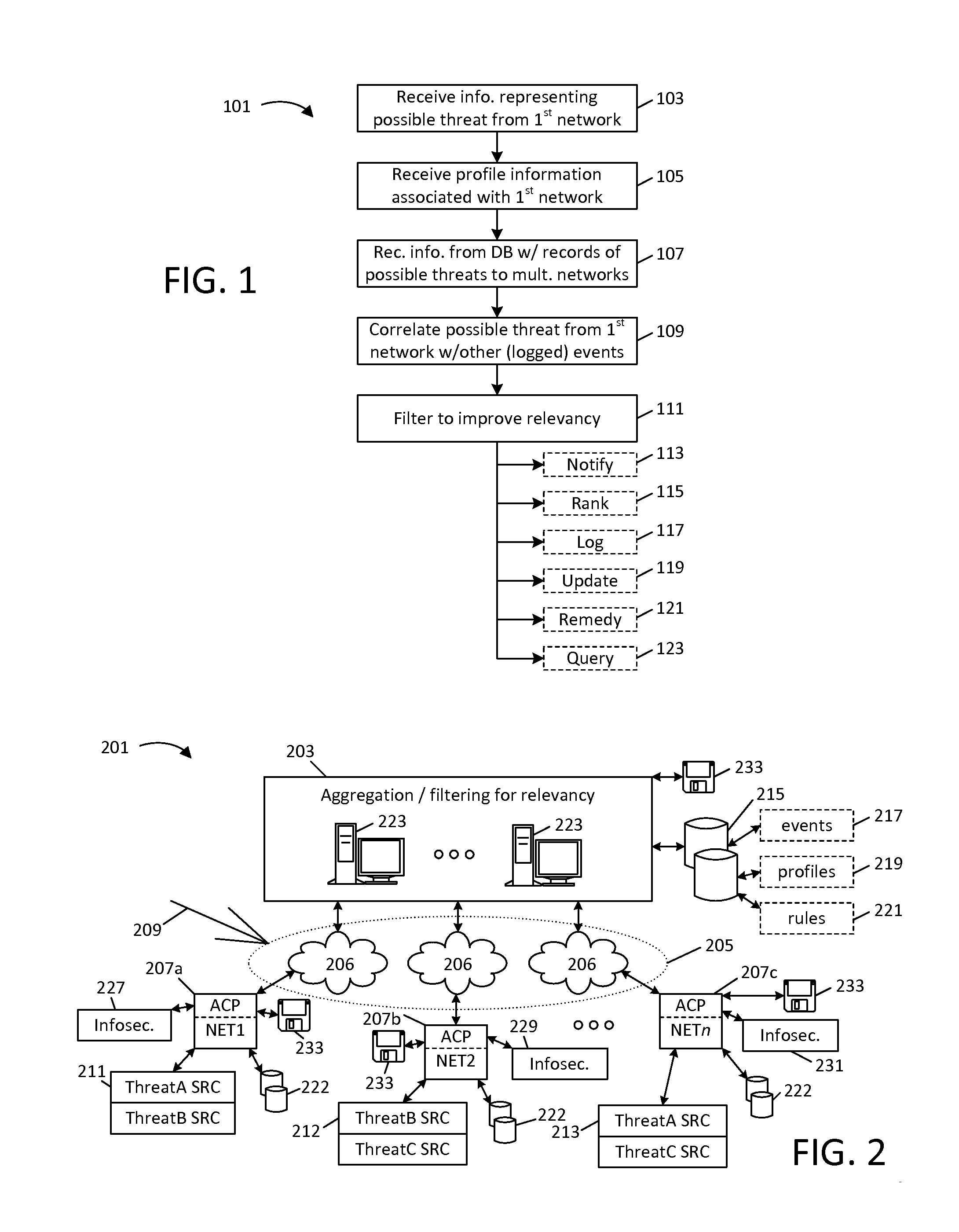
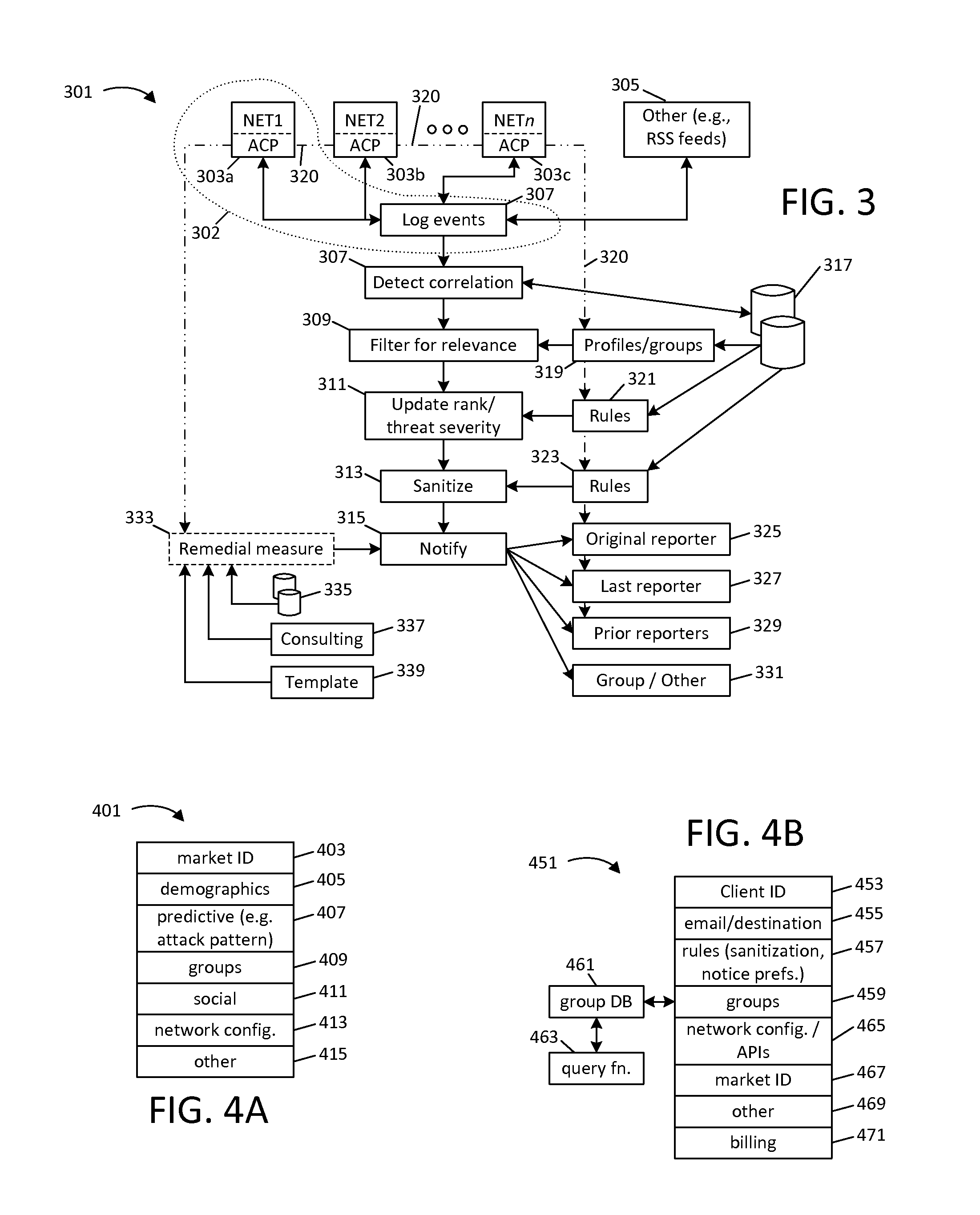
Techniques for sharing network security event information
ActiveUS20150207813A1Memory loss protectionError detection/correctionInformation sharingPrivate network
This disclosure provides techniques for pooling and searching network security events reported by multiple sources. As information representing a security event is received from one source, it is searched against a central or distributed database representing events reported from multiple, diverse sources (e.g., different client networks). Either the search or correlated results can be filtered and / or routed according at least one characteristic associated with the networks, for example, to limit correlation to events reported by what are presumed to be similarly situated networks. The disclosed techniques facilitate faster identification of high-relevancy security event information, and thereby help facilitate faster threat identification and mitigation. Various techniques can be implemented as standalone software (e.g., for use by a private network) or for a central pooling and / or query service. This disclosure also provides different examples of actions that can be taken in response to search results.
Owner:SERVICENOW INC
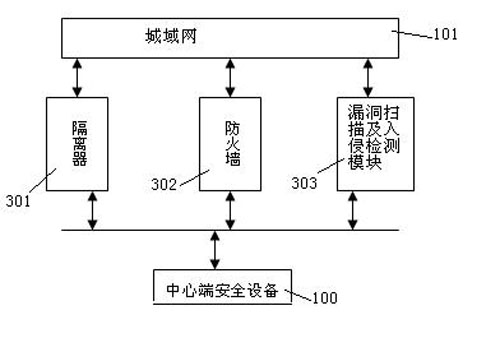
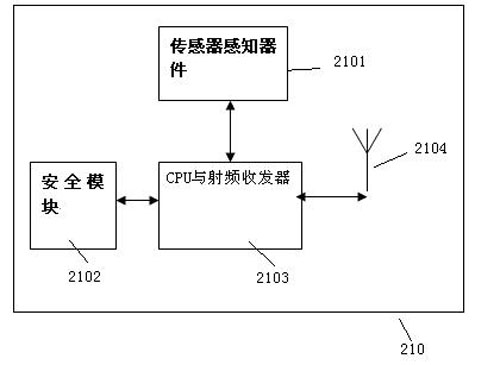
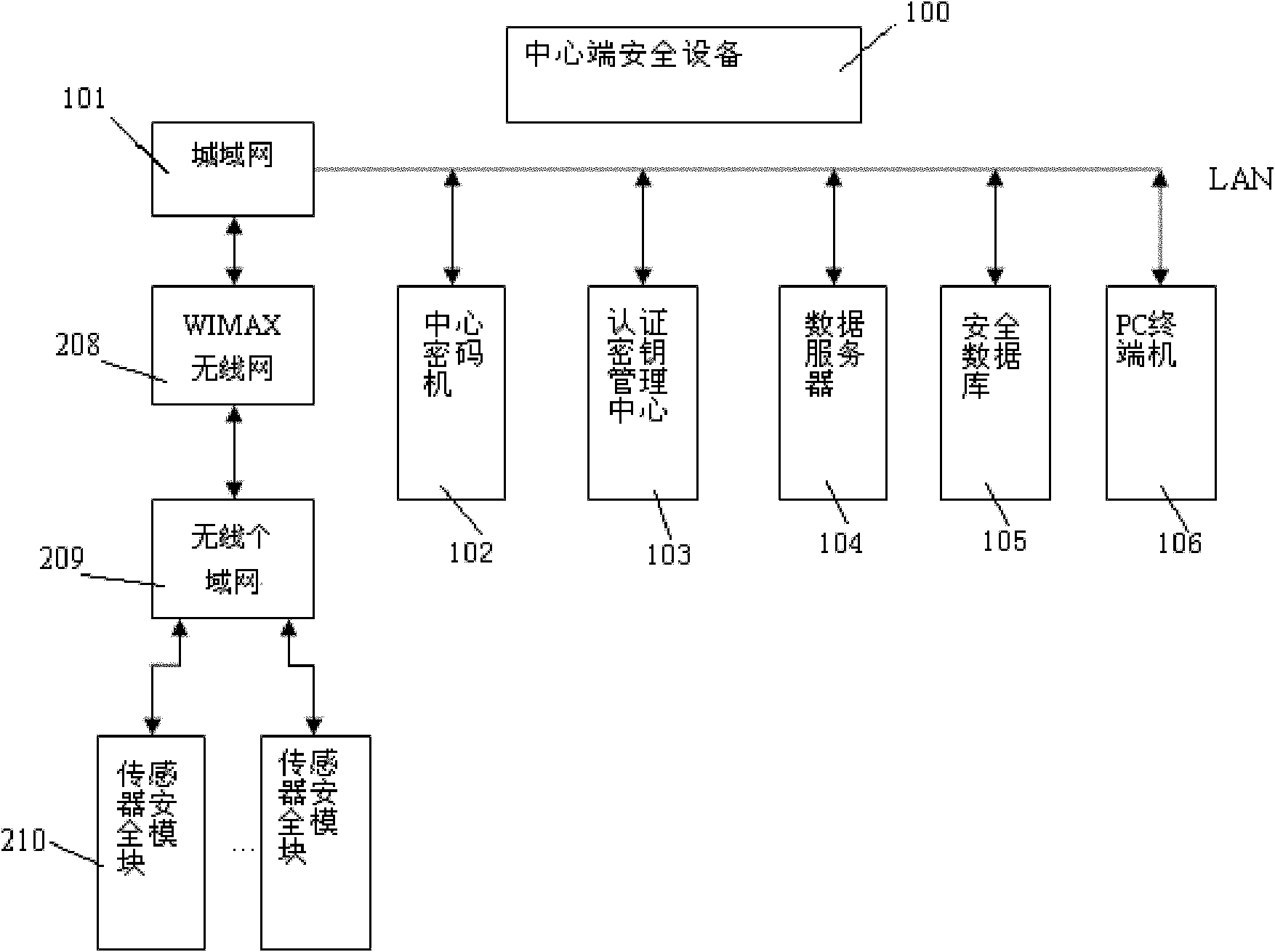
Network architecture security system for Internet of Things and security method thereof
InactiveCN102036231ARealize detection controlRealize secure transmissionNetwork topologiesTransmissionCommunications securityConfidentiality
The invention aims at providing a network architecture security system for Internet of Things and a security method thereof, comprising security protective measures sequentially established in the system from inside to outside, which are mainly reflected in that a security device at a central terminal of the Internet of Things comprises a central cipher machine, a central authentication secret key management center, a data server, a security database and the like, and then the security of each sensor terminal in a Personal Area Network and the like. Compared with the prior art, the invention has the advantages that: 1. according to the characteristics of the Internet of Things, Internet security technology of the Internet of Things is realized; 2. the security protective measures sequentially established in the system from inside to outside are mainly reflected in the security device at the central terminal and security modules at each sensor terminal, thus ensuring the security of sensing information, equipment, communication and application, as well as security management; and 3. multi-level security systems are deployed in the aspects of security mechanism and management, such as the confidentiality, integrity, authenticity and non-repudiation of data, and equipment legitimacy.
Owner:BEIJING BINGGANG TECH DEV CO LTD
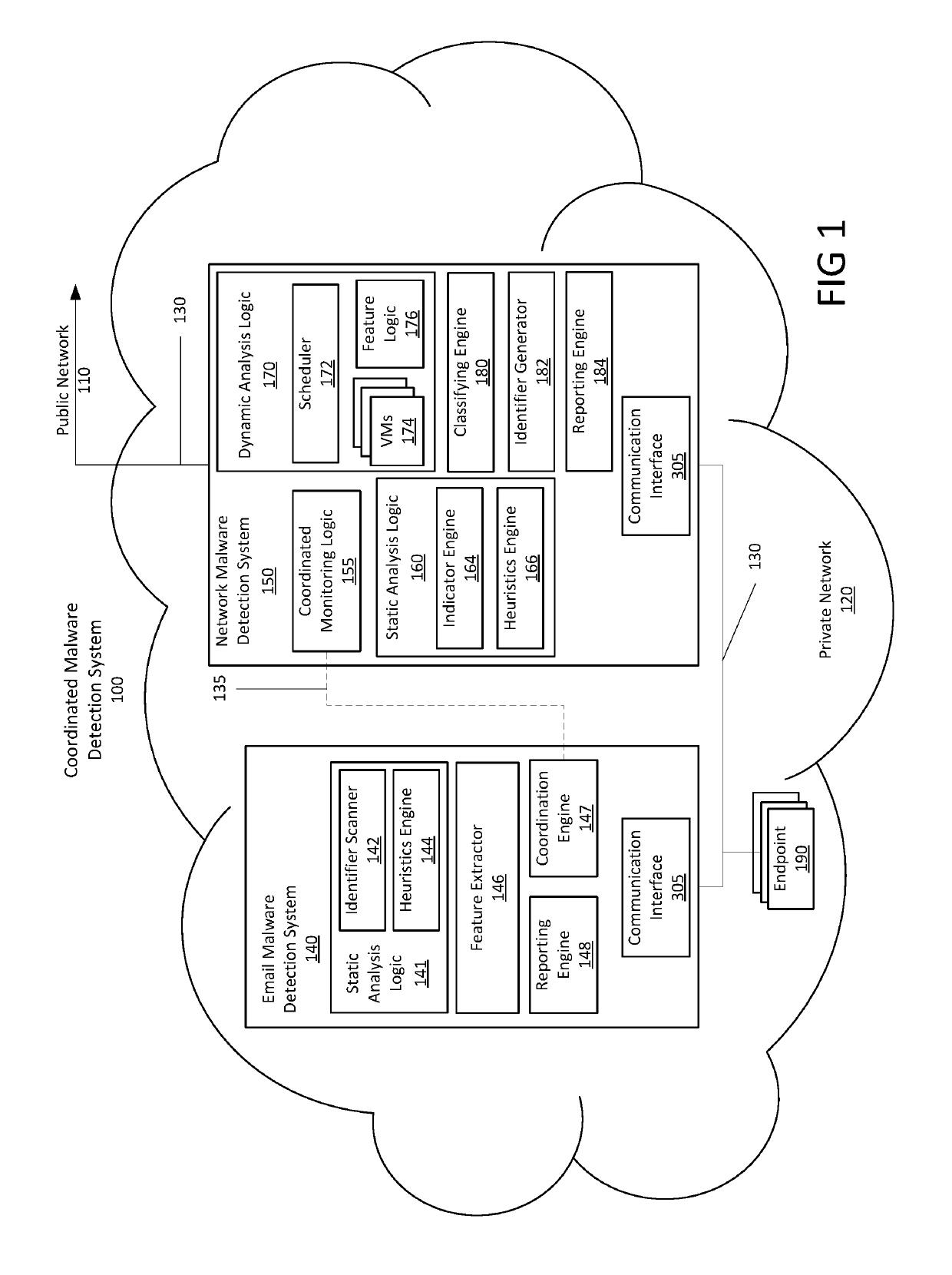
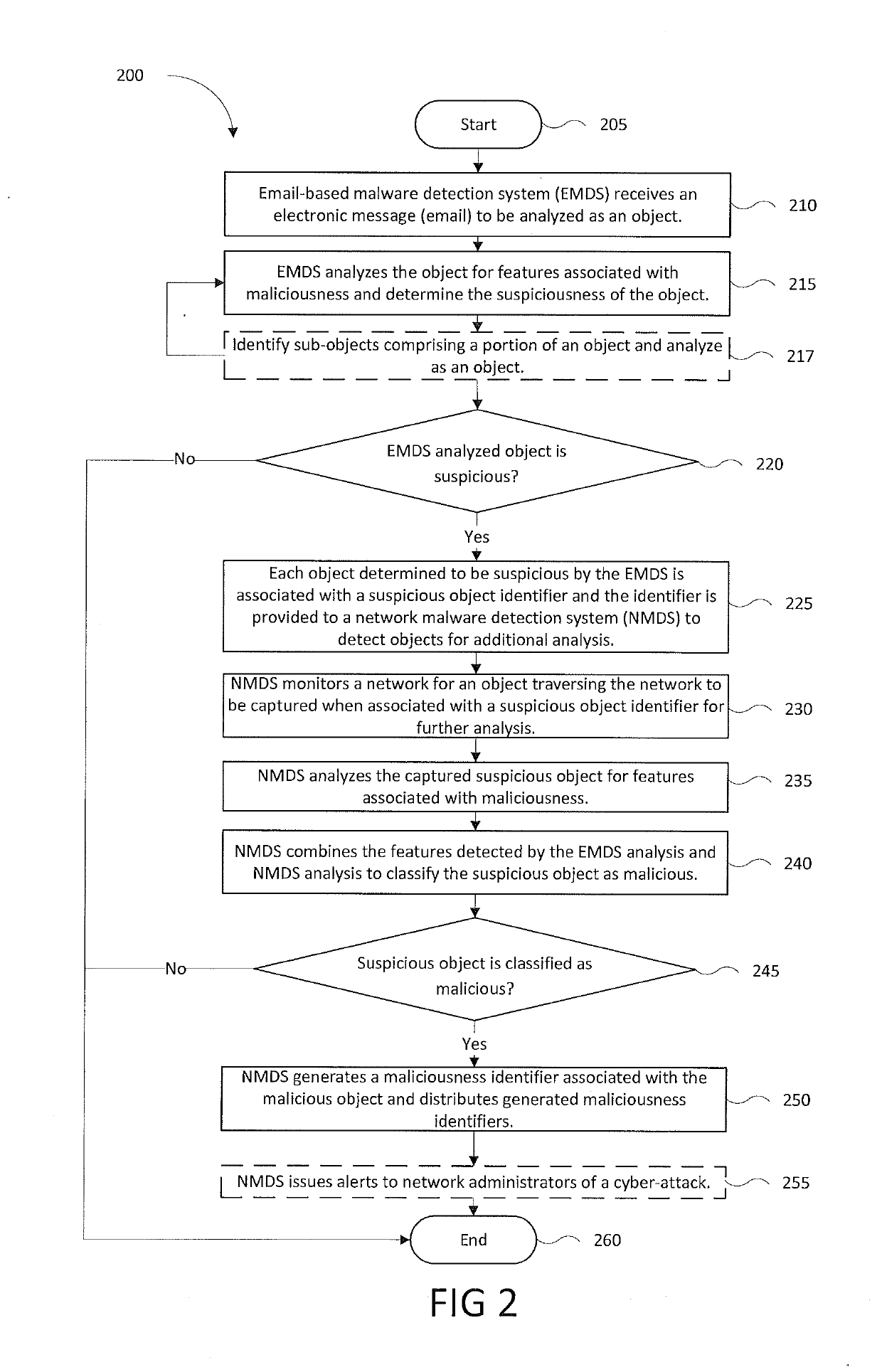
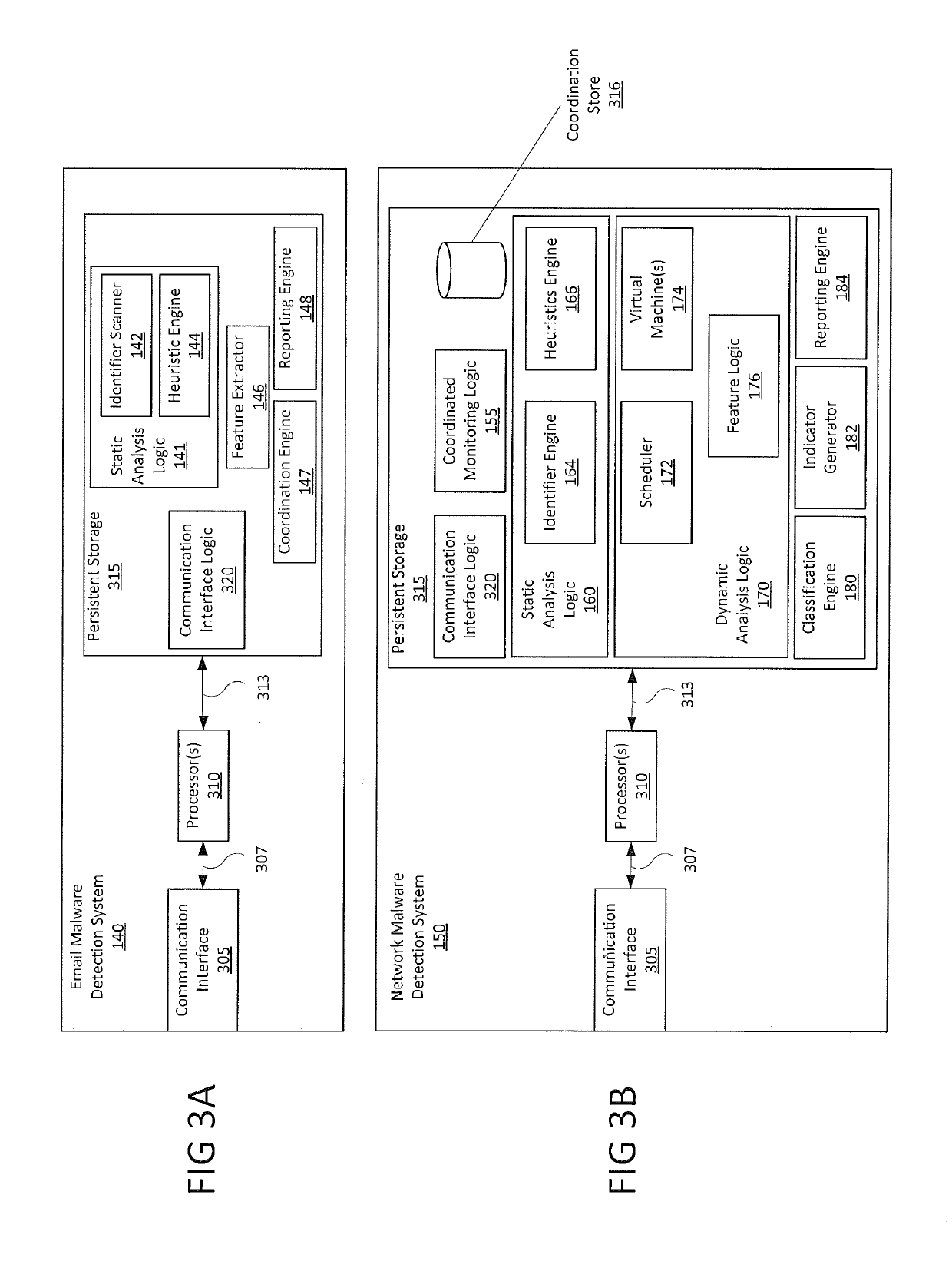
Multi-vector malware detection and analysis
A computerized method to coordinate the detection capabilities of an email-based malware detection system with the detection capabilities of a network-based malware detection system and prevent multi-vector cyber-security attacks. The described system detects and analyzes suspicious objects via the email vector and monitors and analyzes associated objects via the network vector, collecting features of each object. The features of associated objects are analyzed, correlated and classified to determine if they are malicious.
Owner:FIREEYE SECURITY HLDG US LLC
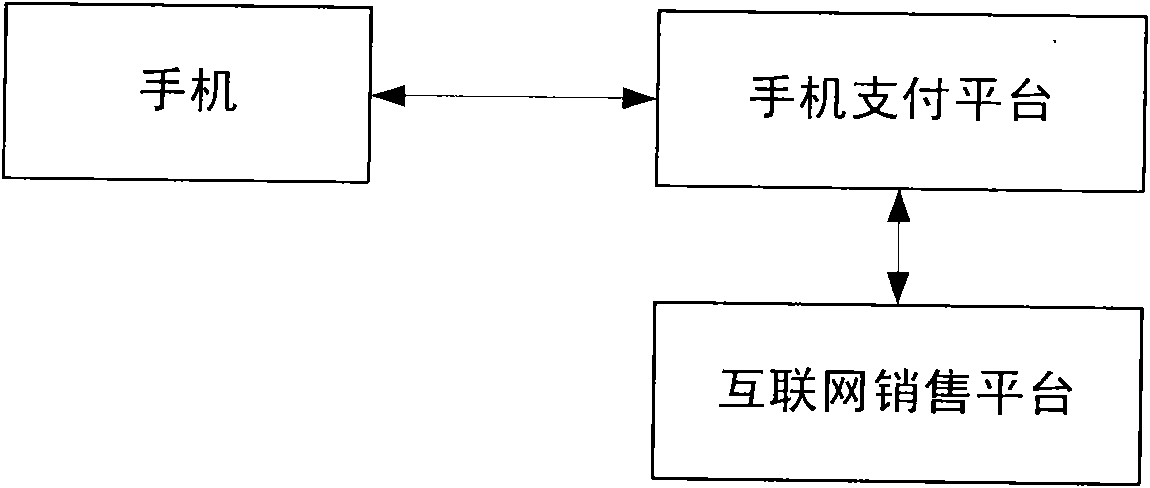
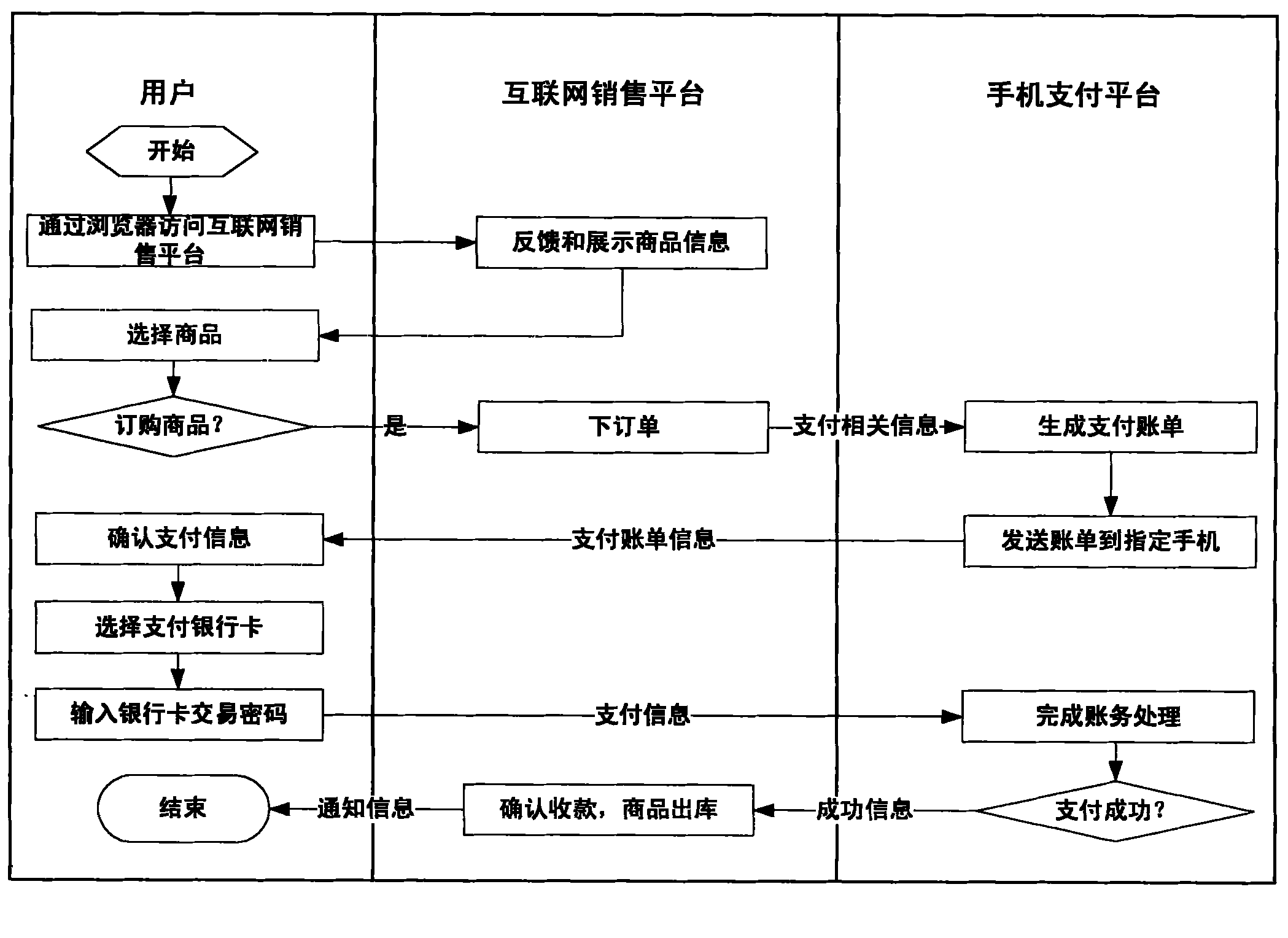
System and method for realizing mobile payment in internet sales
InactiveCN101840549ASimplify the payment processConvenient paymentCommerceWireless communicationSmart cardClient-side
The invention discloses a system and a method for realizing mobile payment in internet sales. The method comprises the following steps that: a user installs a payment client by using a mobile phone which is provided with a financial smart card bound with bank card information; a mobile phone payment platform receives a shopping list after the user shops on an internet sales platform; the mobile phone platform sends a shopping bill through the payment client; the user pays on the mobile phone; the payment client sends the payment information to the mobile phone payment platform after the realization of payment; the mobile phone payment platform sends the payment information to the internet sales platform after checking; and finally, the internet sales platform sends a successful payment message to the mobile phone sales platform and the user, so the payment is finished. Due to the adoption of the system and the method for realizing the mobile payment in the internet sales, the payment process in an internet sales mode is greatly simplified; a user can conveniently and quickly perform remote payment operation; the operation process is very safe; the user can ask others to pay instead at will, so the user or a paying agent can conveniently and quickly pay by using the mobile phone no matter where the user or the paying agent is.
Owner:成都中联信通科技股份有限公司
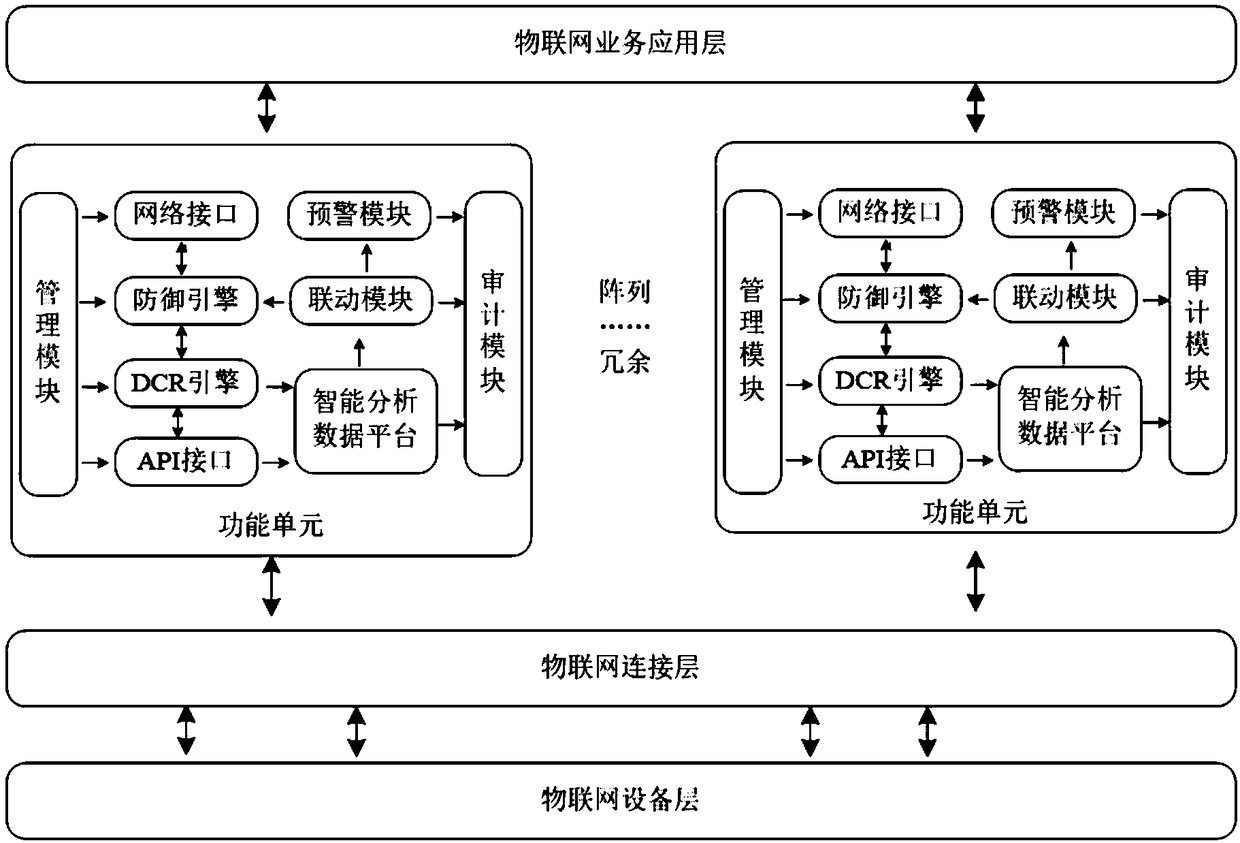
Internet-of-things safe cloud platform based on deep data traffic perception
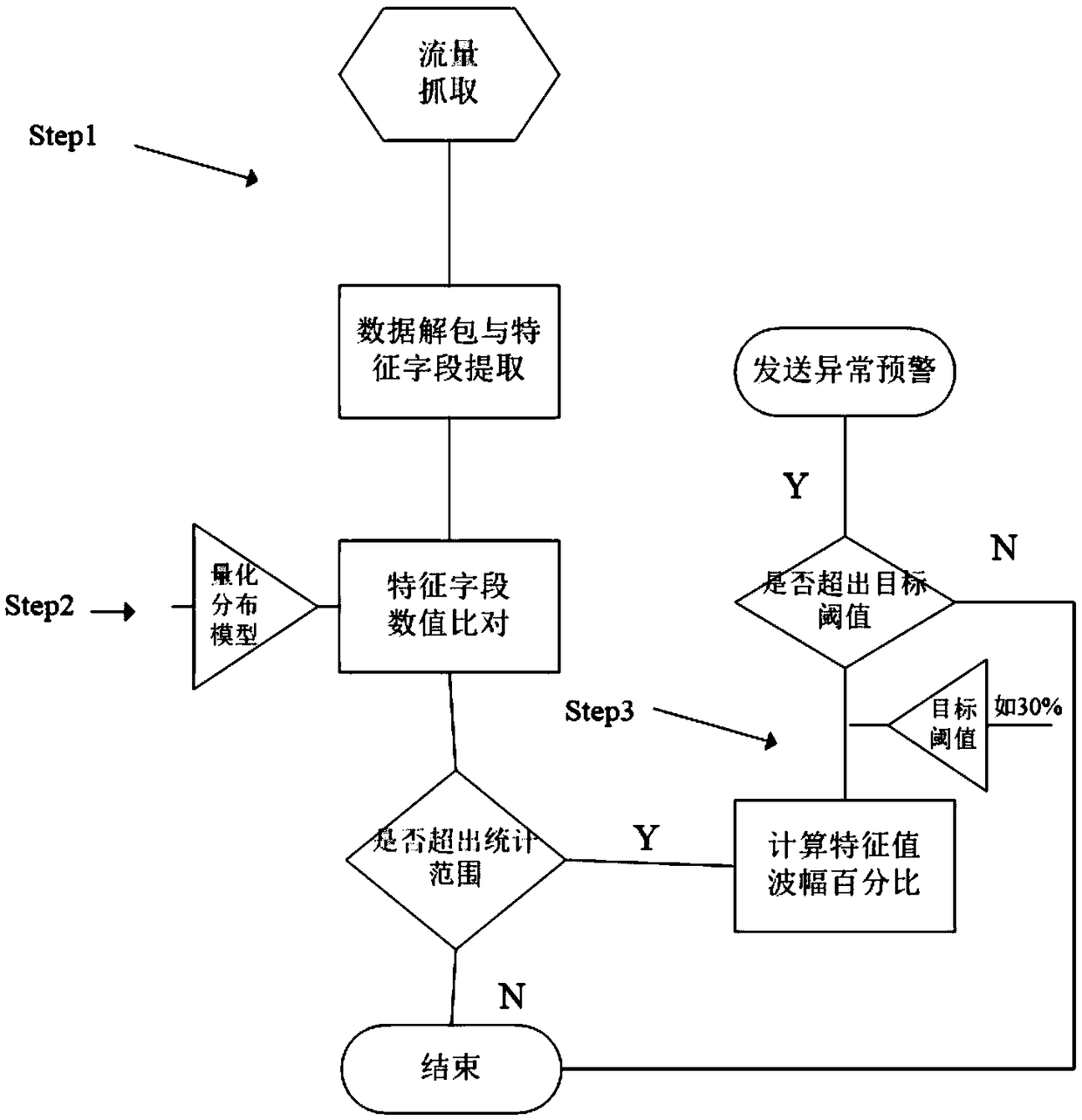
ActiveCN109391700AThe test result is accurateReduce security costsData switching networksData packInternet traffic
The invention discloses an Internet-of-things safe cloud platform based on deep data traffic perception. The Internet-of-things safe cloud platform comprises a functional unit arranged between an Internet-of-things connecting layer and a service application layer, wherein the functional unit comprises a deep engine perception engine which is used for identifying service attribute of a current datapacket, and extracts the characteristic parameter of a characteristic field according to the service kind for performing classification statistics analysis. Particularly the functional unit performsthe following steps of 1, extracting key information of an IP layer, a transmission layer and partial application layer of network data traffic, matching an application characteristic database, and identifying the protocol type of the current data traffic; 2, in the current protocol type, extracting the service data characteristic of the network traffic flow, and constructing a quantitative distribution model of a data load; and 3, based on the service data characteristic, identifying the characteristic field of an unknown traffic data packet and extracting the field value of the characteristic field, recording the change amount and outputting. The Internet-of-things safe cloud platform has advantages of increasing a classification method based on key content identification, realizing deepanalysis to each behavior parameter of Internet-of-things data traffic and effectively ensuring network safety of the Internet-of-things system.
Owner:北京华清信安科技有限公司
Energy internet safety intelligent trading system and method thereof based on block chain technology
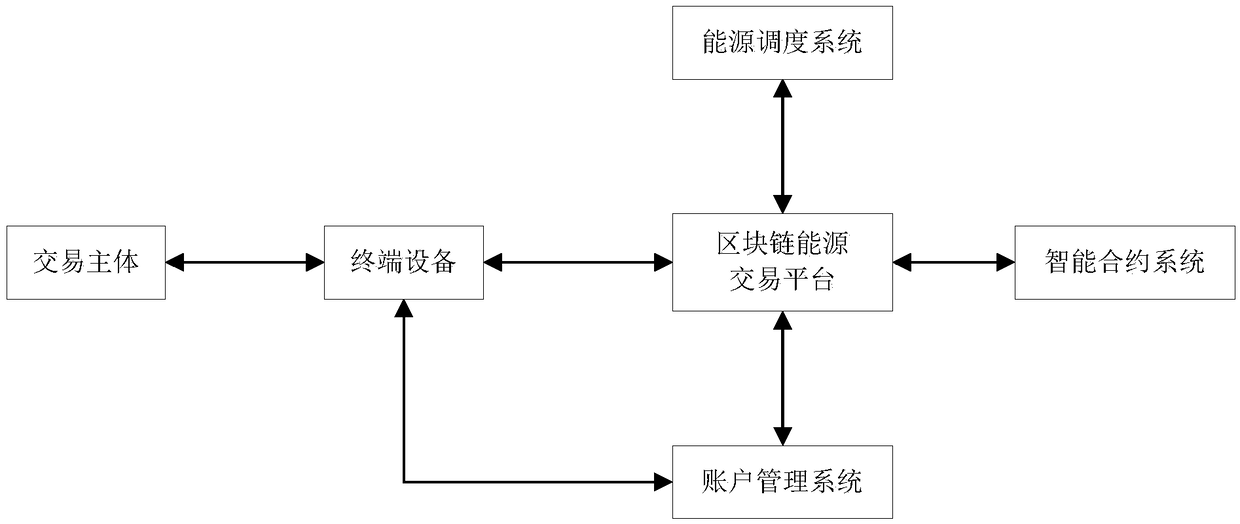
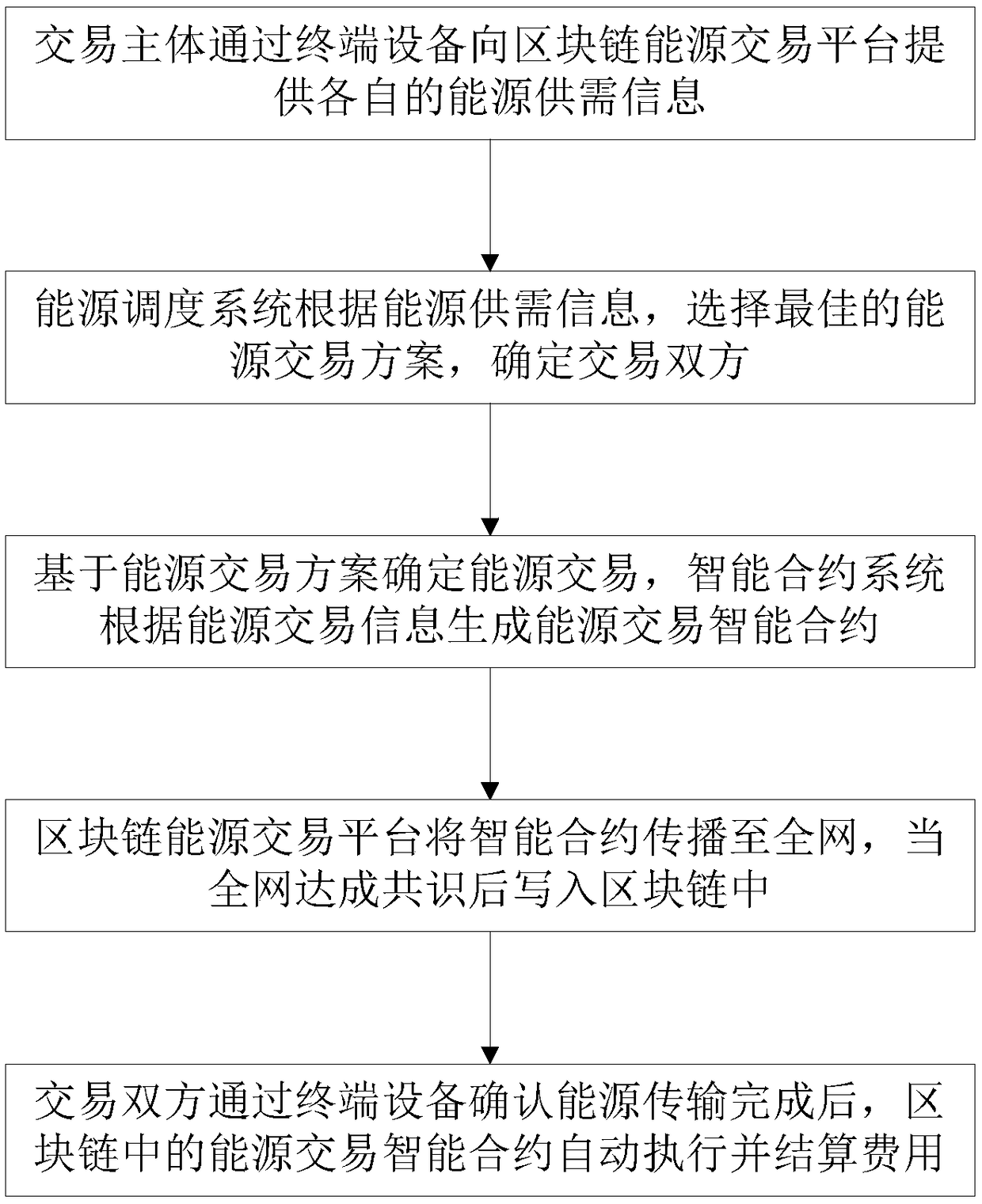
ActiveCN108564471AThe transaction process is simple and efficientHigh degree of automationFinanceInformation technology support systemThird partyTerminal equipment
The invention discloses an energy internet safety intelligent trading system and a method thereof based on block chain technology. The system comprises a block chain energy trading platform, a terminal device, an energy scheduling system and a smart contract system. The terminal device and the block chain energy trading platform are in energy supply and demand information interaction; the block chain energy trading platform and the energy scheduling system are in energy supply and demand information and energy trading scheme interaction; and the block chain energy trading platform and the smart contract system are in intelligent contract information interaction. The trading system combines the block chain technology and a smart contract, and eliminates the role of a third-party trading center in the energy trading process; all participants in the trading are in equal status; and energy trading is executed automatically according to a preset smart contract.
Owner:NANJING UNIV OF POSTS & TELECOMM
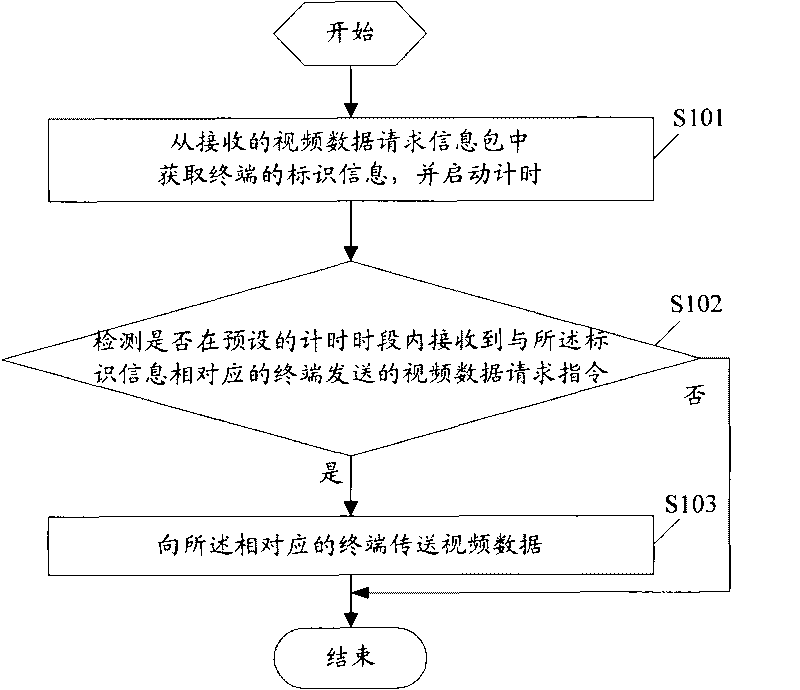
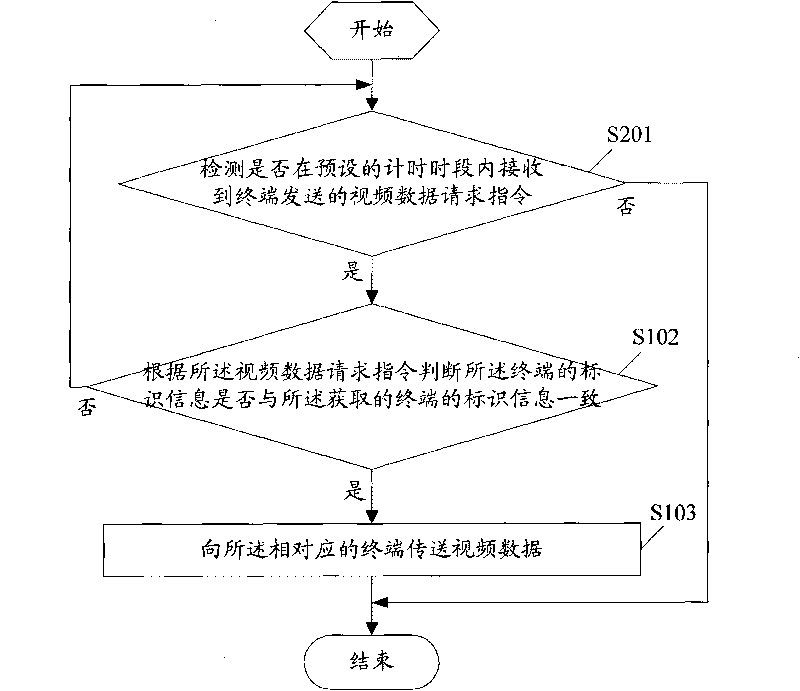
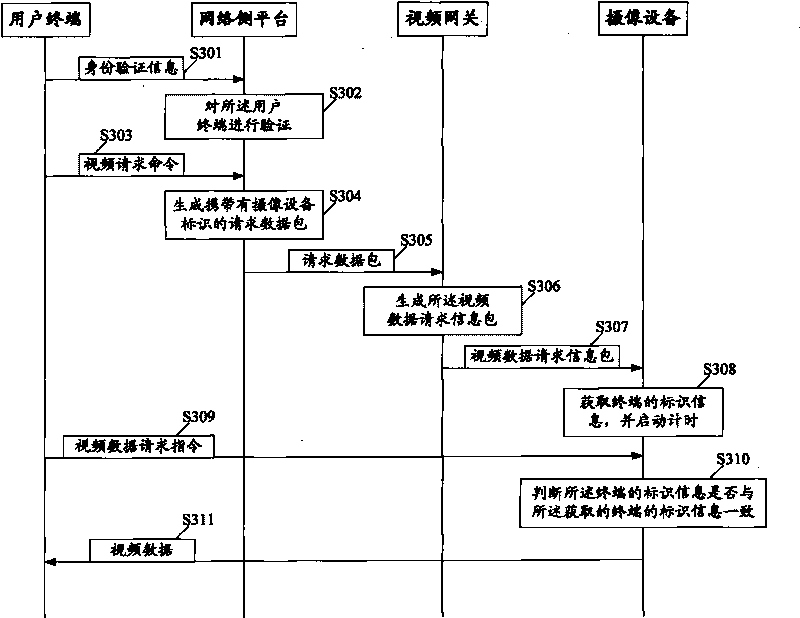
Method and system for transmitting video data and camera equipment
InactiveCN101720030ASecure deliveryFix security issuesData switching by path configurationClosed circuit television systemsReliable transmissionData shipping
The embodiment of the invention discloses a method for transmitting video data, comprising the following steps of: acquiring the mark information of a terminal from a received video data request information packet, and starting timing; detecting whether a video data request command sent by the terminal which corresponds to the mark information is within a preset timing period or not; if so, transmitting the video data to the corresponding terminal. Accordingly, the embodiment of the invention also discloses camera equipment and a system for transmitting the video data. The embodiment of the invention prevents the safety problem that a user can acquire the video data by sending a request for viewing real-time videos to network camera equipment, realizes the safe and reliable transmission of the video data, effectively ensures the individual privacy safety of the user and enhances the user experience because the user can safely, flexibly and fast acquire the video data through a network in any place.
Owner:GUANGDONG TRI SUN ELECTRONICS TECH
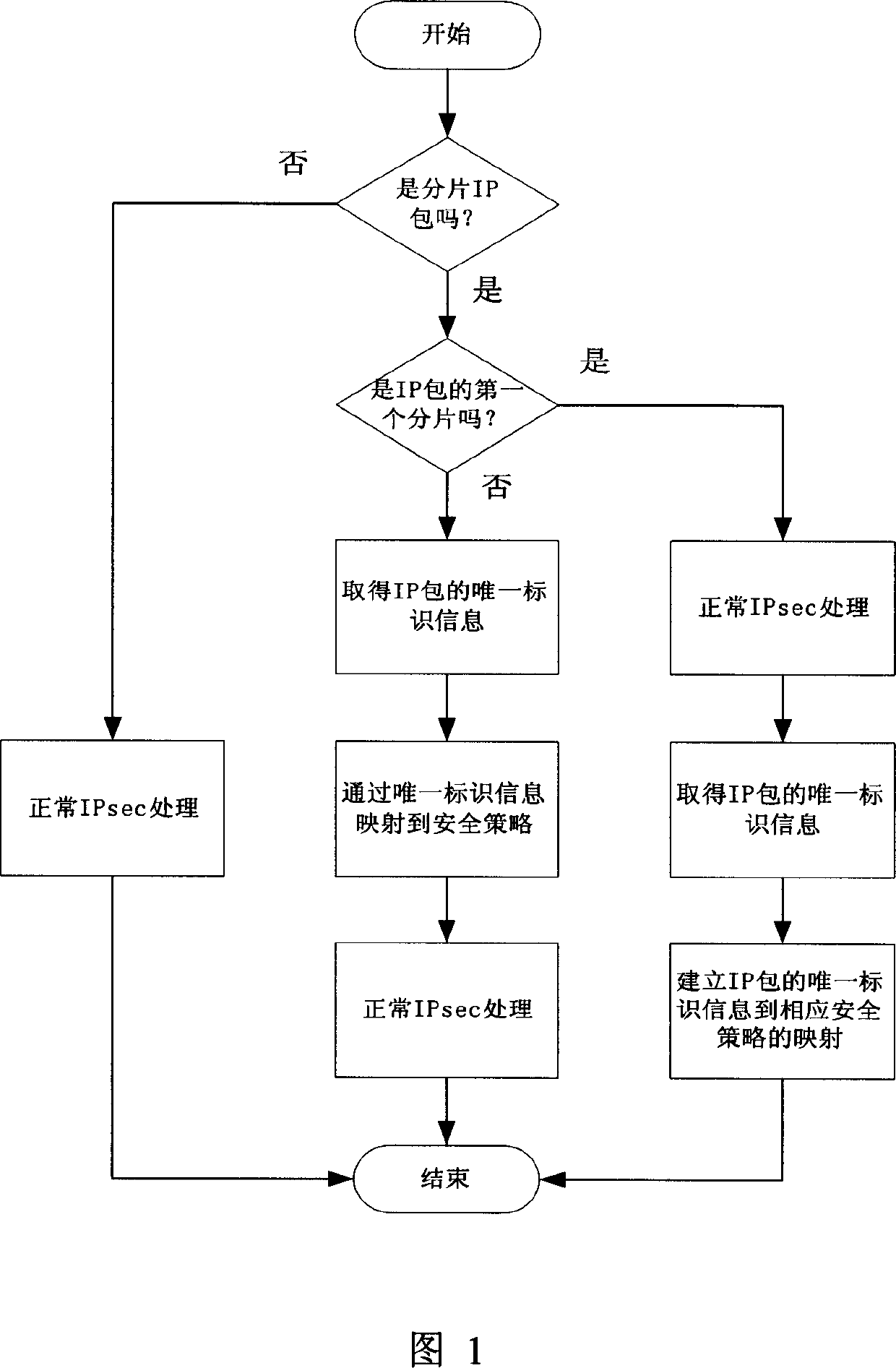
Internet safety protocol high-speed processing IP burst method
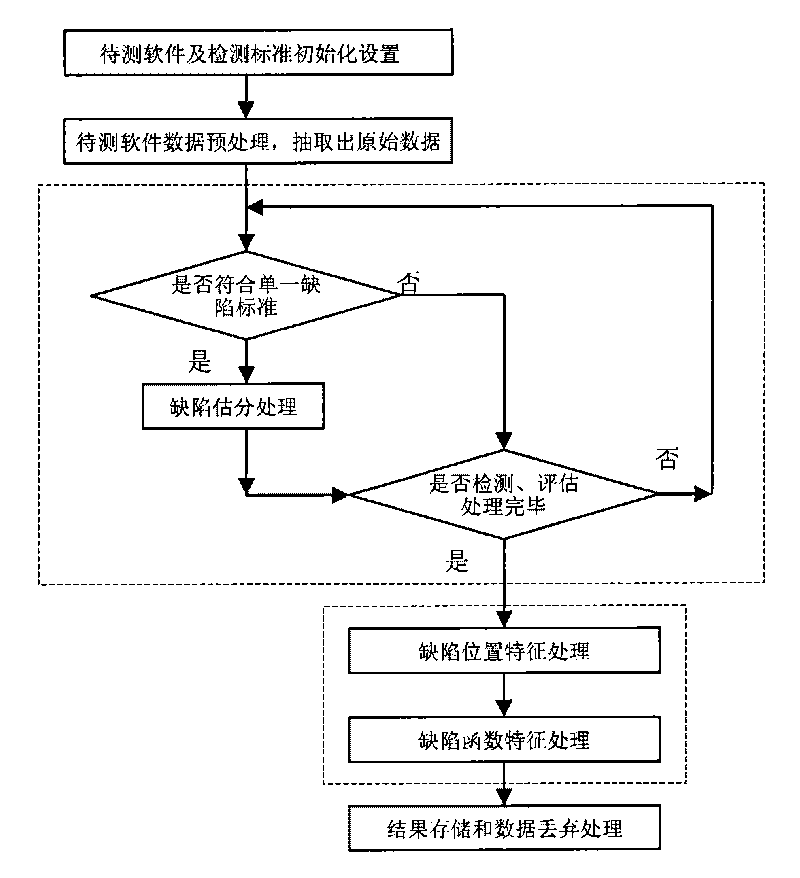
InactiveCN1777174AImprove forwarding performanceIncrease business support coverageSecuring communicationCryptographic protocolIP fragmentation
The method includes procedures: when processing first IP banding, network device of starting use of Internet secure protocol picks up information for unique identifying the IP message from the IP banding; then, building mapping from the information to relevant security policy; when processing other bandings of the IP message, Internet secure protocol maps to relevant security policy through the said unique information so as to implement process in high speed for the IP banding by the Internet secure protocol. Comparing with prior art, the invention overcomes disadvantages of using lots of memory, weighting process burden of gateway, lowering network throughput. The invention raises service range supported by network device, and guarantees high forwarding performance of network device.
Owner:ZTE CORP
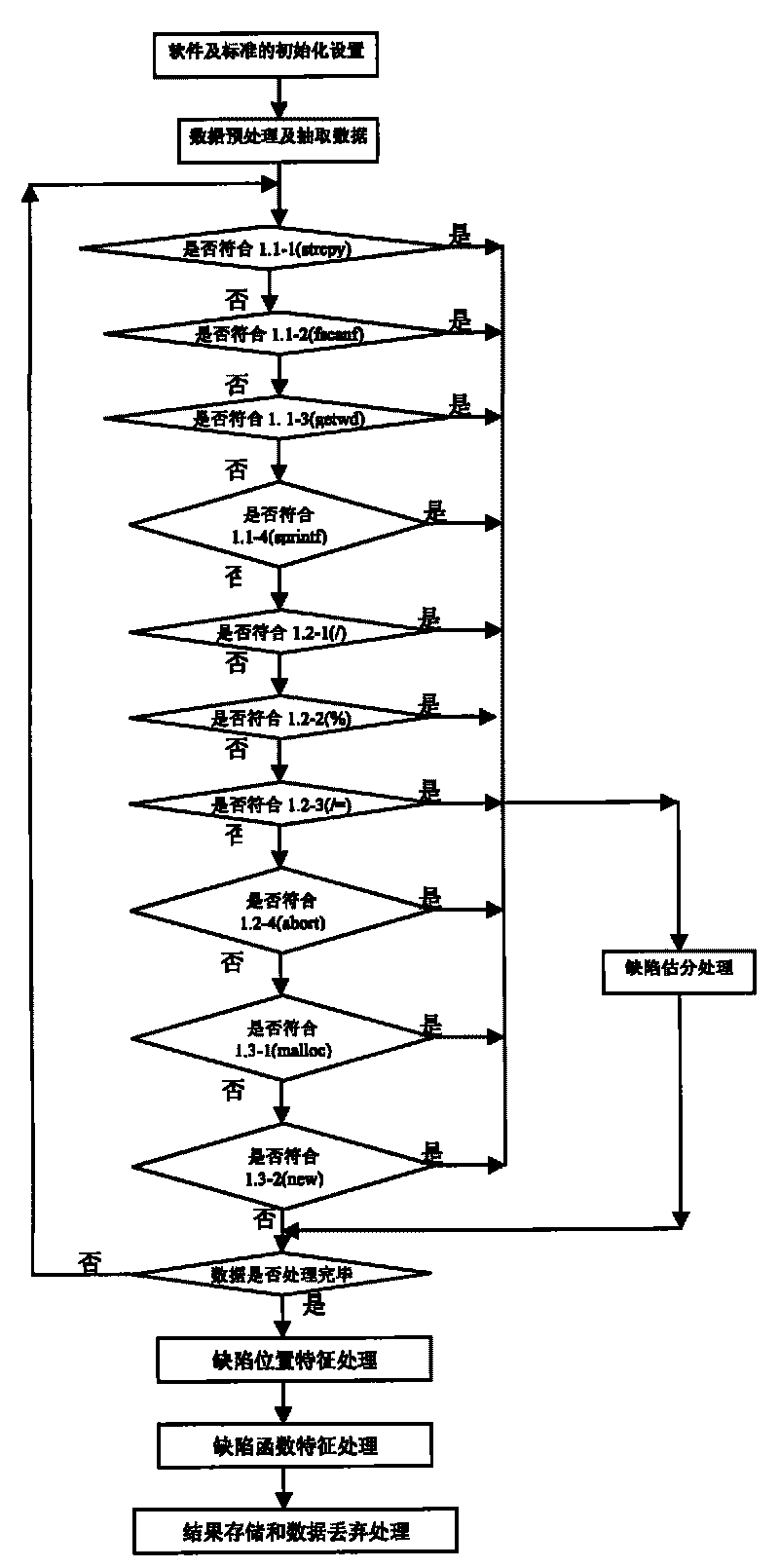
Comprehensive processing method based on software safety defect detection and functional module framework thereof
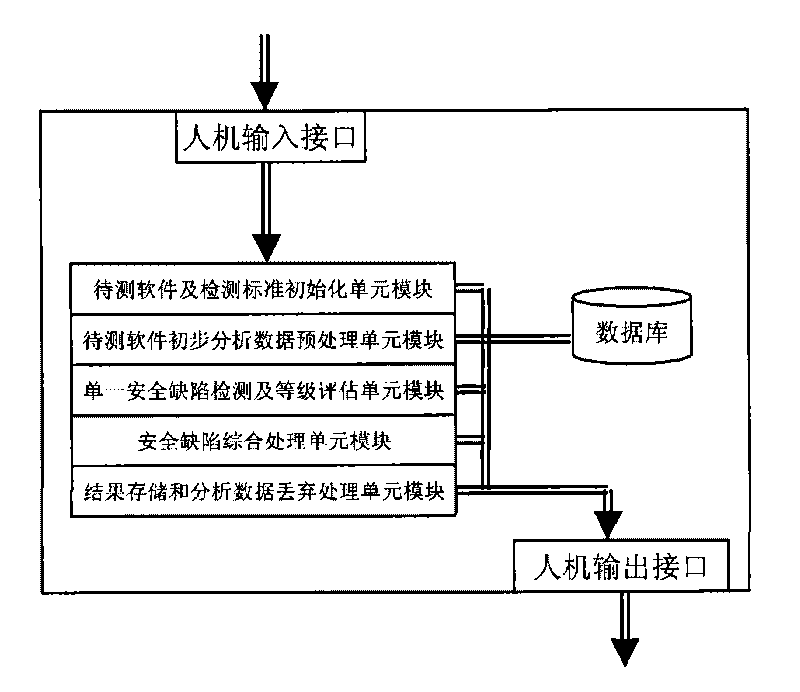
InactiveCN101706749ANo functionNo needSoftware testing/debuggingPlatform integrity maintainanceAnalysis dataIntegrated processing
The invention provides a method based on software safety defect detection and a functional module framework device adopted by the method, belonging to the network safety field. The method comprises initialization of software to be detected and detection standards, preprocessing of preliminary analysis data of the software to be detected, sequential detection according to the single safety defect standard and safety defect grade evaluation, comprehensive processing of the safety defects and detection result storage and data discard. The functional module framework comprises a unit module for carrying out initialization on the software to be detected and the detection standards, a unit module for processing the preliminary analysis data of the software to be detected, a unit module for carrying out detection according to the single safety defect standard and evaluating the safety defect grades, a unit module for carrying out comprehensive processing on the safety defects, a unit module for storing the detection results and discarding the data and a database. The invention can carry out overall detection and comprehensive processing on the safety defects of the software and has the characteristics of wide detection range, strong adaptability to the safety defects of the software, high accuracy and reliability of detection and comprehensive processing results and no special requirements on the functions and properties of the software, etc.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
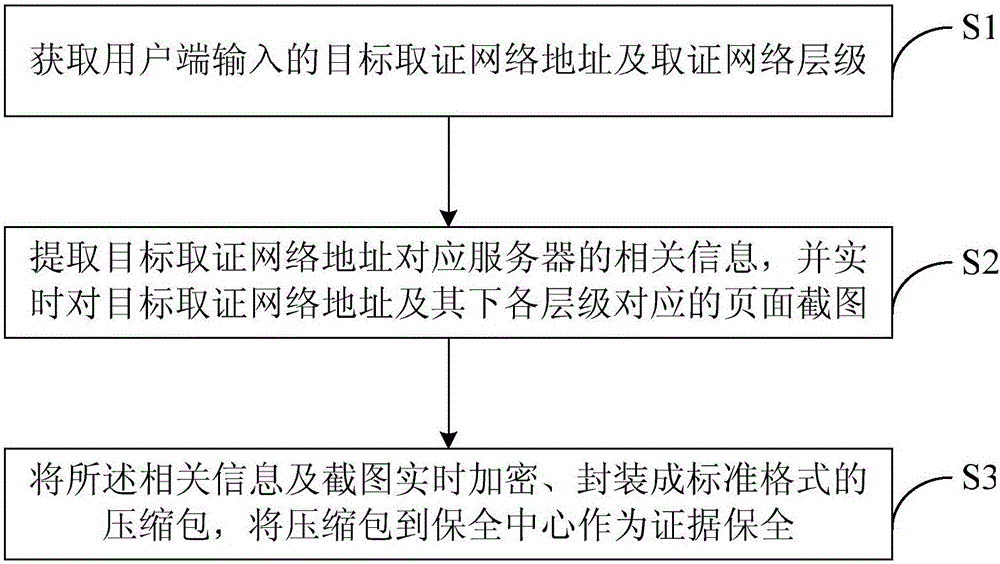
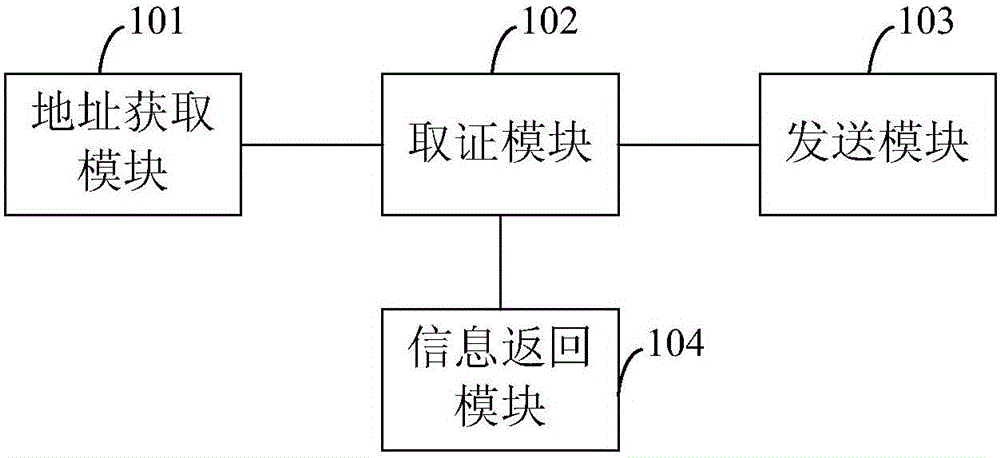
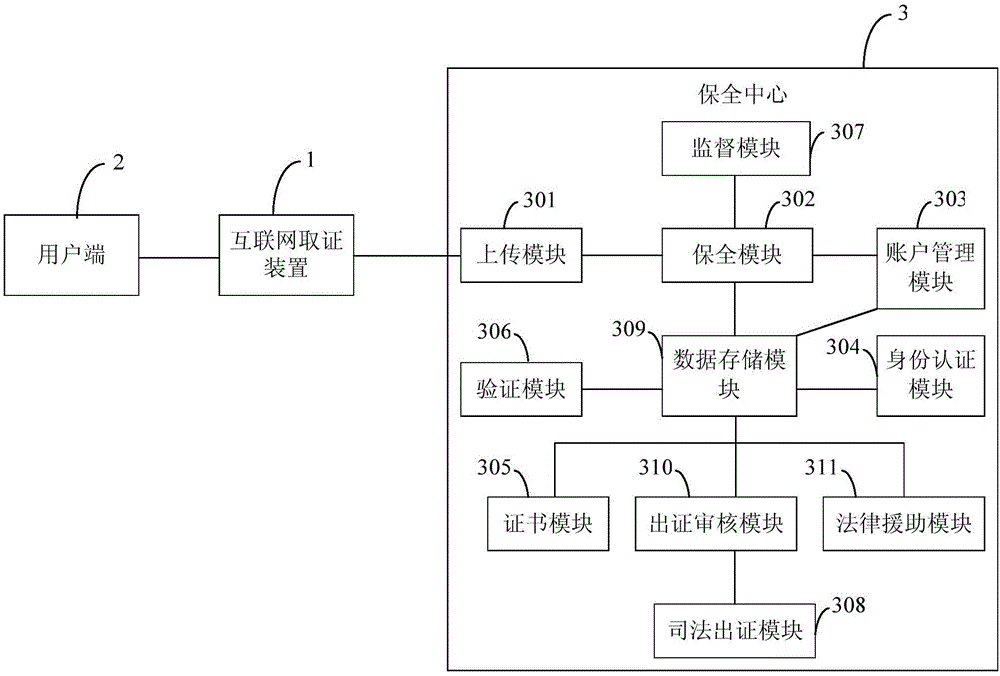
Internet evidence obtaining method, device and Internet security system
InactiveCN106254078AImprove securityAvoid problems that are easy to be tampered with and have low credibilityEncryption apparatus with shift registers/memoriesUser identity/authority verificationRelevant informationNetwork addressing
The invention belongs to the Internet technical field and discloses an Internet evidence obtaining method. The method includes the following steps that: S1, a target evidence obtaining network address and an evidence obtaining network level which are inputted by a user end are obtained; S2, the relevant information of a server corresponding to the target evidence obtaining network address is extracted, and content involving infringement is intercepted in real time; and S3, the relevant information and the intercepted content are encrypted in real time and packaged into a compressed packet of a standard format, and the compressed packet is transmitted to a security center, so that the compressed packet can be protected as evidences. According to the Internet evidence obtaining method, the Internet evidence obtaining device and the Internet security system of the invention, the relevant information of the server and the content about infringement are directly obtained from the server corresponding to the target evidence obtaining network address, since the security of the network server is higher than that of a client browser, the problem of low reliability which is caused by a condition that evidences obtained by the client browser are easy to tamper can be solved.
Owner:冯颖
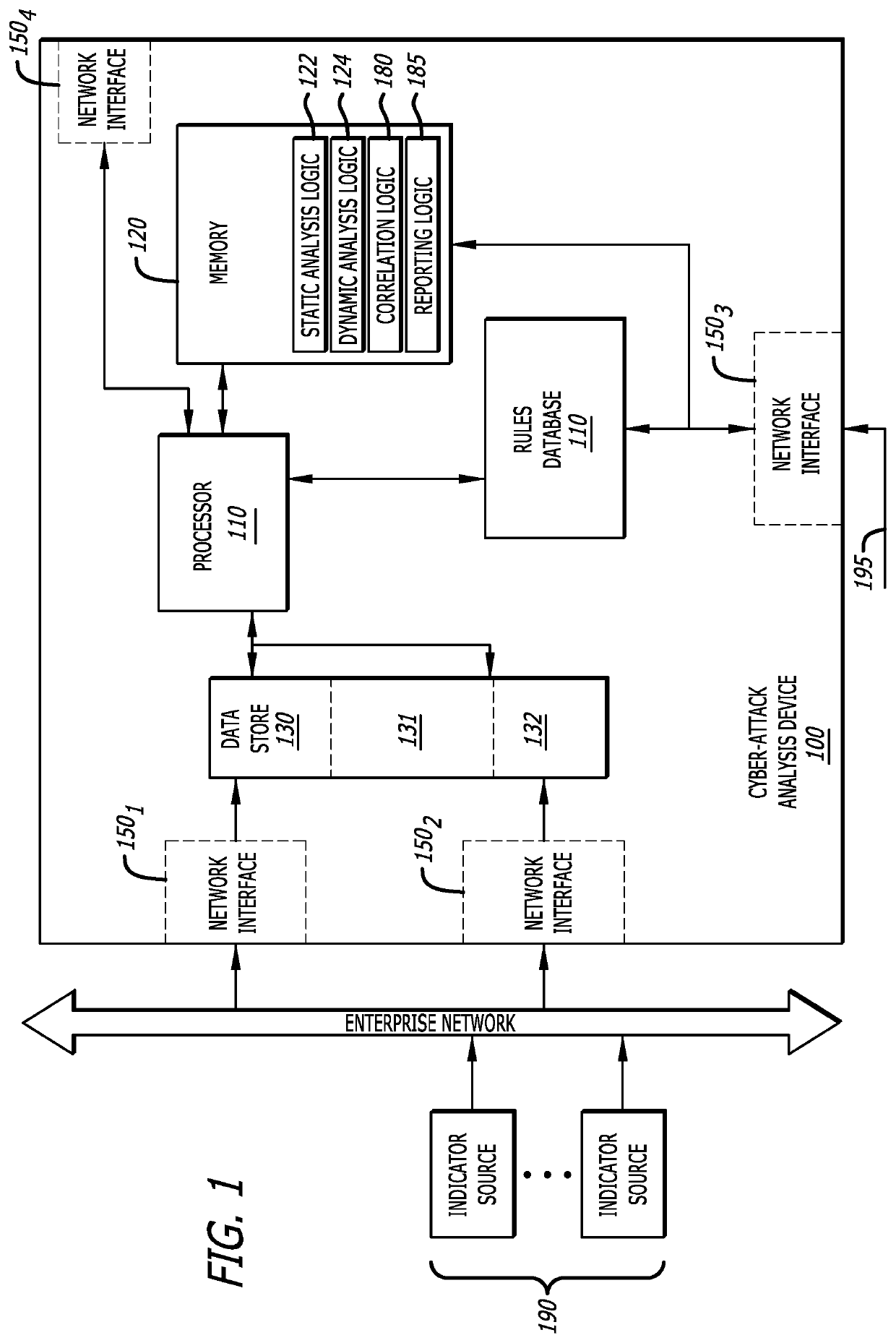
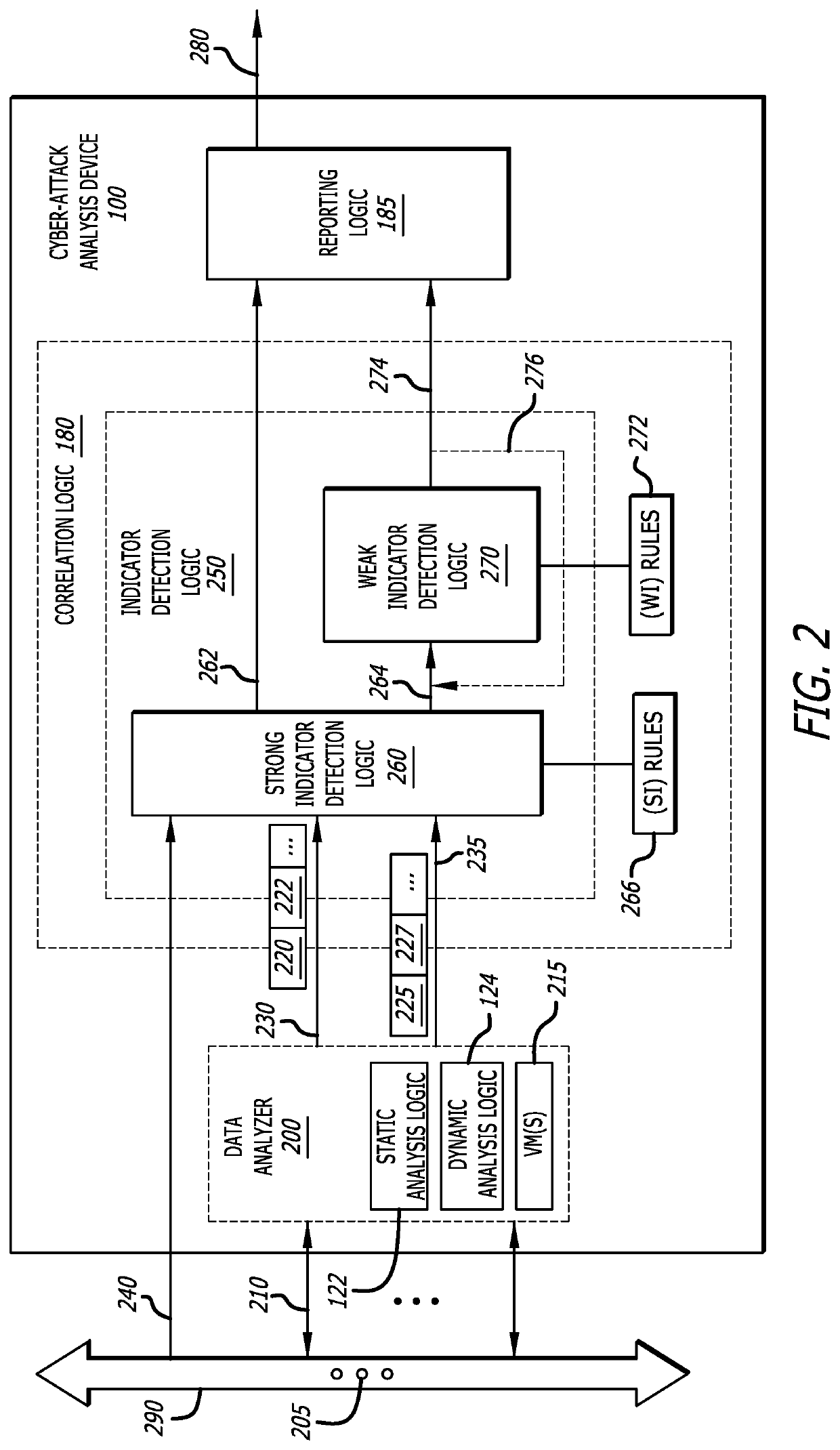
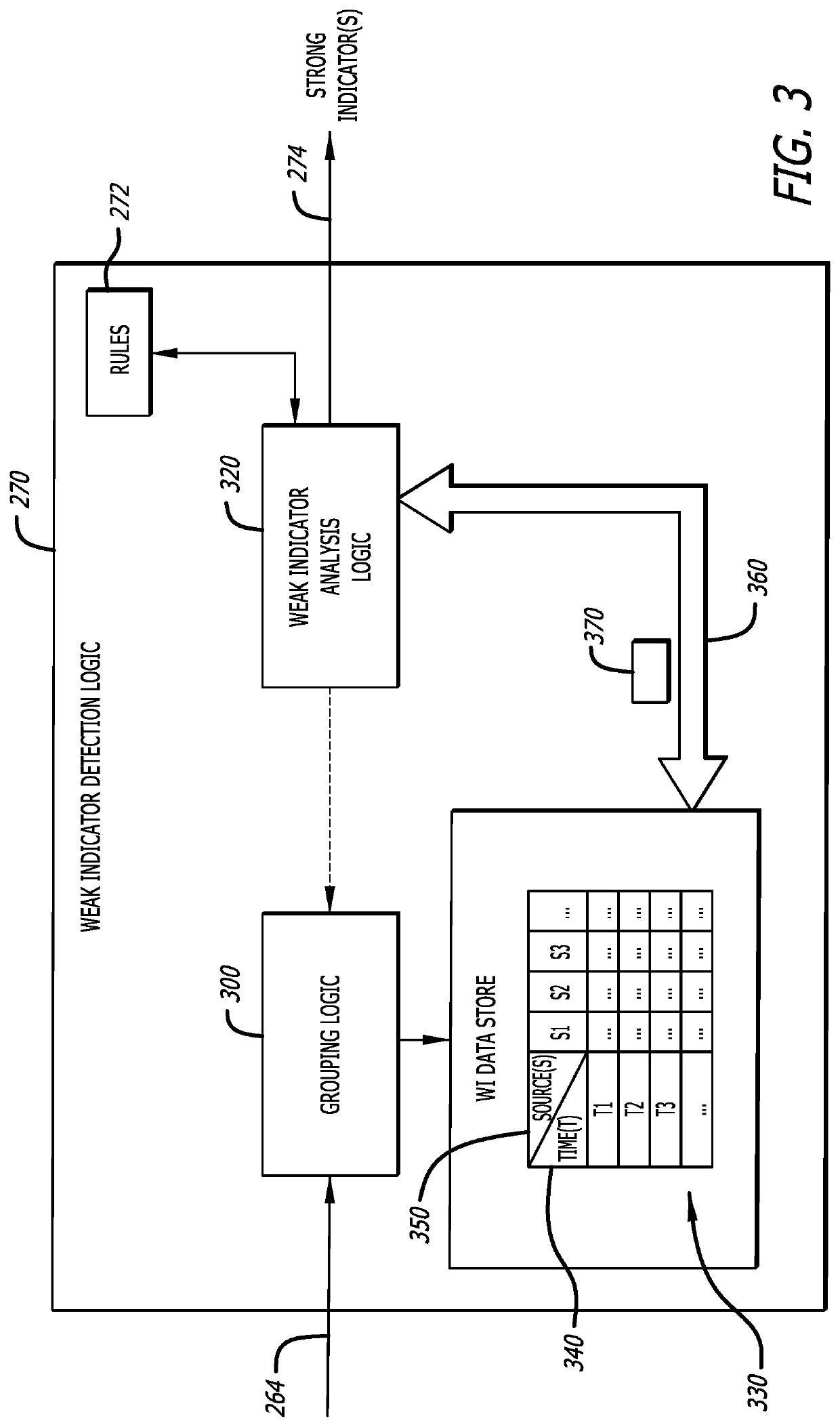
Cyber-security system and method for weak indicator detection and correlation to generate strong indicators
ActiveUS10601848B1Unauthorized memory use protectionComputer security arrangementsCyber-attackAttack
A method for detecting a cyber-attack is described. The method features (i) collecting a first plurality of weak indicators, (ii) grouping a second plurality of weak indicators from the first plurality of weak indicators where the second plurality of weak indicators being lesser in number than the first plurality of weak indicators, and (iii) performing a correlation operation between the second plurality of weak indicators and one or more patterns or sequences of indicators associated with known malware. A weak indicator of the first plurality of weak indicators corresponds to data that, by itself, is not definitive as to whether the data is associated with a cyber-attack being conducted on a source of the weak indicator.
Owner:MANDIANT +1
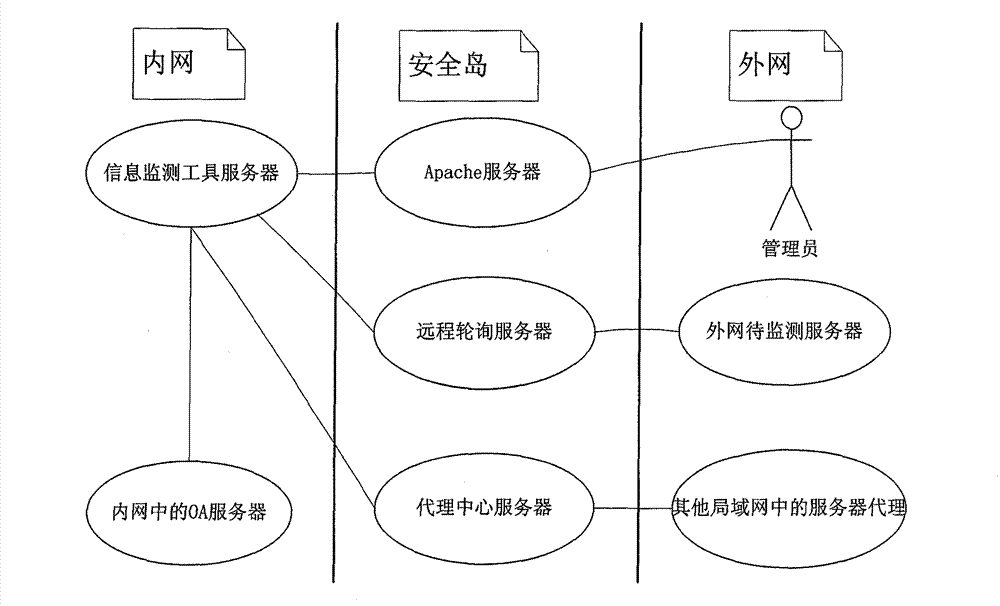
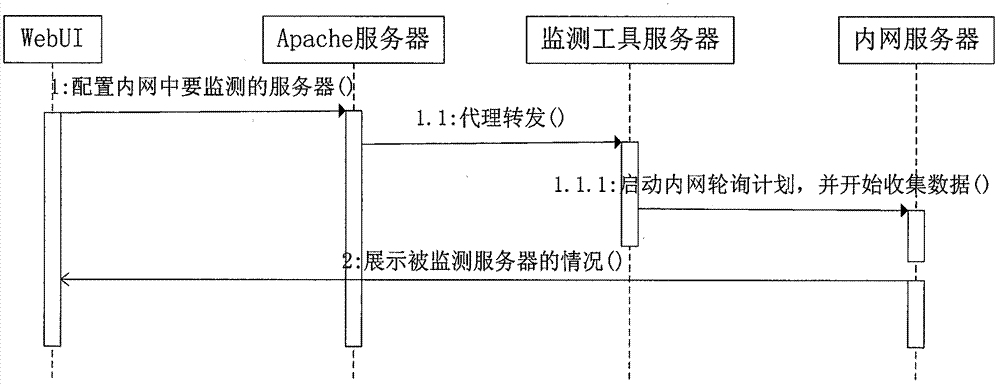
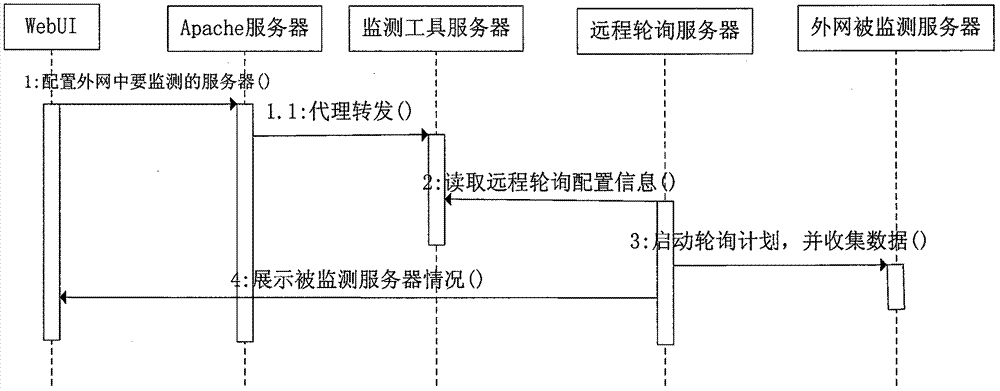
Server network monitoring mode
The invention discloses a safety island based network and realizes a network monitoring mode which is capable of monitoring servers among different networks. For a special network where internet safety is particularly important, the safety island based network realizes a novel monitoring mode for monitoring servers among different networks, such as servers among internal networks, servers in the Internet and other local area network servers. Further more, a server to be monitored can be configured easily through a WebUI (Web User Interface).
Owner:PCI TECH GRP CO LTD
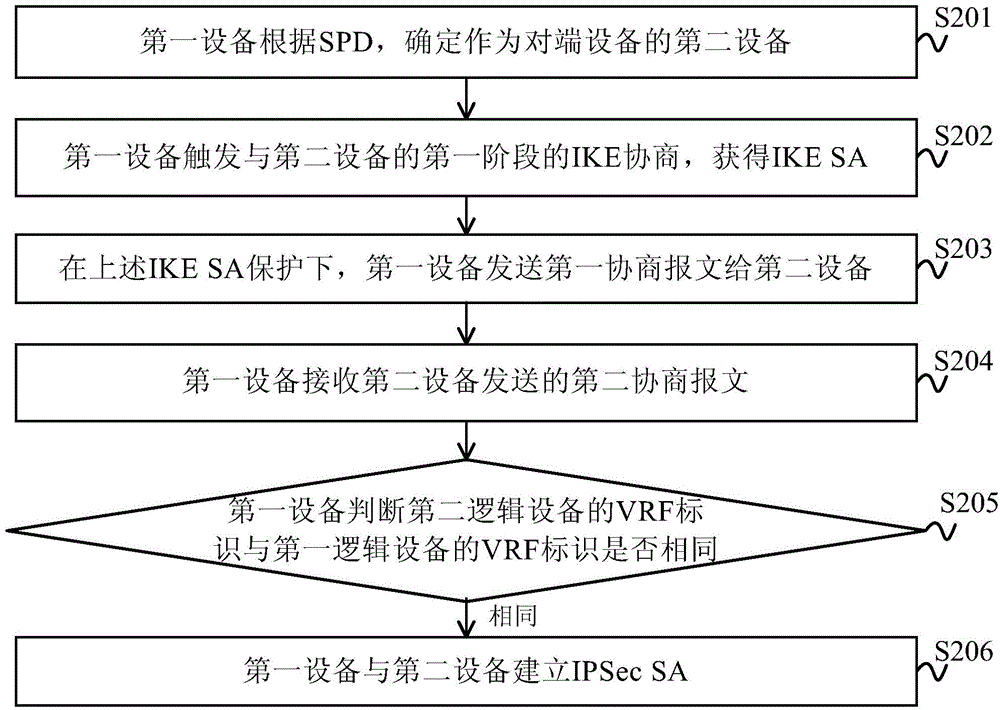
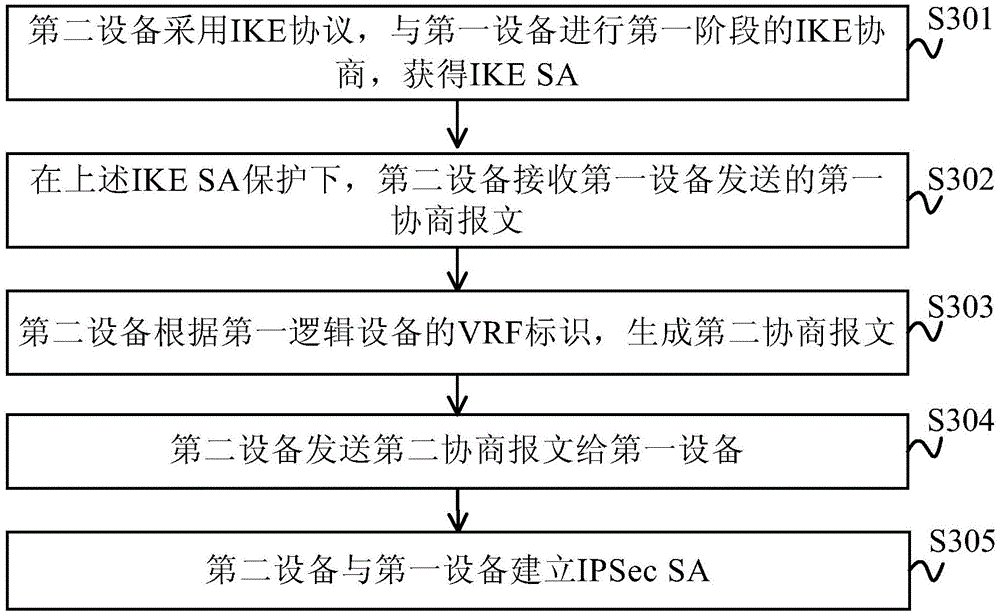
Method and device for establishing Internet safety protocol safety alliance
The invention provides a method and device for establishing an Internet safety protocol safety alliance. In the embodiment of the invention, a VRF identifier is carried in a negotiation message as a part of the characteristics of the flow needed to be protected for exchange in an IKE negotiation process, for example, a first negotiation message carries a VRF identifier of a first logic device, a second negotiation message carries a VRF identifier of a second logic device, an IPSec SA is established through IKE negotiation according to various VRF identifiers, and various IPSec SAs are chosen to be encrypted for the flow of various VRF identifiers according to a safety strategy. The method and device can realize that the operator provides the IP spaces which can be independently programmed to various logic devices on the basis of the VRF identifier, provides a fully isolate IPSec protection function and realizes the flow distinguishing between various companies. Besides, one IP address is adopted to protect the flows of multiple companies in order to save the IP address source of the public network.
Owner:HUAWEI DIGITAL TECH SUZHOU
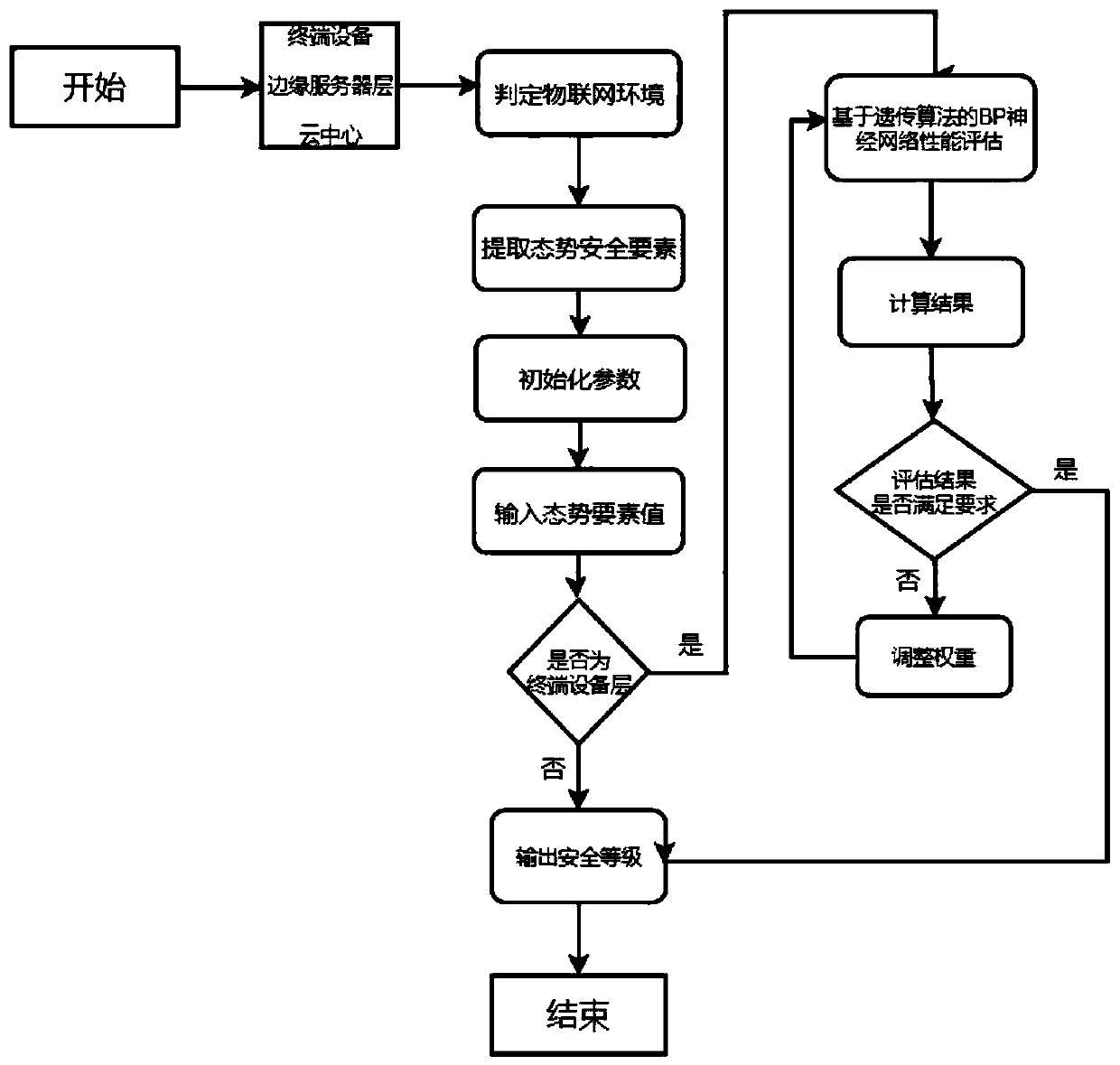
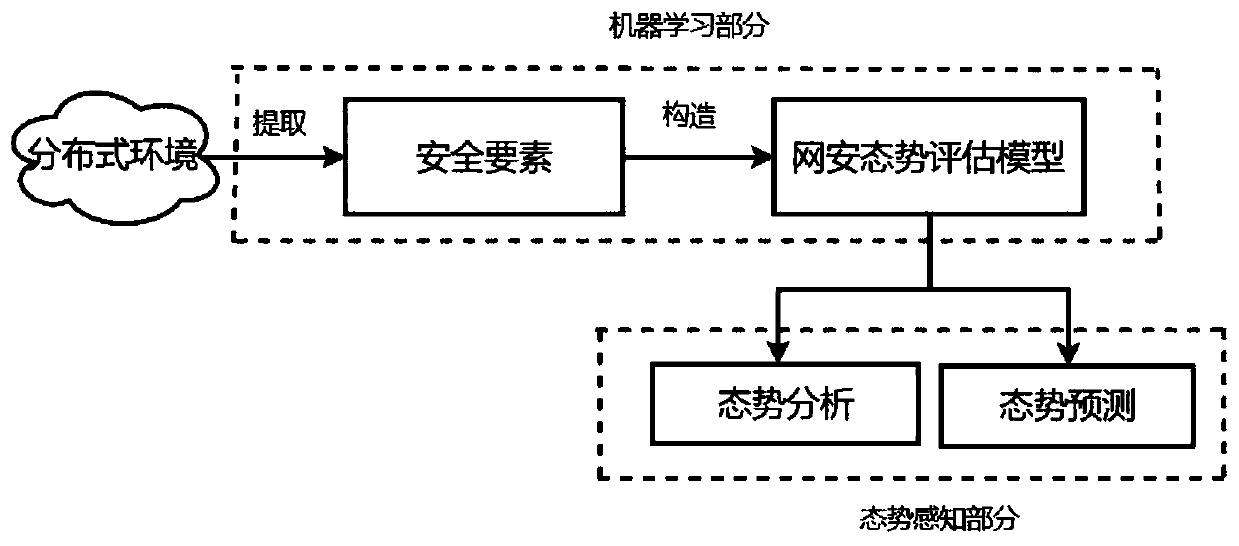
Internet of Things environment situation awareness method based on machine learning
ActiveCN110830287AReal-time monitoring of security statusThe result is accurateData switching networksNeural learning methodsEngineeringArtificial intelligence
An Internet of Things environment situation awareness method based on machine learning comprises two parts of machine learning and situation awareness, the safety problem existing in an Internet of Things distributed network environment is more complex, and a traditional situation awareness method mainly aims at a centralized network and cannot be effectively applied to the Internet of Things environment. Situational safety elements existing in a distributed environment are reasonably extracted; and modeling the extracted situation elements by using a machine learning method, constructing a network safety situation evaluation model of the Internet of Things environment, and analyzing and predicting the safety situation of the environment, thereby assisting safety personnel or users to respond and troubleshoot safety threats in the environment in time.
Owner:陕西粟米科技有限公司
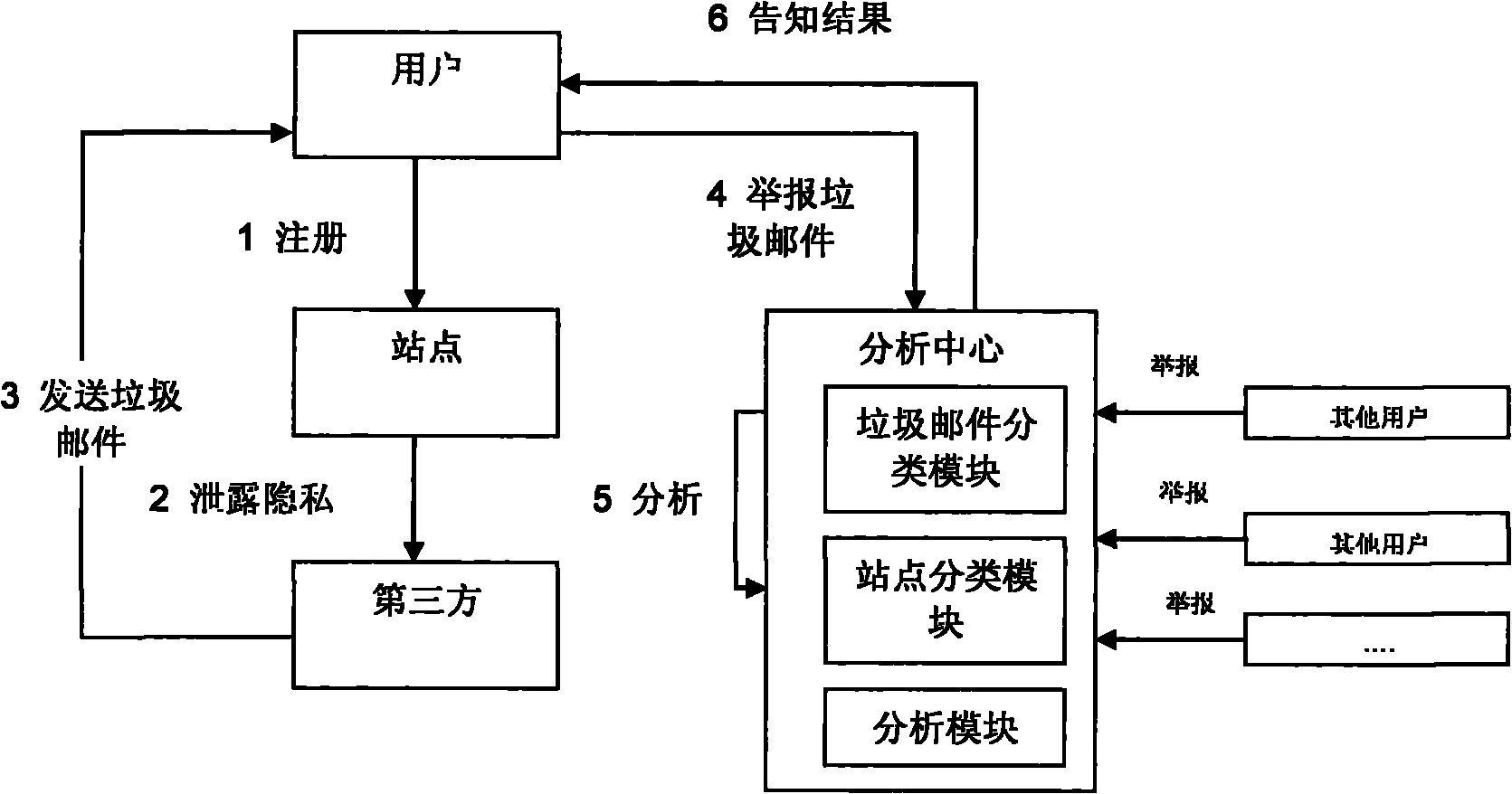
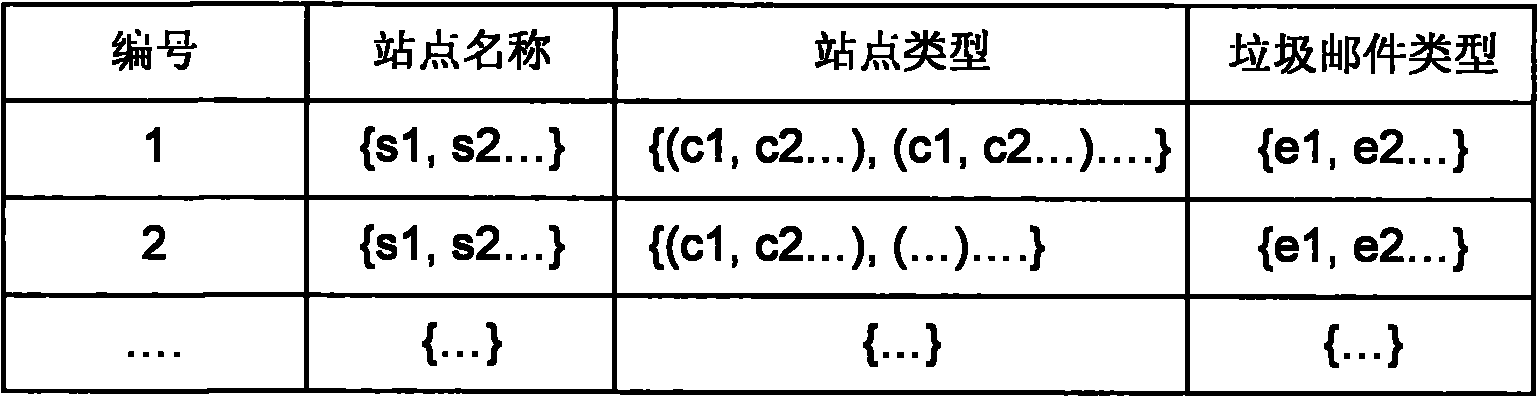
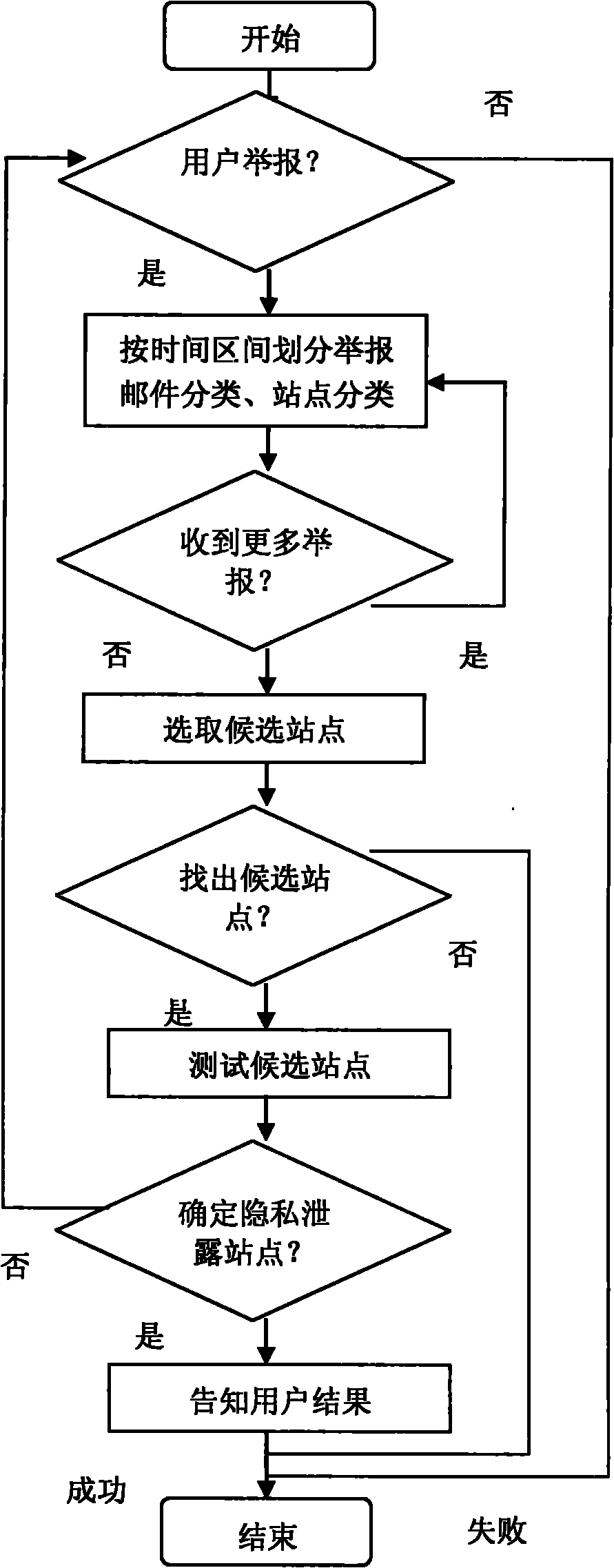
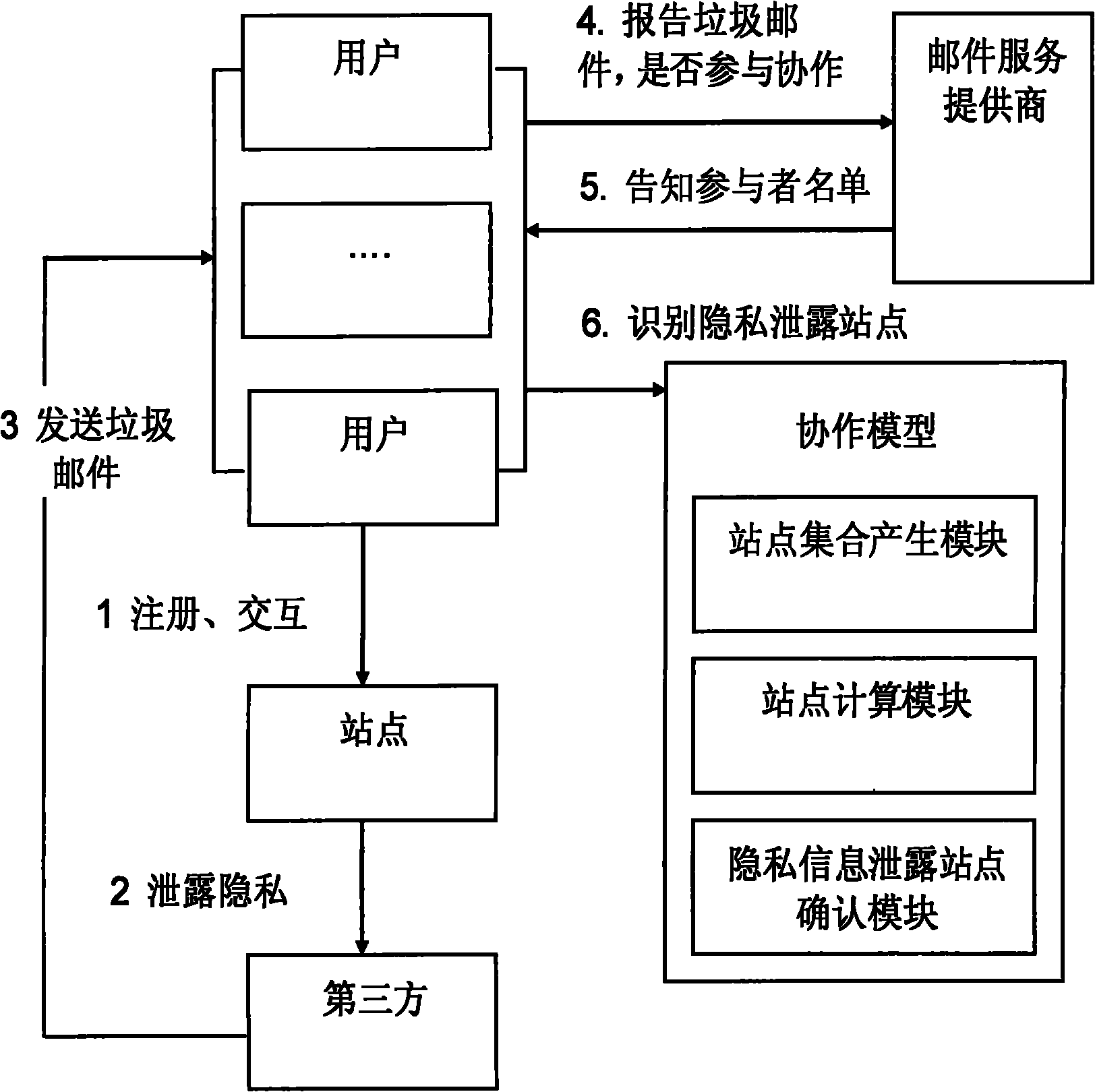
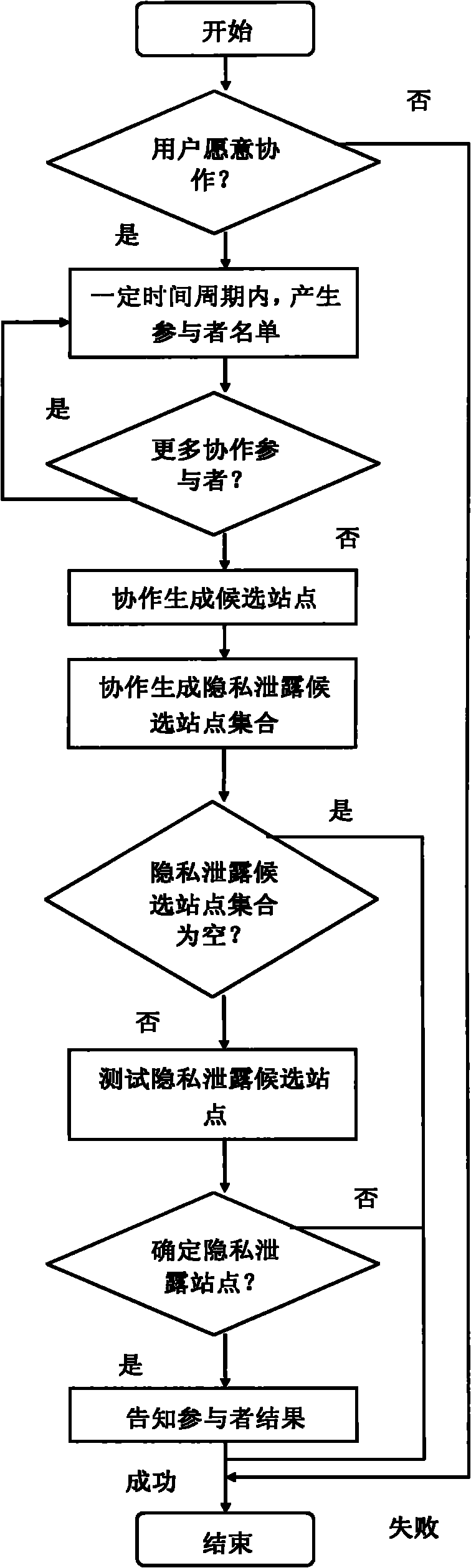
Method for tracking leakage of private information
InactiveCN101819616APrivacy protectionProtect private informationComputer security arrangementsTransmissionThird partyInternet privacy
The invention discloses a method for tracking the leakage of private information, and belongs to the field of computer network safety for tracking the leakage of the private information in a network environment. The invention aims to provide the method for tracking the leakage of the private information and solve the problem that a user may receive advertising junk mails frequently after the private information of the user is leaked to a third party by a Web service site. An analysis centre is adopted in the invention, and the user can report the junk email to the analysis centre after receiving the junk email, so the website which leaks the private information can be found out by the analysis method of the analysis centre and notified to the user. The method of the invention can be used for tracking the website which leaks the private information, so that the user can change the trust or interactive mode of the website which leaks the private information and even resort to laws so as to protect the private information.
Owner:BEIJING UNIV OF TECH
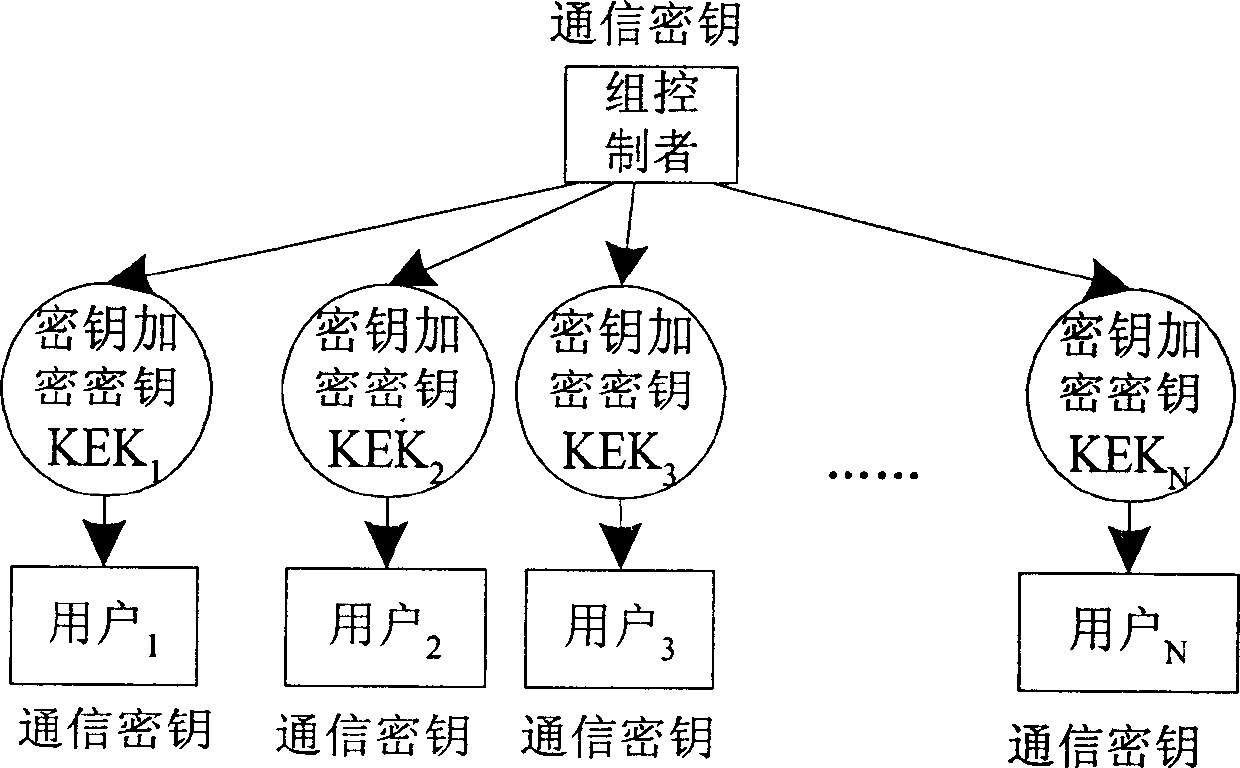
Group broadcast cipher key managing method based on physical layer
InactiveCN1716853AReduce overheadEfficient managementSpecial service provision for substationMultiple keys/algorithms usageExtensibilityMulticast network
The present invention discloses a kind of managing method for group transmission key secret code based on the physical levels of group transmission network. It relates to internet safety group transmission field, which is used as a means for graduating subgroup, group transmission key secret code administration and group transmission communication in the group transmission service, thus reducing the expenses for the renewal of the group key secret code. The source of group transmission uses the local subgroup communication key secret code with the SEK data, transmit it to the physical subgroup; and after the local physical subgroup of the group safety agent has received, deciphered it, then it uses the communication key secret code with enciphered data of the logical subgroup to transmit it to other physical subgroups, and the other physical subgroups of the group safety agents, having received it, use the logical subgroup communication key secret code with encryption group to transmit it to the group transmitting receivers of the physical subgroup. The group transmitting receivers use the local transmission key secret code to obtain data through decryption. The invention can effectively divide the subgroups and resolve the problem of the key secret code administration of the safety group transmission, thus reducing the expenses for the renewal of the group transmission key secret code without limitation to scope and with favorable expansion.
Owner:UNIV OF SCI & TECH OF CHINA
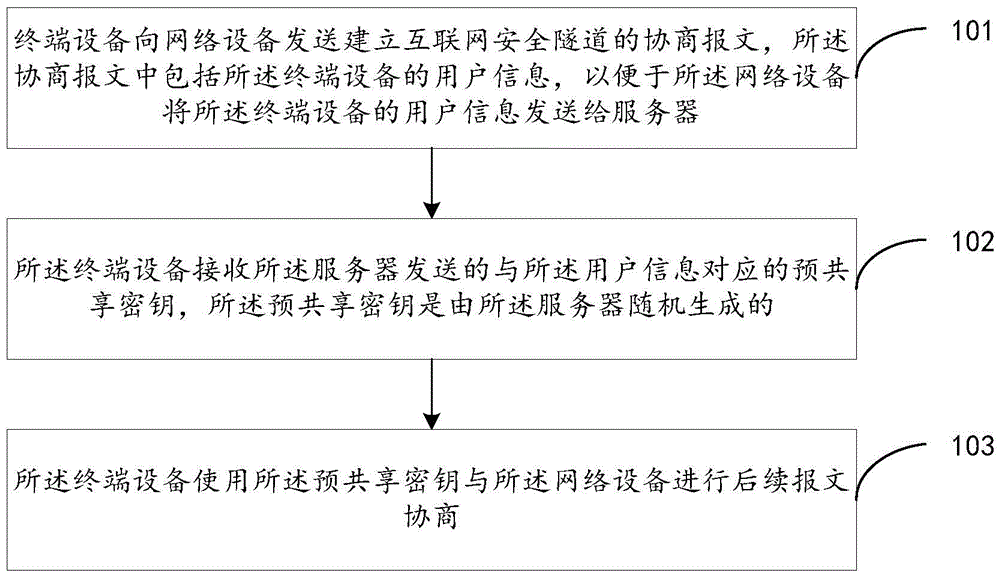
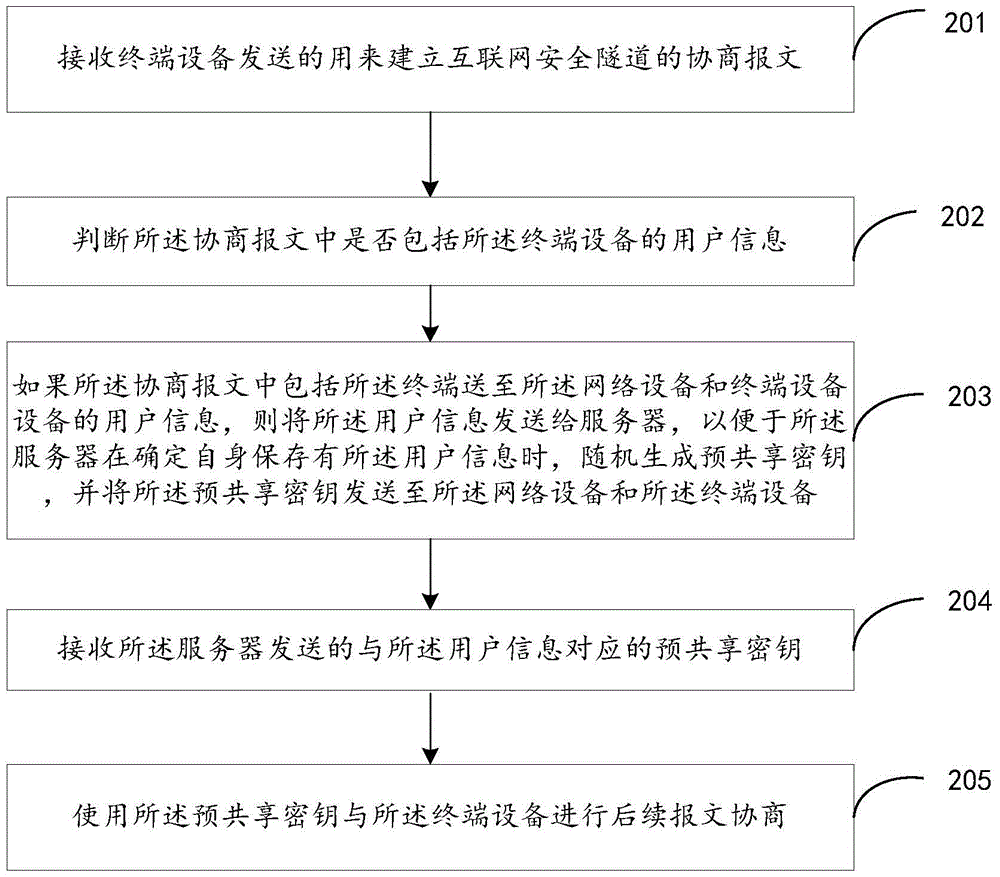
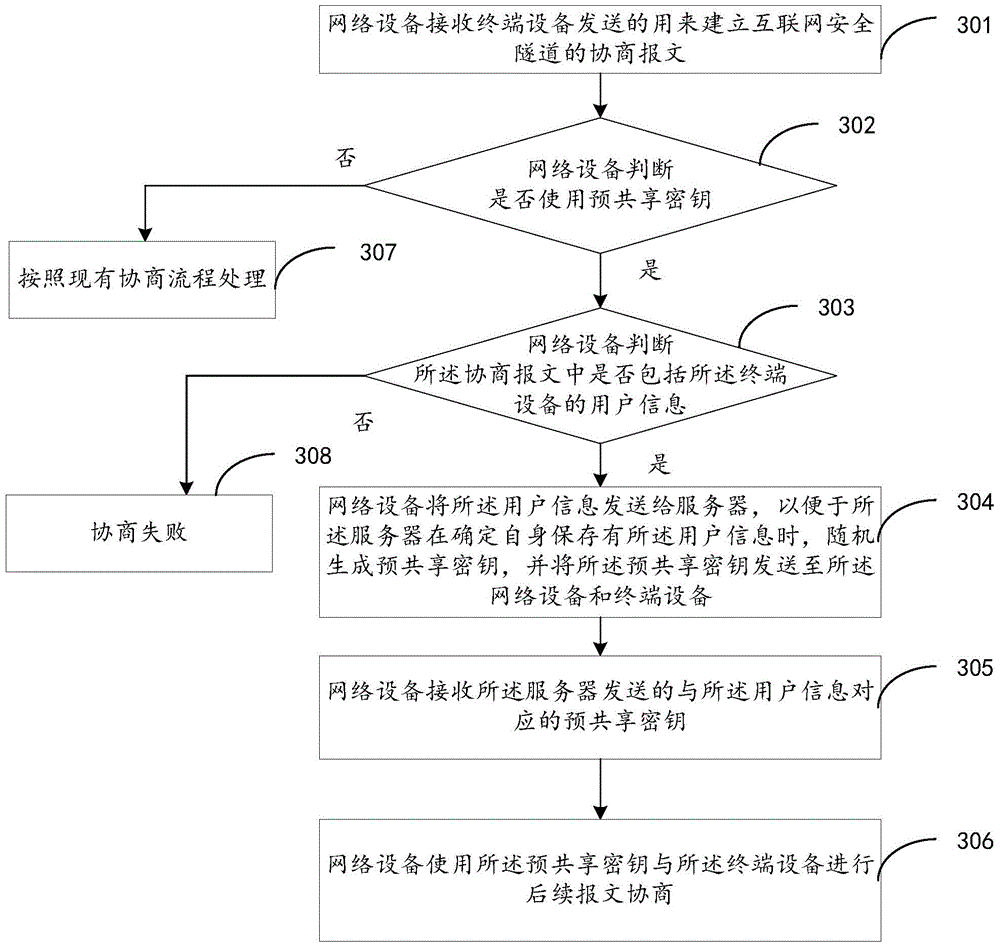
Pre-shared key obtaining method, pre-shared key distribution method and pre-shared key distribution device
ActiveCN105763318AImprove securityKey distribution for secure communicationDistribution methodTerminal equipment
The present invention provides a pre-shared key obtaining method, a pre-shared key distribution method and a pre-shared key distribution device. The pre-shared key obtaining method comprises: receiving negotiation message for building an Internet safety tunnel sent by a terminal device; determining whether the negotiation message includes the user information of the terminal device or not; if the negotiation message includes the user information of the terminal device, sending the user information to a server to facilitate randomly generating a pre-shared key when the server is determined to store the user information by itself, and sending to pre-shared key to a network device and the terminal device; receiving the pre-shared key, corresponding to the user information, sent by the server; and employing the pre-shared key and the terminal device to perform follow-up message negotiation. According to the embodiment of the invention, the pre-shared key obtaining method, the pre-shared key distribution method and the pre-shared key distribution device employ a pre-shared key to perform negotiation so as to prevent the pre-shared key from being solved by attackers and avoid pretending to be a real user to access the internal network for data stealing, therefore the safety of the IKE negotiation is improved.
Owner:NEW H3C TECH CO LTD
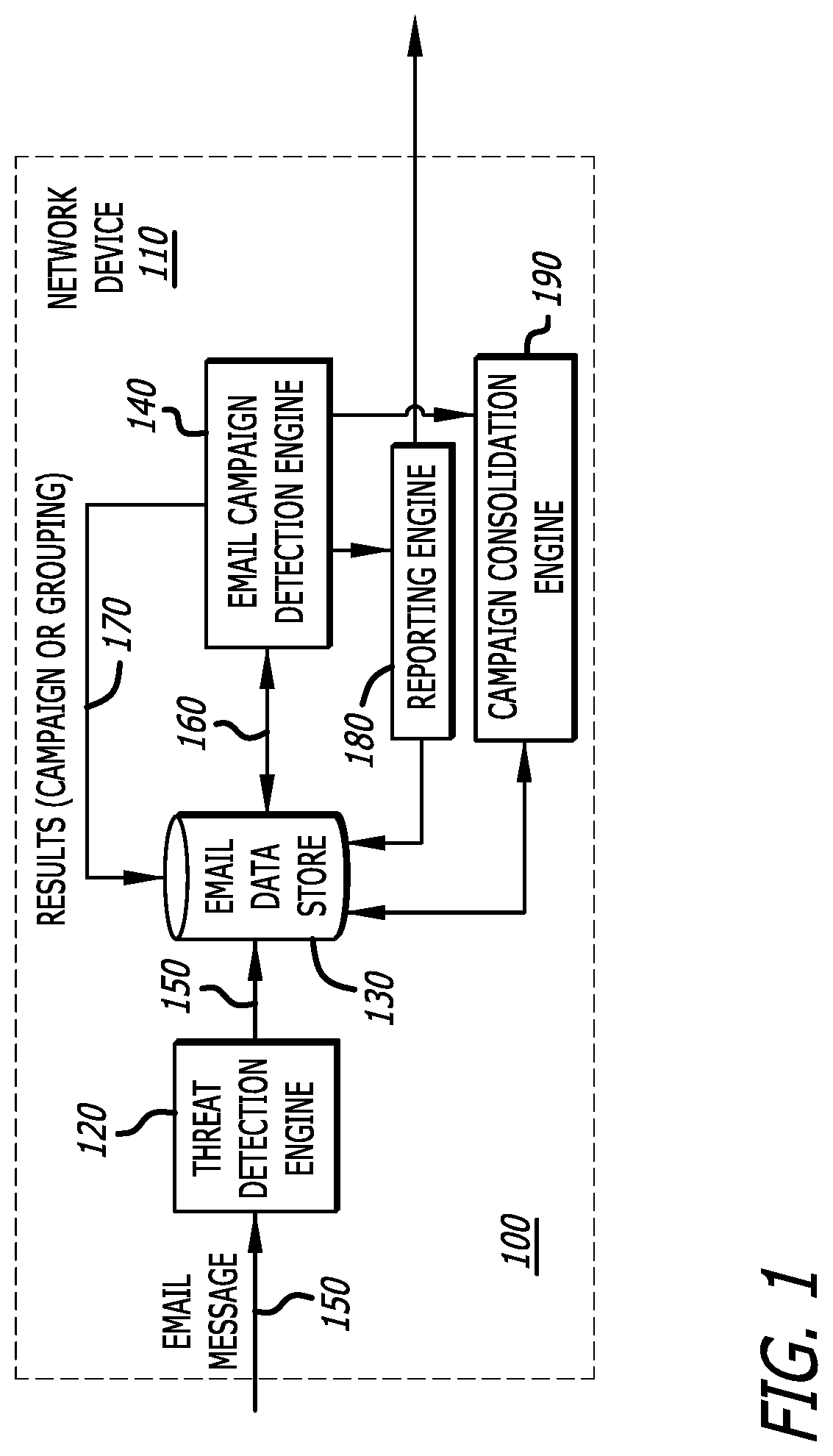
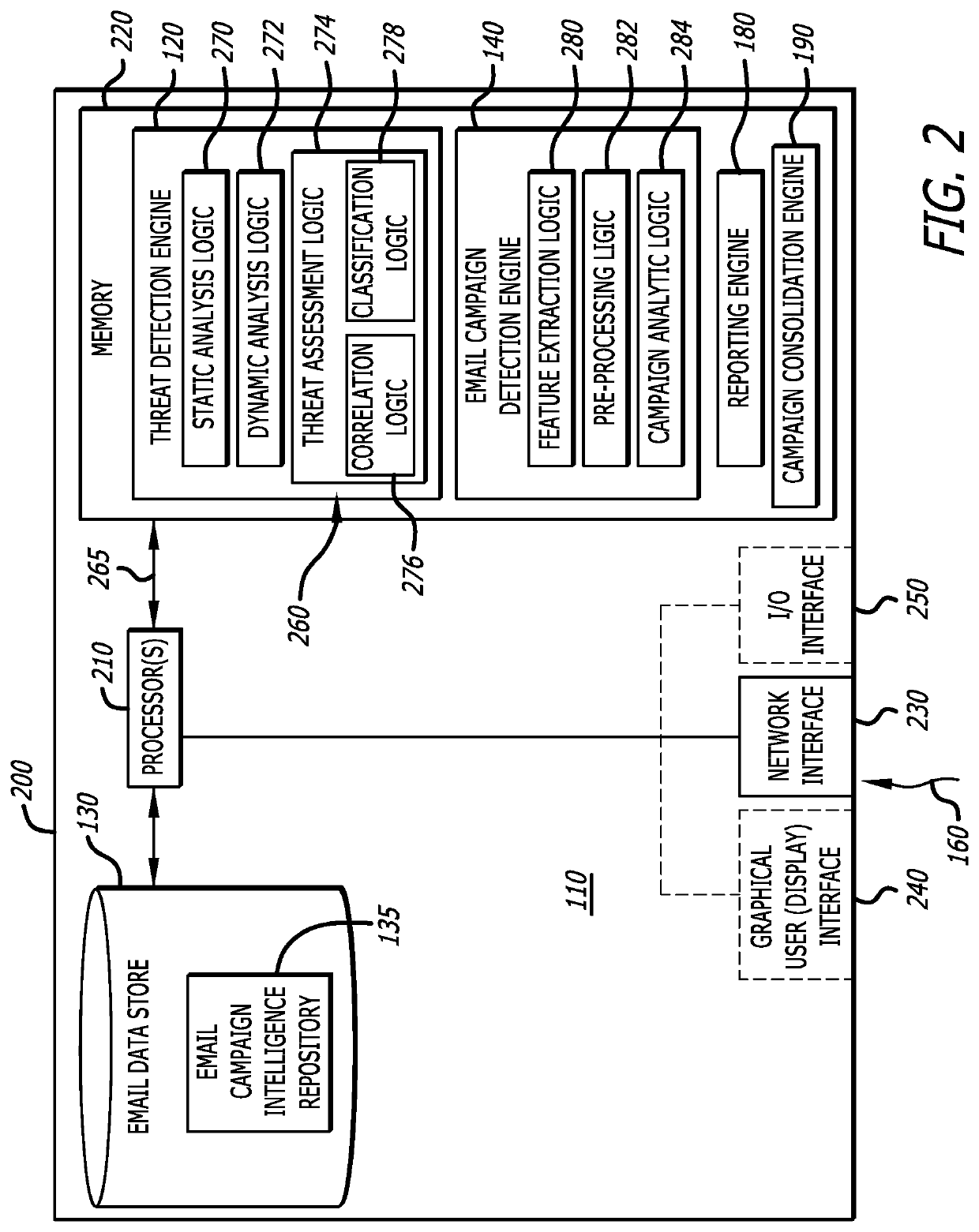
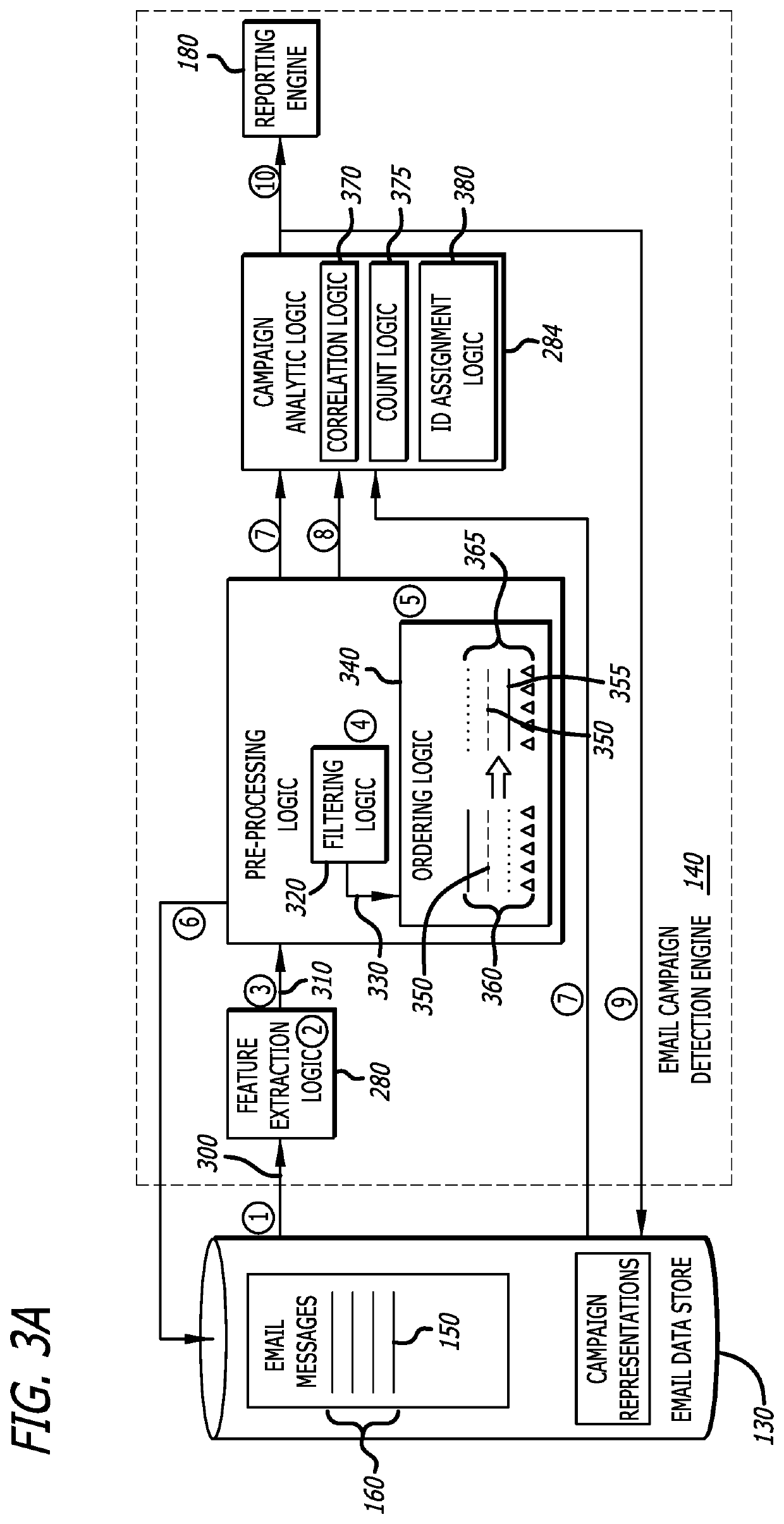
System and method for detecting repetitive cybersecurity attacks constituting an email campaign
According to one embodiment, a system for detecting an email campaign includes feature extraction logic, pre-processing logic, campaign analysis logic and a reporting engine. The feature extraction logic obtains features from each of a plurality of malicious email messages received for analysis while the pre-processing logic generates a plurality of email representations that are arranged in an ordered sequence and correspond to the plurality of malicious email message. The campaign analysis logic determines the presence of an email campaign in response to a prescribed number of successive email representations being correlated to each other, where the results of the email campaign detection are provided to a security administrator via the reporting engine.
Owner:FIREEYE SECURITY HLDG US LLC
Systems and methods for determining a job score from a job title
ActiveUS10992699B1Allocation is accurateImpact the amount of inbound and outbound communicationEnsemble learningBiological modelsAttackSecurity awareness
Embodiments disclosed herein describe a server, for example a security awareness server or an artificial intelligence machine learning system that establishes a job score for a user based on the user's job title. In embodiments, the vulnerability of a user to malicious cybersecurity attacks, the propensity for the user to engage with a malicious attack, and the severity of a malicious attack likely to be sent to the user and the severity of the harm to the user's organization is the user engages with the malicious attack is represented in a user risk score. The risk score for a user of a security awareness system, or for a group of users of a security awareness system, may be calculated based on one or more of a frequency score for the user, a propensity score for the user, a severity score for the user, and a job score for the user.
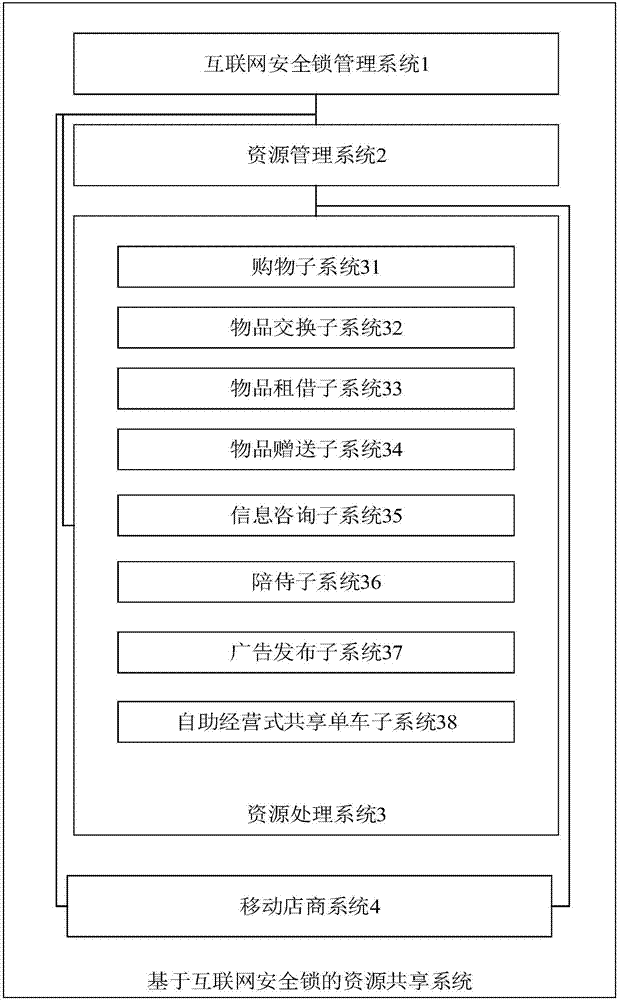
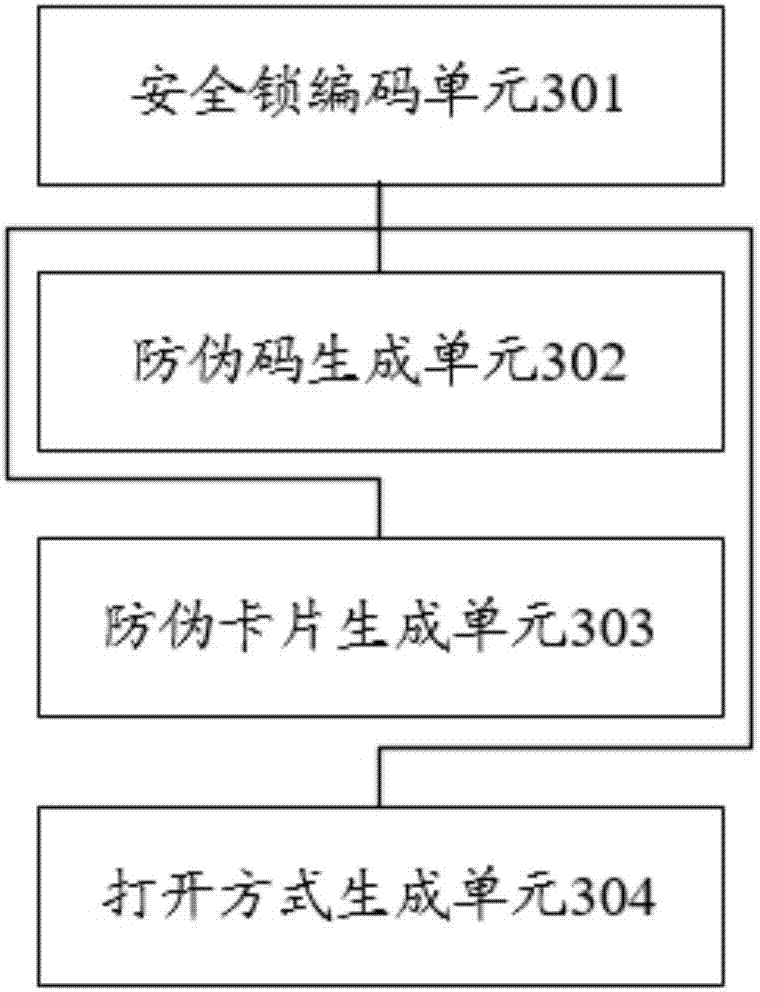
Resource sharing system based on internet safety locks
InactiveCN106952374AImplement leaseExchangeIndividual entry/exit registersBuying/selling/leasing transactionsResource Management SystemComputer science
The invention discloses a resource sharing system based on internet safety locks. Internet safety locks are coded uniformly, the safety locks become new code carriers, then the codes of the safety locks are precisely matched with the information sources of National Internet of Things Label Center and Article Numbering Center of China, and thus the system users and various resources of users are integrated into an organic whole. The system comprises an internet safety lock management system, a resource management system, a resource processing system, and a mobile shop system.
Owner:李建魁
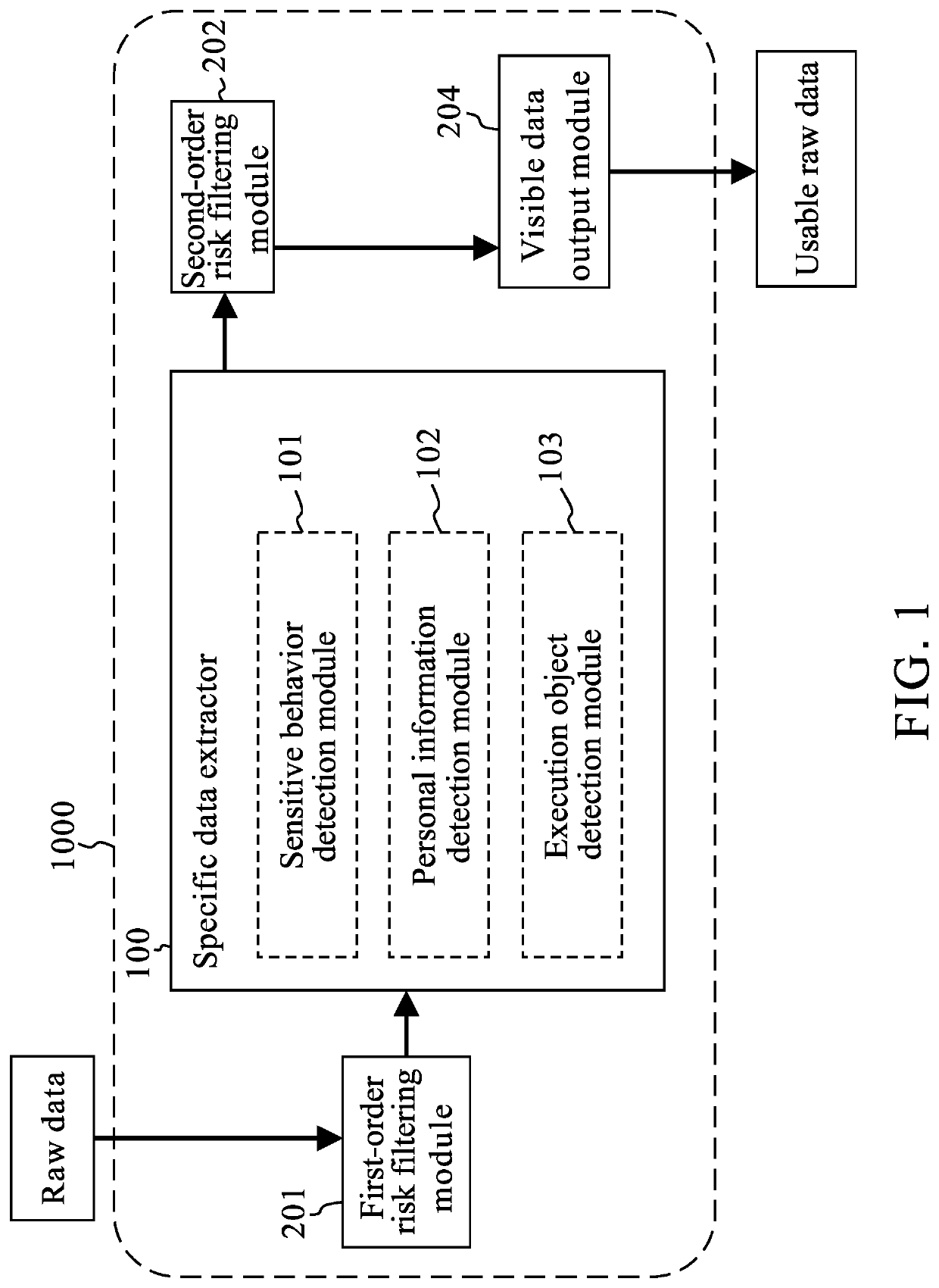
Data collection system for effectively processing big data
PendingUS20220200959A1Improve usabilityImprove securityWeb data indexingSpecial data processing applicationsData ingestionEngineering
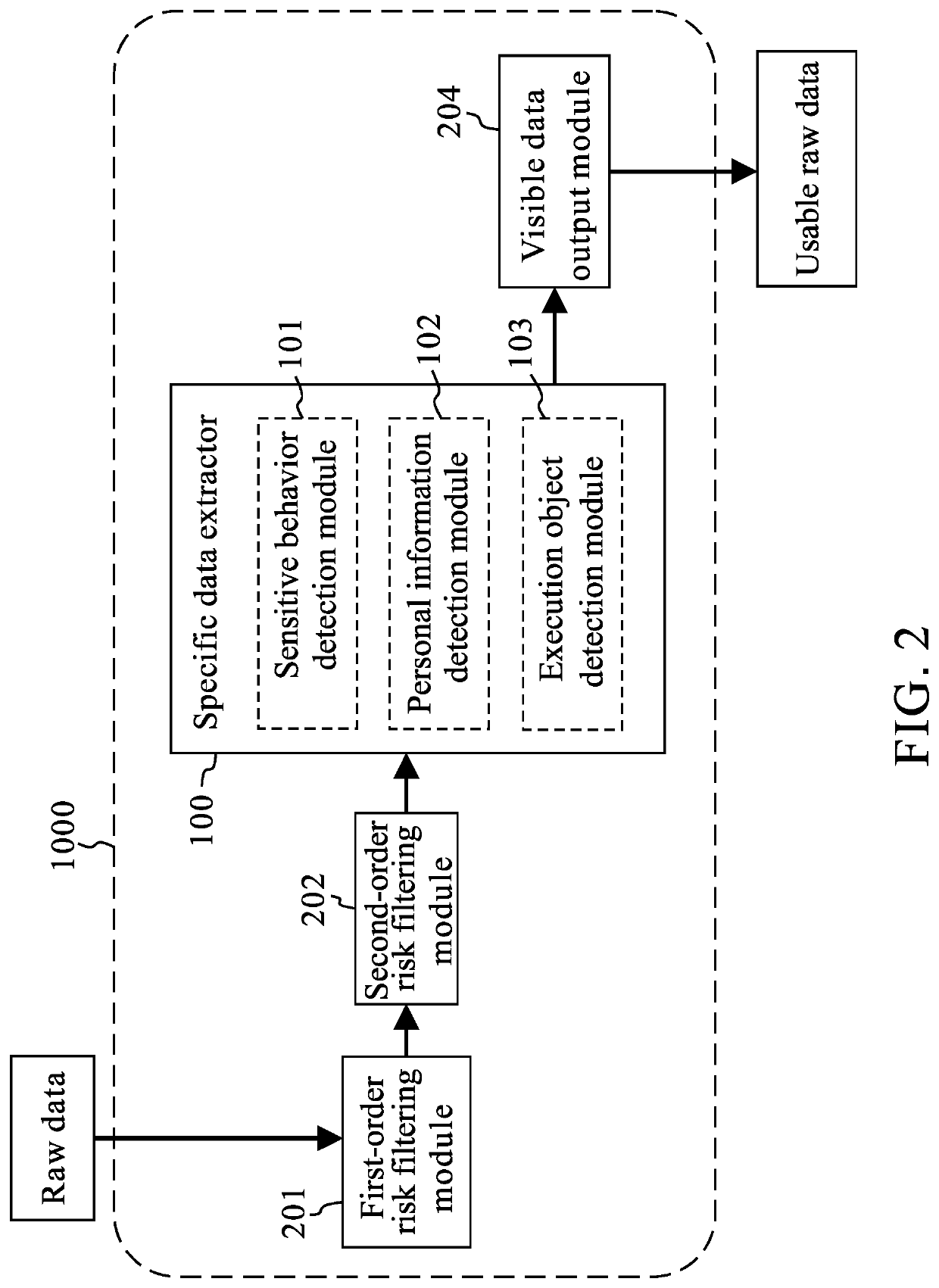
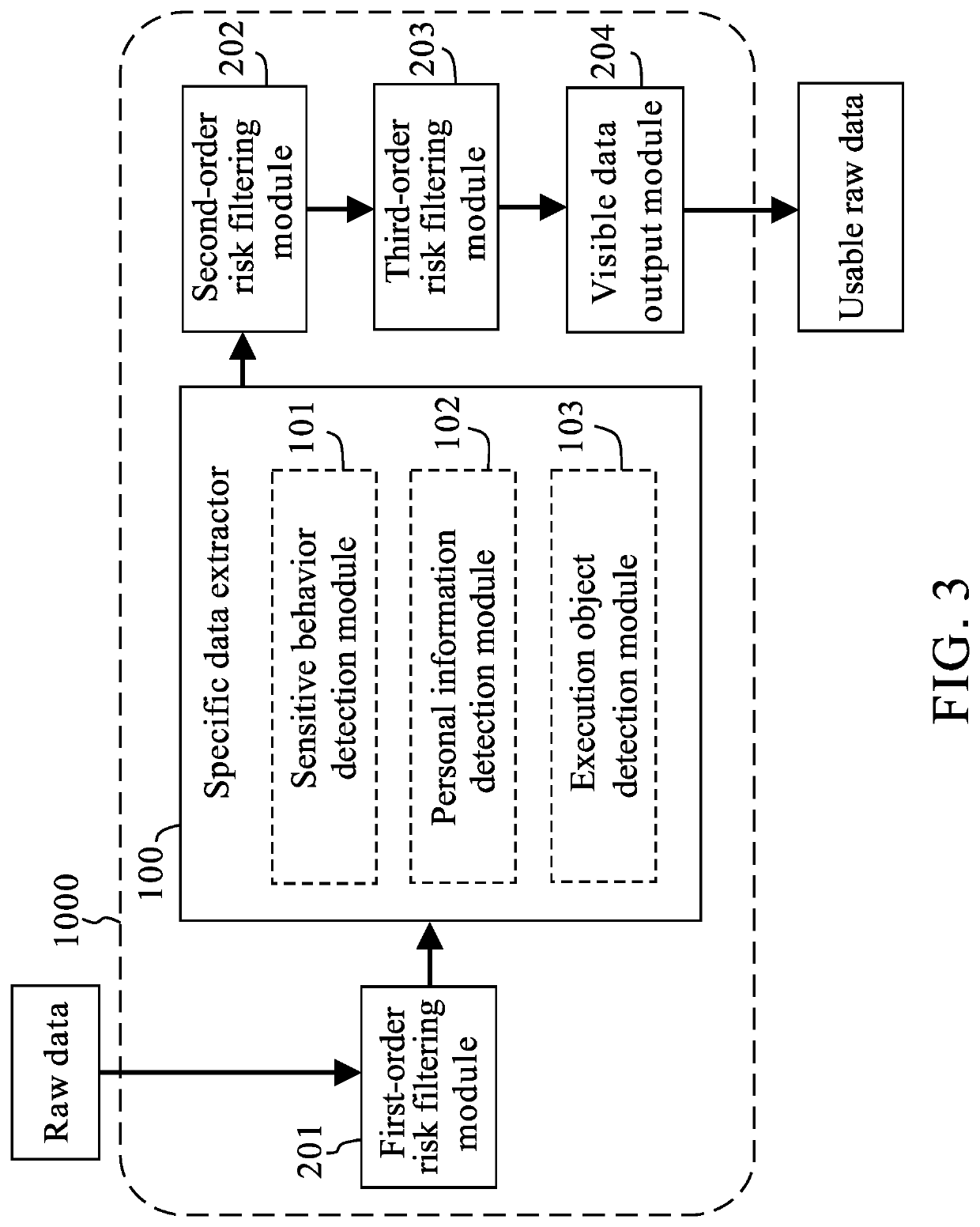
Data collection system for effectively processing big data is provided. The data collection system includes multiple risk filtering modules up to third order or higher and a specific data extractor, wherein the multiple risk filtering modules and the specific data extractor are connected in series. The data collection system is capable of filtering received raw data through the multiple risk filtering modules so as to remove data with cyber security risks or system security issues, and keeping required data by the specific data extractor. In addition, the system can assist the user automatically to carefully select raw data through a combination of means of data classification, data normalization, and data clustering analysis. Thereby the system effectively enhances usability and security of data collection.
Owner:AHP TECH INC
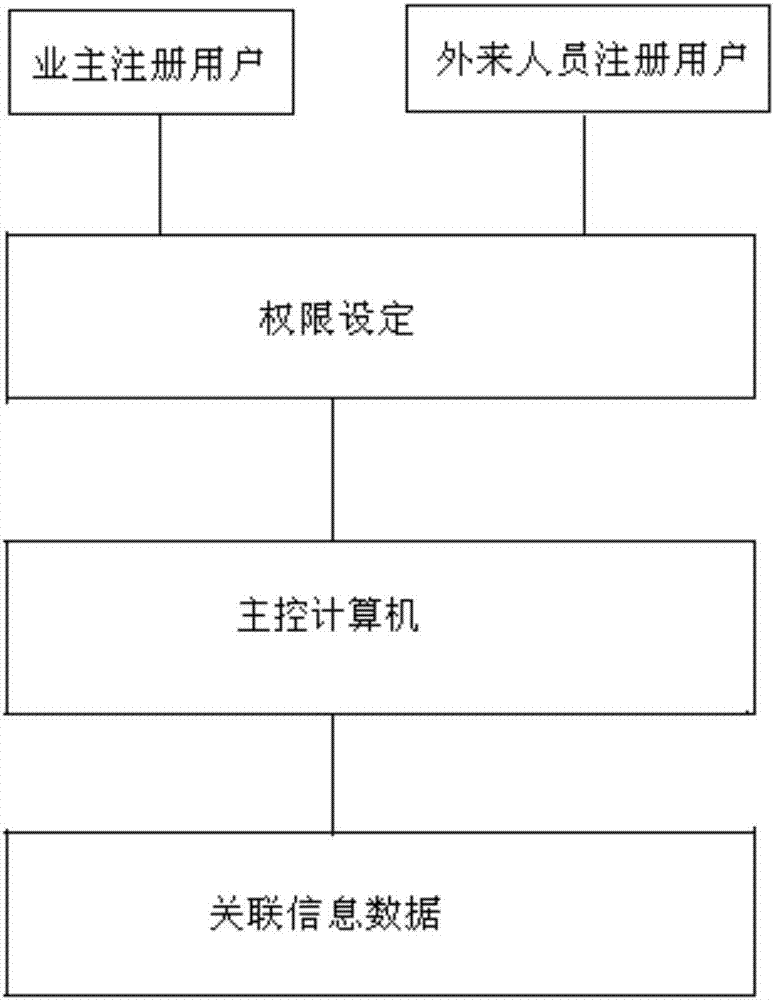
Internet-specification entrance guard and safety management system
PendingCN106875522AAccess to effective controlStrengthen security managementIndividual entry/exit registersSafety management systemsComputer science
The invention discloses an internet-specification entrance guard and safety management system. The internet-specification entrance guard and safety management system comprises a registered user, a mobile terminal, entrance guard management software, a master control computer, an image acquisition module, an image recognizing module and an entrance guard control module, wherein the entrance guard management software is connected with the master control computer through the internet; the master control computer is separately connected with the image acquisition module, the image recognizing module and the entrance guard control module; the registered user needs to upload registered user image identity information while registering on the entrance guard management software through the mobile terminal. The internet-specification entrance guard and safety management system is artificial intelligent application of internet entrance guard safety management, is simple in structure, is scientific to use, and is convenient to operate; the image identity information must be used for successful registering on the entrance guard management software, an interpersonal relationship is established according to the register user formal information, safety of internet safe management interpersonal relationship is improved, and internet safety management is realized by taking image identity associated information as basis.
Owner:姜茂清
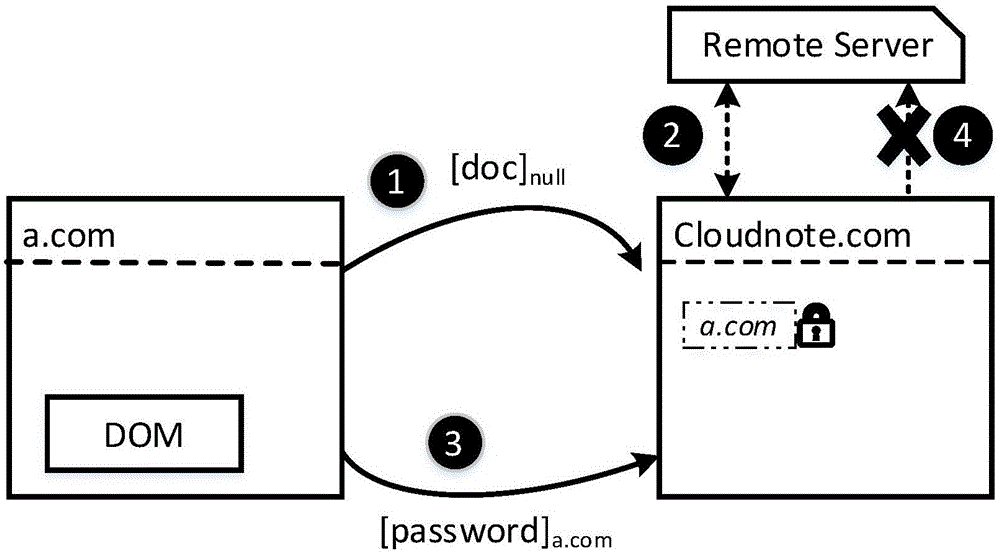
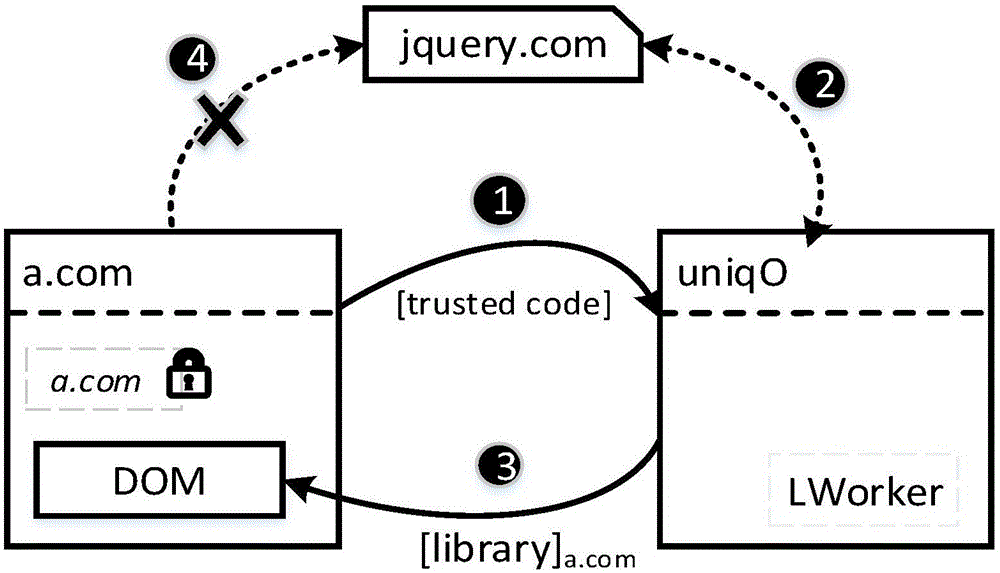
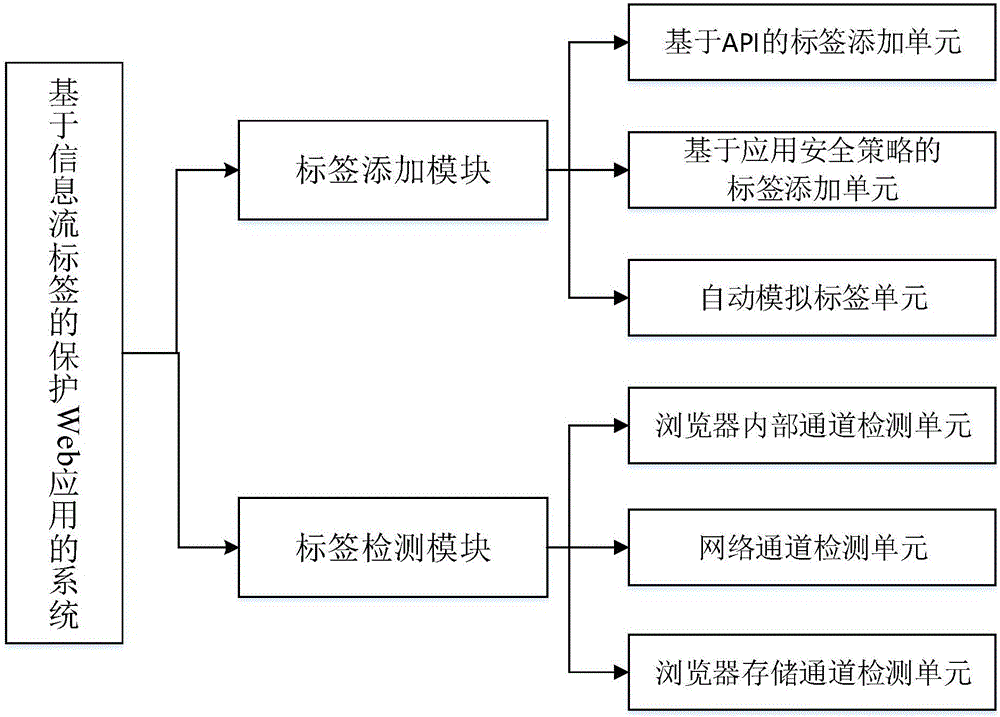
Web user privacy protection system and method based on information stream tag
ActiveCN107180202AGuaranteed CompatibilityIntegrity guaranteedDigital data protectionWebsite content managementLight-weight processProtection system
The invention discloses a Web user privacy protection system and method based on an information stream tag, and belongs to the field of Internet safety. The system comprises a tag adding module and a tag detection module, wherein a novel access control tag model applied to a Web environment is designed in the tag adding module for adding a tag to a message transmitted between a Web component and a Web component; when the Web component comprises a third-party code, a light-weight process is designed for isolating a third-party dangerous code; meanwhile, the tag is aimed to design a message transferring rule to track a user privacy information message so as to track the user privacy information message. The invention also realizes the Web user privacy protection method based on the information stream tag. The technical scheme disclosed by the invention is suitable for Web applications of which the safety level needs to be improved, wherein the Web applications have sensitive user information. The Web application can be free from a situation that the third-party code is damaged, and the privacy information of the user can be protected.
Owner:HUAZHONG UNIV OF SCI & TECH
Cooperative identification method of Web service based site revealing user privacy information
InactiveCN101984629APrivacy protectionUser identity/authority verificationThird partyInternet privacy
The invention provides a cooperative identification method of a Web service based site revealing user privacy information, belonging to the computer network security field. Aiming at the problem that users often receive spam mails with advertising nature after the Web service based site reveals the user privacy information to a third party, the invention provides the method for identifying the Web service based site revealing the user privacy information. The users who receive the spam mails and intend to participate in identification of the site revealing the privacy information can cooperatively identify the site revealing the user privacy information. In the method, by adopting the technique of decomposing input of participants, the participants do not know input of other participants,thus the privacy of the participants is farthest protected.
Owner:BEIJING UNIV OF TECH
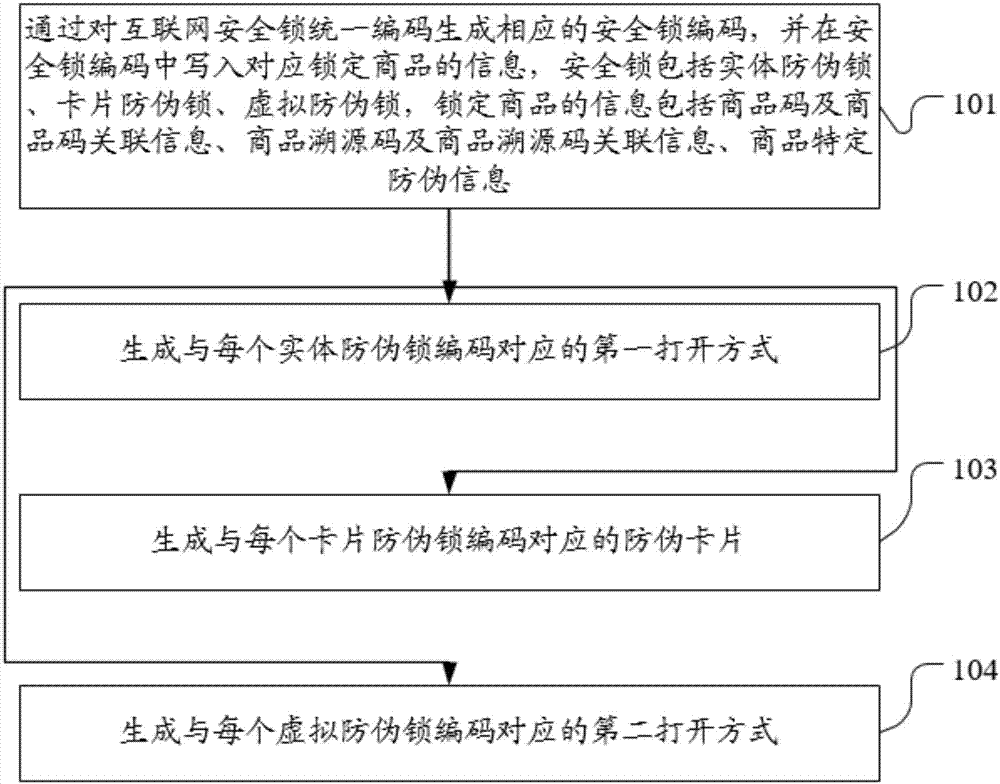
Goods false proof method and system based on Internet safety lock
InactiveCN106940859AAchieve anti-counterfeiting goalsAnti-lostDigital data protectionCommerceProduct traceabilityCard security code
The embodiment of the present invention discloses a commodity anti-counterfeiting method and system based on an Internet security lock. By uniformly encoding the Internet security lock and writing the locked commodity information into the security lock code, the user can verify the identity of the commodity through the security lock. Information to identify the authenticity of the goods, so as to achieve anti-counterfeiting. The method in the embodiment of the present invention includes: generating a corresponding security lock code by uniformly encoding the Internet security lock, and writing information corresponding to locked commodities in the security lock code, the security lock includes a physical anti-counterfeiting lock, a card anti-counterfeiting lock, Virtual anti-counterfeiting lock, the information of the locked commodity includes commodity code and commodity code associated information, commodity traceability code and commodity traceable code associated information, commodity specific anti-counterfeiting information; generating the first opening method corresponding to each entity anti-counterfeiting lock code ; Generate an anti-counterfeit card corresponding to each of the card anti-counterfeit lock codes; generate a second opening method corresponding to each of the virtual anti-counterfeit lock codes.
Owner:李建魁
System and method for self-adjusting cybersecurity analysis and score generation
A system and method for self-adjusting cybersecurity analysis and score generation, wherein a reconnaissance engine gathers data about a client's computer network from the client, from devices and systems on the client's network, and from the Internet regarding various aspects of cybersecurity. Each of these aspects is evaluated independently, weighted, and cross-referenced to generate a cybersecurity score by aggregating individual vulnerability and risk factors together to provide a comprehensive characterization of cybersecurity risk using a transparent and traceable methodology. The scoring system itself can be used as a state machine with the cybersecurity score acting as a feedback mechanism, in which a cybersecurity score can be set at a level appropriate for a given organization, and data from clients or groups of clients with more extensive reporting can be used to supplement data for clients or groups of clients with less extensive reporting to enhance cybersecurity analysis and scoring.
Owner:QOMPLX INC
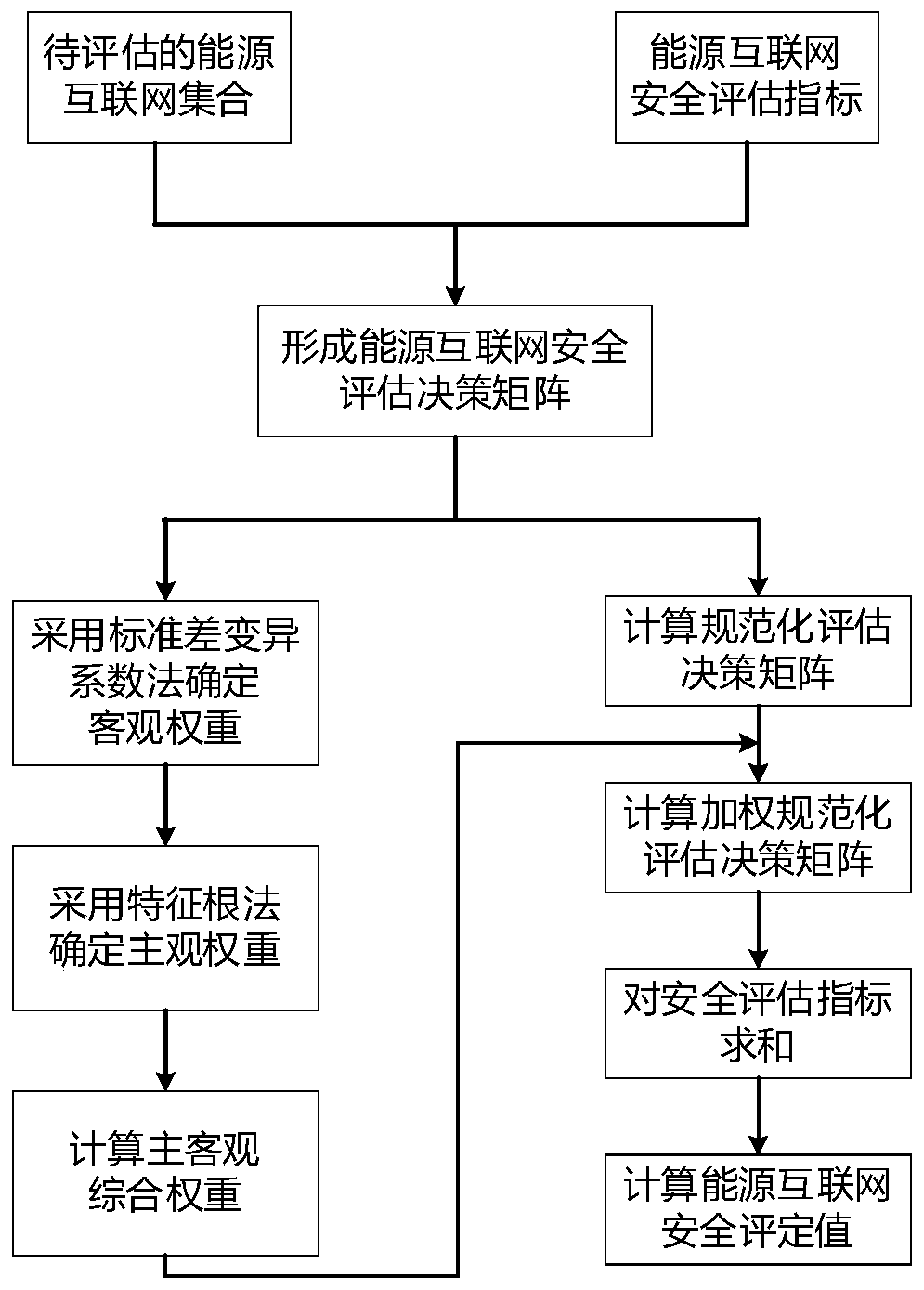
Multi-attribute decision-making method for energy internet security assessment
InactiveCN109784732AResolve interferenceEnsure safetyTechnology managementResourcesOperabilityInformation security
The invention discloses a multi-attribute decision-making method for energy internet security assessment, which comprises the following steps: firstly, establishing eight energy internet security assessment index sets from four aspects of natural disaster threats, network structure vulnerability, system equipment risks and information security threats, and collecting each index data to form an assessment decision-making matrix; determining the objective weight of each safety assessment index by adopting a standard deviation variation coefficient method; adopting a characteristic root method toobtain subjective weight of the multi-expert group, and calculating subjective and objective comprehensive weight of the safety assessment index; and finally, evaluating the safety level of the energy internet by adopting a comprehensive proportion evaluation method. The energy internet safety assessment index system is comprehensive. The assessment method has high operability, a given energy internet safety assessment result has high reference value, weak safety links and potential risk threats existing in energy internet construction can be found out, and the assessment method has positivesignificance in guaranteeing safe and stable operation of the energy internet.
Owner:SOUTHWEST JIAOTONG UNIV
Method and system for remediating cybersecurity vulnerabilities based on utilization
A technology solution for remediating a cyberattack risk for a web application, including receiving device engagement data for the web application, receiving a security scanning analysis from a static application security testing (SAST) tool that includes a security flaw found in the web application and a severity level for the security flaw, and a plurality of other security flaws found in one or more other web applications and severity levels associated with each of the plurality of other security flaws. The technology solution includes determining a plurality of criticality adjustment values for the security flaw and each of the plurality of other security flaws, applying a criticality adjustment value to the security flaw to modify a severity level for the security flaw, prioritizing the security flaw and the plurality of other security flaws based on the modified severity level to generate prioritized security flaw action items, and mitigating the cyberattack risk for the web application according to the prioritized security flaw action items.
Owner:SAUDI ARABIAN OIL CO
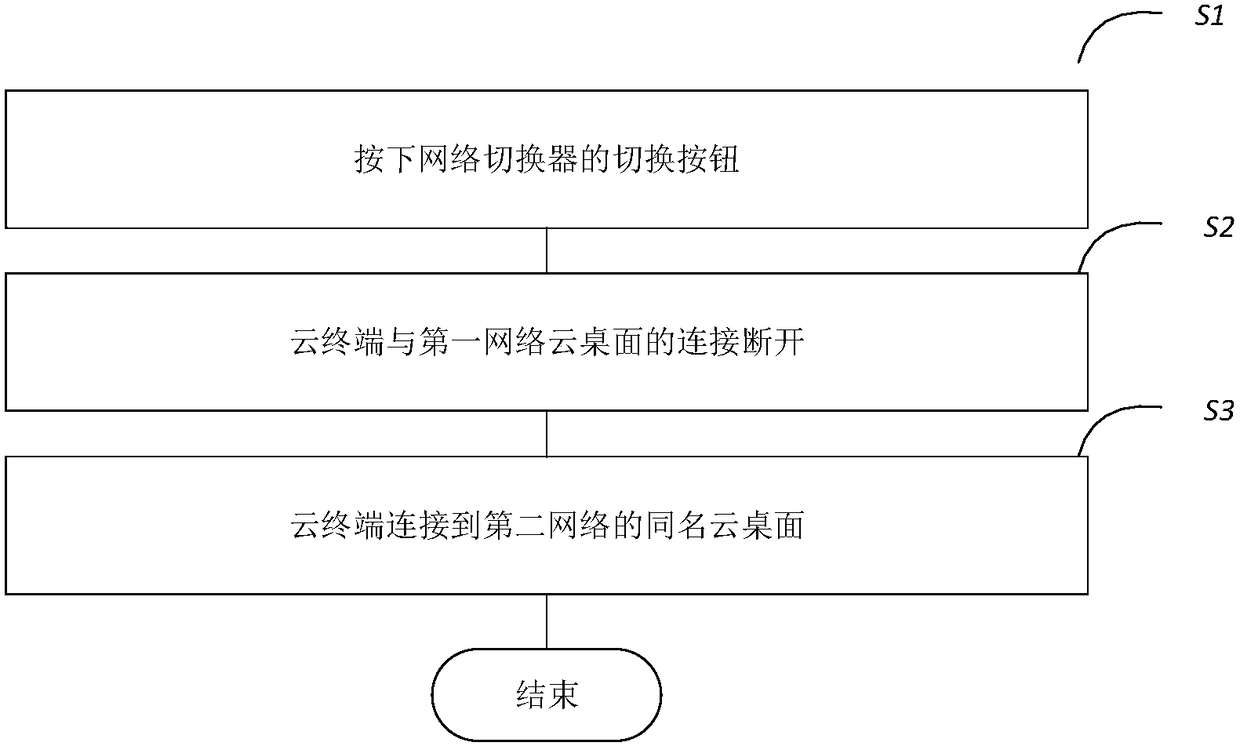
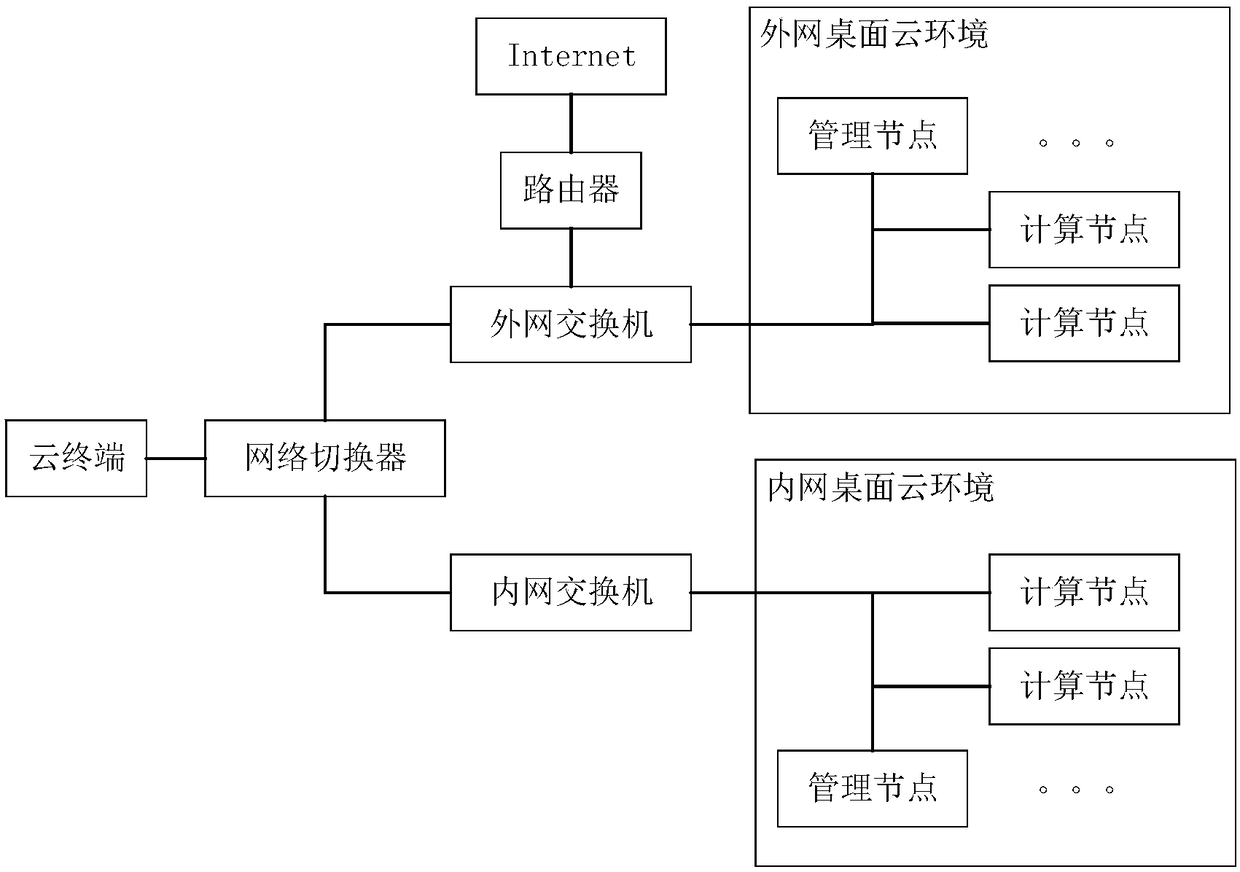
Dual-network-isolated cloud desktop connection method and system
The invention relates to the technical field of internet safety and especially relates to a dual-network-isolated cloud desktop connection method and system. The method is characterized in that a cloud terminal realizes switching of connection between a first network and a second network through a network switcher, realizes continuous detection of connectivity of the network through a cloud terminal agent module, and feeds back and reminds users according to the detection obtained connectivity information. The system comprises the cloud terminal agent module, a cloud desktop management module,a network switcher, an intranet switch and an extranet switch. The method and system can provide a physically completely-isolated intranet / extranet cloud desktop for the users without transforming the cloud terminal, automatically connect to the cloud desktop in the switching process and have the advantages of low cost, convenient use and easy upgrade and the like.
Owner:G CLOUD TECH
Internet of Things information protection system based on multiple verification
PendingCN113595969AProtection securityProtection reliabilityPublic key for secure communicationData acquisitionInformation security
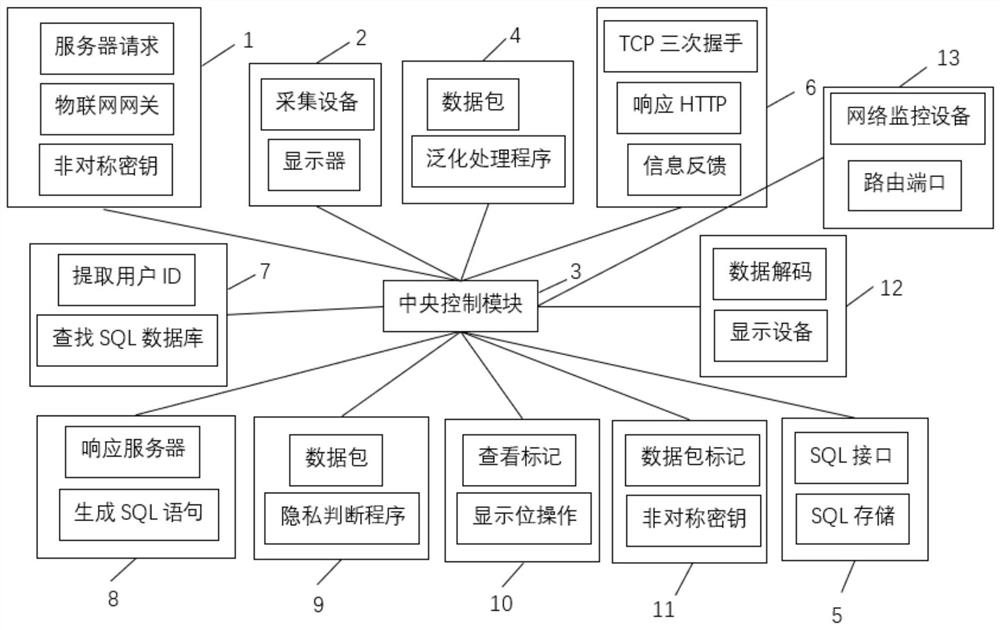
The invention belongs to the technical field of information security, and discloses an Internet of Things information protection system based on multiple verification. The system comprises an equipment verification module, a data acquisition module, a central control module, a generalization processing module, a storage module, a network request acquisition module, a user identity verification module, a response module, a data judgment module, a privacy hiding module, a data transmission module, a display module and a network security monitoring module. According to the method, firstly, equipment verification is carried out, the safety and reliability of information collection node equipment are protected, meanwhile, generalization processing is carried out on node information and other contents of collected data, and equipment information is effectively hidden; and meanwhile, distributed storage can ensure the security of information storage and improve the information calling efficiency. According to the method, the request is responded after the identity of the user is verified, secondary verification is carried out on the request data, private data are hidden, and the safety and traceability of information are guaranteed.
Owner:彭松英
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com