Method for tracking leakage of private information
A technology of privacy information and user privacy, applied in the field of computer network security, can solve the problem of users with advertisements, etc., to achieve the effect of protecting privacy information and protecting privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
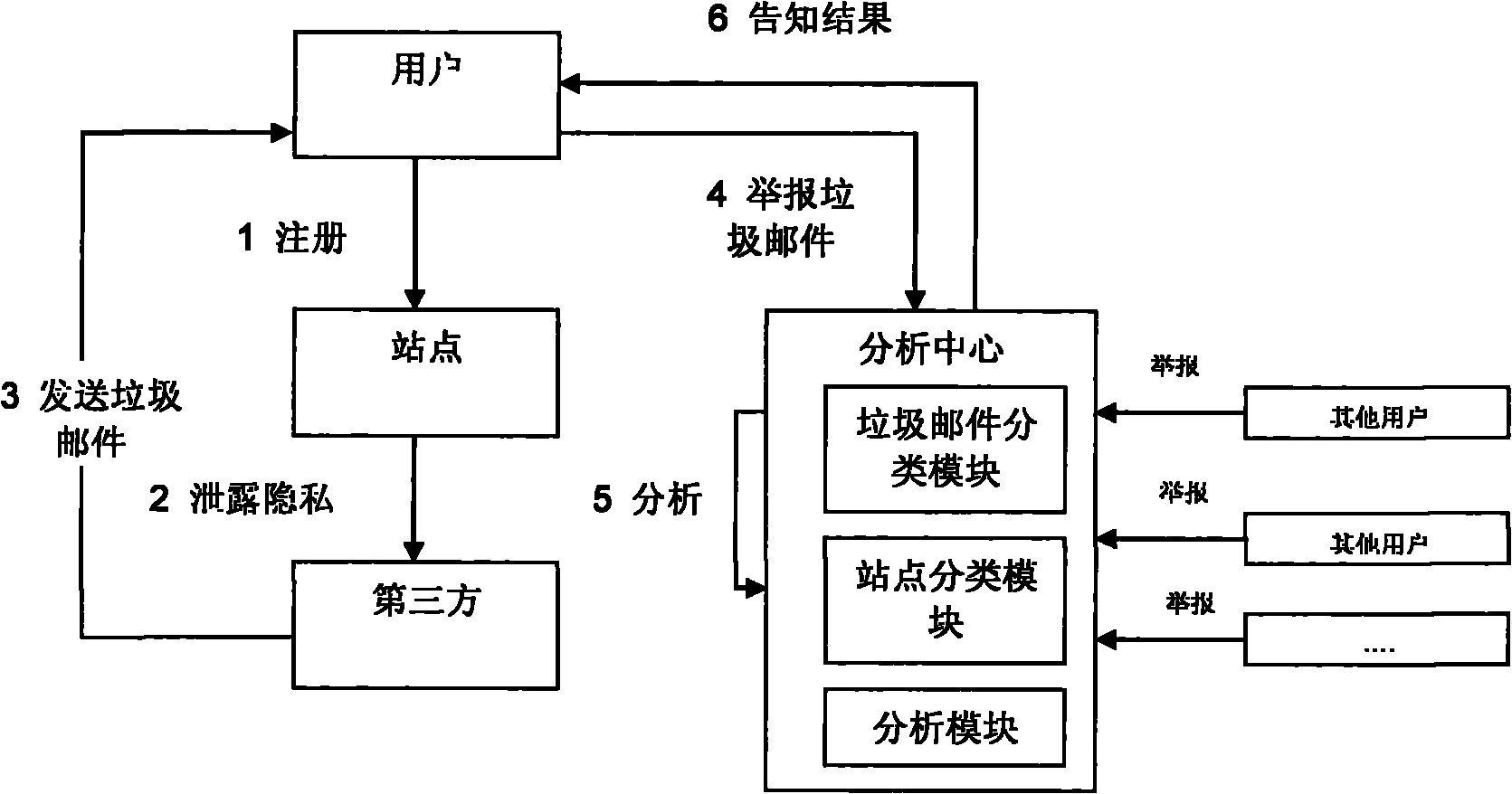
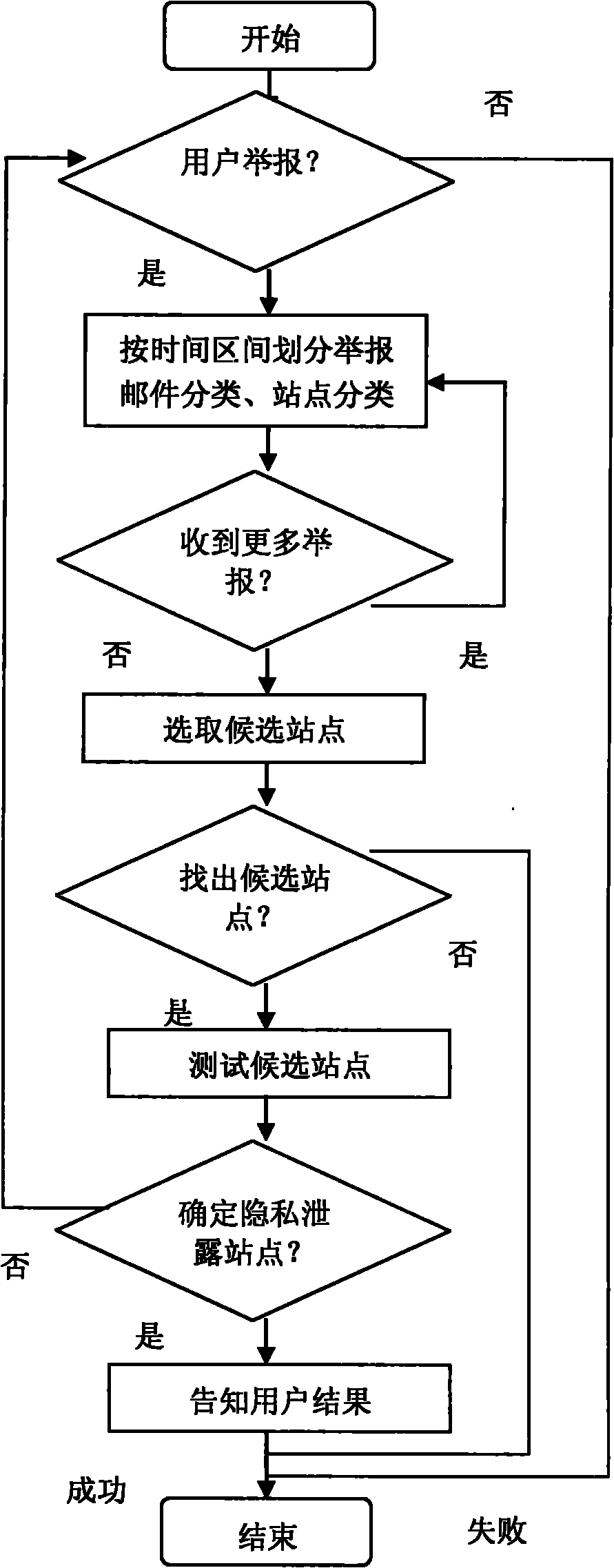
[0033] Specific embodiments of the present invention Taking an e-commerce website that leaks private information of a user's purchase tendency as an example, the method for tracking private information leakage of the present invention is described.
[0034] User A visits e-commerce website S during this month 1 Browse the purchase information of cosmetics and clothing, S 1 It is the site that User A registered two months ago. By analyzing user A's browsing history, the e-commerce website leaks the user's private information about clothing and cosmetics and A's email address to a third party P, and the third party P begins to send some spam emails advertising cosmetics to A.
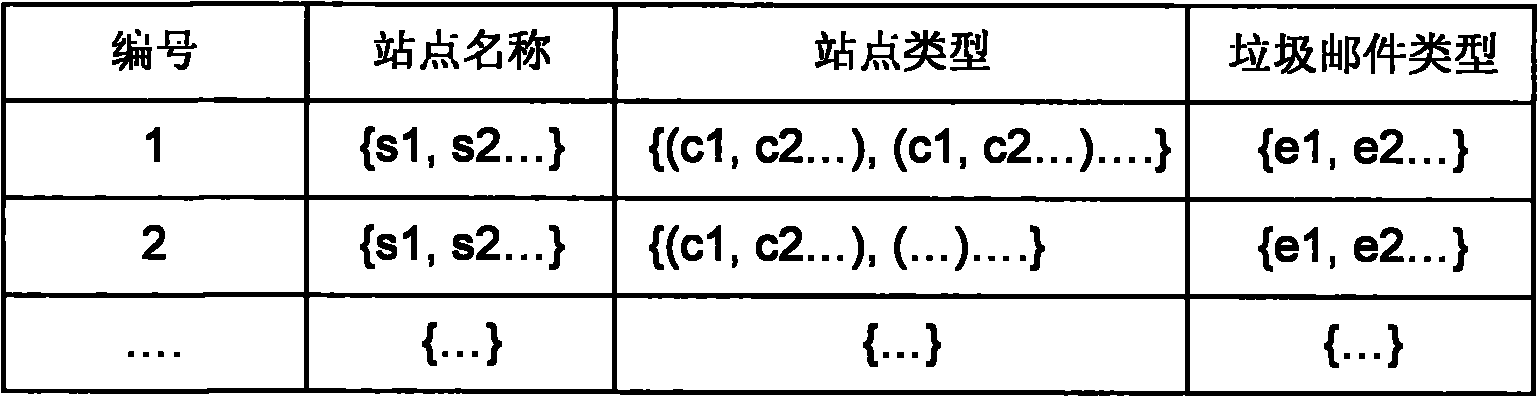
[0035] A often receives spam about cosmetics, so A registers an account in the analysis center, and sends the received spam E and the website {S that A has registered within a month 2 , S 3 , S 4 , S 5}Report to Analysis Center.
[0036] Analyze the report received from user A, and classify the spam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com