Dual-network-isolated cloud desktop connection method and system
A connection method and cloud desktop technology, applied in the field of Internet security, can solve problems such as hidden safety hazards, inconvenient maintenance, and increased costs, and achieve the effects of easy upgrades, low cost, and convenient use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the purpose of the present invention, technical characteristics and method obtain clearer description, below in conjunction with accompanying drawing and example, be described in detail, concrete implementation process is as follows:
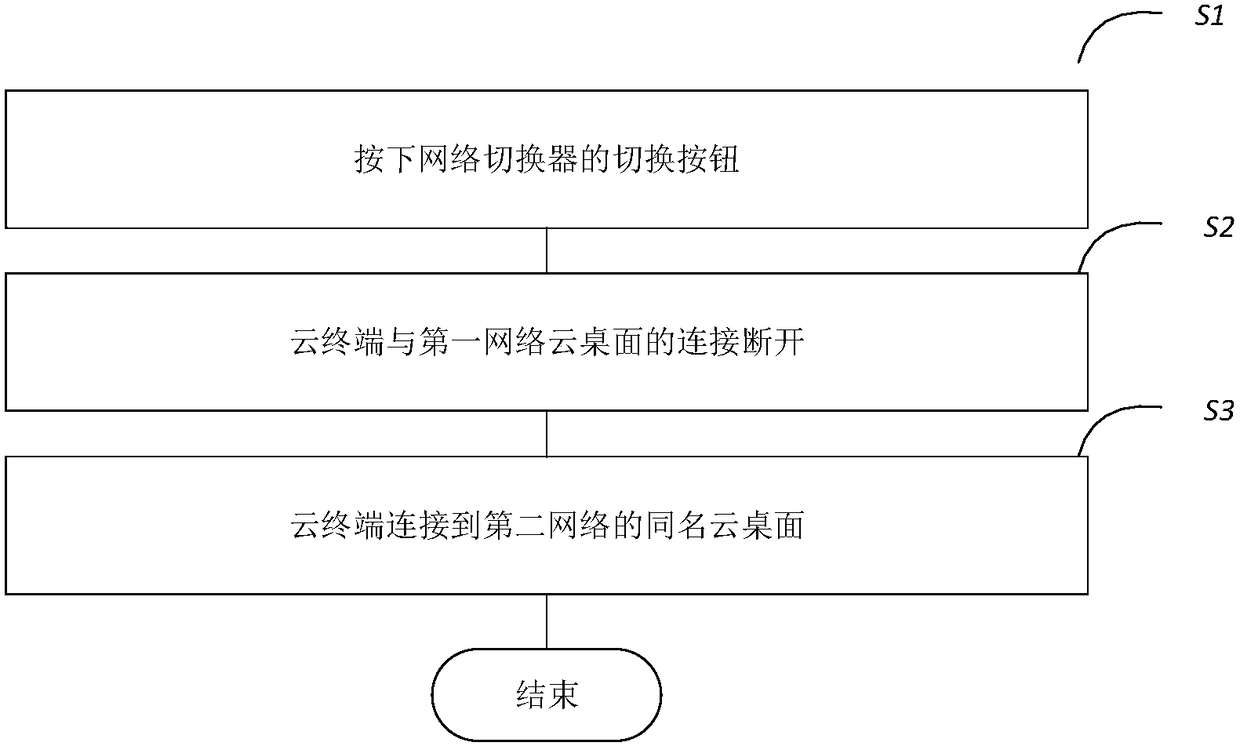
[0030] figure 1 It is a flowchart of the method of the present invention. Such as figure 1 As shown, the method includes:
[0031] S1: Press the switch button of the network switcher;
[0032] S2: The connection between the cloud terminal and the first network cloud desktop is disconnected;
[0033] S3: The cloud terminal is connected to the cloud desktop with the same name in the second network.
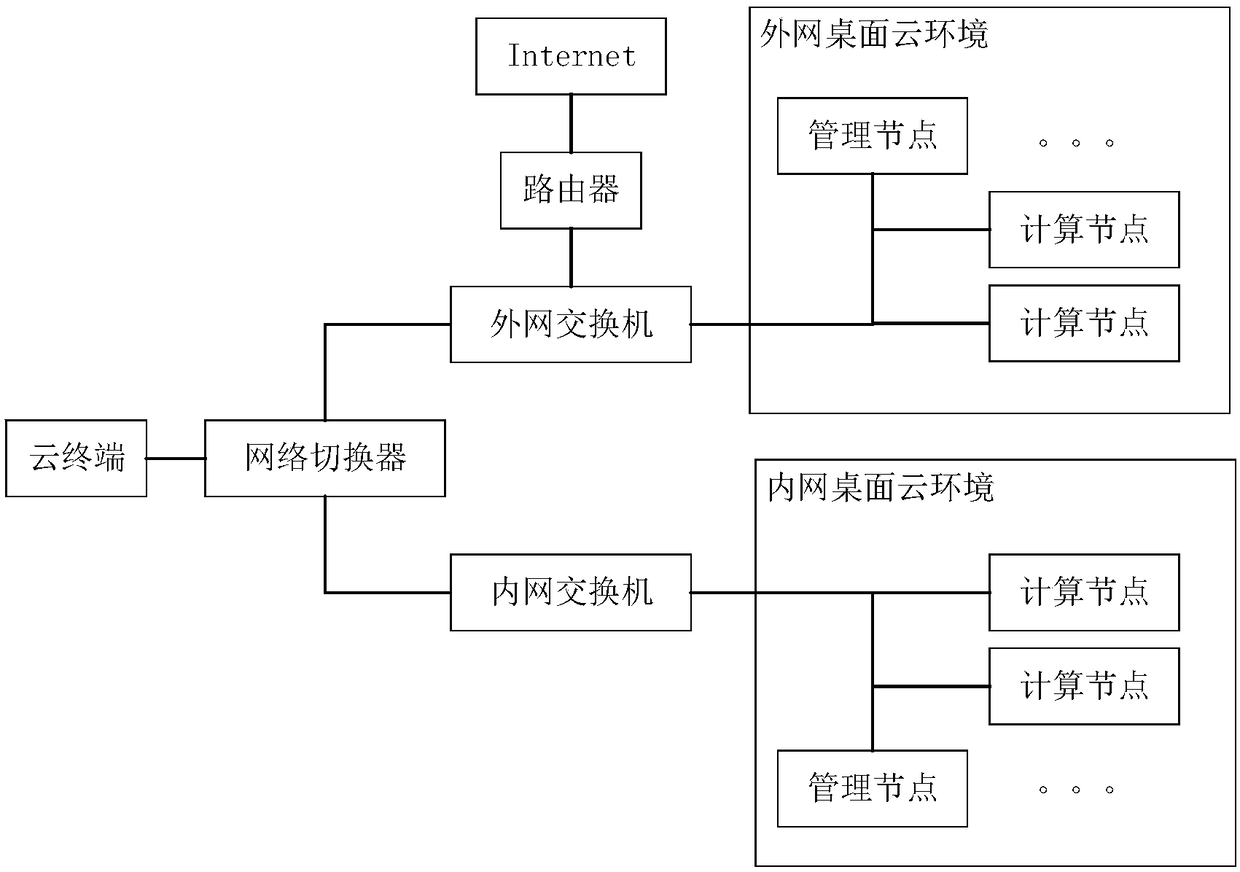
[0034] Before steps S1-S3, open the network connected to the cloud terminal as the first network. When the switch button of the network switcher is pressed, the first network is disconnected and switched to the second network. At this time, the cloud terminal and the cloud desktop of the first network is disconnected.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com