Group broadcast cipher key managing method based on physical layer
A technology of multicast key and management method, applied in the field of Internet security multicast, can solve the problems of high overhead and affecting the quality of multicast service, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Below in conjunction with accompanying drawing and embodiment, content of the present invention and the background technology on which it is based are described in detail:
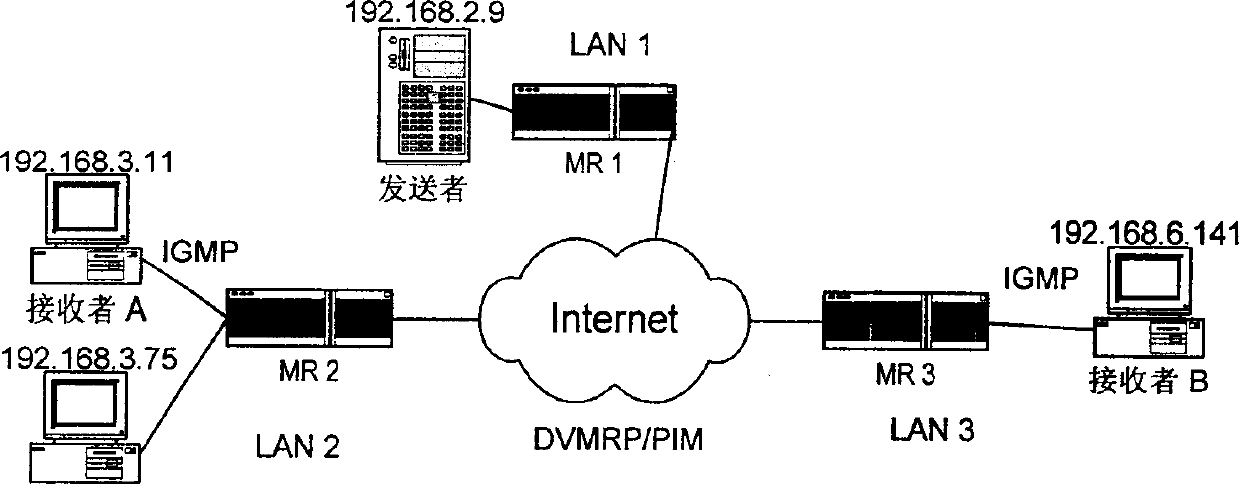
[0031] (1) Simple Key Distribution Center (SKDC)
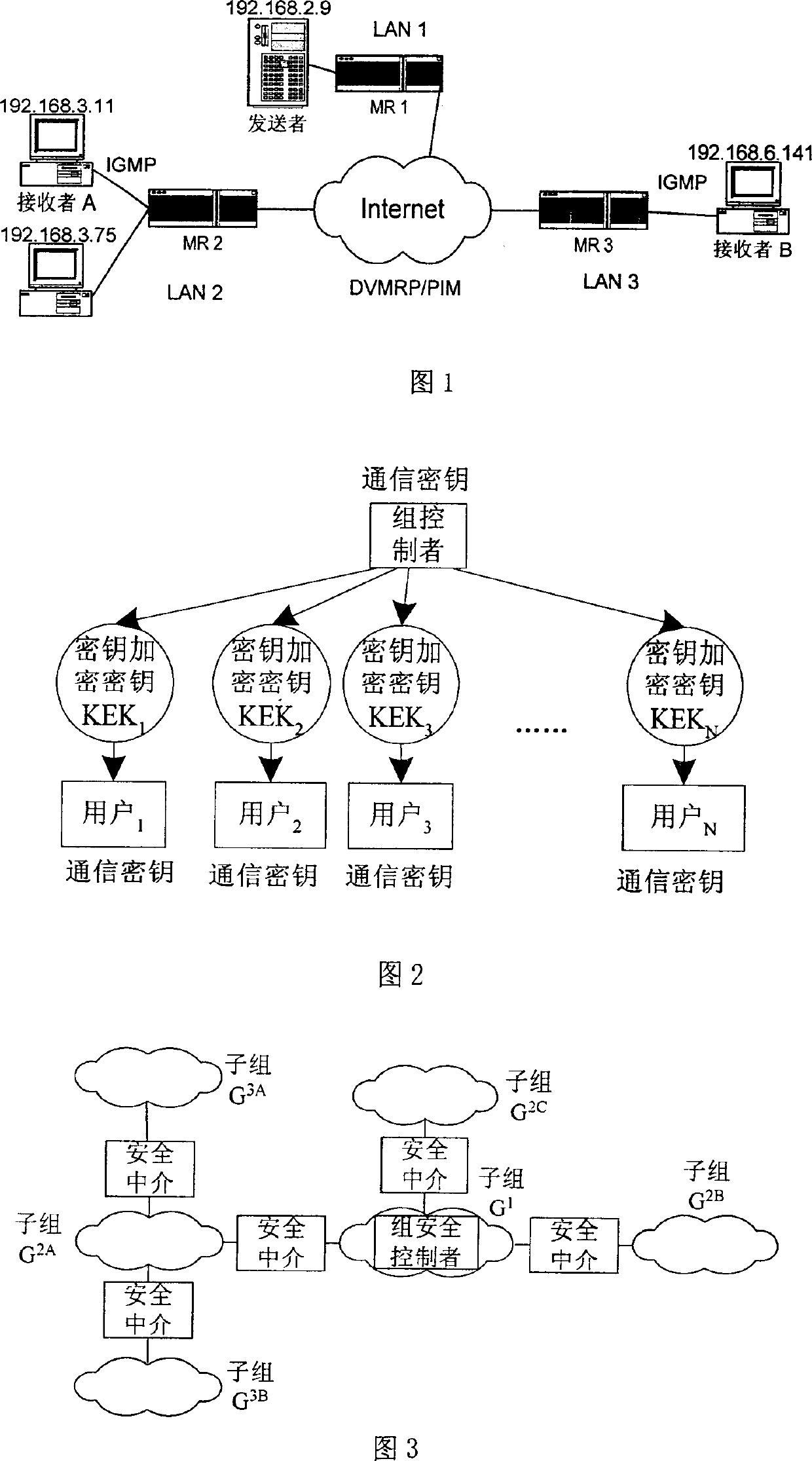
[0032] In the existing multicast model, any host is allowed to join the multicast group without verification, and there is no access control for the multicast participants. Any host can send a join request message to an adjacent multicast router, and the router sends a join request to the upper multicast tree. Once the join request is successful, the multicast tree will be extended to the subnet, and the host that sent the join request can receive multicast data.
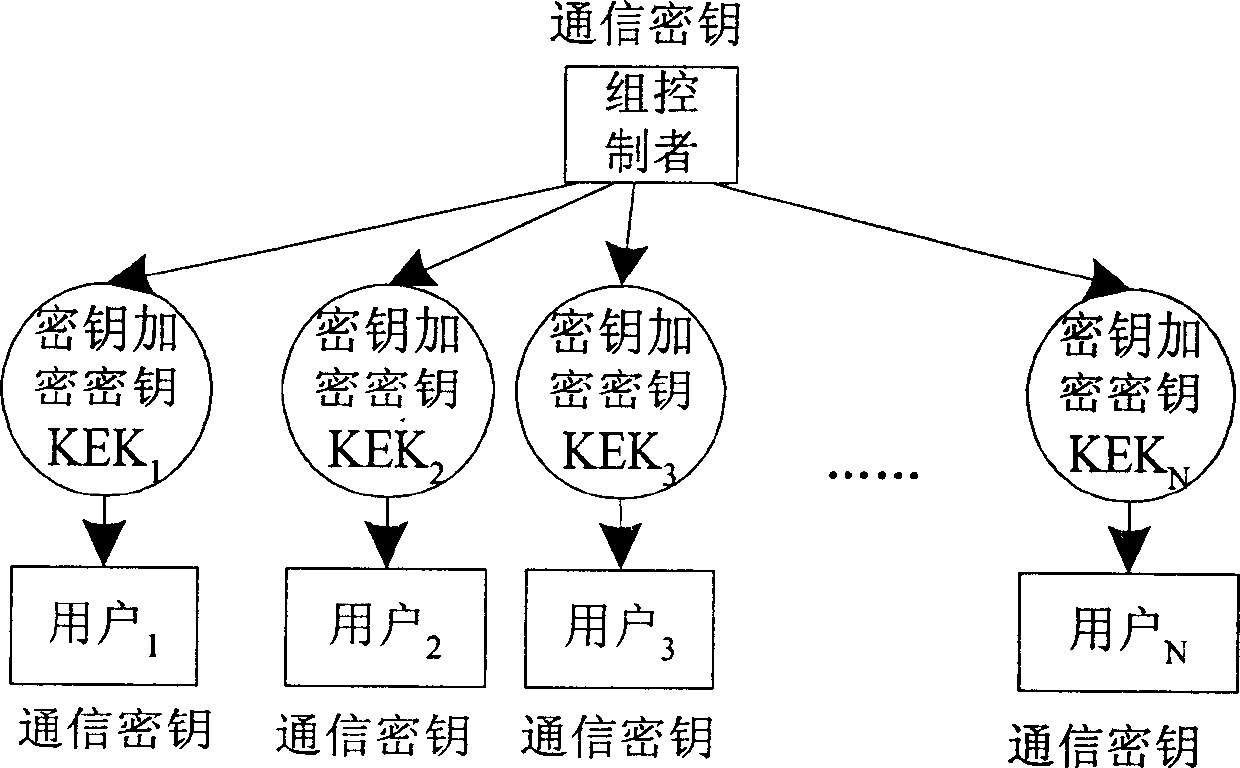
[0033]For a communication service, the most practical and feasible security measure is to perform symmetric encryption on the service data (for example, using encryption algorithms such as DES). The characteristic of symmetric encryption is that the key for encrypting data and the key f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com