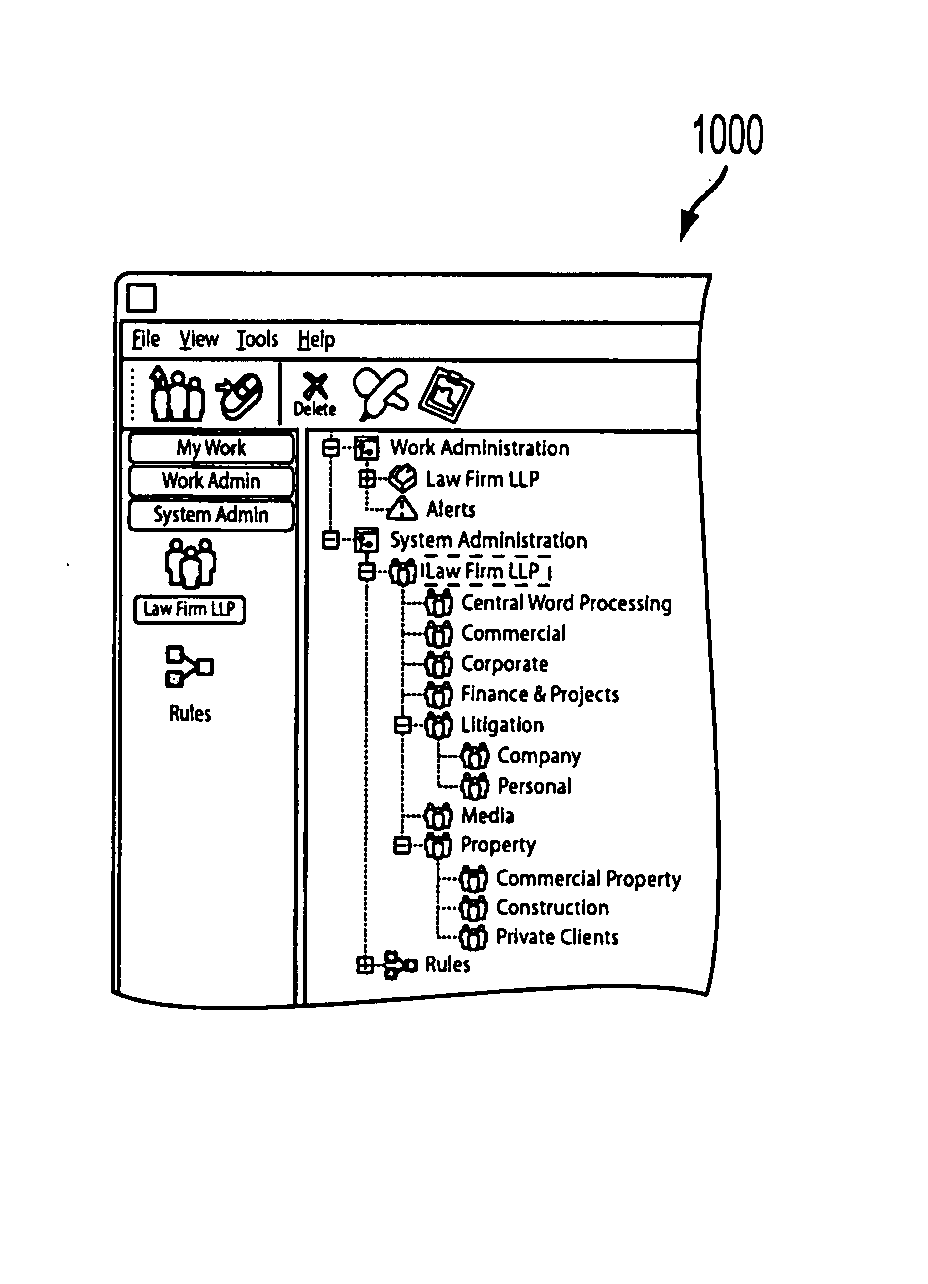
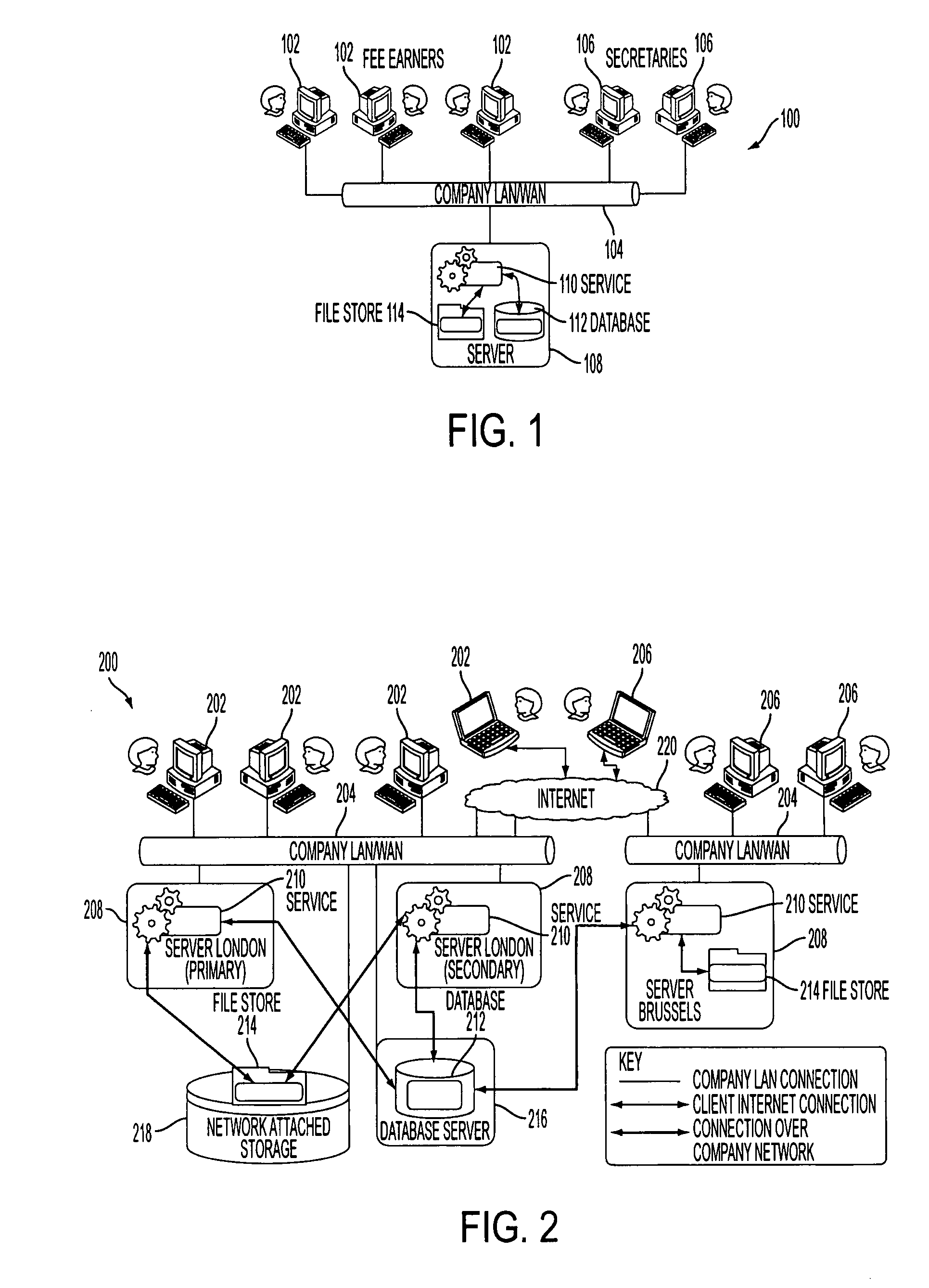
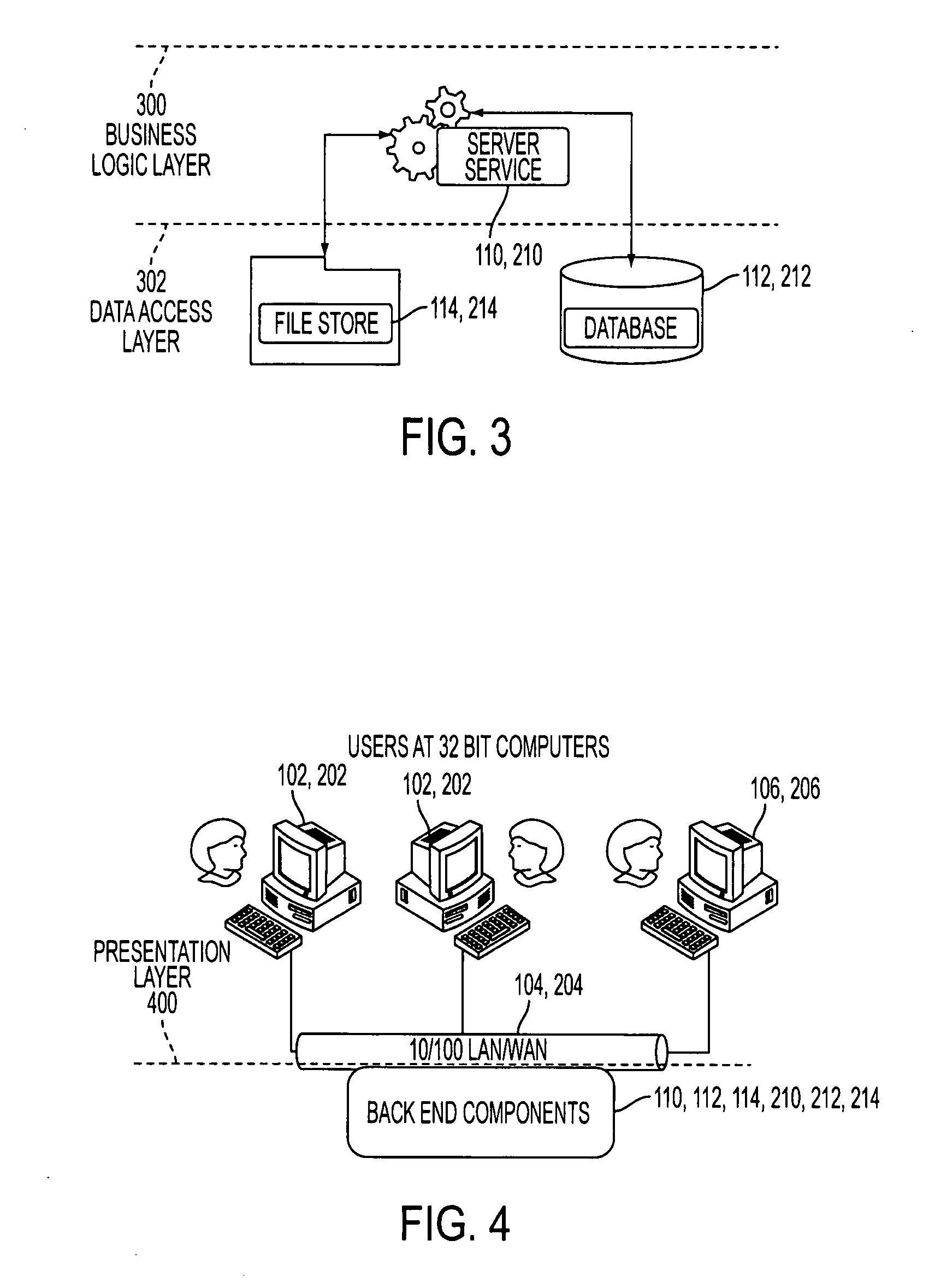
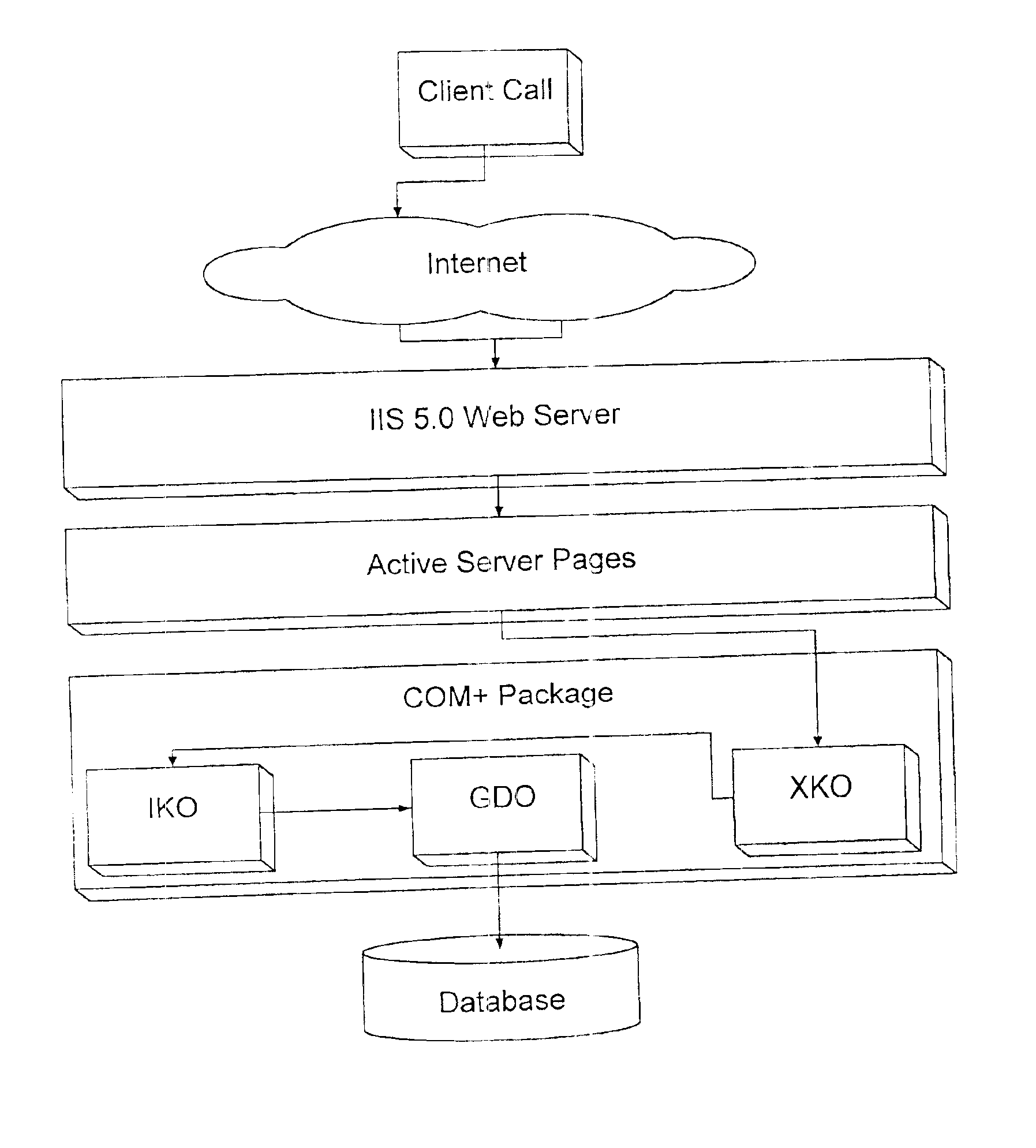
Patents
Literature
476 results about "Data access layer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
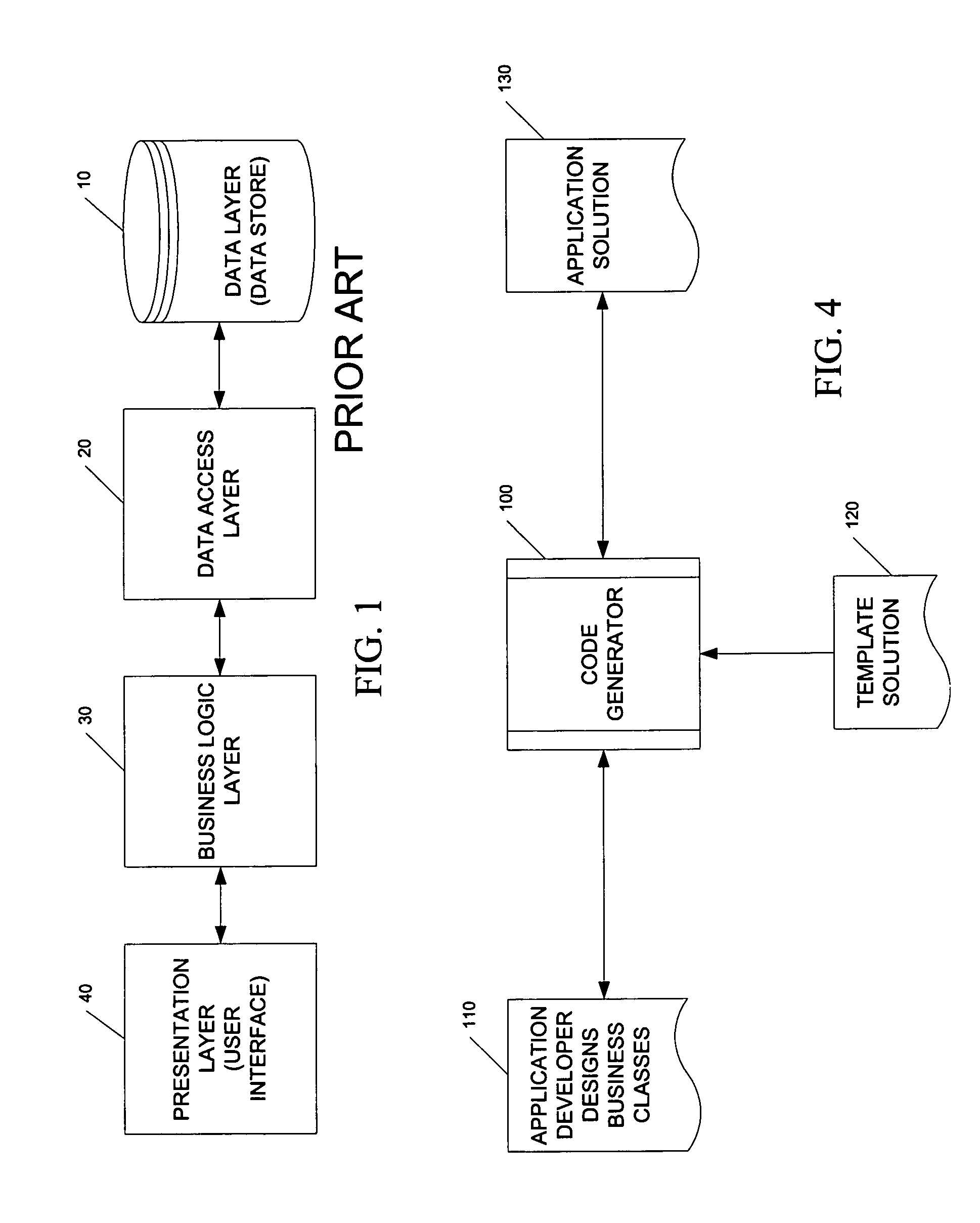
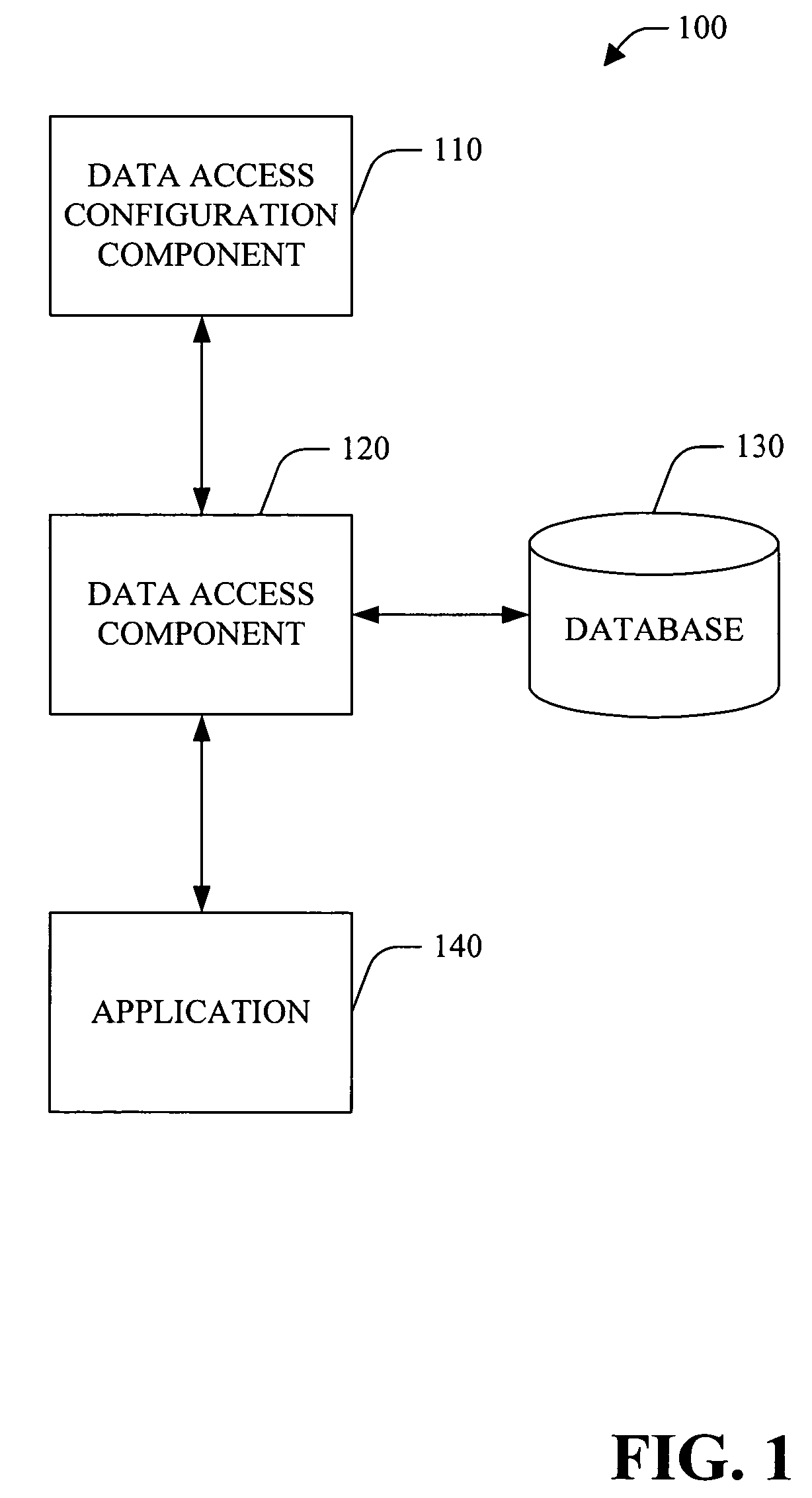
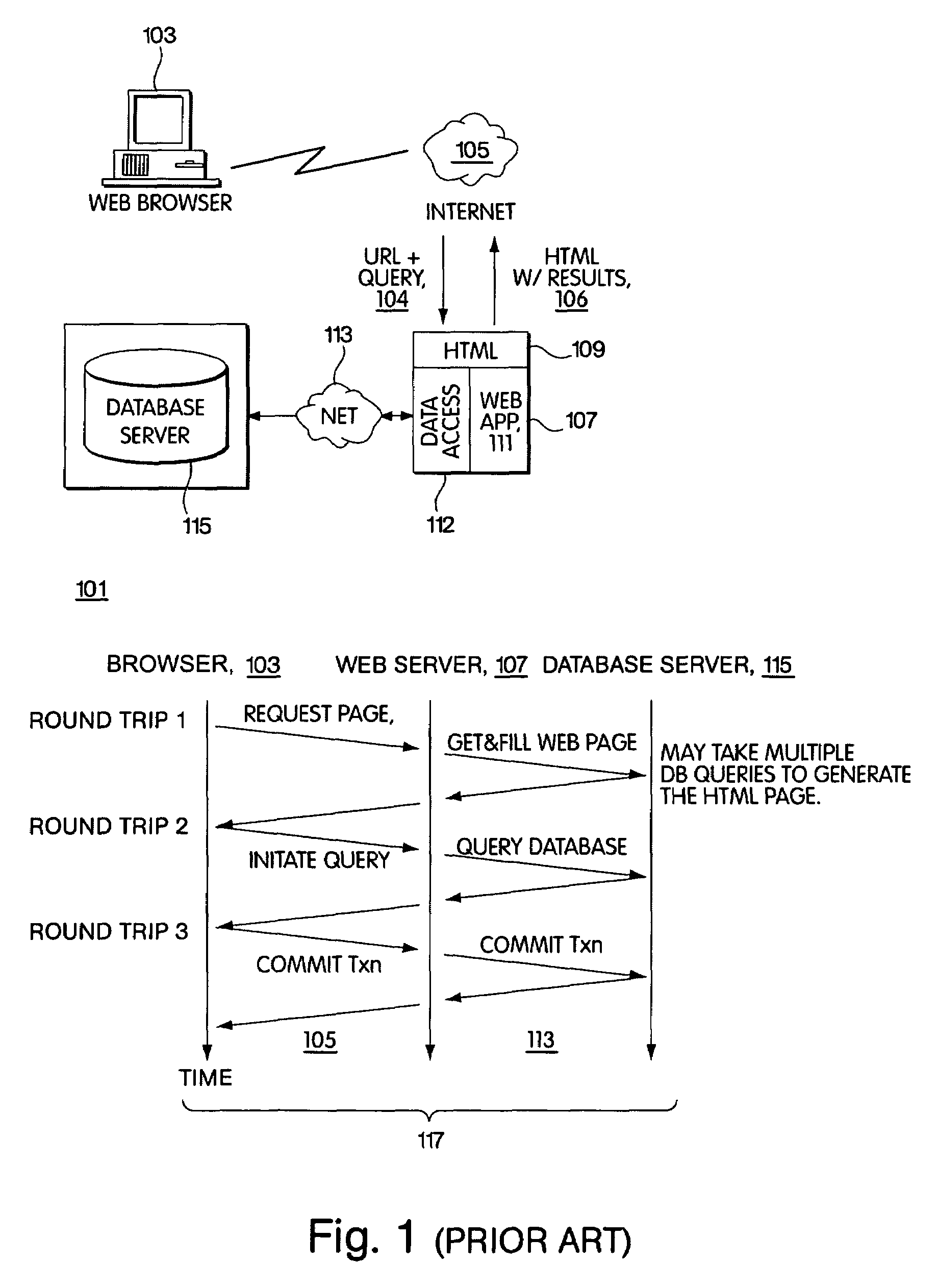
A data access layer (DAL) in computer software, is a layer of a computer program which provides simplified access to data stored in persistent storage of some kind, such as an entity-relational database. This acronym is prevalently used in Microsoft environments.
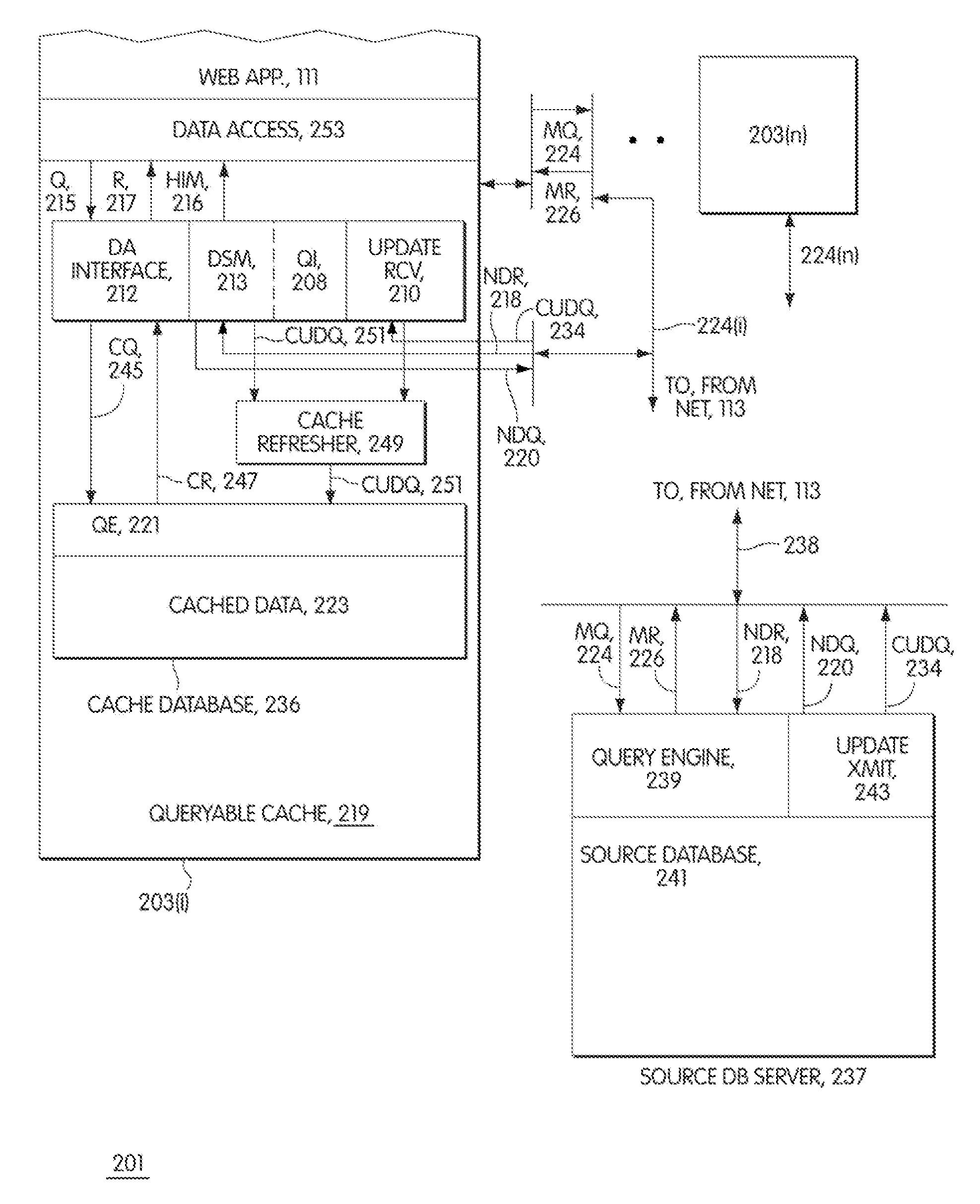
Dynamic caches with miss tables
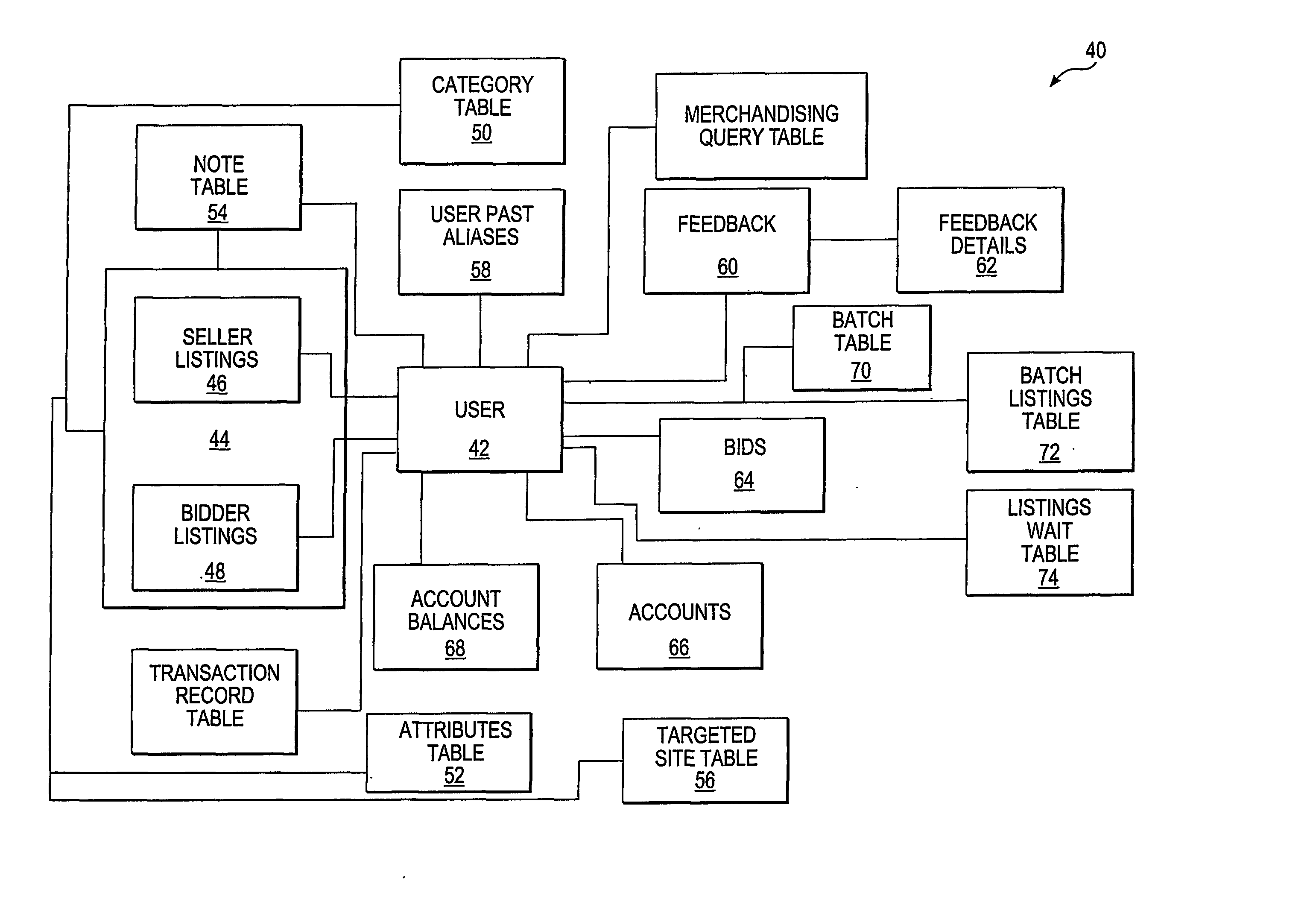
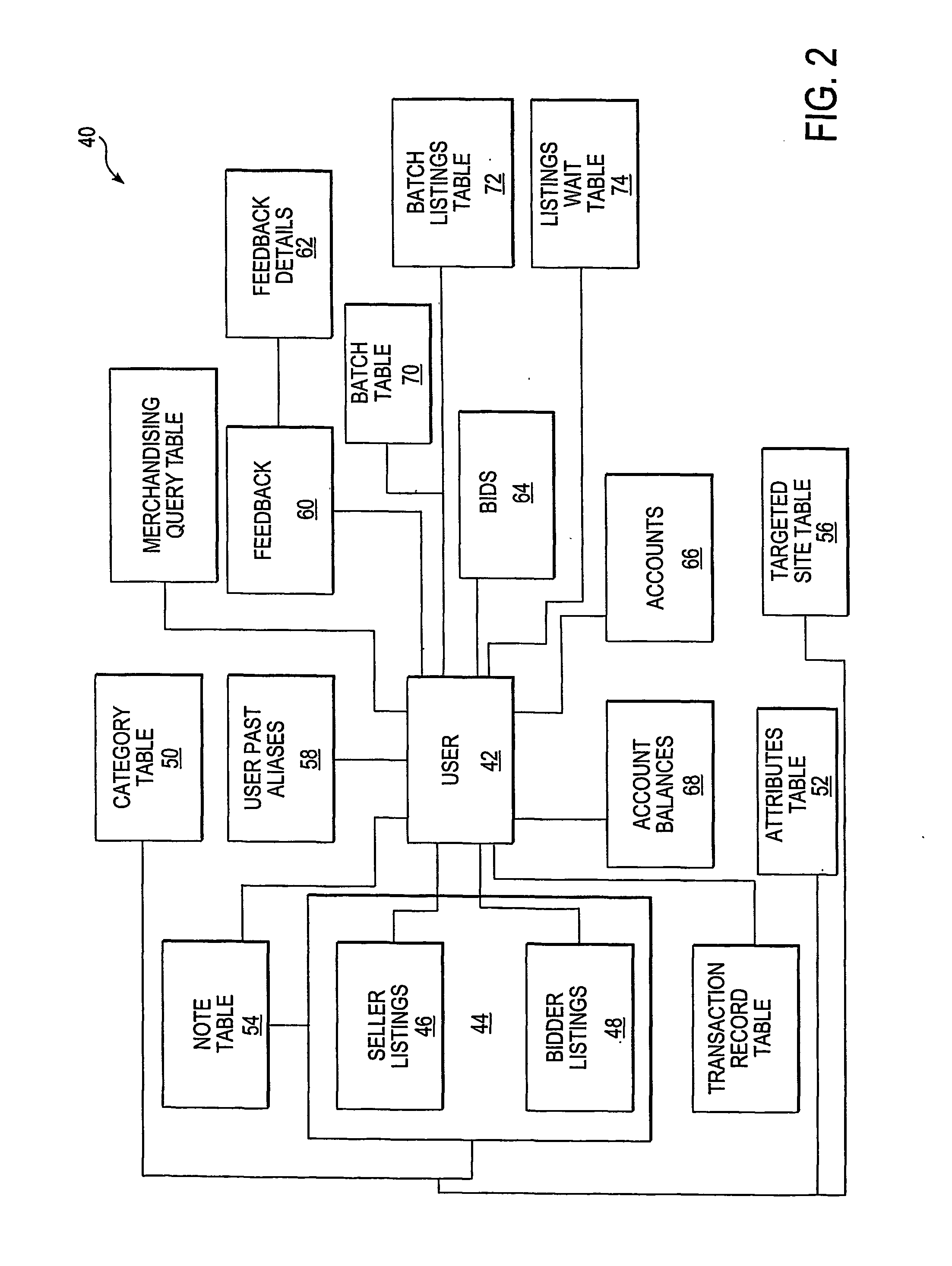
InactiveUS6487641B1Digital data information retrievalMemory adressing/allocation/relocationWeb serviceData source
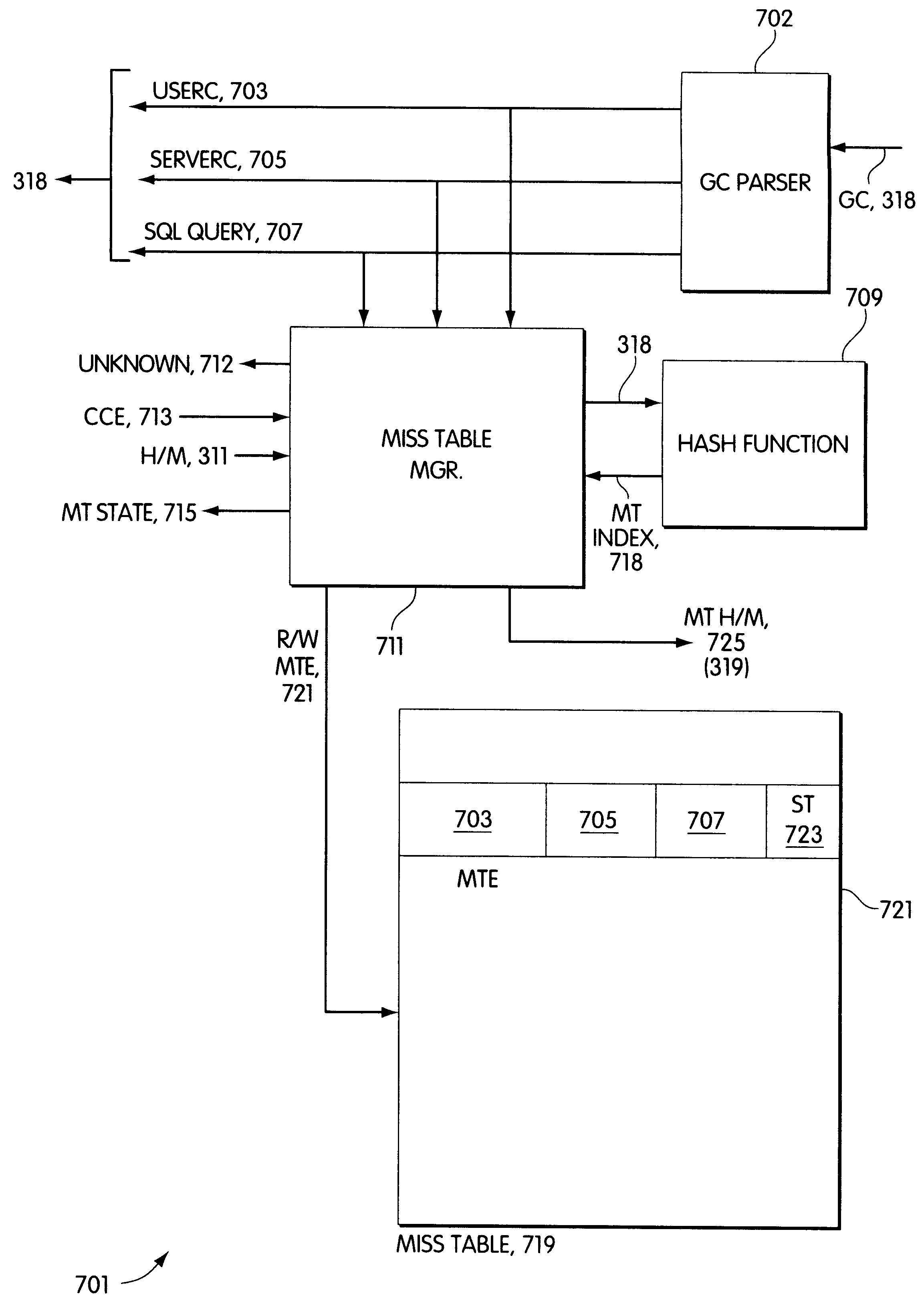
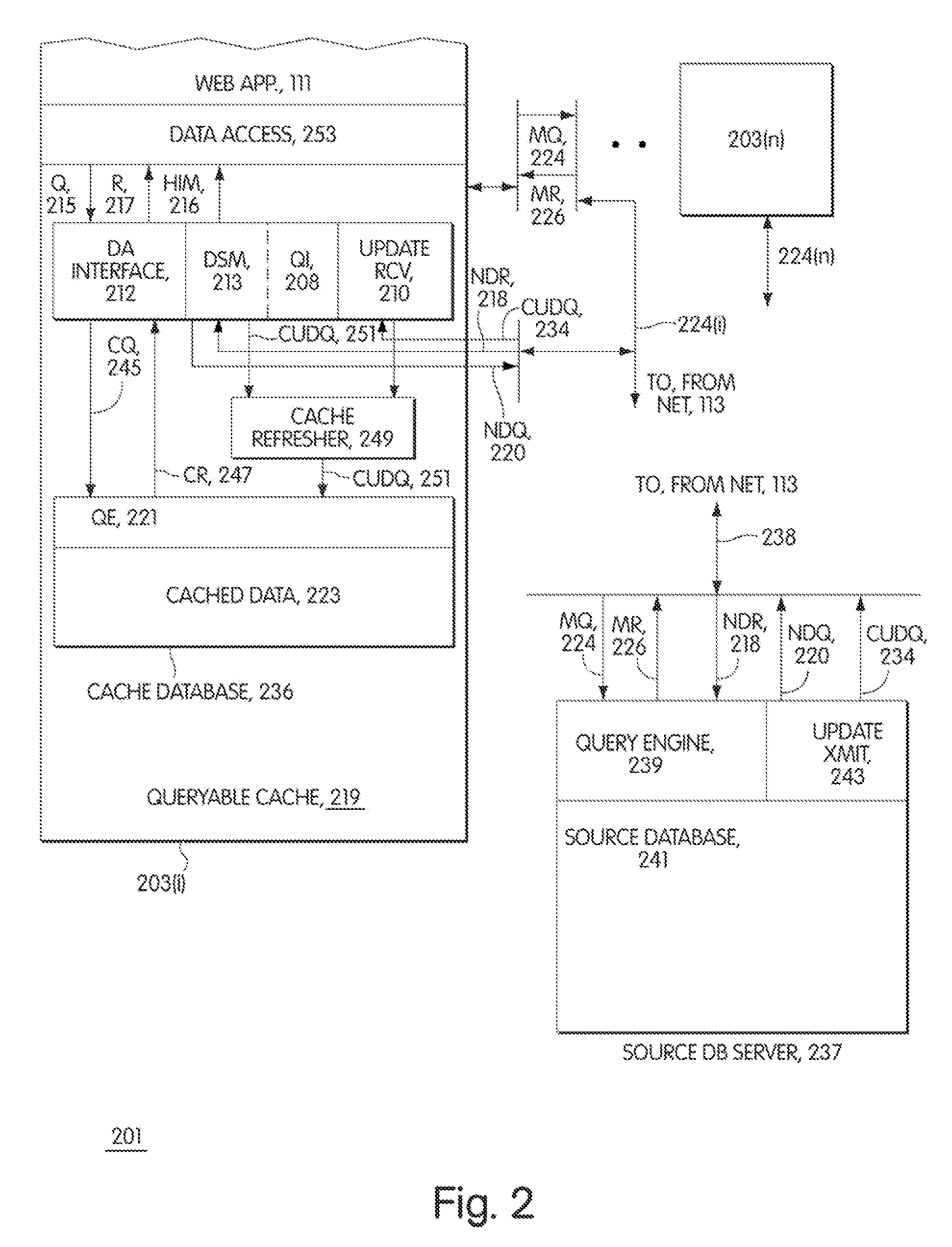
A middle-tier Web server with a queryable cache that contains items from one or more data sources. Items are included in the cache on the basis of the probability of future hits on the items. When the data source determines that an item that has been included in the cache has changed, it sends an update message to the server, which updates the item if it is still included in the cache. In a preferred embodiment, the data source is a database system and triggers in the database system are used to generate update messages. In a preferred embodiment, the data access layer determines whether a data item required by an application program is in the cache. If it is, the data access layer obtains the item from the cache; otherwise, it obtains the item from the data source. The queryable cache includes a miss table that accelerates the determination of whether a data item is in the cache. The miss table is made up of miss table entries that relate the status of a data item to the query used to access the data item. There are three statuses: miss, indicating that the item is not in the cache, hit, indicating that it is, and unknown, indicating that it is not known whether the item is in the cache. When an item is referenced, the query used to access it is presented to the table. If the entry for the query has the status miss, the data access layer obtains the item from the data source instead of attempting to obtain it from the cache. If the entry has the status unknown, the data access layer attempts to obtain it from the cache and the miss table entry for the item is updated in accordance with the result. When a copy of an item is added to the cache, miss table entries with the status miss are set to indicate unknown.
Owner:ORACLE INT CORP
Code generator tool for building software applications with reusable components
InactiveUS7761848B1Eliminate timeEliminate resourceDigital data processing detailsMultiple digital computer combinationsData setData access
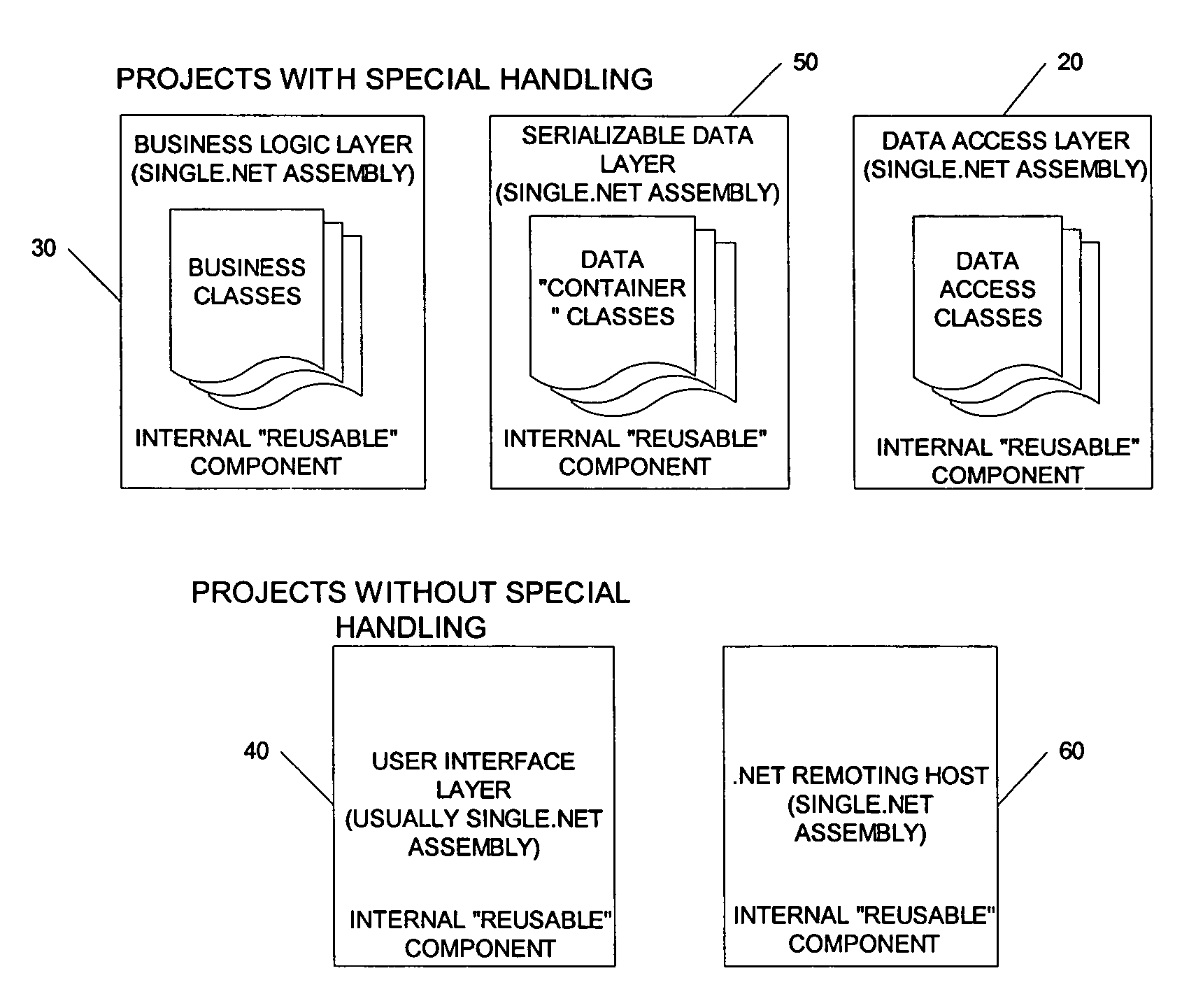
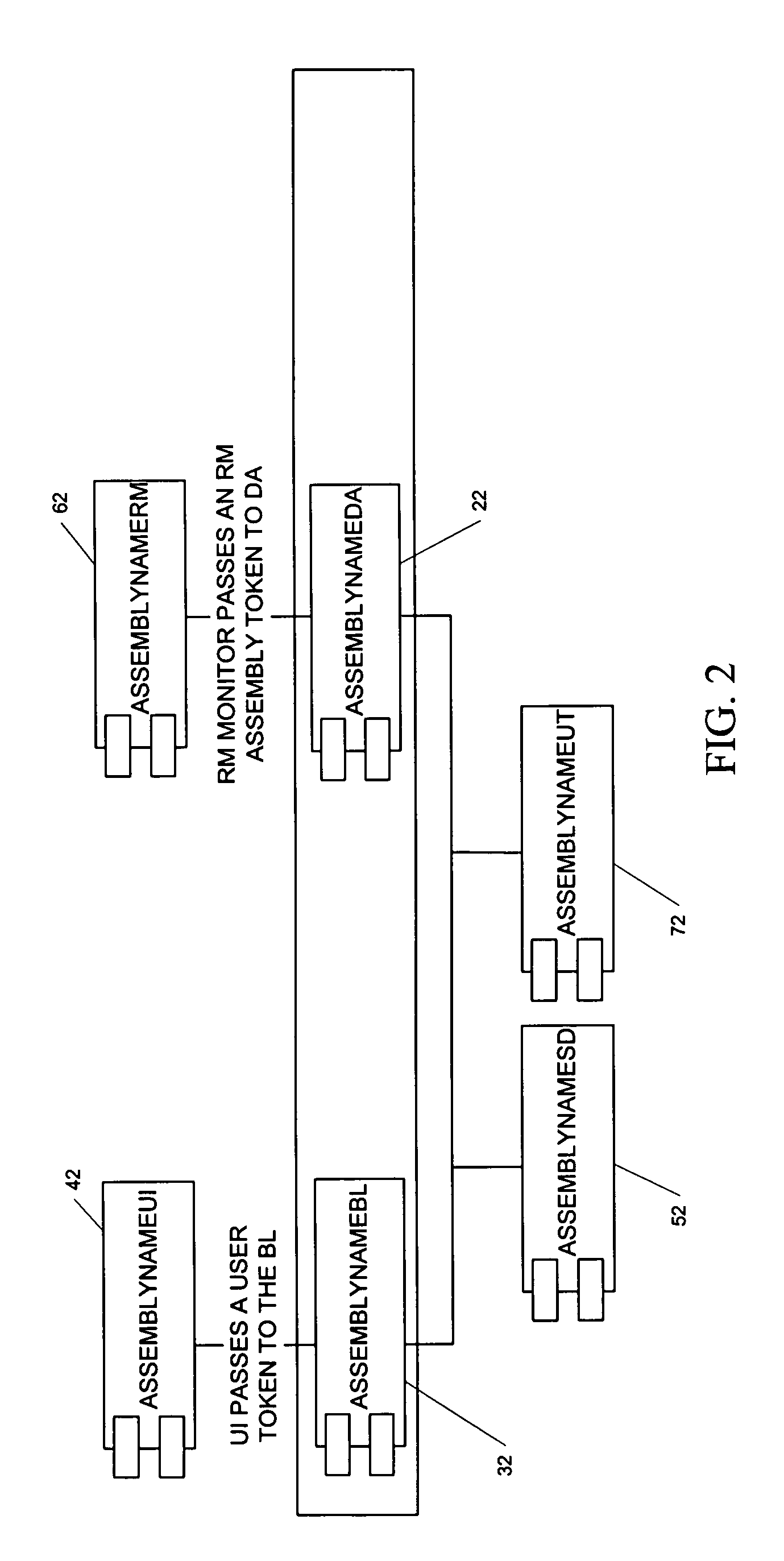
A method and computer program product for building a multiple layer object-oriented software application with reusable components. The method includes the steps of creating business classes containing business logic for the software application; reading templates utilizing reusable components from a template solution file; and generating programming code for the software application based on the created business classes and selected template. The multiple layers include a data layer, a data access layer, a business logic layer and a user interface layer with executable logic for each layer placed into a corresponding assembly data structure. Security tokens are required to access the classes and methods in either the business logic assembly or data access assembly. A serializable data assembly includes container classes that are used to pass data between the business logic layer and data access layer when a dataset or data table is not appropriate. A code generator user interface enables an application developer to define a namespace, a deploy directory name, a database type, an application type, a target source code directory, and a plurality of class specifications and search criteria.
Owner:OPEN INVENTION NEWTORK LLC
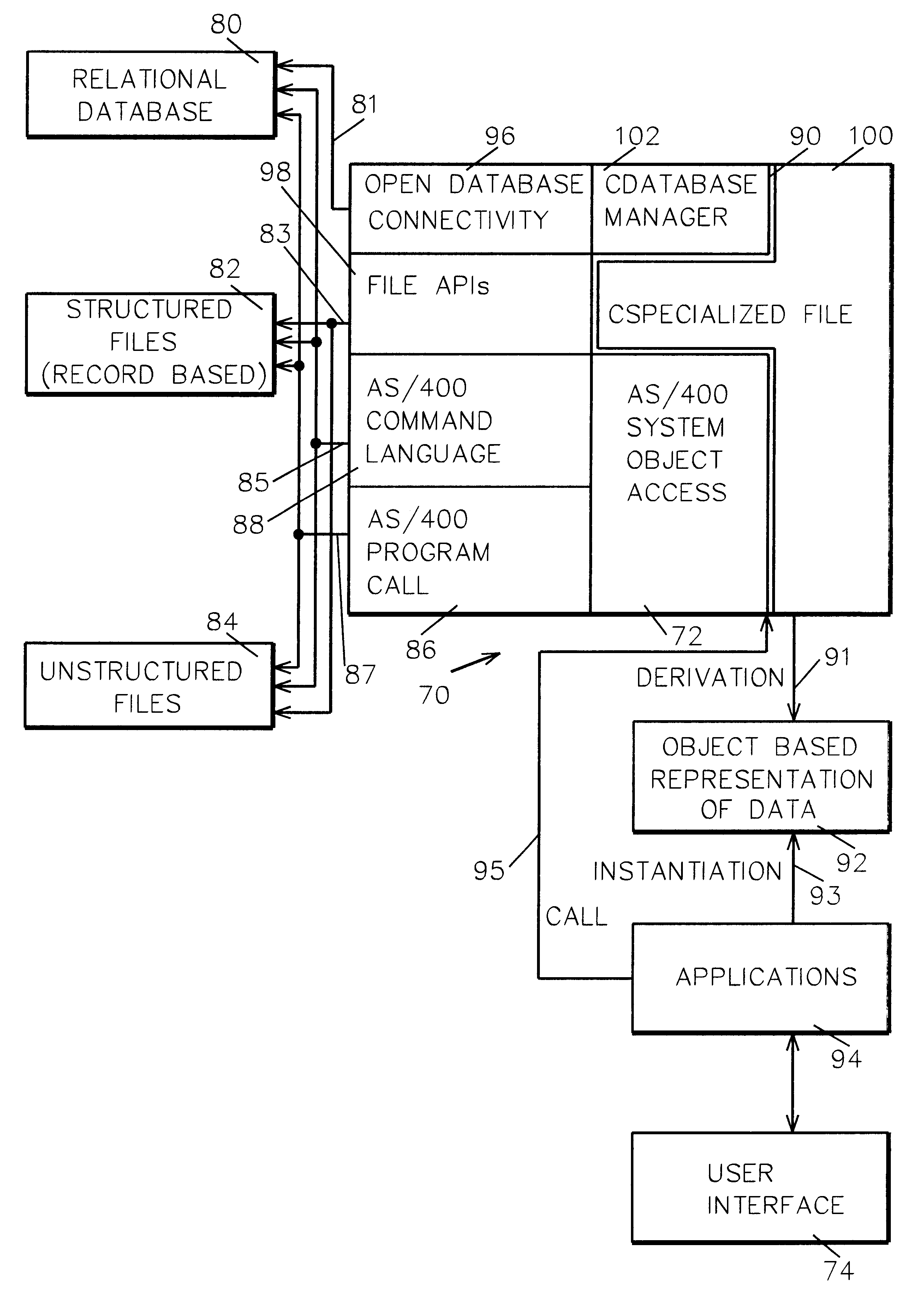
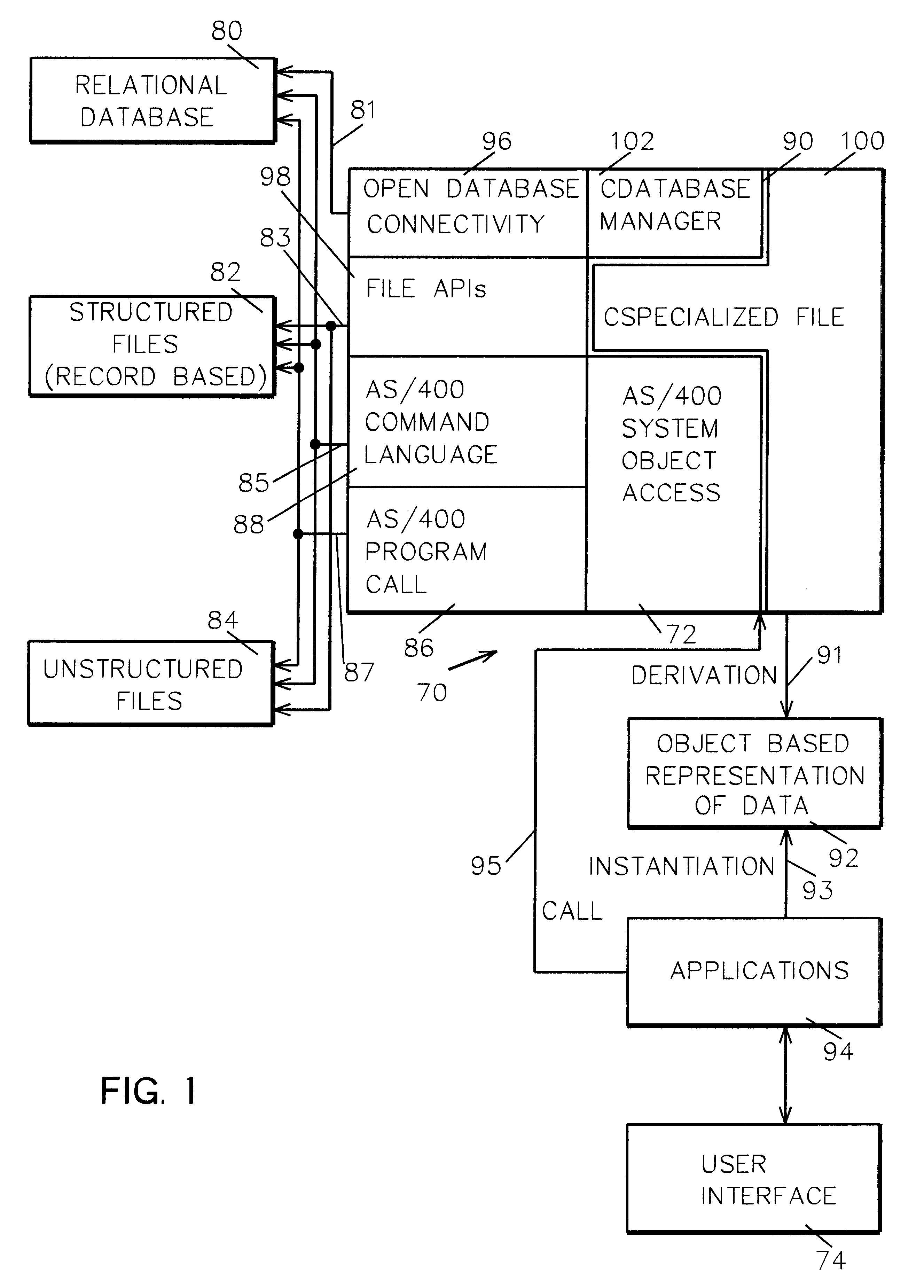
System and method for data manipulation in a dynamic object-based format
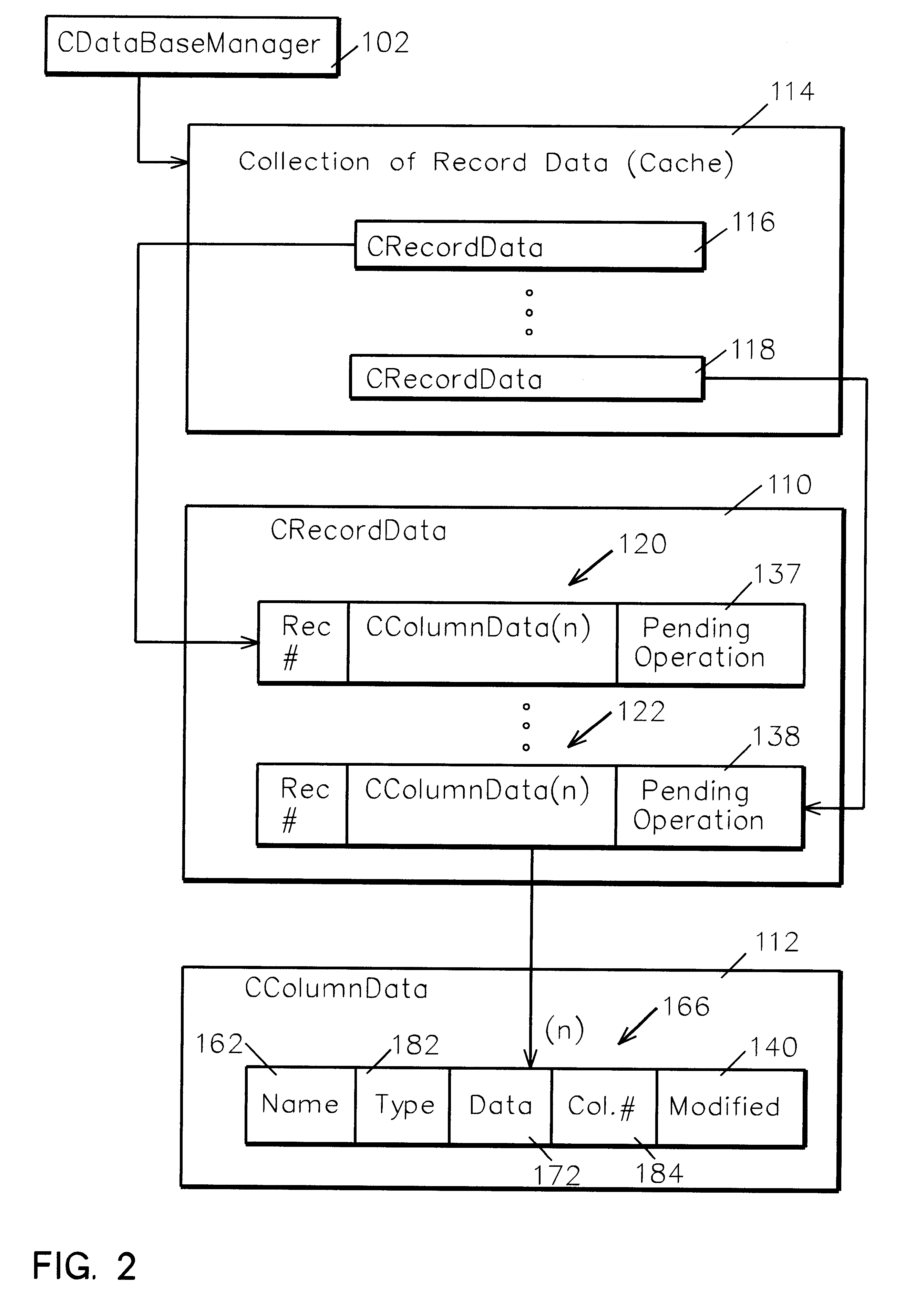
An extensible framework provides a unified interface for data manipulation in a dynamic object-based format. A data access layer of the Transmission Control Protocol / Internet Protocol (TCP / IP) Graphical User Interface (GUI) component uses ODBC to read and write files. Four abstractions implement the framework. These are (1) a CDatabaseManager class that provides access to data stored in a database; (2) a CSpecializedFile class which composes a CDatabaseManager that abstracts the management of reading and writing to database files and provides a unified interface for use by accessors. If the base class functionality of the CSpecializedFile class is not sufficient then derived specialized file classes are implemented to override the CSpecializedFile commit method and update the file in a different-fashion and / or implement specialized get / set methods by column data item and data type; (3) a CRecordArray class which manages vectored access to information stored as objects in a CColumnData class; and (4) a CColumnData object which manages changes made to the information and saves it when requested.
Owner:IBM CORP
Data loss protection through application data access classification
ActiveUS20100115614A1Memory loss protectionError detection/correctionData accessApplication software
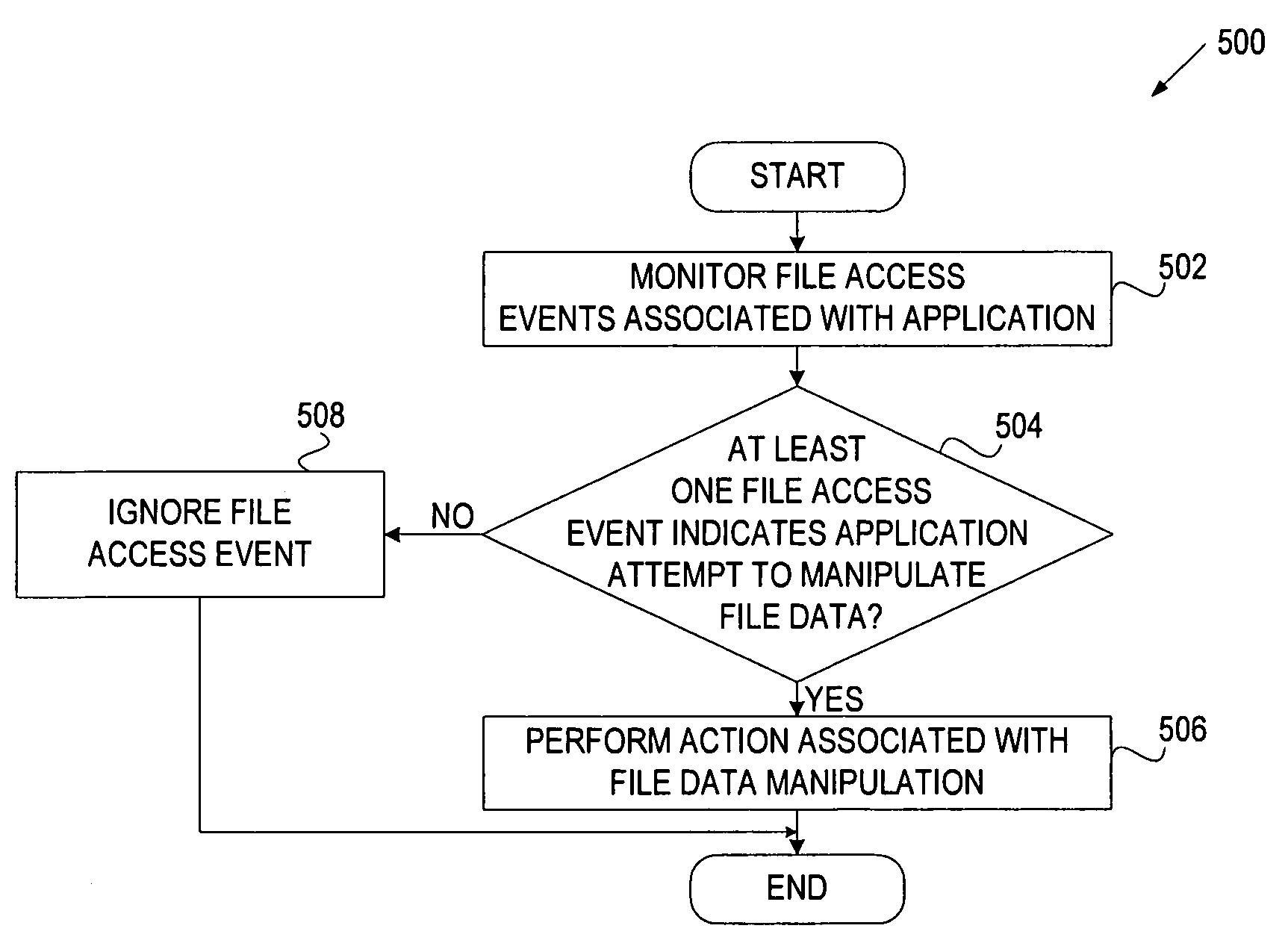
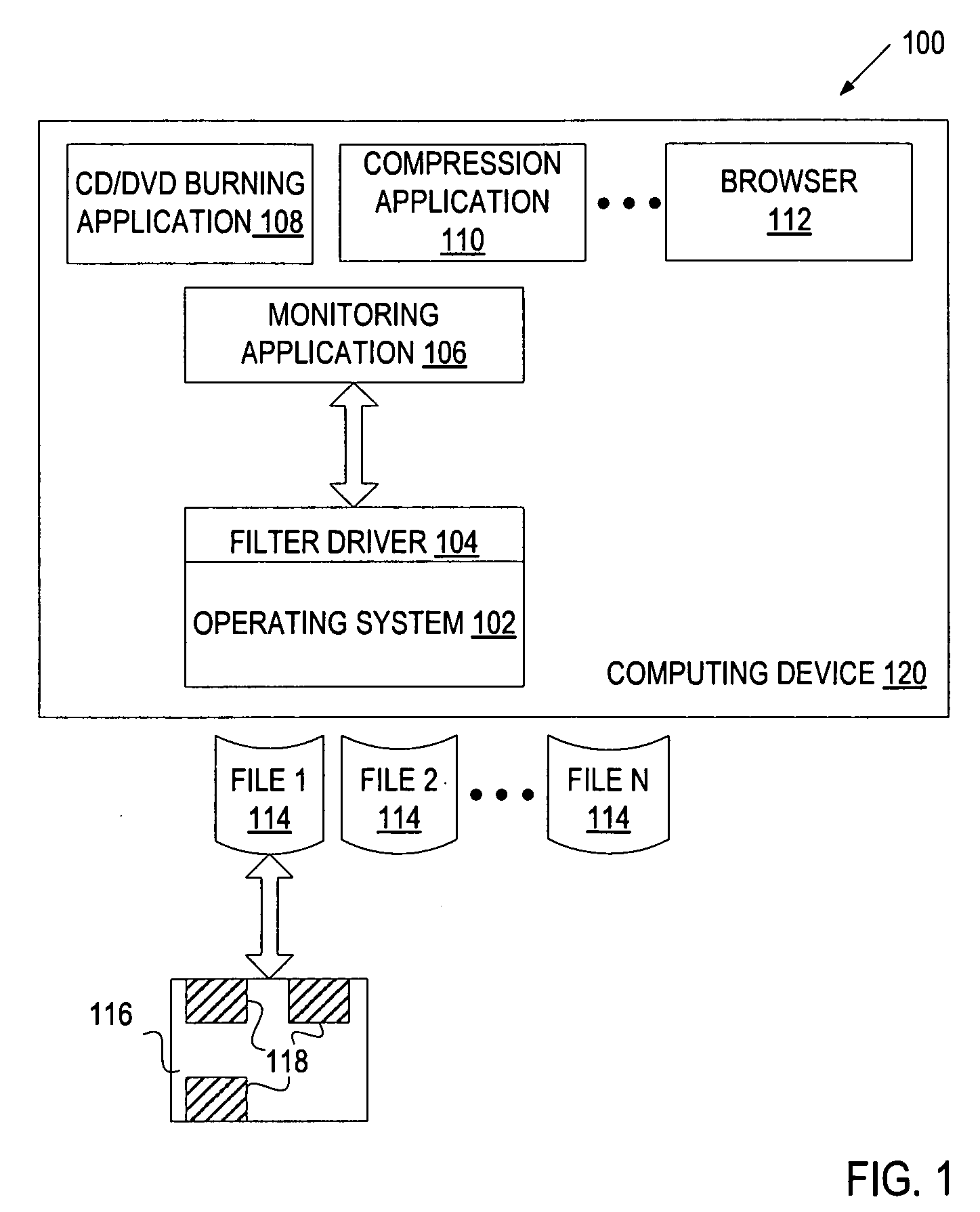
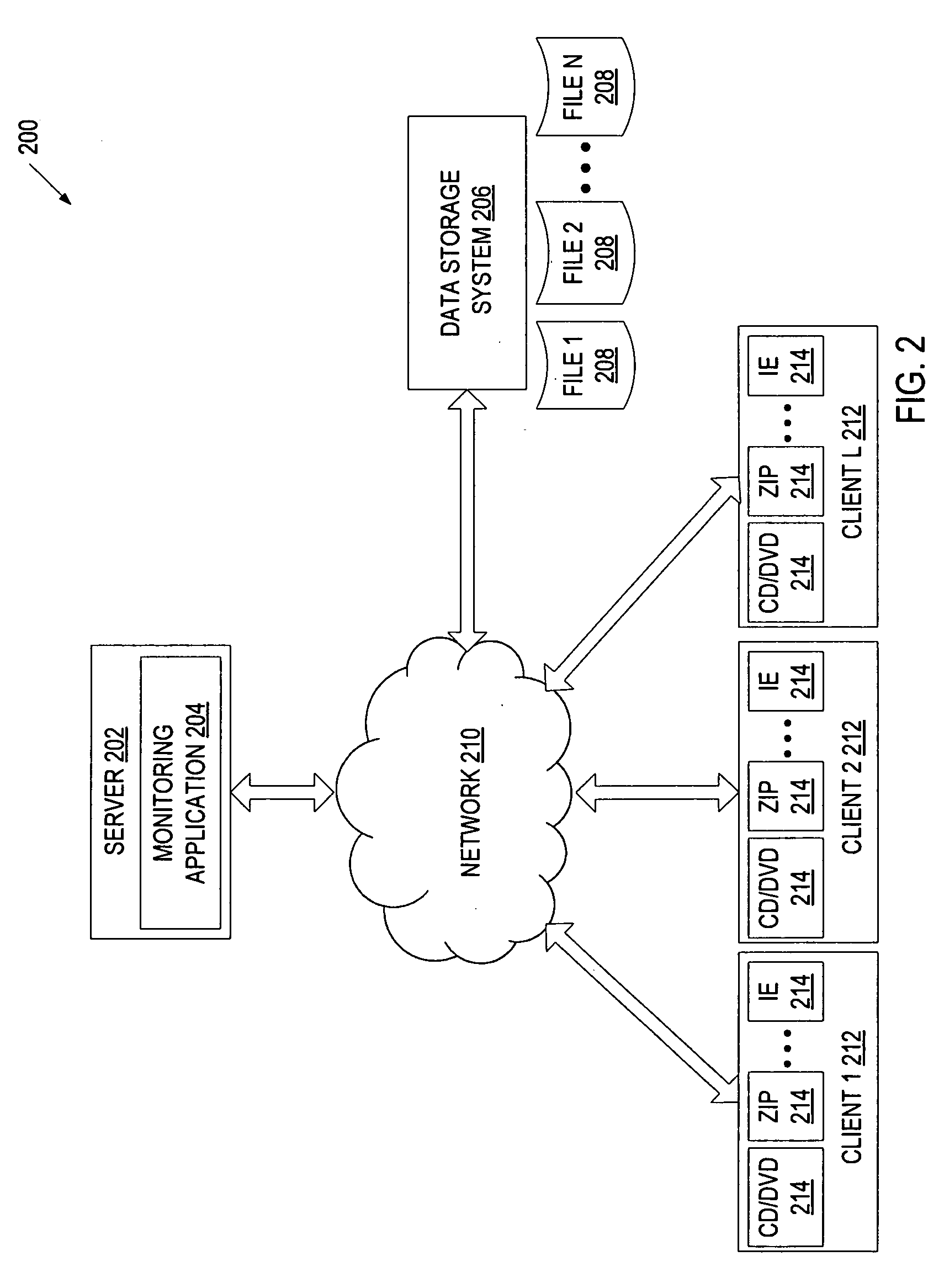
A method and apparatus for classifying behavior of an application based on its data access pattern is described. In one embodiment, the method includes monitoring file access events associated with an application, and determining whether at least one of the file access events indicates the application's attempt to manipulate data of a file. If at least one file access event indicates the application's attempt to manipulate the data within the file, then at least one action is caused to be performed.
Owner:CA TECH INC
Method and apparatus for delivering healthcare
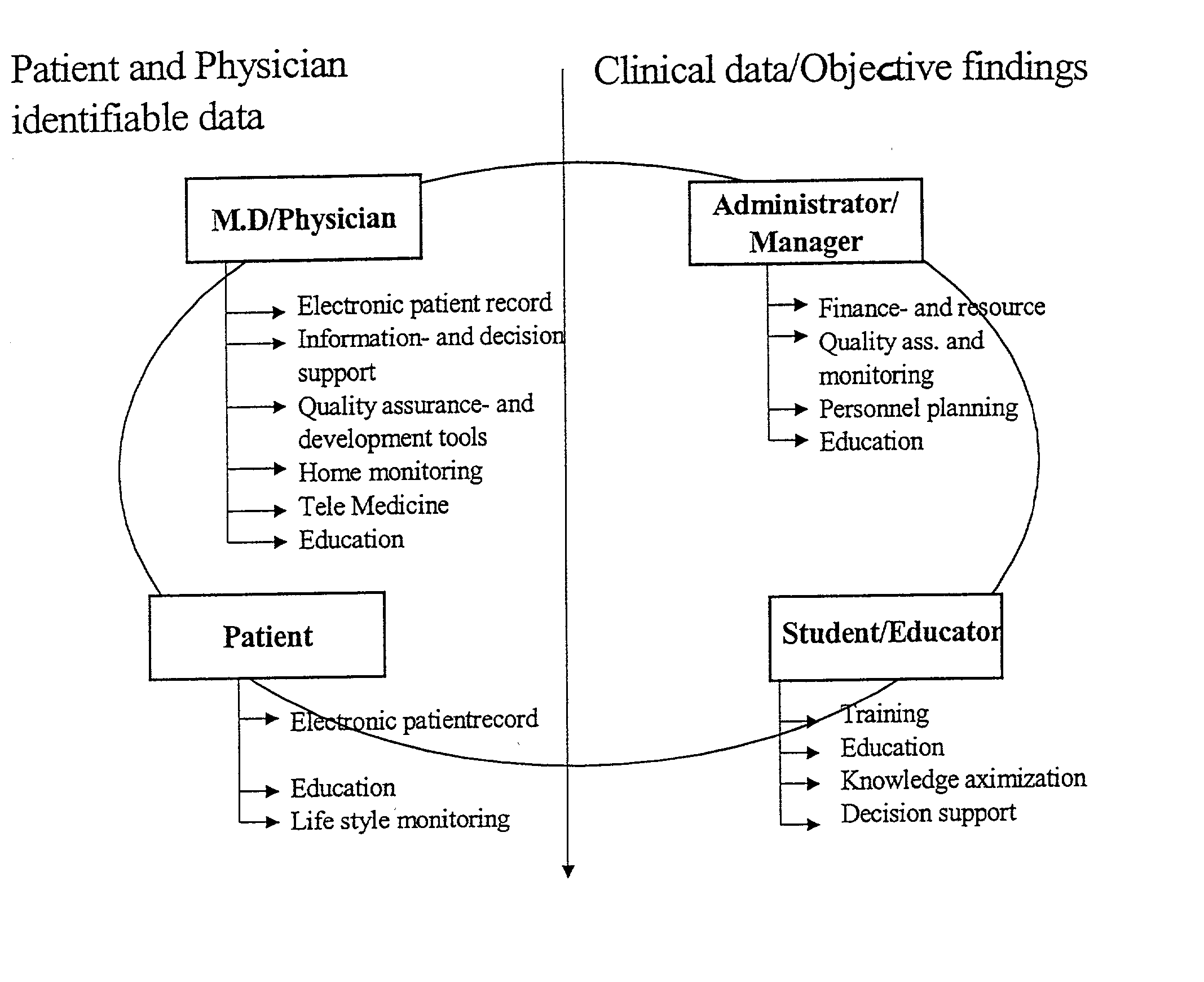
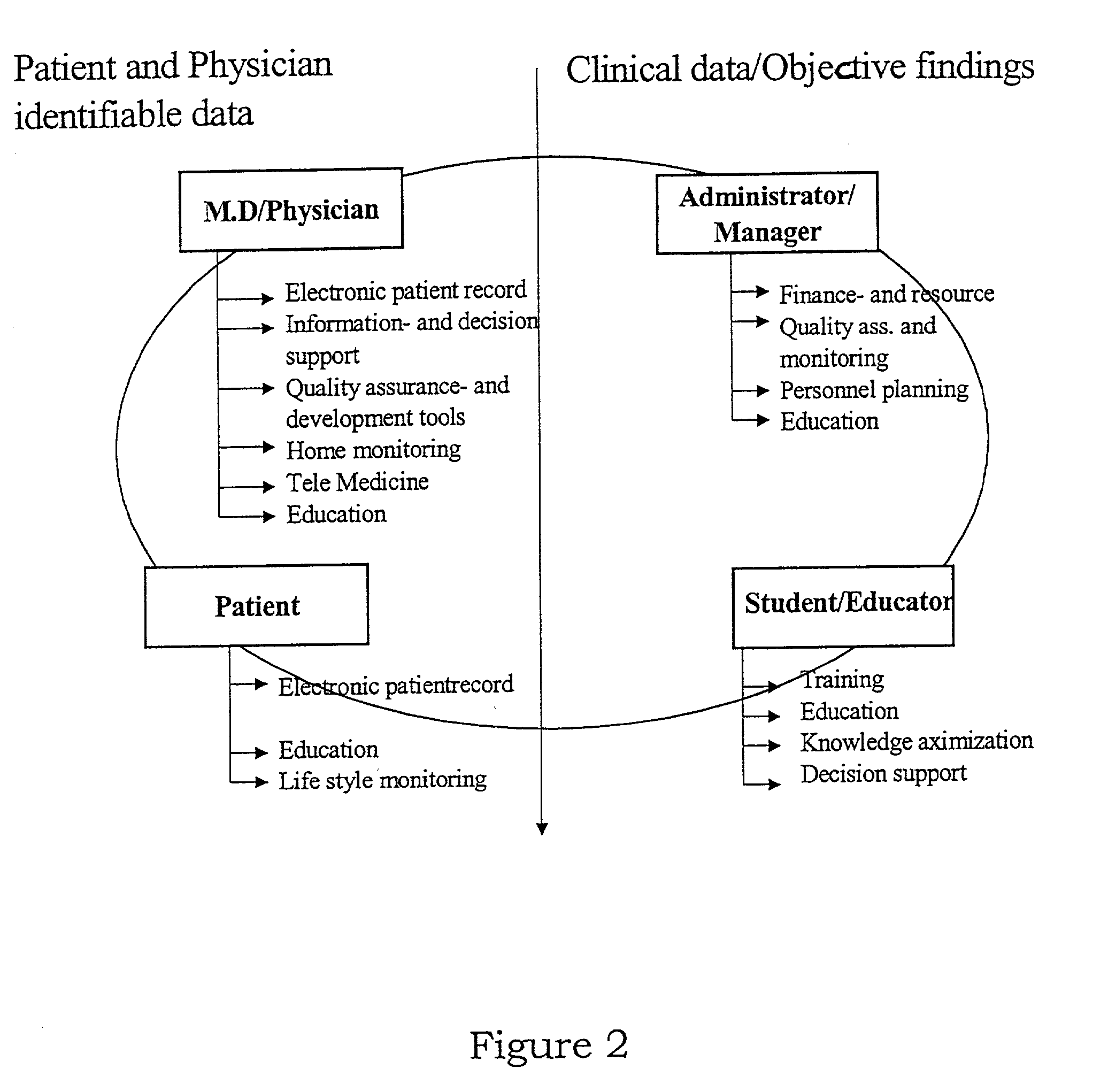
InactiveUS20020178031A1Easily be integrated into existing healthcare systemData processing applicationsLocal control/monitoringPatient dataProtocol Application
A healthcare management system integrates medical practitioners, healthcare administrators, patients and educators / students. Patient data is stored in a repository as clinical data with associated patient data. The clinical data is available for medical practitioners, educators and students without the patient data. The system is structured as an application layer accessed by user terminals and separated from the repository by a data access layer which stores details of where, and in what format, data is stored.
Owner:PIHL LTD
Data access layer design and code generation
InactiveUS7711740B2Easy data accessEasy accessDigital data processing detailsSoftware designCommon Language RuntimeData access
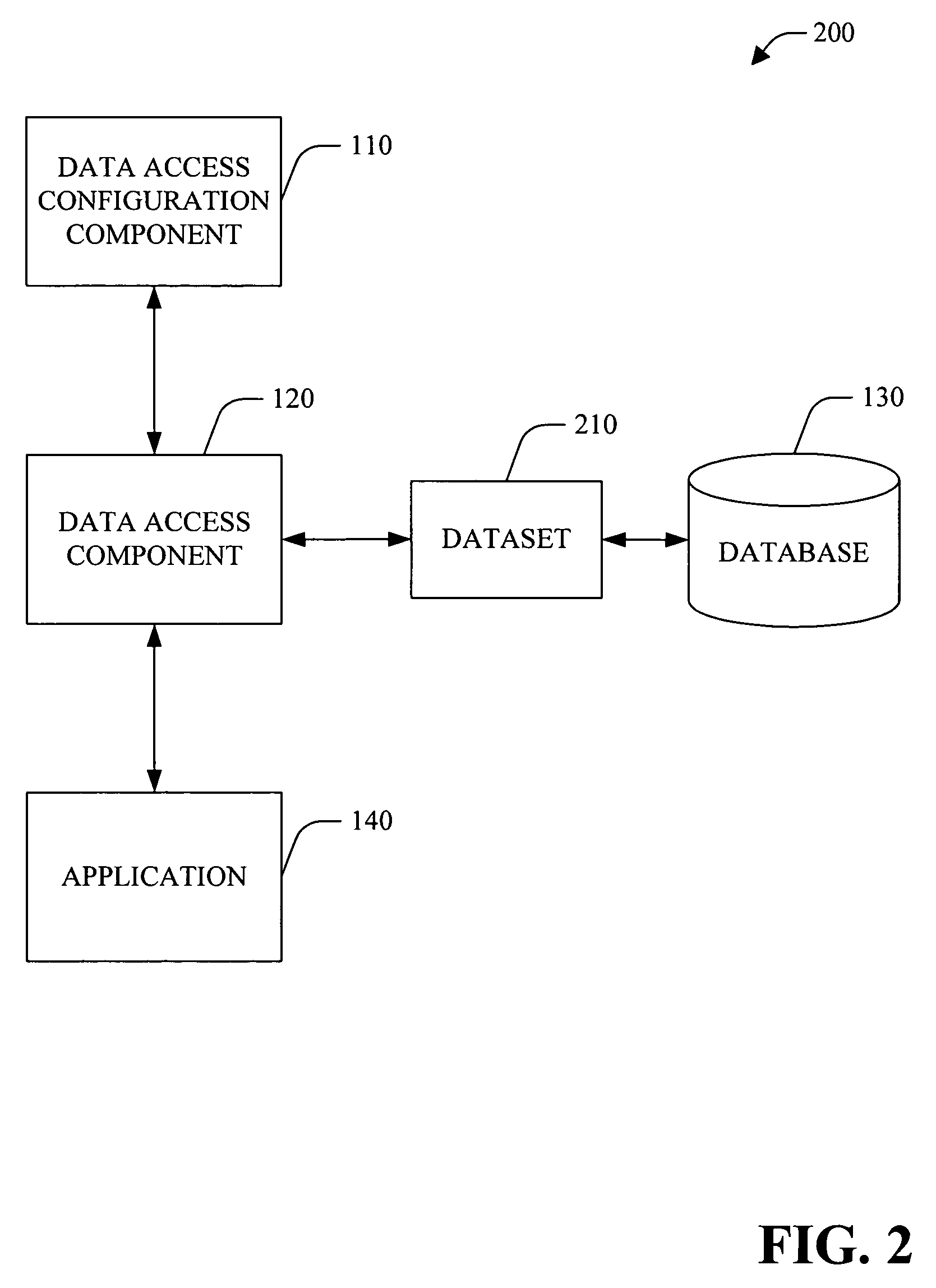
A system and method that facilitate data access in a software development environment is provided. The system generates strongly typed objects that encapsulate raw, untyped data access logic and groups together like database commands in a common data access component. The system provides a mapping between database types and common language runtime data types including the impedance mismatch of null representations. The system configures data access component(s) that are employed at design-time to facilitate access to data object(s) by application(s) and allows a user of the configured data access component(s) to improve developer productivity and / or reduce the quantity of runtime errors introduced into code. The data access component can be instanced on multiple forms components and / or with the developer's own class(es). Thus, change(s) to a query and / or interface are accomplished within the data access component and be available to the forms components and / or object(s) that utilize the data access component.
Owner:MICROSOFT TECH LICENSING LLC
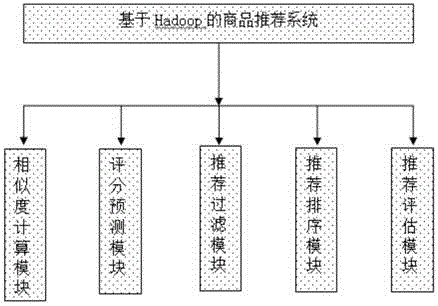
Hadoop-based commodity recommendation system
InactiveCN106600302AEasy to expandInnovative designSpecial data processing applicationsMarketingDesign planExtensibility
The invention provides a Hadoop-based commodity recommendation system comprising five layers: a data access layer, a data model layer, a recommendation algorithm layer, a recommendation engine layer, and a recommendation application layer. The insides of all layers employ modularization designs and all layers interact with each other based on interfaces, thereby realizing high cohesion and low coupling of the system architecture and high extensibility. The database of the system employs Hive; convenient on-line shopping functions like commodity browsing, purchasing payment, logistics allocation, after-sales service and the like can be provided for users. On the basis of the high-efficiency, reliable, and convenient-extension distributed system infrastructure, the system is suitable for large-scale data storage and computing processing; the system based on a novel design and a good design plan has the broad market promotion prospects.
Owner:玺阅信息科技(上海)有限公司
Seamless data migration across databases
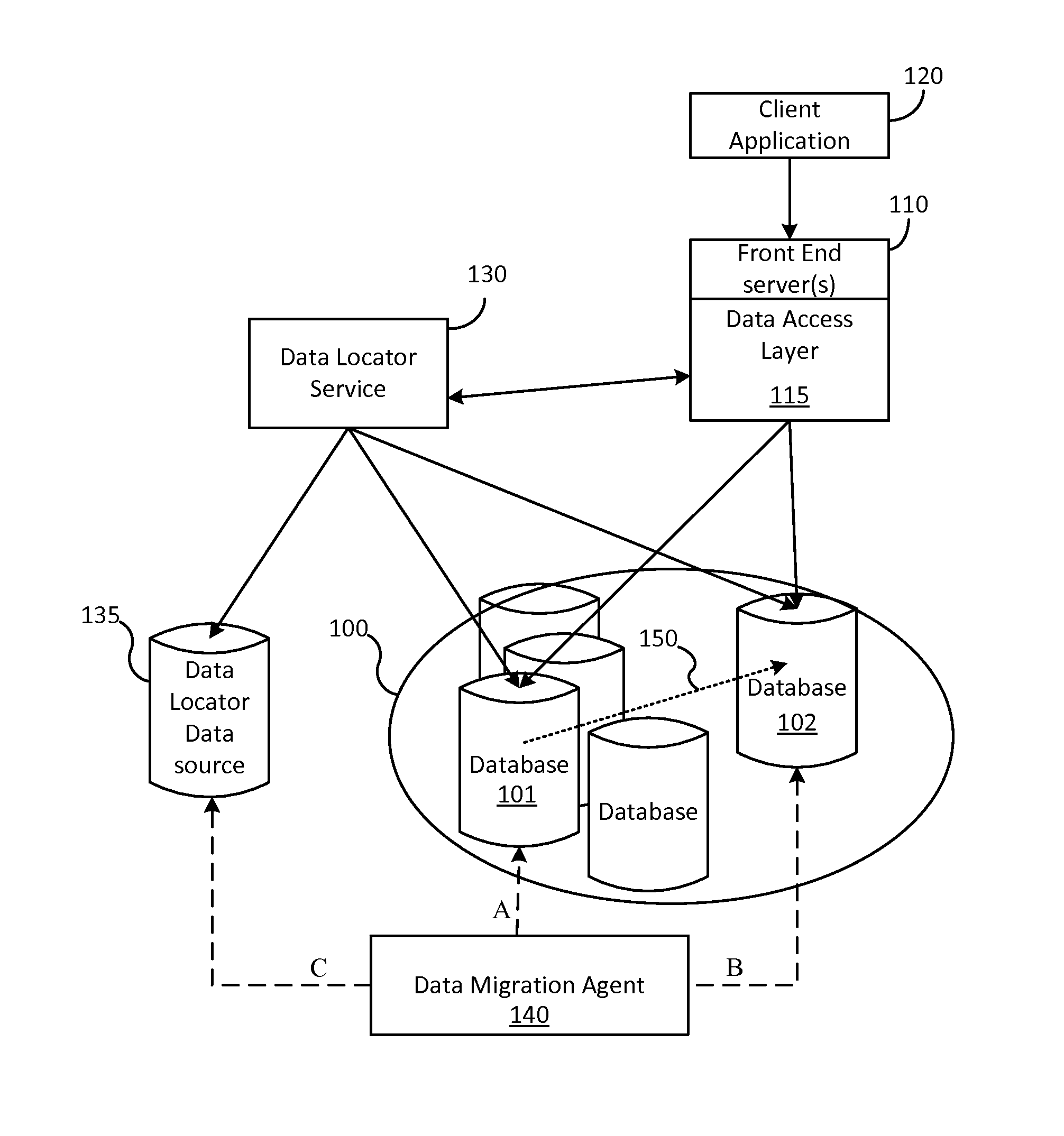
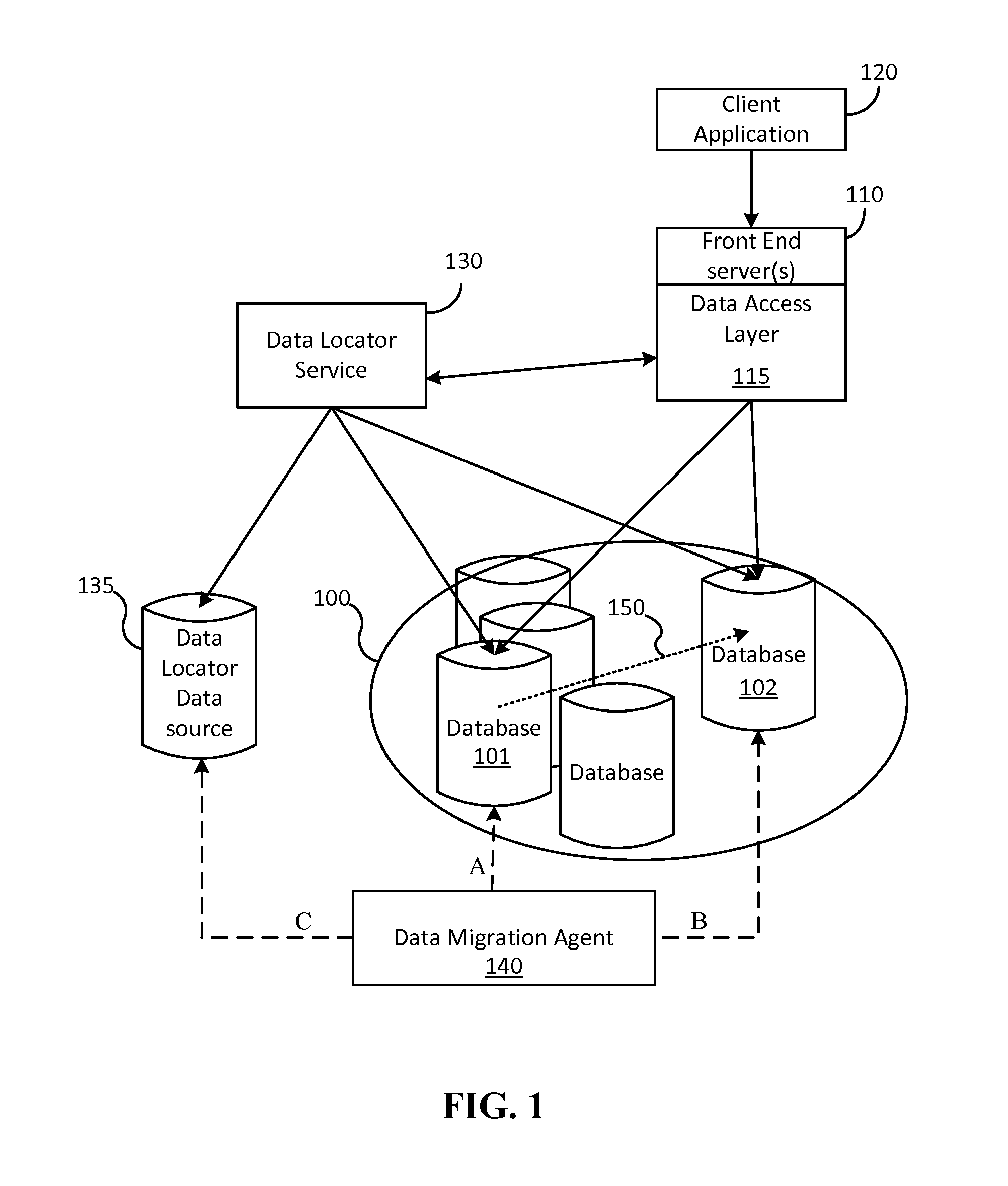
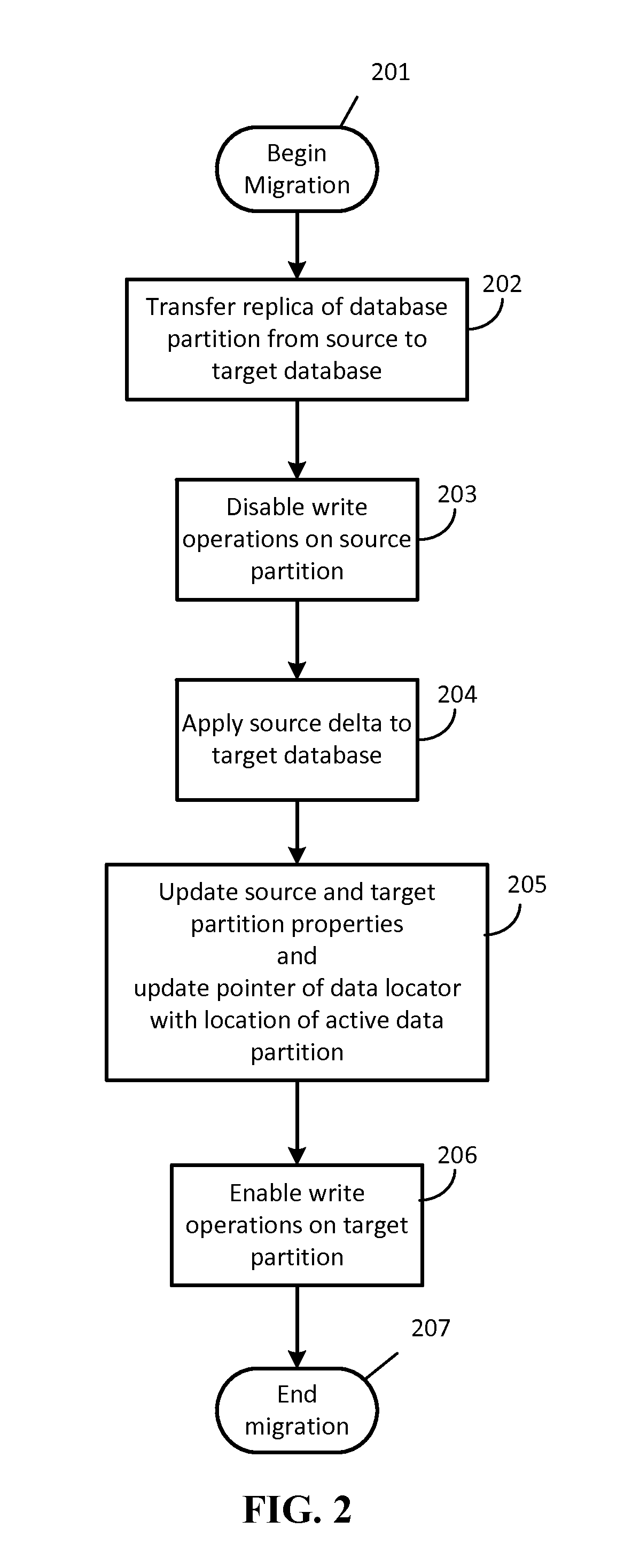
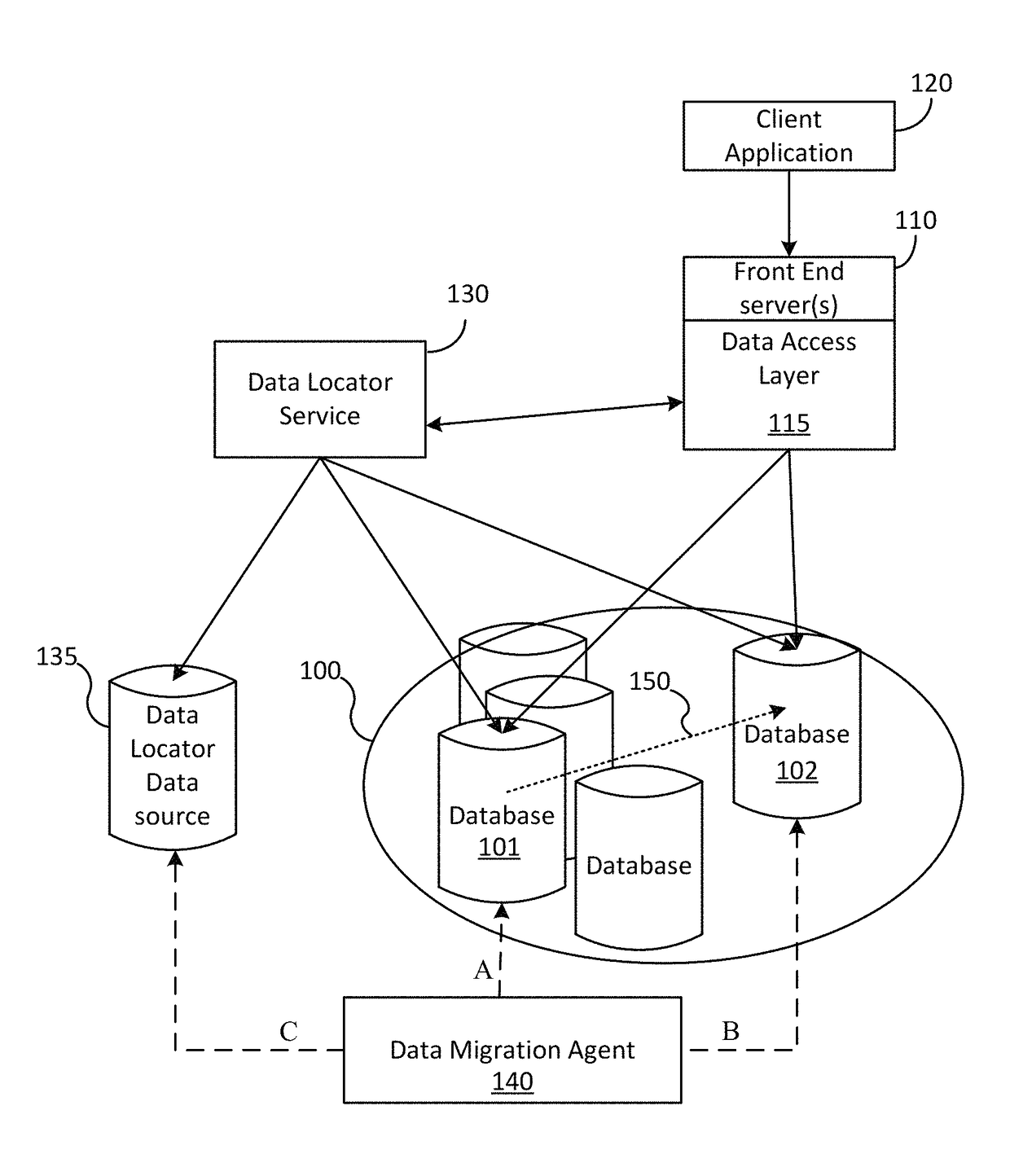
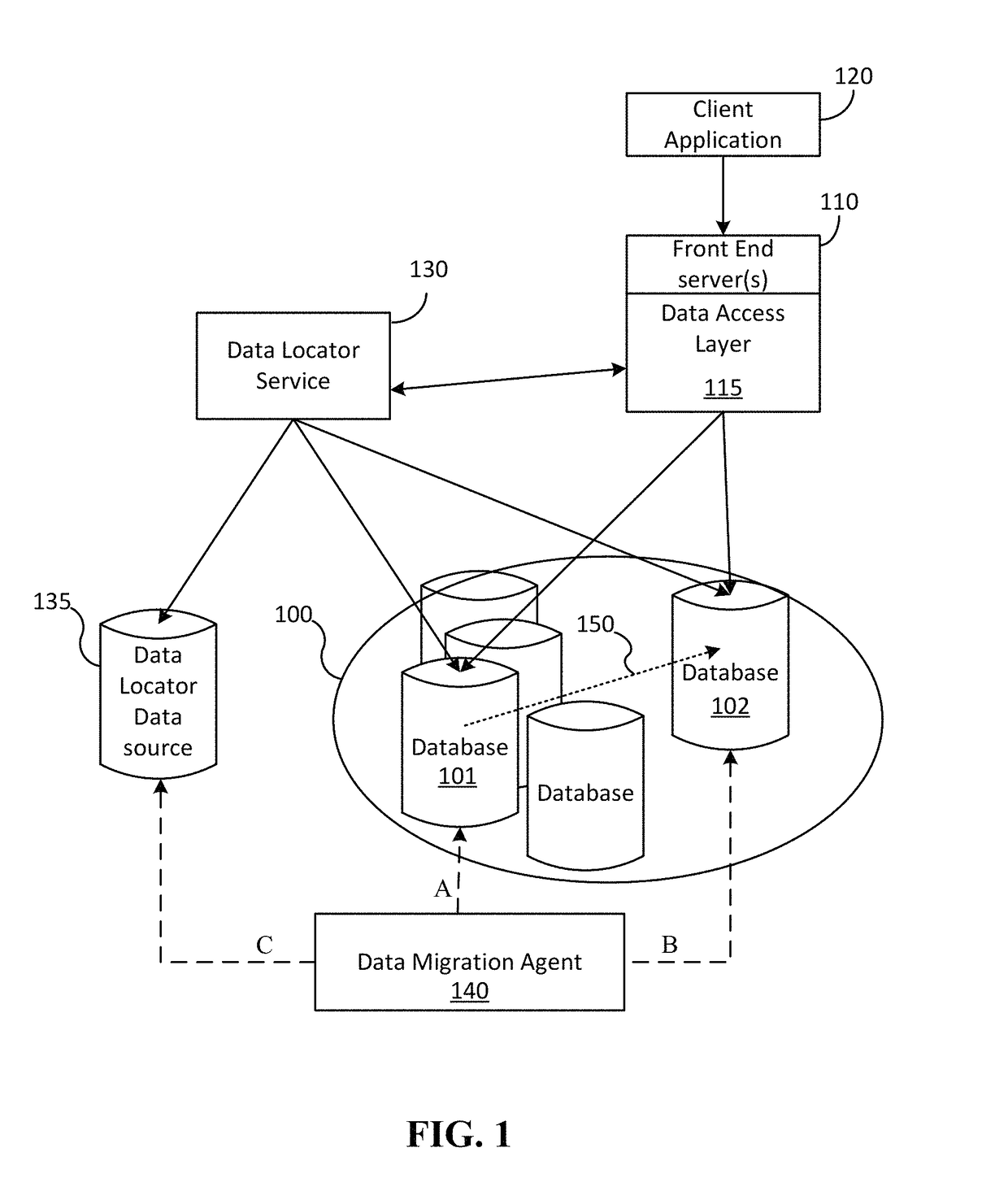
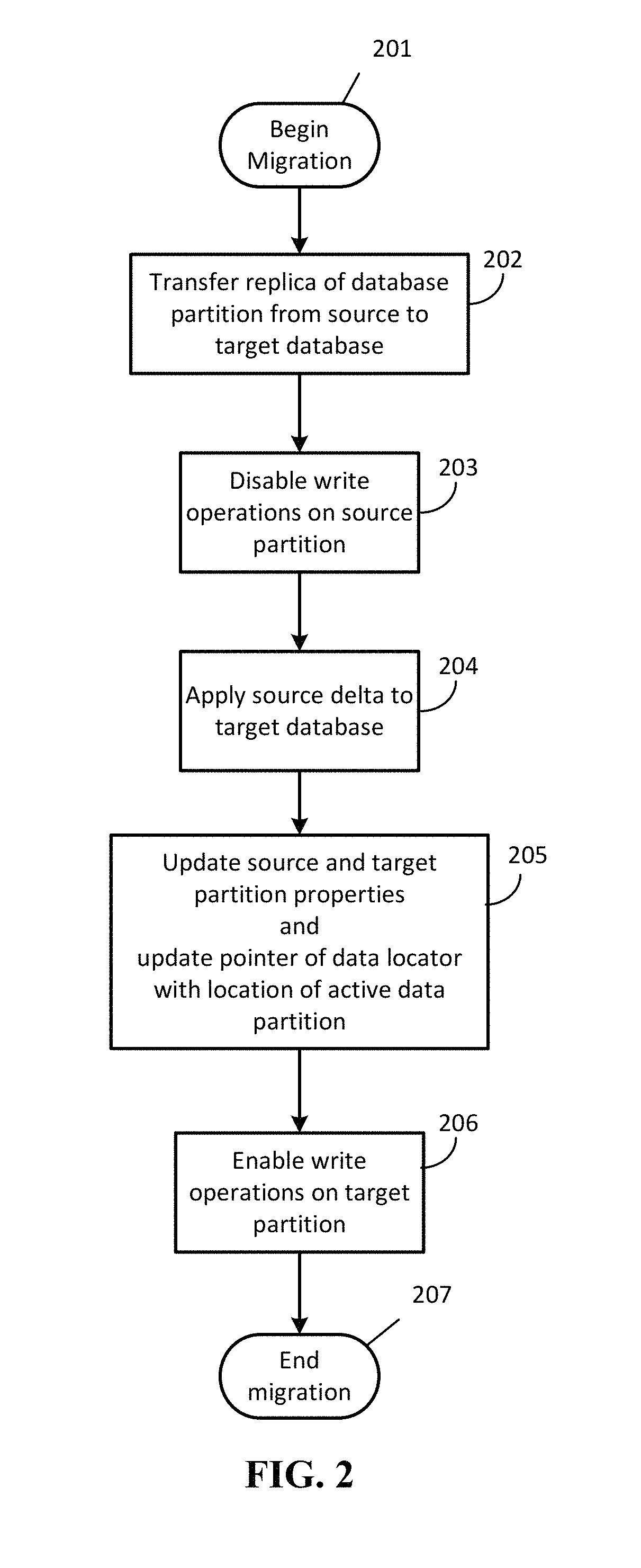
ActiveUS20150254257A1Minimal impactMinimal disruptionDigital data processing detailsDatabase distribution/replicationDistributed Computing EnvironmentData access layer
Techniques are disclosed for enabling the migration of data with minimized impact on consumers of the data. A data migration agent updates pointers to active data locations and coordinates a migration from a first data resource to a second data resource so that seamless migration may be carried out. A data access layer of a distributed computing environment can take advantage of the pointers and metadata written by the data migration agent to serve requests to resources of the distributed computing environment so that read availability is available regardless of migration status.
Owner:MICROSOFT TECH LICENSING LLC
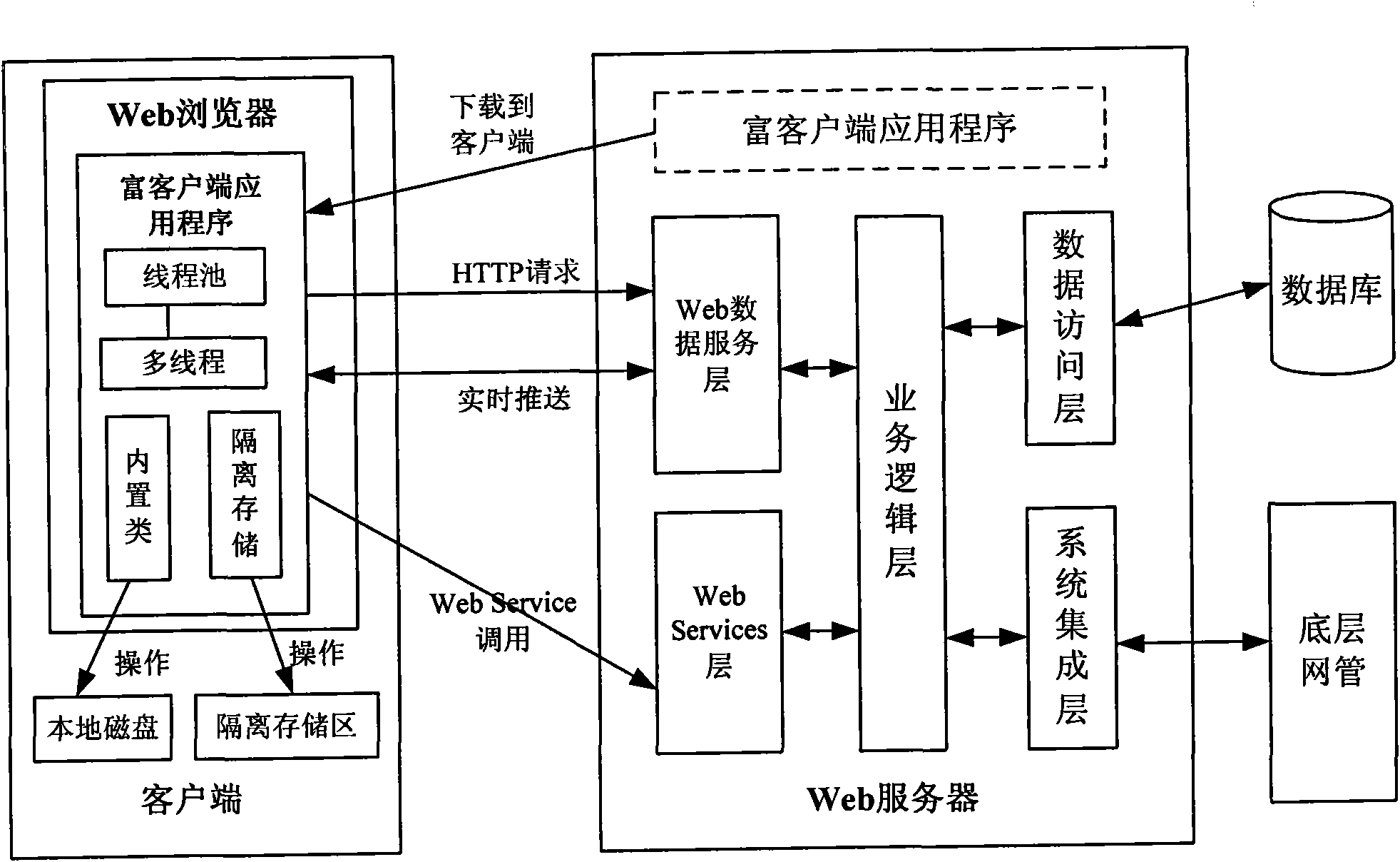
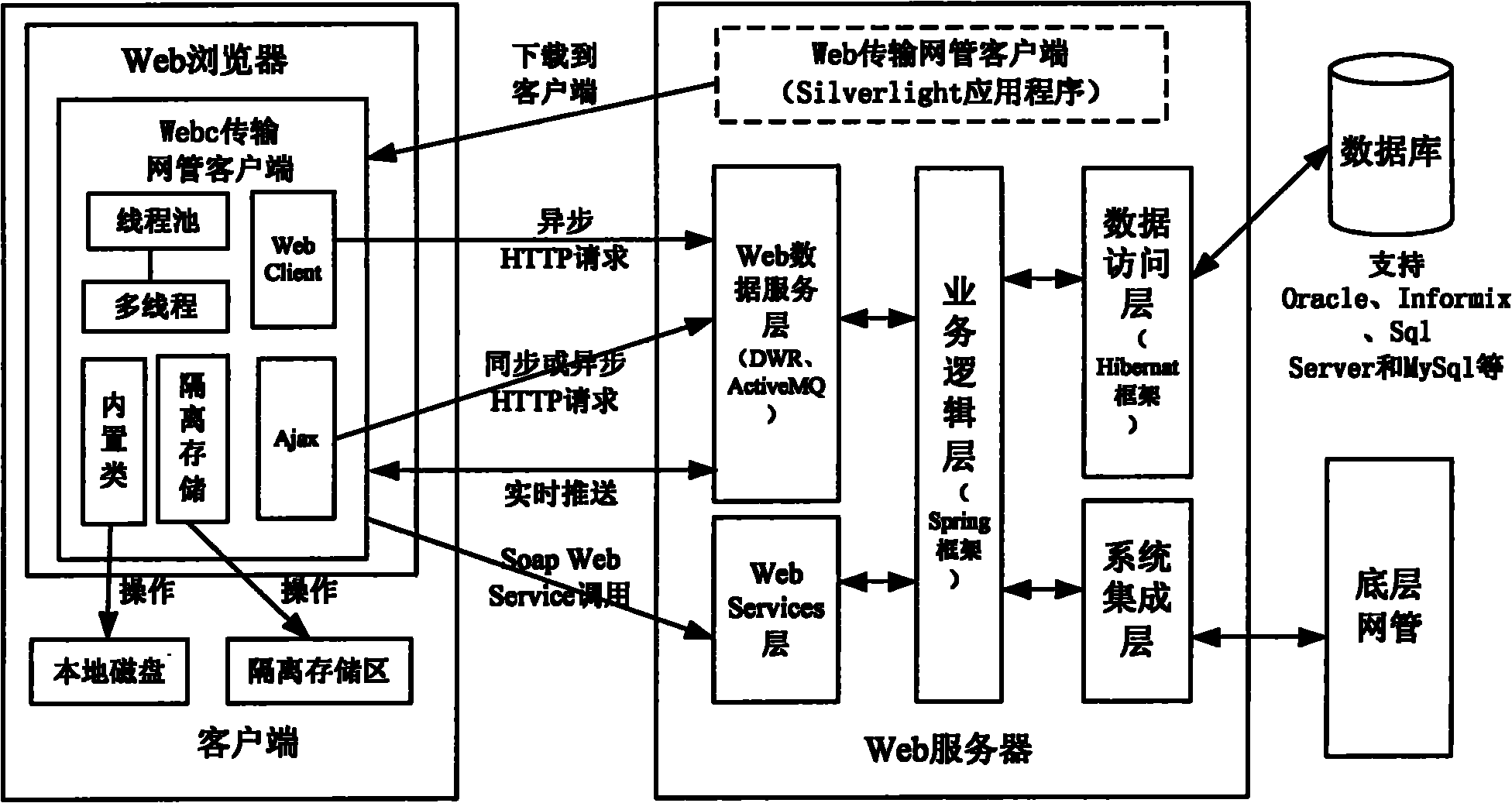
RIA-based high-performance Web transmission network management system and implementation method thereof
ActiveCN101895431APowerful operationTake advantage ofData switching networksWeb data servicesWeb service
The invention relates to an RIA-based high-performance Web transmission network management system and an implementation method thereof. The Web transmission network management system comprises a Web browser arranged on a client; the Web browser downloads a rich client application program from a Web server to a local computer through an HTTP protocol, and runs the program off line or on line; the Web server comprises the rich client application program, a Web data service layer, a Web services layer, a business logic layer, a data access layer and a system integration layer. The system and the method are applied to a telecom transmission network management system by effectively using an RIA architecture and rich client technology, and run the network management client with strong operational function on the Web browser of a main flow. The Web transmission network client has various complicated graphical user interfaces, supports local refreshing interfaces, directly performs synchronous or asynchronous interaction with a server, receives data pushed by the server in real time and can fully use computation resources and storage resources of the local computer.
Owner:FENGHUO COMM SCI & TECH CO LTD
Web servers with queryable dynamic caches
InactiveUS7526481B1Digital data information retrievalData processing applicationsData setWeb application
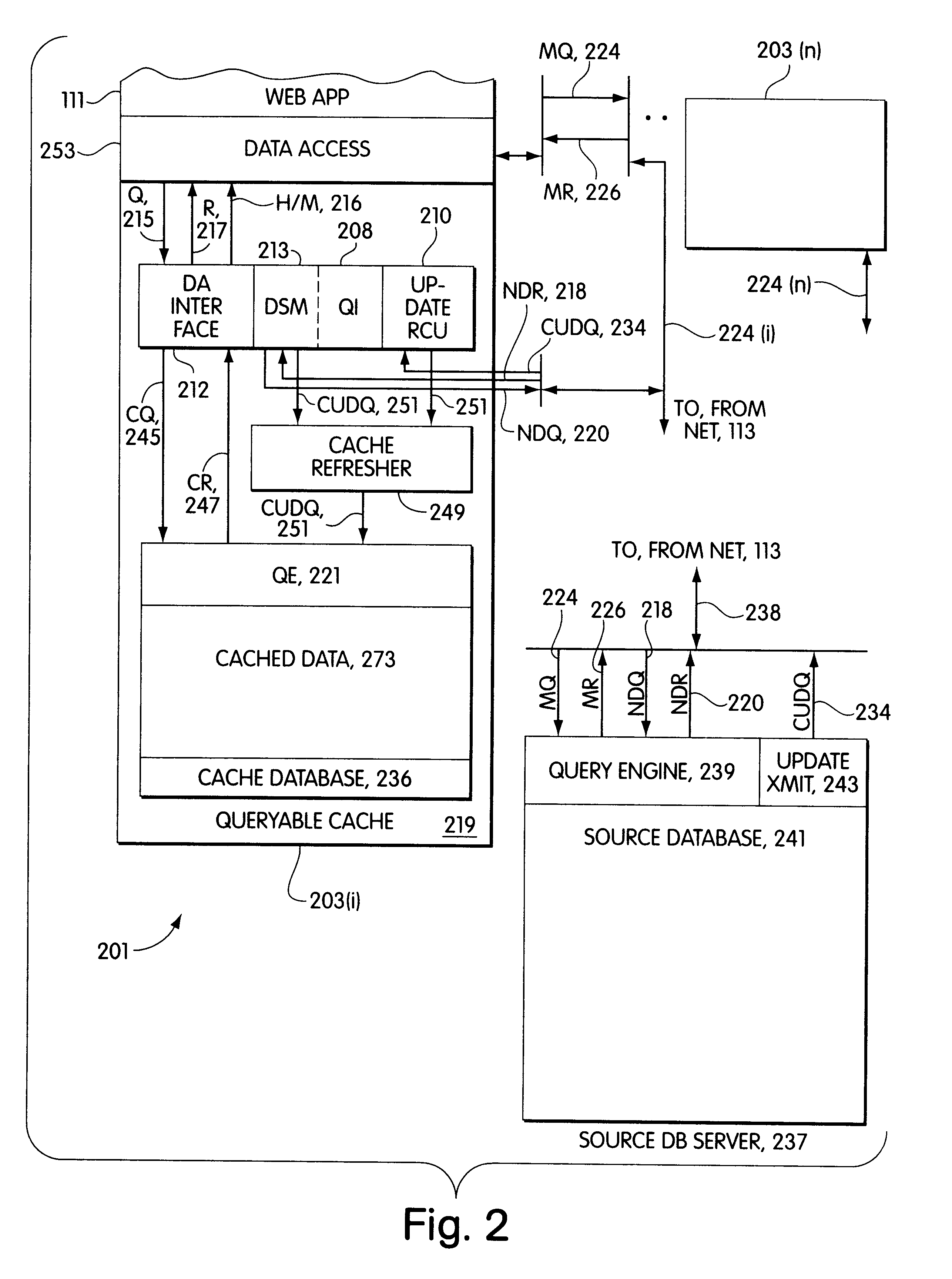
A middle-tier Web server with a queryable cache that contains items from one or more data sources. Items are included in the cache on the basis of the probability of future hits on the items. When the data source determines that an item that has been included in the cache has changed, it sends an update message to the server, which updates the item if it is still included in the cache. As disclosed, the data source is a database system and triggers in the database system are used to generate update messages. The data access layer determines whether a data item required by an application program is in the cache. If it is, the data access layer obtains the data item from the cache; otherwise, it obtains it from the data source. The Web application programs use global data set identifiers to identify data sets, while the cached data sets are identified by local data set identifiers. The cache receives a query context of global data set identifiers, determines whether the data sets of the query context are cached, and if they are, provides the local data set identifiers for the query context to the access layer, which then uses the local data set identifiers to query the cache.
Owner:ORACLE INT CORP
Method, device and system for data disaster tolerance
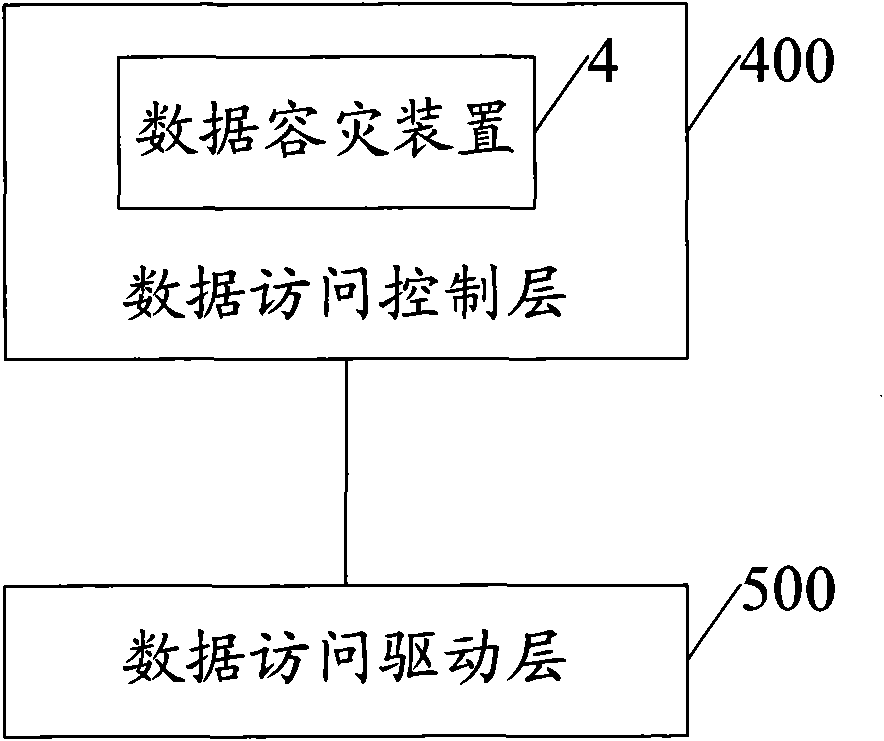
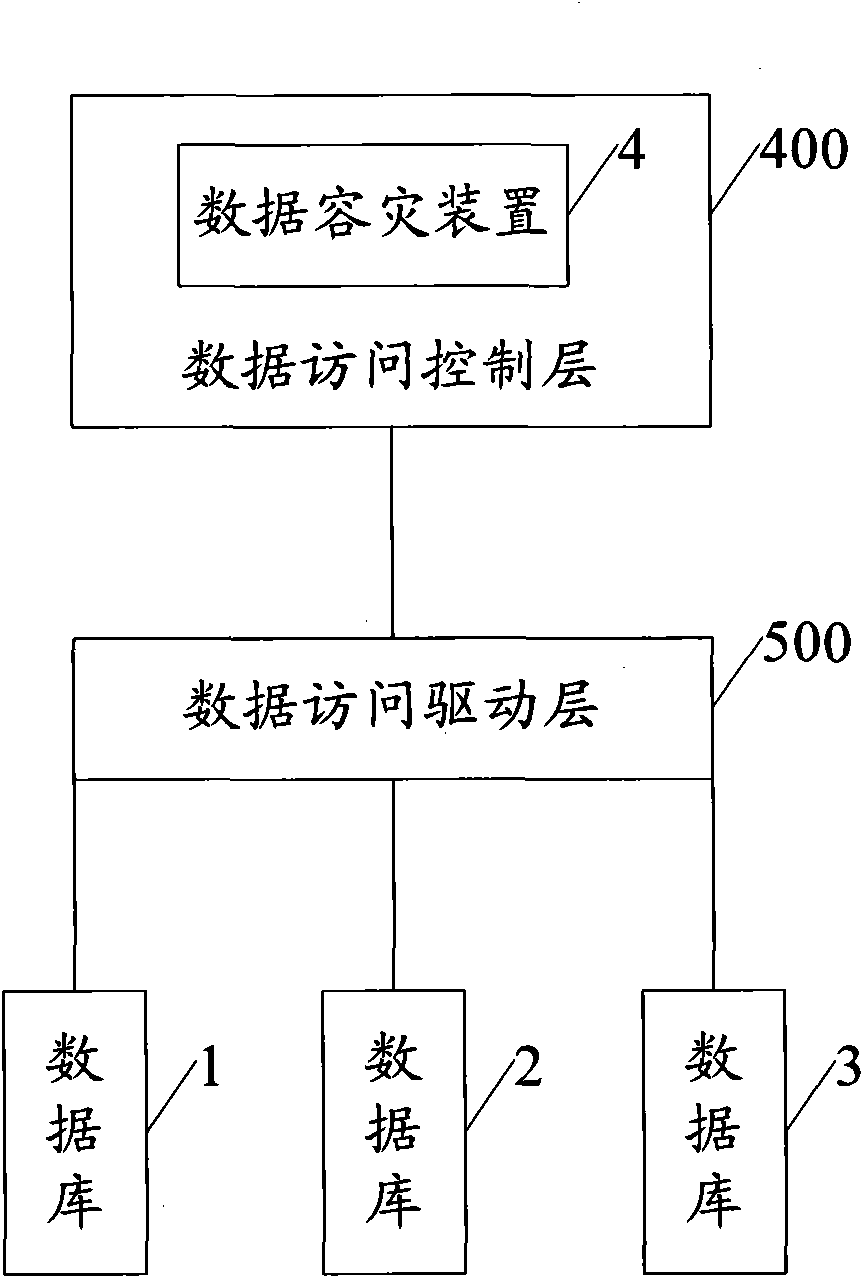
ActiveCN101667181AQuick switchSpecial data processing applicationsData access controlData access layer
The embodiment of the invention discloses a method, a device and a system for data disaster tolerance. The method comprises: configuring disaster tolerance in a plurality of databases in a data accesscontrol layer, wherein the configuration comprises a main database one or more spare databases of the main database, objects to be copied in the main database and access operation types of the objects to be copied in main database and the spare databases, and the data access control layer is between a data access driving layer and an application system; accessing the main database according to the disaster tolerance configuration; and when the access to the main database fails, switching to one of the spare database of the main database. The method, the device and the system can quickly switch to a spare database to continue accessing the database.
Owner:泰州市海通资产管理有限公司
An urban emergency commanding operation system and the corresponding implementation method
ActiveCN101216926AIncrease flexibilityQuickly build and deployData processing applicationsCommand systemGeneral purpose computer
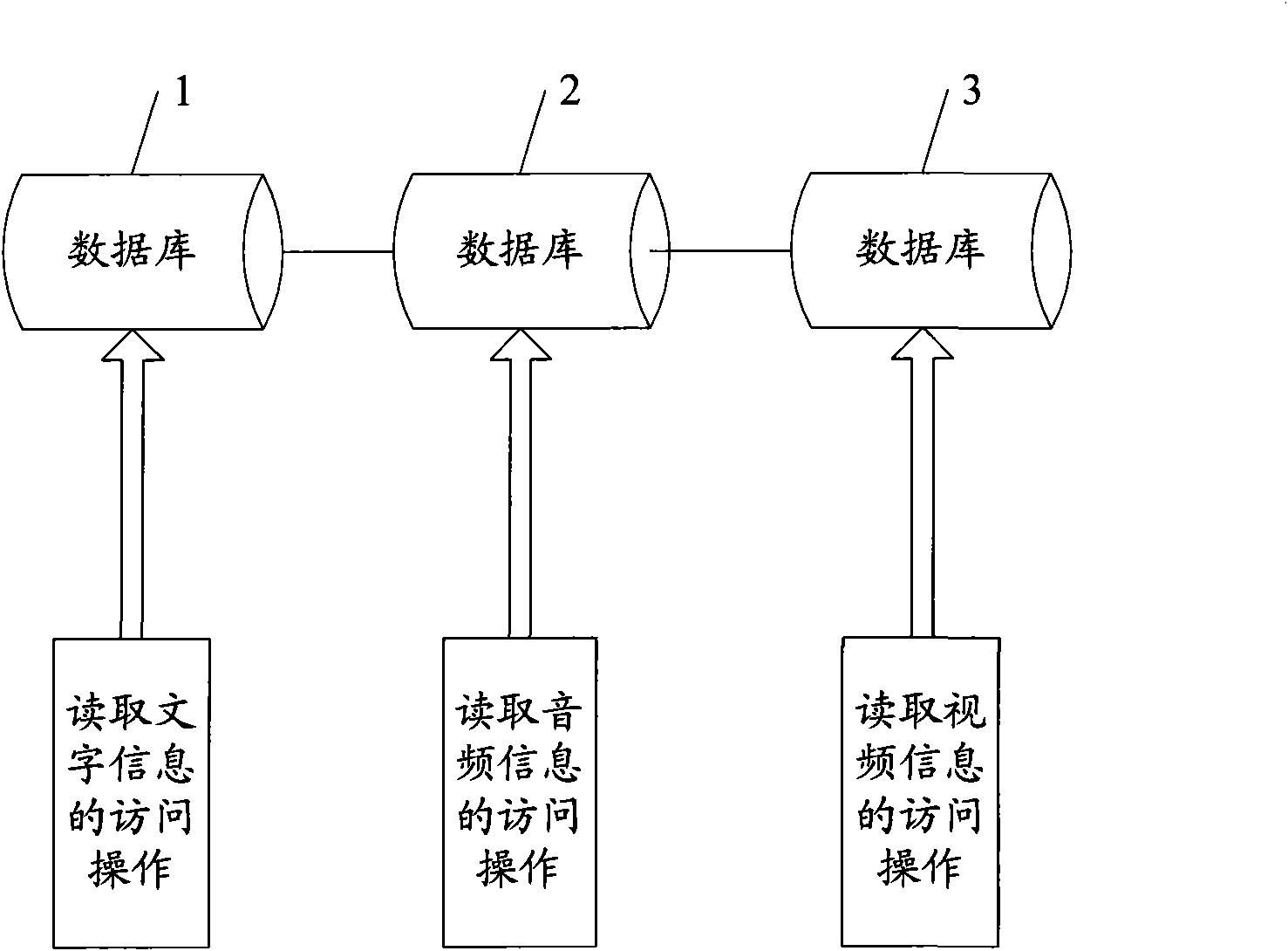
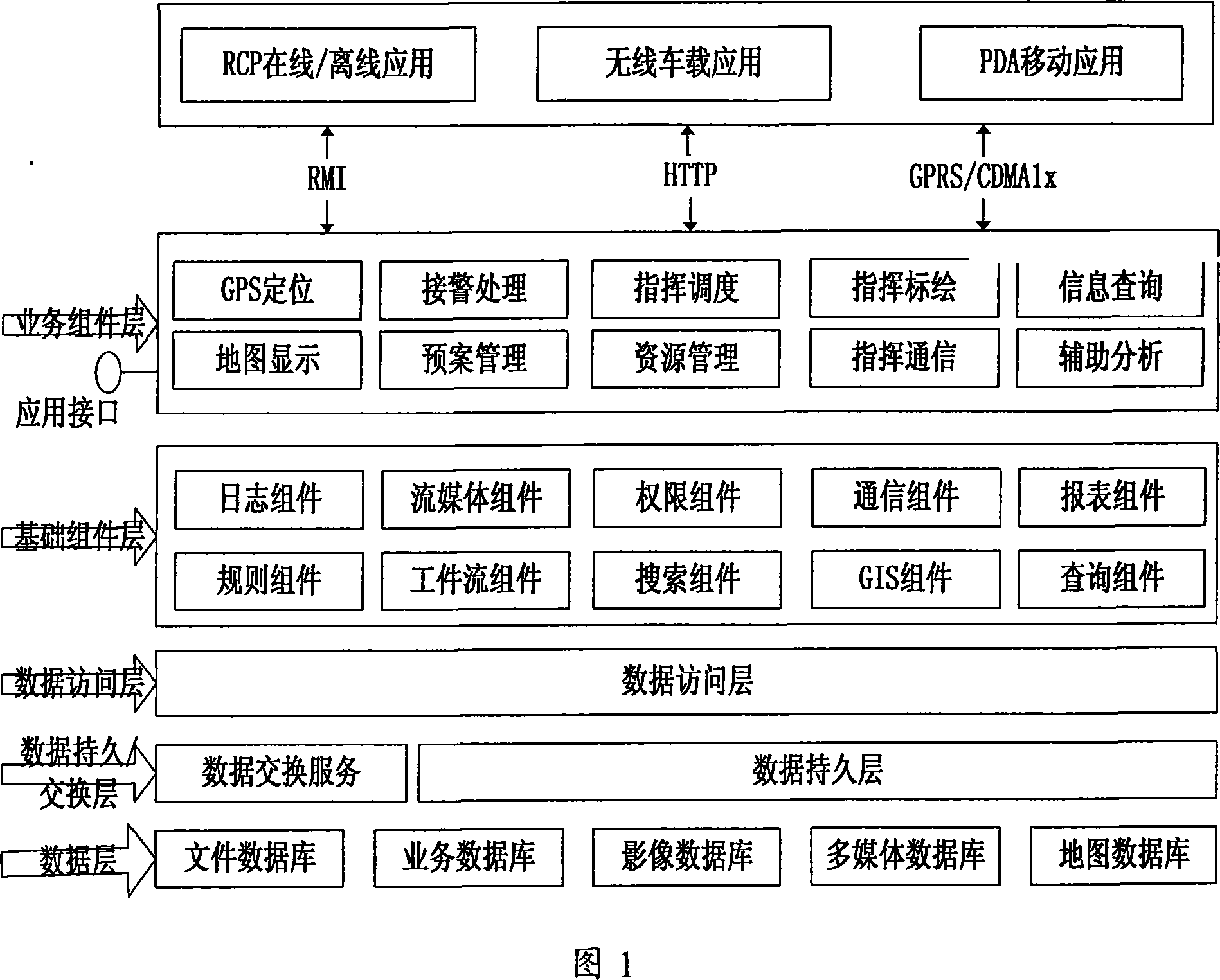
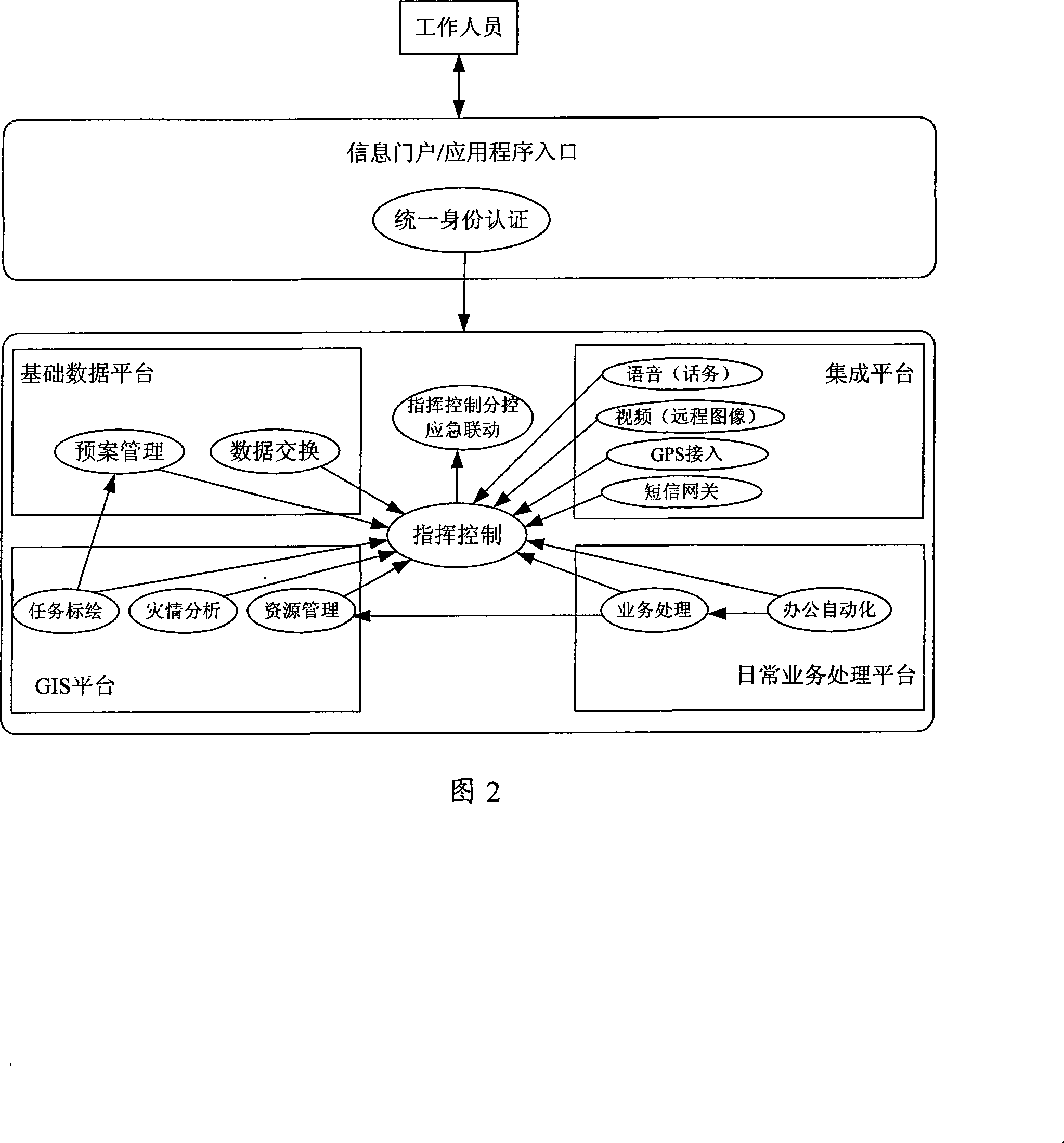
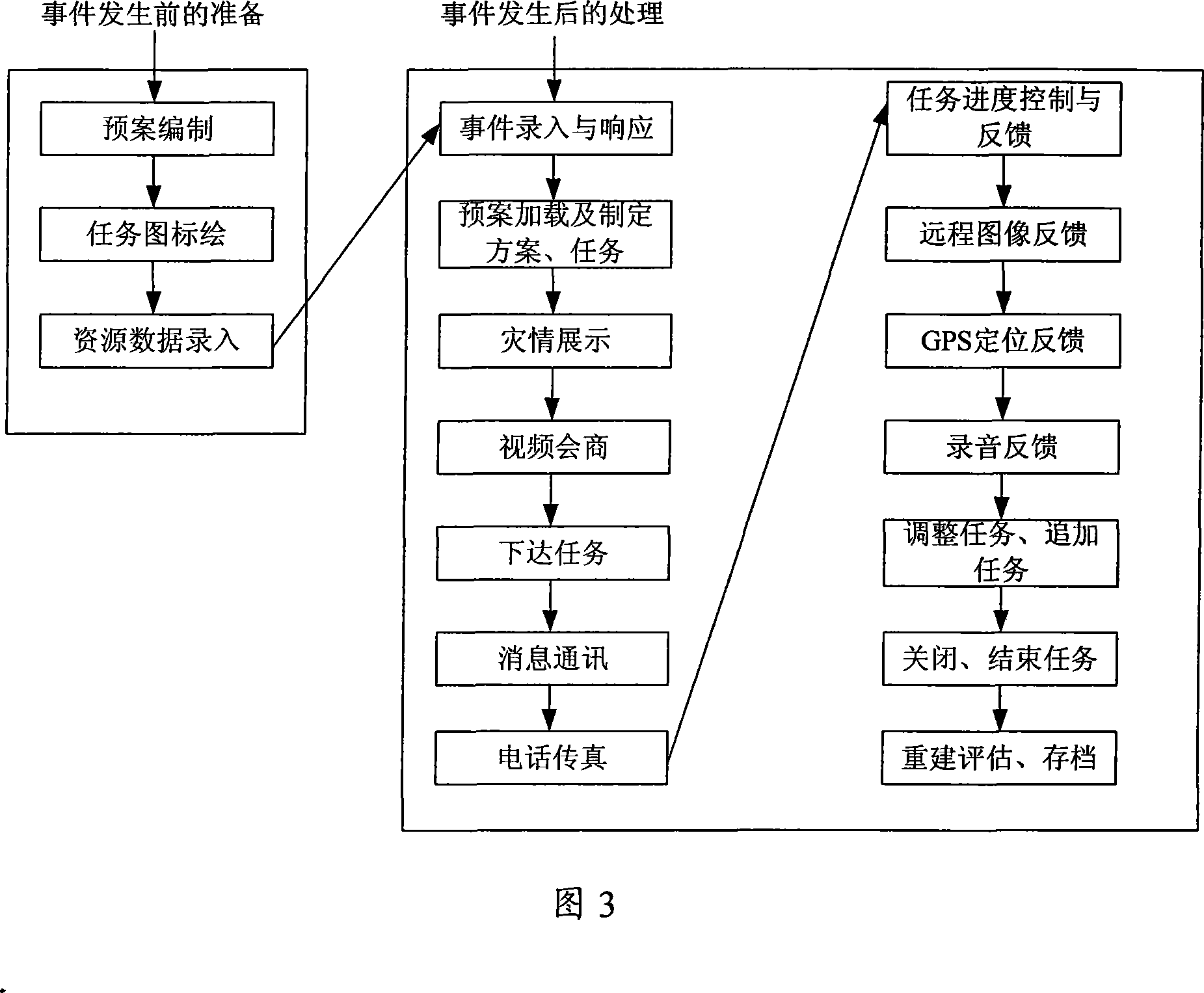
The invention discloses a city emergency command system and an implementation method thereof, comprising a data layer for storing the basic data of the emergency command, a data persistent switching layer for data switching service and data persistent service, a data access layer for accessing the data layer via the data persistent switching layer, a basic component layer for providing componentswith basic access function, a service component layer for providing service logic function and application interfaces, and an application layer connecting with a server via the corresponding communication agreement. Due to adopting the general purpose computer technology and the prior network communication technology, the inventive system and the implementation method build a command automated system into an advanced intelligent information data processing and automated command center which can quickly build and deploy a processing application system and set a emergency command system, widelyrealizing the multiplexing and flexibility of the system extension.
Owner:SHENZHEN HAILITE SCI & TECH DEV
Integrated high-performance application software architecture and construction method thereof
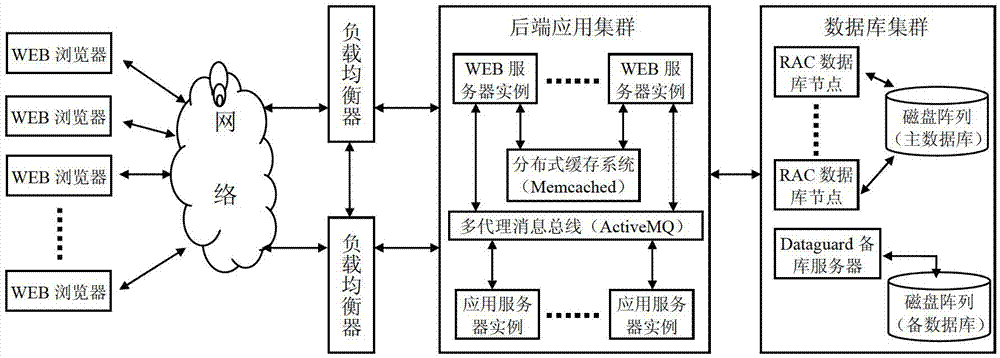
InactiveCN102968310AImprove performanceImprove development efficiencySpecific program execution arrangementsExtensibilityFault tolerance
The invention relates to the field of development of computer application software, in particular to an integrated high-performance application software architecture and a construction method thereof. The integrated high-performance application software architecture comprises a WEB layer cluster, a backend application cluster, a database cluster and a message-oriented middleware cluster, wherein the WEB layer cluster supports a J2EE cluster technology and is used for providing the capacity of a business presentation layer of a J2EE frame; the backend application cluster supports the J2EE cluster technology and is used for providing the processing capacity of a business logic layer of the J2EE frame; the database cluster supports the J2EE cluster technology and is used for providing the capacity of a data access layer of the J2EE frame; and the message-oriented middleware cluster supports the J2EE cluster technology and is used for providing the message communication capacity between distributed J2EE components. Based on the integrated high-performance application software architecture and the construction method thereof, a software architect and a developer can determine a software scheme and a deployment scheme within short time and provides high-performance application service; and a J2EE application system designed according to the software architecture can meet the requirements on high availability, extensibility and fault tolerance.
Owner:武汉烽火普天信息技术有限公司
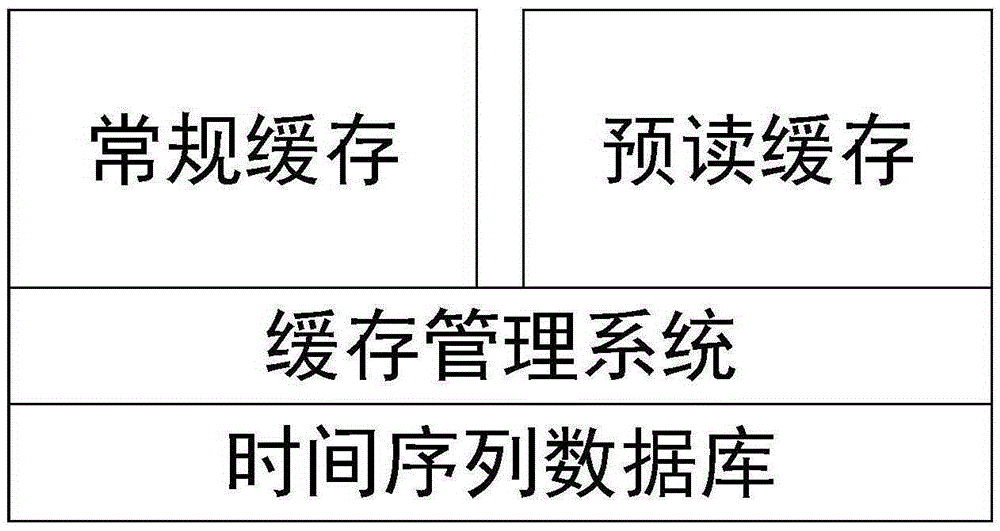
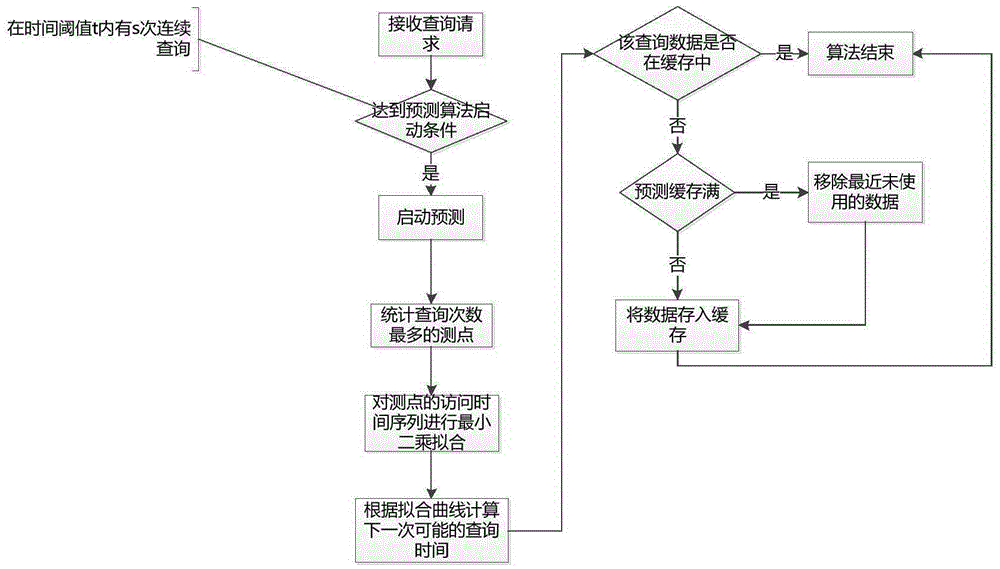
Access trend prediction based time series database cache management method
ActiveCN105426411AImprove Data Retrieval EfficiencyCalculation speedSpecial data processing applicationsData accessTrend prediction
The invention provides an access trend prediction based time series database cache management method. The method comprises: on the basis of providing a data access cache by a conventional database, establishing a time series database dual-cache mechanism; and in addition to a conventional cache, adding a prediction data cache for predicting pre-loading of access data to load the access data into a memory before data access so as to increase the query speed. The method is used for effectively managing the time series database data cache to improve the efficiency of data cache hitting and system data query. A system analyzes recent access data and predicts a data access trend, and the prediction data is loaded to increase the data access speed. The method is suitable for time series database data cache management and is used for improving the efficiency of time series database data query.
Owner:NR ELECTRIC CO LTD +1
Hybrid-mode smartphone application development framework
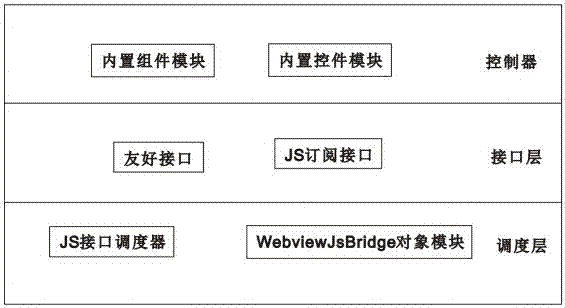
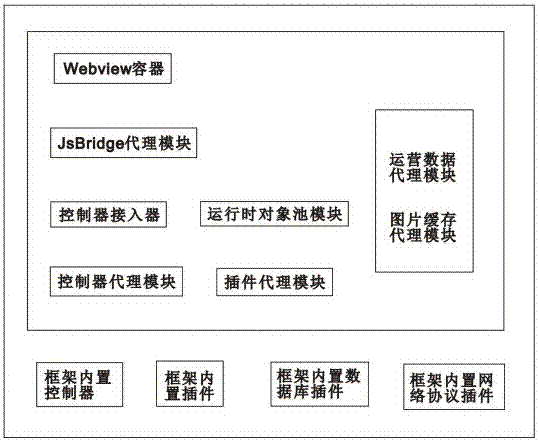
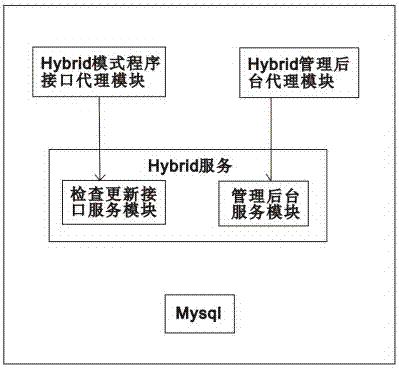
ActiveCN106951233AIncrease flexibilityAchieve decouplingSoftware engineeringSpecific program execution arrangementsControl layerApplication software
The invention discloses a hybrid-mode smartphone application development framework. The development framework comprises a JS SDK framework, a client framework and a server framework; the JS SDK framework comprises a control layer, an interface layer and a scheduling layer; the control layer comprises a built-in component module and a built-in control module; the interface layer comprises a friendly interface and a JS subscription interface; the scheduling layer comprises a JS interface scheduler and a WebviewJsBridge object module; the client framework is used for providing an operating environment for a web page of a Hybrid APP in an offline package page mode; the server framework comprises a server control layer, a service layer and a data access layer; the server control layer is used for connection and interaction between operation on the page and a bottom layer; the service layer is connected into a kernel in a plug-in form to provide support for the server control layer; and the data access layer is connected into the kernel in a plug-in form to provide a network request and sqlite data operation. The development framework provides a whole set of solution for rapid iterative development, online deployment and building block type integration of application programs according to functional requirements.
Owner:GUANGZHOU TIANGAO SOFTWARE TECH CO LTD
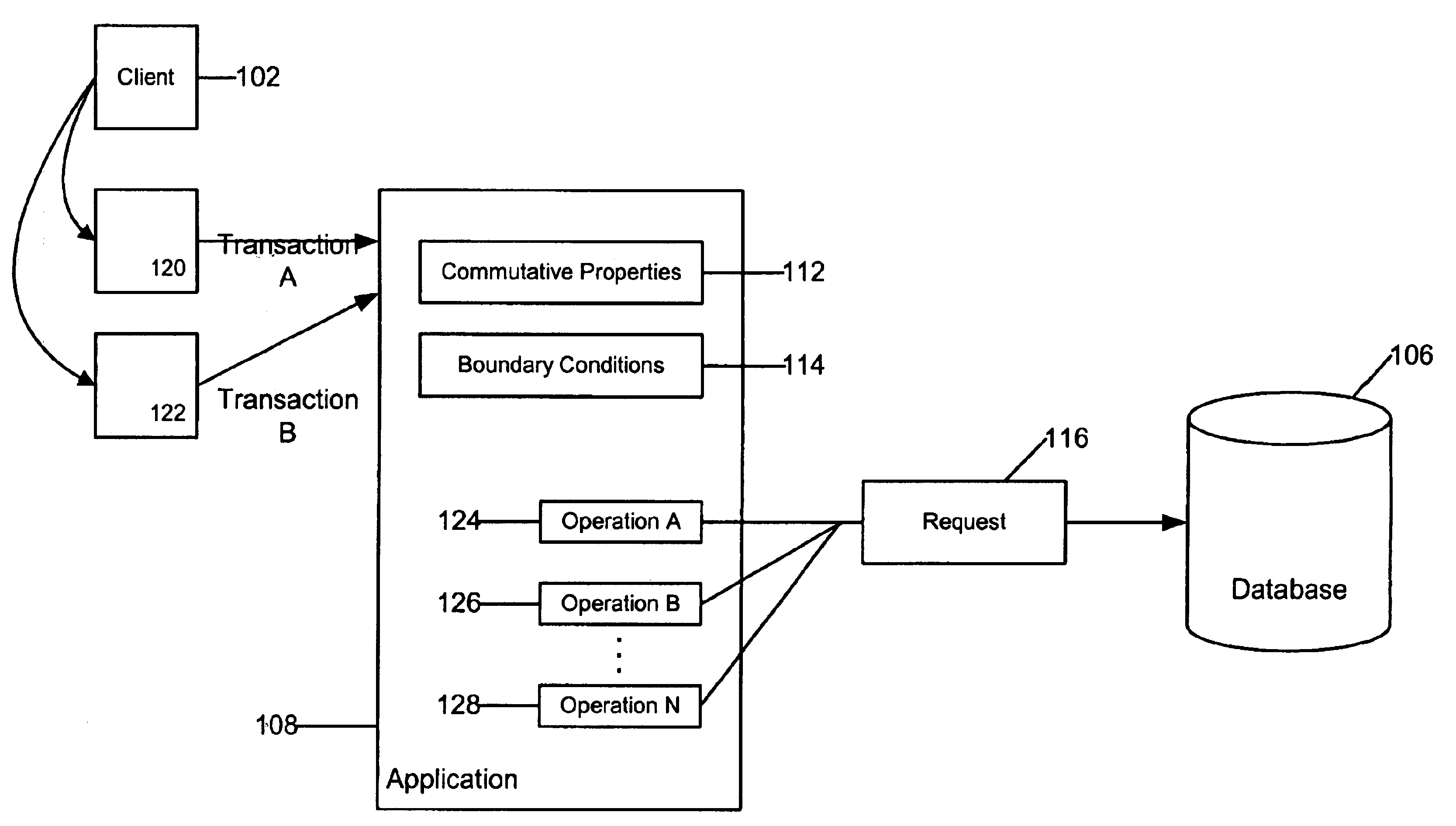
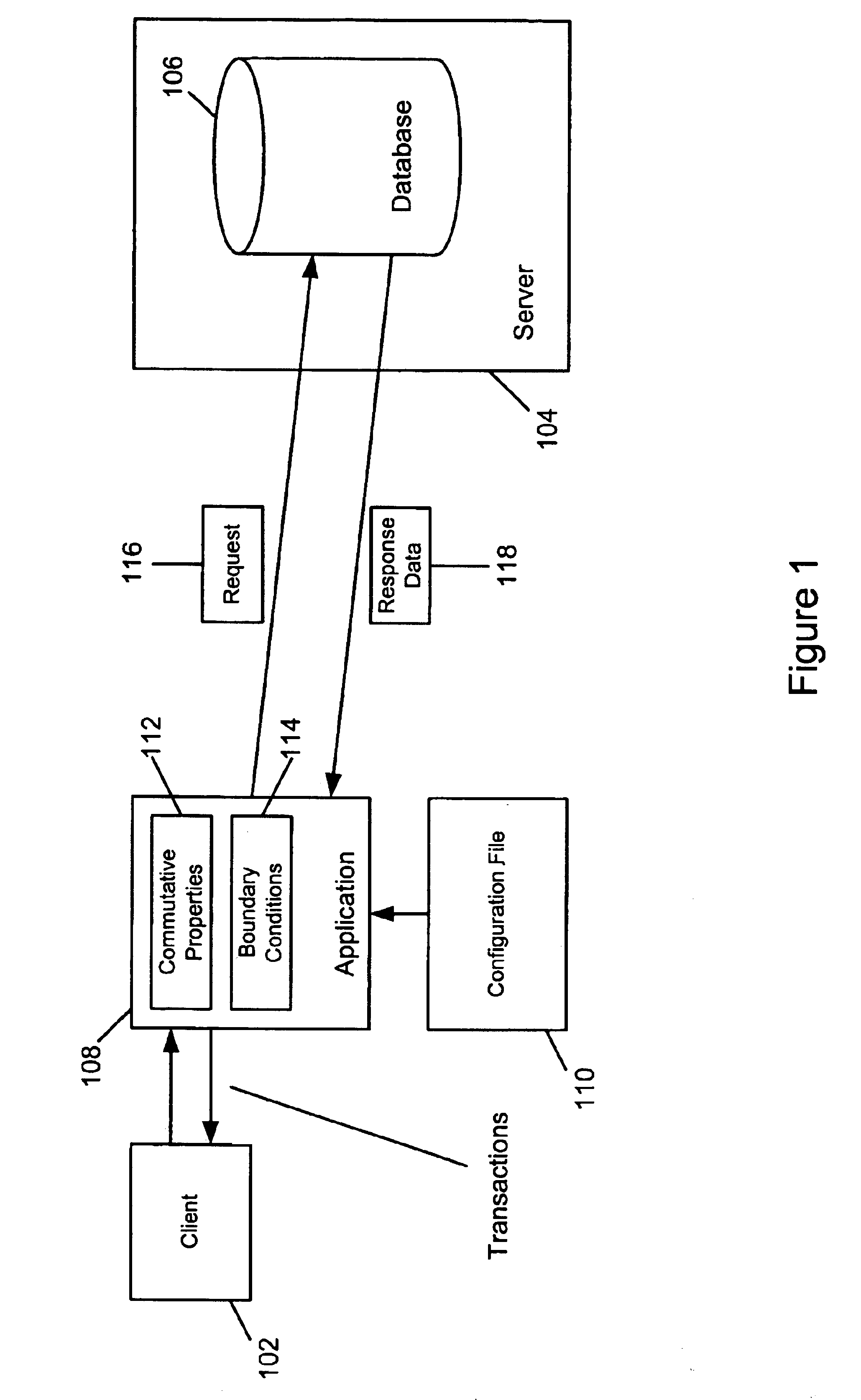
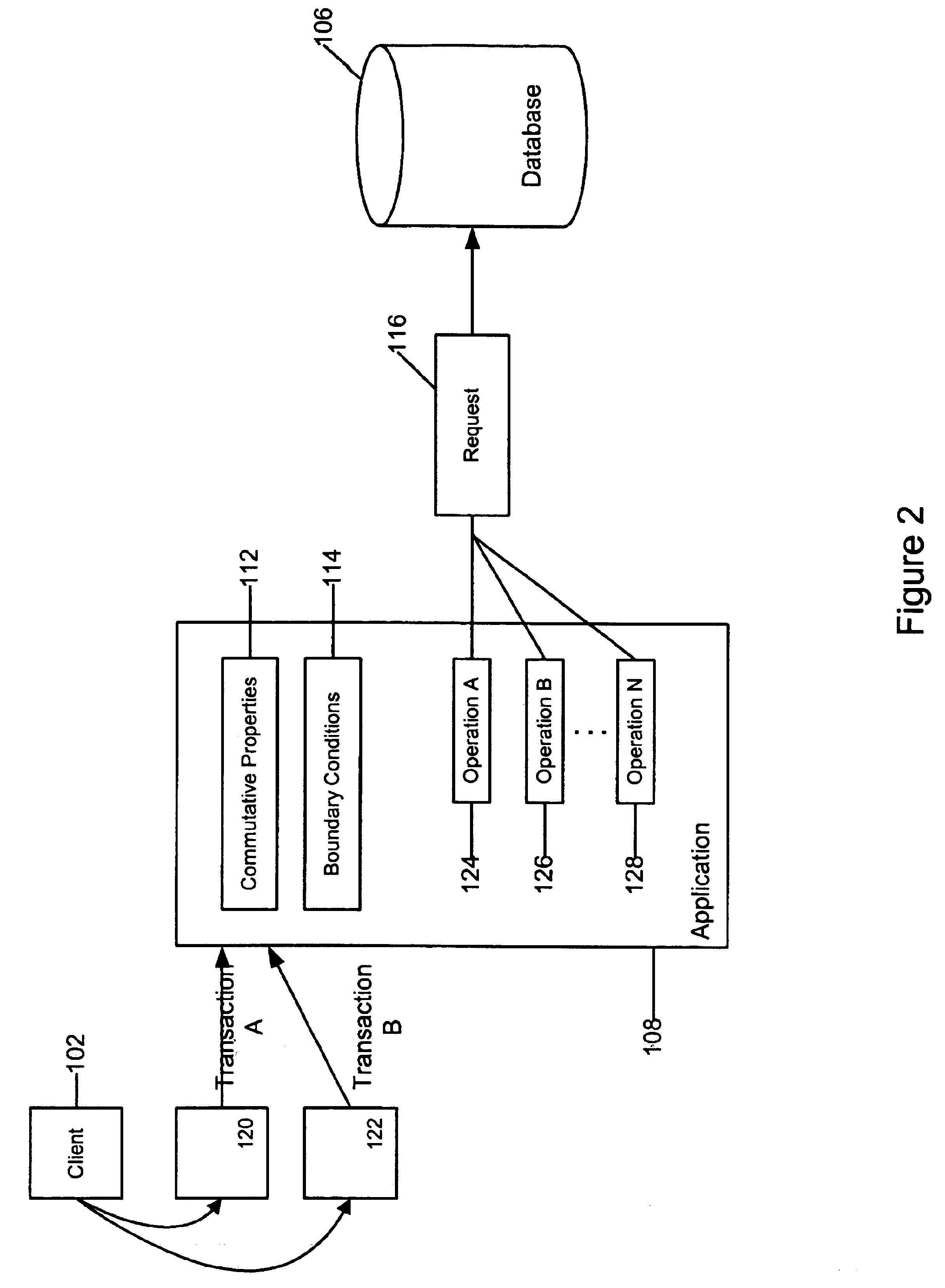
System and method for performing commutative operations in data access systems
InactiveUS6898587B2Easy to useEasy to customizeData processing applicationsDigital data processing detailsData accessSoftware development
An embodiment of the invention allows a software developer or administrator to use their knowledge and / or development of a particular application, to optimize the performance of data access and updates to the database. In order to do this, an embodiment of the invention makes use of the developers knowledge of particular transaction and transaction operations that can be performed in a commutative manner. The overall effect is to perform the operations in a parallel fashion so that one operation does not block or restrict the processing of a second operation. The result is an increase in database access or performance, without any resulting decrease in database reliability.
Owner:ORACLE INT CORP
Marketing analysis data market system
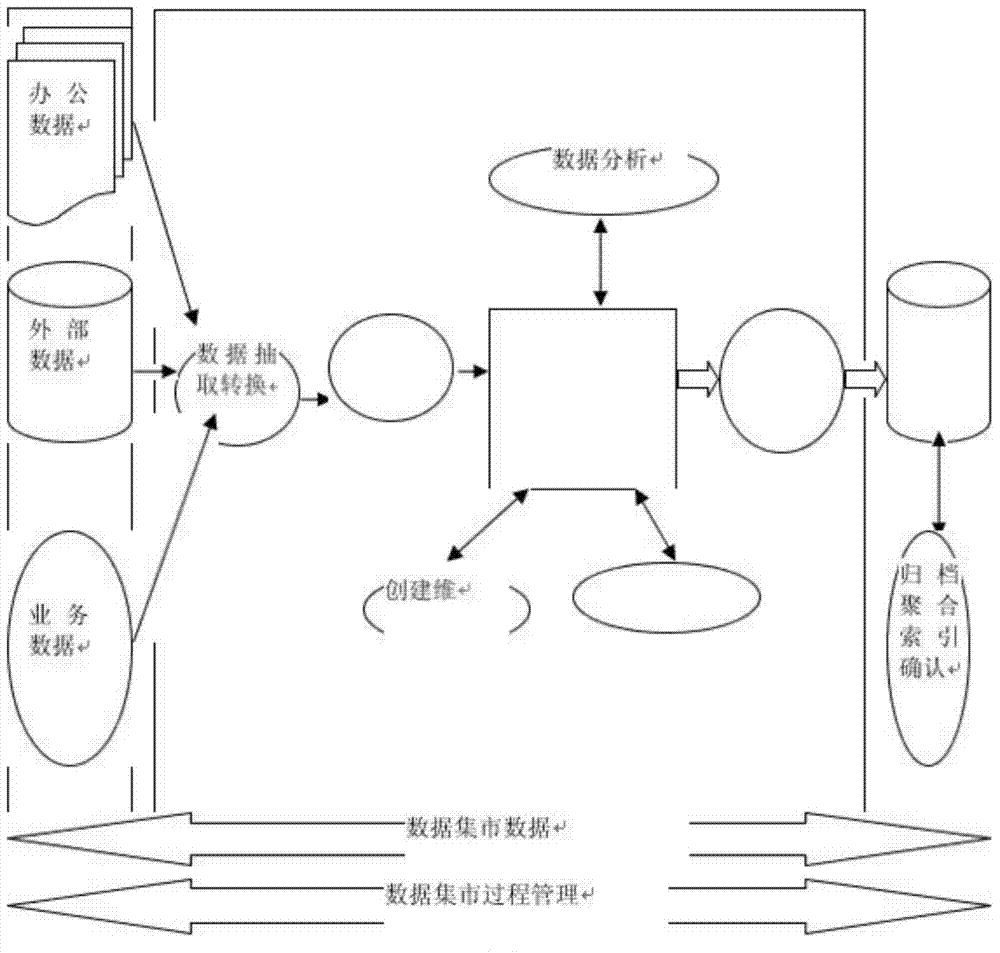
The invention provides a marketing analysis data market system. The marketing analysis data market system comprises a data access layer, a data extraction module, a data conversion module, a data cleaning module, a log and alarm sending module and a data downloading module, a data packet of the data access layer contains office data, external data and service data, and models of the system includes a data logic model and a data physics module. Firstly, necessity in designing the marketing data market is analyzed and ETL data processing including noise data processing, data uniformity and data quality and the like is analyzed by discussing a data integration method, and various data sources can be reorganized and processed by a data transition tool. In addition, the physics model in the data market is realized according to the physic list structure of the logic model. Finally, application prospect of the data market in the marketing analysis is expected.
Owner:DONGYANG AIWEIDE ADVERTISING MEDIA
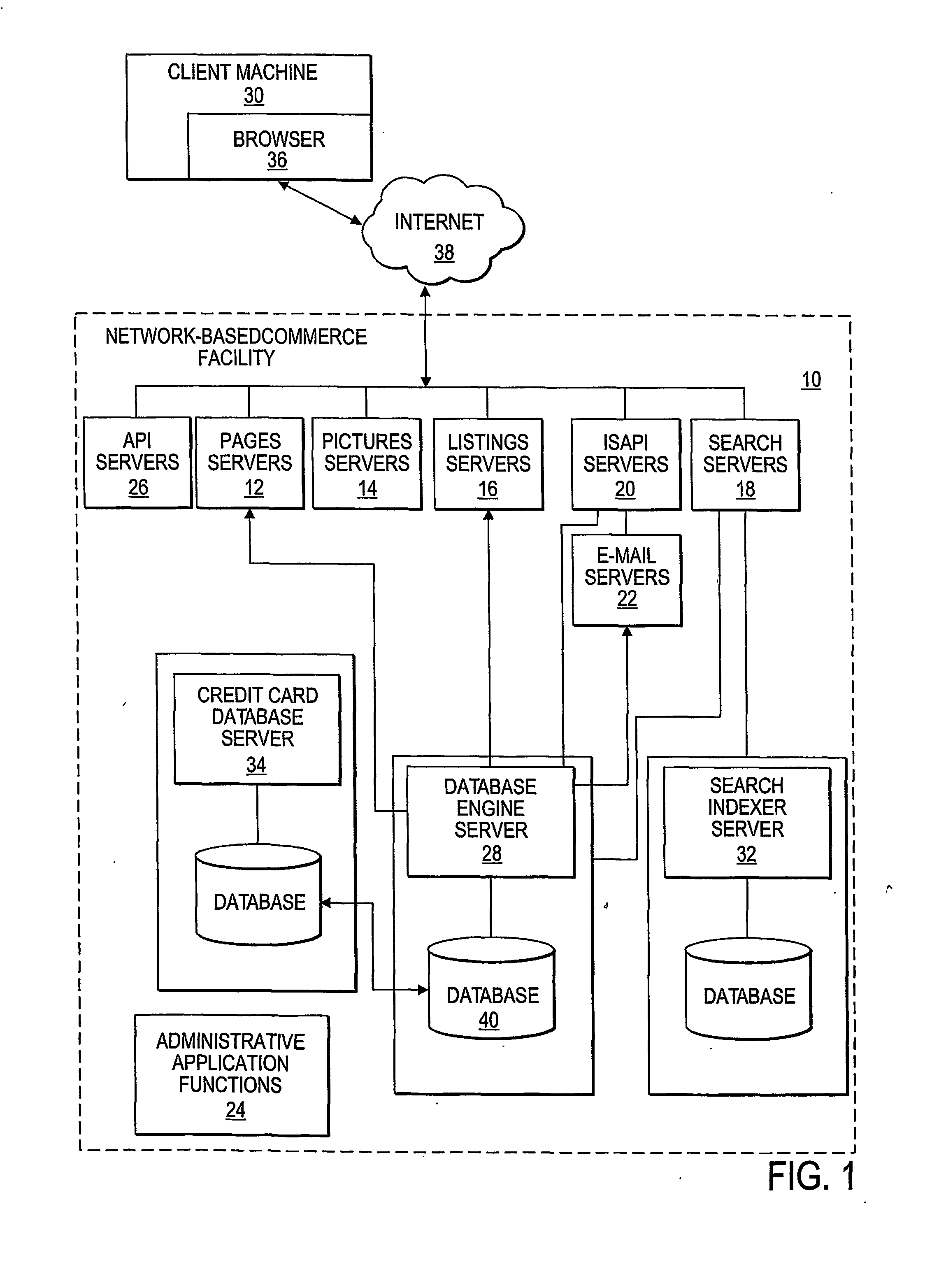
Method and system for managing data transaction requests
InactiveUS20060294038A1Digital data information retrievalData processing applicationsAbstraction layerData content
A method and system is provided to process data transactions in a data store including a plurality of databases. The system may comprise a computer interface module to receive a data transaction request from at least one requesting computer and a data store interface module to interface the system to the plurality of databases. The system also includes a data access layer defining an abstraction layer to identify at least one database of the plurality of databases. The data transaction request may be an object orientated request and the plurality of databases may be horizontally distributed wherein the data access layer defines an object orientated abstraction layer between the computer interface module and the plurality of databases. In one embodiment a data dependent routing module is provided that generates a query to a database that is identified based on content of the data in the data transaction request.
Owner:PAYPAL INC
System and method to optimize database access by synchronizing state based on data access patterns
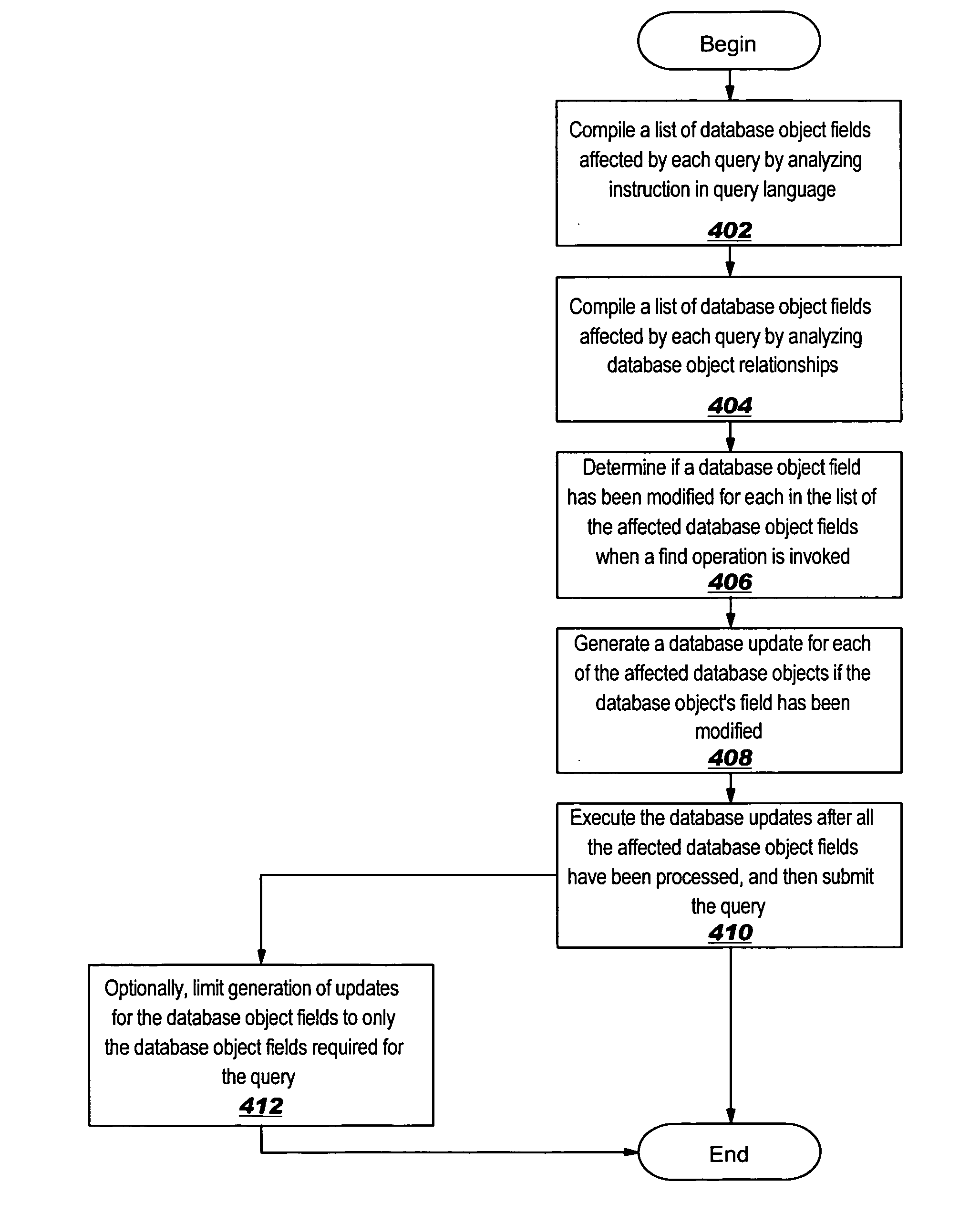
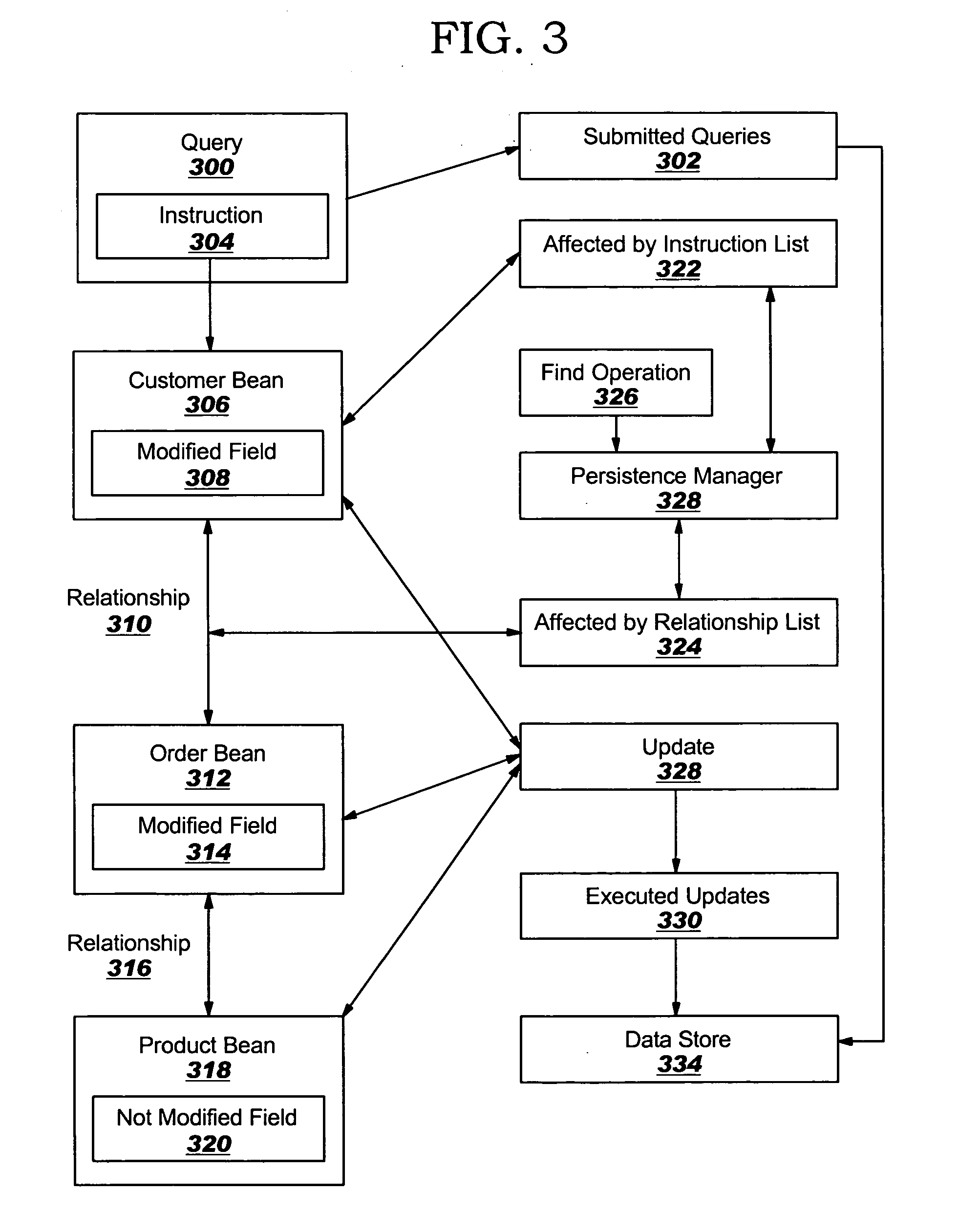
InactiveUS20060230019A1Avoiding excessive round tripDatabase updatingDatabase queryingData processing systemAnalysis data
A method, apparatus, and computer program product in a data processing system for avoiding excessive database round trips. A list of a database object fields affected by queries is compiled by analyzing instructions in a database query language. A list of database object fields affected by queries is also compiled by analyzing database object relationships. Using the combined list of affected database object fields, when a find operation is invoked, a determination is made as to whether the affected database object fields have been modified. Next, if the affected database object fields have been modified, database updates are generated for the affected database objects containing the affected database object fields. After that, the database updates are executed after all affected database object fields have been processed. Finally, the queries are submitted.
Owner:IBM CORP
Hadoop-based k-means clustering analysis system and method of network security log
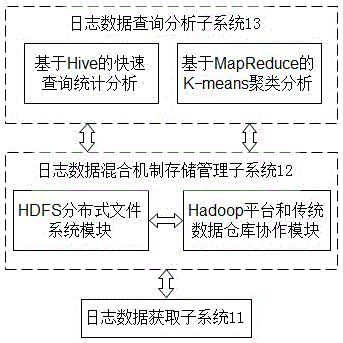
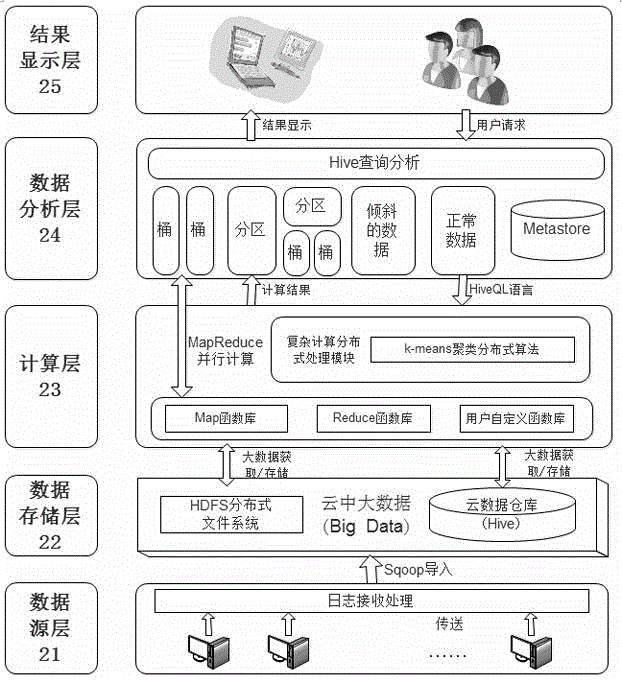
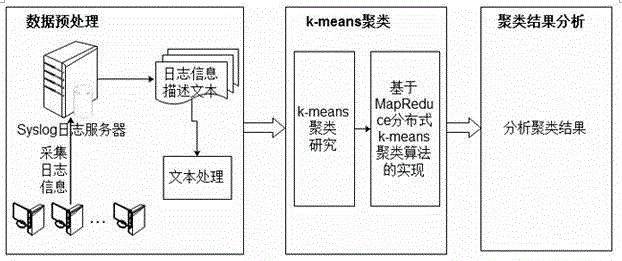
InactiveCN105138661AAccurate expressionCompensationDatabase management systemsSpecial data processing applicationsData warehouseQuery analysis
The invention provides a hadoop-based k-means clustering analysis system and method of a network security log. The hadoop-based k-means clustering analysis system comprises a log data acquisition subsystem, a log data mixing mechanism storage management subsystem and a log data analysis subsystem. The method includes the steps that in a data storage layer, a mixing storage mechanism with Hadoop cooperating with a traditional data warehouse is adopted to store log data, a Hive operation interface is provided in a data access layer, the data storage layer and a computing layer receive instructions from a Hive engine, and efficient query analysis on the data is achieved by being matched with MapReduce through HDFS; when mining analysis is conducted on log data, MapReduce is adopted to conduct clustering mining analysis on the network security log through a k-means algorithm; the framework with the Hadoop cooperating with the traditional data warehouse is adopted, the detects of the traditional data warehouse on the aspects of mass data processing, storage and the like, and meanwhile an original traditional data warehouse is fully used; clustering analysis is conducted through the MapReduce-based k-means algorithm, and safety grade evaluation and early warning can be conducted on log data timely.
Owner:NORTHWEST UNIV(CN)
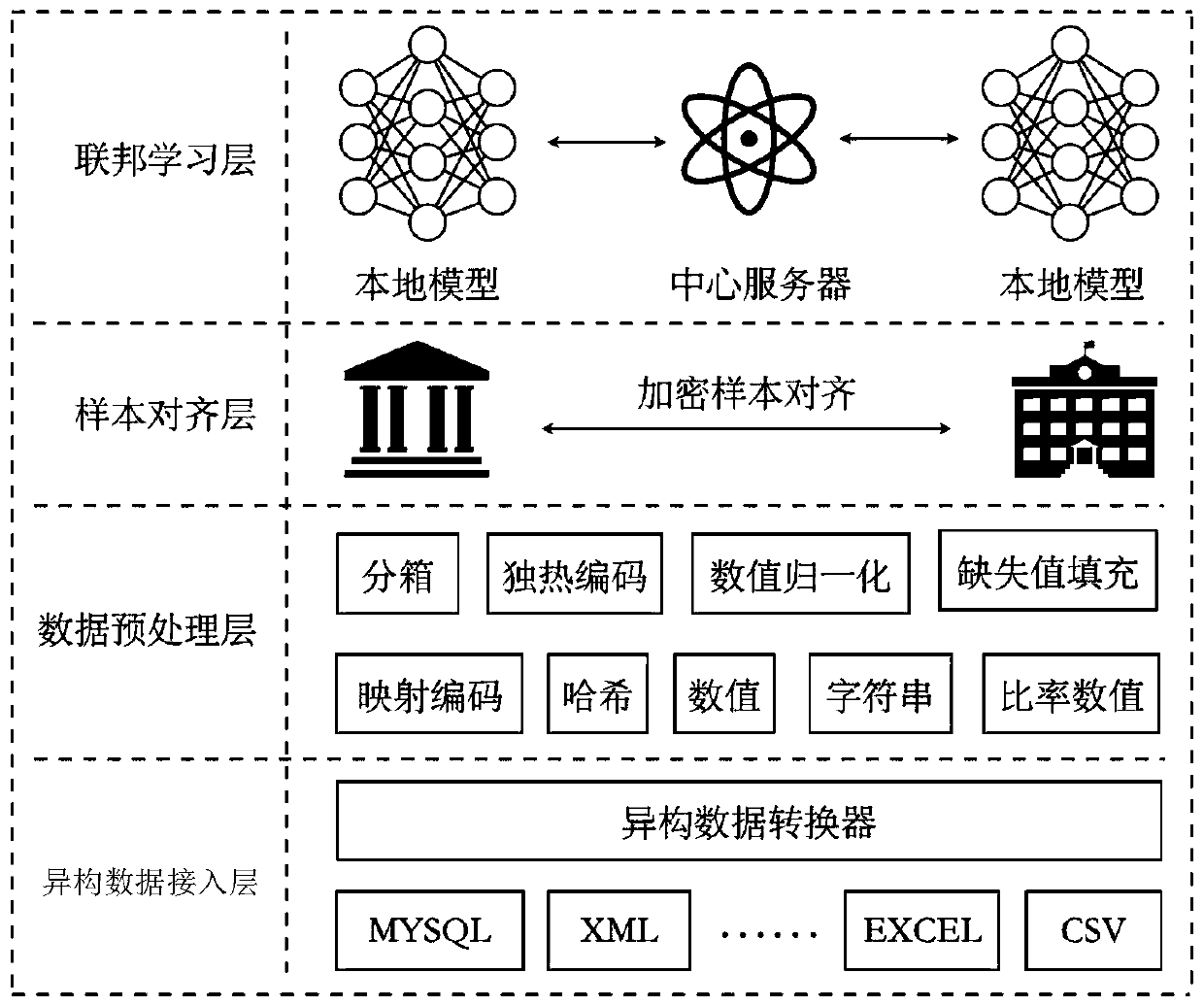
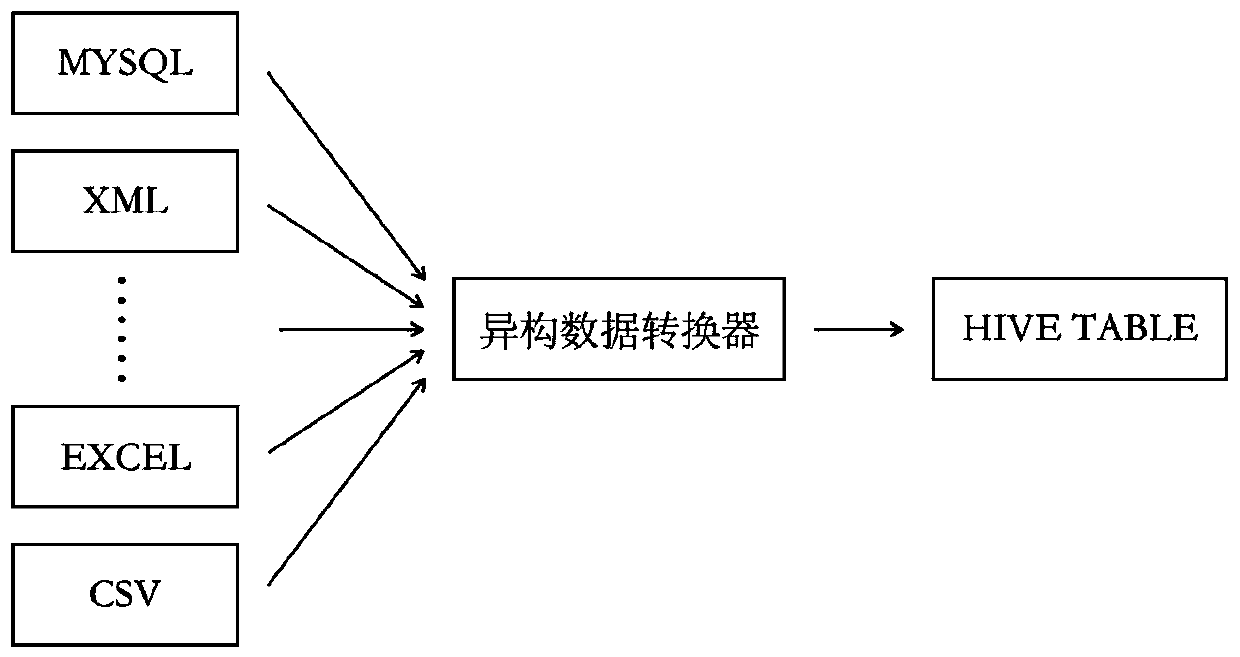
Credit risk control system and method based on federation mode
The invention relates to a big data technology, and aims to provide a credit risk control system and method based on a federation mode. The system comprises a heterogeneous data access layer used foraccessing and converting data, a data preprocessing layer used for preprocessing original data, and a sample alignment layer used for keeping training samples of different data providers aligned, anda federated learning layer used for training a local model by utilizing the participant local data and forming a global model after gradient aggregation. The invention provides a unified data access format, data preprocessing and a risk prediction model based on federated learning, and solves the challenge problem brought by data heterogeneity and privacy leakage to risk control. A central serverdoes not need to participate in the model training and learning process, and it can be guaranteed that user privacy is not eavesdropped. Risk control modeling can be carried out by combining a plurality of different participants, the modeling process is standardized, the risk control capability is finally improved, and the cost is reduced for enterprises.
Owner:ZHEJIANG UNIV
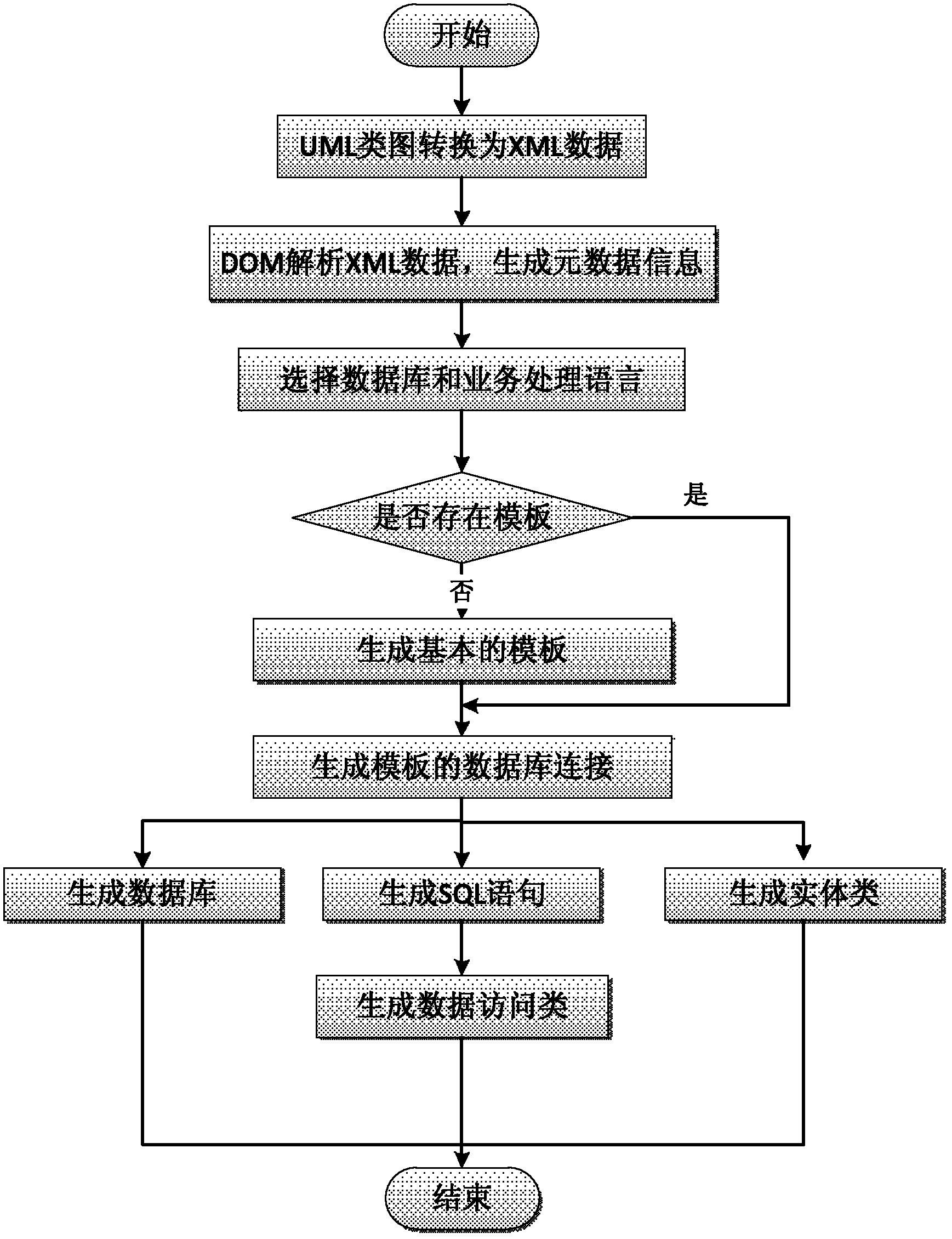
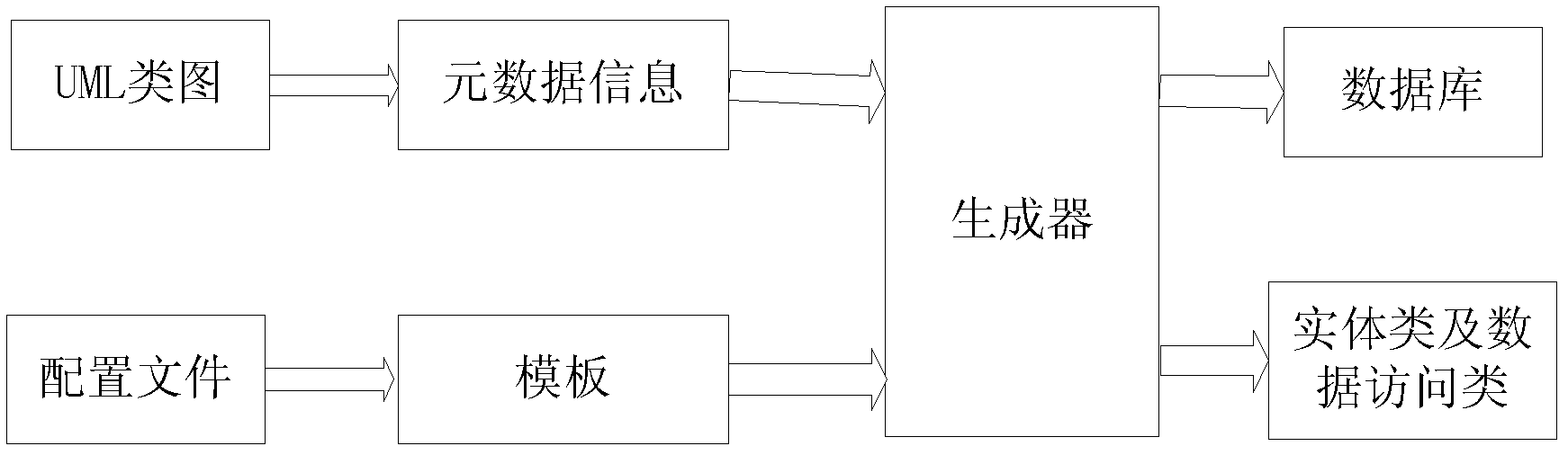
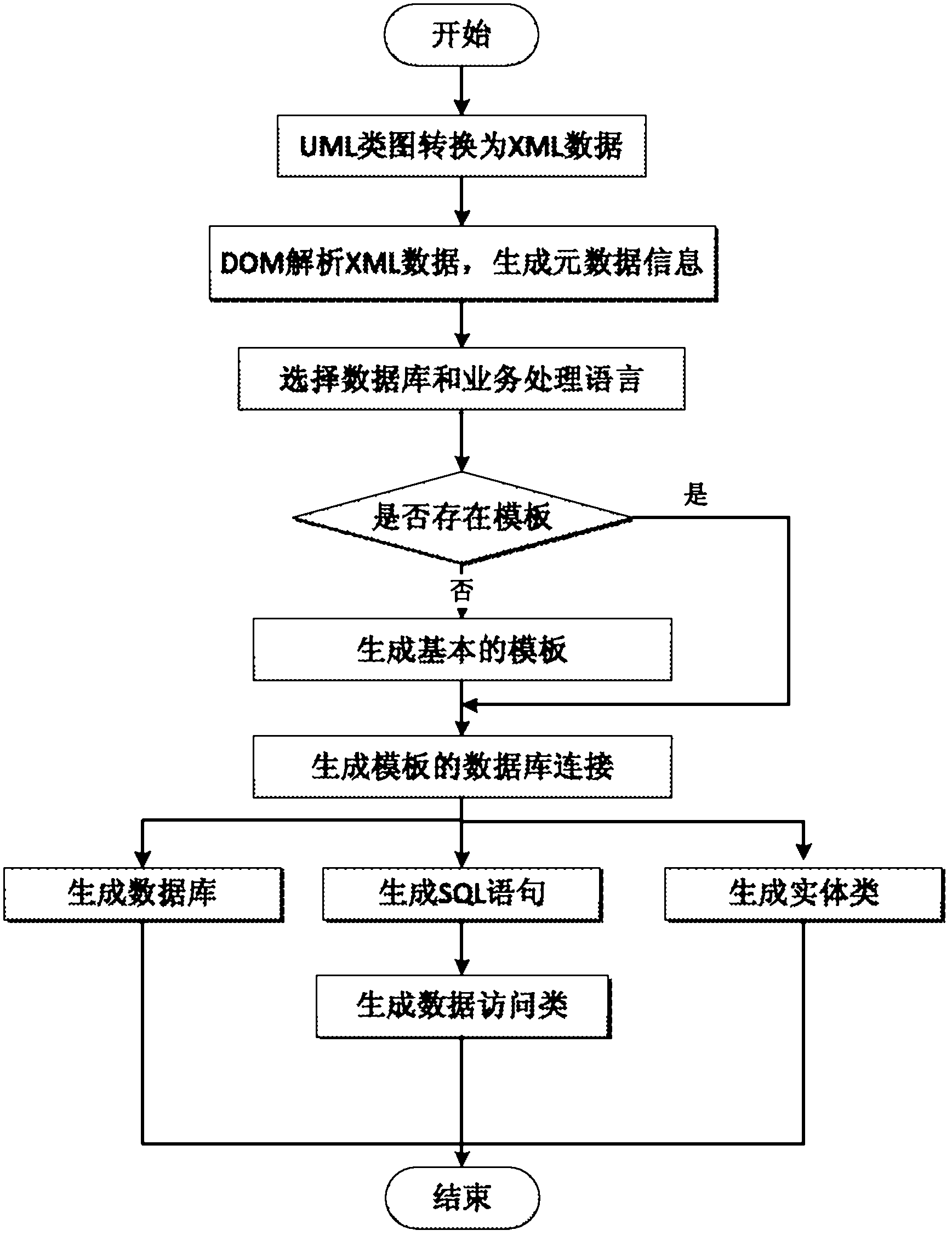
Configurable method for automatically generating database and accessing data
ActiveCN102663103AAchieve conversionImprove acceleration performanceSpecial data processing applicationsExtensibilityMaintainability
The invention discloses a configurable method for automatically generating a database and accessing data. The configurable method includes converting a UML (unified modeling language) class image designed in a business requirement analysis stage into an XML (extensible markup language) file; generating metadata information by means of analyzing and reading the XML file; selecting a used database and used business processing language by means of selecting a configuration file by a user; generating a database template, an entity class template and a data access class template; and generating a database, an entity class and a data access class of a system by the aid of a generator of the system according to the metadata information and the generated templates. The metadata information includes basic attributes including the accessibility, the name and the type of an object. By the aid of the configurable method, the UML class image is converted to the database, the entity class, the data access class and the like, accordingly, the database and a data access layer can adapt to change of the object and change of the attributes of the object, when the type of the database and the business processing language are changed, only the design of the UML class image needs to be modified to regenerate a database and a data access layer, and extensibility and maintainability of the system are improved.
Owner:BEIJING YUCHEN SHIMEI SCI & TECH
Digital dictation workflow system and method
InactiveUS20080086305A1Metadata audio data retrievalElectronic editing digitised analogue information signalsNetwork connectionClient-side
A digital dictation workflow system and method employing a plurality of client devices and at least one server. Certain client devices are operable to record audio information dictated by a user for storing as a digital audio file in a file store, and others are operable to receive and reproduce the stored digital audio file as audio. The server is connected to the client devices via a network, and manages storage and retrieval of the digital audio file to and from the file store and the client devices. The system and method further employ at least one database for storing dictation data pertaining to the digital audio file stored in the file store, and can be configured in a three-tier arrangement with the client devices being present in a presentation layer, the server present in a business logic layer, and the file store and database present in a data access layer.
Owner:BIGHAND
System uses an interface controller for managing operations of devices that each has a unique communication protocol
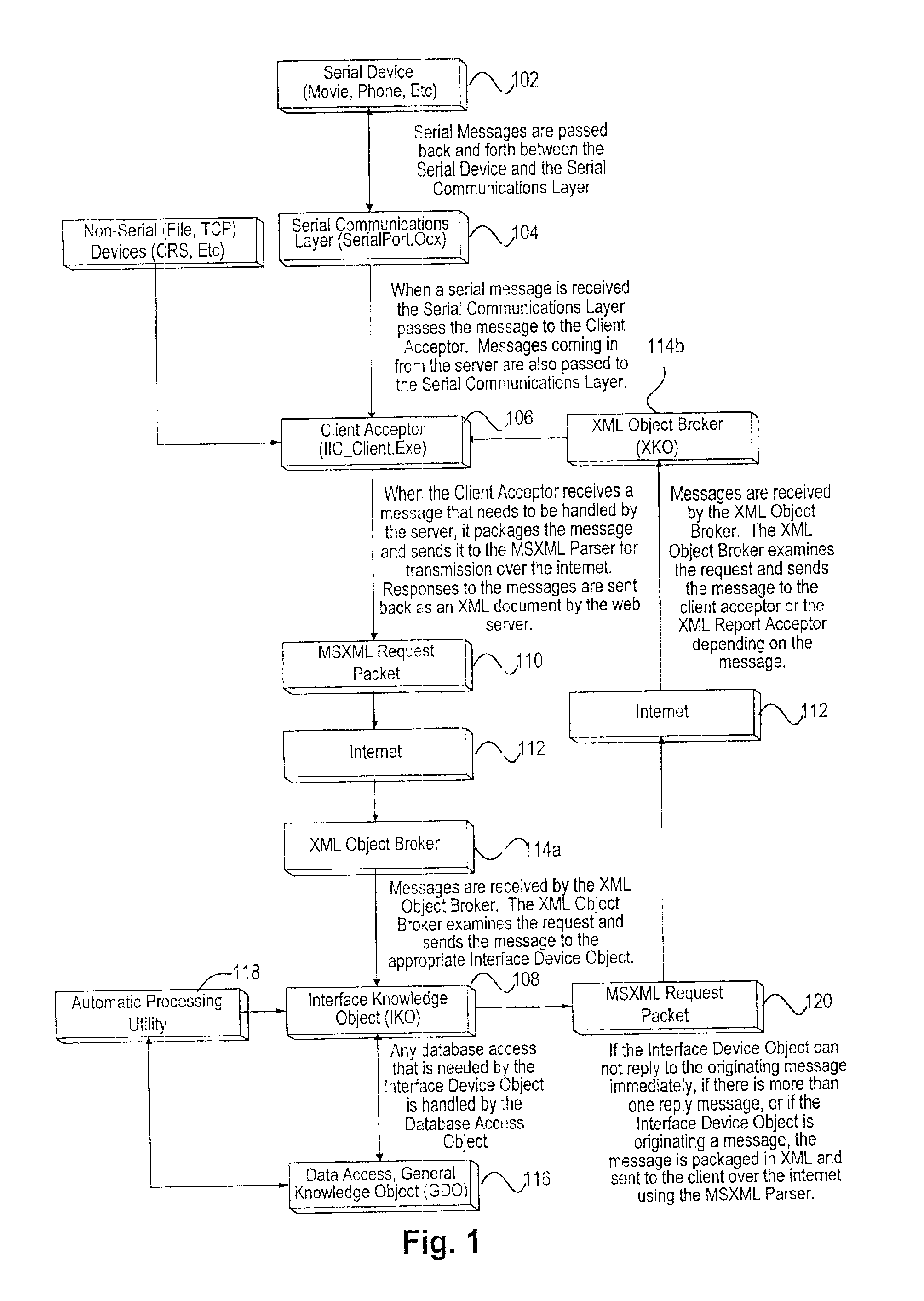
InactiveUS6857023B2Easy to manageMultiple digital computer combinationsElectric digital data processingInformation processingNetwork communication
An interface controller for managing operation of a plurality of devices via a wide area network is provided. Each of the devices has a unique communication protocol associated therewith. A network communications layer is provided for communicating with the plurality of devices via the wide area network and a client application associated with the plurality of devices. An information processing layer is also provided for communicating with the network communications layer. The information processing layer has a set of objects corresponding to each of the plurality of devices. The information processing layer is also for interacting with a data access layer on behalf of each of the plurality of devices using the corresponding objects. Interaction between the information processing layer and the data access layer on behalf of all of the plurality of devices is governed by a single set of rules.
Owner:PEGASUS SOLUTIONS INC
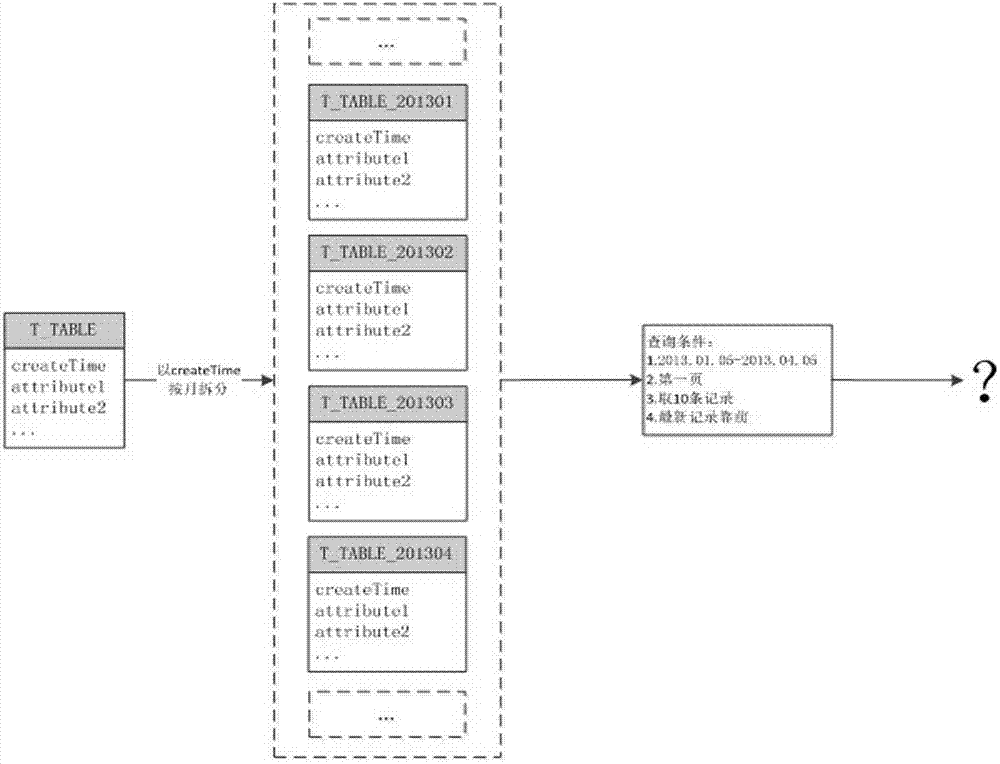
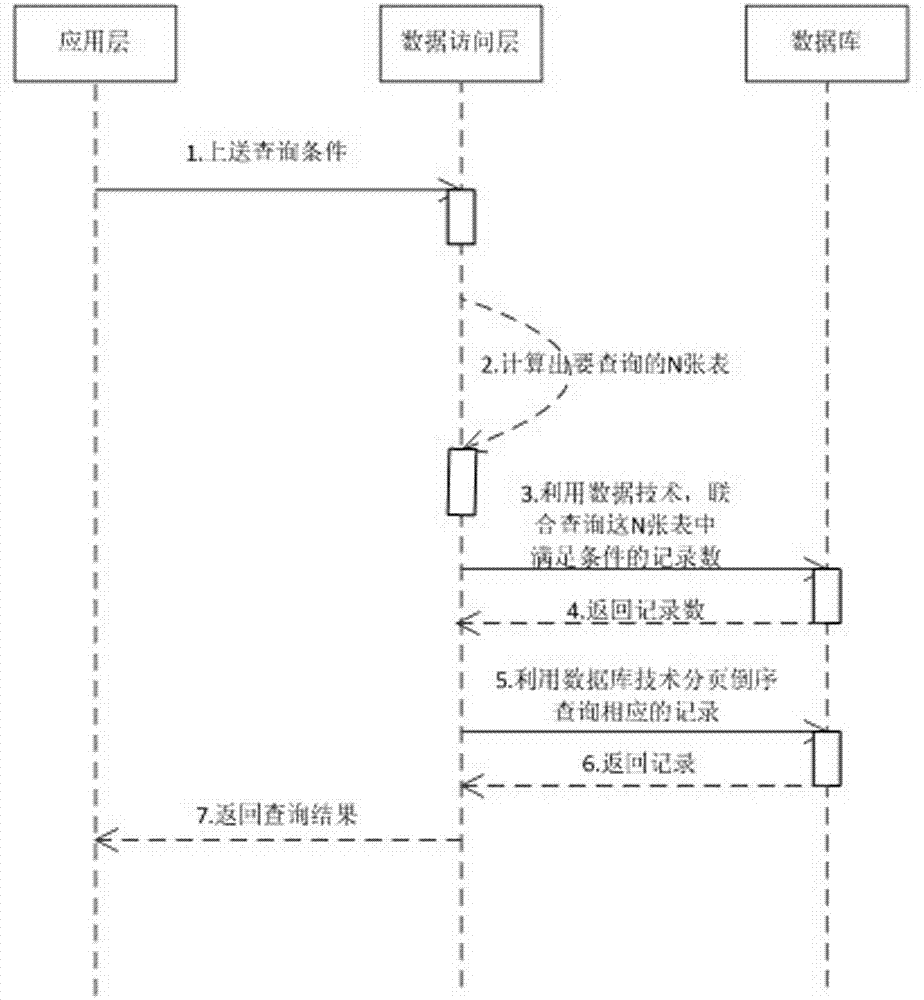
Table-by-table and page-by-page query method and system for database
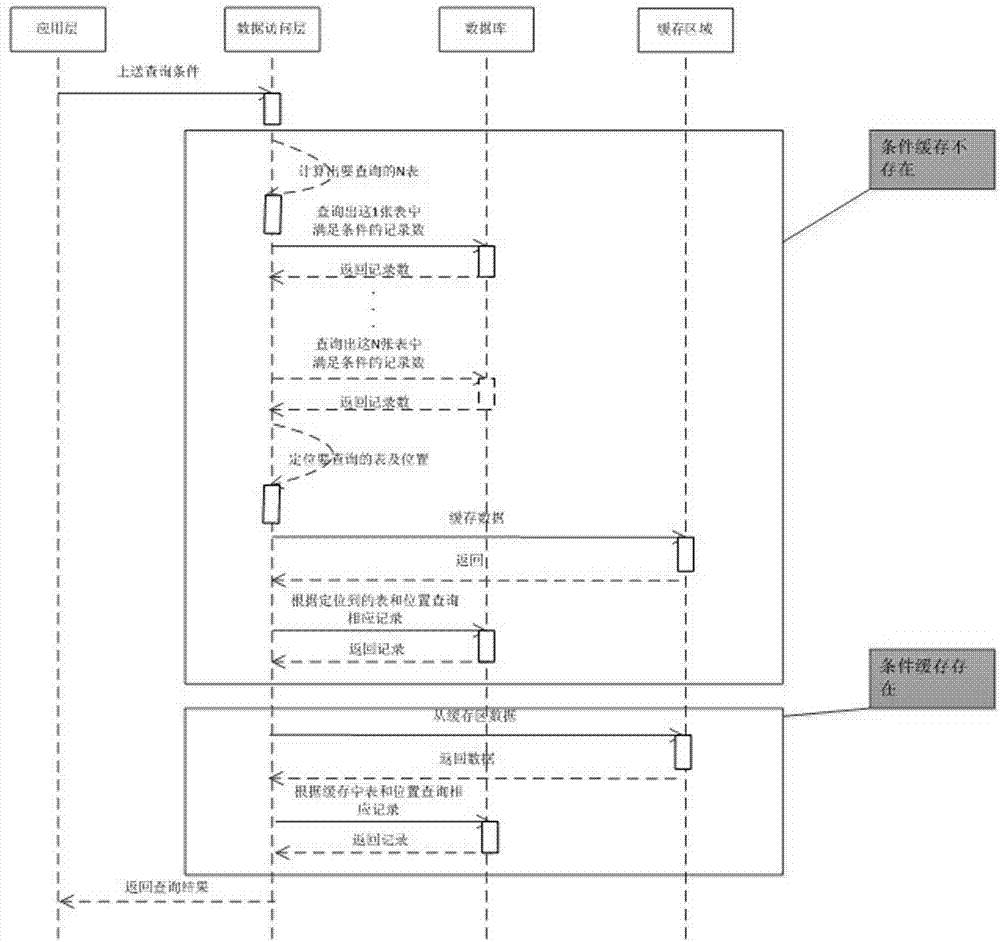
ActiveCN104123340ARelieve stressSolve the problem that seriously consumes database resourcesSpecial data processing applicationsTable (database)Data access layer
The invention relates to a table-by-table and page-by-page query method and system for a database. An application layer can send a query request to a data access layer, the data access layer can calculate out N tables meeting the query conditions and respectively query the record numbers, meeting the conditions, of the tables, then the position of the table where a request page is arranged and the positions of records in the table can be located according to the request page and the record number of the request page, the database can be queried to obtain corresponding records according to the position of the table and the positions of the records in the table, and finally results are returned to the application layer. Before accessing the database and processing the results, the data access layer can access a cache area to read or store corresponding data. By means of layer-by-layer and page-by-page query, the effective utilization of resources in the database is improved, and the burden of a database system is relieved.
Owner:数贸科技(北京)有限公司
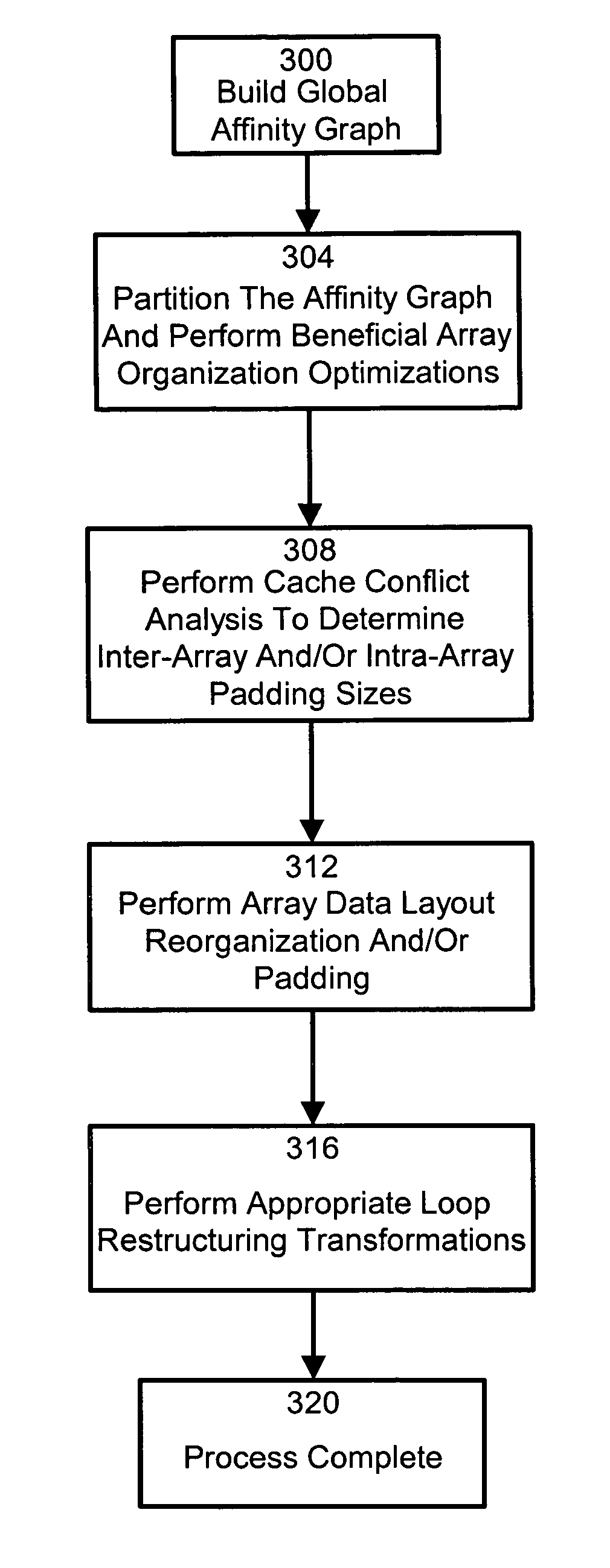
Compiler with cache utilization optimizations
A compiling program with cache utilization optimizations employs an inter-procedural global analysis of the data access patterns of compile units to be processed. The global analysis determines sufficient information to allow intelligent application of optimization techniques to be employed to enhance the operation and utilization of the available cache systems on target hardware.
Owner:INT BUSINESS MASCH CORP
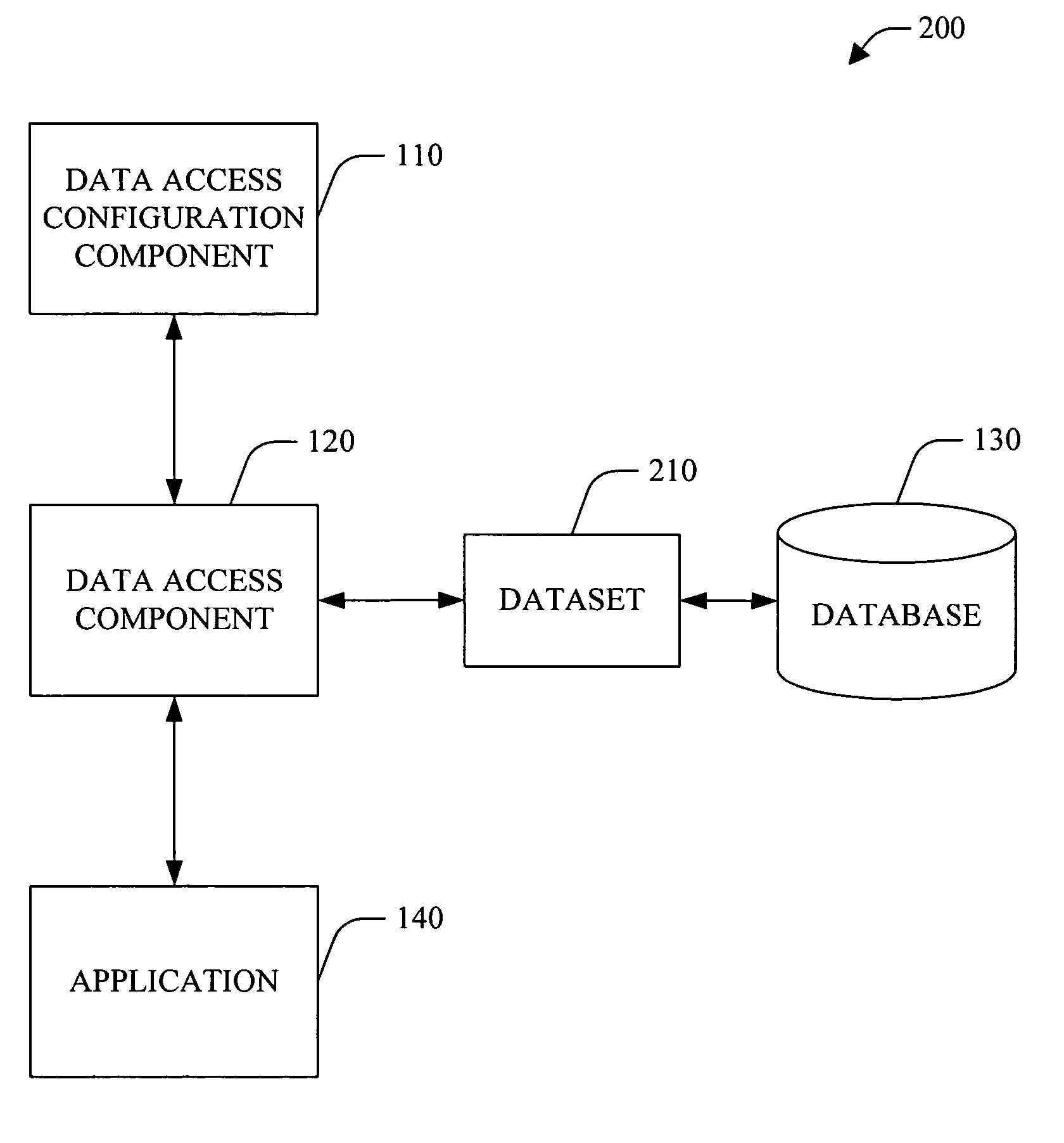
Database and data access layer
InactiveUS20100268705A1Efficient constructionEasy to buildDigital data processing detailsResourcesManaging changeBusiness intelligence
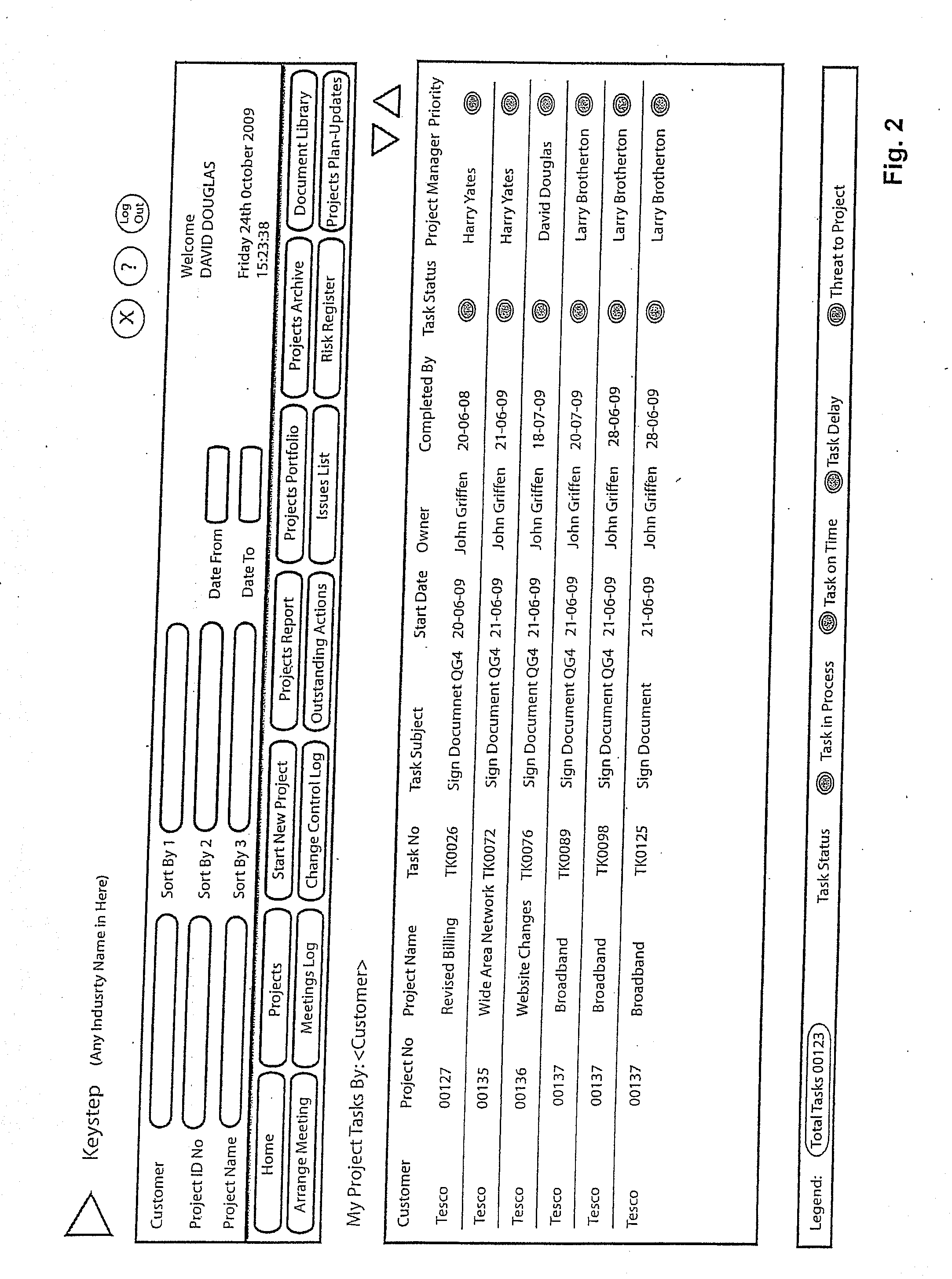
The system of the present invention facilitates the collection, processing, optimization and communication of data. Project data is accessed through an architecture, comprising an access layer, with programs for retrieving, processing and communicating data from a database, and a Customer User Interface (CUI) presentation layer. The CUI provides individual users with interaction throughout the project life-cycle, for example, for recording and processing information, completing project tasks, producing and managing documents, managing changes, issues and risks and producing reports and business intelligence, including individual project and projects portfolio status indicators.
Owner:PROJECT MANAGEMENT SOFTWARE
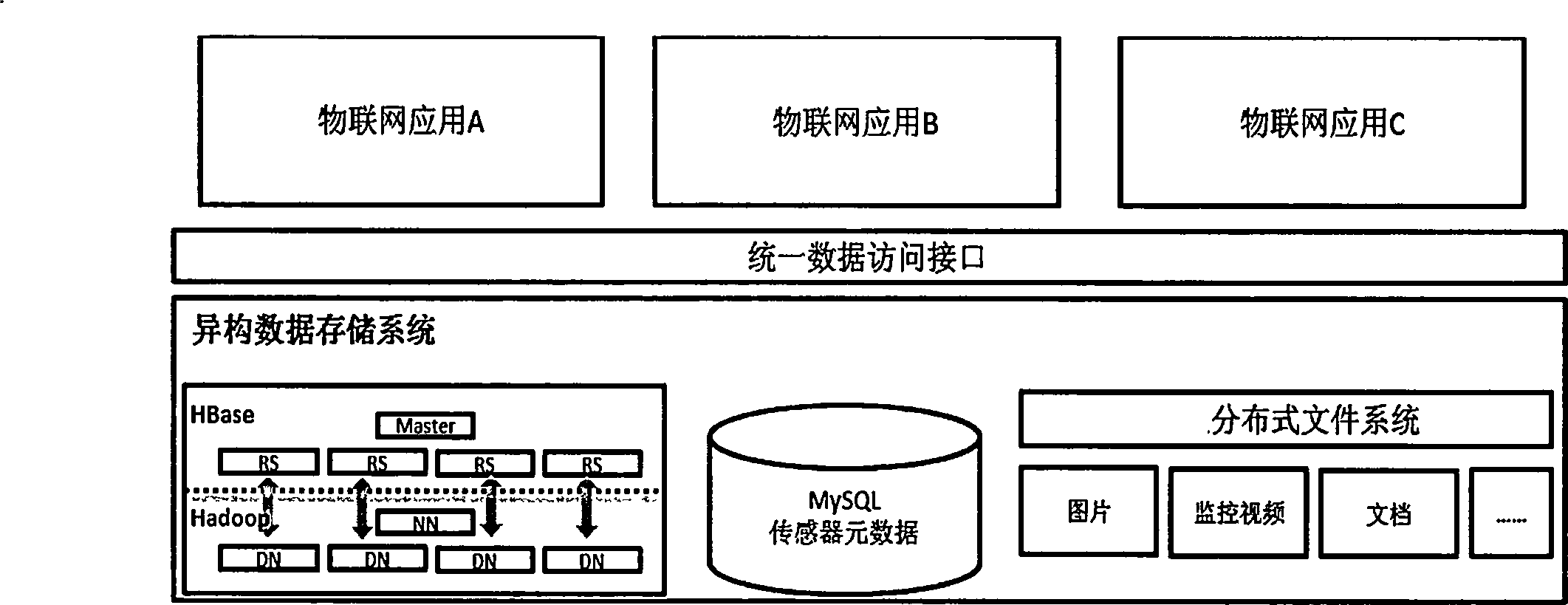
Internet of things heterogeneous data storage method and system
The invention discloses an Internet of things heterogeneous data storage method and a storage system. The internet of things heterogeneous data storage method comprises the steps that various types of data are stored in a column-based mode through an HBase distributed storage system, an MySQL metadatabase carries out registration management on the stored data, and finally the data access layer is configured in a centralized manner, so that applications based on the database can use the unified data interface. According to the Internet of things heterogeneous data storage method and the storage system, the unified storage mode is adopted through the unified data interface, the storage of different types of data and data from different sources is effectively supported; the column-oriented storage mechanism is extended by utilizing the HBase technology, so that the storage volume can be extended horizontally; the memory mapping file mechanism is adopted to effectively improve the storage and management efficiency of large files; and the data redundancy storage technology is adopted to greatly improve the system reliability and the accessibility. The Internet of things heterogeneous data storage method and the storage system can well solve the storage problem of various types of data, has efficient storage and utilization capability on large files, and is also low in cost and high in robustness.
Owner:上海和伍物联网系统有限公司
System and method for providing insurance data processing services via a user interface
ActiveUS8176145B1ResourceLow costFinanceGeneral purpose stored program computerWeb browserApplication software
A system architecture for providing remote access to insurance applications from a remote location is provided, including: a presentation layer located at the remote location that provides tools for navigating within one of the insurance applications and executing business transactions, wherein the presentation layer is based on web browser technology; an application layer that enforces predetermined rules of business on commands and transactions input from the remote location; a data access layer that manages physical storage of data relating to the insurance applications in databases and provides the application layer with access to application data; and a distributed technical layer separating a presentation logic of the presentation layer from an application logic of the application layer, wherein the distributed technical layer is configured to coordinate an execution of the insurance applications on one or more different platforms.
Owner:THE TRAVELERS INDEMNITY
Seamless data migration across databases
ActiveUS9720991B2Minimal impactMinimal disruptionDatabase distribution/replicationSpecial data processing applicationsDistributed Computing EnvironmentData access layer
Techniques are disclosed for enabling the migration of data with minimized impact on consumers of the data. A data migration agent updates pointers to active data locations and coordinates a migration from a first data resource to a second data resource so that seamless migration may be carried out. A data access layer of a distributed computing environment can take advantage of the pointers and metadata written by the data migration agent to serve requests to resources of the distributed computing environment so that read availability is available regardless of migration status.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com