Patents
Literature
611results about How to "Minimal impact" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
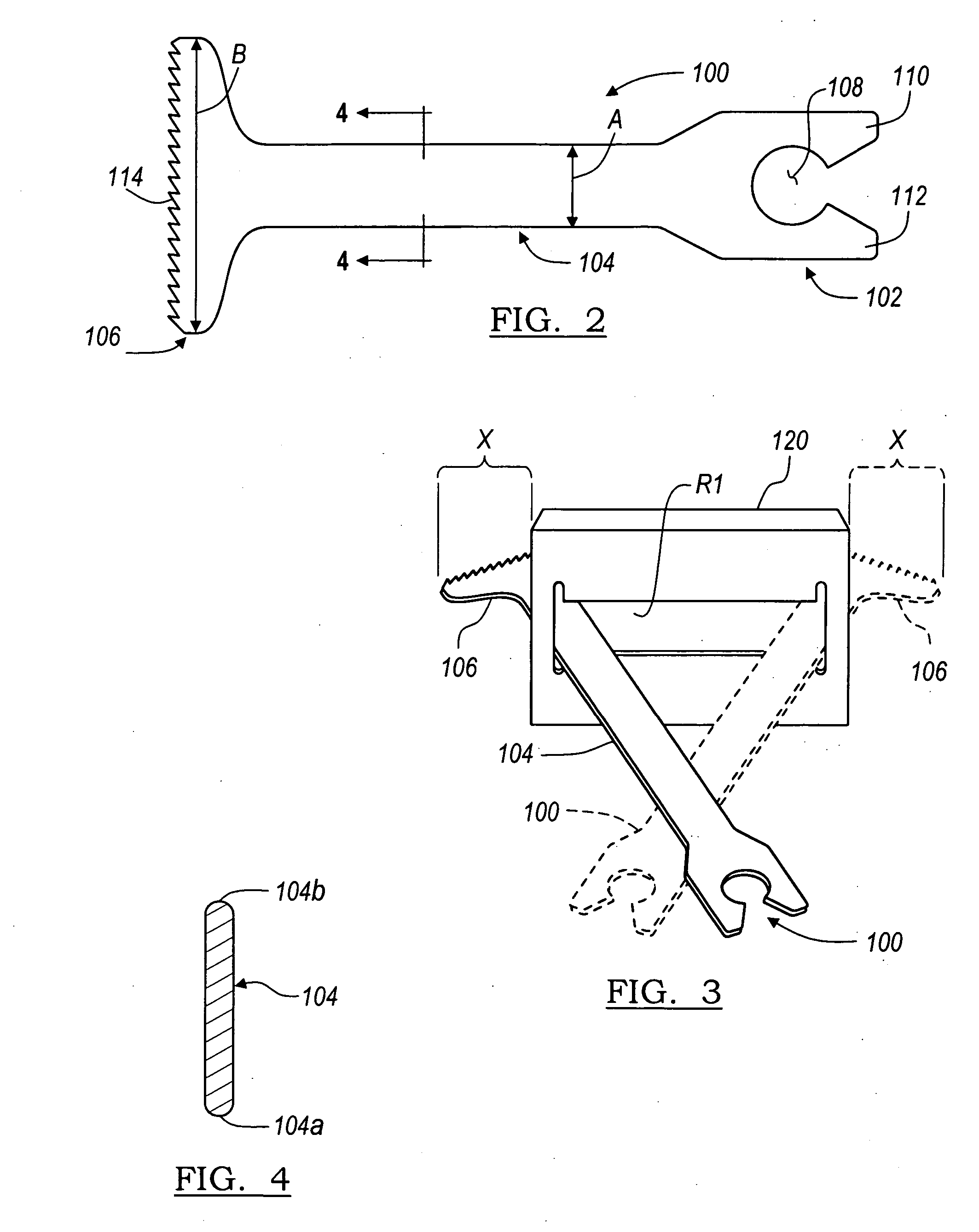
Software-based method for gaining privacy by affecting the screen of a computing device
InactiveUS7779475B2Improve privacyMinimal impactDigital data processing detailsUnauthorized memory use protectionGraphicsInternet privacy
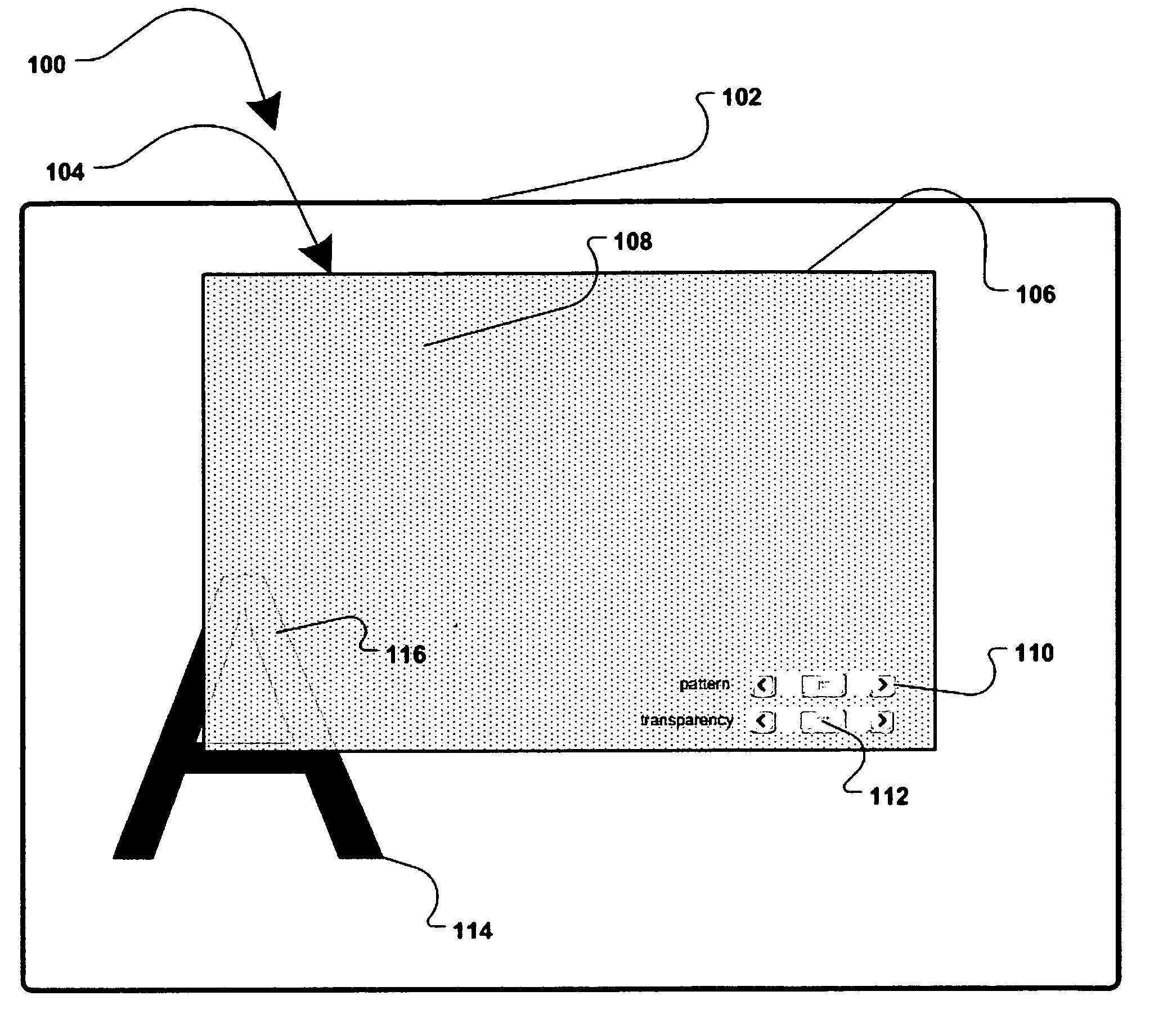
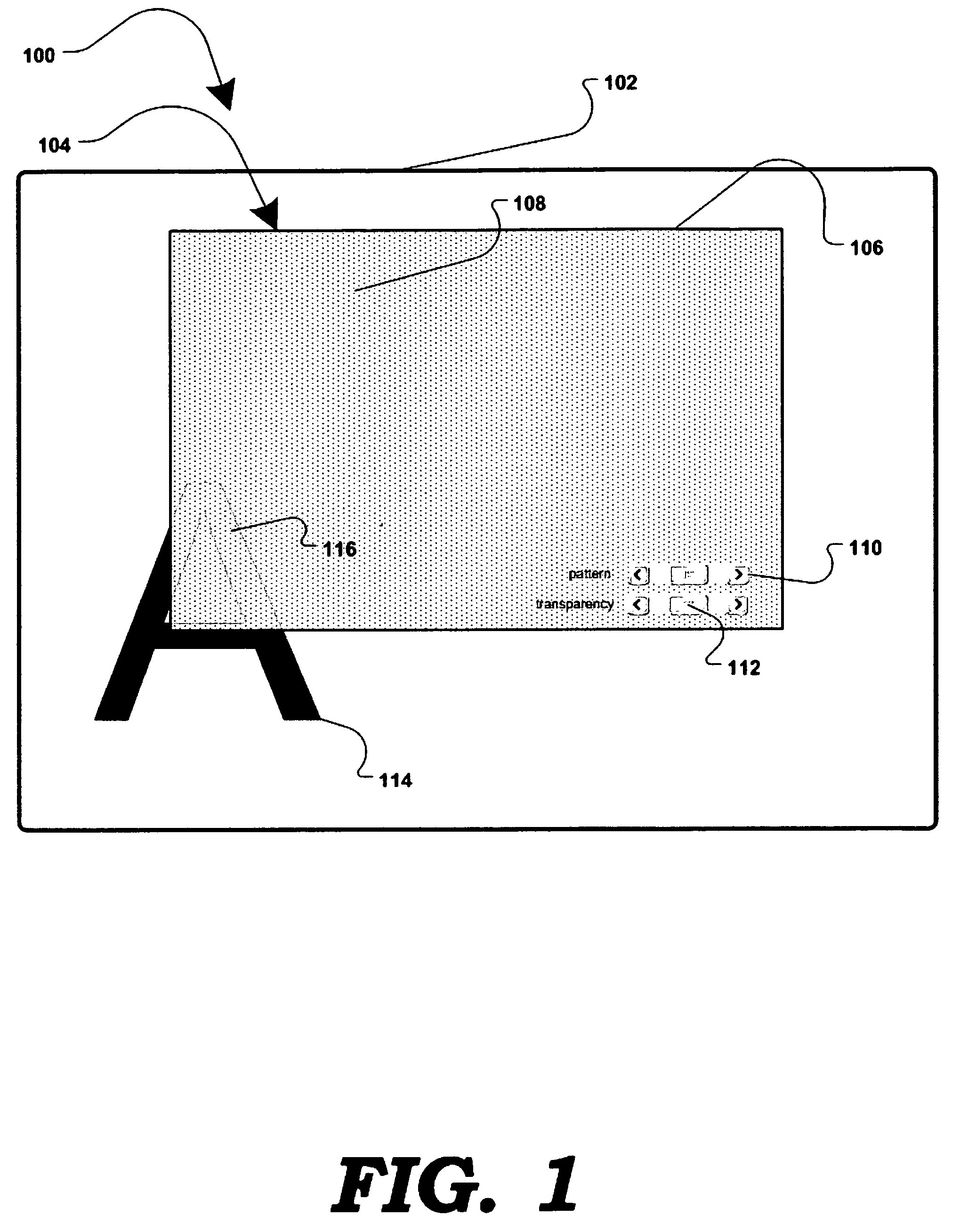
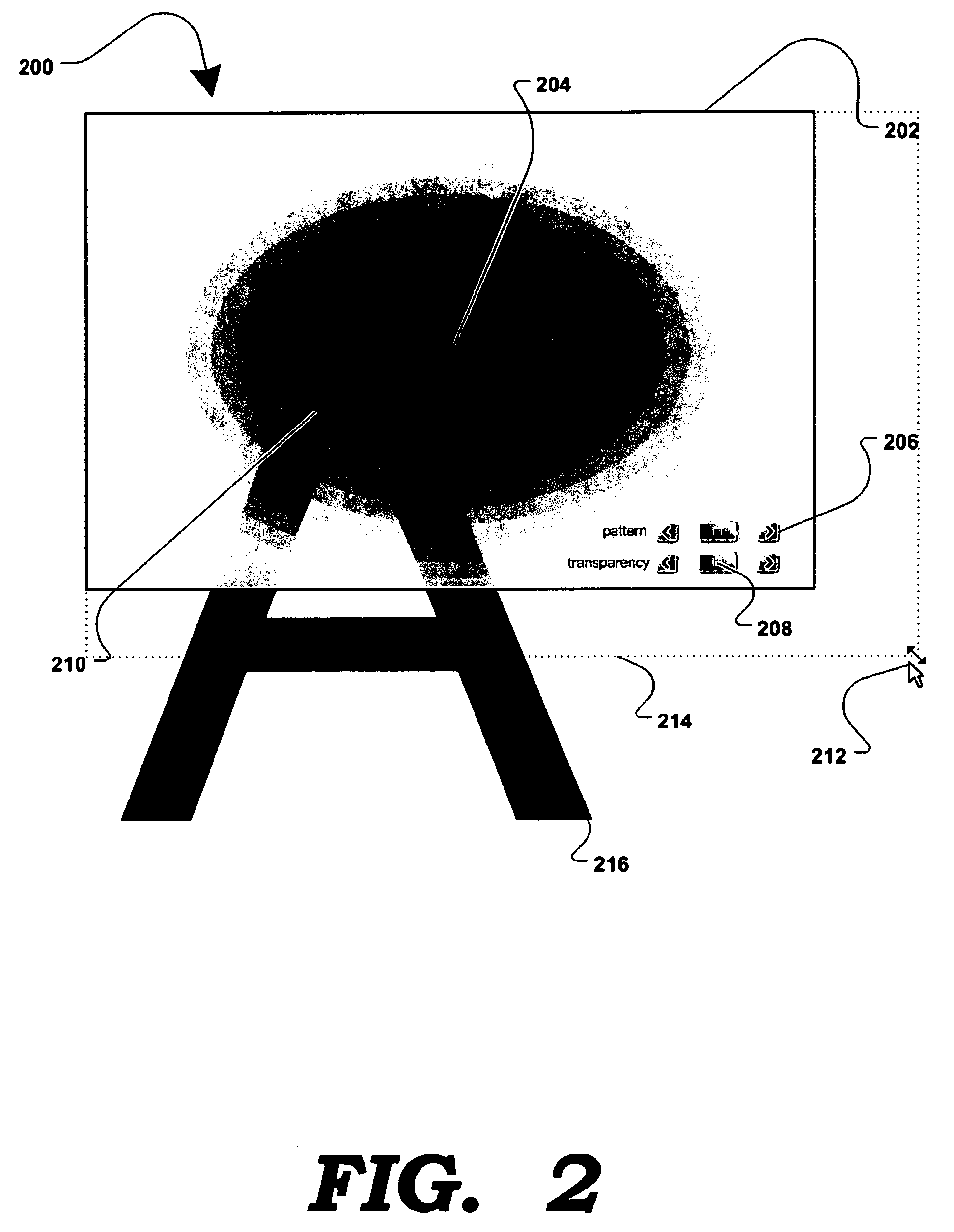
A method and apparatus for allowing the user of an electronic device to enhance privacy over a display with the use of software, are disclosed. A security window including a translucent graphical effects region may be displayed on the electronic device such that it overlays content the user may choose to protect. The security window allows the protected content to remain discernable for the user of the device yet substantially indiscernible to a person at a further distance and / or greater viewing angle from the screen of the device. One or more security windows, each of which may be of any size, shape, texture, translucency level and any other graphical or behavioral properties may be displayed on the display associated with the electronic device. The user may control the size, shape, texture, translucency level and any other graphical or behavioral properties of the security window and graphical effects region. The user may invoke or terminate a security window with the single click of a button. Security windows may automatically attach to applications in focus, or be attached in response to a user command, and allow uninterrupted usability of those applications.
Owner:PETNOTE
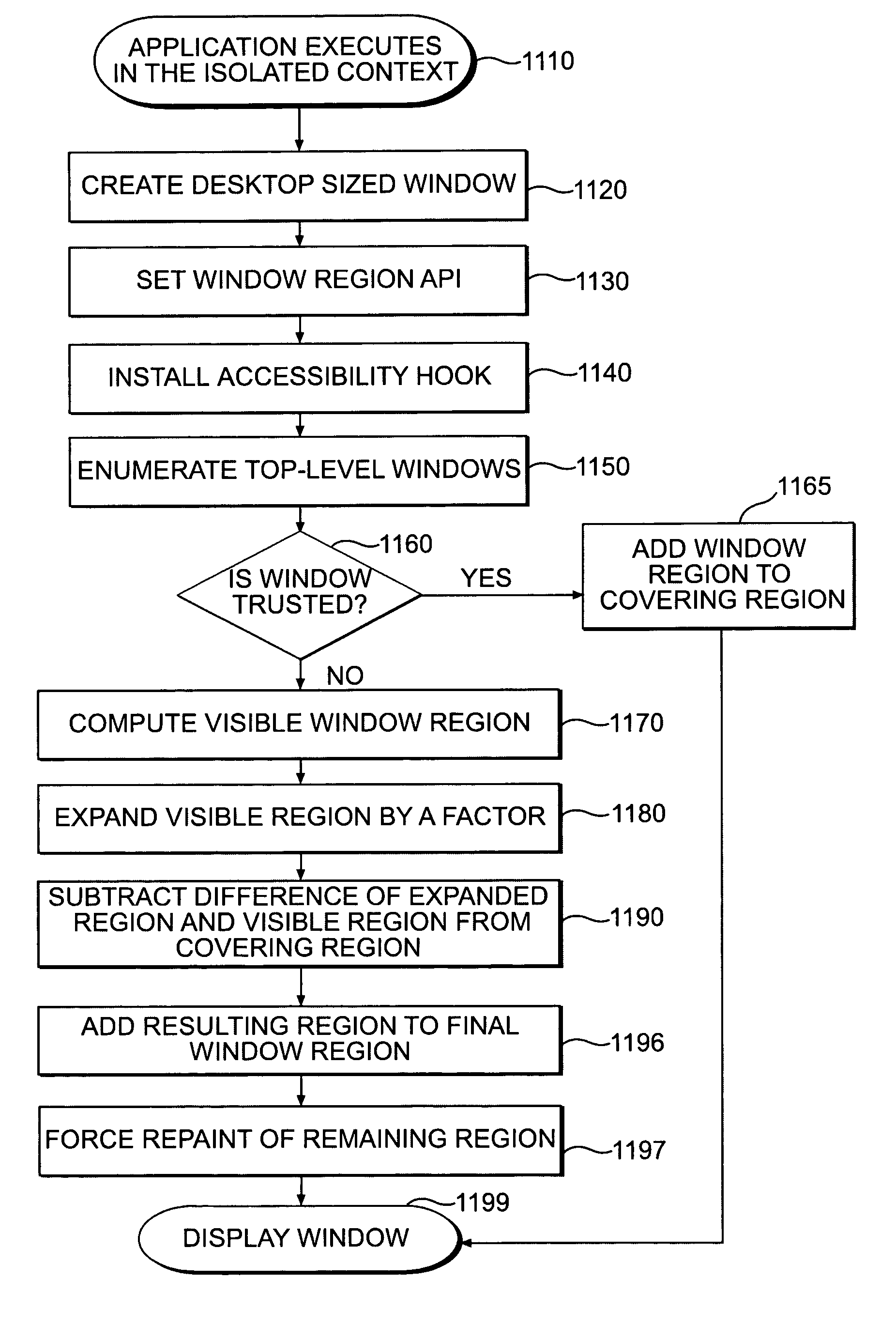
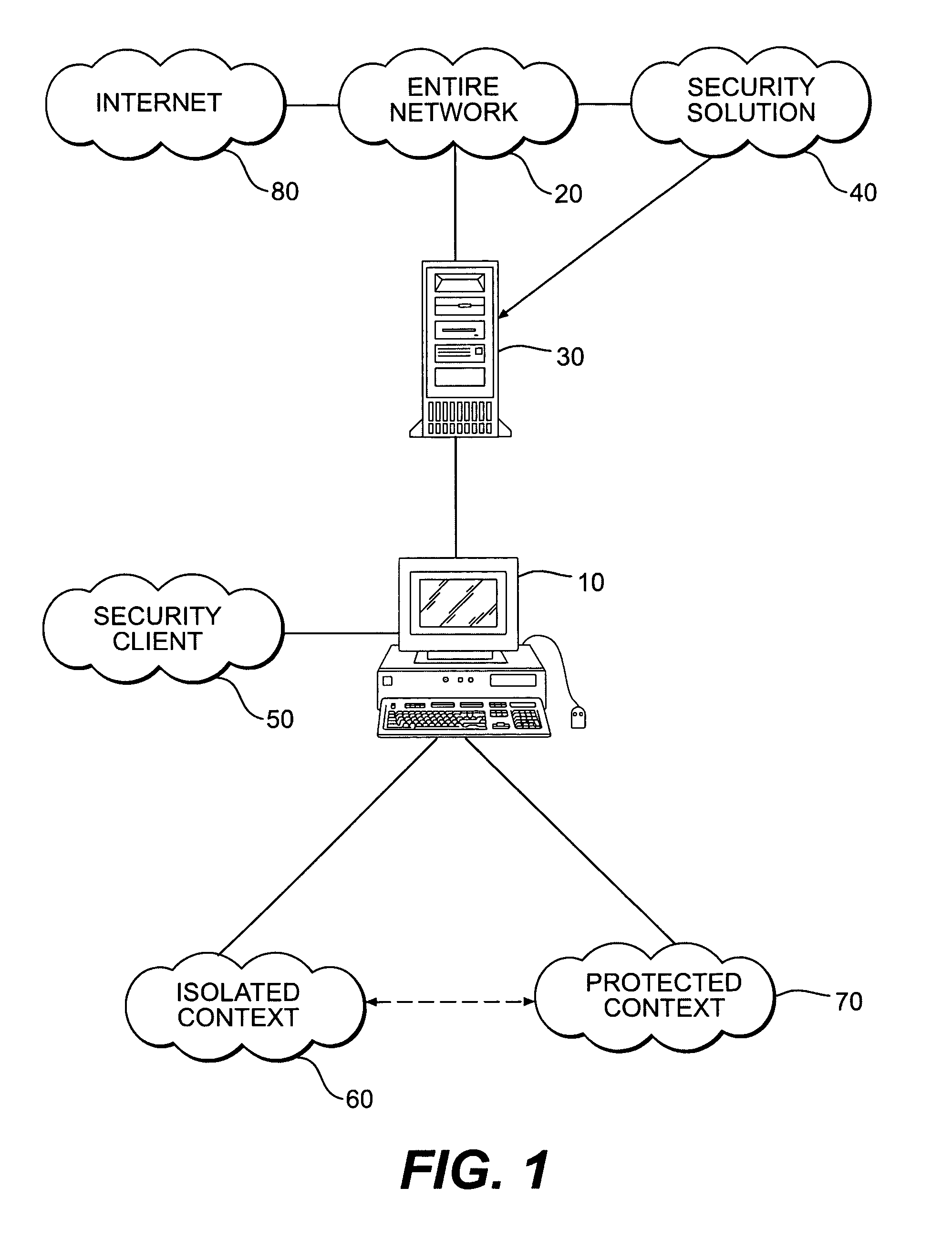
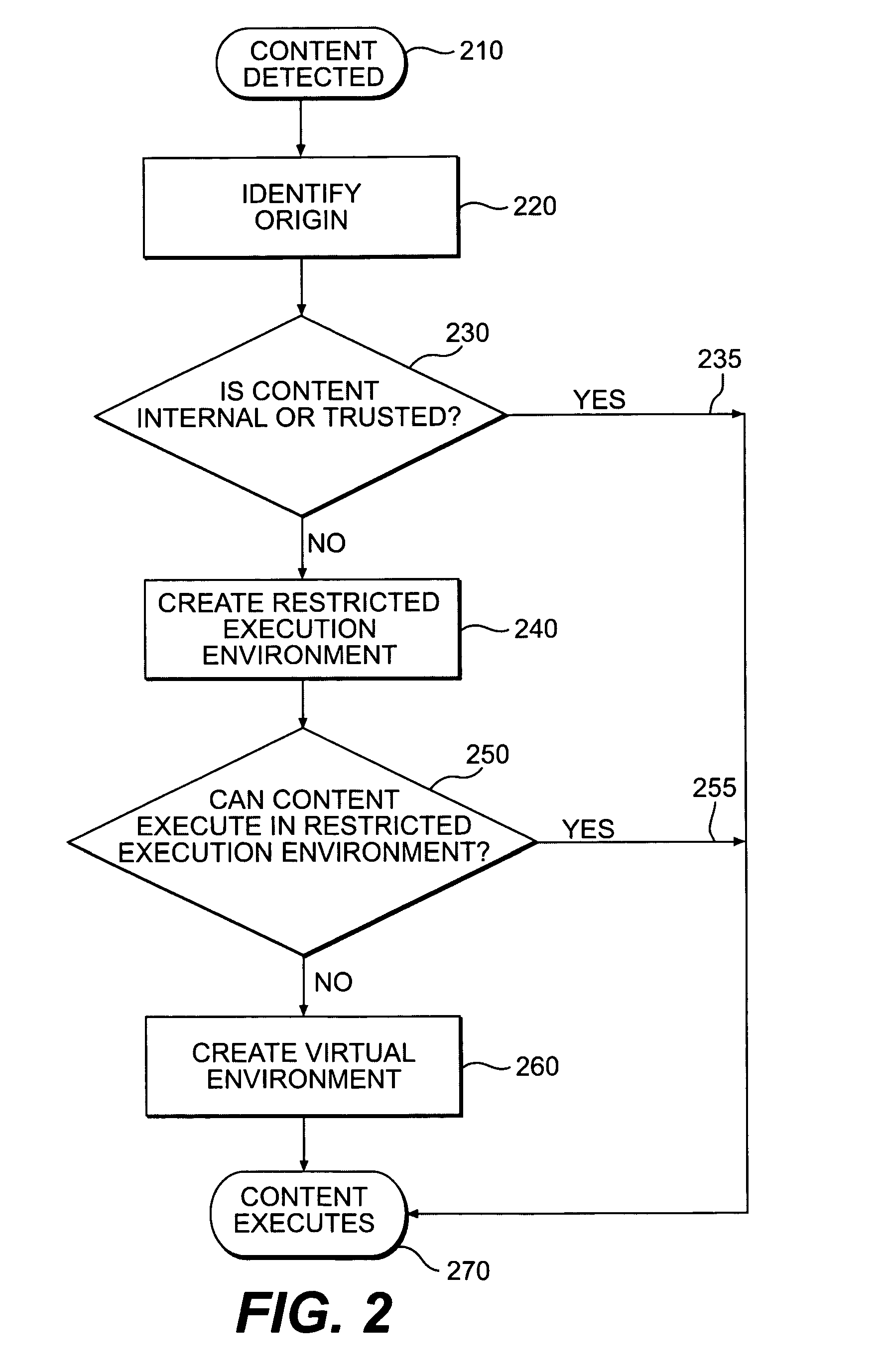
Systems and methods for secure client applications
ActiveUS20050149726A1Avoid attackMinimize impactDigital data processing detailsHardware monitoringVirtualizationClient-side
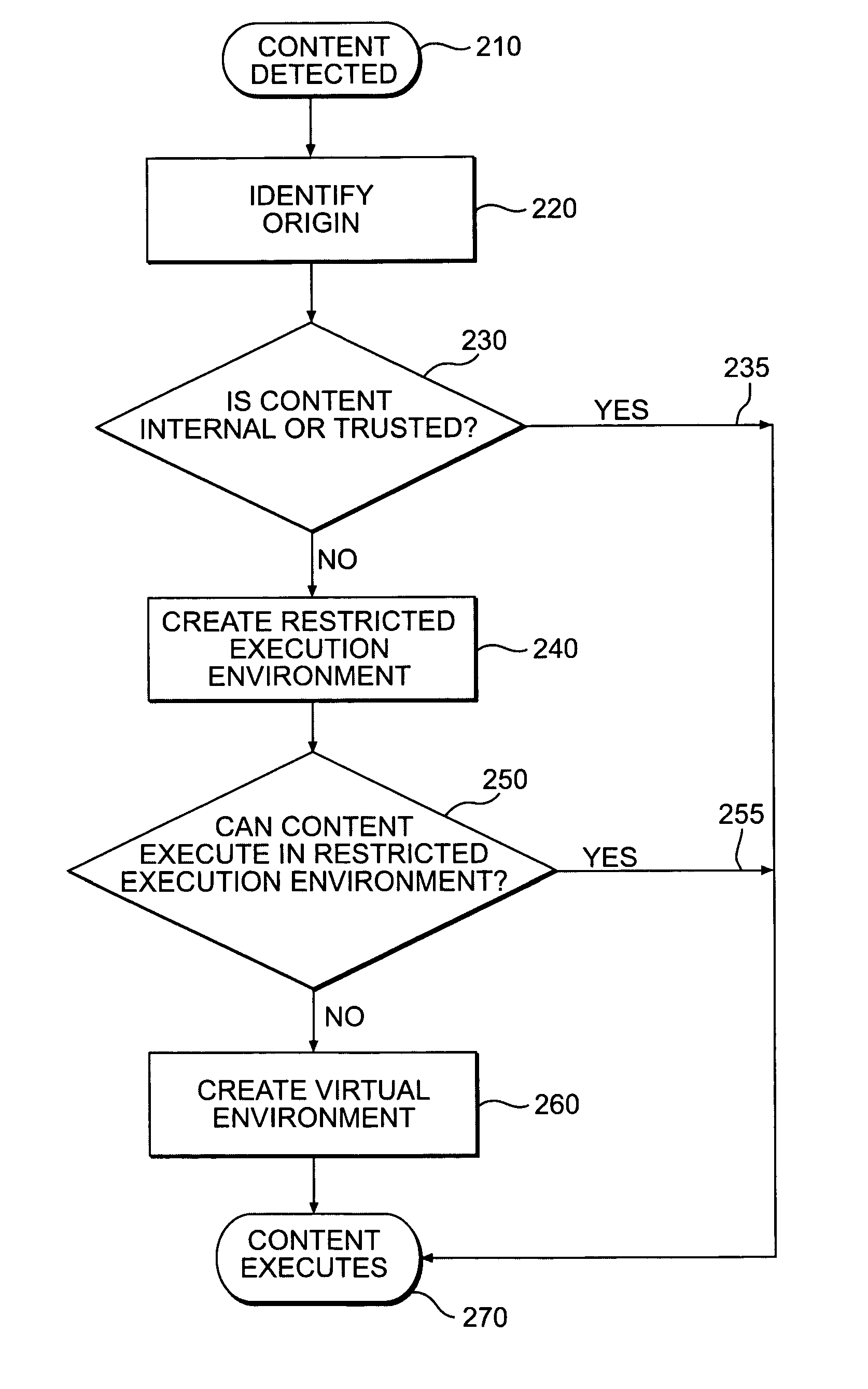
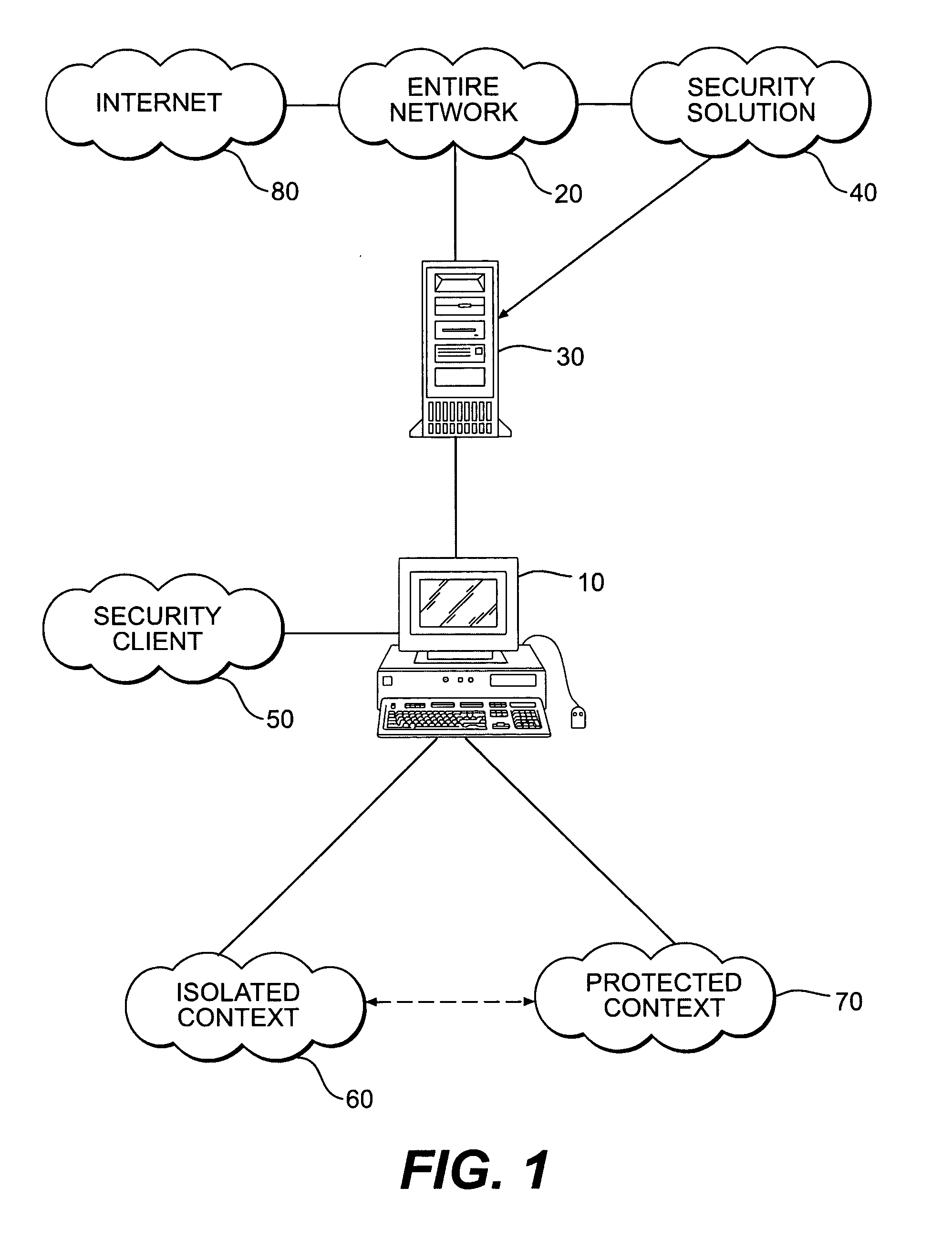
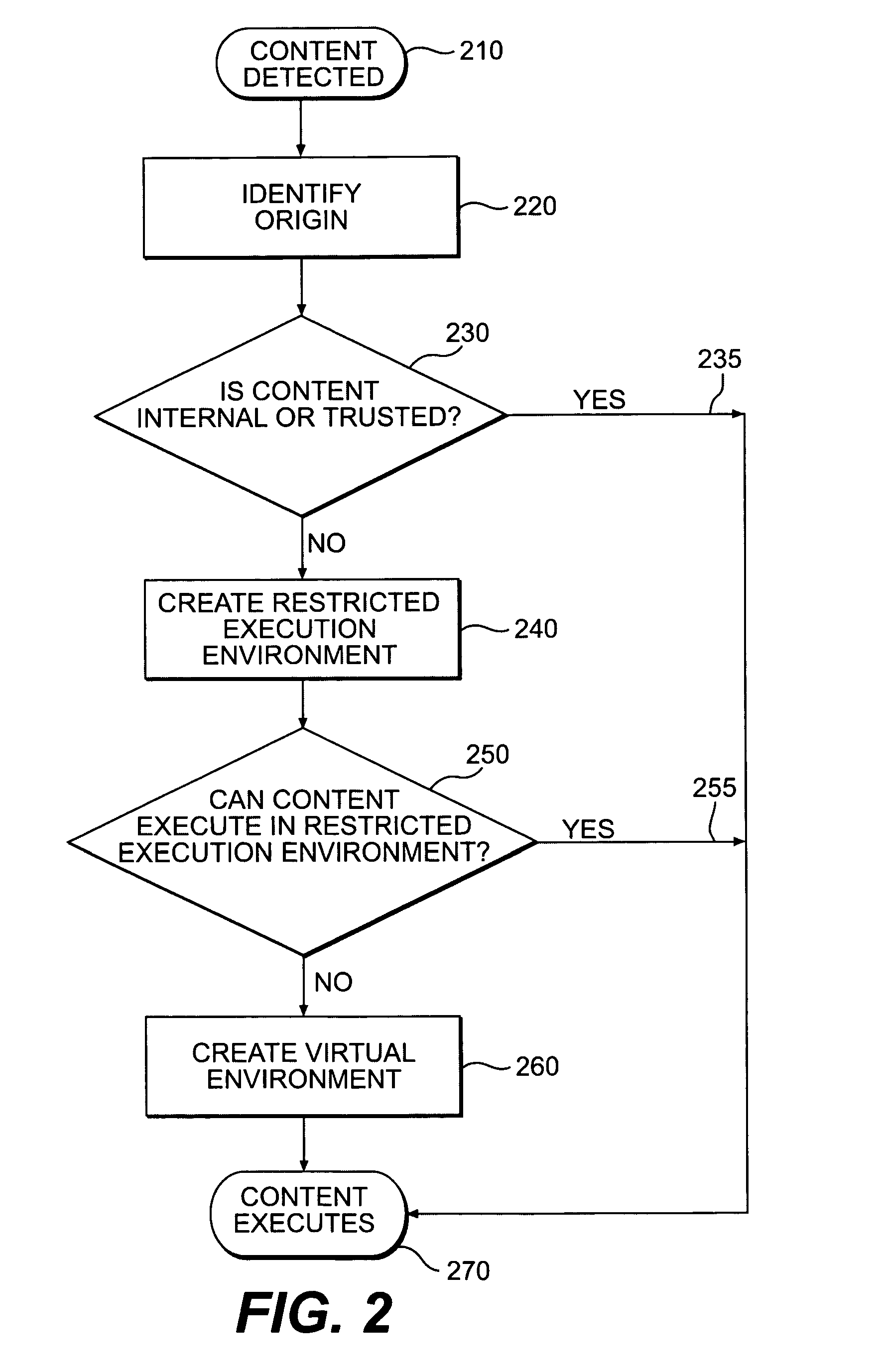
An innovative security solution which separates a client into a Protected Context, which is the real files and resources of the client, and an Isolated Context, which is a restricted execution environment which makes use of virtualized resources to execute applications and modify content in the Isolated Context, without allowing explicit access to the resources in the Protected Context. The solution further consolidates user interfaces to allow users to seamlessly work with content in both contexts, and provide a visual indication of which display windows are rendered from content executed in the Isolated Context.
Owner:GOOGLE LLC
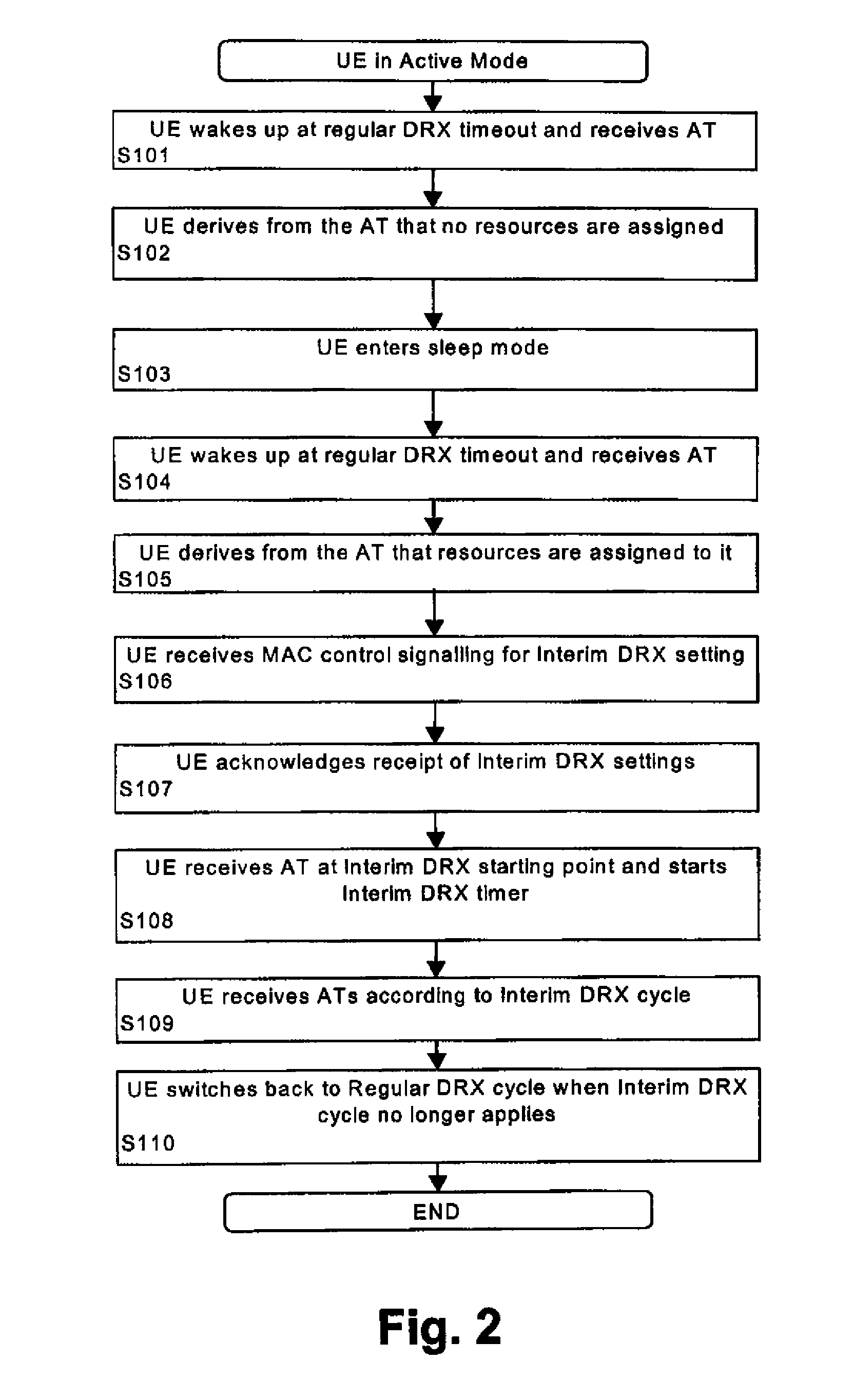
Method and system for providing interim discontinuous reception/transmission
ActiveUS20070291728A1Flexible DRX/DTXEasy to adjustPower managementEnergy efficient ICTComputer hardwareControl layer
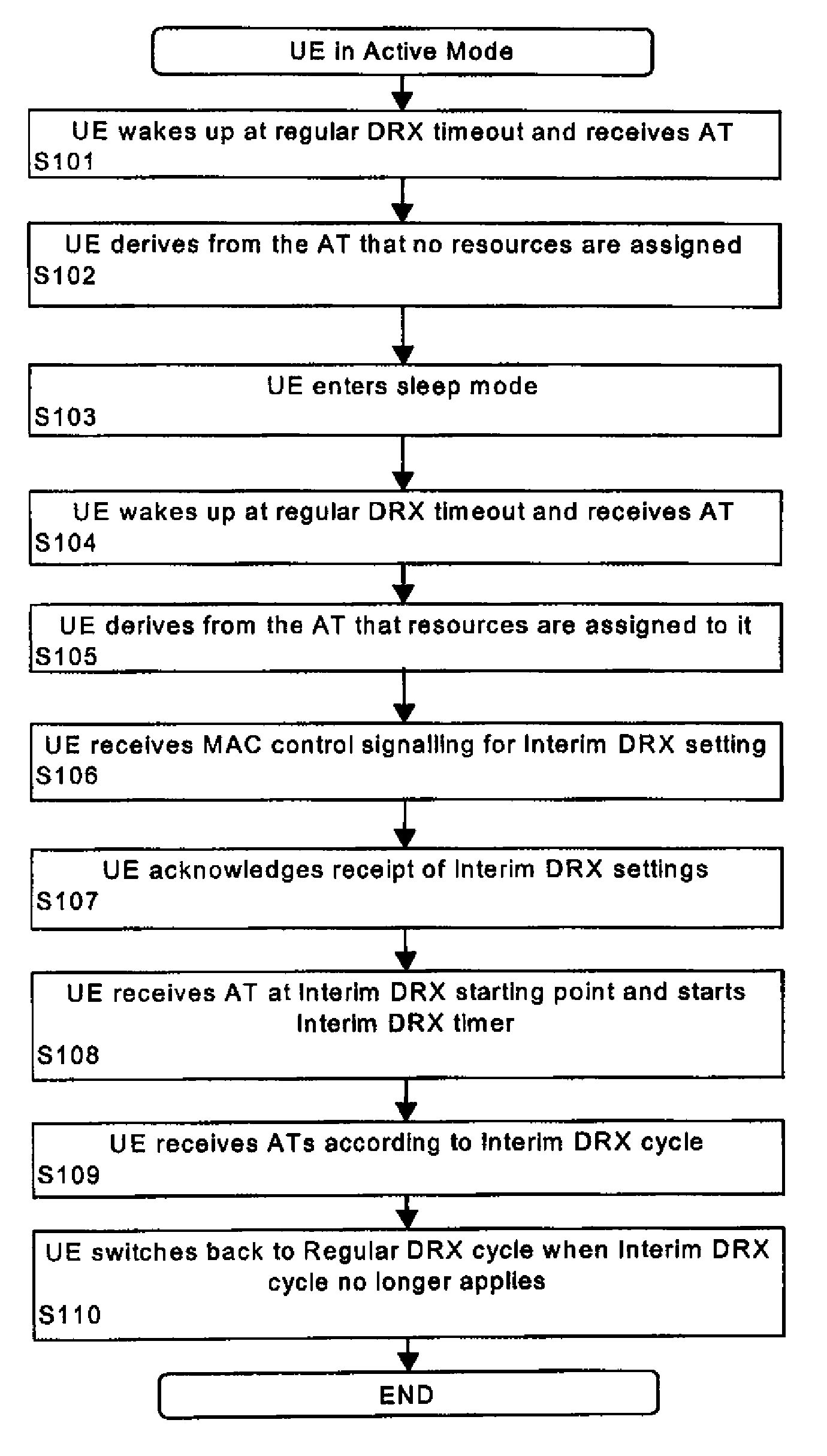
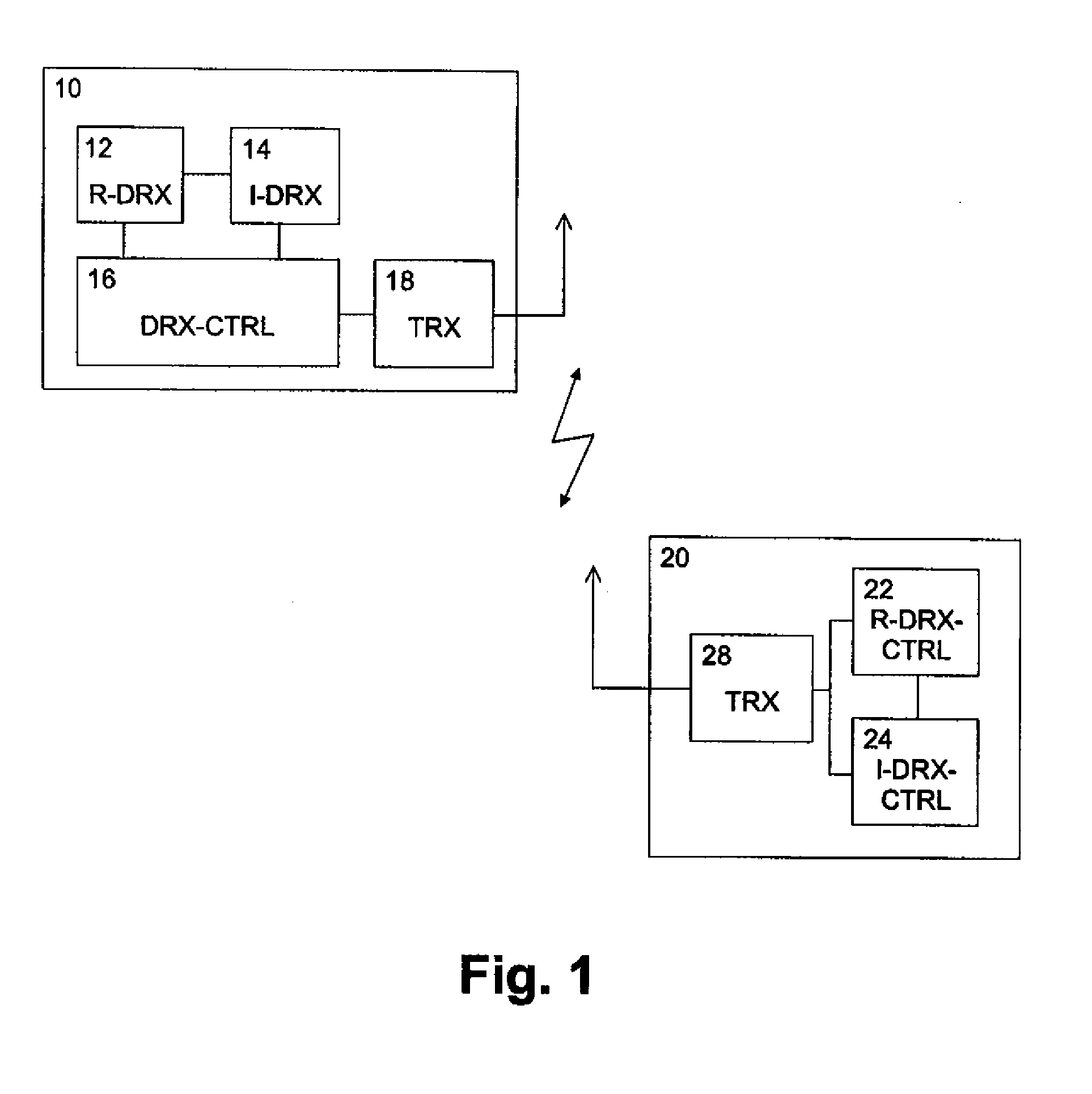
A method, terminal device, network element, system and computer program product for controlling discontinuous reception or transmission at a terminal device of a communication network are disclosed. A regular discontinuous reception or transmission cycle of a regular discontinuous reception or transmission scheme is set by using a first control layer, and in addition thereto a shorter temporary discontinuous reception or transmission cycle of an interim discontinuous reception or transmission scheme can be set by using a second control layer. This arrangement provides long discontinuous reception or transmission cycles for power consumption improvements while at the same time ensuring that the network can easily and flexibly shorten these cycles for increased data throughput, if needed.
Owner:NOKIA TECHNOLOGLES OY
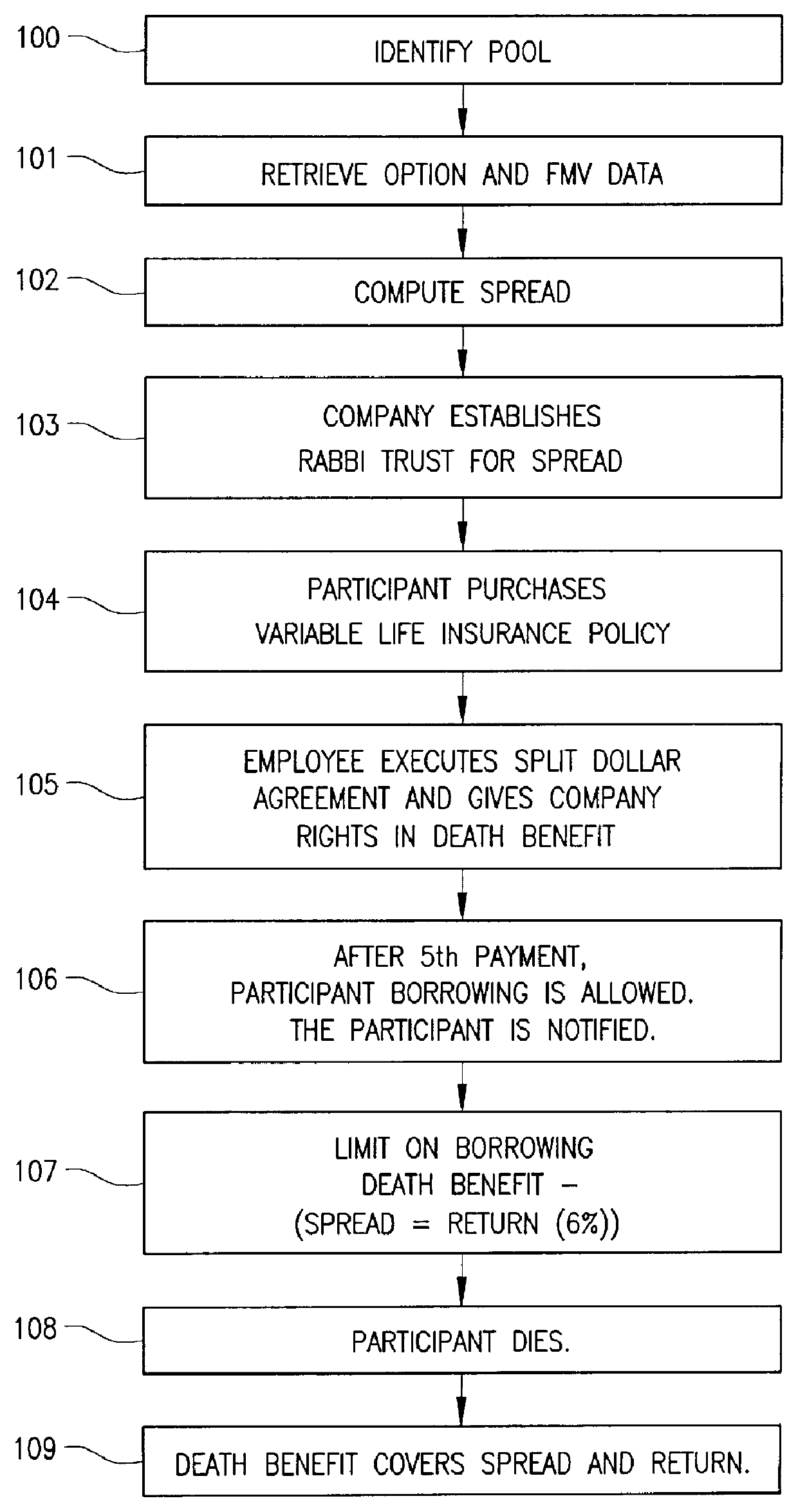
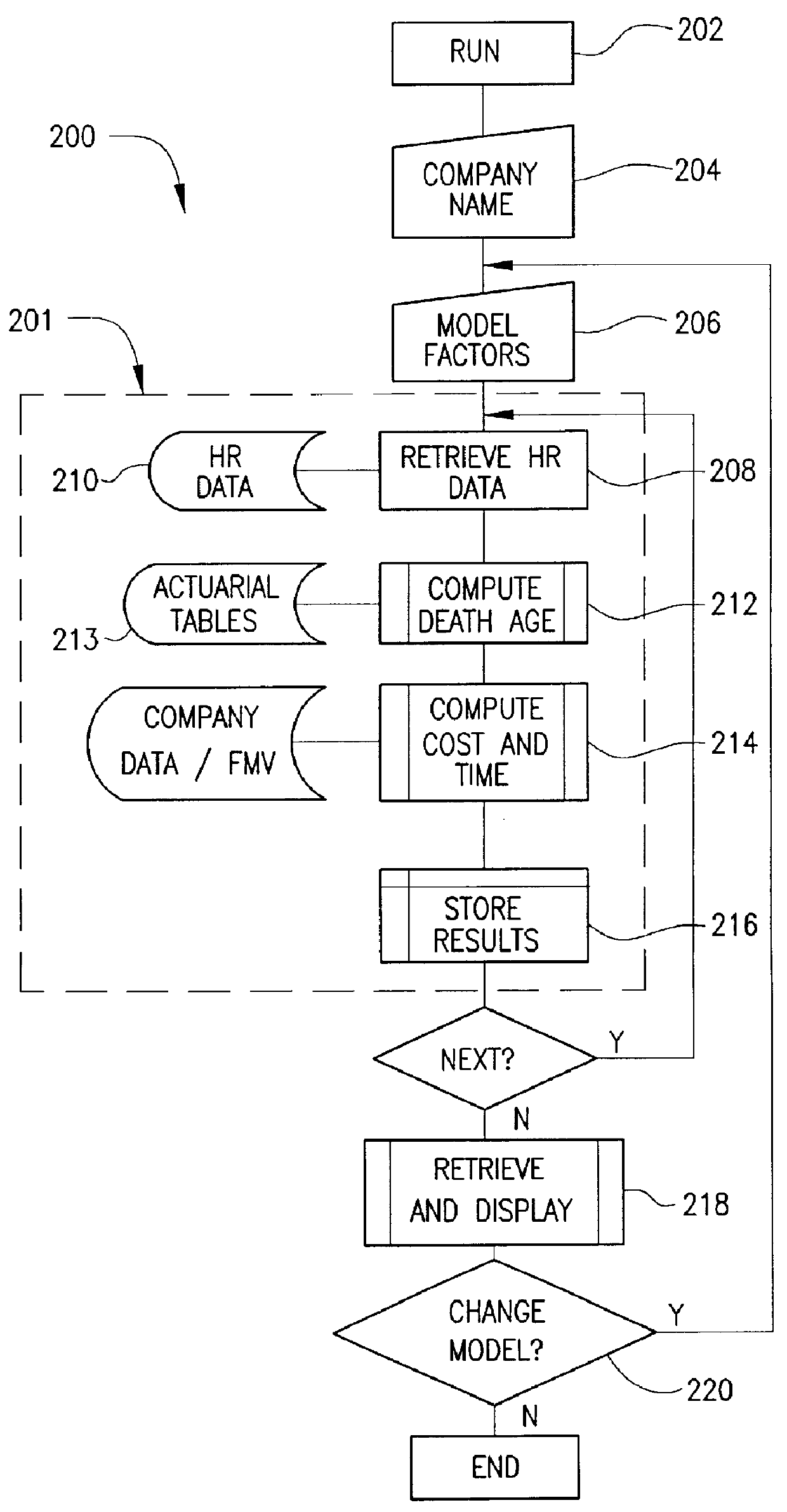
Method and apparatus for modeling and executing deferred award instrument plan
A method and apparatus for deferred award instrument plan by identifying at least one participant in the deferred award plan, retrieving financial data related to stock options corresponding to the identified participant, computing a spread associated with the retrieved stock options, establishing a rabbi trust with the spread, determining whether a life insurance policy has been purchased by the participant, determining whether a split dollar agreement has been executed, monitoring and paying at least one premium for the life insurance policy and notifying the participants that a payment associated with the life insurance policy has been paid.
Owner:ASCENSUS INSURANCE SERVICES
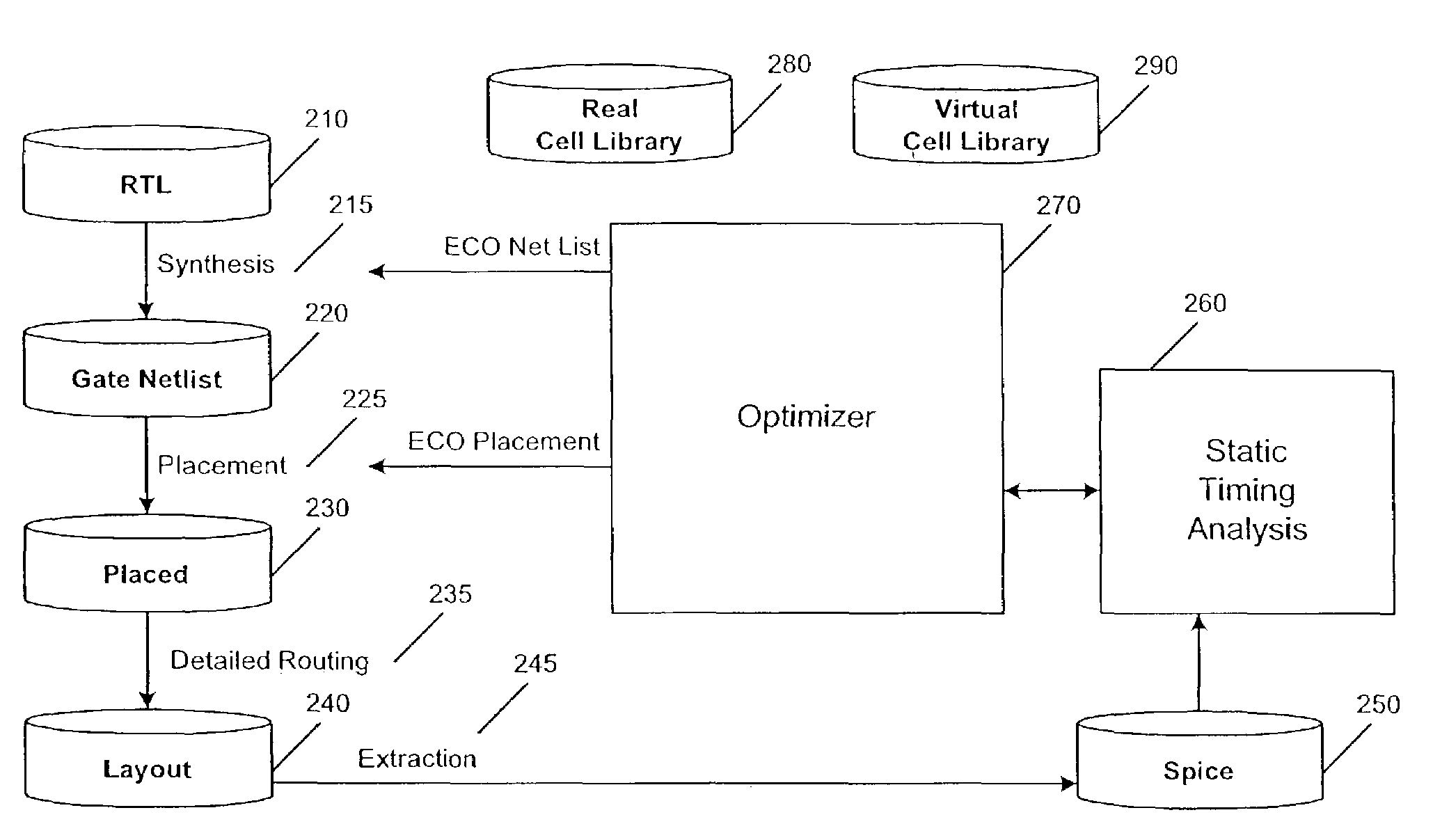
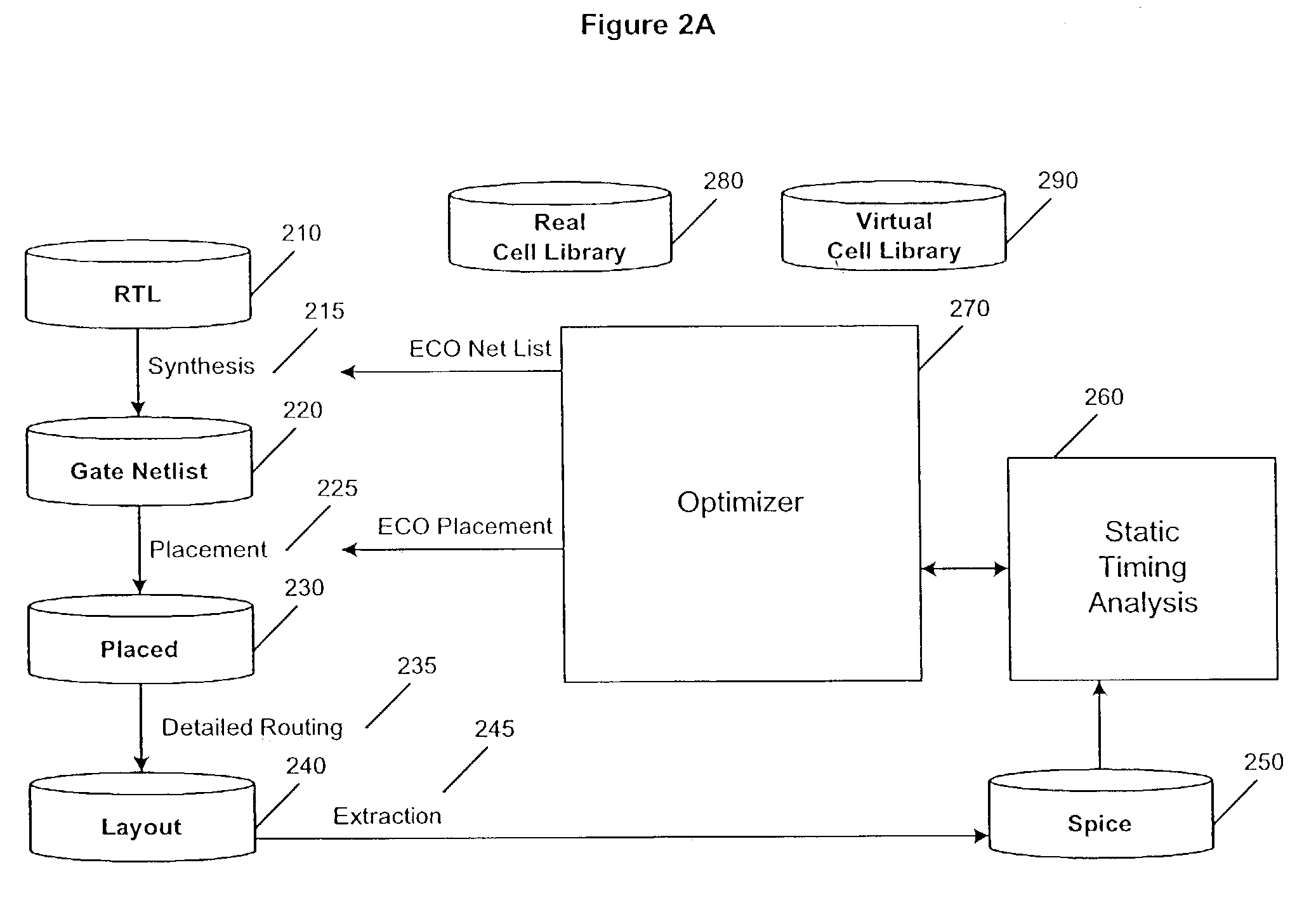
Optimization of circuit designs using a continuous spectrum of library cells
InactiveUS7107551B1Minimal impactSimple designMulti-objective optimisationSoftware simulation/interpretation/emulationVirtual cellSoftware engineering
A method and apparatus for optimizing a circuit design using a library of cells in which a continuous spectrum of cells are provided. A library containing real and virtual cells is used so that cells can be selected across a wide spectrum of a design parameter, such as drive strength. The cells are provided in discrete steps small enough that the effect of having a continuous spectrum of cells is achieved. After optimization, only the cells finally selected need be actually synthesized, and when these constitute a small percentage of the total number of cells, the impact to library size and final placement and routing is minimized. Thus the ability to optimize across a continuous spectrum is achieved while preserving a cell library based design flow.
Owner:ARM INC
System and method of securing networks against applications threats
InactiveUS20080047009A1Easy to deployMinimal impactMemory loss protectionError detection/correctionWeb applicationInternet privacy
A system and method for protection of Web based applications are described. A Web application security system is included within a computer network to monitor traffic received from a wide area network, such as the Internet, and determine if there is a threat to the Web application. The Web application security system monitors web traffic in a non-inline configuration and identifies any anomalous traffic against a profile that identifies acceptable behavior of a user of the application. Any anomalous traffic is analyzed and appropriate protective action is taken to secure the Web application against an attack.
Owner:TRUSTWAVE HOLDINGS
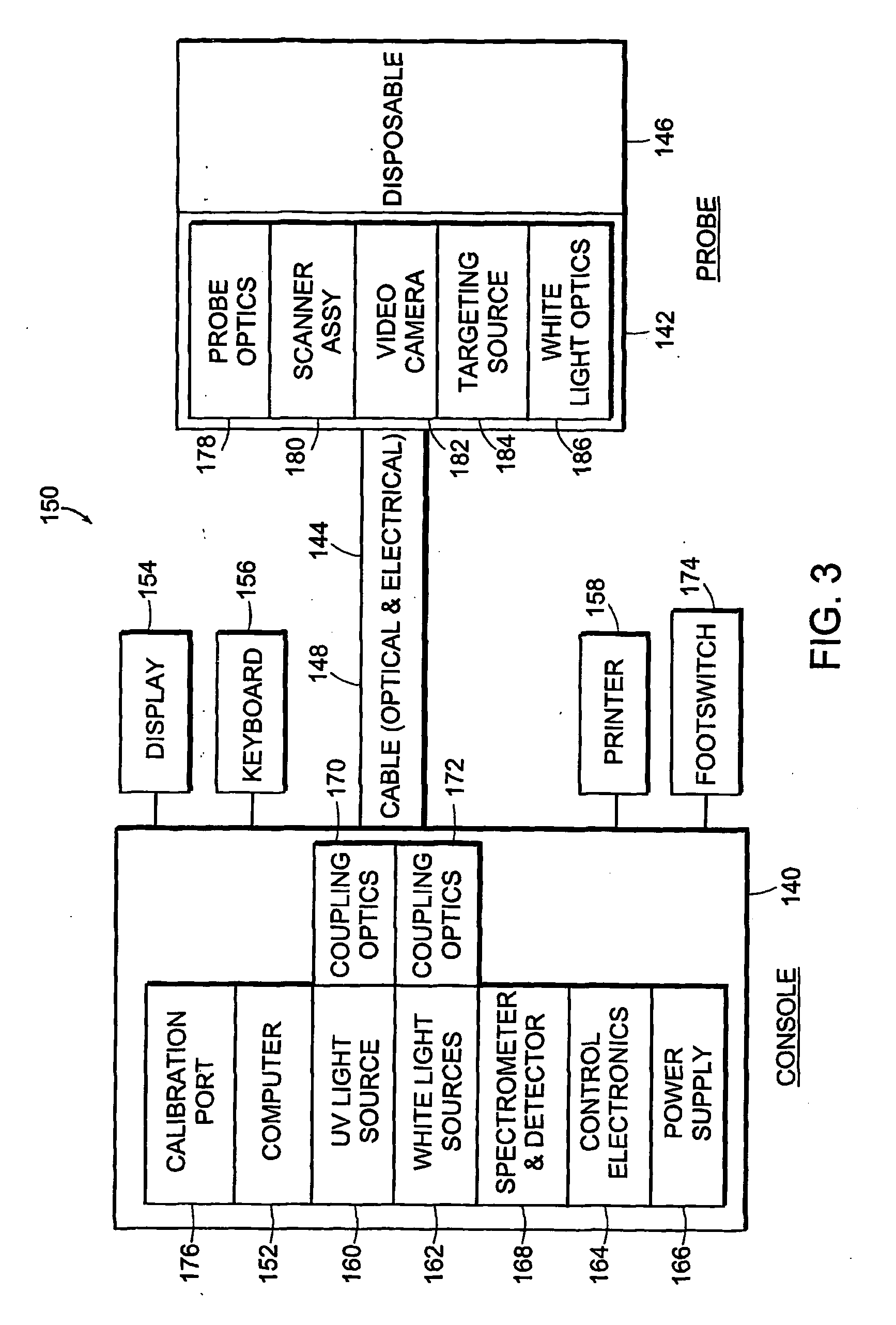
Systems for identifying, displaying, marking, and treating suspect regions of tissue
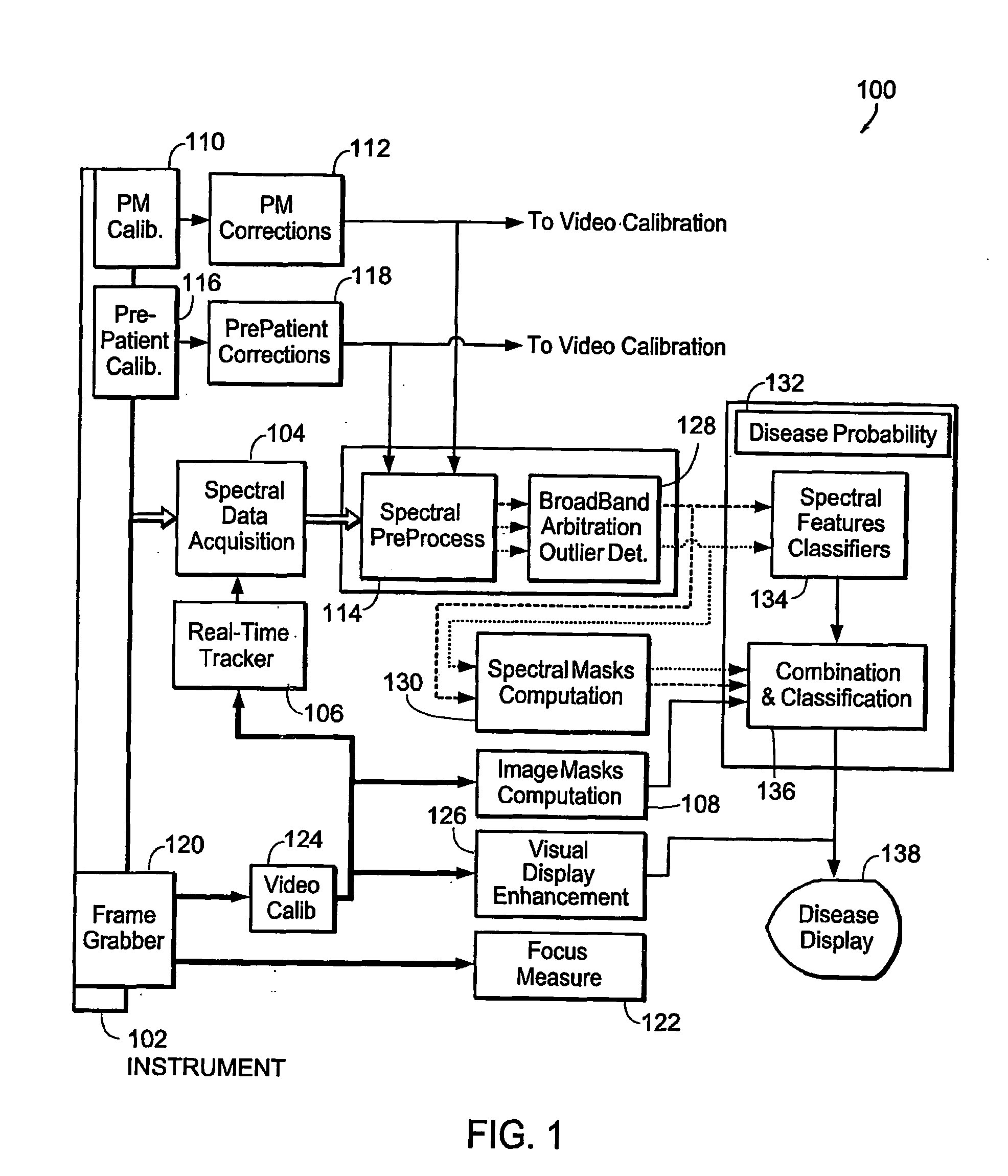
InactiveUS20060013454A1Minimal impactFacilitates minimally-invasive treatmentImage enhancementImage analysisReflectance spectroscopyFluorescence spectra
The invention provides systems for automatically localizing areas of disease within a tissue sample using fluorescence spectra, reflectance spectra, and video images obtained from the sample. The invention further provides systems for displaying, marking, and treating the identified areas so that healthy surrounding tissue suffers minimal impact upon treatment and / or excision of the diseased tissue. The invention facilitates minimally-invasive treatment by accurately directing treatment to only those areas that are identified as diseased.
Owner:MEDISPECTRA
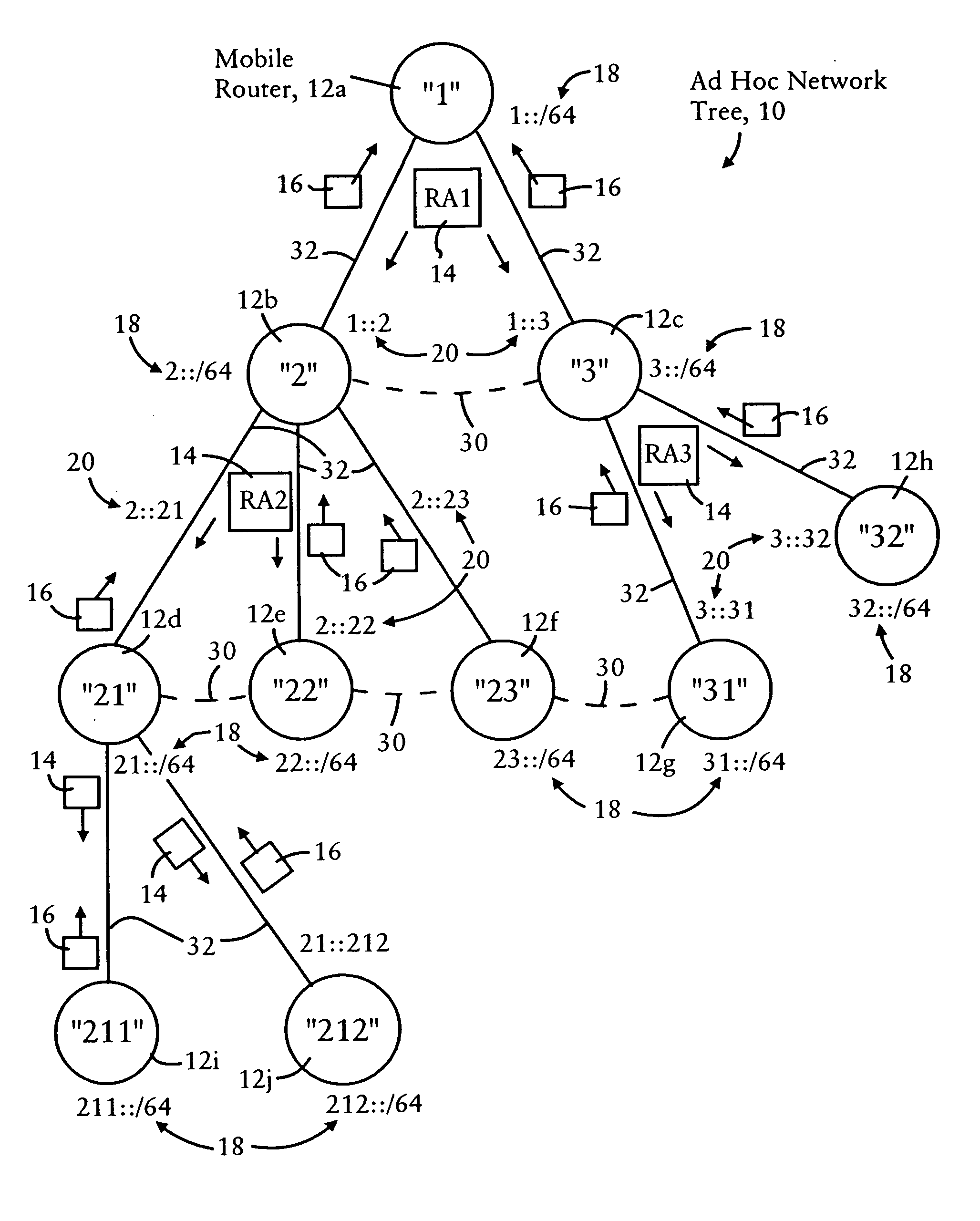
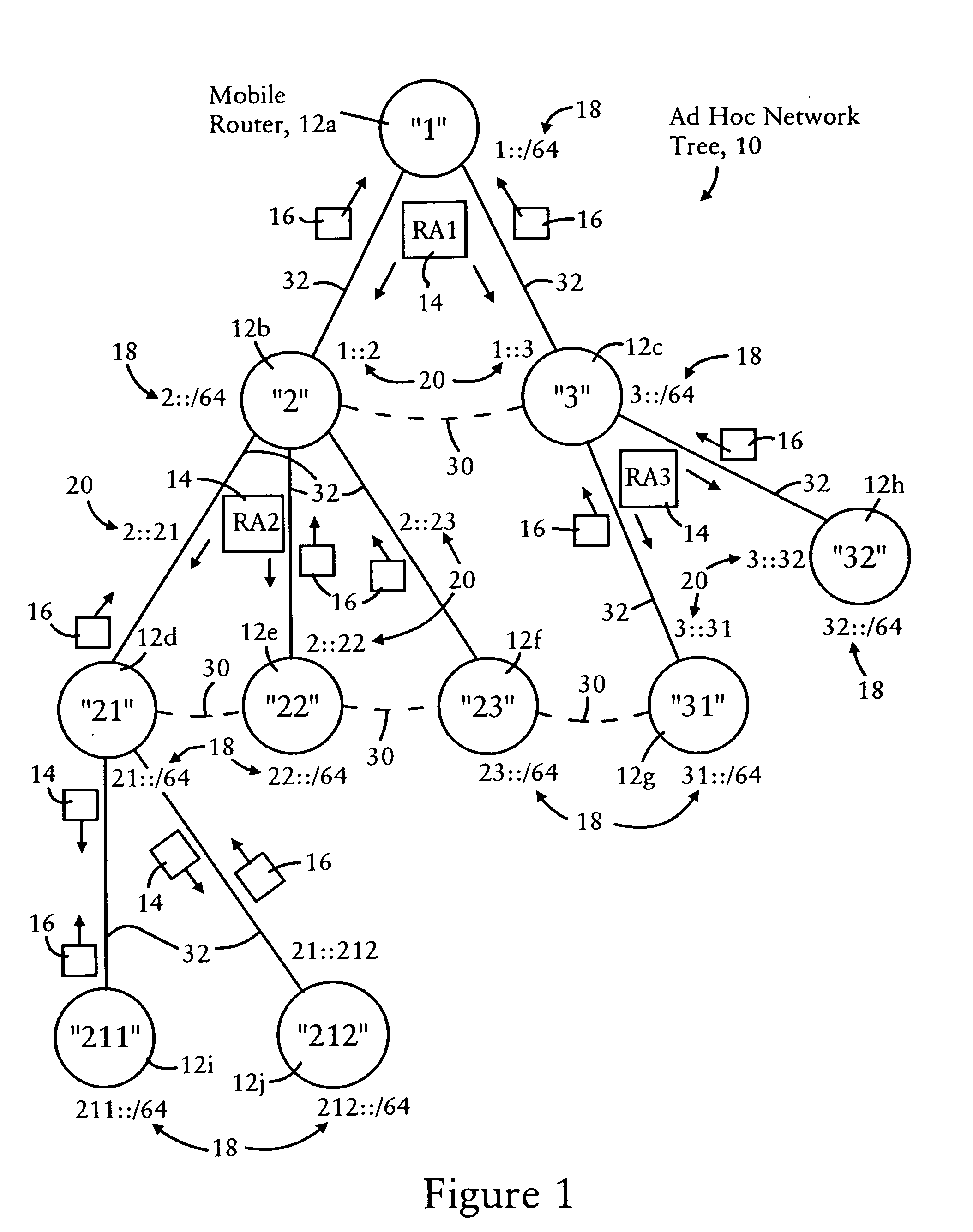
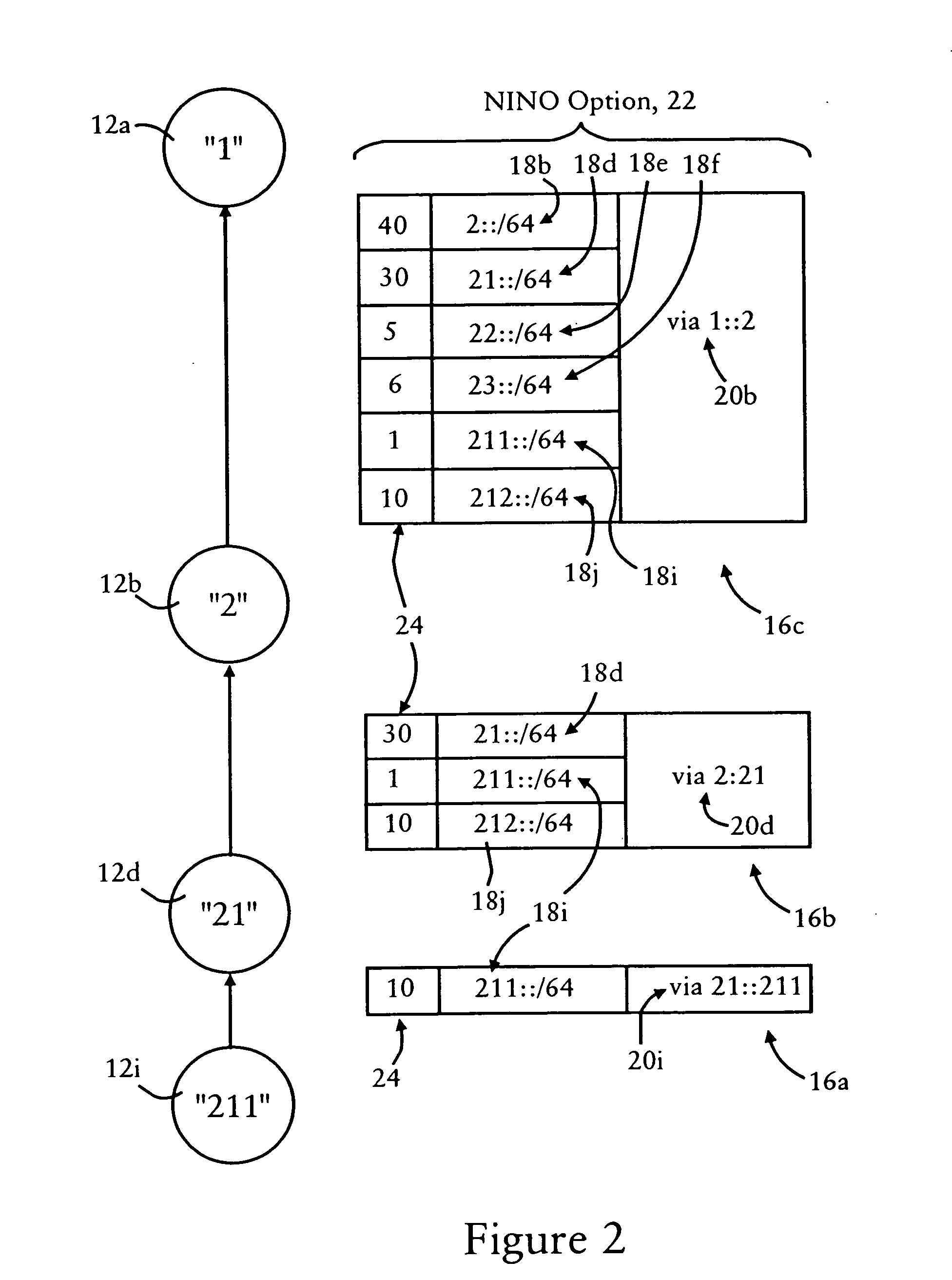
Arrangement for providing optimized connections between peer routers in a tree-based ad hoc mobile network
InactiveUS20060227724A1Reduce necessityAvoid congestionError preventionFrequency-division multiplex detailsEngineeringSelf-organizing network
Mobile routers in a tree-based network topology with a single clusterhead in an ad hoc network establish connectivity based on each attached mobile router sending a neighbor advertisement message to an attachment mobile router via a corresponding egress interface. Any neighbor advertisement message received by a mobile router is used to identify specified network prefixes that are reachable via the source of the neighbor advertisement message. Each attached mobile router outputs to its attachment router another neighbor advertisement message that specifies the network prefix used by the mobile router, and the specified network prefixes from its attached mobile routers. The mobile router also identifies peer mobile routers having the same depth, and selectively shares limited routing information with the peer routers, enabling the mobile router to bypass the clusterhead and reach remote prefixes via the peer routers without burdening the tree.
Owner:CISCO TECH INC
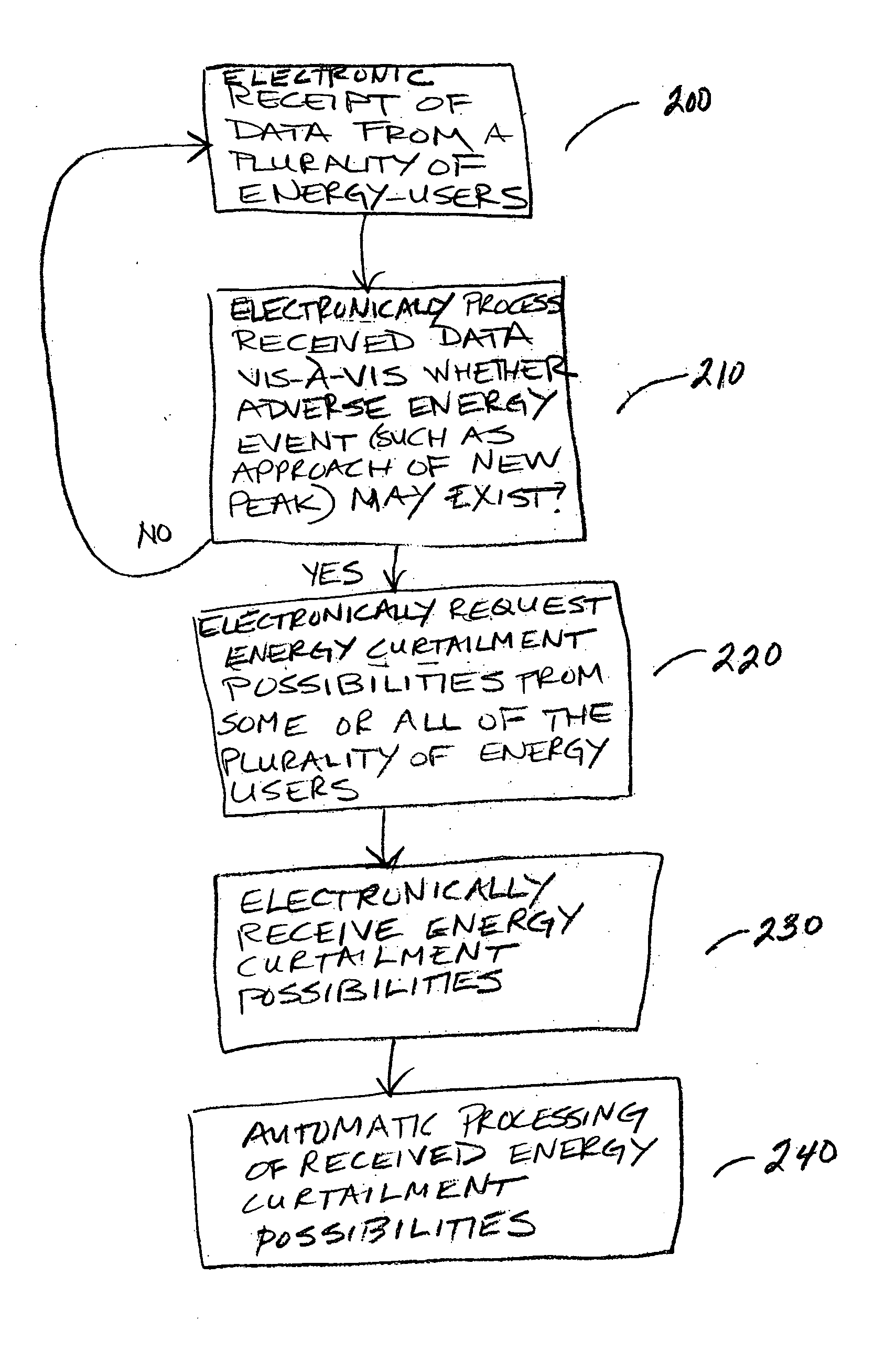
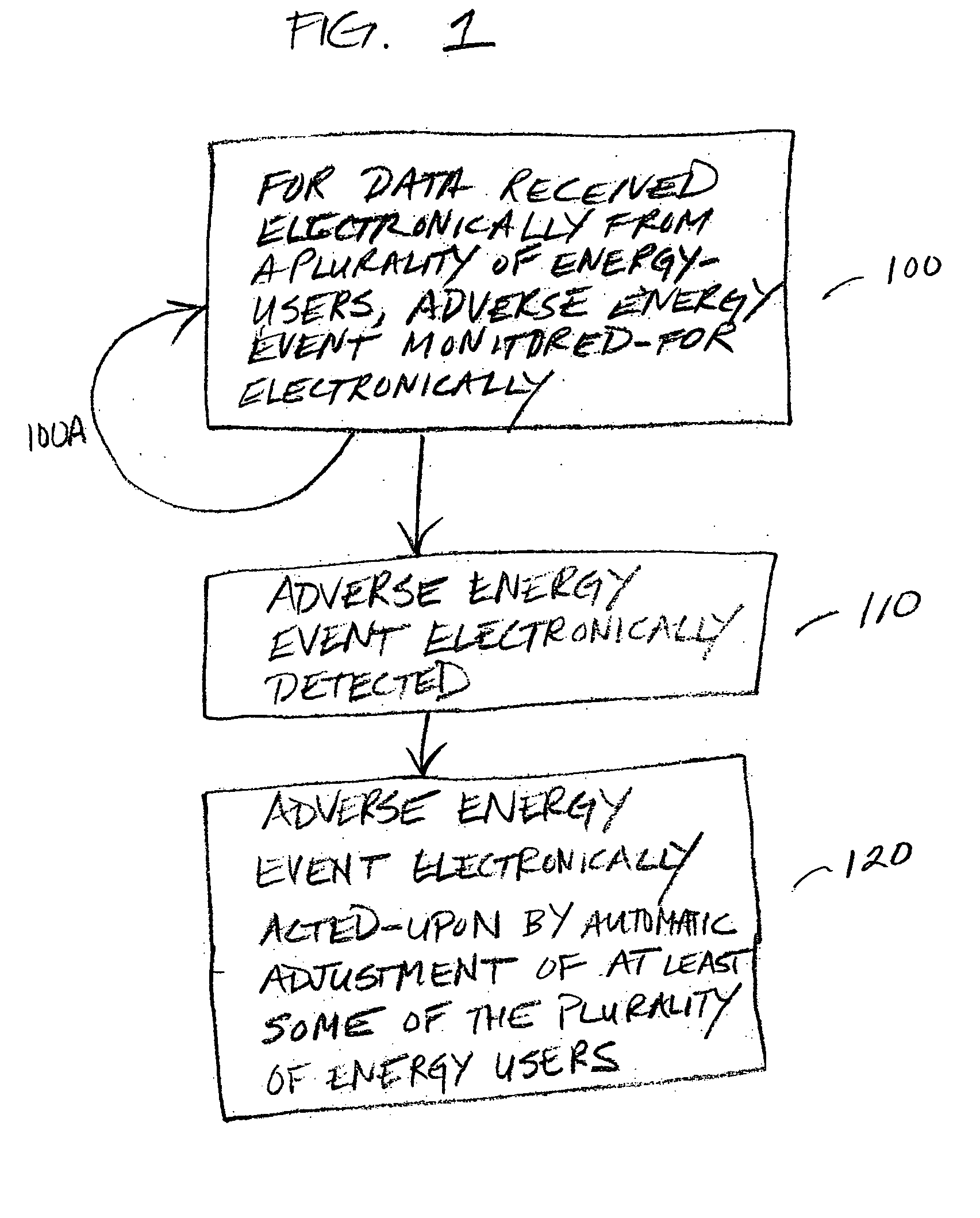
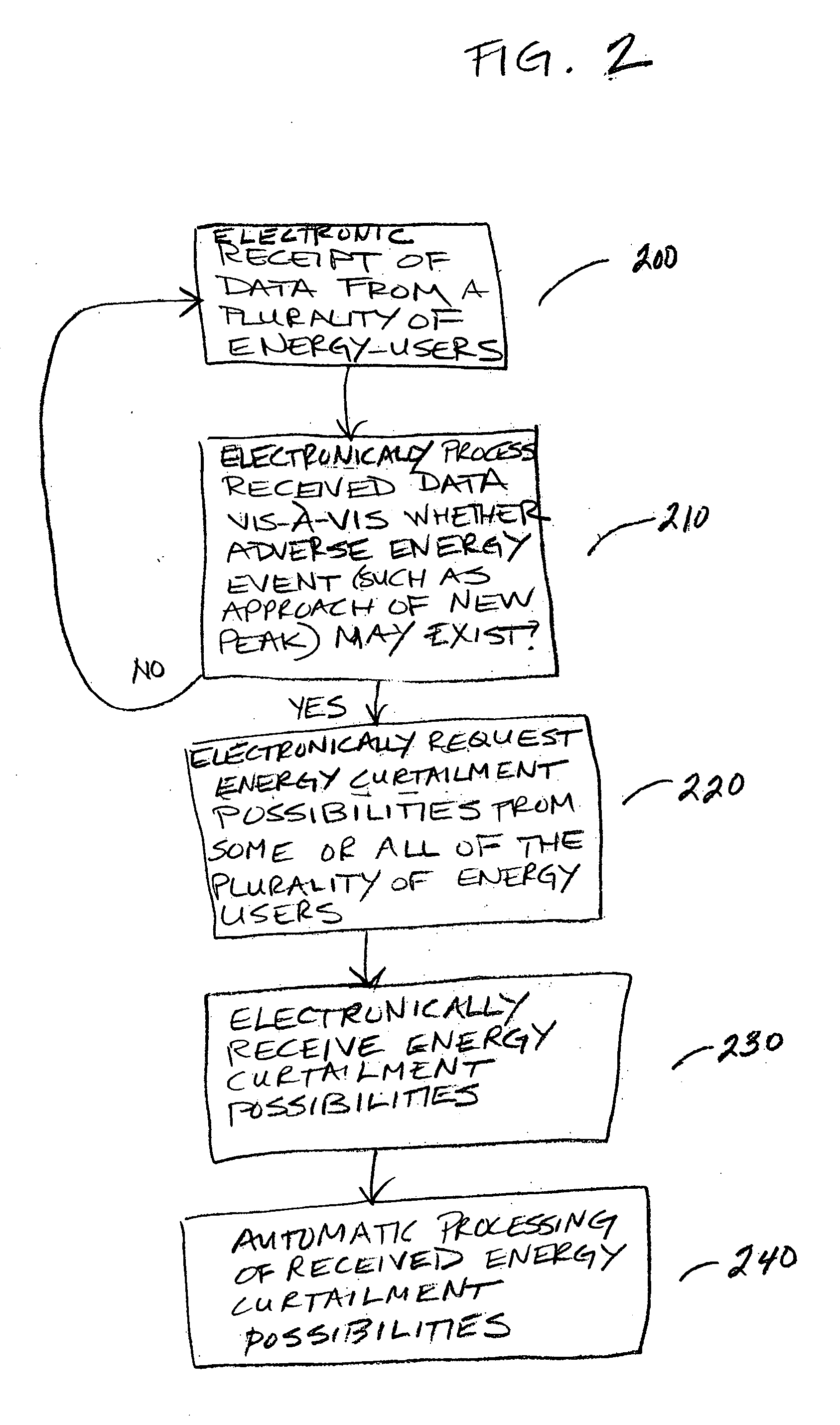
Automatic energy management and energy consumption reduction, especially in commercial and multi-building systems
InactiveUS20050038571A1Minimal impactLevel controlLoad forecast in ac networkReal time analysisNerve network
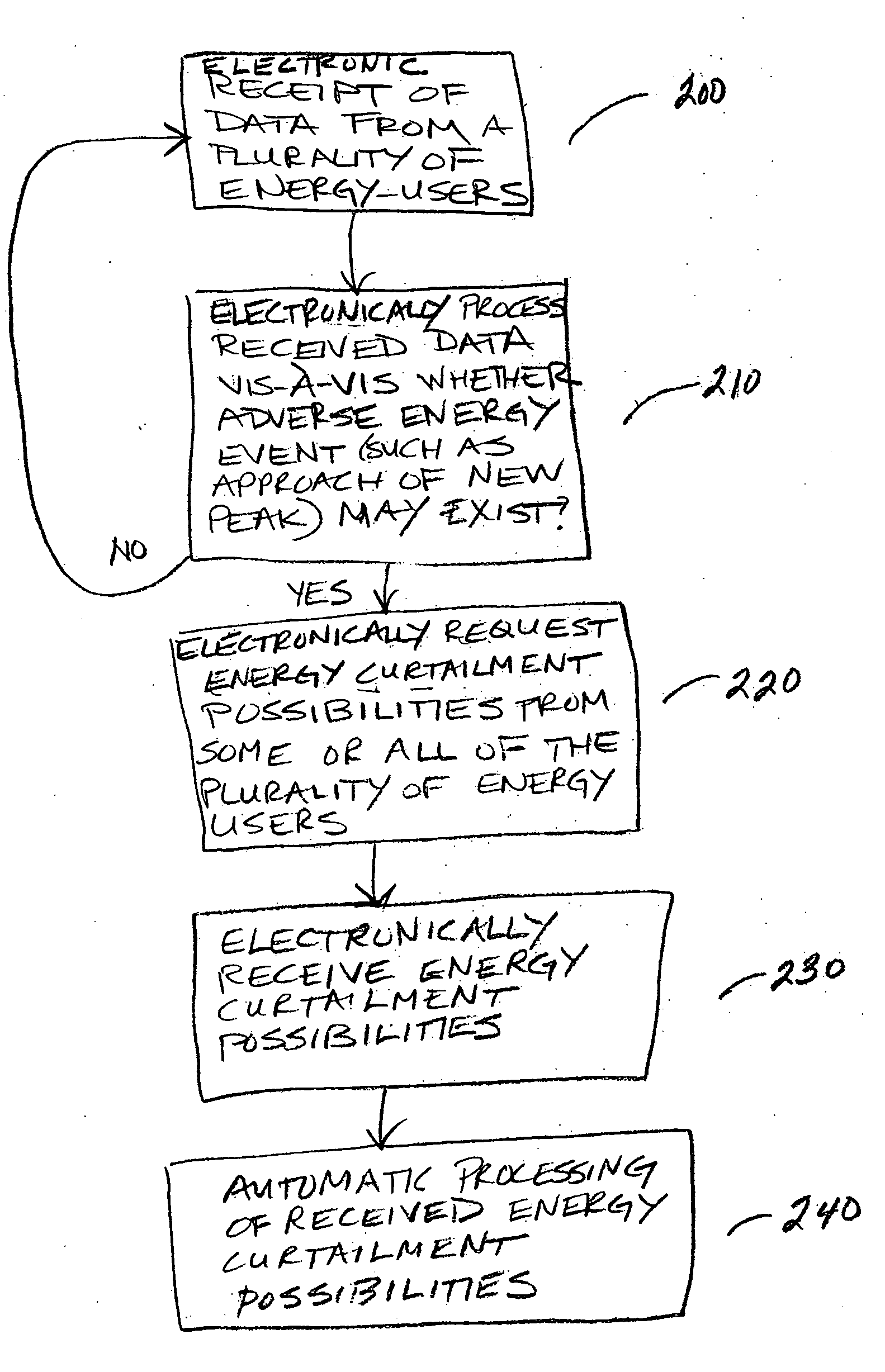
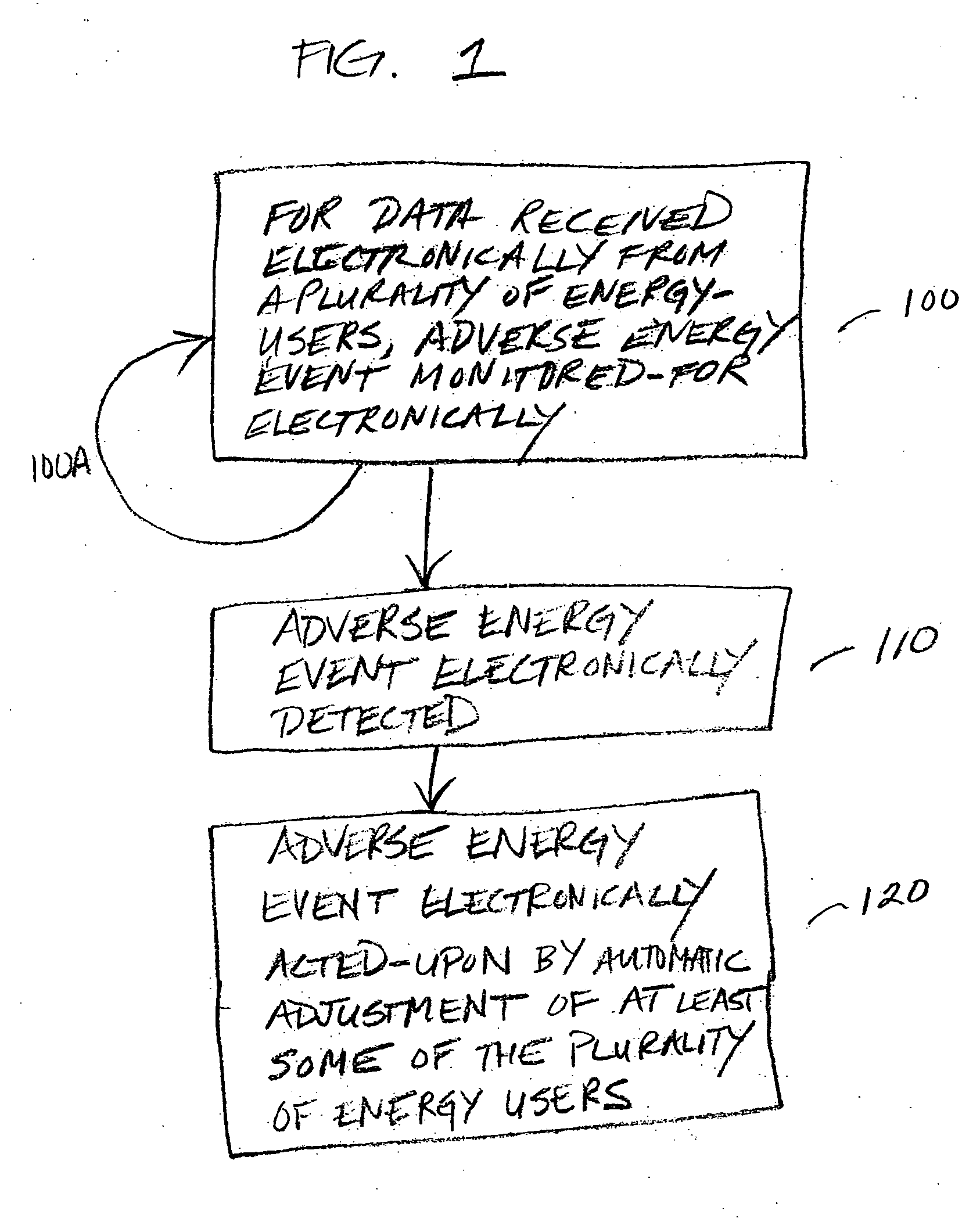
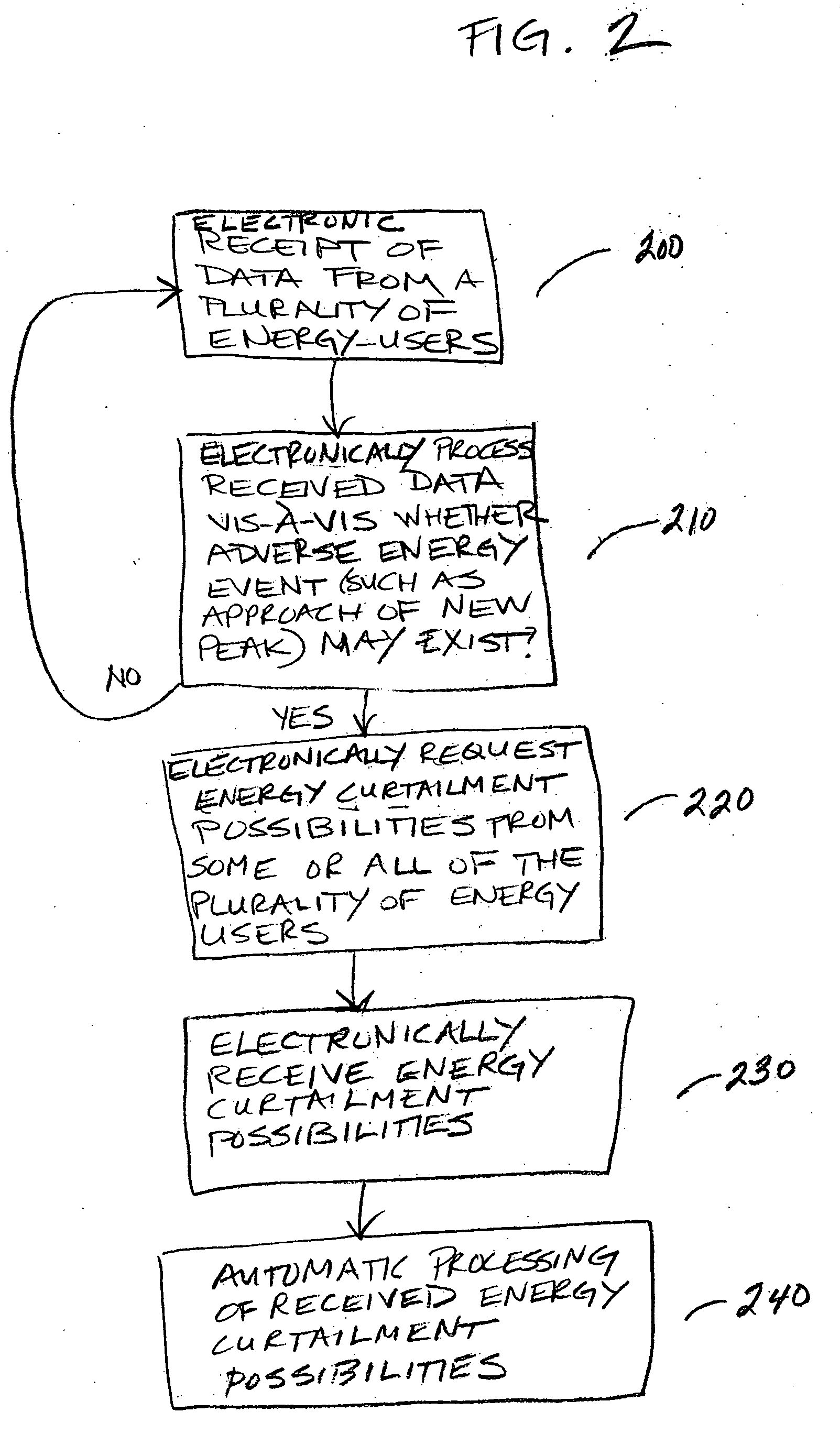
Automatic energy management is provided, in even the most complex multi-building system. The necessity of a human operator for managing energy in a complex, multi-building system is reduced and even eliminated. Computer-based monitoring and computer-based recognition of adverse energy events (such as the approach of a new energy peak) is highly advantageous in energy management. Immediate automatic querying of energy users within a system of buildings for energy curtailment possibilities is provided. Such immediate, automatic querying may be answered by the energy users through artificial intelligence and / or neural network technology provided to or programmed into the energy users, and the queried energy users may respond in real-time. Those real-time computerized responses with energy curtailment possibilities may be received automatically by a data processing facility, and processed in real-time. Advantageously, the responses from queried energy users with energy curtailment possibilities may be automatically processed into a round-robin curtailment rotation which may be implemented by a computer-based control system. Thus, impact on occupants is minimized, and energy use and energy cost may be beneficially reduced in an intelligent, real-time manner. The invention also provides for early-recognition of impending adverse energy events, optimal response to a particular energy situation, real-time analysis of energy-related data, etc.
Owner:INTERCAP CAPITAL PARTNERS
Discontinuous reception operation with additional wake-up opportunities
ActiveUS20150003311A1Short response timeMinimal impactPower managementTransmission systemsLongest cycleShort length
The invention relates to methods for improving the DRX operation of a UE by introducing an additional DRX wake-up cycle, which runs in parallel to the short and / or long DRX cycle. The DRX wake-up cycle defines time intervals after which the UE starts monitoring the PDCCH for a wake-up duration of time; the UE does not perform any other operation during the wake-up duration apart from monitoring the PDCCH. The time intervals of the wake-up cycle between the wake-up durations are preferably shorter than the one of the DRX long cycle, and may have the same or a shorter length than the ones of the DRX short cycle. The wake-up duration may be as long as the on-duration of the DRX short / long cycle, or may be preferably much shorter, such as only one or a few subframes.
Owner:APPLE INC
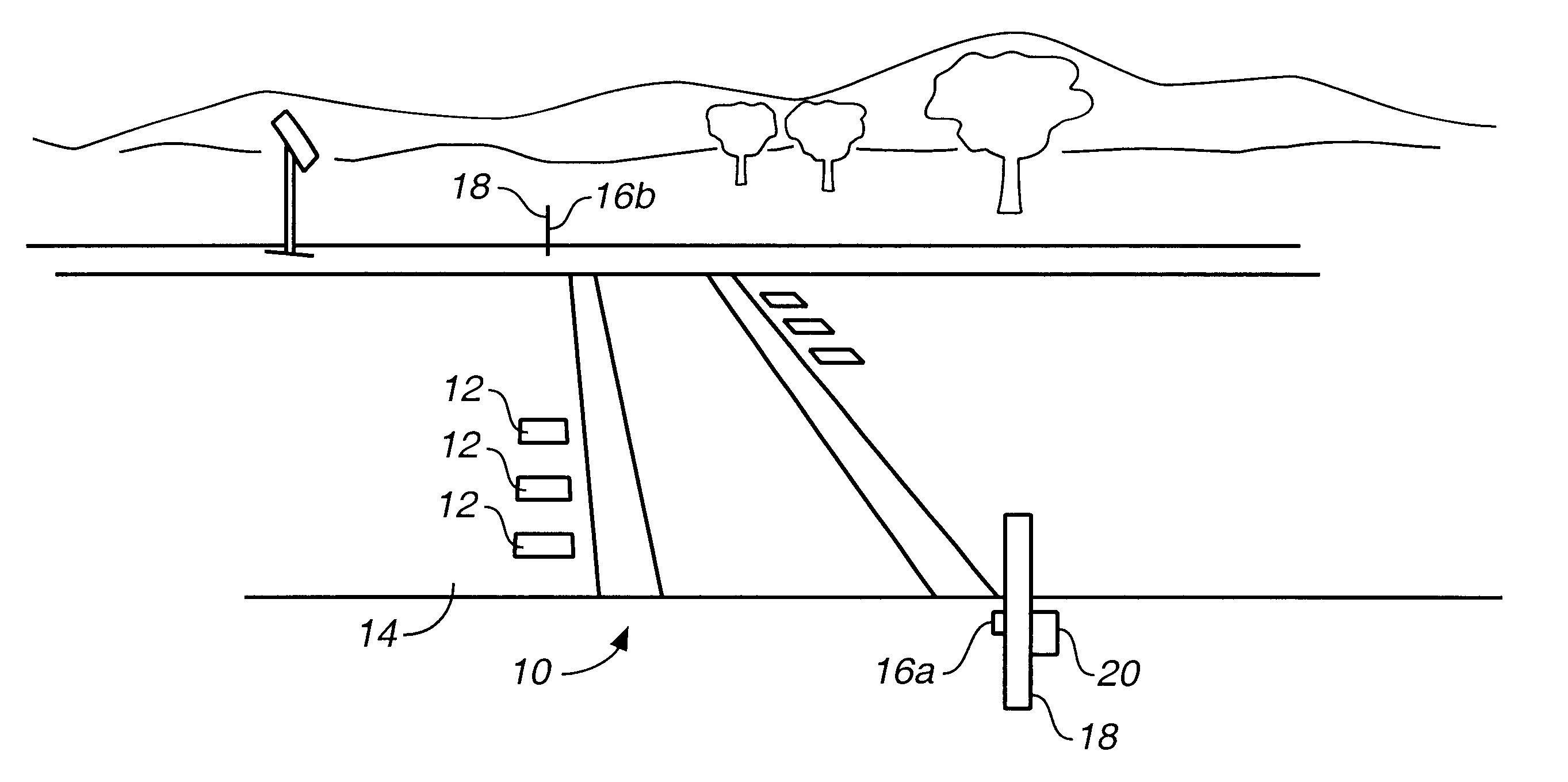
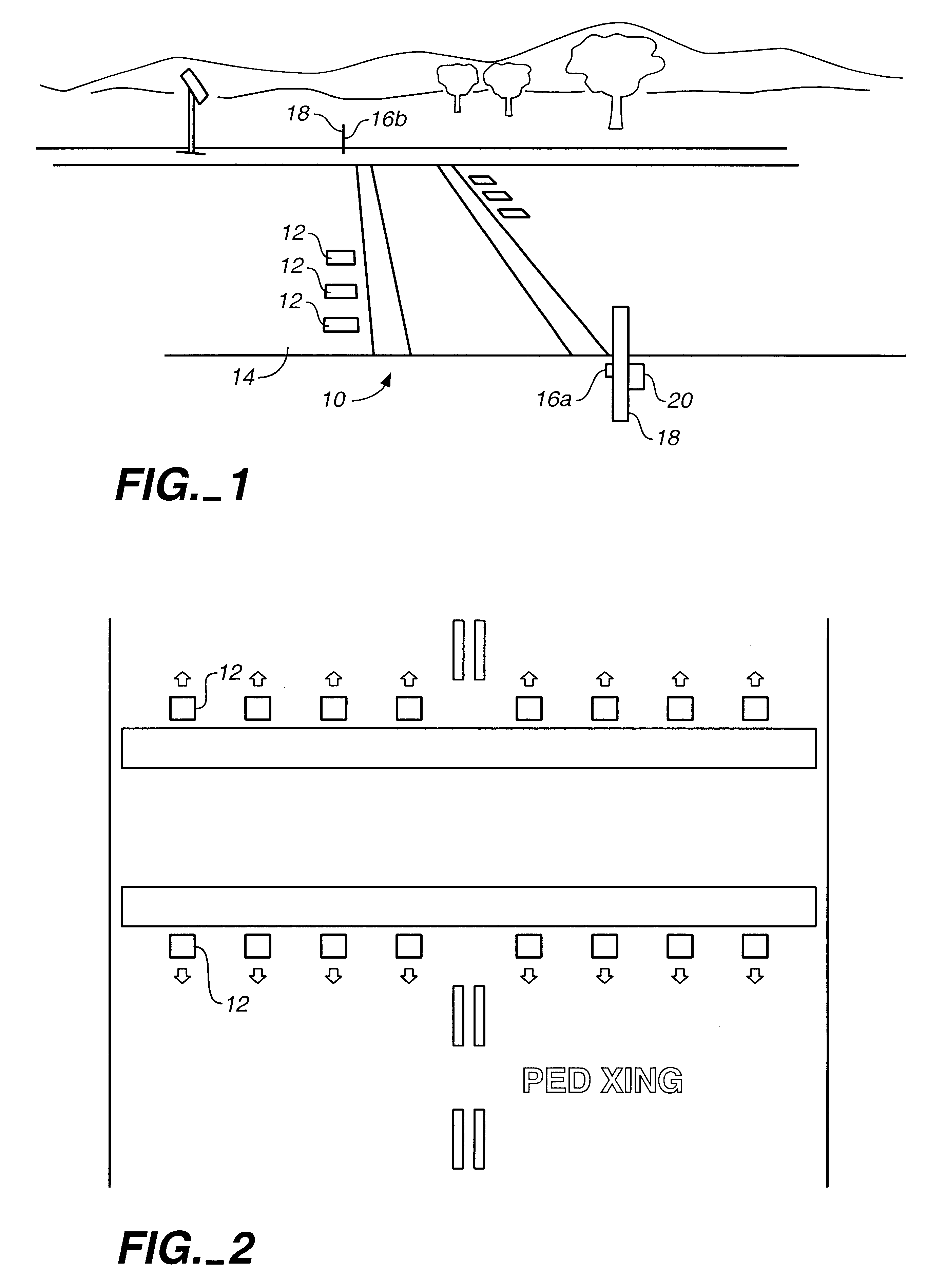
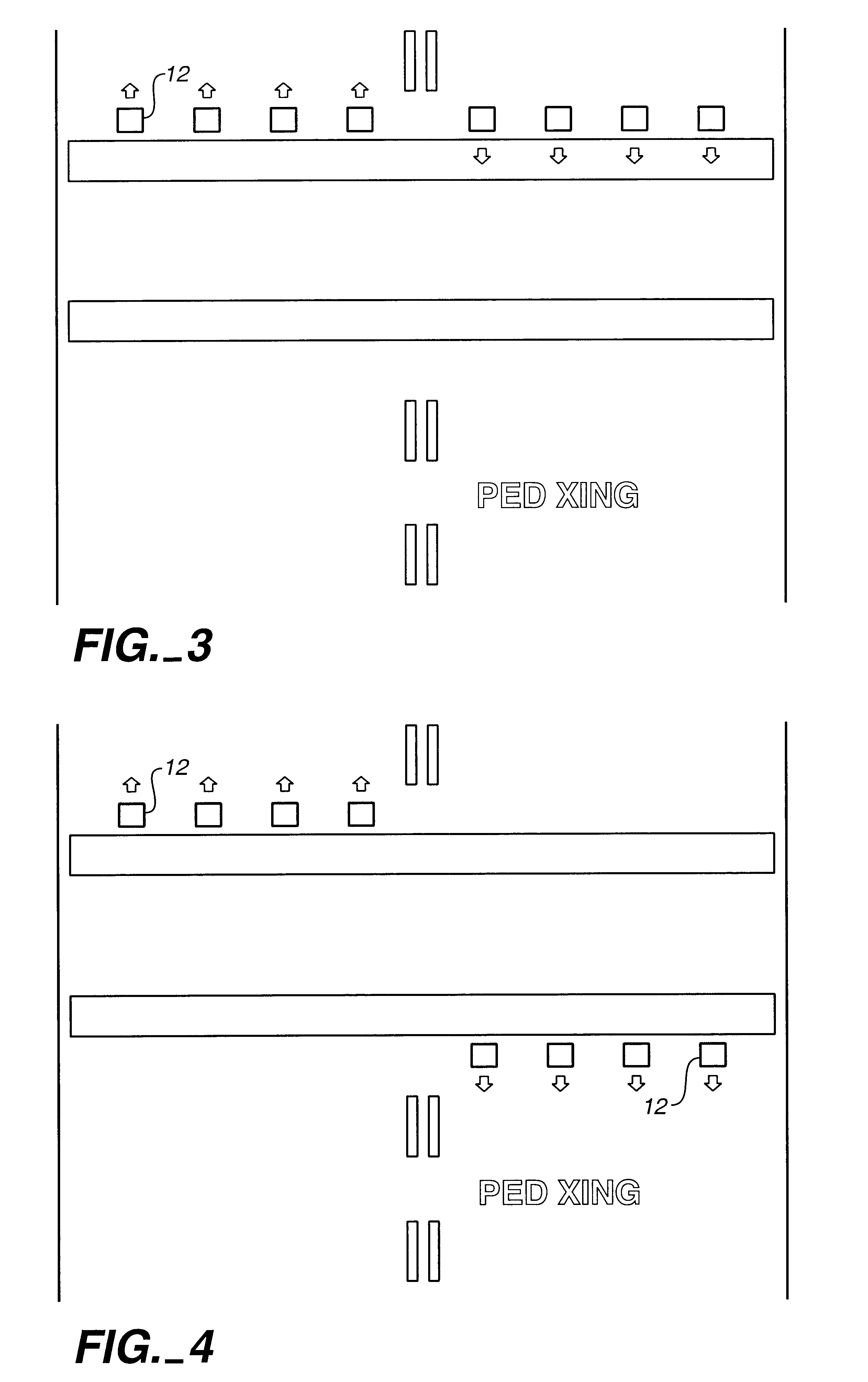
Pedestrian crosswalk signal apparatus-pedestrian crosswalk
InactiveUS6384742B1Low costEasy to installControlling traffic signalsPortable emergency signal deviceSurface mountingWarning system
A traffic warning system which alerts approaching vehicle traffic to the presence of a pedestrian in a crosswalk. The system includes a plurality of surface mounted lights partially embedded in and placed across a roadway. The lights are activated by the pedestrian, either by manual switch or by a sensor, before he enters the crosswalk. Once activated, the flashing lights warn drivers of approaching vehicles that the pedestrian may have entered the crosswalk, and that caution should be exercised.
Owner:LIGHTGUARD SYST
Systems and methods for secure client applications
ActiveUS7694328B2Minimize impactMinimal impactDigital data processing detailsUser identity/authority verificationSecurity solutionVirtualization
An innovative security solution which separates a client into a Protected Context, which is the real files and resources of the client, and an Isolated Context, which is a restricted execution environment which makes use of virtualized resources to execute applications and modify content in the Isolated Context, without allowing explicit access to the resources in the Protected Context. The solution further consolidates user interfaces to allow users to seamlessly work with content in both contexts, and provide a visual indication of which display windows are rendered from content executed in the Isolated Context.
Owner:GOOGLE LLC
Automatic energy management and energy consumption reduction, especially in commercial and multi-building systems
InactiveUS20050043862A1Minimal impactMechanical power/torque controlLevel controlReal time analysisNew energy
Automatic energy management is provided, in even the most complex multi-building system. The necessity of a human operator for managing energy in a complex, multi-building system is reduced and even eliminated. Computer-based monitoring and computer-based recognition of adverse energy events (such as the approach of a new energy peak) is highly advantageous in energy management. Immediate automatic querying of energy users within a system of buildings for energy curtailment possibilities is provided. Such immediate, automatic querying may be answered by the energy users through artificial intelligence and / or neural network technology provided to or programmed into the energy users, and the queried energy users may respond in real-time. Those real-time computerized responses with energy curtailment possibilities may be received automatically by a data processing facility, and processed in real-time. Advantageously, the responses from queried energy users with energy curtailment possibilities may be automatically processed into a round-robin curtailment rotation which may be implemented by a computer-based control system. Thus, impact on occupants is minimized, and energy use and energy cost may be beneficially reduced in an intelligent, real-time manner. The invention also provides for early-recognition of impending adverse energy events, optimal response to a particular energy situation, real-time analysis of energy-related data, etc.
Owner:INTERCAP CAPITAL PARTNERS
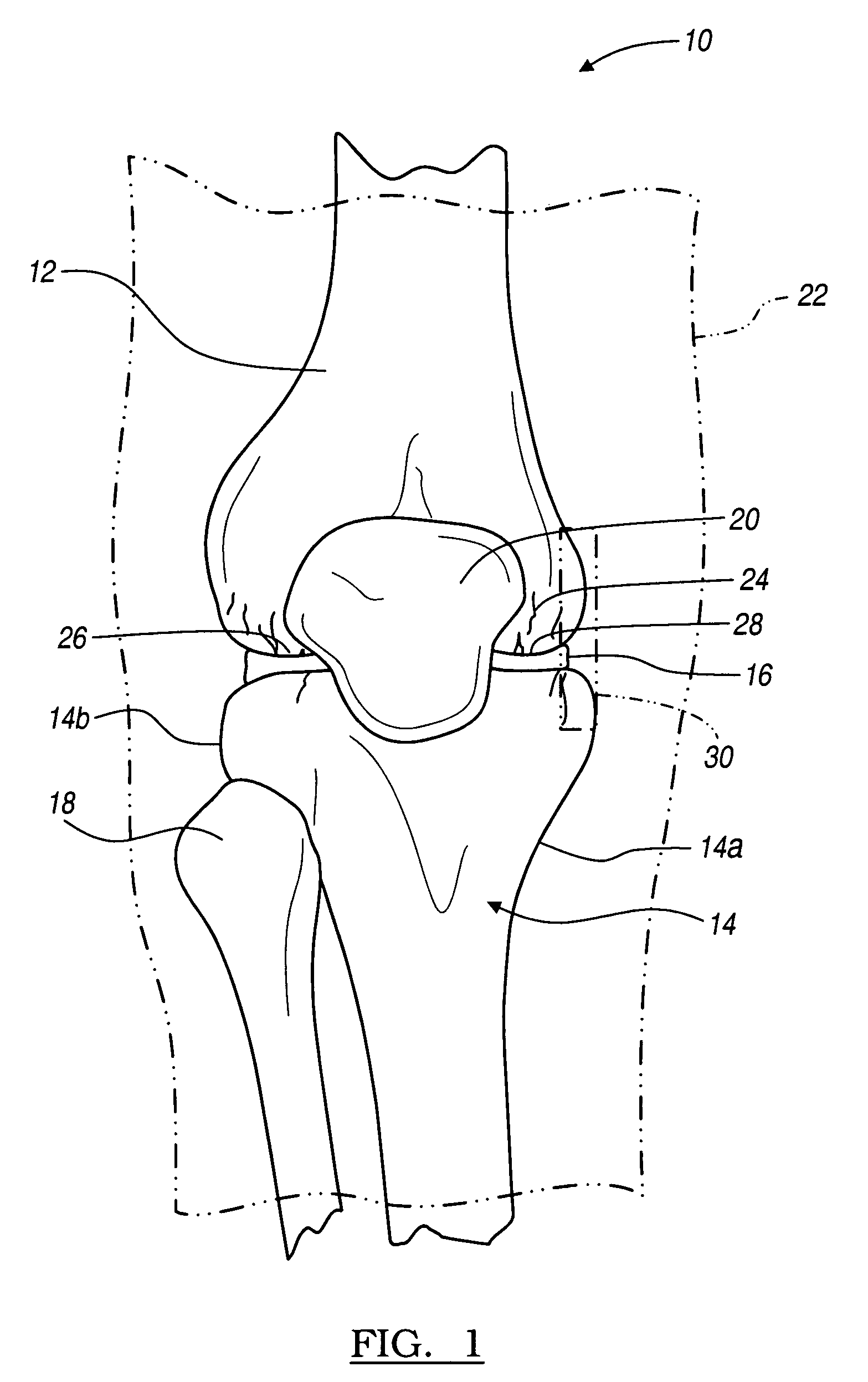
Instrumentation for knee resection
InactiveUS7789885B2Minimal impactMinimally invasivelyDiagnosticsNon-surgical orthopedic devicesKnee JointBiomedical engineering
Owner:BIOMET MFG CORP
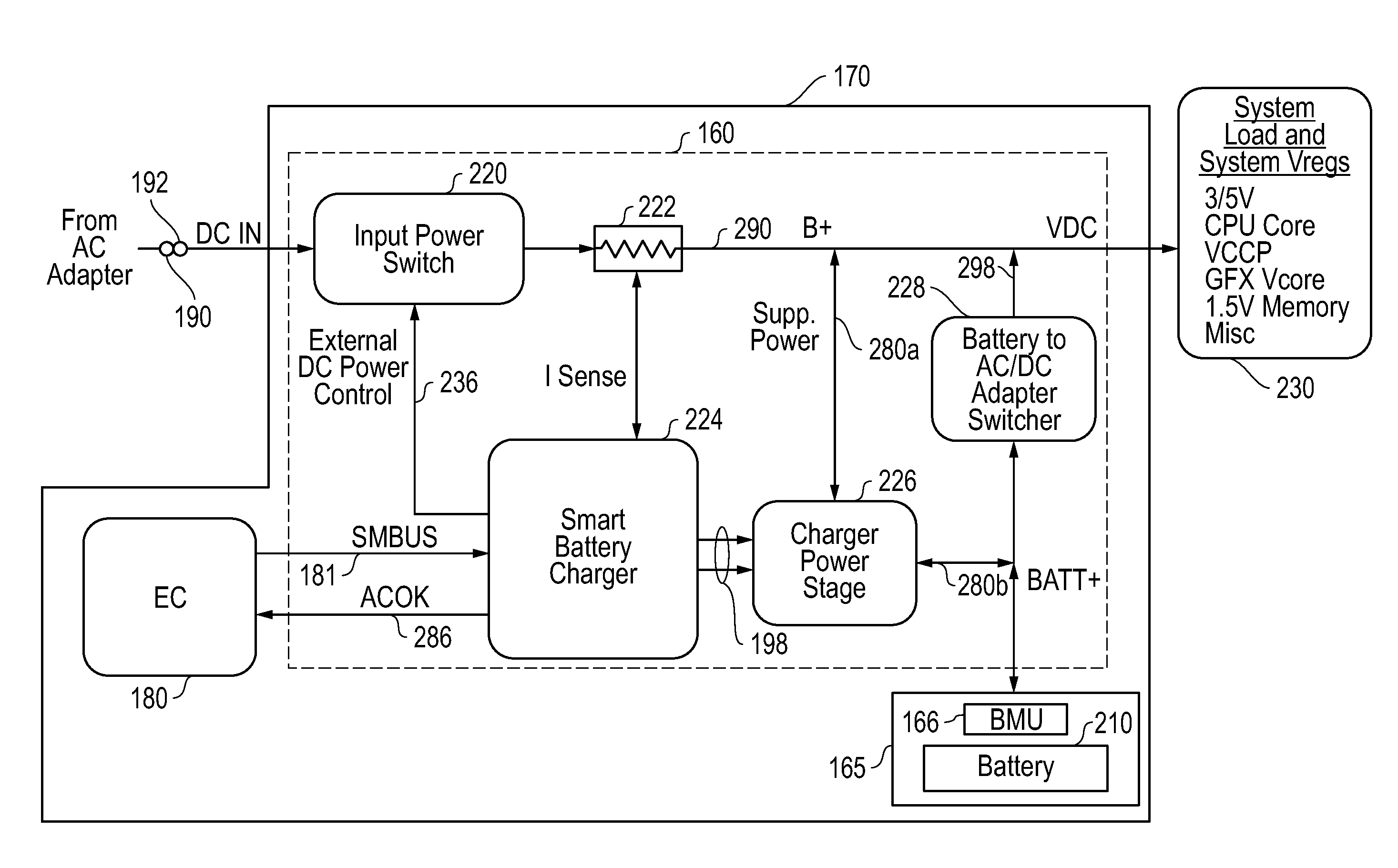
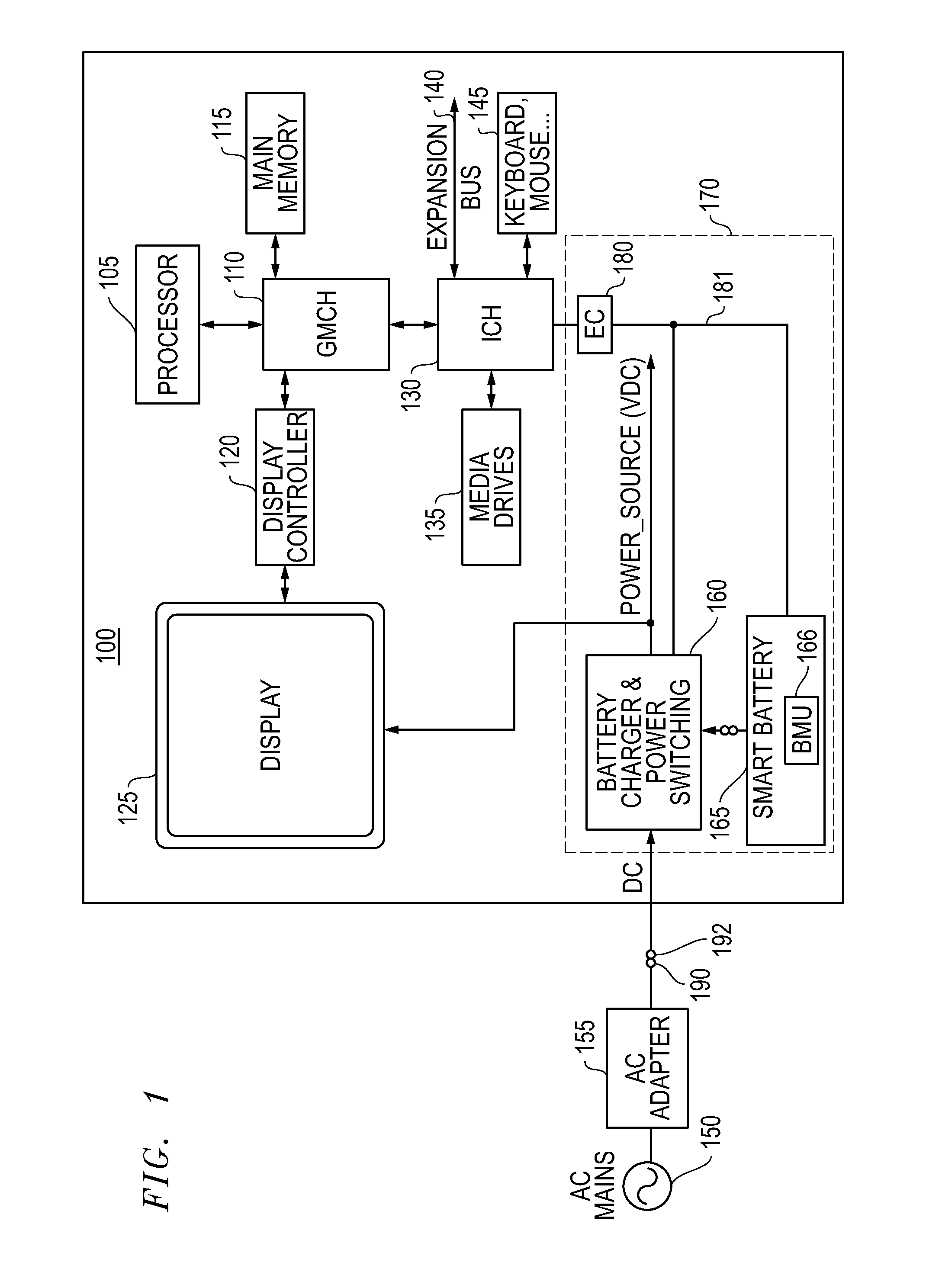
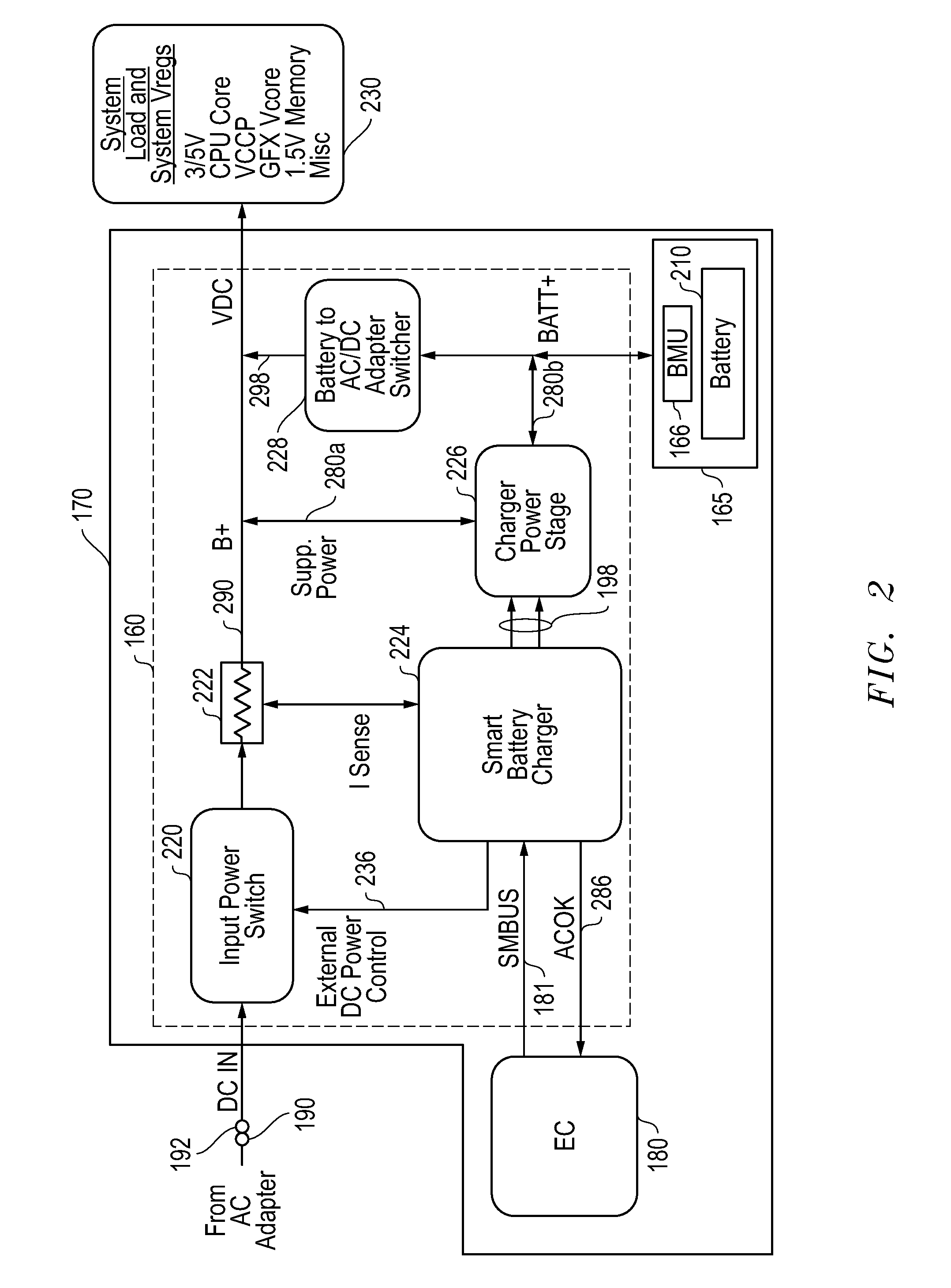
Systems and methods for providing supplemental power to battery powered information handling systems
ActiveUS20130339757A1Raise countMinimize impactVolume/mass flow measurementPower supply for data processingBattery chargeElectrical battery
Systems and methods are disclosed for providing supplemental power to a battery powered information handling systems. The disclosed systems and methods may be implemented to intelligently control the selected use of supplemental power so as to reduce or substantially prevent an increase in battery usage cycle count by only allowing use of supplemental power above a given minimum supplemental battery charge level threshold. Battery cycle count may be further enhanced by only again allowing recharging of the system battery pack when its charge level drops below the minimum supplemental battery charge level threshold, and then recharging to a maximum recharge battery charge level threshold which also may be selectable by a user and / or provider of the information handling system.
Owner:DELL PROD LP
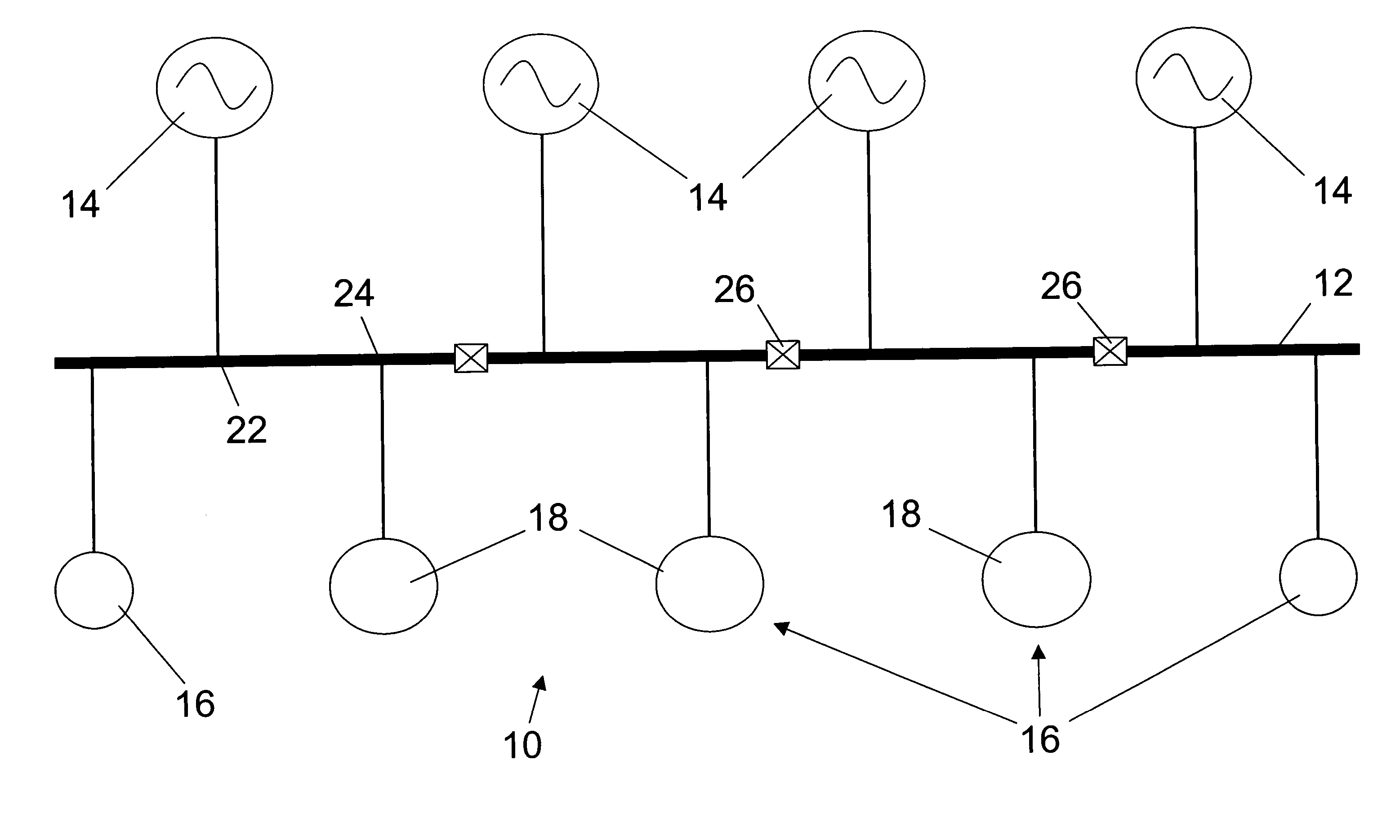
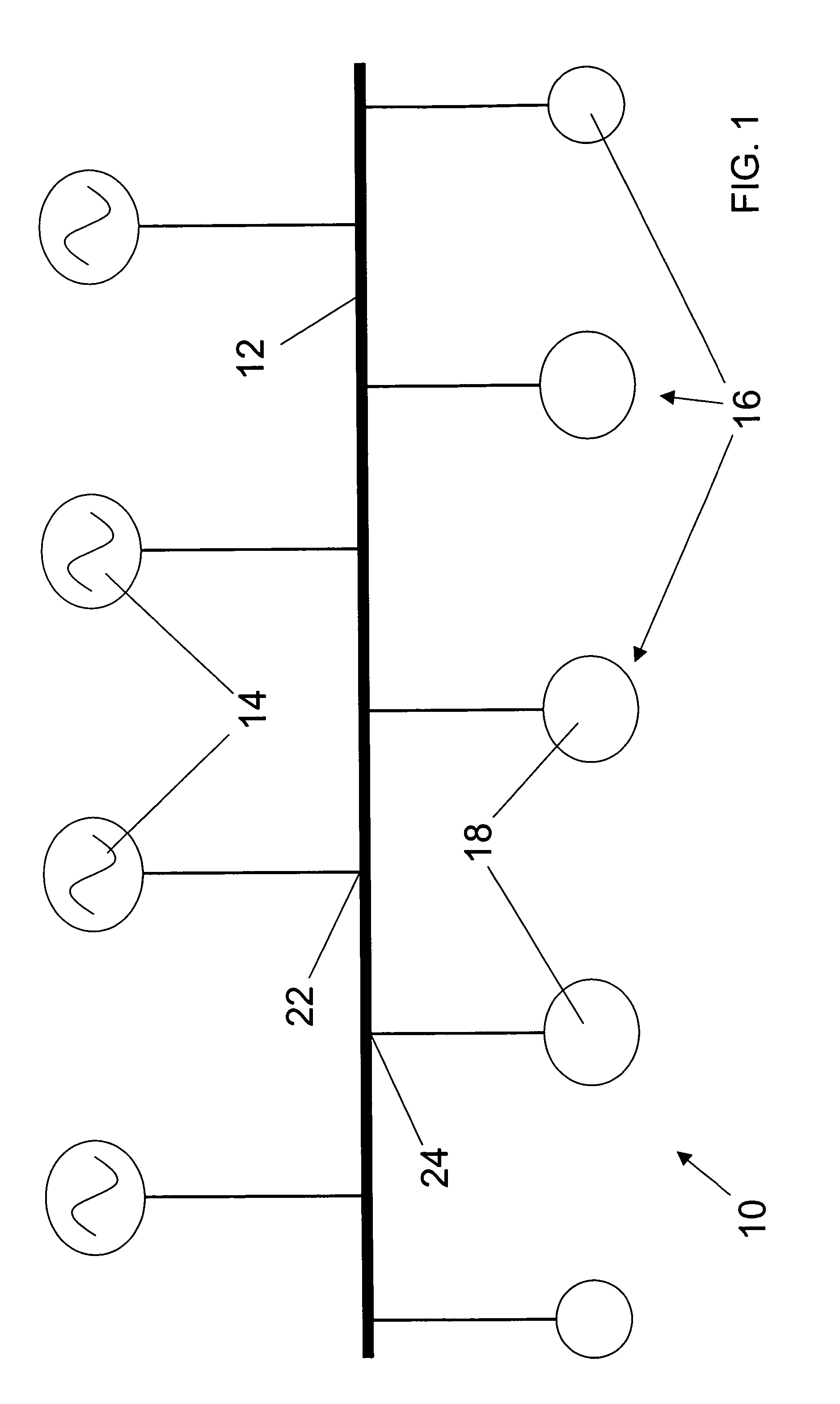
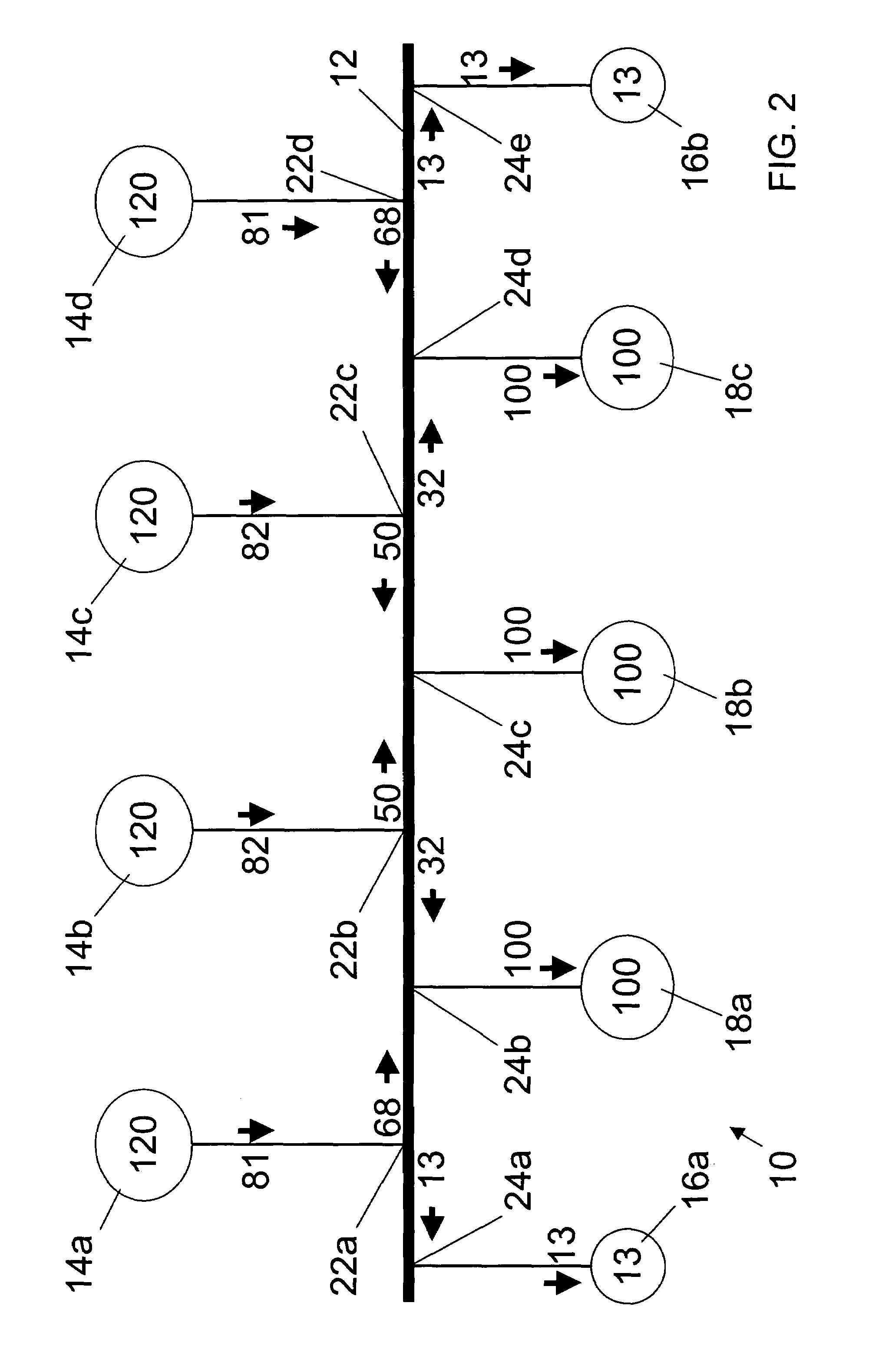
Stand-alone electrical system for large motor loads
ActiveUS7388303B2Sufficient rateMinimal impactSolidificationLiquefactionElectric power systemDistributed power
An electrical power system that can be used to interconnect a plurality of generators to a plurality to loads while being rated at less than a total power consumed. The system is preferably used to distribute power for a Liquefied Natural Gas (LNG) facility. The system broadly comprises a primary bus connected between the generators and the loads, such as electrical compressor motors used in the LNG facility. The generators and the loads are arranged along the primary bus in order to distribute the power from the generators to the loads, without overloading the primary bus.
Owner:CONOCOPHILLIPS CO
System And Method For Removing Contaminants
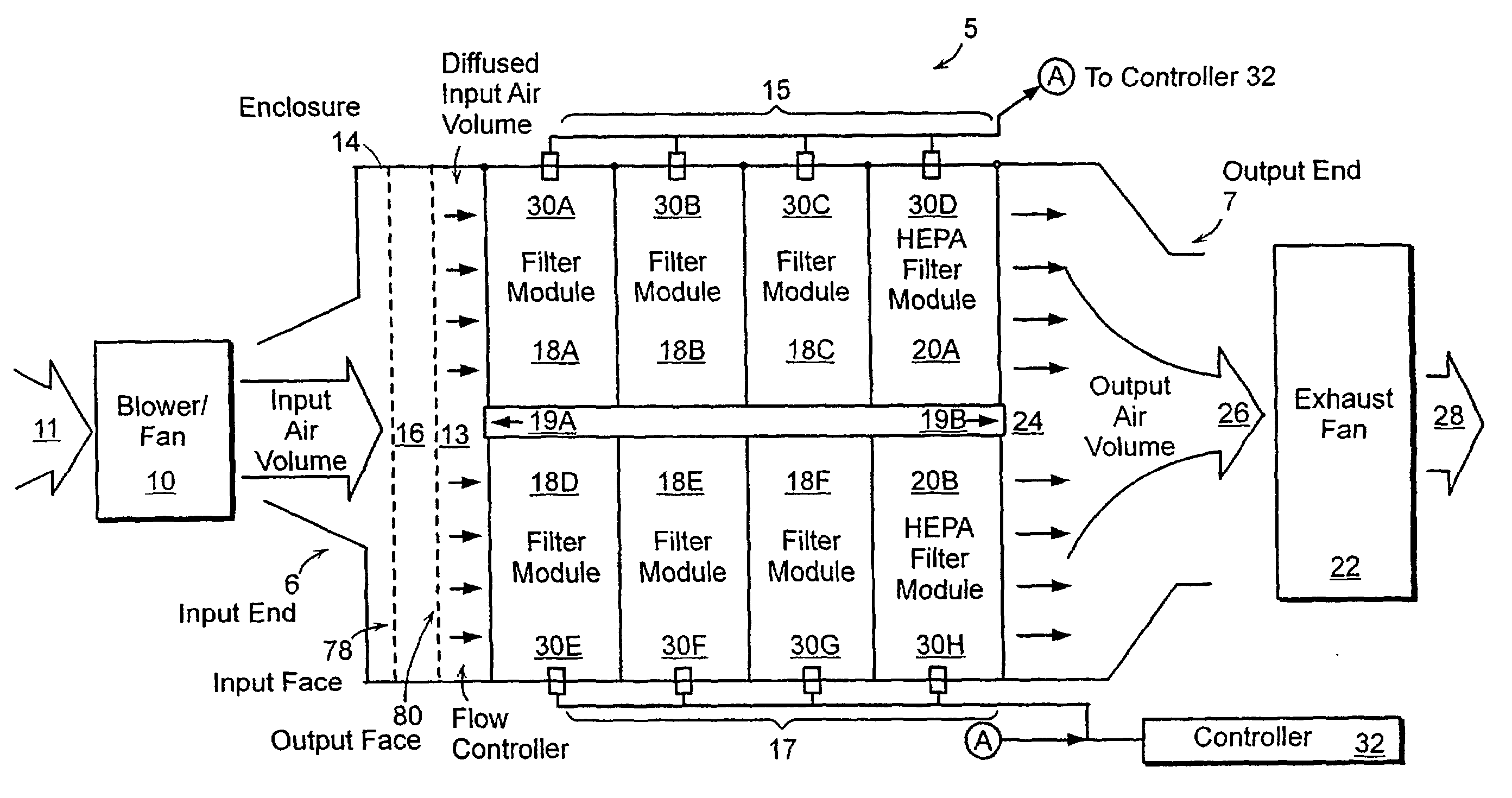
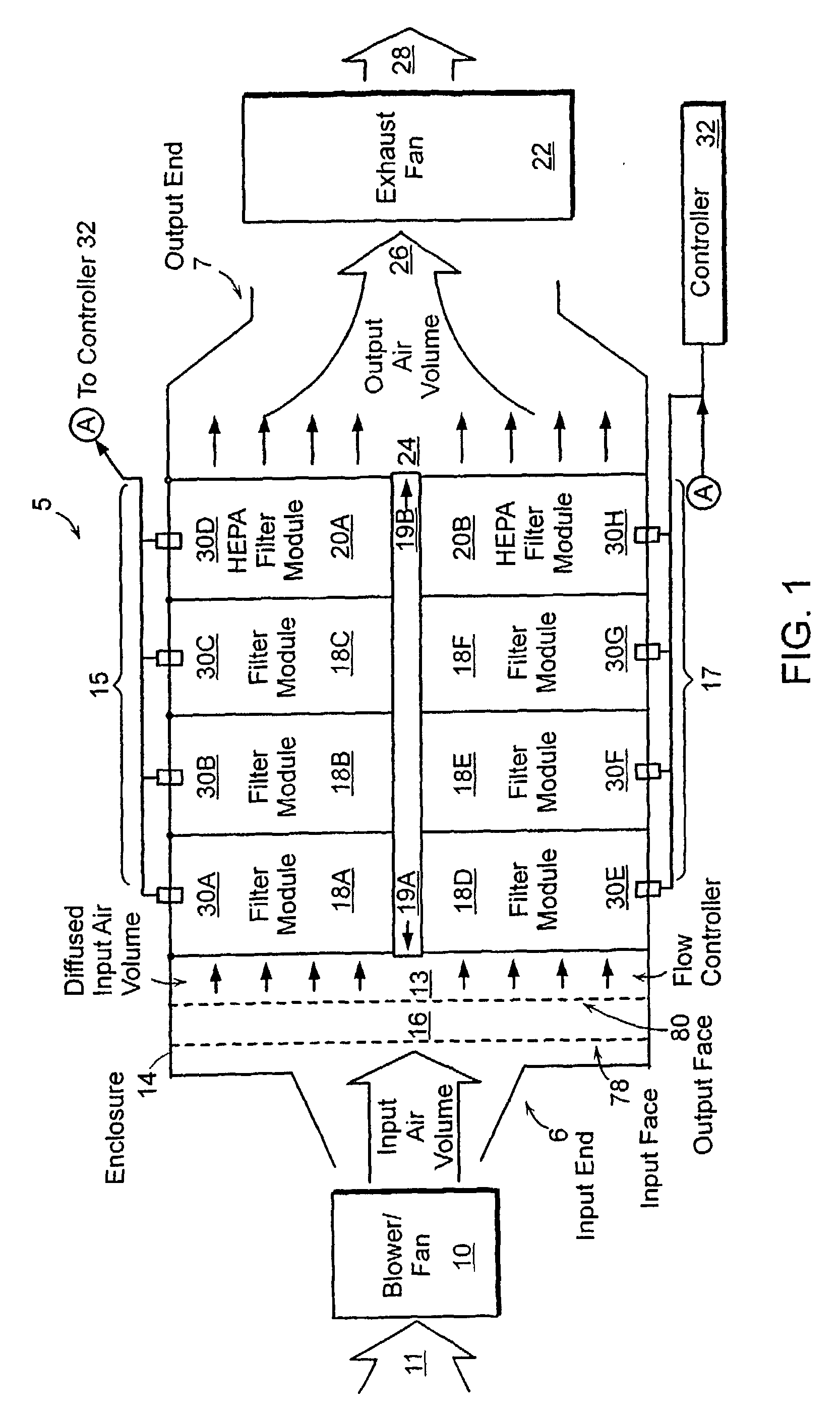
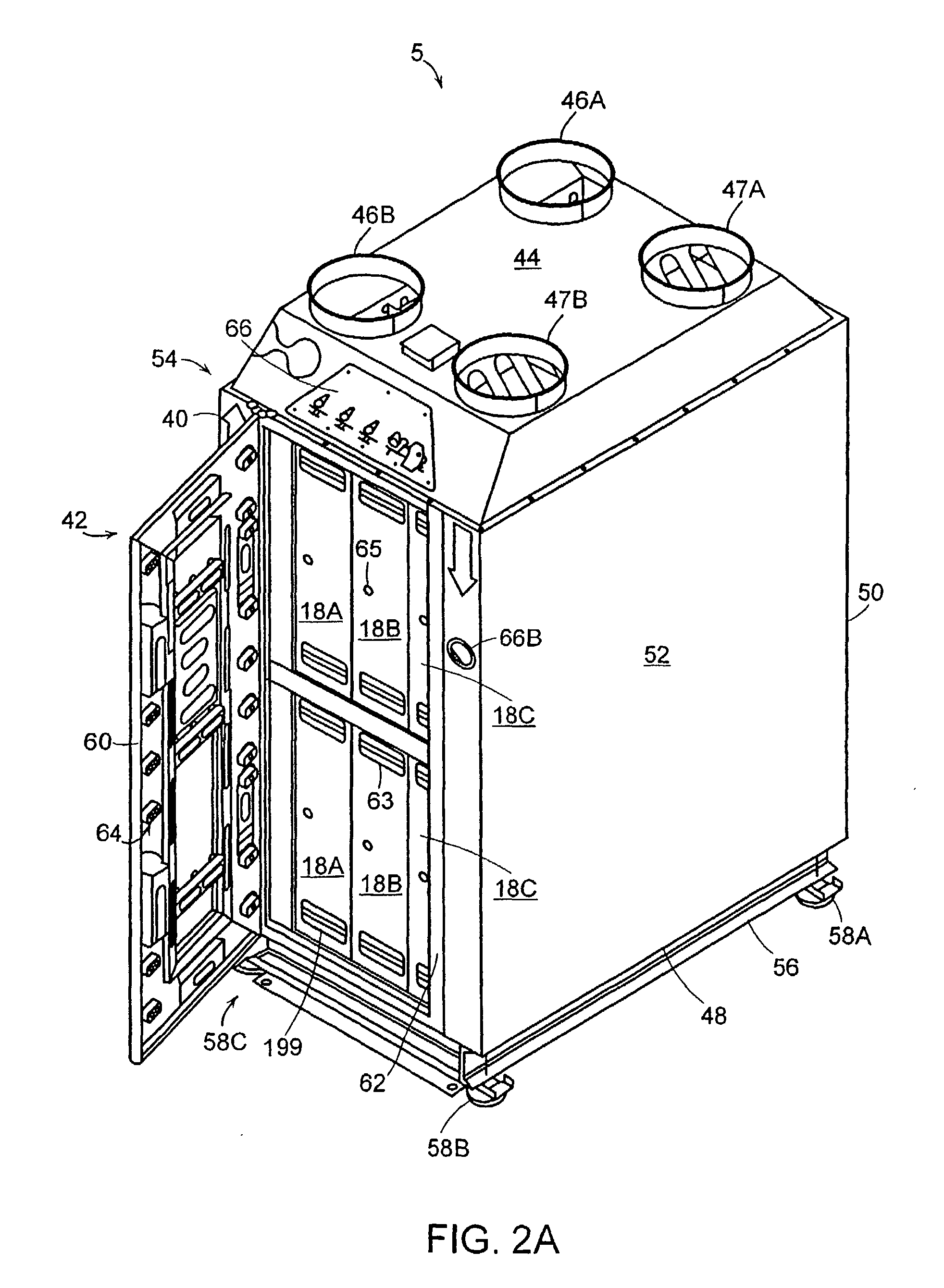
ActiveUS20080078289A1Long period of timeHEPA filterAnalysing fluids using sonic/ultrasonic/infrasonic wavesCombination devicesProduct gasProcess engineering
The invention provides a system and method comprising an apparatus for removing contaminants from a gas in a semiconductor processing device, which can include a filter unit having at least two parallel filter stages located therein. The filter stages are designed to remove a least a portion of the contaminants present in the gas flowing through them. The apparatus can also include a flow controller for distributing the gas flow among the filter stages. In one embodiment, the controller may consist of a diffuser plate. The invention also provides a sampling tube orifice for gas flow control in a system or method of the invention. In another embodiment, an apparatus for removing contaminants from a gas in a clean room comprises a filter unit having at least two parallel filter stages, which are used to remove a portion of the contaminants in the gas as it passes through the apparatus.
Owner:ENTEGRIS INC
Apparatus and Method for Providing an Alternate Flow Path in Isolation Devices
ActiveUS20100155064A1Easy to operateReduce stepsFluid removalSealing/packingRadial positionEngineering
An apparatus for use in a wellbore is described, the apparatus having a tubular body and a throughbore which defines a primary fluid path through the apparatus. An expanding element is disposed around the tubular body and is configured to provide an annular barrier in a space between the tubular body and a surrounding wall. A conduit defining a secondary flow path through the apparatus is provided, and is configured to be in fluid communication with at least one alternate path, such as a shunt tube. The conduit is arranged to vary the secondary flow path along a longitudinal direction of the apparatus, for example to redirect the flow path to a radial position closer to the tool body. The conduit is configured to have a reduced effect on the operation of the expanding element, while still allowing the conduit to be coupled to alternate flow paths of adjacent apparatus.
Owner:WEATHERFORD UK LIMITED
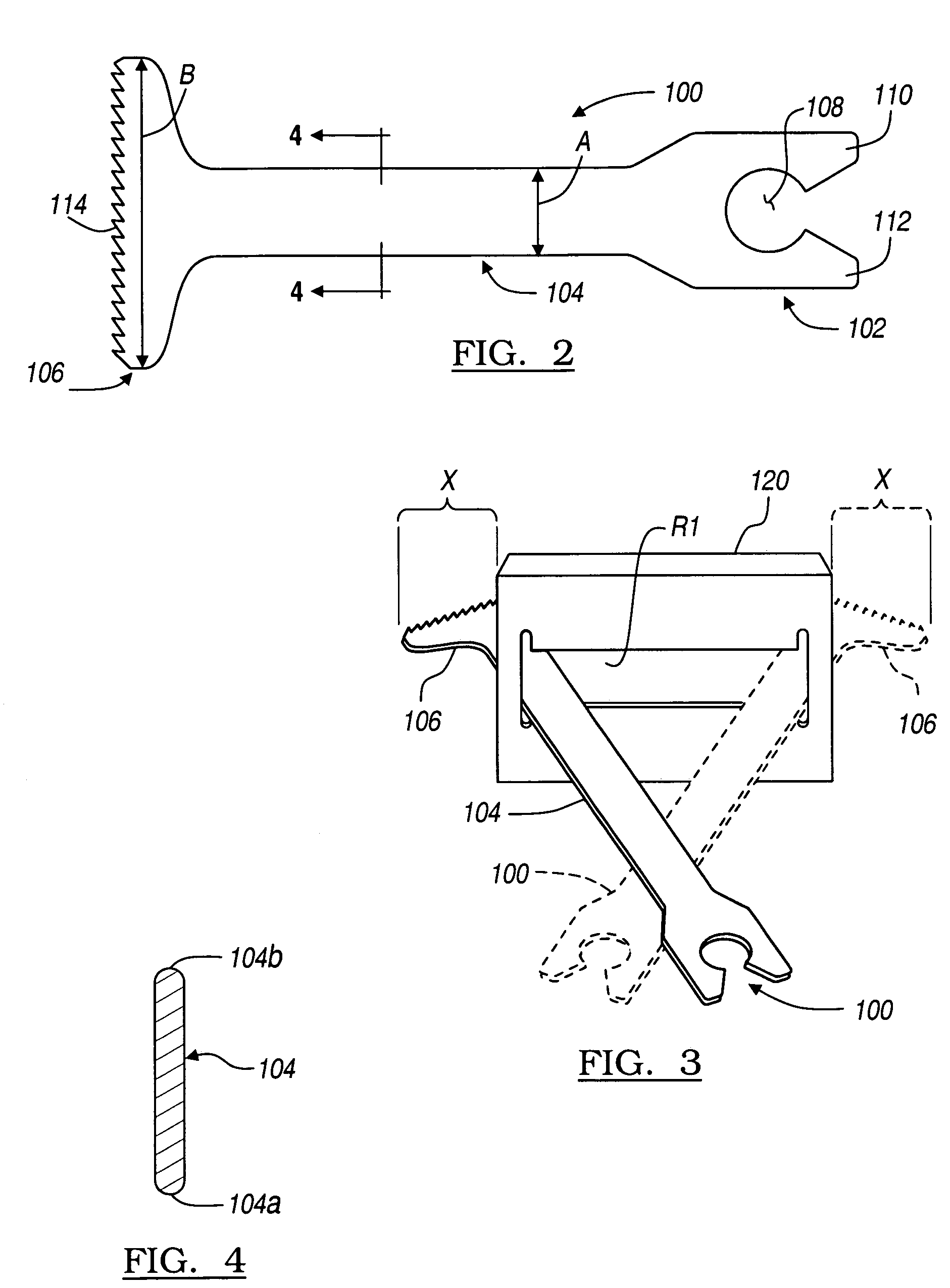
Instrumentation for knee resection
InactiveUS20060142774A1Minimally invasivelyMinimal impactNon-surgical orthopedic devicesSurgical sawsKnee JointProsthesis
Disclosed is a method and apparatus for performing a procedure relative to a selected portion of the anatomy, for example, preparing a portion of a joint, such as a knee, for implantation of a prosthesis. The manner of preparing the selected portion of the anatomy can be assisted with the various apparatuses disclosed.
Owner:BIOMET MFG CORP
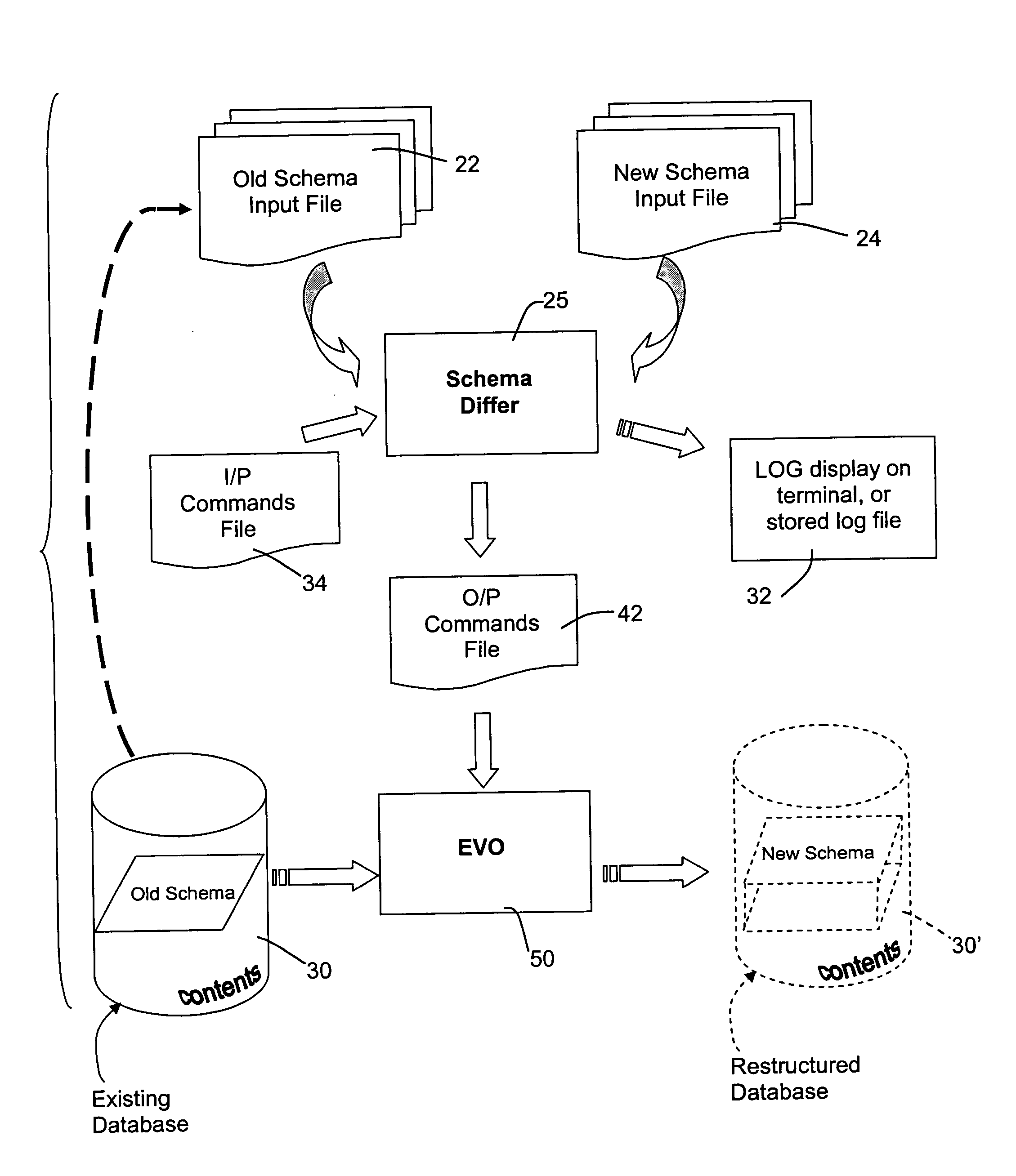
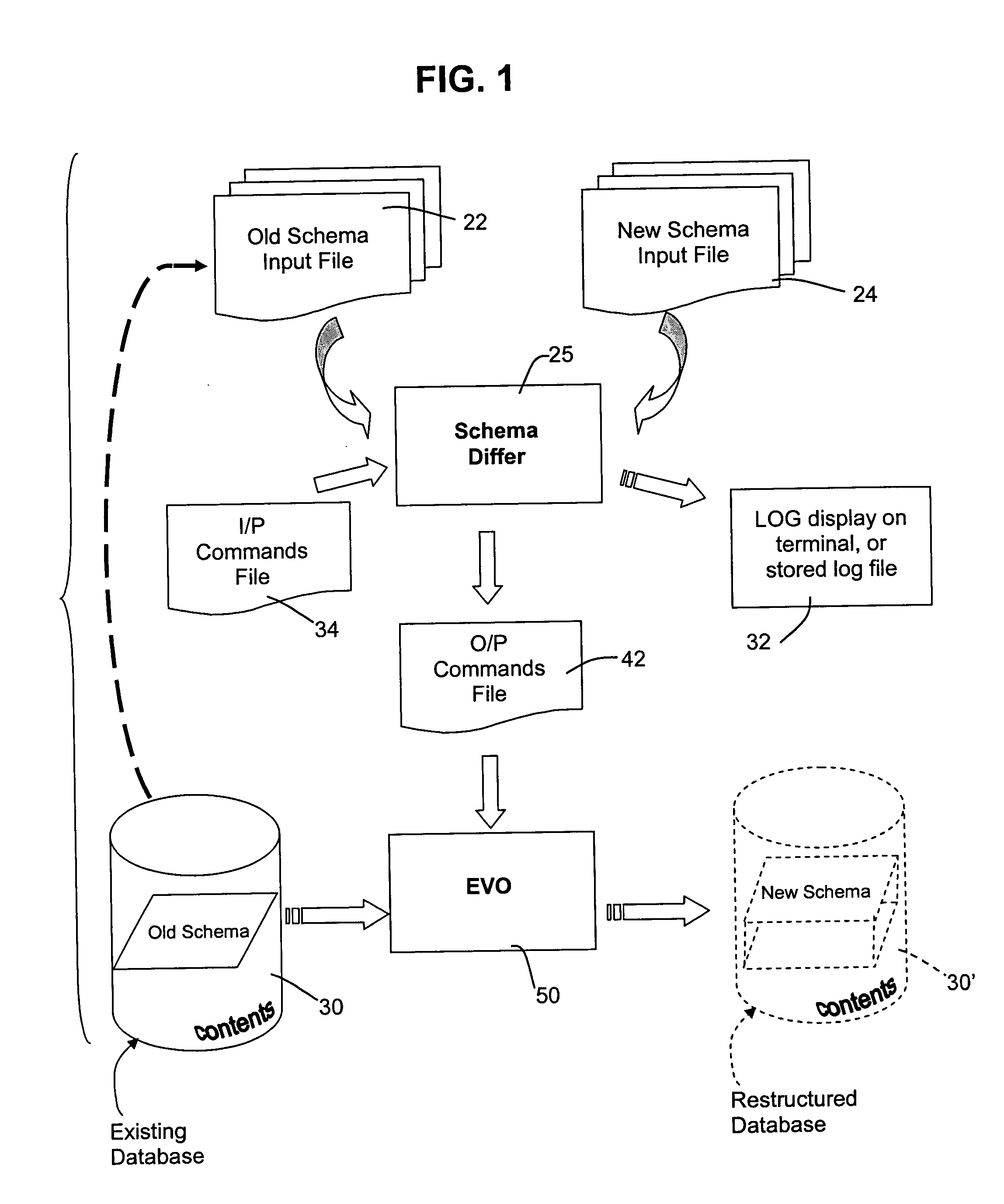
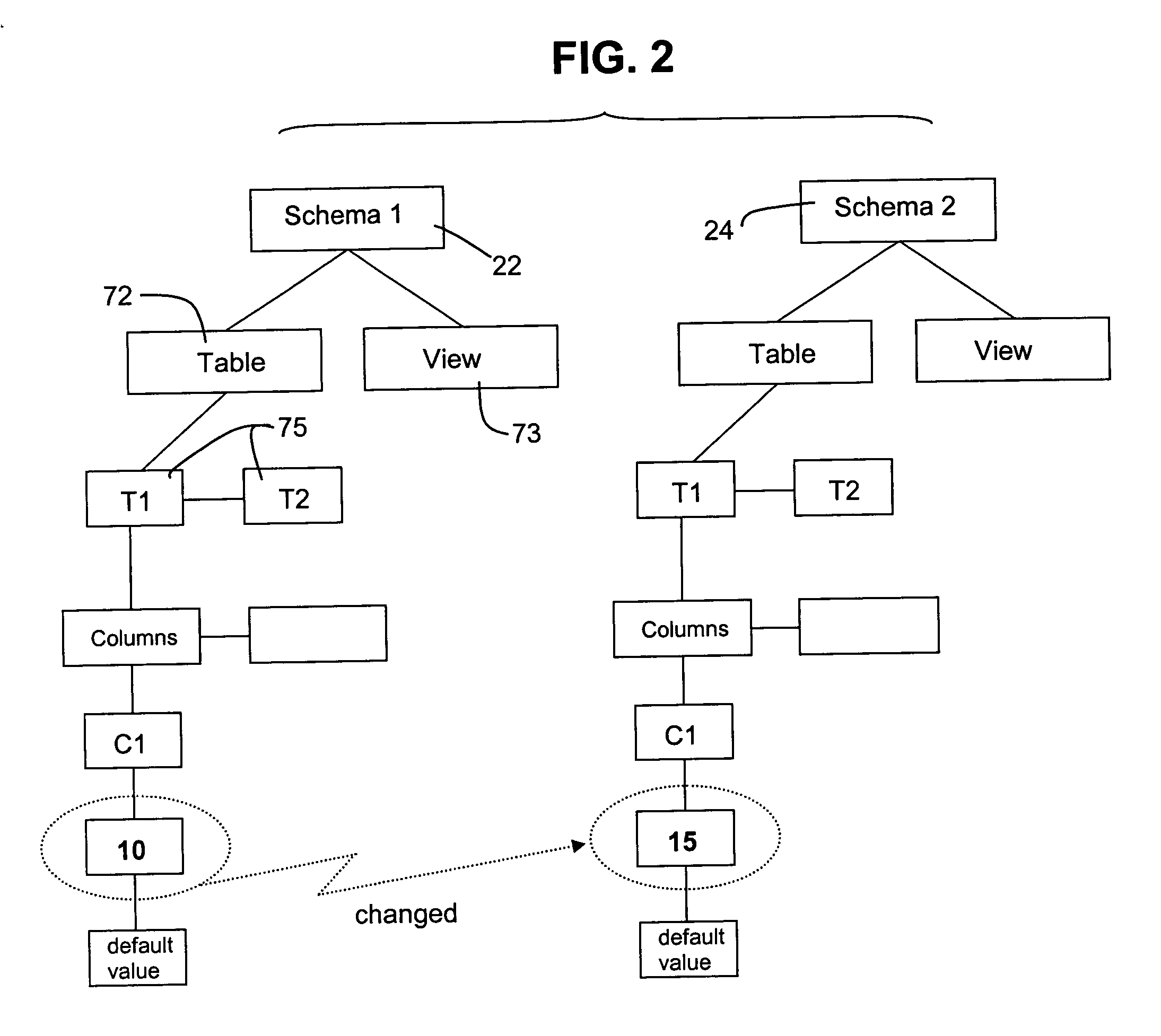
Method for automated database schema evolution
InactiveUS20050071359A1Easy to changeMinimal impactDigital data information retrievalSpecial data processing applicationsSchema for Object-Oriented XMLAutomated database
A database structure of a sort defined by an access and query language that defines tables of variables having labels and field characteristics, such as ANSI structured query language (SQL), is modified by determining the structural differences between an existing schema and a new schema, independent of database contents. The differences are processed to generate commands that are then applied to evolve an existing database from the old schema or structure to the new one. This avoids the need to dump and restructure the contents of the old database for reload into an empty new database that has been prepared to meet the new schema.
Owner:LUCENT TECH INC
Breathing air filtration devices
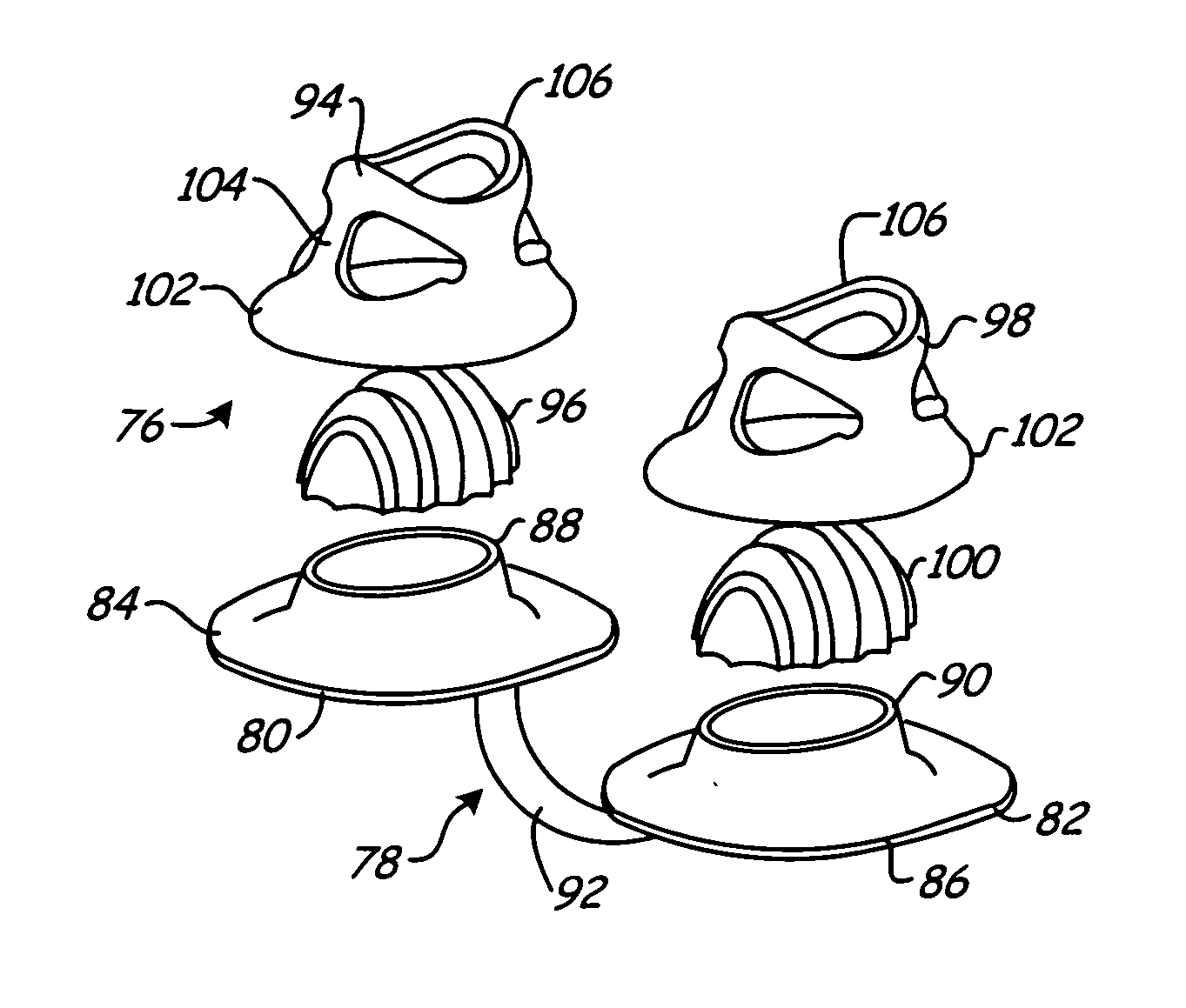
ActiveUS20080023007A1Easy to useMinimal impactRespiratorsBreathing filtersAir filtrationNasal cavity
A nasal air filtration device includes a pair of either planar or concave-convex filters, a support structure incorporating a pair of generally annular bases or sleeves for supporting the filters, and a bridge that couples the bases or sleeves to maintain them in a desired spaced-apart relation and to determine a desired angular relationship. The support structure is insertable into the nasal cavities to position the filters within corresponding nasal cavities. Flexible rims maintain the support structure and the filters in spaced-apart relation to the surrounding nasal wall. The rims conform to surrounding nasal tissue to form seals. The rims can be selectively inclined to facilitate insertion and resist accidental removal. In certain embodiments the device is combined with a filter that covers the mouth to provide an air filtration system.
Owner:AIRWARE HLDG
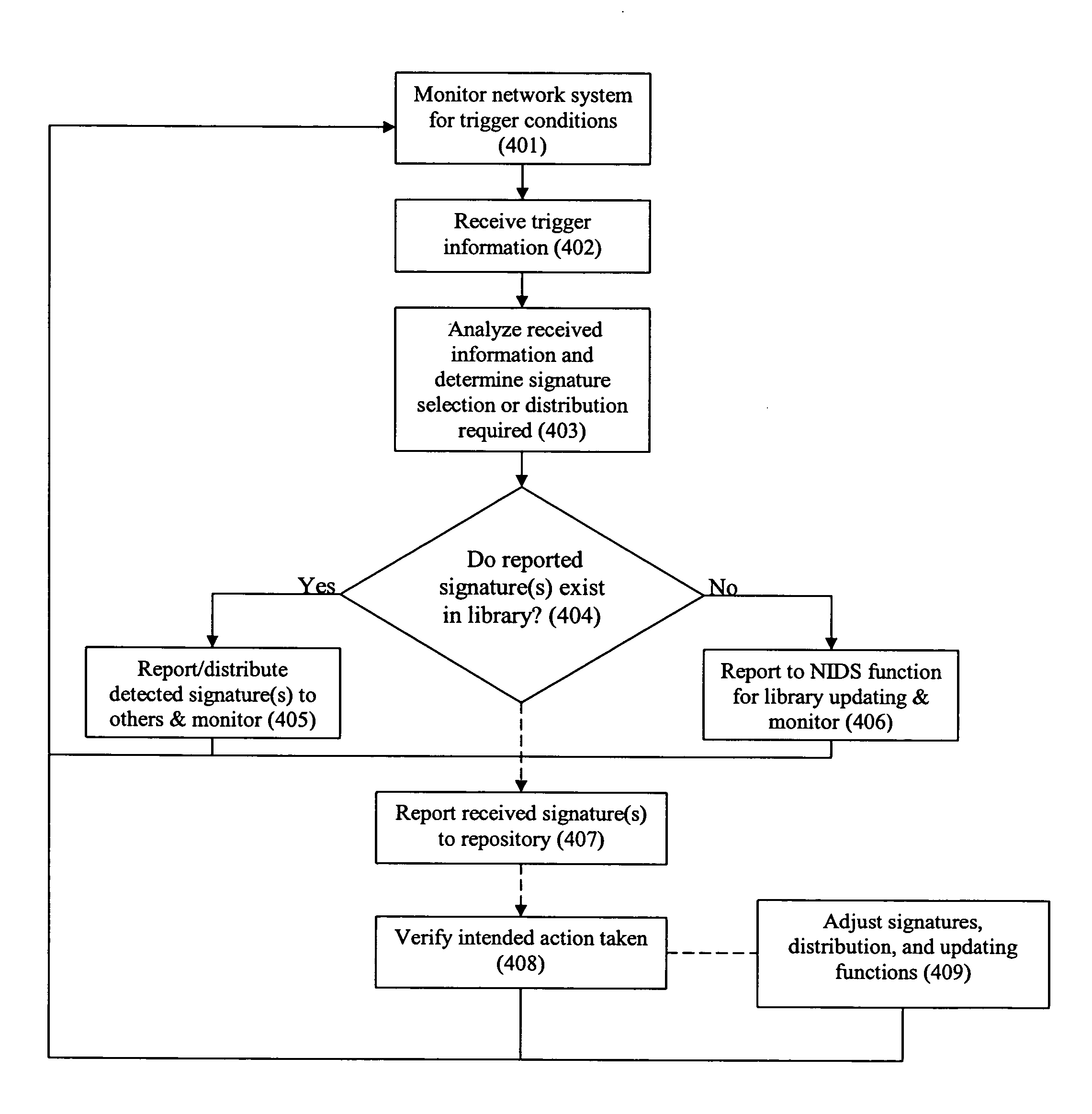
System and method for dynamic distribution of intrusion signatures
ActiveUS20050076245A1Easy to detectMinimize impactMemory loss protectionDigital data processing detailsNetworked systemCentral repository
A system and method for the dynamic distribution of intrusion signatures to aid in protecting a network system from harmful activities. An analysis function includes means for identifying one or more intrusion signatures to be dynamically distributed to an intrusion detection function for monitoring. The analysis function and / or the intrusion detection function may be centralized or distributed. Monitoring may be prioritized, localized, and made operational or non-operational. The intrusion detection function may be embodied in either or both of an appliance and a network forwarding device. The analysis function may distribute the intrusion detection function in addition to the intrusion signatures. In one embodiment of the invention, the system includes an intrusion detection function and a dynamic intrusion signatures function. The intrusion detection function monitors for and reports detected intrusion signatures. The dynamic intrusion signatures function determines whether reported intrusion signatures exist in a library of signatures associated with a particular intrusion detection function. If the reported signature does not exist in the library, the library is updated. Detected intrusion signatures are reported to similarly enabled devices for library analysis and updating, if necessary. The related method includes the steps of monitoring for intrusion signatures or other triggering events, analyzing the events and updating IDS signature libraries as necessary. Optional steps of the method include verifying that reported information has been received and acted upon, and recording of the detection, reporting, and updating information in a central repository. The system and method enable dynamic distribution of IDS signatures enabling improved network IDS coverage while limiting the processing and storage requirements of network devices, particularly forwarding devices such as switches and routers that may include the IDS function. That capability enables broader coverage, faster and better tuned responses to harmful activities.
Owner:EXTREME NETWORKS INC
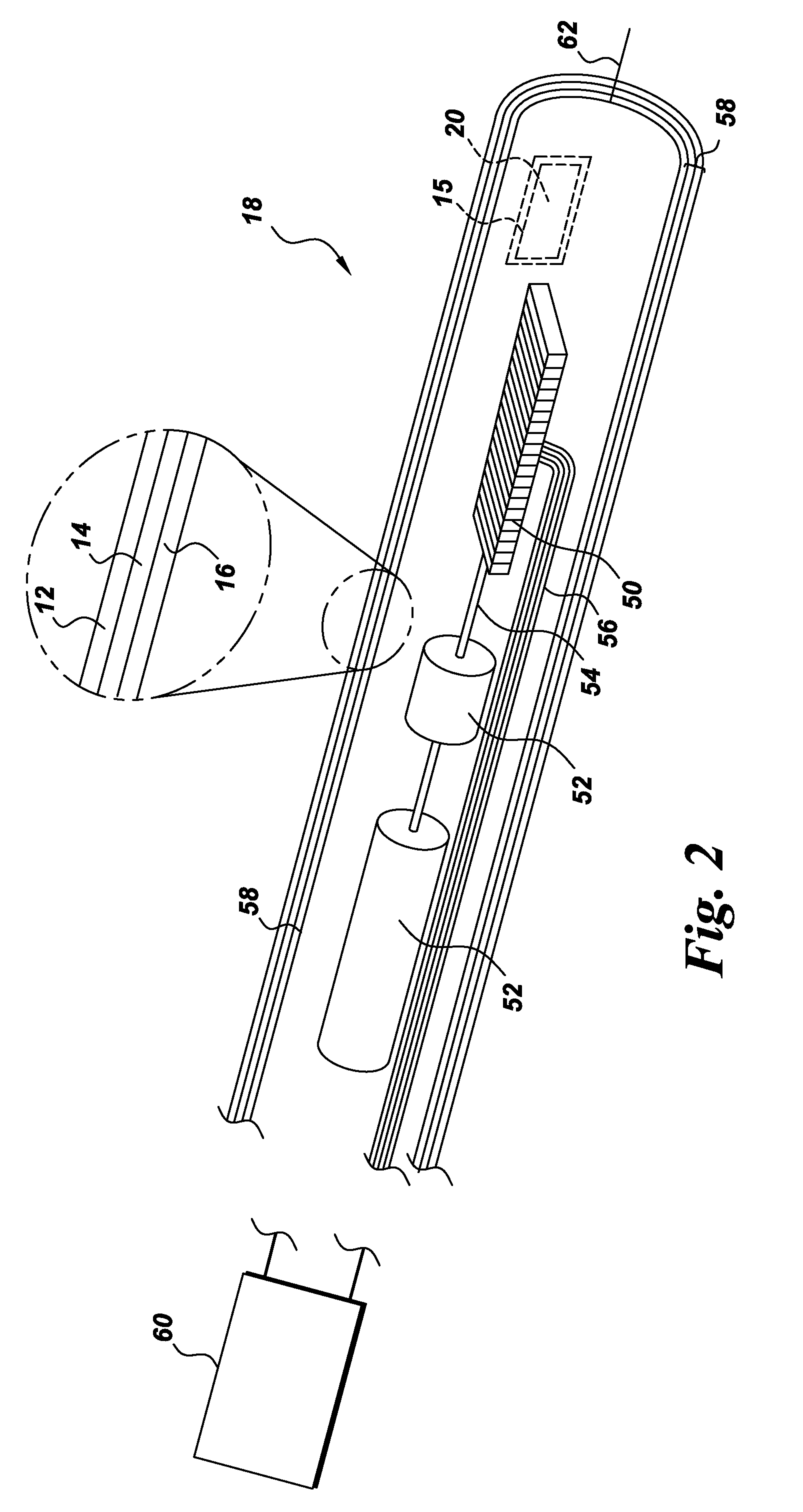
Ultrasound catheter housing with electromagnetic shielding properties and methods of manufacture
InactiveUS20100249602A1Minimal impactUltrasonic/sonic/infrasonic diagnosticsSurgeryMedicineElectromagnetic shielding
An ultrasound catheter housing with electromagnetic shielding properties and methods of manufacturing is provided. The ultrasound catheter housing comprises a an inner thin wall polymer tube extruded using an ultrasonically transparent polymer, a thin metalized layer deposited on the outer surface of the inner tube, and an outer thin wall polymer tube, which may be the same or a different ultrasonically transparent material. In another embodiment an ultrasound catheter comprising the ultrasound catheter housing is provided.
Owner:GENERAL ELECTRIC CO
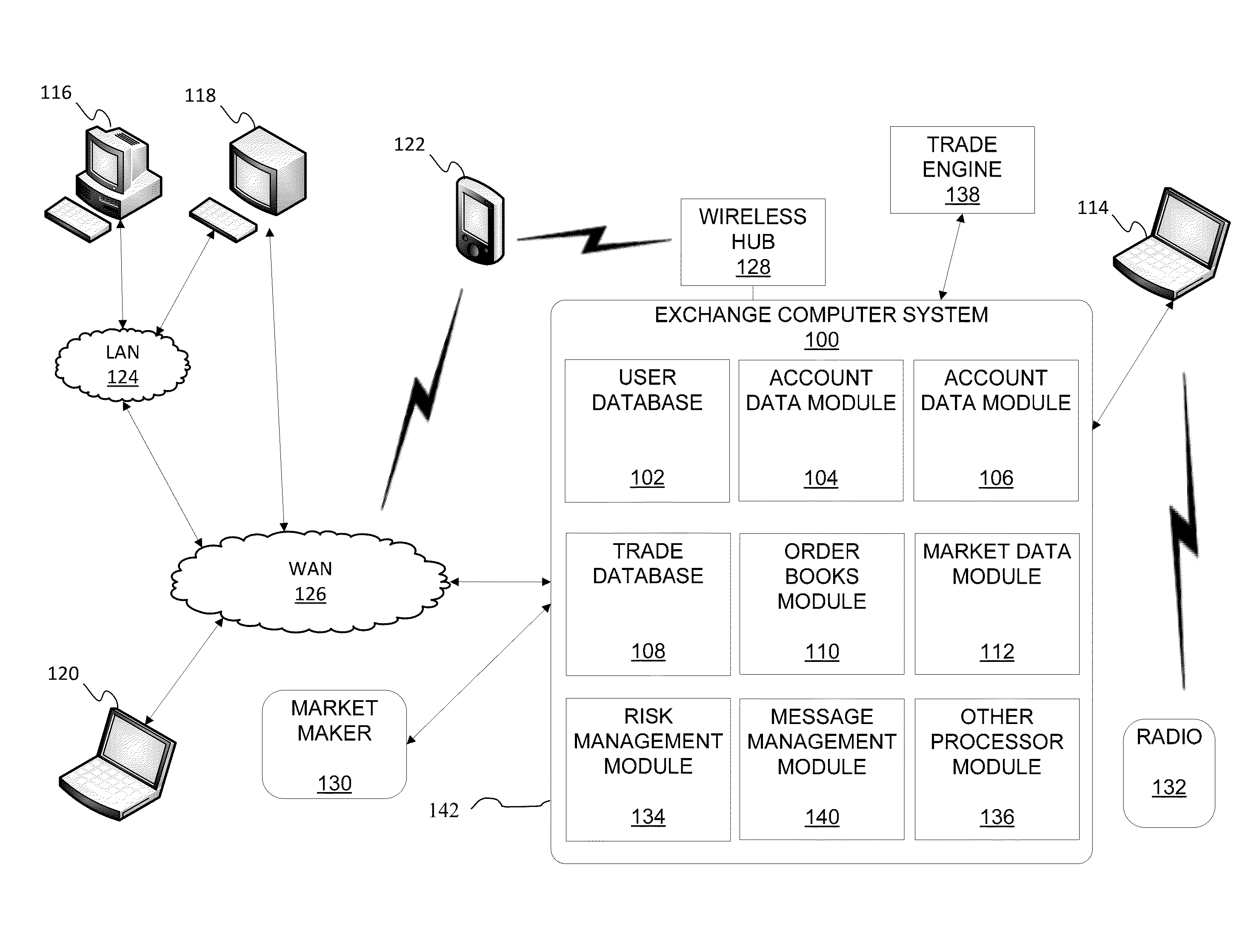
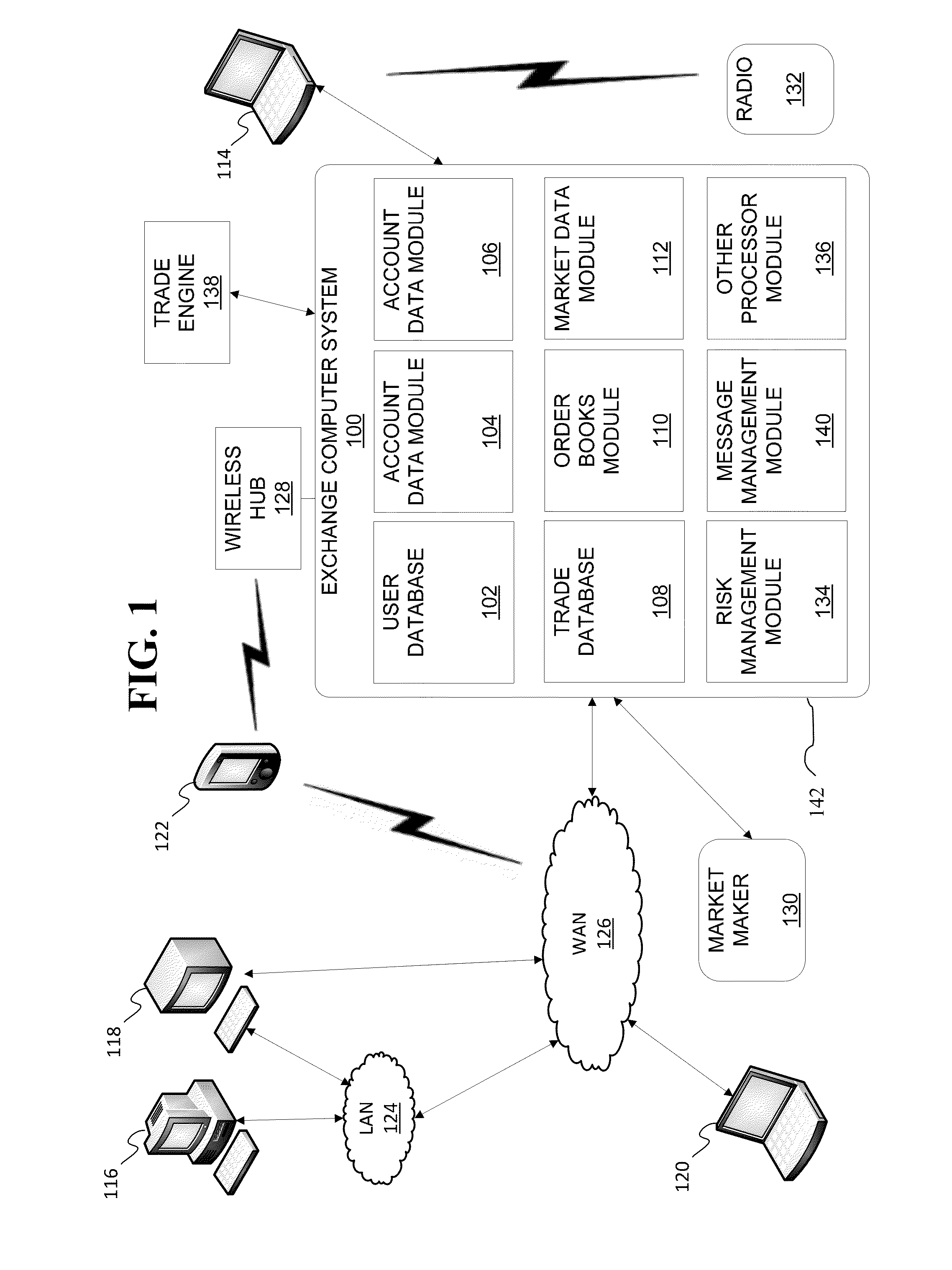
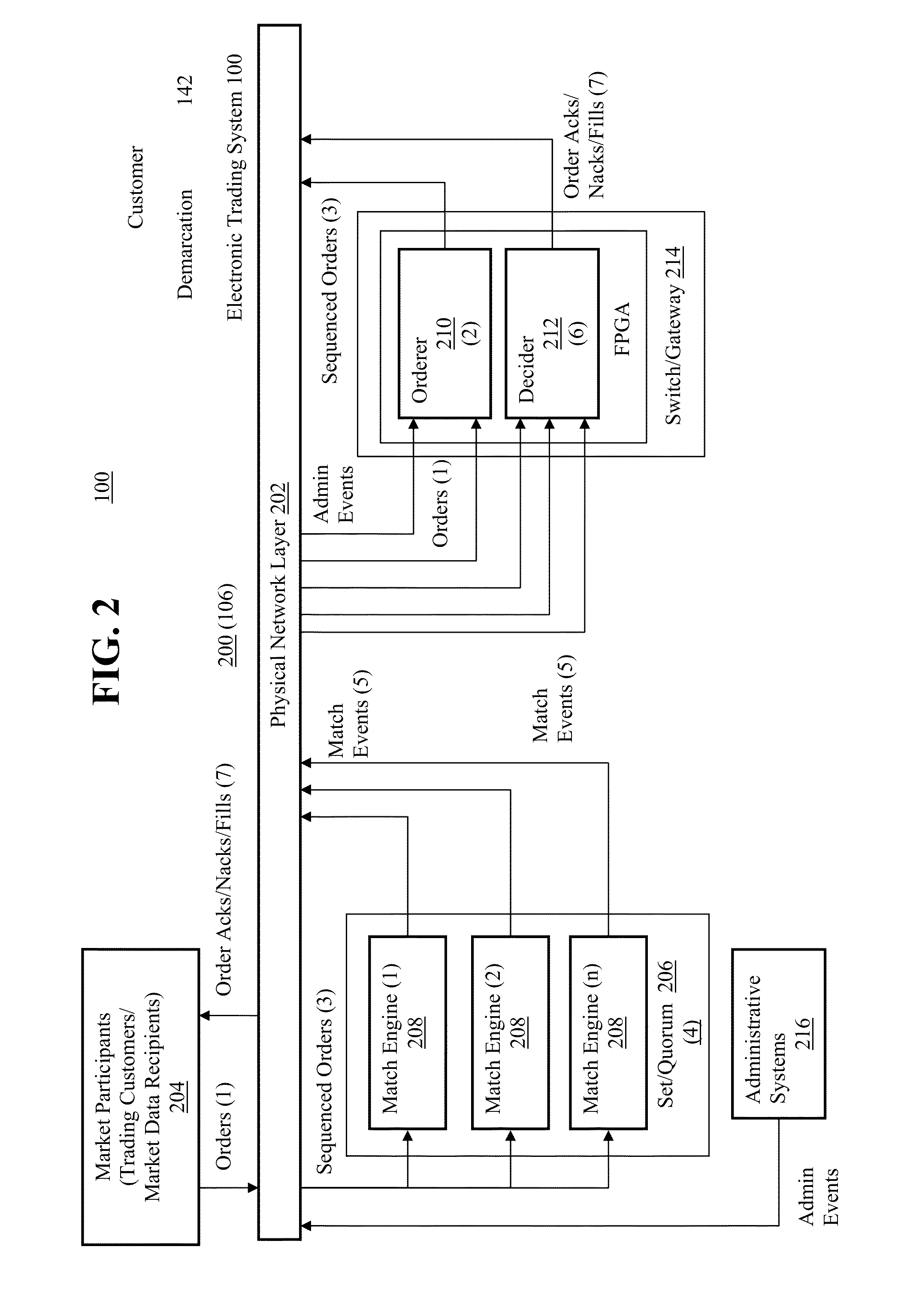
Transactionally Deterministic High Speed Financial Exchange Having Improved, Efficiency, Communication, Customization, Performance, Access, Trading Opportunities, Credit Controls, and Fault Tolerance
The disclosed embodiments relate to implementation of a trading system, which may also be referred to as a trading system architecture, having improved performance which further assures transactional determinism under increasing processing transaction loads while providing improved trading opportunities, fault tolerance, low latency processing, high volume capacity, risk mitigation and market protections with minimal impact, as well as improved and equitable access to information and opportunities.
Owner:CHICAGO MERCANTILE EXCHANGE INC
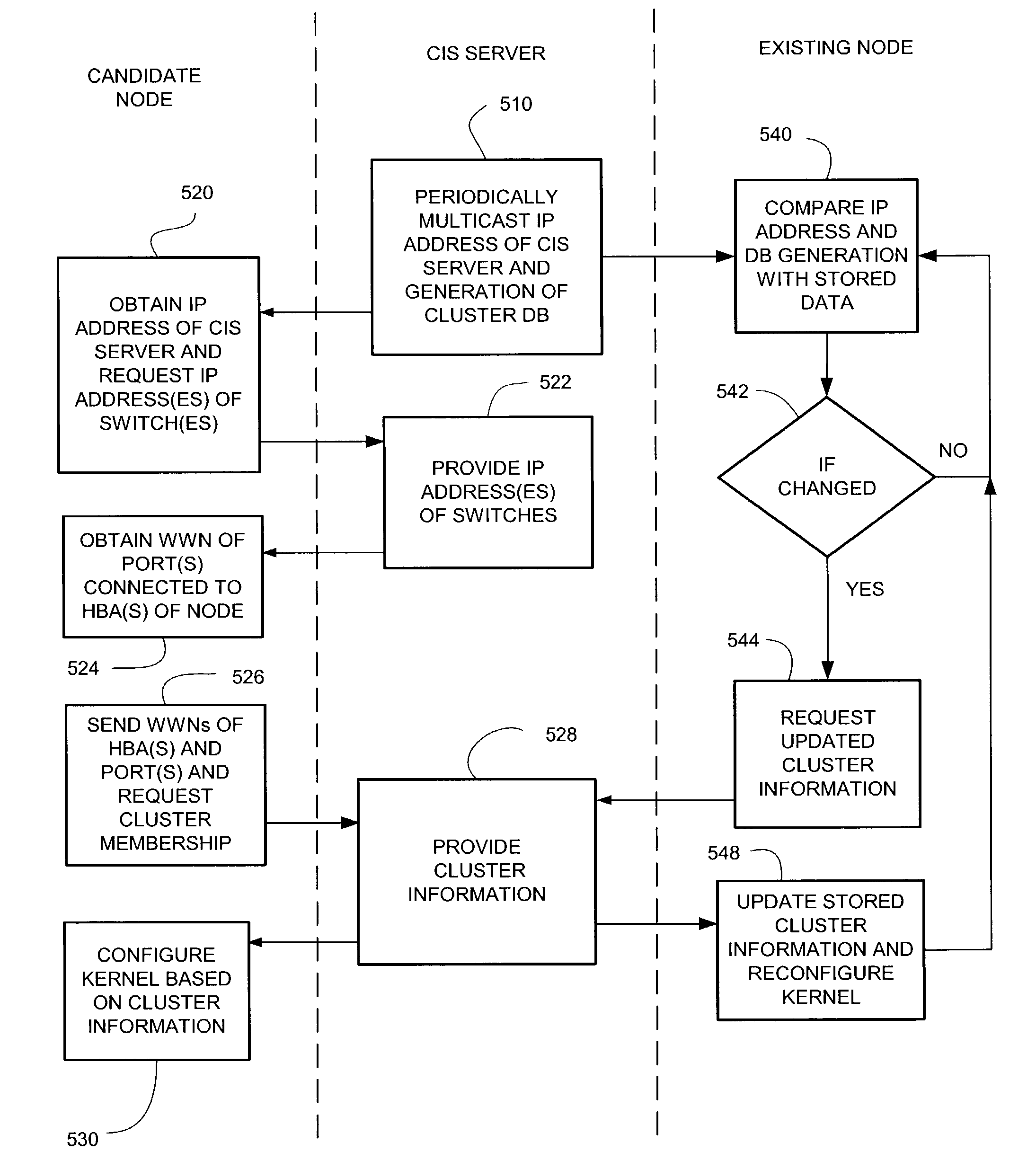
Multi-class heterogeneous clients in a clustered filesystem
InactiveUS7617292B2Minimal impactError detection/correctionMultiple digital computer combinationsOperational systemStorage area network
A cluster of computer system nodes connected by a storage area network include two classes of nodes. The first class of nodes can act as clients or servers, while the other nodes can only be clients. The client-only nodes require much less functionality and can be more easily supported by different operating systems. To minimize the amount of data transmitted during normal operation, the server responsible for maintaining a cluster configuration database repeatedly multicasts the IP address, its incarnation number and the most recent database generation number. Each node stores this information and when a change is detected, each node can request an update of the data needed by that node. A client-only node uses the IP address of the server to connect to the server, to download the information from the cluster database required by the client-only node and to upload local disk connectivity information.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Stand-alone electrical system for large motor loads
ActiveUS20050116541A1Sufficient rateMinimal impactSolidificationBatteries circuit arrangementsElectric power systemEngineering
An electrical power system that can be used to interconnect a plurality of generators to a plurality to loads while being rated at less than a total power consumed. The system is preferably used to distribute power for a Liquid Natural Gas (LNG) facility. The system broadly comprises a primary bus connected between the generators and the loads, such as electrical compressor motors used in the LNG facility. The generators and the loads are arranged along the primary bus in order to distribute the power from the generators to the loads, without overloading the primary bus.
Owner:CONOCOPHILLIPS CO
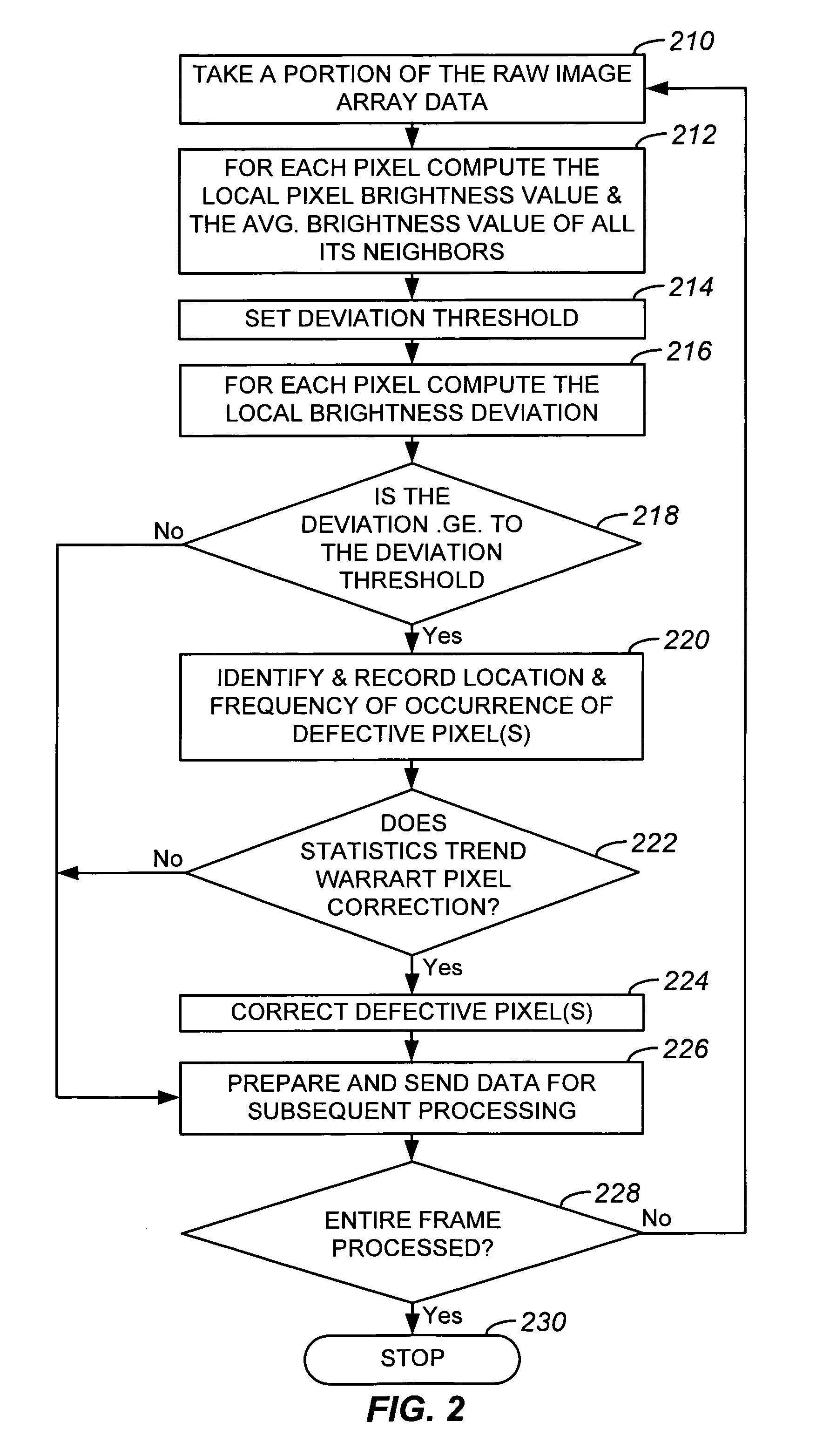
Dynamic anomalous pixel detection and correction
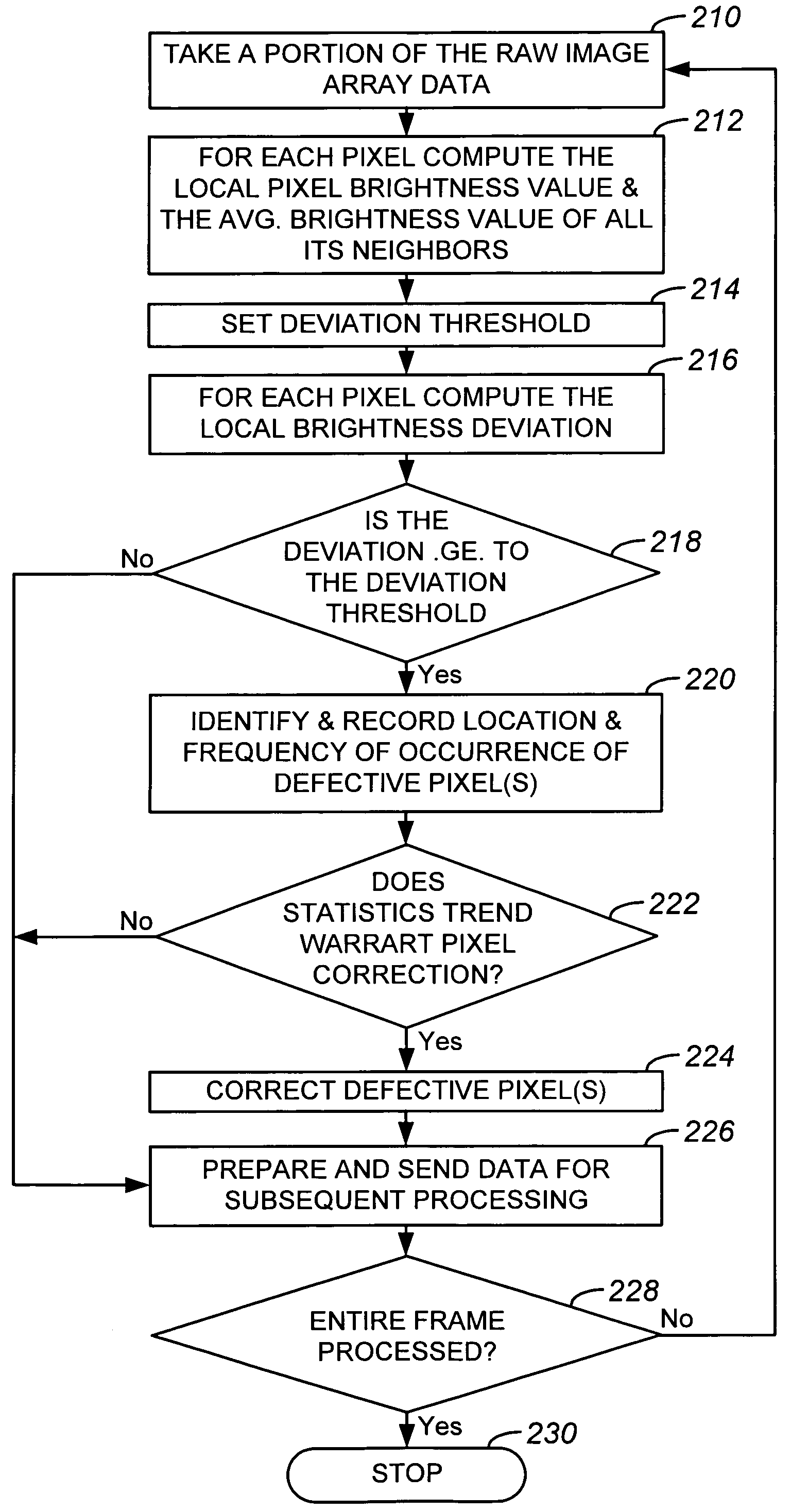
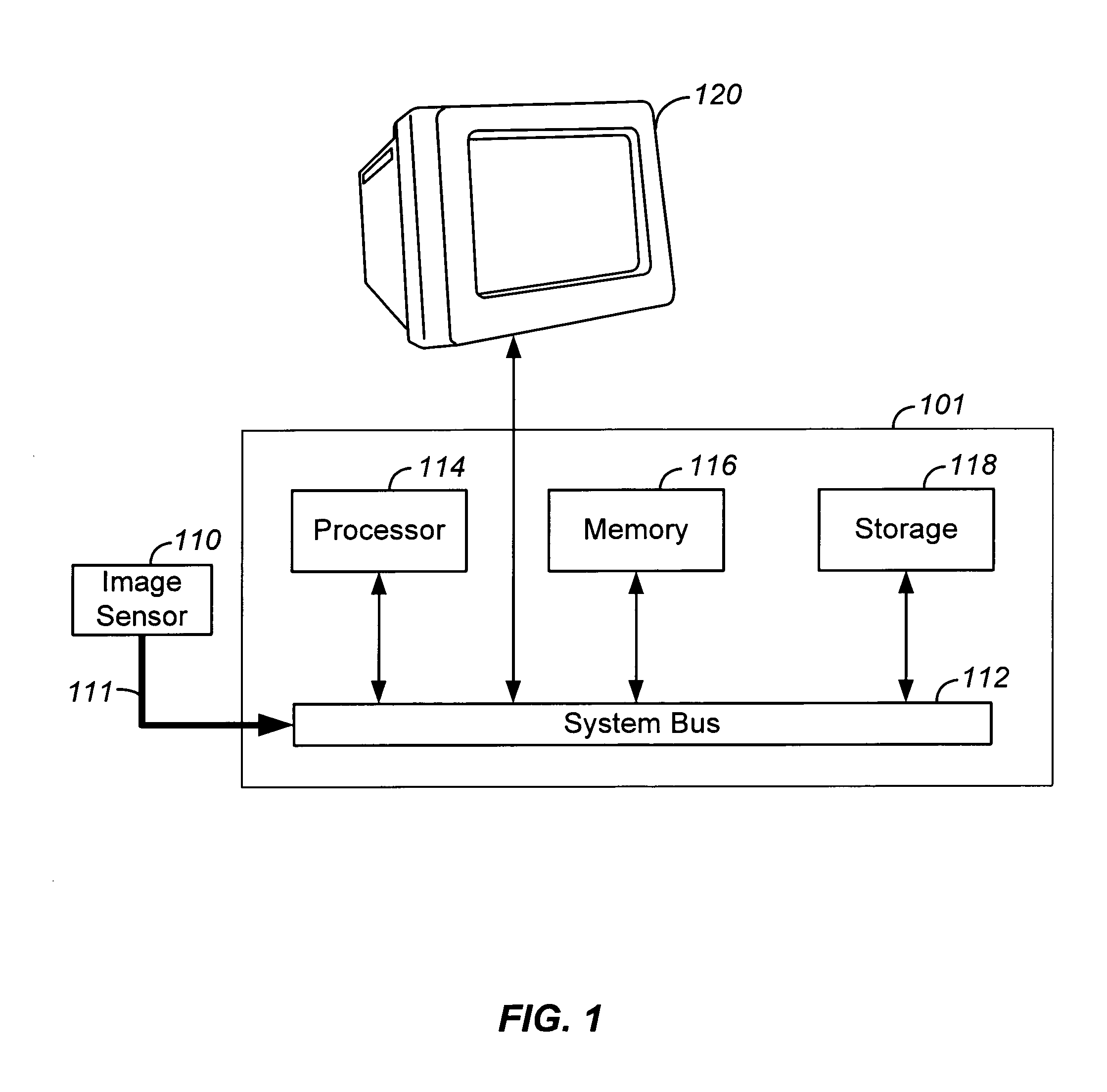
InactiveUS7009644B1Minimally affectedImpact rateTelevision system detailsColor signal processing circuitsPattern recognitionCMOS sensor
A method and a system for dynamically detecting and correcting anomalous pixels in the raw data taken from an image sensor array such as a CCD or a CMOS sensor array, thus allowing the use of dumb cameras to capture digital images for subsequent use by an intelligent host—such as being displayed on a computer monitor. This invention uses software algorithms running on an intelligent host processor to dynamically correct the anomalous pixels in the raw data taken from an image sensor array typical of those in a digital still or a video camera. Using the combination of a dumb camera which provides raw data to an intelligent host, which does all the subsequent image processing, the system works by scanning an image frame for pixels that vary more than a specified amount in their brightness value from their neighboring pixels and designating those as defective pixels. The location and frequency of the photosites sending the defective pixels are stored in a statistical database in the computer's memory. The brightness value of a defective pixel is then replaced by a local brightness value obtained from the defective pixel's neighboring pixels. The process includes video subsampling, meaning that the defective pixel detection is carried out and repeated at a pre-specified frame rate to ensure optimum detection and correction at a minimal level of scanning. A statistical database is kept so that truly anomalous pixels can over time be distinguished from false detection of true anomalies in the target image, lighting or other environmentally induced anomalies.
Owner:LOGITECH EURO SA
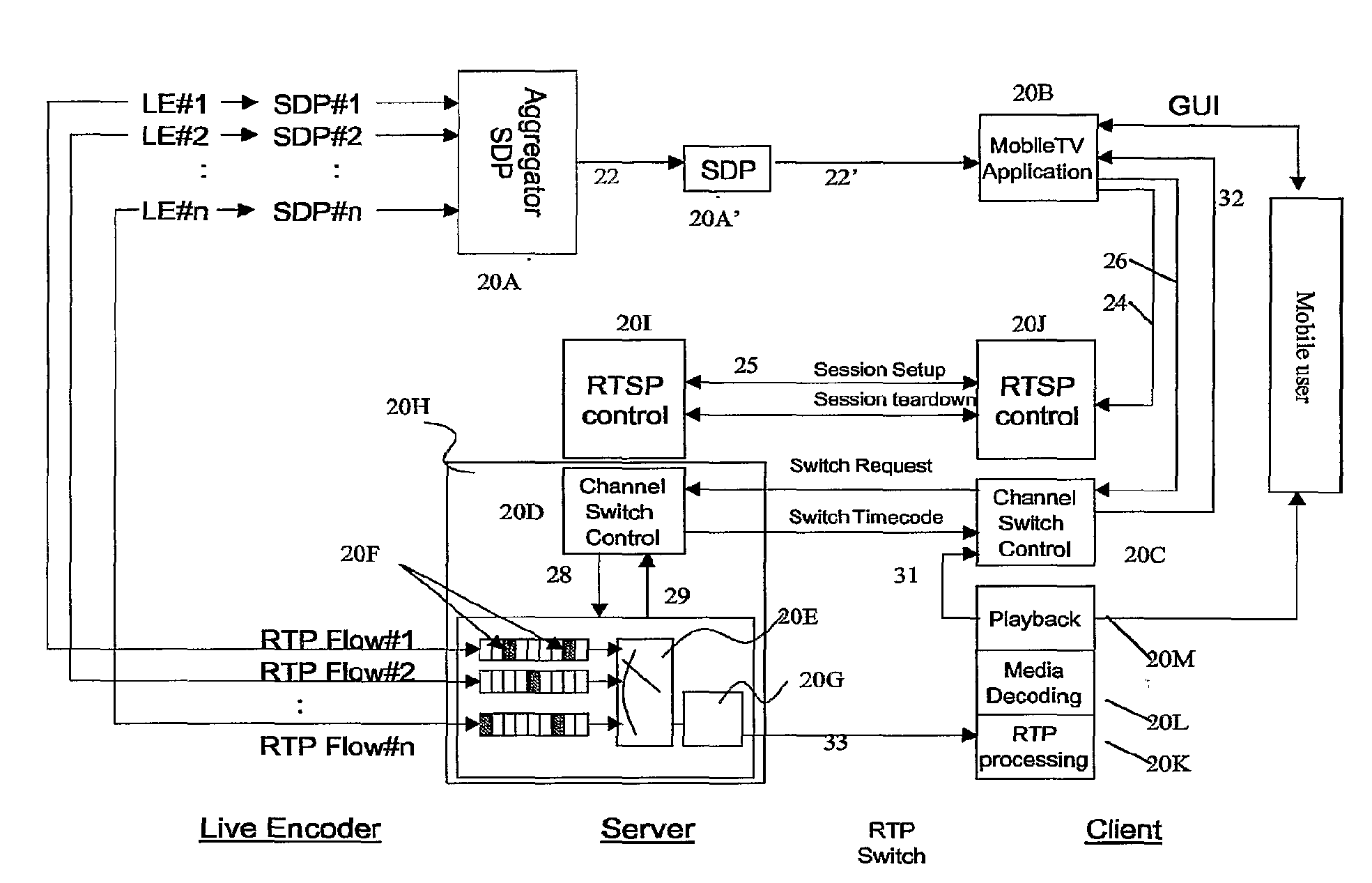
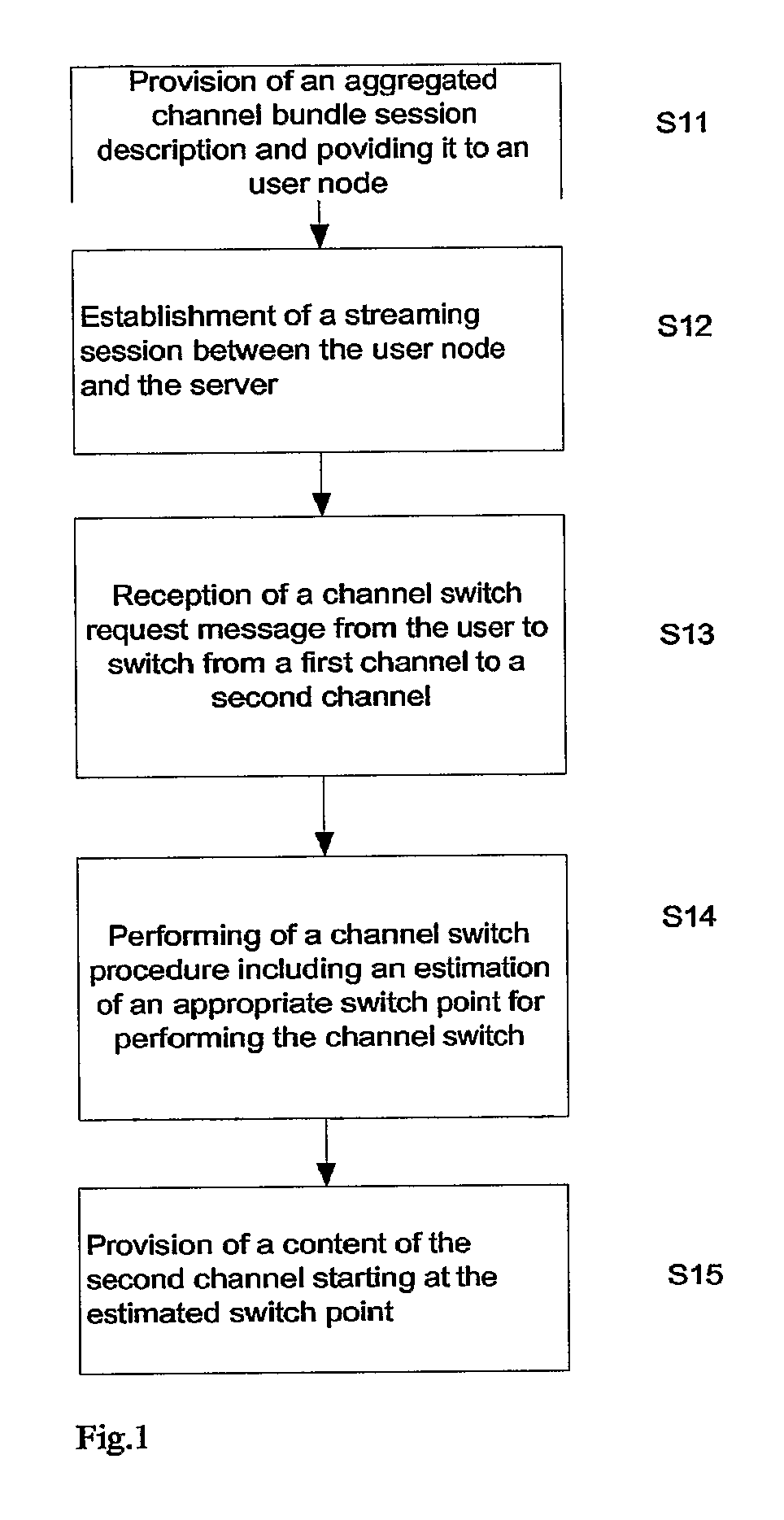
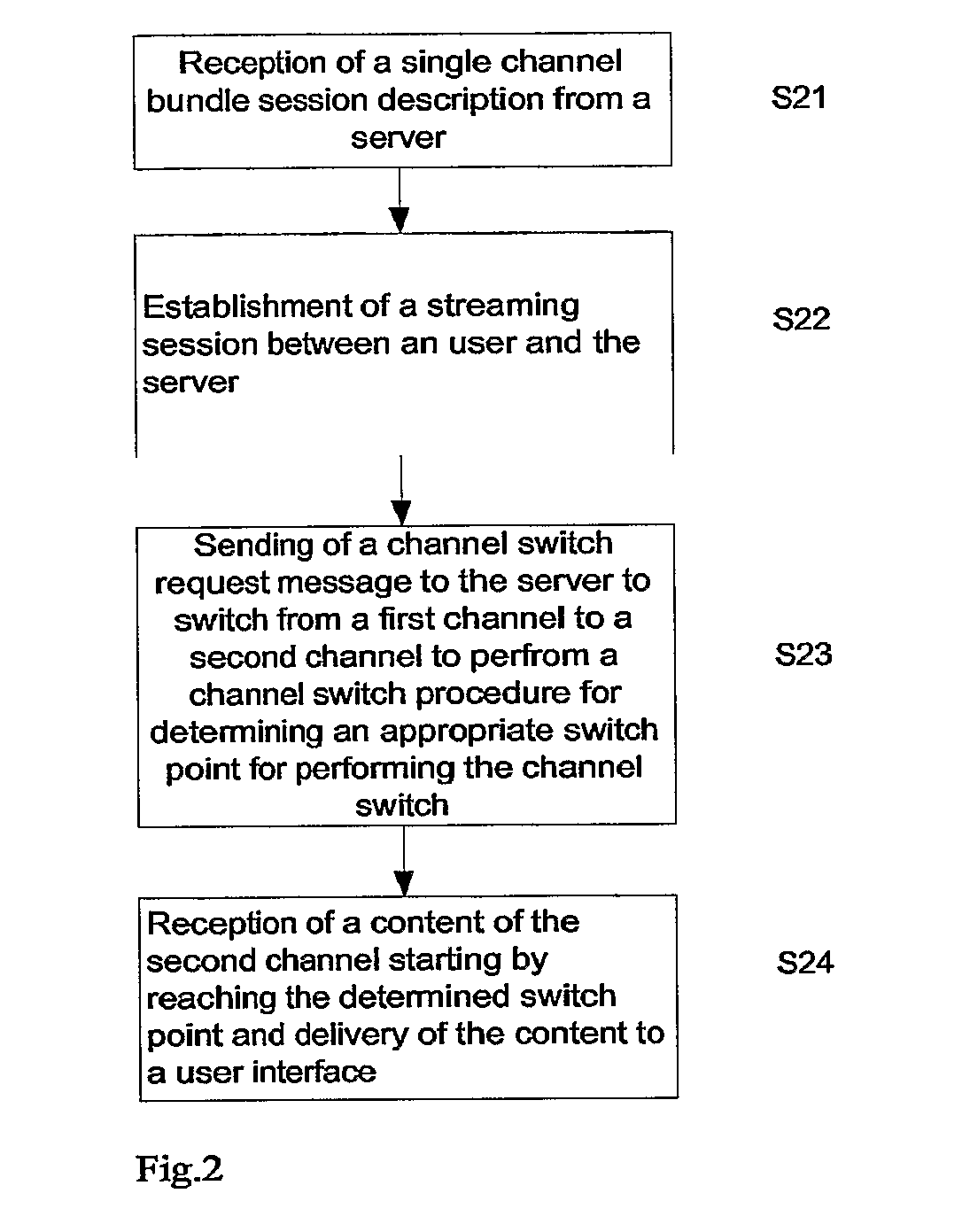
On-Demand Multi-Channel Streaming Session Over Packet-Switched Networks
InactiveUS20080151885A1Avoid excessive delayMinimal impactPulse modulation television signal transmissionData switching by path configurationTemporal informationSingle session
An aggregation procedure for aggregating of a number of session descriptions parameters corresponding to a multitude of channels into one single session description. Each channel is described by a mandatory unique identifier. A corresponding client application processes the SDP describing the channel bundle and uses the found information for allowing a user to switch to a channel associated with a certain identifier. Signaling of a channel switch control unit, which is part of the multi-channel streaming server, receives a multitude of RTP flows and selects one of the flows for forwarding to the client. A switching point determination is a part of the channel switch control unit and determines the next possible point of time for switching to a requested channel. The client application receives time information for the switch point in response to a channel switch request.
Owner:TELEFON AB LM ERICSSON (PUBL)
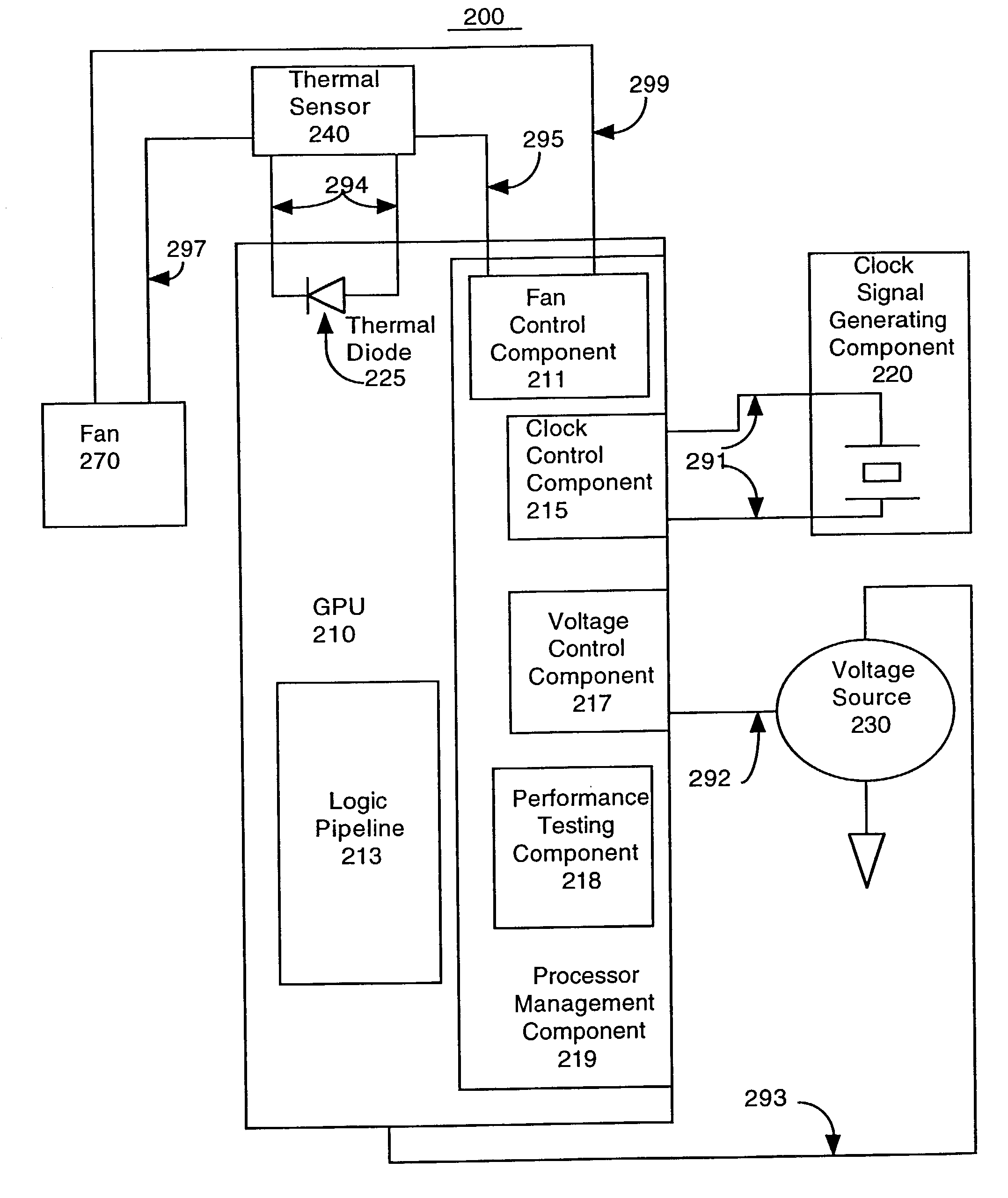
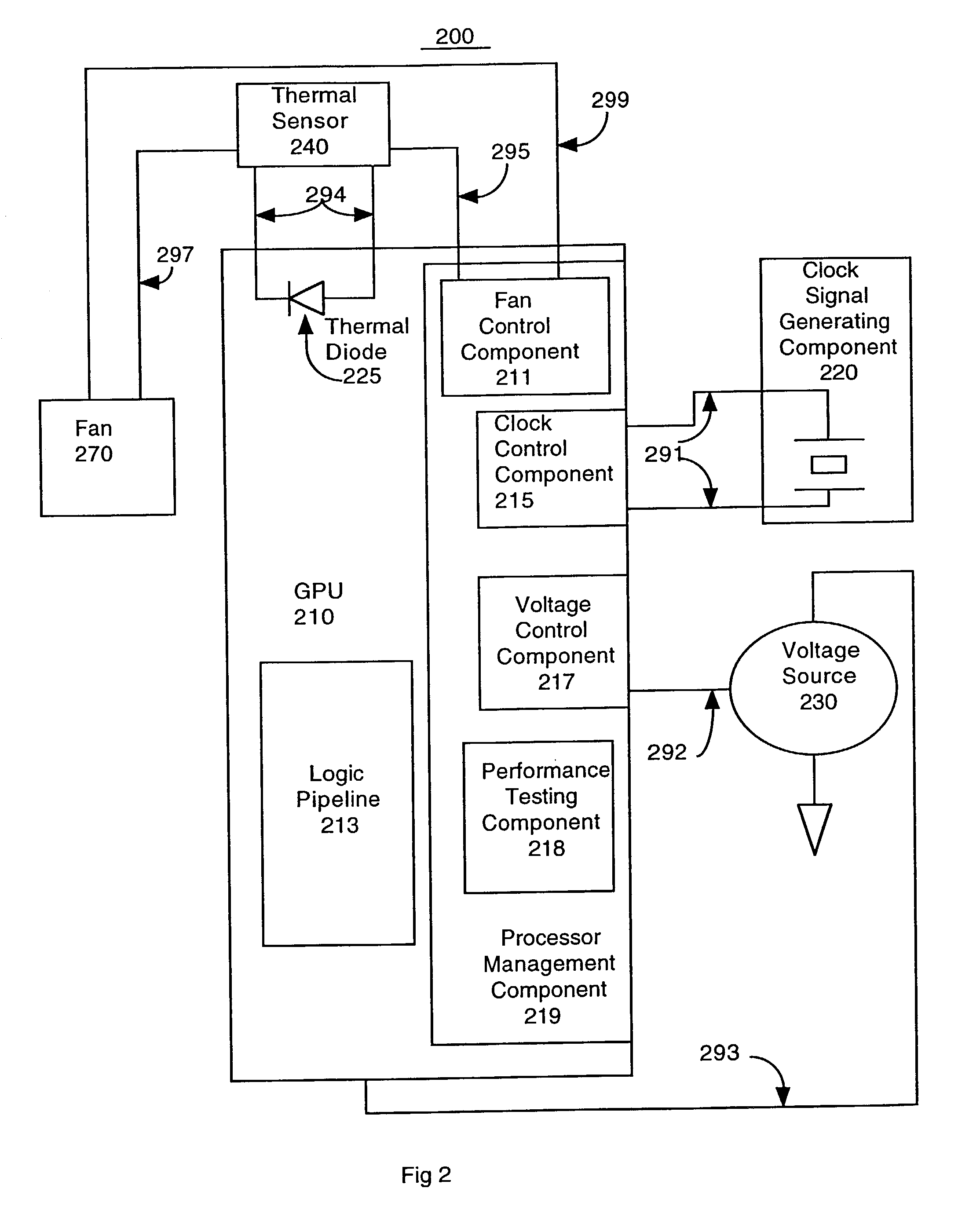
Processor performance adjustment system and method
ActiveUS7882369B1Enhance performance of processorMinimal impactEnergy efficient ICTVolume/mass flow measurementEmbedded systemError ratio
The present invention performance enhancement and reliability maintenance system and method pushes a processor to its maximized performance capabilities when performing processing intensive tasks (e.g., 3D graphics, etc). For example, a clock speed and voltage are increased until an unacceptable error rate begins to appear in the processing results and then the clock speed and voltage are backed off to the last setting at which excessive errors did not occur, enabling a processor at its full performance potential. The present invention also includes the ability to throttle back settings which facilitates the maintenance of desired reliability standards. The present invention is readily expandable to provide adjustment for a variety of characteristics in response to task performance requirements. For example, a variable speed fan that is software controlled can be adjusted to alter the temperature of the processor in addition to clock frequency and voltage.
Owner:NVIDIA CORP
Secure bootloader for securing digital devices
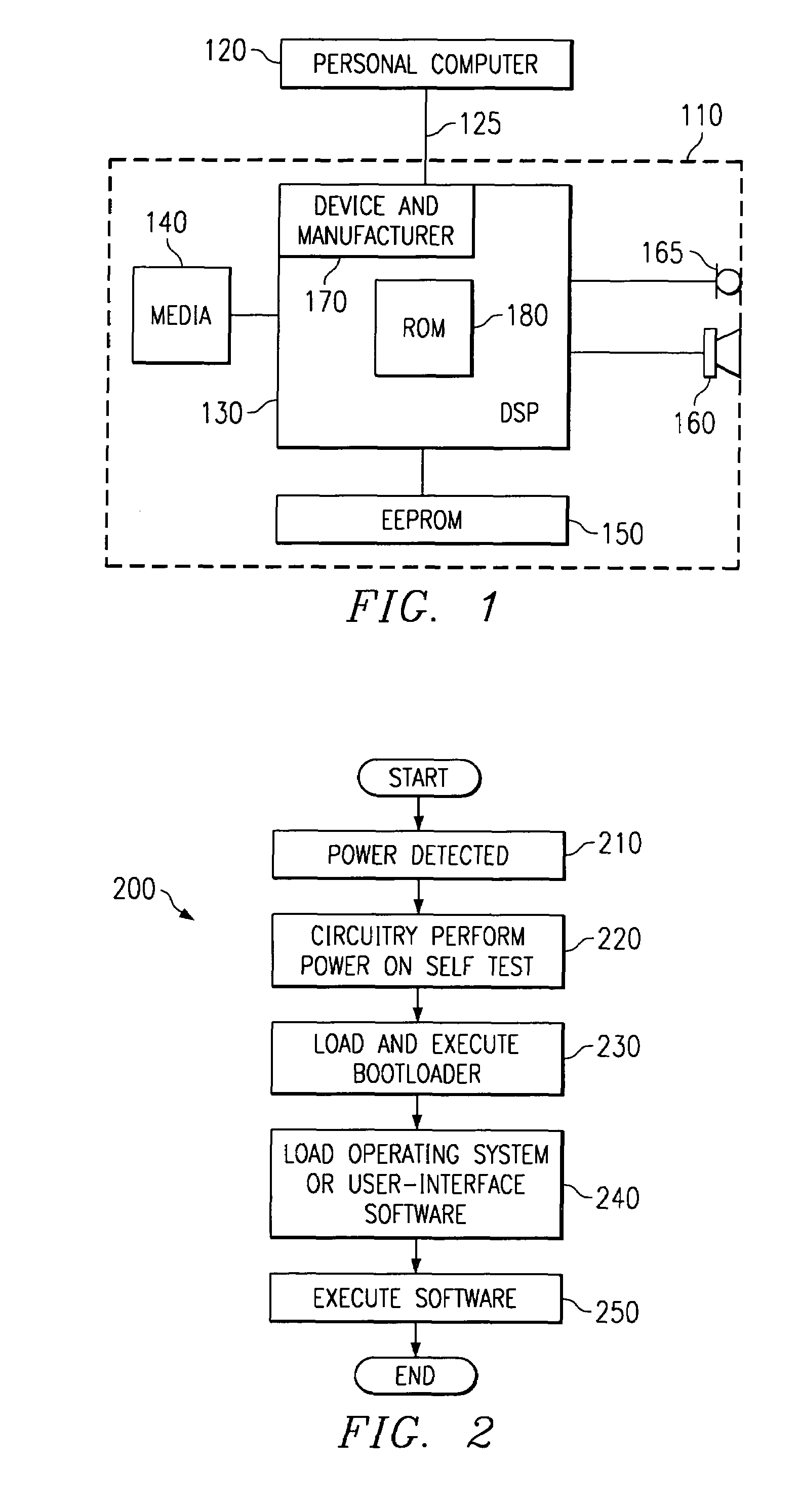
ActiveUS7237121B2Sufficient level of flexibilitySmall overall net increase of die areaDigital data processing detailsUser identity/authority verificationComputer scienceDigital device
A secure bootloader for securing software and systems in a digital device 110 by ensuring only encrypted and authenticated boot software is loaded and executed in the digital device 110. The encrypted boot software is read into the device 110 and authenticated. If the boot software is not authenticated, then the digital device 110 does not boot.
Owner:TEXAS INSTR INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com