Patents
Literature
140results about How to "Avoid excessive delay" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
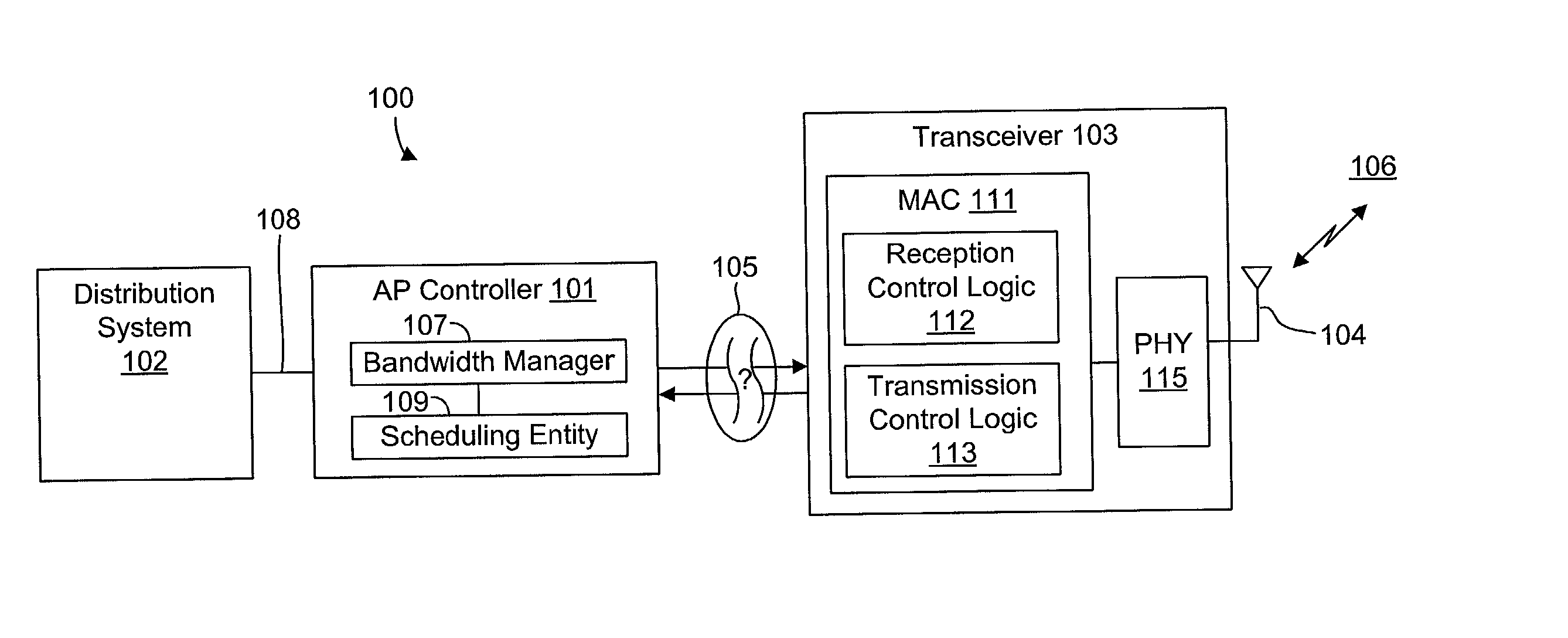
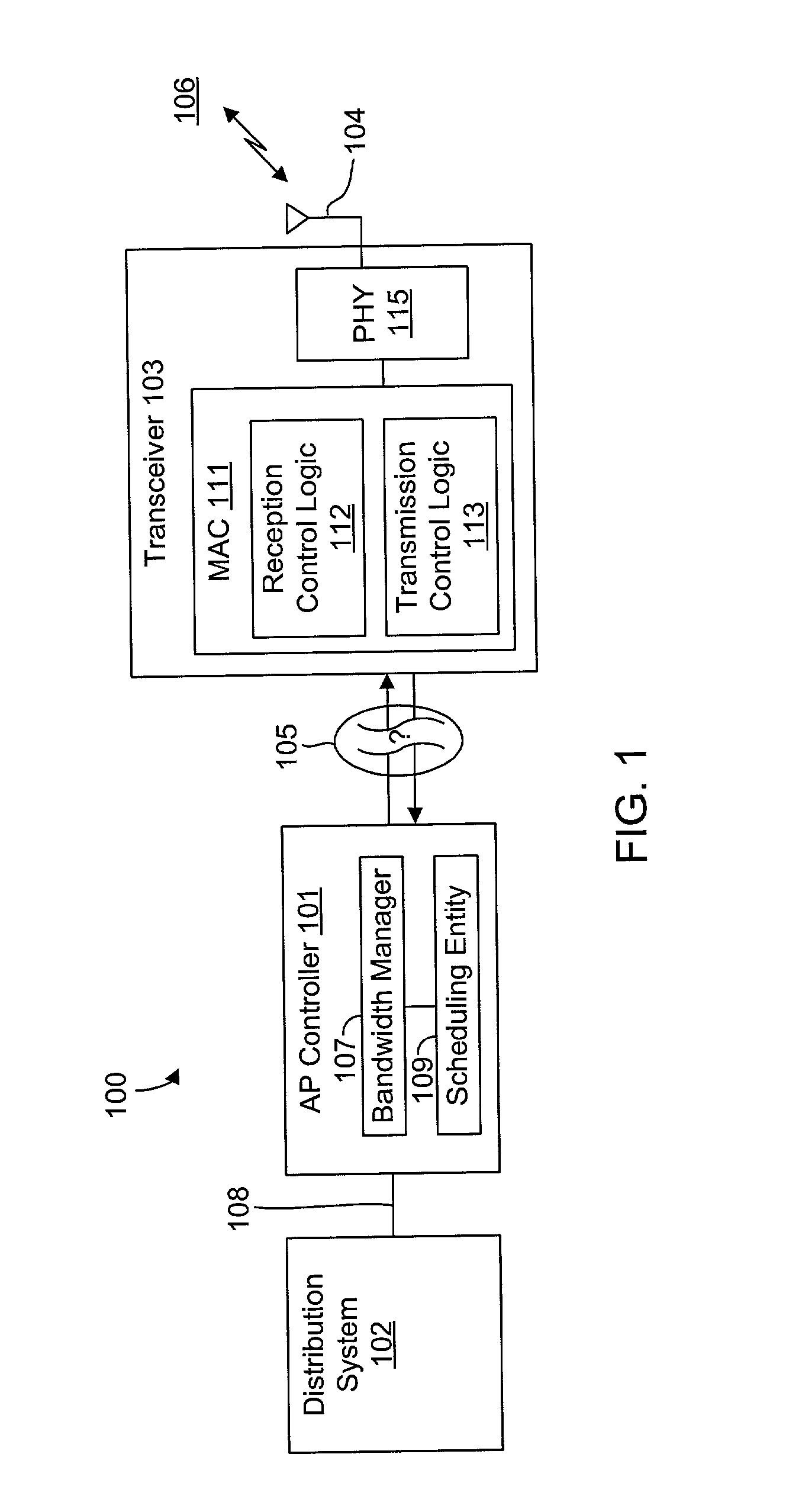
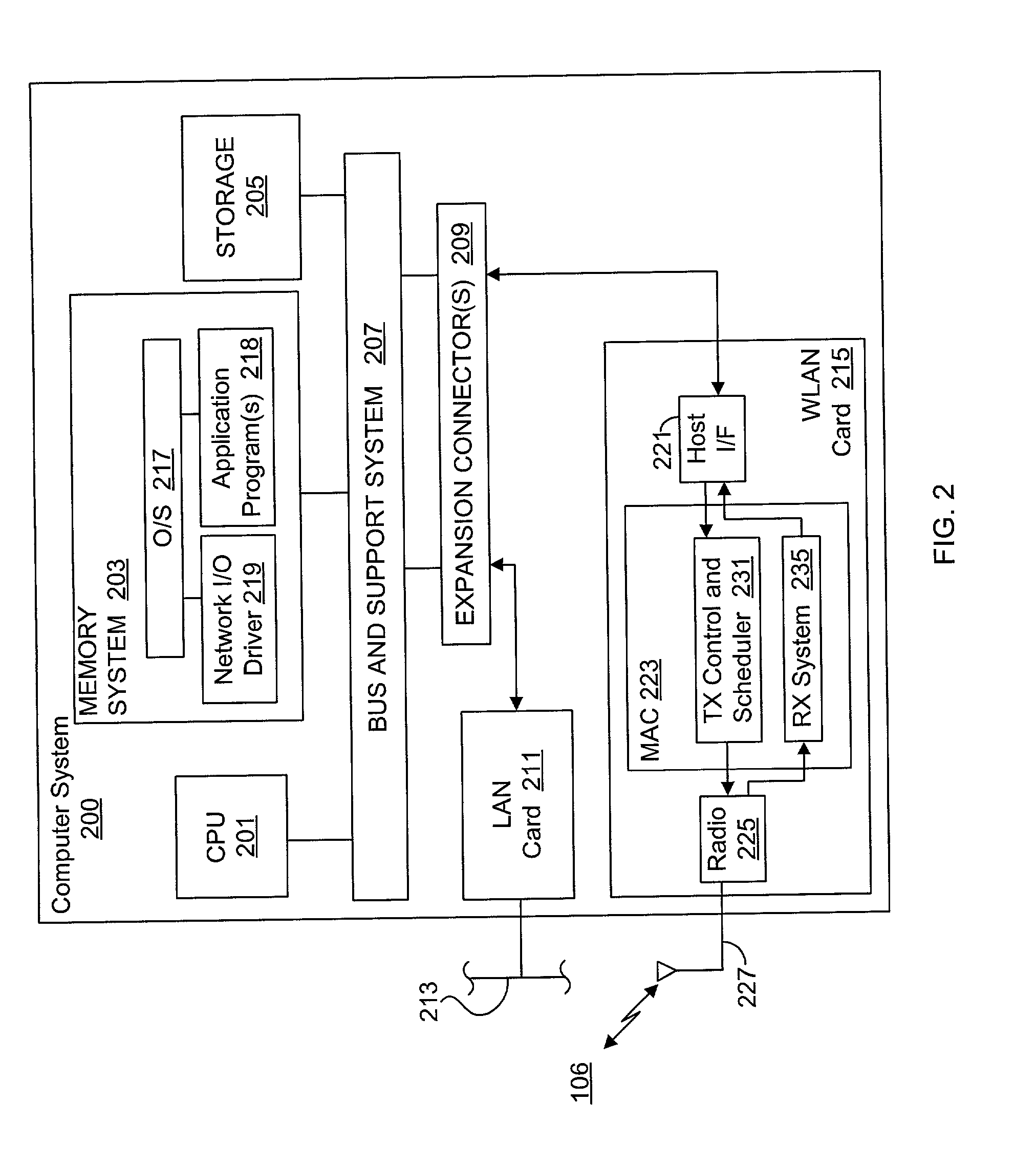
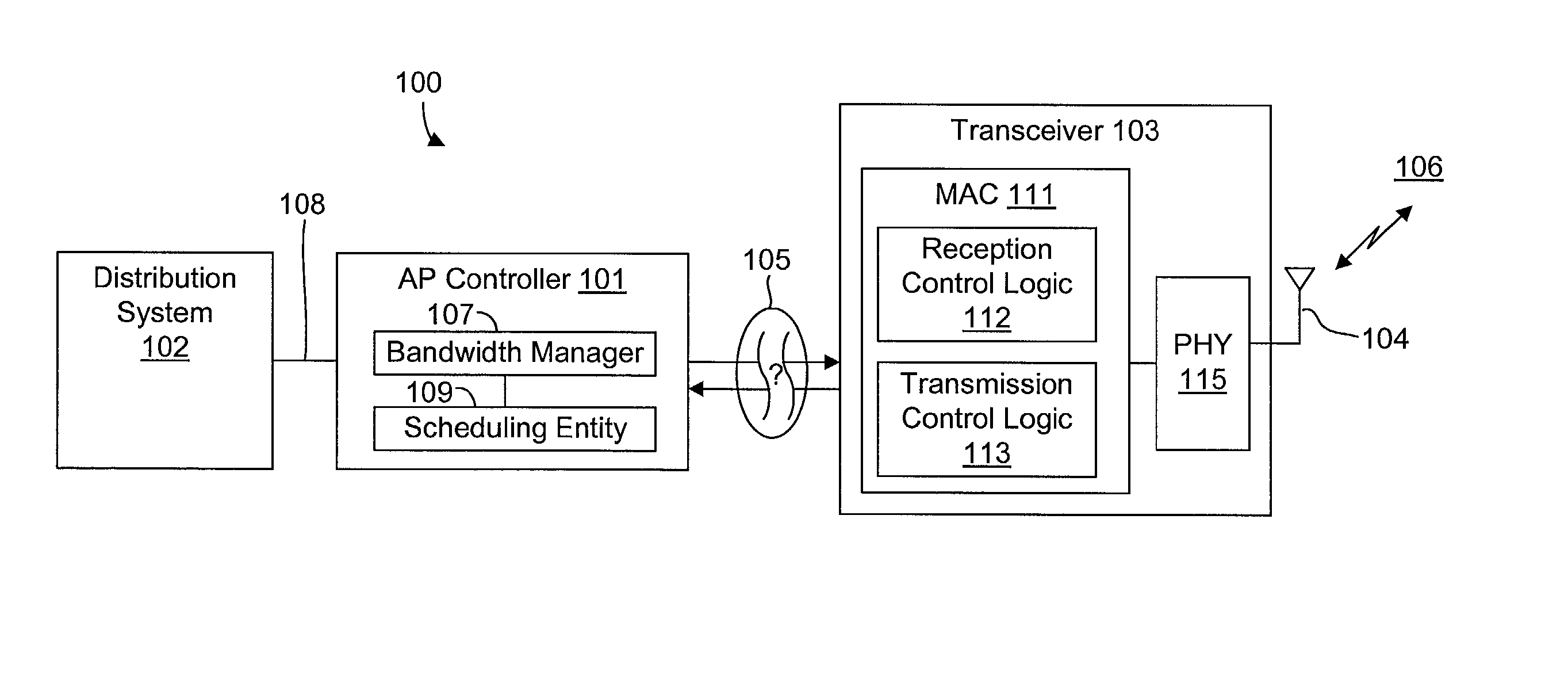
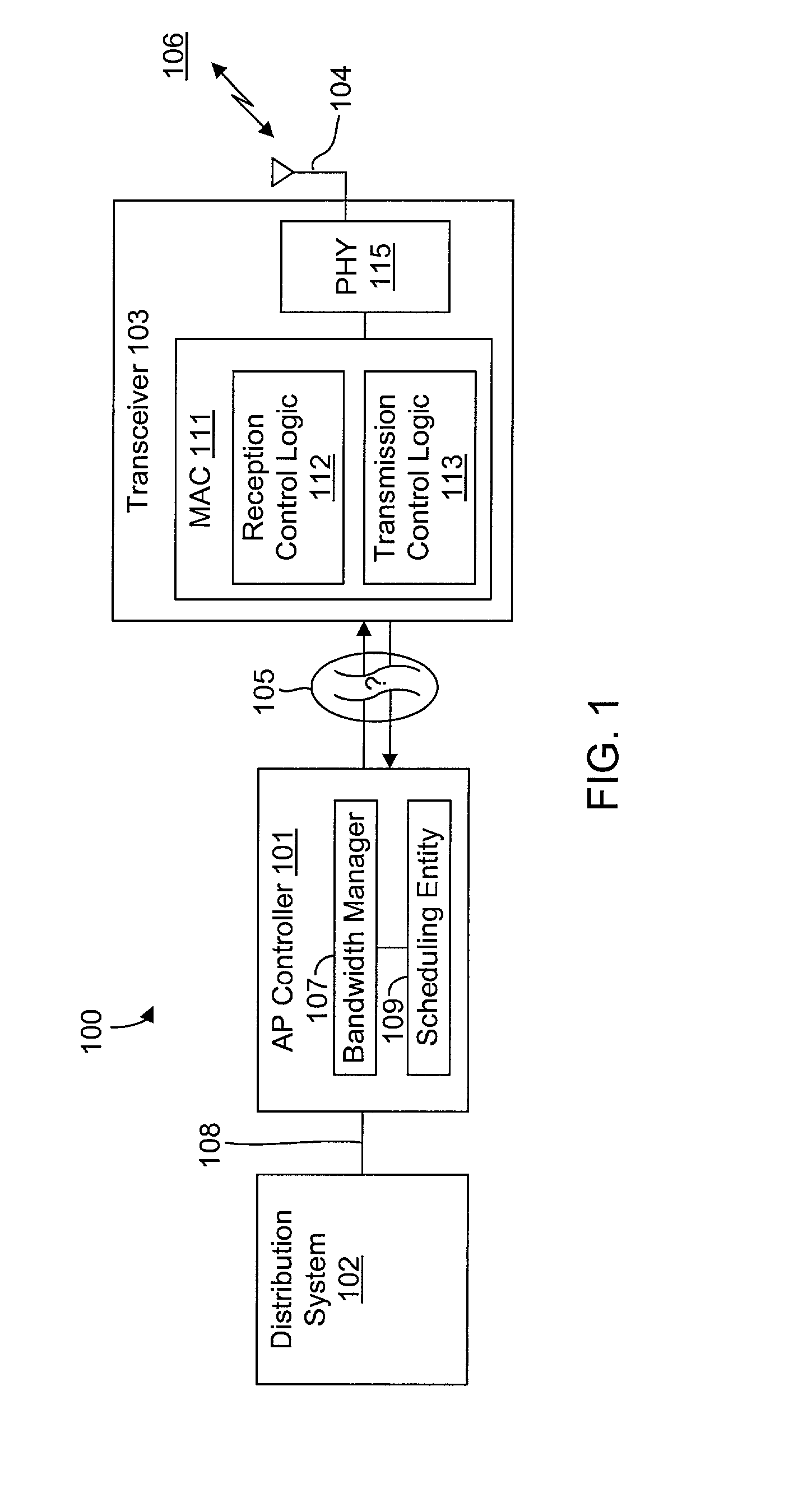
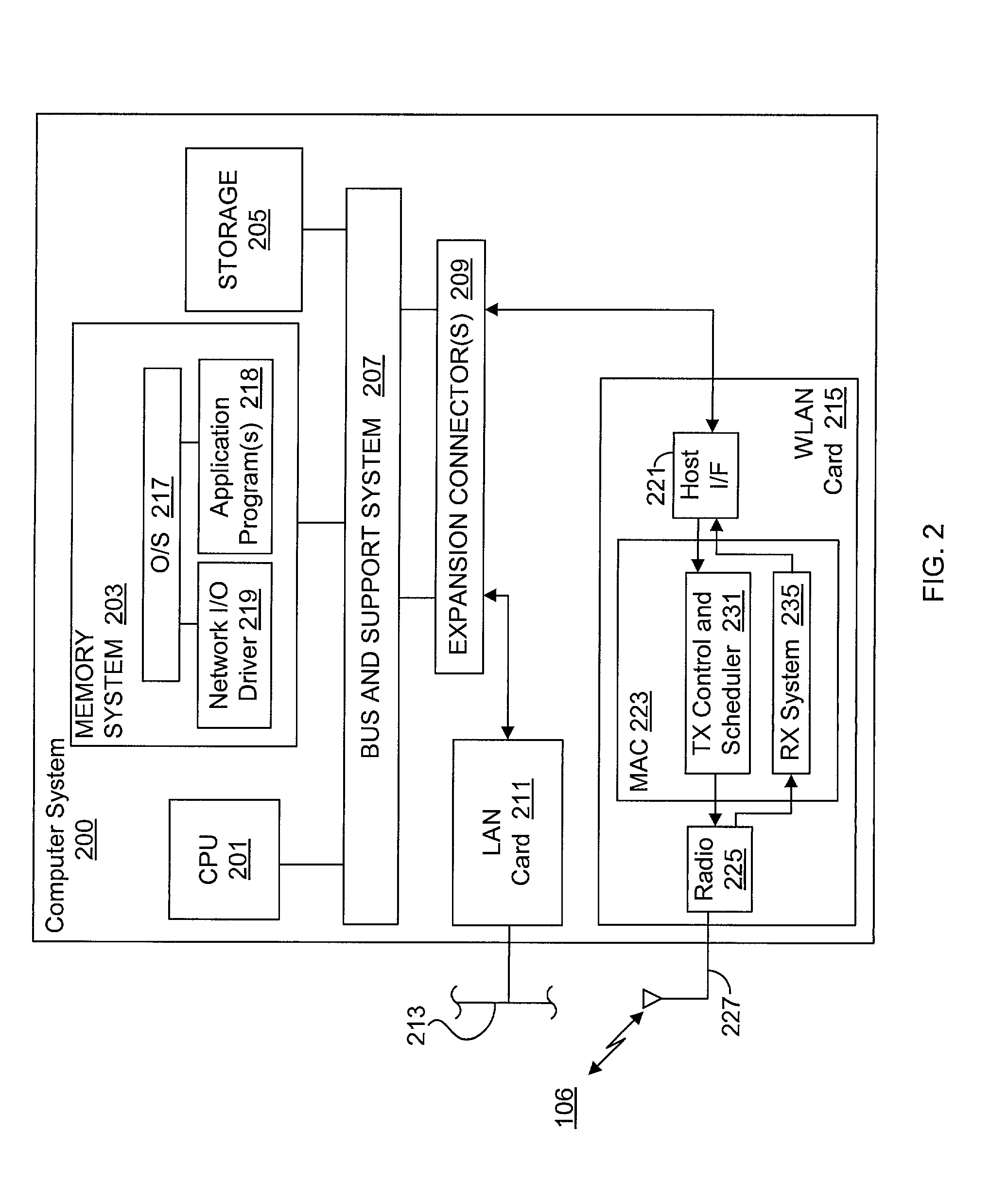
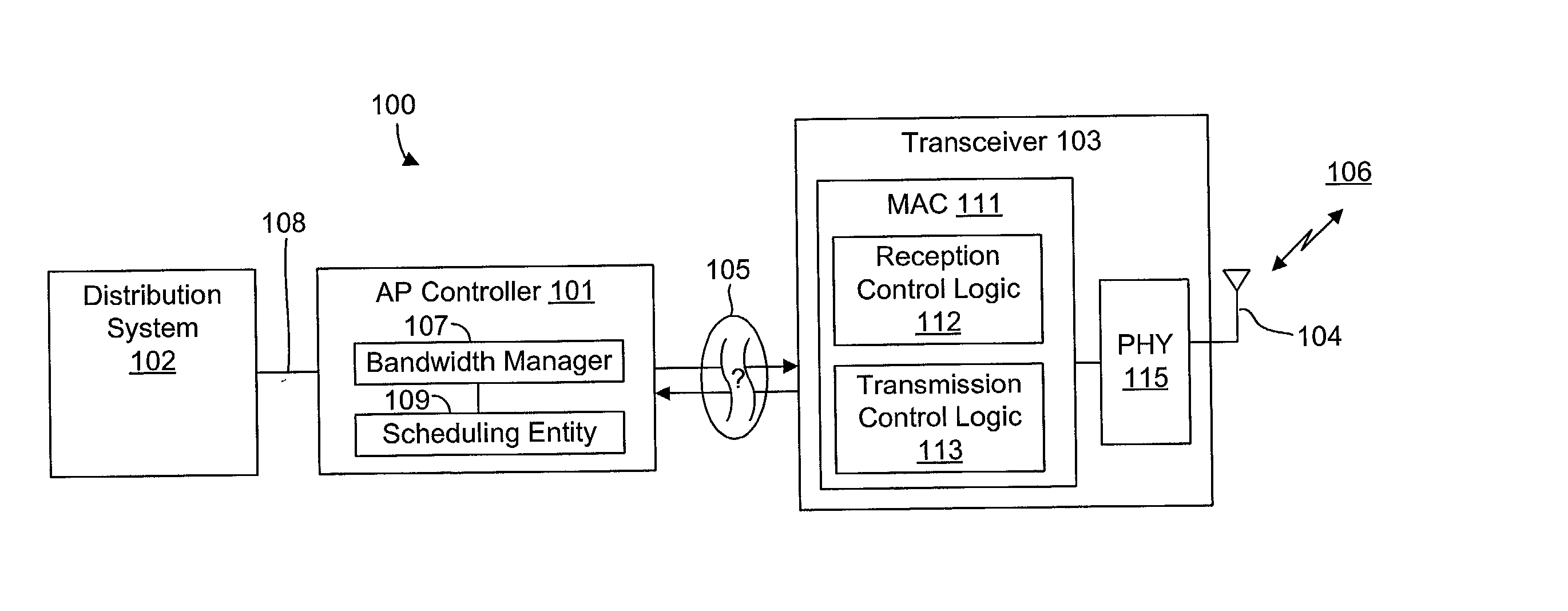
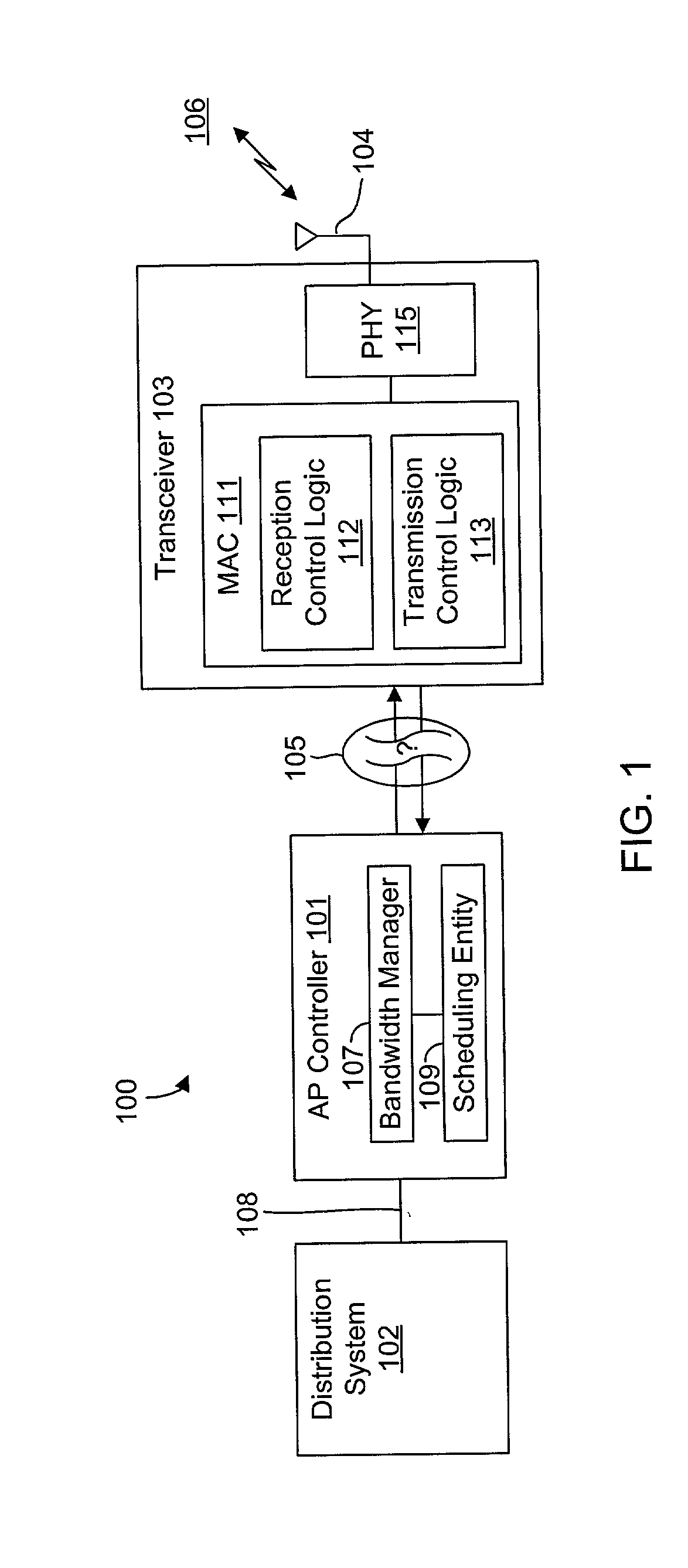
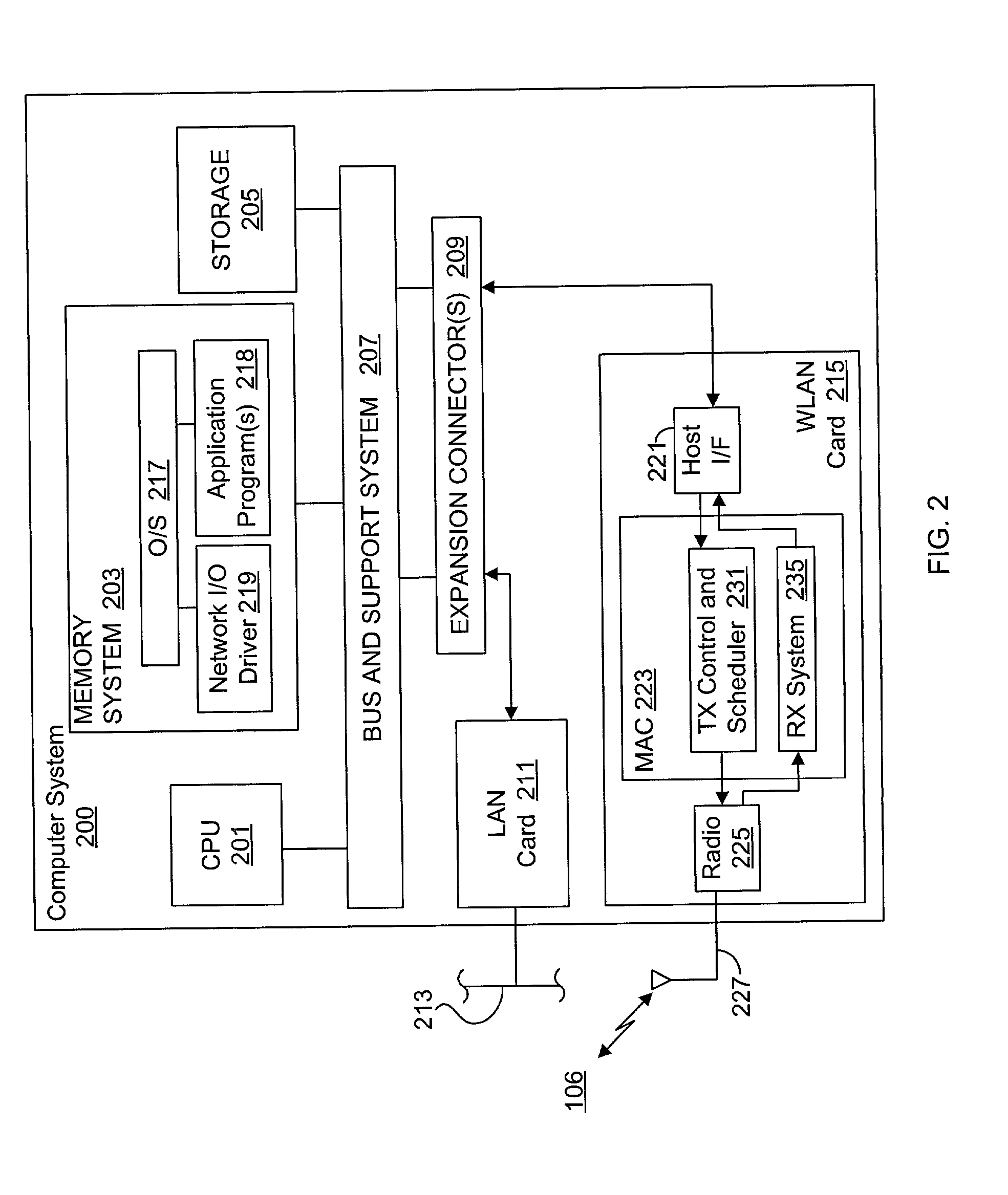
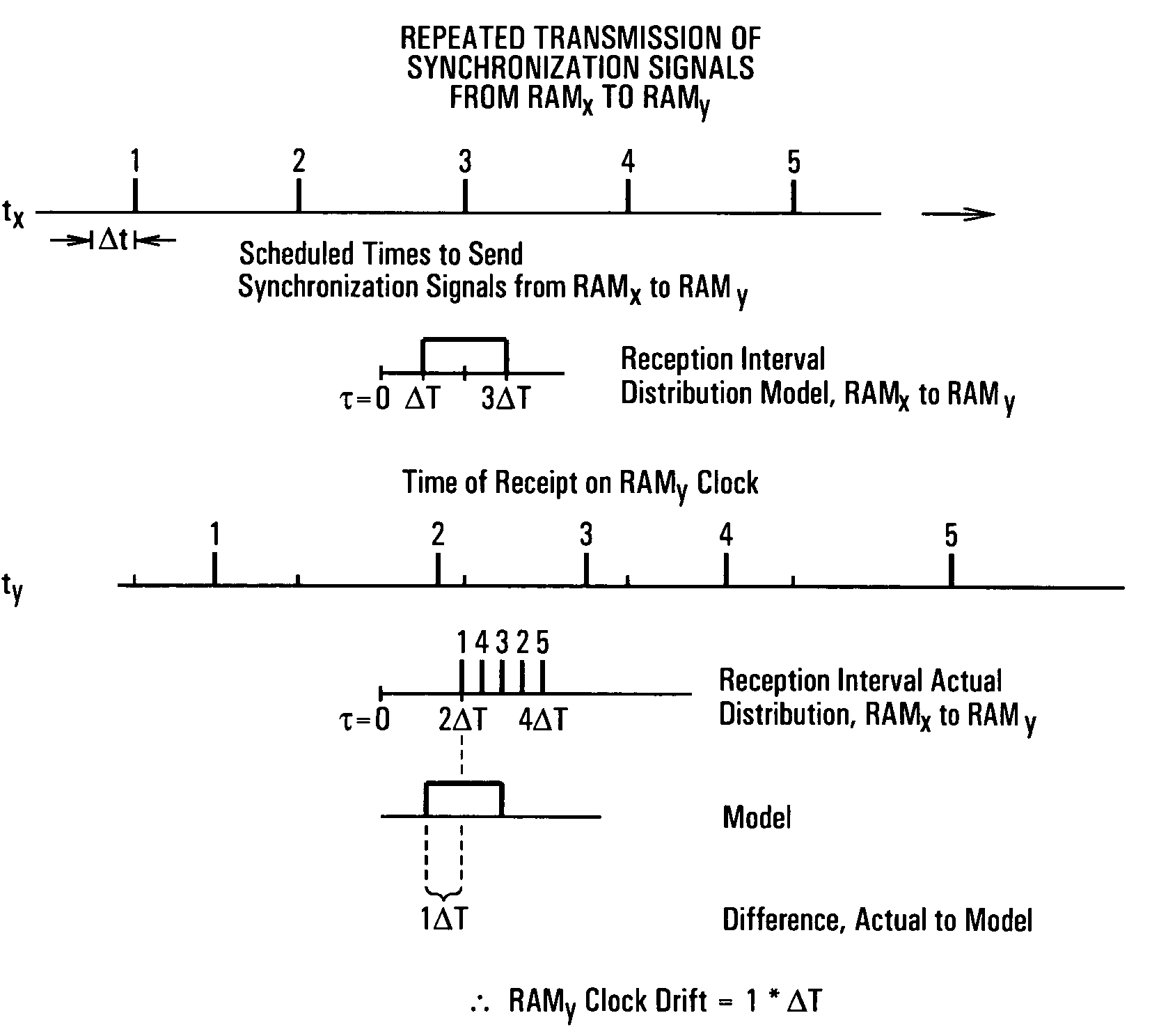
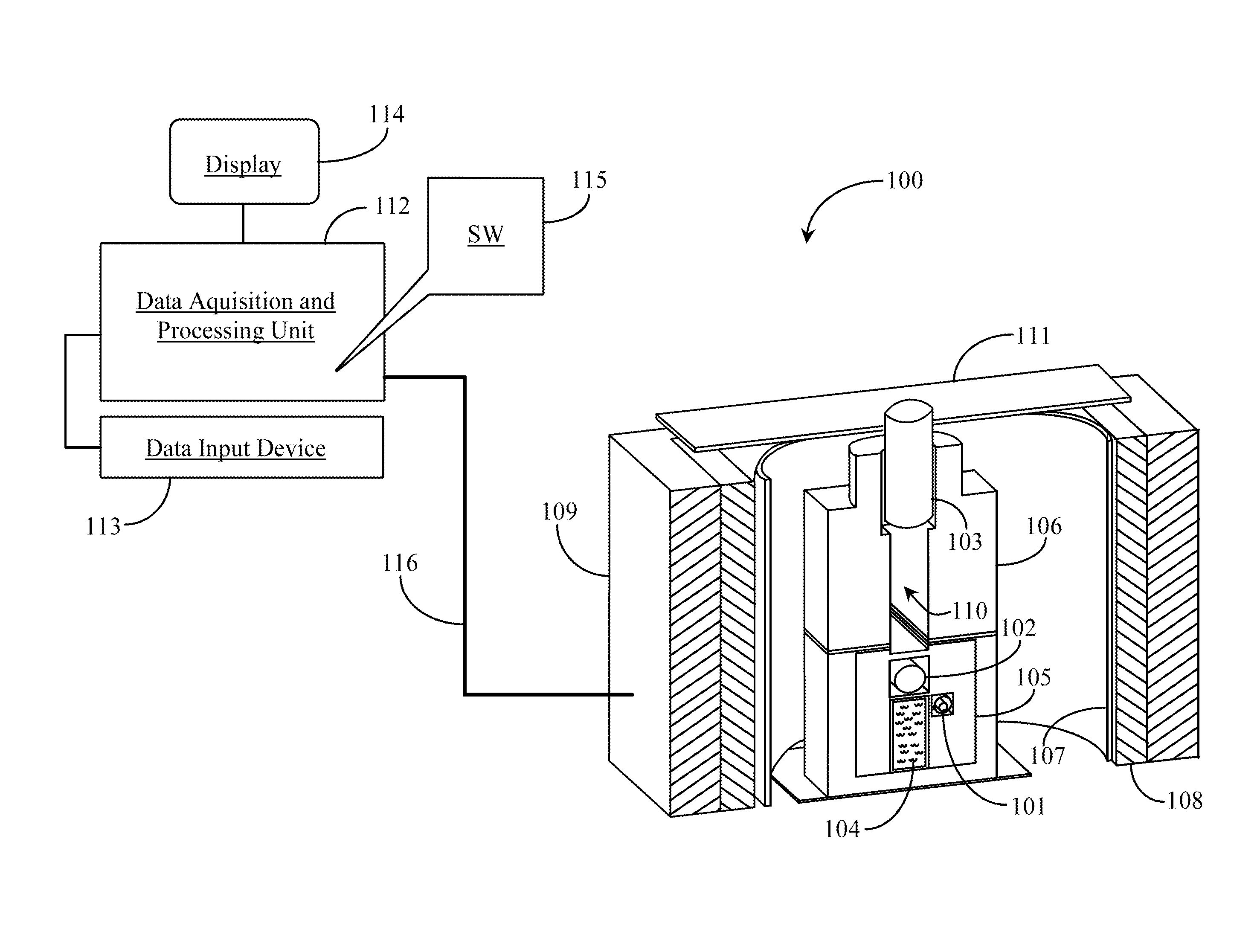
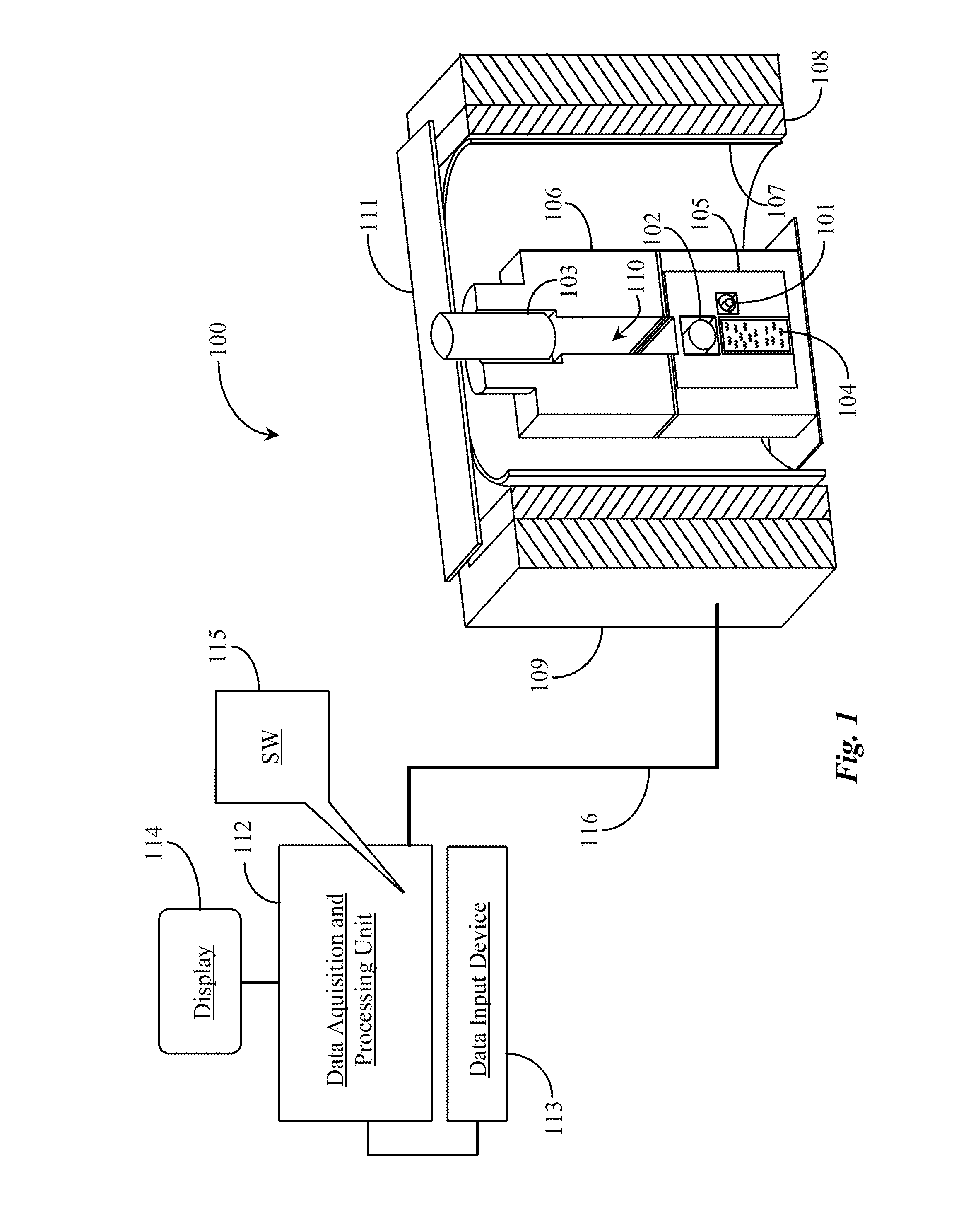
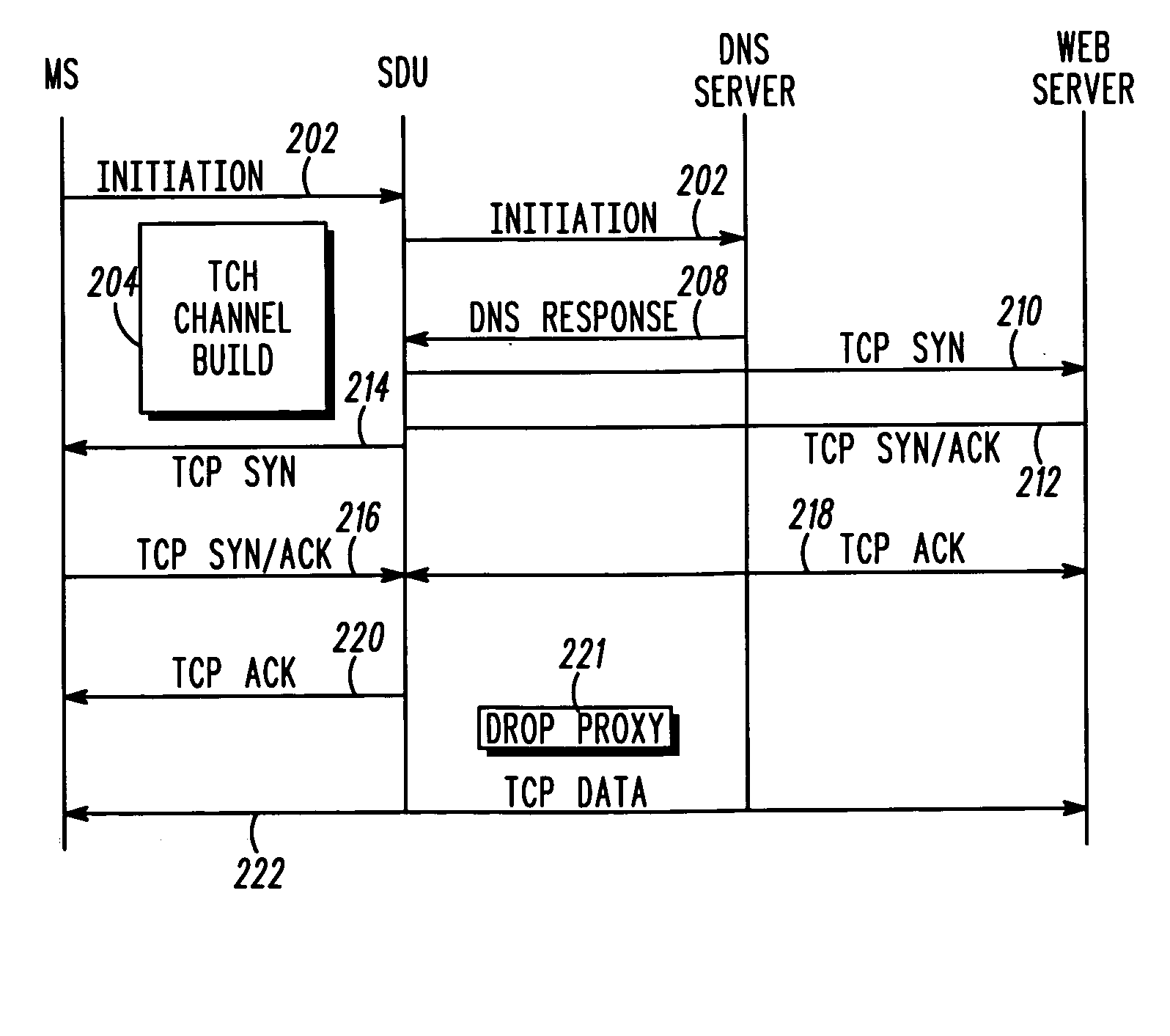
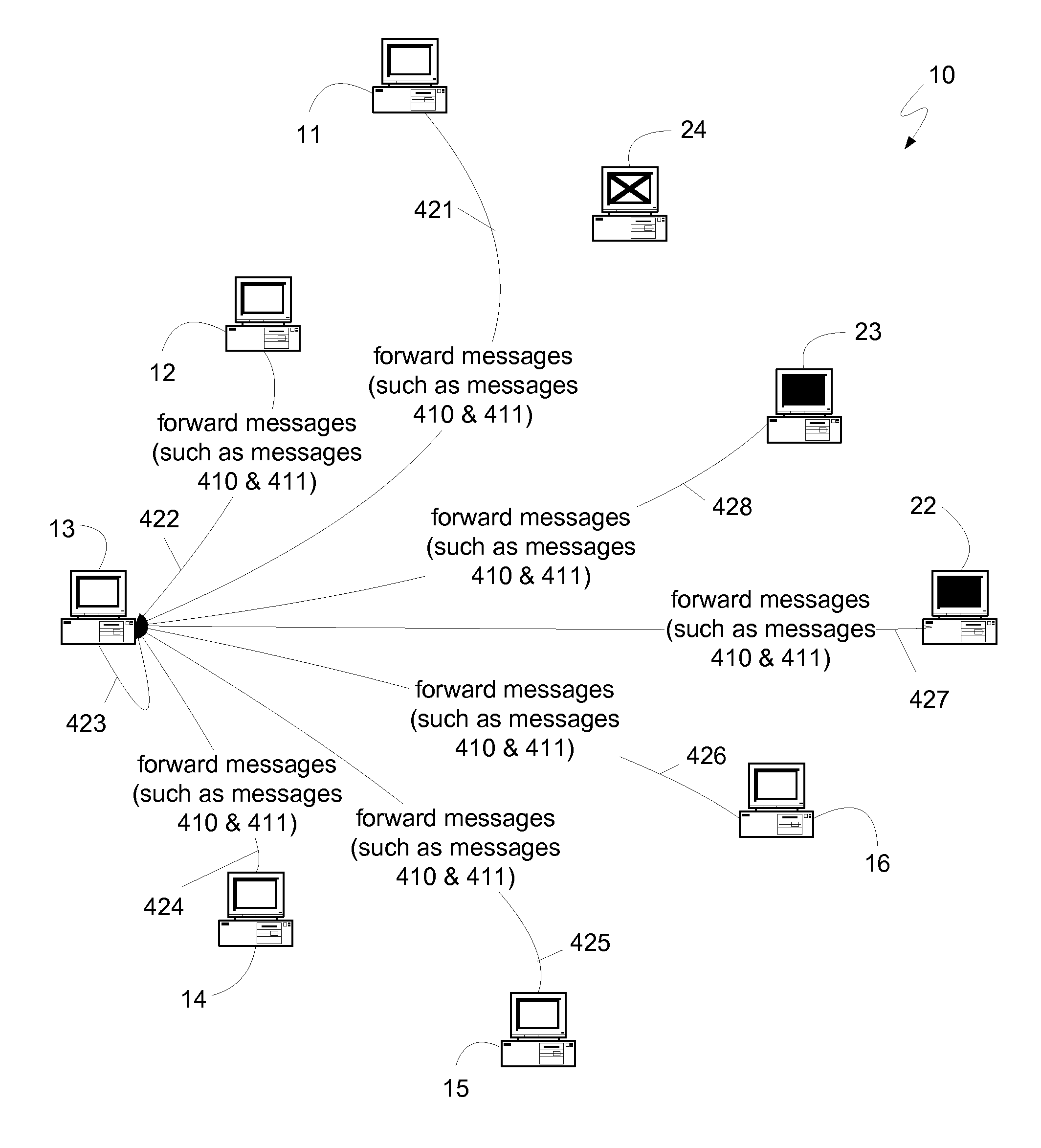
System and method for synchronizing data trasnmission across a variable delay interface
InactiveUS20020089927A1Significant overheadLimitation in wireless bandwidthError prevention/detection by using return channelFrequency-division multiplex detailsSufficient timeComputerized system
A method of synchronizing data transmission between a host computer system and a transmitter across an interface with variable delay or latency. The host computer system marks transition frames between successive transmission intervals and transfers the outgoing frames across the variable interface to the transmitter. The transmitter enqueues outgoing frames into one or more FIFO transmission queue(s) and processes the enqueued frames as appropriate for the communication protocol in use. Marked frames are detected as they reach the head of the appropriate transmit queue. In particular, while bypassing is not active, the transmitter transmits unmarked frames until the end of the current interval, or until there is insufficient time in the interval to transmit another frame or until a marked frame is detected. While bypassing is not active, the transmitter terminates transmission from the transmit queue when a marked frame is detected during each interval. While bypassing is active, the transmitter discards unmarked frames without transmission until a marked frame is detected. During each interval, the transmitter activates bypassing if a marked frame has not been detected and deactivates bypassing if a marked frame is detected while bypassing is active. The transmitter enables queue mark operation if a marked frame is detected while queue mark operation is not enabled. The transmitter increments a bypass counter each time an interval ends without detecting a marked frame, and disables queue mark operation if the bypass counter reaches a predefined limit.
Owner:CONEXANT
System and method for providing a selectable retry strategy for frame-based communications
InactiveUS20020089959A1Eliminate timeBroaden applicationError prevention/detection by using return channelNetwork traffic/resource managementTransceiverCommunications system
A frame-based communications system with selectable retry strategy including a controller that programs a retry strategy field of a frame descriptor of a frame, where the retry value indicates a selected one of a normal retry count, an alternative retry count, and at least one "no retry" option. The system includes a transceiver that attempts retransmission of the frame up to as many times indicated by a selected retry count or until expiration of a frame transmit duration, or that does not attempt retransmission if the retry value indicates no retry. The no retry options may include treating the first attempt as successful or returning an unsuccessful attempt as a failure. The frame itself may be programmed with a request to not acknowledge a successfully received frame to recapture the time normally allocated to acknowledgement frames. The transceiver may include acknowledgement logic that is configured to suppress an acknowledgement frame.
Owner:CONEXANT
System and method of repetitive transmission of frames for frame-based communications
InactiveUS20020089994A1Function increaseLower latencyError prevention/detection by using return channelNetwork traffic/resource managementCommunications systemFrame based
A communications system including a scheduling entity and a transceiver coupled across a variable timing interface. The scheduling entity forwards frames for transmission and identifies selected frames as persistent. The transceiver includes a queue, a frame manager and a transmission scheduler. The frame manager receives and enqueues forwarded frames and the transmission scheduler dequeues and transmits frames from the queue and forwards persistent frames back to the frame manager. The transmission scheduler includes persistence logic that detects a persistent mark and asserts a persistent signal that is detected by the transmission scheduler. The scheduling entity identifies a persistent frame by setting a bit in a transmit control field of the frame descriptor. The scheduling entity sends a clear persistence command to the transceiver to clear a persistent mark of an identified frame. The transceiver may be configured for wireless communications.
Owner:CONEXANT
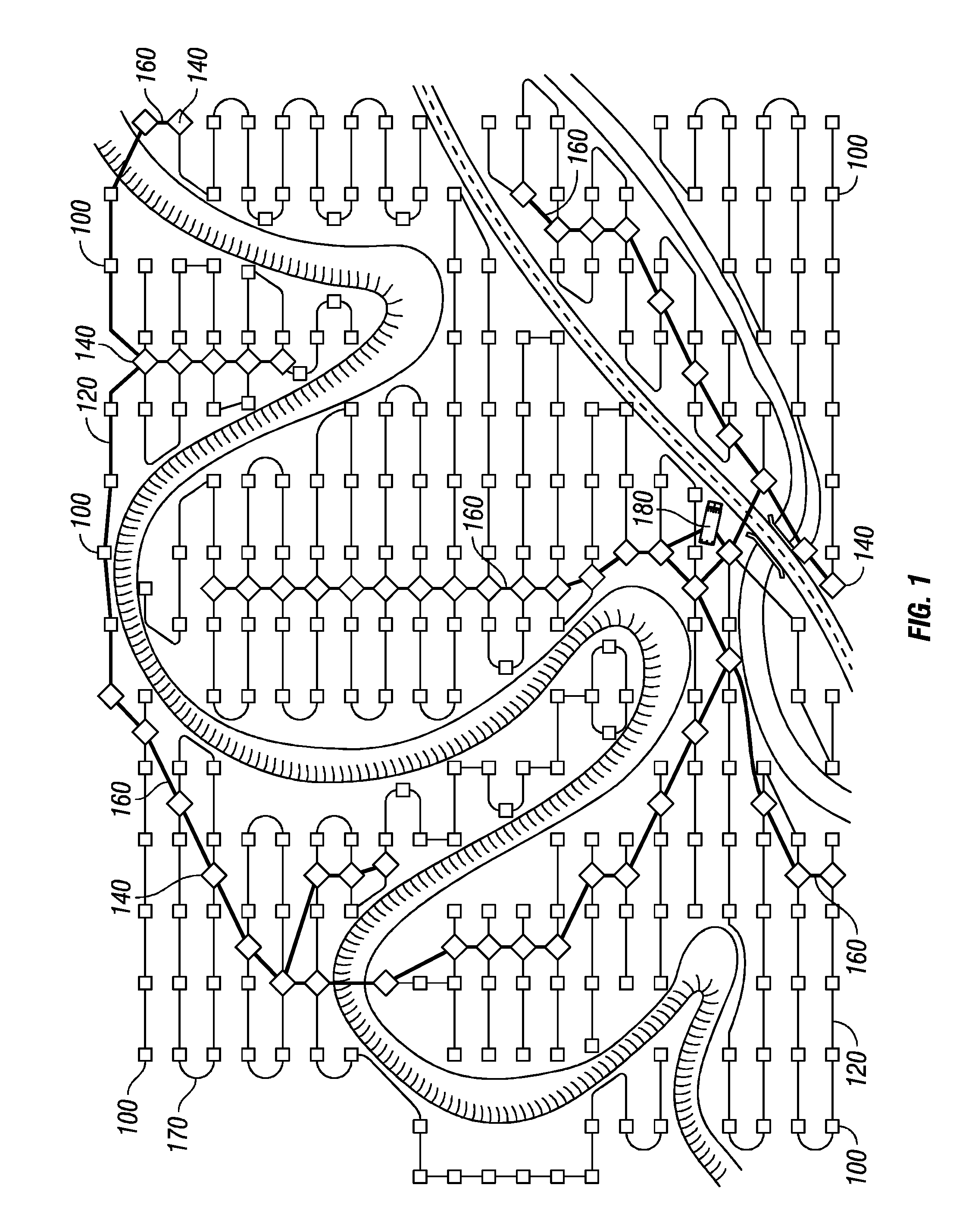
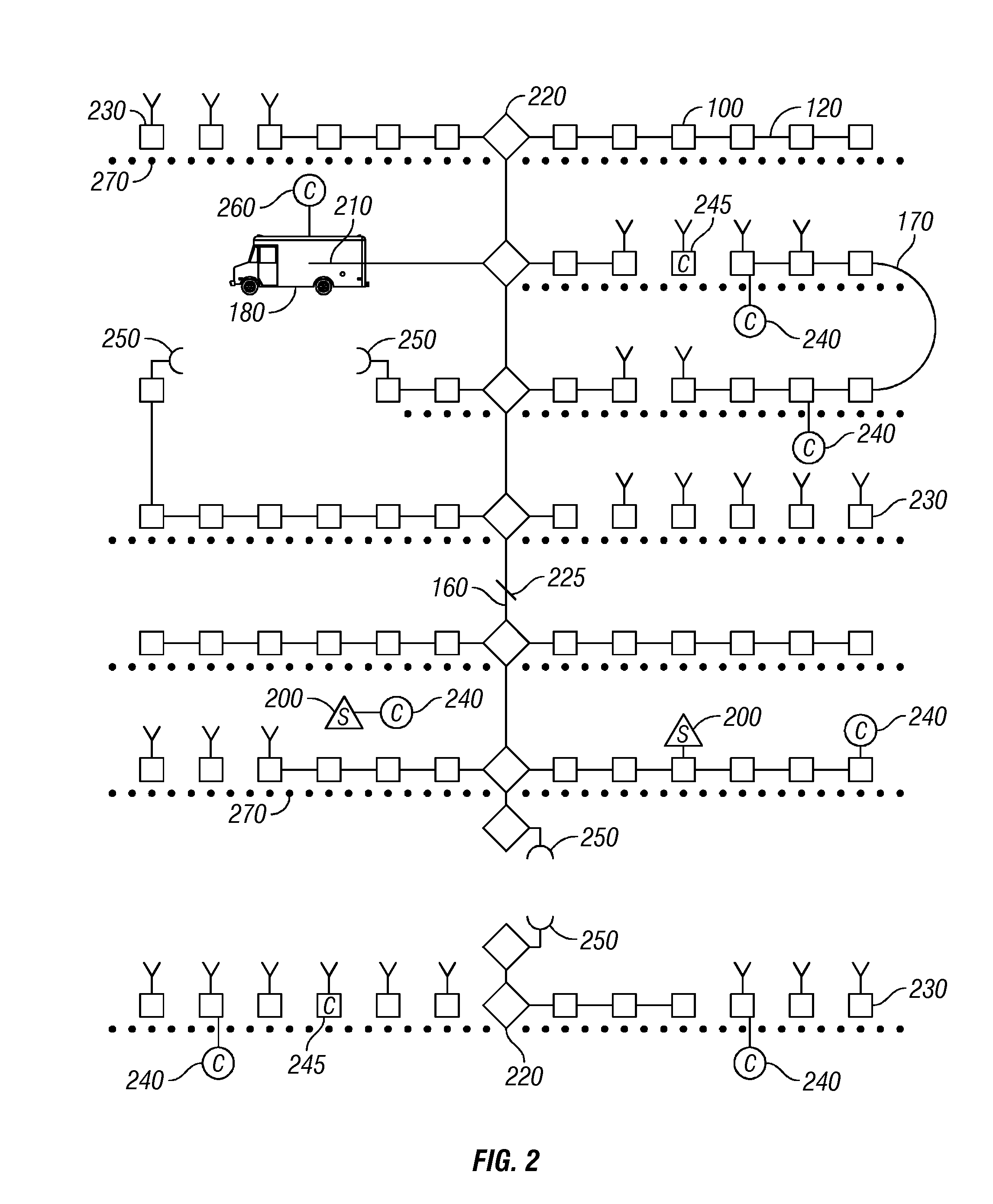
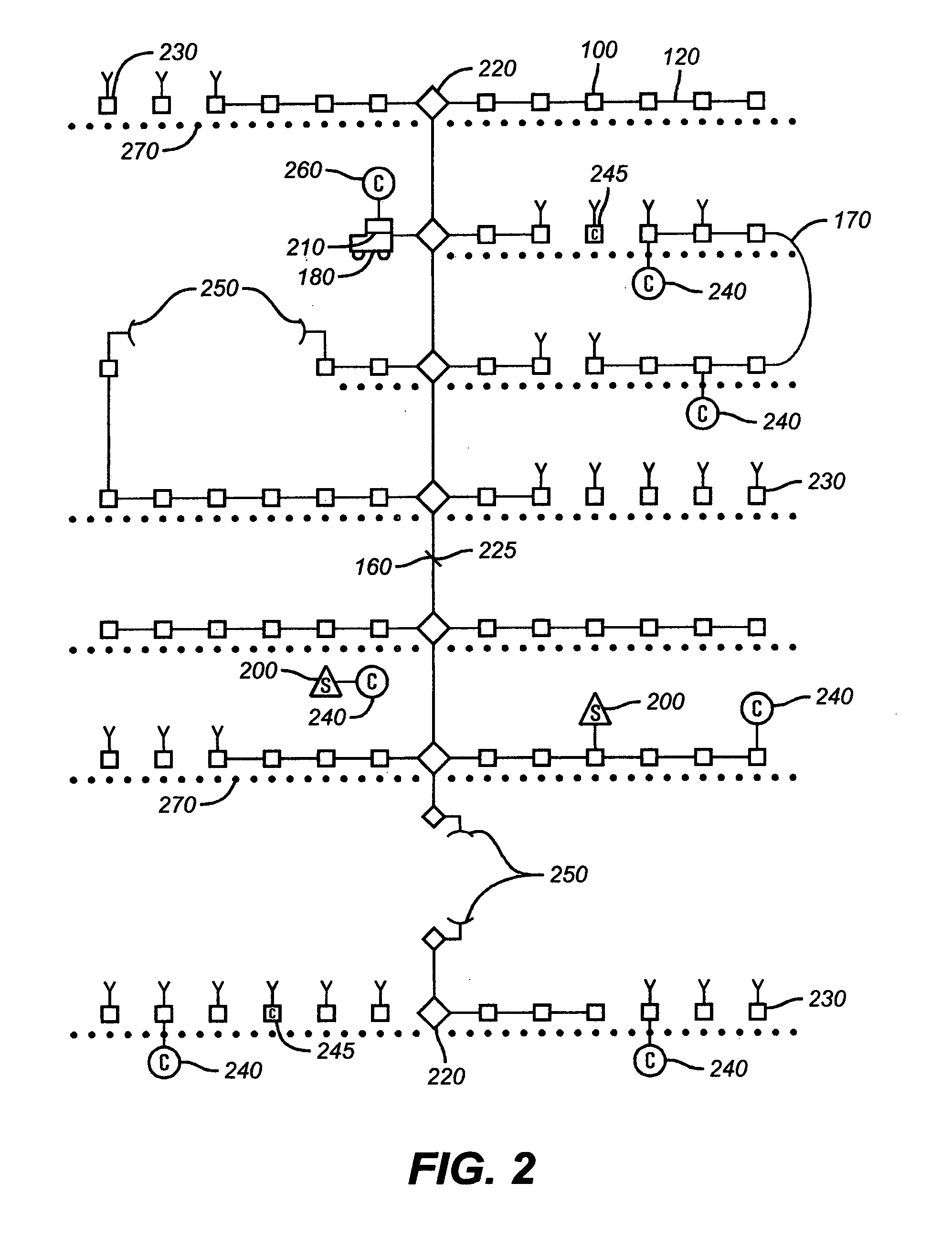
Synchronization and positioning of seismic data acquisition systems
InactiveUS20050047275A1Good synchronizationLess transmission delaySeismic signal receiversSeismic signal transmissionData acquisitionGlobal positioning system receiver
A network distributed seismic data acquisition system comprises seismic receivers, connected to remote acquisition modules, receiver lines, line tap units, base lines, central recording system and a seismic source event generation unit. Global positioning system receivers of full or partial capability are combined with some of these modules and units and a master global positioning receiver aids the distributed receivers. The global positioning receivers may be used to synchronize high precision clocks as well as to provide positioning information. A master clock is designated and one or more high precision clocks is added to the network to correct for timing uncertainty associated with propagation of commands through the network. Seismic receivers and seismic sources are thereby synchronized with greater accuracy than otherwise possible, thus enabling an improvement in subsurface geologic imaging.
Owner:GEO X SYST
Fast transaction commit
InactiveUS7558883B1Few message delayMaintain consistencyError detection/correctionDatabase distribution/replicationClient-sideComputing systems
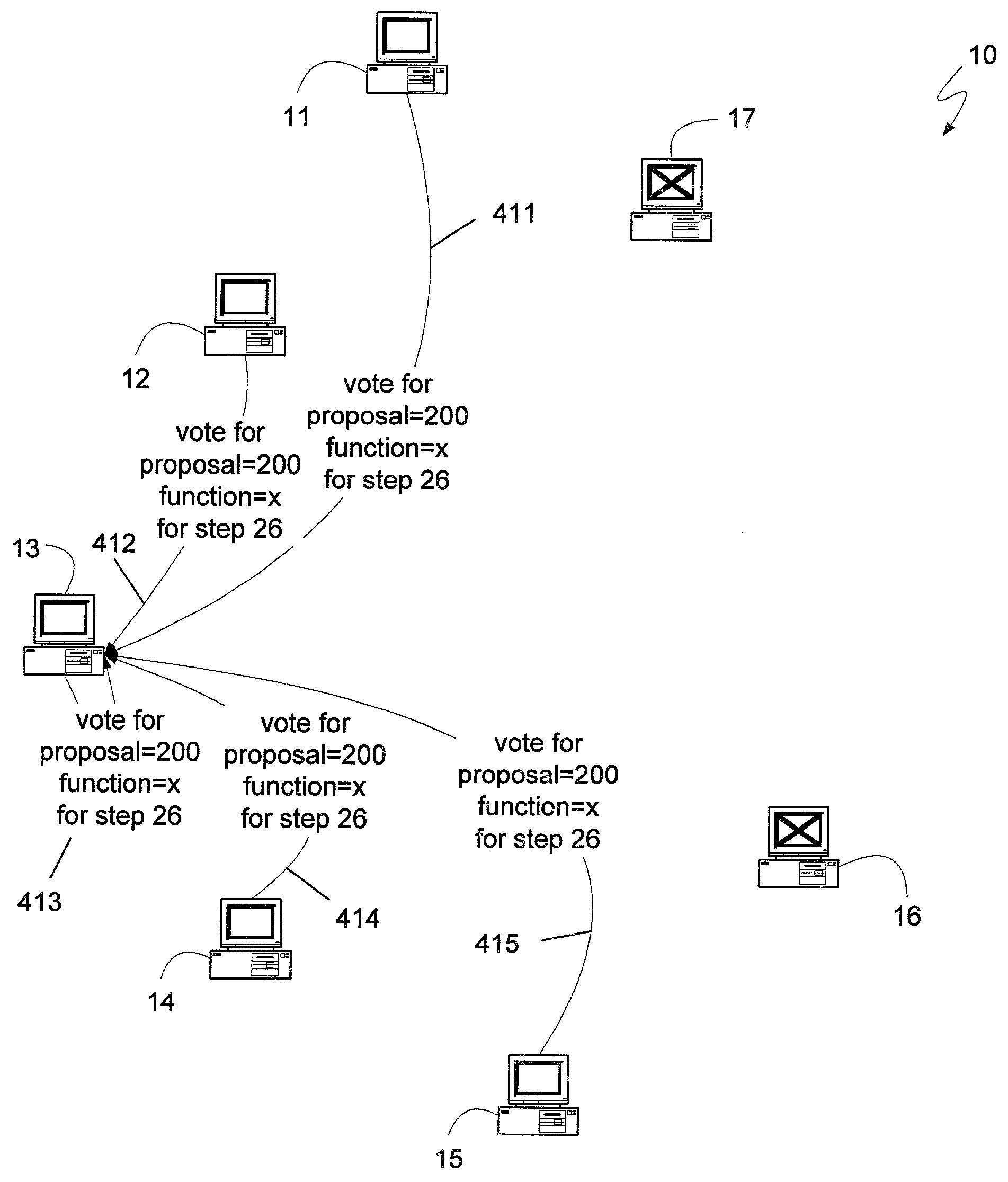
A distributed computing system, having a sufficient number of devices and requiring a sufficiently large number of devices to select any proposal, can maintain synchronization between its constituent devices and respond to client requests with as few as two message delays. A leader can synchronize the devices of the system and establish a safe proposal number for all current and future steps of the system. Devices can then receive client requests directly, treating the request as a proposal having the proposal number determined previously by the leader, and voting for the proposal. If the client receives an indication from a least a quorum of devices, where a quorum can be the minimum number of devices that can be operational at a given time, the client can know that the request was selected. If two or more clients attempt to request different functions at approximately the same time, the system may not select either request, in which case a leader can be requested to determine if any requests may have been selected, and to reestablish a safe proposal number. Systems with fewer devices can also implement the message-delay-reducing algorithm if they can also revert to the standard Paxos algorithm if an insufficient number of devices are operational. Such algorithms can be used to provide an efficient method for determining whether to commit or abort a client transaction.
Owner:MICROSOFT TECH LICENSING LLC
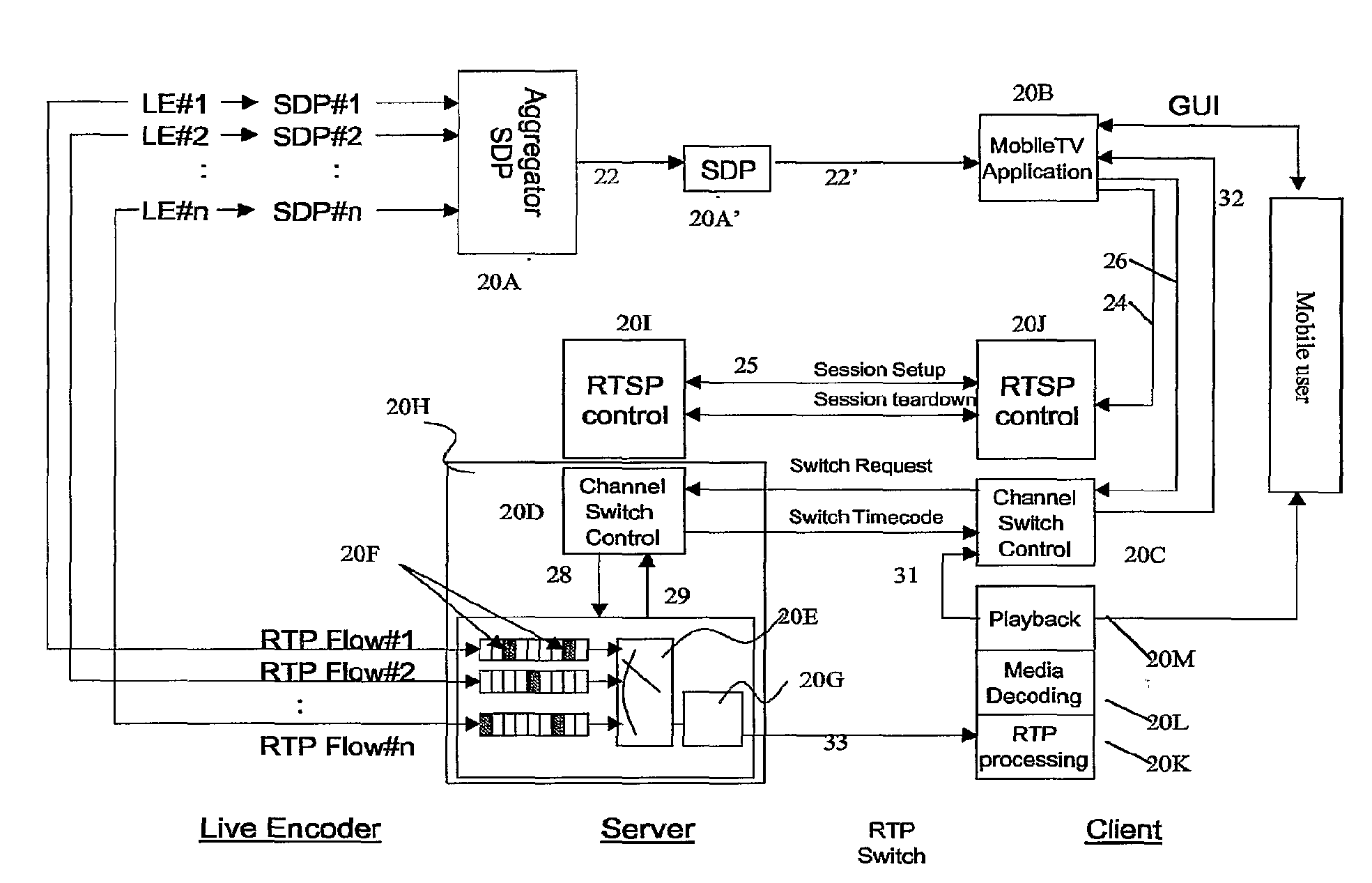
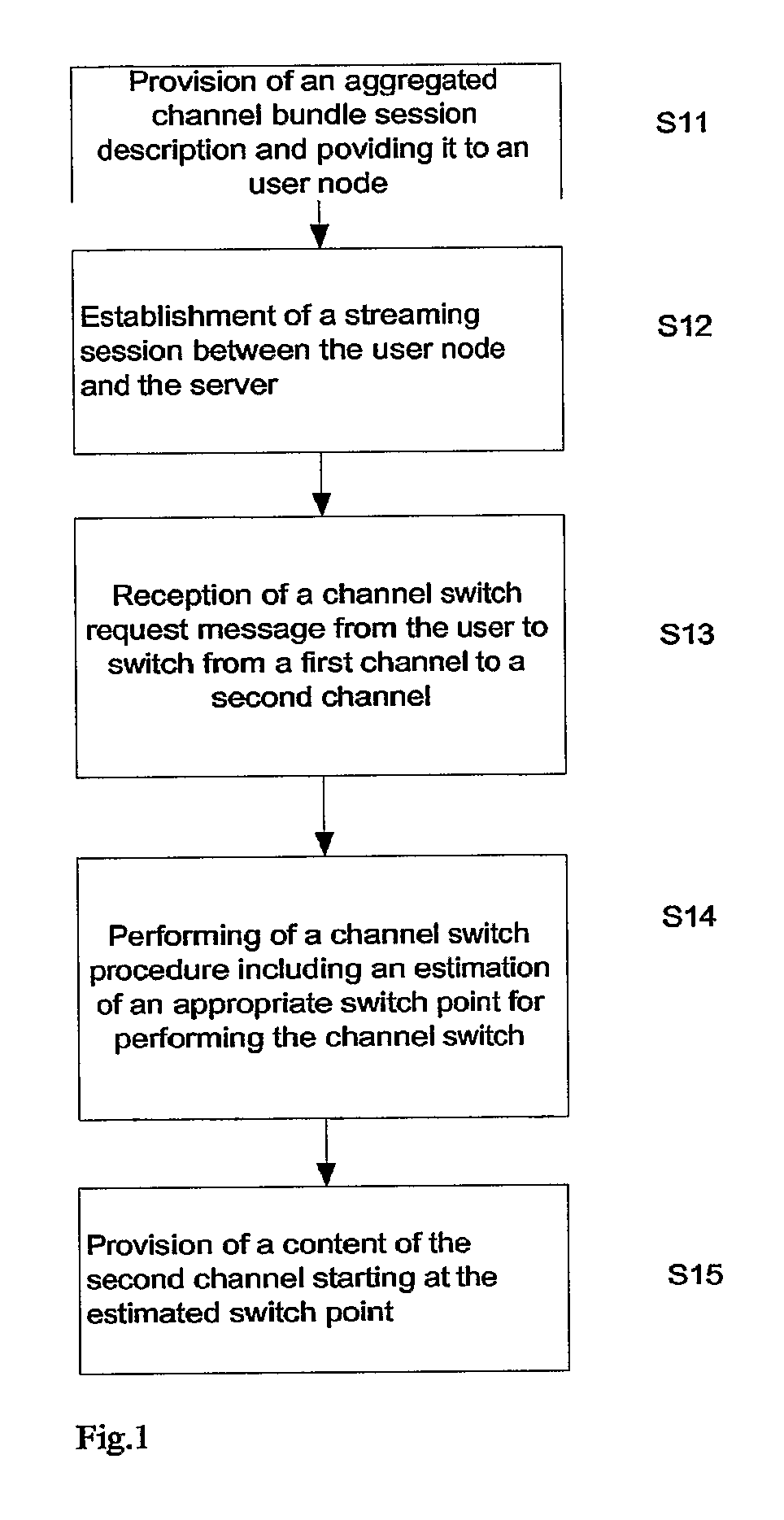
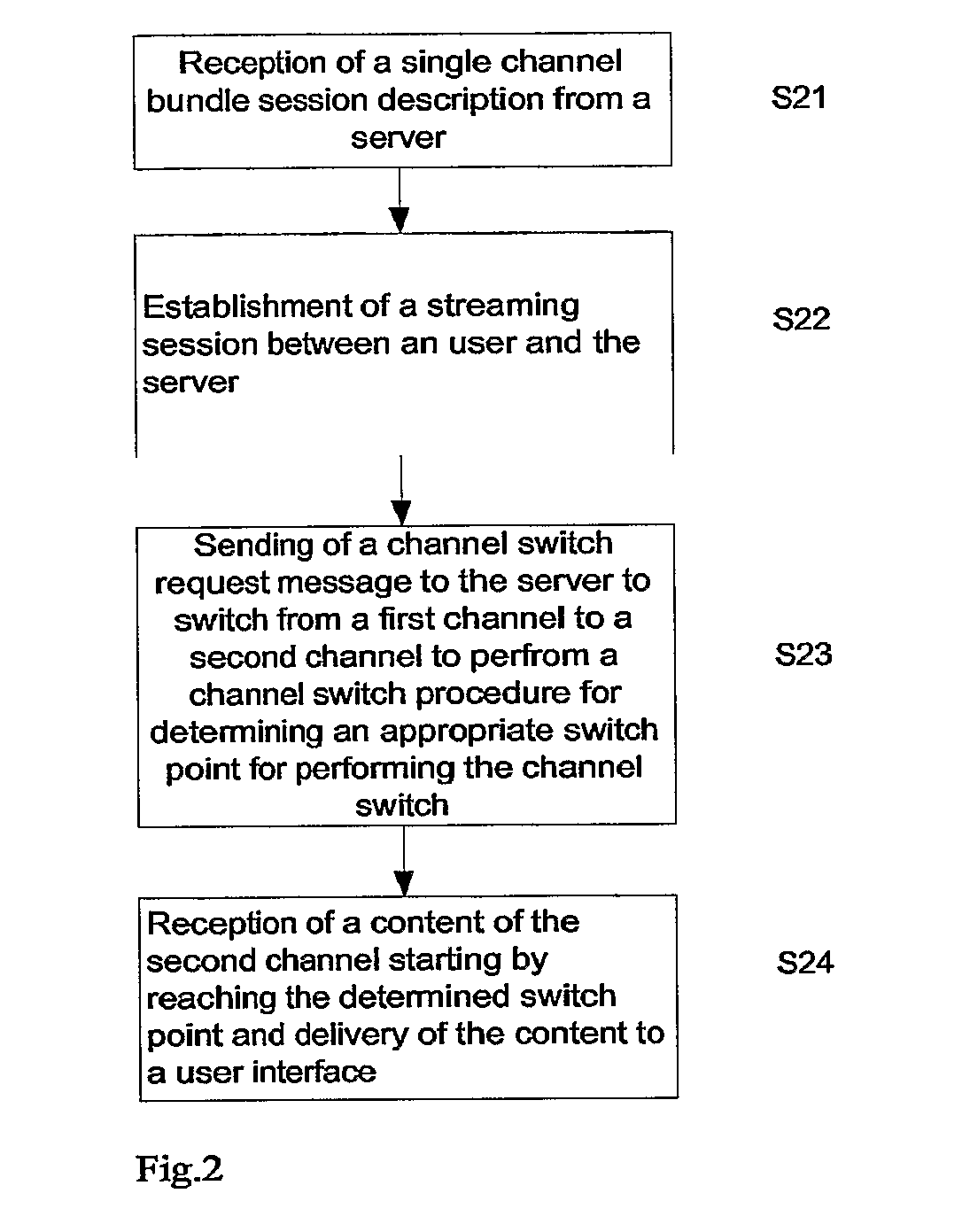
On-Demand Multi-Channel Streaming Session Over Packet-Switched Networks
InactiveUS20080151885A1Avoid excessive delayMinimal impactPulse modulation television signal transmissionData switching by path configurationTemporal informationSingle session
An aggregation procedure for aggregating of a number of session descriptions parameters corresponding to a multitude of channels into one single session description. Each channel is described by a mandatory unique identifier. A corresponding client application processes the SDP describing the channel bundle and uses the found information for allowing a user to switch to a channel associated with a certain identifier. Signaling of a channel switch control unit, which is part of the multi-channel streaming server, receives a multitude of RTP flows and selects one of the flows for forwarding to the client. A switching point determination is a part of the channel switch control unit and determines the next possible point of time for switching to a requested channel. The client application receives time information for the switch point in response to a channel switch request.
Owner:TELEFON AB LM ERICSSON (PUBL)
Fast byzantine paxos
ActiveUS7620680B1Accurate authenticationProvide securityMultiple digital computer combinationsTransmissionDigital signatureClient-side
A distributed computing system can operate in the face of malicious failures on the part of some of its constituent devices, and provide a minimum of message delays between receiving a client request and providing a response, when each device within the system verifies the sender of any message it receives, and the propriety of the message. The sender can be verified through message authentication schemes or digital signature schemes. The propriety of a message can be verified by receiving a sufficiently large number of equivalent, properly authenticated messages. If the number of malicious devices is represented by the variable “M”, a sufficient number of equivalent, properly authenticated messages to verify that the message is true can be any number of messages greater than M. Furthermore, to verify that a leader device is not maliciously submitting different proposals to different devices using the same proposal number, a quorum of devices can be required to select a proposal, where a quorum is a sufficiently large number of devices such that any other quorum has, as a majority of its devices, non-malicious devices from the first quorum. Therefore, the distributed computing system can operate properly with M number of malicious failures and F number of total failures, and with a minimum of message delays, if the number of constituent devices in the distributed computing system is greater than 3F+2M. Additionally, if the distributed computing system can revert to a more traditional algorithm if too many devices fail or become malicious, it can use a message-delay-reducing algorithm while having as few as 2Q+F+2M+1 constituent devices, where Q is the number of devices that can fail and still allow the system to use a message-delay-reducing algorithm.
Owner:MICROSOFT TECH LICENSING LLC
Synchronization of seismic data acquisition systems
ActiveUS7269095B2Good synchronizationLess transmission delaySeismic signal transmissionSeismic signal recordingTime errorData acquisition
A network distributed seismic data acquisition system comprises seismic receivers connected to remote acquisition modules, receiver lines, line tap units, base lines, a central recording system and a seismic source event generation unit synchronized to a master clock. One or more high precision clocks is added to the network to correct for timing uncertainty associated with propagation of commands through the network. Seismic receivers and seismic sources are thereby synchronized with greater accuracy than otherwise possible. Timing errors that interfere with the processing of the seismic recordings are greatly reduced, thus enabling an improvement in subsurface geologic imaging.
Owner:INOVA SYST CORP
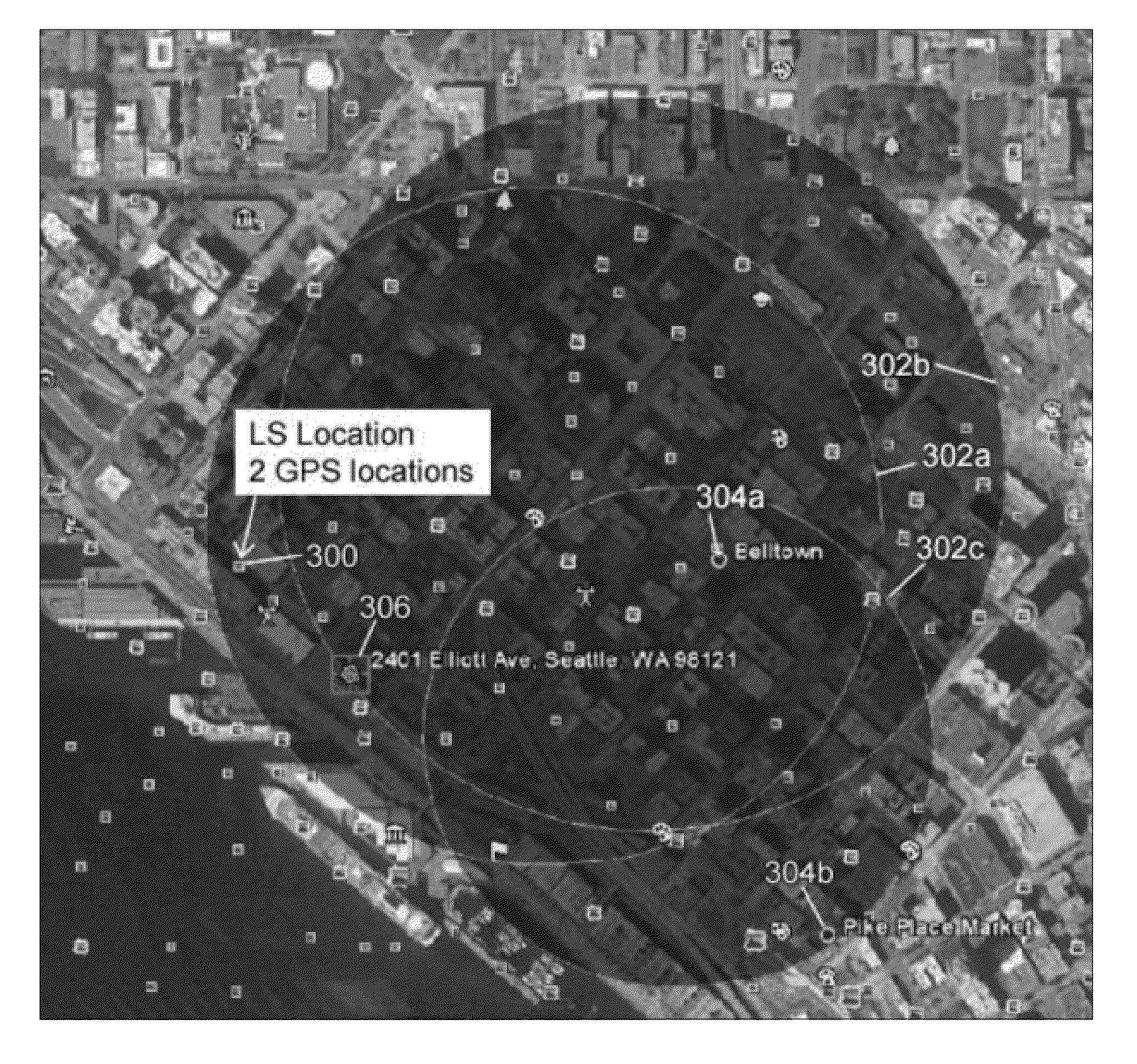
Location agent geofence
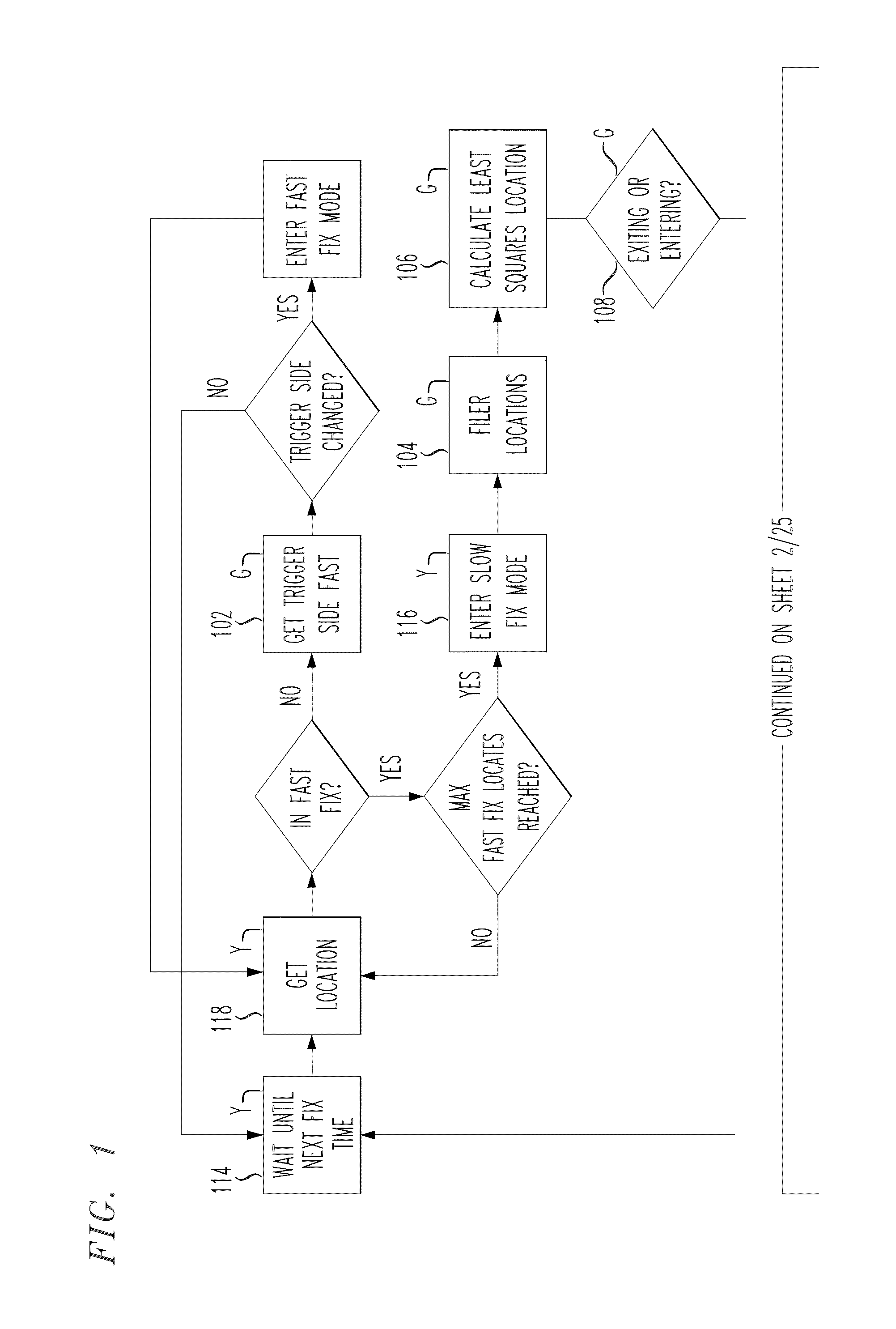
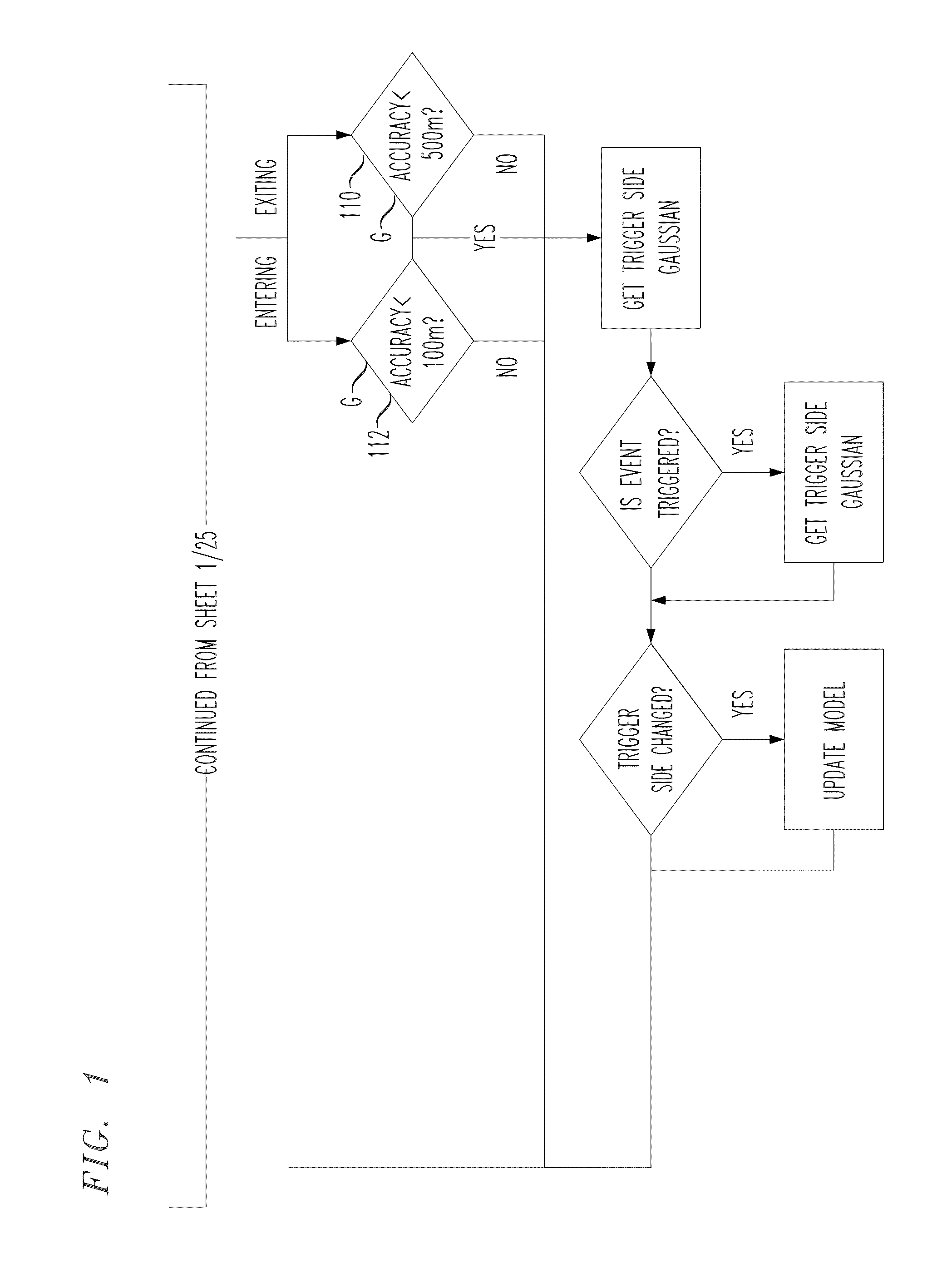
InactiveUS20130231137A1Avoid excessive delayExcessive delayPosition fixationSatellite radio beaconingLeast squaresData variability
A least squares geofence method that introduces inventive geofence steps and modifies existing geofence steps to minimize trigger misfires caused by data variability and location blunders and to minimize delayed / missed entry triggers generated under urban and / or indoor conditions. The least squares geofence method periodically retrieves sample locations for a target wireless device to determine that device's geographic location and to evaluate a corresponding side condition. Sample locations retrieved with accuracies greater than 1 km are filtered. If a potential change in side condition is detected for a given device, the least squares geofence method retrieves five fast location fixes for that device and evaluates a weighted least squares (LS) location estimate based on sample locations retrieved. A LS location estimate is then filtered according to an anticipated trigger event and the least squares geofence method evaluates a final geofence side condition based on the LS location estimate previously computed.
Owner:TELECOMM SYST INC
Dynamic java class loading for application execution
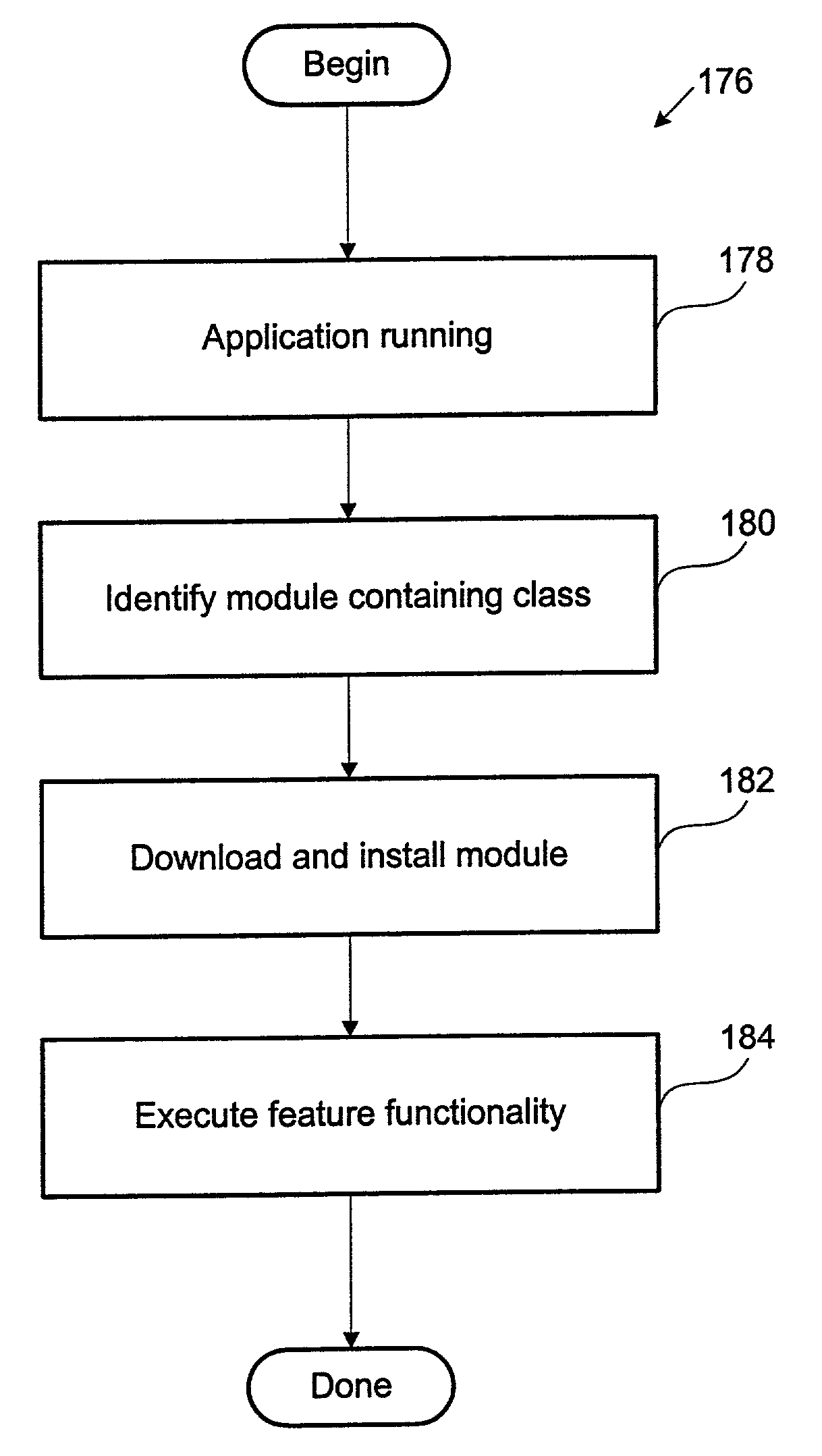
InactiveUS7028295B2Efficient downloadAvoid excessive delayInterprogram communicationDigital computer detailsGeneral purpose computerJava classes
Methods and an apparatus for downloading an application over a distributed network are provided. One exemplary method includes a computer implemented method executed by a general purpose computer, where the computer implemented method is capable of downloading an executable program from a networked storage to the general purpose computer. The method initiates with downloading a core module where the core module includes classes necessary to run an engine of the executable program. Then, the core module is installed which in turn module provides instant user functionality. The installed core module includes code for, requesting a class not associated with the core module, searching non-core modules of the executable program for the requested class, and downloading to the general purpose computer a non-core module containing the requested class while the executable program provides the user functionality.
Owner:SEIKO EPSON CORP
Method and device for obtaining measurements of downhole properties in a subterranean well
InactiveUS20160320769A1Less stored energySmall and less-expensiveProgramme controlSurveyEnvironmental geologyStructural property
Embodiments of the invention provide an untethered apparatus for measuring properties along a subterranean well. According to at least one embodiment, the untethered apparatus includes a housing, and one or more sensors configured to measure data along the subterranean well. The data includes one or more physical, chemical, geological or structural properties in the subterranean well. The untethered apparatus further includes a processor configured to control the one or more sensors measuring the data and to store the measured data, and a transmitter configured to transmit the measured data to a receiver arranged external to the subterranean well. Further, the untethered apparatus includes a controller configured to control the buoyancy or the drag of the untethered apparatus to control a position of the untethered apparatus in the subterranean well. The processor includes instructions defining measurement parameters for the one or more sensors of the untethered apparatus within the subterranean well.
Owner:SAUDI ARABIAN OIL CO
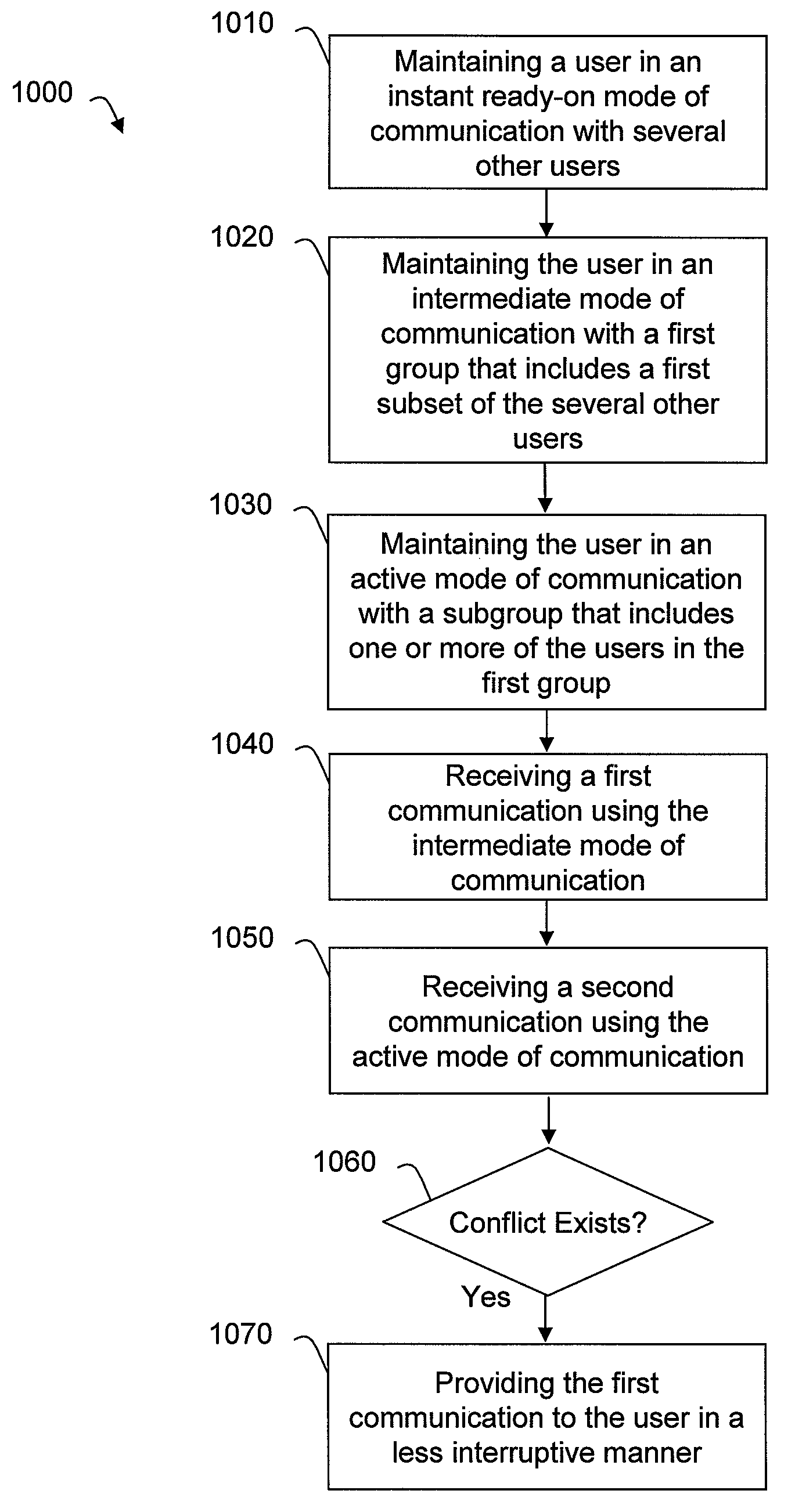
Multiparty communications systems and methods that optimize communications based on mode and available bandwidth
ActiveUS8390670B1Minimize bandwidth consumptionEasy to distinguishTelevision conference systemsBroadcast service distributionCommunications systemMultiparty communication
Improved methods, systems, and devices for managing communications are provided. A user device may display all ongoing communications so that a user can visualize the communications network or some subset thereof (e.g., a subgroup or group of users). A system may maintain the user device in an instant ready-on mode of communication with the other user devices. A user may then initiate communications with a subgroup (e.g., a pair) or group without initiating a new connection. Accordingly, a user can simultaneously and fluidly communicate at the subgroup level, at the group level, or at the inter-group level. Moreover, users can function as independent actors that can freely form and leave subgroups as well as groups.
Owner:SHINDIG
Portable System for Analyzing and Determining Elemental Composition of Rock Samples
InactiveUS20120046867A1No impediment to efficiencyLow costElectric/magnetic detection for well-loggingMaterial analysis using wave/particle radiationElemental compositionNeutron emission
A portable system for elemental analysis includes one or more neutron emitters, a chamber for containing a test sample, at least one gamma ray detector electrically connected to a data acquisition system, and software or firmware executing on the data acquisition system from a non-transitory physical medium, the software or firmware providing a first function for producing one or more gamma ray spectrums, a second function for applying correction factors to the one or more gamma ray spectrums, and a third function for analyzing the corrected gamma ray spectrum or spectrums to determine a deconvolved elemental composition of the test sample.
Owner:HELIOCENTRIC TECH
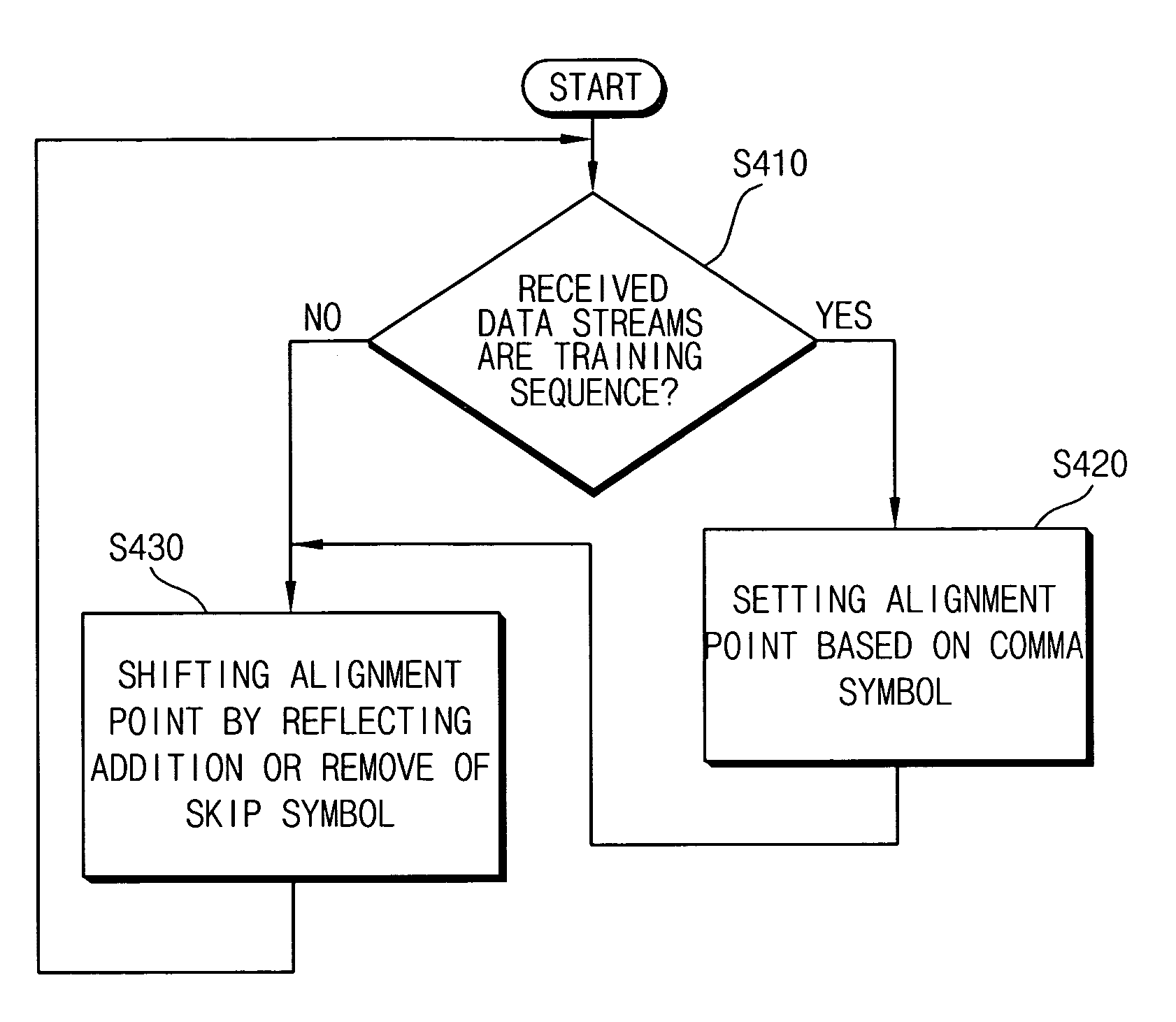
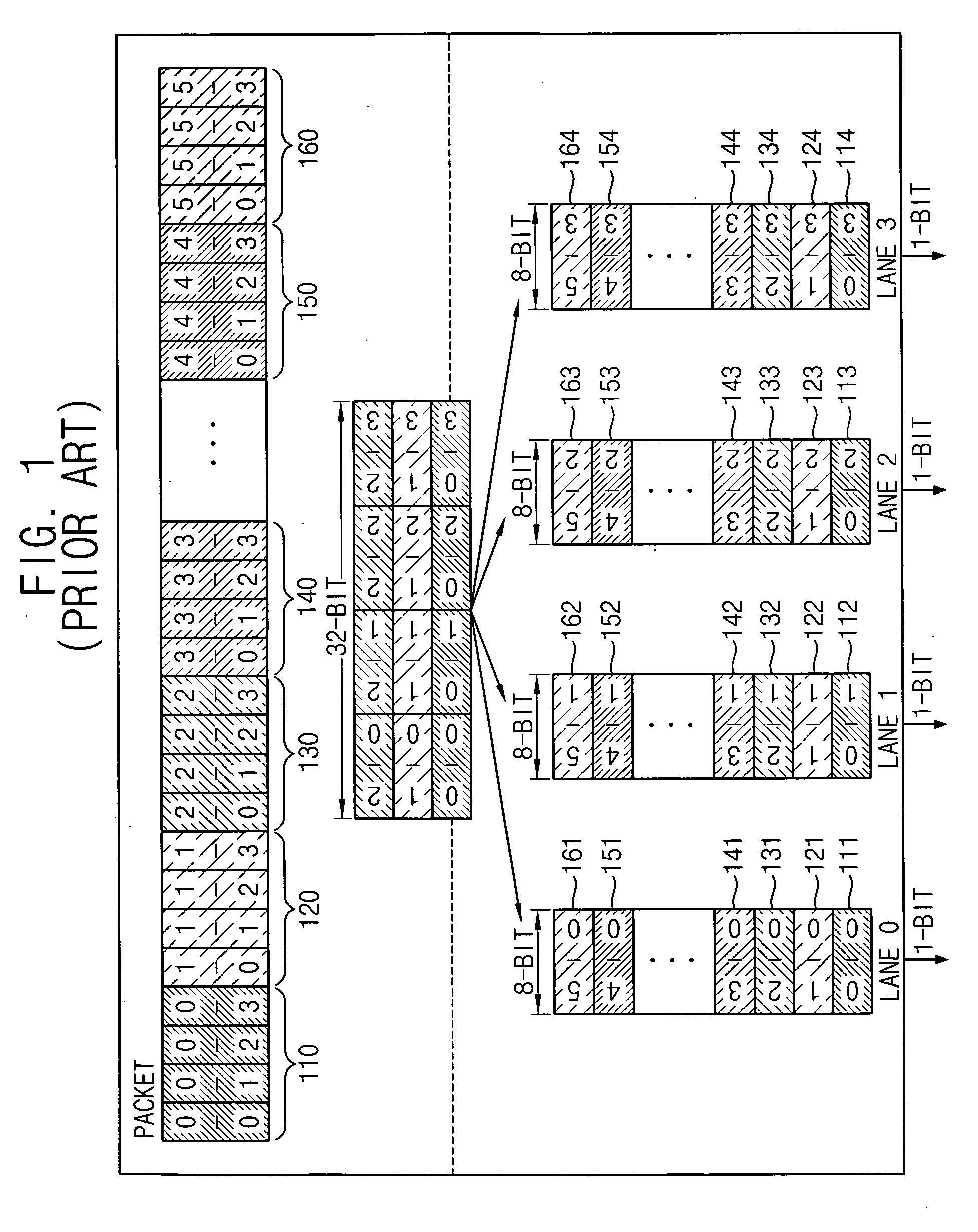
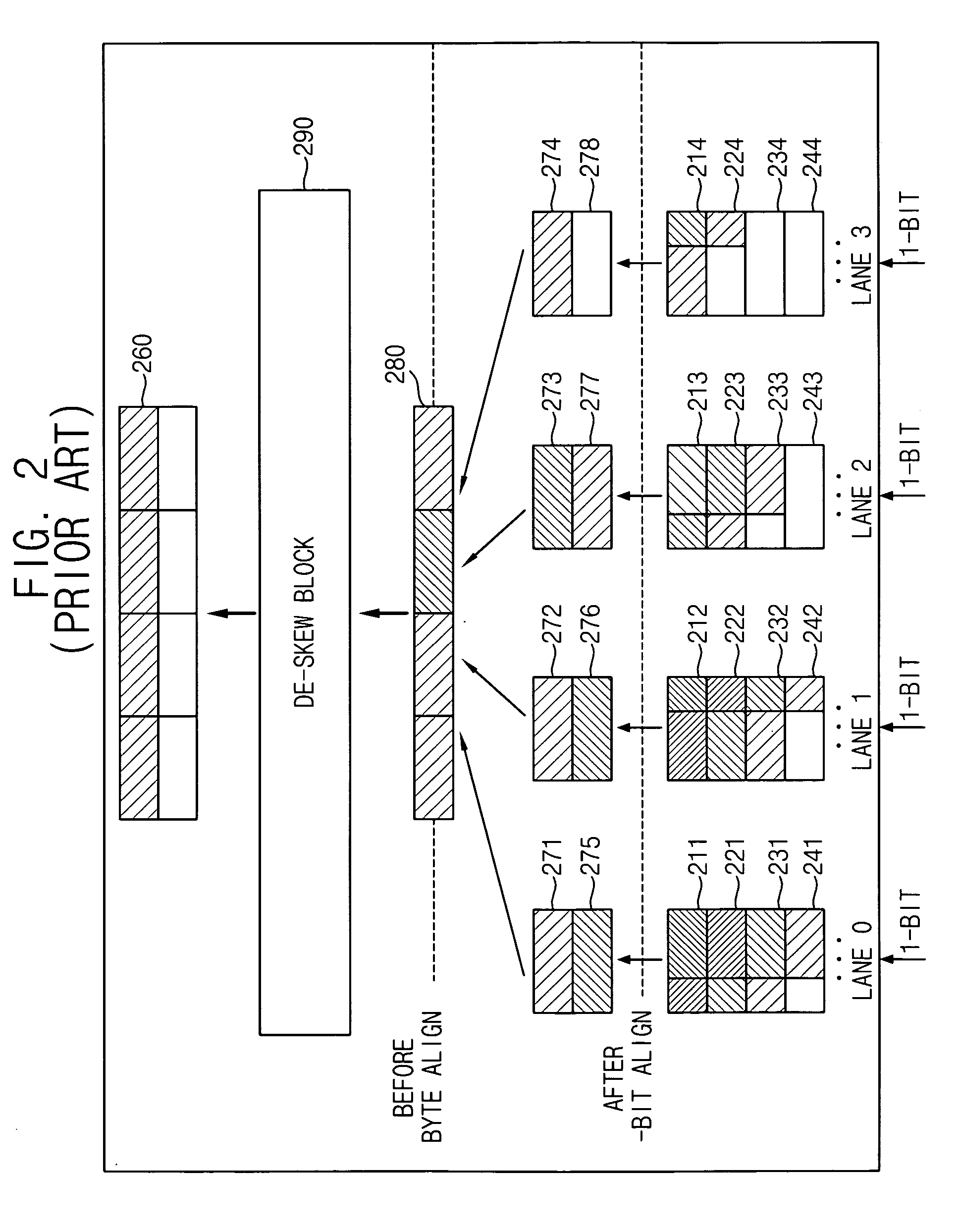
Method of compensating for a byte skew of PCI express and PCI express physical layer receiver for the same
ActiveUS20060156083A1Avoid excessive delayExcessive delayError preventionTransmission systemsPhysical layerPCI Express
A method of compensating for a byte skew of a PCI Express bus, the method including determining whether received data are in a training sequence or not, setting an alignment point corresponding to each of the lanes based on a comma symbol included in the training sequence when the received data are in the training sequence, and shifting the alignment point by reflecting an addition or a removal of a skip symbol on the received data through each of the four lanes when the received data are not in the training sequence. Therefore, the byte skew of the PCI Express bus may be effectively compensated for despite the addition or the removal of the skip symbol.
Owner:SAMSUNG ELECTRONICS CO LTD
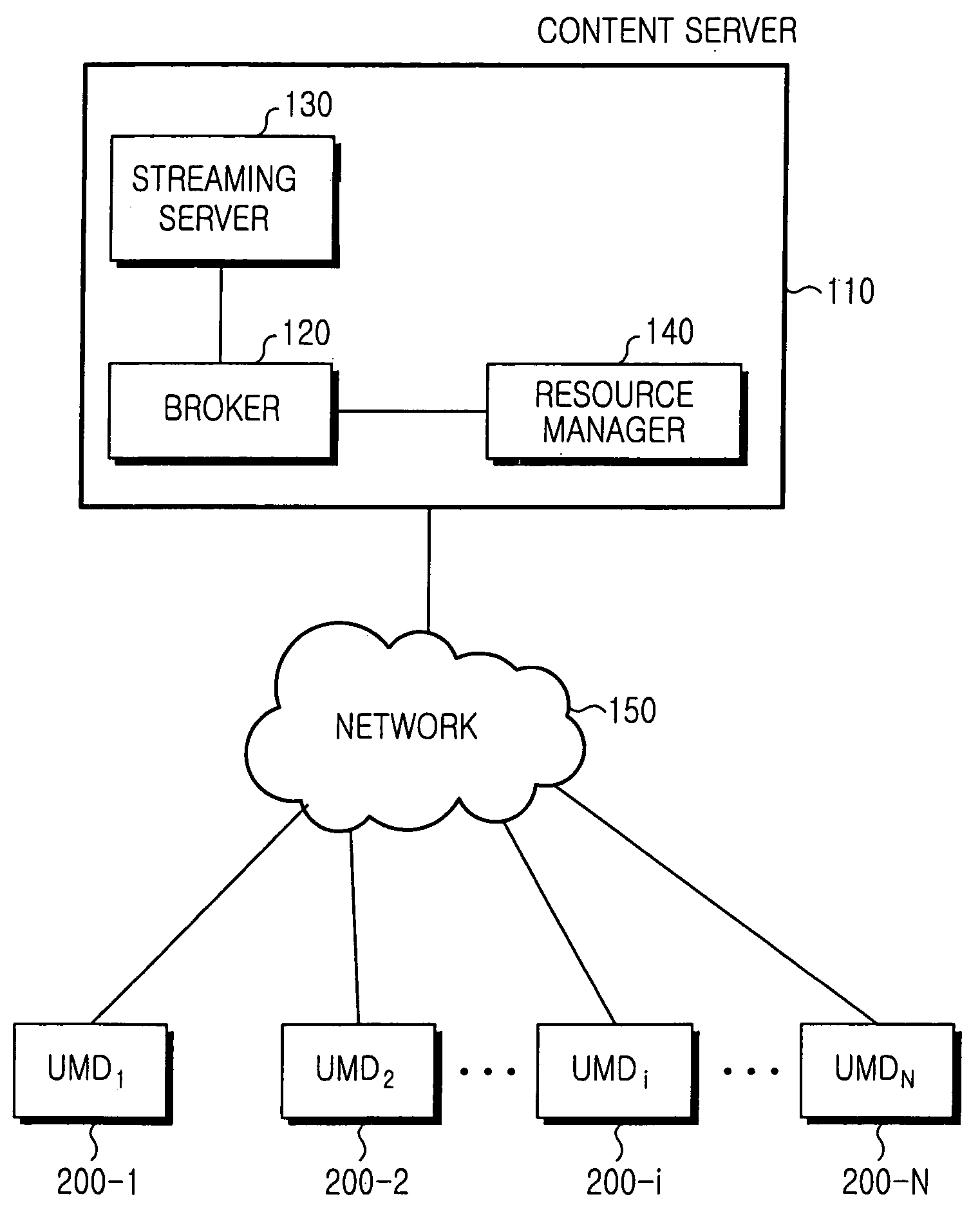
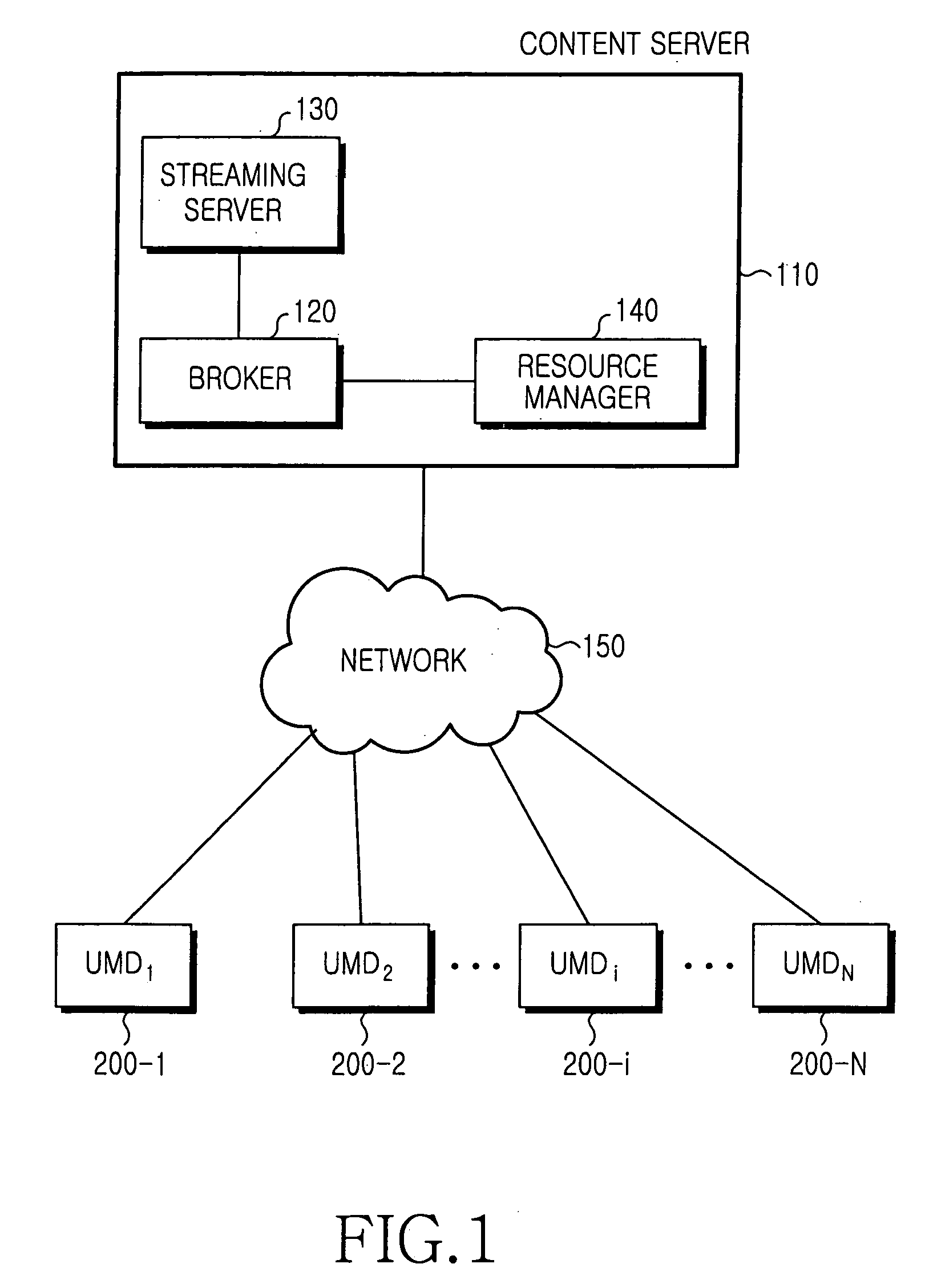
Method for streaming multimedia content
InactiveUS20060075453A1Reduce delaysLess buffer delayAnalogue secracy/subscription systemsMultiple digital computer combinationsNetwork connectionClient-side
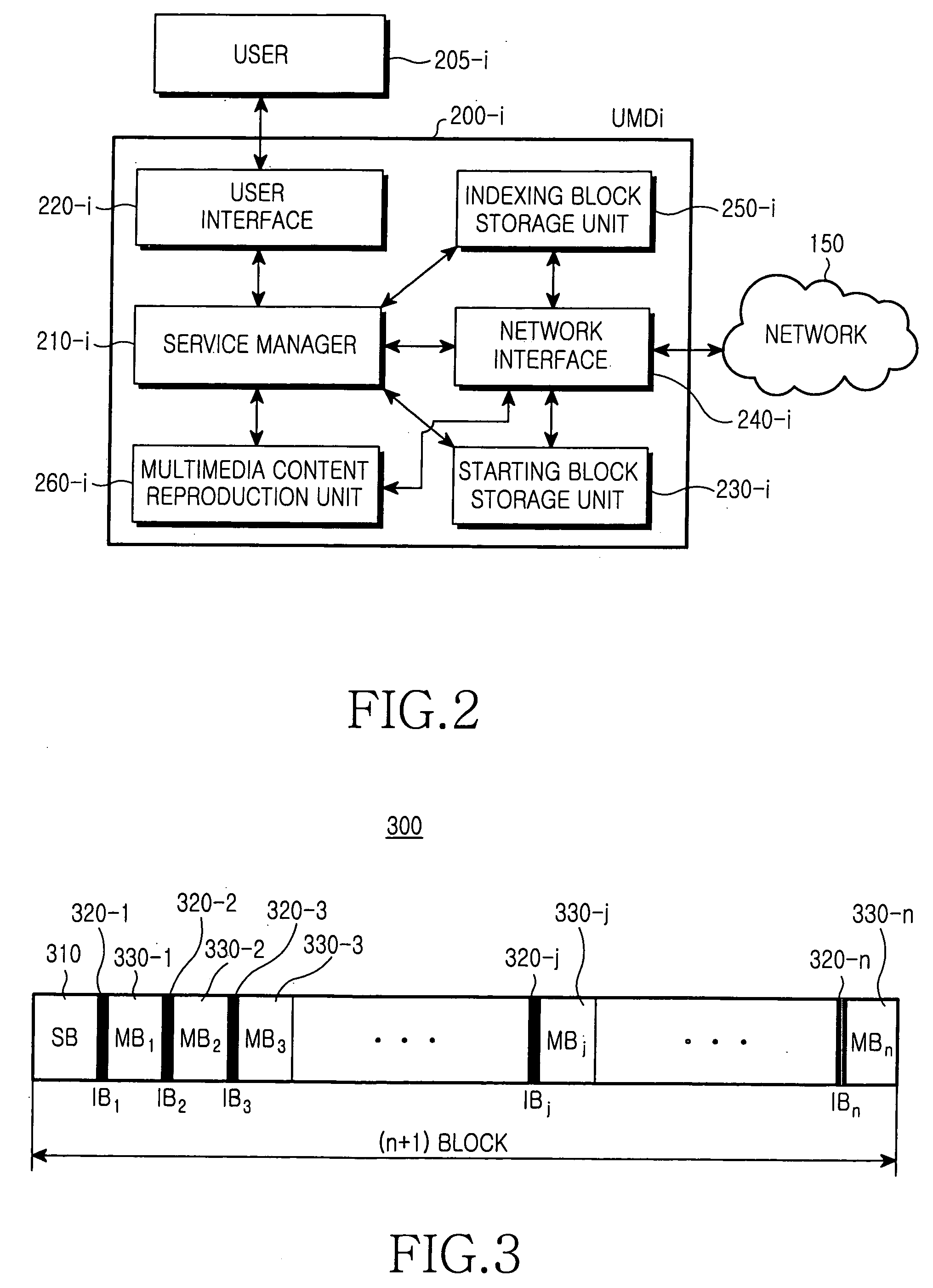
Streaming multimedia content from a content server to client, user multimedia devices (UMDs) connected to the content server through a network includes the steps of monitoring storage states, of UMDs connected to the network, for preset multimedia content, and automatically transmitting a starting block of the content to any UMD not yet storing the block. Tasks preparatory to streaming are advantageously off-loaded to the client side and distributed among UMDs, to realize reduced bandwidth and delay and to conserve on storage capacity of a UMD.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for improving performance margin in logic paths
InactiveUS20050201188A1Improve delay marginAvoid excessive delayDigital storagePower supply for data processingProduct dataOxide semiconductor
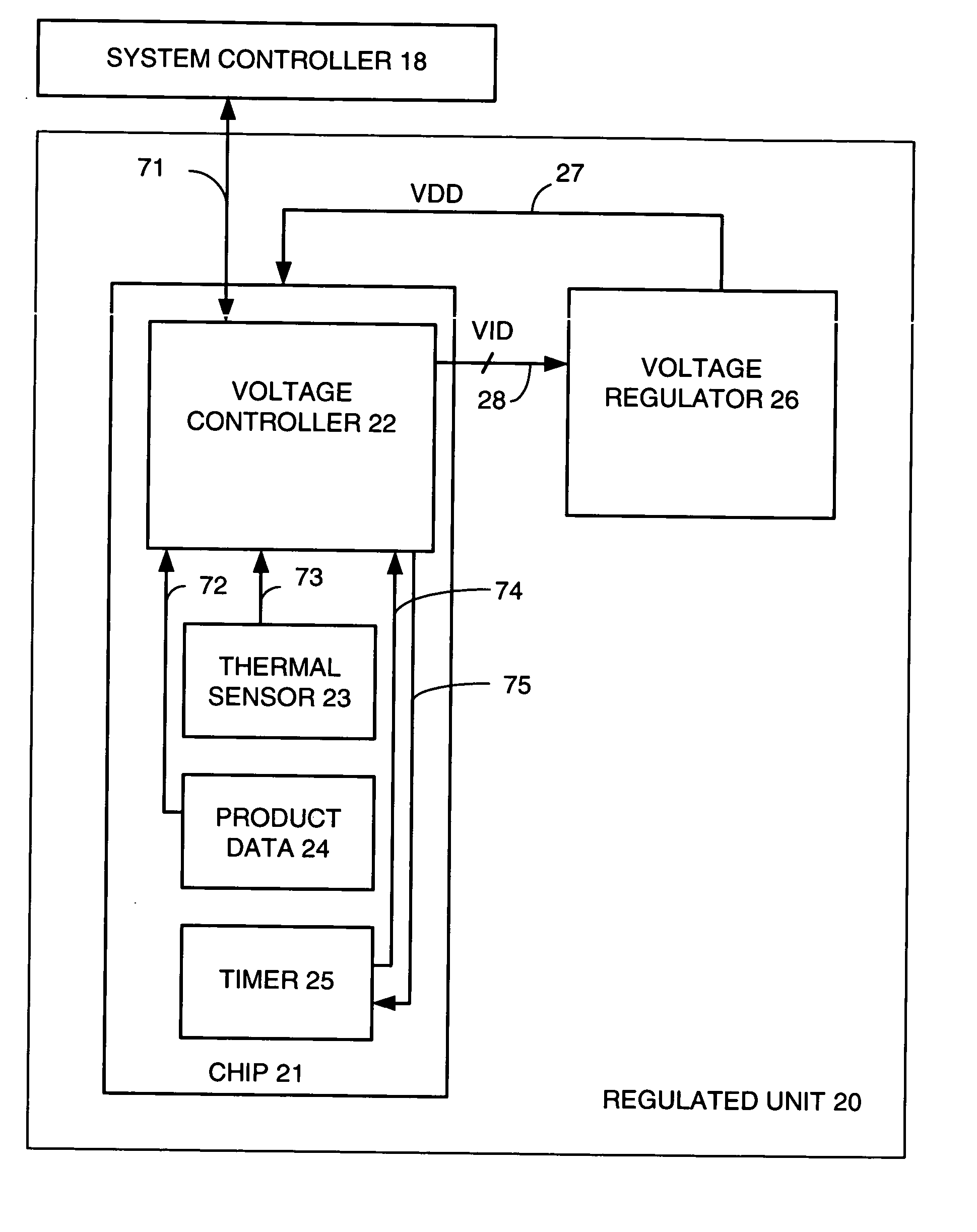
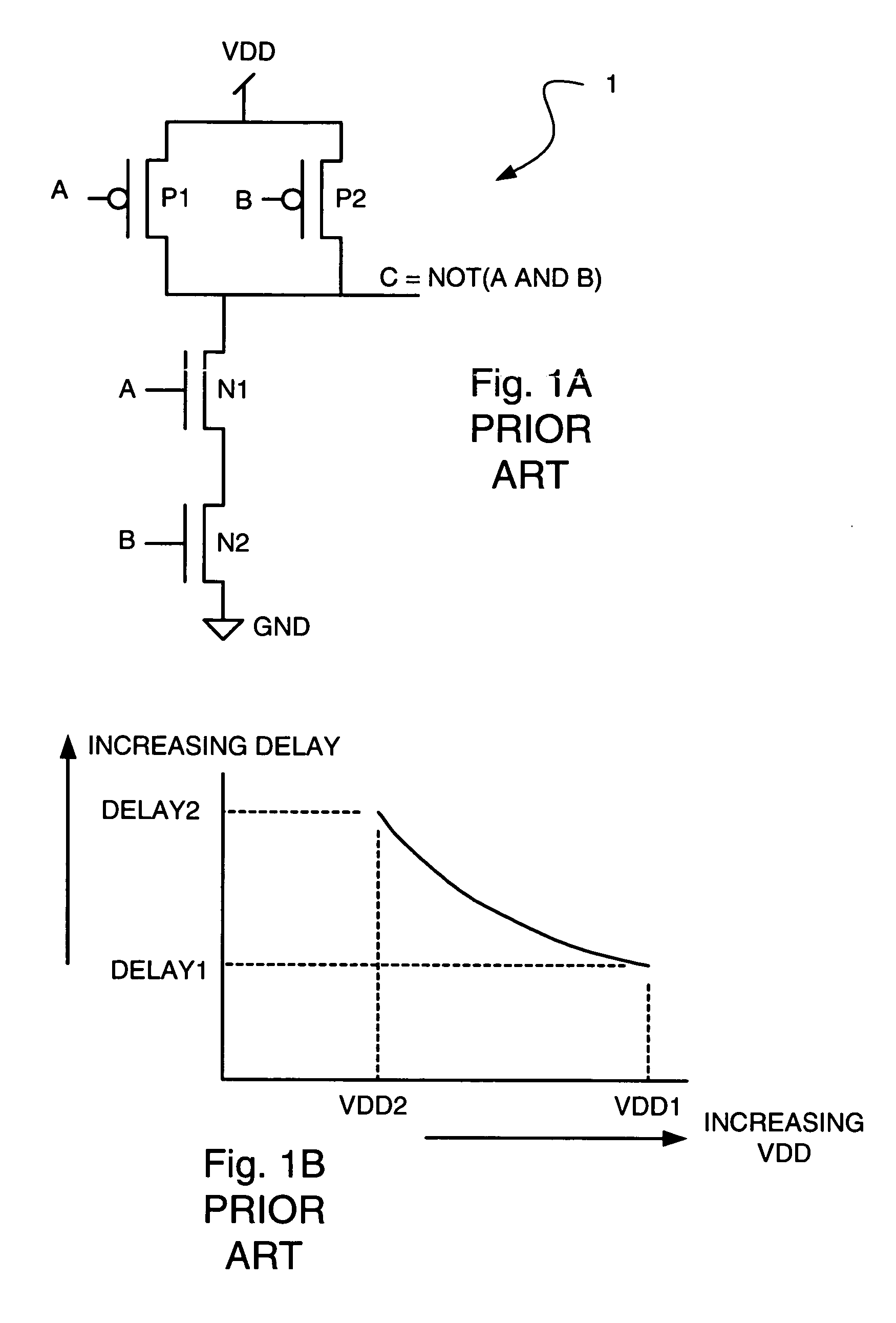
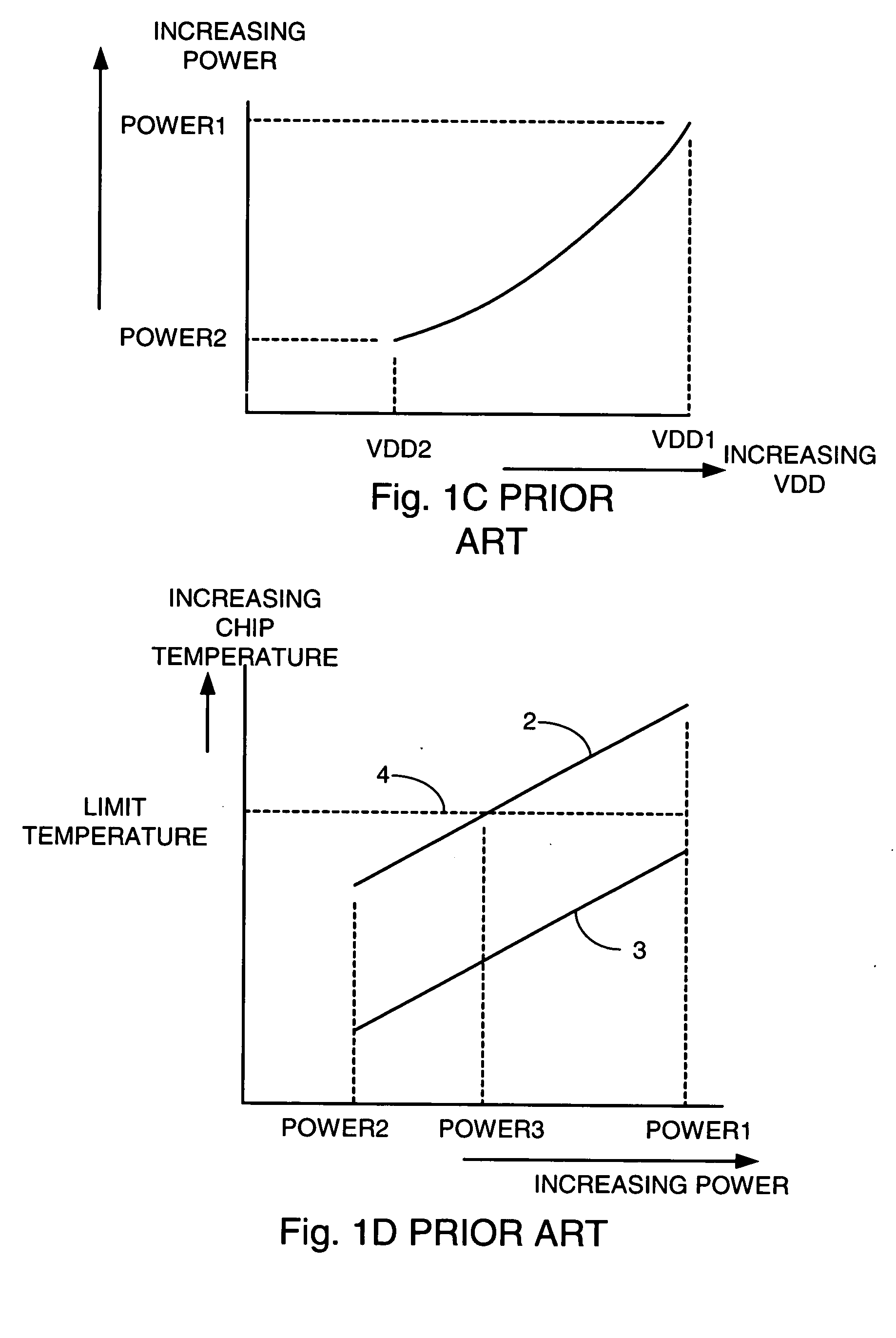
An apparatus and method is disclosed for improving timing margins of logic paths on a semiconductor chip. Typical logic embodiments, such as CMOS (Complementary Metal Oxide Semiconductor), have path delays that become shorter as supply voltage is increased. Embodiments of the present invention store product data on each particular chip. The product data includes, for examples, but not limited to, a voltage range having a low limit voltage and a high limit voltage, a limit temperature, and performance of the particular chip in storage for the particular chip. Each chip has a voltage controller, a timer, and a thermal monitor. The voltage controller communicates with a voltage regulator and dynamically causes a voltage supply coupled to the chip to be as high as possible in the voltage range, subject to the limit temperature.
Owner:GOOGLE LLC
Method of using dwell times in intermediate orbits to optimize orbital transfers and method and apparatus for satellite repair
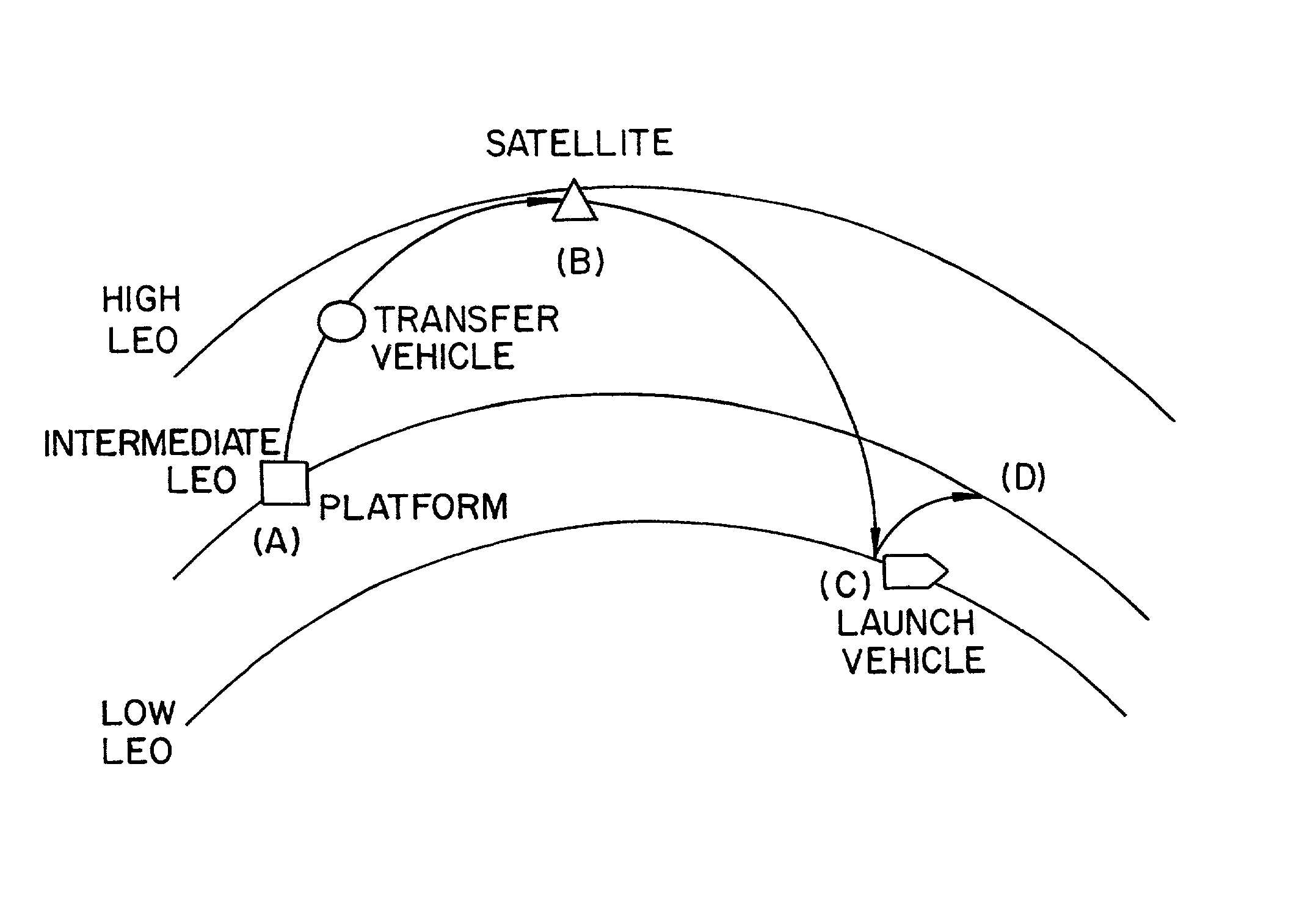
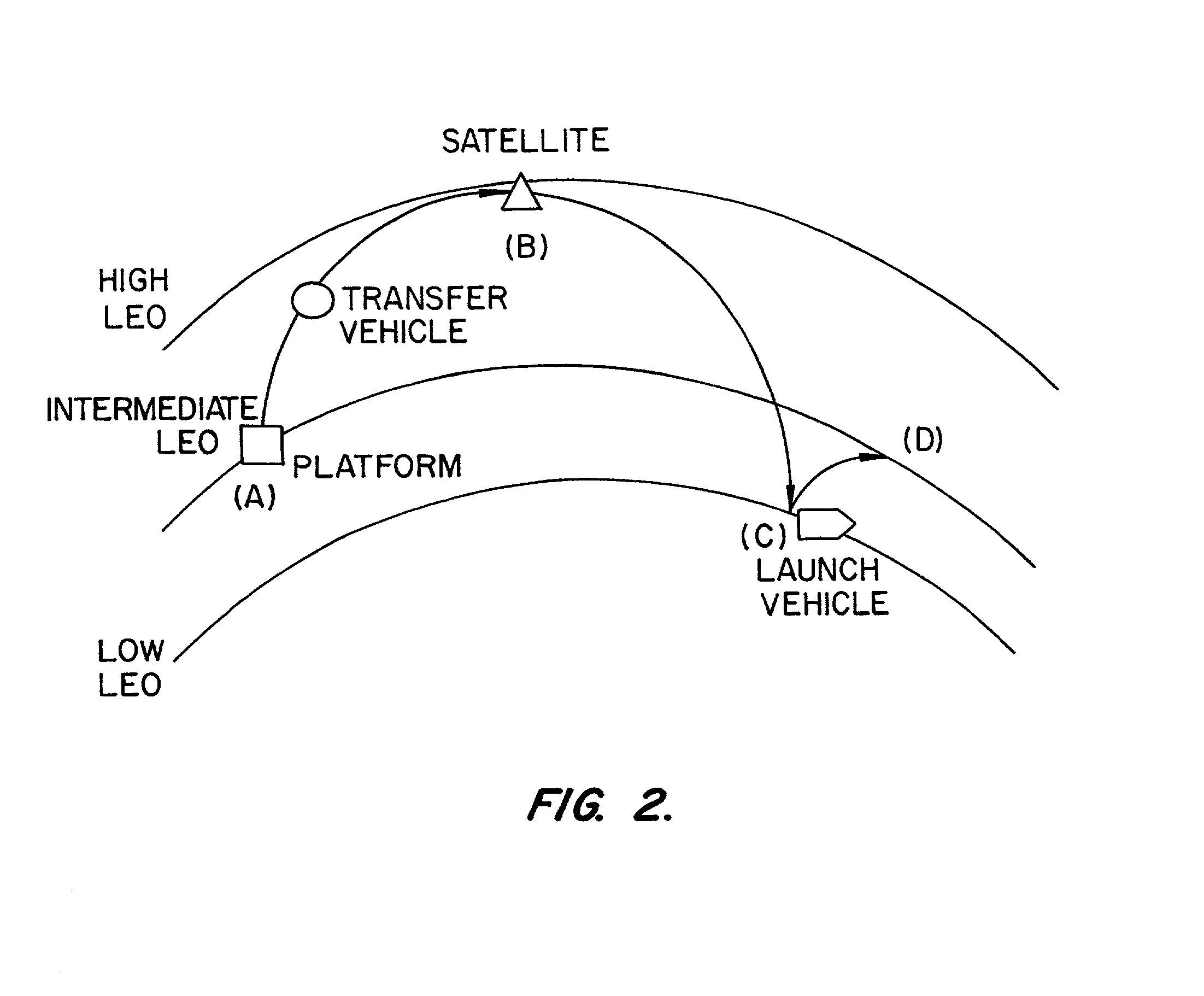
InactiveUS20020130222A1Reduced mission durationLess complexLaunch systemsCosmonautic component separationFlight vehicleTeleoperated robot
A reusable space vehicle docked in an intermediate orbit for rescue missions allows a satellite to be serviced with less delay, energy expenditure, and cost than a space vehicle launched from Earth for each mission. The reusable repair vehicle can be moved from one orbit to another with minimal energy expense while not having to wait for a launch window. Once a servicing need is identified, a destination orbit is identified for the space vehicle and a minimum energy path is identified. If the time to the next launch window between the docking orbit and the destination orbit happens to be near enough to allow for a timely rendezvous, the space vehicle is moved directly to the destination orbit. The space vehicle can be a vehicle designed to be piloted by humans or telerobotically. In one implementation, the inactive space vehicle is docked in an Intermediate LEO orbit (altitudes of approximately 250 km to approximately 500 km) and is used to rendezvous with objects in High LEO orbits (altitudes of approximately 500 km to approximately 1500 km) or objects in Low LEO orbits (altitudes of approximately 250 km or less). The space vehicle can be a modified lunar lander.
Owner:CONSTELLATION SERVICES INT
Synchronization and positioning of seismic data acquisition systems
InactiveUS20080189044A1Good synchronizationIncrease profitBeacon systemsSeismic signal transmissionData acquisitionGlobal positioning system receiver
A network distributed seismic data acquisition system comprises seismic receivers, connected to remote acquisition modules, receiver lines, line tap units, base lines, central recording system and a seismic source event generation unit. Global positioning system receivers of full or partial capability are combined with some of these modules and units and a master global positioning receiver aids the distributed receivers. The global positioning receivers may be used to synchronize high precision clocks as well as to provide positioning information. A master clock is designated and one or more high precision clocks is added to the network to correct for timing uncertainty associated with propagation of commands through the network. Seismic receivers and seismic sources are thereby synchronized with greater accuracy than otherwise possible, thus enabling an improvement in subsurface geologic imaging.
Owner:GEO X SYST
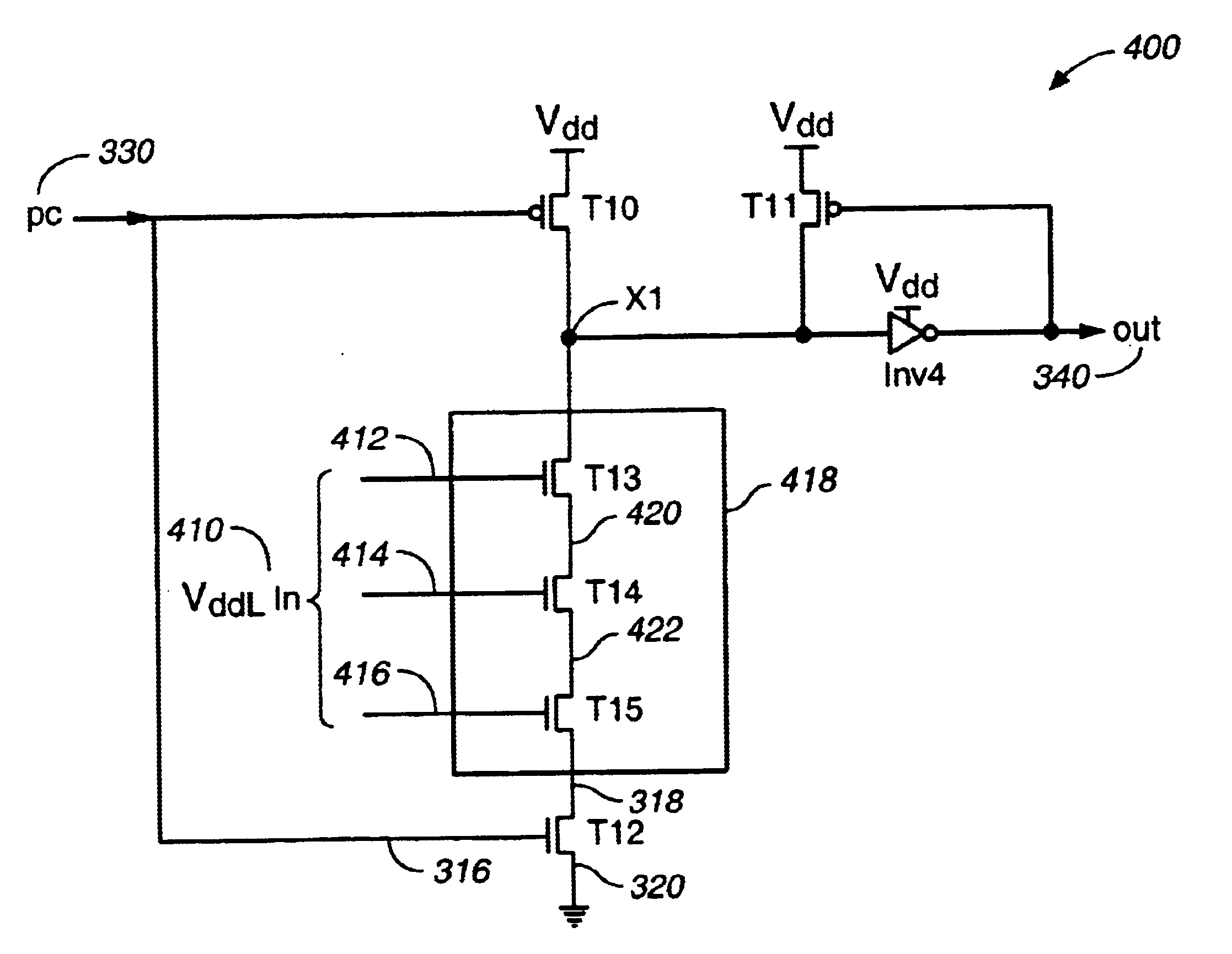
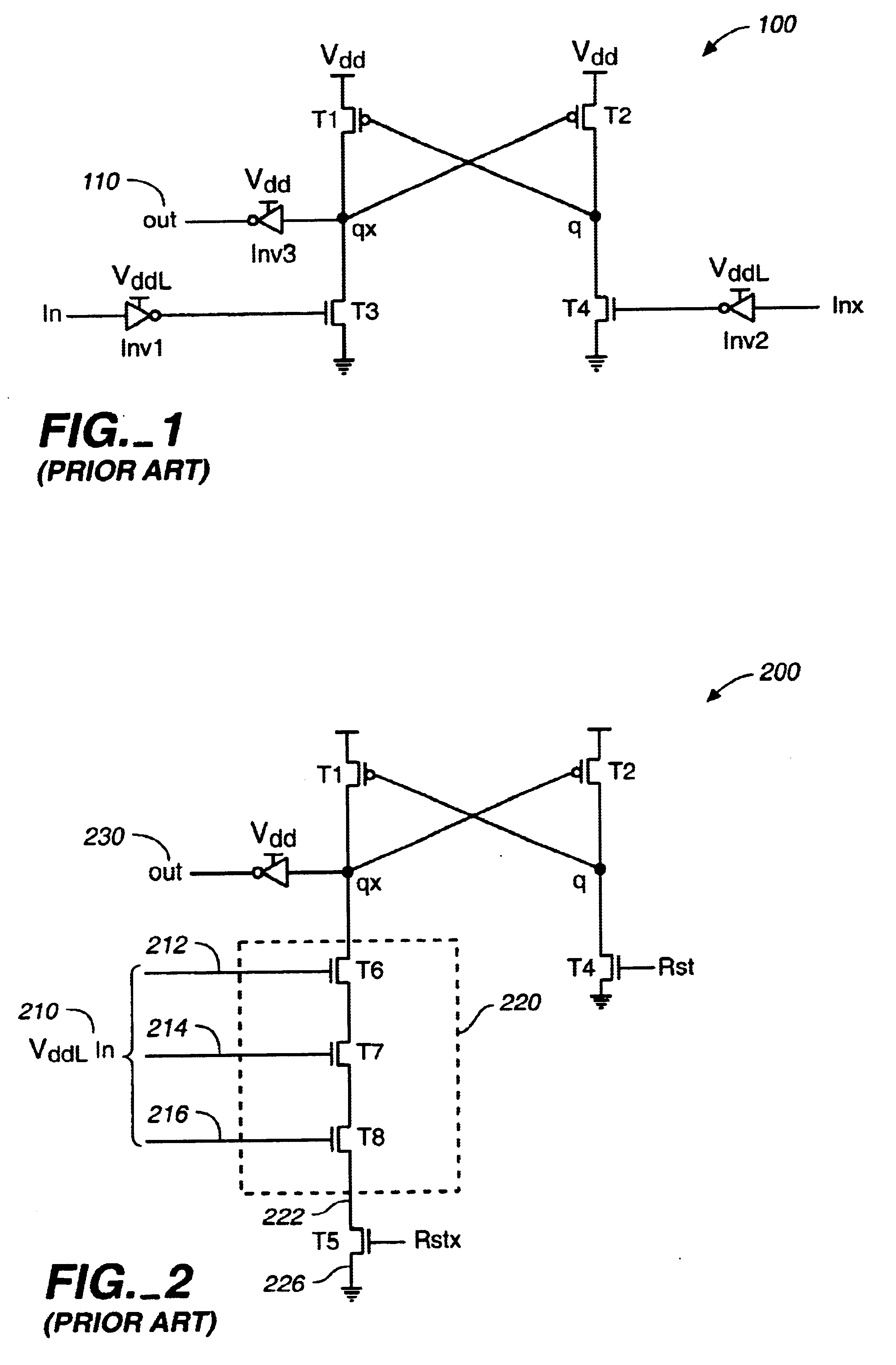
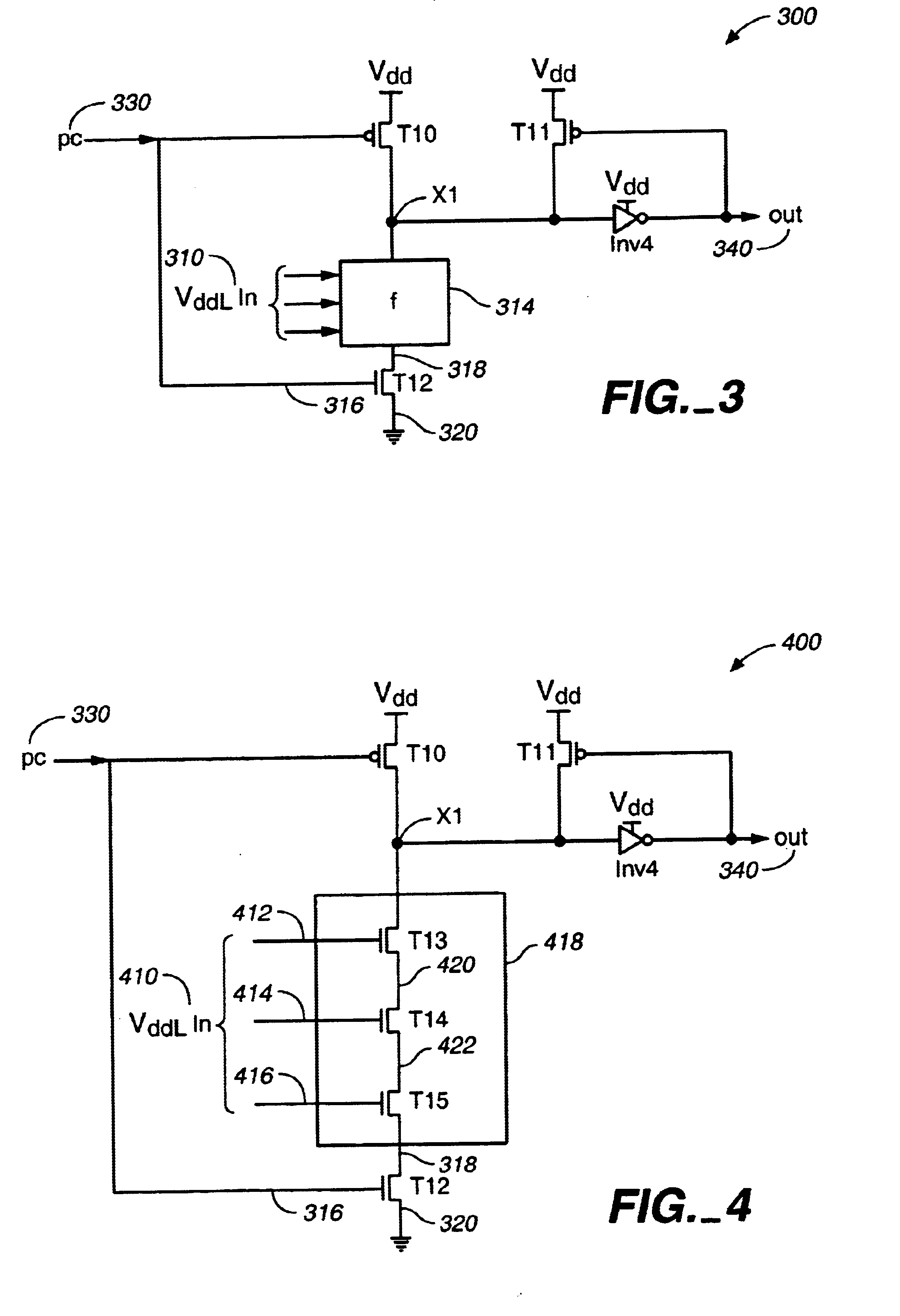
Low-to-high voltage conversion method and system
InactiveUS6842046B2Avoid excessive delayReduce power consumptionLogic circuits coupling/interface using field-effect transistorsDomino logicLow voltage
A system and method, for converting a voltage input from a low voltage source to a voltage output at a high voltage source using a domino logic circuit design. An embodiment provides a low to high voltage conversion system. The system includes: a pull-up transistor coupled to a high voltage source for charging a node, when a precharge signal is received; a low voltage source used for setting an input voltage; a pull-down network for discharging the node depending, at least in part, on the input voltage; and an output voltage determined from the node.
Owner:FUJITSU LTD
Multiparty communications systems and methods that utilize multiple modes of communication
ActiveUS8405702B1Facilitate communicationAvoid excessive delayTelevision conference systemsBroadcast service distributionCommunications systemGroup level
Improved methods, systems, and devices for managing communications are provided. A user device may display all ongoing communications so that a user can visualize the communications network or some subset thereof (e.g., a subgroup or group of users). A system may maintain the user device in an instant ready-on mode of communication with the other user devices. A user may then initiate communications with a subgroup (e.g., a pair) or group without initiating a new connection. Accordingly, a user can simultaneously and fluidly communicate at the subgroup level, at the group level, or at the inter-group level. Moreover, users can function as independent actors that can freely form and leave subgroups as well as groups.
Owner:SHINDIG
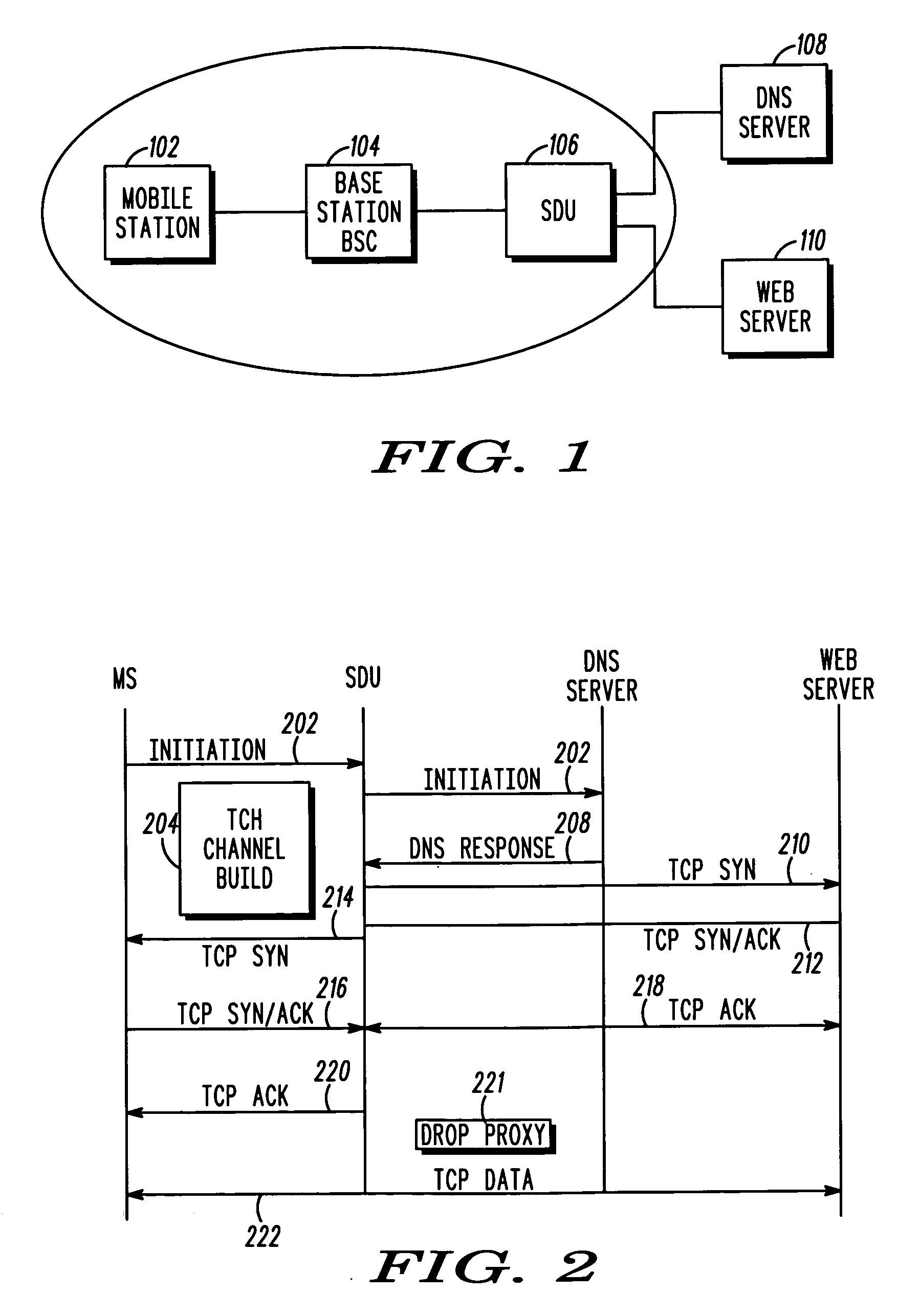
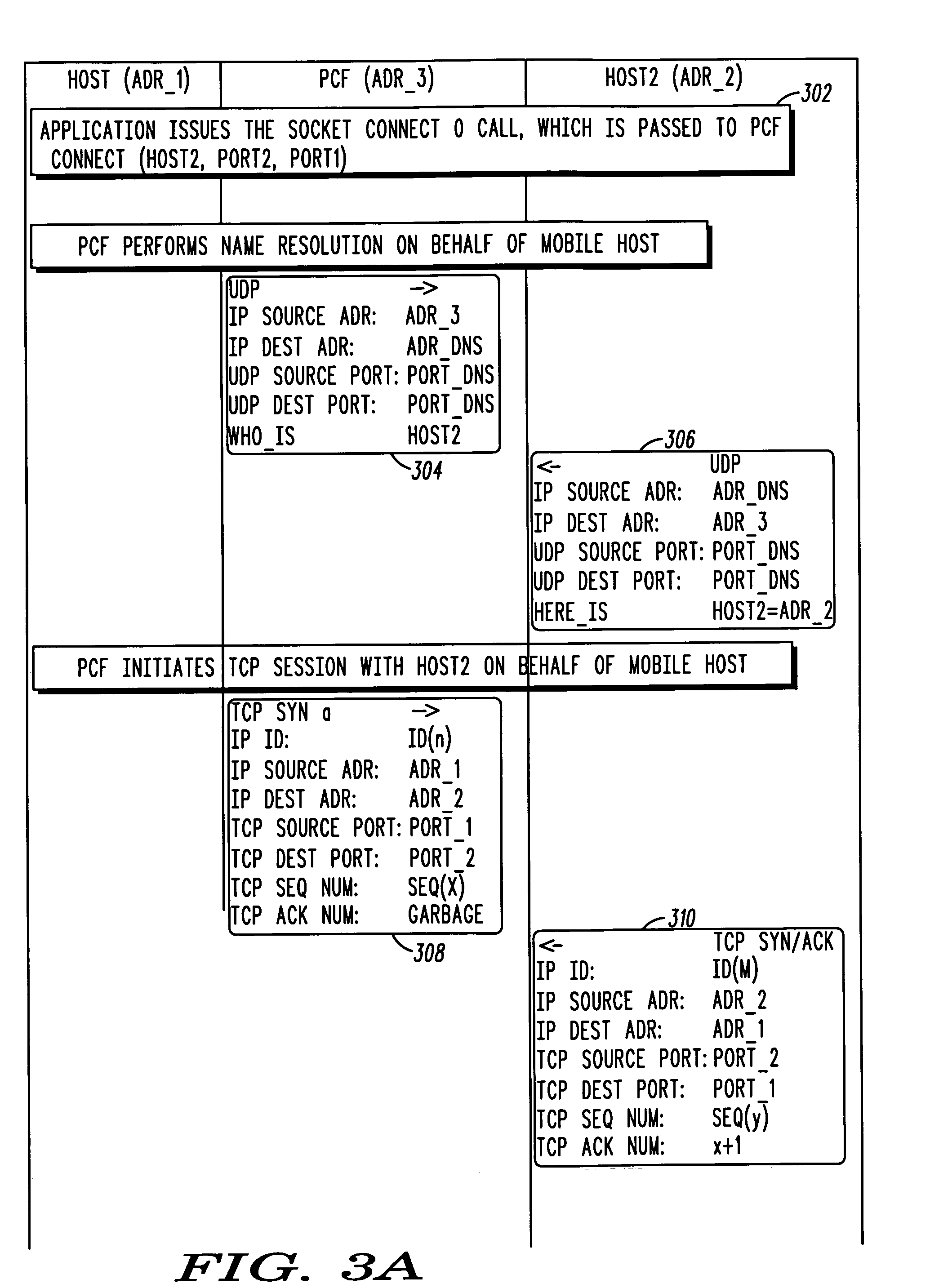
System and method for network-assisted connection in a wireless environment
InactiveUS20060056379A1Faster establishment of data sessionImprove user experienceTime-division multiplexConnection managementComputer networkRadio networks
A system and method establishes a data session between a mobile device and a destination server. A radio traffic channel is established between the mobile device and a radio network. At least partially simultaneous to establishing the radio traffic channel, the radio network establishes a connection between the mobile device and the destination server.
Owner:MOTOROLA INC
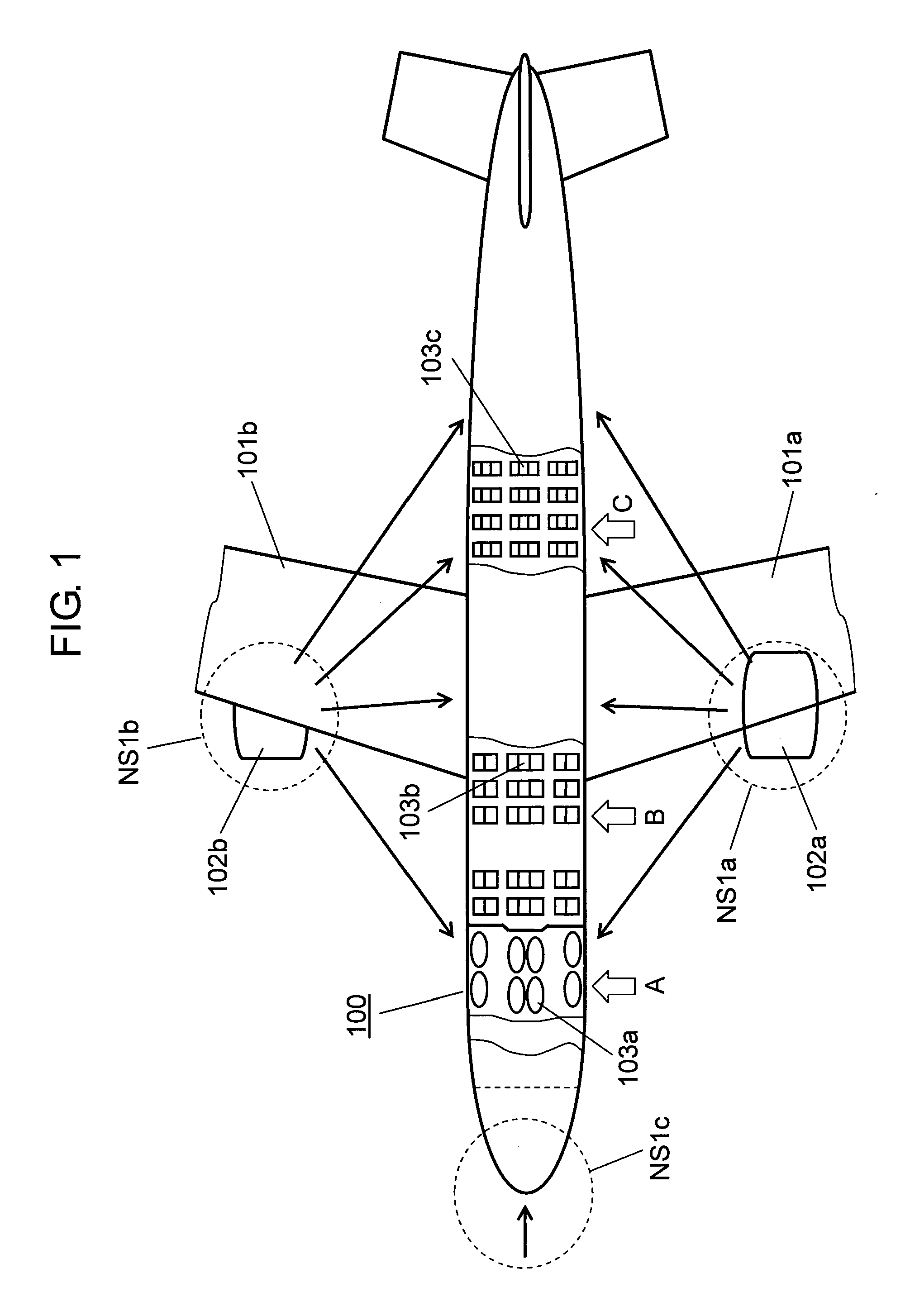
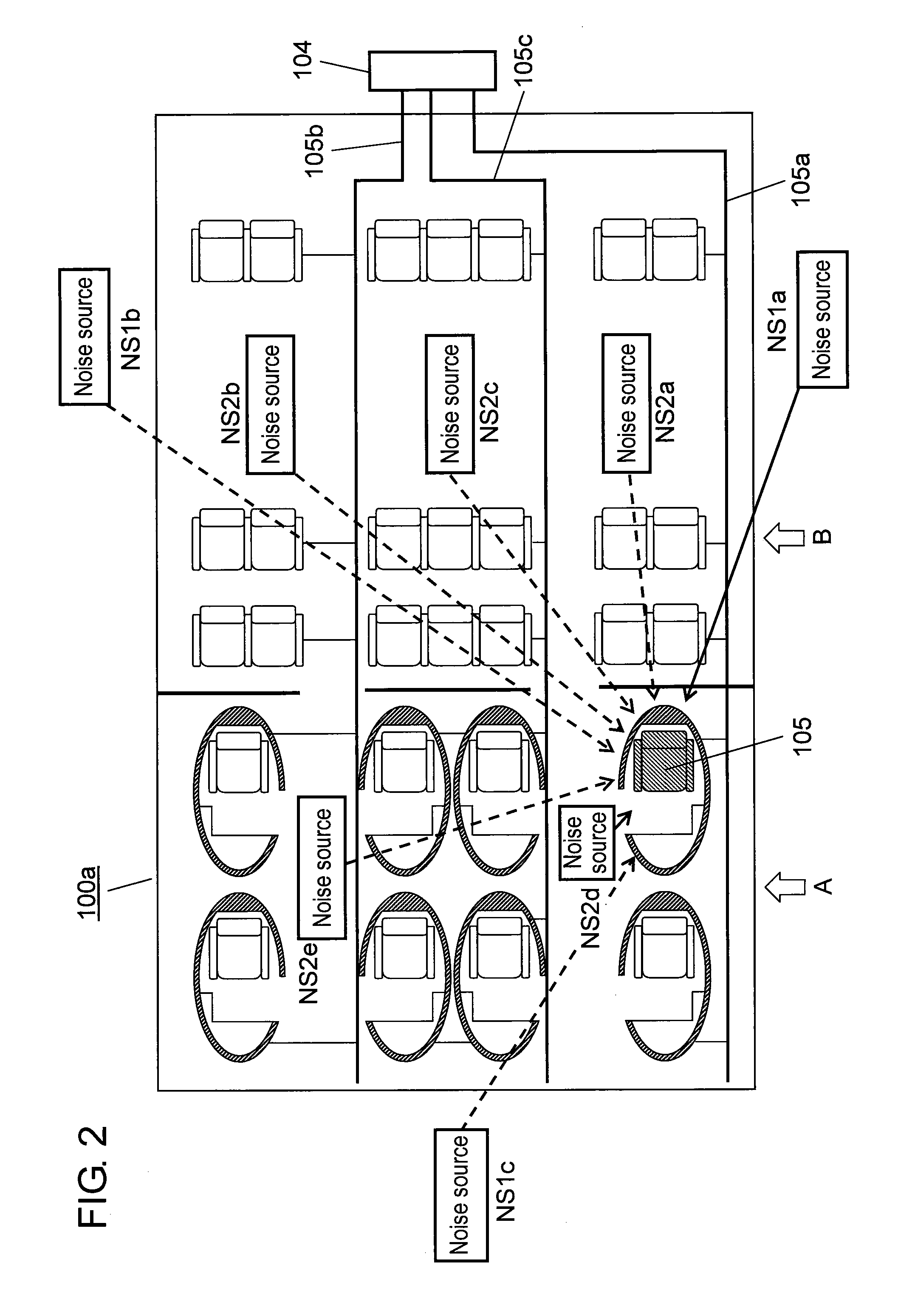
Noise reduction device
ActiveUS20100111317A1Increase volumeHigh in capacity of reproducing low-frequency soundVehicle seatsEar treatmentNoise controlEngineering
A noise reduction device, including a microphone for detecting noise, a noise controller for reversing the phase of noise detected by the microphone based on information outputted from the microphone, and a speaker for outputting sound based on information outputted from the noise controller, is arranged at a seat surrounded by a shell portion having a cavity, wherein a speaker is disposed in the cavity of the shell portion.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
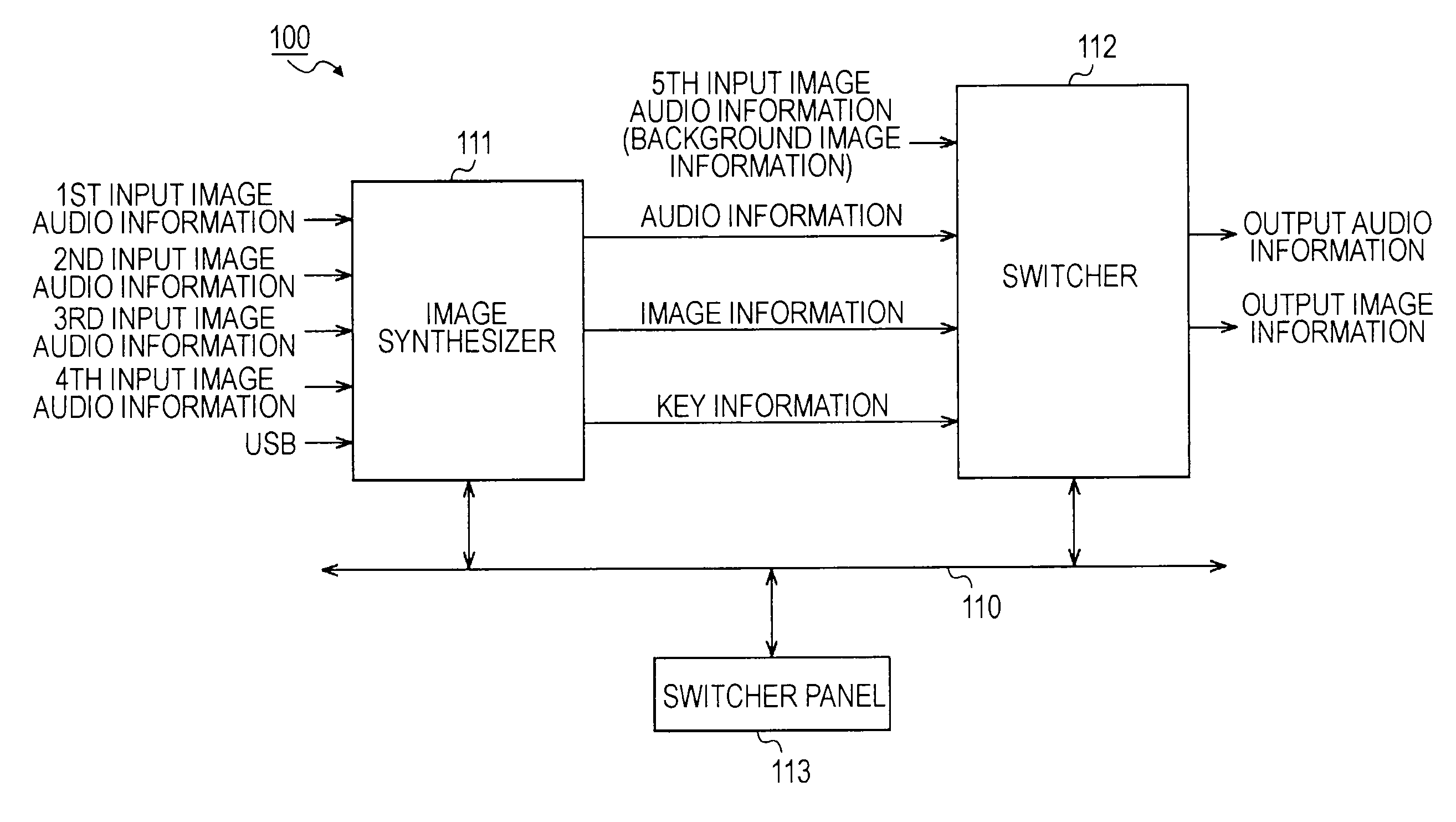
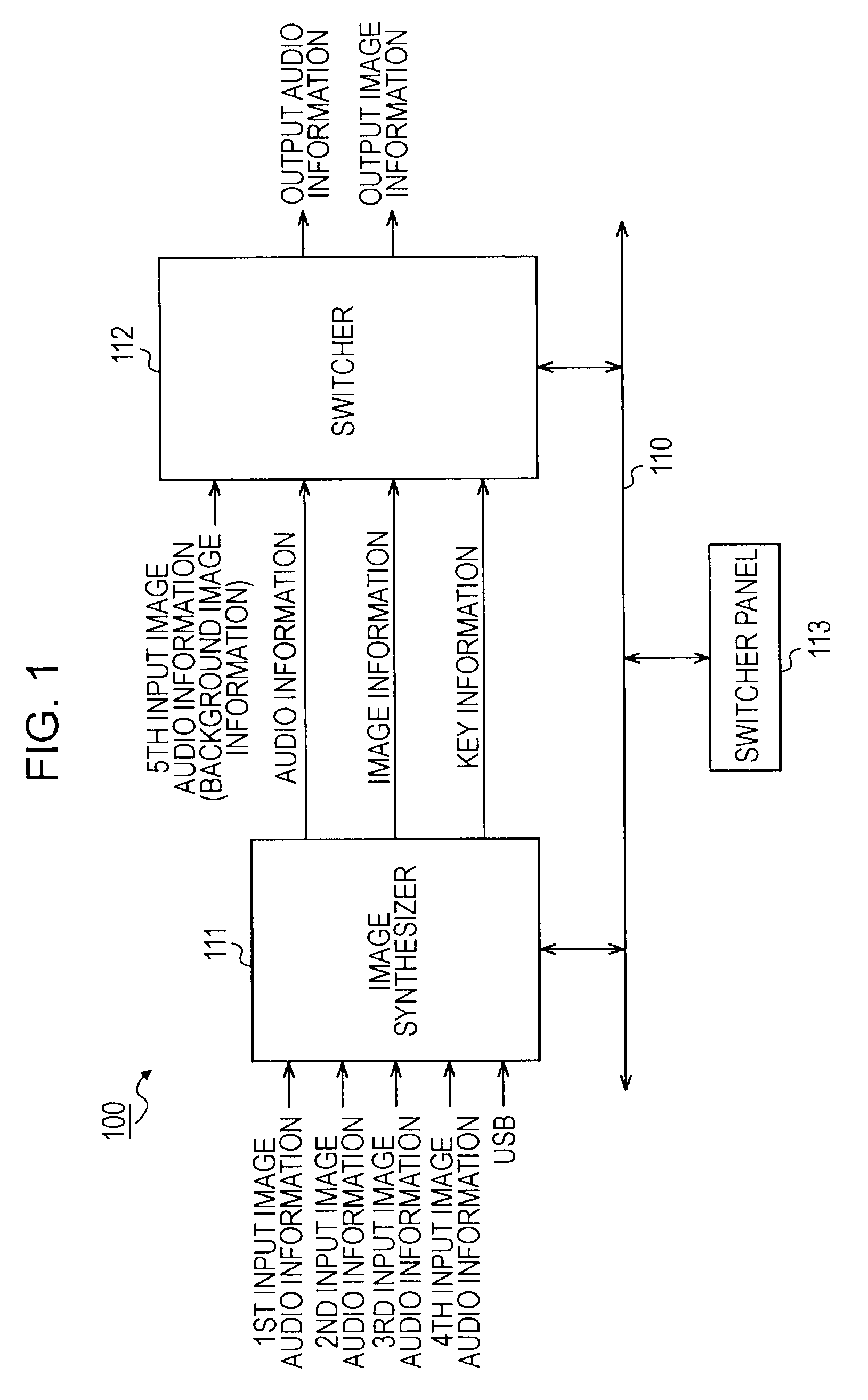
Information processing device and method, and program
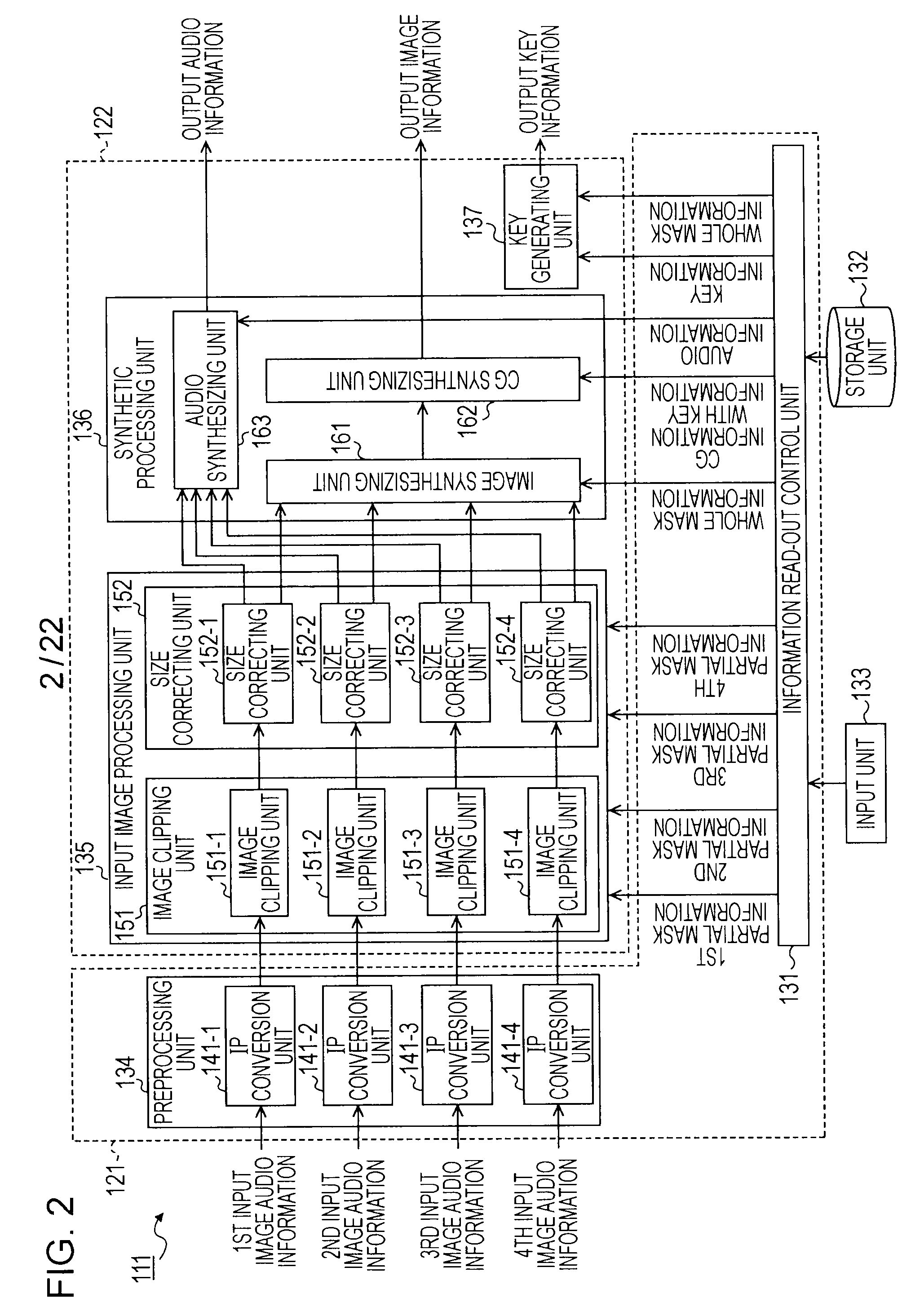
ActiveUS20090256858A1Avoid excessive delayComplicated processingCharacter and pattern recognitionCathode-ray tube indicatorsInformation processingComputer vision
An information processing device includes: a clipping unit configured to subject a plurality of images to clipping processing for clipping a part of an image as a partial image to clip a partial image from each of the plurality of images; a size correcting unit configured to correct an image size regarding each of a plurality of the partial images clipped by the clipping unit; and a synthesizing unit configured to connect the partial images of which the image sizes have been corrected by the size correcting unit to generate a synthetic image.
Owner:SONY CORP
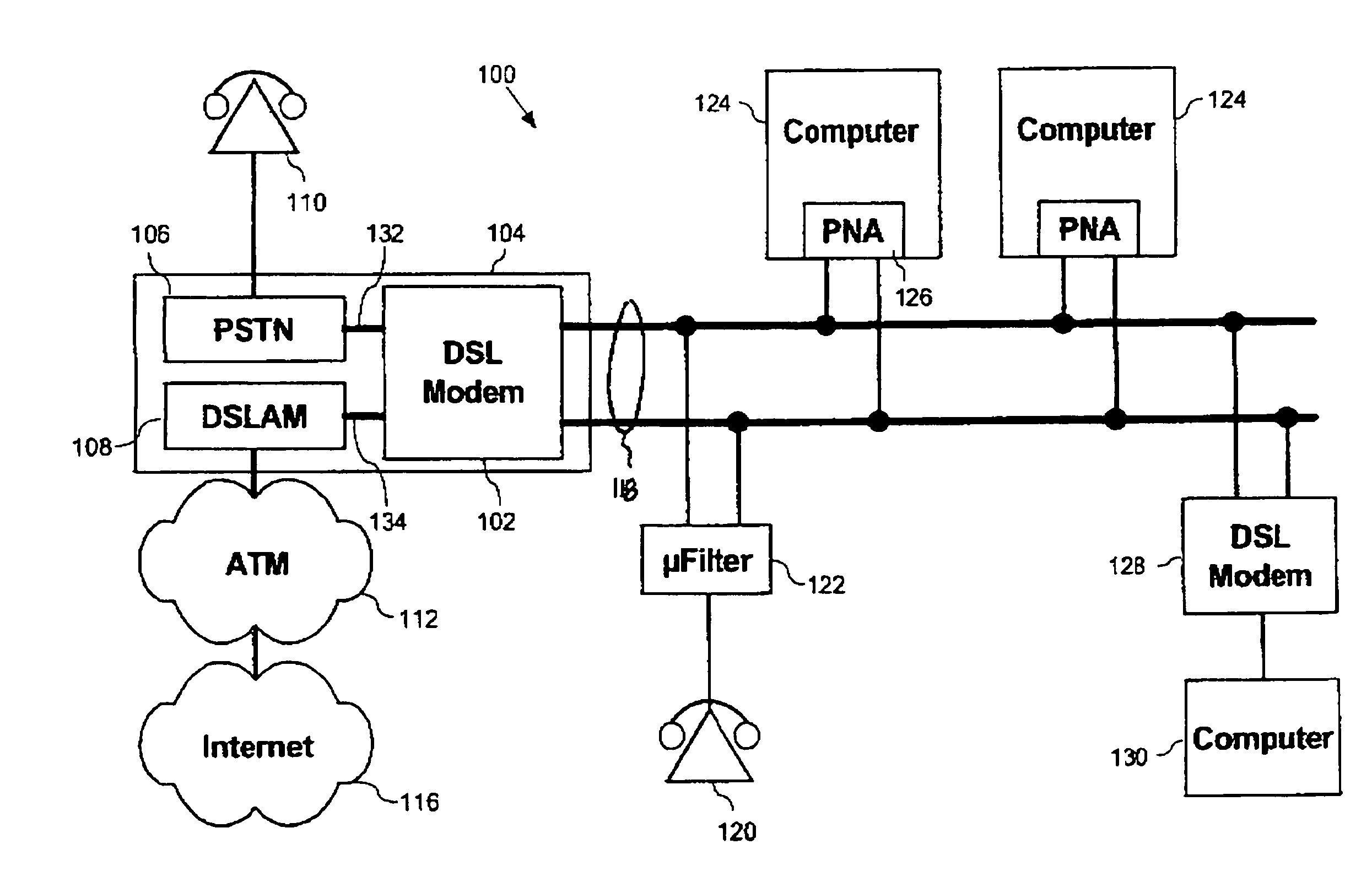
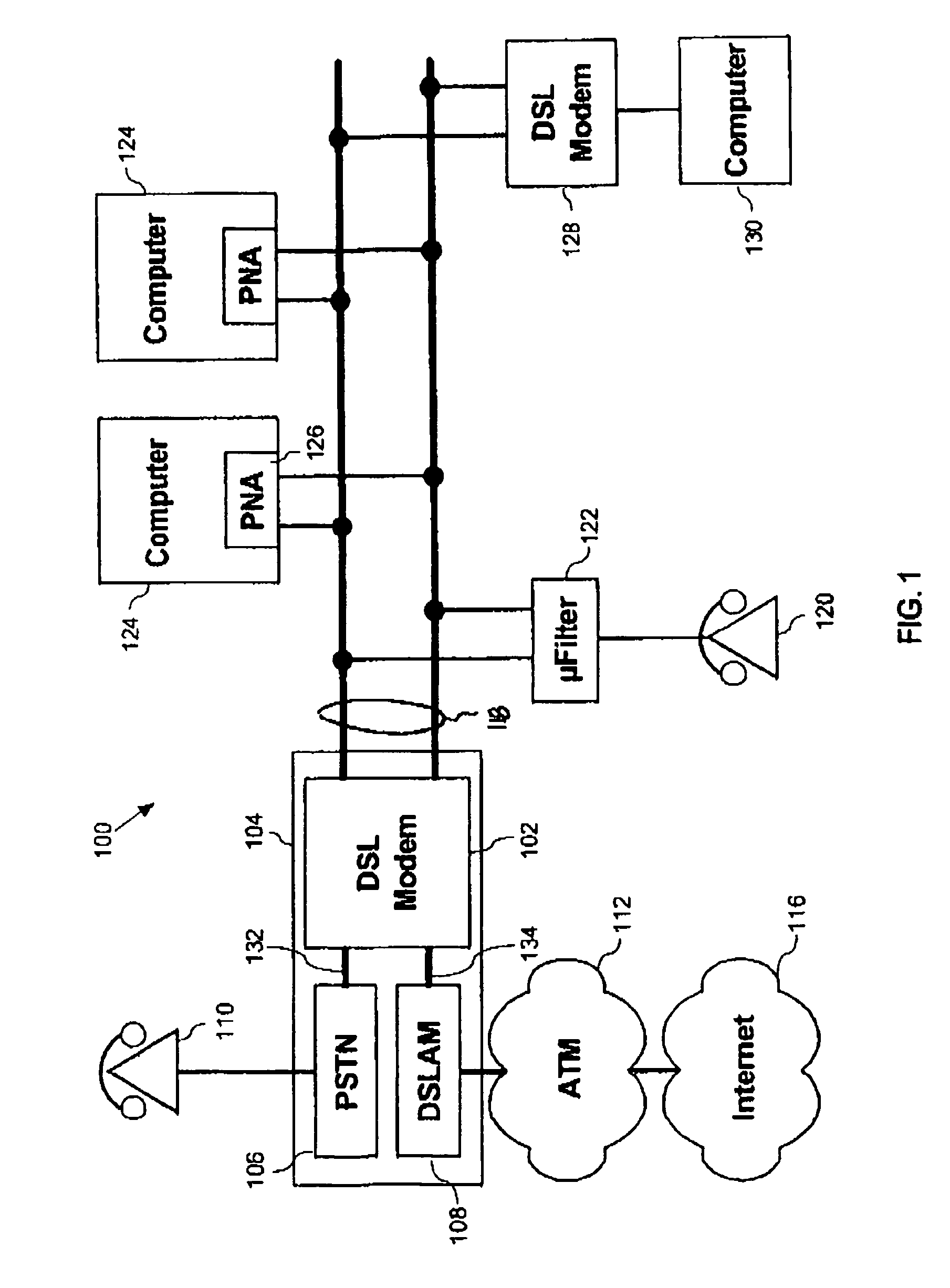
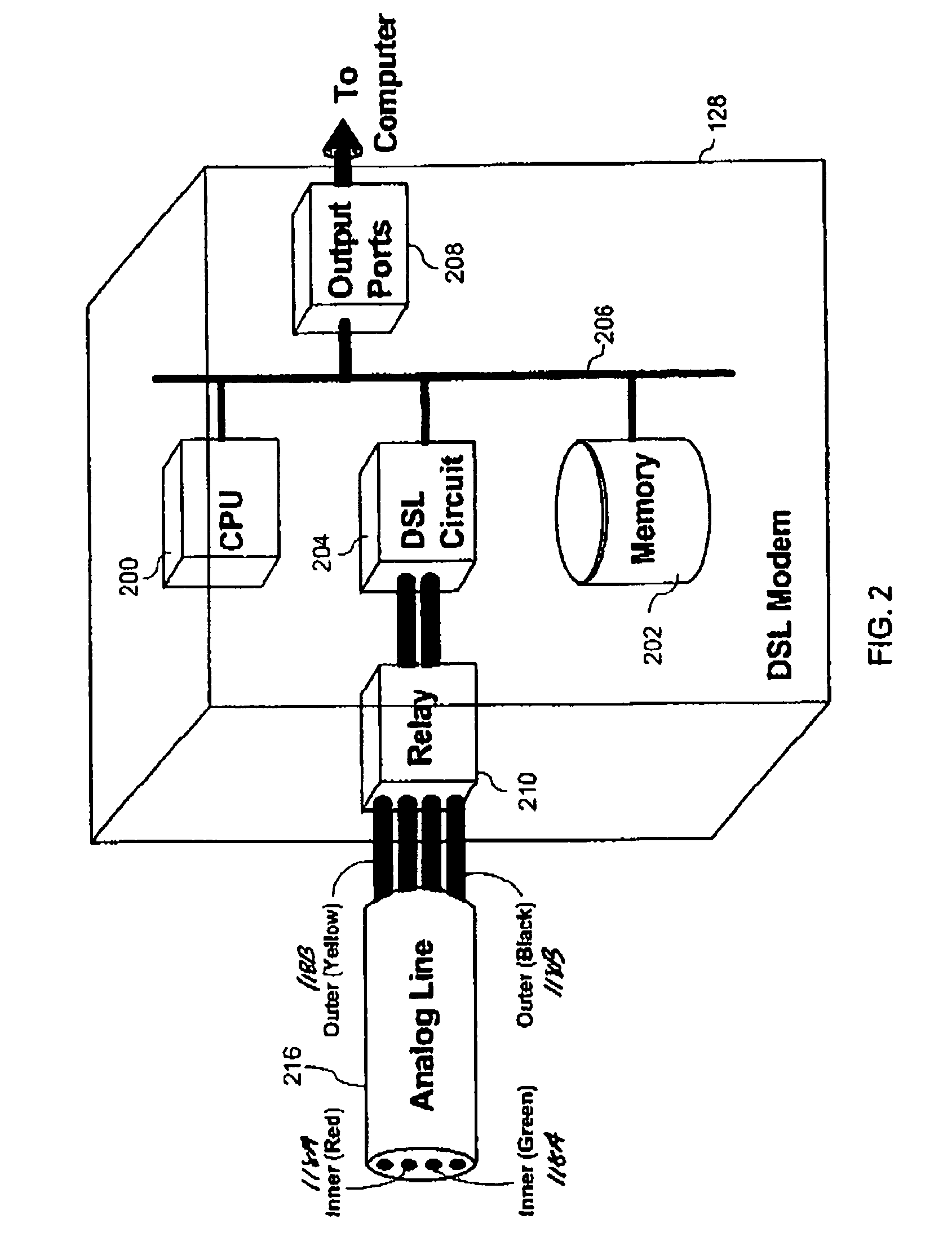
System and method for auto-configuration of a DSL modem
InactiveUS7012899B1Avoid excessive delayLow costError preventionTransmission systemsModem deviceAuto-configuration
The method for the automatic configuration of a DSL modem, comprises connecting a DSL modem to an analog telephone line, automatically determining available communication resources on the analog telephone line, and thereafter automatically configuring the DSL modem based on the available communication resources. Automatic configuration of the DSL modem is essentially undertaken by (i) automatically ascertaining if a circuit capable of communicating DSL signals is available by automatically detecting if a DSL communication circuit exists on the analog telephone line, and thereafter (ii) automatically configuring the DSL modem for a virtual communication route that is confirmed to be working by automatically identifying a virtual communication route for communications between the DSL modem and a communications network. A DSL modem which performs this methods is also provided.
Owner:HUGHES ELECTRONICS
Fast Byzantine Paxos
InactiveUS20100017495A1Avoid excessive delayCorrect behaviorMultiple digital computer combinationsTransmissionClient-sideComputing systems
A distributed computing system can operate in the face of malicious failures on the part of some of its constituent devices, and provide a minimum of message delays between receiving a client request and providing a response, when each device within the system verifies the sender of any message it receives, and the propriety of the message.
Owner:MICROSOFT TECH LICENSING LLC
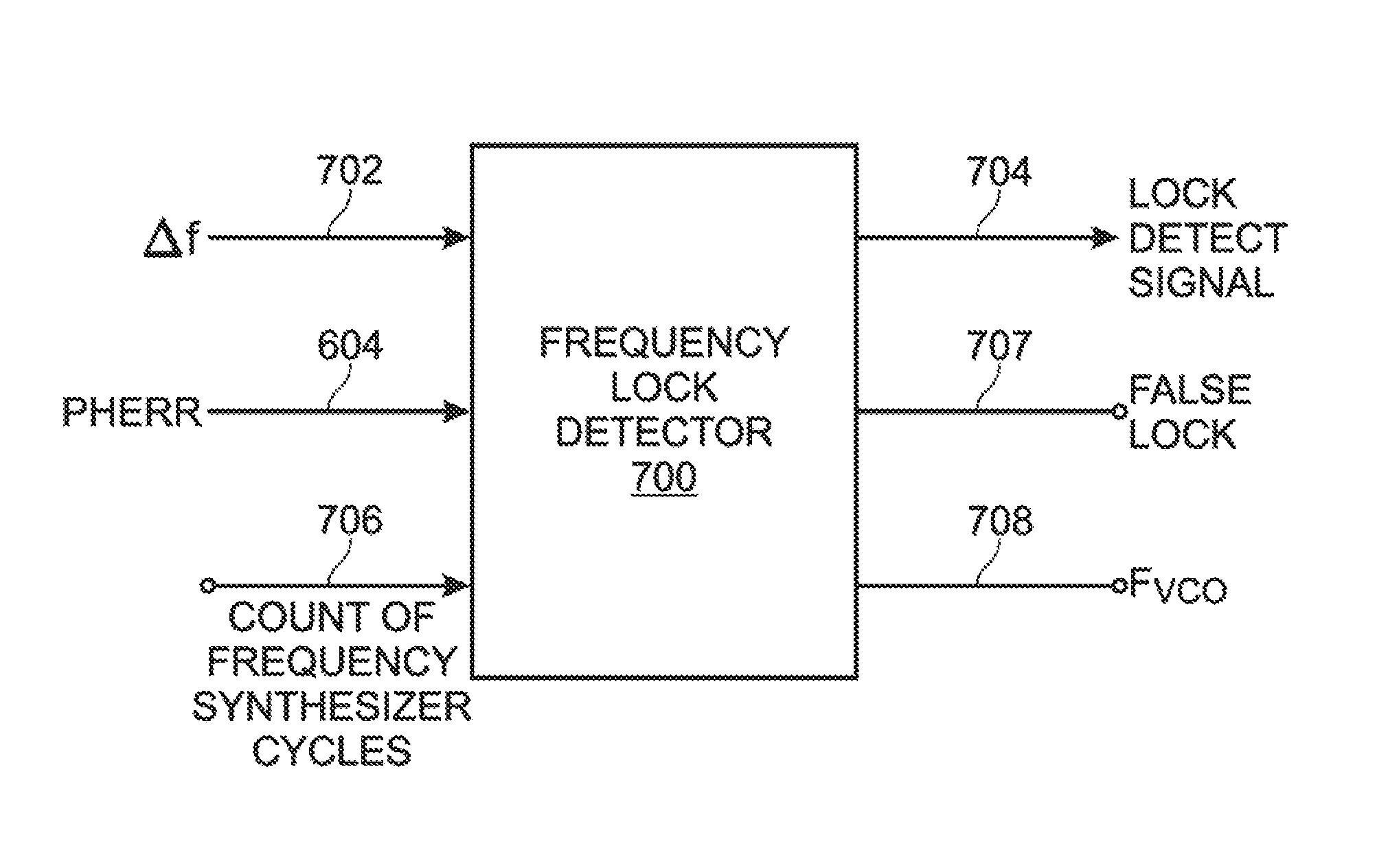
Lock detection using a digital phase error message
ActiveUS8248106B1Improve performanceReduce power consumptionPulse automatic controlFrequency/rate-modulated pulse demodulationClock rateEngineering
A system and method are provided for frequency lock detection using a digital phase error. A lock detection module accepts a digital phase error (pherr) message proportional to an error in phase between a reference clock and a (synthesizer clock*Nf). Also accepted is a unitless frequency error tolerance value (Δf). The lock detection module periodically supplies a lock detect signal, indicating whether the synthesizer clock frequency is within the frequency error tolerance value of the reference clock frequency.
Owner:MACOM CONNECTIVITY SOLUTIONS LLC
Synchronization of seismic data acquisition systems
InactiveUS20070253289A1Good synchronizationSimple methodSeismic signal transmissionSeismic signal recordingTime errorData acquisition
Owner:INOVA SYST CORP
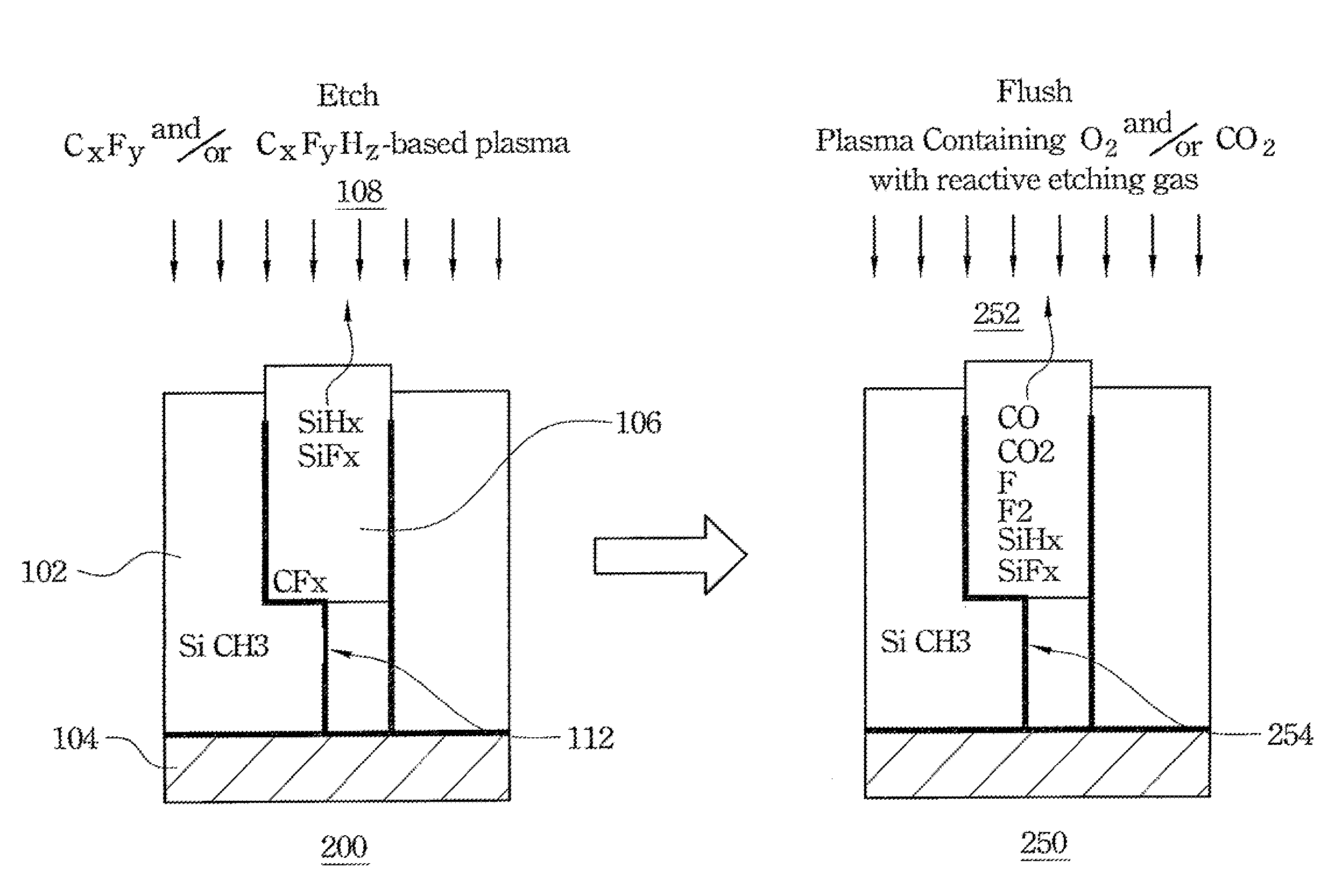
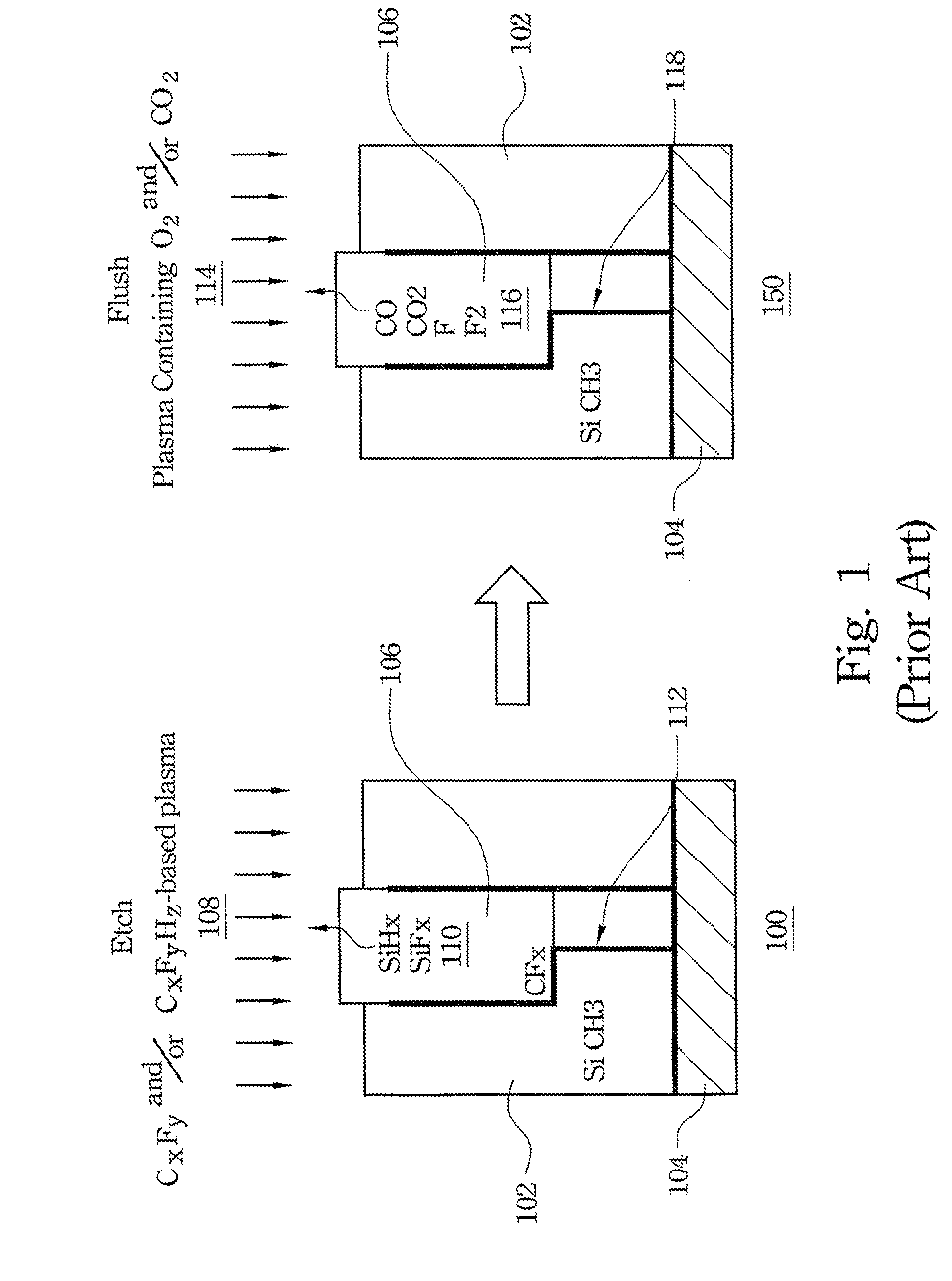
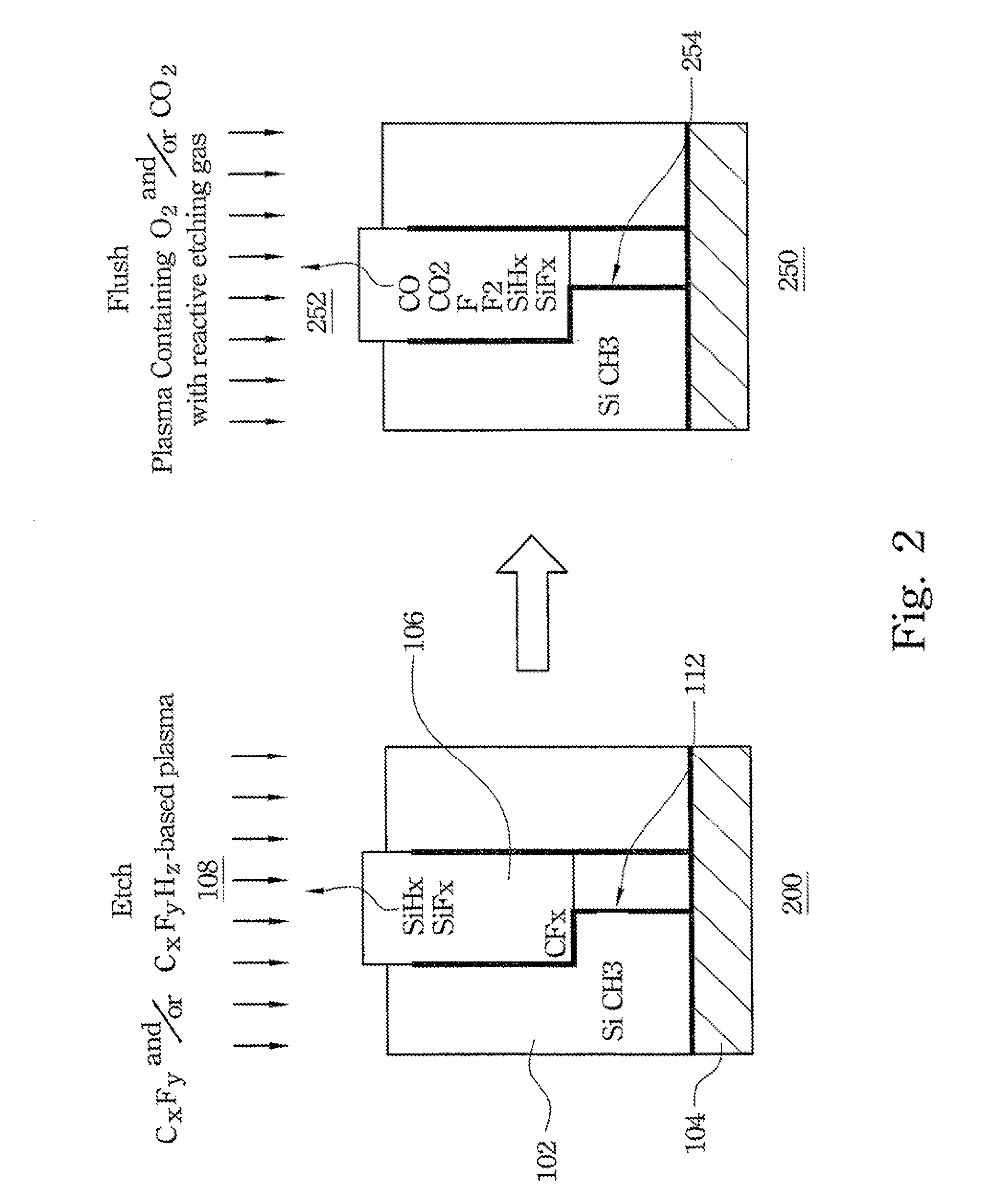
Method for Fabricating Low-k Dielectric and Cu Interconnect
ActiveUS20080311756A1Increase capacitanceImprove RC delaySemiconductor/solid-state device manufacturingDelayed timeIntegrated circuit
A system and method for improving the performance of an integrated circuit by lowering RC delay time is provided. A preferred embodiment comprises adding a reactive etch gas to the ash / flush plasma process following a low-k dielectric etch. The illustrative embodiments implement a removal of the damage layer that is formed during a low-k dielectric etch.
Owner:TAIWAN SEMICON MFG CO LTD
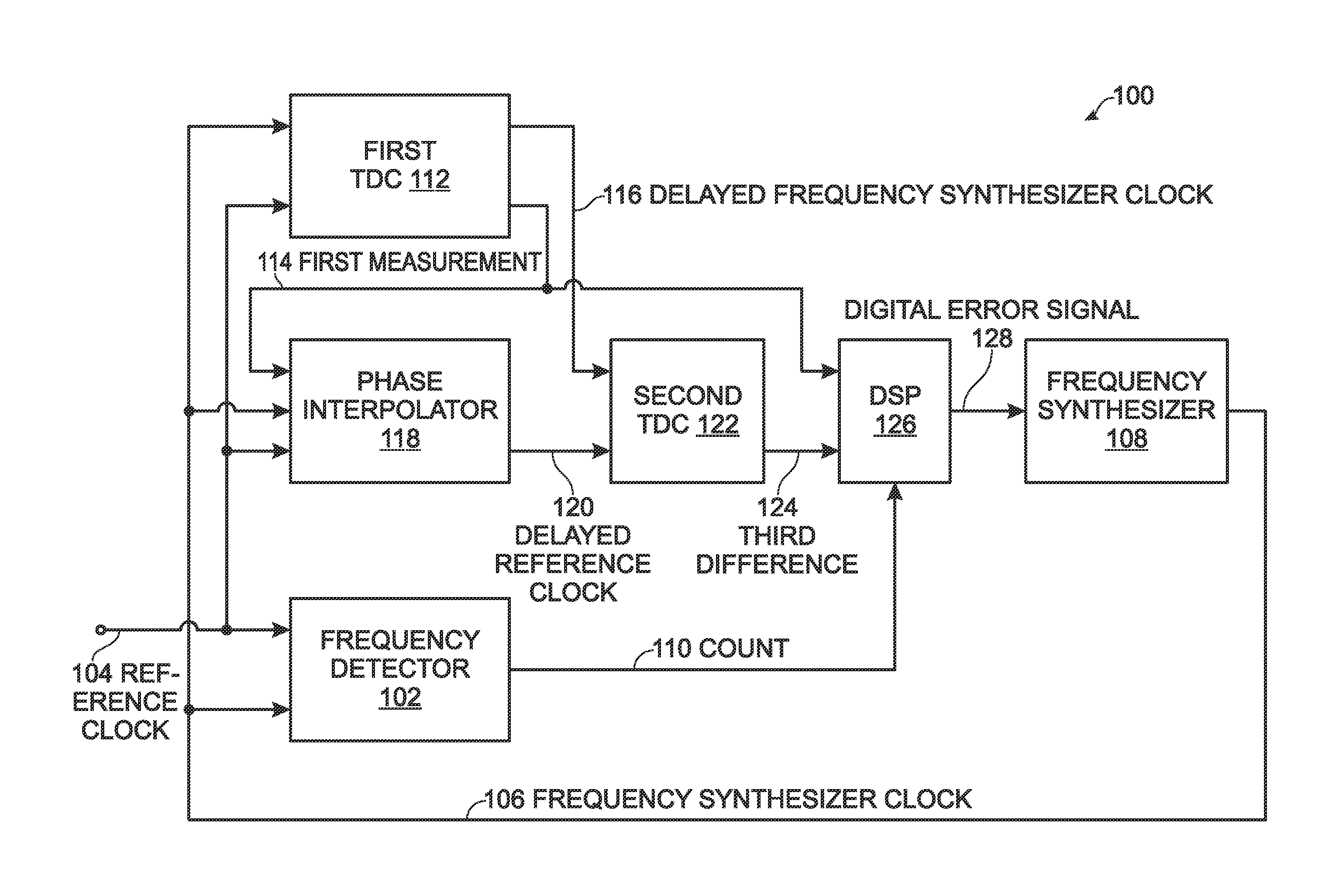
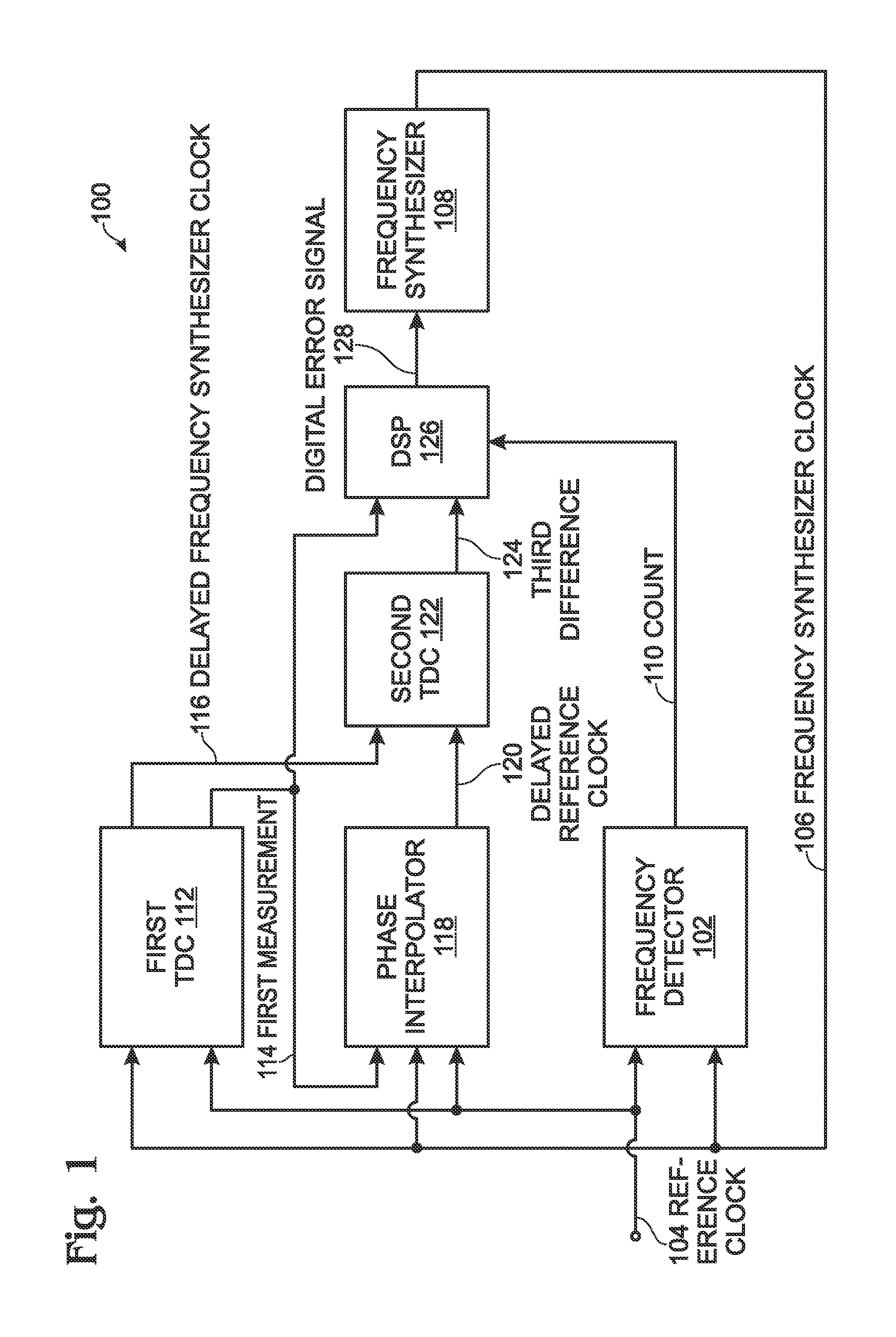
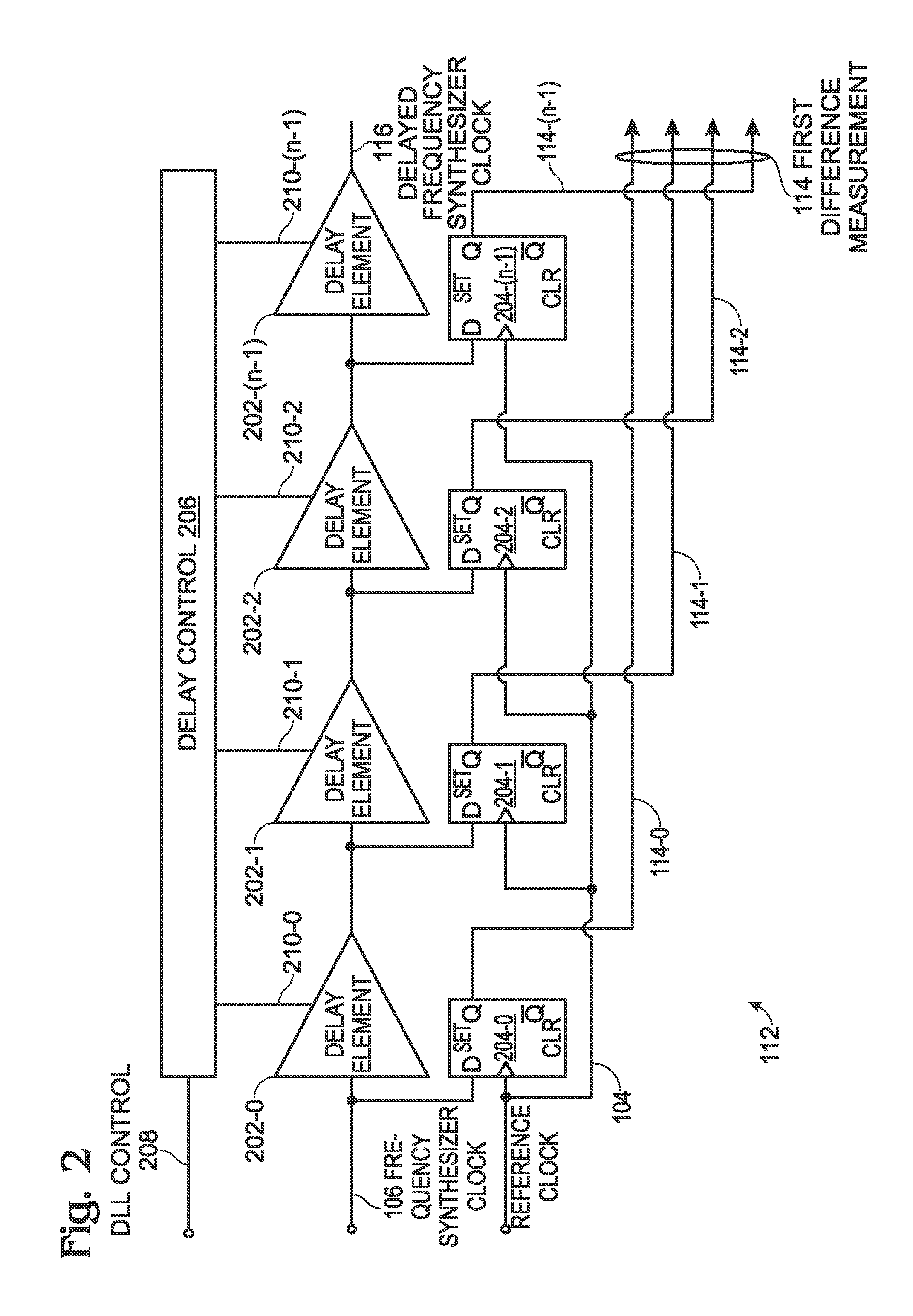
Successive time-to-digital converter for a digital phase-locked loop
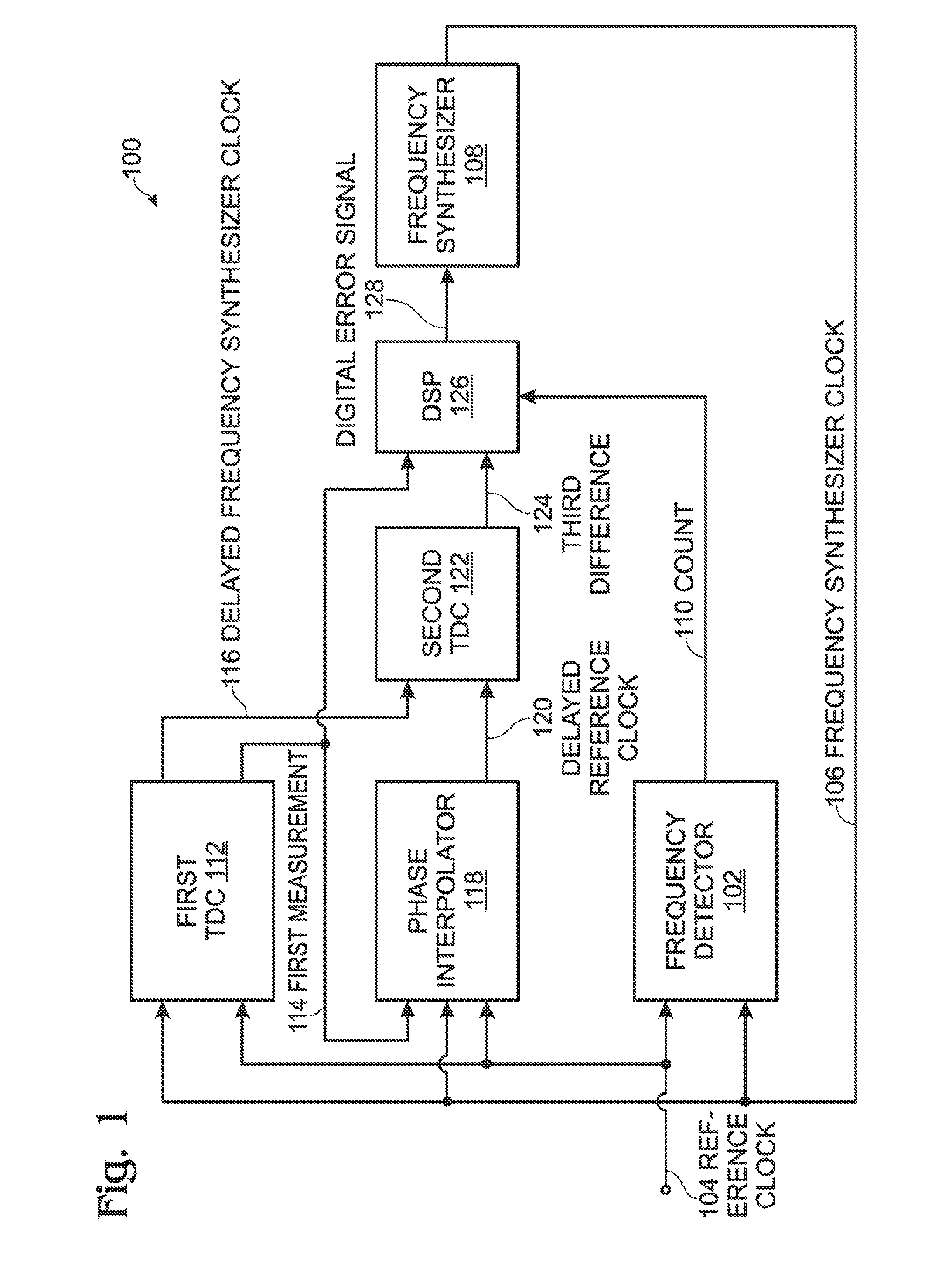
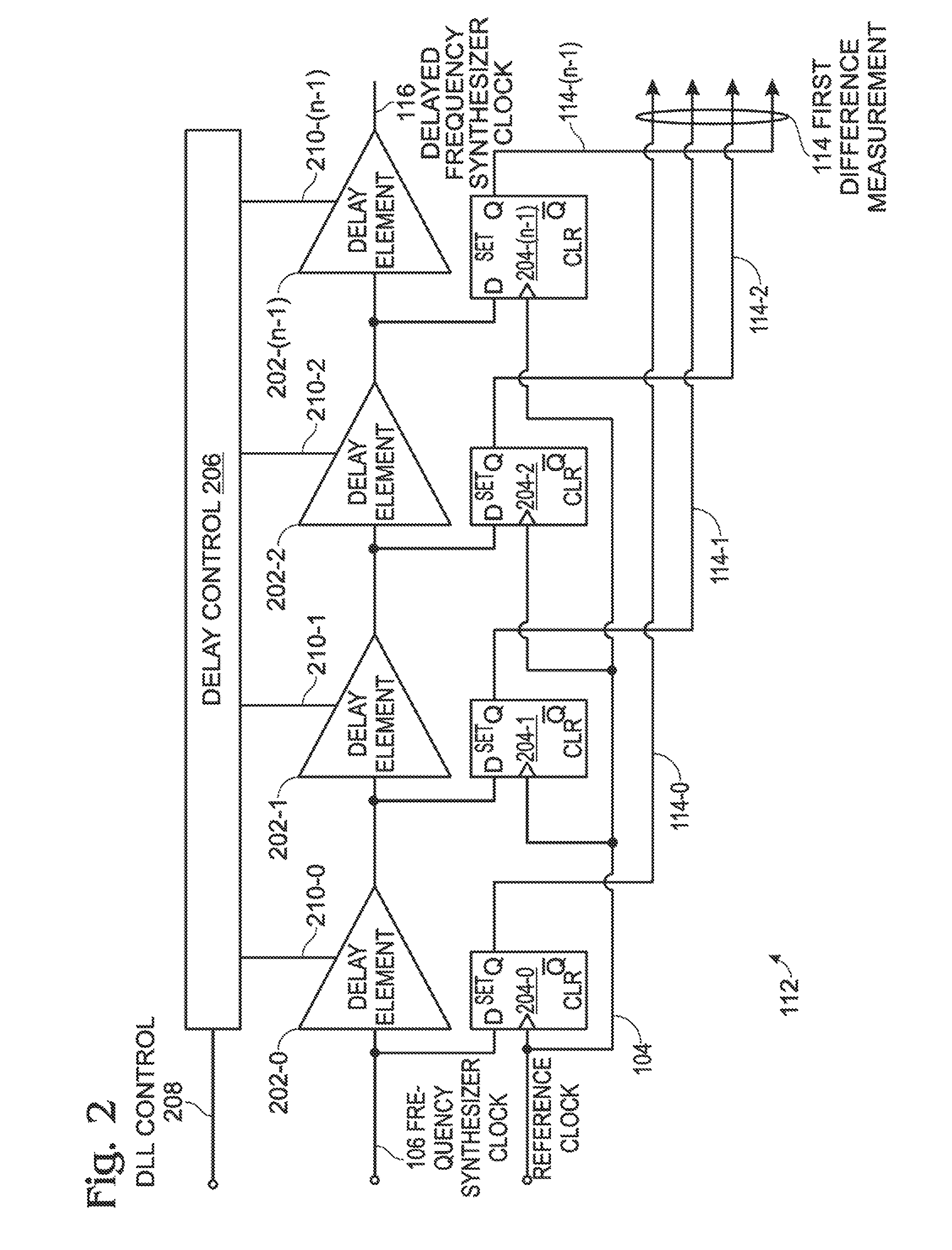
ActiveUS8106808B1Reduce power consumptionPromote high performanceElectric signal transmission systemsPulse automatic controlFrequency synthesizerDigital converter
A successive time-to-digital converter (STDC) method is provided for supplying a digital word representing the ratio between a phase-locked loop PLL frequency synthesizer signal and a reference clock. The number of frequency synthesizer clock cycles per reference clock cycle is counted. A first difference is measured between a reference clock period and a corresponding frequency synthesizer clock period. In response to the first measurement, a second difference is measured between a delayed reference clock period and the corresponding frequency synthesizer clock period, where the second difference is less than the first difference. A third difference is measured as a time duration between the delayed reference clock period and the corresponding delayed frequency synthesizer clock period. The first and third difference measurements and the count of the number of frequency synthesizer clock cycles per reference clock cycle are used to calculate a digital error signal supplied to the frequency synthesizer.
Owner:MACOM CONNECTIVITY SOLUTIONS LLC
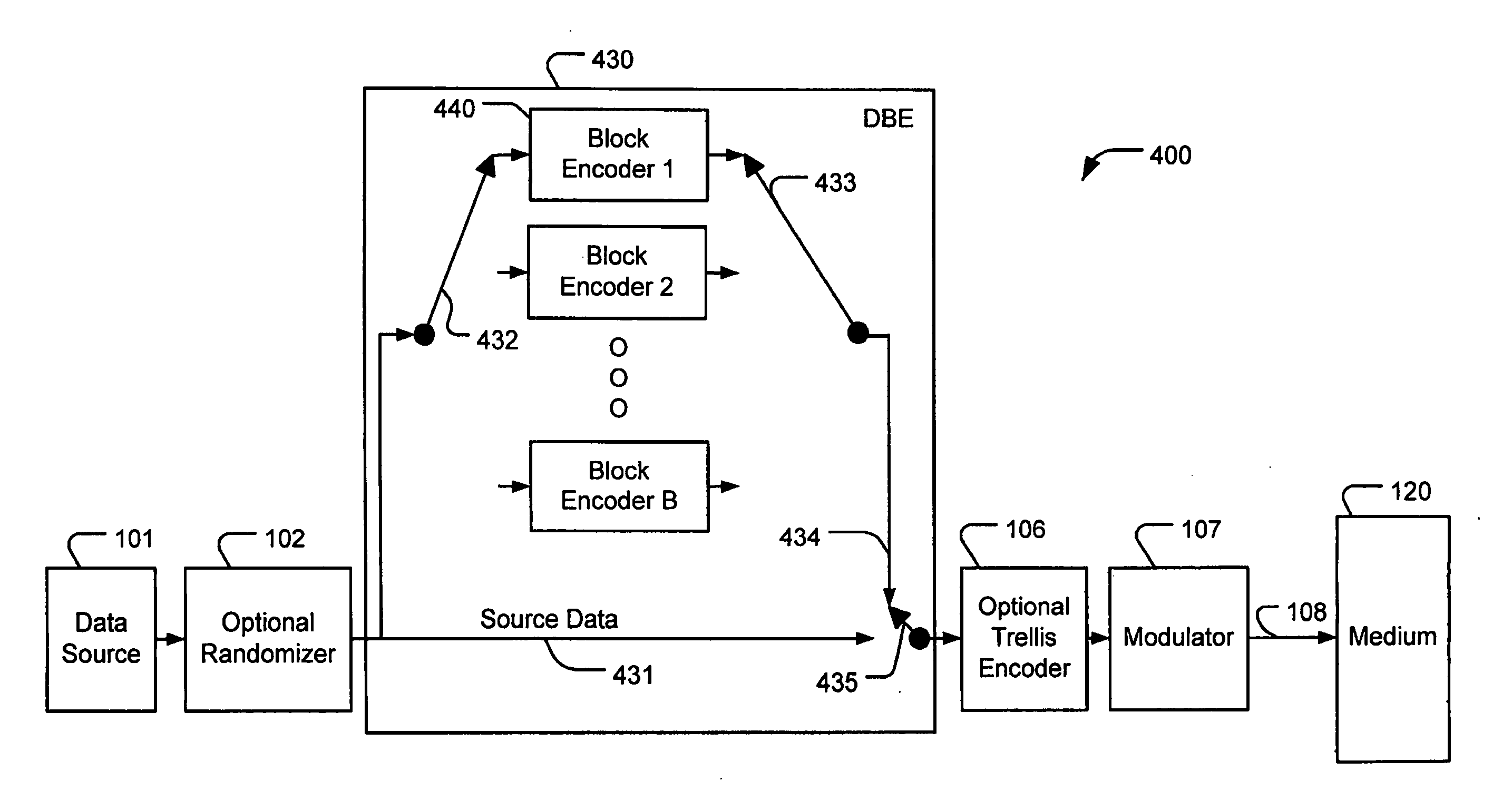
Distributed block coding (DBC)
InactiveUS20080065971A1Avoid excessive delayReduce complexityOther error detection/correction/protectionError detection/correctionDBcCommunications system
Various embodiments implement distributed block coding (DBC). DBC can be used for, among other things, distributed forward error correction (DFEC) of source data in communication systems or parity backup for error correction of source data in storage systems where the source data may be corrupted by burst errors. A distributed block encoder (DBE) encodes sequential source data symbols with a plurality of sequential block encoders to produce interleaved parity codewords. The interleaved parity codewords enable decoding of error-corrected source data symbols with a distributed block decoder (DBD) that utilizes a plurality of sequential block decoders to produce the error-corrected source data symbols. A distributed register block encoder (DRBE) and a distributed register block decoder (DRBD) can each be implemented in a single block encoder and a single block decoder, respectively, by using a distributed register arrangement.
Owner:SUNRISE IP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com