Patents
Literature
426 results about "Hard coding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
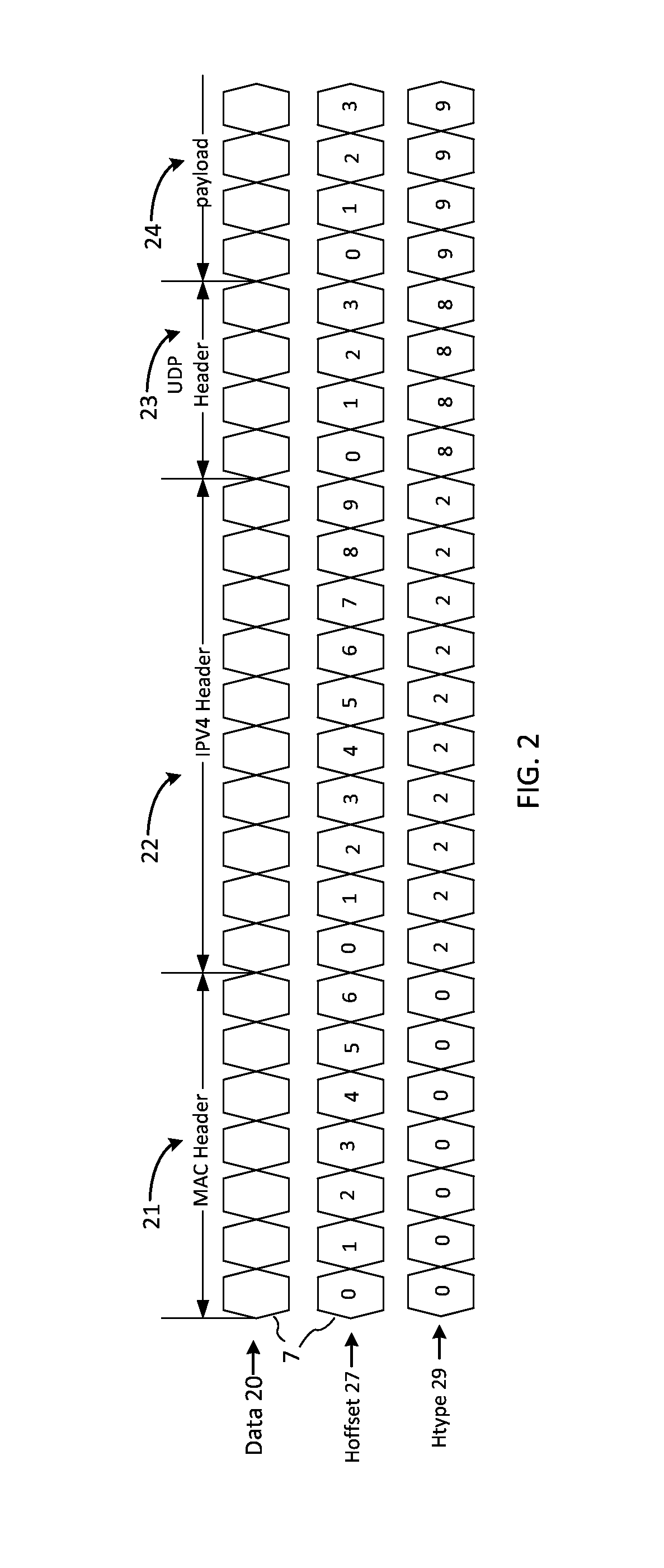
Hard coding (also hard-coding or hardcoding) is the software development practice of embedding data directly into the source code of a program or other executable object, as opposed to obtaining the data from external sources or generating it at run-time. Hard-coded data typically can only be modified by editing the source code and recompiling the executable, although it can be changed in memory or on disk using a debugger or hex editor. Data that are hard-coded usually represent unchanging pieces of information, such as physical constants, version numbers and static text elements. Softcoded data, on the other hand, encode arbitrary information like user input, HTTP server responses, or configuration files, and are determined at runtime.
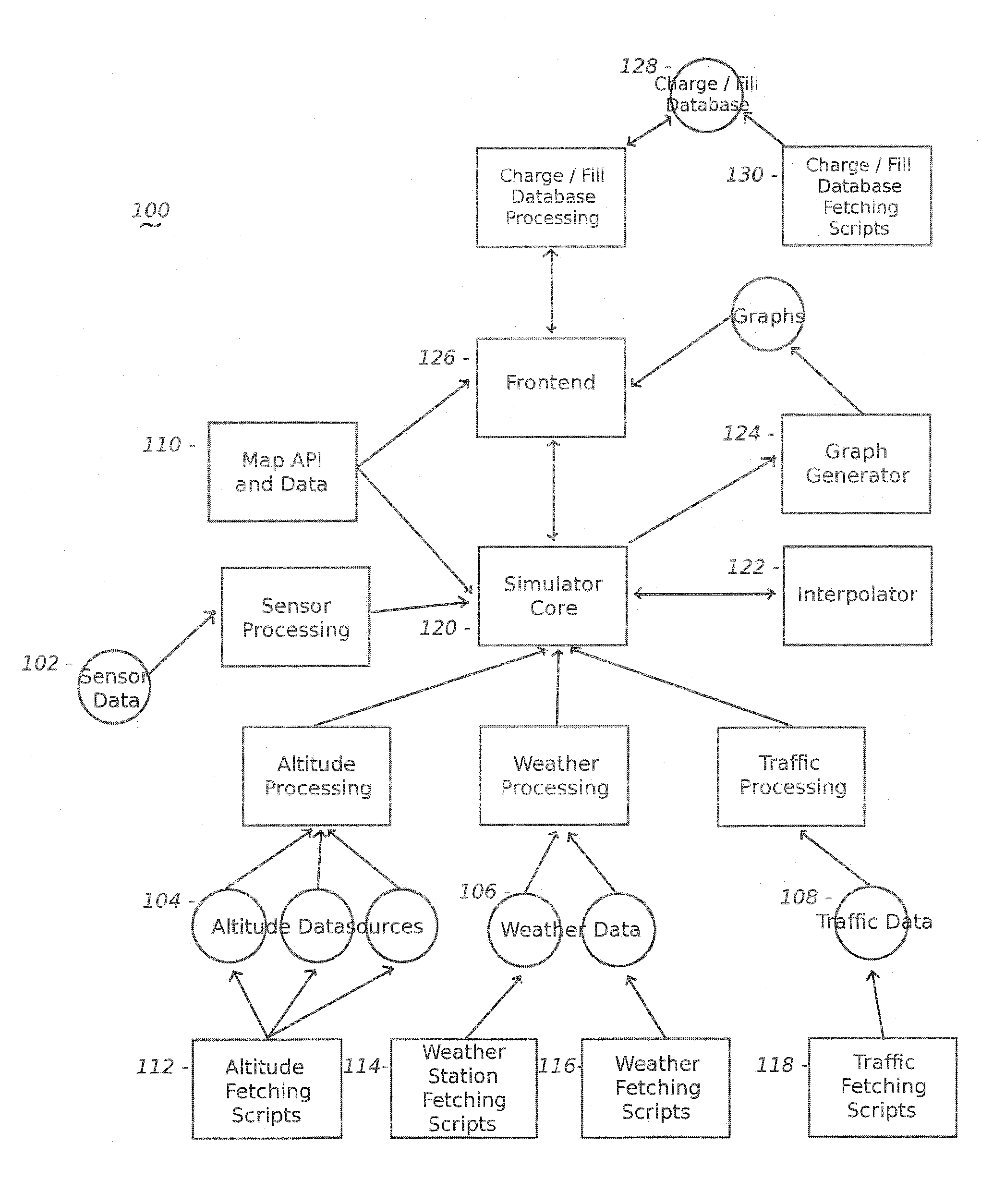
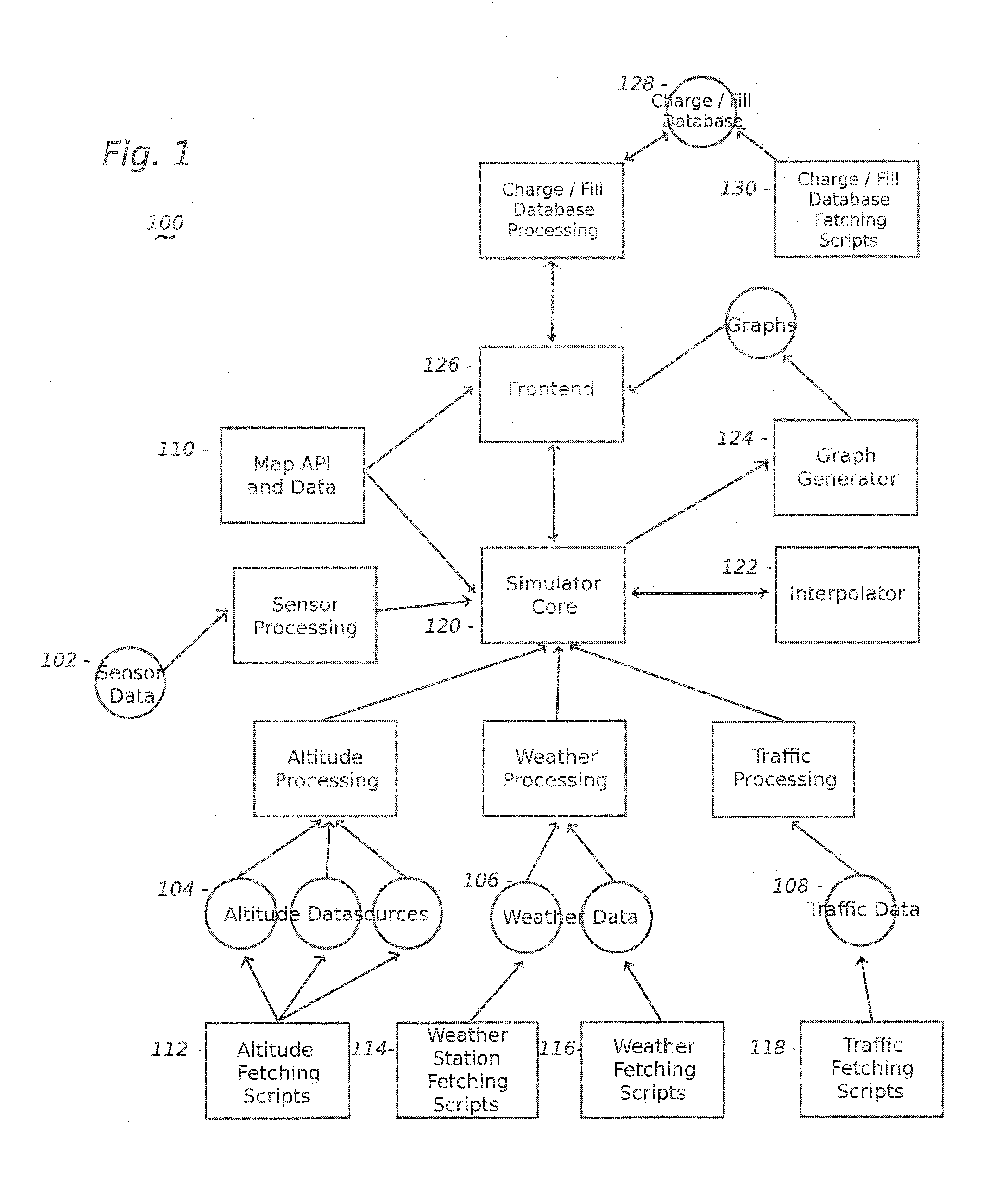
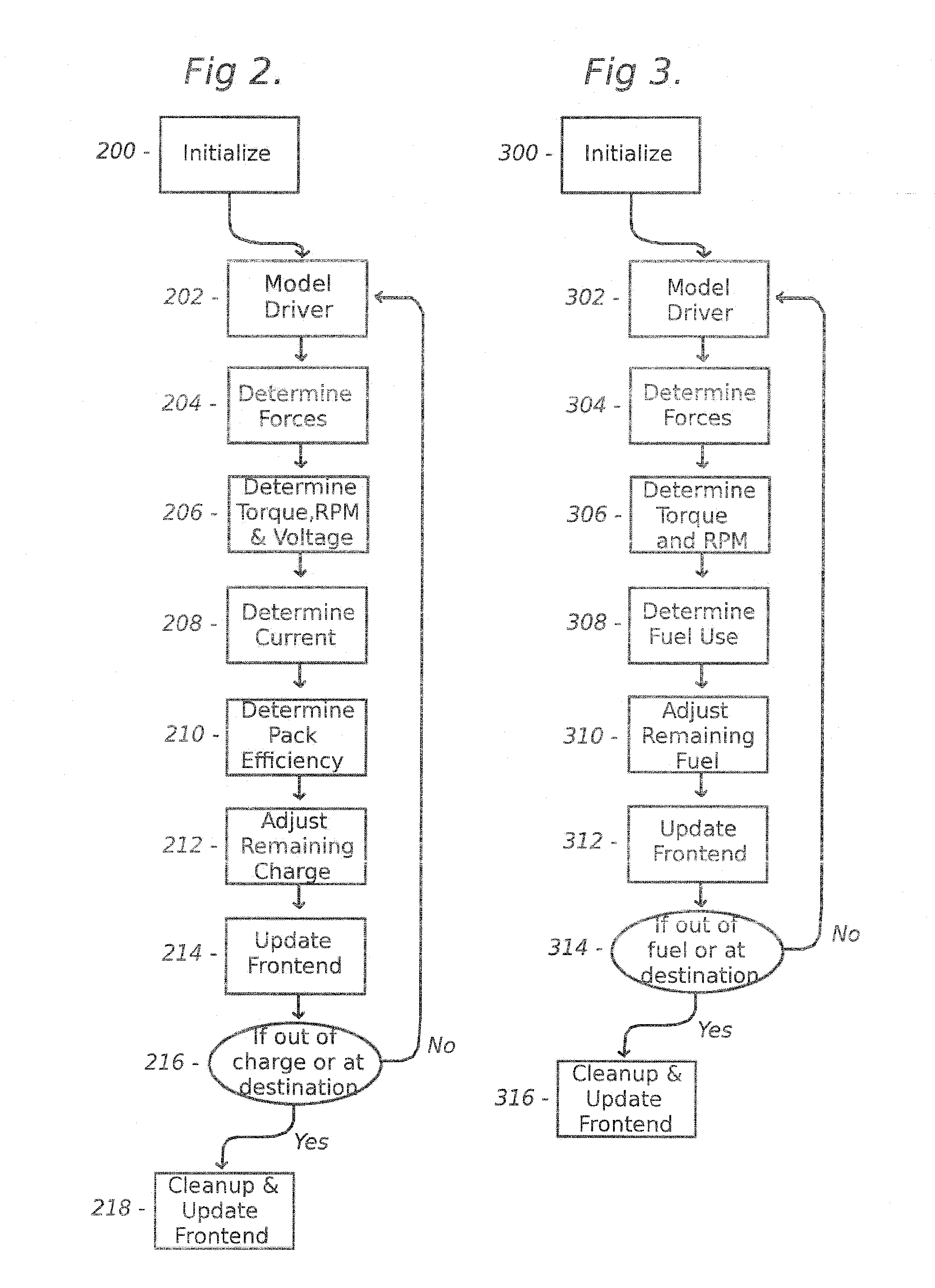
Vehicle Range Finder
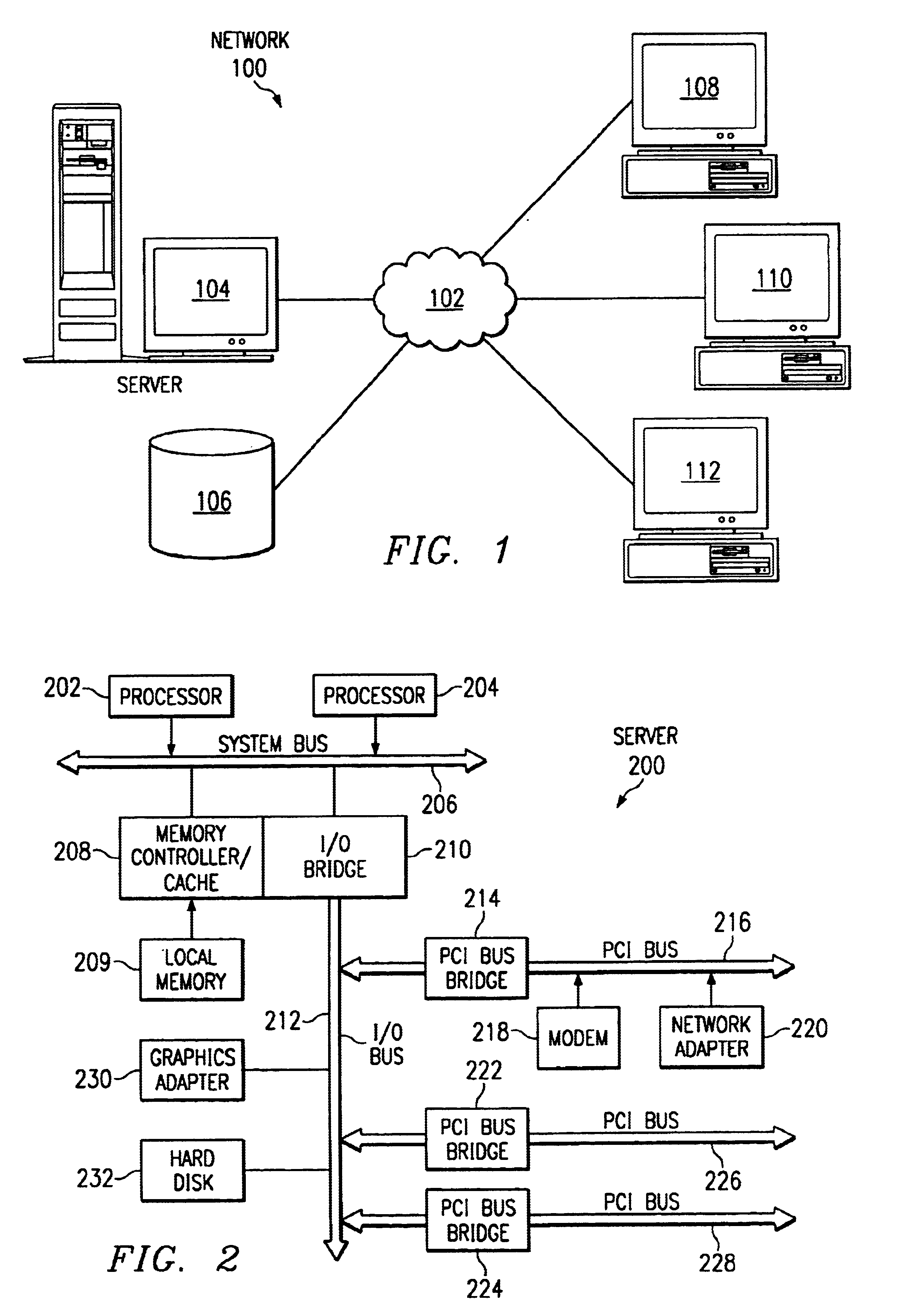
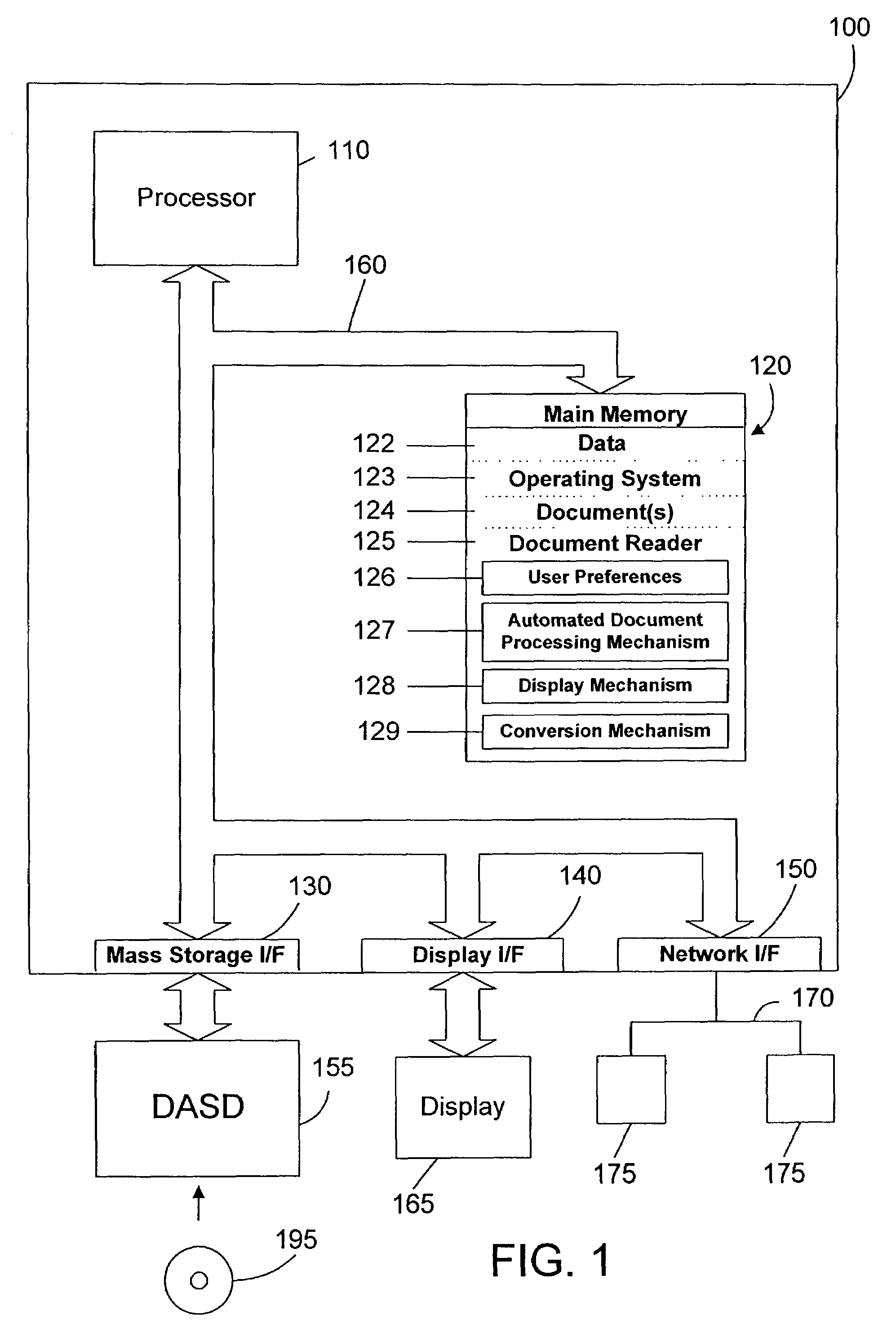
The present invention includes, among other embodiments, a system embedded in a vehicle including several inputs. The inputs may include one hard coded data, data from sensors on the vehicle, data from external sensors, user coded data, data received from remote databases, data received from broadcast data steams or data that has been accumulated during use of the vehicle. The inputs provide information regarding vehicle speed, motor rpm, motor torque, battery voltage, battery current, and battery charge level, etc. The embedded system also includes a processor unit that receives information from the plurality of inputs and calculates at least an expected vehicle range. The results of any calculations completed by the processing unit is supplied as an output to a display unit, which then displays the information to the user.
Owner:CELADON APPL
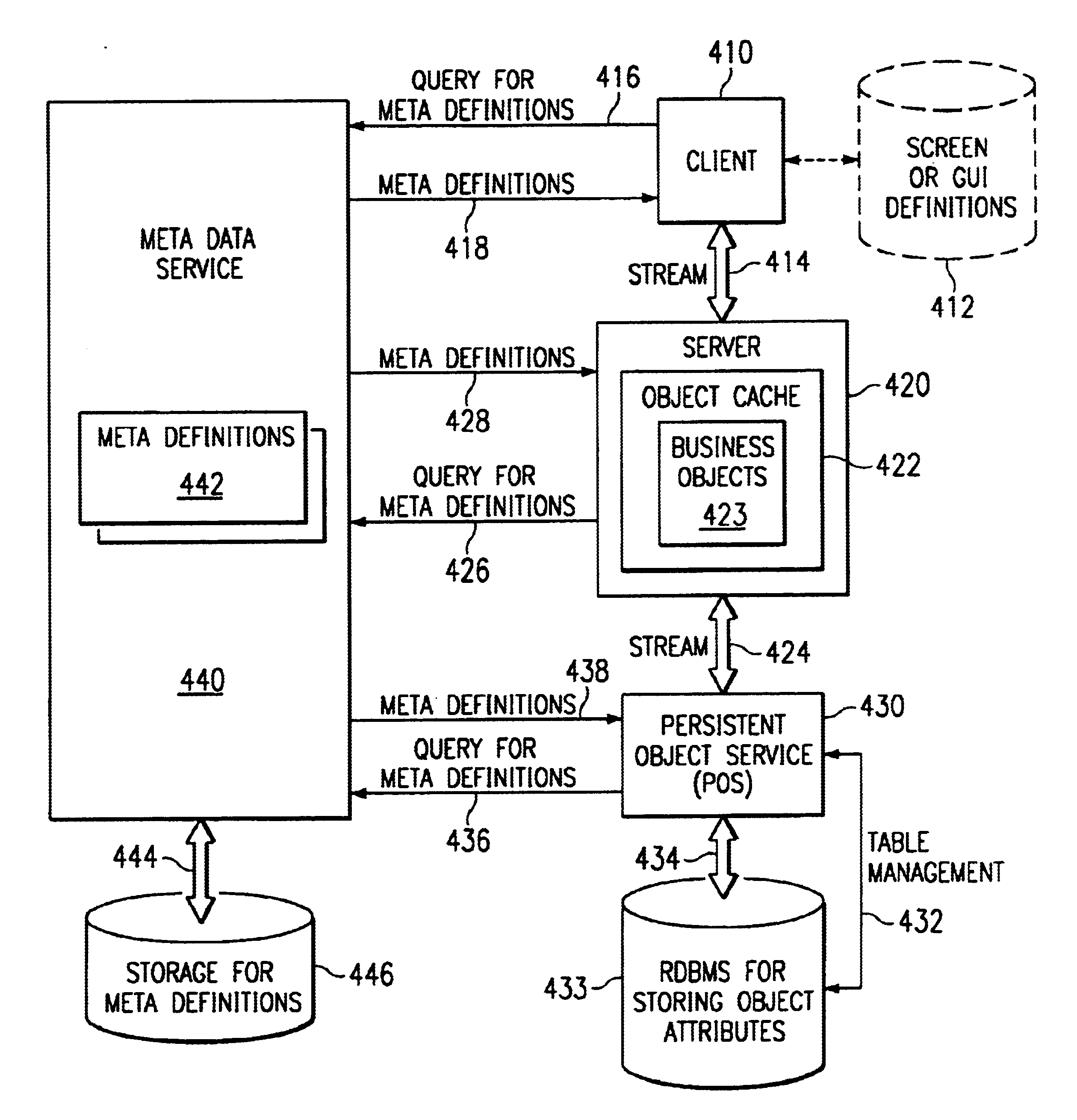
Method and apparatus for a Meta Data Service in a data processing system
InactiveUS6857123B1Precise processingData processing applicationsInterprogram communicationHard codingData processing system
As a solution to the problem of distributed knowledge of data object definitions, data object definitions are removed from the source code. A Meta Data Service is created and made available on a network which knows the definitions of all of the objects that are used by applications that are designed to use the Meta Data Service. When an object is created, the Meta Data Service creates and stores a meta definition for the object. Data objects are passed over a network in a “soft” format. Applications within a distributed data processing system are designed in such a manner such that, at any stage of object processing, an application does not assume to understand the definition or structure of an object, nor is an application hard-coded with the object definitions. At each stage, an application queries the Meta Data Service for the meta definition of the object before proceeding with the processing of an object. The application then receives a meta definition for the data object that allows the application to perform properly tailored processing for the data object.
Owner:IBM CORP
Automated transaction management system and method
InactiveUS6862573B2Reduce errorsReduce labor costsOffice automationResourcesHard codingHuman operator
An automated knowledge dependent transaction management system for processing both the front-end and back-end of a transaction is provided. The system contains hard-coded transaction management module to support the processing of deterministic manual work independent of the specific transactions. According to the invention, the hard-coded module is separated from the business logic that comprise the definition and configuration of the transaction specific data models, business rules and process steps which drive the manual work of human operators. Such separation of code and business logic allows any ordinary business administrator without any computer programming experience to quickly develop the business logic through a simple GUI. Further, any change in the business logic can be implemented quickly using the GUI by the ordinary administrator to accommodate changes in the business environment without relying on computer programmers.
Owner:VERSATA
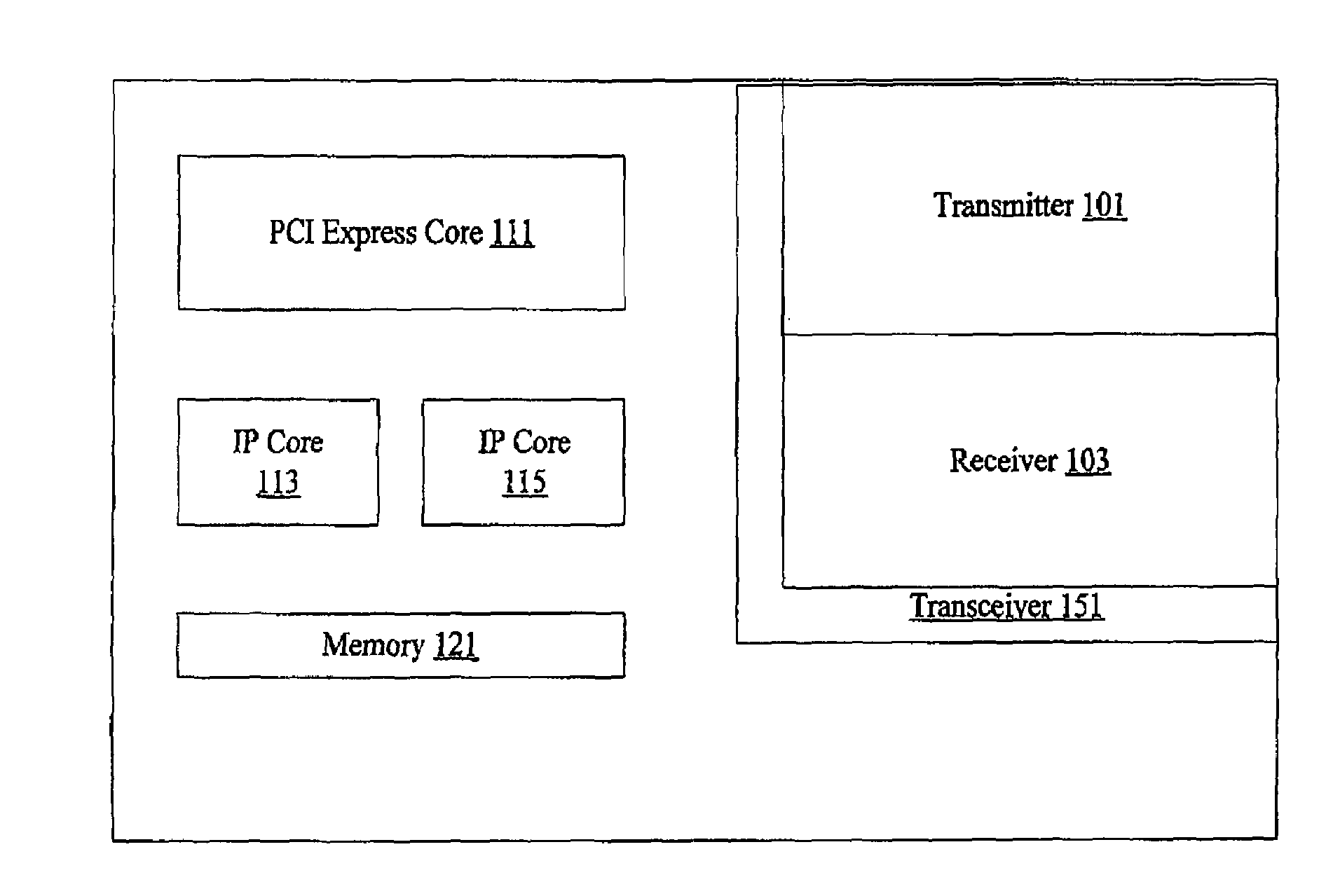
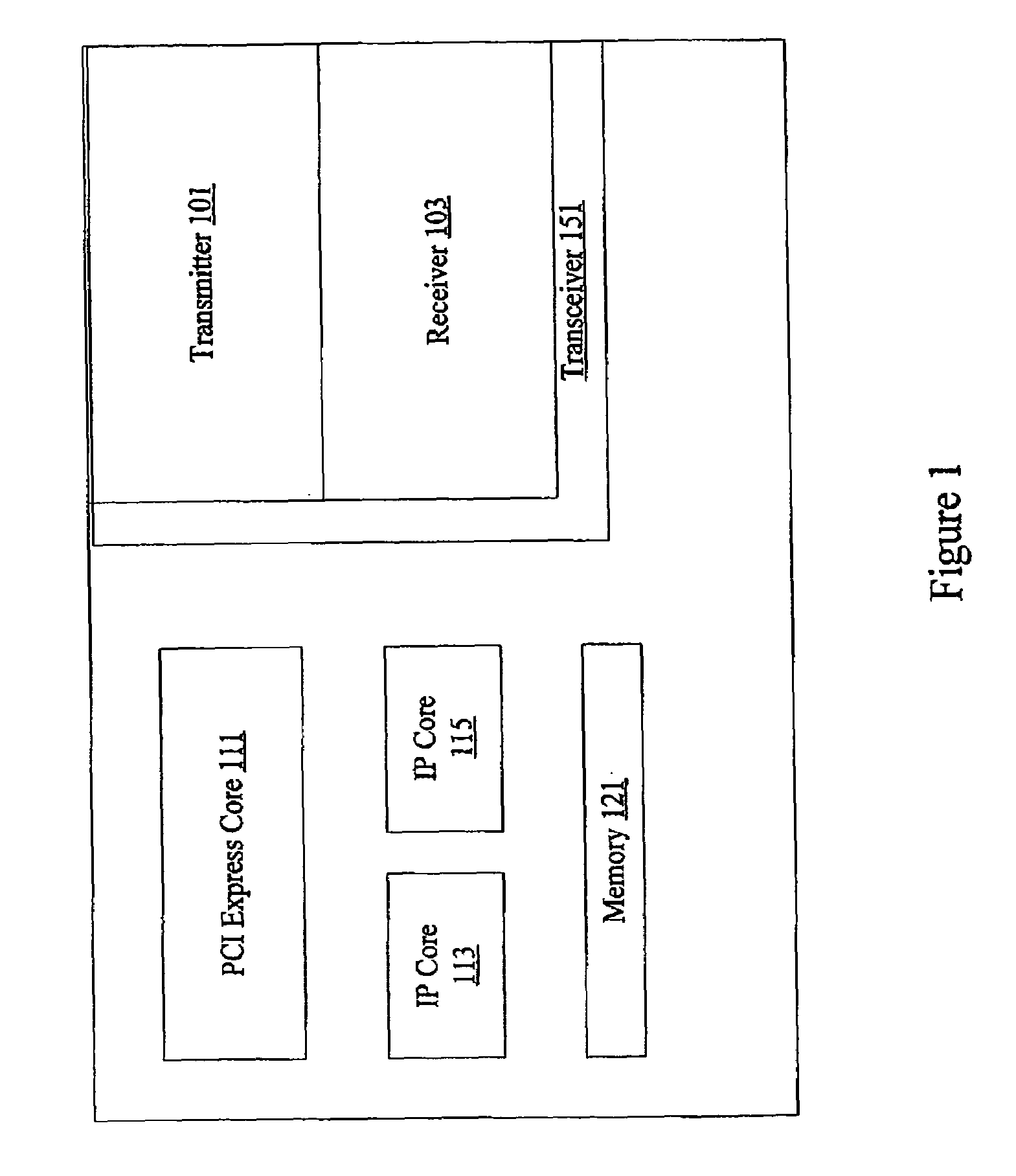
Embedded PCI-Express implementation
InactiveUS7257655B1Reduces logic resource costEffectiveTime-division multiplexData switching by path configurationQuality of serviceHard coding
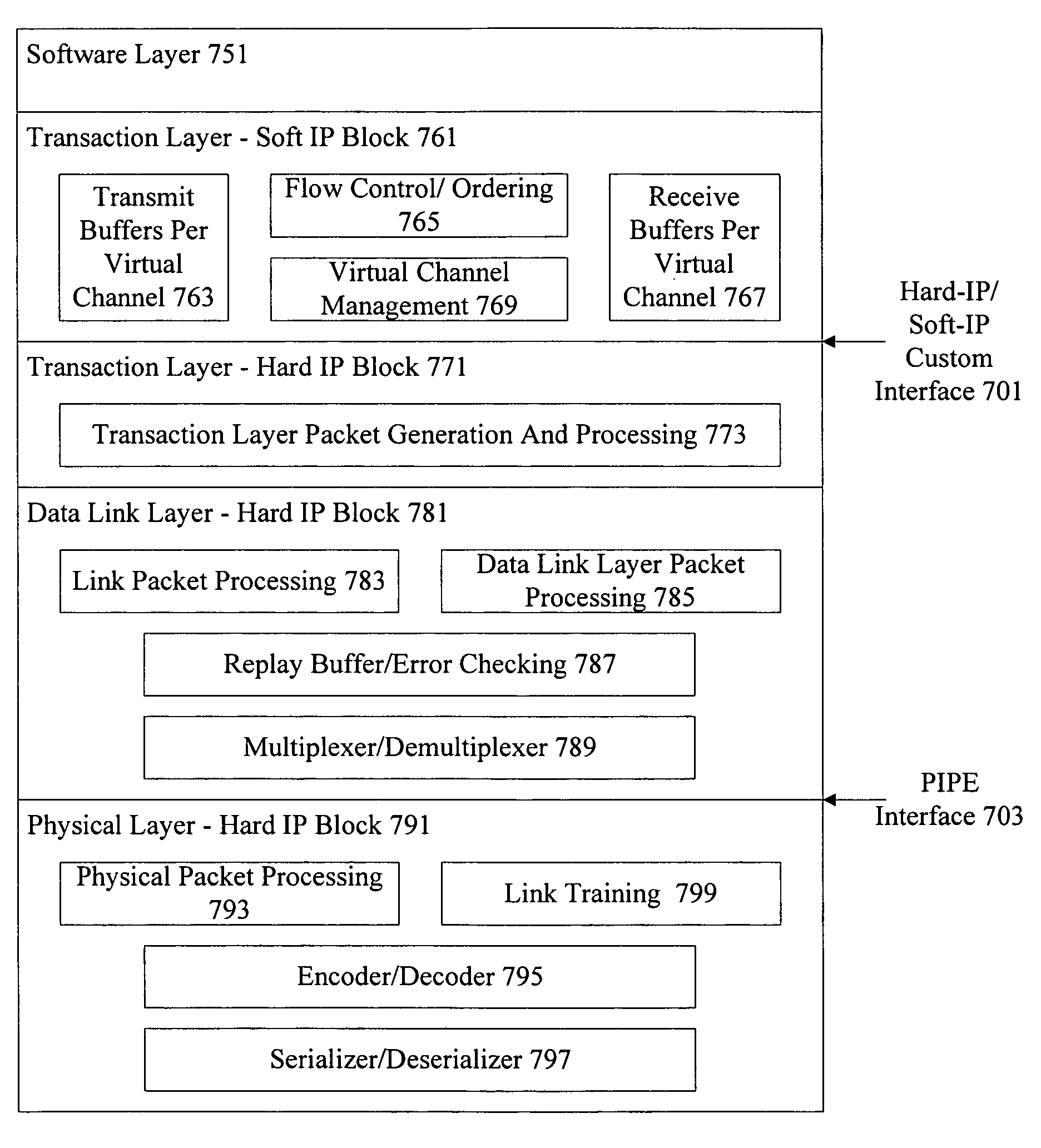
Methods and apparatus provide PCI Express support on a programmable device. A device includes a hard-coded transceiver that supports functionality associated with the PCI Express physical layer and link layer. The hard-coded transceiver can also support part of the PCI Express transaction layer. Soft-coded logic is used to support higher layer functionality including a portion of the transaction layer to allow custom configuration of PCI Express features such as virtual channels, buffers, prioritization, and quality of service characteristics. The hybrid solution reduces logic resource cost and provides an effective custom configurable solution.
Owner:ALTERA CORP
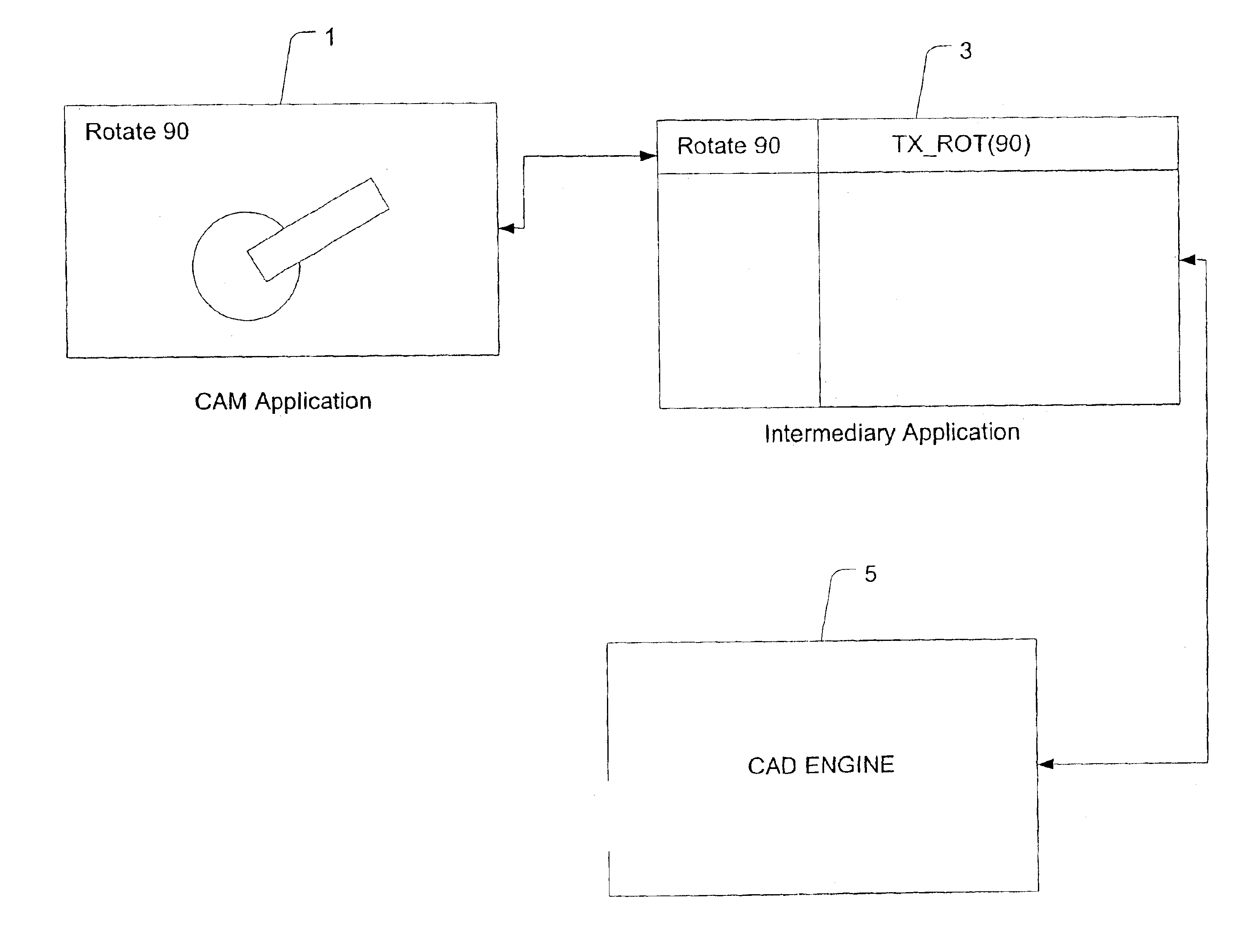
Method and system for CAD engine independence
InactiveUS6868359B2Digital computer detailsSpeed measurement using gyroscopic effectsHard codingSoftware engineering
An exemplary embodiment is a system providing CAD engine independence for a coordinate measurement system. The system includes an interface between a coordinate measurement system application and a CAD engine application. The interface is specific to the CAD engine application and allows a single coordinate measurement system application to be interfaced to one or more CAD engines without the dependency of hard coding to a particular CAD engine.
Owner:FARO TECH INC
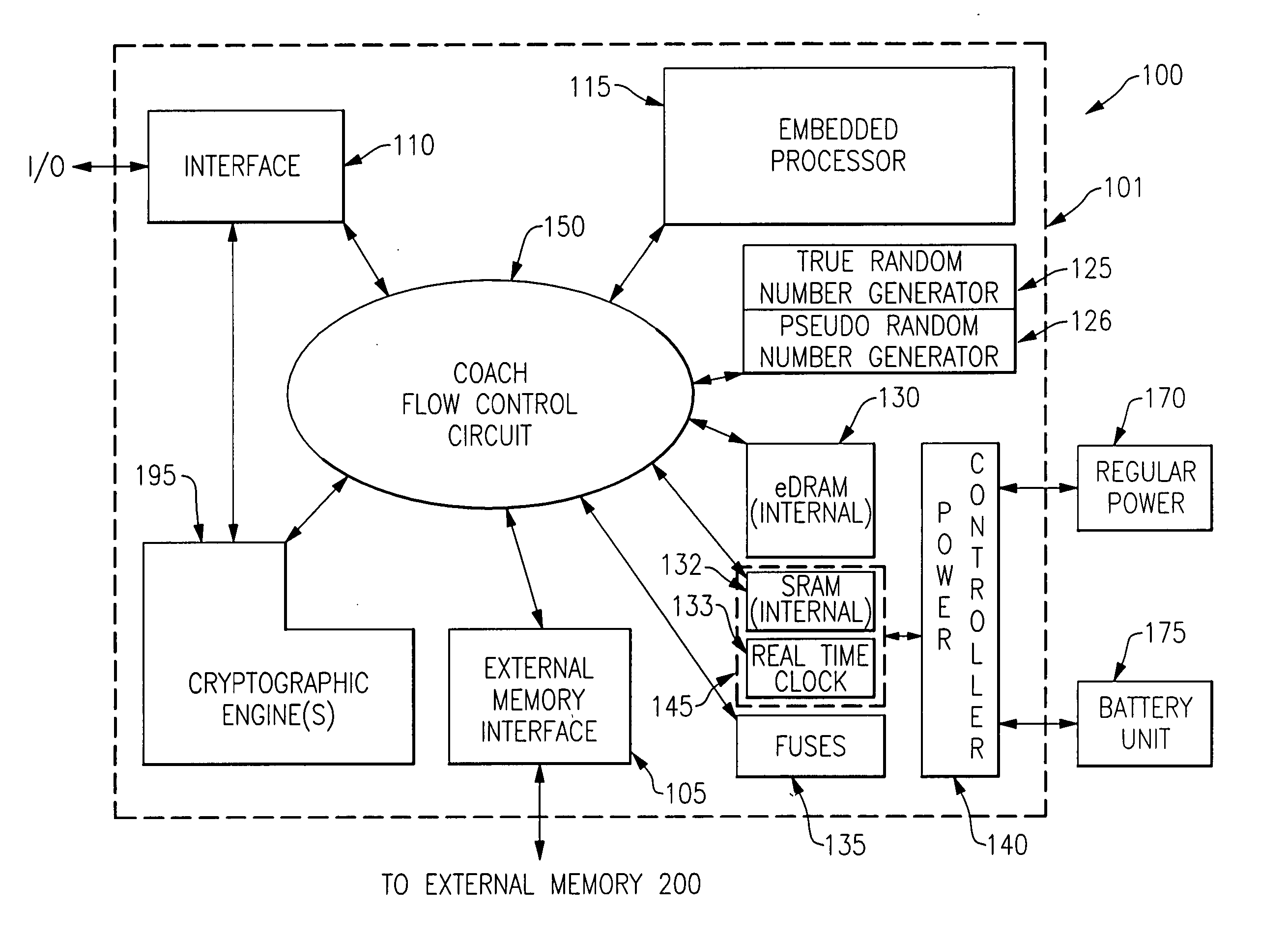
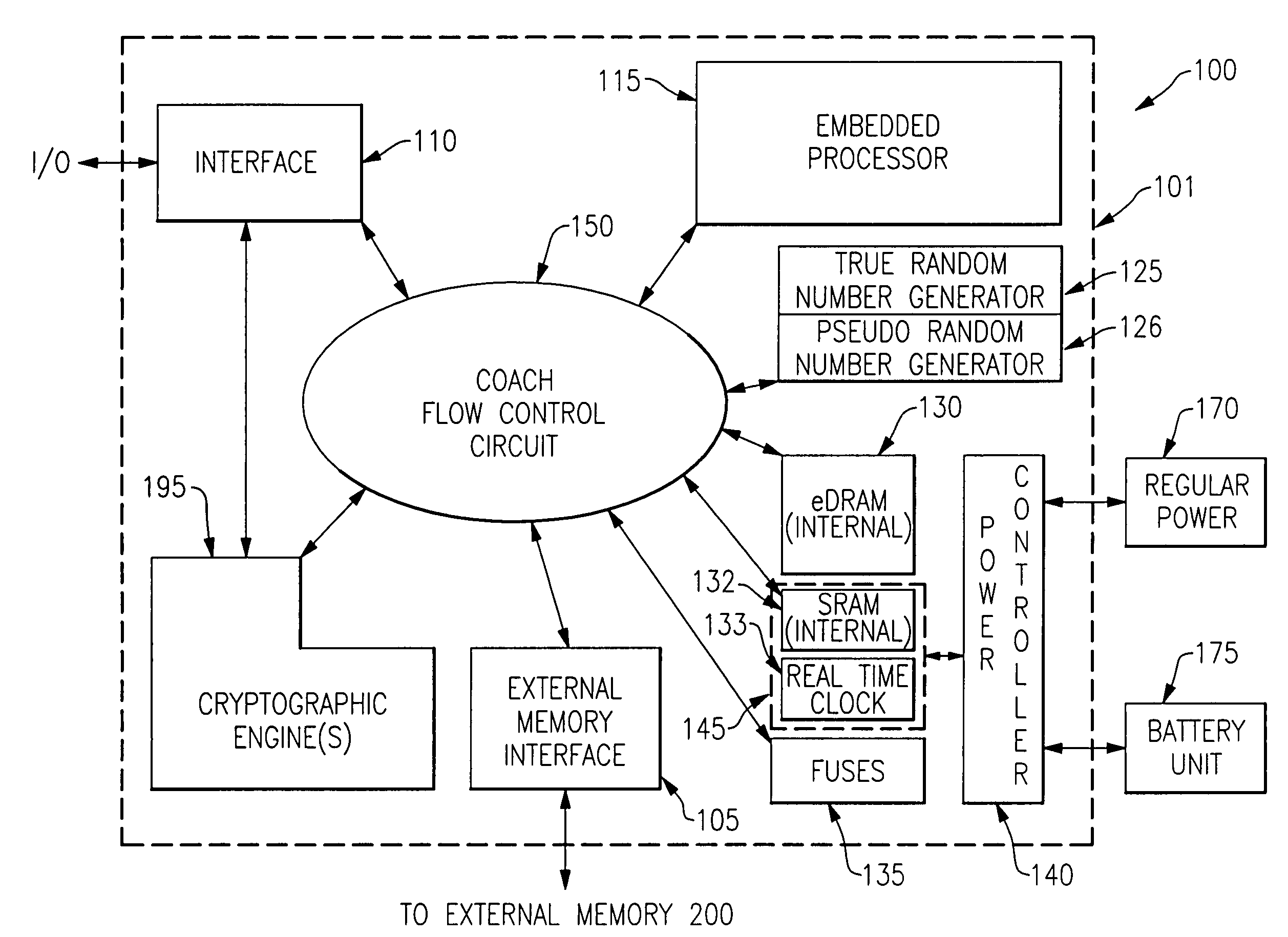
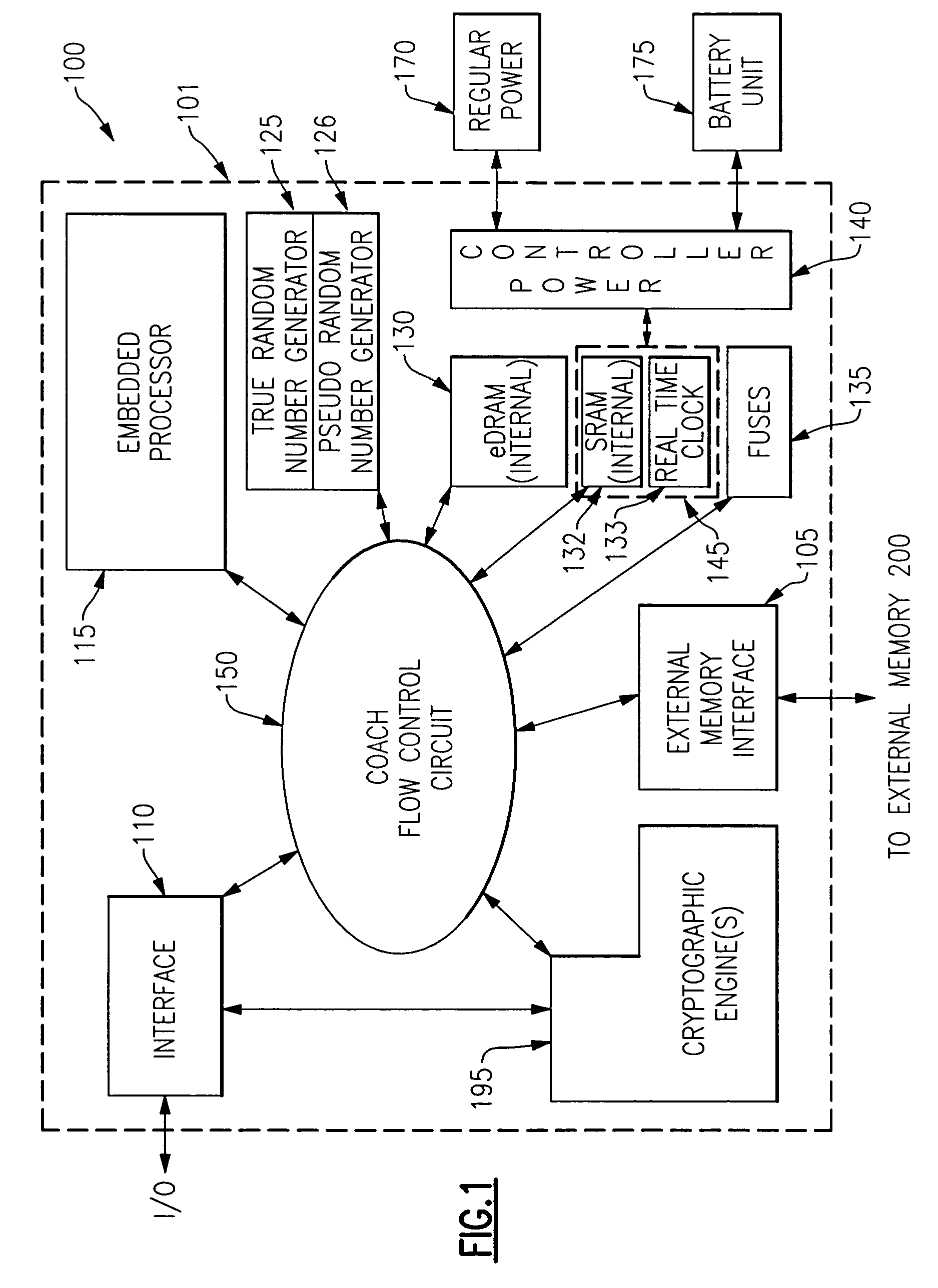
Integrated circuit chip for encryption and decryption having a secure mechanism for programming on-chip hardware
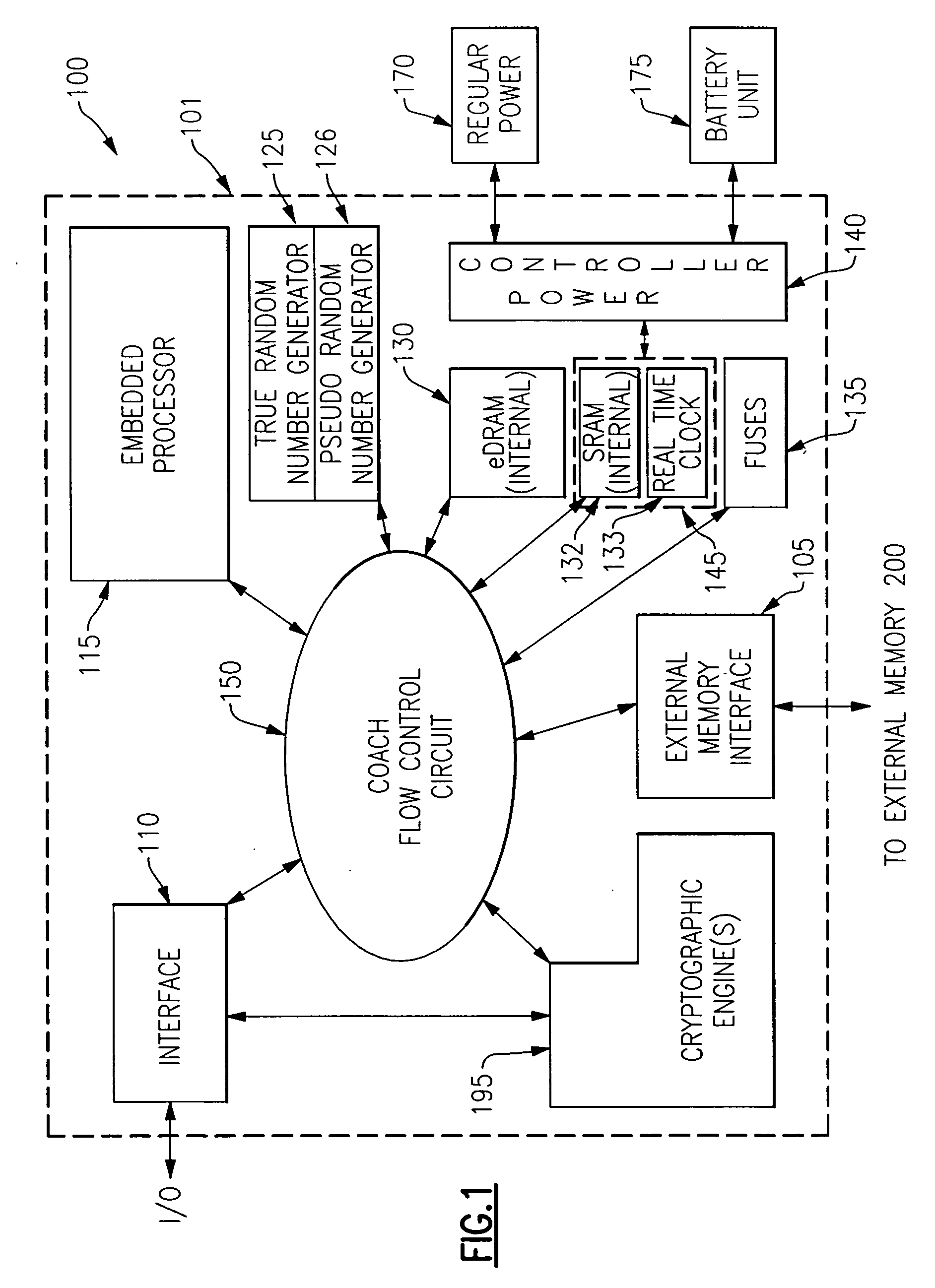
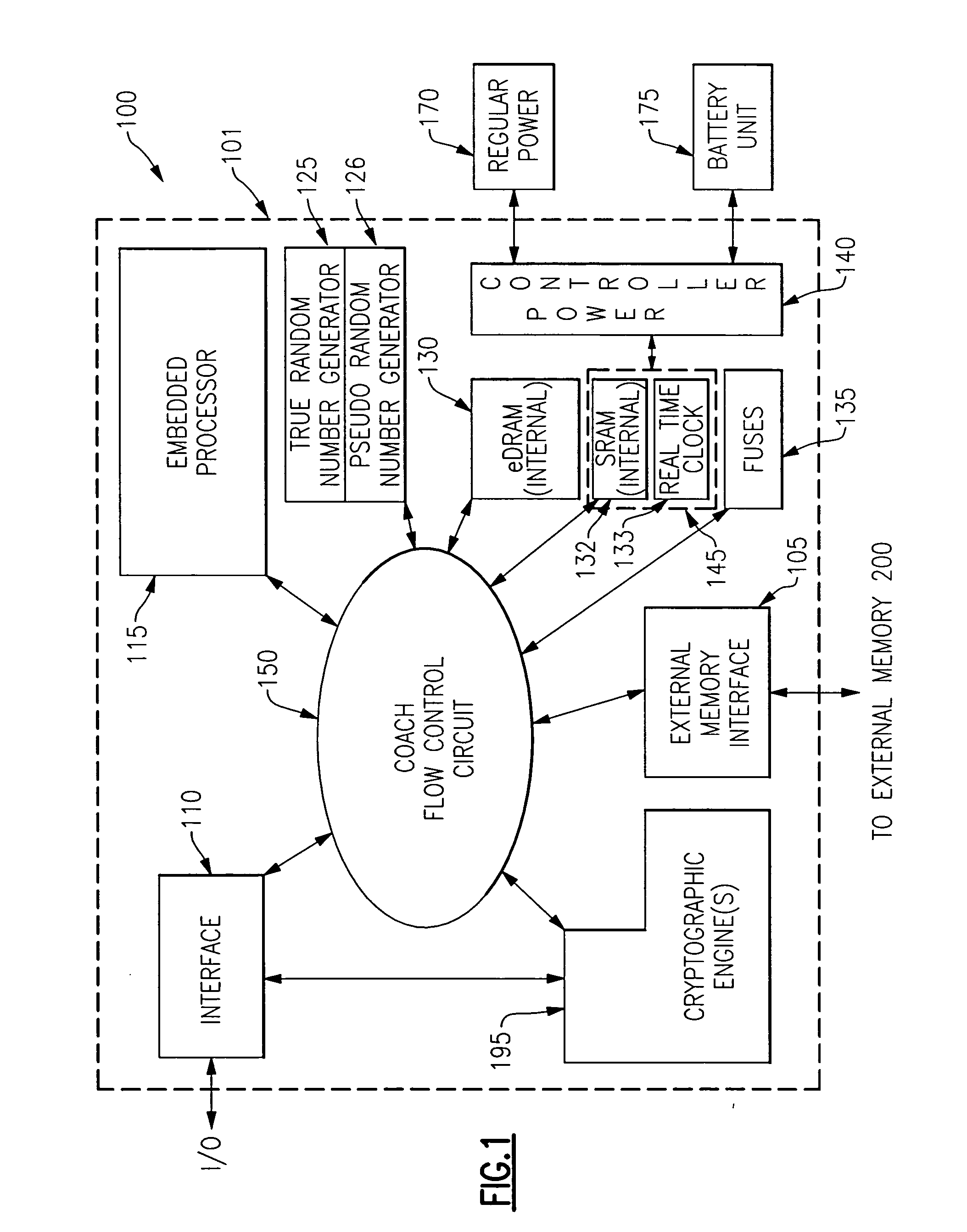
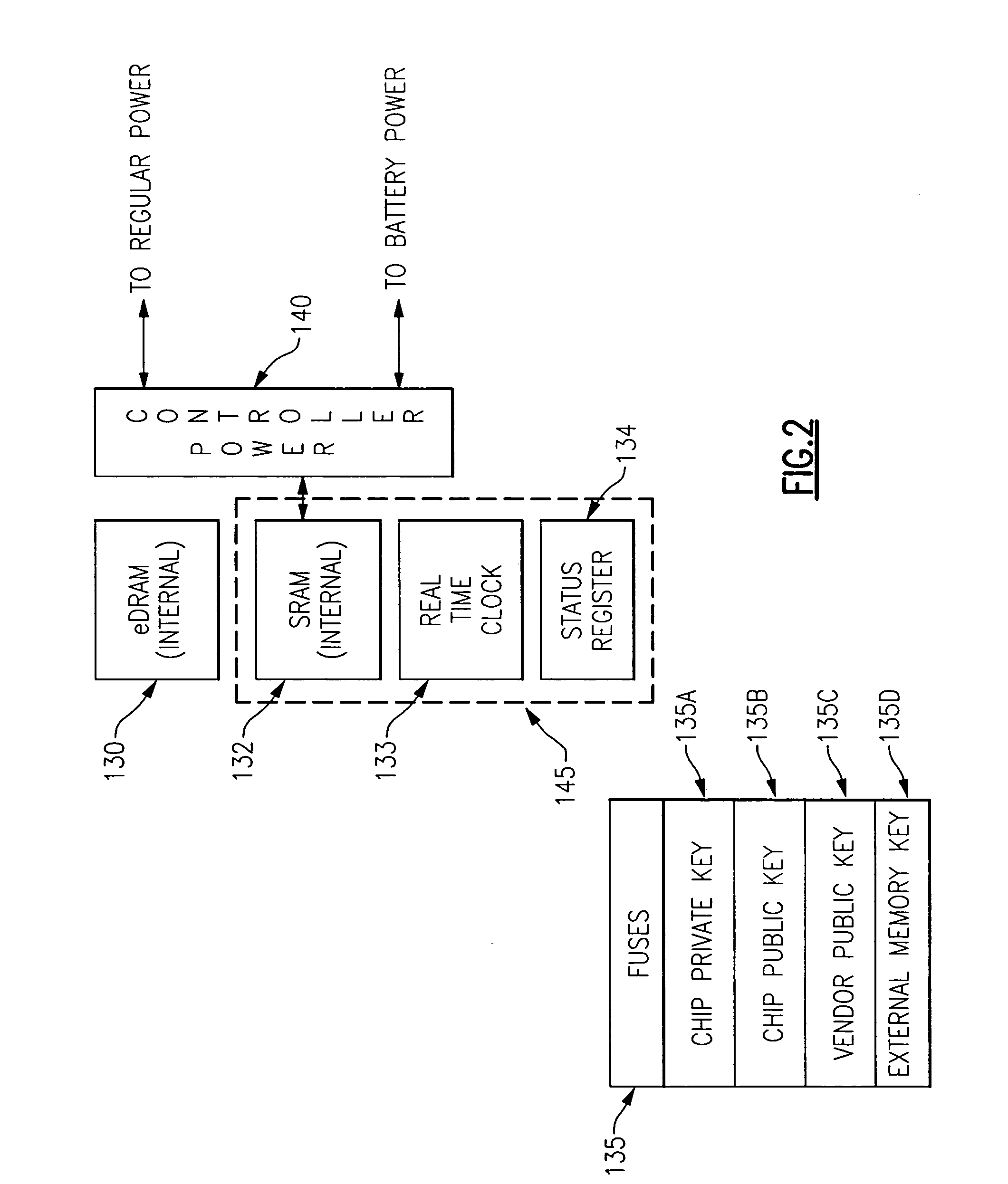
InactiveUS20060059372A1Improve process capabilityInhibit involvementUnauthorized memory use protectionHardware monitoringHard codingChip architecture
An integrated circuit chip is provided which contains one or more processors and one or more cryptographic engines. A flow control circuit having a command processor accepts requests and data via a secure external interface through which only encrypted information is passed. The flow control circuit mediates decryption of this information using cryptographic keys that are present in hard coded form on the chip. In particular the flow control circuit includes a programmable hardware portion which is configurable in a secure manner to create a flexible internal chip architecture. The chip also includes a volatile memory disposed on a voltage island on which is maintained either through a battery backup or from a fixed power source (mains). The chip is thus enabled to securely perform cryptographic operations with the processors controlling the cryptographic engines through the flow control circuit.
Owner:IBM CORP
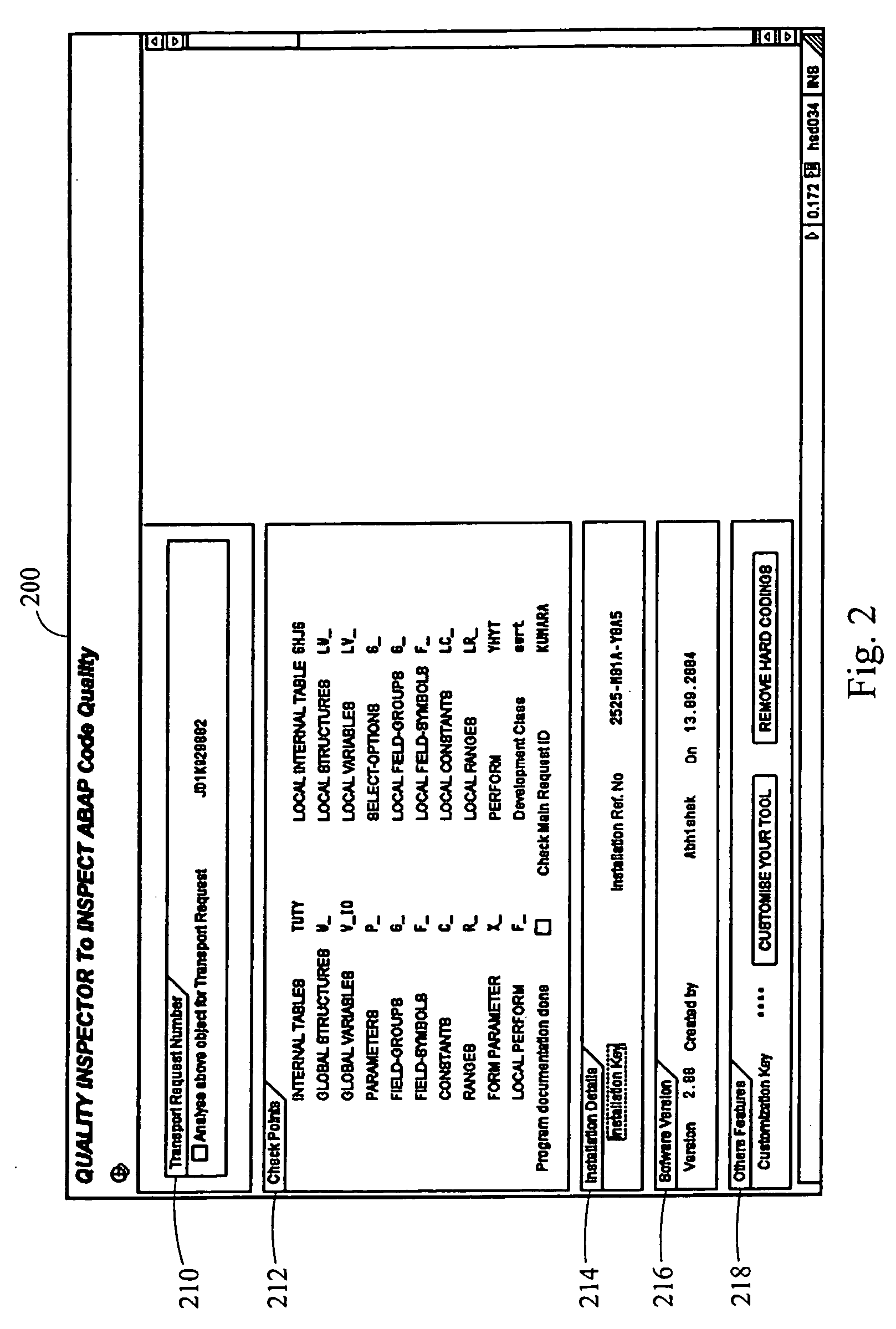
Quality inspector tool
InactiveUS20070283325A1Easy to trackEnhances writing and editingError detection/correctionCode refactoringData processing systemHard coding
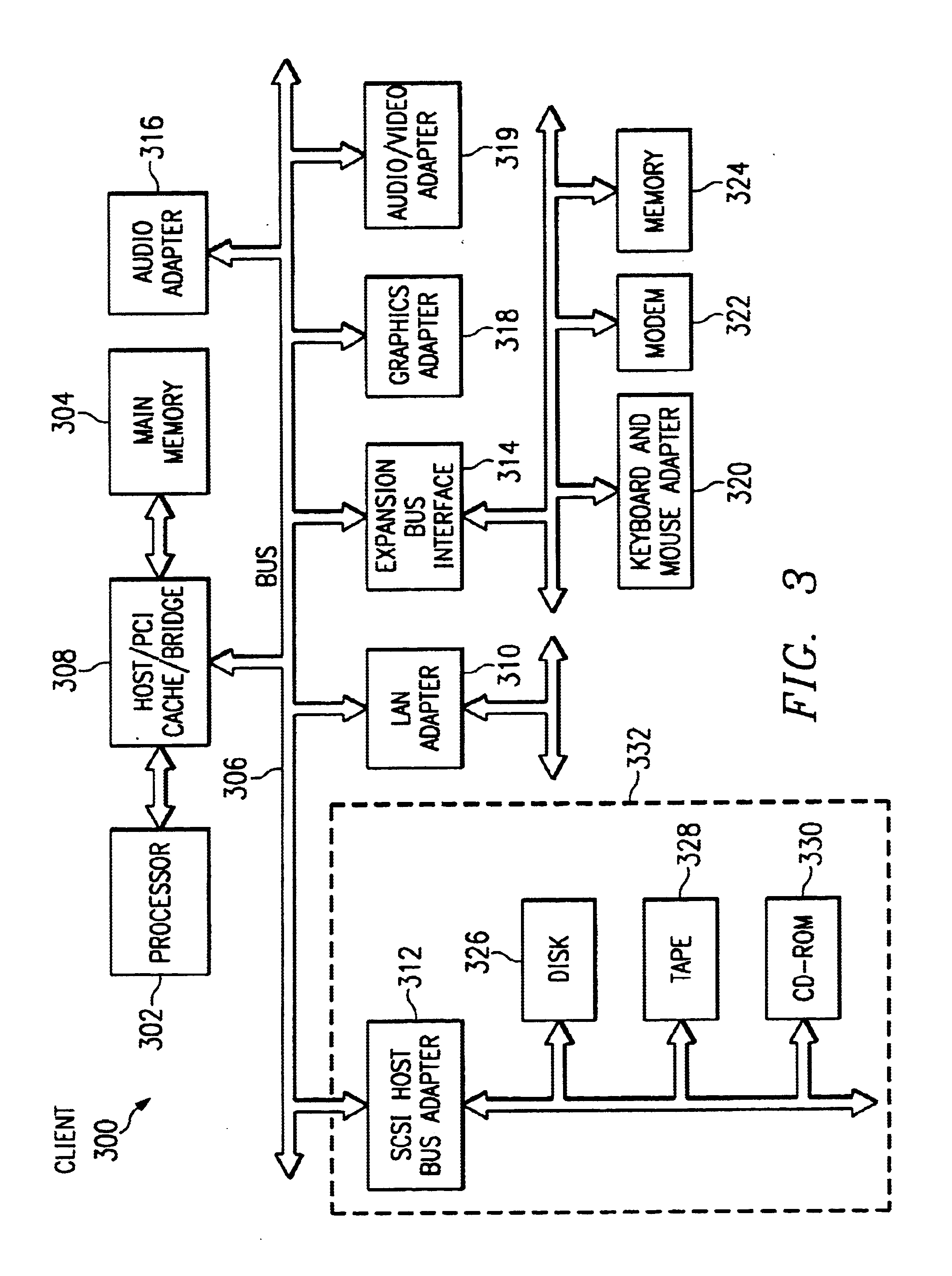
A data processing system, method, and instructions executable on a computer inspect the quality of software code. A summary report is generated that summarizes aspects of the current status of a software project. The summary report may include which portions of code have been written, which have been edited to predetermined standards, and which remain to be written. Errors in the code may be identified. Warnings associated with portions of the code may be generated, as well as suggested changes to the code. For comparison, the suggested code changes may be displayed along side of the corresponding portions of the pre-existing code that the suggested code is intended to replace. Hard coded values may be automatically identified. Text elements corresponding to each hard coded value may be automatically created. Subsequently, each hard coded value may be automatically replaced by the corresponding text element. Revisions to pre-existing code may be inspected.
Owner:ACCENTURE GLOBAL SERVICES LTD
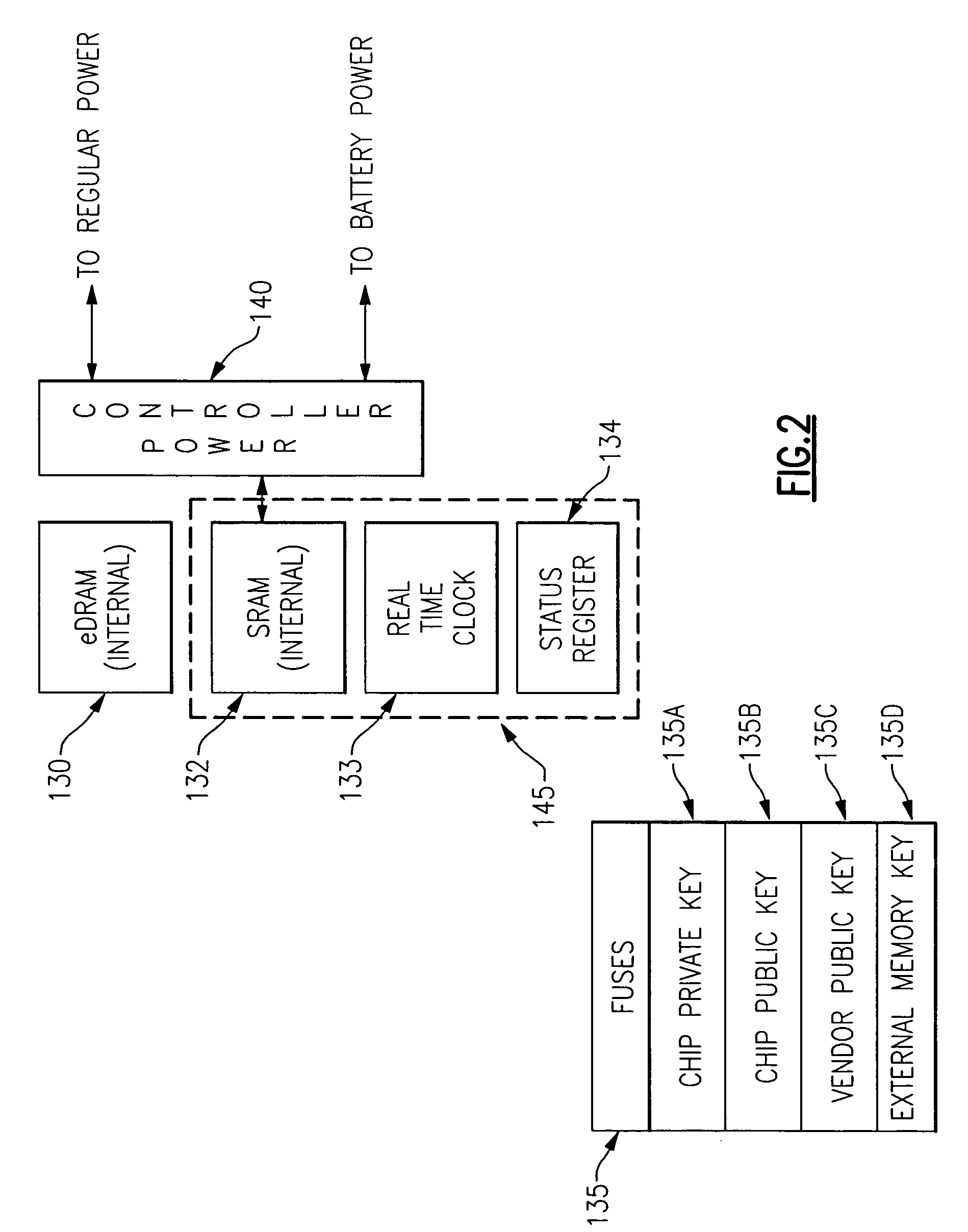
System and method for processing by distinct entities securely configurable circuit chips
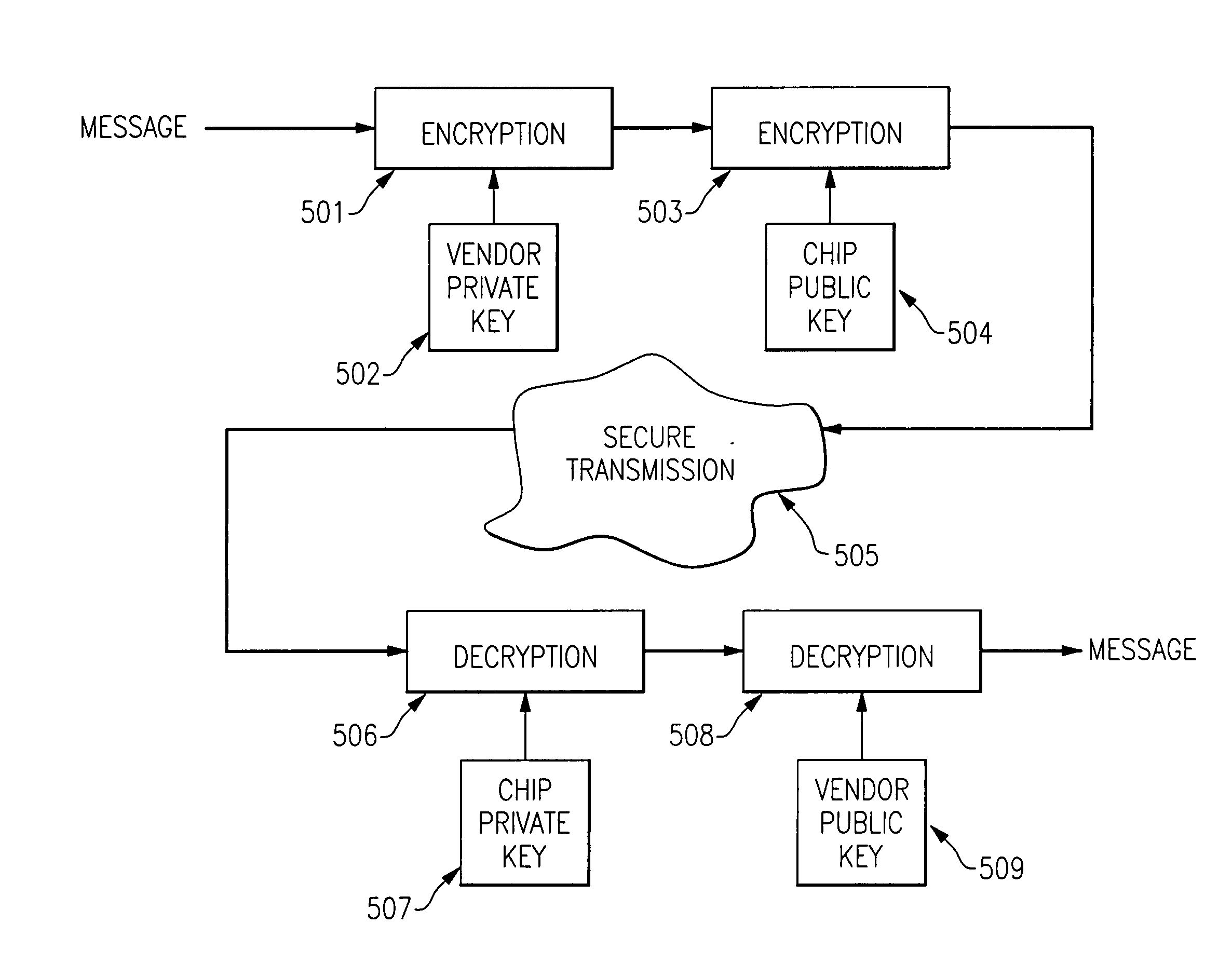
InactiveUS20060059368A1Improve process capabilityInhibit involvementUser identity/authority verificationUnauthorized memory use protectionHard codingThird party
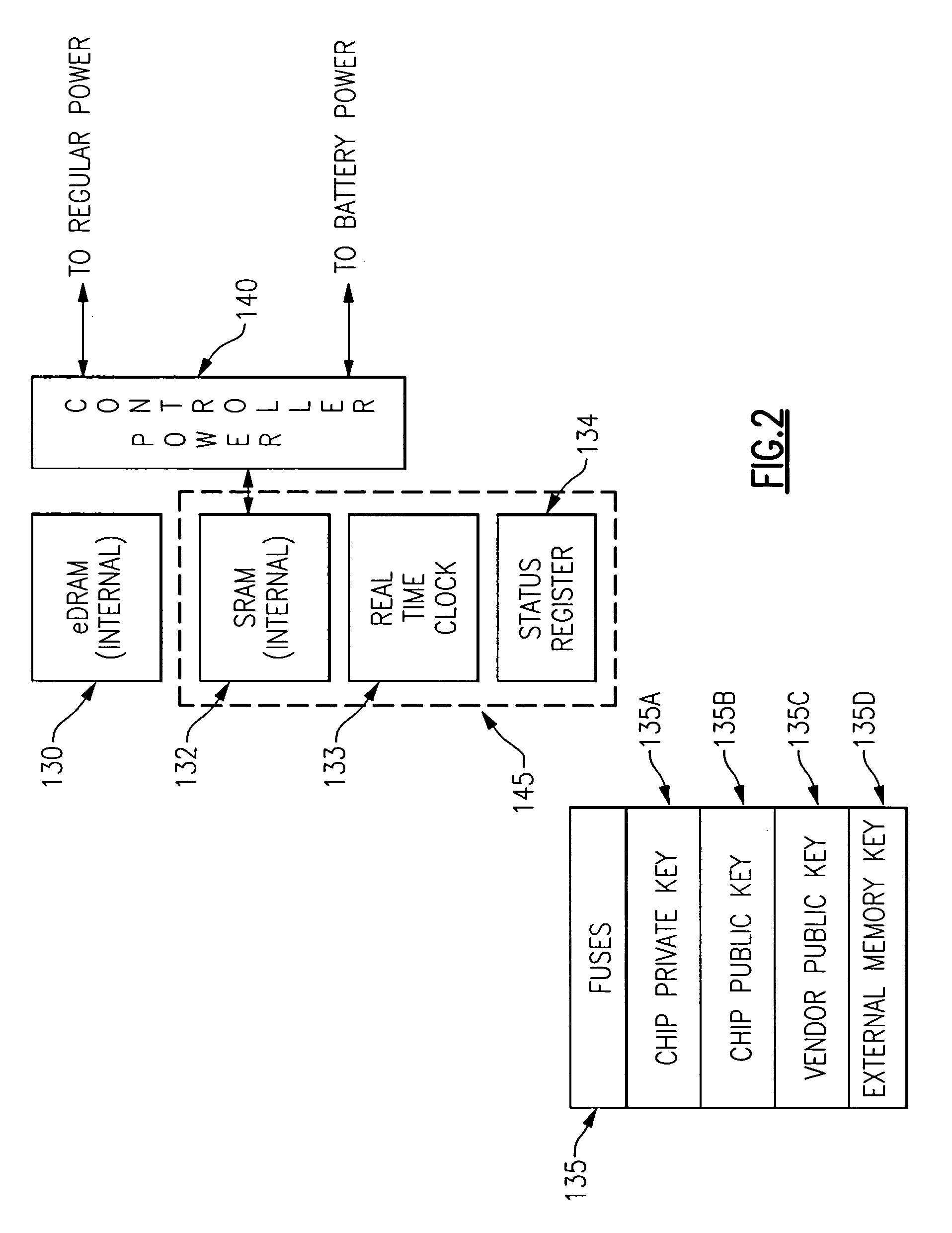
A system and method are provided in which a third party chip vendor is enabled to securely program an electronic circuit chip supplied from a chip manufacturer. The chip vendor supplies a vendor's public cryptography key to the chip manufacturer who hard codes it on the chip along with a chip private key and a chip public key. One or more cryptographic engines on the chip, which preferably has a tamper resistant / detecting boundary, are used to decrypt program instructions supplied to the chip after having been encrypted with the vendor's private key and the chip public key. The chip includes a processor and an associated memory which receives a version of the instructions decrypted with the chip private key and the vendor's public key. The chip also preferably includes programmable hardware which is also securely programmable by the downstream chip vendor. The chip, as processed by the chip vendor is shipped with a battery in place to provide power for maintaining data held in volatile memory portions of the chip.
Owner:IBM CORP
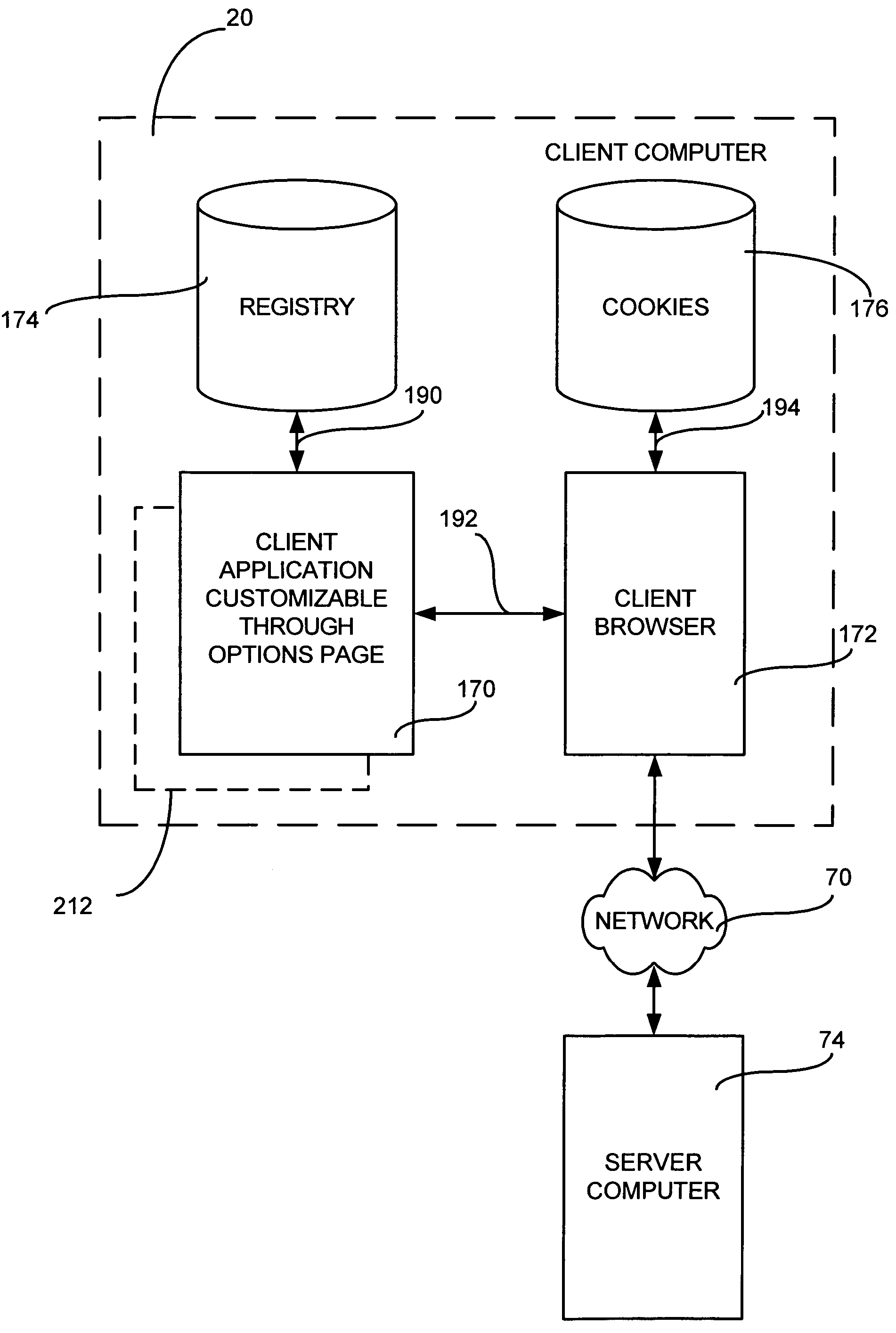
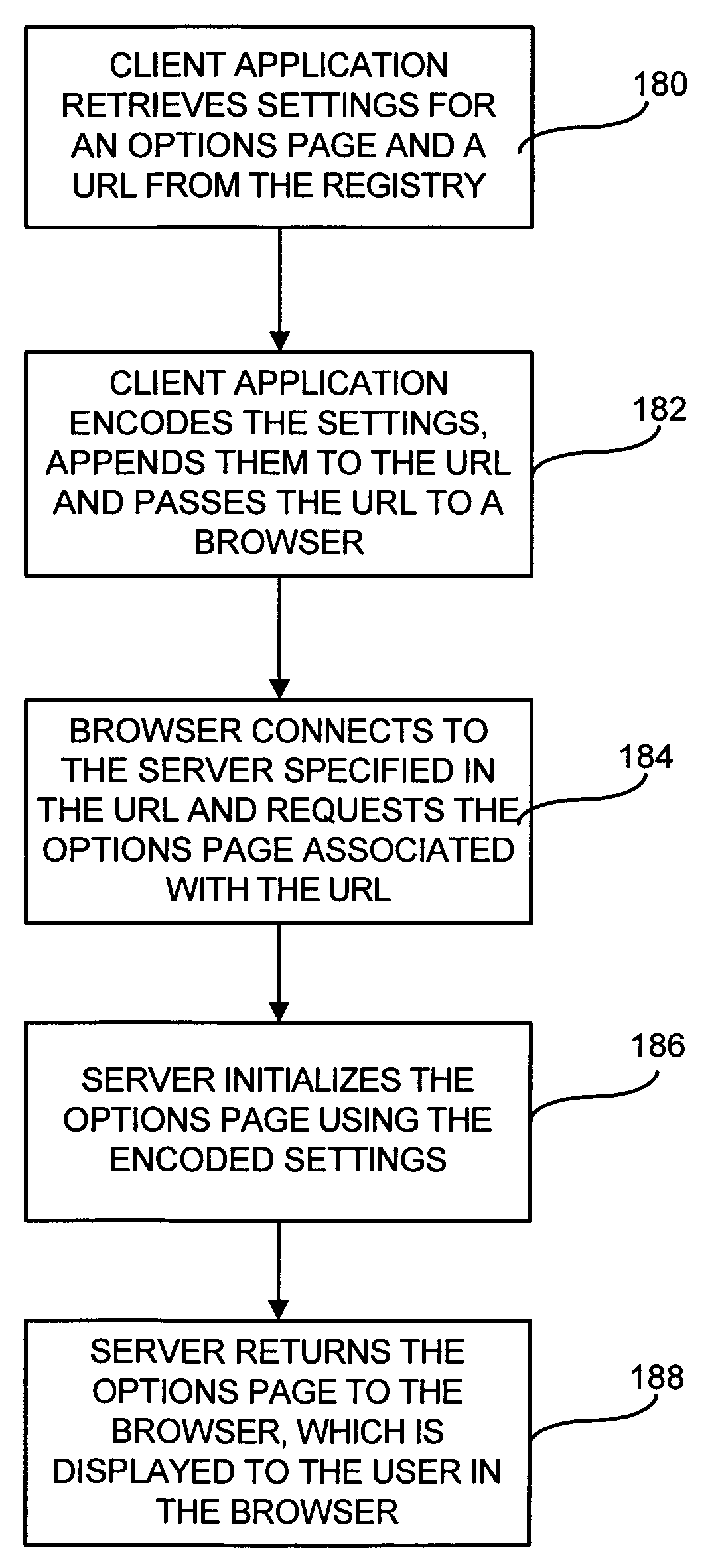
Customizing a client application using an options page stored on a server computer
InactiveUS20050010647A1Natural language data processingMultiple digital computer combinationsHard codingClient-side
A method and apparatus for displaying an options page for client application in a network environment. Instead of hard coding the options page within the client application, the options page is stored on a server computer and may be updated dynamically without modifying the client application. In one aspect, the user requests to view the options page using menu commands generated by the client application. In response to the user request, the client application launches a browser, if needed, and passes the current settings for the options page to the browser along with an address pointing to the location of the options page on a server computer. The browser connects to the server computer specified in the URL, requests the page associated with the address, and passes the user settings to the server computer. The server computer generates a current version of the options page, initializes the options page by applying the user settings to the options page, and downloads the options page to the browser for display. In another aspect, the user makes changes to the options page in the browser to customize the client application. The browser sends the changes to the server and the server returns the changes to the browser as a special file type. The browser uses a helper function to handle the special file type and launches an application that saves the user settings on the client computer.
Owner:NBCUNIVERSAL
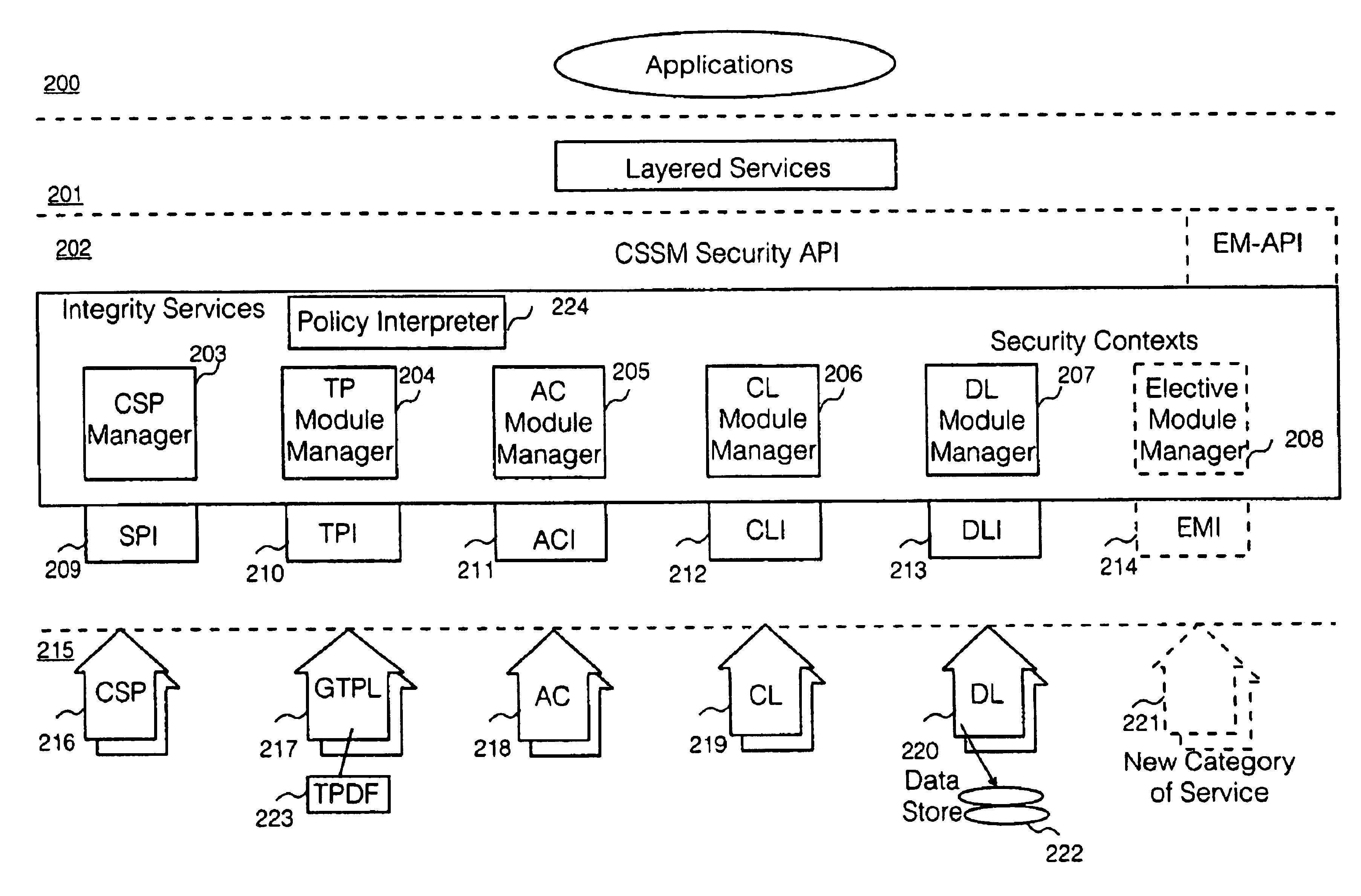
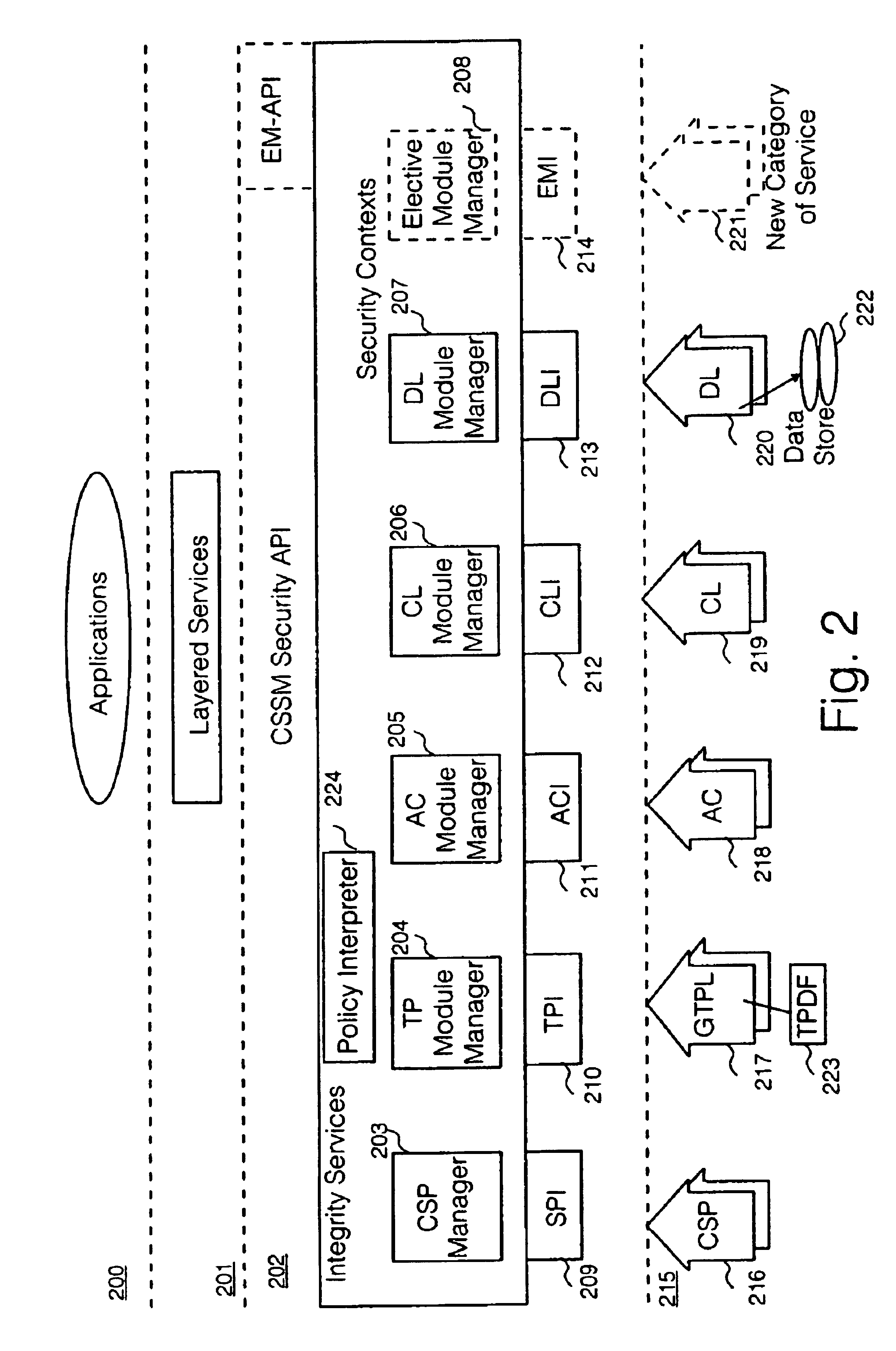
Security policy applied to common data security architecture
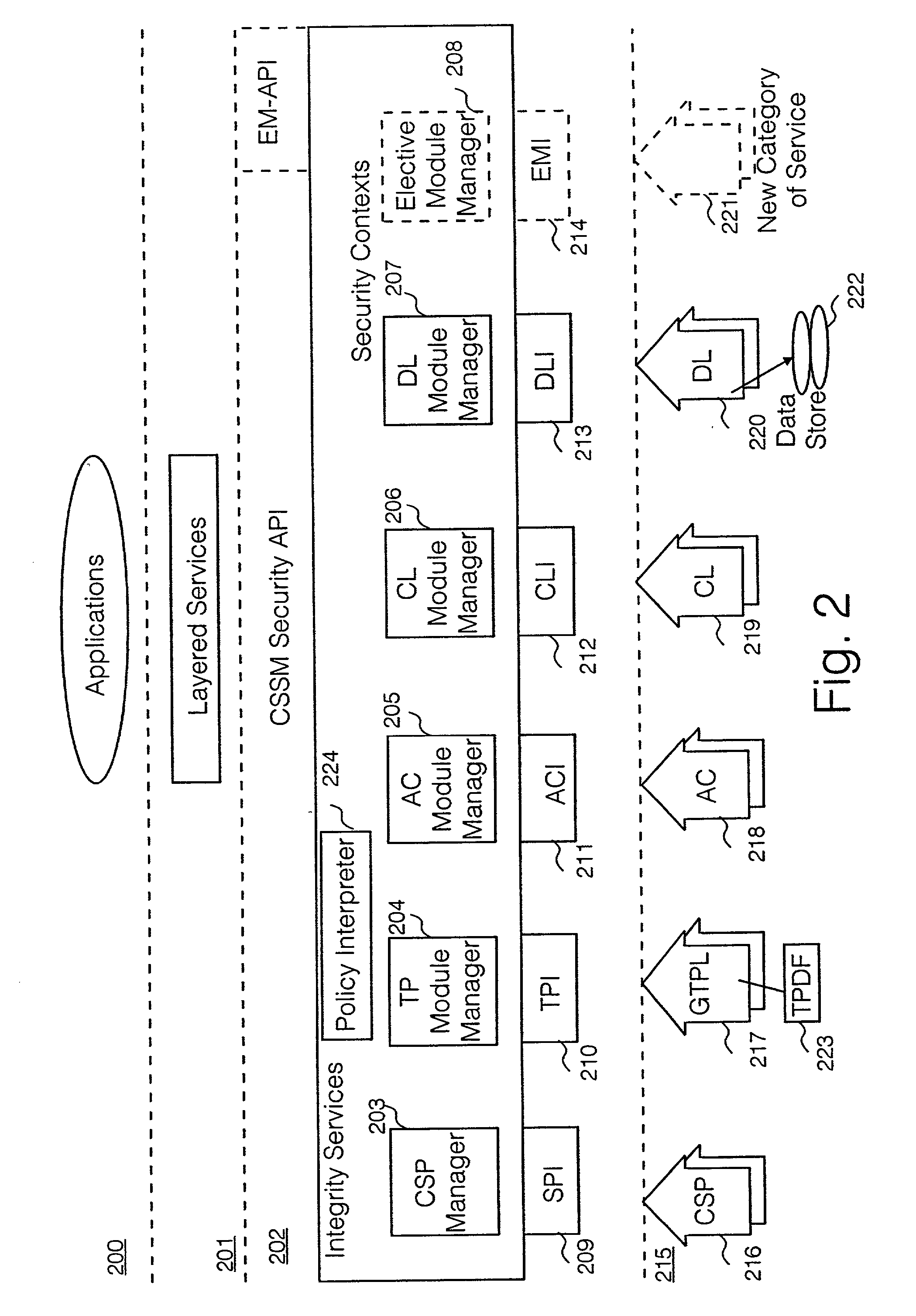
InactiveUS20010018746A1Digital data processing detailsUser identity/authority verificationHard codingSemantics
An improved architecture is provided, based upon the prior art common data security architecture, with the modification of adding in a generic trust policy library (217) at an add-in security modules layer (215) and a policy interpreter (224) at a common security services manager layer (202), so that individual users may provide sets of trust policies in the form of a trust policy description file (223), which uses a generic policy description language provided by the architecture. The architecture provides a generic method of incorporating trust policies into a computing platform in a manner which avoids a prior art problem of the semantics of trust policies which are hard-coded in prior art trust policy modules (117). The architecture also improves management flexibility. In the present disclosure, a generic policy description language is provided, which enables different users to define the semantics of a plurality of trust policies.
Owner:HEWLETT PACKARD DEV CO LP
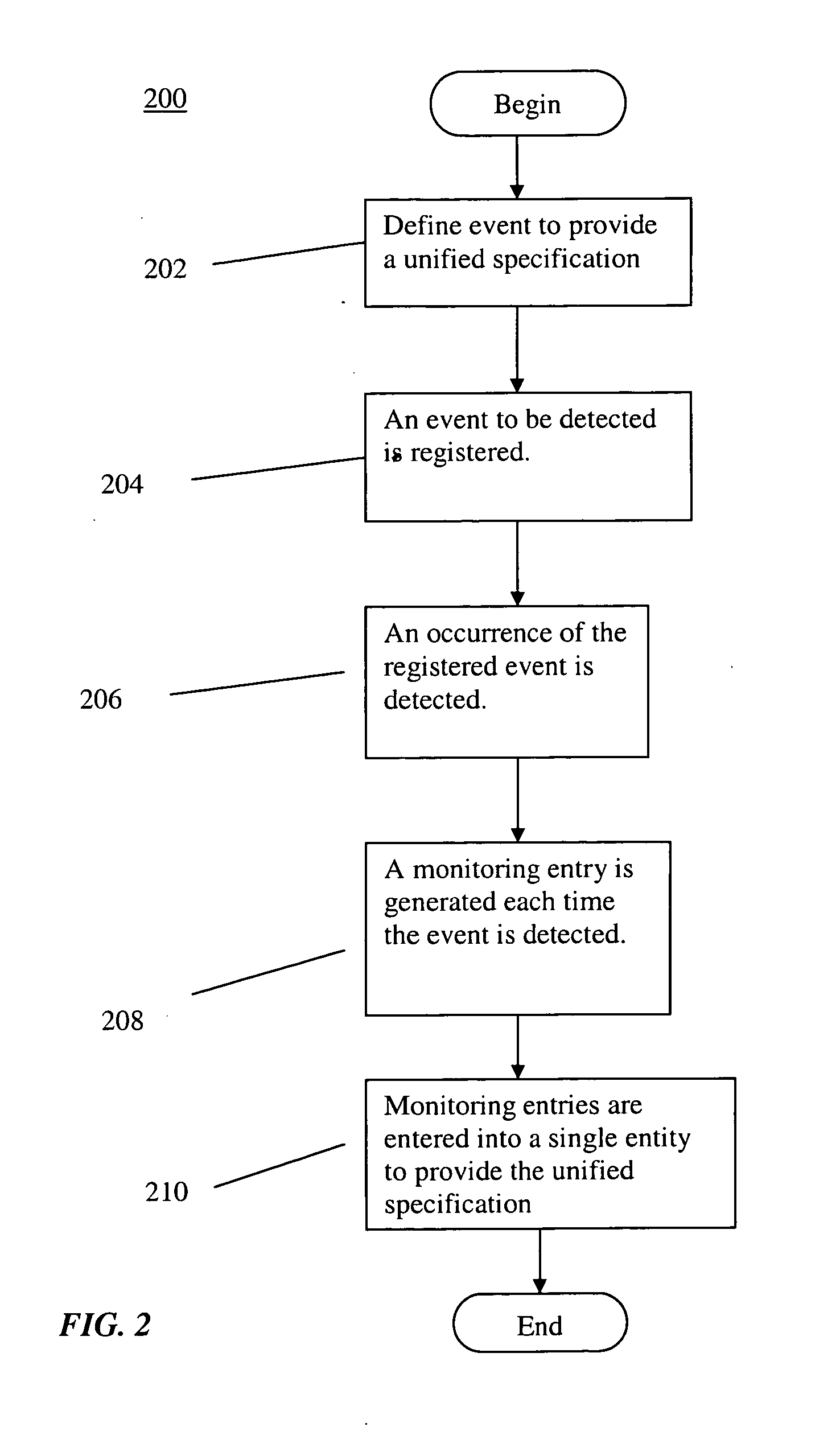
System and method for vertical integrated performance and environment monitoring
A system and method includes steps, or acts, of: defining one or more events to provide a unified specification; registering one or more events to be detected; detecting an occurrence of at least one of the registered event or events; generating a monitoring entry each time one of the registered events is detected; and entering each of the monitoring entries generated into a single logical entity. The method can also be implemented as machine executable instructions executed by a programmable information processing system or as hard coded logic in a specialized computing apparatus such as an application-specific integrated circuit (ASIC).
Owner:IBM CORP
Security policy applied to common data security architecture
InactiveUS6941471B2Digital data processing detailsUnauthorized memory use protectionHard codingSemantics
An improved architecture is provided, based upon the prior art common data security architecture, with the modification of adding in a generic trust policy library (217) at an add-in security modules layer (215) and a policy interpreter (224) at a common security services manager layer (202), so that individual users may provide sets of trust policies in the form of a trust policy description file (223), which uses a generic policy description language provided by the architecture. The architecture provides a generic method of incorporating trust policies into a computing platform in a manner which avoids a prior art problem of the semantics of trust policies which are hard-coded in prior art trust policy modules (117). The architecture also improves management flexibility. In the present disclosure, a generic policy description language is provided, which enables different users to define the semantics of a plurality of trust policies.
Owner:HEWLETT PACKARD DEV CO LP
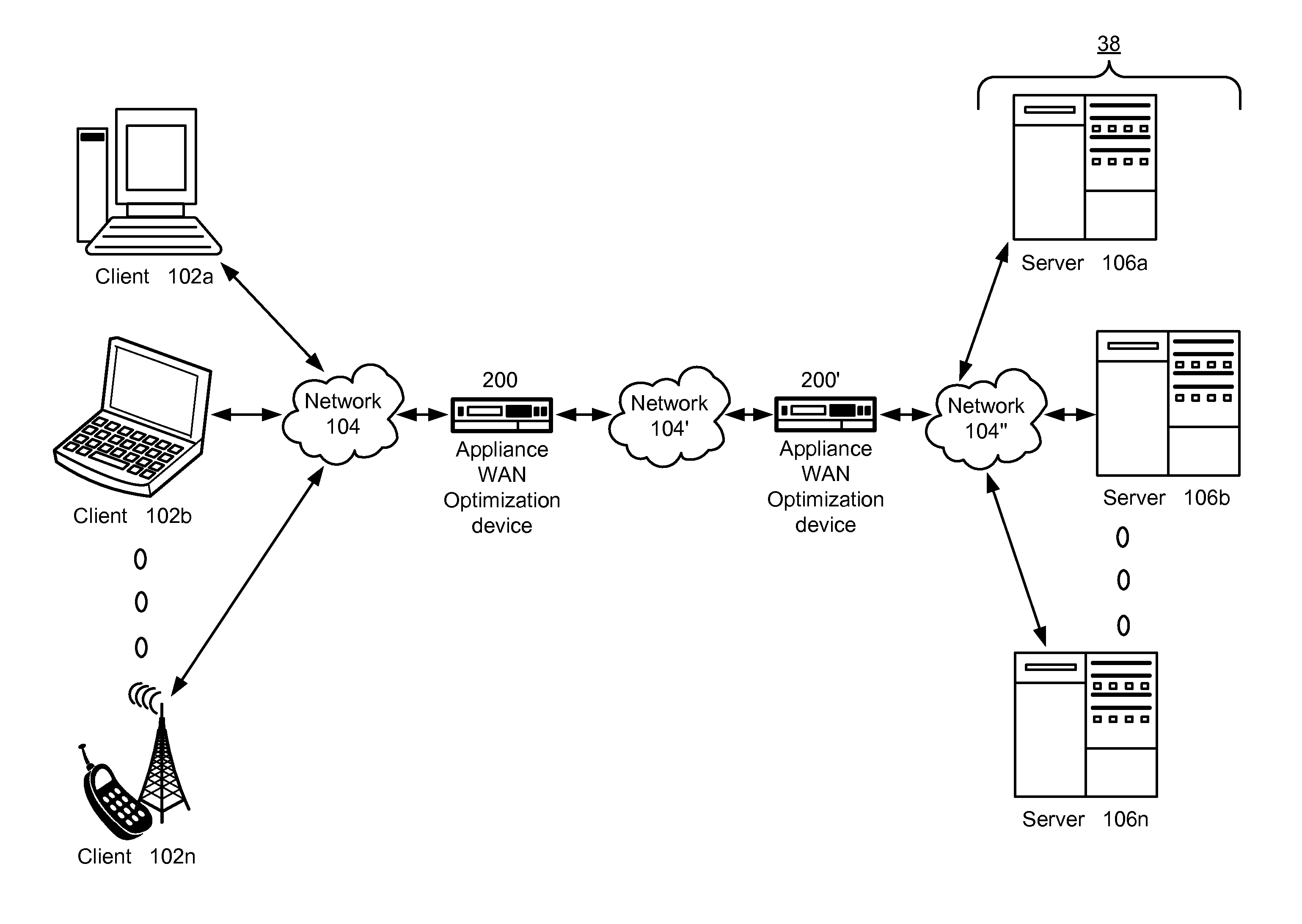
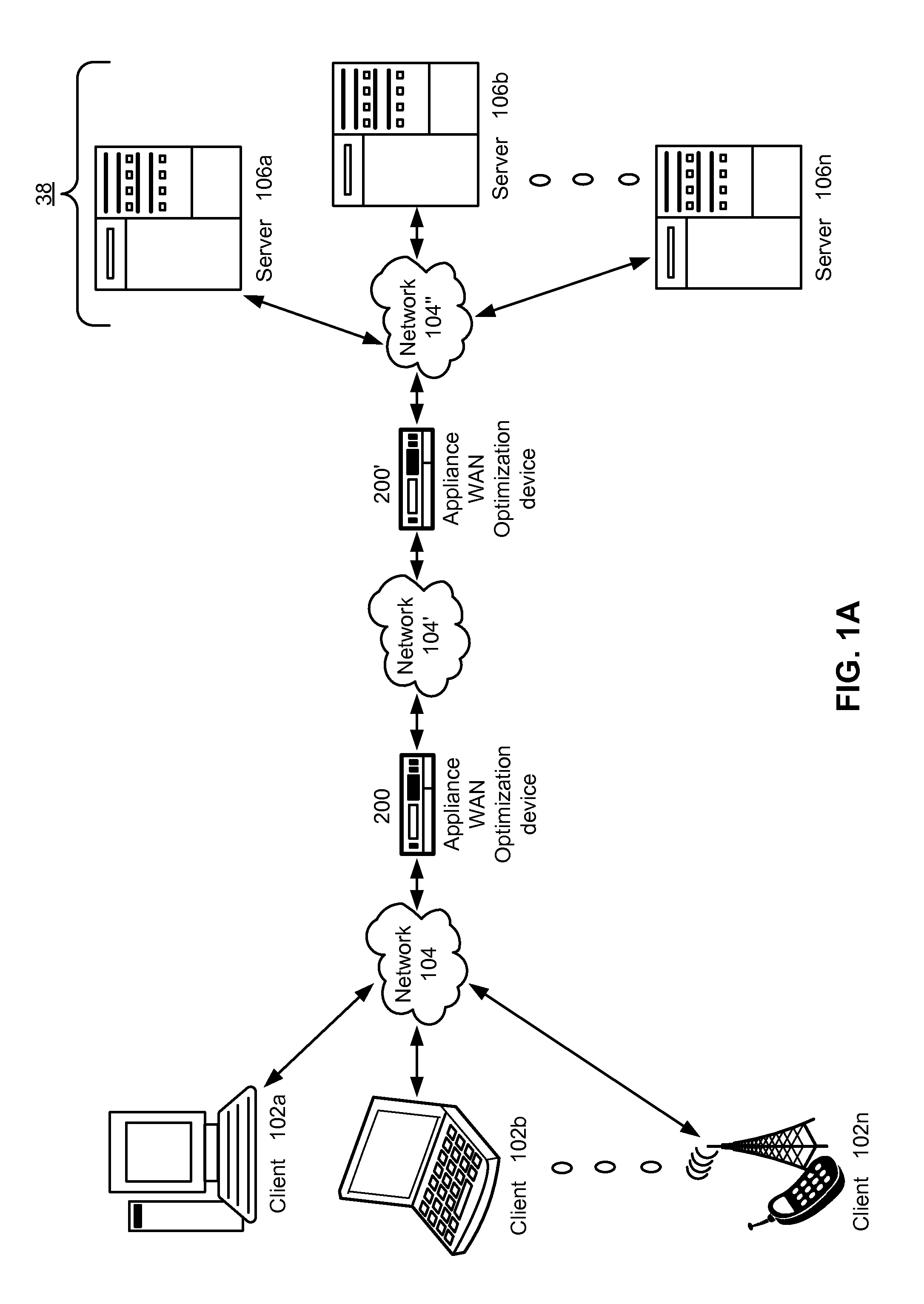
Prioritizing highly compressed traffic to provide a predetermined quality of service
ActiveUS20130094356A1Easy transferReduce the amount of memoryError preventionFrequency-division multiplex detailsHard codingQuality of service
A network optimization engine can be used to optimize the transmission of network traffic by employing means to prioritize highly compressed network traffic over other network traffic. The network optimization engine accomplishes network traffic optimization by calculating a compression ratio for received data packets and determining whether the calculated compression ratios exceed a compression ratio threshold. The predetermined compression ratio threshold can be a hard coded value or an empirically determined compression ratio threshold that is calculated using a sample of the received network packets. Network packets having a compression ratio that exceeds the compression ratio threshold are classified as highly compressed network traffic and transmitted according to a transmission scheme that is different than a transmission scheme used to transmit non-highly compressed network traffic.
Owner:CITRIX SYST INC
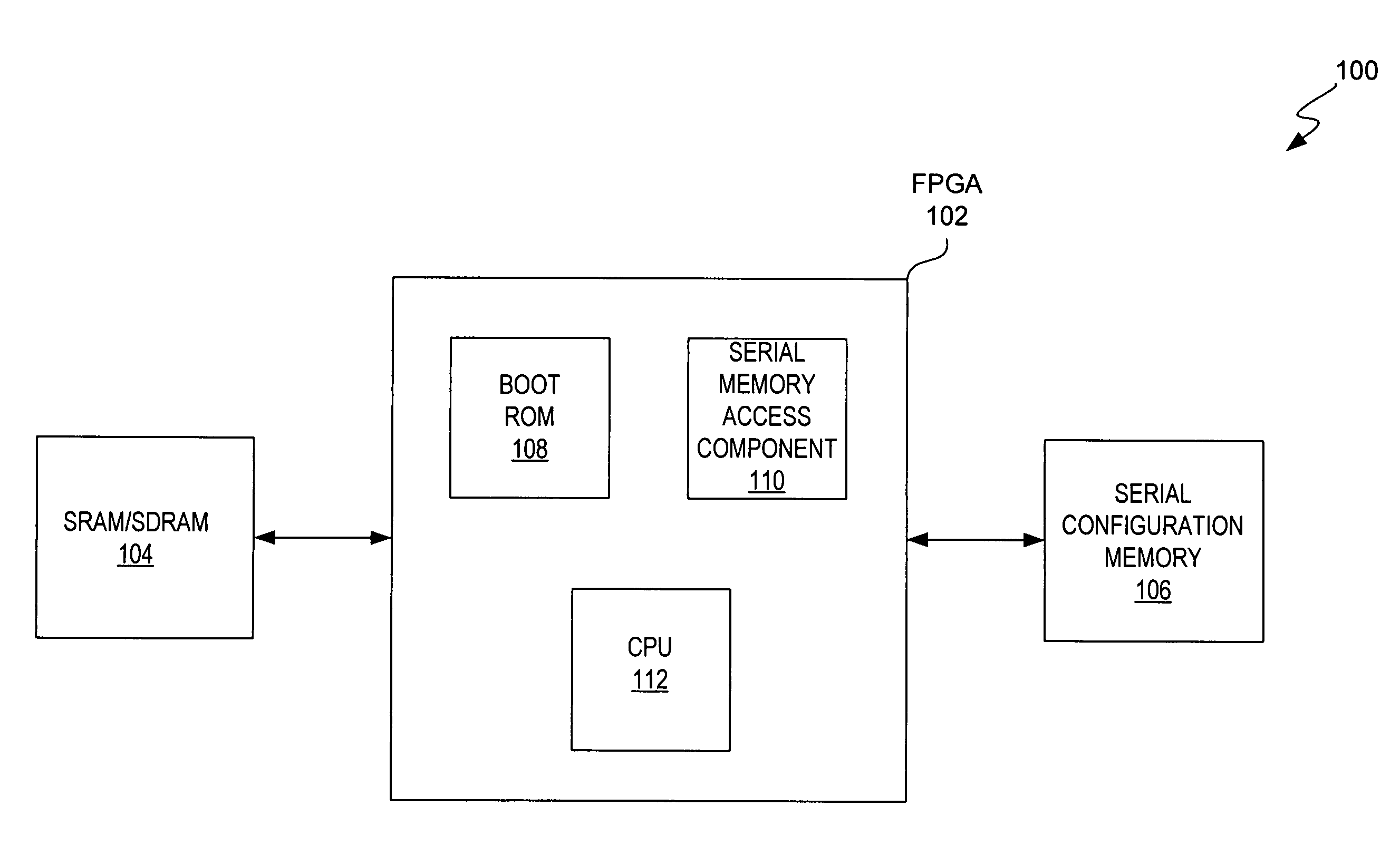
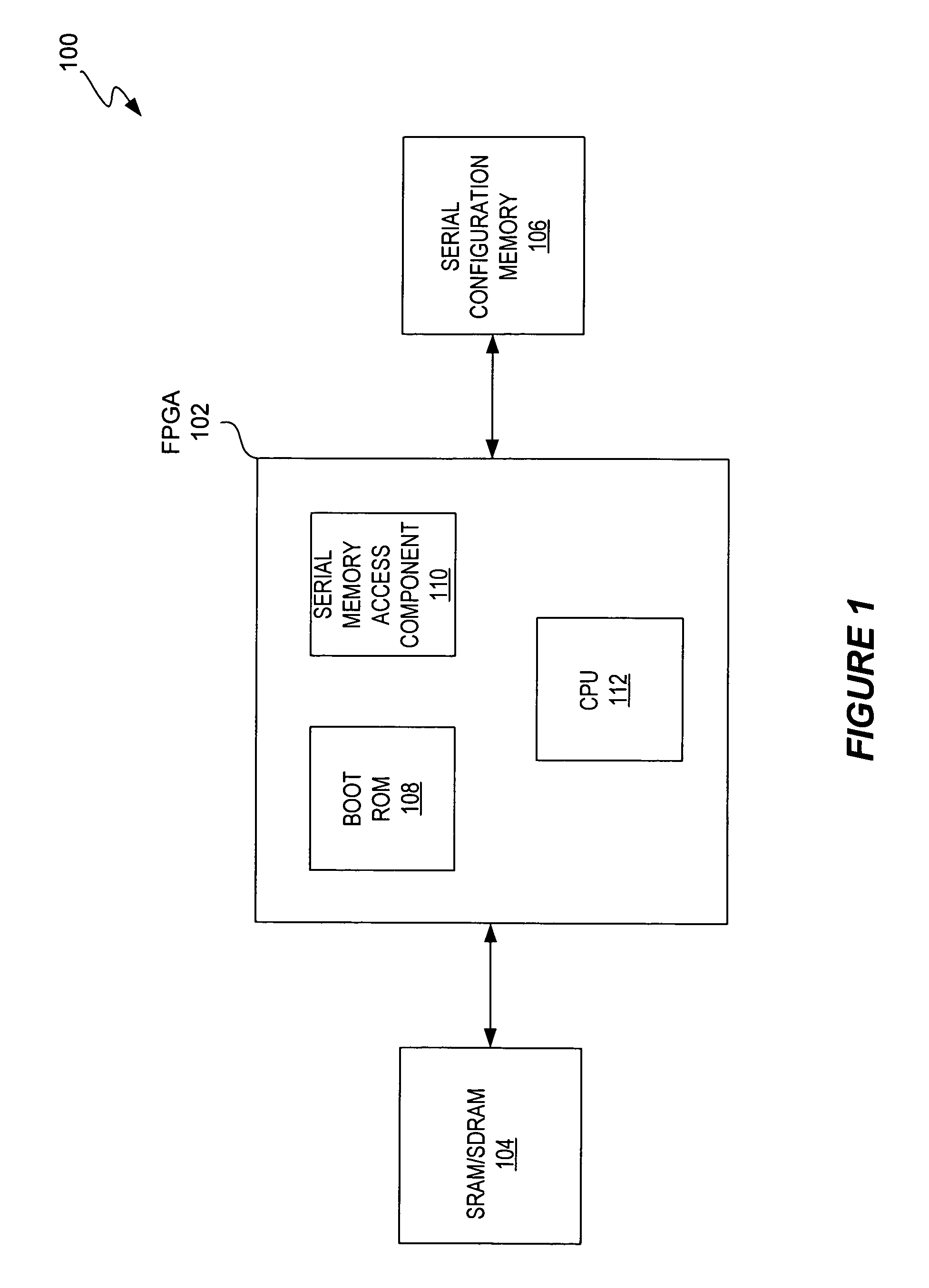
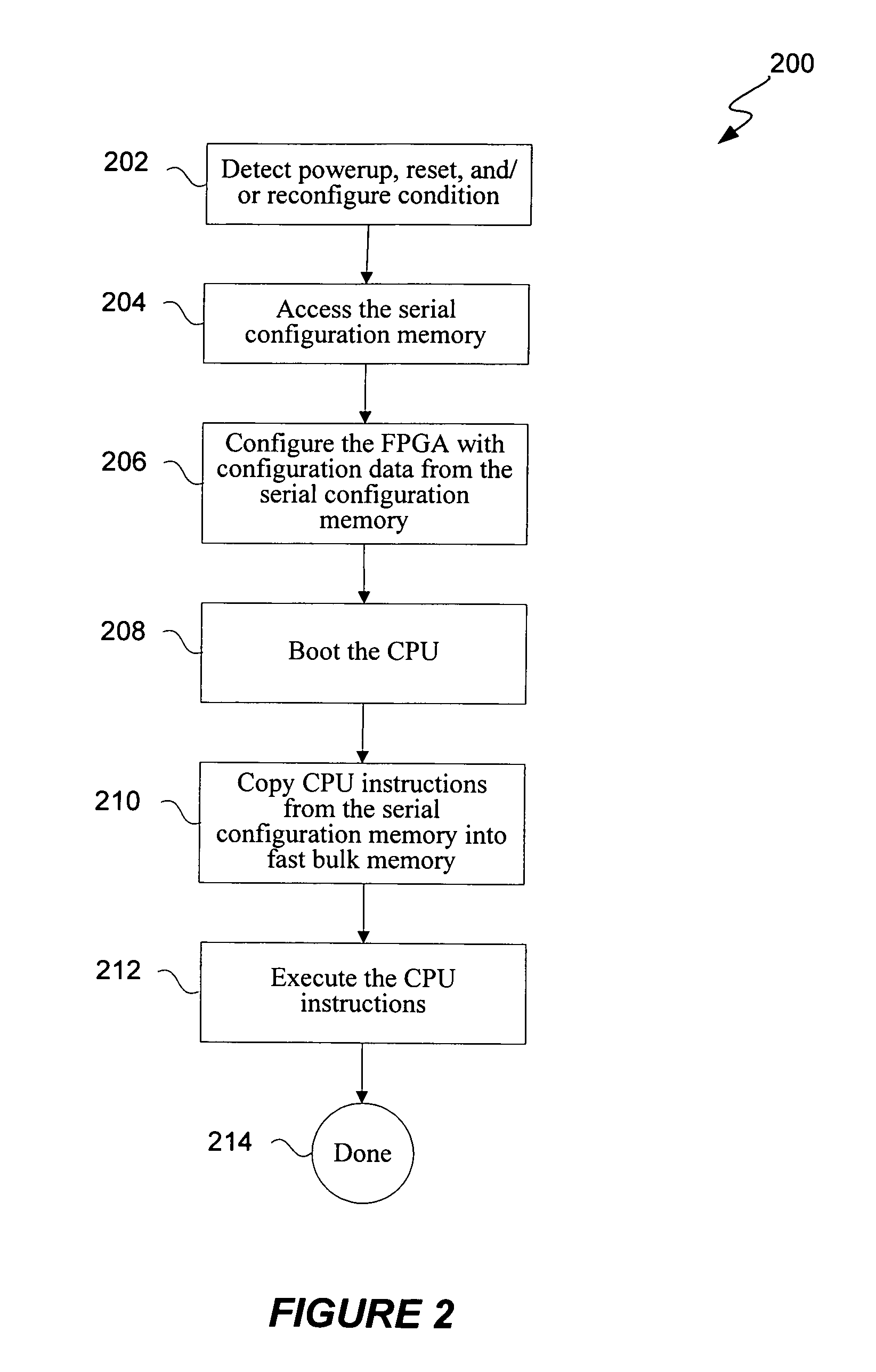
Booting mechanism for FPGA-based embedded system
ActiveUS7822958B1Cost-effective and efficient solutionSolid-state devicesDigital computer detailsMass storageHard coding
According to various embodiments of the present invention, a programmable device assembly includes an FPGA coupled to a nonvolatile serial configuration memory (e.g., serial flash memory) and a volatile fast bulk memory (e.g., SRAM or SDRAM). The nonvolatile serial configuration memory contains both the FPGA configuration data and CPU instructions. When a predetermined condition occurs, a serial memory access component that is hard coded on the FPGA automatically reads the configuration data from the nonvolatile serial configuration memory. The configuration data is used to configure the FPGA with various components, including a CPU, a boot ROM with code for a boot copier, and a bus structure. When the CPU boots, code for the boot copier is executed so that the CPU instructions are copied from the nonvolatile serial configuration memory to the volatile fast bulk memory. The CPU then executes the CPU instructions stored in the volatile fast bulk memory.
Owner:TAHOE RES LTD
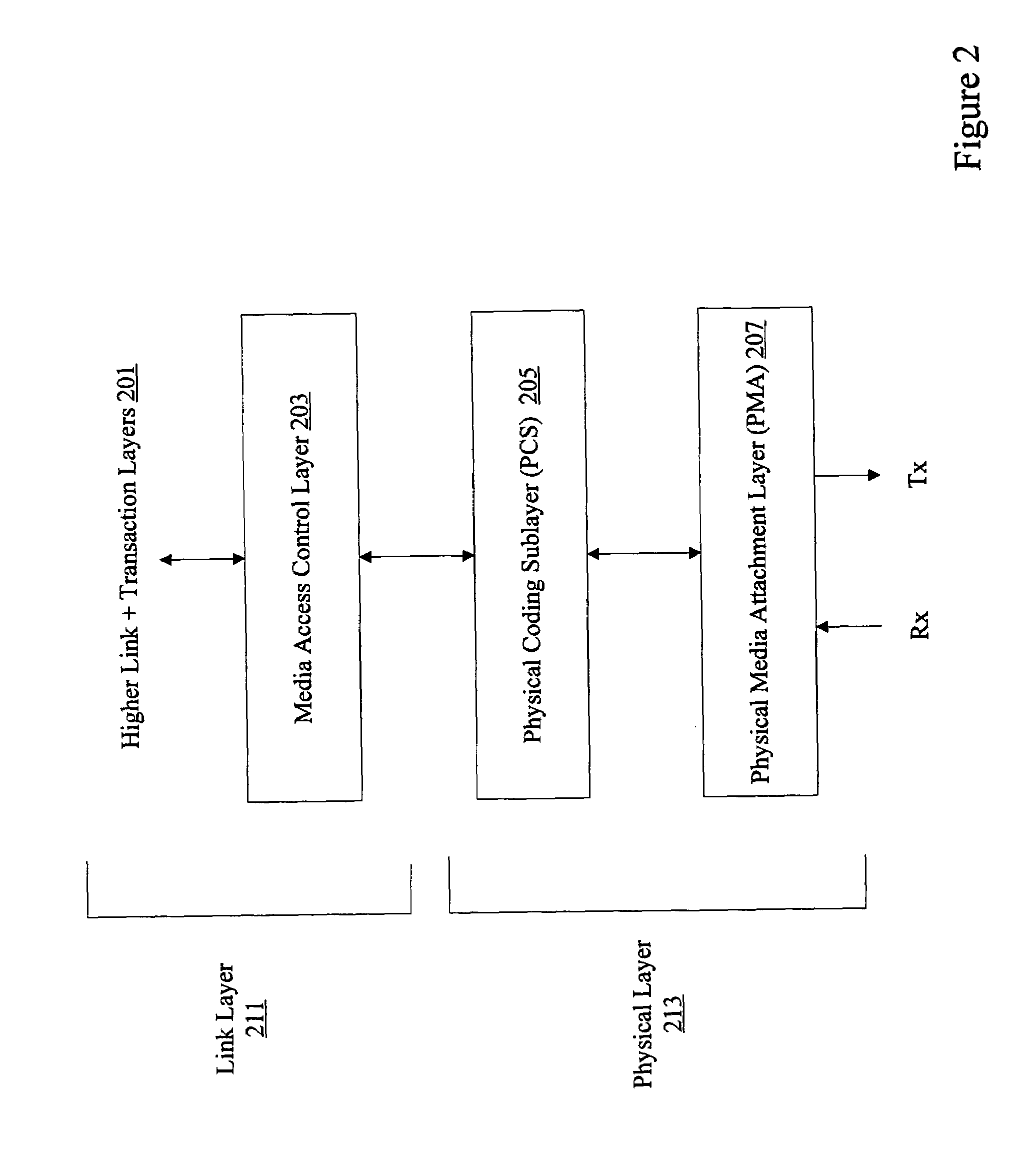
Implementation of PCI express
Methods and apparatus are provided for providing PCI Express support. A device includes a hard-coded transceiver configured to support protocols such as Fibre Channel and the 10 Gigabit Attachment Unit Interface (XAUI), but the transceiver does not fully support PCI Express. Interface circuitry is configured to supplement or replace hard-coded transceiver components to provide PCI Express support. Interface circuitry allows PCI Express cores to operate with the transceiver that does not fully support PCI Express.
Owner:ALTERA CORP
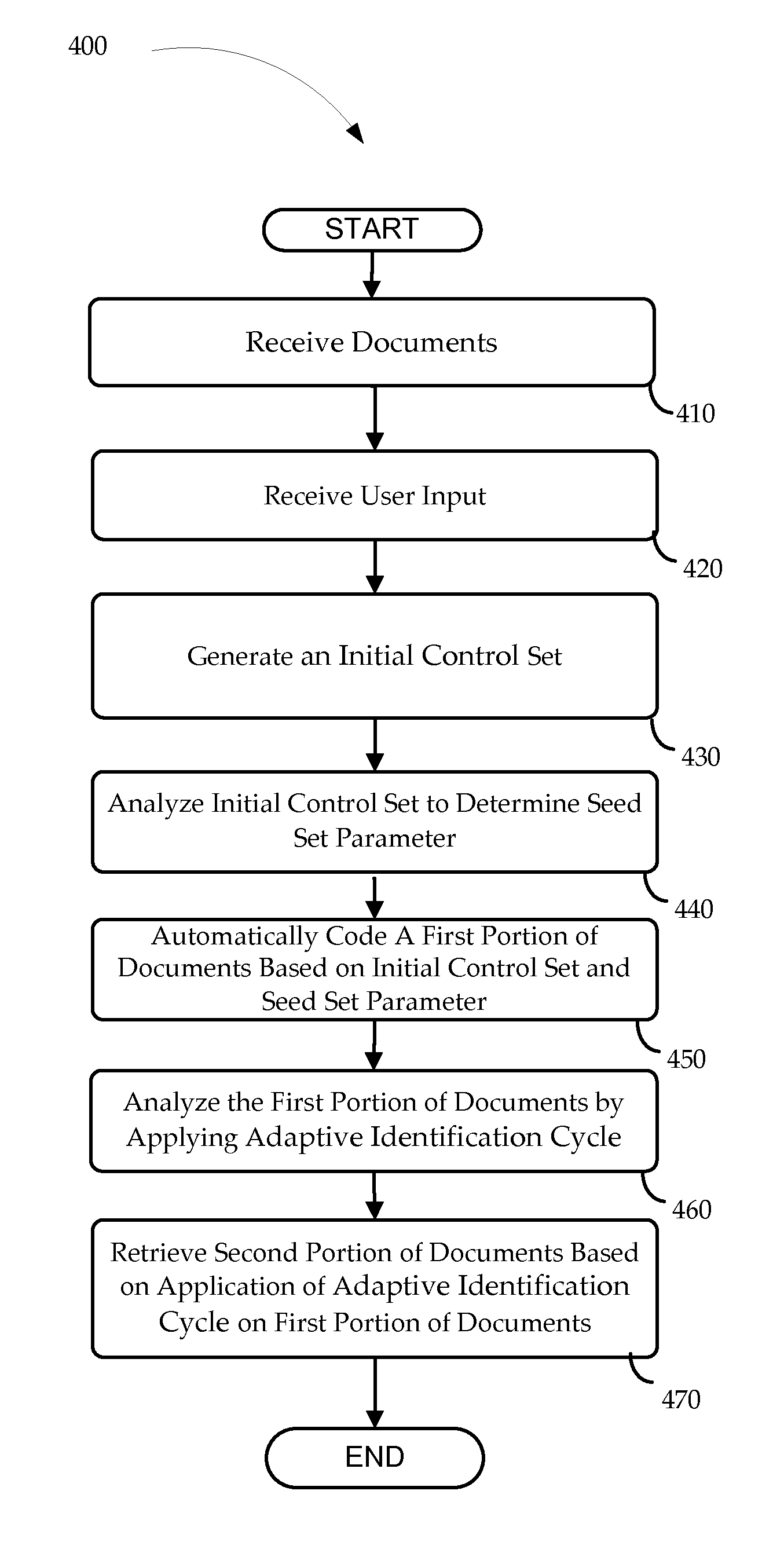
Systems and methods for predictive coding
ActiveUS7933859B1Improve accuracyQuality improvementInput/output for user-computer interactionKernel methodsHard codingControl set
Systems and methods for analyzing documents are provided herein. A plurality of documents and user input are received via a computing device. The user input includes hard coding of a subset of the plurality of documents, based on an identified subject or category. Instructions stored in memory are executed by a processor to generate an initial control set, analyze the initial control set to determine at least one seed set parameter, automatically code a first portion of the plurality of documents based on the initial control set and the seed set parameter associated with the identified subject or category, analyze the first portion of the plurality of documents by applying an adaptive identification cycle, and retrieve a second portion of the plurality of documents based on a result of the application of the adaptive identification cycle test on the first portion of the plurality of documents.
Owner:OPEN TEXT HLDG INC
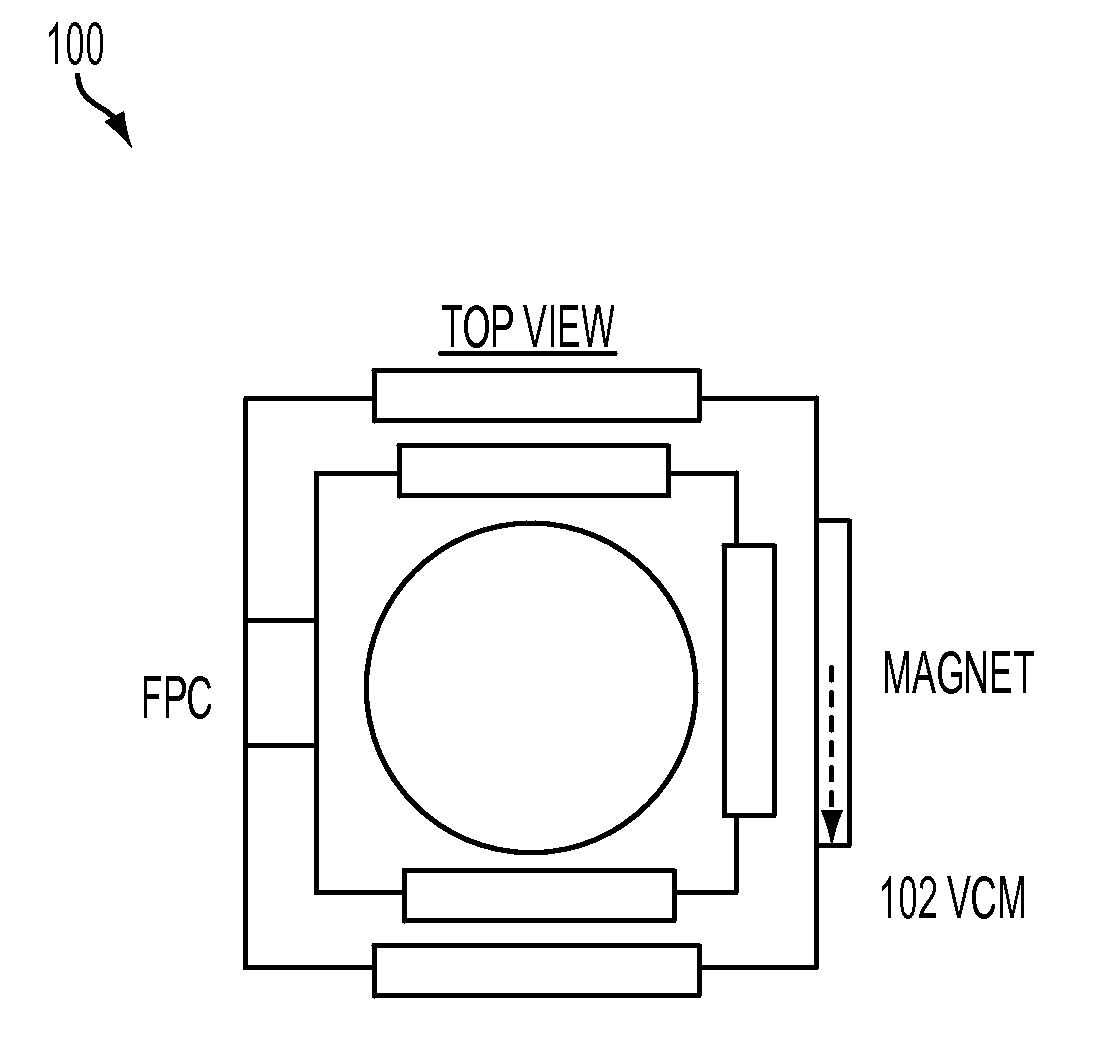
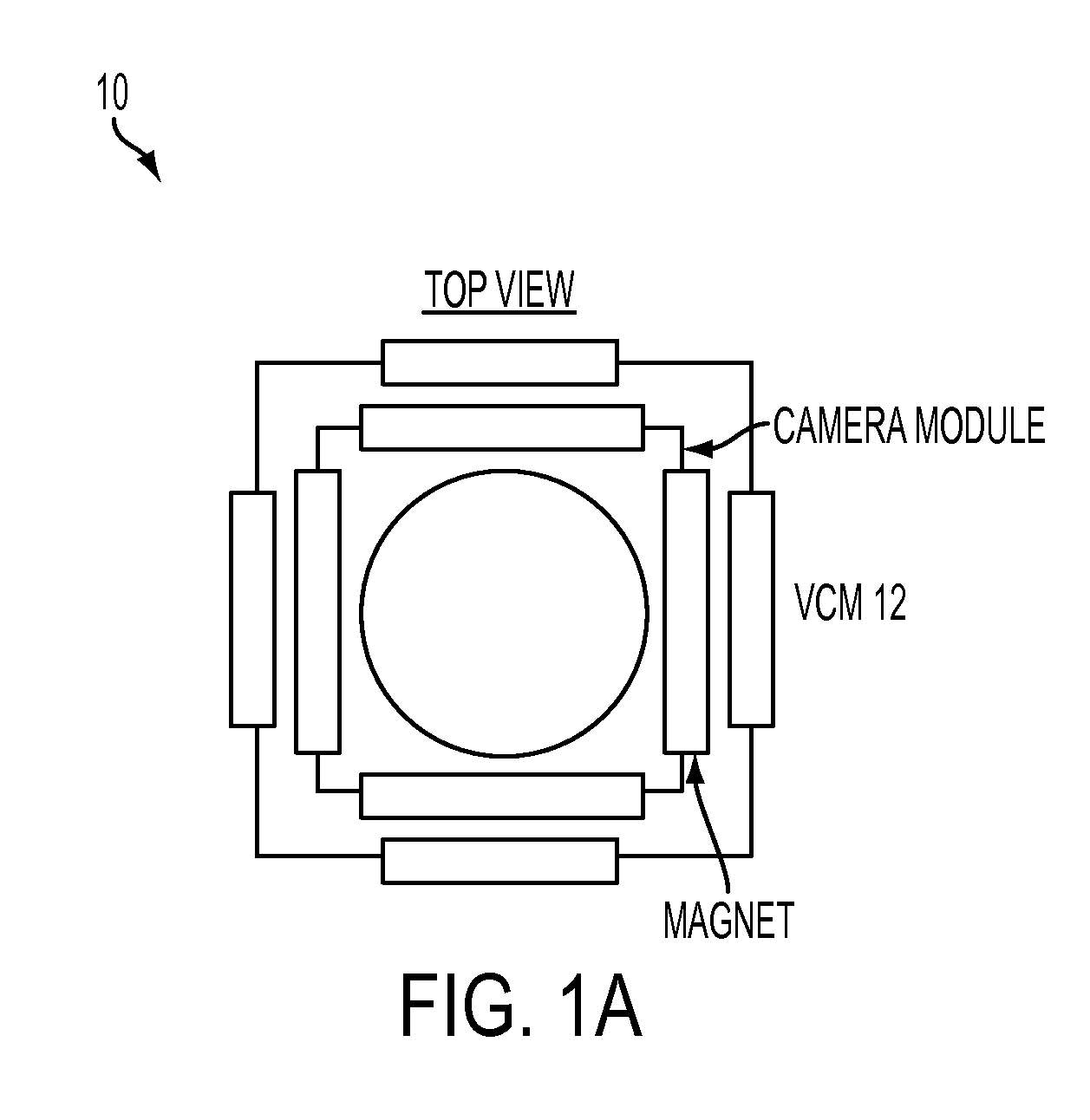
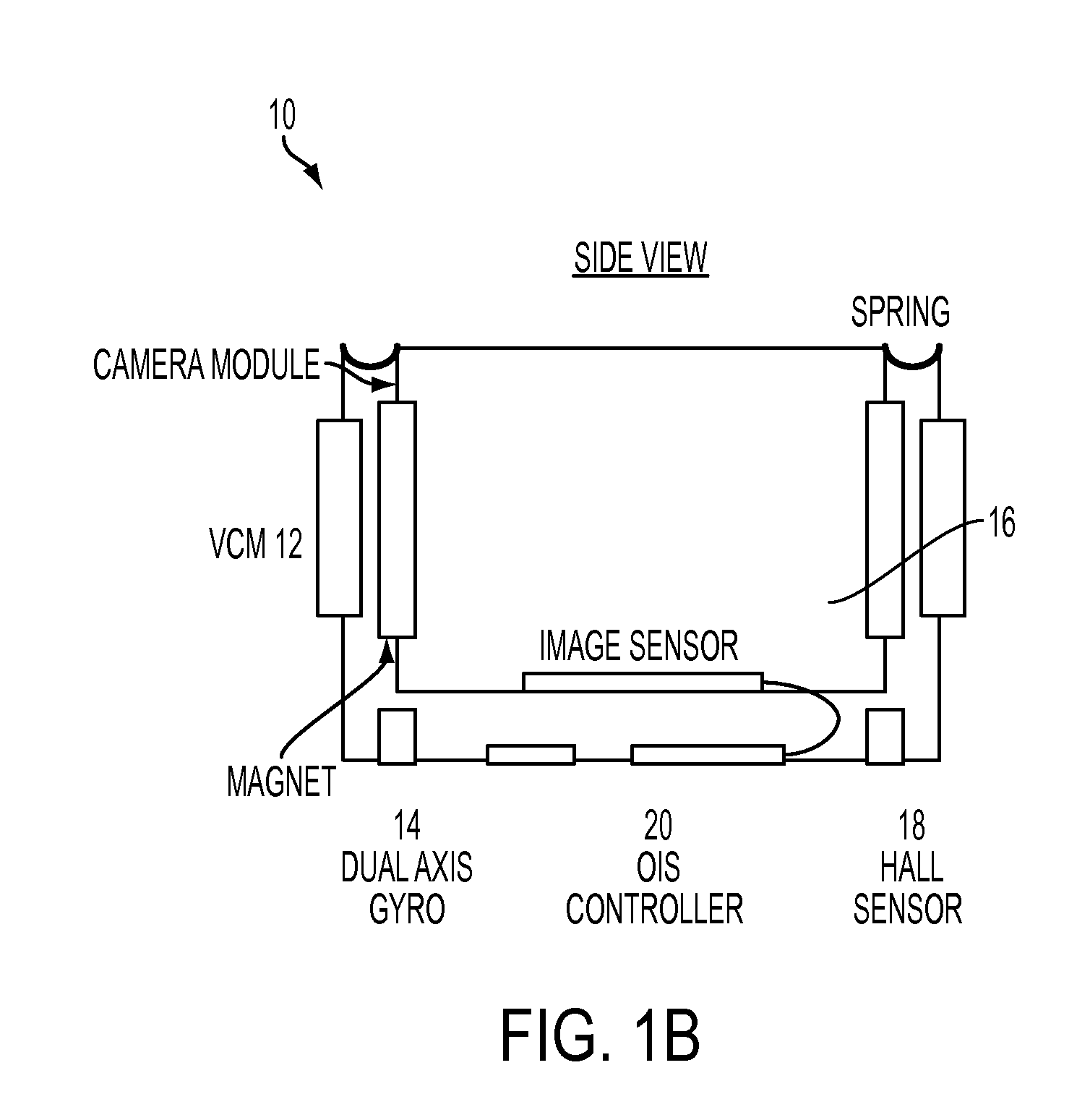
Optical image stabilization in a digital still camera or handset
An optical image stabilization system for a camera module is disclosed. The stabilization system comprises a voice coil motor (VCM), at least one digital gyroscope for receiving signals from the VCM, and an angular velocity sensor for receiving signals from the digital gyroscope and outputting an angular position error signal. The stabilization system further comprises signal processing logic for receiving the error signal, and comparing the error signal to a reference signal and providing a stabilized image based upon that comparison, wherein the hard-coded logic, digital gyroscope and rate and position sensor resides on the same chip.
Owner:INVENSENSE
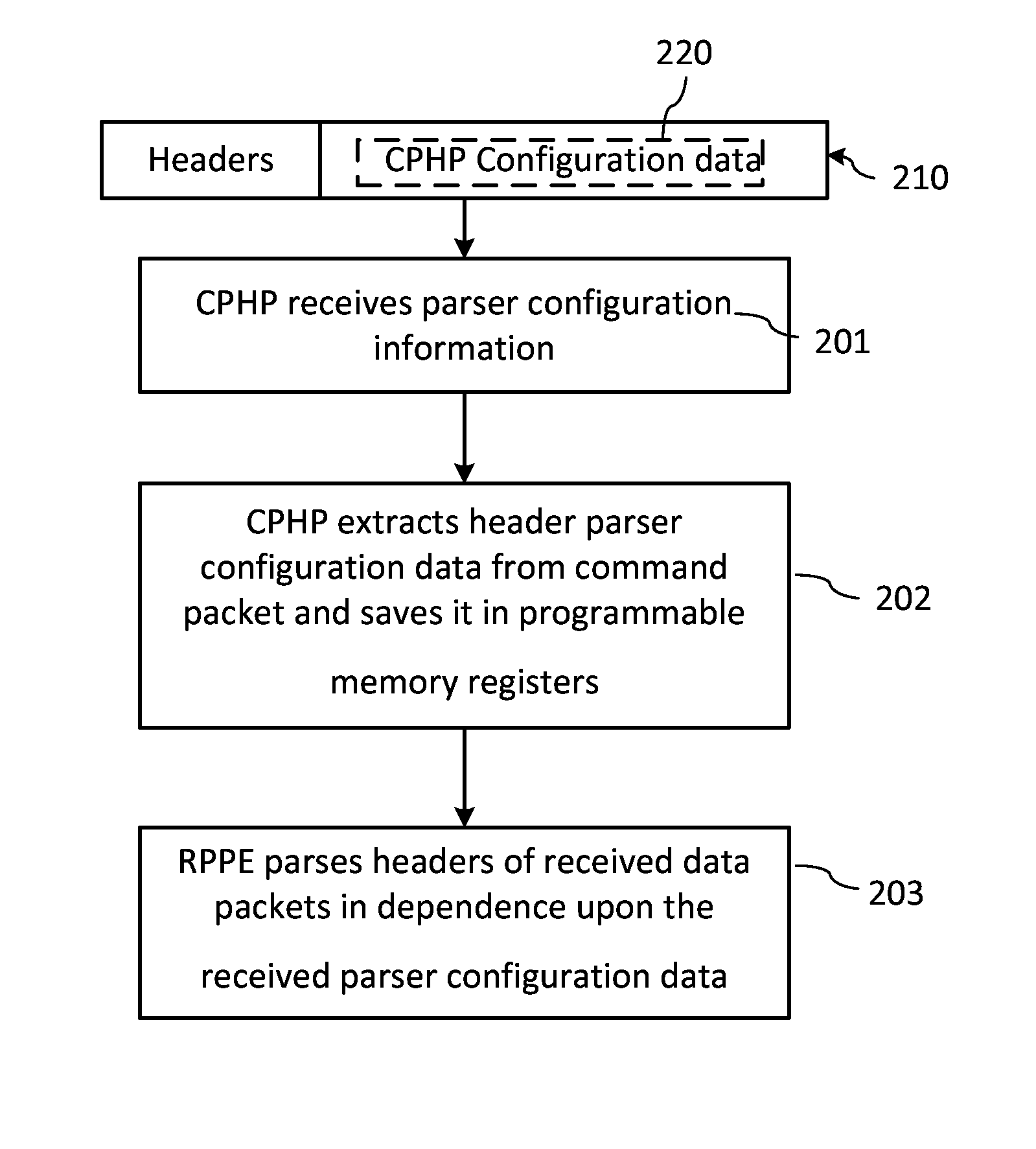
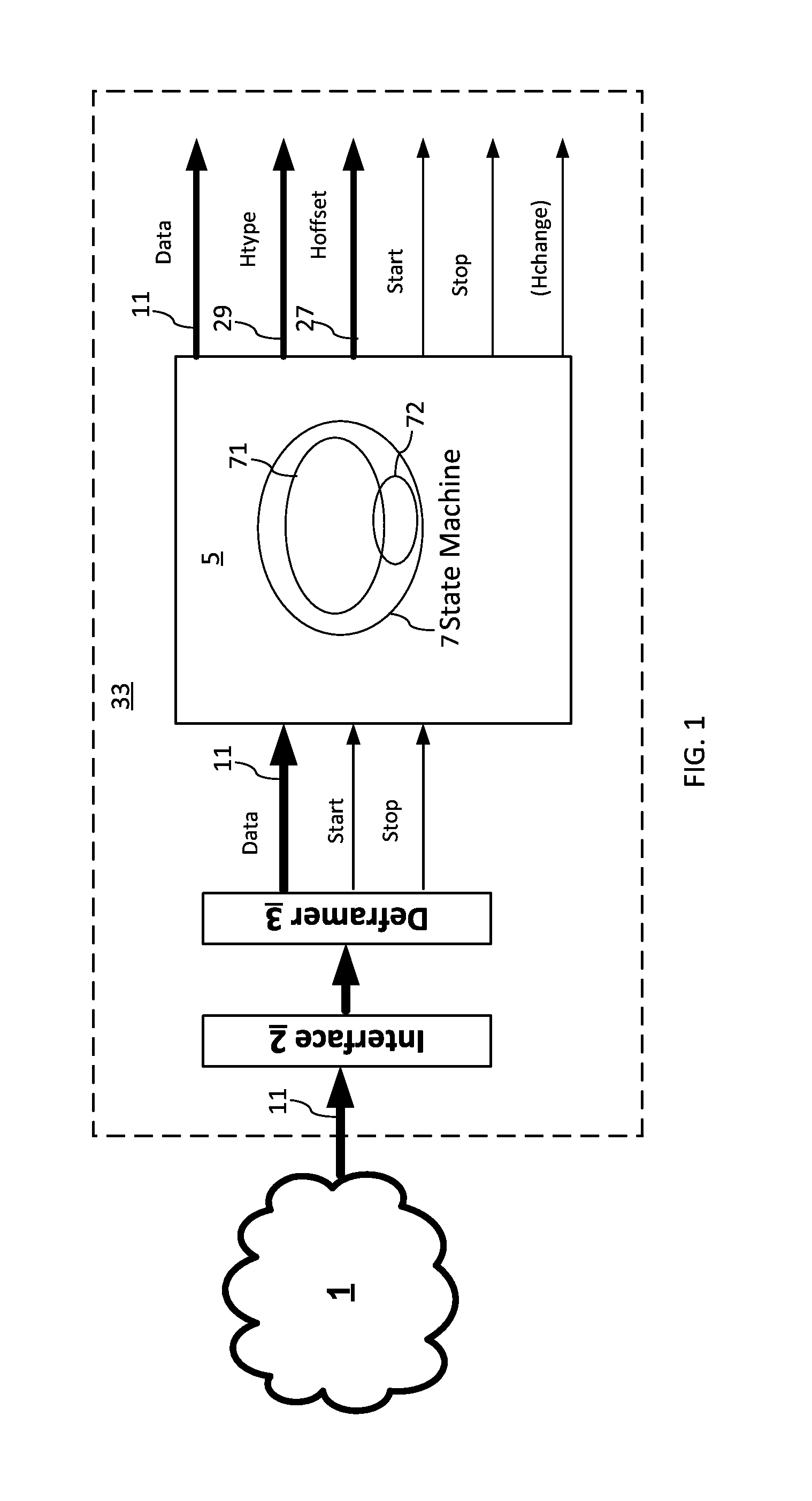
Reconfigurable packet header parsing
The invention relates to a method and device for configurable parsing of packet headers in a network. A configurable packet header parser (CPHP) includes hard-coded packet header logic implementing a hard-coded state machine and a reconfigurable header parsing logic that is coupled to the hardcoded logic and includes programmable registers. The CPHP is remotely programmable by means of a command packet parser that may receive command packets carrying CPHP configuration data and program the registers with the CPHP data to enable parsing packet including new types of headers. The hybrid hard-coded / programmable CPHP requires only a relatively small number of programmable elements enabling ASIC-based implementation.
Owner:VIAVI SOLUTIONS INC
System and method for providing dynamically authorized access to functionality present on an integrated circuit chip
ActiveUS20060059345A1Improve process capabilityInhibit involvementVolume/mass flow measurementUser identity/authority verificationComputer hardwareHard coding
A mechanism is provided in which access to the functionality present on an integrated circuit chip is controllable via an encrypted certificate of authority which includes time information indicating allowable periods of operation or allowable duration of operation. The chip includes at least one cryptographic engine and at least one processor. The chip also contains hard coded cryptographic keys including a chip private key, a chip public key and a third party's public key. The chip is also provided with a battery backed up volatile memory which contains information which is used to verify authority for operation. The certificate of authority is also used to control not only the temporal aspects of operation but is also usable to control access to certain functionality that may be present on the chip, such as access to some or all of the cryptographic features provided in conjunction with the presence of the cryptographic engine, such as key size.
Owner:IBM CORP
Fast inquiring method using dynamic inquiring language
ActiveCN103279509ASpeed up developmentQuick searchSpecific program execution arrangementsSpecial data processing applicationsHard codingData access
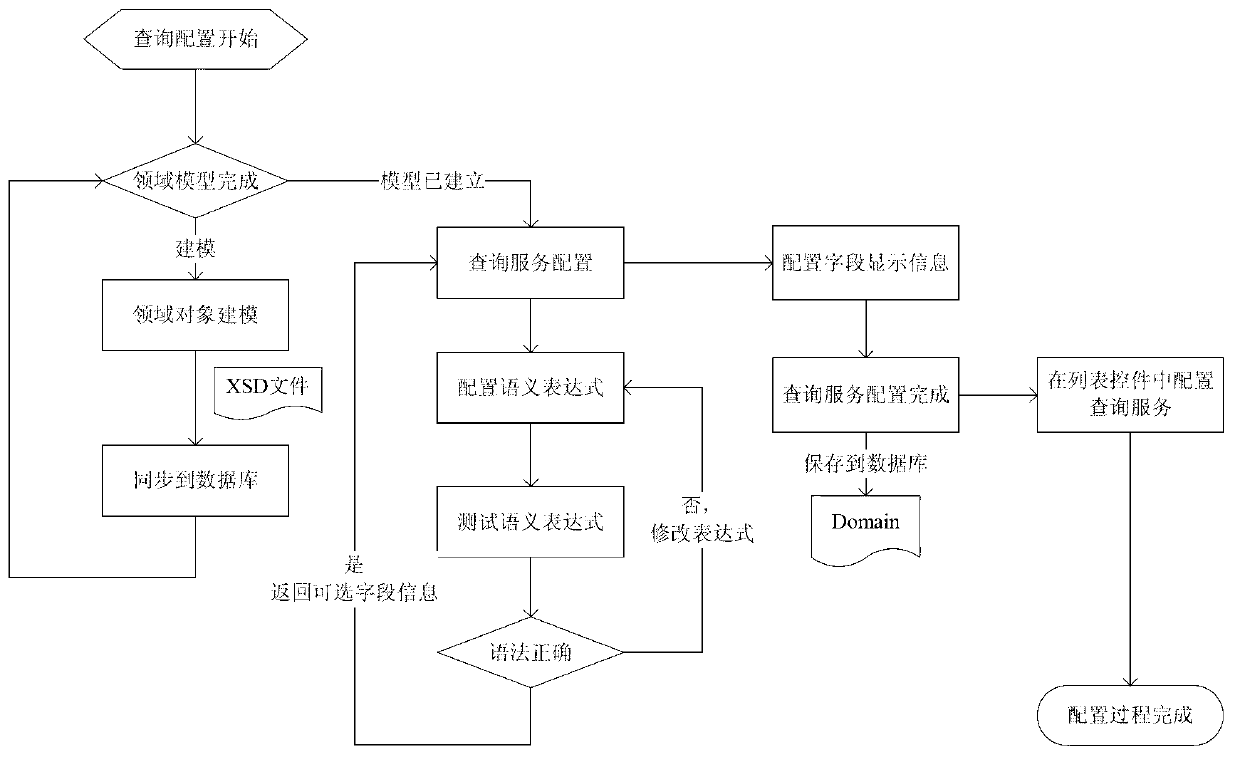
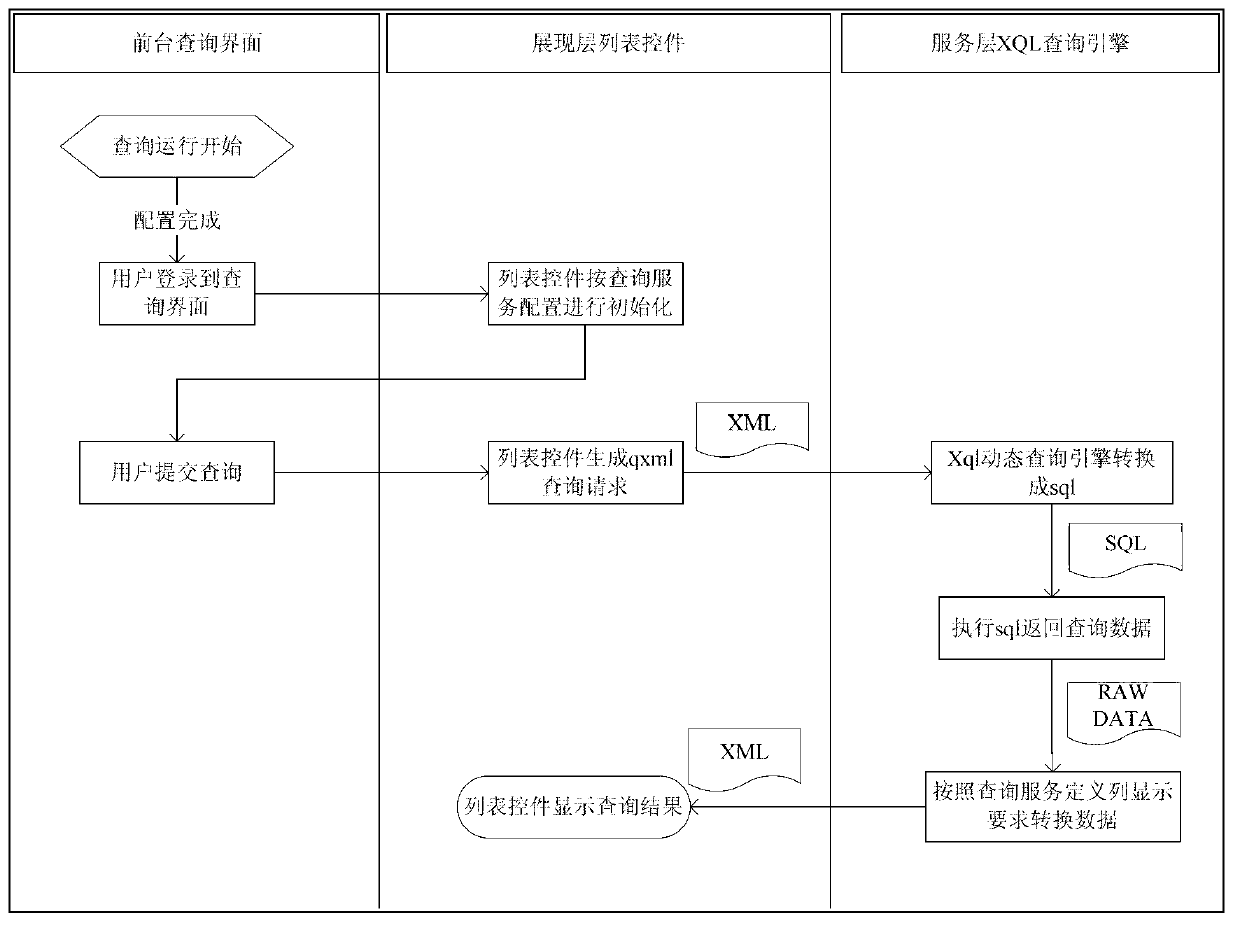
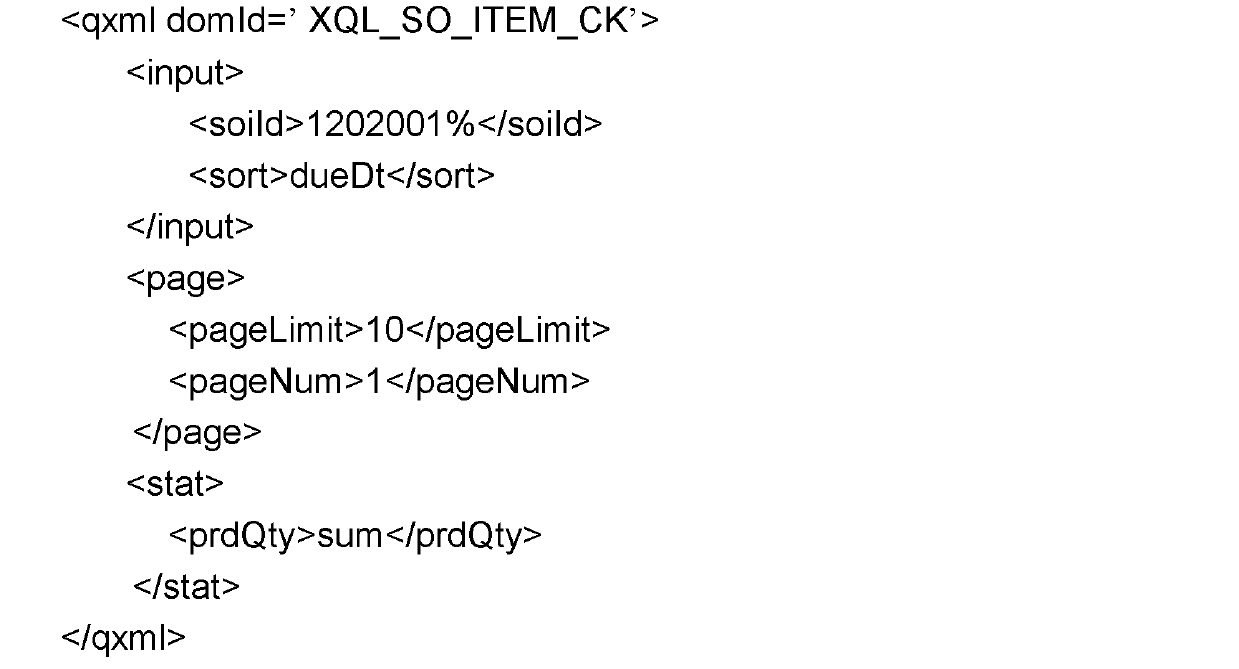
The invention discloses a fast inquiring method using a dynamic inquiring language, and belongs to the field of service system technology platforms. The fast inquiring method using the dynamic inquiring language achieves flexible and fast inquiring through field-object semanteme modeling and an XQL dynamic inquiring language data access mode. An XQL is a dynamic analysis language which is independently innovated and invented and is used for describing Xsd semanteme. Taking material inquiring as an example, when needing to inquire the information of a material according to the number of the material, a user just needs to write / mat[matId=#matId]. If also wanting to see order information of the material, the user just needs to modify the expression to be / mat[matId=#matId] / +po, and accordingly requirements can be met. The fast inquiring method using the dynamic inquiring language has the advantages of abandoning a previous multi-layer hard-coded inquiring achieving mode and meeting flexible, efficient and fast inquiring requirements of the user through an inquiring engine and configuration mode.
Owner:BEIJING SHOUGANG AUTOMATION INFORMATION TECH
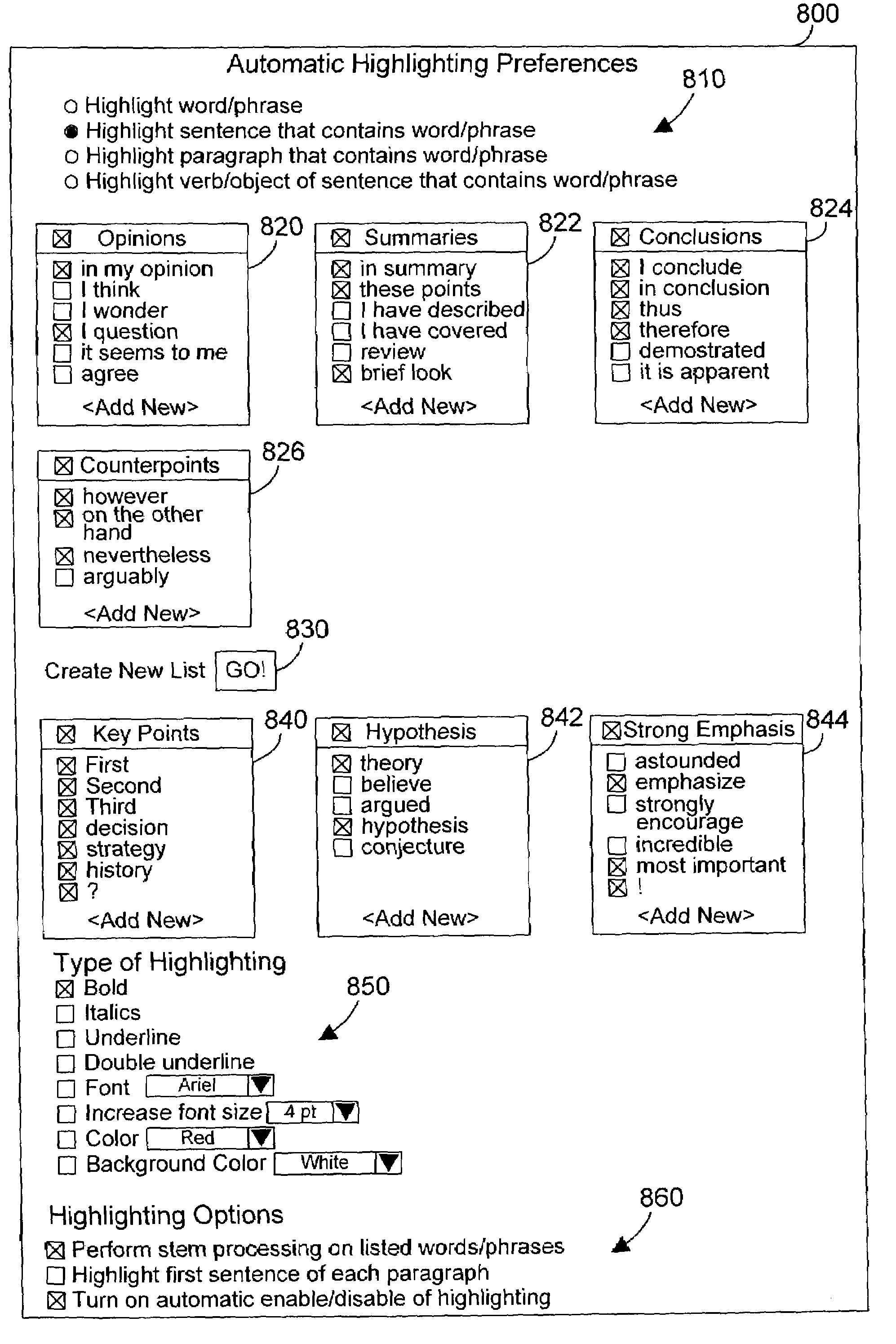
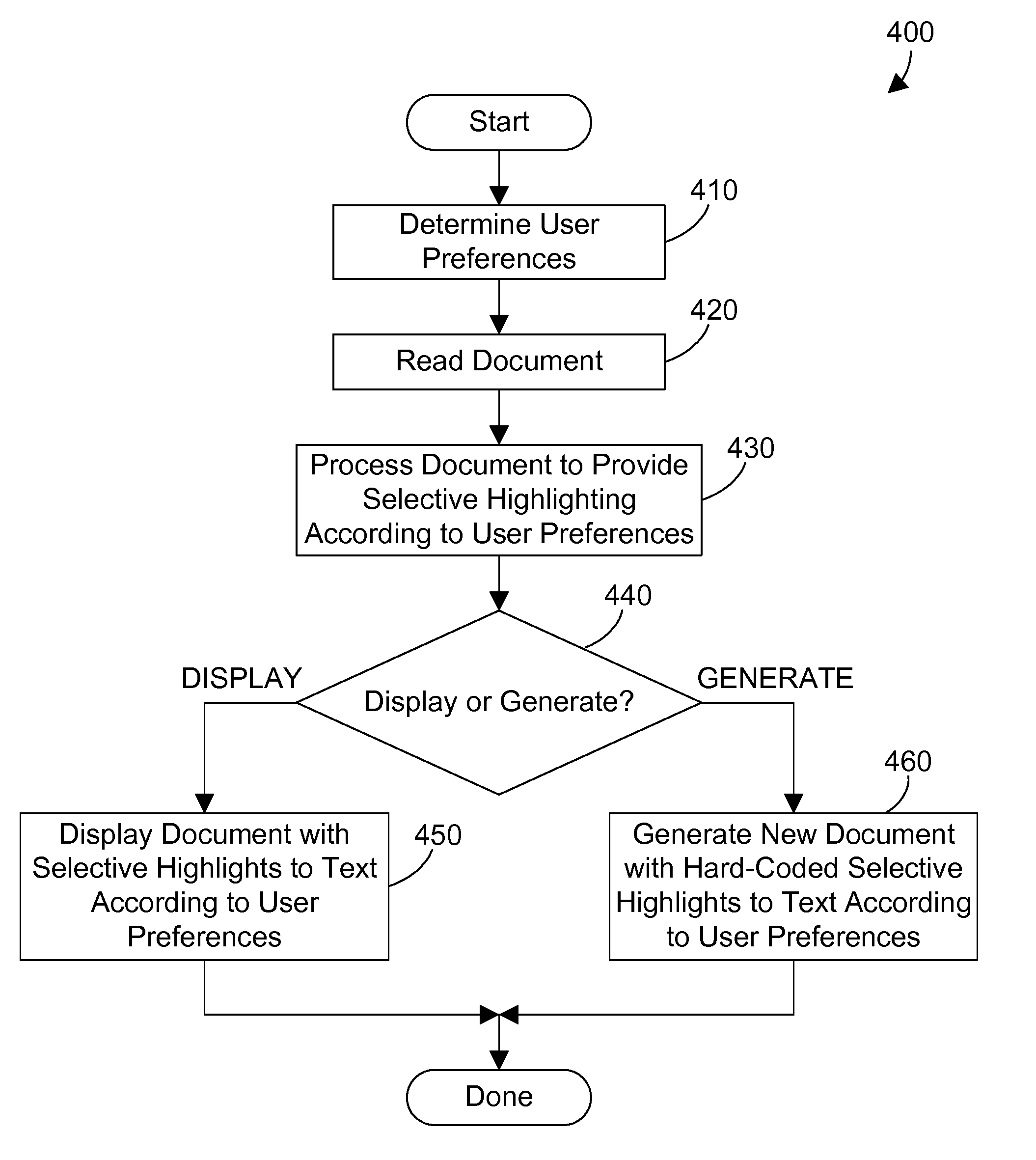
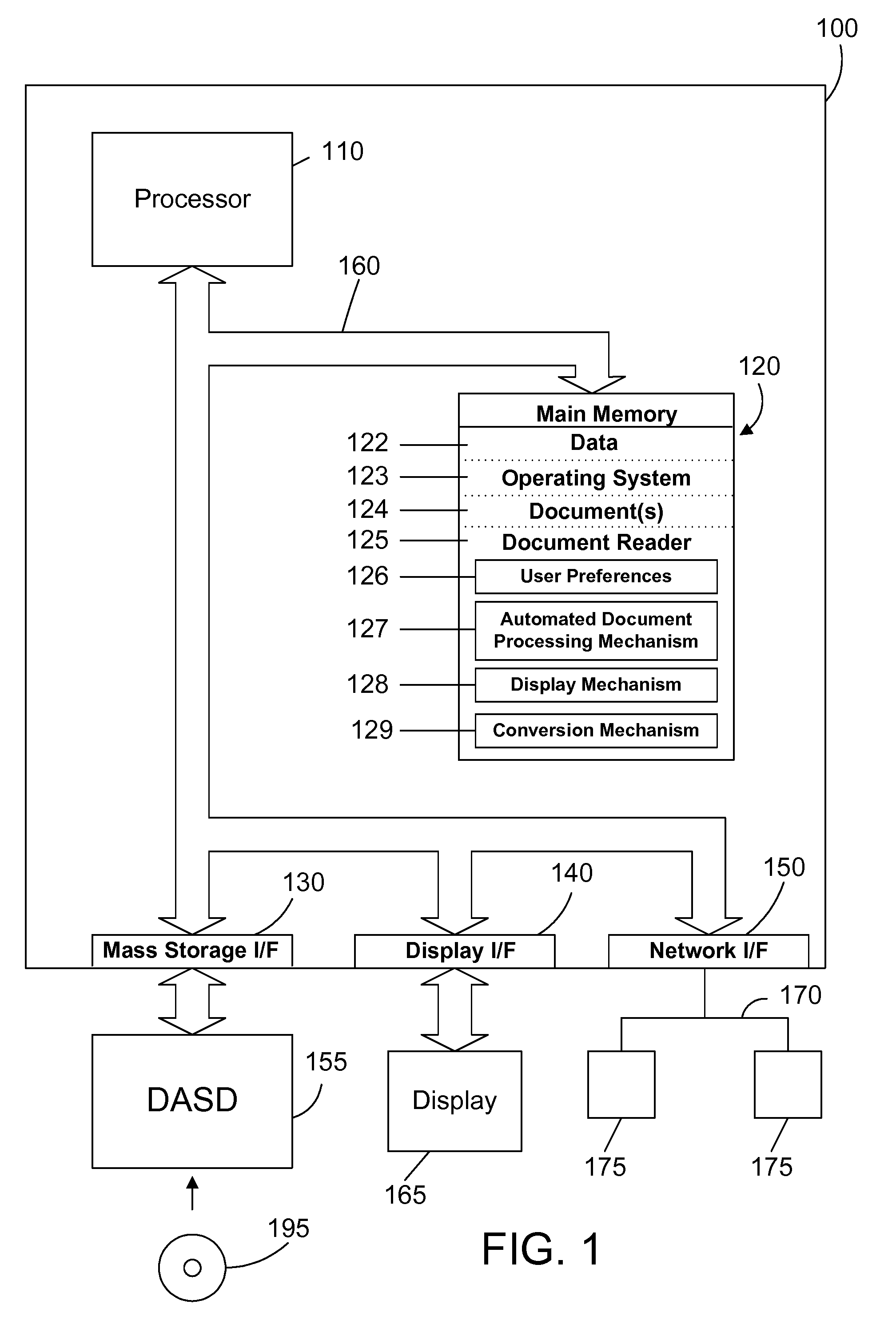
Apparatus and method for automatically highlighting text in an electronic document
InactiveUS7194693B2Enhance and alter appearanceCathode-ray tube indicatorsSpecial data processing applicationsHard codingElectronic document
An apparatus and method helps a user to determine parts of an electronic document that are of interest by allowing the user to define preferences for processing an electronic document, and by automatically highlighting one or more portions of the document according to the user preferences. Highlighting includes any way to enhance or alter the appearance of text, including bold, italics, underlining, change in font style, change in font size, change in color, change in background color, etc. The automatic highlighting of portions of the document attract the user's eyes to that portion of the document, which helps the user to discern whether or not the highlighted portion is relevant or interesting. The preferred embodiments also include a document generator that takes an input document and generates therefrom an output document that has one or more highlighted portions that are hard-coded into the document according to the user preferences. The preferred embodiments further include the ability to automatically enable or disable the highlighting of a document according to characteristics of the electronic document, or the user's actions (such as the speed of scrolling through a document). In addition, the preferred embodiments include markup language tags that allow an author of a document to define portions of interest that may be highlighted when highlighting is enabled.
Owner:INT BUSINESS MASCH CORP
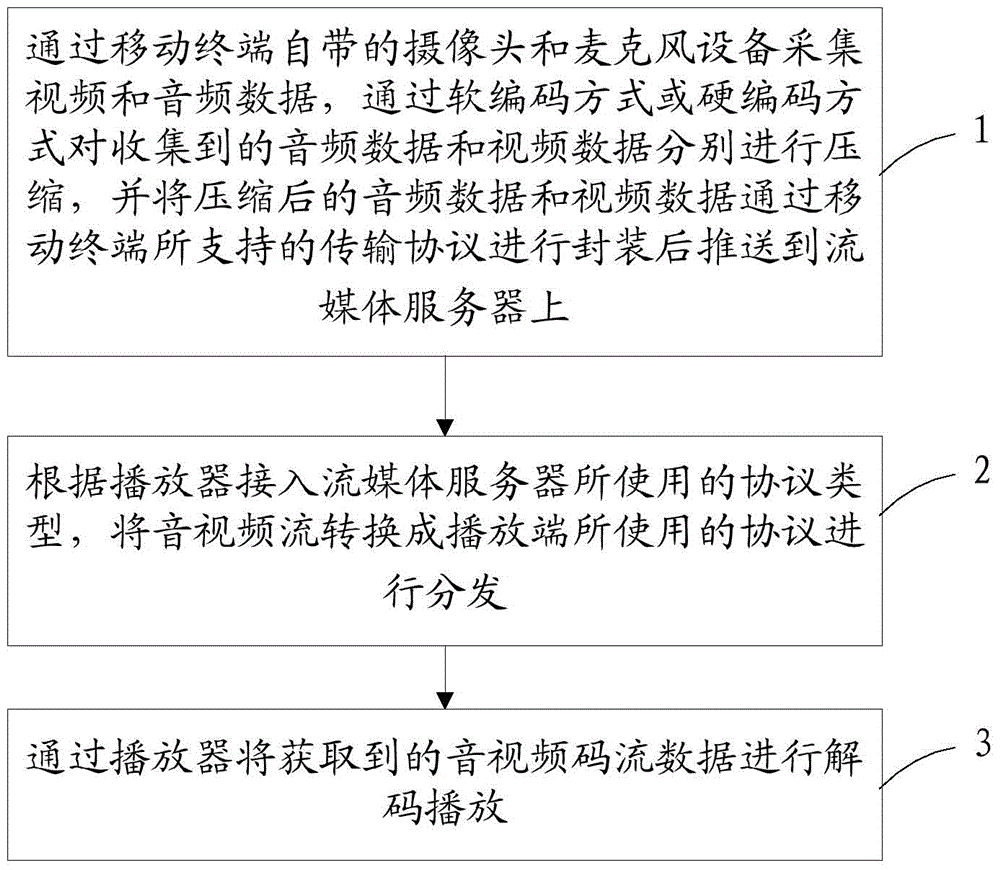
Method and system for live broadcast of mobile terminal
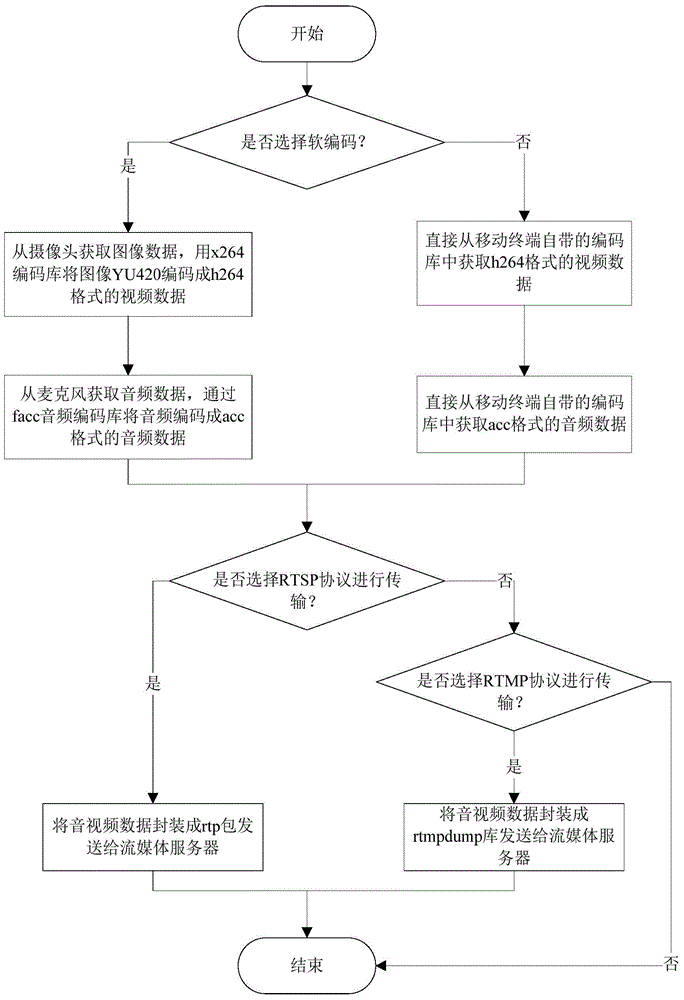
ActiveCN105025327ADoes not affect running speedLow costSelective content distributionHard codingVideo streaming
The invention provides a method for live broadcast of a mobile terminal, and a streaming media server which supports multiple protocols and a players used for playing network video streaming on a mobile device need to be provided, wherein the player is developed based on an open source playing VLC multimedia player. The method includes: Step 1. collecting video and audio data through the mobile terminal, compressing the collected audio data and video data through soft coding mode or a hard coding mode, and after packaging the compressed audio and video data through a protocol that the mobile terminal supports, pushing to the streaming media server; Step 2. according to the type of the protocol used when a player is accessed to the streaming media server, converting audio and video streaming to the protocol used by the player to be distributed; and Step 3. decoding and playing audio and video code steam data through the player. The invention also provides a system for live broadcast of the mobile terminal, and the system supports a dual-coding mode and multi-protocol transmission of data and realizes video collection and live broadcast on the mobile terminal.
Owner:中电福富信息科技有限公司
Object relational mapping method and device as well as processor
ActiveCN104899225ARealize dynamic assemblyEasy maintenanceSpecial data processing applicationsHard codingMultiplexing
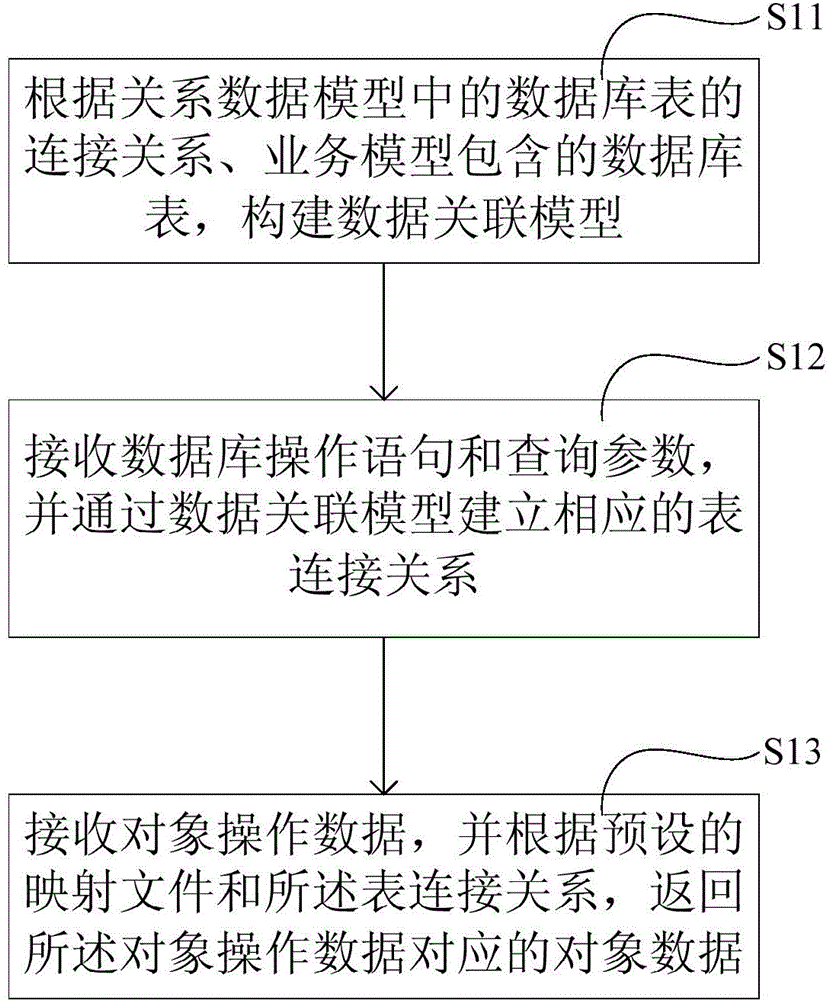
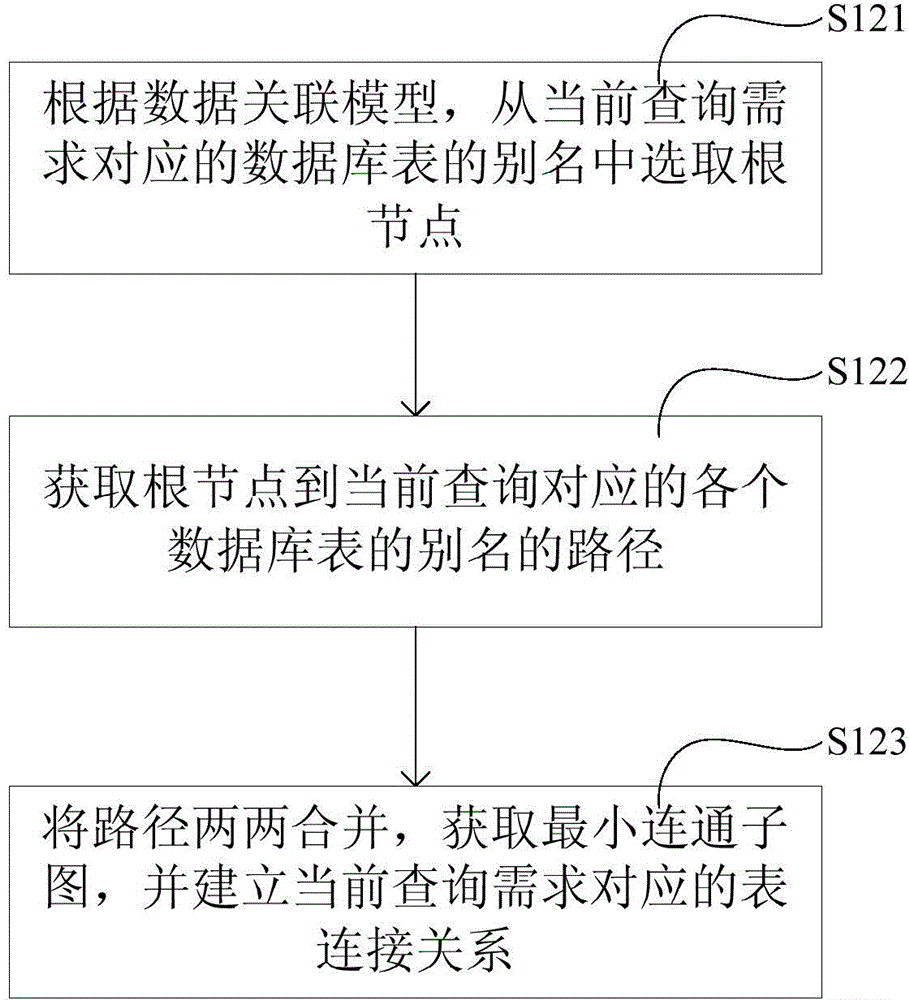
The present invention discloses an object relational mapping method and device as well as a processor. According to the method, when data in a database table are required to be queried, an alias name of the database table corresponding to a current query and a physical field of the database table are determined according to received database operation statements and query parameters, and a corresponding table connection relationship is constructed; and then corresponding object data are returned according to received object operation data and a preset mapping relationship. The method achieves object relational mapping, can be applied to a complicated data model and is used for solving the problem of confused coding in the existing hard coding technology; in addition, according to the object relational mapping method disclosed by the present invention, current query conditions and table connection relationships can be assembled according to object data and mapping files, so that the flexibility is high, and the degree of multiplexing is high.
Owner:北京国资融资租赁股份有限公司
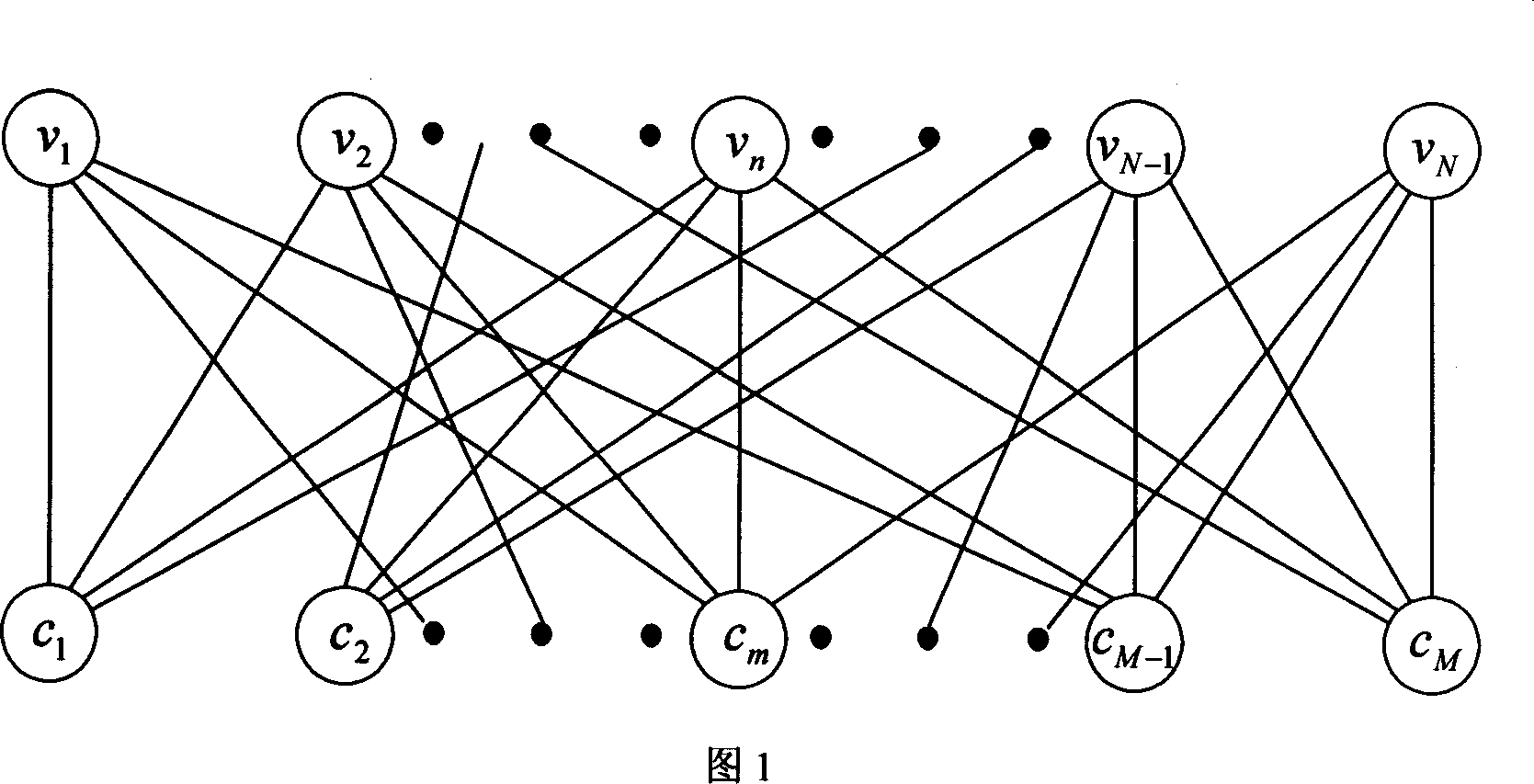
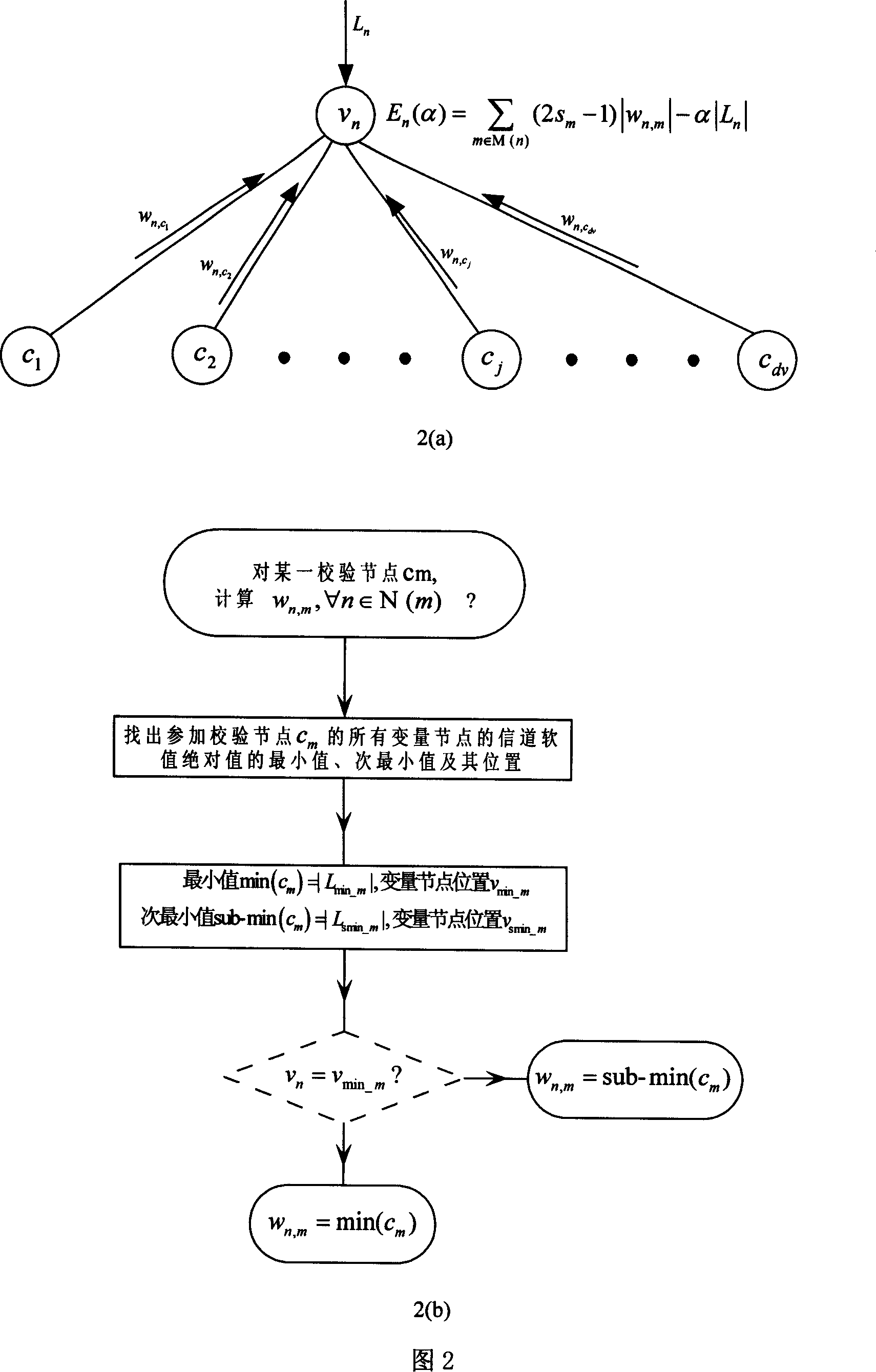
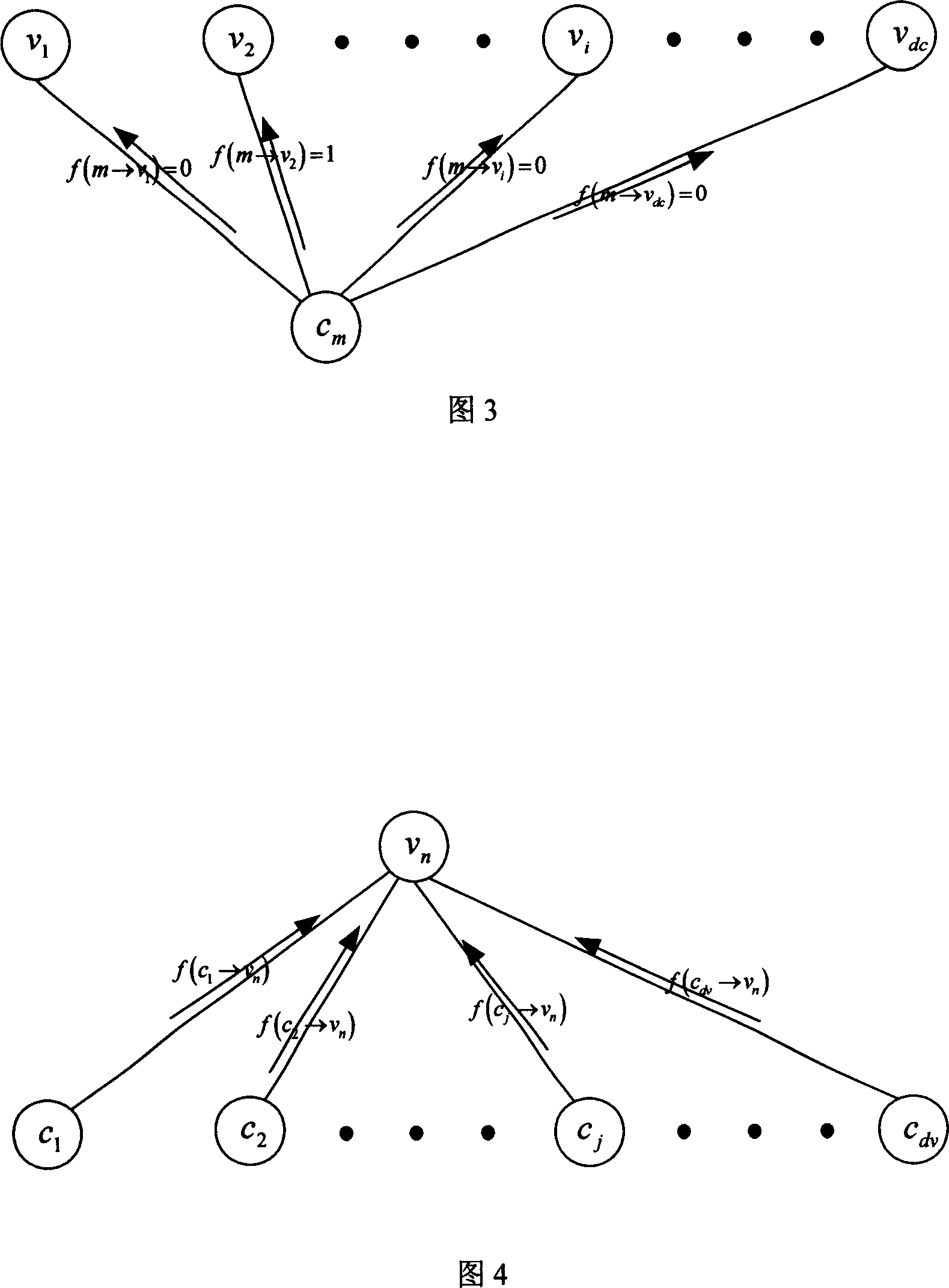
Parallel weighting bit upturn decoding method of low density check code
InactiveCN101018060ADecoding convergence speed improvedOverall Computational Complexity ReductionError correction/detection using multiple parity bitsCode conversionHard codingLow-density parity-check code
Compared with prior art, the parallel-WBF coding method for soft decision coding on LDPC improves convergence speed greatly, and comprises exactly: hard deciding received signal to obtain a hard-decision code and try to decide whether it satisfies all check relation, yes to end; or else, to any failure node, finding out the variable node with the largest WBF decision, and sending unique signal to this node; then, counting signal quantity, selecting all nodes whose signal quantity over a threshold, taking parallel WBF to the position of hard-code; updating the hard-code, going to next iteration.
Owner:SOUTHEAST UNIV
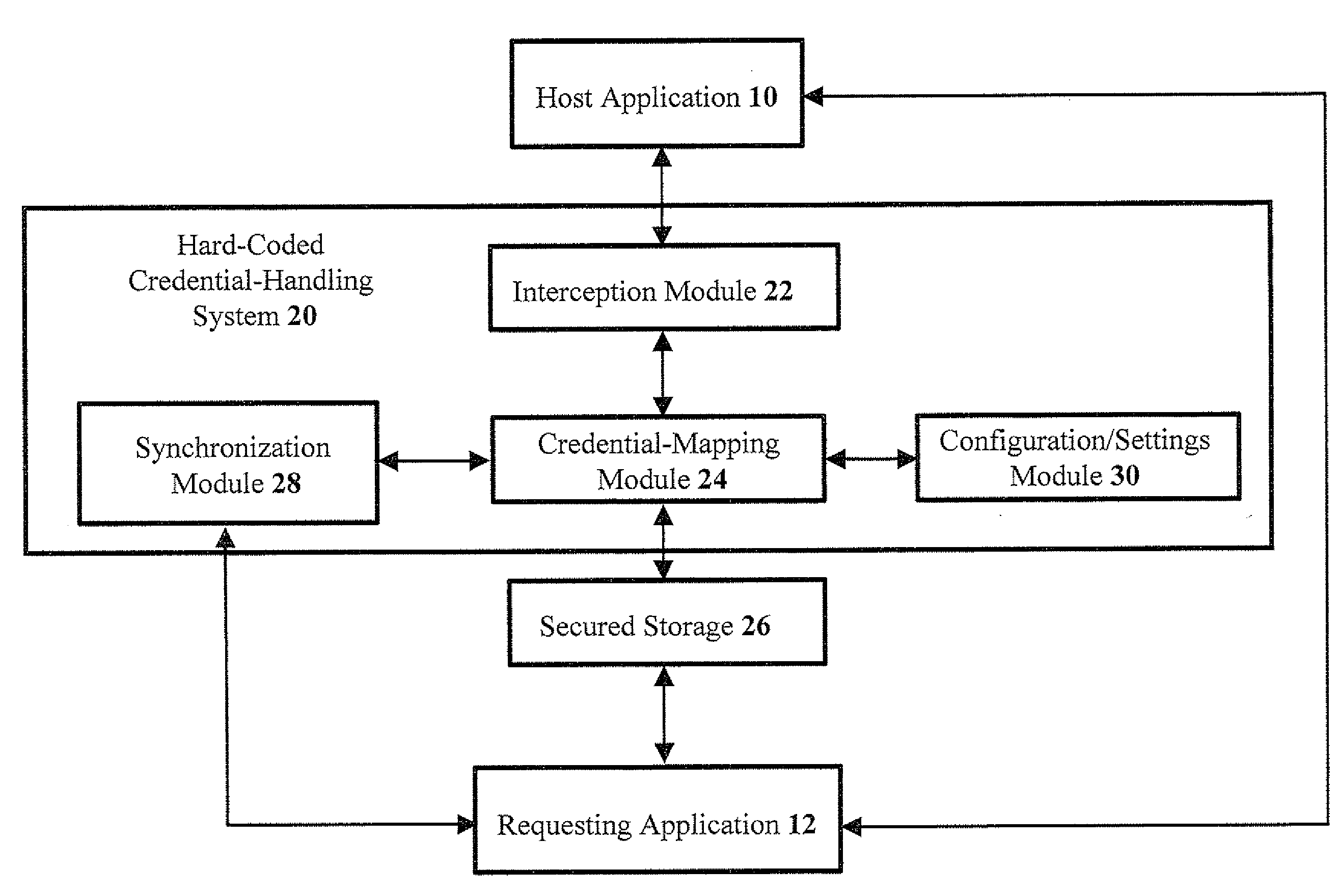
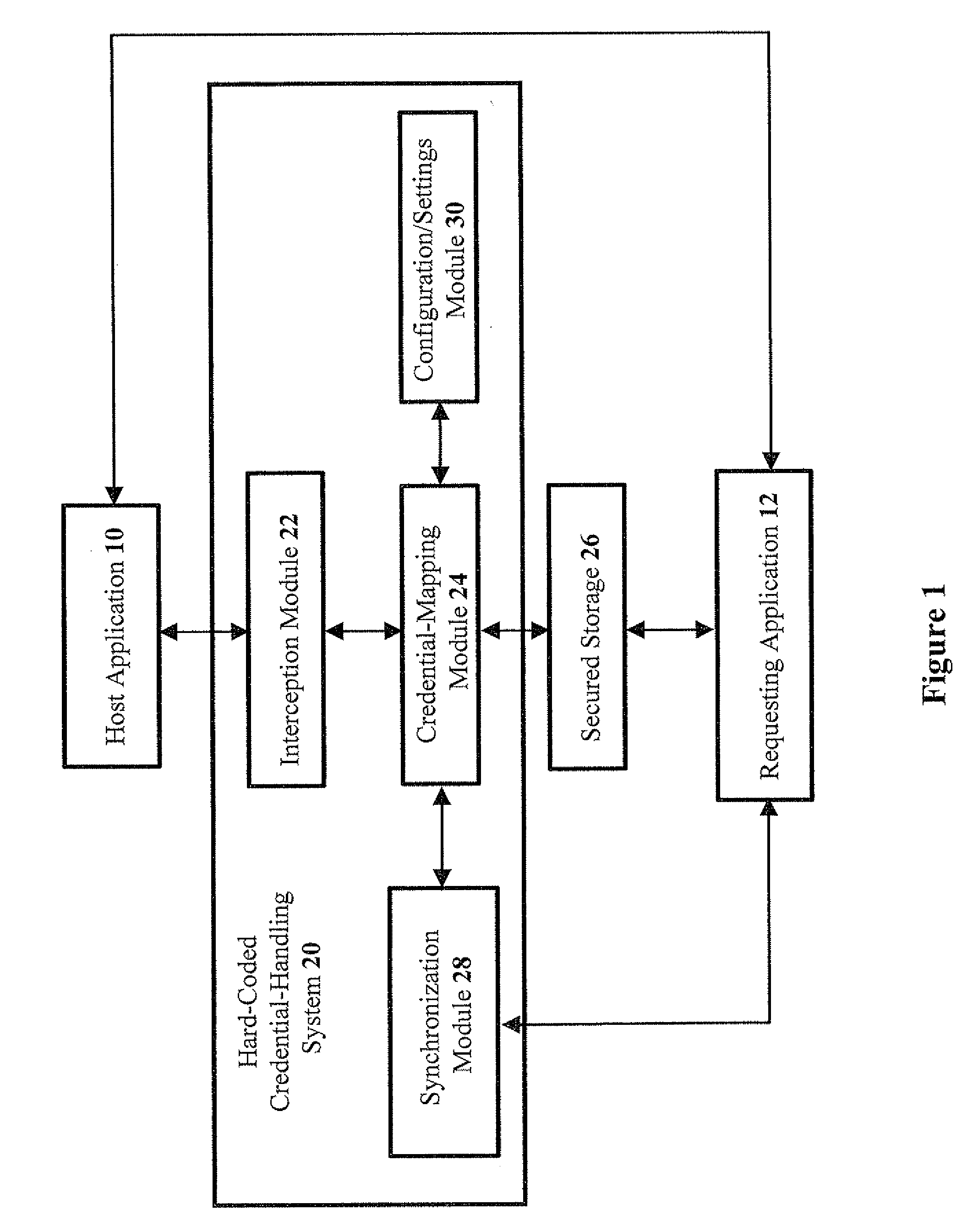
Methods and systems for solving problems with hard-coded credentials
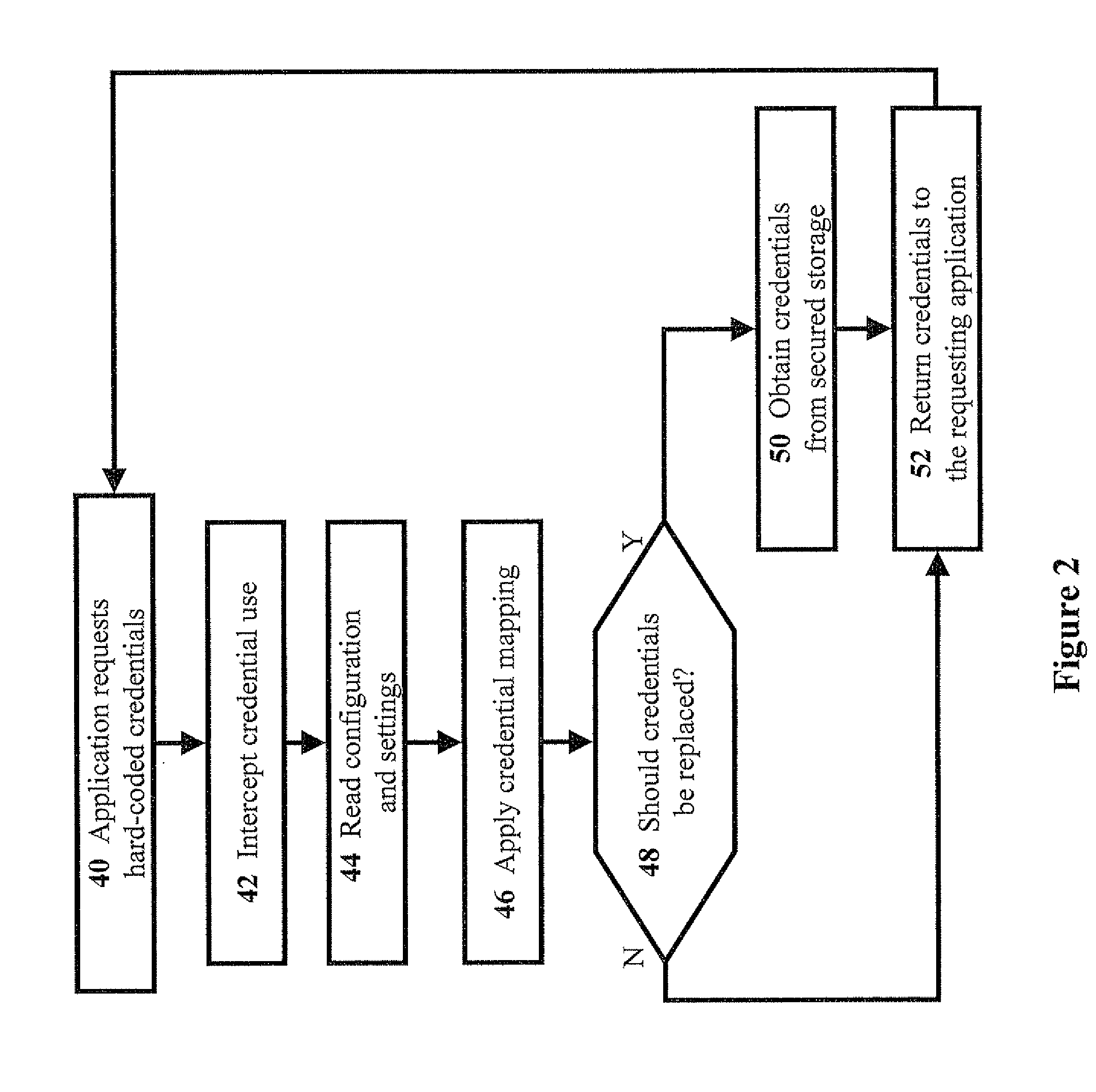
ActiveUS20080196101A1Reduce operating costsEliminate useMemory loss protectionDigital data processing detailsHard codingSystem configuration
The present invention discloses methods, media, and systems for handling hard-coded credentials, the system including: an interception module configured for: intercepting credential usage upon receiving an application request for application credentials in order to provide access to a host application; a configuration / settings module configured for reading system configurations and settings for handling the application credentials; a credential-mapping module configured for: applying appropriate credential-mapping logic based on the system configurations and settings; and upon determining that the application credentials need to be replaced, obtaining appropriate credentials from a secured storage. Preferably, the interception module is further configured for: prior to the intercepting, hooking a connection API of the host application upon access of a credential location in which the application credentials are stored; and wherein the credential-mapping module is further configured for: subsequent to the hooking, using the appropriate credentials to connect the host application with the connection API.
Owner:CYBER ARK SOFTWARE
Apparatus and method for automatically highlighting text in an electronic document
InactiveUS20070061717A1Enhance and alter appearanceCathode-ray tube indicatorsSpecial data processing applicationsElectronic documentHard coding
An apparatus and method helps a user to determine parts of an electronic document that are of interest by allowing the user to define preferences for processing an electronic document, and by automatically highlighting one or more portions of the document according to the user preferences. Highlighting includes any way to enhance or alter the appearance of text, including bold, italics, underlining, change in font style, change in font size, change in color, change in background color, etc. The automatic highlighting of portions of the document attract the user's eyes to that portion of the document, which helps the user to discern whether or not the highlighted portion is relevant or interesting. The preferred embodiments also include a document generator that takes an input document and generates therefrom an output document that has one or more highlighted portions that are hard-coded into the document according to the user preferences.
Owner:CRAGUN BRIAN JOHN +1
Customizing a client application using an options page stored on a server computer
InactiveUS7321917B2Natural language data processingMultiple digital computer combinationsHard codingClient-side
A method and apparatus for displaying an options page for client application in a network environment. Instead of hard coding the options page within the client application, the options page is stored on a server computer and may be updated dynamically without modifying the client application. In one aspect, the user requests to view the options page using menu commands generated by the client application. In response to the user request, the client application launches a browser, if needed, and passes the current settings for the options page to the browser along with an address pointing to the location of the options page on a server computer. The browser connects to the server computer specified in the URL, requests the page associated with the address, and passes the user settings to the server computer. The server computer generates a current version of the options page, initializes the options page by applying the user settings to the options page, and downloads the options page to the browser for display. In another aspect, the user makes changes to the options page in the browser to customize the client application. The browser sends the changes to the server and the server returns the changes to the browser as a special file type. The browser uses a helper function to handle the special file type and launches an application that saves the user settings on the client computer.
Owner:NBCUNIVERSAL
Self-optimizable code
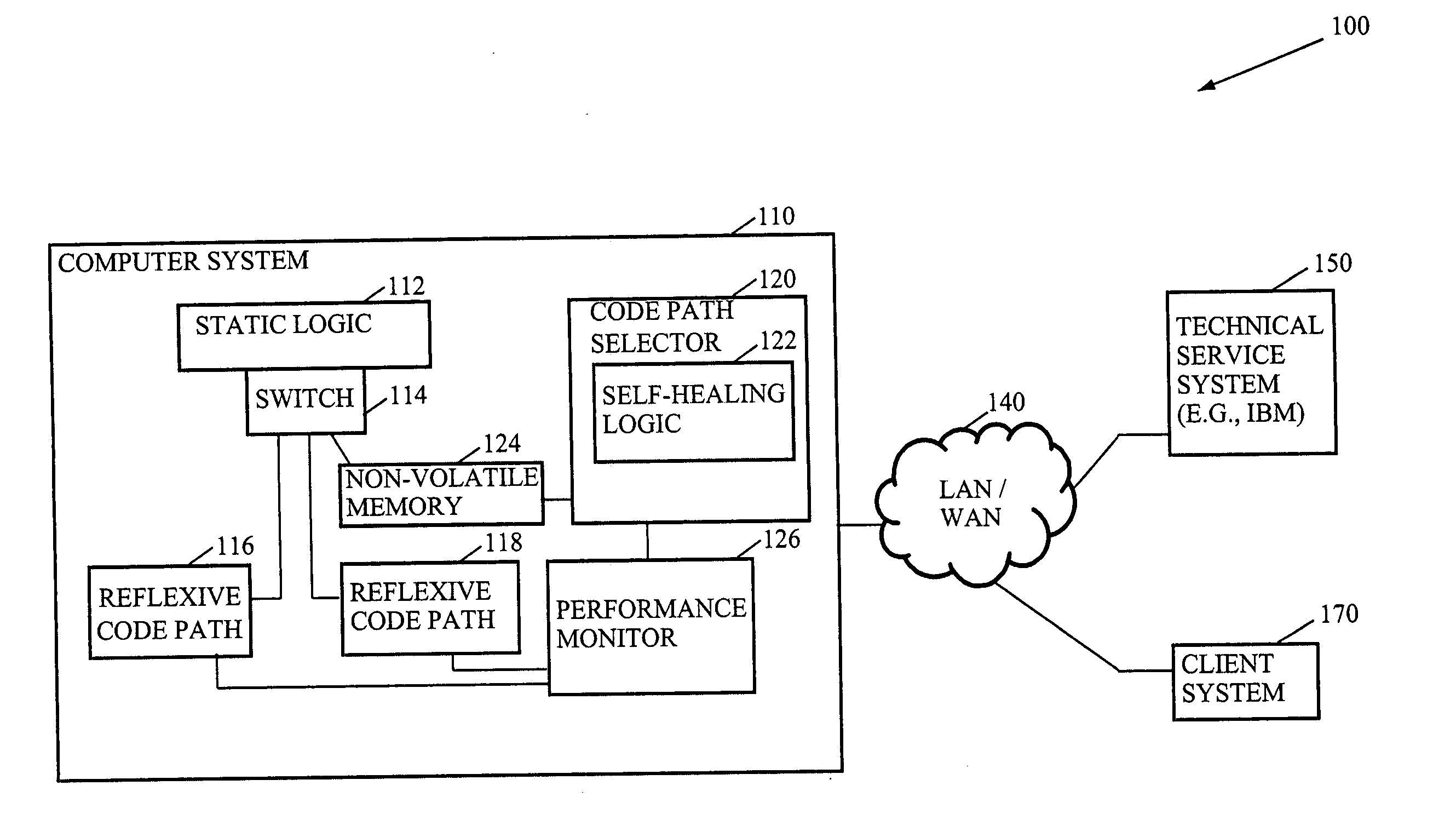
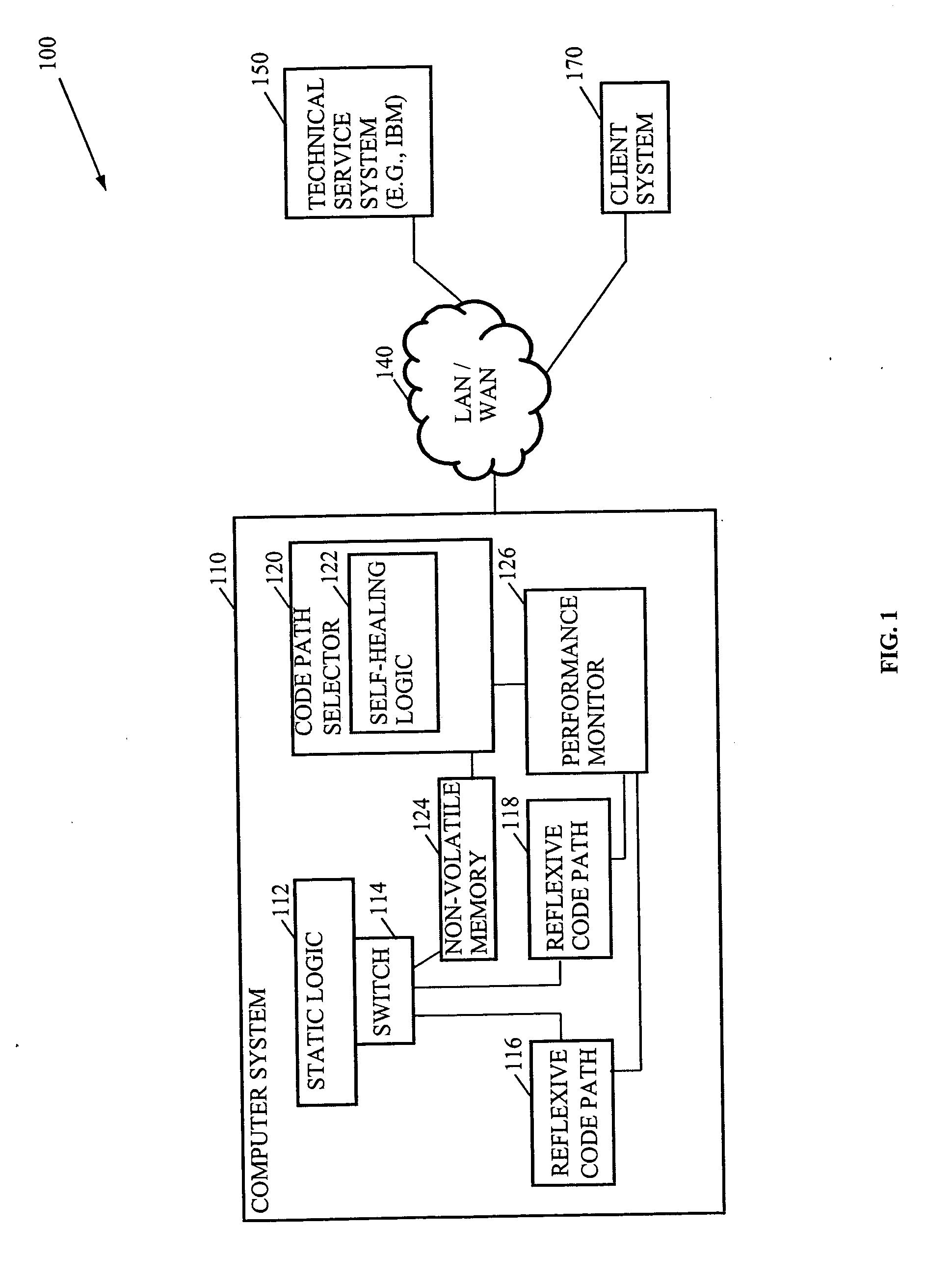
InactiveUS20060053421A1Improve task efficiencyError detection/correctionMultiprogramming arrangementsHard codingParallel computing
Methods, systems, and media to increase efficiency of tasks by observing the performance of generally equivalent code paths during execution of the task are disclosed. Embodiments involve a computer system with software, or hard-coded logic, that includes reflexive code paths. The reflexive code paths may be identified by a software or hardware designer during the design of the computer system. For that particular computer system, however, one of the code paths may offer better performance characteristics so a monitor collects performance data during execution of the reflexive code paths and a code path selector selects the reflexive code with favorable performance characteristics. One embodiment improves the performance of memory allocation by selectively implementing a tunable, linear, memory allocation module in place of a default memory allocation module.
Owner:IBM CORP
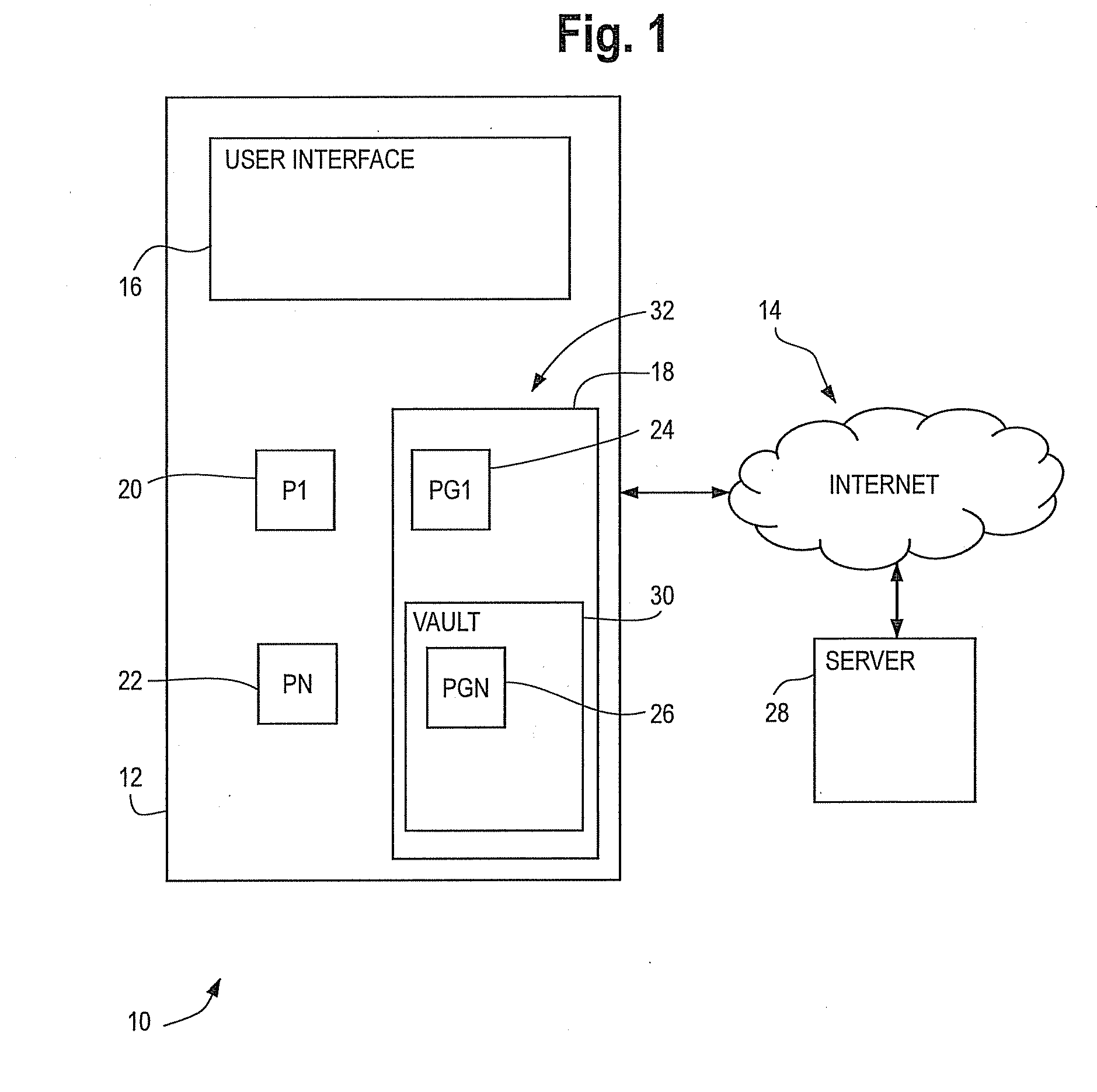
Mobile data vault
A portable electronic device is provided. The portable electronic device includes a data interface module that processes files associated with a user, the data interface module receives and validates a password from a user of the portable electronic device before the user is allowed access to files processed by the data interface module, an encryption key formed by the data interface module upon validation of the password, the encryption key further comprising the password, a hard coded private string and a serial number of the portable electronic device and a data storage area that stores files received from the data interface module the stored files are encrypted using the encryption key and where neither the encryption key or the password are stored in an unencrypted format anyplace within the portable electronic device.
Owner:PERKAUS & FARLEY L L C +1
Electronic table general-purpose data parsing and leading-in method
InactiveCN101452441AAvoid mappingAvoid processing powerSpecial data processing applicationsGeneral purposeHard coding
Owner:INSPUR SOFTWARE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com