WASM smart contract vulnerability detection method based on symbolic execution
A smart contract and symbolic execution technology, applied in the direction of error detection/correction, software testing/debugging, program code conversion, etc., can solve the problem that the system cannot be guaranteed to be completely correct and reliable, and achieve the effect of improving the efficiency of vulnerability detection and facilitating subsequent expansion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be further described in detail below in conjunction with the accompanying drawings.
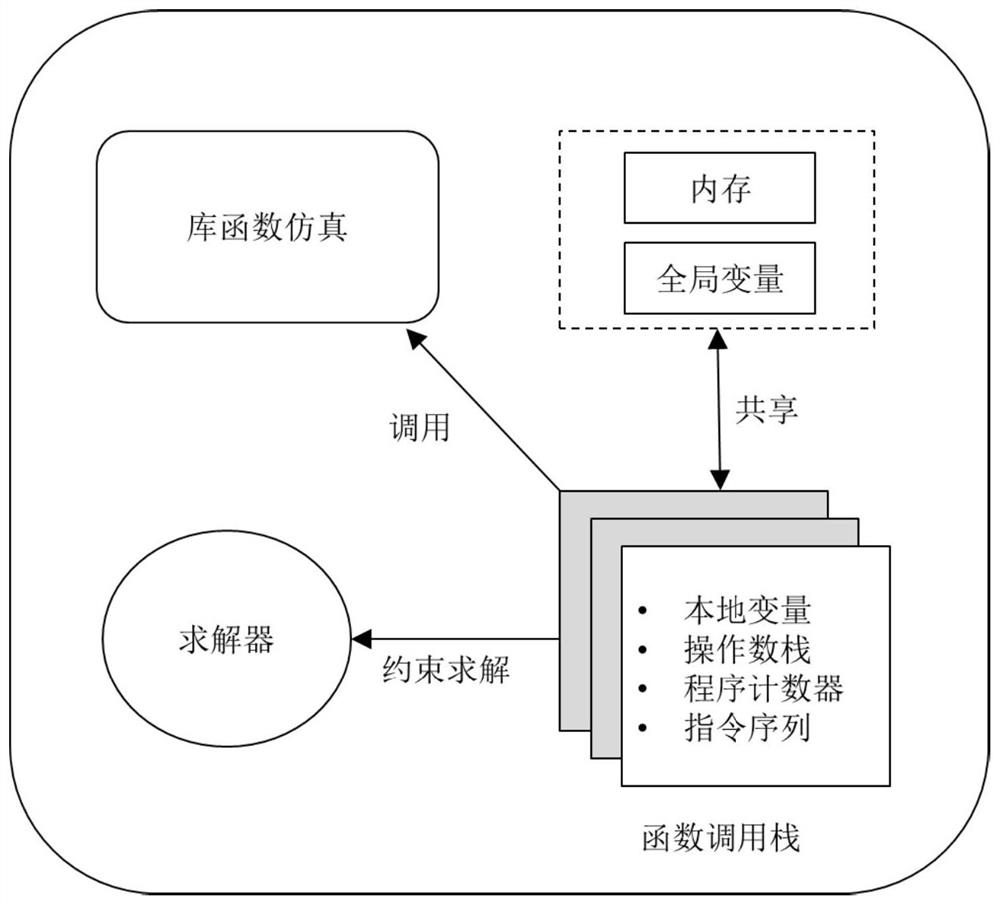
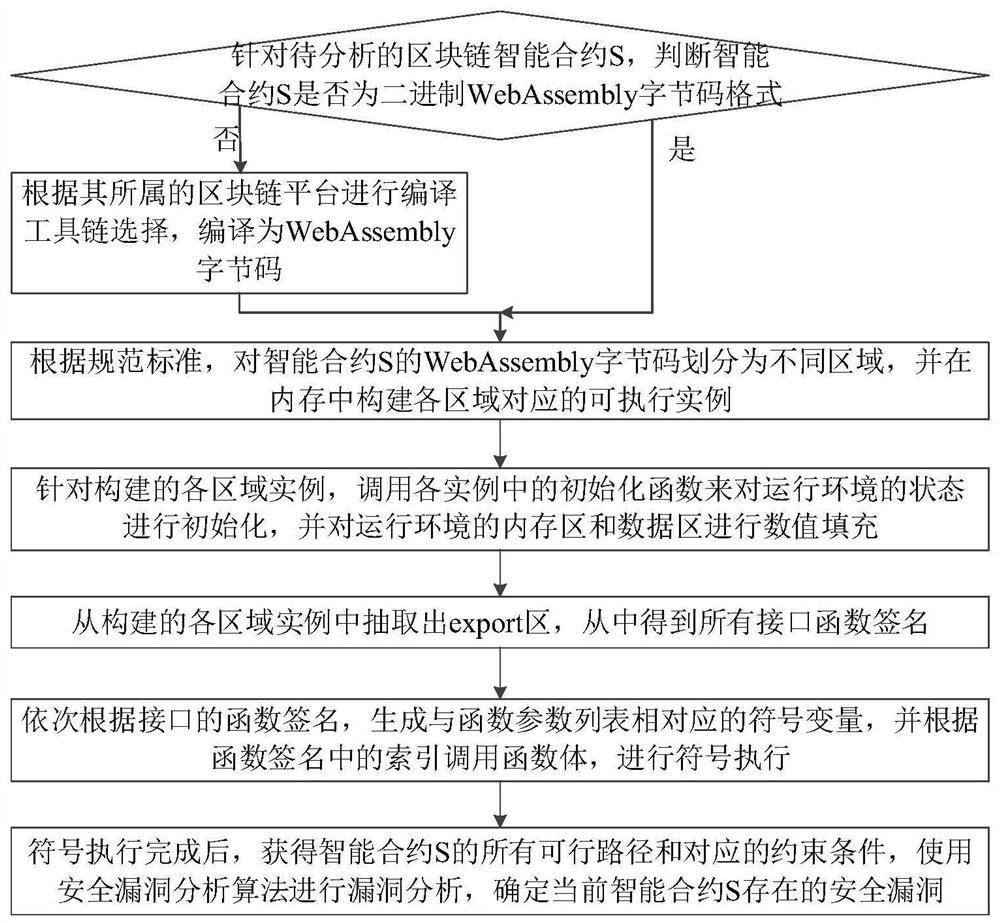
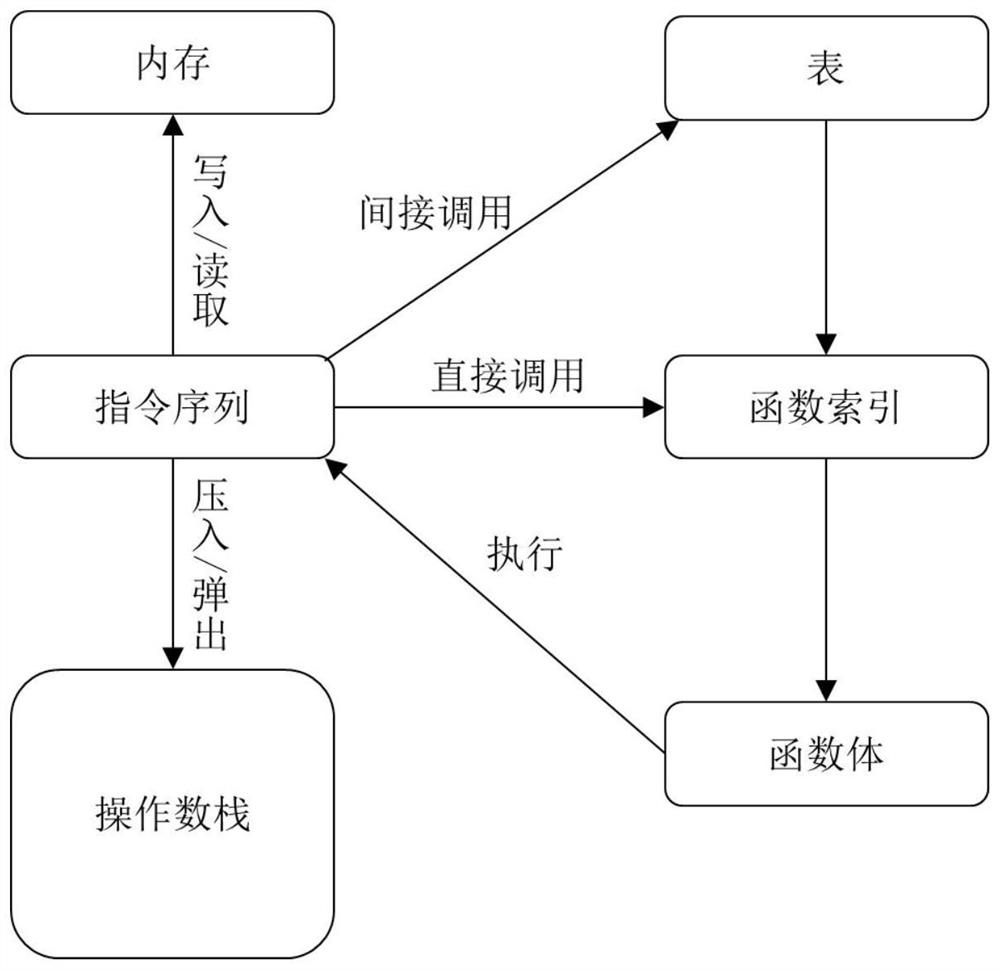
[0058] Based on the symbolic execution technology in software testing, the present invention provides conditions for the detection and location of security vulnerabilities in blockchain smart contracts. The basic principles are as follows: figure 1As shown, the symbolic execution engine is mainly composed of four parts: function call stack, execution environment (including memory and global variables), library function simulation and solver. What the symbolic execution engine processes is WebAssembly bytecode. After parsing the bytecode, an executable instance is generated, and the symbolized variables are recorded and executed symbolically. Symbolic execution starts from the entry function of the bytecode. The engine will create a function call stack and push the function call information into the stack. The contents of the stack frame include local variable...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com